Canaux
108470 éléments (108470 non lus) dans 10 canaux
 Actualités
(48730 non lus)
Actualités
(48730 non lus)
 Hoax
(65 non lus)
Hoax
(65 non lus)
 Logiciels
(39066 non lus)
Logiciels
(39066 non lus)
 Sécurité
(1668 non lus)
Sécurité
(1668 non lus)
 Referencement
(18941 non lus)
Referencement
(18941 non lus)
éléments par Ian Barker
BetaNews.Com
-

Security operations centers face high levels of staff turnover
Publié: août 29, 2019, 2:59pm CEST par Ian Barker
New research from managed detection and response company CRITICALSTART finds that security operations center (SOC) analysts are being overwhelmed by alerts and this is leading to high rates of analyst turnover. In the past year, 80 percent of respondents reported SOC turnover of more than 10 percent of analysts, with nearly half reporting between 10 and 25 percent turnover. 35 percent report losing a quarter or more of their SOC analysts in under a year. The number of alerts is increasing, with 70 percent of respondents investigating 10 or more alerts each day (up from 45 percent last year) while… [Continue Reading] -

Only a quarter of UK firms prioritize security when buying new tech
Publié: août 28, 2019, 3:51pm CEST par Ian Barker
Only 24 percent of organizations are prioritizing security when it comes to technology investment according to a new report from UK-based software company Advanced. For the report the company surveyed over 500 senior decision makers working in UK businesses, both SMEs and large enterprises, to explore the state of digital transformation. It shows that just 34 percent admit that regulatory change is triggering the purchase of new technology in their organisation, which is surprisingly low given the introduction of GDPR in May last year. Justin Young, director of security and compliance at Advanced says: The GDPR should have been a… [Continue Reading] -

New solution delivers improved website defenses
Publié: août 28, 2019, 3:00pm CEST par Ian Barker
DDoS attacks remain a major problem for businesses and can have serious consequences. Data center services supplier US Signal is launching a new cloud-based offering. Building on the company’s partnership with Cloudflare it delivers a robust, customizable service that protects organizations against online threats including DDoS, ransomware, malicious bots and application-layer attacks. US Signal's new Website and Application Security Solution filters unwanted or malicious traffic before it reaches a customer network. This leads to cleaner web traffic and more effective use of resources, such as internet bandwidth and server capacity, which are needed to host applications and websites. Filtering controls,… [Continue Reading] -

Looking deep into Magecart
Publié: août 28, 2019, 12:32pm CEST par Ian Barker
The Magecart JavaScript attack that captures online payment information has been around since 2016. A new study for Arxan Technologies produced by Aite Group takes a detailed look at the attack. This research follows the trail of servers compromised by Magecart groups, as well as the collection servers to which the sites were actively sending stolen credit card data, in an effort to examine commonalities between victim websites and the tactics, techniques, and procedures used to compromise the servers. Arxan and Aite Group have also worked with federal law enforcement to notify the 80 victim sites discovered during this research as well as… [Continue Reading] -

One in four workers would steal information to get a job at a competitor
Publié: août 27, 2019, 3:45pm CEST par Ian Barker
Would you take information from your employer to help you get a job at a competitor? 24 percent would according to a new survey of almost 500 IT professionals carried out at Blackhat USA 2019. The survey by behavior-based security specialist Gurucul finds that managed service providers (34 percent) and developers (30 percent) pose the leading sources of third party risk, and that if someone was to commit fraud it would most likely occur in the finance department (32 percent). "What these findings show is that insider fraud is a top concern among IT security professionals, as are the security… [Continue Reading] -

Budget and staffing limits mean SMBs struggle with security
Publié: août 27, 2019, 3:05pm CEST par Ian Barker
SMBs around the world continue to cite budget constraints, paired with a lack of time and personnel to research new security threats, as the main obstacles facing the implementation of their IT security according to a new report. The study from Untangle Inc studied over 300 SMBs, compiling data on budget and resource constraints, breaches, IT infrastructure, cloud adoption and more. Security is ranked as a top IT priority for 80 percent of those surveyed, but 29 percent spend less than $1,000 on IT security annually. The lack of a dedicated IT security workforce is also apparent with 52 percent… [Continue Reading] -

Over half of social media logins are fraudulent
Publié: août 26, 2019, 3:01pm CEST par Ian Barker
Social media sites are a popular target for cybercriminals. It shouldn't come as too much of a surprise therefore to find that 53 percent of logins on social media sites are fraudulent and 25 percent of all new account applications are too. These are among the findings of a study by anti-fraud platform Arkose Labs which analyzed over 1.2 billion transactions spanning account registrations, logins and payments from financial services, e-commerce, travel, social media, gaming and entertainment industries, in real time. "We are in an era where online identity, intent, business, metrics and content can all be faked. This can… [Continue Reading] -

How cloud-based training can help address the cybersecurity skills gap [Q&A]
Publié: août 26, 2019, 12:04pm CEST par Ian Barker
It's widely acknowledged that there's a skills shortage in the cybersecurity field. Many businesses are looking to address this by training their own security talent, but this in itself can be a challenge. We spoke to Zvi Guterman, founder and CEO of virtual IT labs company CloudShare to find out how the cloud can help address security training issues. BN: There is a growing shortage of skilled cybersecurity professionals. What role does training play in addressing this? ZG: Organizations are having a hard time finding experienced talent to fill cybersecurity positions. Research from ESG/ISSA indicates that 70 percent of organizations… [Continue Reading] -

Five vendors account for nearly a quarter of all vulnerabilities
Publié: août 23, 2019, 2:55pm CEST par Ian Barker
Just five major vendors account for 24.1 percent of disclosed vulnerabilities in 2019 so far, according to a new report from Risk Based Security. The report also reveals that 54 percent of 2019 vulnerabilities are web-related, 34 percent have public exploits, 53 percent can be exploited remotely and that 34 percent of 2019 vulnerabilities don't yet have a documented solution. "34 percent of vulnerabilities do not have a solution, which may be because vendors are not patching. This can occur when the researcher has not informed the vendor, so they don't know about the vulnerability," says Brian Martin, vice president… [Continue Reading] -

Interest in VMWare Cloud use on AWS grows
Publié: août 22, 2019, 4:01pm CEST par Ian Barker
A new survey of over 1,100 IT professionals carried out by managed service provider Faction reveals growing usage of and interest in VMware Cloud on AWS. According to the study 64 percent of respondents say they have workloads in Azure, 57 percent AWS, 25 percent VMware Cloud on AWS, and 26 percent Google. But 29 percent of respondents plan to increase workloads on VMware Cloud on AWS in the next 12 months, while 15 percent plan to start running workloads and 14 percent plan to increase the number of workloads. Top use cases stated for those using using VMware Cloud… [Continue Reading] -

Hacktivism in decline as it returns to its roots
Publié: août 21, 2019, 4:27pm CEST par Ian Barker
Hacktivism has its origins in small groups of people banding together to achieve common goals. In recent years, however, it's become associated with larger groups and even nation states using the guise of hacktivism for geopolitical purposes. A new report from the Insikt Group at Recorded Future though suggests that overall hacktivism is in decline. In the last ten years, the number of large-scale, international hacking operations most commonly associated with hacktivism has risen astronomically, only to fall off just as dramatically after 2015 and 2016. The report suggests this is areturn to normal, in which hacktivist groups are usually… [Continue Reading] -

What makes enterprises more efficient at patching vulnerabilities?
Publié: août 21, 2019, 3:10pm CEST par Ian Barker
The companies most effectively managing security vulnerabilities are those using a patch tool, relying on risk-based prioritization tools, and having multiple, specialized remediation teams that focus on specific sectors of a technology stack. A new report from cyber risk specialist Kenna Security, produced in conjunction with the Cyentia Institute, reveals that businesses with mature, well-funded vulnerability management programs are more likely to patch vulnerabilities faster. However, this doesn't necessarily mean the companies patch the riskiest vulnerabilities first. Companies using the Common Vulnerability Scoring System (CVSS) to prioritize vulnerabilities for remediation tend to be slower in patching high-risk vulnerabilities. Also those… [Continue Reading] -

IBM extends its commitment to open hardware
Publié: août 20, 2019, 6:04pm CEST par Ian Barker
IBM has used the Linux Foundation Open Source Summit today to announce that it will contribute key technologies to the open community. The company is opening up the POWER Instruction Set Architecture (ISA), the definitions developers use for ensuring that hardware and software work together on POWER. With the ISA and other technologies being contributed to the open community, developers can build new hardware that takes advantage of POWER's enterprise-leading capabilities to process data-intensive workloads and create new software applications for AI and hybrid cloud built to take advantage of the hardware’s unique capabilities. IBM will also contribute multiple other… [Continue Reading] -

Almost a third of healthcare workers haven't had cybersecurity training
Publié: août 20, 2019, 4:56pm CEST par Ian Barker
Because of the volumes and types of data that it holds the healthcare industry is a prime target for cybercriminals. So it's a little concerning that a new survey of healthcare staff from Kaspersky shows 32 percent of respondents in North America say that they have never received cybersecurity training from their workplace. The report also shows a lack of awareness of the federal regulations, in both the US and Canada, in place to keep patient information safe and secure. According to the report, nearly a fifth of US respondents (18 percent) report they don't not know what the HIPAA security… [Continue Reading] -

Deception technology speeds up detection of attacks
Publié: août 15, 2019, 3:59pm CEST par Ian Barker
Users of deception technology report a 12X improvement in the average number of days it takes to detect attackers operating within an enterprise network. New research for Attivo Networks carried out by Enterprise Management Associates suggests attacker dwell times can be as low as 5.5 days with deception in use compared to an average of 78 to 100 days for those not using the technology. When respondents were asked to rank 12 security tools for detecting insider threats, 30 percent ranked deception technology, tied with next-generation endpoint security, as the most effective tool in detecting insider threats. "Quantifying the return… [Continue Reading] -

Over 3,800 data breaches reported in the first half of 2019
Publié: août 15, 2019, 3:05pm CEST par Ian Barker
2019 is on track to be another 'worst on record' year for data breaches according to a new report from Risk Based Security which finds the number of reported breaches has gone up by 54 percent and the number of exposed records by 52 percent compared to the first six months of 2018. It shows 3,813 breaches have been reported in the first six months of 2019, exposing more than 4.1 billion records. Eight breaches alone have exposed over 3.2 billion records, 78.6 percent of the total, between them. The business sector accounts for 67 percent of reported breaches, which… [Continue Reading] -

Executives believe AI will help businesses cope with changing environments
Publié: août 15, 2019, 12:38pm CEST par Ian Barker
A new study by management consultancy AT Kearney reveals that confidence is growing among C-suite executives that technology will help businesses navigate a complex and rapidly changing environment. In an age of increasing automation and artificial intelligence (AI), leaders recognize the differentiating role of non-technical and interpersonal skills such as creativity and leadership -- skills that are not only difficult to find but also expected to become even more important. 42 percent for example say that creativity and innovation skills are hard to find. Shortage of these skills suggests that demand to develop AI endowed with emotional intelligence could intensify.… [Continue Reading] -

60 percent of UK consumers not happy with their data being used for analytics
Publié: août 14, 2019, 5:03pm CEST par Ian Barker
Customers are more worried than ever about the way their data is used and shared by companies, particularly for analytics, according to a new report. The Customer State of Mind survey from data protection specialist Trūata shows 60 percent of UK customers are uneasy with companies using their personal data for analytics. Recent high-profile data leaks have also added to this negative perception of the way personal data is managed by brands. In fact, more than seven in ten (71 percent) internet users are worried that their personal data could be used to commit fraud against them if it were… [Continue Reading] -

Norman the Cryptominer uses sophisticated techniques to avoid discovery
Publié: août 14, 2019, 4:15pm CEST par Ian Barker
Researchers at Varonis have released information on a new cryptominer variant, which the team has dubbed 'Norman', that uses various techniques to hide and avoid discovery. Norman was discovered during investigations of an ongoing cryptomining infection that had spread to nearly every device at a midsize company. Almost every server and workstation at the business was infected and since the initial infection, which took place over a year ago, the number of variants and infected devices had grown. Most of the malware variants relied on DuckDNS (a free, Dynamic DNS service). Some needed it for command and control communications, while… [Continue Reading] -

Education is top target for cyberattacks
Publié: août 14, 2019, 3:23pm CEST par Ian Barker
The education sector has become one of the most sought after targets for cybercriminals, according to the latest report from Malwarebytes Labs. In the first half of 2019, the top three largest categories of threats identified among education institutions' devices are adware (43 percent), Trojans (25 percent) and backdoors (three percent). However, ransomware dropped to less than one percent in this period -- though it was higher both before and after the study. The Emotet, TrickBot and Trace Trojans have been particularly active in education, with the three representing nearly half of all Trojans detected (44 percent) and more than… [Continue Reading] -

Free VPN apps pose a privacy risk on both Android and iOS
Publié: août 13, 2019, 4:27pm CEST par Ian Barker
Both Apple and Google are allowing numerous potentially unsafe free VPN apps to remain in their app stores, despite being aware of privacy risks according to research from Top10VPN.com. Among the string of serious privacy issues uncovered but not acted upon is the discovery that nearly 60 percent of the most popular free VPN apps are secretly Chinese-owned. The study examined the 30 apps making up the top 20 search results for 'VPN' across the two app stores, digging deep into their ownership, professionalism and policies. It finds 59 percent of apps have hidden Chinese ownership, despite the strict VPN… [Continue Reading] -

British Airways e-ticketing leaves passengers' sensitive data at risk
Publié: août 13, 2019, 3:11pm CEST par Ian Barker
Less than a year on from a breach which exposed the details of hundreds of thousands of customers, British Airways systems are still leaving passengers' personal information at risk. New research from mobile security provider Wandera has discovered an e-ticketing system vulnerability that leaves passengers' personally identifiable information (PII) exposed. Through unencrypted check-in links, which are distributed via email by British Airways, hackers intercepting link requests -- on a public Wi-Fi network for example -- are able to access passengers' booking references and surnames. Using these details, hackers are then able to steal even more information or even manipulate the… [Continue Reading] -

Connectivity could make digital cameras vulnerable to ransomware
Publié: août 12, 2019, 11:24am CEST par Ian Barker
Modern digital cameras with wireless and USB capabilities could be vulnerable to ransomware and malware attacks, enabling attackers to hold precious photos and videos to ransom. Check Point Research reveals that the standardized protocol known as Picture Transfer Protocol (PTP) used to transfer digital images from camera to PC has critical vulnerabilities. Although initially focused on image transfer, the PTP has evolved to include dozens of different commands that support anything from taking a live picture to upgrading the camera's firmware. Check Point used Canon's EOS 80D DSLR camera which supports both USB and WiFi and found PTP vulnerable to… [Continue Reading] -

Almost half of employees have access to more data than they need
Publié: août 9, 2019, 12:30pm CEST par Ian Barker
A new study of over 700 full-time US employees reveals that that 48 percent of employees have access to more company data than they need to perform their jobs, while 12 percent of employees say they have access to all company data. The survey by business app marketplace GetApp also asked employees what classifications of data protection are in place at their company. No more than a third of businesses were found to use any one individual data classification. The lowest in use are Proprietary (15 percent) and Highly Confidential (18 percent). The most commonly used are Confidential -- 33… [Continue Reading] -

Load balancer flaw could lead to major breaches at large organizations
Publié: août 9, 2019, 11:16am CEST par Ian Barker
A security flaw in the F5 Networks’ BIG-IP load balancer, which is popular among governments, banks, and other large corporations, could be exploited to allow network access. F-Secure senior security consultant Christoffer Jerkeby has discovered the issue in the Tcl programming language that BIG-IP's iRules (the feature that BIG-IP uses to direct incoming web traffic) are written in. Certain coding practices allow attackers to inject arbitrary Tcl commands, which could be executed in the security context of the target Tcl script. "This configuration issue is really quite severe because it's stealthy enough for an attacker to get in, achieve a… [Continue Reading] -

Ransomware turns its sights on large organizations
Publié: août 8, 2019, 4:11pm CEST par Ian Barker
Detections of ransomware aimed at businesses rose by a massive 363 percent between the second quarter of 2018 and the same period this year. Meanwhile consumer ransomware is down 34 percent. The latest quarterly threat report from Malwarebytes also sees a 235 percent overall increase in threats aimed at organizations from enterprises to small businesses, with ransomware as a major contributor. In particular public sector bodies like municipalities, educational institutions, and healthcare organizations have become prime targets, likely because of legacy infrastructure, outdated hardware and software applications, and lack of security funding in these sectors. "It seems like every other… [Continue Reading] -

Software producers need more flexible licensing models in order to compete
Publié: août 8, 2019, 3:33pm CEST par Ian Barker
Once upon a time you bought a license for a piece of software and you could, essentially, run it forever. While much of the market has now shifted to subscription models, 65 percent of producers are still offering perpetual licenses, while 74 percent utilize subscription models for some or all of their products. A new report from Flexera, which looks at changing licensing and deployment models, finds that when software producers are asked how they will change their monetization models over the next 18 months, both usage and subscription models will see the strongest increases. 48 of respondents see subscription… [Continue Reading] -

IBM launches new toolkit to boost understanding of and trust in AI
Publié: août 8, 2019, 2:43pm CEST par Ian Barker
AI and machine learning have demonstrated some impressive abilities in recent years, but the models behind the technology and the reasons why it came to the decision it did are often hard for the people interacting with it to understand. In order to help people gain an insight into machine decision making, IBM Research is launching AI Explainability 360, a comprehensive open source toolkit of state-of-the-art algorithms that support the interpretability and explainability of machine learning models. AI Explainability 360 includes eight new algorithms developed by IBM Research, along with quantitative metrics to help measure explainability. It's open source, so… [Continue Reading] -

Half of companies won't move mission critical workloads to the cloud
Publié: août 8, 2019, 12:20pm CEST par Ian Barker
A new report from enterprise file sharing platform FileCloud looks at cloud and data security and finds that 50 percent of companies don’t plan on moving mission critical workloads to the public cloud. The survey of 150 professionals from industries including health care, financial services and educational institutions finds that shifts in perceptions of data security are impacting movement to the cloud. Among the findings are that 64 percent of businesses believe using personal sharing apps for storing and sharing office documents is the top threat for data security within an organization. In addition 82 percent of company admins think… [Continue Reading] -

Biggest ransomware threat is encryption of shared cloud files
Publié: août 7, 2019, 3:20pm CEST par Ian Barker
The cybercriminal's most effective weapon in a ransomware attack is the network itself, which enables the malicious encryption of shared files on network servers, especially files stored in infrastructure-as-a-service (IaaS) cloud providers. This is according to a new report from threat detection specialist Vectra which finds that by encrypting files that are accessed by many business applications across the network, attackers achieve an economy of scale faster and far more damaging than encrypting files on individual devices. "The fallout from ransomware attacks against cloud service providers is far more devastating when the business systems of every cloud-hosted customer are encrypted,"… [Continue Reading] -

Enterprise security pros spend too long researching suspicious URLs
Publié: août 7, 2019, 2:42pm CEST par Ian Barker
Phishing threats tend to be fast moving, so the ability to block them quickly is essential for protection. But a new survey finds that even large companies with multi-layer security controls and multiple threat feeds lack adequate safeguards to protect their employees from phishing attacks that employ links to malicious sites. The study from SlashNext reveals that 56 percent of respondents correctly note that phishing URLs typically remain active for a very short time, under an hour to just several hours. This underlines the need for both proactive and real-time threat detection as well as fast deployment of threat intelligence… [Continue Reading] -

You're replacing me with a robot? That’s fine
Publié: août 7, 2019, 11:46am CEST par Ian Barker
While people prefer to see jobs go to other humans rather than robots, it seems the opposite is true when it comes to their own jobs. This is a finding of new research from Stefano Puntoni, professor of marketing at Rotterdam School of Management, Erasmus University, released today in a co-authored article in Nature Human Behaviour. It reveals that people experience more negative feelings when they are replaced by another person than when they are replaced by a robot. This creates a psychological incentive for people to prefer being replaced by robots. "This is the first paper to explore the… [Continue Reading] -

You're replacing me with a robot? That's fine
Publié: août 7, 2019, 11:46am CEST par Ian Barker
While people prefer to see jobs go to other humans rather than robots, it seems the opposite is true when it comes to their own jobs. This is a finding of new research from Stefano Puntoni, professor of marketing at Rotterdam School of Management, Erasmus University, released today in a co-authored article in Nature Human Behaviour. It reveals that people experience more negative feelings when they are replaced by another person than when they are replaced by a robot. This creates a psychological incentive for people to prefer being replaced by robots. "This is the first paper to explore the… [Continue Reading] -

Trojans account for more than 70 percent of opportunistic email attacks
Publié: août 6, 2019, 5:07pm CEST par Ian Barker
Analysis by Mimecast of 67 billion attack emails between April and June this year reveals that opportunistic attacks are dominated by Trojans, which make up 71 percent. Targeted attacks are lower in volume but are specifically designed to get past commodity malware scanners by using newly detected or updated malware not detectable with file signatures. The report notes a significant increase in impersonation attacks, leveraging well-known basic social engineering techniques to target individuals for fast and easy financial gain. Interestingly, the report cites that threat actors are adapting how they engage their targeted victims, initiating through email first, then shifting to… [Continue Reading] -

Half of risky online transactions come from mobile devices
Publié: août 6, 2019, 4:30pm CEST par Ian Barker
New research from fraud prevention and multi-factor authentication specialist iovation reveals that 49 percent of all risky transactions now come from mobile devices, up from 30 percent in 2018, 33 percent in 2017 and 25 percent in 2016. Looked at geographically, North America with 59 percent of all risky transactions coming from mobile devices, leads the way. In 2018, it was Asia at 53 percent. In 2017, it was North America with 55 percent, and in 2016, it was North America again with 36 percent. The top industry for mobile fraud so far in 2019 is telecommunications with 75 percent… [Continue Reading] -

The top 11 security threats to cloud computing
Publié: août 6, 2019, 3:40pm CEST par Ian Barker
Data breaches and misconfigurations come out top of the Cloud Security Alliance's latest Top Threats report which reveals an 'Egregious Eleven' list of cloud security threats. This year's list no longer includes issues that fall to cloud service providers (CSPs), such as denial of service, shared technology vulnerabilities, CSP data loss and system vulnerabilities. This suggests these are either being well addressed or are no longer perceived as a significant business risk of cloud adoption. The top 11 in order of significance are: Data Breaches Misconfiguration and inadequate change control Lack of cloud security architecture and strategy Insufficient identity, credential,… [Continue Reading] -

SMEs forced to meet cybersecurity demands in order to win contracts
Publié: août 6, 2019, 2:51pm CEST par Ian Barker
Supply chain threats are a major problem for enterprises and they are forcing smaller businesses to take security more seriously in order to win contracts. A study by cyber security awareness platform CybSafe shows nearly 37 percent of organizations have been required to achieve a recognized cyber security standard by their enterprise customers before successfully securing contracts. This represents a nine percent increase over 2017. In addition 40 percent of enterprises have now ensured that cyber security is part of their contract with SMEs -- a six percent increase on 2017, and 66 percent of enterprises have inquired about cyber… [Continue Reading] -

Handling user feedback data and the rise of 'ResearchOps' [Q&A]
Publié: août 6, 2019, 1:08pm CEST par Ian Barker
Customer experience has become a massive, sprawling industry that includes the many systems and touchpoints that lie between companies and their users. It's projected to be a $32B market by 2025. One of the most interesting new sub-categories emerging within customer experience is ResearchOps. It's a new discipline -- with a growing community of practitioners -- focused on better infrastructure around customer research, and operationalizing the user research process so it can be done faster and have a bigger impact. Product teams have many tools for managing code repositories, product roadmaps and engineering tickets. But user feedback and research tends… [Continue Reading] -

Second quarter sees an 18 percent rise in DDoS attacks
Publié: août 5, 2019, 3:42pm CEST par Ian Barker
In the second quarter of 2019, the total number of DDoS attacks grew by 18 percent, compared to the same period in 2018 according to a new report from Kaspersky. There is, however, a drop compared to the first quarter of this year, with attacks down 44 percent. Kaspersky attributes this to seasonal variation with DDoS attack usually declining in late spring and summer. The seasonal decrease only had a negligible effect on the number of attacks on the application layer though, these reduced by just four percent compared to the previous quarter. These type of attacks target certain functions… [Continue Reading] -

When did computers get smarter than us?
Publié: août 5, 2019, 11:48am CEST par Ian Barker
There are few aspects of our everyday lives that don’t now rely on computers at some level. But does this reliance on technology mean that the machines are getting smarter than we are? Server and network monitoring specialist CloudRadar has put together an infographic examining our reliance on technology. It looks at the effects of technology failures, at how machines are good at the repetitive tasks that we find boring, and at how computers can now beat us at many games. It also looks at how computers compare to our brains. You can view the full graphic below. Photo Credit:… [Continue Reading] -

New platform helps automate security operations
Publié: août 1, 2019, 4:38pm CEST par Ian Barker
Speed of response is critical for security teams, which is why many companies employ Security Orchestration, Automation and Response (SOAR) tools. Security automation platform LogicHub is looking to take SOAR a step further with the launch of a SOAR+ platform offers autonomous detection and response, advanced analytics and machine learning to automate decision making with accuracy across disparate security operations. "SOAR technology is good for automating the ingestion and enrichment of data and automating incident response once analysts make decisions about what actions to take," says Kumar Saurabh, CEO of LogicHub. "The gap in security automation today, however, lies in… [Continue Reading] -

New solution uses backup data to find vulnerabilities
Publié: août 1, 2019, 3:50pm CEST par Ian Barker
Finding and addressing vulnerabilities is a major headache for businesses, left unattended they can lead to cyberattacks and data breaches. Data management company Cohesity is looking to make detection easier with a new application that uses backup data to assess the vulnerabilities, or risk posture, of an enterprise's IT environment. Cohesity CyberScan works by scanning backup copies on Cohesity DataPlatform (instead of the live production copy) to identify any vulnerabilities across an organization's IT environment, including the operating system, computer, network devices, and configurations. The application gives a global view of all vulnerabilities through an easy-to-read security dashboard along with… [Continue Reading] -

25 percent of security analysts' time is wasted on false positives
Publié: août 1, 2019, 3:11pm CEST par Ian Barker
Security analysts in US enterprises spend around a quarter of their time chasing false positives because security alerts or indicators of compromise (IOCs) are erroneous. This is among the findings of research carried out by Exabeam and the Ponemon Institute which also shows that security teams must evaluate and respond to nearly 4,000 security alerts per week. While false positives are the largest drain on resources, the study also shows that investigating actionable intelligence and building incident timelines; and cleaning, fixing and/or patching networks, applications and devices resulting from an incident each take over 15 percent of a security team’s… [Continue Reading] -

85 percent of enterprise web traffic is cloud services
Publié: août 1, 2019, 11:21am CEST par Ian Barker
A new study based on aggregated, anonymized data from millions of global users reveals that cloud services now account for 85 percent of all enterprise web traffic. The report from cloud security company Netskope also reveals that heavy use of cloud services is often driven by multiple instances of cloud service usage across an organization. Cloud storage and collaboration apps make up the majority of the top 20 cloud services list, with consumer-focused social media services like Facebook, Twitter, LinkedIn and YouTube also prominent on the list, a sign that more enterprises are allowing employees to use corporate networks for… [Continue Reading] -

Flexera helps businesses tackle vulnerabilities more quickly
Publié: juillet 31, 2019, 3:14pm CEST par Ian Barker
In the modern world it's vital for businesses to know what software they have, and where vulnerabilities lie. Flexera already assists IT and security teams to do this with its Software Vulnerability Manager, and it's now launching new modules to help address threats. It's produced two new modules for SVM. The first of these is the Vendor Patch Module, which allows organizations to take advantage of insights and mitigate them more quickly, by using comprehensive patch coverage -- with more than 1,000 out-of-the-box patches. Additionally, the Vendor Patch Module delivers details to help companies more easily create over 1,000 additional patches.… [Continue Reading] -

Phishing and credential stuffing remain top threats
Publié: juillet 31, 2019, 12:43pm CEST par Ian Barker
As we have seen in another report today, the financial sector remains a prime target for cybercriminals. Phishing attacks and credential stuffing are the two most common forms of attack used against the industry according to another report from Akamai. In the six months between December 2018 and May 2019, nearly 200,000 phishing domains were discovered by the research and 50 percent of all unique organizations impacted are from the financial services sector. In addition the report reveals 3.5 billion attempts at credential stuffing during an 18-month period, putting the personal data and banking information of financial services customers at… [Continue Reading] -

Financial sector faces a broad range of cyberthreats
Publié: juillet 31, 2019, 11:49am CEST par Ian Barker
The finance industry is a prime target for cyberattacks and a new report from F-Secure shows that it's facing a wide range of threats that go far beyond traditional theft. Attacks targeting banks, insurance companies, asset managers and similar organizations can range from common script-kiddies to organized criminals and state-sponsored actors. And these attackers have an equally diverse set of motivations for their actions, with many seeing the finance sector as a tempting target due to its importance in national economies. "This is a useful way to think about cyber threats, because it is easy to map attacker motivations across… [Continue Reading] -

Businesses still at risk from outdated operating systems
Publié: juillet 30, 2019, 4:29pm CEST par Ian Barker
A new report reveals that 32 percent of businesses still have Windows XP installed on at least one device on their network and 79 percent of businesses are running Windows 7, which will reach its end of service in January 2020, on one or more devices. The study from IT industry marketplace Spiceworks also shows many businesses are turning to next-generation security solutions like AI-powered threat intelligence and security-as-a-service to face security threats and vulnerabilities including outdated operating systems, limited use of encryption, and a lack of in-house security expertise. The report reveals that 53 percent of businesses don't have… [Continue Reading] -

More than half of enterprises don't know if their security tools are working
Publié: juillet 30, 2019, 3:35pm CEST par Ian Barker
According to a new report, 53 percent of enterprise security leaders don't know if their security tools are working, despite massive spending. The study carried out for continuous validation specialist AttackIQ by the Ponemon Institute shows companies surveyed are spending an average of $18.4 million annually on cybersecurity and 58 percent will be increasing their IT security budget by an average of 14 percent in the next year. Yet 63 percent of respondents say they've observed a security control reporting that it blocked an attack when it actually failed to do so. In addition only 39 percent of respondents think… [Continue Reading] -

Organizations struggle with container security
Publié: juillet 30, 2019, 2:53pm CEST par Ian Barker
Containerization has seen rapid adoption in recent years, but a new study from container security specialist StackRox reveals organizations struggling with security issues. The report shows that while two-thirds of organizations have more than 10 percent of their applications containerized, 40 percent of them remain concerned that their container strategy doesn't adequately invest in security. Another 34 percent say that their strategy lacks sufficient detail. Kubernetes is the most popular container platform, with 86 percent now running it. Nearly three-quarters (70 percent) of respondents are running containers on premises, 53 percent are running them in hybrid mode, with containers deployed… [Continue Reading] -

Qualys makes IT asset discovery and inventory app available for free
Publié: juillet 29, 2019, 3:48pm CEST par Ian Barker
Security and compliance specialist Qualys is announcing today that it's making its Global IT Asset Discovery and Inventory app available to all businesses for free. With the app users can automatically create a continuous, real-time inventory of known and unknown assets across a global IT footprint. The assets can be anything from on-premises, endpoints, multi-cloud, mobile, containers, OT and IoT. It also allows automatic classification, normalization, and categorization of assets to ensure clean, reliable, and consistent data. In-depth asset details provide fine-grained visibility on the system, services, installed software, network, and users. There's the ability to search across millions of… [Continue Reading] -

65 percent of cybersecurity analysts say they've considered quitting
Publié: juillet 29, 2019, 3:18pm CEST par Ian Barker
Working in a security operations center is stressful, so much so that 65 percent of analysts report having considered changing careers or quitting their jobs. This is among the findings of a new study carried out by the Ponemon Institute for data analytics platform Devo Technology, which also finds that 49 percent say their SOC is not fully aligned with business needs. The top barrier to SOC success, according to 65 percent of respondents, is the lack of visibility into the IT security infrastructure and the top reason for SOC ineffectiveness, according to 69 percent, is a lack of visibility… [Continue Reading] -

Fewer than three percent of people say they would try Facebook Libra for payments
Publié: juillet 26, 2019, 11:36am CEST par Ian Barker
Facebook announced last month that it was launching its own Libra cryptocurrency. But the results of a new survey suggest that the social network is struggling to gain consumer trust in its system. Messaging app Viber surveyed 2,000 people in the US and UK and finds that fewer than three percent of Americans and only 1.4 percent in the UK say they would be willing to try Libra for payments. In addition, 13.9 percent of Americans and 16.6 percent of Brits say they definitely wouldn't use Libra for payments. When asked if they would trust Facebook to keep their information… [Continue Reading] -

66 percent of SMBs don't believe they’re vulnerable to a cyberattack
Publié: juillet 25, 2019, 3:54pm CEST par Ian Barker
Most small and medium businesses are seriously underestimating their vulnerability to cyberattacks according to a new study. The report from password manager company Keeper Security shows that 66 percent don't think they will fall victim to an attack. But this confidence is contradicted by a study last year that showed 67 percent of SMBs had been attacked in the past year. The latest study finds that only about one in ten (12 percent) understand the reality that an attack is very likely, no matter how big or small the company. Interestingly, newer companies are likely to have greater awareness of… [Continue Reading] -

Banking malware grows as cryptominers decline
Publié: juillet 25, 2019, 3:12pm CEST par Ian Barker
The latest mid-year Cyber Attack Trends Report from Check Point shows mobile banking malware attacks are up 50 percent compared to the first half of 2018, while the number of organizations hit by cryptominers is down to 26 percent, from 41 percent last year. Among the top banking malware variants are Ramnit (28 percent), a Trojan that steals banking credentials, FTP passwords, session cookies and personal data; Trickbot (21 percent), which first emerged in October 2016; and Ursnif (10 percent) a Trojan that targets the Windows platform. Other shifts in the threat landscape include increased focus on supply chain attacks… [Continue Reading] -

IT professionals under pressure from email attacks
Publié: juillet 25, 2019, 11:53am CEST par Ian Barker
Email attacks are causing major problems for IT professionals, with over a third (38 percent) blaming them for increased stress at work. A survey of 660 IT professionals by Barracuda Networks reveals that 38 percent also admit to worrying about email attacks outside of work hours and 16 percent have canceled personal plans due to email attacks. These attacks cause problems for productivity too. Those in EMEA countries flag the most emails as suspicious, but 44 percent of respondents agree that less than 10 percent turn out to actually be fraudulent. Among respondents 81 percent spend 30 minutes or more… [Continue Reading] -

22 percent of businesses hit by phishing attacks in the last quarter
Publié: juillet 23, 2019, 4:45pm CEST par Ian Barker
In the past three months 22 percent of businesses have suffered a data breach as a result of an email attack according to a new report. The study released by email security platform GreatHorn spoke to more than 1,000 professionals to get a better understanding of the current state of enterprise email security. The results show that 24.4 percent of survey respondents indicate that malicious email messages, including impersonations, wire transfer requests, payload attacks/malware, business services spoofing, and credential theft attempts, reach their inbox every day, with an additional 25.4 percent that report seeing attacks at least weekly. When separating… [Continue Reading] -

Password stealing malware on the rise as 60 percent more users are targeted
Publié: juillet 23, 2019, 3:36pm CEST par Ian Barker
Password stealing malware is a key weapon in the cybercriminals' armoury, seeking to grab data directly from users' web browsers using a range of methods. According to new data from Kaspersky, the number of users, targeted by password stealers, has peaked from less than 600,000 in the first half of 2018 to over 940,000 during the same period in 2019. Over the past six months, Kaspersky has detected high levels of activity by the stealers in Europe and Asia. Most frequently, the malware has targeted users in Russia, India, Brazil, Germany and the USA. One of the most widely spread… [Continue Reading] -

New developer program helps strengthen IoT security
Publié: juillet 23, 2019, 3:06pm CEST par Ian Barker
Securing Internet of Things devices is an ongoing problem for businesses, developers often have to sift through a raft of unorganized and disparate information to find the IoT security solution that works best for them. Identity and security specialist GlobalSign is launching an IoT developer program designed specifically to assist developers with device identity integrations that strengthen security operations for IoT and industrial IoT (IIoT) ecosystems. The program includes an IoT developer portal to provide a centralized location where developers can access all the tools they need to successfully integrate Public Key Infrastructure (PKI)-based device identity as part of their… [Continue Reading] -

Enterprises are modernizing data architectures but still have major concerns
Publié: juillet 22, 2019, 3:36pm CEST par Ian Barker
A new study of over 300 IT executives in large enterprises by database company DataStax reveals all are modernizing their data architecture, but most are still struggling with major challenges. The results show 99 percent of IT execs report challenges with architecture modernization and 98 percent with their corporate data architectures (data silos). Vendor lock-in (95 percent) is also a key concern among respondents. "What this report makes clear is that data is certainly the hardest part of architecture modernization," says DataStax SVP and chief product officer Robin Schumacher. "While the cloud makes so many things around architectures much easier,… [Continue Reading] -

UK office workers waste 1.8 billion hours a year because of poor technology
Publié: juillet 19, 2019, 12:56pm CEST par Ian Barker
Office workers across the UK are wasting 14 days per person each year -- or 1.8 billion hours a year in total -- because the technology they’re given isn't good enough. A new study of 2,000 office workers from technology solutions company Insight shows 80 percent at some point have felt they don't have the technology they need to do their jobs properly. While 34 percent also say not being equipped with the right technology makes remote and flexible working difficult and stressful. There's a problem with the information they're getting too. Less than half (47 percent) of the information… [Continue Reading] -

Enterprises struggle to support edge workloads
Publié: juillet 17, 2019, 3:36pm CEST par Ian Barker
The use of edge computing is driving a need for more local computing power, but a new study reveals that enterprises are facing problems when it comes to supporting edge workloads. The survey of more than 300 storage professionals from computational storage specialist NGD systems finds that while enterprises are rapidly deploying technologies for real-time analytics, machine learning and IoT, they are still using legacy storage solutions that are not designed for such data-intensive workloads. In fact, 54 percent of respondents say their processing of edge applications is a bottleneck, and they want faster and more intelligent storage solutions. 60… [Continue Reading] -

New platform simplifies the creation of interactive online guides
Publié: juillet 17, 2019, 1:48pm CEST par Ian Barker
As we carry out more of our day-to-day tasks online, there's increasing demand for guides and tutorials to help users get the best from services and products. But creating these guides can be time consuming and take developer time away from other tasks. A new platform called Stonly seeks to let anyone create easy-to-follow guides called 'Stonlies' without any need to write code. Content including text, images and videos can be combined with interactive capabilities to ensure the viewer only gets relevant information. Alexis Fogel, Stonly's co-founder, explains, "Stonly solves two problems that every company has: explaining how their product or… [Continue Reading] -

IBM helps developers use open source and machine learning
Publié: juillet 16, 2019, 4:31pm CEST par Ian Barker
As artificial intelligence and machine learning become more widespread, it's essential that developers have access to the latest models and data sets. Today at the OSCON 2019 open source developer conference, IBM is announcing the launch of two new projects for developers. First is the IBM Data Asset eXchange (DAX), an online hub for developers and data scientists to find carefully curated free and open datasets under open data licenses. Where possible, datasets posted on DAX will use the Linux Foundation's Community Data License Agreement (CDLA) open data licensing framework to enable data sharing and collaboration. DAX also provides unique access to… [Continue Reading] -

Symantec launches new zero trust cloud access security technology
Publié: juillet 16, 2019, 3:46pm CEST par Ian Barker
Increasing volumes of business network traffic are now directed at the cloud and companies need a cost effective way to secure them. Symantec is announcing updates and innovations across its portfolio of products, giving enterprises the ability to enforce zero trust security policies across SaaS applications, corporate applications hosted in the cloud, email and the internet. Zero trust access security gives authorized users access only to the network and cloud resources they need to accomplish tasks and strictly enforces data security and threat prevention polices. As well as access controls, the solution provides visibility and content scanning capabilities, allowing enterprises… [Continue Reading] -

Businesses gain better control of cloud and mobile devices
Publié: juillet 16, 2019, 3:03pm CEST par Ian Barker
Enterprises around the world are gaining control of previously unmonitored and unsupported cloud applications and mobile devices in their IT environments according to a new report. The 2019 Trusted Access report from Duo Security looks at more than a million corporate applications and resources that Duo protects. Among the findings are that cloud and mobile use has resulted in 45 percent of requests to access protected apps now coming from outside business walls. This has led to businesses enforcing security controls that establish user and device trust before granting access to applications, known as zero-trust security. These include strengthening user… [Continue Reading] -

How cloud technology can help SMBs to compete [Q&A]
Publié: juillet 15, 2019, 3:42pm CEST par Ian Barker
Smaller businesses have always found it hard to compete against their larger rivals, but that's starting to change as technology allows a leveling of the playing field. So how can technology, and in particular the cloud, help to give smaller companies an edge? We spoke to John Buni, CEO and co-founder of the CleanCloud SaaS platform and founder of bespoke tailoring company Tailor Made London, to find out. BN: Isn't it always going to be difficult for smaller businesses to go up against dominant players, especially in the internet age? JB: Not necessarily. When e-commerce and Amazon in particular started to make… [Continue Reading] -

New platform streamlines cloud storage support and recovery
Publié: juillet 15, 2019, 3:12pm CEST par Ian Barker
As businesses move more of their workloads to the cloud they depend on data and applications always being available and secure. But this can conflict with the need for regulatory compliance and effective backup regimes. Quest Software is launching a new version of its QoreStor product that helps businesses to easily move, recover and store data from on premise and cloud locations. QoreStor 6.0 enables software defined hybrid cloud secondary storage, with support for Microsoft Azure and AWS systems. Features include enterprise class compression and backup-vendor agnostic deduplication technology. It also offers QoreSto's Cloud Tier cloud native storage technology to… [Continue Reading] -

Why application security should be a key part of development [Q&A]
Publié: juillet 12, 2019, 5:00pm CEST par Ian Barker
As data protection legislation tightens and breaches continue to make headlines, there is increased pressure on businesses to implement security by design in their applications. For many this has meant a move to DevSecOps. We spoke with Rusty Carter, vice president of product management at application security specialist Arxan to find out why this approach is becoming essential. BN: Why are businesses turning to DevSecOps? RC: The push to DevOps from a business point of view is increasing rapidly. The critical piece that is generally missing from many approaches is that we need to make developers smarter about their code… [Continue Reading] -

Two-thirds of organizations think they'll need AI to respond to future cyber threats
Publié: juillet 11, 2019, 5:42pm CEST par Ian Barker
New data from the Capgemini Research Institute reveals that 69 percent of organizations believe that they won't be able to respond to critical cyber threats without AI. Over half (56 percent) of executives say their cybersecurity analysts are overwhelmed by the vast array of data they need to monitor to detect and prevent intrusion. In addition, the type of cyberattacks that require immediate intervention, or that cannot be dealt with quickly enough by analysts, have increased These high priority threats include attacks affecting time-sensitive applications (42 percent saying they have gone up, by an average of 16 percent), and automated,… [Continue Reading] -

New platform simplifies handling multi-cloud environments
Publié: juillet 11, 2019, 3:49pm CEST par Ian Barker
The rise of cloud adoption has led many businesses to adopt an environment where computing requirements are decoupled from storage and scale independently. But this leads to problems with accessibility and data management. A new platform launched today by Alluxio provides improved orchestration for data engineers managing and deploying analytical and AI workloads in the cloud, particularly for hybrid and multi-cloud environments. "With a data orchestration platform in place, a data analyst or scientist can work under the assumption that the data will be readily accessible regardless of where the data resides or the characteristics of the storage. They can… [Continue Reading] -

Summer heightens cyber security risks
Publié: juillet 11, 2019, 3:07pm CEST par Ian Barker
You might think that cyber attacks are a constant year round activity, or perhaps that they are focused on peak shopping periods like Christmas. But a new study from threat protection specialist Lastline reveals many security professionals believe their organizations are more at risk in summer. In a survey of 1,000 security professionals more than half believe cyber attacks are seasonal and 58 percent of those (30.5 percent overall) say that they see more attacks during the summer months. Nearly a half of security professionals (47 percent) report seeing an increase in phishing attacks during the summer, which makes some… [Continue Reading] -

It's 2029, you're paying more to read this page at peak time (and we're paying your ISP to stop you visiting other tech sites)
Publié: juillet 9, 2019, 4:40pm CEST par Ian Barker
What would a world be like where ISPs and businesses are in control of everything you see and do online? A world, in other words, without net neutrality. VPN comparison site TheBestVPN.com has been considering this and has created an interactive simulator looking at what the web without net neutrality could look like in 2029. Among the predictions are that ISPs may be able to block types of connection devices -- so they can force users to use a specific type of Wi-Fi router, rather than a third-party one, or even determine what types of PC, smartphone, and games console… [Continue Reading] -

Financial services businesses at high risk of mobile attacks
Publié: juillet 9, 2019, 3:06pm CEST par Ian Barker
Financial services are at greater risk of phishing and man-in-the-middle attacks on mobile devices than businesses in other industries according to a new report. The study from mobile security specialist Wandera analyzed mobile device data from 225 financial services customers and reveals financial services organizations are experiencing a higher volume of phishing attacks than their peers in other sectors (57 percent compared to 42 percent cross-industry). They are at a higher risk of man-in-the-middle attacks too (36 percent compared to 24 percent) perhaps due to higher than normal travel activity and public Wi-Fi usage. "In the financial services industry, as in… [Continue Reading] -

Cyber incidents cost $45 billion in 2018
Publié: juillet 9, 2019, 12:53pm CEST par Ian Barker
Cybercriminals are getting better at monetizing their activities, with more than two million cyber incidents in 2018 resulting in over $45 billion in losses, with actual numbers expected to be much higher as many cyber incidents are never reported. The Internet Society's Online Trust Alliance (OTA) has released a report which finds the financial impact of ransomware rose by 60 percent last year, and losses from business email compromise doubled, despite the fact that overall breaches and exposed records were down. "While it's tempting to celebrate a decreasing number of breaches overall, the findings of our report are grim," says… [Continue Reading] -

Seven out of 10 Brits want tougher penalties for breaching privacy rules
Publié: juillet 8, 2019, 12:14pm CEST par Ian Barker
According to a new survey carried out by YouGov for data privacy company myGaru 71 percent of of UK adults want to see tougher action in penalising companies that abuse data privacy by misusing third party data. Around a third of the public (34 percent) have already made changes to the privacy settings of one or more of their social media accounts since the Cambridge Analytica Facebook scandal and 19 percent say they would make more or new changes in the future. Overall, 44 percent of consumers have become more concerned about how their data is used by third parties,… [Continue Reading] -

Companies turn to instant messaging in response to rising email threats
Publié: juillet 4, 2019, 12:02pm CEST par Ian Barker
In a new study of IT decision makers by Barracuda Network, 94 percent of participants admit that email is still the most vulnerable part of their organization's cyber security. The survey of 280 decision makers focused on the email threat landscape and email security practises. It discovered that 75 percent have been hit with brand impersonation emails, the largest threat as identified in the survey with ransomware coming in second on 47 percent. Email threats are predicted to increase in the coming year by 87 percent of respondents. A majority (75 percent) also say they have witnessed a steady increase… [Continue Reading] -

Poor management of data harms businesses' ability to gain value from it
Publié: juillet 3, 2019, 3:43pm CEST par Ian Barker
Less than 40 percent of companies in Europe, the Middle East and Africa (EMEA) are confident they can manage, secure and gain insight from data, and use it responsibly according to new research from Oracle. The study finds that on average 42 percent of respondents do not have a data management strategy in place. Only 35 percent are highly confident they can manage data to generate meaningful insights, and key departments are still not accepting both accountability and responsibility for data management. In addition data security protocols are often not understood, or followed. "We know that being able to leverage… [Continue Reading] -

Second screens could be dragging down corporate networks
Publié: juillet 3, 2019, 3:03pm CEST par Ian Barker
Having a second monitor is a great way of improving your productivity, but new research from network solutions company Gigamon suggests this could also be driving higher bandwidth consumption. Of the 200+ IT professionals surveyed, 59 percent believe that second screens are, or could be, being used for non-work-related activity, like streaming music or watching videos. "When companies offer their staff second screens, the impact this is going to have on internet traffic is unlikely to be considered," says Ollie Sheridan, security engineer for EMEA at Gigamon. "However, our study clearly shows that a lot of employees are using their… [Continue Reading] -

Microsoft launches Threat and Vulnerability Management for enterprises
Publié: juillet 3, 2019, 11:08am CEST par Ian Barker
Scheduled vulnerability scanning can leave blind spots between scans leaving organizations vulnerable. In response to this problem, Microsoft has partnered with a number of enterprise customers to create a new Threat and Vulnerability Management solution as a built-in feature of Microsoft Defender Advanced Threat Protection. It uses a risk-based approach to discover, prioritize and remediate endpoint vulnerabilities and misconfigurations. Users benefit from continuous discovery, prioritization of threats based on business context, built-in remediation through integration with Microsoft Intune and Microsoft System Center Configuration Manager, and more. One of the program partners is Telit, a global leader in IoT enablement. Telit… [Continue Reading] -

UK gets an easier way to switch mobile providers
Publié: juillet 1, 2019, 4:15pm CEST par Ian Barker
If you've ever tried to switch mobile phone providers in the UK you'll know that if you want to keep your existing number after the transfer it involves getting a PAC (porting authorization code) from your old provider. Obtaining this has in the past involved phoning them up and having them plead with you not to leave while offering you all kinds of special offers to persuade you to stay. Well not any more. From today UK mobile users who want to switch can get a PAC just by sending a text. The changes have been brought in by telecoms… [Continue Reading] -

Exploring the ethics of AI
Publié: juin 28, 2019, 3:42pm CEST par Ian Barker
Artificial intelligence is appearing in more and more of our everyday technology. But it raises a number of questions about how it will react in challenging situations. Security education comparison site Cyber Security Degrees has produced an infographic looking at the ethics of AI and how we feel about its impact on our lives. Driverless cars for example could potentially save around a million lives a year by eliminating 90 percent of accident fatalities, but there are worries about how it should react when an accident is unavoidable. 76 percent believe driverless cars should save as many lives as possible,… [Continue Reading] -

A smart retro-look microphone for gaming or conferencing -- MXL AC-404-LED [Review]
Publié: juin 28, 2019, 2:54pm CEST par Ian Barker
We are increasingly using our PCs for communication, whether it's making Skype calls or just chatting to other online gamers. But while laptops and some monitors have built in microphones they are not always ideally located or the best quality. If you are serious about the fidelity of your conference calls or whatever then you need to add an external microphone. The MXL AC-404-LED connects to a USB port, it has a pleasingly retro design and it feels nicely weighty thanks to its metal case. There's a soft, rubbery coating on the base so it isn't going to slide around… [Continue Reading] -

Is Google Safe Browsing falling short on mobile?
Publié: juin 27, 2019, 3:33pm CEST par Ian Barker
Google has a pretty good record when it comes to protecting its users against online threats. Part of this is its Safe Browsing technology which scans billions of URLs each day to discover dangerous websites. But research by mobile threat defense specialist Wandera has discovered a disparity between the protections available within Google’s desktop browser compared to its mobile browser. Over a period of eight months, Wandera's threat research team repeatedly found that URLs that were being flagged as 'deceptive sites' when opened through the Google Chrome desktop browser were not being identified as malicious on the Chrome mobile app. The company… [Continue Reading] -

New offering gives enterprises greater flexibility in security training
Publié: juin 27, 2019, 3:17pm CEST par Ian Barker
Cybersecurity is often as much about people as it is about technology. But despite increasing their spending, organizations are still struggling to close the cybersecurity skills gap. Training and certification company Offensive Security is launching a new program for enterprises designed to simplify the cybersecurity training process and allow organizations to invest more in cybersecurity skills development. Called OffSec Flex, it allows users to purchase blocks of practical, hands-on training, certification and virtual lab offerings, allowing them to increase and enhance the level of cybersecurity talent available within their organizations. "Cybersecurity training is not just for security professionals anymore," says… [Continue Reading] -

Data fragmentation is the main reason public cloud doesn't deliver
Publié: juin 26, 2019, 4:40pm CEST par Ian Barker
When IT managers adopted the cloud they believed it would simplify operations, increase agility, reduce costs, and provide greater insight into their data. Yet 91 percent say it hasn't delivered all the expected benefits and 88 percent that it isn't meeting management expectations. A new study of 900 senior decision makers, for data management company Cohesity carried out by Vanson Bourne, finds that of those who feel the promise of public cloud hasn't been realized, 91 percent believe it's because their data is fragmented in and across public clouds and could become nearly impossible to manage long term. Part of… [Continue Reading] -

Major vulnerability found in EA's Origin gaming client
Publié: juin 26, 2019, 3:50pm CEST par Ian Barker
Researchers at Check Point working with CyberInt have uncovered a chain of vulnerabilities in the Origin gaming client developed by Electronic Arts (EA). If exploited, the vulnerabilities could have led to player account takeover and identity theft. Researchers have responsibly disclosed the vulnerabilities to EA, in accordance with coordinated vulnerability disclosure practices, to fix the vulnerabilities and roll out an update before threat actors could exploit the flaw. "Protecting our players is our priority," says Adrian Stone, senior director, game and platform security at Electronic Arts. "As a result of the report from CyberInt and Check Point, we engaged our… [Continue Reading] -

Consumers less willing to share information following privacy scandals
Publié: juin 26, 2019, 3:20pm CEST par Ian Barker
In the wake of privacy scandals like that involving Cambridge Analytica consumers are changing their online behavior and sharing less information. This is among the findings of new research from privacy app FigLeaf which shows 82 percent of online users in the US and 75 percent in the UK are choosing to change the way they behave online. Of these respondents, 74 percent say they are sharing less information. Those who say that recent privacy scandals have had no impact on their online behavior say the prevailing reasons are that they are already highly protective of their information, or that they… [Continue Reading] -

Public cloud workloads set to double by 2021
Publié: juin 26, 2019, 3:04pm CEST par Ian Barker
On average, businesses run 27 percent of their workloads and applications in public clouds and expect this figure to nearly double to 48 percent within the next one to two years, according to a new study. The report from IT marketplace Spiceworks shows 69 percent of businesses believe the flexibility of cloud environments will allow them to more easily adopt emerging technologies such as edge computing, serverless computing, and container technologies. Around a third of businesses say they plan to adopt these technologies by 2020. Adoption rates are even higher in large enterprises -- those with more than 5,000 employees.… [Continue Reading] -

Sumo Logic launches threat benchmarking for AWS
Publié: juin 25, 2019, 5:02pm CEST par Ian Barker
As more and more apps and data move to the cloud, identifying and ranking threats becomes an increasingly difficult task. Machine data analytics platform Sumo Logic is launching a new Global Intelligence Service for Amazon GuardDuty that delivers almost real-time actionable insights to allow customers to benchmark themselves against other adopters of Amazon Web Services cloud infrastructure, strengthen cloud security posture, improve threat detection, and enhance regulatory compliance. "In today's hyper-connected world, organizations are facing rapidly evolving business requirements that demand them to completely rethink their architecture, IT environments and application stacks that comprise the backbone of their businesses," says… [Continue Reading] -

Cloud identity solution lets developers deliver passwordless login and MFA
Publié: juin 25, 2019, 4:16pm CEST par Ian Barker
Identity specialist Ping identity is announcing an update to its PingOne for Customers IDaaS solution that means developers can now deliver passwordless and advanced multi-factor authentication from custom mobile applications. Enhancements include a mobile SDK that allows development teams to send push notifications to custom mobile applications for MFA, APIs for logins via social media accounts, and support for single sign-on via Security Assertion Markup Language (SAML). To comply with GDPR the solution has added a dedicated data center in the European Union, giving enterprises confidence that user data added to the EU data center is completely isolated from users… [Continue Reading] -

Carbon Black adds Linux support and more to its endpoint protection solution
Publié: juin 25, 2019, 3:40pm CEST par Ian Barker
Endpoint protection company Carbon Black is adding a number of features to its platform, including Linux support and Amazon Web Services and container protection. The cloud-native platform gives security and IT teams remote access to cloud workloads and containers running in their environment, making it easier to resolve configuration drift, address vulnerabilities in real time, confidently respond to incidents and demonstrate compliance with business policies and industry regulations. The cloud workload and container protection capabilities are available from the same universal agent and cloud-native platform protecting Microsoft Windows, macOS and Linux endpoints. "The industry is quickly moving into the cloud… [Continue Reading] -

Impersonation attacks focus on payroll and supply chain
Publié: juin 25, 2019, 3:23pm CEST par Ian Barker
Impersonating a company's CEO or other senior executive has become a favorite technique for cybercriminals seeking to extract payments from businesses. Historically this has been aimed at accounts payable departments, but the latest email threat report from FireEye shows attackers using two new variants to target payroll and supply chains. The payroll variant targets the department with an email requesting changes to an executive’s personal data, such as bank details, with the objective of diverting an executive’s salary to a third-party account. While the supply chain version targets the accounts payable department by impersonating an email from a trusted supplier… [Continue Reading] -

Vulnerable software components widely used by enterprises
Publié: juin 25, 2019, 11:36am CEST par Ian Barker
The average UK enterprise has downloaded over 21,000 software components with a known vulnerability in the past year alone, according to new data from Sonatype the DevSecOps automation specialist. Sonatype's fifth annual State of the Software Supply Chain Report has studied over 12,000 enterprise development companies globally and shows that of the average 248,000 open source components downloaded by British business in 2018, 8.8 percent have a known security flaw. Of these vulnerabilities, 30 percent -- some 6300 -- are deemed to be critical, posing a serious risk to the security of software. Adversaries are increasingly targeting open source components… [Continue Reading] -

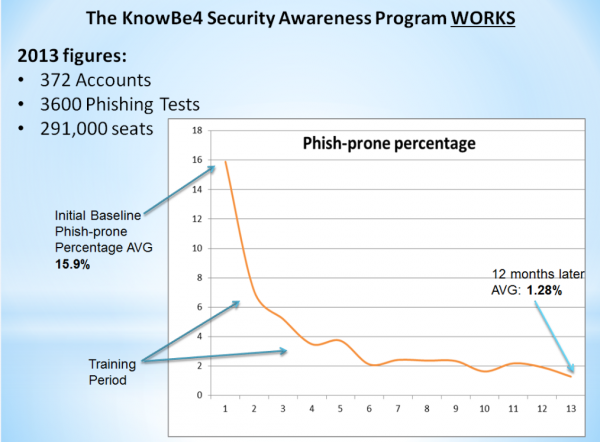
Lack of awareness training raises phishing risk
Publié: juin 24, 2019, 3:40pm CEST par Ian Barker
We know that phishing attacks are gaining in sophistication and are one of the most popular ways of hackers and cybercriminals gaining access to an organization's systems. But this type of attack is notoriously difficult to guard against using technology and employee awareness is a big part of any business' defense strategy. This is underlined by a new report from awareness training company KnowBe4 which looks at the level of risk and finds that 29.6 percent of organizations are 'phish-prone'. The construction industry is particularly at risk, with 38 percent of small companies and 37 percent of smaller companies being… [Continue Reading] -

Is technology harming our ability to write?
Publié: juin 20, 2019, 4:35pm CEST par Ian Barker
The pen may be mightier than the sword, but it seems that because of technology our writing skills may be about to go the same way as our swashbuckling. Stationery supplier www.euroffice.co.uk has polled over 2,400 Brits to find out how people feel about their handwriting, how frequently they write and if technology is killing the hand written word. When asked about their handwriting just 15 percent of people thought it was good. However, a much larger set of people rate themselves poorly, with 42 percent saying their handwriting was bad and 35 percent that it was terrible. When asked… [Continue Reading] -

Cloud-based security service offers web app and API protection
Publié: juin 20, 2019, 3:03pm CEST par Ian Barker
Web app and API exploits are among the leading threats to business at the moment. Organizations with a major web presence face malicious traffic and sophisticated bots trying to damage their brands. In order to protect against these threats, Instart is launching a new Web App and API Protection (WAAP) platform. This is a cloud-based platform, powered by a single rules engine and a unified threat intelligence system, to defend against application vulnerabilities, sophisticated bots, and browser-based attacks. "While modern web apps bring immeasurable benefits to consumers, they also add significant complexity to IT organizations looking to secure them and… [Continue Reading] -

Parents' lack of cybersecurity knowledge holds back children's career choices
Publié: juin 20, 2019, 11:42am CEST par Ian Barker
The majority of UK parents are in the dark when it comes to advising their children on a career in cybersecurity, research from cybersecurity training provider, SANS Institute, shows. Although IT remains one of the top choices of career that parents would make for their children, parents have very little idea about the lucrative area of cybersecurity. This is exacerbating the skills gap in cyber security that the UK is currently facing -- with the industry not doing enough to promote itself. According to the research, 72 percent of parents have never considered a career in cybersecurity for their children,… [Continue Reading] -

Artificial intelligence -- for good or evil?
Publié: juin 19, 2019, 5:00pm CEST par Ian Barker
AI is popping up in all sorts of things at the moment, but what happens when it goes wrong or is used for questionable purposes? A new report from Malwarebytes Labs looks at how AI is being used, with a particular emphasis on cybersecurity, and at the concerns that are growing surrounding its use. For the security industry, AI has the ability to process large volumes of data and therefore help combat the growing number of new malware variants being deployed every day. This can help with smart detections and freeing up researchers to focus on deeper analysis of more… [Continue Reading] -

Linux Mint vs Windows 10 -- which is best for small business productivity?
Publié: juin 19, 2019, 4:59pm CEST par Ian Barker
If you're using an old computer in your small business, the likelihood is that you don't have a great deal of money to splash on powerful hardware. You might therefore be tempted to look for extra performance by using Linux -- and save on the cost of buying the OS into the bargain. But is there really that much of an advantage? James Mawson of Australian site DXM Tech Support has conducted a series of tests to find out. Using a basic HP 245 G6 with an AMD E2-9000e processor set up to dual boot, he ran the same tasks using… [Continue Reading] -

Security assurance needs a business-focused approach
Publié: juin 19, 2019, 3:00pm CEST par Ian Barker
Business leaders want to be confident that their operations will continue running as normal without information being compromised. But in today’s fast-moving, interconnected world where the threat landscape is constantly evolving, security assurance programs often provide a false level of confidence. The Information Security Forum (ISF) is releasing a new report, Establishing a Business-Focused Security Assurance Program which explores how individuals responsible for providing security assurance in their organization can meet the specific needs of business stakeholders. "Taking a business-focused approach to security assurance is an evolution. It means going a step further and demonstrating how well business processes, projects… [Continue Reading] -

New platform brings together technologies to improve enterprise cybersecurity
Publié: juin 18, 2019, 3:47pm CEST par Ian Barker
Cybersecurity tools are often designed to work in isolation from each other and that can leave enterprise security operations fragmented as well as difficult and expensive to manage. A new integrated platform called GreyMatter from ReliaQuest, launched today, aims to bring together technologies, processes and teams to provide greater visibility and control over enterprise security operations. "ReliaQuest understands that a security team's strategy must deliver consistency for the business while also constantly evolving, and we are committed to providing the necessary technologies and ongoing support that our customers need to achieve that difficult balance," says Brian Murphy, CEO of ReliaQuest.… [Continue Reading] -

The impact of data privacy on the healthcare industry
Publié: juin 18, 2019, 12:41pm CEST par Ian Barker
Healthcare companies are constantly consuming and sharing information to build better patient profiles and improve outcomes. Yet a new report reveals that only 70 percent are very or extremely confident in knowing exactly where their sensitive data is. The study from data privacy specialist Integris shows that of these 50 percent update their inventory of personal data once a year or less, and a mere 17 percent of respondents are able to access sensitive data across five common data source types. Data privacy has a wider impact on businesses too. Proving compliance with business obligations like data sharing agreements is… [Continue Reading] -

The biggest data breaches of the last 15 years
Publié: juin 17, 2019, 5:23pm CEST par Ian Barker
We've become pretty well accustomed to large scale data breaches over recent years. But that doesn’t mean that the numbers involved aren't still significant. Web hosting comparison site HostingTribunal has put together an infographic looking at the 15 biggest breaches of the last 15 years. More than 14,717,618,286 records have been lost or stolen since 2013 due to data breaches, and 3,353,178,708 records were compromised in the first half of 2018 alone. In 2017, 86 percent of all breaches worldwide occurred in North America, and in 2018 45.9 percent of data breaches in the US were in the business sector.… [Continue Reading] -

Humans are still the weakest link in information security
Publié: juin 17, 2019, 11:38am CEST par Ian Barker
According to a new report, more than half of all C-suite executives (53 percent) and 28 percent of small business owners who suffered a data breach say that human error or accidental loss by an external vendor/source was the cause. The annual data protection report from information security service Shred-It also finds 21 percent of executives and 28 percent of small business owners admit deliberate theft or sabotage by an employee/insider was the cause of the data breach. This compares to 43 percent of executives and 31 percent of SBOs who say deliberate theft or sabotage by an external vendor… [Continue Reading] -

Organizations urged to patch for BlueKeep as latest malware charts are revealed
Publié: juin 13, 2019, 3:22pm CEST par Ian Barker
Check Point Research, has released its Global Threat Index for May 2019 and is warning organizations to check and patch for the BlueKeep Microsoft RDP flaw in Windows 7 and Windows Server 2008 machines, to prevent the risk of it being exploited for ransomware and cryptomining attacks. BlueKeep affects nearly a million machines accessible to the public internet and many more within organizations' networks. The vulnerability is critical because it requires no user interaction in order to be exploited. RDP is already an established, popular attack vector which has been used to install ransomware. "The biggest threat we've seen over… [Continue Reading] -

Computer downtime is biggest workplace irritant
Publié: juin 13, 2019, 12:06pm CEST par Ian Barker
Computer downtime ranks as the most significant irritant in the workplace according to a new survey. The study of employees at 500 UK businesses carried out by YouGov for Cherwell Software finds 41 percent naming downtime, ahead of forgotten passwords (23 percent), the lack of parking spaces (22 percent) or stolen meeting rooms (15 percent). When asked to pick their top two information technology frustrations, slow response times to fixing computer problems was named by 29 percent and the difficulty of reaching IT staff by 24 percent. On the question of who should be held most accountable for a major… [Continue Reading] -

Security startup aims to provide better visibility into the cloud
Publié: juin 12, 2019, 4:08pm CEST par Ian Barker
As businesses move more of their systems to the cloud to drive digital transformation and gain a competitive edge, IT security teams can struggle to retain the ability to secure data and manage risk. Israeli startup Orca Security is announcing its Cloud Visibility Platform which uses patent-pending SideScanning technology to deliver comprehensive visibility into the security posture of an organization's cloud footprint in a matter of minutes. It uses a single, simple integration into the cloud infrastructure layer to automatically assess the security state of every discovered asset throughout the entire technology stack. It takes in the entire cloud control… [Continue Reading] -

New API network adapters allow for greater automation
Publié: juin 12, 2019, 3:21pm CEST par Ian Barker
Among the top networking challenges for enterprises are lack of skills, fragmented management tools and lack of end-to-end network visibility. Network automation specialist Itential is launching new purpose-built API adapters for Cisco systems that offer support for third party management tools and provide enterprises and service providers with a single network API that simplifies integration and enables end-to-end automation across complex, multi-domain and multi-vendor environments. "Network automation is inherently a multi-domain problem as the vendor ecosystem continues to introduce a litany of controllers and orchestrators as the new management plane," says Chris Wade, Itential's CTO. "Itential is focused on minimizing… [Continue Reading] -

LastPass Business brings single sign-on to over 1200 apps
Publié: juin 11, 2019, 3:41pm CEST par Ian Barker
Hundreds of cloud applications are being used in businesses and IT teams are pressured to achieve high levels of security without introducing complex authentication processes that may reduce workforce productivity. LogMeIn, developer of the LastPass password management program is launching a new suite of LastPass Business solutions delivering a comprehensive identity offering, built for small and medium sized businesses. It introduces new single sign-on technology for more than 1,200 apps pre-integrated into the solution as well as existing password management capabilities. In addition there's LastPass MFA, an adaptive, biometric-based authentication solution, and LastPass Identity, a unified access and authentication solution… [Continue Reading] -

New enterprise platform secures digital assets in transit
Publié: juin 11, 2019, 3:12pm CEST par Ian Barker
Last month $40 million worth of Bitcoin was stolen in the Binance hack and it's estimated that more than $3 billion has been stolen over the last 18 months due to key theft and stolen credentials. In order to guard against this type of theft, new company Fireblocks is launching an enterprise platform to protect crypto currency and other digital assets in transit. "While Blockchain based assets by themselves are cryptographically secure, moving digital assets is a nightmare. After interviewing over 100 institutional customers, including hedge funds, broker-dealers, exchanges, and banks, we concluded that the current process is slow and… [Continue Reading] -

Over three billion fake emails sent out daily
Publié: juin 11, 2019, 1:15pm CEST par Ian Barker
At least 3.4 billion fake emails are sent around the world every day, according to a new report from email verification company Valimail, with the majority of suspicious emails coming from US-based sources. The report shows that email impersonation -- accounting for 1.2 percent of all email sent in the first quarter of 2019 -- is a phishing attacker's primary weapon to gain access into an organization's network, systems, intellectual property and other sensitive assets. The fake email problem -- which is not easily blocked by traditional cybersecurity defenses -- can be tackled by implementing widely accepted email authentication standards.… [Continue Reading] -

Wi-Fi past, present and future
Publié: juin 10, 2019, 4:39pm CEST par Ian Barker
Wireless networking is something we've come to take for granted in recent years. ISPs often give away a wireless router when you sign up for an internet connection with the consequence that Wi-Fi is now in most homes. Networking specialist Netgear has produced an infographic looking at the origins of Wi-Fi, how it's developed and where it’s going in future. The idea of wireless communication goes back to the 1920s, but practical applications for networking didn't start to appear until the early 1970s. The first large-scale Wi-Fi network was installed in 1993 and since then adoption has been rapid and… [Continue Reading] -

Want someone's personal data? Give them a free donut
Publié: juin 7, 2019, 4:53pm CEST par Ian Barker
While you might expect Homer Simpson to hand over personal details in exchange for a donut, you wouldn't expect cybersecurity professionals to do the same. However, technology services provider Probrand has carried out a study at a cyber expo attended by UK security professionals, where attendees voluntarily shared sensitive data including their name, date of birth and favourite football team -- all to get their hands on a free donut. This follows recent news that millions of accounts are still using '123456' as a password, with people's names, favourite football teams and favourite bands also commonly employed. "We wanted to put this… [Continue Reading] -

Biggest hindrance to enterprise network visibility is lack of IT staff
Publié: juin 6, 2019, 4:06pm CEST par Ian Barker
Network performance monitoring specialist AppNeta has released its 2019 State of Enterprise IT Report, which finds that as enterprise IT deals with fundamental changes networking infrastructure teams are being stretched to the limit. The biggest hindrances to network visibility are seen as lack of IT staff (25.6 percent), poor network management tools, (24.8 percent) and lack of visibility into app delivery paths (24.7 percent). These lead to problems with resolving issues, and 40 percent of respondents say that these lead to employee frustration, with another 25 percent experiencing a loss in overall productivity. IT teams are also have to deal… [Continue Reading] -

Dark net malware becomes more targeted
Publié: juin 6, 2019, 3:10pm CEST par Ian Barker
The dark net has become a haven for custom-built, targeted malware, with threats tailored to specific industries or organizations outnumbering off-the-shelf varieties by two to one, according to a new study. The research from application containment company Bromium also finds four in 10 dark net vendors are selling targeted hacking services aimed at FTSE 100 and Fortune 500 businesses. "The dark net has become a veritable candy store for anyone looking to steal IP and corporate data or disrupt business operations," says Gregory Webb, CEO of Bromium. "A world once dominated by off-the-shelf malware has been replaced by a service-driven,… [Continue Reading] -

SecureAuth enhances identity management with intelligent cloud service
Publié: juin 6, 2019, 12:16pm CEST par Ian Barker
Secure identity company SecureAuth is launching enhancements to its solution with the announcement of Intelligent Identity Cloud. This gives CISOs and IT professionals the ability to deploy the same capabilities in the cloud, on-premises, or as a hybrid of the two, addressing business demands of agility and dramatically improving identity security. The Intelligent Identity Cloud service is included as part of all SecureAuth Identity Platform deployments whether hybrid, on-premises or cloud. The automated cloud-based service includes a broad set of adaptive authentication risk checks that use a big-data approach and machine learning to improve identity security by recognizing legitimate users… [Continue Reading] -

81 percent of SMEs think AI is crucial to cyber security
Publié: juin 3, 2019, 11:04am CEST par Ian Barker
New research from threat detection specialist Senseon looking at the state of cyber security in SMEs reveals increasing uncertainty about whether the investment into the security solutions they’re currently using is worth the cost. The survey also reveals that SMEs have been slow to implement AI solutions, despite the vast majority of SMEs surveyed (81 percent) thinking that AI will be fundamental to the future of cyber security. Although 88 percent of SMEs do have a dedicated security budget, more than half (53 percent) think increased budget would help them deal with their cyber security workload. However, budgetary constraints are… [Continue Reading] -

Staff break IT rules in order to do their jobs with management the worst offenders
Publié: mai 31, 2019, 12:51pm CEST par Ian Barker
A new survey of more than 3,000 people around the world finds 46 percent of employees access personal documents on their work device without the IT department's permission. The study from Snow Software also shows 41 percent of global employees are going behind IT's back to get professional software and applications. Interestingly management-level employees (manager, director, vice president or executive) are almost twice as likely to use unauthorized professional or personal software and applications. Vice presidents and C-level executives lead the way in using work apps (57 percent) and personal apps (51 percent) on their work devices without permission. Entry-level… [Continue Reading] -

Why digital transformation must be optimized for speed and success [Q&A]
Publié: mai 31, 2019, 11:12am CEST par Ian Barker
Companies worldwide across all industries are enacting digital transformation (DX) initiatives -- and for good reason. If completed successfully, modern technology implementation drives competitive advantage and makes business operations much more real-time. However, the journey to the DX finish line is unfortunately sometimes much more of sprint than a marathon, as speed is the currency for organizations to complete the process. This begs the question, how can business leaders implement a swift digital transformation while reaping the success and benefits that these initiatives promise? We spoke with Jamshid Rezaei, CIO of business communications specialist Mitel, to get the answer to… [Continue Reading] -

New tool allows files to be encrypted and shared wherever they’re stored
Publié: mai 30, 2019, 3:04pm CEST par Ian Barker
One of the best ways of preventing sensitive files from falling into the wrong hands is to encrypt them, but the process of encrypting and decrypting can be a chore, especially if you want to share the information. VPN service NordVPN is set to launch its own NordLocker security tool, designed to safeguard files whether they are stored locally or in the public cloud, and make them easy to share. "We at NordVPN believe that the digital environment must be better than it is today. As a company, we strive to move towards becoming an all-around cybersecurity solution that people… [Continue Reading] -

More than 70 percent of consumers fear becoming ID theft victims
Publié: mai 29, 2019, 4:54pm CEST par Ian Barker
The more the internet has become essential to our daily lives, the more people are waking up to the threats that it poses to their safety. In a new study by F-Secure, 71 percent of respondents say they feel that they will become a victim of cybercrime or identity theft, while 73 percent express similar fears about their children. The survey finds that over half of the consumers have had a family member affected by some form cybercrime (51 percent). Malware or viruses are the most common threats encountered followed by credit card fraud and then SMS/call fraud. One out… [Continue Reading] -

Identity and access management proving too difficult for many businesses
Publié: mai 29, 2019, 2:53pm CEST par Ian Barker
According to a new study, businesses find identity and access management (IAM) and privileged access management (PAM) among their most difficult operational tasks. The survey, by access management firm One Identity, of 200 attendees to the 2019 RSA Conference, finds that while a third of respondents say PAM is the most difficult operational task, only 16 percent of respondents cite implementing adequate IAM practices as a top-three concern when it comes to securing the cloud. In addition just 14 percent of survey respondents say better employee access control would have a significant impact on their cybersecurity. All of which suggests… [Continue Reading] -

GDPR one year on -- what have we learned and what happens next?
Publié: mai 24, 2019, 3:11pm CEST par Ian Barker
This weekend marks exactly a year since the introduction of the EU's GDPR legislation shook up the world of data protection and sent businesses around the world into a flurry of compliance activity. So, what has the industry learned over the past year and what are the ongoing challenges we can expect to see? We've gathered the views of some industry experts. It's clear that the introduction of GDPR has led to greater awareness when it comes to protecting personal information. Dr Gero Decker, CEO and co-founder of business transformation specialists Signavio, says, "A year on, businesses now understand what… [Continue Reading] -

How microsegmentation can deliver zero trust security [Q&A]
Publié: mai 24, 2019, 11:21am CEST par Ian Barker
With a never-ending supply of new security threats presenting themselves every day, it can be tough for IT departments to keep up. While perimeter security continues to be important, the sheer volume of novel attacks means that, eventually, an attack will bypass defenses and gain a foothold in the interior. To harden the network interior, best practice now calls for microsegmentation to achieve a zero trust environment, but that’s not easy to do. To get more information on today’s security landscape, we spoke with Peter Smith, the chief executive officer of Edgewise Networks, a security solution provider of zero trust… [Continue Reading] -

Quality issues with training data are holding back AI projects
Publié: mai 23, 2019, 3:58pm CEST par Ian Barker
For many organizations, AI and machine learning are seen as a route to greater efficiency and competitive advantage. But according to a new study conducted by Dimensional Research for Alegion almost eight out of 10 enterprise organizations currently engaged in AI and ML report that projects have stalled, and 96 percent of these companies have run into problems with data quality, data labeling required to train AI, and building model confidence. "The single largest obstacle to implementing machine learning models into production is the volume and quality of the training data," says Nathaniel Gates, CEO and co-founder of Alegion, a… [Continue Reading] -

Why change management is essential to digital transformation projects [Q&A]
Publié: mai 23, 2019, 3:10pm CEST par Ian Barker
Digital transformation is currently an attractive option for many businesses. But to make it work it needs to be effectively managed. We spoke to Nital Hooper, senior manager consulting at consultancy company Servita to find out about the importance of change management to successful digital transformation. BN: Can you achieve transformation without change management? NH: As Sinatra would say, 'you can't have one without the other'. Change management, often seen as the fluffy part of transformation, is the love to the marriage of vision, strategy and IT. Usually we see no investment in change management, or when we do, it’s… [Continue Reading] -

72 percent of cyber security professionals have considered quitting over lack of resources
Publié: mai 23, 2019, 11:39am CEST par Ian Barker
A new study from Censornet into the challenges facing cyber security professionals shows that 79 percent think their companies are suffering from a lack of resources, both in terms of people and technology, and 72 percent have considered leaving their jobs for this reason. The survey also finds that security professionals are not being helped by their security solutions. 65 percent want more technology but the average number of security products used is already 33 and 57 percent report they are suffering from alert overload. What's more, ineffective cyber security technology is the joint second threat facing organizations, alongside unexpected… [Continue Reading] -

DDoS attacks increase 84 percent in three months
Publié: mai 21, 2019, 4:46pm CEST par Ian Barker
The number of DDoS attacks during the first quarter of 2019 increased by 84 percent compared with the previous quarter according to a new report from Kaspersky Lab. This reverses last year's trend of declining DDoS attacks as attackers shifted their attention to other sources of income, such as crypto-mining. As well as increasing in number attacks are also getting longer. The number of DDoS attacks that lasted for more than an hour doubled in quantity, and their average length increased by 487 percent. These statistics confirm Kaspersky Lab experts’ hypothesis that hackers are evolving their techniques and are now… [Continue Reading] -

A traditional approach to security harms digital transformation efforts
Publié: mai 21, 2019, 3:54pm CEST par Ian Barker
Half of security professionals who adopt a more traditional or reactive approach to their data protection and security don't believe they will reach their digital transformation goals in the next five years. This is among the findings of a report from data protection company TITUS which conversely finds that nine out of 10 security professionals deploying a strategic approach believe their current efforts will address digital transformation needs within five years and that their organization would achieve its digital transformation goals in the same timescale. "In speaking with organizations of all sizes, it's clear there are two approaches to security --… [Continue Reading] -

Enterprises struggle with providing secure hybrid access
Publié: mai 21, 2019, 2:53pm CEST par Ian Barker
As businesses move towards hybrid IT environments they increasingly face threats, gaps and investment challenges to keep their systems secure. The study from secure access specialist Pulse Secure surveyed enterprises with 1000+ employees in the US, UK, Germany, Austria and Switzerland and finds that while they are taking advantage of cloud computing, all enterprises have on-going data center dependencies. The most severe incidents come from a lack of user and device access visibility and lax endpoint, authentication and authorization access controls. Over the last 18 months, half of all companies surveyed dealt with malware, unauthorized/vulnerable endpoint use, and mobile or web… [Continue Reading] -

Most enterprises now run containers in production
Publié: mai 21, 2019, 12:12pm CEST par Ian Barker
New research from storage and data management company Portworx shows 87 percent of IT professionals are now running container technologies, with 90 percent of those running in production. In addition seven out of 10 are running at least 40 percent of their application portfolio in containers -- an increase from two years ago, when just 67 percent of teams were running container technologies in production. Yet despite their pervasiveness, containers aren't without issues. When asked to name their top challenges to container adoption, respondents most frequently cited security (51 percent), data management (40 percent) and cross-cloud/multiple cloud support (36 percent).… [Continue Reading] -

UK age verification rules could put users at risk
Publié: mai 21, 2019, 11:11am CEST par Ian Barker
With age verification checks for users of adult sites in the UK set to come into force this summer, cyber security company F-Secure says that the new rules could increase the risk of identity theft and other cyber crimes. Under the new laws, British internet users will be required to verify their age in order to access adult content websites. This could be by sharing personal information such as passport, driving license, phone number or credit card details with third-party age verification platforms, or by buying a 'porn pass' at a store. "Preventing kids from accessing certain types of online… [Continue Reading] -

New self-service platform helps developers apply AI at the edge
Publié: mai 17, 2019, 2:44pm CEST par Ian Barker
In the past AI has mostly depended on expensive solutions running in the cloud, restricting its use to a relatively small number of companies. But with the growth of the IoT and ever greater volumes of information that need to be processed fast, there's more demand for AI at the edge. Xnor is launching a new self-service platform called AI2GO, that enables developers, device creators and companies to build smart, edge-based solutions without needing training or background in AI. The platform offers hundreds of fully-trained edge AI models, so developers no longer need to worry about data collection, annotation, training,… [Continue Reading] -

Application development industry faces major challenges
Publié: mai 16, 2019, 4:02pm CEST par Ian Barker
Demand for application development is soaring, but the industry faces some major challenges according to a new report. The study from OutSystems shows the number of applications slated for delivery in 2019 has increased by 60 percent, and 38 percent of respondents plan to deliver 25 or more apps this year. But with this demand come problems, 46 percent of respondents say the average time to deliver a web or mobile application is five months or more. Not surprising then that 64 percent of IT professionals say they have an app dev backlog, and only 39 percent say their backlog… [Continue Reading] -

Half of companies missed GDPR compliance deadline
Publié: mai 16, 2019, 3:09pm CEST par Ian Barker
Only half of companies achieved compliance with GDPR before the May 25, 2018 deadline, and most companies took seven months or longer to achieve readiness. This is among the findings of a new report from privacy management platform DataGrail which also reveals that two-thirds of companies assigned dozens, or even hundreds, of employees to manage GDPR compliance. Based on survey results, it's likely the average organization spent 2000 to 4000 hours in meetings preparing for GDPR, while half of privacy management decision makers spent at least 80 hours personally preparing for GDPR, and another 80 hours to sustain compliance "Businesses… [Continue Reading] -

UK consumers want businesses to do more to protect their data
Publié: mai 16, 2019, 12:49pm CEST par Ian Barker
Protecting your digital footprint is growing more important and the results from a survey of 2,000 UK adults by Kaspersky Lab finds that people believe there is not enough business or state protection currently in place to defend it. The study finds 41 percent of UK respondents think that businesses should do more to protect their personal data, including passwords, addresses and bank account details, from hacking. More than a quarter think there is not enough state support with regards to data security and cyber-protection and 12 percent have been so concerned by a high-profile data breach that they have… [Continue Reading] -

Four out of five people expect Facebook to have another data privacy issue this year
Publié: mai 15, 2019, 4:28pm CEST par Ian Barker
People are becoming more aware of the need to protect their data online, not just because of the rate of cybercriminal activity, but also because large organizations are frequently being careless with the data they hold. A new survey of 1,000 people from OpenVPN reveals that four out of five people are expecting Facebook to face at least one more data privacy issue in the next year. In addition 71 percent say recent scandals have somewhat or severely negatively affected their view on Facebook, while 37 percent trust tech giants less now because they don’t think the companies have properly… [Continue Reading] -

New tool helps protect sensitive data on Oracle databases
Publié: mai 15, 2019, 3:15pm CEST par Ian Barker
With GDPR in effect and privacy regulations being planned in other parts of the world, many organizations are looking at their database management to ensure stored data is complaint and doesn’t threaten the business. For Oracle users, Quest Software is launching its Toad for Oracle -- Sensitive Data Protection (SDP) Module. This allows database admins to to detect and receive notification of personally identifiable information (PII) data residing in databases, select encryption and redaction options immediately after detection, and perform ongoing monitoring "Manual methods to identify personal data are ineffective and put companies at risk. When non-compliance penalties for GDPR… [Continue Reading] -

Perception vs reality in web security
Publié: mai 15, 2019, 1:44pm CEST par Ian Barker
A new study from Harris Poll, commissioned by Google shows that while more people than ever are using the internet -- with 1.4 billion expected to be online by 2022 -- there's a gap between perception and reality in regard to online safety. In the study 55 percent of Americans aged 16 or over gave themselves an A or B in online safety and security, but the results don't back this up. 70 percent wrongly identified what a safe URL should look like and 97 percent got at least one question wrong on a basic six-question security test. Among 16-24 year… [Continue Reading] -

How open source is helping removing data silos in the enterprise [Q&A]
Publié: mai 14, 2019, 5:31pm CEST par Ian Barker
Historically data has been stored in silos in order to deliver a quick solution. But in the longer term silos can slow down decision making, make modifying systems harder, and hinder compliance with regulations. One of the ways to break down barriers between silos is to allow data to be freely shared between them and open source has a big part to play in this. We spoke to Mandy Chessell, distinguished engineer at IBM Cognitive Applications, and recently elected leader of the Technical Steering Committee of the ODPi, to learn more. BN: The current mindset seems to be that all… [Continue Reading] -

How open source is helping remove data silos in the enterprise [Q&A]
Publié: mai 14, 2019, 5:31pm CEST par Ian Barker
Historically data has been stored in silos in order to deliver a quick solution. But in the longer term silos can slow down decision making, make modifying systems harder, and hinder compliance with regulations. One of the ways to break down barriers between silos is to allow data to be freely shared between them and open source has a big part to play in this. We spoke to Mandy Chessell, distinguished engineer at IBM Cognitive Applications, and recently elected leader of the Technical Steering Committee of the ODPi, to learn more. BN: The current mindset seems to be that all… [Continue Reading] -

46 percent of organizations consider taking personal data out of the cloud
Publié: mai 14, 2019, 4:09pm CEST par Ian Barker
A new study finds that 46 percent of organizations which store customer personally identifiable information (PII) in the cloud are considering moving it back on premises due to data security concerns. The research from information security software company Netwrix also shows that of the 50 percent of organizations that store customer data in the cloud, 39 percent had security incidents in the past year and more than 50 percent of those couldn’t diagnose the problem. Among other findings are that although 50 percent of respondents store PII of customers and employees in the cloud, far fewer are willing to store… [Continue Reading] -

AI-driven platform brings automation to field service organizations
Publié: mai 14, 2019, 3:17pm CEST par Ian Barker
As technology becomes increasingly complex and more devices are connected to the IoT, so the volume and complexity of field service requests increases too. To help deal with this, automation company Zinier is launching its new Intelligent Service Automation and Control (ISAC) platform, an AI-driven solution enabling field service organizations to operate more efficiently. The ISAC platform uses machine learning to analyze data and provide real-time insights, driving productivity and enabling customers to inject automation into the service delivery chain. By comparing a constant flow of field data against historical trends, ISAC can recommend the best course of action at… [Continue Reading] -

Website attacks turn to stealth to boost their success
Publié: mai 13, 2019, 5:15pm CEST par Ian Barker
The story of website attacks in 2018 was one of high profile cybercrime, targeted at cryptocurrency, business, elections and more. A new report from website security specialist SiteLock reveals that attackers are now taking a stealthier approach. Websites experienced 62 attacks per day on average in 2018 from more than 330 bots. Despite the high volume of attacks though the number of infected websites remained constant at one percent throughout 2018, equating to 17.6 million websites worldwide at any given time. How likely a site is to be compromised is down to its risk factors. SiteLock uses a proprietary Risk Assessment,… [Continue Reading] -

Rock Jaw T5 Ultra Connect wireless earphones [Review]
Publié: mai 10, 2019, 4:03pm CEST par Ian Barker
Previously when we've reviewed earphones from Rock Jaw we've found them to be a good compromise between affordability and performance. The T5 Ultra Connect is the first wireless product we've seen from the firm, so we were keen to find out how they measure up. As always with this brand the packaging makes you feel you're buying a quality product. In the box you get the earphones themselves, three sets of different sized rubber tips, plus three sets of 'Comply' noise isolating memory foam tips, a mesh pouch, a USB cable and -- as with other Rock Jaw products we've… [Continue Reading] -

Is latency the cloud's Achilles heel? [Q&A]
Publié: mai 10, 2019, 11:10am CEST par Ian Barker
The cloud is arguably the most transformative enterprise technology in the past two decades. Yet, as powerful as it is, it faces a huge latency problem -- and the big public cloud providers know it. Their data centers can't be everywhere and close to every end-user, so the big distances created result in unavoidable latency. On its own, the public cloud can't power smart cities, autonomous vehicles, primary storage or any other application that requires a predictable, high-speed response for large data sets that reside in many locations. A self-driving car can't wait seconds for data it sends to the… [Continue Reading] -

Uncovering the everyday frustrations of cybersecurity professionals
Publié: mai 9, 2019, 4:26pm CEST par Ian Barker
Anyone who has worked in IT knows that it can be a frustrating experience at times. A new survey carried out by network security provider Lastline at RSAC 2019 set out to discover security professionals' attitudes and frustrations towards their jobs. These come from a number of places, including resources, management and other workers. We all know that there's a skills shortage in security, but funding is often an issue too. Only two percent of those surveyed say they already have adequate funding. However, over a quarter of those surveyed (28 percent) think it wouldn't take much to get additional… [Continue Reading] -

Americans are overconfident about cybersecurity
Publié: mai 8, 2019, 12:21pm CEST par Ian Barker
A new study from Webroot that examines the cyber hygiene habits of 10,000 Americans, 200 in each state, reveals that 88 percent feel they take the right steps to protect themselves from cyberattacks. However, just 10 percent scored 90 percent or higher on a cyber hygiene test, with the average respondent getting only 60 percent. Digging deeper into the findings, 79 percent of Americans say they have heard of malware, but only 28 percent could explain what it is. Similarly 70 percent have heard of phishing, but only 33 percent could explain what it is, and 49 percent have heard… [Continue Reading] -

Shining a light onto the dark web
Publié: mai 7, 2019, 5:23pm CEST par Ian Barker
The dark web is, by its very nature something of an object of mystery. It's easy to think of it as a huge, closed community hidden from the world in dusty corners of the internet. But what's the reality? Threat intelligence specialist Recorded Future has done some research to try to understand the dark web's true nature. The company spidered around 260,000 onion pages to approximate the full reachable Tor network from a starting set of onion sites that it pulled from public lists and its own content. What it found is that the dark web is in fact rather… [Continue Reading] -

New risk assessment capabilities help secure containers
Publié: mai 7, 2019, 4:08pm CEST par Ian Barker
Container security company NeuVector is releasing new security risk assessment capabilities for enterprises using Kubernetes in production environments. The features, added to its existing container security offering, include new dashboard widgets and downloadable reports to provide security risk scores for the most critical run-time attack risks, network-based attacks and vulnerability exploits in containers. An overall risk score summarizes all available risk factors and provides advice on how to lower the threat of attack -- thus improving the score. A service connection risk score shows how likely it is for attackers to move laterally to probe containers that are not segmented… [Continue Reading] -

Companies continue to struggle with privileged access management
Publié: mai 7, 2019, 3:20pm CEST par Ian Barker
Privileged accounts can be a headache for organizations so you'd expect managing them to be a high priority for security teams. However, a new report from Thycotic reveals that 85 percent fail to achieve even basic privileged security hygiene. In addition 55 percent have no idea how many privileged accounts they have or where they’re located, while over 50 percent of their privileged accounts never expire or get deprovisioned. Of the 450 organizations surveyed at the 2019 RSA conference, just 18 percent are storing all their privileged accounts in a secure privileged access management (PAM) vault or password manager. Among… [Continue Reading] -

97 percent of companies now use agile development methods
Publié: mai 7, 2019, 1:40pm CEST par Ian Barker
Agile is clearly becoming the norm in the development community according to the findings of a new report from CollabNet VersionOne which has been charting the agile landscape for 13 years. The report shows 97 percent of organizations now practicing agile development methods. That's not to say its use is universal, however, only 22 percent of respondents report that all their teams are agile, 26 percent more than half and 48 percent less than half. Accelerating software delivery is given as the top reason for adoption (cited by 74 percent of respondents), but other reasons include improving team morale (34… [Continue Reading] -

Reported data breaches up more than 56 percent
Publié: mai 7, 2019, 11:41am CEST par Ian Barker
According to the latest Data Breach Report from Risk Based Security the number of reported data breaches was up 56.4 percent in the first quarter of 2019 compared to the same period last year. The increase in reporting could be a result of new legislation like GDPR that obliges businesses to be more open about security issues. The number of exposed records was also up by 28.9 percent. Already in 2019, there have been three breaches exposing 100 million or more records. The report shows 1,903 breaches were reported through March 31, in total exposing approximately 1.9 billion records. For… [Continue Reading] -

Microsoft announces Internet Explorer mode for Edge to aid enterprise compatibility
Publié: mai 6, 2019, 6:20pm CEST par Ian Barker
As part of this week's Build 2019 Microsoft is announcing a number of enhancements to the Edge browser including an Internet Explorer mode for enterprises. This is aimed at cutting the need for IT staff to manage multiple solutions. Allowing legacy IE-only content -- such as intranet sites -- to be opened in Edge without the need to change any settings or launch a different browser. "We hear from our customers that most enterprises rely on a multiple-browser solution today, and we hear from our customers and partners that this experience is disjointed and confusing," says Kyle Pflug, senior PM… [Continue Reading] -

Why firewalls still matter [Q&A]
Publié: mai 6, 2019, 5:29pm CEST par Ian Barker
Firewalls have been used to protect networks and endpoints from the very early days of the web. In recent years many people have been predicting its demise, yet the firewall is still with us. Why is this and how has the firewall evolved to protect enterprises in the 21st century? We spoke to Ruvi Kitov, founder and CEO of network security specialist Tufin to find out. BN: Why has the firewall defied expectations to remain a key part of network security? RK: I understand why some people think this -- the idea that the perimeter is dead has taken root… [Continue Reading] -

Physical threats rank alongside cybersecurity for many US businesses
Publié: mai 6, 2019, 4:07pm CEST par Ian Barker
A new study into the threats faced by US businesses produced by Securitas Security Services reveals that in many sectors businesses are concerned as much or more with physical threats such as shootings than they are with cyber security. It also shows rising concern about the threats posed to organizations by insiders, of the 27 threat categories security executives consider to be a concern, 21 may be caused or carried out by an insider. Looking at the top threats of last year, while cyber and internet security still comes out on top overall, threats from shootings or assaults are now… [Continue Reading] -

IBM uses technology to help hurricane-hit communities
Publié: mai 6, 2019, 12:16pm CEST par Ian Barker
To mark the start of US National Hurricane Preparedness Week this week, The Weather Company, an IBM Business, is releasing not just its 2019 hurricane forecast, but also analytic data that looks at how weather affects preparedness, emotion and consumer habits. In addition, through its Code and Response deployment initiative which aims to put open source technologies to use for social good, IBM is taking action to help save the lives of people in communities that are vulnerable to natural disasters. Among the findings are that severe weather conditions make 55 percent of Americans more anxious or stressed. The chances… [Continue Reading] -

Data breaches spark increased interest in password managers
Publié: mai 2, 2019, 5:30pm CEST par Ian Barker
People have been predicting the death of the password for some time, but it's still the case that most online accounts rely on them, even if supplemented by another feature like 2FA. A new report from Avira to coincide with World Password Day shows that so far in 2019, there have been at least four major data breaches, each impacting more than 200 million records. This has led to many sets of credentials and passwords like Collection #1 being made available on the dark web. The more accounts you have the greater your chance of being hacked. Those with six… [Continue Reading] -

Social media phishing attacks up more than 70 percent
Publié: mai 2, 2019, 3:19pm CEST par Ian Barker
Social media phishing, primarily on Facebook and Instagram, has seen a 74.7 percent increase in the first quarter of 2019. A new report on the current phishing landscape from predictive email defense company Vade Secure also shows that Microsoft has retained its spot as the most impersonated brand for four straight quarters, due to the potentially lucrative returns to be gained from Office 365 credentials. It also reveals increasing sophistication in attacks. For example with Office 365 phishing attacks, cybercriminals will often mirror the actual Office 365 login page, pulling JavaScript and CSS directly from the legitimate website and inserting… [Continue Reading] -

Lack of security and operations basics leave businesses unprepared for breaches
Publié: mai 2, 2019, 12:54pm CEST par Ian Barker
A new report from endpoint management specialist 1E reveals 77 percent of IT decision makers polled believe that they are not well prepared to react to a serious data breach and 60 percent have experienced a security breach in the past two years. The study conducted by Vanson Bourne polled 300 decision makers from from IT operations and 300 from IT security, and finds 80 percent say digital transformation increases cyber risk. Only 23 percent believe that the IT operations and IT security teams work together extremely well to secure the business. Nearly all (97 percent) believe that their organization… [Continue Reading] -

US companies waste over two months a year resetting passwords
Publié: mai 2, 2019, 11:58am CEST par Ian Barker
To mark today's World Password Day, access and identity management company OneLogin has released a report that shows IT professionals at US companies waste 2.5 months a year resetting internal passwords. It also finds that almost half of US businesses (44 percent) take up to a month or more to deprovision ex-employees, while 28 percent take a full working week. OneLogin surveyed 300 IT decision makers across the US to discover their attitudes towards password hygiene. Nearly two-thirds (65 percent) of respondents don't check employee passwords against common password lists and more than three-quarters (76 percent) don't check employee passwords… [Continue Reading] -

AIOps tools successful in delivering value for 87 percent of organizations
Publié: mai 1, 2019, 4:29pm CEST par Ian Barker
Artificial Intelligence Operations (AIOps) tools are delivering value through proactive IT operations and improved hybrid infrastructure resilience in 87 percent of implementations, according to a new report. The study from OpsRamp reveals the three biggest benefits of AIOps tools as productivity gains from the elimination of low-value, repetitive tasks across the incident lifecycle (85 percent), rapid issue remediation with faster root cause analysis (80 percent), and better infrastructure performance through noise reduction (77 percent). Concerns surrounding AIOps deployments are, data accuracy/trust in the reliability of AIOps tool recommendations (67 percent), lack of skilled employees with data science and machine learning… [Continue Reading] -

Digital transformation is putting government data at risk
Publié: mai 1, 2019, 3:36pm CEST par Ian Barker
The push towards digital transformation in the US government is putting sensitive data at risk, according to a new report from data protection specialist Thales. Almost all (98 percent) of respondents from federal agencies report that they are using sensitive data within digital transformation technology environments. Yet, less than a third of respondents are using data encryption within these environments. The report finds that agencies continue to move to multi-cloud environments as part of their digital transformation efforts with 78 percent of respondents using sensitive data in the cloud. Specifically, 66 percent of respondents have 26 or more Software-as-a-Service (SaaS)… [Continue Reading] -

New Arcserve release helps protect hybrid environments
Publié: mai 1, 2019, 3:00pm CEST par Ian Barker
With the launch of its latest Unified Data Protection (UDP) product, backup specialist Arcserve is aiming to remove the multiple points of failure typically introduced into IT environments through a piecemeal, 'do-it-yourself' approach to data backup and disaster recovery. Using an image-based technology, the new Arcserve UDP extends proven backup and DR technologies to protect every type of workload, including Nutanix AHV and Microsoft Office 365. It offers a 'done-for-you' method to achieve seamless business continuity and disaster recovery and cut recovery time objectives (RTOs) and recovery points objectives (RPOs) to minutes and seconds. In addition to support for Microsoft… [Continue Reading] -

What is fueling container and multicloud adoption? [Q&A]
Publié: mai 1, 2019, 10:57am CEST par Ian Barker
Containers and cloud native applications are transforming how quickly and reliably organizations can bring ideas to market, while also providing the key building blocks for multicloud strategies. But for all the speed, agility, and elasticity these technologies promise, they also create a complexity tipping point. Across industries, IT staff looking to deliver on the benefits of container and multicloud strategies -- without being overwhelmed by complexity -- are increasingly turning towards workload automation. To give us more insight on the rise of containers and multicloud adoption, we spoke with senior product marketing manager, Asena Hertz at Turbonomic, one of the… [Continue Reading] -

15 percent of IT professionals have more data sources than they can count
Publié: avril 30, 2019, 4:39pm CEST par Ian Barker
Data is essential for modern business, but managing it effectively can be difficult. Big data can be just too big to handle. A new survey from unified operations specialist Ivanti looks at the challenges IT professionals face when it comes to silos, data and implementation. Among its findings are that 15 percent of IT professionals say they have too many data sources to count. In addition more than half (51 percent) report they have to work with their data for days, weeks or more, before it's actionable. Only 10 percent of respondents say the data they receive is actionable within… [Continue Reading] -

Slow database deployment creates bottleneck for software delivery
Publié: avril 30, 2019, 4:18pm CEST par Ian Barker
Deploying database changes is complex and demanding and combined with growing pressure to deliver application updates faster is creating a problem for businesses. According to a survey by database automation company Datical 91 percent of respondents report they have to re-work database changes multiple times before they are ready for production deployment. This backs up another key finding among survey participants, that 80 percent agree it takes longer to deploy database code changes than other types of code changes. In addition 84 percent of application stakeholders have had serious production issues due to database change errors; 57 percent of all… [Continue Reading] -

Third party risk is biggest enterprise cyber threat
Publié: avril 30, 2019, 3:28pm CEST par Ian Barker
As supply chains become more integrated and businesses rely more on using the cloud, so the risk that they face also increases. A new study commissioned by vendor monitoring company RiskRecon and conducted by the Cyentia Institute shows that 84 percent of organizations host critical or sensitive assets with third parties. A typical firm has 22 internet-facing hosts, but some maintain over 100,000 and 65 percent of hosts sit on infrastructure owned by an external entity. 27 percent of firms host assets with at least 10 external providers. 32 percent of organizations host their data in foreign countries. "Your risk surface… [Continue Reading] -

The rapid rise of the social media influencer
Publié: avril 30, 2019, 11:46am CEST par Ian Barker
One of the key trends of the last few years has been the growth of influencer marketing via sponsored content on social media. New research from marketing platform Socialbakers into Instagram marketing shows that in North America, influencer-sponsored posts have grown by over 150 percent from 2018 to 2019. "Consumers are increasingly seeking out reviews and trusted voices when making purchasing decisions. This has created a huge opportunity for influencers and brands to team up to create authentic connections with audiences," says Yuval Ben-Itzhak, CEO of Socialbakers. "Our findings indicate that brands that collaborate with authentic and relevant influencers increase… [Continue Reading] -

Dark Web-leaked banking credentials leap 129 percent
Publié: avril 29, 2019, 5:00pm CEST par Ian Barker
A new report into the financial services threat landscape shows that there has been a huge increase in the number of banking credential leaks, while instances of compromised credit cards increased by 212 percent year-on-year. The report from threat protection platform IntSights reveals many of the leaked credentials came from the Collection #1 database of over 773 million unique email addresses and 21 million unique passwords released onto the Dark Web in January this year. Financial services organizations were targeted in 25.7 percent of all malware attacks last year, more than any of the other 27 industries tracked. While financial… [Continue Reading] -

More than half of companies have sensitive files open to all employees
Publié: avril 29, 2019, 3:45pm CEST par Ian Barker
The latest data risk report from security company Varonis reveals that 53 percent of companies have at least 1,000 sensitive files open to all employees, putting them at risk of data breaches. Keeping old sensitive data that risks fines under HIPAA, GDPR and the upcoming CCPA is a problem too. The report finds over half of data is stale and 87 percent of companies have over 1,000 stale sensitive files, with 71 percent having over 5,000 stale sensitive files. Problems with passwords are highlighted as well with 38 percent of users having passwords that never expire, up from 10 percent… [Continue Reading] -

Automated governance platform helps businesses use data safely
Publié: avril 29, 2019, 3:12pm CEST par Ian Barker
Data privacy is a major concern for businesses, made more acute by the raft of new compliance and data protection rules appearing around the world. Immuta is launching a platform with no-code, automated governance features that enable business analysts and data scientists to securely share and collaborate with data, dashboards, and scripts without fear of violating data policy and industry regulations. Features include Automated Policy Inheritance which eliminates the need for human intervention to manage policies across mashed up data sources. Analysts can instantaneously and securely create integrated data sources, share derived data from them and collaborate across the organization… [Continue Reading] -

Free test checks website security and PCI DSS compliance
Publié: avril 29, 2019, 11:33am CEST par Ian Barker
Good website security is essential to give customers confidence in your business, but for smaller organizations testing can prove difficult. To address this issue, security testing and risk rating company ImmuniWeb is launching a free website security test that can be used by anyone. When run the test verifies PCI DSS requirements, fingerprints versions of over 100 most popular CMS, web frameworks and over 165,000 of their plugins, and runs a comprehensive vulnerability check for all known vulnerabilities in the fingerprinted software. In addition it checks over 20 HTTP headers related to security, encryption or privacy for strong configurations in… [Continue Reading] -

Email threats become more focused and malware gets harder to detect
Publié: avril 25, 2019, 3:52pm CEST par Ian Barker
Spam emails containing malware significantly dropped in 2018, to just six percent, down from 26 percent in 2017. But at the same time malware is becoming more sophisticated and harder to detect. These are among the findings of the latest Global Security Report from Trustwave. The largest single category of malware encountered is downloaders at 13 percent. Remote access Trojans (RATs) at 10 percent and web shells at eight percent, both of which give attackers extensive control over compromised computers, are the second and third most common types of malware discovered. Memory scrapers and dumpers used to steal payment card… [Continue Reading] -

Ransomware detections up 200 percent with businesses the main target
Publié: avril 25, 2019, 3:02pm CEST par Ian Barker
The latest quarterly threat research from Malwarebytes for Q1 2019 reveals a 200 percent jump in ransomware and continued increase in business targets for cyberthreats. This shift back to ransomware comes in the wake of a continued decline in cryptomining, as well as an increased focus on mobile attacks and large-scale business invasions. There's been a drop of 10 percent for consumer ransomware detections and a 33 percent drop in consumer-focused ransomware compared to the same period last year. Meanwhile businesses ransomware detections are up over 200 percent compared to the previous quarter and over 500 percent more than this… [Continue Reading] -

Virtual support agent streamlines service desk management
Publié: avril 24, 2019, 4:02pm CEST par Ian Barker
One of the biggest challenges for service desk teams is striking the right balance between business-critical projects and keeping up with everyday problems and requests. To help relieve this problem, ManageEngine, the IT management division of Zoho, is incorporating Zia, Zoho's AI assistant, as a virtual IT support agent in its cloud-based service desk software, ServiceDesk Plus. "While business end users want on-demand access to IT service desk personnel, IT support staff prefer to focus on higher priority activities and do away with attending to level 1 support. Zia brings perfect balance to service desk operations by offering end users… [Continue Reading] -

IoT devices put healthcare networks at risk
Publié: avril 24, 2019, 3:12pm CEST par Ian Barker
The proliferation of healthcare Internet-of-things devices, along with unpartitioned networks, insufficient access controls and the reliance on legacy systems, has exposed a vulnerable attack surface that can be exploited by cybercriminals, according to a new report. The study by network threat detection specialist Vectra also shows gaps in policies and procedures can result in errors by healthcare staff members. Examples of these errors include improper handling and storage of patient files, which is a soft spot for cybercriminals when they target global organizations and industries looking for weaknesses to exploit. "Healthcare organizations struggle with managing legacy systems and medical devices… [Continue Reading] -

AI-powered predictive engagement helps businesses keep customers
Publié: avril 24, 2019, 12:49pm CEST par Ian Barker
New research from customer engagement company Freshworks reveals that 56 percent of consumers are willing to drop a brand after a single bad experience. The survey of 3,000 individual consumers across the US, UK, Germany, France, India, and Australia, demonstrates that 69 percent have a clear preference for brands that offer proactive notifications and service. It also reveals that 47 percent of consumers globally have higher customer service expectations from their favorite brands than they had in the last two years. Nearly a third would also be willing to pay a premium for great service experiences. In the US, the… [Continue Reading] -

Employees put sensitive data at risk in workplace chat sessions
Publié: avril 23, 2019, 1:12pm CEST par Ian Barker
Around a quarter of employees share confidential information via chat sessions, and a similar number talk badly about their boss, while 78 percent wouldn’t care if some of this information was exposed publicly. These are among the findings of a new study by secure collaboration platform Symphony which surveyed over 1,500 employees in the US and UK about their workplace communication habits. Other bad habits include 27 percent knowingly connecting to an unsecured network, 25 percent using a personal email to conduct business, 36 percent using personal computers or phones to conduct work, and 29 percent sharing work materials with… [Continue Reading] -

Over half of data-driven initiatives are failing
Publié: avril 19, 2019, 3:06pm CEST par Ian Barker
More than half of data-driven initiatives are failing in business, with 27 percent of failures due to a skills shortage according to new research from analytic database company Exasol. In the public sector, financial services and energy and utilities companies the failure rate rises to more than 60 percent. And in retail and financial services 40 percent blame skills shortages for failures. The most common initiatives to fail are data consolidation (29 percent), data migration (28 percent) and GDPR (20 percent). Financial services and IT/telecoms organizations are the worst for GDPR failure at 31 percent and 30 percent respectively. Other… [Continue Reading] -

All endpoint security tools eventually fail
Publié: avril 18, 2019, 11:07am CEST par Ian Barker
The endpoint is on the front line of the network security battle, but a new study from Absolute reveals that endpoint security tools and agents fail, reliably and predictably. The study analyzed data from six million devices and one billion change events over the course of a year. It finds the complexity of endpoint device controls creates a false sense of security among organizations while, in reality, causing security gaps and significant risks due to regular and reliable tool failure. "Evolving security threats have caused enterprises to layer on more and more endpoint controls, increasing complexity, impacting performance, and in… [Continue Reading] -

Tracking the continuing bad bot arms race
Publié: avril 17, 2019, 4:20pm CEST par Ian Barker
In 2018 bad bots accounted for one in five website requests (20.4 percent of web traffic), while good bots decreased slightly to make up 17.5 percent of traffic. This is among the findings of Distil Networks' latest annual Bad Bot Report which investigated hundreds of billions of bad bot requests from 2018 over thousands of domains to provide deeper insight into the daily automated attacks. "Bot operators and bot defenders are playing an incessant game of cat and mouse, and techniques used today, such as mimicking mouse movements, are more human-like than ever before," says Tiffany Olson Kleemann, CEO of… [Continue Reading] -

Security, connectivity and data analysis are top IoT developer concerns
Publié: avril 17, 2019, 3:51pm CEST par Ian Barker
A new survey of IoT developers reveals their top concerns are security (38 percent of respondents), connectivity (21 percent), and data collection and analysis (19 percent). Performance (18 percent), privacy (18 percent), and standards (16 percent) are also areas cited as particularly challenging. These findings come from The Eclipse Foundation which has surveyed more than 1,700 developers via its IoT Working Group. "This year's survey results reflect the opportunities and challenges surfaced by the accelerating market adoption of IoT solutions and services," says Mike Milinkovich, executive director of the Eclipse Foundation. "Developers are contending with interoperability and performance challenges across… [Continue Reading] -

AMD brings more performance to embedded processors
Publié: avril 17, 2019, 11:25am CEST par Ian Barker
The rise of edge devices, customer service terminals, digital signage and so on has led to increased demand for embedded processing. Chip maker AMD is expanding its offering in this market with the launch of the new Ryzen Embedded R1000 Series SoC. This offers embedded customers dual core, quad-threaded performance, as well as the ability to run fanless, low power solutions for 4K displays, while providing leading-edge security features. "The AMD Ryzen Embedded R1000 builds out the Ryzen Embedded family and provides a compelling option for customers that want access to the powerful 'Zen' and 'Vega' architecture and are looking for a… [Continue Reading] -

Understanding the Brazilian hacking community [Q&A]
Publié: avril 16, 2019, 4:21pm CEST par Ian Barker
We tend to think of hacking communities as being concentrated in the Far East or the former Soviet bloc, but of course there hackers elsewhere that we don't hear so much about. Researchers at Recorded Future have been investigating hacking communities around the world, and their latest report covers Brazil. It finds that hackers in Brazil are keen to follow the money and have shown an impressive ability to bypass internet banking security controls and ATM security. What's more the country's high level hackers often succeed in overcoming two factor authentication. One of the reasons we hear relatively little about… [Continue Reading] -

New platform helps search and analysis of cloud-stored data
Publié: avril 16, 2019, 3:30pm CEST par Ian Barker
As companies store ever larger amounts of data, the current solutions and services available to handle it become more and more costly and difficult to manage. To address these challenges, Boston-based CHAOSSEARCH is launching a new platform that delivers rapid search and analytics through a managed service, based on simple, elastic storage. The platform helps eliminate the need to move or transform data into specific siloed databases via patent pending Data Edge technology. Data Edge fully indexes datasets with its built-in schema detection, normalization and compression algorithms. Customers can dynamically and seamlessly combine storage with indexing for live and historical… [Continue Reading] -

Government websites top the charts for online trust
Publié: avril 16, 2019, 1:18pm CEST par Ian Barker
The Internet Society's Online Trust Alliance (OTA), which identifies and promotes online security and privacy best practices, announced today the results of its latest Online Trust Audit and Honor Roll. The Audit finds that 70 percent of analyzed websites qualified for the Honor Roll, the highest proportion ever, and up from 52 percent in 2017, driven primarily by improvements in email authentication and session encryption. Perhaps surprising is that the US Federal government category has surged to the front with 91 percent of sites placing on the honor roll, a dramatic turnaround from 2017 when government sites had bottomed out… [Continue Reading] -

Energy industry vulnerable to attacks on outdated systems
Publié: avril 16, 2019, 11:35am CEST par Ian Barker
Critical infrastructure sites and energy distribution facilities are increasingly being targeted by cybercriminals. But many of the systems in use today were installed and built before 24/7 internet connections. A new report from Finnish cybersecurity company F-Secure highlights the fact that cybersecurity was not a realistic threat when these systems were manufactured, and legacy protocols and systems never had the built-in security controls that we take for granted today. Connecting these systems to the internet has opened them up to attacks from myriad angles. "Espionage and sabotage attacks against CNI (Critical National Infrastructure) organizations have increased over the years and… [Continue Reading] -

Cyber hygiene is at an all-time low
Publié: avril 15, 2019, 5:05pm CEST par Ian Barker
Well-known attacks and attack vectors remained successful because security personnel did not address vulnerabilities and apply patches according to a new report from cybersecurity and visibility business Ixia. IT vendors created code or configurations that led to many successful security breaches in 2018, but IT operations and security personnel shared the blame due to ignorance of the latest patches and challenges in deploying patches in a timely manner. In addition Ixia observed more new devices joining networks than ever before, but also more devices designed and deployed without proper measures to stop or even limit threats. Well-understood SQL injections and… [Continue Reading] -

European financial services industry struggling with lack of data skills
Publié: avril 12, 2019, 3:40pm CEST par Ian Barker
Nearly 40 percent of financial services businesses are failing to implement data initiatives due to a lack of skills, with almost a third saying that their GDPR initiatives are failing, according to a new study. The report produced by Vanson Bourne for analytics database company Exasol is based on responses from 500 IT and business decision makers, from enterprises in Germany and the UK. It also reveals 75 percent of financial services enterprises admit that their operations and decision making would be severely disrupted on a day-to-day basis if they didn't have access to data. Worryingly, just over a third say… [Continue Reading] -

Security professionals think cybersecurity is a bigger threat to the US than border security
Publié: avril 11, 2019, 3:41pm CEST par Ian Barker
A new survey of security professionals taken at this year's RSA reveals that 92 percent of respondents feel that cybersecurity is a bigger threat to the US than border security. Yet government, and media, attention seems far more focused on the latter. The study from AI-powered security company Lastline also asked respondents which of the tech giants they trust the least with their data, not surprisingly 76 percent name Facebook. Others, Amazon (25 percent), Apple (24 percent), Google (20 percent) and Microsoft (27 percent) all scored relatively evenly when asked who they trust most. The results also show a significant lack… [Continue Reading] -

Tax identities up for sale on the dark web
Publié: avril 11, 2019, 12:17pm CEST par Ian Barker
While banking and identity information has been traded on the dark web for a long time, a new report from Carbon Black shows a new focus on tax identities. The company's research shows previous year's W-2 forms and 1040 forms available on the dark web at relatively low cost, ranging from $1.04 to $52. Names, social security numbers and birthdates can be obtained for a price ranging from $0.19 to $62. There are also how-to guides on illicitly cashing out tax returns available for as little as $5. The sellers that offer these listings usually have for sale other similar… [Continue Reading] -

Businesses complacent about mainframe security
Publié: avril 10, 2019, 3:54pm CEST par Ian Barker
Although 85 percent of companies say mainframe security is a top priority, just 33 percent always or often make mainframe decisions based on security finds a new report. The study from mainframe vulnerability specialist Key Resources Inc, based on research by Forrester Consulting also finds 67 percent of respondents admit that only sometimes or rarely are they factoring security into mainframe decisions. Respondents' top mainframe priorities are cited as data breach prevention, compliance, risk management, IT cost reduction/optimization and application availability. But despite this desire for data breach prevention, scanning for OS vulnerabilities is consistently ranked as a low priority.… [Continue Reading] -

A quarter of phishing emails bypass Office 365 security
Publié: avril 10, 2019, 3:17pm CEST par Ian Barker
According to a new study analyzing more than 55 million emails, 25 percent of phishing emails bypass Office 365 security, using malicious links and attachments as the main vectors. Other findings of the report from cloud-native security firm Avanan include that 33 percent of emails contain a link to a site hosted on WordPress and 98 percent of emails containing a crypto wallet address are phishing attacks. "Cloud-based email, despite all of its benefits, has unfortunately launched a new era of phishing attacks," says Yoav Nathaniel, lead security analyst at Avanan. "The nature of the cloud provides more vectors for… [Continue Reading] -

Securing serverless computing, the latest cloud paradigm [Q&A]
Publié: avril 10, 2019, 11:23am CEST par Ian Barker
The cloud-skills shortage has made security a major challenge for enterprises. In fact, virtually every data breach in the cloud today is due to human error, rather than brilliant hacking. Hackers don't even bother launching attacks in the public cloud; they simply look for misconfigured systems that leave data exposed. Against this backdrop, a whole new cloud model is taking hold -- serverless computing. In a world where cloud certifications and security skills are already in short supply and causing chaos in the cloud, what will serverless computing do to compound that problem for enterprises? Is it possible for organizations… [Continue Reading] -

Cohesity launches as-a-service backup for Google Cloud
Publié: avril 9, 2019, 6:01pm CEST par Ian Barker
As companies move more of their workloads to the cloud they want to ensure that their data is properly protected. Storage specialist Cohesity is launching a new software as a service (SaaS) solution that delivers enterprise-grade backup and recovery for applications running on the Google Cloud platform. Cohesity Cloud Backup Service for Google Cloud eliminates the need for customers to deploy backup software, infrastructure, or custom scripts. Instead, customers can benefit from backup SaaS capabilities that are easy to use and integrate natively with GCP. "With organizations looking to leverage the cloud and eliminate the need to provision infrastructure, backup… [Continue Reading] -

BullGuard adds to its product line with a VPN
Publié: avril 9, 2019, 3:26pm CEST par Ian Barker
Cybersecurity company BullGuard is launching its own VPN for Windows, Mac, Android and iOS, intended to make it simple for users to ensure their online privacy. Designed to be easily used across multiple devices, BullGuard VPN features a simplified user interface and quick connect functionality, enabling consumers to fly under the radar and surf the internet in stealth mode while retaining complete anonymity via military-grade encryption. "Cybersecurity to date has been primarily focused on keeping consumers and their devices safe from online threats, but cybercriminals also pose a threat to consumer privacy," says BullGuard CEO, Paul Lipman. "In today's cyberthreat… [Continue Reading] -

Zoho launches new commerce and marketing platforms
Publié: avril 9, 2019, 2:57pm CEST par Ian Barker
Cloud business system company Zoho is launching two new platforms. Commerce Plus uses Zoho's customer experience, finance, analytics, and intelligence software to provide businesses an interconnected, first-of-its-kind commerce experience platform. The Zoho Marketing Platform can support over 20 different marketing channels, including websites, social, events, text, email, ads, offline, and more. "Businesses today are forced to navigate the technology jungle to figure out the right applications needed to run their operations -- this is no different, and can be even more challenging, in commerce," says Raju Vegesna, Zoho's chief evangelist. "With Commerce Plus, we offer one platform to run an… [Continue Reading] -

Digital transformation? Don't ask me
Publié: avril 9, 2019, 12:09pm CEST par Ian Barker
According to new research among British businesses, 57 percent of employees either don't understand (20 percent) or misinterpret (37 percent) the meaning of 'digital transformation'. The research, conducted by YouGov among employees at 500 businesses with 50 or more employees, on behalf of service management Cherwell Software also finds that 64 percent say their employers only adopt new technology once it enters the mainstream. Just nine percent of employers are considered to be 'digital innovators'. There are mixed reactions to artificial intelligence too, with 34 percent negative (made up of 21 percent threatened, five percent confused and eight percent saddened),… [Continue Reading] -

Understanding the LockerGoga ransomware attacks
Publié: avril 9, 2019, 11:22am CEST par Ian Barker
Last month Aluminum manufacturer Norsk Hydro was hit by a large scale ransomware attack that affected its systems across the globe and caused severe disruption to its operations with an estimated impact of more than $35 million.. The attack used the LockerGoga ransomware and the threat research team at Securonix has been monitoring the malware, which also caused problems for a number of other companies. In order to avoid defenses, LockerGoga payloads are signed with a valid digital certificate issued by multiple certificate authorities. Spreading the malware required access to the network with Server Message Block and Active Directory management… [Continue Reading] -

Credential stuffing attacks target media streaming services
Publié: avril 8, 2019, 3:55pm CEST par Ian Barker
The entertainment industry and in particular streaming services is among the biggest targets of credential stuffing attacks according to a new report. The study from digital delivery platform Akamai, unveiled at the NAB Cybersecurity and Content Protection Summit in Las Vegas this week, focuses on credential abuse attacks against online video and music streaming services. It reveals three of the largest credential stuffing attacks against streaming services in 2018, ranging in size from 133 million to 200 million attempts, took place shortly after reported data breaches, indicating hackers were likely testing stolen credentials before selling them. Stolen credentials can be… [Continue Reading] -

Fastly takes Azure closer to the edge
Publié: avril 8, 2019, 3:07pm CEST par Ian Barker
As businesses grow to serve complex user experiences, cooperation between network providers is vital. Enterprises want pain-free portability of application stacks and services optimized for their needs between multiple providers. Edge cloud platform Fastly is announcing that it’s connecting its edge network with Microsoft Azure. "At Fastly, we're consistently seeing our customers and the market embrace strategies that leverage multiple providers. Integrations such as the one between Fastly's edge cloud network and Microsoft Azure make it easier for our customers to do so," says Artur Bergman, founder and CEO of Fastly. "Our partners at Microsoft are aligned on this, and… [Continue Reading] -

90 percent of critical infrastructure hit by cyberattacks
Publié: avril 5, 2019, 4:42pm CEST par Ian Barker
A new survey of professionals in industries using industrial control systems (ICS) and operational technology (OT) finds 90 percent of respondents say their environment has been damaged by at least one cyberattack over the past two years, with 62 percent experiencing two or more attacks. The study commissioned by Tenable from the Ponemon Institute also finds 80 percent of respondents cite lack of visibility into the attack surface, knowing what systems are part of their IT environments, as the number one issue in their inability to prevent business-impacting cyberattacks. More than a third (37 percent) report at least one significant… [Continue Reading] -

Why bare-metal containers are scaring VMware [Q&A]
Publié: avril 5, 2019, 11:23am CEST par Ian Barker
With a market capital of $73 billion and a stock price that has more than tripled in three years, VMware is one of the big hitters of the IT industry. The company has dominated the market since it introduced virtual machine server abstraction 19 years ago. But some industry watchers cite the rise of containers as an existential risk to VMware. This new way of software deployment was popularized by developers via the Docker container format, and more recently is taking the data center by storm as enterprises take containers into production and standardize on Google’s Kubernetes orchestration platform. We… [Continue Reading] -

Financial sector concerned about third-party cyber risk
Publié: avril 2, 2019, 4:52pm CEST par Ian Barker
Many organizations work with hundreds of third parties, creating new risks that must be actively managed. The financial industry, in particular, has a massive business ecosystem made up of legal organizations, accounting and human resources firms, management consulting and outsourcing firms, and information technology and software providers. A new study into the financial services sector from security ratings company BitSight finds that 97 percent of respondents say cyber risk affecting third parties is a major issue. In addition, nearly 80 percent of respondents say they have terminated or would decline a business relationship due to a vendor's cybersecurity performance. One… [Continue Reading] -

Companies overconfident in management of sensitive data
Publié: avril 2, 2019, 4:02pm CEST par Ian Barker
A new study into how enterprises manage sensitive data reveals overconfidence in knowing where private data resides, and the use of inadequate tools such as spreadsheets to track it. The research from Integris Software shows 40 percent are 'very' or 'extremely' confident in knowing exactly where sensitive data resides, despite only taking inventory once a year or less. Yet a mere 17 percent of respondents are able to access sensitive data across five common data source types. The survey exposes the lack of visibility companies have on where their data lives. Nearly 45 percent of respondents say they need to… [Continue Reading] -

Taxpayers worry about online fraud but offline habits could be putting them at risk
Publié: avril 2, 2019, 3:31pm CEST par Ian Barker
As we approach the tax return season, a survey from document destruction and information security company Shred-It reveals that 38 percent of US taxpayers say they are worried they will become a victim of tax fraud or tax identity theft. Yet according to the study 45 percent admit to storing tax paperwork in a box, desk drawer or unlocked cabinet at home or work. What's more, 19 percent admit they don't shred tax paperwork or physical documents containing sensitive information before throwing them away. While nearly half of taxpayers (48 percent) will file their own taxes online via tax preparation… [Continue Reading] -

85 percent of organizations don't meet basic levels of PAM security
Publié: avril 2, 2019, 2:50pm CEST par Ian Barker
While 78 percent of organizations now include privileged credential protection as part of their cyber security policies, their privileged access management (PAM) security practices are still lacking. According to a new study by PAM specialist Thycotic, 85 percent of respondents are still struggling to get beyond the initial phase of PAM maturity. A worrying 55 percent of organizations have no idea how many privileged accounts they have or where they're located. In addition more than half of organizations' privileged accounts never expire or get deprovisioned. Only 18 percent of organizations are storing all their privileged accounts in a secure privileged… [Continue Reading] -

Attackers target supply chains using 'island hopping'
Publié: avril 2, 2019, 1:07pm CEST par Ian Barker
Around half of recent cyberattacks use 'island hopping' techniques, seeking to target not just one network but those along the supply chain too. This is one of the findings of the latest Global Incident Response Threat Report from Carbon Black. It also finds that 70 percent of attacks now attempt to move laterally around the network. Attacks are becoming more sophisticated in their attempts to avoid detection too. 56 percent of survey respondents have seen attacks deploying some form of counter measures. Of these 87 percent tried to destroy logs and 70 percent used evasion tactics. While the finance and… [Continue Reading] -

Vulnerabilities leave financial mobile apps open to attack
Publié: avril 2, 2019, 11:10am CEST par Ian Barker
A new report reveals widespread security inadequacies and protection failures among consumer financial applications. The research for Arxan Technologies, carried out by Aite Group, says these vulnerabilities can lead to the exposure of source code, sensitive data stored in apps, access to back-end servers via APIs, and more. Among key findings are that 97 percent of all apps tested lacked binary code protection, making it possible to reverse engineer or decompile the apps exposing source code to analysis and tampering. 90 percent of the apps tested shared services with other applications on the device, leaving data from the financial institution's… [Continue Reading] -

IoT attacks increase but rely on the same old weaknesses
Publié: avril 1, 2019, 3:08pm CEST par Ian Barker
Internet of Things devices have proved to be problematic in their vulnerability to cyber attacks. This is underlined by a new report from F-Secure which finds that threats and the number of attacks continue to increase, but still depend on well-known security weaknesses, such as unpatched software and weak passwords. The number of IoT threats observed by F-Secure Labs doubled in 2018, growing from 19 to 38 in the space of a single year. But many of these threats still use predictable, known techniques to compromise devices. Threats targeting weak/default credentials, unpatched vulnerabilities, or both, made up 87 percent of… [Continue Reading] -

Continuous response needed to combat cyber attacks
Publié: mars 29, 2019, 5:01pm CET par Ian Barker
As the threat landscape continues to rapidly evolve, businesses need to be able to react quickly and have an effective strategy to deal with attacks. Security specialist F-Secure is calling for greater emphasis on both preparing for a breach as well as fast and effective containment that has the correct balance of people, process and technology. "Cyber breaches are now a fact of life for many companies. It's no longer a matter of 'if' a company will be breached, the question is 'when'. And that calls for a shift in how organizations handle many aspects of security," says F-Secure Countercept… [Continue Reading] -

90 percent of tech companies are vulnerable to email spoofing
Publié: mars 29, 2019, 3:56pm CET par Ian Barker
Phishing is a major problem for large organizations, but while there are standards to authenticate email and prevent phishers from spoofing domains with fake emails, a majority of companies have not made full use of them. The tech sector has moved faster than some but while they are beginning to implement protection many companies in this sector are still at an early stage with the result that 90 percent are still vulnerable to impersonation. A new report from Valimail shows that 49 percent of large global technology companies have DMARC records of some kind, indicating that they have, at minimum,… [Continue Reading] -

We're getting better at backing up our data -- but we're also losing more
Publié: mars 29, 2019, 3:14pm CET par Ian Barker
A new study released by Acronis ahead of Sunday's World Backup Day shows 92.7 percent of consumers are backing up their computers -- an increase of more than 24.1 percent from last year and the largest ever year-on-year increase. This could be because the report also shows that 65.1 percent of those surveyed say either they or a family member has lost data as a result of an accidental deletion, hardware failure or software problem -- a jump of 29.4 percentage points from last year. "At first glance, those two findings might seem completely incompatible -- how can more data… [Continue Reading] -

Large enterprises face problems with unsecured applications
Publié: mars 28, 2019, 4:09pm CET par Ian Barker
A new survey of more than 200 CISOs in the US and Canada finds that large enterprises typically operate 1,300 or more complex applications but only protect 60 percent of them, leaving more than 500 applications unprotected at a time where adversarial attacks are increasing. The study from crowdsourced security company Bugcrowd along with the Enterprise Strategy Group (ESG), also shows strong interest in using DevOps to automate security. Nearly four out of five organizations have adopted DevOps, and more than four out of five are planning to integrate cybersecurity processes and controls in the continuous integration and continuous delivery… [Continue Reading] -

Encryption backdoors raise the likelihood of attack
Publié: mars 28, 2019, 1:11pm CET par Ian Barker
Countries with government-mandated encryption backdoors are more susceptible to nation-state attacks according to 73 percent of security professionals. A survey from machine identity protection company Venafi also finds 69 percent believe countries with encryption backdoors suffer economic disadvantages in the global marketplace as a result. "This is a tense moment for industry professionals because they know backdoors make our critical infrastructure more vulnerable," says Kevin Bocek, vice president of security strategy and threat intelligence at Venafi. "This is not rocket science; backdoors inevitably create vulnerabilities that can be exploited by malicious actors. It's understandable that so many security professionals are… [Continue Reading] -

More than half of internet users think complete digital privacy is impossible
Publié: mars 27, 2019, 5:22pm CET par Ian Barker
According to a report from Kaspersky Lab, 56 percent of internet users feel that complete privacy in the modern digital world is impossible. For many people, their worries about digital privacy may come from personal experience. Kaspersky's research finds that 26 percent of people have had their private data accessed by someone without their consent, rising to almost a third (31 percent) among 16- to 24-year-olds. The consequences of having their privacy compromised have ranged from experiencing stress (36 percent), to facing spam and advertisements (25 percent) to losing money (21 percent). An interesting finding is that once people believe complete… [Continue Reading] -

Data breaches more common than rain in the UK
Publié: mars 27, 2019, 4:56pm CET par Ian Barker
The UK has something of a reputation for its wet climate, and its citizens for constantly talking about the weather. So it may come as a surprise to find that in the UK the chance of experiencing a data breach is higher than that of encountering a rainy day. A survey by technology services company Probrand shows 43 percent of UK businesses having suffered a cyber breach or attack in the last 12 months as against just 36.4 percent chance on average of encountering a wet day. More worrying is that the study finds 44 percent of businesses are failing… [Continue Reading] -

Need for data portability is driving cloud strategies
Publié: mars 27, 2019, 3:38pm CET par Ian Barker
The rise in container use and demands for data portability are driving decisions on cloud adoption according to a new report. Workload automation specialist Turbonomic surveyed over 800 IT professionals to examines the underlying dynamics fueling cloud-native/container and multicloud adoption. Among the findings are that 83 percent of respondents expect workloads to move freely across clouds. The primary drivers for workload portability and true multicloud elasticity are a desire to have best-of-breed cloud services and guarantee application availability. The majority of respondents (62 percent) have already embarked on their cloud native/container journey -- with adoption accelerating. On average, respondents estimate… [Continue Reading] -

Digital cold war and other emerging threats we'll face in the next two years
Publié: mars 27, 2019, 3:06pm CET par Ian Barker
A new report from the Information Security Forum looks at the threats organizations can expect to face over the next two years as a result of increasing developments in technology. The Threat Horizon 2021 report highlights three major themes that will present particularly difficult cyber security challenges for businesses. "By 2021 the world will be heavily digitized. Technology will enable innovative digital business models and society will be critically dependent on technology to function," says Steve Durbin, managing director of the ISF. "This new hyperconnected digital era will create an impression of stability, security and reliability. However, it will prove… [Continue Reading] -

Next generation cyber defense driven by analytics and machine learning
Publié: mars 26, 2019, 4:42pm CET par Ian Barker
The biggest problem for security teams is often too much data and many are addressing this by turning to analytics and machine learning, according to a new report. The study from CyberEdge Group surveyed 1,200 IT security decision makers and practitioners and finds 47 percent intend to deploy advanced analytics solutions in the next year. More than 90 percent of IT security organizations have invested in ML and/or artificial intelligence technologies to combat advanced threats, and more than 80 percent say they are already seeing a difference. That said, the percentage of organizations affected by a successful cyberattack rose slightly… [Continue Reading] -

61 percent of CISOs believe employees have leaked data maliciously
Publié: mars 25, 2019, 3:57pm CET par Ian Barker
A new study reveals that 79 percent of IT leaders believe that employees have put company data at risk accidentally in the last 12 months, and 61 percent believe they have done so maliciously. The research from data security company Egress also explores how employees and executives differ in their views of what constitutes a data breach and what is acceptable behavior when sharing data. Insider data breaches are viewed as frequent and damaging occurrences, of concern to 95 percent of IT leaders, yet employees are either unaware of, or unwilling to admit, their responsibility. IT leaders are most likely… [Continue Reading] -

Unplanned service interruptions lead to stress for engineers
Publié: mars 25, 2019, 3:16pm CET par Ian Barker
Unplanned service interruptions which can include outages, operational overload, slowdowns in delivery, notification fatigue and other unanticipated events represent a major issue according to a new global survey of site reliability engineers (SREs). The study by digital experience monitoring specialist Catchpoint reveals that 49 percent say they have worked on an incident in the last week, while the same percentage state they have worked on outages longer than a day in their career. What's more these incidents are stressful, with 67 percent of SREs who feel stress after each incident not believing that their company cares about their well-being. "While… [Continue Reading] -

Trend micro calls in artists to make cybersecurity beautiful
Publié: mars 22, 2019, 3:49pm CET par Ian Barker
When you think of cybersecurity, art and beauty probably aren't the first things that come to mind. But if Trend Micro has its way that could be about to change. The company has commissioned a number of artists to create what it calls The Art of Cybersecurity. This is a series of works based on security data, with the idea of shifting the perception of protecting systems from a burden, to something beautiful. Six different artists have created works based on things including unknown threats, endpoint threats, and phishing attacks. The works will be used in Trend Micro's advertising and… [Continue Reading] -

Panic Button secures data -- by destroying it
Publié: mars 22, 2019, 1:01pm CET par Ian Barker
One of the biggest worries about someone gaining unauthorized access to your computer is that they can view and steal your data. The CyberYozh security group has launched a product that protects your sensitive files, browser data and more, by taking the nuclear option of destroying it. Panic Button is, says the company, useful in emergency situations when a user cannot prevent someone from accessing his or her computer. When activated, Panic Button is capable of destroying files specified by the user as well as their activity in an OS and a browser. It can also be activated in logic… [Continue Reading] -

New vulnerability reporting platform aims to make open source safer
Publié: mars 21, 2019, 4:11pm CET par Ian Barker
Vulnerabilities in open source code represent a risk for businesses, but the process of reporting them is cumbersome and that can leave software open to risk. Without a standard for responsible disclosure, even those who want to disclose vulnerabilities responsibly can get frustrated with the process and turn to public lists or social media, where bad actors can easily find the details before fixes are created. Plus, open source projects often don't have the resources to validate that all vulnerabilities reported are real issues. Software supply chain management company Sonatype, is announcing a partnership with HackerOne, to create The Central… [Continue Reading] -

Windows Virtual Desktop preview goes public
Publié: mars 21, 2019, 12:16pm CET par Ian Barker
Back in September last year Microsoft announced the launch of its Virtual Desktop to allow Windows to be run in the cloud. At the time, however, it was only a private preview. Today the public preview launches, so anyone with an Azure subscription can try out the service. Windows Virtual Desktop offers simplified management, a multi-session Windows 10 experience, optimizations for Office 365 ProPlus, and support for Windows Server Remote Desktop Services (RDS) desktops and apps. It means users can deploy and scale Windows desktops and apps on Azure quickly and with built-in security. It should be attractive to businesses… [Continue Reading] -

SoftNAS vulnerability lets attackers bypass authentication
Publié: mars 20, 2019, 4:23pm CET par Ian Barker
Researchers have uncovered a vulnerability in the SoftNAS Cloud data storage platform that could be used to gain access to the webadmin interface without valid user credentials. Security technology company Digital Defense found the previously undisclosed vulnerability which arises if customers have not followed SoftNAS deployment best practices and have openly exposed SoftNAS StorageCenter ports directly to the internet. SoftNAS provides a software-defined cloud NAS for AWS, Microsoft Azure and Vmware among others, so it's widely deployed in many businesses. The vulnerability only affects SoftNAS Cloud versions 4.2.0 and 4.2.1. A patch is available for download via Software Update in… [Continue Reading] -

Free tool protects businesses against ransomware and other threats
Publié: mars 20, 2019, 3:40pm CET par Ian Barker
Ransomware and other threats like adware and cryptominers are still a major threat to businesses. But smaller companies may be struggling to find the resources to combat them. To address this problem Kaspersky Lab is today releasing the next generation of its free Kaspersky Anti-Ransomware Tool for Business. It uses Kaspersky's endpoint protection technologies which cover a wider range of platforms and risks beyond ransomware, including pornware and other porn-related cyberthreats. The existing protection of the tool covering desktops has now been extended to servers running Windows Server versions to ensure the comprehensive integrity of corporate data. The tool's anti-ransomware… [Continue Reading] -

Insider threats pose the biggest security risk
Publié: mars 20, 2019, 2:55pm CET par Ian Barker
According to a new study 91 percent of IT and security professionals feel vulnerable to insider threats, and 75 percent believe the biggest risks lie in cloud applications like popular file storage and email solutions including Google Drive, Gmail and Dropbox. The report from SaaS operations management specialist BetterCloud also shows 62 percent of respondents believe the biggest security threat comes from the well-meaning but negligent end user. "The rise of SaaS in the digital workplace has made companies more vulnerable than ever to insider threats," says David Politis, founder and CEO of BetterCloud. "A major reason is SaaS has… [Continue Reading] -

8 out of 10 top vulnerabilities target Microsoft products
Publié: mars 19, 2019, 3:42pm CET par Ian Barker
Prioritizing vulnerabilities can be difficult if you don't know which ones are being actively exploited. The latest annual research from Recorded Future looks at the top vulnerabilities and which products they are targeting. In 2018, the company observed more exploits targeting Microsoft products compared to Adobe ones. Eight out of 10 vulnerabilities exploited via phishing attacks, exploit kits, or RATs were targeting Microsoft products. While Adobe has been a popular target in the past, only one Adobe Flash vulnerability made the top 10. This is likely due to a combination of better patching and Flash Player's impending demise in 2020.… [Continue Reading] -

Mid-sized businesses lead the way in workplace technology
Publié: mars 19, 2019, 3:07pm CET par Ian Barker
Medium-sized businesses now account for over 60 percent of US jobs, and are investing fast in technology, but they must ensure they have the skills and management in place to avoid falling behind. A new study from Aruba looks at how mid-sized businesses around the world are currently adopting workplace technology, Among key findings are that almost two-thirds (63 percent) of medium-sized business employees rate the choice of technology, applications and IT support at their company as either good or very good. That compares to 53 percent of those also surveyed from the largest companies. Medium-sized businesses are also ahead… [Continue Reading] -

Organizations not effective at getting value from their data
Publié: mars 19, 2019, 1:45pm CET par Ian Barker
Businesses increasingly understand that staying competitive means making smart use of their data. But a new survey from Syncsort finds that just nine percent of respondents say their organization is 'very effective' at getting value from data while 48 percent responded 'somewhat effective'. Making data accessible to users across the enterprise is the third most cited IT challenge and only half call their organization effective in getting data insights to business users. But in spite of this, 'improved access to data' only ranks fourth on the list of business initiatives IT indicated they would support in 2019, behind increased operational/workforce… [Continue Reading] -

How edge computing is making 5G possible [Q&A]
Publié: mars 19, 2019, 10:50am CET par Ian Barker
This month, Verizon announced its intention to increase its use of edge computing technology, having tested edge functions in its 5G network in Houston resulting in massively decreased network latency. This move is another example of how new technologies will enable and extend digital transformation projects at the edge, and this is only the beginning. In light of this and an upcoming flurry of 5G announcements and projects, how exactly will edge computing tie into this 5G future? What are the benefits and when can we expected to see these technologies adopted on a wider scale? We spoke with Jason… [Continue Reading] -

Addressing the skills gap with advanced web attack training now available online
Publié: mars 18, 2019, 2:58pm CET par Ian Barker
There is a shortage of cybersecurity professionals and coupled with the exponential growth in web applications used within businesses and by consumers around the world, there's a growing risk of flaws being exploited. To combat this problem penetration testing specialist Offensive Security is making its Advanced Web Attacks and Exploitation (AWAE) training available as an online course. AWAE is one of the most in-demand security training courses in the industry, as illustrated by the fact that a live version of the course was the fastest-selling live training class at Black Hat USA 2019, selling out in less than 30 minutes.… [Continue Reading] -

Gearbest issues response to data breach
Publié: mars 15, 2019, 3:27pm CET par Ian Barker
Following on from yesterday's story about eCommerce site Gearbest leaking customer data the company has issued an official response to ethical hacker Noam Rotem’s report. It says that its own servers are secure but that, "external tools we use to temporarily store data" may have been accessed by others leading to security having been compromised. The statement goes on to say: The external tools we use are intended to improve efficiency and prevent data overload and the data will only be stored in such tools for less than three calendar days before it is automatically destroyed. Considering possible data security breaches,… [Continue Reading] -

A fifth of Americans don't trust anyone to protect their data
Publié: mars 15, 2019, 3:00pm CET par Ian Barker
Around 20 percent of Americans suffer from security fatigue and don’t trust anyone to protect their personal data according to a new study. The research from hardware security company nCipher Security reveals that many people want more control over their personal data privacy and most want tighter controls on how others handle and safeguard their personal data. Identity theft is survey participants' leading concern related to sharing personal data online. Nearly one in five (18 percent) of survey respondents have been victims of cyberattack and two out of three (68 percent) say they fear identity theft. That may help explain… [Continue Reading] -

Zippyshare mysteriously blocked in the UK
Publié: mars 15, 2019, 11:52am CET par Ian Barker
The Zippyshare file hosting service is currently blocked for users in the UK. Anyone visiting the site will be presented with a '403: Forbidden' message when they try to access the site. Users on a number of ISP forums are asking whether this is due to some blocking action on the part of service providers, but it appears that for some reason the site is blocking itself from UK IP addresses. The problem started a few days ago with posts about it first appearing on Sunday. Some suspected a copyright block but Zippyshare has always been one of the more… [Continue Reading] -

Gearbest security flaw leaks millions of order and user details
Publié: mars 14, 2019, 5:05pm CET par Ian Barker
A badly configured server at Gearbest, the Chinese purveyor of technology and other stuff online, has leaked millions of user profiles and order details. White hat hacker Noam Rotem discovered an Elasticsearch server that was -- indeed still is at the time of writing -- leaking millions of records each week. These include customer data, orders, and payment records. The server wasn't protected with a password, potentially allowing anyone to search its data. Rotem published details of the leak at VPNmentor. Data exposed includes details of products bought and shipping information, plus payment details, email addresses, and other customer data… [Continue Reading] -

Businesses plan to use more AI and machine learning in cybersecurity this year -- even though they don't understand it
Publié: mars 14, 2019, 4:30pm CET par Ian Barker
The use of more artificial intelligence to improve security has been touted for a while. New research from Webroot reveals that a majority of business are now actively exploring the technology. It finds 71 percent of businesses surveyed in the United States plan to use more artificial intelligence and machine learning in their cybersecurity tools this year. However, a worrying 58 percent say that aren't sure what that technology really does. Although over one-third (36 percent) of organizations experienced a damaging cyberattack within the last year, the majority are still extremely confident (83 percent) they have all the tools they… [Continue Reading] -

Analysis of Remote Access Trojans helps understand third-party business risk
Publié: mars 14, 2019, 3:36pm CET par Ian Barker
Remote Access Trojans (RATs) are often used to steal information from enterprise networks. By looking at network metadata, analysts at threat intelligence firm Recorded Future have been able to identify RAT command-and-control (C2) servers, and more crucially, which corporate networks are communicating to those controllers. This offers insight about third-party organizations that Recorded Future clients can use to get a better understanding of potential third-party risk to their own data. The research identified active malware controllers for 14 malware families between December 2, 2018 and January 9, 2019. It then focused analysis on a subset of malware -- Emotet, Xtreme RAT,… [Continue Reading] -

Brits are more scared of spiders than cybercrime
Publié: mars 13, 2019, 5:03pm CET par Ian Barker
Cybercrime and hacking has overtaken flying, dogs and clowns in the top 10 list of things the British are most scared of, but still only ranks in sixth place behind spiders, heights, snakes, dentists and small spaces. Arachnids top the list despite there being less than a one-in-a-million chance of being bitten by a spider badly enough to warrant going to hospital in the UK. Cybersecurity company McAfee has released these findings to coincide with this week's 30th anniversary of the World Wide Web (and tomorrow's National Spider Day). According to the report, 23 percent of Brits have admitted to… [Continue Reading] -

Stricter payment requirements in Europe could drive fraud elsewhere
Publié: mars 13, 2019, 3:50pm CET par Ian Barker
From September this year the second Payment Services Directive (PSD2) comes into force across the EU. This will require payment service providers to offer strong customer authentication (SCA) and third-party access to bank accounts or risk losing their their payment provider license. But a new report today from fraud prevention company iovation suggests that stricter requirements for fraud prevention in Europe will drive fraud to other regions such as the US. The study, carried out with research firm Aite Group, also shows that with just six months to go most companies are still unprepared for PSD2. In fact, a recent… [Continue Reading] -

Researchers find two Android malware campaigns with over 250 million downloads
Publié: mars 13, 2019, 3:15pm CET par Ian Barker
Check Point Research has uncovered two massive mobile adware and data stealing campaigns, which have already had a combined total of over 250 million downloads globally. Both target mobiles using Android, and exploit the mobile app development supply chain to infect devices and perform malicious actions. The first is SimBad, a mobile adware campaign that has already had 147 million downloads across 210 infected apps on the Google Play Store. Called 'SimBad' because most of the infected apps are simulator games, the worldwide campaign makes phone usage unbearable for users by displaying countless ads outside of the app, with no… [Continue Reading] -

New platform helps enterprises to deploy and manage microservices networking
Publié: mars 13, 2019, 1:10pm CET par Ian Barker
More and more organizations are moving to a cloud-native, microservices architecture. But doing this at scale can be challenging as businesses lose the ability to trace, debug, and ultimately manage rapidly proliferating services. New company Tetrate is aiming to shake up the microservices networking market by combining the best of open source technologies with enterprise-grade extensibility, scalability, and performance. Tetrate's platform brings agility and security to the enterprise via intelligent traffic management for data centers and private and public clouds. The company's flagship products and services will help transform IT faster, to better support application availability and manageability concerns for… [Continue Reading] -

Two-thirds of Android antivirus apps block less than 30 percent of threats
Publié: mars 12, 2019, 5:17pm CET par Ian Barker
In one of the biggest tests of Android antivirus software ever conducted, out of 250 apps tested the majority proved to be dubious, unsafe or ineffective. Independent testing organization AV-Comparatives put the apps to the test against an array of common threats and found that some are not properly protecting users. Less than one in 10 of the apps tested defended against all 2,000 malicious apps, while over two thirds failed to reach a block rate of even 30 percent. Employing an automated test process (developed in co-operation with the University of Innsbruck), the test used physical Android devices rather… [Continue Reading] -

Continuous Delivery Foundation aims to boost success of open source projects
Publié: mars 12, 2019, 5:05pm CET par Ian Barker
An industry group made up of 22 members is launching a Continuous Delivery Foundation (CDF) to develop, nurture and promote open source projects, best practices and industry specifications related to continuous delivery. Founding members of the CDF include the Linux Foundation, Google, Microsoft, Netflix, Red Hat, CloudBees and the Jenkins Community The CDF will house a variety of open source projects, initial ones including Jenkins, Jenkins X, Spinnaker and Tekton. Additional projects are expected to join, with the goal of bringing together a continuous delivery ecosystem to build specifications and projects around portability and interoperability. "The time has come for… [Continue Reading] -

Employees waste two hours a day searching for data
Publié: mars 12, 2019, 3:16pm CET par Ian Barker
According to new research from data protection specialist Veritas Technologies, employees are losing two hours a day searching for data, and data management challenges are costing businesses as much as $2 million a year. On the other hand the study of 1,500 IT decision makers across 15 countries, carried out by Vanson Bourne for Veritas, shows organizations that invest in effective day-to-day management of their data have reported cost savings and better employee productivity as a result. Almost three-quarters (70 percent) say they have reduced costs, while 69 percent say their employees are now empowered to be more productive. "Organizations… [Continue Reading] -

Coinhive dominates malware charts before being shut down
Publié: mars 11, 2019, 12:50pm CET par Ian Barker
Coinhive continued to hold the top spot in Check Point Research's February Global Threat Index, impacting 10 percent of organizations worldwide, even though its services were shut down on March 8th. In February, the two most prevalent malware variants were cryptominers, followed by the Emotet banking Trojan. Coinhive has seen a downward trend in its global impact, from 18 percent of organizations in October 2018 to 12 percent in January 2019 and with a further two percent drop in February. This decrease has been caused by the rising cost of mining along with the decline in Monero's value. Cryptoloot rose… [Continue Reading] -

Windows 10 is now on more than 800 million devices
Publié: mars 8, 2019, 4:03pm CET par Ian Barker
The install base of Windows 10 has topped the 800 million mark according to the Microsoft Story Labs site. Microsoft executive Yusuf Mehdi tweeted the news yesterday. This is an increase of 100 million since September last year and it seems likely that the increase has been partly driven by the impending end of support for Windows 7. In October Microsoft said that more than 1.5 billion devices were running Windows, these latest figures therefore mean that more than half of Windows machines are now on Windows 10. Although Microsoft has been busy shifting its focus to services supplied from the… [Continue Reading] -

How the tech industry is becoming more attractive to women
Publié: mars 8, 2019, 3:23pm CET par Ian Barker
It won't have escaped your notice that today is International Women's Day. The technology sector has traditionally been a male dominated one, but it seems that efforts to attract more women are paying off. Analysis from Eclat Marketing of speakers at last week's RSA Conference shows a 53 percent increase in female speakers, with 232 compared to 153 in 2018. Male and female keynote speakers at RSA 2019 were also on almost equal footing, with 25 women speaking about various topics across the information security industry, compared to only eight the previous year -- an increase of 213 percent. Additional… [Continue Reading] -

New tool aims to improve the effectiveness of workforce communication
Publié: mars 8, 2019, 12:10pm CET par Ian Barker
At a time when there's intense competition in the jobs market, the importance of workforce communication in employee engagement is often overlooked. San Francisco-based communications platform SocialChorus is launching a new tool called Content Planner that gives organizations a single place to plan their content strategies and measure the impact of employee communications. "Marketers and sales teams have long benefited from tools to assist in their strategic planning, collaboration and measurement, but resources for internal communicators to take this same approach have often lagged behind," says Tim Christensen, chief technology officer at SocialChorus. "By helping organizations more strategically plan and… [Continue Reading] -

Banking Trojan attacks up by 16 percent in 2018
Publié: mars 7, 2019, 12:17pm CET par Ian Barker
Attacks using banking Trojans are among the most popular with cybercriminals as they are focused directly on financial gain. According to a new report from Kaspersky Lab, 889,452 users of Kaspersky Lab solutions were attacked by banking Trojans last year, an increase of 15.9 percent compared to 2017. Of the attacked users, almost a quarter were corporate ones, a figure that has remained fairly consistent for the last three years. According to Kaspersky Lab experts, the reason behind this is clear: while attacks on consumers will only provide access to personal banking or payment system accounts, successful hits on employees… [Continue Reading] -

How a new approach to threat detection can help with the security skills shortage [Q&A]
Publié: mars 6, 2019, 4:26pm CET par Ian Barker
There is an acknowledged shortage of security talent in the West, but at the same time a lack of opportunity in many developing nations such as South America and India is leading to fledgling talent utilising its expertise for nefarious acts rather than for legal activity. But a new approach to threat detection and prevention could help address the skills shortage while giving cybersecurity talent in developing countries the chance to earn an honest wage. We spoke to Steve Bassi, CEO of PolySwarm to find out more. BN: What is PolySwarm and how does it work? SB: It's a decentralized… [Continue Reading] -

Russian doll malware spreads via Pirate Bay
Publié: mars 6, 2019, 3:18pm CET par Ian Barker
Researchers at Kaspersky Lab have uncovered a new strain of malware spreading via The Pirate Bay torrent tracker site. Named after the classic Russian doll, PirateMatryoshka aims to infect users' computers with adware and tools that spreads further malware onto the device. It carries a Trojan-downloader disguised as a hacked version of legitimate software used in everyday PC activity. Torrent services are a popular target for cybercriminals looking to distribute malicious code, not least because users in search of illegal content often disconnect their online security solutions or ignore system notifications in order to install the downloaded content. PirateMatryoshka is… [Continue Reading] -

MS Word bug can be used to bypass security systems
Publié: mars 5, 2019, 5:09pm CET par Ian Barker
Researchers at email and data security company Mimecast have uncovered a bug in Microsoft Word that can be used to bypass security systems. The bug incorrectly handles integer overflows and can be used to circumvent security systems and fool parsers to deliver remote code that can take complete control over a compromised machine. The problem has been reported to Microsoft which has acknowledged that it is unintended behavior. It has declined to release a security patch at this time though, as the issue on its own does not result in memory corruption or code execution. The problem may be fixed… [Continue Reading] -

Microsoft Word bug can be used to bypass security systems
Publié: mars 5, 2019, 5:09pm CET par Ian Barker
Researchers at email and data security company Mimecast have uncovered a bug in Microsoft Word that can be used to bypass security systems. The bug incorrectly handles integer overflows and can be used to circumvent security systems and fool parsers to deliver remote code that can take complete control over a compromised machine. The problem has been reported to Microsoft which has acknowledged that it is unintended behavior. It has declined to release a security patch at this time though, as the issue on its own does not result in memory corruption or code execution. The problem may be fixed… [Continue Reading] -

Internet users are too confident they're protected
Publié: mars 5, 2019, 3:11pm CET par Ian Barker
Given the number of high profile security breaches that make the headlines, you'd expect people to be wary about online security. But a new study by Malwarebytes Labs shows a mismatch between people's confidence in their own privacy and security practices and their actual behavior. Malwarebytes surveyed almost 4,000 people and finds that while data privacy was a top concern, with trust in companies to maintain it painfully low, users do not follow through with some of the more difficult and cumbersome cybersecurity best practices to keep their data safe. The company believes this gap between perception and reality to… [Continue Reading] -

Students aren't aware of cybersecurity career opportunities
Publié: mars 5, 2019, 1:37pm CET par Ian Barker
It's well known that there is a skills shortage in cyber security, with a predicted global shortfall of 1.8 million cybersecurity professionals by 2022. But new research, commissioned by cybersecurity training organization the SANS Institute and conducted by respected research firm Vanson Bourne polled 4000 students across the UK and EMEA and reveals a lack of awareness of careers in the sector. The study shows 84 percent of surveyed UK students have never considered a career in cyber security, compared to 50 percent of surveyed students in Saudi Arabia and 46 percent in the UAE. Germany leads the way cyber… [Continue Reading] -

Attack traffic up 32 percent in 2018
Publié: mars 5, 2019, 11:00am CET par Ian Barker
Levels of attack traffic observed by F-Secure's network of decoy honeypots in 2018 increased by 32 percent over the previous year, and increased fourfold in the latter half of 2018 compared with the first half of the year. The report suggests that many companies may not have the visibility they need to catch attacks that make it past preventative measures like firewalls and endpoint protection. F-Secure's survey finds that 22 percent of companies didn't detect a single attack over a 12-month period. 20 percent of respondents detected just a single attack during that time frame, and 31 percent detected between… [Continue Reading] -

Open source breaches up by 71 percent
Publié: mars 4, 2019, 4:09pm CET par Ian Barker
Open source breaches have increased by 71 percent over the last five years, while 26 percent of companies have reported a confirmed or suspected web application breach in the past year alone according to a new report. The study from open source governance specialist Sonatype also shows 41 percent of executives admit their company doesn’t follow an open source governance programme. "Underpinning 80 to 90 percent of an enterprise application, open source components have played an instrumental role in driving innovation and accelerating time to market," says Derek Weeks, vice president and DevOps advocate at Sonatype. "But with as many… [Continue Reading] -

New specification sets the standard for passwordless logins
Publié: mars 4, 2019, 3:49pm CET par Ian Barker
The World Wide Web Consortium (W3C) and the FIDO Alliance have today announced that the Web Authentication (WebAuthn) specification is now an official web standard. W3C's WebAuthn recommendation, a core component of the FIDO Alliance's FIDO2 set of specifications, is a browser/platform standard for simpler and stronger authentication. Already supported in Windows 10, Android, and Google Chrome, Mozilla Firefox, Microsoft Edge and Apple Safari (in preview), WebAuthn allows users to log into their internet accounts using their preferred device. Web services and apps can -- and should -- turn on this functionality to give their users the option to log… [Continue Reading] -

How Open Banking could make online transactions safer [Q&A]
Publié: mars 1, 2019, 11:01am CET par Ian Barker
We recently reported on how formjacking has become a popular and lucrative form of online fraud. It’s difficult for the consumer to detect which makes it a particular hazard. But in the UK the new Open Banking standard, aimed at making it easier for consumers to share financial data across organizations, could make formjacking and other frauds obsolete. We spoke to Luca Martinetti, CTO and co-founder of financial API provider TrueLayer to find out more BN: Isn't open banking just aimed at increasing competition in the banking sector? LM: Open Banking is about much more than simply increasing competition. Fundamentally,… [Continue Reading] -

Demand for blockchain and security engineers soars
Publié: février 28, 2019, 5:50pm CET par Ian Barker
If you want to secure your future in the IT industry then it seems that blockchain and security are the areas you need to be in. A report from career marketplace Hired shows that in the past year there has been a 517 percent increase in demand for blockchain engineers year on year, and a 132 percent jump for security engineers. But while blockchain engineering is the most in-demand skill, only 12 percent of survey respondents identified it as the top technology they want to learn about. When it comes to preferences, 51 percent of survey respondents name Python as… [Continue Reading] -

Home endpoints twice as likely to be infected as businesses
Publié: février 28, 2019, 4:56pm CET par Ian Barker
Despite the fact that in recent months we've seen cybercriminals focusing their efforts on businesses, 68 percent of infections are seen on consumer endpoints, compared to 32 percent on business endpoints. This is one of the findings of the latest Webroot Threat Report, which also shows that legitimate websites are frequently compromised to host malicious content, with 40 percent of malicious URLs hosted on good domains. Phishing attacks have increased 36 percent, with the number of phishing sites growing 220 percent over the course of 2018. Phishing sites now often use SSL certificates and HTTPS to trick internet users into… [Continue Reading] -

40 percent of ticketing site traffic comes from bad bots
Publié: février 28, 2019, 4:10pm CET par Ian Barker
If you've ever tried to book tickets for a concert, festival or event you will know that it can be something of a frustrating experience, and bots could be making it even more so. New research from Distil Networks finds 39.9 percent of traffic on ticketing sites comes from bots used by brokers, scalpers, hospitality agencies, and sundry criminals to execute a number of attacks, including denial of inventory, spinning and scalping, scraping seat map inventory, fan account takeover, and fraud. "Although the ticketing industry has led the way in terms of bot legislation, as seen with the BOTS Act… [Continue Reading] -

Isolating privileged access is critical to security
Publié: février 28, 2019, 3:19pm CET par Ian Barker
A new study reveals that 87 percent of cybersecurity professionals believe separating privileged environments from corporate, internet-exposed environments is highly critical for protecting sensitive information. But the Privileged Access Workstations (PAW) survey carried out by Cybersecurity Insiders for endpoint security company Hysolate also finds that time-consuming access processes and the inability to install apps, browse the web or plug in external devices, are key implementation roadblocks. "Privileged users are targeted by cyberattackers because they have direct access to an enterprise's crown jewels. The good news, according to the PAW survey, is that the overwhelming majority of enterprises believe protecting these… [Continue Reading] -

97 percent of companies struggle to deploy and manage public clouds
Publié: février 28, 2019, 1:12pm CET par Ian Barker
Public cloud adoption is growing fast, but it's not without problems. A new report from network verification company Veriflow uncovers a disconnect between network and other teams involved in the management and oversight of the public-cloud portion of their networks. IT teams are struggling with network infrastructure challenges caused by the cloud, such as impaired visibility and more frequent security threats. A startling 97 percent of companies report having problems with deploying and managing public clouds. This presents a growing problem that could put organizations at financial risk. "Public cloud deployments are rapidly growing but IT teams do not have… [Continue Reading] -

Optimizing cost is key priority for cloud users
Publié: février 27, 2019, 3:52pm CET par Ian Barker
Optimizing existing cloud use for cost savings is the top initiative for users in 2019 for the third year in a row, increasing to 64 percent from 58 percent in 2018. This is one of the findings of the RightScale 2019 State of the Cloud Report from Flexera. Among other highlights are that enterprises plan to spend 24 percent more on public cloud in 2019 compared to 2018. The sums involved are significant with 13 percent of enterprises spending more than $12 million a year on public cloud, while 50 percent spend more than $1.2 million annually. However, respondents estimate… [Continue Reading] -

Credential stuffing remains a major problem for retail sites
Publié: février 27, 2019, 2:54pm CET par Ian Barker
Thanks to the huge volume of stolen credentials now available online, credential stuffing has become a major issue for the retail industry. A new report from edge platform specialist Akamai shows that hackers directed credential abuse attempts at retail sites more than 10 billion times from May to December last year. Hackers target login pages for banks and retailers on the premise that many customers use the same login credentials for multiple services and accounts. Interest in retail is driven by the value of merchandise, which hackers can acquire through compromised accounts and then resell. The report reveals that hackers… [Continue Reading] -

Peer analytics offers better visibility into security performance
Publié: février 27, 2019, 12:36pm CET par Ian Barker
It's useful for security and risk leaders to know their industry's security performance standards and be able to perform peer and sector-wide security benchmarking. But the information to be able to do that isn't always easily available. Security ratings company BitSight is launching a new Peer Analytics feature on its platform that allows the comparison of security performance across global organizations. BitSight Peer Analytics provides organizations with leading industry and critical peer group cybersecurity performance measurements. This gives security leaders real-time access to broad, deep, meaningful, objective data and metrics on industry-wide security and peer-level performance across multiple categories of… [Continue Reading] -

How next generation technology is transforming the data center [Q&A]
Publié: février 27, 2019, 11:11am CET par Ian Barker
The demands of digital transformation inevitably lead to additional stresses on the data center. It's no surprise then that enterprises are increasingly turning to technology solutions to improve their data center management and workload monitoring. But what can these solutions deliver and how effective are they? We spoke to Jeff Klaus, GM of data center management solutions at Intel, to find out. BN: What are some key benefits of data center management solutions? JK: There are several benefits to a data center management solution, but the overarching advantage for businesses is the ability to receive a holistic view of its… [Continue Reading] -

Mobile security platform combines biometrics and behavior to enhance security
Publié: février 26, 2019, 4:36pm CET par Ian Barker
Multi-factor authentication specialist Veridium is launching a new behavior analytics feature to better protect user identities and prevent malicious activity. Incorporated in the VeridiumID authentication platform, InMotion increases the reliability of all native biometrics for authentication by pairing behavioral data captured on smartphones with users' biometrics, making it more difficult for malicious actors to spoof their fingerprints or faces to gain access to accounts. "As data breaches and insider threats increasingly plague the enterprise, businesses are in need of a strong solution that can better recognize and verify users’ identities," says Ionut Dumitran, Veridium's head of product development. "With user… [Continue Reading] -

Americans more likely to stop dealing with a brand after a breach but Brits hold a grudge for longer
Publié: février 26, 2019, 3:49pm CET par Ian Barker
New research into consumer trust and spending habits by contact center payment security company PCI Pal shows 62 percent of Americans report that they will stop spending with a brand for several months following a hack or breach, versus 44 percent of Brits. But when the British do react they do so for the long term, 41 percent of British consumers never return to a brand after a hack compared to only 21 percent of Americans. Perception of security is important too -- 31 percent of UK consumers state that they spend less with brands they perceive to have insecure… [Continue Reading] -

The cloud moves too fast for security say 60 percent of security pros
Publié: février 26, 2019, 2:59pm CET par Ian Barker
Cloud-based business initiatives are accelerating faster than security organizations' ability to secure them according to 60 percent of respondents to a new survey. The study by network security company FireMon also finds that in many cases security personnel are not even included in cloud business initiatives. Only 56 percent of respondents say that network security, security operations or security compliance teams are responsible for cloud security. In the remaining 44 percent of cases, IT/cloud teams, application owners or other teams outside the security organization are responsible for cloud security. The relationship between DevOps and security is similarly inconsistent. 39 percent… [Continue Reading] -

Cybercriminals earn over $3 billion a year from social platforms
Publié: février 26, 2019, 1:10pm CET par Ian Barker
Social media-enabled cybercrimes are generating at least $3.25 billion in global revenue annually according to a new report. The study released by virtualization-based security company Bromium and researched and written by Dr Mike McGuire, senior lecturer in criminology at the University of Surrey, looks at the range of techniques used by cybercriminals to exploit trust and enable rapid infection across social media. It also details the range of services being offered in plain sight on social networks, including, hacking tools and services, botnets for hire, facilitated digital currency scams and more traditional criminal activities. Among the findings are that reports… [Continue Reading] -

'Hi, how can we scam you today?' -- Office 365 phishing site comes with live chat support
Publié: février 25, 2019, 5:26pm CET par Ian Barker
An increasingly common -- and frankly rather annoying -- feature of many commercial websites is the little chat box that pops up in the bottom right corner and asks if you need any help. Security researcher Michael Gillespie has revealed that an Office 365 phishing site is using this live support technique to give its page an air of legitimacy. As BleepingComputer reports, the site isn't particularly convincing, but it seems likely that if scammers see results from this technique they will get better at using it over time. Starting a chat session sees the scammers use social engineering to… [Continue Reading] -

New platform helps enterprise networks get closer to the edge
Publié: février 25, 2019, 3:10pm CET par Ian Barker
Driven by the growth of mobile computing, IoT devices and the upcoming 5G rollout, edge networking is on the rise and leading businesses to take a fresh look at their networking strategies. But going from a traditional approach to a virtualized, cloud-native, and software-driven network that connects headquarters to multiple branches and deploys new services like SD-WAN, Virtualized Customer Premises Equipment (vCPE), and IoT devices isn’t easy. Orchestration platform provider, Cloudify is launching its new Cloudify Spire, platform designed to connect and control distributed networks, devices, and applications all the way to the edge. Spire uses micro-orchestration architecture that scales… [Continue Reading] -

The changing enterprise mobile threat landscape
Publié: février 21, 2019, 4:35pm CET par Ian Barker
As enterprises continue the shift towards mobile devices there's concern that the risks could begin to outweigh the benefits. Mobile security specialist Wandera has released a new report on the mobile threat landscape which looks at the risks faced by enterprise mobile users. Among some worrying findings are that 77 percent of users had some form of PII leaked in 2018, with 70 percent of Wi-Fi sessions conducted over an unencrypted connection. In addition 43 percent of companies have at least one mobile device among their employees with no lock screen. Phishing remains the biggest threat and 57 percent of… [Continue Reading] -

83 percent of US organizations have accidentally exposed sensitive data
Publié: février 21, 2019, 3:13pm CET par Ian Barker
According to a new survey 83 percent of security professionals believe that employees have accidentally exposed sensitive customer or business data at their organization. The study from data protection specialist Egress also finds that accidental data breaches are often compounded by a failure to encrypt data prior to it being shared -- both internally and externally. The five most common technologies that have led to accidental data breaches by employees are external email services like Gmail and Yahoo (51 percent), corporate email (46 percent), file sharing services like FTP sites (40 percent), collaboration tools such as Slack and Dropbox (38… [Continue Reading] -

Employees and contractors expose information online in 98 percent of organizations
Publié: février 20, 2019, 4:14pm CET par Ian Barker
Employees and contractors are exposing confidential and sensitive information online and in the cloud in some 98 percent of organizations. This is found primarily in Dropbox, Google, and Microsoft SharePoint. This is among the findings of a new report from insider threat specialist Dtex Systems which has analyzed information from work-issued endpoints and more than 300,000 employee and contractor accounts. All of the assessments detected employees and contractors transferring confidential and sensitive data via unencrypted USB drives, personal email accounts, and cloud applications, an increase of 10 percent over 2018. In addition 97 percent of assessments detected employees and contractors… [Continue Reading] -

Cloud data warehouses are key to digital transformation
Publié: février 20, 2019, 3:16pm CET par Ian Barker
Cloud data warehouses (CDW) offer broader data capabilities, stronger performance, and greater flexibility than traditional on-premise databases according to a new survey. But the study by TDWI on behalf of Talend also shows enterprises need to follow some best practices to overcome implementation challenges and increase investment return. While survey respondents noted that adopting CDWs was critical to helping them achieve faster performance and lower costs, and take advantage of cloud features, there were a number of challenges associated with CDWs as well. More than half of respondents cite 'data governance' as a top challenge, closely followed by 'integrating data… [Continue Reading] -

Formjacking is the new cash generator for cybercriminals
Publié: février 20, 2019, 11:29am CET par Ian Barker
The latest Symantec Annual Threat Report reveals that cybercriminals are continuing to follow the money, but as ransomware and cryptojacking show falling returns they are turning to other techniques. One of these is formjacking -- essentially virtual ATM skimming -- where cybercriminals inject malicious code into retailers' websites to steal shoppers' payment card details. On average, more than 4,800 unique websites are compromised with formjacking code every month. Symantec has blocked more than 3.7 million formjacking attacks on endpoints in 2018, with nearly a third of all detections occurring during the busiest online shopping period of the year -- November… [Continue Reading] -

Branded calling solution seeks to rebuild trust in mobile calls
Publié: février 19, 2019, 4:14pm CET par Ian Barker
A few months ago we reported on a study that found half of calls to mobiles would soon be scams without more effective protection measures being introduced. First Orion the company behind that survey is addressing the problem with the launch of a new platform that gives consumers confidence in answering calls, but also helps businesses get their legitimate communications through. The Engage platform lets businesses brand their outgoing calls with graphics to identify them as genuine. It also allows them to have details of why they are calling displayed on the phone's screen -- such as banks calling to… [Continue Reading] -

New solution protects converged IT and OT environments
Publié: février 19, 2019, 3:14pm CET par Ian Barker
The line between information technology and operational technology is an increasingly blurred one. As companies drive towards digital transformation so OT environments increasingly interconnect with IT, resulting in a complex, sensitive and vastly expanded attack surface. This means OT security responsibility is often moving to to the CISO. Yet traditional IT security solutions lack the ability to continuously discover and assess sensitive OT assets. Cyber exposure specialist Tenable is addressing this issue with the launch of an integrated cyber exposure solution to provide a unified view of cyber risk spanning IT and OT, from enterprise applications to industrial control systems.… [Continue Reading] -

New access suite delivers a software defined perimeter for hybrid environments
Publié: février 19, 2019, 2:44pm CET par Ian Barker
The move to accessing applications from the cloud and provisioning resources dynamically has led to organizations moving to a zero trust strategy to guard against attacks and data leaks. However, this can be hard to achieve with hybrid environments. Secure access specialist Pulse Secure is adding Software Defined Perimeter (SDP) architecture to its platform to extends its foundation of Zero Trust access for hybrid IT. The move provides enterprises and service providers with unrivaled provisioning simplicity, security posture fortification and lower total cost of ownership. "Business leaders face a digital imperative to boost user productivity, while also mitigating the risk… [Continue Reading] -

The speed and cost of internet around the world
Publié: février 18, 2019, 4:20pm CET par Ian Barker
Within any given country, while you might have a choice of different internet providers, the speeds they offer and the prices they charge tend to be broadly similar. UK-based comparison site Compare the Market has done some interesting research looking at the costs and speeds of broadband around the world. So prepare to be made jealous, or smug, depending on where you live. Fastest place to be is Singapore with average download speeds of 185.25 Mbps. Iceland is second with 153.3 Mbps, followed by South Korea with114.31 Mbps. The US is fifth with 107.28 Mbps while the UK is 27th… [Continue Reading] -

How enterprises can cut the risk of cloud vendor lock in [Q&A]
Publié: février 18, 2019, 11:25am CET par Ian Barker
While most CIOs have now identified the benefits cloud can have for their business, concerns over becoming locked in with a single vendor can still be a major barrier to rolling out projects. We spoke to Richard Best, general manager at COMPAREX UK, to find out why this is the case and what companies can do to avoid vendor lock in. BN: What are CIOs most pressing concerns over cloud? RB: While most CIOs have now identified the benefits cloud can have on their business, worries over vendor lock-in can still be a major obstacle to adoption. Freedom of Information… [Continue Reading] -

How contact centers have become a prime target for hackers [Q&A]
Publié: février 15, 2019, 3:53pm CET par Ian Barker
With growing security threats and compliance being taken seriously, companies are more aware than ever of the need to protect their data. This means hackers must work harder to try to steal information and contact centers are in the front line. We spoke to Ben Rafferty, chief innovation officer at security and compliance specialist Semafone to find out how contact centers are under threat and what can be done to protect them. BN: What makes call centers particularly vulnerable? BR: They've always been vulnerable, but they haven't historically been attacked. What's happened -- certainly in the US with the introduction… [Continue Reading] -

Dark web tags harm website performance and put data at risk
Publié: février 14, 2019, 5:03pm CET par Ian Barker
Website tags, small pieces of JavaScript code or small images, are often used to collect information about users. But they can add to load times and if misused can be a security risk too. A new study from digital governance specialist Crownpeak reveals over 1,700 'dark web' tags found on websites belonging to companies in the Fortune 100, causing a total average website latency of 5.2 seconds. Crownpeak categorised tags into 'first-party tags' -- added directly to the source code of a web page, and 'dark web tags' -- injected by first-party tags either intentionally or unintentionally. The 20 worst… [Continue Reading] -

Zoho launches next generation Office Suite with added AI
Publié: février 14, 2019, 4:14pm CET par Ian Barker
Popular cloud-based office suite Zoho is launching a new version of its software complete with AI-powered personal assistant. Zoho Office is made up of four cloud-based productivity software applications -- Zoho Writer, Zoho Sheet, Zoho Show, and Zoho Notebook. These are fully integrated with each other and with Zoho Mail the company’s messaging app Cliq. Key feature of the latest version is the use across the board of the 'Zia' AI-powered assistant. In Zoho Writer, Zia can detect context-based grammar mistakes, rate the readability score of each document, and suggest style corrections to improve overall writing quality. In Zoho Sheet,… [Continue Reading] -

Roses are red, violets are blue, Valentine scammers are out to trick you
Publié: février 14, 2019, 3:28pm CET par Ian Barker
A Nigeria-based gang of scam artists, known as Scarlet Widow, have been using romance scams to trick victims out of large amounts of cash. Secure email company Agari has uncovered the scam which involves posting fake personas on the largest dating websites like Match, eHarmony, and OKCupid. Scarlet Widow also targets relationship seekers on more specialized sites, such as Dating4Disabled.com, FarmersDatingSite.com, and DivorcedPeopleMeet.com, and uses sites for people seeking partners in the US military, including MilitaryCupid.com. Fake personas used include 'Laura Cahill,' a Texan model working in Paris; 'Starling Micheal,' a handsome United States Army captain stationed in Afghanistan, whose… [Continue Reading] -

Mobile marketers increase their focus on data
Publié: février 13, 2019, 3:43pm CET par Ian Barker
Data has become an increasingly popular resource for marketers, new research from marketing platform YouAppi reveals that 98 percent of respondents say they have increased their organizational investment in data. What's more that investment is paying off, 97 percent say they have seen improvement, with more than half of those calling the improvements ‘significant.’ Areas of investment include reporting and dashboard technology (81 percent), in-house data analytics teams (64 percent), purchasing third party performance data (47 percent), adding more data-centric roles on internal teams (46 percent) and hiring outside agencies for data analysis (24 percent). As well as increased spending,… [Continue Reading] -

Only one in three organizations is confident of avoiding a data breach
Publié: février 13, 2019, 3:06pm CET par Ian Barker
A majority of organizations are not confident in their ability to avoid major data breaches according to a new study. The report for breach avoidance company Balbix, based on research from the Ponemon Institute, shows that 68 percent feel their staffing is not adequate for a strong cybersecurity posture and only 15 percent say their patching efforts are highly effective. It also reveals that 67 percent feel they don't have the time and resources to mitigate all vulnerabilities in order to avoid a data breach, and 63 percent say 'inability to act on the large number of resulting alerts and… [Continue Reading] -

Security worries hold back second-hand mobile device market
Publié: février 13, 2019, 11:01am CET par Ian Barker
According to the results of a new study, 58 percent of global consumers have yet to trade in an old mobile device, though 64 percent report they would be willing to do so if more stringent data management processes were in place. The research by data erasure specialist Blancco shows 66 percent of respondents have some concern that data on their old devices might be accessed or compromised after trade-in. "The secondary mobile device market is a huge success story," says Russ Ernst, EVP, products and technology at Blancco. "Each of its major stakeholders -- operators, OEMS and 3PLs --… [Continue Reading] -

Could the 3D video selfie replace 2FA?
Publié: février 12, 2019, 5:16pm CET par Ian Barker
The industry is constantly looking for ways to bolster login security. Multi-factor authentication and knowledge-based systems are popular but can be cumbersome, so how about using something you carry around all the time, yourself -- or indeed yourselfie? Identity specialist Jumio is launching Jumio Authentication, a video-selfie authentication tool enabling users to verify themselves during high-risk transactions and unlock everything from online accounts to rental cars, replacing passwords on any device. "As more of our important interactions move online, establishing trust digitally has become critical," says Stephen Stuut, CEO of Jumio. "Jumio is pioneering selfie-based authentication to allow businesses to… [Continue Reading] -

Unmanaged open source code could put companies at risk
Publié: février 12, 2019, 4:15pm CET par Ian Barker
More than half the code found in commercial software packages is open source, but if it isn’t properly tracked businesses might be in the dark on the number of vulnerabilities and license compliance issues that exist in their applications. Software supply chain specialist Flexera has released a report looking into the state of open source license compliance, based on analyzing data from 134 software audits. On average, the Flexera audit teams find one issue within every 32,873 lines of code. That might sound like a small number, but most applications now have well over 1,000,000 lines of code. Flexera discovered… [Continue Reading] -

Phishing gets more personal and harder to detect
Publié: février 12, 2019, 3:28pm CET par Ian Barker
An analysis of phishing attacks in the final quarter of 2018 reveals the majority of attacks showed an increase in target personalization, making them considerably more difficult to detect. The study by email protection start up INKY shows 12 percent of phishing attacks in the period took the form of corporate VIP impersonations, 10 percent were sender forgery and six percent were via corporate email spoofing. The corporate impersonation attacks often take place in real time and involve a scenario where the CEO (or perhaps someone from finance) is claimed to be in a meeting, or is in a limited… [Continue Reading] -

Data integration is the number one challenge for enterprises
Publié: février 12, 2019, 1:22pm CET par Ian Barker
Almost half of respondents to a new survey identify ever-increasing disparate data sources as a major pain point. The study from development technology specialist Progress also finds 44 percent of respondents are worried about integrating cloud data with on-premises data, making real-time hybrid connectivity critical. Increased data security vulnerabilities, penalties and regulations are creating new challenges and opportunities for data integration too. More than 65 percent of survey respondents say they have to comply with one or more standards. Standards-based access is growing in popularity as the number of data sources continues to grow at a rapid pace. Over 50… [Continue Reading] -

Machine learning tool helps prioritize vulnerabilities
Publié: février 11, 2019, 4:19pm CET par Ian Barker
One of the keys to keeping systems secure is to effectively prioritize vulnerabilities. Given the volume, with 16,500 new vulnerabilities disclosed in 2018 alone, though this is a tough task. To help businesses focus on the highest risks, Tenable is launching a new Predictive Prioritization tool that uses machine learning to zoom in on the three percent of vulnerabilities with the greatest likelihood of being exploited in the next 28 days. Predictive Prioritization analyzes Tenable's vulnerability data combined with third-party vulnerability data and threat intelligence across 150 data sources using a proprietary machine learning algorithm to predict the likelihood that… [Continue Reading] -

New cloud app helps businesses understand their IT environments
Publié: février 11, 2019, 3:18pm CET par Ian Barker
As systems become more complex it can be hard for enterprises to understand their IT environment, which presents a problem for operations and security teams. Cloud-based security specialist Qualys is launching a new IT Asset Inventory cloud application to provide quick analysis of complex and interconnected global IT environments, and help collaboration on security remediation efforts. Qualys Asset Inventory collects and analyzes data about assets across hybrid environments, and delivers up-to-date, comprehensive and continuous information about those assets along with their security and compliance posture. "You simply cannot secure what you do not know, and our new groundbreaking global IT… [Continue Reading] -

Number of DDoS attacks falls but sophistication improves
Publié: février 7, 2019, 3:47pm CET par Ian Barker
2018 saw a decline of 13 percent in the overall number of DDoS attacks when compared to the previous year, but cybercriminals are turning to longer, more sophisticated, mixed and HTTP flood attack techniques. This is revealed in Kaspersky Lab's DDoS Q4 2018 Intelligence Report, which also shows the average attack duration has grown. Compared with the beginning of the year, the average length of attacks has more than doubled -- from 95 minutes in Q1 to 218 minutes in Q4 2018. The most common type of attack is User Datagram Protocol (UDP) flooding (accounting for 49 percent), but these… [Continue Reading] -

Microsoft continues to beat Google in battle of the enterprise apps
Publié: février 7, 2019, 11:25am CET par Ian Barker
A new survey from identity platform Okta shows that 67 percent of knowledge workers prefer Microsoft Word over Google Docs, while only 15 percent report the opposite. Another 16 percent identify Google Docs as a top-three most frustrating app. When it comes to email, 49 percent prefer Microsoft Outlook over Gmail, while 35 percent report the opposite. The study also looks at the fastest growing apps, where security and collaboration dominate. The top five are KnowBe4 (with 178 percent growth), LastPass (132 percent), ProofPoint (122 percent), Jamf Pro SAML (120 percent) and Zoom (107 percent). Security apps take the top… [Continue Reading] -

Airline e-ticketing systems put passenger data at risk
Publié: février 6, 2019, 4:37pm CET par Ian Barker
Airlines could be putting the personal data of their passengers at risk by using unencrypted links, according to a new report. Researchers at security and data management company Wandera have uncovered a vulnerability affecting a number of e-ticketing systems that could allow third parties to view, and in some cases even change, a user's flight booking details, or print their boarding passes. The problem affects a number of major airlines including Southwest, Air France, KLM and Thomas Cook. All of these have sent unencrypted check-in links to passengers. On clicking these links, a passenger is directed to a site where… [Continue Reading] -

Two-thirds of organizations bypass IT for digital transformation projects
Publié: février 6, 2019, 3:15pm CET par Ian Barker
According to a new report released by The Economist Intelligence Unit and sponsored by BMC software, 66 percent of organizations bypass IT when buying new technologies for digital transformation. But despite this, 43 percent of firms still hold IT accountable if something goes wrong with their digital transformation initiatives. The findings are based on a survey of senior executives and administrators in Asia-Pacific, Europe, Latin America and North America. Reasons given for the lack of collaboration with IT departments on digital transformation initiatives include misalignment in objectives, with non-IT teams prioritizing revenue growth and reducing costs, in contrast to IT… [Continue Reading] -

Google launches new tools to help protect your accounts
Publié: février 5, 2019, 4:36pm CET par Ian Barker
To coincide with Safer Internet Day, search giant Google is launching two new tools to help users detect if their username and password have been compromised. Google's own research published today shows that many people still reuse passwords. The new tools are designed to raise awareness of account issues. Password Checkup is a new Chrome extension which detects if a username and password on a site you use has been compromised. If it has, the extension will trigger a warning and suggest that you change your password. This proactive safety measure reduces the risk of account hacking by ten times,… [Continue Reading] -

Most people believe they're more secure online than they really are
Publié: février 5, 2019, 4:05pm CET par Ian Barker
New research commissioned by Google, carried out by Harris Poll and released to coincide with Safer Internet Day suggests there is a gap between perception and reality when it comes to online security. The majority of people (69 percent) give themselves an A or B when it comes to protecting their online accounts -- only five percent give themselves a D or an F. In fact, most people (59 percent) believe that their accounts are safer from online threats than the average person and 61 percent say they are too smart to fall for a phishing scam. But despite this… [Continue Reading] -

New tool makes it easier to secure IoT devices
Publié: février 4, 2019, 2:56pm CET par Ian Barker
Internet of Things devices are appearing in more and more companies, but with them comes the threat of cyberattacks. To reduce this risk Extreme Networks is launching a simple security solution to help organizations protect unsecured IoT devices. Called Defender for IoT it can be deployed on any network and is easy for even non-technical staff at schools, hospitals, retailers and hospitality venues to use to isolate and protect both wired and wireless IoT devices from cyberattacks. Most IoT devices lack embedded security as they were built to run on private networks where the assumption was it was tightly controlled,… [Continue Reading] -

Are 'pop-up' SOCs the answer to protect major events? [Q&A]
Publié: février 1, 2019, 3:58pm CET par Ian Barker
Increasingly high profile one-off events like sports tournaments and elections are becoming the target of hackers. Protecting these is tough because even if the hosts have a sound security infrastructure for day-to-day operations, they often don't have the resources necessary to lock down a large scale, high-profile event which requires additional physical and cybersecurity to protect against disruption, revenue loss or other irreversible damage. The answer may lie in the idea of a 'pop-up' security operations center (SOC) which can be deployed quickly to deal with times of abnormal traffic and network distress at large events. We spoke to Dave… [Continue Reading] -

Have you plugged it in? The silliest IT support calls of 2018
Publié: février 1, 2019, 12:52pm CET par Ian Barker
Just as the biggest problem with a car is often the nut holding the wheel, many IT support issues are down to the user rather than the equipment. UK-based support company Probrand has compiled a list of some of the oddest support calls it has received over the past year. It also reveals that in the first week of January, the volume of support calls was 47 percent higher than an average week, mainly from workers who needed assistance with logging in and resetting their password, having forgotten it over the Christmas break. "After the Christmas shutdown or bank holiday… [Continue Reading] -

Over 90 percent of organizations hit by targeted email attacks
Publié: janvier 31, 2019, 4:12pm CET par Ian Barker
Over the past year, business email compromise (BEC) scams have jumped by 60 percent. In addition more than 90 percent of organizations report being hit by targeted email attacks, with 23 percent suffering financial damage as a result. These findings come from the Q1 2019 Email Fraud and Identity Deception Trends report by secure email specialist Agari. The report shows that 96 percent of successful data breaches now begin with an email, and 20 percent of attacks come from compromised accounts. Brand impersonation remains the most common attack vector, used in 50 percent of advanced email attacks in the fourth… [Continue Reading] -

CISOs must change their outlook or lose their jobs
Publié: janvier 31, 2019, 3:20pm CET par Ian Barker
Chief information security officers (CISOs) are now involved in 90 percent of significant business decisions, but just 25 percent of business executives see CISOs as proactively enabling digital transformation -- which is a key goal for 89 percent of organizations. These are among the findings of a new study by IDC sponsored by Capgemini but which also shows 15 percent still believe information security is a blocker of innovation. At present, less than 25 percent of business executives think CISOs proactively enable digital transformation. To stay relevant, CISOs must become business enablers. They need to adopt business mindsets and push… [Continue Reading] -

New context sensitive tool helps businesses comply with data protection
Publié: janvier 30, 2019, 3:06pm CET par Ian Barker
The introduction of new regulatory and privacy laws around the world is forcing companies to become more aware of the personal customer info they are holding, but it can be hard to identify sensitive information. AI-based compliance platform Cognigo is launching a new data protection capability that can differentiate between sensitive and non-sensitive data based on language context. NLP Contextualization collects, extracts, and labels data across all data storage silos whether stored on premises or in the cloud. It then analyzes the context of terms that may relate to specific persons in the sentence to determine whether or not sensitive… [Continue Reading] -

How data is changing the face of marketing [Q&A]
Publié: janvier 29, 2019, 5:46pm CET par Ian Barker
Thanks to increased ability to collect data in real time, and the use of AI to process and interpret that data, marketers have more opportunity than ever to personalize their offerings to customers. But what does this mean for enterprises when it comes to spending their marketing budgets and establishing a digital strategy? We spoke to the CEO of Digital Marketing Agency, Solomon Thimothy to find out how digital marketing can be used to drive business growth. BN: What are the most important sources of customer data for marketers? ST: Google Analytics, Facebook Analytics, and the company's CRM. First, even… [Continue Reading] -

Symantec boosts its endpoint security offering
Publié: janvier 29, 2019, 4:08pm CET par Ian Barker
Sophisticated attackers are increasingly taking advantage of the complexity of endpoint environments to exploit gaps and discover new paths to lucrative targets. Symantec is announcing enhancements to its endpoint security portfolio designed to defend against the most sophisticated cyberattacks as well as improving application discovery and risk assessment. Symantec has incorporated advanced protection and hardening into its endpoint security solution which delivers a coordinated, adaptive endpoint defense that is simple for security teams to manage. This defense framework reduces the attack surface and delivers protection from unauthorized access, known vulnerabilities, zero-day attacks, and everything in between. All this is delivered… [Continue Reading] -

Rush to digital transformation puts security of data at risk
Publié: janvier 29, 2019, 3:13pm CET par Ian Barker
Digital transformation projects are underway in the vast majority of businesses, according to a new report, but 'aggressive' transformers are most at risk from data breaches. The latest Data Threat Report from Thales eSecurity shows digital transformation in some form is happening in 97 percent of organizations. 86 percent say they feel vulnerable to threats, yet less than a third of respondents (only 30 percent) are using encryption within these environments. As companies move to the cloud or multi-cloud environments as part of their digital transformation, protecting their sensitive data is becoming increasingly complex. Nine out of 10 respondents are… [Continue Reading] -

JavaScript is favorite language among developers
Publié: janvier 29, 2019, 12:01pm CET par Ian Barker
A survey of over 70,000 developers from around the world reveals that 73 percent say they are proficient in JavaScript. The study from hiring platform HackerRank shows JavaScript has replaced Java which took the top spot last year. AngularJS has maintained its spot as the most popular framework year-on-year, though the number of developers reporting experience with React jumped notably to 25 percent in 2018 from 19 percent in 2017. "Hiring and retaining skilled developers is critical for businesses everywhere. Recruiters and hiring managers need a deep understanding of who developers are, what they care about and what they want… [Continue Reading] -

69 percent of employees share passwords with colleagues
Publié: janvier 28, 2019, 2:47pm CET par Ian Barker
According to a new study, 69 percent of respondents admit to sharing passwords with others in the workplace, and 51 percent reuse an average of five passwords across their business and personal accounts. The study by authentication key vendor Yubico and Ponemon, released to coincide with Data Protection Day, also finds two-factor authentication isn't widely used, 55 percent don't use it at work and 67 percent don't use it for their personal accounts. More than half of respondents (51 percent) say they have experienced a phishing attack in their personal life, while 44 percent have had a phishing attack at… [Continue Reading] -

Automated attacks target cloud infrastructure
Publié: janvier 24, 2019, 3:24pm CET par Ian Barker
Enterprises continue to grow their cloud usage, but this inevitably presents challenges when it comes to keeping systems secure. New research from Securonix Threat Research highlights an increase in automated attacks targeting cloud infrastructures. Some of the attacks, for example Moanacroner, are trivial, targeted single-platform attacks where the focus is mainly on cryptomining. Others, are multi-platform threats where multiple functionalities (cryptomining, ransomware, botnet/worms, etc.) are combined as part of the same malicious threat, for example Xbash. The researchers note that, "In most cases, the focus of the attacks is on installing a second-stage payload for cryptomining and/or remote access. In… [Continue Reading] -

Feel overlooked and underappreciated? You must work in IT security
Publié: janvier 24, 2019, 12:13pm CET par Ian Barker
Most IT security professionals in the UK feel they’re suffering from an image problem among fellow workers, according to new research commissioned by privileged access management specialist Thycotic. Almost two thirds of respondents (63 percent) feel that their security teams are either viewed as the company naysayers -- specifically either 'doom mongers' or a 'necessary evil' (36 percent). In addition, 27 percent of respondents say company security and security professionals are just something that runs in the background which employees don’t really notice. 38 percent believe that they’re viewed as 'policemen.' When asked if they'd ever experienced negativity towards their… [Continue Reading] -

New solution protects enterprises against ransomware
Publié: janvier 23, 2019, 5:47pm CET par Ian Barker
Ransomware attacks are increasingly well targeted and complex, and they can prove devastating for businesses. Storage specialist Cohesity is launching a new set of anti-ransomware capabilities for its DataPlatform that can directly combat attacks. It offers three levels of security, the first is prevention which guards backup copies. If an attacker tries to modify a backup, Cohesity DataPlatform will write the data to a new instance, keeping the original snapshot intact and preserved. It also allows selected jobs to be locked to ensure a higher level of protection. Plus multi-factor authentication helps guard against phishing or brute force password attacks.… [Continue Reading] -

New Android app allows simple two-factor authentication across all apps and accounts
Publié: janvier 23, 2019, 3:10pm CET par Ian Barker
We're all being encouraged to use two-factor authentication to make our online accounts more secure. But 2FA can be a major pain when you update to a new device and have to re-authenticate everything. Even when users save their private 2FA keys to migrate onto new devices, it can still take time to manually reset 2FA for each account. Now though specialist in Mobile cybersecurity Rivetz is launching a new Authenticator app that offers backup and recovery of 2FA keys using mobile devices' existing hardware security capabilities. In a Rivetz-commissioned survey of 1,000 US adults, 49 percent of respondents say… [Continue Reading] -

Consumer threats down as cybercriminals target business
Publié: janvier 23, 2019, 11:21am CET par Ian Barker
Consumer threats declined by three percent in 2018 as cybercriminals learned that businesses can deliver a much bigger payout. The latest State of Malware report from Malwarebytes shows consumer threats decreased steadily across the board including a 30 percent drop in adware, an 84 percent decrease in hijacker tools, a 28 percent decrease in worm activity and a 29 percent drop in ransomware. At the same time business threats increased by 79 percent as cybercriminals set their sights on the workforce. For example, Trojan threat detections increased by 132 percent. The report also saw riskware tools jump 126 percent, backdoor… [Continue Reading] -

The most-clicked phishing lines of 2018
Publié: janvier 22, 2019, 4:55pm CET par Ian Barker
Security awareness training company KnowBe4 has put together its latest list of the most-clicked phishing subject lines. Popular categories for phishing messages include, deliveries, passwords, company policies, vacations and IT department. Other popular keywords are, Amazon, Wells Fargo and Microsoft. "Clicking an email is as much about human psychology as it is about accomplishing a task," says Perry Carpenter, chief evangelist and strategy officer at KnowBe4. "The fact that we saw 'password' subject lines clicked four out of four quarters shows us that users are concerned about security. Likewise, users clicked on messages about company policies and deliveries each quarter… [Continue Reading] -

Poor integration costs businesses $500,000 a year
Publié: janvier 22, 2019, 4:25pm CET par Ian Barker
Businesses across all industries face B2B, application, and cloud integration challenges that jeopardize revenue opportunities and threaten growth, and more than half of organizations report that those challenges take a $500,000 toll on the business every year. A study by cloud integration specialist Cleo reveals that of IT decision makers surveyed, 57 percent say poor integrations and lack of resources contribute to hundreds of lost orders each year, leading to annual revenue losses in the range of $250,000 to $500,000. "The fact that the majority of businesses face revenue losses of at least $250,000 each year is a startling statistic,… [Continue Reading] -

Businesses can safely delay patching most vulnerabilities
Publié: janvier 22, 2019, 3:50pm CET par Ian Barker
Patching vulnerabilities is often seen as a key element of keeping systems secure. But a new report suggests businesses could be 'smarter' in their patching regimes and prioritize the issues that present most risk. The study from Kenna Security suggests companies are increasingly recognizing that the majority of vulnerabilities are never weaponized or exploited in a cyberattack. The data shows that organizations patched a total of over two billion vulnerabilities of the three billion seen over the survey period, indicating that enterprises have the resources to address the vulnerabilities that pose the greatest risk. This can be accomplished by implementing… [Continue Reading] -

Cryptominers dominate 2018's malware landscape
Publié: janvier 22, 2019, 11:25am CET par Ian Barker
The four most prevalent malware types in 2018 were cryptominers and they impacted 37 percent of organizations globally. The latest security report from Check Point shows that despite a fall in the value of all cryptocurrencies, 20 percent of companies continue to be hit by cryptomining attacks every week. At the same time ransomware attacks have fallen sharply, impacting just four percent of organizations globally. Cryptominers have also evolved recently to exploit high profile vulnerabilities and to evade sandboxes and security products in order to expand their infection rates. Among the report's other findings are that 33 percent of organizations… [Continue Reading] -

Two-thirds of DDoS attacks target communications service providers
Publié: janvier 21, 2019, 3:12pm CET par Ian Barker
Communications service providers were targeted by 65.5 percent of DDoS attacks in the third quarter of 2018 according to a new report. The Q3 2018 Threat Report from Nexusguard shows attackers contaminated a diverse pool of IP addresses across hundreds of IP prefixes by using very small-sized junk traffic. "Perpetrators are using smaller, bit-and-piece methods to inject junk into legitimate traffic, causing attacks to bypass detection rather than sounding alarms with large, obvious attack spikes," says Juniman Kasman, chief technology officer for Nexusguard. "Diffused traffic can cause communications service providers to easily miss large-scale DDoS attacks in the making, which… [Continue Reading] -

Enterprise IT continues to move to the cloud
Publié: janvier 17, 2019, 3:26pm CET par Ian Barker
Cloud adoption in enterprises is already very high and growth is likely to continue in 2019 according to the latest cloud adoption survey from NetEnrich. The study of IT decision makers in businesses with 500 or more employees shows 85 percent of respondents report either moderate or extensive production use of cloud infrastructure, while 80 percent say their companies have moved at least a quarter of all their applications and workloads to the public cloud. In addition 86 percent of respondents have re-architected some or all of their applications to use cloud-native services. Benefits from these changes include a faster… [Continue Reading] -

Poor information management harms productivity
Publié: janvier 17, 2019, 1:08pm CET par Ian Barker
Poor information management processes are making jobs harder for staff and reducing their productivity and effectiveness in the workplace, according to new research from information management specialist M-Files Corporation. Navigating different systems and locations to find the correct version of a file they are looking for negatively affects productivity according to 82 percent of respondents. In addition, 91 percent of respondents say their job would be easier if they could quickly and easily access the most current version of a document, without having to worry about the system or repository in which it resides. The study also identifies a number… [Continue Reading] -

Compliance fears inhibit cloud adoption
Publié: janvier 16, 2019, 5:07pm CET par Ian Barker
According to a new survey, 88 percent of IT decision makers at mid- to large-sized companies think having to meet compliance standards in the cloud inhibits further cloud adoption within their company. The study from Wakefield Research and Logicworks, finds that among senior management -- those most close to and responsible for cloud execution and performance -- the figure is even higher, with 97 percent agreeing that compliance inhibits cloud adoption. Across companies of all sizes, 77 percent of IT decision makers think that they would not pass all of their compliance audits for cloud resources. This problem is compounded… [Continue Reading] -

MSSP program helps smaller businesses defend against phishing
Publié: janvier 16, 2019, 3:43pm CET par Ian Barker
Cybercriminals are increasingly recognizing that smaller businesses can be be lucrative targets as they are able to devote less resources to security. Phishing defense specialist Cofense is launching a new Managed Security Service Provider (MSSP) program aimed at providing SMBs with human-driven solutions designed to stop active phishing attacks. Cofense has partnered with a targeted group of service providers to provide their customers the dedicated resources required to strengthen defenses, build attack resiliency and ultimately stop real attacks in progress. "Phishing remains the top cause of security breaches, and when it comes to leveraging humans to help stop those threats… [Continue Reading] -

New Fortnite vulnerabilities put users' privacy at risk
Publié: janvier 16, 2019, 3:06pm CET par Ian Barker
Researchers at security firm Check Point have uncovered vulnerabilities in the popular online game Fortnite that would allow attackers to intercept and steal Fortnite users’ login credentials without them being aware of the theft. The attack manipulates Fortnite's login process to capture usernames and passwords. Armed with these details attackers could view any data stored in the game, buy more V-Bucks in-game currency at users' expense, and access all the user’s in-game contacts as well as listen in on and record conversations taking place during game play. To fall victim to this attack a player needs only to click on… [Continue Reading] -

Cryptominers still dominate the malware charts
Publié: janvier 14, 2019, 3:21pm CET par Ian Barker
The latest Global Threat Index from Check Point shows that at the end of last year cryptominers still took the top three places in the malware charts, despite an overall drop in value across all cryptocurrencies in 2018. Coinhive retained its number one position for the 13th month in a row, impacting 12 percent of organizations worldwide. XMRig was the second most prevalent malware with a global reach of eight percent, closely followed by the JSEcoin miner in third with a global impact of seven percent. The report also shows banking Trojans rising up the index, with Ramnit, a banking… [Continue Reading] -

Organizations suffer breaches despite confidence in their security measures
Publié: janvier 10, 2019, 2:57pm CET par Ian Barker
According to a new survey, 85 percent of respondents are either very or somewhat confident in their organization's security program, yet 41 percent say their company has experienced a security breach and 20 percent more are unsure. The study from big data specialist Syncsort finds the most common type of breaches are virus/malware attacks (76 percent) and phishing (72 percent). Interestingly, virus attacks came from internal sources roughly half the time while phishing usually came from external sources (78 percent). On a positive note, 50 percent of breaches were identified in less than a day, while 26 percent were identified… [Continue Reading] -

Video sensors, medical devices and security worries -- IoT predictions for 2019
Publié: décembre 21, 2018, 3:39pm CET par Ian Barker
More and more devices in our homes and workplaces are gaining smart capabilities as the Internet of Things starts to move from niche to mainstream. But greater adoption also means an expanded threat surface. So what can we expect to see from the IoT in 2019? We’ve rounded up the opinions of some industry experts. Manufacturers are increasingly turning to smart features to make their products stand out, says DH2i CEO and co-founder, Don Boxley. "Making smart products, IoT devices, is the new product differentiator -- even ovens have IP addresses now. Companies that have been investing in IoT initiatives understand… [Continue Reading] -

Faster innovation, increased competition and repatriation -- cloud predictions for 2019
Publié: décembre 20, 2018, 3:37pm CET par Ian Barker
Use of the cloud is now well established in many businesses. But that's not to say that it isn’t still a fast moving sector of the industry. With greater competition than ever and the pace of innovation showing little sign of slowing down, we’ve put together some expert views on what might be in store for cloud users in 2019 Competition between major public cloud providers is expected to increase according to Sanjay Beri, CEO of Netskope. "As the pace of digital innovation and demands pertaining to new cloud features, costs, geographic coverage, and support increases, the cloud wars between… [Continue Reading] -

IoT malware up over 200 percent in 2018
Publié: décembre 19, 2018, 4:01pm CET par Ian Barker
New malware targeting IoT devices grew 72 percent, with total malware growing 203 percent in the last four quarters according to McAfee's third quarter threat report. This growth has been partly due to devices being harnessed for cryptomining. IoT devices such as cameras or video recorders have not typically been used for this because they lack the CPU power of desktop and laptop computers. However, cybercriminals have taken notice of the growing volume and lax security of many IoT devices and have begun to focus on them, harnessing thousands of devices to create a mining super-computer. New coin-mining malware grew… [Continue Reading] -

One in three networks has exposed passwords
Publié: décembre 19, 2018, 3:10pm CET par Ian Barker
Passwords are exposed in Group Policy Preferences in 32.2 percent of networks, according to new research, leaving them open to the risk of hackers traveling laterally through the network. The study from identity and access specialist Preempt also shows organizations lack visibility and control when it comes to their passwords and privileged users. Almost 97 percent of inspected enterprises revealed at least one security issue between Active Directory issues and password policies, while 72.2 percent had 'stealthy admins' -- users with excessive administrative privileges that could be used or manipulated by malicious actors. "While cybersecurity spending is at all time… [Continue Reading] -

AI security solutions are popular with executives -- but are they really working?
Publié: décembre 19, 2018, 2:42pm CET par Ian Barker
According to a new study released by ProtectWise, AI has already established a strong foothold in the security space, with 73 percent of respondents reporting that they have implemented security solutions that incorporate at least some aspect of AI. Most organizations cite AI's ability to improve the efficiency of security staff members and make investigation of alerts faster as top priorities. But it's executives, not the people who manage security, who are the biggest advocates for AI. 55 percent of respondents say that the strongest advocates for AI-based security products in their organization are IT executives, while 38 percent say… [Continue Reading] -

Addressing the skills gap, cyber wars and a new wave of immersive intelligence -- AI predictions for 2019
Publié: décembre 18, 2018, 5:08pm CET par Ian Barker
Artificial intelligence has been 'the future' for quite a long time, but it seems that the potential of the technology is at last starting to have an impact on the real world. What do industry experts think will be the things we'll see from AI in 2019? We've put together some of their opinions below. Huw Owen, head of EMEA and APJ at Couchbase says, "The opportunities and need for artificial intelligence and machine learning are well understood: with projects such as IBM’s Watson already showing its potential. With this groundwork already in place, 2019 will be the year where… [Continue Reading] -

Shutterstock reveals the most searched celebs and events of 2018
Publié: décembre 18, 2018, 3:15pm CET par Ian Barker
The internet is a serious and valuable tool for research and commerce, but we all know it's mostly about cute kittens and celebrities. Photo service Shutterstock has been analyzing the search data from its site to reveal most searched for names around the world and has produced an infographic of the result. It's no surprise to see royal wedding couple Harry and Meghan (the Duke and Duchess of Sussex -- just in case there's an OBE in the post) top the list of search increases with a jump of a massive 6,550 percent, more than double that of second place… [Continue Reading] -

Artificial intelligence -- force for good or force for evil?
Publié: décembre 18, 2018, 12:14pm CET par Ian Barker
There are a lot of benefits to be gained from artificial intelligence, but its use also raises concerns over the impact it is likely to have on jobs, privacy and more. Enterprise AI specialist noodle.ai has produced an infographic looking at the positive and negative impacts of the technology. On the positive side AI is expected to create over two million jobs by 2020. It also has the potential to free up humans to undertake more fulfilling and creative tasks. Machine learning could help produce better medical treatments and driverless vehicles could cut the number of road accidents. The other… [Continue Reading] -

The beginning of the end for the password, more regulation and more IoT risks -- cybersecurity predictions for 2019
Publié: décembre 17, 2018, 5:18pm CET par Ian Barker
When we looked at security predictions at this time last year some experts were predicting that we'd see attacks on cryptocurrencies and that we'd continue to see a rise in the scale and profile of attacks. They've been proved right on both counts over the course of 2018, so what is next year going to have in store? We've canvassed the views of a number of industry figures to find out what they see as the key security issues for 2019. The end of the password The end of the password as a prime security measure is something people have… [Continue Reading] -

How to stop Windows 10 sharing your data
Publié: décembre 14, 2018, 11:55am CET par Ian Barker
Earlier this week we reported on how Windows 10 could be sharing your activity data even if you had told it not to. In response Microsoft has released a statement from Marisa Rogers, privacy officer at its Windows and Devices Group. Microsoft is committed to customer privacy, being transparent about the data we collect and use for your benefit, and we give you controls to manage your data. In this case, the same term 'Activity History' is used in both Windows 10 and the Microsoft Privacy Dashboard. Windows 10 Activity History data is only a subset of the data displayed… [Continue Reading] -

Education sector poorly prepared for cyberthreats
Publié: décembre 13, 2018, 3:37pm CET par Ian Barker
Data is a vital resource in the education sector and increasingly schools and colleges store information in digital form. Digital technology is also moving into the classroom, but of course all this comes with greater risk. Yet according to new research from security rating service SecurityScorecard, across 17 industries in the US education comes second to last in terms of total cybersecurity. According to the report education performs poorly in several key areas of cybersecurity. It also shows that hackers have become increasingly adept at stealing school and student data, but the education industry is no better prepared to deal… [Continue Reading] -

Email security systems leave organizations vulnerable
Publié: décembre 12, 2018, 4:05pm CET par Ian Barker
Email and data security company Mimecast has released the results of its latest Email Security Risk Assessment (ESRA) which finds that mail security systems inaccurately deemed nearly 17,000 dangerous files 'safe' this quarter. That represents a 25 percent increase over the previous quarter. Dangerous file types like jsp, .exe, .dll and .src are rarely emailed for legitimate purposes and can be used launch a cyberattack. The report also finds 21,183,014 spam emails, 17,403 malware attachments, 42,350 impersonation attacks and 205,363 malicious URLS, all missed by security providers and delivered to users' inboxes. This latest report concludes that an aggregate 12… [Continue Reading] -

60 percent of organizations have suffered disruptive cyber events in the last two years
Publié: décembre 12, 2018, 3:12pm CET par Ian Barker
A new study reveals that 60 percent of organizations globally have suffered two or more business-disrupting cyber events -- defined as cyberattacks causing data breaches or significant disruption and downtime to business operations, plant and operational equipment -- in the last 24 months. What's more the research, carried out by the Ponemon Institute for cyber risk specialist Tenable, shows 91 percent have suffered at least one such cyber event in the same time period. But despite this documented history of damaging attacks, the study finds that the majority of organizations (54 percent) are not measuring, and therefore don't fully understand,… [Continue Reading] -

2018's worst password fails revealed
Publié: décembre 12, 2018, 1:47pm CET par Ian Barker
Despite newer technologies, most of us still rely on passwords to secure our accounts. We are not, however, very good at choosing them or looking after them. Password management company Dashlane has produced a list of the 10 worst password fails of 2018. 1. Topping the list is Kanye West who was caught unlocking his iPhone with the passcode '000000' during his White House meeting with Donald Trump. 2. In second place is the US Department of Defense. An audit by the Government Accountability Office (GAO) found numerous cybersecurity vulnerabilities in several of the Pentagon's systems. Among the disturbing issues… [Continue Reading] -

Phishing improves in quality as major brands are targeted
Publié: décembre 12, 2018, 12:38pm CET par Ian Barker
It used to be easy to spot a phishing email, you just looked out for bad grammar and URLs that clearly didn't correspond to the organization being impersonated. Recently though they've become harder to detect. According to the latest Global Threat Report from Comodo Cybersecurity, phishing really is getting better and it now represents one in every 100 emails received by enterprises. The most frequently targeted brands by phishing in the third quarter of 2018 goes to Microsoft (19 percent), followed by PayPal (17 percent) and Google (9.7 percent). Top three phishing emails ranked by subject line over the same… [Continue Reading] -

Amplification bots used to raise the popularity and legitimacy of Twitter posts
Publié: décembre 11, 2018, 5:08pm CET par Ian Barker
Earlier this year we looked at Duo Security's research into Twitter bots which focused on fake followers. The company has now published some further research looking at amplification bots. So what is an amplification bot? They exist to boost content through likes and retweets. Duo has produced an algorithm to identify these bots and was able to find more than 7,000 over a 24 hour period. "These bots exist to spread content and disseminate it to more people, and to raise the credibility or the popularity of that content by spiking retweet numbers," Jordan Wright, principal R&D engineer at Duo says.… [Continue Reading] -

Enterprises turn to software solutions to manage endpoint devices
Publié: décembre 11, 2018, 4:20pm CET par Ian Barker
As businesses embrace digital transformation, things like the growth of distributed workforces and remote work are impacting both the day-to-day responsibilities and long-term plans of IT managers. Software and cloud managed services company Unify Square has commissioned a survey from Osterman Research to sample the views of IT managers who oversee unified communications (UC) and workstream collaboration (WSC) environments. The findings show that 43 percent of respondents anticipate the portion of their total UC budget dedicated to device management expenditures will grow over the next three years. "There's no question that the UC industry is experiencing a tectonic shift, driven by… [Continue Reading] -

Christmas tech gadgets increase household cyber risks
Publié: décembre 11, 2018, 1:26pm CET par Ian Barker
Many people will be receiving new tech gadgets over the Christmas period, including smartphones, gaming consoles, tablets, connected toys, and a whole range of apps to go with them. But new research from from cybersecurity training organization the SANS Institute finds that while people are aware of the risks these devices can pose, they may not have the skills to properly protect them. The study of 1000 parents and 1000 students aged 14-18 in the UK finds 72 percent of parents and 68 percent of students see the biggest cybersecurity risk to their family as the theft of their personal… [Continue Reading] -

Windows 10 sends activity history to Microsoft even when told not to
Publié: décembre 11, 2018, 12:17pm CET par Ian Barker
We all know that Windows 10 logs data about what you do on your PC. What you may not be aware of is that it still sends that information to Microsoft even if you have told it not to. Sneaky, huh? People on Reddit have been discussing the issue and finding that even if the option to send data to the cloud is turned off it still shows in the online Privacy Dashboard. You can check this for yourself. Go to Settings, Privacy, Activity History and uncheck Let Windows synchronise my activities from this PC to the cloud. You can… [Continue Reading] -

The benefits of a cloud-based testing regime [Q&A]
Publié: décembre 10, 2018, 11:26am CET par Ian Barker
DevOps teams are under constant pressure to release faster, improve quality and keep costs under control. This means testing increasingly becomes a priority to ensure accelerated releases and many companies are turning to cloud-based testing tools. However, as with any move to the cloud, there are some challenges that need to be overcome. We spoke to Uzi Eilon, chief technology officer at cloud-based testing platform Perfecto to find out more. BN: It seems like everyone is moving everything to the cloud. What are the benefits of cloud-based testing and what has caused the shift to cloud-native solutions? UE: It seems… [Continue Reading] -

How deception can provide an edge in fighting cyberattacks [Q&A]
Publié: décembre 7, 2018, 3:40pm CET par Ian Barker
Businesses are starting to recognize that it may be impossible to keep attackers completely out of their networks, so they are starting to look for ways of fighting them more efficiently. One of the ways of doing this is to use decoys to lure attackers and allow the threat to be dealt with before it affects live systems. We spoke to Carolyn Crandall, chief deception officer at Attivo Networks to find out more about how this deception technology works and what it can do. BN: How common is the use of deception technology? CC: Like Fight Club, the first rule… [Continue Reading] -

96 percent of employees struggle to locate files
Publié: décembre 6, 2018, 3:14pm CET par Ian Barker
According to a new report, 96 percent of all employees face some sort of difficulty when looking for the most recent version of a document or file. The study from information management company M-Files also reveals that 83 percent of staff worldwide are forced to recreate documents that already exist but can't be found. "Information and the speed at which it flows throughout an organization is a key determinant of business success," says Greg Milliken, senior vice president of marketing at M-Files. "The faster your staff can find and leverage information, the better your chances will be for achieving a… [Continue Reading] -

Oaxis Timepiece -- smart style meets smart tech
Publié: décembre 6, 2018, 12:18pm CET par Ian Barker
For many people wearing a watch is as much about how it looks as how it works. In these days of smart devices that often requires a trade off between style and function. Do you leave your good-looking watch at home while you wear your smart watch, or do you look a bit needy by putting a wearable fitness tracker or similar on your other wrist? With the Oaxis Timepiece you no longer have to make the choice. The Timepiece is a good-looking analogue watch with smart functions that include a fitness tracker, heart rate monitor and alerts for smartphone… [Continue Reading] -

69 percent of employees use work devices for personal tasks
Publié: décembre 5, 2018, 4:54pm CET par Ian Barker
New research released by security awareness and email protection company Mimecast finds that more than two-thirds of employees admit to personal use of work devices during office hours. Mimecast surveyed more than 1,000 people who use company-issued devices (such as mobile phones, desktop computers or laptops) in the workplace, in order to understand their behavior, but also their awareness of basic threats plaguing organizations. The top three personal uses are reading the news (53 percent), checking personal email (33 percent) and browsing social media (23 percent). Additionally, nearly 28 percent say they use their company-issued device for personal reasons for… [Continue Reading] -

Symantec launches neural network device to protect critical infrastructure
Publié: décembre 5, 2018, 3:20pm CET par Ian Barker
Operational technology is critical in areas like energy, oil and gas, manufacturing, and transportation, but it's often be based on legacy systems which can be difficult to keep secure, with updates often needing to be carried out using USB devices. The threat of attacks is very real though and the consequences especially disastrous, yet many control systems are running outdated software, leaving them vulnerable to attack. To combat these risks Symantec is launching its Industrial Control System Protection (ICSP) Neural, the industry's first neural network-integrated USB scanning station that helps organizations protect critical infrastructure by preventing the devastating physical consequences of… [Continue Reading] -

Latest malware tries to avoid detection and maintain persistence
Publié: décembre 5, 2018, 2:41pm CET par Ian Barker
Malware is constantly evolving in an attempt to steal data or make money for the people behind it. A new report by Malwarebytes Labs reveals the latest shift towards attacks that can avoid detection but also stay on a system to be reactivated later. Using fileless malware is just one example among many attack methodologies currently evading traditional security defenses and maintaining persistence. Among current threats from this new generation of malware are the banking trojan combined with a downloader and botnet known as Emotet, along with its commonly seen accomplice TrickBot. These threats primarily use email distribution with malicious… [Continue Reading] -

Popular VTech children's tablet can be easily controlled by hackers
Publié: décembre 5, 2018, 12:07pm CET par Ian Barker
Risk management and cybersecurity specialist SureCloud has discovered that the popular VTech Storio Max children's tablet can easily be hacked, enabling criminals to take control of the devices and snoop on unsuspecting victims. This can be done by simply adding an image or link to a website. When accessed by a child via the tablet's web browser, the exploit would attack the tablet and enable the attacker to take full control of the device. A feature of the VTech tablet is that only websites selected by parents can be accessed. Six child-friendly websites are allowed by default. However, at least… [Continue Reading] -

Fake ransomware 'cures' actually just pay the scammer
Publié: décembre 4, 2018, 3:15pm CET par Ian Barker
In an interesting new trend some companies are claiming to be able to unlock encrypted files following a ransomware attack, but are in fact simply acting as brokers between victims and attackers. Researchers at Check Point have discovered a Russian IT consultancy named Dr. Shifro that claims to unlock and recover consumers' and businesses' encrypted files. In fact, the company simply pays the ransomware's creator themselves and passes the cost onto the victim at a 75 percent-plus profit margin. So victim's files are decrypted, the cybercriminal gets a ransom payment and Dr. Shifro pockets a substantial fee. In one case… [Continue Reading] -

100 million Quora users data exposed in major breach
Publié: décembre 4, 2018, 12:18pm CET par Ian Barker
Question and answer site Quora has revealed that its user data has been compromised as a result of unauthorized access to its systems by a 'malicious third party'. The breach occurred on Friday and Quora is still investigating the causes. It has taken the step of logging out all users who may have been affected and forcing them to reset their passwords. It also says it will continue to make security improvements. It’s believed the leak may have exposed data from social networks like Facebook and Twitter if users chose to link these to their Quora accounts. Quora has more… [Continue Reading] -

Enterprises struggle to fill the cloud skills gap
Publié: décembre 3, 2018, 12:25pm CET par Ian Barker
According to a new study 94 percent of respondents find it at least 'somewhat difficult' to recruit candidates with the right technology and business skills for driving digital innovation. The report from AIOps platform company OpsRamp shows that over 60 percent of IT professionals say that a majority of their applications are either built or run using hybrid cloud architectures. This means organizations will need vastly different skills, technologies, and processes to run their infrastructure and operations over the next five years as they adopt a cloud-first posture. The report shows that 77 percent of enterprise IT teams are working… [Continue Reading] -

DDoS attacks on eCommerce reach their highest levels over the Black Friday weekend
Publié: novembre 30, 2018, 12:27pm CET par Ian Barker
Cybercriminals are just as keen to exploit the holiday shopping boom as anyone else, with DDoS attacks on eCommerce providers increasing by over 70 percent on Black Friday compared with other days in November. On Cyber Monday, attacks increased by 109 percent compared with the November average. Cloud anti-DDoS company Link11 has released data showing several attacks observed during Black Friday and Cyber Monday were of up to 100 Gbps bandwidth, and the average attack volume on both days was just under 6Gbps. Attack volumes approaching 6Gbps far exceed the capacity of most websites. Link11 is warning online merchants, payment… [Continue Reading] -

Americans most worried about attacks on the financial sector
Publié: novembre 29, 2018, 3:43pm CET par Ian Barker
Americans are more worried about a cyberattack disrupting the financial and banking system than attacks against hospital/emergency services, voting systems or power grid/energy supply companies. This is among the findings of a survey by ESET to mark National Critical Infrastructure Security and Resilience Month, which surveyed 1,500 Americans to discover their views on critical infrastructure attacks. It also finds that 58 percent of people say that they believe it is 'likely' that the US will suffer a large scale disruption on CI in the next two years and people are most worried about cyberattacks on the financial sector (26 percent)… [Continue Reading] -

Botnets disrupted in major anti-fraud operation
Publié: novembre 28, 2018, 3:02pm CET par Ian Barker
An anti-fraud operation led by the FBI has succeeded in disrupting a scam that has seen cybercriminals using botnets to manipulate internet traffic from 1.7 million IP addresses and generate nearly 30 million dollars in fraudulent ad revenue. The ad fraud ring, known as '3ve' had been operating for a number of years and built two different botnets by spreading Kovter and Boaxxe malware to individuals through spam emails and drive-by downloads. These have been used to manipulate internet traffic and direct it to ads run by the ring and sold to customers under the pretense that the traffic was… [Continue Reading] -

Internet traffic set to explode over the next five years
Publié: novembre 27, 2018, 4:03pm CET par Ian Barker
By 2022 more IP traffic will be created on global networks than in the entire 32 year life of the internet to date. This rather startling prediction comes from network infrastructure specialist Cisco which reckons that by 2022, 60 percent of the global population will be internet users. More than 28 billion devices and connections will be online, and video will make up 82 percent of all IP traffic. "The size and complexity of the internet continues to grow in ways that many could not have imagined. Since we first started the VNI Forecast in 2005, traffic has increased 56-fold,… [Continue Reading] -

Protecting the US voting infrastructure [Q&A]
Publié: novembre 27, 2018, 11:10am CET par Ian Barker
It's two years since international forces interfered with the security of the US elections. However, with the US midterm elections behind us and the presidential elections ahead, vulnerabilities in the country’s voting infrastructure still remain. Simply put, it's not hard to hack into US voting systems. Don't believe it? Just ask the 11-year old who hacked a replica of the Florida election website to change results in under 10 minutes. We might not have seen widespread cyberattacks on the day of the midterms, but as we saw multiple opportunities for hacking and disruption in the run up, the presidential elections… [Continue Reading] -

Cyberattacks set to spike over the Black Friday/Cyber Monday weekend
Publié: novembre 26, 2018, 3:36pm CET par Ian Barker
Businesses should expect to see a spike in potential cyberattacks starting with Black Friday and Cyber Monday and continuing throughout the holiday shopping season, according to a new report. The report from predictive security specialist Carbon Black shows that global organizations encountered a 57.5 percent increase in attempted cyberattacks during the 2017 holiday shopping season. "Based on existing precedent, we expect the same trend to continue, if not increase, during the 2018 holiday shopping season," says Tom Kellermann, Carbon Black's chief cybersecurity officer. "During the holiday season, there is often a ton of noise in the online world and attackers… [Continue Reading] -

BullGuard and NordVPN partner to boost consumer privacy
Publié: novembre 21, 2018, 4:01pm CET par Ian Barker
As more and more of us rely on mobile devices to access the internet, traditional endpoint security solutions don’t always provide the protection we need. Cybersecurity company BullGuard is partnering with VPN specilaist NordVPN to launch a new consumer anonymity solution. "Cybersecurity to date has focused heavily on traditional end-point security solutions and been primarily about keeping consumers and their devices safe from online threats. Cybercriminals now pose a threat to consumer privacy as well. In order to adequately protect consumers in today's cyberthreat landscape, security and privacy must be equally addressed," says BullGuard CEO, Paul Lipman. "Partnering with NordVPN allows… [Continue Reading] -

Amazon discloses names and addresses -- but doesn't disclose details
Publié: novembre 21, 2018, 12:49pm CET par Ian Barker
If you're an Amazon customer you may have received a rather strange email this morning. It states that the company has, "...inadvertently disclosed your name and email address due to a technical error." It then goes on to say, "The issue has been fixed. This is not a result of anything you have done, and there is no need for you to change your password or take any other action." None of which is terribly reassuring. Although it doesn't include the customer's name it doesn't look like a phishing attack as there is no link and no call to action.… [Continue Reading] -

European DDoS attack volumes more than double
Publié: novembre 20, 2018, 3:20pm CET par Ian Barker
In Europe DDoS attack volumes have increased sharply during the third quarter 2018 according to a new report. The report from DDoS protection specialist Link11 shows the average attack volume more than doubled in July, August and September, to 4.6 Gbps (up from 2.2 Gbps in Q2). Attacks are also becoming increasingly complex, with 59 percent of incidents using two or more vectors -- up from 46 percent in Q2. The highest-volume attack observed by Link11 in 2018 rose to 371 Gbps in Q3, an increase of 75 percent compared to the maximum of 212 Gbps observed in Q1. In… [Continue Reading] -

Almost a quarter of reported vulnerabilities have no known solution
Publié: novembre 19, 2018, 5:23pm CET par Ian Barker
The number of reported vulnerabilities in 2018 is seven percent down on the same period last year, according to a new report from Risk Based Security. It's not all good news though, as 24.9 percent of 2018's reported vulnerabilities currently have no known solution which is a reminder that, while patching is very important, it can't be relied on exclusively as a remedy. Vulnerabilities with a CVSSv2 score of 9.0+, often referred to as 'critical', accounted for 15.4 percent of all published vulnerabilities through the third quarter. Also, Risk Based Security's own VulnDB published 4,823 more vulnerabilities than CVE/NVD through… [Continue Reading] -

Businesses struggle with the rate of growth in API use
Publié: novembre 19, 2018, 3:21pm CET par Ian Barker
In the last few years APIs have become a critical enabler of digital transformation for businesses across all sectors. Cybersecurity company Ping Identity has surveyed more than 100 security and IT professionals to determine their concerns surrounding the increased use of APIs. Among the findings are that APIs are continuing to expand at a rapid rate, 25 percent of respondents say their company has over 1,000 APIs, while 35 percent report having between 400–1,000. This compares to a January 2018 survey found that companies manage 363 different APIs on average, with 39.2 percent managing between 400-1,000 APIs and 7.2 percent… [Continue Reading] -

70 percent of SMBs suffer cyberattacks
Publié: novembre 16, 2018, 3:41pm CET par Ian Barker
Cyberattacks are often thought of as being a problem just for large organizations. But a new study by the Ponemon Institute, sponsored by Keeper Security, shows that small businesses increasingly face the same cybersecurity risks as larger ones. The number of attacks is on the rise -- with 67 percent experiencing a cyberattack and 58 percent experiencing a data breach in the last 12 months. Yet nearly half of respondents (47 percent) say they have no understanding of how to protect their companies against cyberattacks. As SMBs become more vulnerable, the risk of employees and contractors causing a data breach… [Continue Reading] -

85 percent of companies permit BYOD but security remains a concern
Publié: novembre 16, 2018, 11:29am CET par Ian Barker
While a large majority of companies now permit employees to use their own devices for work, they have concerns over security and privacy. Organizations are making BYOD available to employees (76 percent), contractors (27 percent), partners (25 percent), customers (22 percent), and suppliers (19 percent). Security concerns are the main barrier to BYOD for 30 percent of respondents. Their main worry is data leakage, followed by unauthorized access to data and an inability to control uploads and downloads. The study from Bitglass shows 51 percent of respondents believe that the number of threats targeting mobile devices has increased in the… [Continue Reading] -

Phishing emails with .com payloads target finance departments
Publié: novembre 15, 2018, 5:19pm CET par Ian Barker
There has been an increase in the use of .com extensions in phishing emails that target financial service departments, according to a new analysis. In October alone, anti-phishing company Cofense Intelligence analyzed 132 unique samples with the .com extension, compared to only 34 samples analyzed in the nine months before. Four different malware families were utilized. The subject lines and email contents of the phishing emails suggest that the threat actor is specifically targeting financial service departments. The two most popular subject line themes use the terms 'payment' and 'purchase order' to tempt recipients to click. The messages have an… [Continue Reading] -

Zoho boosts its CRM capability with AI
Publié: novembre 15, 2018, 4:41pm CET par Ian Barker
Business software specialist Zoho is launching the latest version of its Zoho CRM Plus suite, an all-in-one customer experience package that enables sales, marketing, customer support, and operations teams to work as one. Using Zia, Zoho's intelligent assistant, and Zoho Analytics, the company's business intelligence and reporting engine, the package helps users to understand customer sentiments, provide better experiences across channels, and enable actions to keep customers content throughout their journey -- all from one place. "Companies now recognize the importance of AI in creating positive experiences for customers. The focus now has shifted to bringing AI across an integrated… [Continue Reading] -

91 percent see hybrid cloud as the ideal model
Publié: novembre 15, 2018, 4:10pm CET par Ian Barker
Enterprise cloud use is increasing, with with 91 percent naming hybrid cloud as the ideal IT model, yet only 18 percent say they have that model today. This is one of the findings of a new study by Nutanix to create the first of what is planned to be a global Enterprise Cloud Index, measuring enterprise plans for adopting private, hybrid and public clouds. The study carried out by Vanson Bourne also shows that application mobility across any cloud is a top priority for 97 percent of respondents -- with 88 percent of respondents saying it would 'solve a lot… [Continue Reading] -

New software capability helps manage third-party cyber risks
Publié: novembre 15, 2018, 3:34pm CET par Ian Barker
With digital transformation enabling supply chains to become ever more integrated, businesses no longer have to worry just about the risks posed by their own systems, they must consider those they are connected to as well. Vendor monitoring solution RiskRecon is launching a new tool that enables enterprises to automatically produce assessments and action plans based on their unique risk requirements, allowing risk professionals to easily understand and act on their third-party risk. Customers configure their risk appetite using a simple administration interface, selecting from a set of default policies or configuring their own policy. Customers can set their own… [Continue Reading] -

SnapLogic launches self-service machine learning platform
Publié: novembre 14, 2018, 5:04pm CET par Ian Barker
Increasing numbers of organizations are interested in the opportunities offered by machine learning, but their efforts are often hindered by a lack of data science talent. California-based SnapLogic is launching a new self-service solution to help break down the barriers to implementing machine learning. SnapLogic Data Science gives enterprises tools to rapidly build and deploy machine learning models from beginning to end. By democratizing end-to-end data science, organizations can achieve higher productivity through accelerated machine learning development using a visual, drag-and-drop interface. Enterprises can also achieve a lower total cost of ownership as they are able to decrease their production… [Continue Reading] -

IT pros believe data will be impossible to manage long term
Publié: novembre 14, 2018, 3:59pm CET par Ian Barker
A new survey of over 900 senior IT decision makers shows that 87 percent believe their organization's secondary data is fragmented across silos and is, or will become, nearly impossible to manage in the long-term. The survey, commissioned by Cohesity and conducted by Vanson Bourne, finds that that 86 percent of decision makers believe it's important to solve the challenges of mass data fragmentation. "IT leaders globally are wrestling with mass data fragmentation and the snowball effect caused by this critical infrastructure challenge," says Mohit Aron, CEO and founder of Cohesity. "Data silos create compute and management silos, and it… [Continue Reading] -

Misconfiguration and runtime security are top container worries
Publié: novembre 14, 2018, 3:15pm CET par Ian Barker
Container and Kubernetes security company StackRox has released a new report looking to understand how adoption of these technologies affects security concerns. The State of Container Security report finds that more than a third of organizations worry that their strategies don't adequately address container security. In addition 15 percent believe their strategies don't take seriously enough the threat to containers and Kubernetes deployments, and more than a third of respondents haven’t started or are just creating their security strategy plan. The main concern, cited by 54 percent of respondents, is risks driven by misconfigurations and accidental exposures. Also 44 percent, indicate that… [Continue Reading] -

Fighting mobile ad fraud with artificial intelligence
Publié: novembre 13, 2018, 5:03pm CET par Ian Barker
The mobile advertising market is massive, around $75 billion worldwide according to Forbes, and that makes it an attractive target for fraudsters. Fraud rates have almost doubled over the past year and companies are under increasing pressure to monitor data for clients, allowing them to identify and prevent the risk of fraud hurting campaign performance. To help tackle this problem mobile advertising specialist WeQ is launching a new SHIELD product to protect its mobile ad clients. Sven Lubek, Managing Director at WeQ, says, "WeQ SHIELD is based on AI technology, which unlike other manual or statically automated systems in the… [Continue Reading] -

New tool helps identify and block phishing attacks
Publié: novembre 13, 2018, 2:53pm CET par Ian Barker
People are often the weakest link in the IT security chain and hackers are keen to exploit this with ever more sophisticated attacks. Predictive email defense specialist Vade Secure is launching a new anti-phishing solution that helps security operations centers identify and block targeted phishing attacks. Called IsItPhishing Threat Detection, it uses machine learning algorithms to perform real-time analysis of around 50 features of the URL and page content. These models have been trained using Vade Secure's global threat intelligence gathered from 500 million mailboxes and 6 million daily URL scans. The number of features checked is optimized using an… [Continue Reading] -

Poor security habits made worse by the speed of digital transformation
Publié: novembre 13, 2018, 11:30am CET par Ian Barker
According to a new study, 75 percent of people admit to reusing passwords across accounts, including work and personal, compared to 56 percent who admitted to doing so in 2014. The Market Pulse Survey by identity management specialist SailPoint shows that digital transformation efforts are leading to increasingly complex IT environments for businesses and employees to manage securely. This has not only introduced more risk, but also a sense of frustration between the IT team trying to secure and enable the business and users who want to work more efficiently. Over half (55 percent) of survey respondents say their IT department can… [Continue Reading] -

Docker launches Windows Server application migration program
Publié: novembre 8, 2018, 4:26pm CET par Ian Barker
Containerization enables organizations to both modernize existing applications and adopt new technologies based on business requirements. But the process of migrating older systems can be daunting. Popular container platform Docker is addressing this with the launch of a new Windows Server application migration program. This is designed to allow businesses to migrate and modernize their legacy Windows Server applications in advance of the end-of-support deadline for Microsoft Windows Server 2008. It's made up of of Docker Enterprise 2.1, the latest release of the container platform, and a set of customized application migration services and tools. This helps companies containerize and… [Continue Reading] -

95 percent of IT security professionals underestimate phishing risks
Publié: novembre 8, 2018, 3:28pm CET par Ian Barker
A new survey of cybersecurity decision-makers shows that most companies lack adequate safeguards against phishing threats and many don't fully understand the risks or how widespread the threat is. The survey from phishing site detection company SlashNext reveals that 95 percent of respondents underestimate how frequently phishing is used at the start of attacks to successfully breach enterprise networks. Only five percent of respondents realize that phishing is the at the start of over 90 percent of successful breaches. In fact, phishing is one of the most used and most successful attack vectors, but despite multi-level security controls and phishing… [Continue Reading] -

Number of data breaches falls but 2018 is still set to be the second worst year on record
Publié: novembre 8, 2018, 1:17pm CET par Ian Barker
In the final quarter of 2018, the number of reported breaches is down by eight percent and the number of exposed records is down around 49 percent, from seven billion in 2017. The latest Data Breach QuickView report from Risk Based Security shows that seven breaches exposed 100 million or more records with the 10 largest breaches accounting for 84.5 percent of the records exposed this year to date. "The number of reported breaches shows some improvement compared to 2017 and the number of records exposed has dropped dramatically," says Inga Goddijn, executive vice president at Risk Based Security. "However,… [Continue Reading] -

Organizations find cloud costs higher than anticipated
Publié: novembre 7, 2018, 5:02pm CET par Ian Barker
Cloud adoption is high, with 78 percent using or planning to use cloud in the future, but most organizations lack a formal strategy to realize the full benefits and 62 percent report higher than anticipated costs. These are among the findings of a new survey by Syncsort that shows only 29 percent report having a centralized strategy and center of excellence in place to proactively plan and manage applications to the cloud, while 42 percent migrate applications on an ad-hoc basis. The cloud is still seen as having many benefits, led by business continuity (84 percent) and IT efficiency (68… [Continue Reading] -

Consumers are more ready to abandon brands following data breaches
Publié: novembre 7, 2018, 4:18pm CET par Ian Barker
According to a new study, 78 percent of people would stop engaging with a brand online and 36 percent would stop engaging altogether if the brand had experienced a data breach. The research by Ping Identity looks at consumer attitudes and behavior in the Post-Breach Era and reveals that people are more willing to make changes to the ways they interact with companies and secure their own personal data following a breach. Ping surveyed more than 3,000 people across the US, UK, France and Germany to find out what they expect from brands when it comes to the safekeeping of… [Continue Reading] -

Continuous authentication helps boost behavioral analytics
Publié: novembre 7, 2018, 3:22pm CET par Ian Barker
In a move to better protect accounts, banks, retailers and service providers are increasingly looking to methods of authentication beyond the password. Behavioral analytics specialist BehavioSec is launching an updated version of its platform, allowing it to detect the suspicious use of attack obfuscation techniques, including the use of VPNs and TOR-routed traffic during login attempts and sessions. It also adds Docker container support to simplify on-premise deployments and a real-time feed of more than 1.5 billion compromised devices, pushing anti-fraud defenses further out to identify attackers before they begin compromising accounts. "Our financial services, retail and other customers all… [Continue Reading] -

Enterprises face more than 100 critical vulnerabilities per day
Publié: novembre 7, 2018, 1:30pm CET par Ian Barker
Enterprises identify 870 unique vulnerabilities on their systems every day, on average. Of those, more than 100 are rated as critical on the common vulnerability scoring system (CVSS) according to a new report. The Vulnerability Intelligence Report from cyber risk company Tenable is based on analysis of anonymized data from 900,000 vulnerability assessments across 2,100 enterprises. It estimates that the industry is on track to disclose up to 19,000 new vulnerabilities in 2018, an increase of 27 percent over 2017. Yet in 2017, public exploits were available for only seven percent of all vulnerabilities, meaning that 93 percent of all… [Continue Reading] -

Consumers still reuse passwords despite knowing the risks
Publié: novembre 6, 2018, 1:38pm CET par Ian Barker
Despite almost half of US consumers (49 percent) believing their security habits make them vulnerable to information fraud or identity theft, 51 percent admit to reusing passwords and PINs across multiple accounts. According to a new fraud awareness survey by information destruction company Shred-it, 39 percent of consumers have been a victim of fraud or identity theft, and 27 percent admit that they don't know how to find out if they've become a victim. While 72 percent think they could determine if an email or phone call they receive is part of a fraudulent scam, 16 percent of consumers say… [Continue Reading] -

Pssst... Wanna buy a digital identity? Only $50
Publié: novembre 5, 2018, 5:02pm CET par Ian Barker
Ever wondered how much your life might be worth? If we're talking about the digital world then the answer might be, 'not very much.' Cybercriminals could sell your complete digital life, including social media accounts, banking details, app data, gaming accounts, and even remote access to servers or desktops, for as little as $50. A new study from Kaspersky Lab has studied dark web markets to determine how much money cybercriminals can make by selling consumers' personal data online. It finds that for under $50, criminals can sell a person's complete digital life on the dark web, including data from breached… [Continue Reading] -

A new approach to data protection at the edge [Q&A]
Publié: novembre 5, 2018, 11:24am CET par Ian Barker
Given the increase in both frequency and complexity of cyberattacks today, it's no surprise that security is coming to the forefront across industries. While people often view cybersecurity as hackers trying to steal data, threats can impact more than just traditional data loss. With new technologies like edge computing emerging, we need to start thinking about protecting physical infrastructure in addition to data at the edge. But is connecting devices at the edge even less secure in the first place? We spoke with Jason Andersen, VP of business line management for Stratus Technologies, to discuss the ways that edge computing… [Continue Reading] -

Microsoft and Amazon most impersonated in email attacks
Publié: novembre 1, 2018, 6:07pm CET par Ian Barker
Nearly two-thirds of all advanced email attacks used emails impersonating Microsoft or Amazon, according to new research by Agari, the email protection specialist. Microsoft was impersonated in 36 percent of all display name impersonation attacks in the third quarter. Amazon was the second most commonly impersonated company, used in 27 percent of these attacks. The pattern differs for high-value targets, such as C-suite executives though, Microsoft was impersonated in 71 percent of these attacks. Dropbox is a distant second at seven percent, followed by United Parcel Service (UPS) at six percent. These attacks often take the form of service updates,… [Continue Reading] -

New monitoring tool checks the dark web for stolen credentials
Publié: novembre 1, 2018, 3:57pm CET par Ian Barker
Stolen login details are highly prized by cybercriminals, whether they are used to penetrate corporate networks or to make extortion emails look more convincing. But often breached companies are slow to let users know their credentials have been stolen. This has begun to change in Europe thanks to GDPR, but in the US there is, as yet, no federal law regulating what companies must do if their users' information is stolen or compromised. Password manager company Keeper Security is helping users know when their password may have been exposed with the launch of BreachWatch, a monitoring product that scours the… [Continue Reading] -

Cyberattacks on energy and utility companies increase
Publié: novembre 1, 2018, 3:25pm CET par Ian Barker
Attacks on infrastructure and energy companies are increasing, but they are occurring inside enterprise IT networks, not directly in the critical infrastructure, according to a new report. AI powered attack detection specialist Vectra finds attackers typically gain a foothold in energy and utilities networks by staging malware and spear-phishing to steal administrative credentials. Once inside, they use administrative connections and protocols to perform reconnaissance and spread laterally in search of confidential data about industrial control systems. "The utility and energy industry heavily focuses on security critical infrastructure," Chris Morales, head of security analytics at Vectra says. "Which means making sure… [Continue Reading] -

Machine learning solution helps protect critical data
Publié: novembre 1, 2018, 1:15pm CET par Ian Barker
One of the problems that businesses can have protecting sensitive data is the task of actually locating it in the first place. Data protection specialist TITUS is launching a new Intelligent Protection solution that offers businesses a model based on their specific data protection needs while using machine learning to provide additional consistency and accuracy to data protection initiatives. TITUS Intelligent Protection enables users to train their solutions to add an element of automation to the identification and classification of documents and emails. This blend of rule-based and automatic or suggested classification means businesses can benefit from the efficiencies of… [Continue Reading] -

Sextortion is back and this time it looks personal
Publié: octobre 31, 2018, 4:58pm CET par Ian Barker
Over the last few weeks you may well have received an email that quotes an old password you once used. It tells you that your account has been hacked, that malware has been placed on your machine to capture data and that you’ve been recorded watching porn. It then demands that you cough up some Bitcoin -- amounts vary -- to prevent this webcam video from being made public on your social networks. It is, of course, a classic sextortion scam. There is no malware and no video, they just want to scare you into thinking there is in the… [Continue Reading] -

Comodo launches enhanced solution to secure internet access
Publié: octobre 31, 2018, 3:11pm CET par Ian Barker
Businesses need to protect themselves against harmful websites, but recognizing which are dangerous and which are not can be a tricky task. Cyber defense company Comodo is launching a new version of its cloud-delivered, DNS-based Security-as-a-Service (SaaS) solution that allows enterprises, medium-sized and small businesses, MSPs and channel partners to protect users’ digital presence. Comodo Dome Shield Platinum implements a highly configurable web filter to check the content and reputation of sites against company IT policy based on both safety and appropriateness. It protects against threats like phishing, bots and botnets, command-and-control servers, spyware and spam. The latest Platinum version… [Continue Reading] -

Misconfigurations put enterprise cloud data at risk
Publié: octobre 31, 2018, 11:37am CET par Ian Barker
While organizations are increasingly using the public cloud to create new digital experiences for their customers, the average enterprise experiences more than 2,200 misconfiguration incidents per month in their infrastructure-as-a-service (IaaS) and platform-as-a-service (PaaS) instances. This is among the findings of McAfee's latest Cloud Adoption and Risk Report which also finds that 21 percent of data in the cloud can now be classed as 'sensitive', putting the business at risk if it's stolen or leaked. Enterprise organizations have an average of 14 misconfigured IaaS/PaaS instances running at one time, and 5.5 percent of AWS S3 buckets have world read permissions,… [Continue Reading] -

Boards have wider cyber security awareness but still struggle to manage risks
Publié: octobre 30, 2018, 5:52pm CET par Ian Barker
Risk management specialist Focal Point Data Risk, has released its latest Cyber Balance Sheet Report showing that wider awareness of risks -- including third-party data breaches, ransomware and geopolitical conflicts -- spurs more security dialogue in the boardroom. However, C-Suite and security leaders still struggle to frame risk in productive decision-making terms and keep an eye on whether companies are operating within an acceptable level of risk. "This year's Cyber Balance Sheet Report dispels the 'cyber is not a boardroom issue' cliché by showing that not only have board members already received the cyber risk message loud and clear, they… [Continue Reading] -

New platform helps enterprises manage third-party cyber risks
Publié: octobre 30, 2018, 4:35pm CET par Ian Barker
Moving to digital transformation means that companies frequently have a host of vendors, suppliers, providers, and subsidiaries, all connected to their network or data and each with the potential to publicly expose customer information, intellectual property, or heavily regulated data. Without continuous insight into these other networks third-party risks can be hard to assess, leaving businesses open to the possibility of data breaches. Intelligence-driven security company LookingGlass is launching a new subscription-based monitoring service. This uses threat data along with a team of expert security and intelligence analysts to mitigate risks and provide continuous visibility into potential exposure. "When it… [Continue Reading] -

Non-Microsoft exploits on the rise as hackers turn to servers
Publié: octobre 30, 2018, 3:19pm CET par Ian Barker
A new report from AlienVault, based on findings from vendors' threat reports in its Open Threat Exchange (OTX) platform, reveals more non-Microsoft exploits are in the top 10 list this year. This is largely due to a rise of server attacks, particularly cryptocurrency-mining botnets that use remote exploits, such as Drupal. The report also sees an IoT exploit make the list for the first time. On a positive note, the OTX Trends Report shows an encouraging uptick in information sharing across the InfoSec industry, including a lot of independent research sharing on Twitter. OTX itself now has more than 100,000… [Continue Reading] -

Major companies' two-factor authentication offerings fall short
Publié: octobre 30, 2018, 1:14pm CET par Ian Barker
With passwords increasingly being seen as insufficient to properly secure access to websites, more and more companies are turning to two-factor authentication. New research from digital identity management experts Dashlane looks at how some of the biggest consumer websites are protecting their users. It looks at 17 of the UK’s most popular sites and finds only four get top marks for their 2FA offerings. Researchers tested each website on three 2FA criteria, awarding one point for SMS or email authentication, one point for software tokens, and three points for hardware tokens, such as YubiKey or U2F authentication, for a maximum… [Continue Reading] -

Could your brain be a target for hackers?
Publié: octobre 29, 2018, 4:43pm CET par Ian Barker
Implanted brain stimulation devices are used by scientists to explore how memories are created in the brain. New research shows that vulnerabilities mean they could be be targeted in future to steal personal information, alter or erase memories or cause physical harm. Sound like science fiction? Researchers from Kaspersky Lab and the University of Oxford Functional Neurosurgery Group have used practical and theoretical analysis to explore the very real vulnerabilities that could exist in implanted devices used for deep brain stimulation. Known as Implantable Pulse Generators (IPGs) or neurostimulators, these devices send electrical impulses to specific targets in the brain… [Continue Reading] -

Analysis of British Airways breach uncovers sophisticated techniques
Publié: octobre 29, 2018, 1:05pm CET par Ian Barker
The British Airways breach earlier this year affected around 380,000 customers and resulted in the theft of data including personal and financial details. The threat research team at Securonix has taken an in-depth look at the breach and the Magecart threat actor behind it, to uncover how it was carried out and offer tips to mitigate and prevent future attacks. The card skimming campaign used against BA has hit several other major victims this year, including the Ticketmaster and Newegg breaches. It works by installing malicious customized JavaScript on the victim's website. This can be done directly by compromising the… [Continue Reading] -

The role of the mainframe in digital transformation [Q&A]
Publié: octobre 26, 2018, 11:20am CEST par Ian Barker
When many enterprises think of mainframes, they think of reliable, workhorse technology and legacy applications. Mobile, windows-based applications are rarely top of mind. However, mainframes still power much of today's digital economy, from mobile banking to online ticket reservations, and still have a place in the enterprise IT stack. We spoke to Steve Hassett, chief operating officer at mainframe integration specialist GT Software, to find out why some enterprises incorrectly assume mainframes are yesterday's technology and why, for many, mainframe integration is so hard. We also asked Steve about how progressive organizations are leveraging their mainframe investment to unlock new… [Continue Reading] -

Majority of CISOs believe security breaches are inevitable
Publié: octobre 25, 2018, 5:40pm CEST par Ian Barker
According to research from Kaspersky Lab, 86 percent of CISOs believe that breaches are inevitable, but too many are stuck in a vicious circle of risk. Financially motivated criminal gangs (40 percent) and malicious insider attacks (29 percent) are the biggest risks to their businesses, and these are the threats that are extremely difficult to prevent, either because they are launched by 'professional' cybercriminals or because they are assisted by employees who are expected to be on the right side. More than half (56 percent) of CISOs are expecting their budgets to increase in the future, though 38 percent of… [Continue Reading] -

Identity and access management a major concern for cloud deployments
Publié: octobre 25, 2018, 3:43pm CEST par Ian Barker
According to a new report, 71.5 percent of violations on AWS occur around identity and access management (IAM). The study from cloud security company Netskope analyzed the Center for Internet Security's Benchmarks for AWS. Many of the IAM violations found involve instance rules, role-based access controls, and access to resources or password policy requirements -- things that enterprises can easily address even without an external security solution. Additional benchmark violations were found in monitoring (19 percent), networking (5.9 percent) and logging (3.6 percent). Looking at data loss prevention (DLP) violations, uploads make up the majority with 55.3 percent, followed by… [Continue Reading] -

Interest in Kodi declines following introduction of anti-piracy measures
Publié: octobre 25, 2018, 12:21pm CEST par Ian Barker
The Kodi Media Center has developed something of a reputation as a platform for pirated content. Although the Kodi Foundation has tried to distance itself from this, it seems other measures are having an effect. The anti-piracy coalition, Alliance for Creativity and Entertainment (ACE), along with new anti-piracy rules in the EU and UK, plus bans on Kodi boxes being sold via online marketplaces, has seen interest in Kodi decline sharply. New research from technology site Comparitech analyzing Google Trends data shows that interest in 'Kodi' as a search term has fallen over 80 percent from 2017 to 2018. There are… [Continue Reading] -

Early adopters delay IoT purchases over security concerns
Publié: octobre 24, 2018, 3:58pm CEST par Ian Barker
While people are still excited about Internet of Things technology, many are delaying buying over concerns about privacy and security. A new survey from cyber security company F-Secure shows that 63 percent of early adopters are looking to purchase new devices, but 50 percent have delayed an IoT purchase because of security concerns. Almost two thirds (63 percent) of UK early adopters are also worried that new internet connected devices, such as wearables and connected home appliances, could lead to a violation of their privacy. Awareness of cyber threats has increased considerably over the past three years: 62 percent of… [Continue Reading] -

Consumers will stop spending with businesses after a breach
Publié: octobre 24, 2018, 3:15pm CEST par Ian Barker
New research finds that that 83 percent of consumers will stop spending with a business for several months in the immediate aftermath of a security breach or a hack. More than a fifth (21 percent) will never return to a brand or a business post-breach, representing a significant loss of revenue, according to the study from secure payments provider PCI Pal. Even being perceived as having lax security practices can be enough to incur spending penalties -- almost half (45 percent) of those surveyed report that they spend less with brands they perceive to have insecure data practices, while over… [Continue Reading] -

Web applications leave companies vulnerable to breaches
Publié: octobre 24, 2018, 12:15pm CEST par Ian Barker
Insecure and outdated web applications are a core source of high-profile data breaches among FT 500 global companies according to new research from web security company High-Tech Bridge. The study reveals that abandoned, shadow and legacy web applications more or less nullify corporate cybersecurity spending and undermine compliance. The research took the 1,000 largest global companies as per the Financial Times: FT US 500 and FT Europe 500 and High-Tech Bridge performed a large-scale discovery and non-intrusive assessment of their external web and mobile applications, SSL certificates, web software and unprotected cloud storage. It found that the 500 largest US… [Continue Reading] -

Want to find the biggest cloud security threat? Look in the mirror [Q&A]
Publié: octobre 24, 2018, 11:11am CEST par Ian Barker
It seems not a day goes by without a new cloud data breach making headlines. And though the victims change, the attack details remain the same. Why do organizations keep repeating the same cloud security mistakes? And how can we break free from this vicious cycle? We spoke to Zach Malone, security engineer at security management specialist FireMon, who discusses these issues and tells us why, to identify the biggest threat to cloud security, we need to look in the mirror. BN: What is the most common cause of cloud breaches? ZM: The vast majority of all the known cloud… [Continue Reading] -

Mac@IBM code goes open source
Publié: octobre 23, 2018, 5:22pm CEST par Ian Barker
During his keynote speech today at the Jamf User Nation Conference in Minneapolis, IBM CIO Fletcher Previn announced that IBM is going to open source its Mac@IBM code. Designed to streamline the integration of corporate-owned or BYOD Apple Mac devices and applications into the enterprise while delivering a personalized experience, Mac@IBM has seen the number of IBMers using Macs increase from 30,000 in 2015 to 134,000 in 2018. The program has led with design and placed the user first, reflecting IBM's belief that IT is a driver of culture change and leads to engaged employees. The lessons learned from the… [Continue Reading] -

Thycotic launches free security toolkit for the higher education sector
Publié: octobre 23, 2018, 4:30pm CEST par Ian Barker
Universities and colleges are uniquely attractive to cyber criminals, because a constantly changing population and the use of large numbers of BYOD machines means lots of potential vulnerabilities. Privileged access management specialist Thycotic is releasing a free Cyber Security Toolkit for College Students and Families, aimed at providing an essential guide to help schools build an understanding of cyber best practices throughout their entire community. Made up of ready-made, easily digested and shareable resources, the toolkit helps education providers address concerns students and families have about the security of the information provided to and collected by their school, while also… [Continue Reading] -

How to spot a fake Twitter follower
Publié: octobre 23, 2018, 3:52pm CEST par Ian Barker
Earlier this year we covered some research from Duo Security published into the activities of Twitter bots. The company has now followed this with a look at how fake Twitter followers operate. Traditional fake followers are challenging to detect on an individual level since they have very little (if any) activity other than following other accounts. However, because fakes operate in groups created by the same bot owner they do tend to share characteristics. Fake followers are used to trick victims into believing spoofed accounts are legitimate. In order to bypass detection though the fakes need to look legitimate too.… [Continue Reading] -

Industrial control systems offer a soft target for attackers
Publié: octobre 23, 2018, 3:11pm CEST par Ian Barker
Security gaps in key areas such as plain-text passwords, direct connections to the internet, and weak anti-virus protections are leaving industrial control systems vulnerable to attack according to a new report. The study from ICS security company CyberX also shows that although the use of Windows XP has declined over the last year there are still older, unpatchable, Windows systems in slightly more than half of all industrial sites. The CyberX report is based on analyzing real-world traffic from production ICS networks, making it an accurate representation of the current state of ICS security. The report is based on data… [Continue Reading] -

Password Check Required Immediately -- and more of 2018's most successful phishing subject lines
Publié: octobre 23, 2018, 12:58pm CEST par Ian Barker
Which subject lines make a person most likely to click a link in a phishing email? Security awareness training company KnowBe4 has analyzed data from simulated phishing tests and 'in the wild' emails to find out. The most successful lines play on user's desire to remain secure with subjects relating to password checks the most clicked. On social media, messages about tagging or new profile views are most likely to be clicked. "Hackers are leveraging an individual's desire to remain security minded or well informed by playing into his/her psyche," says Perry Carpenter, chief evangelist and strategy officer, KnowBe4. "They… [Continue Reading] -

Free tool allows Office 365 users to test their email threat detection
Publié: octobre 22, 2018, 3:07pm CEST par Ian Barker
Email is still one of the most common ways for attackers to target individuals or businesses, whether it’s through phishing attacks or delivering malware. Although you may have protection measures in place it can be hard to know if they’re working effectively. Intelligence-led security company FireEye is launching a new capability that allows organizations to evaluate email threat detection efficacy with a no-charge evaluation service FireProof Email Threat Analysis is designed to help organizations easily discover how they can better protect themselves against email-based threats. The evaluation is free, with no software or hardware to install, and no email delivery… [Continue Reading] -

The life of an ethical hacker [Q&A]
Publié: octobre 19, 2018, 3:54pm CEST par Ian Barker
We often hear the term 'ethical hacker', but what exactly does this involve and is it something you can actually make a career out of? We spoke to Jim O'Gorman president of online penetration testing training provider Offensive Security to find out what being an ethical hacker is all about and what skills you need if you want to become one. BN: How would you define an ethical hacker? JO: I think the best definition would be someone that will not cause any harm based on their hacking activities, and is taking the actions with the approval of all proper parties.… [Continue Reading] -

OpsRamp brings AI and machine learning to IT operations
Publié: octobre 18, 2018, 4:26pm CEST par Ian Barker
IT operations is an area that often involves analyzing and reacting to a series of events and that makes it a strong candidate for automation. Operations platform specialist OpsRamp has recognized this with the launch of OpsQ, an intelligent event management, alert correlation, and remediation solution for hybrid enterprises. Using OpsQ IT operations teams can optimize and automate routine tasks with context and insight to aid understanding the business impact of an IT issue and ensure rapid service restoration. OpsQ introduces powerful machine learning models that learn how frequently specific alert sequences occur and recognize events related to the same cause.… [Continue Reading] -

Enterprise security teams struggle to balance budgets against demands
Publié: octobre 18, 2018, 3:26pm CEST par Ian Barker
Businesses are increasingly moving more of their operations to the cloud and this leads to a greater focus on securing these workloads. Cloud infrastructure security company Threat Stack has released a new report created by Vanson Bourne which shows 54 percent of businesses are worried that they will soon outgrow their security solutions. Budgets are expected to increase by 19 percent over the next two years, but organizations are struggling with a disconnect between security and DevOps and are facing difficulties in determining where to allocate this budget in the face of rapidly evolving infrastructure. A common complaint within organizations… [Continue Reading] -

New AI tool helps streamline outsourcing of mundane tasks
Publié: octobre 18, 2018, 1:30pm CEST par Ian Barker
In many organizations, time and productivity is lost by staff by working on repetitive tasks that would be better suited for outsourcing, rather than focusing on the knowledge-based work that they are employed to do. This is a problem that shouldn't be underestimated, Harvard Business Review reckons that knowledge workers spend up to 41 percent of their time on tasks that could be competently carried out by others. To address this issue and help make outsourcing tasks easier, New York-based company Invisible has built an artificially intelligent bot, which it calls a Digital Assembly Line. Users can email, call, or text… [Continue Reading] -

Webroot launches VPN to protect Wi-Fi users
Publié: octobre 17, 2018, 4:07pm CEST par Ian Barker
Many people rely on connecting to Wi-Fi networks when they are out and about, but using public hotspots does present a significant security risk. The best way to protect yourself is to use a VPN and cybersecurity company Webroot is launching its own in the form of Webroot WiFi Security, to provide security and privacy for users who connect to WiFi networks using Windows, Mac, and Android operating systems. Webroot WiFi Security is specifically designed to protect consumers from malicious threats that could steal financial and personal information, passwords, or infect a device with malware. In addition it provides anonymity… [Continue Reading] -

Cybersecurity faces a worldwide shortage of almost 3 million staff
Publié: octobre 17, 2018, 3:17pm CEST par Ian Barker
New research from (ISC)² -- the world's largest non-profit association of cybersecurity professionals -- reveals a worldwide skills gap of 2.9 million. The Asia-Pacific region is experiencing the highest shortage, at 2.14 million, in part thanks to its growing economies and new cybersecurity and data privacy legislation being enacted throughout the region. North America has the next highest gap at 498,000, while EMEA and Latin America contribute 142,000 and 136,000 to the staffing shortfall, respectively. The findings show 63 percent of respondents reporting that their organizations have a shortage of IT staff dedicated to cybersecurity. This is cause for concern… [Continue Reading] -

Financial firms not keeping up with electronic communication risks
Publié: octobre 17, 2018, 12:53pm CEST par Ian Barker
In a world of evolving technologies and shifting demographics within the workforce, and within firms' customer bases, organizations need to rethink their approach to the adoption and oversight of electronic communications. But a new study from data archiving specialist Smarsh shows that financial organizations are not keeping pace with their retention and supervision efforts -- particularly with a growing, younger workforce that relies on expanding, mobile-friendly channels, such as social media and text messaging. While email remains the main method of electronic communication, social and mobile platforms are playing an increasingly important role in how firms, and investors, conduct business.… [Continue Reading] -

Big businesses take the lead in machine learning
Publié: octobre 16, 2018, 4:25pm CEST par Ian Barker
Data science and machine learning professionals within larger organizations are feeling significantly more satisfied with their progress than those in smaller organizations, according to a new study. The report from machine learning specialist Algorithmia shows that those in organizations with 2,500+ employees are 80 percent more likely to be 'satisfied' or 'very satisfied' with their progress as compared to professionals in companies of 500 employees or less. Among other key findings are that 92 percent of respondents in companies with 10,000 employees or more say their organization's investment in machine learning has grown by at least 25 percent in the… [Continue Reading] -

Complexity is an obstacle to effective security tools
Publié: octobre 16, 2018, 3:36pm CEST par Ian Barker
Although IT operations personnel often help influence the selection of cyber security tools, nearly two out of three say complexity is one of the biggest hindrances in their effectiveness. The study by privileged access management company Thycotic shows complexity in deployment is cited by30 percent and complexity in daily use by 34 percent. "Security tools that are complex to deploy and difficult to use on a daily basis can negatively impact the tool's effectiveness," says Joseph Carson, chief security scientist at Thycotic. "If IT Ops does not adopt and even embrace a security tool, it risks becoming a waste of… [Continue Reading] -

Digital transformation increases risk of cyberattacks
Publié: octobre 16, 2018, 2:55pm CEST par Ian Barker
The drive to digital transformation is exposing companies to higher and more costly cyber risks according to a new study of over 1,300 businesses. The study from research firm ESI ThoughtLab, together with a cross-industry coalition of organizations, including HP, KnowBe4, Opus and others, shows that cyber risks rise dramatically as companies embrace new technologies, adopt open platforms, and tap into the ecosystems of partners and suppliers. While firms now report the biggest impacts as being from malware (81 percent), phishing (64 percent), and ransomware (63 percent), in two years they expect massive growth in attacks through partners, customers and… [Continue Reading] -

Enterprises still face roadblocks to using analytics
Publié: octobre 15, 2018, 4:23pm CEST par Ian Barker
Business and IT decision makers are becoming increasingly frustrated by the complexity, bottlenecks and uncertainty of today's enterprise analytics, according to a survey of senior leaders at enterprise-sized organizations from around the world. The study by research firm Vanson Bourne for data intelligence company Teradata finds significant roadblocks for enterprises looking to use intelligence across the organization. Among key findings are that 74 percent of senior leaders say their organization's analytics technology is complex, with 42 percent of those saying analytics is not easy for their employees to use and understand. What's more 53 percent say that their organization is actually… [Continue Reading] -

New technology helps businesses to assess cyber risks
Publié: octobre 15, 2018, 3:38pm CEST par Ian Barker
In a world of digital transformation projects that increasingly mean more links to suppliers and partners, it can be hard for companies to assess the risk presented by opening up their data to third-parties. To address this problem RiskRecon is launching new asset valuation algorithms that automatically determine the inherent risk value of any internet facing system. "Risk professionals spend too much time analyzing mountains of issues to determine the risk relevance," says Kelly White, co-founder and CEO of RiskRecon. "RiskRecon automatically contextualizes every issue with issue severity and asset value that enables professionals to easily identify risk priorities and needed action." RiskRecon… [Continue Reading] -

Cyberattacks shift their focus onto business in third quarter
Publié: octobre 15, 2018, 3:00pm CEST par Ian Barker
After a relatively quiet first half of the year, cyberattacks have come back with a bang in the third quarter according to the latest report from Malwarebytes. Businesses seem to have become the main focus of attacks, experiencing more cybercriminal activity this quarter, with detections up by 55 percent, while consumer detections increased by only four percent over the last quarter. Trojans are making a comeback too, rising 86 percent from the last quarter. Trojans were the number one detection for both businesses and consumers, due in part to the active and widespread Emotet campaign. Ransomware has also picked up… [Continue Reading] -

UK government launches guidance to help secure IoT devices
Publié: octobre 15, 2018, 12:57pm CEST par Ian Barker
There are expected to be more than 420 million internet connected devices in use across the UK within the next three years and if poorly secured these can leave people exposed to security issues and even large scale cyberattacks. To address this, a new voluntary Code of Practice is being launched by the UK government to help manufacturers boost the security of internet-connected devices such as smartwatches, virtual assistants and toys. Minister for Digital, Margot James, says From smartwatches to children's toys, internet-connected devices have positively impacted our lives but it is crucial they have the best possible security to… [Continue Reading] -

Businesses risk penalties by not wiping data from old equipment
Publié: octobre 12, 2018, 3:22pm CEST par Ian Barker
New research from IT procurement company Probrand shows that 68 percent of UK businesses have failed to wipe the data from IT equipment before disposal, leaving them open to fines under GDPR if data is exposed. In addition 70 percent admit to not having an official process or protocol for disposing of obsolete IT equipment. What's more, even four months after GDPR came into effect, 66 percent of workers admit they wouldn't know who to approach in their company in order to correctly dispose of old or unusable equipment. Matt Royle, marketing director at Probrand says: Given the amount of… [Continue Reading] -

Should businesses prepare for ransomware with a cryptocurrency stash? [Q&A]
Publié: octobre 12, 2018, 11:56am CEST par Ian Barker
An increasing number of enterprises are considering pre-purchasing cryptocurrency in anticipation of potential ransomware attacks. But is this a valid risk-reduction strategy for enterprises? To get some views on this controversial issue, we spoke with Mike Doran, senior security consultant with the enterprise incident management team at cybersecurity specialist Optiv, and former computer forensics examiner with the St. Louis Metropolitan Police Department. BN: Explain to us what you're seeing out in the real world relative to enterprises and cryptocurrency. MD: Ransomware has become so prevalent that it has become a standard part of the tabletop exercises we do with clients… [Continue Reading] -

Two out of three worry about identity theft but half still engage in risky behavior
Publié: octobre 11, 2018, 4:00pm CEST par Ian Barker
A new survey from identity management specialist SailPoint in conjunction with US National Cybersecurity Awareness Month finds two out of three professionals are extremely concerned about their personal identity being stolen. Yet despite this half admit that they would participate in the types of risky behavior that increase the threat of leaked information and a potential breach. Poor security habits include repeating personal login credentials across work accounts (22 percent), allowing someone else to use their office badge if they asked (19 percent), and snooping on a co-worker's salary if they were mistakenly given access to a file containing that… [Continue Reading] -

94 percent of big-business leaders would consider moving off mainframes
Publié: octobre 11, 2018, 3:27pm CEST par Ian Barker
A new survey of senior IT decision makers at some of the world's largest organizations that still rely on legacy mainframe systems reveals that most want to move away from the technology due to the high cost and inflexibility that it has brought to their business. The study from Microsoft and LzLabs surveyed IT leaders in the US, Canada, UK, France and Germany, and finds concerns about the skills crisis limiting number of mainframe professionals left in the market, and the importance of being able to leverage cloud deployment, agile development, and open source initiatives. Of those surveyed 94 percent… [Continue Reading] -

Hackers, geeks and thieves -- analysis of dark web communities reveals varied motives
Publié: octobre 10, 2018, 5:09pm CEST par Ian Barker
When we talk about the dark web it's easy to think of it as an amorphous malevolent blob. But new research from Recorded Future reveals some key differences between dark web communities in different parts of the world. The company's Inskit Group of researchers has actively analyzed underground markets and forums tailored to Russian and Chinese audiences over the past year and has discovered a number of differences in content hosted on forums, as well as differences in forum organization and conduct. The findings show that Russian-speaking cybercriminals value money above all else. Their fora don't have much room for… [Continue Reading] -

Carbon Black launches advanced threat hunting from the cloud
Publié: octobre 10, 2018, 3:45pm CEST par Ian Barker
Most endpoint detection tools collect only a limited set of data, which can make it hard for teams to track down and combat threats. To address this issue, endpoint security specialist Carbon Black is launching a new threat hunting tool as part of its Predictive Security Cloud (PSC). Cb ThreatHunter continuously collects unfiltered data, giving security teams all the information they need to proactively hunt threats, uncover suspicious and stealthy behavior, disrupt active attacks, repair damage quickly and address gaps in defenses before attackers can. "One year ago at Cb Connect in San Francisco, we outlined our vision to rapidly… [Continue Reading] -

68 percent of enterprises are not ready to cope with DNS attacks
Publié: octobre 10, 2018, 3:03pm CEST par Ian Barker
A new study reveals that 68 percent of the top 50 companies on the Fortune 500 rankings are not adequately prepared for the next major DNS attack. The Global DNS Performance Report by network intelligence company ThousandEyes shows that DNS best practices are not widespread in major enterprises and SaaS providers, leaving them needlessly vulnerable. It also finds DNS performance varies widely for public resolver providers and managed providers across regions and countries. Out of fifteen measured public DNS providers, newcomer Cloudflare was found to have overall fastest performance, followed by Google and OpenDNS, both of which improved over their… [Continue Reading] -

Half of new app development requests end in failure
Publié: octobre 9, 2018, 6:58pm CEST par Ian Barker
In the US and across European countries, 50 percent of all new app development requests end in failure -- either by not being delivered at all, or being delivered without meeting the original business need. According to research carried out by IDG for low-code development platform Appian, 16 percent of new development projects requested by EMEA enterprises never even get started. Of those that do, 14 percent are started but never finished, and 20 percent of new development projects in both EMEA and the US get completed but don't meet the business need. In the US, marketing is more likely… [Continue Reading] -

Symantec delivers integrated approach to cloud security
Publié: octobre 9, 2018, 4:55pm CEST par Ian Barker
Companies increasingly rely on cloud applications and infrastructure for their critical systems. Protecting these is vital and to help businesses do so, Symantec is launching an expansion to its cloud security portfolio. Symantec’s Cyber Defense Platform offers a broad range of protection, providing visibility and control for virtually any cloud app and integrations with CloudSOC CASB, Cloud Workload Protection (CWP) and Data Loss Protection (DLP). It also provides deep cloud protection, giving customers the ability to track more risk attributes and scan cloud applications and repositories with new API Integrations. "Our cloud security suite was designed with innovative new features… [Continue Reading] -

77 percent of CISOs get conflicting advice on changing regulation
Publié: octobre 9, 2018, 4:19pm CEST par Ian Barker
A new report released ahead of the Infosecurity North America event to be held next month, shows that the majority of chief information security officers (CISOs) are receiving conflicting advice about new or changing regulation. In addition, when asked what regulatory bodies should do to help promote a smooth rollout of privacy regulations, 35 percent of respondents say that regulators should provide clearer communication about compliance requirements. Regulatory bodies should allow a grace period so organizations can tweak their processes without penalty, according to 31 percent. Additionally, 17 percent say that regulatory bodies should permit more time for compliance, and… [Continue Reading] -

Basic identity and access management tasks are still a struggle for many
Publié: octobre 9, 2018, 3:40pm CEST par Ian Barker
One in three organizations rely on outdated and manual methods, like spreadsheets, to manage privileged accounts, and there's widespread lack of confidence among IT professionals in access control and privileged account management programs. This is among the findings of a new report from One Identity which also shows one in 20 organizations have no way of knowing if users retain access even after they’ve left the organization. In addition to 31 percent of businesses using manual administrative account management methods, a surprising one in 25 organizations don't manage administrative accounts at all. Two thirds (66 percent) grant privileged account access… [Continue Reading] -

Attacks on IIS web servers soar over the last quarter
Publié: octobre 9, 2018, 3:11pm CEST par Ian Barker
Attacks targeting IIS servers have shown a massive 782 times increase, from 2,000 to 1.7 million, over the last quarter according to a new report. The report from threat protection specialist eSentire reveals that most attacks targeting IIS web servers originated from China-based IP addresses. There's also an eclectic range of operating systems among the attacking infrastructure involved -- over 400 of the attacking IPs had Shodan records indicating they were Windows machines (including XP, 7, 8, 2008, and 2012). Additionally, nearly 350 FTP servers and over 100 mail servers were reported. There were also VPN servers, MikroTik devices (reported… [Continue Reading] -

4.5 billion records compromised in first half of 2018
Publié: octobre 9, 2018, 1:38pm CEST par Ian Barker
The first half of 2018 saw 945 data breaches which led to 4.5 billion data records being compromised worldwide, according to a new report. The latest Breach Level Index from digital security company Gemalto shows that compared to the same period in 2017, the number of lost, stolen or compromised records increased by a massive 133 percent, though the total number of breaches slightly decreased, suggesting attacks are getting more severe. A total of six social media breaches, including the Cambridge Analytica/Facebook incident, have accounted for over 56 percent of total records compromised. Of the 945 data breaches, 189 (20… [Continue Reading] -

Arcserve launches cloud solution for business continuity
Publié: octobre 9, 2018, 1:10pm CEST par Ian Barker
The more enterprises rely on technology the more they suffer when systems fail. Data protection provider Arcserve is aiming to reduce the impact of unplanned downtime with a new cloud solution. Arcserve Business Continuity Cloud eliminates the need for other data protection tools and management consoles with fully-integrated capabilities to protect and restore applications and systems in any location, on-premises and in public and private clouds. According to new data released by Arcserve, 64 percent of global IT decision-makers agree that protecting business-critical data has not become easier over the past five years, despite efforts to adopt solutions to simplify… [Continue Reading] -

Artificial intelligence used to identify social engineering risks
Publié: octobre 8, 2018, 3:00pm CEST par Ian Barker
Security awareness training company KnowBe4 is launching a new version of its platform using artificial intelligence to identify evolving risks. It includes a Virtual Risk Officer that helps security or IT professionals identify risks at the user, group or organizational level, resulting in better decision making for their security awareness plans. This is supplemented by a Virtual Risk Score which alerts admins to which users or groups are particularly vulnerable to social engineering attacks. These scores help organizations identify which groups are most apt to click on a phishing link, who has or hasn't been trained and which are the… [Continue Reading] -

Understanding the privacy paradox
Publié: octobre 8, 2018, 11:26am CEST par Ian Barker
In the modern world people often say they care about privacy, but their actions don't reflect their words. Exploring this privacy paradox is a new infographic from privacy app company Keepsafe. It shows that 35 percent of people have concerns when making purchases on their mobile devices, but 43 percent do so anyway in the name of convenience. Among other findings are that 65 percent aren't comfortable when disclosing personal information to websites, but only 51 percent would use an app to protect their personal phone number online. Among millennials, 48 percent have private content on their phones, yet 78… [Continue Reading] -

Insiders cause more than half of data breaches
Publié: octobre 3, 2018, 4:49pm CEST par Ian Barker
Most companies consider hacker attacks to be the most dangerous threat, but according to a new report, insiders cause the majority of security incidents by either malicious or accidental actions. The study from threat detection specialist Netwrix looks at the experiences and plans over 1500 organizations have in addressing IT risks. The insider threat is underlined by the fact that 44 percent of respondents either don't know or are unsure what their employees are doing with sensitive data. Among the findings are that not all critical security controls are reviewed regularly as required by best practices. The most neglected controls… [Continue Reading] -

Data theft malware targets Fortnite players
Publié: octobre 3, 2018, 3:29pm CEST par Ian Barker
It's no surprise that the release of a new season of Fortnite has led to a rise in scammers keen to exploit gamers who are eager to sample the new software. Among a rash of supposed free passes and free Android versions of the game that hide surveys and other nuisances, researchers at Malwarebytes have uncovered a malicious program seeking to steal data and Bitcoins. The malware was offered by a YouTube account under the guise of a cheat and had received more than 2,000 views a day after uploading. Clicking the link takes you to a survey page which… [Continue Reading] -

67 percent of organizations believe hackers can penetrate their network
Publié: octobre 3, 2018, 1:38pm CEST par Ian Barker
Around two-thirds of executives and IT professionals responding to a new survey believe that hackers would be able to penetrate their networks. The study from security and application delivery company Radware focused on global companies and reveals that at least 89 percent of respondents have experienced attacks against web applications or web servers of the past year. Almost half (46 percent) of organizations surveyed say they have experienced data security breaches in the last 12 months, and respondents find application layer attacks to be the most difficult to both detect and mitigate. In particular, respondents reporting of encrypted web attacks… [Continue Reading] -

One in four cyberattacks targets ordinary users
Publié: octobre 2, 2018, 4:44pm CEST par Ian Barker
While the majority of cyberattacks are aimed at businesses and other organizations, an increasing number are targeting ordinary users, according to the latest report from Positive Technologies. The most attractive targets were personal data (30 percent) and credentials (22 percent), especially for online banking. To steal this data, attackers compromised a wide range of websites, including web stores, ticket vendors, and hotel booking services. A doubling of the number of attacks on cryptocurrencies in the second quarter saw attackers steal over $100 million in total. The share of attacks on web resources has also increased year-on-year (32 percent in Q2… [Continue Reading] -

Behavioral analysis used to predict cybersecurity threats
Publié: octobre 2, 2018, 4:01pm CEST par Ian Barker
Internet of Things security specialist ZitoVault has patented a new means of predicting upcoming cybersecurity events. While most existing approaches only address the real-time detection of threats or anomalies based on a limited set of pre-established data points, ZitoVault's latest patent uses a new approach. It defines how to correlate a broader array of behavioral data, including third-party data, social media, phone, text and email activity, context of searches within and outside of corporate domains, financial data, travel history and changes in HR status. The system provides a software architecture for linking users to events and to other users by partitioning… [Continue Reading] -

Financial services breaches triple since 2016
Publié: octobre 2, 2018, 3:07pm CEST par Ian Barker
2018 has seen nearly three times as many breaches at financial services organizations as there were in 2016, according to a new report. The study by cloud access security broker Bitglass finds there have been 103 breaches in this year’s report compared to just 37 two years ago. Hacking and malware were responsible for nearly three quarters (73.5 percent) of all breaches in 2018. This is a massive increase over previous years, when they were responsible for 20 percent -- just behind the leader, lost and stolen devices, which caused 25 percent of breaches. The top three financial services breaches… [Continue Reading] -

Bigger isn't better when it comes to password security
Publié: octobre 1, 2018, 3:01pm CEST par Ian Barker
A new study by LogMeIn, the company behind the LastPass password manager shows that size matters in password security, but not in the way that you might think. Looking at anonymized data from over 43,000 companies, the study produced a security score and a password strength score for each. Businesses with fewer than 25 employees had the highest average security score of 50, but the average drops as company size increases. Having more employees means more passwords and unsanctioned apps, as well as extra opportunities for dangerous password behavior. In larger organizations, it's simply more challenging for IT to hold… [Continue Reading] -

ESET launches cloud-based security management solution for SMBs
Publié: septembre 27, 2018, 5:11pm CEST par Ian Barker
Smaller businesses are not immune to cyber security threats, but they often don't have the budgets or staffing resources to deal with them. To address this, endpoint security specialist ESET is launching a new cloud-based remote security management solution specifically designed for the IT security challenges faced by SMBs. ESET Cloud Administrator is a management console allowing centralized management of ESET security products including, ESET Endpoint Antivirus and Security for Windows, ESET Endpoint Antivirus and Security for macOS and ESET File Security for Microsoft Windows Server. As a cloud-hosted service, it offers SMBs a convenient, hassle-free platform, with the ability… [Continue Reading] -

Security is developers' top concern for open source components
Publié: septembre 27, 2018, 4:39pm CEST par Ian Barker
Developers rate security as their top concern when dealing with open source components, above integration and functionality, according to a new study. The report from open source security and license compliance management company WhiteSource reveals that an average developer invests 15 hours a month dealing with open source security vulnerabilities, but only a small fraction of that time (25 percent) is devoted to actual remediation. There's has been a significant rise in the number of open source vulnerabilities, up 60 percent from 2016 according the report, which presents development and security teams with the challenge of ensuring that their products… [Continue Reading] -

Schools should offer formal information security classes
Publié: septembre 27, 2018, 4:18pm CEST par Ian Barker
Digital threats are evolving fast and that leads to increasing demand for security professionals to tackle them. A new report from AI-driven security company Lastline looks at how existing practitioners feel about education in their field. Among the findings are that 85.5 percent of infosec professionals believe that US schools should offer more formal classes in the field. When asked which institutions should take responsibility for educating today's youth about digital security, those surveyed offered a wider range of opinions. K-12 teachers received the greatest amount of support at 30.3 percent of respondents. Parents and higher education organizations followed close behind at 28.1… [Continue Reading] -

The changing network security landscape
Publié: septembre 27, 2018, 3:23pm CEST par Ian Barker
The adoption of the cloud and as-a-service delivery models means that the company network, which was once a closed environment, has now expanded into a range of other areas. Alongside this expansion comes a new range of risks and a new study from cloud-delivered security specialist ProtectWise in conjunction with Osterman Research looks at the latest network security challenges and how they are being met. Among its findings are that the number of security staff in a company doesn't equate to the size of the business. The largest companies only have 30 percent more security staff than mid-sized companies, despite averaging 10… [Continue Reading] -

Bandwidth Alliance gets together to take on AWS data transfer fees
Publié: septembre 26, 2018, 3:26pm CEST par Ian Barker
The fear of being locked in to a particular service is one of the key worries that companies have when moving to the cloud. This is partly because suppliers, including AWS, charge data transfer fees or bandwidth when you want to move to another host. Now content delivery network Cloudflare is forming the Bandwidth Alliance, a coalition of cloud and infrastructure companies (including IBM, Digital Ocean, Backblaze, Dreamhost, and Packet) that are committed to waiving bandwidth fees for customers when interconnecting directly to Cloudflare's network. "If you're hosting on most cloud providers, data transfer charges, sometimes known as 'bandwidth' or… [Continue Reading] -

Cryptomining malware surges in second quarter
Publié: septembre 25, 2018, 4:39pm CEST par Ian Barker
Cryptocurrency mining malware has seen an increase of 86 percent in the second quarter of 2018, according to a new report from McAfee Labs. After gaining ground the fourth quarter of 2017 to around 400,000 samples, new cryptomining malware samples grew a stunning 629 percent to more than 2.9 million in Q1 of 2018. This trend has continued in with more than 2.5 million new samples detected. McAfee Labs has also identified what appear to be older malware programs, such as ransomware, newly retooled with mining capabilities. In some cases, cryptomining targets specific groups rather than a broad field of… [Continue Reading] -

Symantec brings improved data loss prevention and rights management to Office 365
Publié: septembre 25, 2018, 4:13pm CEST par Ian Barker
Protecting data in the cloud and ensuring compliance with rules and regulations is a complex task. The adoption off SaaS applications like Office 365 makes it even more so. Symantec is launching an enhanced version of its Data Loss Prevention technology to protect data in Office 365 and allow users to safely share it internally as well as with partners and contractors. Symantec's DLP uses a powerful combination of detection technologies backed by advanced machine learning to classify sensitive personal information. These include Sensitive Image Recognition (SIR) with Optical Character Recognition (OCR). When data is shared with third parties, identity-based… [Continue Reading] -

Companies continue to use vulnerable open source components
Publié: septembre 25, 2018, 3:12pm CEST par Ian Barker
Use of known vulnerable open source components has increased by 120 percent over the last year and 62 percent of organizations say they have no meaningful control over OSS components, according to a new study. Sonatype's fourth annual State of the Software Supply Chain Report shows that open source continues to be a key driver of innovation -- with software developers downloading more than 300 billion open source components in the past 12 months. However, hackers are exploiting this growing trend, and even beginning to inject vulnerabilities directly into open source projects. Currently over 1.3 million vulnerabilities in OSS components… [Continue Reading] -

New solution adds biometric authentication to messaging platforms
Publié: septembre 24, 2018, 3:11pm CEST par Ian Barker
Messaging systems like Skype, Slack, Telegram and others are increasingly used by both individuals and businesses. But how do you know the person you're talking to is who they say they are? A new product from biometric solutions company ID R&D offers multi-layer continuous authentication across messaging platforms without any impact on the user experience. Called SafeMessage, it provides authentication of verified users by adding a positive ID icon with each incoming message, ensuring the authentic biometric identity of the sender. There are no additional steps needed by a sender to enable this authentication check. All biometric data is collected… [Continue Reading] -

Almost 80 percent of people dislike content recommendation widgets
Publié: septembre 21, 2018, 11:39am CEST par Ian Barker
We've all seen them on news websites, at the bottom of pages or lurking in side bars, those 'Promoted stories' with cheesy headlines like, 'What she looks like now will amaze you!' Well, it perhaps won't surprise you to learn that most people don't like them. A study by interactive content specialist Arkadium shows that 79 percent of those surveyed disapprove of sites using content recommendation widgets. The links aren't fooling anyone much into thinking they're news either, with 73 percent of respondents aware that articles within these content recommendation widgets were often sponsored and paid for. "Publishers are doing… [Continue Reading] -

Kaspersky launches updated small business security solution
Publié: septembre 20, 2018, 5:20pm CEST par Ian Barker
Small businesses are just as vulnerable to cyber threats as larger ones, but often they have few resources to devote it IT security. With the launch of its next generation of Kaspersky Small Office Security, Kaspersky Lab aims to offer smaller businesses protection from cybercrime without the need for technical cybersecurity expertise or regular hands-on administration. Features in the new version include extended protection again ransomware and coin miners, with the System Watcher now available for protection of Windows file servers in addition to already protecting endpoint computers. A new approach to alert notifications won't disturb employees, unless the event… [Continue Reading] -

Linksys launches enterprise grade Wi-Fi network management for SMBs
Publié: septembre 20, 2018, 4:40pm CEST par Ian Barker
Businesses of all sizes are dependent on wireless networks, but for smaller organizations the costs of deploying and managing a suitably fast and secure can be prohibitive. Networking specialist Linksys is launching its new Cloud Manager, a cloud-hosted Wi-Fi management platform purpose-built for small business environments that reduces costs and increases operational efficiencies. "There is a gap in the market for affordable, business-grade cloud managed Wi-Fi management platforms designed specifically for SMBs," says Wayne Newton, director of commercial business at Linksys. "Current offerings are either built with consumer-grade hardware or with expensive, enterprise features with prohibitive annual hosting fees. A… [Continue Reading] -

Retail industry continues to struggle with cybersecurity
Publié: septembre 20, 2018, 4:15pm CEST par Ian Barker
A new report from risk rating organization SecurityScorecard finds that the retail industry is the second lowest performer in terms of application security. SecurityScorecard continually monitors more than 200,000 businesses across the world and the report compares the average grade of the retail industry to other vertical markets. Retail is particularly vulnerable to social engineering attacks, partly because the industry employs a higher proportion of younger, less experienced people. Interestingly small business accounted for 43 percent of attacks with 62 percent of those arising out of phishing and social engineering. "This year the retail industry's security posture fell lower than… [Continue Reading] -

Staff feel pressure to over achieve when working from home
Publié: septembre 20, 2018, 3:14pm CEST par Ian Barker
Working from home has long had a stereotype image of people sitting around in their pajamas drinking coffee while logged into the office computer but not doing very much actual work. But new research from remote access tool LogMeIn, shows 46 percent of UK workers feel the need to show that they are actually being productive when working from home. While 36 percent of workers admit to suffering from pressure to appear 'more responsive' on email while working remotely, 23 percent also feel a pressure to work more hours; encroaching more on family time than if they had gone to… [Continue Reading] -

Fake bank apps found on Google Play store
Publié: septembre 19, 2018, 3:56pm CEST par Ian Barker
Cybersecurity company ESET has discovered six fake banking and personal finance apps on the Android store. The apps had been installed more than 1,000 times total before being taken down by Google. ESET believes all of the apps are the work of a single attacker. They have impersonated six banks from New Zealand, Australia, the United Kingdom, Switzerland and Poland, and the Austrian cryptocurrency exchange Bitpanda. Using bogus forms, the malicious fakes phish for credit card details and login credentials to the impersonated legitimate services. Some of the apps take advantage of the absence of an official mobile app for… [Continue Reading] -

Sapho brings machine learning to the enterprises
Publié: septembre 19, 2018, 3:11pm CEST par Ian Barker
Access to up to date information is essential for businesses, but as data proliferates it's too often the case that people spend time searching for the information they need to do their jobs. Employee experience portal Sapho is integrating machine learning into its product so that metrics that are typically hard to access, due to complex applications or time-consuming dashboards, will now be delivered directly to employees without needing them to conduct an information search. "The lack of employee engagement in today's enterprises is impacting companies’ ability to attract, empower and retain employees," says Fouad ElNaggar, CEO of Sapho. "It's… [Continue Reading] -

Credential stuffing attacks target financial services
Publié: septembre 19, 2018, 1:23pm CEST par Ian Barker
A new report from cloud delivery company Akamai reveals that the financial services industry has become a prime target for credential stuffing botnets. Between May and June 2018, Akamai detected more than 8.3 billion malicious login attempts. However, many botnets attempt to remain in stealth mode for as long as possible. The report highlights two attacks on financial services sites. One botnet attack caused a major financial company's login attempts to spike from an average of approximately 50,000 an hour to over 350,000 in one afternoon. The other saw a credit union attacked by three botnets at the same time,… [Continue Reading] -

Half of adults look for online recommendations rather than ask their partners
Publié: septembre 18, 2018, 5:13pm CEST par Ian Barker
More than half of adults worldwide are more likely to consult digital resources than their significant other (SO) for recommendations for products and services according to a new report by cloud database company DataStax. In the US, 64 percent of adults choose digital resources over their SO, in the UK it's 61 percent, and Germany, 52 percent. The French, however, are still inclined to the offline approach with only 45 percent of adults choosing digital resources over their SO. Among other findings are that 69 percent of international adults are willing to spend extra to reduce their wait times for… [Continue Reading] -

Employees engage in unsafe online behavior despite understanding risks
Publié: septembre 18, 2018, 4:35pm CEST par Ian Barker
A survey of more than 400 full-time employees in the US shows that, despite having a general understanding of security risks, people still tend towards unsafe behavior. The study by Spanning Cloud Apps finds many are under-prepared for the increasing sophistication and instance of ransomware and phishing attacks. More than half (55 percent) admit to clicking links they don't recognize, 59 percent say they would allow a colleague to use their work computer and 34 percent are unable to identify an insecure eCommerce site. Recognition of of unfamiliar URLs from popular sites like Facebook and the New York Times, along… [Continue Reading] -

93 percent of execs report positive long-term outlook for mainframes
Publié: septembre 18, 2018, 4:01pm CEST par Ian Barker
Far from them being the technology of the past, attitudes towards mainframes are increasingly positive according to a new survey. The study from IT solutions company BMC finds 93 percent of executives and 92 percent of all respondents view the mainframe as a strong long-term platform -- the highest level in five years. "Digitization and mobility are placing incredible pressure on both IT and mainframes to manage a greater volume, variety, and velocity of transactions and data, with workloads becoming more volatile and unpredictable," says Bill Miller, president of ZSolutions at BMC. "The 2018 BMC Mainframe Research Report shows a… [Continue Reading] -

Enterprises need to adopt 'zero-trust' security posture
Publié: septembre 18, 2018, 3:06pm CEST par Ian Barker
Privileged access management specialist Thycotic has released the results of its latest survey, conducted at this year's Black Hat, on hackers' perspectives on vulnerabilities and the attack vectors they find easiest to exploit. It shows that 50 percent of hackers surveyed -- 70 percent of whom describe themselves as ethical -- say they easily compromised both Windows 10 and Windows 8 within the past year. Knowing that compromise of user accounts is probably inevitable, organizations need to move to a 'zero-trust' posture that emphasizes least privilege to limit over privileged accounts that give hackers wide and undetected access. Unfortunately this isn't… [Continue Reading] -

The poor security habits of SMB executives
Publié: septembre 17, 2018, 5:16pm CEST par Ian Barker
Over half of small business executives are convinced their business is not a target for cybercriminals, according to a new report. The study from consulting and managed services company Switchfast also shows that 31 percent of senior management employees shared the password to their work email with another co-worker, while only 18 percent of associates have. More alarming is the fact that passwords of senior management are more likely to contain personally identifiable information (26 percent), like social security numbers or birthdays, compared to 19 percent of associates. Among other worrying stats is that 17 percent of men and 12… [Continue Reading] -

32 percent of data breaches lead to executive job loss
Publié: septembre 14, 2018, 3:19pm CEST par Ian Barker
In North America 32 percent of data breaches have resulted in a C-level manager, president or CEO losing their job, according to new research. The study from Kaspersky Lab shows that 42 percent of businesses worldwide experienced at least one data breach in the last year. When a data breach occurs it not only results in a costly recovery burden, now put at $1.23 million on average, but it can also impact the company's reputation, customer privacy, and even severely impact employees' careers. The research highlights how responsibility for a breach often extends beyond technical IT employees. Among employees let… [Continue Reading] -

Cold boot attack leaves Apple and Microsoft systems vulnerable to data theft
Publié: septembre 13, 2018, 4:42pm CEST par Ian Barker
Researchers at cyber security company F-Secure have discovered a weakness in modern computers' firmware that attackers can use to steal encryption keys and other sensitive information. Physical access to the computer is needed to exploit the weakness, but once an attacker has gained this they can successfully perform the attack in around five minutes. "Typically, organizations aren’t prepared to protect themselves from an attacker that has physical possession of a company computer," says F-Secure's principal security consultant Olle Segerdahl. "And when you have a security issue found in devices from major PC vendors, like the weakness my team has learned… [Continue Reading] -

Kodi add-ons used to distribute currency miners
Publié: septembre 13, 2018, 3:43pm CEST par Ian Barker
Users of the Kodi media center may already know that the Netherlands-based repository for third-party add-ons, XvBMC, was recently shut down due to copyright violations. Researchers at security company ESET have discovered that the repository was also part of a malicious cryptomining campaign dating back to December 2017. This is the second instance of Kodi being used for cryptojacking this year. "According to our research, the malware we found in the XvMBC repository was first added to the popular third-party add-on repositories Bubbles and Gaia (a fork of Bubbles), in December 2017 and January 2018, respectively," says ESET's Kaspars Osis,… [Continue Reading] -

New partnership aims to bring deeper insights from machine data
Publié: septembre 13, 2018, 3:13pm CEST par Ian Barker
The rise of the Internet of Things has presented businesses with huge volumes of data, but harnessing that to produce useful insights can be a challenge. A new partnership between Trifacta, a leader in data preparation, and Sumo Logic, a cloud-native machine data analytics platform, is aimed at driving improved business intelligence. "Today's analytics economy requires organizations to harness the power of machine data in order to gain critical insights that drive business decisions, but without the right tools it can be difficult to leverage for a specific set of business use cases," says Bruno Kurtic, founding VP of product… [Continue Reading] -

Tech Talent Matrix helps businesses hire the best developers
Publié: septembre 12, 2018, 4:20pm CEST par Ian Barker
Finding the right technical talent has become a priority for businesses, but they often lack the data needed to know if they are getting it right. The current way for companies to evaluate the success of their recruiting relies on blunt metrics like number of hires, time to hire and employee retention rate. None of which tell companies if they’ve hired the right people. Now HackerRank, a company that helps evaluate technical talent based on skill, is launching a Tech Talent Matrix, a machine learning-based tool that gives companies the data they need to hire the right software developers. "Companies… [Continue Reading] -

Malware-less email attacks on the rise -- especially on Thursdays
Publié: septembre 12, 2018, 3:09pm CEST par Ian Barker
As email security solutions focus on detecting malware, cybercriminals are now adapting their attacks, exposing organizations to more malware-less assaults such as CEO fraud. The report by intelligence-led security company FireEye is based on analysis of a sample set of over half-a-billion emails from the first half of 2018. It finds only 32 percent of email traffic seen was considered 'clean' and actually delivered to an inbox. The report also finds that one in every 101 emails had malicious intent. "Not only is email the most pervasive form of communication, it is also the most popular vector for cyberattacks. This… [Continue Reading] -

Half of US mobile traffic will be scam calls by 2019
Publié: septembre 12, 2018, 1:17pm CEST par Ian Barker
Unwanted and scam phone calls are an increasing problem. Analysis by call management company First Orion predicts that nearly half of all calls to mobile phones in the US will be fraudulent in 2019 unless the industry adopts and implements more effective call protection solutions. Over the past year, First Orion's data shows a drastic increase in scam calls -- from 3.7 percent of total calls in 2017 to 29.2 percent in 2018 -- and that number is projected to reach 44.6 percent by early 2019. A number of techniques are used to persuade call recipients to pick up. The… [Continue Reading] -

Improving endpoint protection is top goal for IT security professionals
Publié: septembre 12, 2018, 12:27pm CEST par Ian Barker
Three quarters of IT security professionals responding to a new survey have named improving endpoint security as one of their top two goals, with 48 percent saying it's most important. The study by Ericom Software, a specialist in securing and connecting the digital workspace, finds 'Becoming compliant with mandatory regulations' is second, with 29 percent of respondents naming it as their top goal. Over 90 percent of participants say that their companies have an active cybersecurity strategy in place. However, almost half are less than 'very confident' that their strategy is sufficient to preempt internet-borne threats. Almost a third report… [Continue Reading] -

Personal devices are a major threat to mobile IT environments
Publié: septembre 12, 2018, 11:11am CEST par Ian Barker
A new survey finds that 58 percent of respondents believe access to their network from non-corporate and personally owned devices such as laptops, desktops or mobile phones is the highest risk in managing remote users. The study from trusted access specialist Duo Security shows that while the trend to remote working has created unmatched flexibility and helped organizations attract top talent globally, it has also introduced a major predicament for IT and security teams. From Duo's findings, 75 percent of respondents report that their users now connect remotely to work applications at least 25 percent of the time. In addition… [Continue Reading] -

70 percent of businesses have experienced unplanned IT disruption in the last year
Publié: septembre 11, 2018, 4:09pm CEST par Ian Barker
A new study from IT solutions provider US Signal reveals that 70 percent of companies have had at least one unplanned IT disruption in the last year. These outages are caused by a variety of factors with natural disasters accounting for 53 percent, errors while implementing new technology (26 percent), ransomware (21 percent) and IT overloads (21 percent). This leads to an understandable level of concern, with 66 percent believing they are vulnerable to IT disruption, and one in 10 stating they feel very vulnerable to these interruptions. Although 58 percent of businesses surveyed say that they have a disaster… [Continue Reading] -

DataOps comes to the cloud
Publié: septembre 11, 2018, 3:21pm CEST par Ian Barker
The movement of data into the cloud creates challenges for enterprises who still rely on traditional data integration software or single-purpose data import tools. DataOps specialist StreamSets is launching new features that help companies efficiently build and continuously operate dataflows that span data centers and the big three cloud platforms -- Microsoft Azure, AWS, and Google Cloud Platform. Features include development automation through a fully-featured dataflow designer that includes 'easy button'connectors for Amazon S3, Elastic MapReduce (EMR) and RedShift; Azure Data Lake Storage, HDInsight and Azure Databricks; and Google DataProc and Snowflake. There's also elastic scaling of cloud, multi-cloud and… [Continue Reading] -

Public cloud services used to boost DDoS attacks
Publié: septembre 11, 2018, 11:01am CEST par Ian Barker
Hackers are increasingly abusing public cloud services in order to launch DDoS attacks, according to new research. The study from anti-DDoS company Link11 shows that a quarter of all DDoS attacks in Europe in the 12 months from July 2017 to June 2018 used public cloud server-based botnets, compared to 18.5 percent in the previous 12 months. Microsoft Azure was the cloud service most exploited for DDoS attacks over this period, with 38.7 percent of such attacks using Azure servers on average. Amazon Web Services (AWS) was used in 32.7 percent of attacks, and Alibaba servers used in 17.9 percent.… [Continue Reading] -

Better communication needed to make progress on digital transformation
Publié: septembre 10, 2018, 4:25pm CEST par Ian Barker
Although a majority of businesses have followed a digital transformation plan, poor top-down communication is proving a barrier to success. A new report from automation specialist Nintex shows that 64 percent of companies have followed a formal digital transformation plan for three years or less, while a third have followed a plan for one year or less. Yet only 53 percent of line of business employees know what digital transformation is, let alone whether their employer has a plan in place. This issue is most concerning for non-management staff, with 67 percent of managers aware of their digital transformation efforts… [Continue Reading] -

Containerization and serverless technology grows as companies shift to digital applications
Publié: septembre 10, 2018, 3:45pm CEST par Ian Barker
Businesses are under increasing pressure to innovate and modernize their architectures at an unprecedented rate to remain competitive and that often means switching to new platforms. The latest research from machine data analytics platform Sumo Logic looks at the trends and visibility into the DevSecOps tools and solutions that are being used as organizations modernize and migrate existing applications. Based on active and anonymized data from more than 1,600 customers and 50,000 users of Sumo Logic's machine data analytics platform, the report provides a rich analysis of mission-critical modern applications and cloud infrastructures running on Amazon Web Services (AWS), Microsoft Azure… [Continue Reading] -

Football team names commonly used in passwords
Publié: septembre 10, 2018, 3:01pm CEST par Ian Barker
Analysis by password manager company Dashlane shows that with the football season getting underway team names are frequently used as passwords. Researchers focused on team names from the National Football League and the English Premier League, using an anonymized database provided by Gang Wang, an assistant professor in the Department of Computer Science at Virginia Tech. The Philadelphia Eagles, winners of this year's Super Bowl, took the top spot for the NFL, while the Dallas Cowboys came in second. Among Premier League teams, the one mentioned most in passwords was Liverpool, followed by London stalwarts Chelsea and Arsenal. "Coming up… [Continue Reading] -

41 percent of industrial control systems attacked in 2018
Publié: septembre 7, 2018, 3:51pm CEST par Ian Barker
Industry increasingly relies on automated systems for the control of processes, but a new report from Kaspersky Lab shows that 41.2 percent of industrial control systems (ICS) computers were attacked by malicious software at least once in the first half of this year. Based on analysis of systems protected by Kaspersky Lab solutions, the data shows that in 2017, the percentage of ICS computers attacked was 36.61 in the first half of the year and 37.75 in the second half. According to Kaspersky, developing economies are accounting for the highest number of ICS computers attacked, while developed regions have the… [Continue Reading] -

Why container frameworks risk taking the focus off development [Q&A]
Publié: septembre 7, 2018, 11:45am CEST par Ian Barker
Enterprises often adopt containers as a way to save money. But they can end up spending time, resources and cash building their own container management framework and in the process getting away from their core business objectives. We spoke to Kieron Sambrook-Smith, chief commercial officer at cloud application specialist Platform.sh, to discuss why enterprises tend to lose sight of business goals in order to manage containers, and the strategies they can implement to stop distracting their developers from doing what they do best, writing code. BN: Why are containers gaining such widespread attention right now? KSS: Containers make application management… [Continue Reading] -

New AI capability helps empower DevSecOps teams
Publié: septembre 6, 2018, 4:05pm CEST par Ian Barker
Security teams are constantly caught between the need to keep pace with security testing and the ability to allow developer teams to operate in a rapid DevOps environment. To address this, application security provider WhiteHat Security is adding artificial intelligence to its dynamic application security testing solution WhiteHat Sentinel Dynamic. Drawing on a data lake of 95 million identified vulnerabilities Sentinel Dynamic will deliver more accurate results faster. This will help developers to create secure web applications at the fast pace demanded by modern business. Using AI software will decrease threat vector identification times and improve the efficiency of false… [Continue Reading] -

Security teams turn to automation to tackle avalanche of alerts
Publié: septembre 6, 2018, 11:28am CEST par Ian Barker
High numbers of alerts and the resources needed to deal with them are causing problems for security teams and leading them to turn to Security Orchestration, Automation and Response (SOAR) tools in order to cope. A new report from security automation specialist Demisto finds teams are being inundated with more than 174,000 alerts every week and security teams are only able to review and respond to around 12,000 of them. It also reveals that it takes an average of eight months to train security analysts to be effective, yet a quarter of these professionals change organizations within two years. Around… [Continue Reading] -

New forecasting solution helps companies reduce cyber risk
Publié: septembre 5, 2018, 4:48pm CEST par Ian Barker
The current feeling is that the chances of a company being hacked is a matter of when rather than if, but businesses continue to struggle with how to actually measure if their security solutions are working. Security ratings company BitSight is launching a new tool that will help customers identify the optimal course of action needed to improve their overall risk posture. BitSight Forecasting uses unique risk and security analytics available through BitSight's ecosystem. With these customers can model various security scenarios and project how changes to processes, technologies and culture are going to impact their environment. Using aggregated security… [Continue Reading] -

How well are high availability applications supported?
Publié: septembre 5, 2018, 3:57pm CEST par Ian Barker
Most businesses have critical applications that are vital to their remaining in operation. But support for these programs is a mixed picture according to a new report. The study from application availability specialist SIOS Technology finds 86 percent of organizations are operating their high availability (HA) applications with some kind of clustering or high availability mechanism in place. Even so, 95 percent of respondents report that they have occasional failure in the underlying HA services that support their applications. Also 98 percent of respondents say that they see either regular or occasional application performance issues. When such issues occur, for… [Continue Reading] -

Over 12 million Brits have fallen victim to online fraud
Publié: septembre 5, 2018, 3:14pm CEST par Ian Barker
Almost one in four Brits (23 percent) have been victims of fraud when shopping online -- with eight percent duped more than once, according to a new study The inaugural Fraud Tracker report from online payment service Shieldpay shows that the average victim loses £608, yet receives only £55 back from their bank. One in seven victims (14 percent) tricked while buying online were defrauded by more than £1000. When looking at the difference between the sexes, the cost of fraud is higher for men -- incurring a loss of £139 more. Banks are facing increased scrutiny about how they… [Continue Reading] -

A third of organizations say their leadership doesn't understand the value of data
Publié: septembre 5, 2018, 12:00pm CEST par Ian Barker
According to a new study, 32 percent of UK business and IT decision makers think their business leaders don't understand the role of data and the value it creates. The research from analytic database firm Exasol finds 80 percent of organizations are unable to function without their data sources, with 25 percent being totally reliant on data to drive daily operations and decision-making. The majority of organizations have also become more reliant on data in the past five years, and 39 percent said they rely significantly more on data today. In addition, 29 percent are actively pursuing a strategy to… [Continue Reading] -

Chrome vulnerability leaves Wi-Fi networks open to attack
Publié: septembre 5, 2018, 11:29am CEST par Ian Barker
Millions of home Wi-Fi networks could be easily hacked, even when the network is protected by a strong password, thanks to a flaw in Chrome-based browsers. Researchers at cybersecurity and penetration testing consultancy SureCloud have uncovered a weakness in the way Google Chrome and Opera browsers, among others, handle saved passwords and how those saved passwords are used to interact with home Wi-Fi routers over unencrypted connections. By design, Chrome-based browsers offer to save Wi-Fi router administration page credentials and re-enter them automatically for users' convenience. As most home routers do not use encrypted communications for management tasks, the researchers… [Continue Reading] -

New tools bring natural language search to big data
Publié: septembre 4, 2018, 3:17pm CEST par Ian Barker
Businesses need easy and fast access to information in order to make effective decisions, but with the rise of big data important information can be hard to access and remain locked away. Visual analytics specialist Arcadia data has announced new search-based BI and analytics which will be available in an upcoming release of its flagship product, Arcadia Enterprise. This will allow users to simply type in natural-language questions and get answers back, encouraging users to embrace modern BI and reap the benefits of its speed and agility. Questions are answered with visualizations based on any size data set. It also… [Continue Reading] -

Six out of 10 Brits think technology will make jobs obsolete
Publié: septembre 4, 2018, 1:11pm CEST par Ian Barker
Technology is destroying jobs, 61 percent of British respondents to a new survey believe, despite evidence to the contrary. The study by polling organization YouGov for recruitment site LynxPro finds only 14 percent believe technology is having no impact on the jobs market, while just 11 percent think it's creating jobs. Older people are more likely to believe jobs are being destroyed by technology. The results show that while 41 percent of 18 to 24-year-olds think technological advances are making jobs obsolete, this increases to 71 percent in people aged 55 and older. But these results contradict those found in… [Continue Reading] -

Botnet distribution of remote access Trojans doubles
Publié: août 31, 2018, 11:43am CEST par Ian Barker
Since the beginning of 2017, the number of remote access Trojan (RAT) files found among the malware distributed by botnets has almost doubled, according to a new report. The botnet activity report from Kaspersky Lab analyzed more than 150 malware families and their modifications circulating through 60,000 botnets around the world. The growth of multifunctional malware, like RATs, provides almost unlimited opportunities for attackers to exploit the infected PC. Njrat, DarkComet, and Nanocore topped the list of the most widespread RATs. Due to their relatively simple structure, these three backdoors can be modified by experienced or inexperienced threat actors. This… [Continue Reading] -

80 percent of enterprises struggle to protect machine identities
Publié: août 30, 2018, 3:59pm CEST par Ian Barker
The protection of human identities tends to be high on the agenda for organizations, but what about machine identities? Recent increases in the number of machines on enterprise networks, shifts in technology, IoT devices and new computing capabilities have created a set of challenges that require increased focus on protecting machine identities. A new study carried out by Forrester for identity protection specialist Venafi shows 96 percent of companies believe that effective protection of both machine and human identities is equally important to the long-term security and viability of their companies. However, 80 percent of respondents admit to struggling with the… [Continue Reading] -

New technology moves AIOps out to the edge
Publié: août 30, 2018, 3:26pm CEST par Ian Barker
Artificial intelligence for operations (AIOps) is gaining ground, allowing businesses to use AI and machine learning on big data from their devices and IT tools to find and address problems in real time. Pioneer in the field Moogsoft is launching a new tool that extends its core AIOps platform capabilities from centralized analytics outwards to the data source. Moogsoft Observe takes time-series and metrics data in real-time and applies AI to detect incidents at the source of the problem rather than exporting them to a central location for analysis. Observe stores only anomalous and contextual data, giving IT teams highly-advanced,… [Continue Reading] -

Attention span of a goldfish? Maybe the message is at fault
Publié: août 29, 2018, 4:26pm CEST par Ian Barker
It's commonly assumed that the internet and electronic communication is making people less able to concentrate and leading to shorter attention spans. But a new study from presentation platform Prezi finds that in fact attention spans may not be shrinking, rather they are evolving to be more selective. The study looked at the effectiveness of content and presentations and how they resonate with business professionals across demographics, including millennials, Generation X, and baby boomers, and finds that the key to engaging content is a compelling narrative combined with stimulating visuals and dialogue. "Our attention spans being shorter than a goldfish's… [Continue Reading] -

SocialChorus platform aims to modernize workforce communications
Publié: août 29, 2018, 3:56pm CEST par Ian Barker
As technology makes many workplaces more fragmented with staff out in the field or working from home, keeping everyone up to date with company activity can become a major challenge. Workforce communications platform SocialChorus is aiming to provide a seamless and scalable experience for internal communicators with the launch of its new Innovation Lab. "Internal communicators manage multiple systems and often spend hours creating differentiated content for different groups of employees," says Tim Christensen, vice president of product and engineering at SocialChorus. "Instead of relying on cascade communications, companies need to modernize their infrastructures to serve the needs of their… [Continue Reading] -

The top cybersecurity concerns for IT and business
Publié: août 29, 2018, 3:08pm CEST par Ian Barker
Everyone is aware that cybersecurity threats are out there, but what are the biggest threats and are IT and business executives worried about the same things? New research from data security specialist Varonis highlights some major differences -- and potential challenges -- when it comes to communicating and aligning on key threats. Corporate executives share the same broad concerns as their IT security teams. When asked to name the top three cybersecurity concerns facing their organizations, both groups cite data loss and data theft/exfiltration as their top two concerns. Opinions differ after that, however, with cybersecurity pros putting ransomware at… [Continue Reading] -

Email security systems miss thousands of malicious links
Publié: août 28, 2018, 4:49pm CEST par Ian Barker
A new study from email security company Mimecast shows that malicious links in emails are being missed by many security systems. Mimecast examined more than 142 million emails that had passed through organizations' email security vendors. The latest results reveal 203,000 malicious links within 10,072,682 emails were deemed safe by other security systems -- a ratio of one unstopped malicious link for every 50 emails inspected. The report also finds an 80 percent increase impersonation attacks in comparison to last quarters' figures. Additionally, 19,086,877 pieces of spam, 13,176 emails containing dangerous file types, and 15,656 malware attachments were all missed… [Continue Reading] -

New real-time dashboard helps resolve live streaming issues
Publié: août 28, 2018, 4:05pm CEST par Ian Barker
Live streaming is increasingly popular, not just for entertainment but for business use too. However, poor quality streaming with pauses and drop outs can rapidly lose you an audience. Live streaming specialist Mux is aiming to address these problems with the launch of its new Real-Time Streaming Dashboard, designed to help video engineers and product managers detect live stream issues in real-time. "We want to give our customers state-of-the-art analytics that help them act quickly on issues that affect their viewers, from the smallest glitches to major outages," says Mux co-founder and CEO Jon Dahl. "Audiences have so many choices… [Continue Reading] -

Fileless malware attacks rise 94 percent in 2018
Publié: août 28, 2018, 3:20pm CEST par Ian Barker
The first half of 2018 has seen a 94 percent rise in fileless malware attacks according to the latest Enterprise Risk Index Report from endpoint security company SentinelOne. It also finds that PowerShell attacks jumped to a record of 5.2 attacks per 1000 endpoints, compared to 2.5 in May. Ransomware attacks remain popular too, ranging from 5.6 to 14.4 attacks per 1000 endpoints. The report also examines the classification of detected documents and executables by the verdict provided by reputation services. More than 70 percent of detected executables were unknown to these services, and more than 90 percent of documents.… [Continue Reading] -

Does your website risk leaking personal data?
Publié: août 24, 2018, 1:12pm CEST par Ian Barker
Recent scandals surrounding the use of personal data, such as the Cambridge Analytica scandal, plus the large fines that can be levied under GDPR, have focused minds on the protection of information. But is your website at risk of exposing your visitors' data? Auditing and monitoring specialist DataTrue has produced an infographic looking at the risks site tags may pose to privacy. These include understanding the tags used on your site and what they are used for. Also whether tags are shared with other businesses for analytics or marketing purposes, this is important because tags may 'piggyback' to other sites… [Continue Reading] -

IT departments struggle to balance innovation against everyday operations
Publié: août 23, 2018, 4:35pm CEST par Ian Barker
Everyday tasks, such as maintaining reliable operations, are outweighing more creative projects, such as leading innovation and supporting new digital business initiatives in IT departments according to a new study. The survey, carried out by IDG Connect, among over 300 IT decision makers, and commissioned by unified operations specialist Ivanti. finds that maintaining critical infrastructure and IT systems is the activity listed more than half (56 percent) of respondents as being expected of IT. After that, the most cited expectations are lowering IT spend (50 percent) and supporting more agile business processes (41 percent). The least cited expectations are enabling… [Continue Reading] -

How technology is changing the way we work
Publié: août 23, 2018, 3:42pm CEST par Ian Barker
As millennials now become the largest component of the workforce, and as the freelance or 'gig' economy grows, expectations around technology in the workplace are changing. Cloud communications and collaboration firm Intermedia has produced a report looking at how companies can utilize technology to foster a more collaborative, productive, and accessible workplace, and at the same time help attract and retain top talent. Among the findings are that mobile apps are helping to redefine office hours. 51 percent of respondents regularly begin their workday (by checking emails, taking calls, etc) on their commutes before reaching the office. 19 percent say… [Continue Reading] -

Now you can insure your business against cryptomining
Publié: août 22, 2018, 4:18pm CEST par Ian Barker
It's common for businesses to insure against the risk of losing their systems to natural disasters or power outages, but a new product allows you to insure against fraudulent use of IT and telephony, including cloud and internet-based services. San Francisco-based cyber insurer Coalition is launching Service Fraud coverage that reimburses organizations for the direct financial losses they incur as the result of being charged for fraudulent use of business services including Software-as-a-Service (SaaS), Infrastructure-as-a-Service (IaaS), Network-as-a-Service (NaaS), and telephony services. "It's a good time to be a cybercriminal," says Joshua Motta, founder and CEO of Coalition. "As the pace… [Continue Reading] -

Europe leads the world in cloud adoption
Publié: août 22, 2018, 3:56pm CEST par Ian Barker
Europeans have the highest cloud adoption rate in the world at 84 percent according to a new report, up by 27 percent since 2016. The study of 20,000 organisations' use of cloud technology was carried out by cloud security company Bitglass finds that Office 365 is the most widely adopted cloud application across EMEA. Some 65 percent of organisations now use Office 365 -- an increase of 51 percent compared to a similar study in 2016. Usage of AWS in EMEA far exceeds the rate of AWS deployments globally, with just eight percent using AWS worldwide while in EMEA that… [Continue Reading] -

90 percent of enterprises run or plan to run VMs in the cloud
Publié: août 22, 2018, 2:51pm CEST par Ian Barker
In a new survey released ahead of this year's VMworld, cloud protection and management company Druva reveals cloud adoption is growing for virtualized workloads, with 90 percent of respondents running, or planning to run, virtual machines in the cloud in 2018. But the survey also highlights significant risks associated with this shift, as organizations discover that on-premises approaches to data management are outdated and no longer adequate for the cloud era. Among other findings are that 41 percent of organizations are currently running VMs in the cloud, up from 31 percent in 2017. AWS remains a leader with 59 percent… [Continue Reading] -

SaaS solution simplifies secondary data and app management
Publié: août 21, 2018, 3:50pm CEST par Ian Barker
Increasingly businesses don't have all of their secondary data and apps in one place. Instead they are spread across multiple locations in house and in the cloud. Storage specialist Cohesity is launching a SaaS-based management solution that empowers customers to see, manage, and take action on their secondary data and applications globally. Cohesity Helios allows management from a single dashboard and lets businesses benefit from powerful analytics and machine learning capabilities to generate valuable insights from untapped data. Features include the ability for admins to define service-level agreements by job and workload, Cohesity SmartAssist will then automatically evaluate required versus… [Continue Reading] -

New platform simplifies enterprise cloud management
Publié: août 21, 2018, 3:18pm CEST par Ian Barker
As systems move to the cloud companies are faced with increased complexity and the need for flexibility. In addition there are roadblocks including intensive data migrations, reliance on legacy systems, and security and regulatory concerns. Information management company M-Files is launching a new information management system that enables organizations to flexibly combine cloud and on-premises deployments with a single user license and without having to lock into one model. M-Files Online offers an intelligent and flexible, system-neutral approach to managing information that can make any organization cloud-ready. This approach unifies information and related policies and processes across an organization's systems… [Continue Reading] -

82 percent of organizations moving to analytics don't know where their critical data is located
Publié: août 21, 2018, 12:11pm CEST par Ian Barker
Although 75 percent of organizations are moving away from traditional business intelligence towards data analytics, a worrying 82 percent say they don't know where their critical data is located. A study for analytics database vendor Exasol, conducted by researchers Vanson Bourne, reveals 'dark data' is still a major challenge for businesses trying to move to an analytics model. Better data (quality, availability and validity) is seen as the main catalyst driving adoption of data analytics within departments, with 62 percent already realizing some of the business value they hoped for. Despite this, businesses are struggling to aggregate and reconcile sources… [Continue Reading] -

Consumers lack trust in IoT devices
Publié: août 21, 2018, 11:14am CEST par Ian Barker
More than half of consumers worldwide are now using IoT devices, yet 64 percent of those have already encountered performance issues and there are widespread fears about what could go wrong, according to a new survey. The study of 10,000 consumers by software intelligence company Dynatrace finds that people experience an average of one and a half digital performance problems every day, and 62 percent fear the number of problems they encounter, and the frequency, will increase due to the rise of IoT. Dave Anderson, digital performance expert at Dynatrace says, The delivery chain behind every connected device is extremely… [Continue Reading] -

IT decision makers look to AI to prioritize operational alerts
Publié: août 20, 2018, 12:08pm CEST par Ian Barker
Faced with an abundance of alerts related to system status IT decision makers are looking to AIOps solutions -- combining big data and machine learning -- to differentiate between legitimate signals and inconsequential noise, according to a new report. The survey from hybrid IT management platform OpsRamp finds 68 percent have experimented with AIOps tools, and nearly three-quarters (73 percent) are taking advantage of AIOps capabilities to gain more meaningful insights into system alerts. Up to half of all incidents are recurring according to 51 percent of respondents, and 48 percent describe their current alert volumes as too noisy, too… [Continue Reading] -

Three-quarters of corporate network breaches are via web applications
Publié: août 17, 2018, 1:05pm CEST par Ian Barker
According to a new report from Kaspersky Lab, 73 percent of successful perimeter breaches on corporate networks in 2017 were achieved using vulnerable web applications. In addition to web applications, another common vector for penetrating the network perimeter was attacks on publicly available management interfaces with weak or default credentials. In 29 percent of external penetration test projects, Kaspersky Lab experts successfully gained the highest privileges in the entire IT infrastructure, including administrative-level access to the most important business systems, servers, network equipment, and employee workstations, on behalf of an 'attacker' that had no internal knowledge of the target organization.… [Continue Reading] -

Telecoms industry sees a higher percentage of advanced attacks
Publié: août 16, 2018, 3:29pm CEST par Ian Barker
Threat intelligence specialist Lastline produces regular reports on the global cyberthreat landscape. Its latest study looks at the telecoms industry and how the threats it faces differ from those in the wider world. Among the findings are that the industry sees a higher percentage of attacks (one in 10) exhibiting advanced threat capabilities, which is greater than the global standard of one in 12. While telecom companies already have adequate security in place, attackers are creating an even more challenging threat environment for these companies. They see a higher proportion of malicious files in network traffic -- one in 370… [Continue Reading] -

Money, power and ego, the factors that drive people to cybercrime
Publié: août 15, 2018, 6:06pm CEST par Ian Barker
We reported last week on a report highlighting how many security professionals are turning to a life of cybercrime. In a follow up research piece, Wendy Zamora at Malwarebytes, has been looking at the psychology, motivations and other underlying factors that drive people to take part in cybercrime. It reveals that most cybercriminals exhibit some common characteristics. These include some measure of technical knowledge, a disregard for the law or rationalization about why particular laws are invalid or should not apply to them and a high tolerance for risk or the need for a 'thrill factor'. They also exhibit control… [Continue Reading] -

Trojans increase as cryptomining declines
Publié: août 15, 2018, 4:45pm CEST par Ian Barker
The second quarter of 2018 has seen a significant increase in Trojan activity, seeing them become the leading type of malware, according to the latest report from Comodo Cybersecurity. At the same time there has been a slight decrease in cryptomining software. However, this has gone hand-in-hand with a sharp increase in their harmful capabilities, including better concealment and stronger persistence. "Trojans have always been a prevalent and dangerous threat, but their evolution in Q2 is particularly interesting as they are now able to hide for longer periods of time and persist despite the efforts of some of the most… [Continue Reading] -

Organizations still struggle with basic firewall management
Publié: août 15, 2018, 3:40pm CEST par Ian Barker
Firewalls remain an important element of security architecture, but many organizations are still struggling with the basics, according to a new study. Security policy management company FireMon has released its 2018 State of the Firewall report which reveals that 94 percent of respondents believe firewalls are as or more critical than ever. Yet despite this, companies are still struggling with basic firewall management, with rule complexity (30 percent), policy compliance and audit readiness (17 percent), and firewall rule optimization (14 percent) emerging as major pain points. The report identifies two contributing factors to firewall management challenges, the first being the… [Continue Reading] -

SnapLogic integrates with GitHub to speed up DevOps capabilities
Publié: août 15, 2018, 3:10pm CEST par Ian Barker
Self-service application specialist SnapLogic is announcing new integration with GitHub to automate critical elements of continuous integration and continuous delivery (CI/CD). The integration enables system administrators to host different versions of their work, including tasks, pipelines, and projects from SnapLogic, with visibility into changes with each update. Admins and users can easily identify which versions they want to add projects and automate the deployment of SnapLogic. The integration allows users to host the pipelines they created in GitHub while maintaining version control so they can continue working on those pipelines later. This means DevOps can continue providing a seamless user… [Continue Reading] -

Finance remains top target for phishing attacks as scammers exploit GDPR
Publié: août 14, 2018, 5:22pm CEST par Ian Barker
New figures from Kaspersky Lab show that more than a third (35.7 percent) of phishing attempts in the second quarter of 2018 attempts were related to financial services via fraudulent banking or payment pages. The IT sector was second hardest hit, with 13.83 percent of attacks targeting technology companies, a 12.28 percent increase compared to Q1. Cryptocurrency remains a prime target too. There were almost 60,000 attempts to visit fraudulent web pages featuring popular cryptocurrency wallets and exchanges from April to June 2018. In addition to traditional phishing, which tries to access victim accounts and private key information, cybercriminals try… [Continue Reading] -

New application helps developers avoid vulnerable GitHub code
Publié: août 14, 2018, 4:04pm CEST par Ian Barker
We reported last week on a new tool to help spot vulnerabilities present in active open source systems. To prevent problems from being introduced into new systems, open source governance specialist Sonatype is launching a tool to enable developers to identify and avoid using open source components that have known vulnerabilities. According to Sonatype's 2018 DevSecOps Community Survey released earlier this year, one in three organizations has suffered suspected or verified breaches due to OSS vulnerabilities. Breaches due to open source vulnerabilities are up by over 50 percent since 2017. "The need for more secure coding practices has never been greater,"… [Continue Reading] -

How you can be hacked via your fax machine
Publié: août 13, 2018, 3:09pm CEST par Ian Barker
Unless you are in regular touch with the 1980s it's probably a while since you gave much thought to using fax machines. Even then you might think your biggest worry would be a paper jam. But new research from Check Point released at Def Con in Las Vegas reveals organizations and individuals could be hacked via their fax machines, using newly discovered vulnerabilities in the communication protocols used in tens of millions of fax devices globally. The Check Point research demonstrated the vulnerabilities using the popular HP Officejet Pro All-in-One fax printers. But the same protocols are also used by… [Continue Reading] -

Over 10,000 vulnerabilities disclosed this year so far
Publié: août 13, 2018, 11:23am CEST par Ian Barker
2018 looks like it's on track to be another record year for vulnerabilities, with over 10,000 disclosed in the half year to June. The newly released 2018 mid-year VulnDB QuickView report from Risk Based Security shows that 16.6 percent of the reported vulnerabilities received CVSSv2 (Common Vulnerability Scoring System) scores of between 9.0 and 10.0, which is a drop from previous years. However, the severity of the vulnerabilities disclosed still remains significant. "An important and compelling statistic is that of the 3,279 vulnerabilities not reported by CVE/NVD (Common Vulnerabilities and Exposures/National Vulnerability Database), 44.2 percent have CVSSv2 scores between 9.0 and… [Continue Reading] -

Hijack attack aims to grab bank details via routers
Publié: août 10, 2018, 5:44pm CEST par Ian Barker
Researchers at DDoS protection specialist Radware have uncovered an attack aimed at Brazilian bank customers that seeks to steal credentials via a compromised router. It employs malware that targets DLink DSL modem routers using exploits dating back to 2015. A malicious agent attempts to modify the DNS server settings in the routers of Brazilian residents, redirecting all their DNS requests through a malicious server. The malicious DNS server is then hijacking requests for the host name of Banco de Brasil and redirecting to a fake, cloned website hosted on the same malicious DNS server, which has no connection whatsoever to the… [Continue Reading] -

The most malware infected cities in the US
Publié: août 10, 2018, 3:11pm CEST par Ian Barker
A new report from EnigmaSoft -- makers of the SpyHunter anti-malware product -- reveals the US cities with the highest rates of malware infection. Systems in Atlanta, Orlando, and Denver are most likely to be infected, with Louisville, Witchita and Anchorage having the lowest infection rates. "It's hard to say exactly why one city or state has a higher rate of infection than others," says EnigmaSoft spokesperson Ryan Gerding. "There's a wide variety at the top of the list. Larger cities, smaller cities, and cities in every geographic area. The same is true for the least infected areas. New York… [Continue Reading] -

Free tool checks for critical open source vulnerabilities
Publié: août 9, 2018, 3:19pm CEST par Ian Barker
Every month details emerge of dozens of new security vulnerabilities, and open source software is not immune from these. In order to help companies stay up to date and ensure vulnerabilities are patched quickly, open source security specialist WhiteSource is launching a free tool that provides companies with immediate, real-time alerts on the 50 most critical vulnerabilities published in the open source community. The standalone CLI tool is free to use and available for anyone to download as a desktop application. Once downloaded, the Vulnerability Checker offers users the opportunity to import and scan any library and run a quick check… [Continue Reading] -

Organizations struggle with 'cyber hygiene’ basics
Publié: août 9, 2018, 1:01pm CEST par Ian Barker
Almost two-thirds of organizations are failing to use established benchmarks to set security baselines and are struggling to maintain visibility into their networks, according to a new report. The study, carried out for security and compliance specialist Tripwire by Dimensional Research, looks at how organizations are implementing security controls that the Center for Internet Security (CIS) refers to as 'cyber hygiene.' Almost two-thirds of the organizations admit they do not use hardening benchmarks, like CIS or Defense Information Systems Agency (DISA) guidelines, to establish a secure baseline. "These industry standards are one way to leverage the broader community, which is important… [Continue Reading] -

The rise of the IoT and artificial intelligence in industry [Q&A]
Publié: août 9, 2018, 11:23am CEST par Ian Barker
While the consumer IoT has captured the imagination with smart appliances and devices, the industrial Internet of Things (IIoT) is a rapidly growing market. According to Accenture, the IIoT market could add $14.2 trillion to the global economy by 2030. IIoT is also breathing new life into industries that are in great need of digital transformation, such as manufacturing, oil and gas, and more. As a result, artificial intelligence and machine learning are quickly becoming one of the biggest priorities for companies that want to make the most of their operational data to increase outputs using less energy and costs.… [Continue Reading] -

Most businesses struggle to get value from operational data
Publié: août 8, 2018, 5:03pm CEST par Ian Barker
Organizations increasingly depend on data to drive improvements in all areas of the enterprise. But a new survey shows that data volumes are affecting productivity, with 68 percent of respondents saying their organization has so much data they struggle to make use of it all. The study of 400 US and European business and IT professionals for Devo Technology, carried out by Vanson Bourne, shows that getting a unified view of information is challenging. 74 percent report their business is currently using different systems for real-time and historical data storage and analysis, and 95 percent say they face obstacles when… [Continue Reading] -

Manufacturing industry at greater risk of cyberattacks
Publié: août 8, 2018, 4:12pm CEST par Ian Barker
Manufacturing businesses are seeing higher-than-normal rates of cyberattack-related reconnaissance and lateral movement activity. This is due to the convergence of IT with IoT devices and Industry 4.0 initiatives, according to a new report from AI-powered attack detection specialists Vectra. "The interconnectedness of Industry 4.0-driven operations, such as those that involve industrial control systems, along with the escalating deployment of industrial internet-of-things (IIoT) devices, has created a massive, attack surface for cybercriminals to exploit," says Chris Morales, head of security analytics at Vectra. State affiliated attackers accounted for 53 percent of attacks on manufacturing, according to the according to the 2018… [Continue Reading] -

Facial recognition tool helps penetration testing
Publié: août 8, 2018, 3:34pm CEST par Ian Barker
Using fake social media profiles is a common technique among hackers in order to gain the confidence of targets and direct them to credential stealing sites. For security and penetration testing teams to replicate this is time consuming as often people have profiles across multiple sites. Ethical hacking specialist Trustwave is using a new tool called Social Mapper that can correlate profiles across multiple sites and make analyzing a person's online presence easier. Social Mapper is an open source tool that takes an automated approach to searching popular social media sites for names and pictures of individuals to accurately detect… [Continue Reading] -

Lure of cybercrime leads security professionals to become 'gray hats'
Publié: août 8, 2018, 11:31am CEST par Ian Barker
The attractions and profitability of the digital underworld are leading some security practitioners to become 'gray hats' and get involved in cybercrime according to a new report from Malwarebytes. The study carried out by Osterman Research finds that in the UK as many as one in 13 security professionals are perceived to be gray hats. Globally, mid-sized organizations (those with 500 to 999 employees) are getting squeezed the hardest, and this is where the skills shortage, and the allure of becoming a gray hat, may be greatest. In the US, security professionals believe that 7.9 percent of their fellow security… [Continue Reading] -

Uncovering the secret life of Twitter bots
Publié: août 6, 2018, 5:01pm CEST par Ian Barker
How do you know if you're reading tweets from a real person or a bot? As bot technology becomes more sophisticated it's increasingly hard to tell. Researchers at Duo Security have collected and analyzed data from 88 million public Twitter accounts using machine learning to spot the tactics used by malicious bots to appear legitimate and avoid detection. The analysis included the application of 20 unique account characteristics in a machine learning model to differentiate a human Twitter account, classified as 'genuine' in the study, from a bot. These characteristics include, among other things, the time between tweets, distinct tweet… [Continue Reading] -

Preempt allows organizations to detect and block hacker reconnaissance tools
Publié: août 2, 2018, 4:17pm CEST par Ian Barker
Increasingly cybercriminals are using their initial attacks to probe systems and look for other vulnerabilities or network resources that they can later exploit. Threat detection platform Preempt is launching new capabilities that allow enterprises to prevent lateral movement and unauthorized domain access due to the misuse of network credentials in reconnaissance tools. It will give organizations the ability to detect use of reconnaissance tools like BloodHound and other Lightweight Directory Access Protocol (LDAP) analysis tools. Additionally, Preempt enables security teams to respond in real time as tools are being used, to prevent a threat before it impacts the network. This… [Continue Reading] -

Carbon Black launches real-time security ops solution
Publié: août 2, 2018, 3:12pm CEST par Ian Barker
Security and operations teams often have no reliable way to assess the current state of endpoints across their enterprise. Lack of visibility is a major concern which leads to greater risk of a breach and a lack of information to take appropriate action after a problem occurs. The latest offering from Carbon Black, Cb LiveOps empowers organizations to ask questions of all their endpoints, take action to remediate in real time, and simplify operational reporting, all from a single platform. "Cb LiveOps changes the game for security operations," says Ryan Polk, Carbon Black's chief product officer. "With a single console… [Continue Reading] -

SMBs rank network security as top concern
Publié: août 2, 2018, 12:26pm CEST par Ian Barker
SMBs are just as likely to be attacked by cybercriminals as larger businesses, yet they lack the budgets and resources to secure their systems and deal with the aftermath of an attack. It’s not surprising then that a poll of more than 350 SMBs worldwide by cybersecurity specialist Untangle finds that firewall and network security are rated as the top security concerns, particularly as more systems move to the cloud. But less than 30 percent of SMBs surveyed have a dedicated IT security professional on their staff. 50 percent distribute IT security responsibilities across other roles. Although 75 percent of… [Continue Reading] -

Massive router hack used to spread CoinHive cryptomining script
Publié: août 2, 2018, 12:00pm CEST par Ian Barker
Researchers at Trustwave have uncovered an attack on tens of thousands of MikroTik routers which is being used to embed CoinHive cryptominer scripts in websites. A surge in CoinHive actvity in Brazil at the start of this week alerted researchers that something was happening. Further investigation showed that MicroTik devices were at the root of the problem and all were using the same CoinHive site key. MikroTik routers are used mainly by internet providers and big organizations, allowing the attack to reach large numbers of users. The attack is believed to have affected at least 70,000 routers in Brazil and… [Continue Reading] -

Android apps carry hidden Windows 10 malware
Publié: août 1, 2018, 5:16pm CEST par Ian Barker
Over 140 apps on the Google Play store have been discovered to contain malicious Windows executable files. Researchers at Palo Alto Networks found that among the infected apps, several had more than 1,000 installations and carried 4-star ratings. The Windows code is of course unable to infect Android devices, but as the researchers point out, "The fact that these APK files are infected indicates that the developers are creating the software on compromised Windows systems that are infected with malware. This type of infection is a threat to the software supply chain, as compromising software developers has proven to be… [Continue Reading] -

Spear phishing attack hits more than 400 industrial companies
Publié: août 1, 2018, 4:32pm CEST par Ian Barker
Researchers at Kaspersky Lab have detected a new wave of spear phishing attacks disguised as legitimate procurement and accounting letters, that have hit more than 400 industrial organizations. The emails have targeted approximately 800 employee PCs, mostly in Russian companies, with the goal of stealing money and confidential data from the organizations, which could then be used in new attacks. The emails are disguised as legitimate procurement and accounting letters, containing content that corresponded to the profile of the attacked organizations and took into account the identity of the employee -- the recipient of the letter. The attackers addressed the… [Continue Reading] -

HP launches flexible systems to enhance in-store retail
Publié: août 1, 2018, 3:56pm CEST par Ian Barker
Retailing presents some unique challenges for IT. Endpoints tend to be in fixed positions which has an effect on how staff interact with customers. HP is unveiling a new portfolio of devices and service offerings designed to enhance the retail experience by freeing the technology to move around. The HP Engage portfolio provides sleek, versatile, and secure systems to meet the evolving needs of retail and hospitality customers. The technology will be available through a Device-as-a-Service (DaaS) offering that makes it easier for retailers to acquire, support, and manage the technology they need to drive their business, as well as… [Continue Reading] -

Virtualization tool helps protect critical IP and high value assets
Publié: août 1, 2018, 3:14pm CEST par Ian Barker
While breaches often focus on consumer or payment information, they also put at risk key intellectual property and business assets. Virualization-based security specialist Bromium is announcing a new product called Protected App, which allows organizations to establish robust, end-to-end protection around their critical intellectual property (IP) and high value assets (HVAs). Protected App safeguards organizations' IP and HVAs from threats such as keylogging, kernel exploits, memory and disk tampering, and man-in-the-middle attacks, with sensitive applications being walled off from the endpoint. "Zero Trust as a concept is solid, but in practice it’s become a real barrier to user productivity," says… [Continue Reading] -

Businesses overestimate consumers' level of 'digital trust'
Publié: juillet 31, 2018, 4:53pm CEST par Ian Barker
How much do you trust businesses with your data? A new report from CA Technologies reveals 48 percent of consumers have stopped using the services of an organization because of a data breach. Yet the study, conducted by analysts Frost & Sullivan shows varying attitudes to data stewardship among businesses, with nearly half admitting to selling customer data, while claiming that data protection is paramount. This is highlighted by a 14-point gap between the Digital Trust Index of consumers (61 percent) and the perceptions by business decision makers and cybersecurity professionals (75 percent), showing mismatched perceptions among these audiences in… [Continue Reading] -

Managed detection and response supports internal security teams
Publié: juillet 31, 2018, 4:20pm CEST par Ian Barker
Companies are facing a constant battle against cyber threats, add to this a growing skills gap and security teams don't always have the staff or knowledge to effectively monitor and respond to threats. Automated detection and response company Fidelis Cybersecurity is launching a new managed detection and response (MDR) service to supplement in-house security resources. The 24x7 Fidelis MDR service provides a team of skilled security experts who use patented technology to analyze rich network and endpoint metadata, content, behavioral and asset characteristics, as well as enterprise IoT devices to aid in hunting and investigations. "With the risk enterprises face… [Continue Reading] -

FireEye uses machine learning to guard endpoints
Publié: juillet 31, 2018, 3:03pm CEST par Ian Barker
Traditional signature-based security solutions find it hard to keep up with the fast pace of malware development, so security companies are turning to other solutions. FireEye is launching a new version of its Endpoint Security product with the addition of a machine learning engine called MalwareGuard. MalwareGuard is the result of a two-year research project from FireEye's data scientists, plus testing in real-world incident responses. The MalwareGuard model is trained using advanced machine learning techniques to enable it to make intelligent malware classifications on its own and without human involvement. The machine learning model is trained using both public and… [Continue Reading] -

How automation can address the challenge of an aging workforce [Q&A]
Publié: juillet 31, 2018, 11:20am CEST par Ian Barker
A trend that's already started and will continue for at least the next decade is the loss of skilled workers as older employees start to retire. The effects are being felt across industries, with Gartner reporting the aging workforce as one of the biggest challenges to the utilities industry. What's more, the skills gap resulting from retiring employees leaving and entry-level employees entering the workforce is causing all industries to look at new solutions to solve the need for experienced and highly skilled workers. New technologies are gaining traction to help address low staffing levels and improve productivity. We spoke… [Continue Reading] -

93 percent are worried about online privacy
Publié: juillet 30, 2018, 3:53pm CEST par Ian Barker
Compared to a year ago 93 percent of people have the same amount or more concern about their online privacy. This is according to a survey of of 1,000 people across the US by VPN comparison site TheBestVPN. It finds 51 percent are worried about their information being stolen by hackers, and 26 percent about companies collecting and sharing data. In addition 14 percent worry about US government surveillance, while nine percent worry about foreign governments. Interestingly perceptions are different between the sexes, while men are more concerned about hackers, women worry more about online surveillance. There are also worries… [Continue Reading] -

AlgoSec launches updated security management for cloud and hybrid
Publié: juillet 30, 2018, 3:00pm CEST par Ian Barker
As businesses shift their systems to the cloud there is inevitably an increase in complexity that makes maintaining security more of a challenge. Security policy management specialist AlgoSec is launching a new version of its Security Management Solution to enable policy management across clouds and software-define networks. As well as support for a wide range of on-premise security devices, and AWS Security Groups, AlgoSec 2018.1 provides full end-to-end automaton of security policy change management processes for Microsoft Azure and Cisco ACI -- from planning, through risk and compliance checks, to deployment directly onto the device -- with zero touch. Other… [Continue Reading] -

SafeWallet aims to make cryptocurrency transactions easier and more secure
Publié: juillet 27, 2018, 3:06pm CEST par Ian Barker
Anyone who has dabbled in Bitcoin or other cryptocurrencies knows that the wallet process for storing and using coins can be a bit of a pain. Wallet users are often forced to use long private keys and mnemonic phrases to back up their crypto-assets, with most wallet apps asking users to print their private keys and mnemonic phrases onto a piece of paper, something which can easily be lost or stolen. That's set to change with the latest version of SafeWallet which lets users recover their crypto-asset wallets using a simple two-layer security system consisting of a QR code-based user… [Continue Reading] -

Free template helps businesses deal with data breaches
Publié: juillet 26, 2018, 4:56pm CEST par Ian Barker
Thanks to legislation like GDPR businesses need to report data breaches promptly or face large fines. However, in the heat of a security incident it can be easy to overlook vital procedures. Privileged account management specialist Thycotic is aiming to help with the launch of a free Incident Response Policy Template to help businesses take the right steps at the right time. "When a company is under attack, the reality is, if you do not already have an incident response plan in place, it's too late to build one without big consequences," says Joseph Carson, chief security scientist, at Thycotic.… [Continue Reading] -

Dashlane 6 adds an identity dashboard to help users understand their online security
Publié: juillet 26, 2018, 3:54pm CEST par Ian Barker
Password manager app Dashlane is launching the latest version of its software complete with a new Identity Dashboard, which provides a complete picture of a user's online security and clear actionable steps to improve it. The dashboard integrates dynamic new features like dark web monitoring, as well as a new Password Health assessment, that put people in complete control of their digital identities. "Managing digital identity has become too complex for almost everyone," says Emmanuel Schalit, CEO of Dashlane. "Massive breaches and data abuses -- like the ones at Facebook, Equifax, and Exactis -- affect us all, and while protecting… [Continue Reading] -

IT professionals increasingly worried about cyber attacks
Publié: juillet 26, 2018, 3:09pm CEST par Ian Barker
IT security professionals are more than twice as worried about data breaches and cyberattacks today than they were this time last year according to two new reports. The International Cyber Benchmarks Index and The Changing Face of Cyber Attacks, from the Neustar International Security Council (NISC), reveal the greatest threats as system compromises and ransomware, with 20 percent listing both as their primary concern Other worries are DDoS attacks (19 percent), financial theft (18 percent), and attacks on intellectual property (17 percent). 47 percent see DDoS attacks as increasingly harmful to their organization this year, compared to 38 percent last… [Continue Reading] -

Demand for dark web malware exceeds supply
Publié: juillet 25, 2018, 3:58pm CEST par Ian Barker
Malware writers have been using a free market model to sell their wares for some time. The success of this approach is clear from new research by Positive Technologies that finds demand for malware creation on the dark web is three times greater than supply. Demand for malware distribution is twice the supply. This mismatch of supply and demand has led to interest among criminals in new tools, which are becoming more readily available in the form of partner programs that include malware-as-a-service and malware distribution-for-hire. The analysis included 25 dark web sites, in Russian and English, with a total… [Continue Reading] -

Security remains top IT concern for SMBs
Publié: juillet 25, 2018, 3:22pm CEST par Ian Barker
Data breaches have serious consequences for SMBs and if not handled correctly can cause serious damage to the business. It's perhaps no surprise then that according to a survey from IT infrastructure company Kaseya security remains the top IT priority for SMBs with 54 percent citing it as their main concern in 2018, up 14 percent from 2017. Network issues are a concern too, 86 percent of respondents report that they experienced at least one IT network outage lasting longer than five minutes over the past year, and 45 percent reported having two to four outages lasting longer than five… [Continue Reading] -

The most successful phishing subject lines revealed
Publié: juillet 25, 2018, 12:24pm CEST par Ian Barker
We all like to think that we're smart enough not to fall for phishing emails, yet a surprising number of people do get caught out by them. A new report from security awareness training company KnowBe4 looks at the most successful phishing emails in the second quarter of 2018. The results show that hackers are playing into users' commitment to security, by using clever subject lines that deal with passwords or security alerts. "Hackers are smart and know how to leverage multiple psychological triggers to get the attention of an innocent victim. In today's world, it's imperative that businesses continually… [Continue Reading] -

Pulling back the curtain on the dark art of SEO [Q&A]
Publié: juillet 25, 2018, 11:29am CEST par Ian Barker
Search engine optimization (SEO), making sure that websites appear high in search results, can often seem like it exists in a sort of twilight zone somewhere between science and witchcraft. So, how does SEO work? What can it do for your business? And if you do any business at all online, can you afford not to do it? We spoke to Chris Rodgers, the founder and CEO of SEO agency Colorado SEO Pros to get answers to these and other questions. BN: Why is there such a mystique surrounding SEO? CR: SEO is really just not understood by most people,… [Continue Reading] -

Linux bots account for 95 percent of DDoS attacks as attackers turn to the past
Publié: juillet 24, 2018, 5:19pm CEST par Ian Barker
Cybercriminals are delving into the past to launch attacks based on some very old vulnerabilities according to the latest report from Kaspersky Lab, and they're using Linux to do it. In the second quarter of 2018, experts have reported DDoS attacks involving a vulnerability in the Universal Plug-and-Play protocol known since 2001. Also, the Kaspersky DDoS Protection team observed an attack organized using a vulnerability in the CHARGEN protocol that was described as far back as 1983. Despite the considerable length of service and the protocol's limited scope, many open CHARGEN servers can be found on the internet for things… [Continue Reading] -

Syncsort helps compliance for IBM i users
Publié: juillet 24, 2018, 3:58pm CEST par Ian Barker
IBM's i operating system -- originally known as OS/400 -- is still popular in many larger and mid-sized organizations, and it is of course subject to the same security and compliance challenges as other systems. Big data specialist Syncsort is launching additions to its Syncsort Assure family of products to help i users achieve compliance with GDPR and other legislation, and strengthen security with multi-factor authentication. "The trend to ensure organizations adequately protect personal data from theft and misuse has driven increasingly strict data privacy regulations like GDPR. This has fueled the rise of regulatory compliance to become a top… [Continue Reading] -

Endpoints leave industrial IoT vulnerable... Err, what's an endpoint?
Publié: juillet 24, 2018, 11:38am CEST par Ian Barker
Of over 200 respondents to a new survey, more than half report the most vulnerable aspects of their IIoT infrastructure as data, firmware, embedded systems, or general endpoints. But at the same time the survey by information security training organization SANS Institute reveals an ongoing debate over what actually constitutes an endpoint. The report finds that most organizations globally are forecasting between 10 and 25 percent growth in their connected devices. This growth rate will cause the systems connected to IIoT devices to double in size roughly every three to seven years. This will ultimately result in increased network complexity… [Continue Reading] -

DevOps -- sorting the leaders from the laggards
Publié: juillet 23, 2018, 6:01pm CEST par Ian Barker
What characterizes companies that do DevOps well compared to those that don't? A new study by Forrester for software testing company Tricentis aims to find out. The research looked at 94 quality metrics that were classified into four categories. Key findings are that an understanding of business risk is the most important determining factor of DevOps and Agile maturity. DevOps experts focus primarily on contextual metrics (e.g. requirements coverage) while others focused on 'counting' metrics (e.g. number of tests). Also experts are more likely to measure the user experience across an end-to-end transaction while others rely on application-specific or team-specific metrics. Among… [Continue Reading] -

Software supply chain attacks set to become a major threat
Publié: juillet 23, 2018, 3:06pm CEST par Ian Barker
According to a new study, 80 percent of IT decision makers and IT security professionals believe software supply chain attacks have the potential to become one of the biggest cyber threats over the next three years. The survey by Vanson Bourne for endpoint security company CrowdStrike finds two-thirds of the surveyed organizations experienced a software supply chain attack in the past 12 months. At the same time, 71 percent believe their organization does not always hold external suppliers to the same security standards. Only 37 percent of respondents in the US, UK and Singapore say their organization has vetted all… [Continue Reading] -

SUSE launches new enterprise Linux to help the move to software-defined infrastructure
Publié: juillet 19, 2018, 5:10pm CEST par Ian Barker
Businesses are increasingly running a mix of traditional and software-defined architectures and the launch of SUSE Linux Enterprise 15 is aimed at bridging the gap between the two. It's a modular operating system that helps make traditional IT infrastructure more efficient and provides an engaging platform for developers. It also aids in integrating cloud-based platforms into enterprise systems, merging containerized development with traditional development, and combining legacy applications with microservices. This 'mulitmodal' approach means organizations can easily deploy and transition business-critical workloads across on-premise and public cloud environments. To facilitate this it uses a common code base to ensure application… [Continue Reading] -

China, Russia and North Korea behind espionage-focused cyberattacks
Publié: juillet 19, 2018, 3:59pm CEST par Ian Barker
Cyberattacks come in many forms and from many sources, but a new report from endpoint security company Carbon Black reveals an increasing number originate from nation states with espionage as their goal. The findings show that 81 percent of incident response (IR) professionals say the majority of attacks come from Russia, while 76 percent say the majority come from China. These foreign actors are seeking more than just financial gain or theft -- 35 percent of IR professionals say the attackers' end goal is espionage. The financial industry is attacked most often according to 78 percent, 73 percent say healthcare… [Continue Reading] -

Half of retailers experience security breaches in the past year
Publié: juillet 18, 2018, 4:14pm CEST par Ian Barker
According to a new report, 52 percent of US retailers have suffered a data breach in the past year and 75 percent have had one at some time in the past. The latest Thales Data Threat Report, Retail Edition, also shows that US retail data breaches more than doubled from 19 percent in the 2017 survey to 50 percent, making retail the second most breached industry vertical this year. There is a continuing push towards new technology according to the report, 95 percent of US retail organizations will use sensitive data in an advanced technology environment (such as cloud, big… [Continue Reading] -

BetterCloud adds activity-based alerts to boost G Suite security
Publié: juillet 18, 2018, 3:43pm CEST par Ian Barker
SaaS management platform BetterCloud is launching a new activity-based alerts solution for Google to strengthen security for G Suite applications. The solution enables organizations to continuously monitor event-related activity for malicious or unauthorized behavior, and automates security responses to rapidly address security risks. "The explosion of SaaS has left organizations with far too many applications to manage and a deluge of data to rein in," says David Politis, CEO and founder of BetterCloud. "Every second of every minute, people are taking actions within SaaS applications such as downloading files, forwarding emails, installing external applications and more. Identifying and assessing anomalous… [Continue Reading] -

Credential stuffing costs businesses over $5 billion a year
Publié: juillet 18, 2018, 3:04pm CEST par Ian Barker
When usernames and passwords are exposed through a data breach or attack on users, criminals harvest these credentials and test them on a wide range of websites and mobile applications, a practice known as 'credential stuffing'. A new report by security and anti-fraud specialist Shape Security looks at the lifecycle of stolen credentials and at the damage their use can cause. The findings show that an average of 15 months elapses between the day credentials are compromised and the day the loss is reported by an organization. This is the most dangerous window of time as criminals can carry out… [Continue Reading] -

Microsoft overtakes Facebook as the #1 spoofed brand
Publié: juillet 17, 2018, 4:54pm CEST par Ian Barker
Phisherfolk love to try to trick people into thinking they are a major brand in order to get them to reveal passwords or personal data. New research from Vade Secure reveals that in the second quarter of this year Microsoft has supplanted Facebook as the most spoofed brand. The social network drops two places to third, behind perennial phishing favorite PayPal. Microsoft unseated incumbent Facebook for the top spot, boosted by a 57 percent increase in phishing URLs. With adoption of Microsoft Office 365 surging, it's clear that it has become a major target for corporate phishing attacks. PayPal moved… [Continue Reading] -

Poor infrastructure monitoring leads to outages, slowdowns and missed targets
Publié: juillet 17, 2018, 4:25pm CEST par Ian Barker
Almost 90 percent of enterprises fail to meet SLA targets due to inadequate monitoring of IT infrastructure, according to a new report. The study by Dimensional Research for infrastructure performance management specialist Virtual Instruments, reveals that 61 percent of respondents report that they experience four or more significant application outages and/or slowdowns each year. This is despite 71 percent using more than five IT infrastructure monitoring tools, but more than half of respondents (54 percent) note that they lack full application and infrastructure visibility. 59 percent say that their application performance issues are related to the underlying infrastructure, and a… [Continue Reading] -

Data lakes improve business decision making
Publié: juillet 17, 2018, 3:29pm CEST par Ian Barker
The data lake has long been a powerful tool for data scientists and engineers. But today’s business environment often requires users without coding or scripting skills to access the data stored in lakes. A new study from analytics and business intelligence specialist Arcadia Data looks in detail at the use of data lakes and the analytical tools that surround them. The results show that most organizations (62 percent) deploy their lakes on Hadoop clusters. 61 percent of all respondents said, "business users can author and edit reports and dashboards without coding." In addition 76 percent of respondents believe, "BI/analytics for… [Continue Reading] -

New solution offers network intrusion detection for containers
Publié: juillet 17, 2018, 1:26pm CEST par Ian Barker
Security-as-a-service provider Alert Logic is using the AWS Cloud Summit to launch an industry first network intrusion detection system (IDS) for containers. It’s available in Alert Logic Cloud Defender and Threat Manager solutions and is able to inspect network traffic for malicious activity targeting containers, providing organizations with faster detection of compromises and reduced risk of attacks to cloud workloads on Amazon Web Services. "Without real-time detection capabilities, attackers and intruders can lurk within containers installing trojans, malware, ransomware and cryptominers or even corrupting and exfiltrating data," says Chris Noell, senior vice president, engineering at Alert Logic. "Network intrusion detection… [Continue Reading] -

McAfee launches new enterprise security portfolio
Publié: juillet 17, 2018, 12:23pm CEST par Ian Barker
As businesses move more of their systems into the cloud the protection they require to keep them safe needs to be more flexible. Cybersecurity specialist McAfee is responding to this challenge with the launch of McAfee MVISION, a portfolio of products which strengthens the device as a control point in security architectures, delivers simplified management, stronger Windows security, behavior analytics, and threat defense for Android and iOS devices. The MVISION portfolio is made up of three elements, McAfee MVISION ePO, McAfee MVISION Endpoint, and McAfee MVISION Mobile. MVISION ePO is a SaaS offering that delivers a simplified, centralized point of… [Continue Reading] -

Cylance unveils Smart Antivirus for consumers
Publié: juillet 12, 2018, 4:07pm CEST par Ian Barker
Traditional signature-based antivirus solutions struggle to cope with the pace of change in today's malware world. But while enterprises have had access to sophisticated machine learning solutions for a while these have largely been denied to consumers. Now though Cylance is launching an AI-based antivirus solution aimed at the domestic internet user. Cylance Smart Antivirus provides predictive security to spot and block threats before they have a chance to run without affecting device performance or disrupting the user. "Consumers deserve security software that is fast, easy to use, and effective," says Christopher Bray, senior vice president of Cylance Consumer. "The… [Continue Reading] -

AI solution delivers accurate voice authentication
Publié: juillet 12, 2018, 3:36pm CEST par Ian Barker
There's growing interest in biometric security solutions as passwords are increasingly seen as outmoded and at risk from phishing and other attacks. Biometric solutions provider ID R&D is launching a new version of its voice biometric security solution, IDVoice. Enhancements to the product allow it to deliver what is claimed to be the industry's fastest and most accurate text-independent biometric verification. "ID R&D is excited to deliver this next-generation approach to voice biometrics which merges robust security and functional usability into a single solution," says Konstantin Simonchik, co-founder and chief science officer of ID R&D. "Through groundbreaking algorithms comprised of… [Continue Reading] -

Business priorities lead to multi-cloud strategies
Publié: juillet 12, 2018, 3:04pm CEST par Ian Barker
A new report finds that 86 percent of businesses describe their cloud strategy as multi-cloud today, with performance and innovation rising above cost savings as the top measures of success. In addition the report, produced by Forrester for enterprise cloud specialist Virtustream, reveals that 60 percent of enterprises are now moving or have already moved mission-critical applications to the public cloud. Almost half of enterprises surveyed report at least $50 million in annual cloud spending. Also a vast majority of respondents plan to increase or maintain their investments over the next two years, including resources devoted to internal staff and… [Continue Reading] -

New solution provides adaptive authentication for Windows and Mac
Publié: juillet 11, 2018, 3:48pm CEST par Ian Barker
Once a user is logged on, they typically have access to a wealth of sensitive applications and systems. Strong authentication at the front door therefore helps boost the overall security of the entire system. A new adaptive authentication system developed by identity automation specialist SecureAuth Corp + Core Security, is available for Windows and Mac systems enabling adaptive and multi-factor authentication for users logging into servers, desktops, and laptops. Adaptive authentication provides the highest level of identity security without negatively impacting the user as risk checks -- such as device recognition, geolocation, and threat detection services -- are done behind… [Continue Reading] -

80 percent of IT decision makers say outdated tech is holding them back
Publié: juillet 11, 2018, 3:21pm CEST par Ian Barker
A study by analysts Vanson Bourne for self service automation specialist SnapLogic looks at the data priorities and investment plans of IT decision makers, along with what's holding them back from maximizing value. Among the findings are that 80 percent of those surveyed report that outdated technology holds their organization back from taking advantage of new data-driven opportunities. Also that trust and quality issues slow progress, with only 29 percent of respondents having complete trust in the quality of their organization’s data. Nearly three-quarters (74 percent) say they face unprecedented volumes of data but struggle to generate useful insights from it,… [Continue Reading] -

Malware infections drop during World Cup matches -- Result!
Publié: juillet 11, 2018, 12:44pm CEST par Ian Barker
Even if you’re not a soccer/football fan, it probably hasn't escaped your notice that there's a World Cup going on in Russia at the moment. We expect big sporting events to be exploited to launch phishing and malware campaigns but researchers at Enigma Software have spotted an interesting new phenomenon -- malware infections actually drop on match days. EnigmaSoft looked at malware infections reported by its SpyHunter anti-malware software installed on customers' computers since the World Cup began last month. On average, malware infections dropped 19.88 percent in countries whose team was playing. This suggests people are switching off their… [Continue Reading] -

100 percent of corporate networks vulnerable to insider attacks
Publié: juillet 10, 2018, 4:54pm CEST par Ian Barker
Penetration testing company Positive Technologies has released some alarming figures surrounding the vulnerability of corporate networks to insider attacks. During testing performed as an internal attacker, the company's researchers were able to obtain full control of infrastructure on all the corporate networks they attempted to compromise. Only seven percent of systems were assessed as having 'moderate' difficulty of accessing critical resources. Penetrating the network perimeter has become easier over time too. The difficulty of accessing the internal network was assessed as 'trivial' in 56 percent of tests in 2017, compared to 27 percent in 2016. On average, Positive Technologies testers… [Continue Reading] -

How much does Google know about you?
Publié: juillet 10, 2018, 1:38pm CEST par Ian Barker
We all know that Google collects data and uses it to sell adverts. But just how well does Google know you? VPN service comparison site TheBestVPN has created a full guide to how the corporation tracks you and what it does with the information. Google's apps give the company a wealth of information on you, from the personal details that make up who you are, to your interests, your past travels, and your future goals. But this is more than just facts and figures. Thanks to facial recognition in Google photos, the search giant probably has a pretty good idea of… [Continue Reading] -

Two out of three IT pros don't comply with all data laws
Publié: juillet 10, 2018, 12:42pm CEST par Ian Barker
According to a new study, 68 percent of IT professionals believe their organizations are failing to carry out all procedures in line with data protection laws. The report from digital security specialist Gemalto also shows 65 percent of companies are unable to analyze all the data they collect and only just over half (54 percent) know where all of their sensitive data is stored. The ability of business to analyze the data they collect varies worldwide with India (55 percent) and Australia (47 percent) best at using the data they collect. In fact, despite nine in 10 (89 percent) global… [Continue Reading] -

The importance of cybersecurity training for business
Publié: juillet 4, 2018, 1:08pm CEST par Ian Barker
While businesses spend a lot of time and effort putting up technical defenses to protect their systems, often the weakest spot is the users. Employees can do harm to the business by visiting infected websites, responding to phishing emails, using business email through public Wi-Fi and more. Spam filtering service EveryCloud has put together an infographic looking at why it’s therefore important for companies to offer cybersecurity training. It looks at the things that can go wrong, including using found USB sticks, poor password habits, and falling for phishing attacks. It also looks at the effects and costs of the… [Continue Reading] -

77 percent of industrial organizations worried about cybersecurity incidents
Publié: juillet 3, 2018, 4:34pm CEST par Ian Barker
Information technology and operational technology are gradually moving closer together thanks to wider connectivity of OT with external networks, and the growing number of industrial IoT devices. While this boosts the efficiency of industrial processes, it also presents new risks and vulnerabilities according to a new report from Kaspersky Lab. The company carried out a survey of 320 global professionals with decision-making power on OT and industrial control system (ICS) cybersecurity from 25 countries. 77 percent of respondents say that their organization is likely to become the target of a cybersecurity incident involving their industrial control networks. Of the concerns… [Continue Reading] -

Over 90 percent of endpoint security incidents involve legitimate binaries
Publié: juin 29, 2018, 3:06pm CEST par Ian Barker
Cybercriminals use a variety of tactics to cloak their activity and that includes using trusted tools, like PowerShell, to retrieve and execute malicious code from remote sources. A new report from eSentire reveals that 91 percent of endpoint incidents detected in Q1 2018 involved known, legitimate binaries. "eSentire Threat Intelligence data shows heavy use of legitimate Microsoft binaries, such as PowerShell and mshta.exe, popular tools for downloading and executing malicious code in the initial stages of a malware infection," says Eldon Sprickerhoff, founder and chief security strategist, eSentire. "PowerShell can also be leveraged by adversaries to reduce their on-disk footprint… [Continue Reading] -

Shift to DevOps leads to more time spent troubleshooting
Publié: juin 28, 2018, 4:09pm CEST par Ian Barker
A new report from log management platform Scalyr reveals that as organizations shift from more traditional architectures to microservices, they release software more frequently, but spend more time troubleshooting issues. The State of DevOps Observability Report, based on a survey of 155 software development practitioners, finds that organizations are shifting away from traditional, monolithic architectures, with three-quarters of survey respondents delivering at least some of their applications and more than one-third delivering most of their applications as microservices. However, this shift has put pressure on DevOps observability. Despite having multiple visibility tools, respondents who deliver software in this modern way… [Continue Reading] -

Comodo CA launches IoT security platform
Publié: juin 28, 2018, 3:20pm CEST par Ian Barker
Certificate authority Comodo CA is expanding out of its traditional area to launch a new platform designed to secure Internet of Things devices. Hackers increasingly target IoT devices that have no security embedded and exposed vulnerabilities. The new Comodo CA IoT unified portal directly addresses this problem by enabling trusted, third-party, mutual authentication of devices to networks. IoT PKI (Public Key Infrastructure) Manager is available across a wide range of industries and applications including industrial automation, medical devices, automotive, telecommunications, smart city/smart buildings and in consumer electronics. "The continued use of self-signed certificates, shared keys and default passwords for IoT… [Continue Reading] -

One in every 17 mobile devices is used to conduct bad bot attacks
Publié: juin 28, 2018, 1:17pm CEST par Ian Barker
Cybercriminals are using mobile devices to avoid detection and execute a number of nefarious acts, according to a new report. The study from bot mitigation specialist Distil Networks finds 5.8 percent -- around one in 17 -- of all mobile devices across six major cellular networks are used in such automated attacks and represent eight percent of all bad bot traffic. The bad bot traffic is deployed against businesses with a web presence, to carry out acts that include web scraping, brute force attacks, competitive data mining, online fraud, account hijacking, data theft, spam and digital ad fraud. Distil sampled… [Continue Reading] -

70 percent would leave a job if their digital activity was secretly monitored
Publié: juin 28, 2018, 12:42pm CEST par Ian Barker
A new Harris Poll commissioned by insider threat detection company Dtex Systems looks at employee attitudes towards the monitoring of their digital activities. Carried out in the wake of data collection, monitoring and privacy scandals at Facebook and elsewhere, it shows that 45 percent of Americans believe it is at least sometimes acceptable for employers to monitor employees' digital activities to protect against security threats and data breaches. A much higher percentage (64 percent) believe that employers have the right to monitor employees' digital activities on personal or work-issued devices used to conduct work for security purposes, as long as… [Continue Reading] -

New tool enables secure enterprise podcasting
Publié: juin 27, 2018, 3:35pm CEST par Ian Barker
As workforces are increasingly spread over multiple locations, in the field or working from home, keeping them up to date and engaged with company news can be a tough task. Increasingly managers are turning to podcasts to help keep sales teams competitive and build corporate community and business alignment among employees, partners and customers. Enterprise communications company uStudio is launching a podcasting solution purpose-built for private enterprise communications. Called uStudio Enterprise Podcasting, it comprises a fully-customizable mobile application with channels, user subscription and off-line listening options, as well as multi-tier content security. Content administrators can easily manage and publish podcasts… [Continue Reading] -

Dashlane launches scanning tool to help you protect online accounts
Publié: juin 27, 2018, 3:04pm CEST par Ian Barker
We all sign up to online accounts for various things but over time it can become hard to remember which address you used for each site, what password you used or indeed whether you’ve previously signed up to a site at all. Password management specialist Dashlane is launching a new feature for mobile users of its password manager called Inbox Security Scan, to give people an insight into the current state of their online accounts. It's available for Gmail on iOS and Android, as well as Outlook, Hotmail, MSN, and Live.com on Android. It scans your email inbox, finds all… [Continue Reading] -

Coin mining malware grows by over 600 percent as criminals 'infect and collect'
Publié: juin 27, 2018, 1:26pm CEST par Ian Barker
A new report from McAfee Labs has seen coin mining malware grow by 629 percent in the first quarter 2018 as criminals seek to cash in on cryptocurrency trends. On average the company has seen five new threat samples every second, including growth in cryptojacking and other cryptocurrency mining malware, and notable campaigns demonstrating a deliberate drive to technically improve on the most sophisticated, established attacks of 2017. "Cybercriminals will gravitate to criminal activity that maximizes their profit," says Steve Grobman, chief technology officer at McAfee. "In recent quarters we have seen a shift to ransomware from data-theft, as ransomware… [Continue Reading] -

Boards focus on security awareness post WannaCry
Publié: juin 27, 2018, 10:41am CEST par Ian Barker
Awareness of cybersecurity at board level is growing as last year's WannaCry attack has highlighted the need to guard against attacks. The research, conducted by Vanson Bourne, as part of an international survey of 500 businesses in the UK, France, Germany and the USA, was commissioned by endpoint protection specialist SentinelOne. Half of all respondents say that there is more visibility of attacks at board level, as reported bottom line losses by companies like Maersk have highlighted the economic cost of ransomware. The biggest board level reaction to ransomware has been on user education, with 54 percent of respondents saying… [Continue Reading] -

New portal offers greater visibility into security gaps
Publié: juin 26, 2018, 4:02pm CEST par Ian Barker
It can be difficult for security teams to identify the weak spots in their organization's controls that put the security of the business at risk. Managed security services provider Proficio is addressing this by launching a new version of its ProView Plus consumer portal that includes ThreatInsight risk scoring. The ThreatInsight score is calculated based on Proficio's proprietary technology and provides customers with intelligent recommendations on how to improve their security posture. It also allows customers to see how their score compares to Proficio’s complete customer base and their specific industry sector. It uses a dashboard that leverages advanced analytics… [Continue Reading] -

SMBs are underprepared for cyberattacks
Publié: juin 26, 2018, 3:17pm CEST par Ian Barker
No business is immune from cyber attack, and smaller companies are often targeted as they lack the resources to put into first class protection. A new survey by cybersecurity company Webroot of 600 IT decision makers (ITDMs) at small- to medium-sized businesses, finds that the attacks organizations believed themselves to be most susceptible to in 2017 are rapidly shifting in 2018, while businesses still feel underprepared. Phishing is now the number one attack that ITDMs believe their organizations are most susceptible to in 2018. Fear of phishing is up from number three last year, with new forms of malware dropping… [Continue Reading] -

Free benchmarking tool helps developers understand their apps
Publié: juin 26, 2018, 12:18pm CEST par Ian Barker
The performance of an app can have a big impact on how users see the business behind it. For developers therefore it's important to understand how their app will work in the real world. To help with this, mobile analytics specialist Adjust is launching a benchmarking tool that will enable companies to understand how well their app is performing across markets and platforms. "Due to fierce competition, app marketing teams no longer focus solely on their own segments, but seek bigger growth in international markets," says Christian Henschel, CEO of Adjust. "Our benchmarking tool enables mobile marketers to define and benchmark… [Continue Reading] -

Consumers don't fully trust digital assistants
Publié: juin 26, 2018, 11:16am CEST par Ian Barker
Given recent scares about digital assistants recording conversations, it's perhaps not surprising that levels of trust in these devices are not high. The latest State of Digital Lifestyles survey from Limelight Networks reveals that adoption of digital assistants is highest in the US where 35 percent of consumers currently own one, however, these consumers still have major trust issues with the devices. Security and possible hacking into digital assistants is a concern 43 for percent, and 46 percent express concerns about data privacy. When it comes to performing specific tasks, less than a third (31 percent) would fully trust a… [Continue Reading] -

How we've come to rely on voice search
Publié: juin 25, 2018, 4:09pm CEST par Ian Barker
Voice search has become increasingly popular in the last few years and figures from Seotribunal show that around half of teens and 41 percent of adults are using it in their day-to-day activities. That number is still rising too with 1.8 million people expected to be using voice search daily by 2021. Seotribunal has put together an infographic showing how the technology is being used and more. In 2017 people were most likely to use voice search at home, but now they're utilizing it in all kinds of places including restaurants, public transport and at work. 52.8 percent use it… [Continue Reading] -

Average initial coin offering has at least five vulnerabilities
Publié: juin 25, 2018, 3:36pm CEST par Ian Barker
Every month there are fresh cryptocurrencies springing up, but new research by Positive.com has discovered an average of five separate vulnerabilities in each initial coin offering (ICO) project examined in 2017. What's more, 47 percent of the ICO vulnerabilities uncovered were medium to high severity. Just one vulnerability is enough for attackers to steal investors' money and do irreparable damage to corporate reputation. Total investment in ICOs exceeded $5 billion in 2017, with the first quarter of 2018 showing no sign of slowing down. With such large sums of money available, incentives for cybercriminals are high, and seven percent of… [Continue Reading] -

Battery saving app infects over 60,000 Android devices
Publié: juin 21, 2018, 3:59pm CEST par Ian Barker
Researchers at RiskIQ have uncovered a scam app that seeks to steal information and launches advert clicking to make money for the scammers. The app is advertised as a battery saver. The twist here is that though it will actually do what it says and cut battery use, it does a lot of nasty stuff too. "Many of the millions of scams we crawl at RiskIQ are relatively straightforward, but every once in a while we find something unique," say researchers Aaron Inness and Yonathan Klijnsma writing on the company's blog. "Usually, scams point to other web pages, but in… [Continue Reading] -

New tool provides email protection for Office 365
Publié: juin 21, 2018, 3:13pm CEST par Ian Barker
Office 365's dominant share of the online business tools market has made it a popular target for cybercriminals launching phishing and malware attacks. To offer users extra protection, email security specialist Vade Secure is launching a new solution that's fully integrated into Office 365 and offers filtering powered by artificial intelligence. Vade Secure for Office 365 is closely aligned with Microsoft's partner-first, cloud-first strategy. It's built from the ground up with a cloud-native, API-based architecture, natively integrates with Office 365 and runs on Microsoft Azure. It blocks advanced attacks using machine learning models that perform real-time behavioral analysis of the… [Continue Reading] -

Attackers use hidden tunnels to steal financial data
Publié: juin 20, 2018, 3:00pm CEST par Ian Barker
Global financial services organizations are targeted by sophisticated cyber attackers in an attempt to steal critical data, according to a new report. The study from threat hunting company Vectra says attackers build 'hidden tunnels' masquerading as other web traffic to break into networks and access critical data and personal information. These tunnels are used to remotely control an attack and steal data while remaining largely undetected. The report shows that while financial services firms didn't experience the same volume of breaches as other industries, they still face considerable risk as lucrative targets of attackers in search of a windfall. "Every… [Continue Reading] -

Average UK home has more than £2,000 worth of broken gadgets
Publié: juin 20, 2018, 1:16pm CEST par Ian Barker
UK households are home to thousands of pounds' worth of broken gadgets, according to new research from technology retailer Laptops Direct. The survey of more than 1,000 UK adults shows that the average household is currently harboring £2,460 of broken technology and gadgets. Smartphones are the most common items in these technology graveyards with 78 percent holding onto them even though they’re broken. A damaged or malfunctioning laptop is in the home of 62 percent of those surveyed and 59 percent have broken iPads and tablets. There's also a lack of urgency when it comes to getting gadgets fixed. 37… [Continue Reading] -

Automation of endpoint security is top priority for IT pros
Publié: juin 20, 2018, 11:28am CEST par Ian Barker
A new survey of IT professionals finds that automating endpoint detection and response processes is a top priority. The study from cyber security training company, the SANS Institute, shows 42 percent of the IT professionals surveyed say their endpoints had been breached, and 82 percent of that group say their breaches involved desktops, while 69 percent cited corporate laptops and 42 percent claimed involvement of employee-owned laptops (42 percent). The top threat vectors for these exploited endpoints were web drive-bys (63 percent), social engineering/phishing (53 percent) and ransomware (50 percent). But while respondents are relying on the security capabilities they… [Continue Reading] -

IBM celebrates 10 years of DevOps with new releases
Publié: juin 19, 2018, 4:29pm CEST par Ian Barker
Over the past decade, DevOps techniques have helped to transform software development teams with a new and more agile approach. But now companies are starting to move beyond the standard DevOps approach in what is being called 'Day 2' DevOps, a world that emphasizes scalability and teamwork. In such environments, development teams shift one way, operations teams shift the other and together they can deliver and manage multiple, complex applications at the same time. In order to meet the challenges of Day 2 DevOps, IBM is making two new announcements -- IBM UrbanCode Deploy 7.0 and IBM UrbanCode Velocity 1.0.… [Continue Reading] -

Website attacks up as smaller businesses are targeted
Publié: juin 19, 2018, 2:47pm CEST par Ian Barker
Website attacks increased 14 percent in the first quarter of 2018 compared to the final quarter of 2017 as cybercriminals set their sights on independent websites and small businesses. Figures from website security specialist SiteLock show that one percent of sampled sites are infected at any one time. This may not sound much, but it means 18.7 million sites are infected. While attacks on big business typically make the headlines, smaller companies shouldn't believe that they're too small to be hacked. In fact smaller companies are often the target of choice for cybercriminals thanks to lower levels of protection. Malicious… [Continue Reading] -

Fans targeted by phishing campaign as World Cup gets underway
Publié: juin 18, 2018, 3:10pm CEST par Ian Barker
As the FIFA World Cup tournament enters its second week, cybercriminals are using a phishing campaign to trick fans into opening an infected attachment. Emails identified by Check Point attempt to lure would-be victims into downloading a schedule of fixtures and a result tracker, but doing so will prove to be an own goal. When opened, the attachment uses a malware variant called 'DownloaderGuide,' a known downloader of potentially unwanted programs (PUPs) that is most commonly used as an installer for applications like toolbars, adware or system optimizers. Check Point researchers have found that in total the campaign includes nine… [Continue Reading] -

72 percent of people fear the theft of their data from company hacks
Publié: juin 18, 2018, 11:17am CEST par Ian Barker
A new survey of 2,000 UK adults reveals that almost three quarters worry that their details will be stolen every time they hand over bank details and email addresses to companies. What’s more around one in five have already had their data stolen according to the study commissioned by BullGuard, and almost a third of these had been out of pocket as a result. "As the results show, the way companies use data really is a huge concern for customers," says Paul Lipman, CEO at BullGuard. "This has particular relevance in the wake of the Dixons Carphone hack in which… [Continue Reading] -

Most organizations are not fully embracing DevOps
Publié: juin 14, 2018, 4:24pm CEST par Ian Barker
Although many businesses have begun moving to DevOps-style processes, eight out of 10 respondents to a new survey say they still have separate teams for managing infrastructure/operations and development. The study by managed cloud specialist 2nd Watch of more than 1,000 IT professionals indicates that a majority of companies have yet to fully commit to the DevOps process. 78 percent of respondents say that separate teams are still managing infrastructure/operations and application development. Some organizations surveyed are using infrastructure-as-code tools, automation or even CI/CD pipelines, but those techniques alone do not define DevOps. Nearly 60 percent say they are using… [Continue Reading] -

Microsoft Office gets a facelift to improve usability
Publié: juin 13, 2018, 5:11pm CEST par Ian Barker
Microsoft has announced that it's giving its flagship Office suite a makeover designed to deliver a balance of 'power and simplicity'. The updates apply to Office.com and Office 365 and will be rolled out over the next few months, the company says it will 'test and learn' as it goes -- those of a cynical mind might see that as code for letting users find the bugs. The changes are based on a 'Three Cs' -- customers, context and control -- principle, designed to focus on the features people use most and making it easier to access them. "Office is… [Continue Reading] -

Data science moves away from big data towards containers and cloud
Publié: juin 13, 2018, 4:40pm CEST par Ian Barker
Traditional Hadoop-style big data is giving way to cloud and container solutions like Docker, according to the results of a new survey. The State of Data Science survey, carried out by Python data science platform Anaconda, among over 4,000 of its users, shows that Docker now makes up 19 percent of data science platforms, beating Hadoop/Spark with 15 percent and Kubernetes at 5.8 percent. This is partly due to the fact that what was 'big data' in 2005, when Hadoop began, now easily fits into a single server's memory and there is now a wide range of alternatives to building… [Continue Reading] -

Free Chrome extension helps internet users spot fake news
Publié: juin 13, 2018, 3:34pm CEST par Ian Barker
The rise of fake news has affected many people's faith in the internet as a reliable source. In order to help with the problem, Adblock Plus maker eyeo is launching a new browser extension called Trusted News. Available free for Chrome browsers, the extension works by checking domains, websites, and news sources against the world's largest network of fact-checking databases. After installing the Trusted News extension, users can navigate to websites as usual but they will now notice a green check-mark or other flags on the extension indicating the nature of the sources used by that site. Besides a green… [Continue Reading] -

UK tech sector gets £2.3 billion investment boost
Publié: juin 13, 2018, 1:39pm CEST par Ian Barker
As part of London Tech Week, 1,600 new jobs and billions of pounds of investment into the UK economy have been announced at an event hosted by Prime Minister Theresa May in Downing Street. Private sector funding comes from companies including Salesforce, which is investing £1.9bn in the UK over the next five years, this will include the opening of its second UK data center in 2019. Mubadala is launching a £300m European investment fund based in the UK, and NTT data is investing £41m to open a new office and Innovation Centre, creating up to 200 jobs over the… [Continue Reading] -

95 percent of parents worry about the risks children face from online games
Publié: juin 13, 2018, 11:10am CEST par Ian Barker
Although a large majority of parents (95 percent) say they’re concerned about the risks online gaming poses, they admit to allowing games to entertain their offspring. A new study by McAfee finds 92 percent of parents allow their children to play at least one hour of video games every day, with eight percent admitting that they allow their children to play more than five hours a day. On average, children play video games for 2.13 hours a day or nearly 15 hours a week. More concerning is that 62 percent of children play games where they directly interact with other… [Continue Reading] -

Two thirds of organizations can't deliver on DevOps
Publié: juin 12, 2018, 4:48pm CEST par Ian Barker
According to a new report, 74 percent of respondents believe DevOps enablement capabilities are essential, very important, or important for their organization. Yet only 33 percent believe their organization has the ability to deliver those capabilities. This is according to research carried out by the Ponemon Institute and sponsored by digital business specialist Embotics, which analyzed the results of a survey of more than 600 individuals responsible for cloud management at organizations with an average budget of $147 million for managing hybrid cloud operations. A sizeable 46 percent of respondents say that their organization's cloud consumption model is 'cloud direct,'… [Continue Reading] -

New solution helps secure infrastructure across OT and IT environments
Publié: juin 12, 2018, 4:11pm CEST par Ian Barker
Historically, infrastructure systems and operational technology (OT) were designed to work in isolation from IT. But in the modern world these environments are increasingly converged and that can open up new attack routes. Cyber exposure specialist Tenable is launching a new solution to manage Cyber Exposure holistically across IT and OT systems. This is based on enhancements to the Tenable.io platform and Industrial Security, an asset discovery and vulnerability detection solution for OT systems, delivered in partnership with Siemens. Features include smart scanning which builds an intelligence layer on top of active scanning and passive network monitoring to assess IT… [Continue Reading] -

Business use of machine data analytics growing faster than expected
Publié: juin 12, 2018, 3:30pm CEST par Ian Barker
New research commissioned by cloud-native analytics platform Sumo Logic from 451 Research, reveals that the degree to which non-IT roles and functions are using machine data analytics for business value is growing faster than anticipated. The findings show the more software-centric a company is, the more likely it is to have 100+ people who use machine data analytics at least once a week, indicating that these companies are recognizing the value of machine data analytics. These businesses are also more likely to have line-of-business users integrating machine data with data from BI tools, to gain the visibility they need to… [Continue Reading] -

IT decision makers limit cloud use due to difficulties with compliance
Publié: juin 12, 2018, 2:46pm CEST par Ian Barker
A new study shows that 87 percent of IT Decision Makers (ITDMs) limit their use of the cloud because of the complexity of managing regulatory compliance. According to the research by WinMagic, which spoke to ITDMs in Germany, India, the UK and US, 24 percent say this means they only work with a single cloud vendor in their infrastructure, rather than exploit the benefits of a multi-cloud environment. Among other findings are that 63 percent feel the need to use multiple infrastructure management tools is a hugely restricting factor in their use of multiple cloud vendors. Looking specifically at managing… [Continue Reading] -

Media and entertainment companies have riskier mobile apps
Publié: juin 12, 2018, 1:20pm CEST par Ian Barker
As the world increasingly turns to mobile devices to access the internet and conduct business, so firms are eager to put out their own apps. But new research from security ratings company BitSight reveals that many companies may be rushing out apps that have vulnerabilities which could lead to data leakage, privilege abuse, unencrypted personally identifiable information (PII), and credential theft. BitSight examined representative samples of more than 1,000 companies in five industry sectors that offer mobile applications on iOS and Android. It found over half of the companies studied in the media and entertainment industry offer risky mobile applications.… [Continue Reading] -

Cryptomining still tops the malware charts for May
Publié: juin 8, 2018, 3:57pm CEST par Ian Barker
Currency miners continue to top the malware charts according to Check Point Software's latest Global Threat Index. May 2018 marks the fifth consecutive month where cryptomining malware has dominated Check Point's index. The Coinhive cryptominer impacted 22 percent of organizations globally during May -- up from 16 percent in April, an increase of nearly 50 percent. Coinhive retained the top spot as the most prevalent malware with Cryptoloot -- another crypto-mining program -- ranked second with a global reach of 11 percent. For the second consecutive month, the Roughted malvertising malware came in third, affecting eight percent of organizations. Check… [Continue Reading] -

71 percent of IT pros believe they can hack any organization
Publié: juin 7, 2018, 5:56pm CEST par Ian Barker
Using one of four common attack vectors, 71 percent of surveyed IT professionals believe they could successfully hack any organization. Based on a survey carried out among attendees to the RSA Conference in April 2018 by vulnerability management specialist Outpost24, 34 percent say that they would use social engineering, 23 percent say they would enter via insecure web applications, 21 percent via mobile devices, while a further 21 percent say they would enter via a public cloud. "Our study shows how confident IT professionals are that most of today's organizations are not as secure as they might believe, and will… [Continue Reading] -

Operations management platform delivers improved visibility and control of hybrid IT
Publié: juin 7, 2018, 4:05pm CEST par Ian Barker
As more systems move to the cloud, companies often struggle with factors like costs and incident response due to a lack of visibility. Operations management platform OpsRamp is launching an update to its SaaS platform that delivers greater visibility for multi-cloud environments and features a new Artificial Intelligence for IT Operations (AIOps) inference engine for more powerful alerting and event correlation. OpsRamp 5.0 features dashboard widgets that show the geographical distribution of IT assets across datacenter and cloud environments; public cloud spend to date, with a breakdown by cloud account, by custom attributes, and other criteria; and public cloud cost… [Continue Reading] -

Cryptocurrencies spark cybercrime gold rush
Publié: juin 7, 2018, 3:29pm CEST par Ian Barker
Cybercriminals are increasingly using the dark web to facilitate cryptocurrency theft on a large scale, according to cybersecurity company Carbon Black. The company’s research has uncovered a total of $1.1 billion in cryptocurrency-related thefts during the past six months and finds there are currently an estimated 12,000 dark web marketplaces selling approximately 34,000 offerings related to crypto theft. These vary widely in price, from as low as $1.04, to as high as $1,000 per offering. The average listing price was $224, while the 'sweet spot' for pricing was around $10. The listings are keen to promote the simplicity of using… [Continue Reading] -

Keeping your data safe while traveling
Publié: juin 7, 2018, 12:57pm CEST par Ian Barker
As we enter the summer people start to go away on vacations and visit sporting events like this year's World Cup in Russia, potentially exposing their digital devices and data to extra risks. VPN advice service vpnMentor has produced a report looking at the particular risks travelers face and how they can protect themselves. The biggest hazard comes from public Wi-Fi which leaves data open to interception. The report recommends avoiding the use of public Wi-Fi if you can, or if you have to use it do so through a VPN service. It also warns about copycat access points that masquerade… [Continue Reading] -

The challenges of securing mobile devices
Publié: juin 6, 2018, 3:05pm CEST par Ian Barker
Mobile devices now account for around half of web traffic and inevitably that makes them more attractive to hackers who see new attack routes via mobile apps. The Information Security Forum is launching a new paper, Securing Mobile Apps: Embracing Mobile, Balancing Control, describing the security challenges associated with acquiring, using and operating mobile apps, and suggesting actions to manage those challenges, while maintaining the business benefits. "Mobile devices are always on, continuously network connected, and have an affinity for being lost or stolen -- yet typically lack the security protection afforded to IT systems. Consequently, app security is tightly… [Continue Reading] -

People are the biggest barrier to cloud success
Publié: juin 6, 2018, 12:17pm CEST par Ian Barker
Enterprises have a clear appetite to move to the cloud, but businesses are creating additional technical complexity and recruitment challenges in the process, according to a new report. The study carried out by 451 Research for cloud provider Skytap finds 67 percent of respondents plan to migrate or modernize at least half their on-premises applications in the next 12-24 months. As a result of this process, nearly two-thirds of respondents expect better customer responsiveness and to be more competitive. However, at least half of respondents to the survey cite common, core business applications including CRM, ERP, and data analytics as… [Continue Reading] -

The key challenges for security operations center staff
Publié: juin 6, 2018, 11:22am CEST par Ian Barker
Security operations centers are understaffed according to 45 percent of professionals who work in them, and of those, 63 percent think they could use anywhere from two to 10 additional employees. This is among the findings of a new survey from Exabeam released today at Infosecurity Europe. It shows 62 percent of managers and frontline employees see inexperienced staff as a problem, compared to just 21 percent of CIO and CISOs. Almost half of all respondents (47 percent) cite keeping up with security alerts as their biggest pain point. Technology is more of a pain point for front-line workers (50… [Continue Reading] -

New analytics platform helps deliver AI for business
Publié: juin 5, 2018, 6:01pm CEST par Ian Barker
The biggest challenges that businesses face when implementing AI projects relate to the handling of data as it often sits in a separate silo. Analytics specialist Databricks is addressing this problem with a Unified Analytics Platform with new capabilities to unify data and AI teams and technologies. It offers MLflow for developing an end-to-end machine learning workflow, Databricks Runtime for ML to simplify distributed machine learning, plus Databricks Delta for data reliability and performance at scale. "To derive value from AI, enterprises are dependent on their existing data and ability to iteratively do machine learning on massive data sets. Today’s… [Continue Reading] -

Florida residents have the worst cybersecurity habits in the US
Publié: juin 5, 2018, 5:24pm CEST par Ian Barker
A study by cybersecurity company Webroot in conjunction with the Ponemon Institute finds Florida to be the worst state in the US for cyber-hygiene. Ponemon surveyed 4,000 people across the US about their cybersecurity knowledge and internet safety practices. Wyoming and Montana come close behind Florida in poor internet habits. The safest online behavior is displayed in New Hampshire, Massachusetts, and Utah. Among the findings are that less than one in four Americans overall (24 percent) regularly monitor bank and credit card statements, block pop-ups, update online account passwords, and take precautions before clicking on an email. Additionally, only 50… [Continue Reading] -

A third of IT professionals don't know how many endpoints they manage
Publié: juin 5, 2018, 4:40pm CEST par Ian Barker
A poll of 1,000 IT professionals across North America and Europe finds that while 88 percent of respondents acknowledge the importance of endpoint management, nearly a third don't know how many endpoints they actually manage. The study by identity and access management company LogMeIn shows a worrying 30 percent of IT professionals don't know how many endpoint devices exist within their organization. Those who do report an average of 750 endpoints including servers, employee computers and mobile devices. Though 71 percent of IT professionals claim they are actively addressing security on hardware, 44 percent are not actively addressing security on software… [Continue Reading] -

Serverless applications open to new wave of cryptojacking
Publié: juin 5, 2018, 3:52pm CEST par Ian Barker
Serverless computing is increasingly popular as it allows developers to upload code for functions to the cloud rather than run it on local servers. But specialist in serverless security PureSec has released a report detailing how hackers can turn a single vulnerable serverless function into a virtual cryptomining farm by taking advantage of the scaleable nature of the architecture. Exploiting the auto-scaling capabilities of serverless architecture, a single attack could hijack resources in order to run hundreds to thousands instances of popular tools that mine cryptocurrencies such as Bitcoin, Ethereum and Monero. Researchers PureSec were able to force serverless functions,… [Continue Reading] -

Sophisticated keyloggers target financial services companies
Publié: juin 5, 2018, 3:09pm CEST par Ian Barker
Analysis of malware samples found among finance firms has uncovered an unusually large number of iSpy keylogger samples. iSpy is a variant of the notorious HawkEye logger. Network-based malware protection specialist Lastline intercepted the logger's communication with the command and control server and detected the active exfiltration of website, email and FTP credentials, as well as license key information for installed products. The company's analysis also detected sophisticated Emotet and URSNIF keyloggers being delivered via Microsoft Office documents. These two strains of malware share an evasion module for detecting dynamic analysis environments, and use common methods for infiltrating financial transactions… [Continue Reading] -

Companies are still struggling to secure the cloud
Publié: juin 5, 2018, 11:52am CEST par Ian Barker
A new survey from data analytics platform Sumo Logic finds a staggering 98 percent of European companies face organizational challenges implementing security in cloud environments. The survey of over 300 IT security professionals responsible for environments with significant investment in both cloud and on-premise IT infrastructure covered the US and Canada, and Europe, The Middle East and Africa (EMEA). Among the findings are that 41 percent of EMEA respondents say that cloud requires a different approach to security management, compared to just 31 percent in the North America. Also 86 percent of EMEA respondents say that their priorities have changed… [Continue Reading] -

44 percent of organizations have suffered a data breach in the last year
Publié: juin 5, 2018, 11:18am CEST par Ian Barker
In the last 12 months, 44 percent of organizations have suffered at least one data breach. More worrying is that of those reporting a data breach, the average was almost 30 data breaches per organization in the last year. This is according to a study from identity management company SailPoint, released at this week's Infosecurity Europe. These breaches cost the organizations nearly $1 million to address from an IT perspective, which excludes fines, lost revenue and brand damage. Perhaps the most troubling survey finding, however, is that nine percent of IT leaders surveyed couldn't confidently say whether or not their organizations had… [Continue Reading] -

Employees in technology-enabled workplaces have better job satisfaction
Publié: juin 4, 2018, 5:27pm CEST par Ian Barker
People are happier in their work and more positive about the future if they're working in a digital environment, according to new research. The report from cloud networking company HPE Aruba also shows workers are positive about using more automated technology, challenging the received wisdom that we’re all scared about machines taking our jobs. The survey of 7,000 employees across 15 countries reveals almost all respondents (93 percent) think their workplace would be improved through greater use of technology, while 64 percent say their company will fall behind the competition if new technology isn't implemented. The same portion (64 percent)… [Continue Reading] -

New tool streamlines workflow automation across platforms
Publié: juin 4, 2018, 4:19pm CEST par Ian Barker
Employees often spend valuable time keeping their various work apps coordinated and synchronized, which harms productivity. Cloud-based mobile app building platform Appy Pie is addressing this problem with the launch of its 'Connect' tool, a productivity solution that allows businesses to streamline tasks and automate workflow across multiple applications simultaneously. Connect increases enterprise productivity by allowing workers and businesses to automate tasks and helps synchronise work from application to application. It allows businesses and employees the ability to establish their own 'Connects' between 20 of the most commonly used apps supported by the Appy Pie Connect network. Apps supported include… [Continue Reading] -

Consumers' privacy concerns not backed by their actions
Publié: mai 31, 2018, 3:20pm CEST par Ian Barker
A large majority of people say they are concerned about their online privacy, but this is not reflected in their actions according to a new study. The survey from Blue Fountain Media reveals that 90 percent of respondents are very concerned about their internet privacy and 48 percent wish 'more was being done about it'. Yet despite this 60 percent of those polled happily download apps without reading terms and conditions, and close to 20 percent still download apps even when they have read the terms and don't like them. A third of those polled say they would delete an… [Continue Reading] -

Bad vibrations: How sound could be used to interfere with your hard drive
Publié: mai 30, 2018, 5:52pm CEST par Ian Barker
It's well known that sound at particular levels can cause problems -- we've all seen demonstrations of wine glasses being shattered by high frequencies, for example. You might not think that's much of an issue for computers, but researchers at the University of Michigan and Zhejiang University in China have shown that sounds can be used to interfere with disks. Last year Princeton researchers showed it was possible to carry out denial of service attacks on hard disk drives, stopping CCTV systems from recording, and causing other problems by directing sounds at the drives. This latest study goes further, seeking… [Continue Reading] -

Enterprise adoption of Office 365 surges as usage of G Suite levels out
Publié: mai 30, 2018, 3:06pm CEST par Ian Barker
Using cloud apps is fast becoming standard practice for businesses and Microsoft Office 365 usage is accelerating ahead of Google's G Suite, according to a new report. The 2018 Cloud Adoption Report from cloud security company Bitglass shows global cloud adoption has topped 81 percent -- a 37 percent increase since 2016 and a 238 percent increase since 2014. Office 365 usage overtook G Suite usage in 2016 and has proceeded to stretch its lead since then. Currently, Microsoft's offering has more than twice as many deployments as Google's. While G Suite usage has remained steady at around 25 percent… [Continue Reading] -

Cryptomining dominates mobile threat landscape
Publié: mai 30, 2018, 12:08pm CEST par Ian Barker
Threat actors are increasingly looking to exploit the popularity and volatility of cryptocurrency in their attacks on mobile devices according to a new report. The latest Mobile Threat Landscape report from threat management specialist RiskIQ analyzed 120 mobile app stores and more than two billion daily scanned resources. An app called Calendar 2 appeared in the Apple App Store in March which began mining Monero digital currency on user devices. Although the app disclosed this activity and offered the option for users to pay fees or use the app with all advanced features disabled, the app developers set mining as… [Continue Reading] -

Why the IIoT and edge computing are pushing data to the fore [Q&A]
Publié: mai 28, 2018, 11:58am CEST par Ian Barker
The possibilities born out of the Industrial Internet of Things (IIoT) may seem endless as the scale of what it can accomplish continues to rise. By adding edge computing into the equation, the benefits for enterprises increase even further due to the real-time capabilities it enables. With this shift comes an increased focus on data, which is at the heart of all IIoT and edge deployments. However, some enterprises are in different stages than others when it comes to utilizing that data and getting the most actionable results out of it for valuable business decision making. We spoke with Jason… [Continue Reading] -

New consolidated identity system simplifies access to enterprise systems
Publié: mai 24, 2018, 4:07pm CEST par Ian Barker
Employee experience platform Sapho is announcing a new identity solution to simplify how employees authenticate into systems and access their data and daily workflows. Sapho's patent-pending Consolidated Identity system means employees can access what they need from a variety of applications without having to go into each application separately. This technology, created by Sapho co-founder and CTO Peter Yared, represents the next generation of Yared's federated identity system which has been in use since the early 2000s. But where federated identity is based on a loose trust model between an individual's identity provider account and the service provider, consolidated identity… [Continue Reading] -

Cryptocurrency not a major threat to enterprises say security professionals
Publié: mai 24, 2018, 3:22pm CEST par Ian Barker
While 84 percent of security professionals believe cryptocurrencies are here to stay, most don't see them as a major threat to the enterprise, despite the rise in cryptomining attacks. A study from network protection specialist Lastline shows 45.2 percent think cryptocurrency is a mainstream alternative to conventional currencies, while 38.9 percent think it's a fringe option. 14.5 percent say they would rather collect their salary in cryptocurrency than in a traditional currency. However, the survey also finds that that seven out of 10 professionals don’t see a threat to their organizations resulting from crypto currency, even though it's well documented… [Continue Reading] -

MariaDB launches Oracle compatible enterprise open source database
Publié: mai 24, 2018, 11:58am CEST par Ian Barker
Enterprise computing has often been reliant on proprietary database architecture, but this can be both complex and costly, putting up a barrier to innovation. Now open source database specialist MariaDB is launching its latest enterprise offering with Oracle compatibility. This allows existing Oracle Database users to reuse existing code and established skill sets when migrating applications or deploying new ones. MariaDB TX 3.0 introduces built-in, system-versioned tables, enabling developers to easily build temporal features into applications. This eliminates the need to manually create columns, tables and triggers in order to maintain row history, freeing DBAs to simply create new tables… [Continue Reading] -

Contextual access management eliminates passwords
Publié: mai 23, 2018, 5:07pm CEST par Ian Barker
Enterprise identity provider Okta is launching a new set of contextual access management capabilities that will allow businesses to eliminate passwords. New Adaptive Single Sign-On (SSO) and enhanced Adaptive Multi-Factor Authentication (MFA) products allow decisions based on signals such as device, IP and geolocation context for smarter, more secure identity and access management. "The best password is no password at all. Today's threat actors are targeting the weakest point of your company’s security -- your people -- and too many are successfully compromising their accounts due to poor or stolen passwords," says Todd McKinnon, CEO and co-founder of Okta. "Over… [Continue Reading] -

Organizations struggle with cloud costs
Publié: mai 23, 2018, 4:49pm CEST par Ian Barker
While businesses often cite cost cutting as a motive for moving to the cloud, a new report reveals that 37 percent of organizations surveyed listed unpredictable costs as a top cloud pain point. The study by cloud management company SoftwareONE also uncovers a lack of transparency into cloud resource usage -- something nearly one third of companies find to be a challenge. These roadblocks put cloud costs in the top two concerns -- only behind security -- for organizations when using the cloud. In fact, 90 percent of all organizations surveyed identified concerns about using the cloud. It's no surprise… [Continue Reading] -

Enterprise data increasingly accessed from mobile devices
Publié: mai 23, 2018, 3:57pm CEST par Ian Barker
Enterprise users are increasingly authenticating into applications from non-office networks, with a 10 percent increase in the average number of unique networks according to the latest Trusted Access Report from Duo Security. Duo also found that 43 percent of requests to access protected applications and data came from outside of the corporate office and network. People are logging into applications, networks and systems wherever, and whenever as work hours start to flex to fit different lifestyles, time zones and travel. Steve Manzuik, director of security research at Duo says, "Enterprises had the biggest increase in terms of authenticating from more… [Continue Reading] -

The bad password habits we just can't break
Publié: mai 23, 2018, 3:04pm CEST par Ian Barker
Despite a range of alternative authentication technologies, many systems still rely on passwords for their security. But a new study from Dashlane shows we’re still pretty bad at password selection. The analysts used research from Dr Gang Wang, an assistant professor in the Department of Computer Science at Virginia Tech, which analyzed over 61 million passwords. Dashlane researchers examined the data for patterns, highlighting simple mistakes that continue to be made by people who use passwords in daily life. Researchers found patterns across the keyboard, from not-so-randomly chosen letters and numbers to popular brands and bands, and even passwords created… [Continue Reading] -

90 percent of financial institutions targeted by ransomware in the last year
Publié: mai 22, 2018, 4:40pm CEST par Ian Barker
Robbing a bank used to involve a mask, a gun and a fast car, but these days it's more likely to be done via the safer and no less lucrative means of a cyberattack. A new report from cloud security specialist Carbon Black, based on responses from CISOs at 40 major financial institutions -- including six of the top 10 global banks -- seeks to better understand the attack landscape. Among the findings are that 90 percent of financial institutions report being the subject of a ransomware attack in 2017. In addition one in 10 respondents report encountering destructive attacks… [Continue Reading] -

Half of employees not aware of their company's GDPR preparations
Publié: mai 22, 2018, 3:54pm CEST par Ian Barker
With GDPR coming into force at the end of this week, new research from Egress Software Technologies found over half of respondents were in the dark about what their company was doing to prepare for the legislation. Only 43 percent of the 1,000 respondents were aware of preparations, there is also a lack of awareness surrounding personal data in general. One in 10 are unaware they are handling personal data in their day-to-day jobs and 57 percent are unable to correctly identify when it would need to be protected. When presented with categories of personal data -- such as addresses,… [Continue Reading] -

Email fraud still a significant threat to businesses
Publié: mai 22, 2018, 3:28pm CEST par Ian Barker
Not so long ago the idea of email fraud mainly involved Nigerian princes asking for your help to liberate a few million dollars. Things have moved on and the scammers have become more sophisticated, but email fraud is no less of a threat according to a new study by email security specialist Agari, which studied activity on 78 criminal email accounts over a period of 10 months. Interestingly Nigeria is still at the heart of email scams, with nine out of 10 of the accounts studied based there. Most focus on business email compromise (BEC) attacks, but romance scams --… [Continue Reading] -

Banks struggle to defend against internal attacks
Publié: mai 21, 2018, 3:31pm CEST par Ian Barker
A new study from vulnerability assessment specialist Positive Technologies shows that banks have built up strong defenses against external attacks but still struggle with internal threats. Whether they use social engineering, vulnerabilities in web applications, or the help of insiders, as soon as attackers access the internal network of a bank, they often find that it's secured no better than companies in other industries. With access to the internal network of client banks, Positive Technologies testers succeeded in obtaining access to financial applications in 58 percent of cases. At 25 percent of banks, they were able to compromise the workstations… [Continue Reading] -

New service offers enterprises fast, easy real-time streaming
Publié: mai 21, 2018, 2:51pm CEST par Ian Barker
Apache Kafka has has become increasingly popular as a data streaming platform but it can be hard for businesses to take full advantage of it without the right skills. Now though Open Source-as-a-Service company Instaclustr is launching a new Kafka-as-a-Service solution to allow enterprises to manage high volume data streams in real-time. Adding Kafka to Instaclustr's existing platform allows users to benefit from the robust provisioning and management patterns used to deliver other leading open source technologies like Apache Cassandra and Apache Spark. Kafka can be run as a standalone managed service or integrated with the other open source data… [Continue Reading] -

Organizations waste billions of dollars preparing data
Publié: mai 17, 2018, 4:14pm CEST par Ian Barker
Clean data is vital if analytics are to deliver useful results, but a new survey reveals that many organizations are still relying on manual and inefficient processes to clean and prepare information. The study by data preparation company Trifacta shows these inefficiencies are draining resources and inhibiting organizations' ability to glean insights that could be crucial to their business decisions. Among the findings are that 65 percent of IT professionals spend half or more of their time at work on data quality assurance, cleanup or preparation. Based on average IT salaries this means organizations worldwide could be spending almost $500… [Continue Reading] -

F-Secure combines AI and human expertise in new security offering
Publié: mai 17, 2018, 3:25pm CEST par Ian Barker
It's no longer enough to just protect the perimeter in order to keep systems secure. It's now necessary to catch file-less attacks, privilege escalation and a whole range of other tactics. The problem for smaller businesses is they often don't have the expertise in house to handle the range of threats. Finnish security company F-Secure is launching a new endpoint detection and response solution that solves this problem by combining industry-leading security expertise with the latest technologies to help organizations catch advanced tactics used by attackers. "Well-maintained security perimeters are great for commodity threats, but targeted attackers are usually prepared… [Continue Reading] -

New partnership delivers SaaS identity and operations management
Publié: mai 16, 2018, 4:12pm CEST par Ian Barker
SaaS operations management platform BetterCloud has announced a partnership with enterprise identity provider Okta to allow companies to provide simple, secure user access while meeting day-to-day operational management and security requirements for their mission-critical SaaS applications. BetterCloud Connector for Okta provides organizations with a strong policy management solution that securely and effectively authenticates, provisions and governs configuration, settings and data within SaaS applications across the enterprise. "Enterprises are facing a massive SaaS sprawl today, making it more difficult and time consuming than ever to manage and secure business-critical data across their application stack," says Shreyas Sadalgi, chief business strategy officer… [Continue Reading] -

US companies may need to provide GDPR rights to all, not just EU citizens
Publié: mai 16, 2018, 3:26pm CEST par Ian Barker
With GDPR implementation just over a week away, a report from US law firm Attorney.IO suggests that rights under the legislation may be available to others besides EU citizens. Based on the answers 129 law professors gave to questions on the GDPR, it points out that GDPR doesn't just apply to citizens of an EU country. It applies to anyone who at any time set foot in an EU country and transmitted their data to a covered internet company. So, for example, a US tourist who visits Germany for one day and returns to the US has rights under the… [Continue Reading] -

How blockchain is set to change the world
Publié: mai 15, 2018, 5:04pm CEST par Ian Barker
In most people's minds blockchain technology is associated with cryptocurrency, but it has potential to be useful in a whole range of other areas. Consumer research company The Opinion Economy has produced an infographic to highlight the potential of blockchain in a whole range of areas. The things it looks at include the building of self-enforcing smart contracts, and the savings that it can offer in administering payments and securing transactions, streamlining operations by cutting out middlemen. There's potential to improve the quality of healthcare and to smooth out real estate transactions too. It could also be used to authenticate… [Continue Reading] -

Publicly disclosed vulnerabilities continue to rise
Publié: mai 15, 2018, 4:46pm CEST par Ian Barker
The first quarter of 2018 has shown a 1.8 percent increase in the number of disclosed vulnerabilities over the same period in 2017, with 5,375 unique vulnerabilities reported. This is one of the findings of Risk Based Security's latest Vulnerability QuickView Report, which suggests that unless the rate of increase slows down 2018 will be another record year. More worrying is that 1,790 (33.3 percent) of the vulnerabilities tracked do not have a CVE ID assigned and therefore are not available in NVD and similar databases that solely rely on CVE. 19.7 percent of these vulnerabilities have a CVSSv2 score… [Continue Reading] -

UK Reported security incidents increase ahead of GDPR
Publié: mai 15, 2018, 3:55pm CEST par Ian Barker
When GDPR comes into force next week, organizations will have 72 hours to report security breaches to a regulator once they become aware of them. Ahead of the new legislation, the UK's Information Commissioner's Office (ICO) has released details of the latest data security trends. Reported incidents in the final quarter of 2017 showed a 17 percent increase over the previous quarter, perhaps indicating that companies are taking a more proactive approach to reporting as GDPR approaches. Incidents in the education sector rose by 32 percent over the same period and those in the charitable and giving sector by 69… [Continue Reading] -

100 percent of organizations have active insider threats
Publié: mai 15, 2018, 3:22pm CEST par Ian Barker
A new study from user behavior intelligence specialist Dtex Systems has uncovered active insider threats in all of the organizations it assessed. Failure to gain visibility is allowing malicious and negligent employees to engage in undetected high-risk activities on every endpoint, on and off the network. Malicious employees are users that intentionally harm their organizations through theft, sabotage, and blatant disregard for security. Negligent employees are those that hurt their organization due to a lack of defenses, lack of awareness, carelessness and error. "Organizations come to us because they know their employees are engaged in risky behaviors. They usually have… [Continue Reading] -

Push notification tool helps marketers engage with mobile users
Publié: mai 15, 2018, 11:33am CEST par Ian Barker
Mobile marketing and analytics specialist Flurry is launching a new push notification tool to help companies engage and retain users across Android and iOS platforms. Flurry Push is a free offering within the new Flurry Marketing Suite that lets app developers send out targeted messages to grow business and build revenue. "We've heard consistently from our developers that messaging is one of the most powerful tools for boosting user engagement," says David Berger, VP, engineering at Oath, Flurry's parent company. "With Flurry Push, we're putting free messaging front-and-center to empower developers to take charge of their app business and address… [Continue Reading] -

Cryptomining malware targets unpatched servers
Publié: mai 14, 2018, 4:02pm CEST par Ian Barker
Cybercriminals are increasingly targeting unpatched server vulnerabilities to infect machines with cryptomining malware, according to a new report. The study from Check Point Software Technologies sees cryptomining malware dominate Check Point’s Top Ten Most Wanted Malware Index, the Coinhive variant retains the top spot with a global reach of 16 percent. Cryptoloot -- another crypto-mining malware -- is close behind with a global reach of 14 percent, while the Roughted malvertising malware came in third (11 percent). Two unpatched server vulnerabilities in Microsoft Windows Server 2003 (CVE-2017-7269) and Oracle Web Logic (CVE-2017-10271) are being targeted in order to illicitly mine… [Continue Reading] -

Shadow devices put enterprise networks at risk
Publié: mai 14, 2018, 11:07am CEST par Ian Barker
A new study finds that enterprise networks have thousands of shadow personal devices including laptops, tablets and mobile phones, as well as Internet of Things devices -- such as digital assistants and smart kitchen appliances -- connecting to them. The report from network control company Infoblox shows 35 percent of companies in the US, UK and Germany reported more than 5,000 personal devices connecting to the network each day. Employees in the US and UK admit to connecting to the enterprise network for a number of reasons, including to access social media (39 percent), as well as to download apps,… [Continue Reading] -

CRM technology isn't keeping pace with business needs
Publié: mai 10, 2018, 4:34pm CEST par Ian Barker
CRM systems should make communication with customers easier, but a new report from ProsperWorks, the CRM tool for Google's G Suite, suggests CRM technology isn't keeping pace with the needs of the digital workforce. ProsperWorks commissioned research firm Lab42 to conduct a survey on sales relationships and CRM pain points from those that frequently use CRM systems. The findings show that the way companies interact with customers is changing but CRM technology is too manual, hasn't evolved and is not focused enough on fostering relationships. It's no surprise then that nearly half of respondents think innovation of CRM should be… [Continue Reading] -

Mobile ad fraud almost doubles compared to 2017
Publié: mai 10, 2018, 3:56pm CEST par Ian Barker
A new report from mobile measurement company Adjust reveals that in the first quarter of this year mobile ad fraud nearly doubled over the same period in 2017. Adjust measured 3.43 billion app installs and over 350 billion events, processing and analyzing 125 terabytes of data per day from 20,000+ apps over the first three months of 2018. Adjust's Fraud Prevention Suite rejected 7.3 percent of all paid installs, the most common being SDK spoofing (37 percent), click injection (27 percent), faked installs (20 percent) and click spam (16 percent). SDK Spoofing has rapidly gained momentum and become fraudsters' preferred… [Continue Reading] -

Companies can turn GDPR compliance into competitive advantage
Publié: mai 10, 2018, 11:57am CEST par Ian Barker
GDPR comes into force on May 25th and will have an effect on all companies that collect user data even if they are outside the EU. Independent identity research and strategy company One World Identity has produced a report that aims to serve as a definitive primer on what companies need to do to comply, and help them turn that compliance into a competitive edge. "Even if a company is not currently governed by GDPR, raising the bar for accuracy in line with the regulation’s principles could have a tangible impact on their bottom line," says Kaelyn Lowmaster, Principal Analyst… [Continue Reading] -

Iran could launch cyber attacks in response to renewed sanctions
Publié: mai 9, 2018, 6:06pm CEST par Ian Barker
President Trump's re-imposition of sanctions against Iran could lead the country to respond by launching cyber attacks on Western businesses within months, according to a new report. Threat intelligence company Recorded Future has today released new research and analysis into the Iranian cyber threat. Since at least 2009, Iran has regularly responded to sanctions or perceived provocations by conducting offensive cyber campaigns say the report's authors. "The Islamic Republic has historically preferred to use proxies or front organizations both in physical conflict -- Hezbollah against Israel and Yemen rebels against Saudi Arabia -- and cyberattacks to achieve its policy goals."… [Continue Reading] -

Most companies not putting adequate investment into application security
Publié: mai 9, 2018, 12:32pm CEST par Ian Barker
According to a new survey from Arxan, only 25 percent of respondents say their organization is making a significant investment in solutions to prevent application attacks. This is despite awareness of the negative impact of malicious activity. A worrying 65 percent of companies say they would be spurred to increase application protection measures only after an end user or customer was negatively affected. "It's disturbing that so many companies acknowledge the increasing risk of application attacks, yet they are doing very little to prevent breaches from occurring," says Joe Sander, CEO of Arxan. "It's backward thinking, and it puts customers… [Continue Reading] -

Data breach activity declines sharply in 2018
Publié: mai 8, 2018, 4:17pm CEST par Ian Barker
The number of data breaches disclosed in the first three months of this year fell to 686 compared to 1,444 breaches reported in the same period of 2017, according to a new report. This still represents the exposure of some 1.4 billion records, although this figure too is down from 3.4 billion in the same quarter last year. The study from Risk Based Security also shows a shift in tactics. The spike in the value of cryptocurrencies that took place in January fueled a rapid expansion into the theft of computing resources. "We knew we were seeing less activity than prior… [Continue Reading] -

Younger generations lack understanding of cybersecurity careers
Publié: mai 8, 2018, 3:39pm CEST par Ian Barker
It's been accepted wisdom for some time that an injection of extra talent is needed to solve the cybersecurity skills shortage. Further confirmation of this comes in the form of a report from ProtectWise looking at the survey responses of 524 technology-savvy millennials and post-millennials in the US, conducted by Enterprise Strategy Group (ESG), to see if there were potential answers to the security skills shortage. The data shows that the younger generation understands and acknowledges that technology and computing are likely to play a significant role in their future careers. This means that the generations that grew up with iPhones… [Continue Reading] -

How managed services can help businesses with GDPR [Q&A]
Publié: mai 7, 2018, 11:15am CEST par Ian Barker
With GDPR implementation now only weeks away many businesses are still not fully prepared for the impact of the new legislation. We spoke to Matt Klassen VP of cloud marketing at IT service management specialist Cherwell Software to find out how managed services can help companies to comply with GDPR by the may 25th deadline and to manage the additional workload it's likely to create. BN: We see a lot of stories at the moment that most businesses aren't ready for GDPR. Is this a fair assessment? MK: I think it is, it's a global problem though I think companies… [Continue Reading] -

The challenges of adopting the Industrial Internet of Things [Q&A]
Publié: mai 4, 2018, 11:51am CEST par Ian Barker
A future enabled by the Industrial Internet of Things (IIoT) is not so far off, with the integration of IoT devices rising across industrial settings from oil and gas to building security. The potential to leverage big data and analytics to optimize operations and efficiencies is driving industrial companies to move to IIoT-enabled devices, but these companies are now faced with the challenge of modernizing their legacy production systems. It can be daunting to convert years or decades worth of data to a new infrastructure, which is why we asked Jason Andersen, VP of business line management for Stratus Technologies,… [Continue Reading] -

73 percent of industrial networks are vulnerable to hackers
Publié: mai 3, 2018, 6:02pm CEST par Ian Barker
The industrial control systems (ICS) used to run equipment in manufacturing, energy, and other sectors are secured differently from office networks. Vulnerabilities often go unpatched, because organizations are afraid to make changes that might cause downtime. To minimize the chances of exploitation of vulnerabilities, measures put in place include placing ICS components on a separate network, isolating them, or air-gapping them entirely from Internet-connected corporate systems. However, penetration testing performed by Positive Technologies has shown that such measures often fall short in practice, leaving attackers plenty of opportunity to access critical equipment. In tests, attackers were able to penetrate the… [Continue Reading] -

The poor password habits of IT professionals
Publié: mai 3, 2018, 5:21pm CEST par Ian Barker
It's World Password Day and we've already looked at tips for safe password use, but a new survey from identity management company SailPoint reveals that IT professionals aren't practising what they preach when it comes to password use. In partnership with research company Vanson Bourne, SailPoint surveyed 400 IT decision makers about their password habits and came up with some worrying results. More than half of respondents (55 percent) admitted to reusing passwords across different sites. Choosing strong passwords isn't a widespread habit either. Of the IT decision makers surveyed, 32 percent had used things like a family member's name in a… [Continue Reading] -

Ransomware attacks up 400 percent in 2017 mainly due to WannaCry
Publié: mai 3, 2018, 3:41pm CEST par Ian Barker
Ransomware attacks grew by 400 percent last year, largely down to the success of the WannaCry attack. It’s perhaps not surprising that other variants slowed down, but this signals a shift in the way ransomware is being used. A new report from F-Secure shows WannaCry accounted for nine out of every 10 ransomware detection reports by the end of the year. The use of other ransomware by cyber criminals seemed to decline though. This is a phenomenon that F-Secure's security advisor Sean Sullivan says points to amateur cyber criminals losing interest in ransomware. "After the summer, there was a noticeable… [Continue Reading] -

Top tips for World Password Day
Publié: mai 3, 2018, 1:25pm CEST par Ian Barker
We're constantly being told that the password's days are numbered. No less a figure than Bill Gates predicted the end of the password as far back as 2004. Yet we still rely on them to protect many of our day-to-day activities. To mark today’s World Password Day, Raj Samani, chief scientist and fellow at McAfee, has produced a set of tips that people can follow to make the best use of passwords. Create Strong Passwords. Never use family names, pets, birthdays, '12345' or 'password'. Many websites and apps will prompt you to include a combination of numbers, lowercase and uppercase… [Continue Reading] -

Most popular travel sites have unsafe password practices
Publié: mai 2, 2018, 4:10pm CEST par Ian Barker
A new study of password and account security on 55 of the world's most popular travel-related sites reveals that 89 percent leave their users' accounts potentially exposed to hackers due to unsafe password practices. The research by password management company Dashlane tested each website on five critical password and account security criteria. A site received a point for each criterion it met, for a maximum score of 5/5. Any score below 4/5 was considered failing and not meeting the minimum threshold for good password security. Only 11 percent (6/55) passed with a score of 4/5 or better, and only one… [Continue Reading] -

Turbonomic delivers AI-powered workload automation for the cloud
Publié: mai 2, 2018, 3:46pm CEST par Ian Barker
Workload automation specialist Turbonomic has released a major update to its software, delivering application-aware infrastructure and making any type of workload -- virtual, cloud and container -- self-managing. Turbonomic's AI-powered decision engine analyzes performance, cost and compliance data across the entire IT stack and generates trustworthy decisions at scale faster than before. It also delivers continuous automation of AWS Reserved Instance (RI) utilization, in concert with re-sizing actions, enabling greater elasticity and often driving 30 percent or more cloud savings. It enables greater understanding of application resource utilization and topology too, and the automating of decisions. New Application Performance Management (APM)… [Continue Reading] -

Critical vulnerability found in infrastructure and manufacturing applications
Publié: mai 2, 2018, 3:04pm CEST par Ian Barker
A critical remote code execution vulnerability has been discovered in two Schneider Electric applications heavily used in manufacturing, oil and gas, water, automation and wind and solar power facilities. The vulnerability, discovered by cyber exposure company Tenable, could, if exploited, give cyber criminals complete control of the underlying system. Attackers would also be able to use the compromised system to move laterally through the network, exposing additional systems to attack. In a worst case scenario, attackers could use the vulnerability to disrupt or cripple plant operations. The vulnerability impacts InduSoft Web Studio, an automation tool used to develop human-machine interfaces… [Continue Reading] -

Phishing and drive-by downloads lead infection methods
Publié: mai 2, 2018, 1:16pm CEST par Ian Barker
The most common infection vectors are still email phishing and drive-by downloads according to the latest threat report from AI security specialist Cylance. The report provides a real-world glimpse into major cyber threats that affected Cylance’s customer base in 2017. Along with industry trends and analysis, and data from thousands of government entities and organizations of all sizes across 160 countries that have adopted a prevention-first approach to security. It shows destructive attacks continue to rise with ransomware families leading the pack, growing three-fold during the year and affecting the healthcare industry the most. More than half of 2017's attacks… [Continue Reading] -

North Korean antivirus software uses decade old pirated scan engine
Publié: mai 1, 2018, 4:09pm CEST par Ian Barker
With a name like 'SiliVaccine' you could be forgiven it's something your doctor would give you if you were worried about turning into a clown. But in fact this is North Korea's home grown antivirus product. Check Point Software has obtained and analyzed a rare copy of the software and discovered key components of its source code to be identical to a 10-year old copy of Trend Micro's AV software. Analysis has also uncovered that SiliVaccine is designed to allow a specific malware signature to pass undetected to users, and an update patch for the software contained JAKU malware, which… [Continue Reading] -

73 percent of UK businesses unaware of lawful basis for processing data ahead of GDPR
Publié: mai 1, 2018, 3:07pm CEST par Ian Barker
A few weeks ago we spoke to ThinkMarble about the impending arrival of GDPR and the company's virtual data protection office service. As the May 25th deadline draws closer, the company has released some research data that shows almost three-quarters of UK businesses are unaware of the lawful basis for processing data and a quarter still don't know, or are unsure of, where the personal data they are responsible for is currently held. The data, sourced from more than 250 businesses that completed ThinkMarble's GDPR Readiness online portal tool, also reveals that 79 percent of businesses haven't reviewed their data… [Continue Reading] -

Windows 10 April 2018 -- what's new for IT pros?
Publié: mai 1, 2018, 12:08pm CEST par Ian Barker
As the keenly awaited Windows 10 April 2018 update (Windows 10 1803) begins its roll out, IT professionals will be interested to see what features it offers them. Among the developments of interest to professionals is the Windows Autopilot feature which offers cloud powered device management. Using Intune, Autopilot now allows the device to be locked during provisioning until policies and settings for the device get provisioned, ensuring that by the time the user gets to the desktop, the device is secured and configured correctly. Autopilot is available on Surface, Lenovo, and Dell devices, with other OEMs coming onboard in… [Continue Reading] -

The impact of AI in the data center [Q&A]
Publié: avril 30, 2018, 5:29pm CEST par Ian Barker
The rise of artificial intelligence (AI), automation and machine learning is changing the way IT professionals approach data center operations and management. And the possibilities are endless -- from lowering operational costs and reducing time to deploy new applications -- there’s no doubt that AI is transforming the data center. We spoke with Hal Woods, chief technology officer of storage and data management specialist Datera, to learn more. BN: How can AI be used to improve data center operations? HW: AI promises to automate operational aspects such as resource allocation and optimization, event handling and contribute critical information to capacity… [Continue Reading] -

81 percent of organizations see an increase in cyber security challenges
Publié: avril 30, 2018, 4:46pm CEST par Ian Barker
A new study from IT solutions provider US Signal reveals that businesses are seeing a greater number of security challenges. The survey of security experts from a cross-section of organizations also shows 40 percent of respondents experienced at least one security incident in the last year, and 13 percent didn't know if they had. The top three challenges are seen as: protecting against email-related threats like ransomware, malware and phishing; transitioning legacy systems that no longer receive security updates; and ensuring the company is always up to date with patches and current software versions. "Knowing how real and damaging the… [Continue Reading] -

Long-lasting DDoS attacks make a comeback as numbers of attacks and targets rise
Publié: avril 26, 2018, 5:40pm CEST par Ian Barker
Long-lasting DDoS attacks made a return in the first quarter of 2018 with the longest attack seen lasting 297 hours (more than 12 days). The last time a longer attack than this occurred was at the end of 2015. This is among the findings of Kaspersky Lab's latest DDoS intelligence report which reveals that in the first quarter of 2018, DDoS attacks were registered against targets in 79 countries. The report sees a significant increase in both the total number and duration of DDoS attacks compared to the final quarter of 2017. The new Linux-based botnets Darkai (a Mirai clone)… [Continue Reading] -

Configuration vulnerability could leave SAP systems open to compromise
Publié: avril 26, 2018, 3:23pm CEST par Ian Barker
A vulnerability arising from the default installation of popular business management platform SAP could lead to a full compromise of the system say researchers. SAP security and compliance specialist Onapsis has revealed the flaw which is found in SAP Netweaver and can be compromised by a remote unauthenticated attacker with only network access to the system. Driven by a security configuration originally documented by SAP in 2005, the problem is still present in the majority of SAP implementations, either because they've neglected to apply security configurations or due to unintentional configuration drifts of previously secured systems. Onapsis has spent the past… [Continue Reading] -

North Korean leaders abandon western social media
Publié: avril 25, 2018, 5:11pm CEST par Ian Barker
Chances are you're not currently friends with Kim Jong Un on Facebook. And it's not likely to happen any time soon according to researchers at Recorded Future who have been looking at the internet usage patterns of North Korea's leaders. In July last year they found that the country's ruling elite were plugged into contemporary internet society, were technologically savvy, and had patterns of internet use that were very similar to users in the West. Repeating the analysis in December, however, they discovered substantive changes in how North Korea's leadership use the internet. In particular, they had almost totally abandoned western social… [Continue Reading] -

Cohesity simplifies the creation of cloud development environments
Publié: avril 25, 2018, 4:25pm CEST par Ian Barker
Secondary storage specialist Cohesity is launching new capabilities that allow organizations to leverage the public cloud for faster application testing and development, while still ensuring seamless backup and recovery. A growing number of enterprises are moving application testing and development onto public cloud infrastructure, taking advantage of its agility and elasticity to speed time to market. Using Cohesity CloudSpin, users can instantly convert backup data stored on Cohesity DataPlatform into a new virtual machine for testing or development in the cloud. It's also announced DataProtect, a modern, web-scale backup solution to integrate with public cloud snapshot APIs to deliver automated… [Continue Reading] -

Security flaw could allow hackers to create hotel master keys
Publié: avril 25, 2018, 3:42pm CEST par Ian Barker
Most hotel chains these days rely on some sort of electronic key card mechanism rather than more traditional locks. Researchers at F-Secure have found that hotels worldwide are using an electronic lock system with a flaw that could be exploited by an attacker to gain access to any room in the building. The attack involves using any ordinary electronic key to the target facility -- even one that's long expired, discarded, or used to access spaces such as a garage or closet. Using information on the key, the researchers are able to create a master key with privileges to open… [Continue Reading] -

Endpoints still vulnerable despite advances in protection technology
Publié: avril 25, 2018, 3:15pm CEST par Ian Barker
Although endpoint security solutions have improved, a new survey of IT security professionals finds that three quarters believe their existing anti-malware solutions would be able to prevent no more than 70 percent of infections. The study from anti-evasion specialist Minerva Labs shows nearly half of the respondents surveyed (48 percent) say that they have seen about the same number of malware infections than previous years while 32 percent claim to have seen an increase in infections. The malware evasion techniques that pose the biggest concern are avoidance of malware analysis and forensic tools (32 percent) followed by fileless or memory… [Continue Reading] -

90 percent of malware given unhelpful labels by AV tools
Publié: avril 24, 2018, 4:01pm CEST par Ian Barker
According to a new study, 90 percent of malicious files are given generic labels by AV tools, such as 'trojan.generic', providing limited guidance for successful remediation and leaving enterprises exposed to subsequent attacks resulting from compromised credentials. The study by breach protection specialist Lastline analyzed tens of millions of samples that were for the most part scanned and released by other security solutions. Among other findings are that both enterprises, and malware authors, use a wide range of file types, illustrating the need to have protection parity across all attack vectors. The file types that malware authors use to launch… [Continue Reading] -

Robin the AI-based assistant automates tedious sales tasks
Publié: avril 24, 2018, 3:07pm CEST par Ian Barker
Sales staff often find themselves spending time on administrative tasks that keep them away from actual selling. San Francisco-based company SalesHero is aiming to change that with the launch of Robin, a new AI assistant for sales staff that learns from the user's actions and automates processes to improve daily productivity. By processing data from users' CRM, customer interactions and SalesHero's own proprietary database of 45 million global company records, Robin takes on the tedious sales tasks that constantly detract from actual selling. Robin intelligently boosts prospecting by offering up new and pertinent accounts and leads. It improves CRM data by… [Continue Reading] -

Online banking security improves but only a third are free of critical vulnerabilities
Publié: avril 23, 2018, 3:29pm CEST par Ian Barker
The percentage of critical vulnerabilities in online banking systems is falling, but two thirds still contain at least one critical vulnerability according to a new report. Enterprise security specialist Positive Technologies has released its Financial Application Vulnerabilities Report, drawn from audits performed by the company. It finds each eBanking system analyzed in 2017 contained, on average, seven vulnerabilities, up from six in 2016. However, high- and medium-risk vulnerabilities made up a smaller portion. Even so only a third of online banks were free of critical vulnerabilities in 2017, whereas in 2016 all financial web applications (except one) had at least… [Continue Reading] -

Companies are keen to move analytics to the cloud
Publié: avril 23, 2018, 2:59pm CEST par Ian Barker
The cloud is the best place to run analytics according to 83 percent of the world’s biggest companies. A new survey for Teradata conducted by Vanson Bourne shows that by 2023, most organizations want to run all of their analytics in the cloud. But an overwhelming 91 percent say that analytics should be moving to the public cloud at a faster rate. A number of barriers are identified to cloud adoption, the biggest being security (50 percent), immature and low-performing available technology (49 percent), regulatory compliance (35 percent) and lack of trust (32 percent). Other concerns center on technology integration… [Continue Reading] -

Martin Lewis suing Facebook over fake ads
Publié: avril 23, 2018, 11:01am CEST par Ian Barker
We reported just over a week ago that fake ads promoting cryptocurrency scams were using the names of leading UK business figures. Now one of those whose names has been featured, consumer advice expert Martin Lewis, is suing Facebook for defamation over the use of his face and name. Lewis, the man behind the MoneySavingExpert.com website, is seeking damages in the high court on the grounds that Facebook failed to prevent or swiftly remove false advertising which has both tarnished his reputation and lured unwitting victims into costly scams. "It is not worth Facebook's while improving its systems," Lewis told… [Continue Reading] -

Cybercrime revenues hit $1.5 trillion a year
Publié: avril 20, 2018, 1:14pm CEST par Ian Barker
We reported earlier this month on the ways in which cyber criminals spend their ill-gotten gains. The company behind those findings, Bromium, has now released more details from its research, which exposes a huge cybercrime-based economy and the professionalization of cybercrime. Complete findings will be presented today at the RSA Conference in San Francisco by researcher Dr Michael McGuire, senior lecturer in criminology at the University of Surrey in England. The report estimates cyber criminal revenues worldwide of at least $1.5 trillion -- equal to the GDP of Russia. In fact, if cybercrime was a country it would have the 13th… [Continue Reading] -

Cyber attacks could cause catastrophic failure say 70 percent of energy security pros
Publié: avril 19, 2018, 3:14pm CEST par Ian Barker
A new study looking at industrial control systems (ICS) security in the energy industry reveals a majority of respondents are worried about potentially catastrophic effects from a successful cyber attack. The study carried out for security and compliance specialist Tripwire by Dimensional Research included 151 IT and operational technology (OT) security professionals at energy and oil and gas companies. It finds 70 percent of respondents are concerned that a successful cyberattack could cause a catastrophic failure, such as an explosion. With widespread recognition of the physical threat cyber attacks present against the energy and oil and gas industry, 97 percent… [Continue Reading] -

Honeypot project reveals attackers are turning to automation
Publié: avril 18, 2018, 5:22pm CEST par Ian Barker
Most businesses are seeking to automate the more tedious aspects of their operations and some new research from security analytics platform Cybereason reveals that hackers are no exception. The company set up a honeypot system masquerading as a financial services company and introduced security flaws in several stages. First usernames and passwords for Remote Desktop Services were released to hacker forums, second additional RDP services with weak passwords were created, and finally other devices were opened up to see which ports got scanned. The most interesting result came after weakening the RDP ports. This attracted the attentions of a bot… [Continue Reading] -

German government moves to open source private cloud
Publié: avril 18, 2018, 12:28pm CEST par Ian Barker
The German federal government is moving to an open source, self-hosted cloud platform from Nextcloud for file sync and sharing and collaboration, in order to protect the data of its citizens. The Federal Information Technology Center (ITZBund), which takes care of IT services for the entire federal government, has been running a pilot of 5000 users with Nextcloud since October 2016 and after a successful tender this will now be rolled out everywhere. ITZBund operates IT Services for over one million administrative and industrial users. In choosing an open source solution from a European company it ensures no vendor lock-in… [Continue Reading] -

Fake Chrome ad blockers used to create botnets
Publié: avril 18, 2018, 11:50am CEST par Ian Barker
More than 20 million Chrome users have been tricked into installing fake ad blockers that could see their machines recruited into a botnet, according to a new report. A fake AdBlock Plus extension fooled many users last year. As many Chrome users discover ad blocking by browsing available extensions, so creating cloned fakes has become a popular tactic for cyber criminals according to AdGuard. These latest extensions are simple rip-offs with a few lines of code and some analytics added by the 'authors'. AdGuard's Andrey Meshkov writing on the company's blog says, "I must say the problem is not new.… [Continue Reading] -

MSPs and resellers see containers as the biggest opportunity since virtual machines
Publié: avril 17, 2018, 4:35pm CEST par Ian Barker
A new survey of channel partners by container platform specialist Diamanti reveals that resellers and service providers see the adoption of containers as a massive disruption and opportunity. Enterprises are rapidly adapting their applications and systems for the cloud, and containers are viewed as a key enabling technology. According to Diamanti's survey, more than 75 percent of channel partners say containers represent a moderate or major money-making opportunity. "Every 10 to 15 years there's a fundamental shift in how IT is delivered and consumed," says Mike Vizard, author of the survey findings and long-time channel and server infrastructure expert. "The… [Continue Reading] -

Most companies not prepared to meet GDPR compliance deadline
Publié: avril 17, 2018, 3:03pm CEST par Ian Barker
A new survey reveals that 60 percent of companies are not likely to meet the May 25 deadline for compliance with the new European GDPR legislation. The study from Crowd Research Partners shows only seven percent of surveyed organizations say they are in full compliance with GDPR requirements today, and 33 percent state they are well on their way to the compliance deadline. While 80 percent confirm GDPR is a top priority for their organization, only half say they are knowledgeable about the data privacy legislation or have deep expertise. A worrying 25 percent have no or only very limited… [Continue Reading] -

Yubico brings FIDO2 passwordless Windows 10 login to enterprises
Publié: avril 17, 2018, 1:23pm CEST par Ian Barker
Hardware authentication specialist Yubico is announcing a new FIDO2 compatible security key which will be supported in Windows 10 devices and Microsoft Azure Active Directory (Azure AD). This means that organizations will have the option to enable employees and customers to sign in to an Azure AD joined device with no password, simply by using the security key to get single sign-on to all Azure AD based applications and services. "Microsoft's FIDO2 implementation using the Security Key by Yubico is just the beginning of a passwordless world; there are no limits as to where this technology can take us," says… [Continue Reading] -

A quarter of organizations have had data stolen from the public cloud
Publié: avril 16, 2018, 4:07pm CEST par Ian Barker
Public cloud services are now in use in 97 percent of organizations, but one in four have experienced data theft and cloud-first strategies are on the decline. These are among the findings of the latest annual cloud report from McAfee. Among other highlights are that 83 percent store sensitive data in the public cloud and 69 percent trust the public cloud to keep their sensitive data secure. However, one in five organizations has experienced an advanced attack against its public cloud infrastructure. "Despite the clear prevalence of security incidents occurring in the cloud, enterprise cloud adoption is pressing on," says… [Continue Reading] -

ESET launches new enterprise security solutions
Publié: avril 16, 2018, 3:07pm CEST par Ian Barker
Cyber security company ESET is using this week's RSA Conference in San Francisco to launch its new range of enterprise security products. These include a new ESET Enterprise Inspector, an Endpoint Detection and Response (EDR) solution, and ESET Dynamic Threat Defense, a tool that provides off-premise cloud sandboxing, which leverages machine learning and behavior-based detection to prevent zero-day attacks. It's also replacing ESET Remote Administrator with an all-new ESET Security Management Center, an enterprise-grade server that provides visibility management and reporting across all operating systems. All of the solutions integrate seamlessly into a single-pane interface and allow for visibility into… [Continue Reading] -

Large scale data breaches provide drive for DevSecOps investments
Publié: avril 16, 2018, 12:23pm CEST par Ian Barker
Breaches related to open source components have grown 50 percent since 2017, and an eye-opening 121 percent since 2014, according to a new survey from open source governance and DevSecOps automation specialist Sonatype. But the survey finds that those companies with mature DevOps practices are 24 percent more likely to have deployed automated security practices throughout their development lifecycle. Investments in open source governance, container security, and web application firewalls are noted as being the most critical to companies pursuing DevSecOps transformations. But resourcing and training still present challenges, 48 percent of respondents admit that they don't have enough time… [Continue Reading] -

UK sets out five principles for the ethical use of AI
Publié: avril 16, 2018, 11:02am CEST par Ian Barker
The UK can be a world leader in the development of AI says a report released today from the House of Lords Select Committee on Artificial Intelligence. The report sets out five principles for the use of AI which have some echoes of Asimov's laws of robotics. The principles are: Artificial intelligence should be developed for the common good and benefit of humanity. Artificial intelligence should operate on principles of intelligibility and fairness. Artificial intelligence should not be used to diminish the data rights or privacy of individuals, families or communities. All citizens should have the right to be educated… [Continue Reading] -

Star UK business names used to promote cryptocurrency scam
Publié: avril 13, 2018, 8:09pm CEST par Ian Barker
In a classic example of social engineering, well-known names from the BBC's Dragons' Den TV series and others are being used to advertise a cryptocurrency scam. Websites claiming to offer cryptocurrency investments are using images and false recommendations from prominent individuals including Deborah Meaden and Peter Jones from Dragons' Den, and Martin Lewis, the founder of MoneySavingExpert.com, without their consent. If you're in the UK you may have seen these ads served on BetaNews a few days ago, though we reported them to AdWords as soon as we became aware. Clicking on an ad takes you to a page made… [Continue Reading] -

More than 44 percent of businesses fall victim to email account takeovers
Publié: avril 13, 2018, 1:16pm CEST par Ian Barker
Targeted attacks launched via a compromised account were the most successful email attack vector in the past 12 months according to new research. The study carried out for email security company Agari by Osterman Research reveals that 44 percent of organizations have been victims of a successful ATO-based attack. Agari identifies five steps to ATO-based attacks, including account access, control, reconnaissance, targeted attacks and data exfiltration or fraudulent financial payments. The attacks come from four types of senders: strangers, employee webmail accounts, trusted third parties and insider business accounts. While strangers accounts send 90 percent of ATO-based attacks, trusted third… [Continue Reading] -

Integration of platforms delivers improved vulnerability handling
Publié: avril 12, 2018, 4:50pm CEST par Ian Barker
Security platform Illumio and cloud security and compliance platform Qualys are announcing a new integration that will enable organizations to visualize vulnerabilities across data centers and clouds. Threat data from the Qualys Cloud Platform is integrated with the Illumio Adaptive Security Platform’s application dependency mapping to show potential attack paths in real time. The integration delivers vulnerability maps, enabling organizations to see connections to vulnerabilities within and between applications. "Digital transformation leads to an explosion of connected environments where perimeter protection is no longer enough. The focus now needs to shift from securing network perimeters to safeguarding data spread across… [Continue Reading] -

Enterprises not prepared for fifth generation cyber threats
Publié: avril 12, 2018, 3:22pm CEST par Ian Barker
A new report reveals that 97 percent of organizations are not prepared for the latest multi-vector, fast-moving, mega-scale Gen V cyber threats targeting businesses. The 2018 Security Report from Check Point analyses the security threats and attacks that organisations globally are experiencing on their networks. It finds just three percent of enterprises are using threat prevention with cloud and mobile security which protects against large-scale, multi-vector Gen V attacks. "We're seeing a new generation of cyber-attacks: these Gen V attacks are multi-vector, fast-moving, and mega-scaled," says Peter Alexander, CMO of Check Point. "Despite this, 77 percent of CISOs expressed concern… [Continue Reading] -

New solution automates Kubernetes security
Publié: avril 12, 2018, 1:06pm CEST par Ian Barker
Kubernetes is one of the most popular container platforms, which means enterprises need fast and decisive responses when security incidents and potential attacks occur within their deployments. Container security specialist NeuVector is launching an enhanced security solution to protect Kubernetes environments by building on the unique NeuVector run-time security automation, which combines east-west traffic visibility with container process monitoring and vulnerability scanning. NeuVector 2.0 adds important new capabilities that include a Kubernetes incident response system alongside advanced process and file system protections to secure against new attack vectors. It adds new automated protections that detect exploits within containers, such as… [Continue Reading] -

Over 2.5 billion records stolen or compromised in 2017
Publié: avril 12, 2018, 12:23pm CEST par Ian Barker
Almost 2.6 billion records were stolen, lost or exposed worldwide in 2017, an 88 percent increase over the previous year. Although data breach incidents decreased by 11 percent, 2017 was the first year publicly disclosed breaches surpassed more than two billion compromised data records since Gemalto began its Breach Level Index in 2013. The index shows that over the past five years, nearly 10 billion records have been lost, stolen or exposed, with an average of five million records compromised every day. Of the 1,765 data breach incidents in 2017, identity theft represents the leading type of breach, accounting for… [Continue Reading] -

Cloud-based routing system optimizes web app performance
Publié: avril 11, 2018, 4:47pm CEST par Ian Barker
How well an online application or website performs has a strong influence on whether users become and remain customers. With the rise of SaaS and market demand for rich content delivery, even milliseconds of latency -- or, worse, downtime -- can dramatically impact user experiences and loyalty, brand reputation, conversions, and, ultimately, the bottom line. DNS solutions specialist NS1 is addressing this issue with the launch of Pulsar 2.0, a cloud-based routing engine that uses real user monitoring data to enable intelligent traffic management decisions for optimal application performance and maximum uptime. "Internet performance is highly variable and can be… [Continue Reading] -

Less than half of enterprises are aware of external sharing and DLP policy violations
Publié: avril 11, 2018, 4:00pm CEST par Ian Barker
Visibility and compliance challenges continue to haunt organizations, with only 44 percent of respondents claiming they have visibility into external sharing and DLP policy violations in their cloud application and environments. The figure comes from a new report produced by cloud access security broker Bitglass which also finds that 85 percent of organizations acknowledge they are unable to identify anomalous behavior across cloud applications. "Cloud security is here to stay as is evident by the concerns and challenges survey respondents highlighted," says Bitglass CMO Rich Campagna. "Enterprise security teams are concerned about the next-generation of cloud threats that pose a risk… [Continue Reading] -

Infoblox and McAfee enhance partnership for threat protection
Publié: avril 11, 2018, 3:09pm CEST par Ian Barker
Network control company Infoblox is announcing an enhanced partnership with McAfee to offer organizations an increased level of sophisticated threat intelligence, as well as faster response time to combat cyber threats. Using a combination of behavioral analytics, machine learning and up-to-date threat intelligence data at the DNS layer, the comprehensive solution can identify potentially infected devices and block DNS-based data exfiltration, including zero-day attacks. Suspicious traffic is redirected from devices to McAfee Web Gateway Cloud Services for deeper levels of content inspection including malware scanning and SSL inspection. Additionally, by sharing indicators of compromise and threat intelligence between the Infoblox… [Continue Reading] -

ZoneFox delivers improved intelligence and risk management to combat insider threats
Publié: avril 11, 2018, 12:55pm CEST par Ian Barker
One of the biggest problems companies face in securing their networks is the number of alerts generated which is why many are turning to AI solutions to cope with the workload. Scottish company ZoneFox is launching an updated version of its security platform that offers better risk management and enriched insights, further time savings and improved scalability. ZoneFox 4.0 employs user and entity behaviour analytics (UEBA) and machine learning, to provide 360-degree visibility across the network and combat insider threats. It combines alerts into one easy to understand user experience, providing simplified access to both policy and AI-based alerts. These… [Continue Reading] -

Zuckerberg Senate testimony shows politicians don't understand Facebook
Publié: avril 11, 2018, 11:48am CEST par Ian Barker
Dressed in a dark suit and looking pale-faced, Facebook chief Mark Zuckerberg was clearly expecting a tough grilling before the Senate committee. In fact he was largely let off the hook, facing a series of questions that mainly served to expose politicians' lack of understanding of the social network's technology. Zuckerberg began by apologizing for his company's failure to protect users' data. He admitted Facebook had made "a lot of mistakes" and that it "didn't do enough" to protect data privacy. However, a series of questions that exposed senators' lack of understanding of how Facebook works did little to put… [Continue Reading] -

Large organizations think SaaS is outpacing security
Publié: avril 10, 2018, 5:13pm CEST par Ian Barker
A new report finds that 64 percent of IT decision makers believe the pace of software as a service (SaaS) application adoption is outpacing their cybersecurity capabilities. The survey from cloud-based web security company iboss shows that 91 percent of IT decision makers agree they need to update security policies to operate in a cloud-first environment. Concerns about moving their organization to the cloud are expressed by 94 percent of IT decision makers, with 61 percent citing data privacy as the primary worry. On average, IT decision makers believe 36 percent of remote or mobile workers bypass security policies, but… [Continue Reading] -

How to spend like a cyber criminal
Publié: avril 10, 2018, 3:27pm CEST par Ian Barker
We all know that there's money to be made from cyber crime, with even entry level hackers being able to make as much as $42,000 a year. But what do they do with that money? An 11 month study by virtualization-based security specialist Bromium looks at what cyber criminals are earning, and what they spend it on. High earners can make up to $2m a year according to the report, with mid-level criminals making up to $900,000 -- more than double the US presidential salary -- and entry level hackers making $42,000. When it comes to spending, 15 percent of… [Continue Reading] -

IBM launches cloud ready 'skinny' mainframe
Publié: avril 10, 2018, 2:47pm CEST par Ian Barker
Despite changes brought about by the cloud, edge computing and distributed systems, the mainframe remains for many businesses, the most stable, secure and mature environment to support IT initiatives including the proliferation of blockchains. IBM is launching its newest cloud ready mainframe -- the IBM z14 Model ZR1 and IBM LinuxONE Rockhopper II, the latest additions to its family of z14 mainframe technology announced in 2017. The new systems feature a 19-inch industry standard, single-frame 'skinny' design allowing for easy placement into both cloud data centers and private cloud environments. "This will bring the power of the IBM Z to… [Continue Reading] -

New standard brings stronger authentication to browsers
Publié: avril 10, 2018, 1:13pm CEST par Ian Barker
In a move to bring simpler yet stronger web authentication to internet users, the FIDO Alliance and the World Wide Web Consortium (W3C) are launching a new standard called Web Authentication (WebAuthn). WebAuthn enables online service providers to offer FIDO Authentication through web browsers. FIDO Authentication makes web access more secure because it uses unique encrypted credentials for each site, eliminating the risk that a password stolen from one site can be used on another. WebAuthn defines a standard web API that can be incorporated into browsers and related web platform infrastructure. This gives users new methods to securely authenticate… [Continue Reading] -

Mobile phishing click rate increases 85 percent
Publié: avril 10, 2018, 12:47pm CEST par Ian Barker
A new report from mobile security specialist Lookout exposes the growing risk from phishing attacks on mobile devices, with an increase in the number of users clicking on URLs that bypass security controls. The mobile phishing URL click rate has increased 85 percent year-on-year. 56 percent of Lookout users received and clicked on their mobile device a phishing URL that bypassed existing layers of phishing defense. Of those mobile users that clicked on a mobile phishing URL, they did so an average of six times per year. In one enterprise experiment, over 25 percent of employees clicked on a link… [Continue Reading] -

17 percent of employees fall for social engineering attacks
Publié: avril 9, 2018, 3:04pm CEST par Ian Barker
Employees are still falling for social engineering techniques leading them to download malicious files, click phishing links, correspond with hackers, and even share contact information for their colleagues. Enterprise security specialist Positive Technologies imitated the actions of hackers by sending emails to employees with links to websites, password entry forms, and attachments. In total, 3,332 messages were sent. If the 'attacks' had been real, 17 percent of these messages would have led to a compromise of the employee's workstation and, ultimately, the entire corporate infrastructure. The findings show the most effective method of social engineering is to send an email… [Continue Reading] -

Consumer cryptomining attacks increase 4,000 percent
Publié: avril 9, 2018, 11:17am CEST par Ian Barker
We already know that cryptomining is currently flavor of the month among malware creators, but a new report released today by Malwarebytes puts some startling figures on the problem. On consumer systems cryptomining detections were up a massive 4,000 percent in the last quarter, while ransomware detections fell 35 percent over the same period. For businesses cryptomining detections rose 27 percent this quarter and ransomware detections 28 percent. However, Spyware is still the cybercriminals' favourite choice, with over 80,000 detections in January alone. "The main focus here is that criminals have moved towards cryptomining and drive-by mining in lieu of… [Continue Reading] -

Variant of Mirai botnet used to target financial sector in January
Publié: avril 5, 2018, 4:36pm CEST par Ian Barker
Researchers at Recorded Future believe that a Mirai botnet variant, possibly linked to the IoTroop or Reaper botnet, was utilized in attacks on at least one company, and probably more, in the financial sector in late January of this year. The botnet targeted one company using at least 13,000 devices, each with a unique IP address, and generated traffic volumes up to 30Gb/s. Recorded Future's Insikt Group of researchers found the attack was 80 percent comprised of compromised MikroTik routers, with the remaining 20 percent composed of various IoT devices including other routers, webcams, TVs, and DVRs. The report's authors… [Continue Reading] -

Cloud use and compliance drive enterprise encryption strategy
Publié: avril 5, 2018, 3:40pm CEST par Ian Barker
The need to protect sensitive data against cyber criminals, address complex compliance requirements, and guard against human error is driving enterprises to adopt encryption. A new study by cyber security company Thales eSecurity, based on research by the Ponemon Institute, shows that 43 percent of respondents report that their organization has an encryption strategy applied consistently across their enterprise. Among other findings are that 84 percent of respondents either use the cloud for sensitive and/or non-sensitive applications and data today, or will do so in the next 12-24 months. Also 61 percent of respondents are using more than one public… [Continue Reading] -

Retail sector leads in data breaches as criminals target corporate networks
Publié: avril 5, 2018, 3:10pm CEST par Ian Barker
The retail sector suffered the most breaches in 2017, accounting for 16.7 percent followed by the finance and insurance industry at 13.1 percent and hospitality at 11.9 percent. Geographically, North America is in the lead with 43 percent of breaches, followed by the Asia Pacific region at 30 percent, Europe, Middle East and Africa (EMEA) at 23 percent and Latin America at four percent. These are among the findings of the latest Trustwave Global Security Report. Among other highlights are that half of the incidents investigated involved corporate and internal networks (up from 43 percent in 2016) followed by eCommerce… [Continue Reading] -

21 percent of open source serverless applications have critical vulnerabilities
Publié: avril 4, 2018, 5:03pm CEST par Ian Barker
Serverless computing is increasingly popular because it eliminates infrastructure concerns. However, a new report raises worries about its security. According to an audit by serverless security company PureSec, more than one in five serverless applications has critical security vulnerabilities. An evaluation of 1,000 open-source serverless projects conducted by the PureSec threat research team finds that 21 percent of them contain one or more critical vulnerabilities or misconfigurations, which could allow attackers to manipulate the application and perform malicious actions. Six percent of the projects even had application secrets, such as API keys or credentials, posted in their publicly accessible code… [Continue Reading] -

Employees have too much access to sensitive data
Publié: avril 4, 2018, 1:21pm CEST par Ian Barker
Lax policies and a lack of control is giving far too many employees access to sensitive data according to the latest Global Data Risk Report from data security specialist Varonis. The report, based on analysis of Data Risk Assessments conducted by Varonis in 2017 for customers and potential customers on their file systems, uncovers some startling figures, with 58 percent of organizations found to have more than 100,000 folders open to all employees. In an average company the report finds 21 percent of all folders are open to everyone. In addition 41 percent have at least 1,000 sensitive files open… [Continue Reading] -

Hiring gamers may be the answer to the cyber security skills gap
Publié: avril 4, 2018, 12:26pm CEST par Ian Barker
A new survey from McAfee says that IT security staff report needing to increase their workforces by 24 percent to adequately manage their organization's cyber threats. Yet a skills crisis means 84 percent admit it's difficult to attract staff and 31 percent say they don't actively do anything to attract new talent. However, 72 percent of respondents say hiring experienced video gamers into the IT department seems like a good way to plug the cyber security skills gap. The threat landscape is growing, both in complexity and volume. According to the report, 46 percent of respondents believe that in the… [Continue Reading] -

New program helps companies meet cloud security goals
Publié: avril 3, 2018, 3:56pm CEST par Ian Barker
Infrastructure and development practices are changing as companies move towards cloud computing, DevOps, and on-demand SaaS delivery models. This means security and operations teams must integrate their approach to securing systems. Cloud security company Threat Stack is launching a Cloud SecOps Program to help companies integrate security and operations initiatives and reduce risk. The Cloud SecOps Program is the first end-to-end offering that provides deep security expertise alongside the Threat Stack Cloud Security Platform. The integrated solution enables companies to securely leverage modern infrastructure and DevOps at scale without recruiting hard-to-find security talent or struggling to interpret and integrate data… [Continue Reading] -

Breakthrough in AI cuts battery drain of mobile voice UIs
Publié: avril 3, 2018, 3:01pm CEST par Ian Barker
We've become increasingly used to technology that uses 'wake words' like, "Hey, Cortana" to initiate interaction. But this technology has, so far, failed to make a big impact in the mobile apps arena, the main reason being the battery drain created by having an app that's constantly listening. That could be about to change as Silicon Valley company Sensory is announcing a breakthrough in running its TrulyHandsfree wake word and speech recognition AI engine directly on Android and iOS smartphone applications at low-power. Until now, always-listening wake word solutions for apps required too much power to be practical, especially for… [Continue Reading] -

New platform delivers improved data management across clouds
Publié: avril 3, 2018, 2:29pm CEST par Ian Barker
Businesses are increasingly using multiple cloud platforms and so need a means of managing all of their data assets wherever they're located. Cloud development company JetStream Software is launching a new cross-cloud data management platform to give cloud service providers and enterprise cloud operations a better way to support workload migration, resource elasticity, and business continuity across multi-cloud and multi-data center set ups. The JetStream Cross-Cloud Platform provides an all-software, hypervisor-integrated solution for multi-cloud, multi-data center operations. The platform is designed to complement VMware cloud infrastructures including VMware Service Provider Partners (VSPPs) and VMware Cloud on AWS. The platform enables… [Continue Reading] -

The best and worst rated countries for internet surveillance
Publié: avril 2, 2018, 6:05pm CEST par Ian Barker
We all know that some countries censor their citizens' access to the internet. But which are the most intrusive when it comes to online surveillance? Consumer security site Security Baron has created an infographic showing the best and worst, along with those named by Reporters Without Borders as, 'enemies of the internet'. There are many results you might expect, China, Vietnam and Saudi Arabia being on the list of 'pervasive' sensors for example. Russia, Burma and Pakistan among others imposing 'substantial' censorship. What may surprise you are the 'selective' sensors, which include India, the US and UK. These three are… [Continue Reading] -

Microsoft opens up its AI training to the public
Publié: avril 2, 2018, 4:40pm CEST par Ian Barker
Businesses are increasingly interested in the opportunities offered by artificial intelligence across a wide range of uses. But there's an increasing shortage of the skills needed to implement AI. Microsoft is helping to address this problem by making its AI training program -- the Microsoft Professional Program in AI, previously only available to employees -- open to the public. The program provides job-ready skills and real-world experience to engineers and others who are looking to improve their skills in AI and data science. It operates through a series of online courses that feature hands-on labs and expert instructors. The training… [Continue Reading] -

Less than half of Android security apps offer effective protection
Publié: mars 30, 2018, 3:15pm CEST par Ian Barker
A new study from independent testing lab AV-Comparatives reveals that of over 200 Android security apps tested the majority are dubious, unsafe or ineffective. The company downloaded 204 apps from the Google Play store in January this year and found 84 of the apps detected over 30 percent of malicious samples, and had zero false alarms. 79 detected under 30 percent of malware samples and/or had a high false alarm rate. The remaining 41 apps have since been removed from the store. These are described by the report as very buggy, unsafe and ineffective apps that appear to have been… [Continue Reading] -

CloudBerry offers 50 percent discount for World Backup Day
Publié: mars 30, 2018, 11:30am CEST par Ian Barker
This Saturday's World Backup Day is set to raise awareness of the importance of backing up important documents. Backup solution specialist CloudBerry is marking the day by offering a 50 percent discount until April 2nd on its CloudBerry Backup program for Windows, Mac, and Linux. The company has also conducted a survey which finds that only 51 percent of internet users actively back up their data, although personal data backup has increased by 15 percent in 2018 compared to 2017. Users back up to the cloud four percent more than last year too. The results show 56 percent of respondents… [Continue Reading] -

DevOps survey highlights complexity and culture worries
Publié: mars 29, 2018, 4:46pm CEST par Ian Barker
Top barriers to DevOps adoption include stagnant organizational cultures and managing a jumble of legacy processes. A new survey of DevOps and IT professionals from sandbox software company Quali finds 22 percent of respondents cite organizational culture, 21 percent legacy processes, and 20 percent growing software complexity as their top concerns. Other worries include the lack of standardized mechanisms for continuous testing (13 percent); managing the setup, tear-down and automation during different stages of the DevOps lifecycle (13 percent); and lack of dedicated budgets for these projects (nine percent). DevOps teams are still highly dependent on IT assistance to help… [Continue Reading] -

Cryptocurrency mining booming in higher education
Publié: mars 29, 2018, 4:13pm CEST par Ian Barker
The higher education sector has seen a big increase in cryptocurrency mining activity according to a new report from AI security company Vectra. Vectra used its Cognito platform to monitor traffic and collect metadata from more than 4.5 million devices and workloads from customer cloud, data center and enterprise environments. It discovered that, of all the cryptocurrency mining detections, 60 percent occurred in higher education. Other sectors escaped lightly by comparison, with entertainment and leisure on six percent, financial services three percent, technology three percent, and healthcare two percent. The highest volume of attacker behaviors per industry is in higher… [Continue Reading] -

79 percent of healthcare pros worried about the security of their personal data
Publié: mars 29, 2018, 3:01pm CEST par Ian Barker
According to new research, 79 percent of healthcare professionals say they are concerned about the cyber security of their own healthcare information. At the same time, 68 percent believe their organizations are doing enough to protect patient privacy and personal information from cyber attackers. The study from identity protection company Venafi, carried out at the HIMSS Conference earlier this month, finds respondents are conflicted about the role of cyber security regulation. A third believe there is too much cyber security regulation in the health care industry and 29 percent feel there is not enough regulation. Yet 87 percent of respondents… [Continue Reading] -

Fewer than 15 percent of businesses are fully confident of recovering data in a disaster
Publié: mars 28, 2018, 5:40pm CEST par Ian Barker
In a new survey ahead of this Saturday's World Backup Day, data protection specialist Arcserve reveals that while downtime is a top concern, many businesses lack confidence in their ability to recover data. In the study of 600 channel partners and IT decision makers across America, Europe and Japan, 57 percent of respondents say they aren't confident in their ability to recover their business data in the event of a downtime or disaster event. Only just over 14 percent say they feel very confident they could recover their data. When channel partners were interviewed, over half (56 percent) reveal their… [Continue Reading] -

Druva unifies data management across clouds
Publié: mars 28, 2018, 4:02pm CEST par Ian Barker
Enterprises increasingly store data in more diverse and complex cloud environments. Data management platform Druva is launching a new version of its cloud platform offering an as-a-service solution that unifies data protection, management and intelligence capabilities for business-critical data. The latest version ensures that customers can view and manage their data across SaaS (Software-as-a-Service), PaaS (Platform-as-a-Service) and IaaS (Infrastructure-as-a-Service) to ensure their data is properly managed through its lifecycle, meets enterprise service level agreements, and achieves consistency of service regardless of where it's ultimately stored. "Moving data to the cloud is not a panacea," says Dave Packer, vice president of… [Continue Reading] -

Carbon Black improves integration with open APIs
Publié: mars 28, 2018, 3:17pm CEST par Ian Barker
Security teams are faced with an increasing range of problems, from the volume of attacks, to lack of visibility into networks and shortage of skills. Endpoint security specialist Carbon Black is launching its own Carbon Black Integration Network (CbIN), a technology partner program designed to improve cybersecurity through collective defense. It's powered by Carbon Black's open APIs and a Cb Predictive Security Cloud (PSC), various open source integrations are available via a GitHub repository. These include a watchlist-sharing framework, the ability to export all process execution and endpoint network connection events through a real-time Event Forwarder, and an option to… [Continue Reading] -

More than half of organizations suffer mobile attacks
Publié: mars 28, 2018, 12:56pm CEST par Ian Barker
Over half (57 percent) of organizations suspect their mobile workers have been hacked, or caused a mobile security issue, in the last 12 months according to a new study. The study by mobile connectivity specialist iPass shows that public Wi-Fi is the most common source of incidents, with 81 percent of respondents saying they had seen Wi-Fi related security incidents in the last year. Cafes and coffee shops (62 percent) rank as the venues where such incidents have occurred most. They are closely followed by airports (60 percent) and hotels (52 percent), with other locations on the list including railway… [Continue Reading] -

Intel contributes code to open source edge computing project
Publié: mars 27, 2018, 5:08pm CEST par Ian Barker
The rise of IoT devices is pushing more systems towards an edge computing model in order to handle the data created more effectively. While several open source projects exist to help solve pieces of the edge puzzle, no single project currently meets the need for a complete edge infrastructure solution. The Akraino Edge Stack community is a new project that aims to address this and today the Linux Foundation is announcing expanded industry support, along with Intel's commitment to open source major components of its Wind River Titanium Cloud portfolio of technologies and the Intel Network Edge Virtualization Software Development… [Continue Reading] -

New asset management platform lets businesses see and secure devices
Publié: mars 27, 2018, 4:29pm CEST par Ian Barker
One of the basic problems businesses face in preventing attacks is effective discovery and identification of their technology assets. This is made worse by the growth of BYOD and Internet of Things devices. Israel-based Axonius is looking to solve this problem with the launch of its Cybersecurity Asset Management Platform to enable customers to see and secure all their devices. "We started this company to solve a very specific, acute problem -- fragmentation," says Dean Sysman, CEO and co-founder of Axonius. "If you were to think back to the 1980s or 1990s, cyber security was easy. It was a simpler… [Continue Reading] -

Zoho launches revamped platform to create business mobile apps
Publié: mars 27, 2018, 3:43pm CEST par Ian Barker
Business operating system Zoho is launching an updated version of its Creator apps builder, delivering the ability to build native mobile apps to automate business processes. Zoho Creator 5 introduces a drag-and-drop interface to complement its HTML/CSS screen creator, and includes pre-built design elements like buttons, layouts, and reports that users can drag onto their page. Users can collate data from various sources within the app and display it in a single place. Once built, pages are completely customizable for mobile devices. For example, users can display five modules on the web, three on a tablet, and only the most… [Continue Reading] -

Top vulnerabilities shift focus from Adobe to Microsoft
Publié: mars 27, 2018, 3:02pm CEST par Ian Barker
A new report from threat intelligence specialist Recorded Future looks at the changing way in which attackers are using vulnerabilities. In contrast to previous years, most of the criminal exploit kits and phishing campaigns seen in 2017 have favored Microsoft products, rather than the Adobe Flash vulnerabilities which previous research showed as being the most popular. Overall 2017 has seen a 62 percent decline in exploit kit development, with only a few exploit kits including AKBuilder, Disdain, and Terror showing significant activity. Dark web forums and marketplaces though continue to offer both high and low-quality exploit kit options, with prices… [Continue Reading] -

McAfee brings machine learning to enterprise security
Publié: mars 27, 2018, 12:13pm CEST par Ian Barker
Cyber security company McAfee is announcing an expanded product portfolio that evolves security operations capabilities and allows for rapid response to today’s threats. McAfee's updated Enterprise Security Manager (McAfee ESM 11) uses a new data architecture optimized for scalability, performance, faster search, and collaboration. This is combined with the newly launched McAfee Behavioral Analytics, and enhanced McAfee Investigator, McAfee Advanced Threat Defense, and McAfee Active Response. All of this is aimed at helping security operation teams to optimize their security infrastructure, leverage automation, improve detection, streamline workflows, and harness the power of human-machine teaming to improve response time and overall… [Continue Reading] -

Almost six out of 10 organizations suffer ransomware attacks
Publié: mars 27, 2018, 11:23am CEST par Ian Barker
New research reveals that 56 percent of surveyed decision makers from IT and risk, fraud or compliance functions report that their organization has suffered a ransomware attack in the last 12 months, compared to under half (48 percent) who said the same in 2016. The study of 500 businesses in the UK, France, Germany and USA commissioned by SentinelOne and carried out by Vanson Bourne shows 69 percent say the most successful ransomware attack resulted in the attacker being able to encrypt some data, with five percent paying the ransom to decrypt the data. Of those whose organization has suffered a ransomware… [Continue Reading] -

One in three consumers owns two or more smart home devices
Publié: mars 26, 2018, 4:52pm CEST par Ian Barker
Smart home technology is catching on in a big way with a third of US consumers now having two or more smart devices, according to a new study. The Smart Home report from GfK Research shows a high level of awareness of the technology, with 58 percent of US consumers saying smart home technology is likely to change their lives in the next few years. The level of agreement with this statement is even higher (68 percent) among those aged 25 to 34, but teens and young adults (18 to 24) actually scored below average at 57 percent. Smart homes… [Continue Reading] -

Unsecured third-party IoT devices could pose major risks for organizations
Publié: mars 26, 2018, 3:15pm CEST par Ian Barker
According to new research, 97 percent believe unsecured IoT devices could be catastrophic for their organization, yet just 29 percent actively monitor for related third-party risks. The study conducted by the Ponemon Institute and risk assurance body Shared Assessments shows 81 percent of respondents say that a data breach caused by an unsecured IoT device is likely to occur in the next two years. The average number of IoT devices in the workplace is expected to increase to an average of 24,762 devices, up from 15,874 last year. Yet 49 percent of respondents don't keep an inventory of IoT devices and… [Continue Reading] -

Virtual data protection officer service helps UK businesses with GDPR compliance [Q&A]
Publié: mars 23, 2018, 5:33pm CET par Ian Barker
With GDPR coming into effect on 25th May, many organizations will find themselves needing to appoint a data protection officer in order to comply. But appointing full-time compliance staff can be a difficult and costly exercise. Which is why cyber security company ThinkMarble is launching a Virtual Data Protection Officer (VDPO) service. The service will offer UK businesses access to a skilled team of cyber security and risk mitigation lawyers that can act as their Data Protection Officer (DPO) under GDPR. The lawyers will work alongside ThinkMarble's multi-disciplinary team of security analysts, incident responders and penetration testers to provide a… [Continue Reading] -

Cryptocurrency industry hit hard by DDoS attacks
Publié: mars 23, 2018, 12:04pm CET par Ian Barker
Although it's relatively new, the cryptocurrency industry was the fifth most attacked by DDoS in the final quarter of 2017. Imperva's latest Global DDoS Threat Landscape Report finds the spike in cryptocurrency prices has attracted the attention of attackers. Also the number of exchanges has increased to 190, up from 70 in Q3. Of these, 24 exchanges have a daily turnover of more than $10 million. With an increasing number of targets, despite the volatility in the price of bitcoin, Imperva expects to see assaults directed at the cryptocurrency industry continue for the foreseeable future. "In the second half of… [Continue Reading] -

Legacy defenses can't keep pace with new cyber threats
Publié: mars 22, 2018, 5:03pm CET par Ian Barker
Attacks such as ransomware are able to bypass legacy security solutions because organizations are neglecting to patch, update, or replace their current products according to a new report. The study from cyber security company Webroot also shows cryptojacking gaining ground, with over 5,000 websites being compromised with JavaScript cryptocurrency miner CoinHive to mine Monero since September 2017. Polymorphism, which involves creating slightly different variants of malicious or unwanted files, has become mainstream too according to the report. In 2017, 93 percent of the malware encountered and 95 percent of potentially unwanted applications (PUAs) were only seen on one machine. This… [Continue Reading] -

Lack of investment in security training adds to skills gap
Publié: mars 22, 2018, 3:34pm CET par Ian Barker
Cyber security is seen as one of the biggest threats to business. Yet employees are not being supported by their organizations when it comes to investing in their continued education and career development. Crowd sourced IT and security training solution Cybrary, along with cyber security research body the Cyentia Institute, have produced a report looking at the cyber skills gap. The study of over 3,000 IT, security and other non-technical professionals finds that two out of three organizations admit finding qualified cyber security professionals is a struggle. In addition 80 percent of respondents don't feel adequately prepared to defend their organizations,… [Continue Reading] -

Malicious mobile apps decrease in final quarter of 2017
Publié: mars 22, 2018, 1:47pm CET par Ian Barker
A new report from digital threat management company RiskIQ states malicious mobile apps declined at the end of 2017. To reach these findings the firm analyzed 120 mobile app stores and it puts the decline down largely to a decrease in the inventory of AndroidAPKDescargar, the most prolific dealer of blacklisted apps. Feral apps -- those available for download outside of a store on the web -- fell in popularity for the first time in several quarters too, slipping from the number two spot and giving way to three other stores. The top stores hosting blacklisted apps are AndroidAPKDescargar with… [Continue Reading] -

Mainframes become more important to enterprises but staff shortages pose problems
Publié: mars 22, 2018, 11:39am CET par Ian Barker
The mainframe is becoming more important to large enterprises, with the percentage of organizations running at least half their business-critical applications on these platforms expected to increase next year. But the loss of skilled mainframe staff, and the failure to subsequently fill these positions, poses significant threats to application quality, velocity and efficiency. These findings come from a new report carried out for Compuware by Forrester which shows that 64 percent of enterprises surveyed will run more than half of their critical applications on the platform within the next year, up from 57 percent this year. In addition 72 percent… [Continue Reading] -

The nine biggest threats organizations face in the next two years
Publié: mars 21, 2018, 3:53pm CET par Ian Barker
The foundations of the digital world are set to be shaken in the next two years according to the findings of a new report from the Information Security Forum (ISF). The Threat Horizon 2020 report highlights nine major threats, broken down into three themes, that organizations can expect to face by 2020 as a result of developments in technology. The first theme is one of looming conflict, within which the report identifies threats from combined cyber and physical attacks, disruption of GPS satellites, and the weaponization of smart devices. Threats arising from cyber and physical attacks will combine to shatter… [Continue Reading] -

New developer tool aids deployment of AI applications
Publié: mars 21, 2018, 3:03pm CET par Ian Barker
There's increasing demand for AI and machine learning solutions from businesses, but often a shortage of skills is holding back implementation. Cloud computing specialist Paperspace is launching a new tool called Gradient to allow developers to tap into a dedicated cloud of AI solutions for building, training and deploying machine learning applications. "There's no denying that AI is the future of every industry, but today’s complex cloud ecosystem coupled with a massive skills gap are threatening innovation," says Daniel Kobran, co-founder of Paperspace. "You shouldn't need decades of experience to build intelligent applications. We designed Gradient to remove infrastructure bottlenecks… [Continue Reading] -

New partnership delivers data-driven insights into customer behavior
Publié: mars 20, 2018, 4:45pm CET par Ian Barker
Businesses have more data than ever about their customers, but it can be hard to extract meaningful insight from it. A new partnership between data warehousing company Snowflake Computing and data analytics platform Segment aims to give enterprises the ability to carry out rapid analysis of customer data at scale. Segment customers now have direct access to an infinitely elastic data warehouse built for the cloud, and Snowflake benefits from a single data connector that brings together more than 40 data sources through Segment’s single API. Through this partnership, customers are able to store and access their aggregated data in… [Continue Reading] -

Average website gets attacked 44 times a day
Publié: mars 20, 2018, 3:41pm CET par Ian Barker
The average website was attacked 44 times a day during the last quarter of 2017, according to new research from security specialist SiteLock. The company analyzed six million sites to identify trends in the behavior and tactics of attackers. Though the number of attacks represents a 25 percent decrease over the previous quarter, it still means a site could be attacked 16,000 times a year. "A decrease in attacks does not mean that websites are safer. In fact, it may even be the opposite," says Neill Feather, president of SiteLock on the company's blog. "Hackers are constantly trying new avenues… [Continue Reading] -

Automated simulation platform helps enterprises understand cyber risks
Publié: mars 20, 2018, 1:03pm CET par Ian Barker
Hackers and cyber criminals often seek to exploit human errors like misconfigurations, poor security practices and the use of shadow IT. In order to help businesses assess the risk XM Cyber is launching an automated advanced persistent threat (APT) simulation platform, HaXM, to continuously expose all attack vectors, above and below the surface. HaXM uses advanced attack techniques to expose the most critical blind spots. In the process, it provides data-driven remediation that focuses on an organization's most critical assets, reduces its IT risk and enables it to optimize its cyber resources. "The best way to prevent a cyber attack… [Continue Reading] -

Picking through the haystack -- the role of AI in cyber security [Q&A]
Publié: mars 19, 2018, 11:13am CET par Ian Barker
Over the past year or so the idea of using artificial intelligence as an aid to cyber security has gained a lot of support. But what role does AI and machine learning have, and what will the future of security look like when it's in widespread use? We spoke to Gene Stevens, co-founder and CTO of network security company ProtectWise to find out. BN: What's the background to ProtectWise? GS: ProtectWise is about five years old, we've been working on bringing enterprise security to large scale, Fortune 2000 businesses. We've found a way of shifting the core analytic security functionality… [Continue Reading] -

How cyber criminals launder their gains
Publié: mars 16, 2018, 12:46pm CET par Ian Barker
The proceeds of cyber crime make up an estimated eight to 10 percent of total illegal profits laundered globally each year, amounting to an estimated $80-$200 billion. This is among the findings of a new report, commissioned by virtualization-based security company Bromium, into the economics of cyber crime and how criminals launder and 'cash out' the profits of their endeavors. Key findings are that virtual currencies have become the primary tool used by cyber criminals for money laundering. However, they are moving away from Bitcoin to less well-known virtual currencies, like Monero, that provide greater anonymity. In-game purchases and currencies… [Continue Reading] -

The shady world of mobile app tracking
Publié: mars 15, 2018, 4:57pm CET par Ian Barker
Most of us click on the Agree button when we install apps without actually reading the privacy agreement. But some new research from Princeton University and other bodies reveals that many apps use a network of third-party services -- often invisible to the user -- that provide analytics, social network integration, and monetization. Often, these mobile advertising and tracking services have an intimate view of the user's activity and are keen to harvest personal data. In all, the team identified 2,121 trackers -- 233 of which were previously unknown to popular advertising and tracking blacklists. These trackers collect personal data including… [Continue Reading] -

Businesses are failing to understand the impact of cloud outages
Publié: mars 15, 2018, 3:42pm CET par Ian Barker
Many firms in the UK are failing to understand their responsibilities in relation to systems in the cloud, according to a new study. The research from Veritas Technologies shows that 66 percent of respondents believe that dealing with cloud service interruptions is the primary responsibility of their cloud service provider. In addition 76 percent believe that their organization's cloud service provider is responsible for ensuring that their workloads and data in the cloud are protected against outages. 77 percent of UK respondents have not fully evaluated the cost of a cloud outage to their business and are therefore ill prepared… [Continue Reading] -

Netskope brings continuous assessment and monitoring to IaaS security
Publié: mars 15, 2018, 3:13pm CET par Ian Barker
Cloud access security specialist Netskope is launching an expansion of its Infrastructure as a Service security offering to add continuous security assessment and monitoring capabilities. With this release customers can use Netskope for IaaS to continuously assess their infrastructure-as-aservice (IaaS) and platform-as-a-service (PaaS) configuration in AWS, with Microsoft Azure to follow soon. It includes the ability to spot infrastructure misconfigurations and vulnerabilities that lead to potential compromise. Netskope is the only cloud access security broker (CASB) with a single platform able to protect sanctioned and unsanctioned software-as-a-service (SaaS), PaaS, and IaaS environments. "The Netskope Cloud Security Platform was designed to… [Continue Reading] -

SAP CRM servers vulnerable to online attack
Publié: mars 14, 2018, 5:10pm CET par Ian Barker
Researchers at cyber security platform ERPScan have disclosed details of two vulnerabilities that allow compromise of the widely used SAP CRM system. CRM is considered as a most critical asset by businesses. A data breach into CRM can be disastrous as it can destroy trust in the business and severely tarnish the brand as well as raising compliance issues. ERPScan made the disclosure at the Troopers security conference. The research indicates that over 500 vulnerable systems are currently available on the internet without a fix. The vulnerability exploits a flaw in the SAP NetWeaver platform, used to automate business processes.… [Continue Reading] -

Misconfigured security measure leads DDoS amplification attacks to soar at end of 2017
Publié: mars 14, 2018, 3:49pm CET par Ian Barker
DDoS attacks using domain name server (DNS) amplification increased more than 357 percent in the fourth quarter of 2017 compared to the previous year. A new report by protection specialist Nexusguard attributes the rise to the use of Domain Name System Security Extensions (DNSSEC), a technology that's intended to add integrity and security to the DNS protocol. If not correctly configured, however, DNSSEC-enabled servers can be deliberately targeted to reflect amplification attacks, due to the large size of the responses they generate. While the overall number of DDoS attacks has fallen 12 percent compared to the same period last year,… [Continue Reading] -

Passwords are stronger in Minneapolis
Publié: mars 14, 2018, 1:26pm CET par Ian Barker
New research reveals the US cities that are best at password security, with Minneapolis topping the list. The study by password manager Dashlane scores cities based on several metrics, including average password strength and average number of reused passwords. It examines password security in America's 20 most populous metropolitan areas as well as 20 additional cities that are home to some of the country’s most important companies and government agencies. While Minneapolis tops the list of most populous cities, the findings show that your password needn't make you sleepless in Seattle -- which came second. San Francisco is placed third… [Continue Reading] -

Critical vulnerability found in Windows Remote Desktop Protocol
Publié: mars 13, 2018, 5:59pm CET par Ian Barker
Researchers at threat prevention specialist Preempt have discovered a flaw in Credential Security Support Provider protocol (CredSSP), which is used by Remote Desktop and WinRM in their authentication processes. An attacker with man-in-the-middle control over the session could use this to gain the ability to remotely run code on the compromised server masquerading as a legitimate user. With remote desktop a popular application to perform remote logins, this vulnerability presents a major concern. This could leave enterprises vulnerable to a variety of threats from attackers including lateral movement and infection on critical servers or domain controllers. The vulnerability affects all… [Continue Reading] -

Many smart devices can be hacked in 30 minutes
Publié: mars 13, 2018, 5:09pm CET par Ian Barker
Off-the-shelf smart devices that include baby monitors, home security cameras, doorbells, and thermostats can be easily hacked according researchers at Israel's Ben-Gurion University of the Negev (BGU). As part of their ongoing research into detecting vulnerabilities in devices and networks expanding in the smart home and Internet of Things (IoT), the BGU researchers disassembled and reverse engineered many common devices and quickly uncovered serious security issues. "It is truly frightening how easily a criminal, voyeur or pedophile can take over these devices," says Dr Yossi Oren, a senior lecturer in BGU's Department of Software and Information Systems Engineering. "Using these… [Continue Reading] -

70 percent of companies would fail an access control audit
Publié: mars 13, 2018, 2:53pm CET par Ian Barker
A new study into privileged access management from account protection specialist Thycotic shows that while over 60 percent of organizations must satisfy regulatory compliance requirements surrounding privilege credential access, a worrying 70 percent would fail an access controls audit. Access to privileged accounts allows more rights and permissions than those given to standard business users, yet 51 percent fail to use a secure logon process for these accounts. "Failing an audit restricts organizations from doing business, it restricts them from government access to request information or bid for contracts, in the payments sector it could hinder their operations," Joseph Carson,… [Continue Reading] -

Flaws could turn smart cameras into data-stealing spy tools
Publié: mars 12, 2018, 4:47pm CET par Ian Barker
Security vulnerabilities in some popular smart cameras, used as baby monitors and for security surveillance, could lead to them being exploited by hackers. Research from Kaspersky Lab has found multiple issues with cameras, manufactured by Korean company Hanwha Techwin, that could allow attackers to obtain remote access to video and audio feeds from the cameras, remotely disable the devices and execute arbitrary malicious code on them. The flaws would also allow attackers to steal personal information such as users' social network accounts and information which is used to send users notifications. Hackers could also remotely 'brick' vulnerable cameras. It's important to… [Continue Reading] -

McAfee tracks eight new threats every second as cyber criminals embrace innovation
Publié: mars 12, 2018, 11:37am CET par Ian Barker
Thanks to a surge in healthcare attacks, cryptocurrency mining and fileless malware, McAfee Labs latest quarterly threat report has seen an average of eight new threat samples per second. Highlights of the report include the healthcare sector experiencing a 211 percent increase in disclosed security incidents in 2017, and fileless malware leveraging Microsoft PowerShell growing 267 percent in the fourth quarter. New ransomware grew 35 percent and ended 2017 with 59 percent growth year on year, however towards the end of the year cryptocurrency mining took off as criminals followed the money. Away from the desktop, new mobile malware decreased… [Continue Reading] -

Dropbox and Salesforce partner to boost enterprise collaboration
Publié: mars 9, 2018, 4:13pm CET par Ian Barker
Cloud platform Dropbox and leading CRM provider Salesforce have announced a new partnership to connect their platforms, allowing companies of all types and sizes to collaborate and connect with their customers across sales, service, marketing, commerce, and more. Users will be able to create branded, customized Dropbox folders within Salesforce Commerce Cloud and Marketing Cloud using a new digital asset engagement solution. Folders will be available to both internal teams and external partners. Because it allows two-way workflows it ensures content stays relevant and up-to-date, whichever platform the user is working in. For example, a retailer using Salesforce Commerce Cloud… [Continue Reading] -

China manipulates vulnerability data to hide intelligence service involvement
Publié: mars 9, 2018, 3:40pm CET par Ian Barker
It's long been known that the Chinese government has links to hacker groups, but new research into the country's national vulnerability database (CNNVD) reveals evidence of data being changed to hide influence by the country’s intelligence service. Research by security intelligence specialist Recorded Future back in November finds that CNNVD is faster than the US national vulnerability database (NVD) in reporting vulnerabilities -- NVD trails CNNVD in average time between initial disclosure and database inclusion (33 days versus 13 days). However, during a follow up to that research, Recorded Future has discovered that China has a process for evaluating whether… [Continue Reading] -

Microsoft Windows Defender fights off massive currency miner attack
Publié: mars 9, 2018, 11:41am CET par Ian Barker
Microsoft has stopped a large scale malware distribution campaign that tried to infect almost 500,000 Windows PCs with a cryptocurrency miner. Windows Defender antivirus software detected 80,000 instances of several Trojans with the payload known as Dofoil or Smoke loader, at noon PST on March 6. Over the next 12 hours, Defender picked up over 400,000 more encounters with the Trojan, mainly in Russia, but also in Turkey and Ukraine. Dofoil uses a technique known as 'process hollowing' on the legitimate explorer.exe binary. The technique creates a new instance of the legitimate prigram but swaps out its code with malware.… [Continue Reading] -

Mobile ad Trojan numbers fall but monetization techniques improve
Publié: mars 8, 2018, 4:28pm CET par Ian Barker
Advertising Trojans were the top mobile malware threat in 2016, however, new figures from Kaspersky Lab show their numbers declined last year but their creators turned to improved monetization methods. Taking advantage of super-user rights to secretly install various applications or bombard an infected device with ads to make use of the smartphone impossible, ad trojans have become a major threat and are also extremely difficult to detect and remove. Kaspersky's report shows the overall number of mobile advertising Trojans exploiting super-user rights declined in 2017 compared to the previous year. This decline seems to have been triggered by an… [Continue Reading] -

Malwarebytes brings endpoint protection to Macs
Publié: mars 8, 2018, 3:07pm CET par Ian Barker
Among IT professionals Malwarebytes is one of the most trusted names for malware detection and removal. Perhaps less well known is that it also provides endpoint protection for businesses and it's now extending that to cover Apple Mac computers. Based on Malwarebytes' telemetry, malware targeting Mac operating systems has more than doubled from 2016 to 2017. In 2017 alone, Mac threats increased by more than 270 percent. New threats identified in the first two months of 2018 indicate a similar pace of development. The company's new Mac product features a single dashboard that unites Endpoint Protection for Windows and Mac… [Continue Reading] -

Businesses under pressure to 'consumerize' logins
Publié: mars 7, 2018, 5:01pm CET par Ian Barker
Almost two-thirds (64 percent) of IT leaders say their security teams are considering implementing consumer-grade access to cloud services for employees. According to the 2018 Identity and Access Management Index from digital security company Gemalto 54 percent of respondents believe that the authentication methods they implement in their businesses are not as good compared to those found on popular sites including Amazon and Facebook. Authentication methods applied in the consumer world can be applied to secure access to enterprise resources 70 percent of IT professionals believe. But despite this, 92 percent of IT leaders express concern about employees reusing personal… [Continue Reading] -

Enterprises turn to multi-cloud environments despite extra complexity
Publié: mars 7, 2018, 4:35pm CET par Ian Barker
Businesses have been adopting the cloud for many reasons, the results of a new study show that large enterprises are increasingly turning to multiple different clouds despite the complexity this creates. The report from hybrid cloud management company Scalr shows several reasons for this approach. Half of enterprises rank disaster recovery as the top reason for implementing multiple clouds, with having a secondary platform for test/dev coming in as a close second at 46 percent. More than one-third (36 percent) cite federation of IT, such as extending self-service to teams without sacrificing policy-based controls, as a main driver. To address… [Continue Reading] -

On the dark web your identity could cost less than the price of an iPhone X
Publié: mars 7, 2018, 3:10pm CET par Ian Barker
What's your identity worth? Not very much according to research by VPN comparison service Top10VPN.com. The site has released its first Dark Web Market Price Index which reveals that an entire personal identity can be bought for just $1,200. A range of details including bank account logins, passport details and even access to your Netflix account are worth money to bidders on dark web markets -- but the low price point of this information sparks concerns that valuable personal details are all too readily available online. In terms of individual accounts, Paypal logins are among the most valuable, changing hands… [Continue Reading] -

McAfee delivers added security for Microsoft Azure
Publié: mars 7, 2018, 1:14pm CET par Ian Barker
Azure is a popular cloud platform for business, but firms need to ensure their applications, underlying cloud infrastructure and data are protected. McAfee is addressing this by extending its Cloud Security Platform to consistently protect Azure, delivering an extensive solution to secure Infrastructure-as-a-Service (IaaS), Platform-as-a-Service (PaaS) and Software-as-a-Service (SaaS). This is the first joint solution since McAfee's acquisition of Skyhigh Networks, and shows the company's commitment to enhancing its cloud security portfolio. "Moving applications, data and workloads to the cloud exposes enterprises to new threats and risks," says Rajiv Gupta, senior vice president of the cloud security business unit, McAfee.… [Continue Reading] -

Perception of cloud security challenges differs across industries
Publié: mars 7, 2018, 11:47am CET par Ian Barker
The cloud brings many benefits to businesses, but it also brings with it risks, the biggest of which concerns the security of information. A new survey from cloud governance specialist Netwrix looks at how different sectors and geographies deal with cloud security. There are interesting differences in the perception of risk across industries. Malware is most feared by health care organizations (61 percent) and government bodies (60 percent). But 62 percent of educational institutions see their own employees to be the biggest threat to cloud security, the largest share among all the industries surveyed. This result is explained by the… [Continue Reading] -

Ransomware gives way to miners as cyber criminals follow the money
Publié: mars 6, 2018, 4:25pm CET par Ian Barker
Cyber criminals have started using sophisticated infection methods and techniques borrowed from targeted attacks in order to install mining software on attacked PCs within organizations says Kaspersky Lab. Some 2.7 million users have been attacked by malicious miners in 2017, according to Kaspersky's data. That's around 50 percent higher than in 2016 (1.87 million). But at the same time ransomware attacks have seen a decline. Spikes in cryptocurrency values have made these attacks lucrative. Users have been falling victim as a result of adware, cracked games and pirated software used by cyber criminals to secretly infect their PCs. Kaspersky reckons the… [Continue Reading] -

AlgoSec launches network security policy management as a service
Publié: mars 6, 2018, 3:27pm CET par Ian Barker
Managing security policy can be a headache for organizations with lots of users. But now business-driven security policy management specialist AlgoSec is launching an as-a-service policy management solution. AlgoSaaS allows enterprise organizations to quickly and easily get the benefits of cloud-based security service offerings. It needs minimal end-user maintenance and is scalable to cope with business growth. Users can automatically manage their network security policies, and align them with their business processes and objectives. AlgoSaaS provides a single pane view that gives users visibility across their entire network security infrastructure, including business applications and their network connectivity flows. It works… [Continue Reading] -

Reliable SMS interception leaves 2FA accounts open to attack
Publié: mars 6, 2018, 2:53pm CET par Ian Barker
Text messages via SMS are often used as part of two-factor authentication strategies to protect login accounts. But a new and worrying study from Positive Technologies shows that real-world attempts to intercept SMS messages are 100 percent successful. The underlying technology behind mobile networks -- Signaling System No 7 (SS7) -- has had known flaws for some time. This latest report looks at major mobile operators in Europe and the Middle East and reveals that virtually every network examined allows eavesdropping on conversations and reading of incoming text messages. Fraud was found to be possible on 78 percent of networks,… [Continue Reading] -

Almost half of US healthcare organizations breached in the past year
Publié: mars 5, 2018, 3:24pm CET par Ian Barker
A new report from information security specialist Thales e-Security reveals that 48 percent of US healthcare organizations reported getting breached in the last year, more than 2.5 times the rate from two years ago. In addition 56 percent report feeling either 'very' or 'extremely' vulnerable to data breaches. More than three-quarters (77 percent) reported at least one breach at some time in the past. This is the highest percentage among all US vertical industries polled in this year’s report. The healthcare industry has been turning its attention towards embracing technologies, including cloud, big data, the IoT and containers in order… [Continue Reading] -

Employees lack awareness of cyber security policies and threats
Publié: mars 2, 2018, 4:28pm CET par Ian Barker
Nearly half (46 percent) of entry-level employees, and 28 percent of all employees, don't know if their company has a cyber security policy, according to new research. The study of 1,000 full time workers from B2B research firm Clutch also shows that employees at all levels of an organization are likely unaware of the IT security threats their companies potentially face. Nearly two-thirds of employees (63 percent) surveyed say they don't know if the quantity of IT security threats their companies face will increase or decrease over the next year. Additionally, among entry level employees, 87 percent say they don't… [Continue Reading] -

New solution streamlines enterprise data integration
Publié: mars 1, 2018, 4:09pm CET par Ian Barker
Companies operate in an increasingly complex data environment, where information can exist across multiple systems and locations. This can mean the movement of data between a variety of sources and targets, such as data lakes and cloud-based infrastructures, without impacting daily business operations. Data integration specialist HVR is addressing this need by launching a distributed architecture to provide easy management and control of data movement. "Data remains the singular most important piece of modernization, even more so than the database or sources and targets, which will continue to evolve," says Anthony Brooks-Williams, CEO of HVR. "Data Lakes and the cloud… [Continue Reading] -

HVR solution streamlines enterprise data integration
Publié: mars 1, 2018, 4:09pm CET par Ian Barker
Companies operate in an increasingly complex data environment, where information can exist across multiple systems and locations. This can mean the movement of data between a variety of sources and targets, such as data lakes and cloud-based infrastructures, without impacting daily business operations. Data integration specialist HVR is addressing this need by launching a distributed architecture to provide easy management and control of data movement. "Data remains the singular most important piece of modernization, even more so than the database or sources and targets, which will continue to evolve," says Anthony Brooks-Williams, CEO of HVR. "Data Lakes and the cloud… [Continue Reading] -

Imaging systems present biggest security risk among connected medical devices
Publié: mars 1, 2018, 3:00pm CET par Ian Barker
A new report from IoT security specialist ZingBox looks at the security of connected medical devices, from infusion pumps and patient monitors to imaging systems and medical device gateways. The most common types of risk originate from user practice issues (such as using embedded browsers on medical workstations to surf the web, conducting online chat or downloading content), accounting for 41 percent of all security issues. This is followed by outdated operating systems or software such as the use of legacy Windows versions, obsolete applications and unpatched firmware. These issues account for 33 percent of all security risks found on… [Continue Reading] -

Financial targets account for more than half of phishing attacks
Publié: mars 1, 2018, 11:59am CET par Ian Barker
More than half of phishing attacks in 2017 were aimed at getting hold of financial information according to a new report. Kaspersky Lab's anti-phishing technologies detected more than 246 million user attempts to visit different kinds of phishing pages, with 54 percent being attempts to visit a financial-related website, compared to 47 percent in 2016. Attacks against banks, payment systems and e-shops grew by 1.2, 4.3, and 0.8 percentage points respectively and made up the top three categories in overall phishing attacks detected. Meanwhile attacks against internet portals, including search engines and social networks fell from second place in 2016… [Continue Reading] -

Over half of enterprises willing to sacrifice security for speed
Publié: février 28, 2018, 4:36pm CET par Ian Barker
A new survey reveals that 52 percent of companies admit to cutting back on security measures to meet a business deadline or objective. The report into SecOps (Security Operations) from intrusion detection company Threat Stack also reveals that 68 percent of companies say their CEO demands that DevOps and security teams don’t do anything that slows the business down. This pressure comes from lower down the business pyramid too, with 62 percent of companies also admitting their operations team pushes back when asked to deploy security technology. "Businesses have grappled with the 'Speed or Security' problem for years but the… [Continue Reading] -

Mid-market organizations hardest hit by ransomware
Publié: février 28, 2018, 3:56pm CET par Ian Barker
Mid-market organizations -- those with 1,000-5,000 employees -- have been hit the hardest with ransomware in 2017, with 29 percent experiencing a ransomware attack, according to a new report. Security awareness training company KnowBe4 has released its 2018 Threat Impact and Endpoint Protection Report which shows organizations in manufacturing, technology and consumer-focused industries experienced the most ransomware attacks. On average, 16 workstations, 5 servers and 22 users within an organization were affected in any given attack with an average downtime of 14 hours. The organizations suffering the most downtime hours were again mid-market and enterprise (5000+ employees) organizations. The more… [Continue Reading] -

Zoho launches an AI-powered assistant for sales teams
Publié: février 28, 2018, 3:21pm CET par Ian Barker
Popular business platform Zoho is aiming to make its CRM offering more attractive to sales teams with the launch of a new AI powered conversational interface. Zia Voice adds speech and chat capabilities to Zia, Zoho's AI-powered sales assistant. Zia can now also predict deal closures and analyze email sentiment. Zia is able to answer questions on everyday CRM information like new leads created, average deal revenue, or even monthly forecasts and converses with salespeople via simple chat and voice messages. It’s able to analyze interaction patterns and the progress of a lead or deal in the pipeline, and suggests the… [Continue Reading] -

The rapid growth of digital data
Publié: février 28, 2018, 11:26am CET par Ian Barker
The volume of digital information in the world is growing at a scarily fast rate. In fact 90 percent of the digital data that exists worldwide today was created within the last two years -- and 2.5 quintillion bytes of extra data are created each and every day. We browse websites, stream music and video, and post on social media all of which contributes to this deluge. But how did data get to be such a key part of modern life? Digital asset management specialist MerlinOne has created an infographic looking at the history of digital content from its inception… [Continue Reading] -

New vulnerability allows attackers to trick single sign on systems
Publié: février 27, 2018, 4:14pm CET par Ian Barker
Single sign on (SSO) is popular with businesses as it allows control of access to multiple resources without the need for lots of different credentials. But researchers at Duo Security have uncovered a vulnerability that can allow attackers to trick systems based on the commonly used SAML (Security Assertion Markup Language) into giving them a higher level of access. Armed with an existing ID and password an attacker with only moderate technical skill can fool the SAML system into authenticating as another user without needing to know that user's password. Since most corporate systems have a standard pattern for user… [Continue Reading] -

65 percent of organizations unable to comply with GDPR 'right to be forgotten'
Publié: février 27, 2018, 3:07pm CET par Ian Barker
One of the key planks of the upcoming GDPR legislation is the right to removal of personal data, the so-called, 'right to be forgotten'. But a new study from big data application provider Solix Technologies reveals that 65 percent of organizations are unsure if an individual's personal information can be purged from all their systems. Among other findings are that 22 percent of organizations are unaware that they must comply with GDPR, even if they are based outside of the European Union but hold data of EU citizens. 38 percent say that all their personal data under the new GDPR… [Continue Reading] -

More than half of IT pros believe their organization was breached at least once in 2017
Publié: février 27, 2018, 1:43pm CET par Ian Barker
A new study of 165 IT and security professionals at medium-sized companies across the US reveals that 53 percent believe their organization was breached one or more times in 2017. The report from security-as-a-service company Cygilant shows a lack of confidence in respondents' ability to protect customer data, with only 16.6 percent very confident that they can successfully protect customer data. In addition 68 percent of those surveyed cite a lack of company resources, including budget and time, as a top cyber security challenge. 80.5 percent say they have underfunded IT security budgets or no budget at all. Among other… [Continue Reading] -

Securing corporate WANs is top challenge for network pros
Publié: février 27, 2018, 1:03pm CET par Ian Barker
Growing complexity is a major issue in securing and managing corporate wide area networks according to a new survey. The study by software-based networking and security specialist Versa Networks shows 68 percent of respondents think deploying and managing network security devices at branch locations is the most challenging aspect of WAN management, followed by increasing costs (53 percent) and information security risks at branch locations (49 percent). 74 percent of organizations surveyed say they utilize a direct internet connection for branch offices and simultaneously must deploy more devices to combat threats and other risks. This growing number of devices increases the… [Continue Reading] -

New intelligence tool improves monitoring of hybrid environments
Publié: février 27, 2018, 11:40am CET par Ian Barker
Digital transformation means businesses need to be able to handle rapid change across a variety of environments. IT operations specialist OpsRamp is launching a new Unified Service Intelligence tool that offers a simpler way to monitor and manage operational environments in a hybrid world. The SaaS solution combines service availability and performance data including discovery, hybrid monitoring and service health dashboards, with incident management capabilities including event correlation, alert notifications and service level management. "The adoption of modern workloads like cloud, containers and serverless have exponentially increased the rate of change. IT teams will need the right tools that are… [Continue Reading] -

FileCloud launches enterprise edition for secure collaboration in large businesses
Publié: février 26, 2018, 2:58pm CET par Ian Barker
File sharing and sync platform FileCloud is launching a new edition aimed at IT administration, management and compliance across enterprise-level systems with over 1000 users. FileCloud Enterprise Edition is cloud agnostic, so it allows businesses to keep their data on any infrastructure of their choice including public, private and hybrid clouds while giving them full control. "Managing secure collaborations across enterprise environments is critical and keeps many CIOs awake at night," says Madhan Kanagavel, CEO of FileCloud. "With just a few clicks, FileCloud's Enterprise Edition helps IT administrators configure user settings, integrate branch office file servers, manage policies and deploy… [Continue Reading] -

Businesses face rising costs from DDoS attacks
Publié: février 23, 2018, 3:11pm CET par Ian Barker
The financial impact of a DDoS attack is continuing to rise globally -- totaling on average over $120,000 per attack for SMBs and over $2 million for enterprises. These findings come from a study by Kaspersky Lab which shows that the cost of a DDoS attack in 2017 was almost $20,000 higher for SMEs than in 2016 and more than half a million dollars more for enterprises. Asked about the specific consequences experienced as a result of a DDoS attack, most organizations (33 percent) claim that the cost incurred in fighting the attack and restoring services is the main burden,… [Continue Reading] -

Hackers hide malware with code signing and SSL certificates
Publié: février 22, 2018, 4:17pm CET par Ian Barker
2017 saw a sudden increase in code signing certificates being used as a layered obfuscation technique to deliver malicious payloads. Recorded Future's Insikt Group has been investigating the criminal underground and has identified a number of vendors currently offering both code signing certificates and domain name registration with accompanying SSL certificates. Particularly interesting is that researchers have found that certificates available on the digital underground are not stolen from legitimate owners, but are created for a specific buyer on request and are registered using stolen corporate identities, making traditional network security appliances less effective at detecting them. "It's been generally… [Continue Reading] -

US government agencies see 20 percent rise in data breaches
Publié: février 22, 2018, 3:25pm CET par Ian Barker
US Federal agencies reported more breaches last year (57 percent) than any other industry sector by a wide margin, well ahead of the global average of 36 percent according to a new report. Yet the findings from Thales eSecurity show that only 42 percent of government respondents claim to be 'very' or 'extremely' vulnerable, compared to 68 percent of US respondents across the board. In the past year 57 percent of federal respondents have experienced a data breach. This marks a big jump from the 2017 report where 34 percent were breached and the 2016 report (18 percent). In contrast… [Continue Reading] -

Ericsson launches marketplace to unlock the cellular IoT ecosystem
Publié: février 22, 2018, 1:39pm CET par Ian Barker
The IoT marketplace has grown, and is continuing to grow, at a rapid rate and this means developers and service providers have often struggled when it comes to collaboration with other networks and devices. Communication services company Ericsson is using MWC 2018 to launch a new IoT Accelerator Marketplace aimed at making it easier for service providers to find IoT apps from the global ecosystem. For application developers and partners it is a window into an IoT ecosystem to connect with service providers through one single platform, exposing global cellular connectivity APIs. It also includes monetization and settlement capabilities to… [Continue Reading] -

HR and marketing lead the way in cloud service adoption
Publié: février 22, 2018, 11:35am CET par Ian Barker
Marketing and HR have the highest number of cloud services per organization, at 121 and 139 respectively. This is among the findings of the latest Netskope Cloud Report which also highlights that because many of these apps are user-led they are flying below the radar of the IT department and could be in breach of policies and controls. Many of the top HR apps in use, like SuccessFactors and Workday, contain personal data, necessitating DLP (Data Loss Prevention) and access controls to ensure usage of that data remains in compliance. Similarly, many marketing apps qualify as shadow IT, or unsanctioned… [Continue Reading] -

Wireless routers seen as essential as smart devices take off
Publié: février 21, 2018, 5:26pm CET par Ian Barker
The wireless router is the number one technology US consumers can’t live without for more than day, according to managed services provider iQor. A working router is necessary for consumers to enjoy smart devices and the connected lifestyle, including smart TVs and streaming devices, multiplayer gaming, tablets, voice controlled virtual assistants and smart speakers, IoT-enabled security systems, and more. According to the survey 64 percent of US adults say they couldn’t be without Wi-Fi for a day. "The fact that the WiFi-connected smart home is the most important technology consumers don't want to be without–over the smartphone–is a shift that… [Continue Reading] -

The $600 billion cost of global cyber crime
Publié: février 21, 2018, 4:01pm CET par Ian Barker
We all know cyber crime is a major problem, but just how big is its worldwide impact? A new report from McAfee and the Center for Strategic and International Studies (CSIS) reckons it costs businesses almost $600 billion a year or 0.8 percent of global GDP. Global losses in 2014 were estimated at $445 billion and the report puts the increase down to criminals quickly adopting new technologies, the ease of engaging in cyber crime -- including an expanding number of cyber crime centers -- and the growing financial sophistication of top-tier criminals. Banks are still the favored target of… [Continue Reading] -

Technology and compliance teams work together to minimize the risk of data breaches
Publié: février 21, 2018, 3:14pm CET par Ian Barker
Organizations are facing an unprecedented variety of cyber risks that have the potential for devastating consequences, but a new study reveals that IT, security and compliance teams individually lack the resources to deal with them. The study for communications compliance specialist Actiance and conducted by IDG Research finds enterprises moving towards a collaborative risk management model with increasing overlap between the different teams. "Although the legacy technologies, buying processes, and functionally-driven priorities of the last 15 to 20 years have left some organizations with redundant and ineffective risk management processes and solutions, many companies have successfully bridged the resulting informational… [Continue Reading] -

New robotic process platform helps businesses stay competitive
Publié: février 21, 2018, 12:00pm CET par Ian Barker
Robotic process automation is increasingly popular with businesses looking to streamline their operations and cut costs. Specialist in this area Redwood Software is launching a new robotic process automation (RPA) platform that offers access to over 35,000 robotic tools for tasks like accounting, payroll, compliance, claims processing and more. The Redwood Robotics product lets users define robotic business processes without having to resort to scripting and low-level user interface based manipulation. This allows them to shift the focus from worrying about controlling the RPA tool, to improving the process and delivering value to the business. The solution works across the… [Continue Reading] -

Top US banks have multiple online security flaws
Publié: février 20, 2018, 3:16pm CET par Ian Barker
Analysis of the internet presence of 25 out of 50 top US banks reveals a worrying number of online security flaws. Threat management company RiskIQ used its Digital Footprint product, which provides a real-time inventory of all internet-facing assets, including the components running on assets that may expose the organization to vulnerability risk. It also correlates newly discovered vulnerabilities with internet-exposed components and assets, highlighting those at risk to inform patching and remediation planning. The banks analyzed returned an average risk score of 74 out of 100. The average bank having 30 domain configuration issues, 42 SSL configuration issues, 87… [Continue Reading] -

GDPR and the challenge of personal data discovery
Publié: février 20, 2018, 11:41am CET par Ian Barker
For enterprises to comply with GDPR it's vital that they have an understanding of where personal data is located in each of their systems. Metadata discovery specialist Silwood Technology is releasing research into five of the largest and most widely used application packages to understand the scale of the challenge encountered by their customers when locating personal data. The research team selected the top five application packages based on customer base and size -- SAP, JD Edwards, Microsoft Dynamics AX 2012, Siebel and Oracle E-Business Suite. It used the terms Date of Birth and Social Security Number for test purposes… [Continue Reading] -

Cyber security in (big) numbers
Publié: février 16, 2018, 4:17pm CET par Ian Barker
We hear a lot about cyber attacks and the latest threats, but it can sometimes be hard to comprehend the scale of the problem. Network security company Bricata has produced an infographic that sets out some of the statistics to put things into context. These include the average cost of a breach, currently $7.35 million; the average CISO salary, $273,000, and venture capitalists investing $3.5 billion into 400+ security startups in 2016. Researchers estimate spending on security defenses will rise to an eye-watering $1 trillion by 2021. The graphic also looks at the threats behind all of this. Ransomware attacks… [Continue Reading] -

Cisco launches cloud-based endpoint protection for MSSPs
Publié: février 16, 2018, 3:06pm CET par Ian Barker
According to Networking specialist Cisco, almost half of SMBs and enterprises in the US are outsourcing at least some of their security to managed security service providers (MSSPs) in order to counter the latest advanced threats. The company is targeting this market by launching a set of new endpoint security solutions aimed specifically at MSSPs. These include three powerful cloud-based tools. AMP for Endpoints prevents breaches and blocks malware at the point of entry, then continues to watch, analyze, and record file activity, regardless of the file's disposition. Cisco Umbrella blocks requests to malicious or unwanted destinations before a connection is… [Continue Reading] -

Growth in Android ransomware slows, but it's getting sneakier
Publié: février 15, 2018, 5:42pm CET par Ian Barker
While Android ransomware is still growing, it's doing so at a slower rate than at its peak in 2016. However, it is using sneaky new techniques to trick users. New findings from researchers at ESET reveal techniques like the misuse of Android's Accessibility services being used to infect devices. The most popular attack technique though remains screen-locking followed by a ransom demand. The most frequently detected variant being the Android/Locker family. One of the most innovative ransomware families, discovered by ESET researchers in the fall of 2017, is DoubleLocker. Built on the foundations of a previously seen banking trojan, it… [Continue Reading] -

2017 breaks record for new vulnerabilities
Publié: février 15, 2018, 4:48pm CET par Ian Barker
More than 20,000 new vulnerabilities were cataloged in 2017 according to breach analysis specialist Risk Based Security. The figures from the company's own VulnDB eclipsed the total covered by MITRE's Common Vulnerability Enumeration (CVE) and the National Vulnerability Database (NVD) by more than 7,900. These vulnerabilities published by VulnDB in 2017 that are not found in CVE/NVD, impact products that are widely used in all sizes of organizations. "Incredibly, we see too many companies still relying on CVE and NVD for vulnerability tracking, despite the US government funded organization falling short year after year," says Brian Martin, VP of vulnerability… [Continue Reading] -

Contractors pose cyber risk to government agencies
Publié: février 15, 2018, 3:28pm CET par Ian Barker
While US government agencies are continuing to improve their security performance over time, the contractors they employ are failing to meet the same standards according to a new report. The study by security rankings specialist BitSight sampled over 1,200 federal contractors and finds that the security rating for federal agencies was 15 or more points higher than the mean of any contractor sector. It finds more than eight percent of healthcare and wellness contractors have disclosed a data breach since January 2016. Aerospace and defense firms have the next highest breach disclosure rate at 5.6 percent. While government has made a… [Continue Reading] -

Why Google is building its own ad blocker
Publié: février 15, 2018, 12:02pm CET par Ian Barker
As one of the major players in online advertising it might seem surprising that Google is introducing its own ad filtering feature to Chrome. Partly though this is a fight back against the increasing use of ad blockers that block Google’s own ads and is aimed at the most annoying ad types like pop ups and autoplay videos. Internet marketing company TechWyse has put together an infographic explaining the thinking behind Google’s decision. 200 million people around the world now use ad blockers, and Google earned over$72 billion from advertising in 2017 and with Chrome accounting for 47.5 percent of… [Continue Reading] -

Cryptomining malware tops January's 'most wanted' list
Publié: février 14, 2018, 4:20pm CET par Ian Barker
Malware seeking to steal processor time for crypto currency mining continues to be a problem, with 23 percent of organizations globally affected by a Coinhive variant in January. These findings come from a study by Check Point which discovered three different variants of cryptomining malware in its top 10 most prevalent listing, with Coinhive ranking first. Coinhive performs online mining of the Monero cryptocurrency when a user visits a web page. It uses implanted JavaScript that uses the computational resources of the user’s machine to mine coins, impacting system performance. In addition to cryptominers, Check Point researchers also discovered that… [Continue Reading] -

NTT Security and ThreatQuotient partner to deliver threat intelligence
Publié: février 14, 2018, 3:16pm CET par Ian Barker
With a wider threat landscape presented by cloud and digital transformation strategies, accurate and up to date threat intelligence is more important than ever to protect against attacks. To meet this need, NTT Security, the specialized security company of NTT Group, has partnered with ThreatQuotient to offer an improved threat intelligence capability. ThreatQuotient's threat intelligence platform ThreatQ, will become part of NTT Security's new threat intelligence services offering and will fully integrate into its Global Managed Security Services Platform. "NTT Security’s global managed security services and channel program is exactly the type of model that we strive to be part… [Continue Reading] -

Cloud adoption is up but 35 percent of spend is wasted
Publié: février 13, 2018, 5:12pm CET par Ian Barker
The dash to move data and applications to the cloud shows no signs of slowing down, but while the adoption of cloud solutions is up there are still major challenges. A new report from cloud delivery specialist RightScale shows that 26 percent of enterprises (with more than 1,000 employees) are spending over $6 million a year on public cloud. But the sector is still growing, 71 percent of enterprises say they will grow public cloud spend more than 20 percent, while 20 percent plan to more than double public cloud spend. Multiple cloud use is common too with respondents already… [Continue Reading] -

Business data is getting bigger
Publié: février 13, 2018, 4:05pm CET par Ian Barker
It probably comes as no surprise that we're all storing more data. But just how much of an impact is this having for businesses. Enterprise file sharing specialist Egnyte says 82 percent of businesses are hybrid-enabled, keeping their data both physically backed up and in put into cloud storage. This is up from 76 percent in 2016. The company analyzed 14 petabytes of data to discover what companies are actually storing and has released the results as an infographic. It finds the average file in 2015 was 2.59 MB -- in 2017 it was up to 3.13 MB (a 20… [Continue Reading] -

Despite challenges, mainframe use is still central to large enterprises
Publié: février 13, 2018, 3:30pm CET par Ian Barker
Mainframes are still vital to many larger businesses and a new report from Syncsort highlights some key trends including the mainframe’s role in strategic projects. The results show the mainframe remains strategic to businesses, with 57 percent of respondents saying it will continue to be the main hub for business-critical applications this year. It will run revenue-generating services for 43 percent. Cost control is a priority though, 51 percent say they plan to cut IT costs by optimizing mainframe resources. Top challenges include reducing general processor CPU usage and related costs (70 percent), meeting security and compliance requirements (63 percent)… [Continue Reading] -

New edge computing platform helps industry handle IIoT data
Publié: février 12, 2018, 3:04pm CET par Ian Barker
Growing amounts of data from Industrial Internet of Things devices is placing increased strain on conventional network infrastructure. One way of dealing with this is to move computing resources closer to the edge, and Stratus Technologies is launching a new virtualized and self-protecting edge computing platform that’s specifically designed for industrial environments. Called ztC Edge, it's aimed at significantly reducing the IT burden for virtualized computing. Its self-protecting and self-monitoring features help reduce unplanned downtime and ensure continued availability of business-critical industrial applications. ztC Edge is made up of multiple redundant nodes that act as a single system. It features… [Continue Reading] -

Security service providers suffer from false positive alert overload
Publié: février 12, 2018, 1:00pm CET par Ian Barker
A new survey of managed security service providers (MSSPs) reveals that they are suffering an avalanche of false positive security alerts. The study from Advanced Threat Analytics reveals that 44 percent of respondents report a 50 percent or higher false-positive rate, half of those experience a 50-75 percent false-positive rate and the remainder a startling 75-99 percent rate. Nearly 45 percent of respondents say they investigate 10 or more alerts each day, that breaks down into 22 percent investigating between 10 and 20 alerts each day, 11 percent investigating 20-40 daily, and 11 percent investigating 50 or more. It takes… [Continue Reading] -

Cylance brings enterprise-grade security to employees' homes
Publié: février 9, 2018, 1:04pm CET par Ian Barker
Businesses go to great lengths to protect their corporate networks, but when staff take work home it can be hard to ensure data is kept secure when using personal devices and accessing data from the cloud. In an innovative move, endpoint protection company Cylance is offering employees of companies that use its software the chance to use Cylance's enterprise-grade AI-powered endpoint prevention to protect their family's home PCs and Macs against malicious attackers. CylancePROTECT Home Edition uses artificial intelligence to render new malware and unknown future variants useless. Employees of eligible Cylance customers can take advantage of it to work… [Continue Reading] -

Check Point launches enterprise cloud protection
Publié: février 8, 2018, 4:19pm CET par Ian Barker
As enterprises move more of their system to the cloud, they open up more of their workloads to potential attack. In order to offer protection against cyberattacks on cloud infrastructure workloads, services and software-as-a-service applications on public and private cloud platforms, Check Point is launching a new family of cloud security products. CloudGuard includes zero-day threat protection, preventing APTs, ransomware and unknown zero-day malware from infecting content in SaaS applications. It also includes Identity Protection to identify and block threat actors or impostors accessing SaaS accounts, and automatically forces encryption of sensitive data, blocking unauthorized sharing of sensitive files. It… [Continue Reading] -

Public cloud services like Microsoft OneDrive and Google Drive fail to protect against zero-day malware
Publié: février 7, 2018, 4:34pm CET par Ian Barker
Hackers and cyber criminals are becoming wise to the fact that they can use cloud applications to spread malware. In response, top cloud providers now offer malware protection in an attempt to stop files containing malware being uploaded. But a new report reveals that placing your trust in this protection may be ill-advised. Cloud access security company Bitglass has found that Google Drive and Microsoft Office 365 (with built-in malware protection) were both unable to detect a piece of zero-day ransomware in a file that was uploaded to the cloud services. In a separate scan of Bitglass customers' cloud applications,… [Continue Reading] -

IT leaders struggle to deliver cost transparency
Publié: février 7, 2018, 3:08pm CET par Ian Barker
A new survey by London-based Coeus Consulting reveals that 88 percent of respondents are unable to demonstrate cost transparency to the rest of the organization. Those that can, however, are best positioned to deliver business agility for digital transformation and are more likely to be represented at senior level in their companies. What the study identifies as 'cost-transparency leaders' are twice as likely to be represented at board level (100 percent versus 54 percent). They are also more likely to be involved in setting business strategy (85 percent against 55 percent), twice as likely to report that the business values… [Continue Reading] -

D-Link DIR-882 EXO AC-2600 MU-MIMO router [Review]
Publié: février 7, 2018, 1:22pm CET par Ian Barker
For many people a router is something that's supplied free by their internet service provider. Consequently they don't give much thought to it unless they encounter problems. Yet, as we attach more and more devices to our home networks we put more demand on our routers and performance can start to suffer. The good news is that there's a whole world of routers out there that offer performance and connectivity features way beyond those of the basic units usually sent out by ISPs. The latest DIR-882 AC-2600 from D-Link is designed for use on fiber or cable systems and comes… [Continue Reading] -

New open source platform offers secure, self-hosted collaboration
Publié: février 6, 2018, 5:03pm CET par Ian Barker
As businesses are keen to embrace flexible working and digital transformation, there’s increased focus on collaboration and sharing of information. But with existing regulations like HIPAA and upcoming ones like GDPR it's important to keep collaboration secure. German company Nextcloud is launching a solution in the form of a self-hosted, open source platform offering end-to-end encryption, video and text chat, and enhanced collaboration. Nextcloud 13 is an enterprise-ready solution which can encrypt data on a per-folder level rather than all-or-nothing approach. It doesn't require users to remember or exchange passwords, or re-uploading of data on sharing. Other features include an… [Continue Reading] -

51 percent of financial services companies believe existing tech is holding them back
Publié: février 6, 2018, 3:47pm CET par Ian Barker
Legacy technology can be a major obstacle to digital transformation projects and, according to a new survey of financial services technology decision makers carried out for business consultancy Janeiro Digital, almost 51 percent say existing technology is holding back innovation. Three of the biggest roadblocks are seen as lack of support for change (34 percent), legacy technology and infrastructure (31.6 percent) and a lack of in-house technical skill (29.5 percent). As a consequence 23 percent of respondents believe their company is behind in digital transformation compared to others in the industry. Only 47 percent are currently implementing new technologies, with… [Continue Reading] -

Enterprises spend more than $16 million on hidden costs of detection-based security
Publié: février 6, 2018, 12:24pm CET par Ian Barker
Most organizations employ some kind of detection-based security to protect their systems. But a new report by cyber security company Bromium reveals that this approach has major hidden costs. Upfront licensing and deployment costs security-detection tools like anti-virus are dwarfed by the cost of human skills and effort needed to manage and assess the millions of alerts and false-positive threat intelligence generated. The findings, based on a survey of 500 CISOs from global enterprises, show that organizations invest $345,300 per year on detect-to-protect security tools. However, the average annual cost to maintain this endpoint security is $16,714,186, per enterprise. This… [Continue Reading] -

Cloud will account for 95 percent of total data center traffic by 2021
Publié: février 5, 2018, 5:38pm CET par Ian Barker
Cloud services are increasingly dominating the internet and could account for 95 percent of data center traffic in three years time. This is among the findings of the latest Global Cloud Index report from networking company Cisco, which finds both consumer and business applications are contributing to the growth in demand. The study forecasts global cloud data center traffic to reach 19.5 zettabytes (ZB) per year by 2021, up from 6.0 ZB per year in 2016. A zettabyte is a billion terabytes, in case you were wondering. Globally, cloud data center traffic will represent 95 percent of total data center… [Continue Reading] -

GDPR and disclosing data breaches [Q&A]
Publié: février 5, 2018, 3:21pm CET par Ian Barker
With GDPR coming into force in May this year, companies are preparing themselves to comply with the new legislation, in particular putting in place procedures to deal with data breaches. But some, like Uber -- who have suffered a breach in the past and covered it up -- may well be wondering whether it’s better to disclose these events now rather than risk them leaking out once GDPR is in force. We spoke to Joseph Carson chief security scientist at privileged access management company Thycotic to find out more about what GDPR might mean for companies that suffer, or have… [Continue Reading] -

Fewer than a fifth of enterprises have a notification plan in place for data breaches
Publié: février 2, 2018, 1:29pm CET par Ian Barker
With the EU's GDPR legislation coming into force in a few months, and new and potentially tougher legislation on data breaches planned in the US, a new study reveals that many enterprises are under prepared. The report from integrity assurance company Tripwire shows that less than a fifth (18 percent) say that they are fully prepared with a process in place to notify consumers in the event of a data breach. The majority (73 percent) say they are 'somewhat prepared' and would have to figure things out 'on the fly.' In addition only 77 percent of companies subject to GDPR… [Continue Reading] -

Cyber criminals in 'gold rush' to exploit cryptocurrencies
Publié: février 1, 2018, 3:48pm CET par Ian Barker
A new report from risk management and threat intelligence company Digital Shadows shows that cyber criminals are looking to exploit the boom in interest and adoption of cryptocurrencies. The study highlights the most common methods used by these criminal actors, which include crypto jacking, account takeovers, mining fraud and scams against initial coin offerings (ICOs). "Cyber criminals follow the money and right now they see in the unregulated and largely unsecure world of digital currencies a huge opportunity to target people, businesses and exchanges and make money quickly and easily," says Rick Holland, VP strategy at Digital Shadows. "In many… [Continue Reading] -

Security is top priority in choosing cloud solutions
Publié: février 1, 2018, 11:31am CET par Ian Barker
Security is the main priority when selecting cloud solutions according to a new report which shows businesses are increasingly adapting their security to suit the cloud. The study for cloud security automation company Lacework carried out by analysts Hurwitz & Associates shows that 'safe and secure' tops the list of desirable cloud characteristics, cited by 53 percent of respondents. In addition 85 percent of respondents recognize that cloud security is different from traditional data center security. Only 35 percent of respondents feel that security limits their ability to maximize the benefits of DevOps and operations automation. 78 percent believe that they… [Continue Reading] -

More than half of decision makers think digital transformation has changed their roles
Publié: janvier 31, 2018, 4:03pm CET par Ian Barker
A new survey of business and IT decision makers reveals that more than half (56 percent) believe their job roles have been changed by digital transformation. The study by the Cloud Industry Forum and Ensono research finds 51 percent reporting an increase in their responsibilities and 47 percent saying they have greater pressure to deliver. The effect isn't the same across departments, however, business decision-makers report they have more freedom to innovate (45 percent compared to 24 percent of IT decision-makers), but the IT department is more likely to report a faster pace of work and increasing workloads. 92 percent… [Continue Reading] -

DDoS threats and bot attacks are biggest threats to API security
Publié: janvier 31, 2018, 2:54pm CET par Ian Barker
APIs power many of our digital experiences, but because they provide a window into applications they also present a security risk. A new study from cyber security company Imperva reveals that 69 percent of companies have public-facing APIs which offer a route to the sensitive data behind applications. The results show 80 percent of organizations use a public cloud service to protect the data behind their APIs with most using a combination of API gateways (63.2 percent) and web application firewalls (63.2 percent). When asked about threats, 63 percent of respondents are most worried about DDoS, bot attacks, and authentication… [Continue Reading] -

Data professionals waste half their time on futile activities and repeated efforts
Publié: janvier 30, 2018, 3:14pm CET par Ian Barker
Analytics and data science is having a major impact on the commercial world, but a new report shows that data professionals are wasting half of their time each week finding, protecting, or preparing data -- costing organizations significant amounts of money. The research commissioned by self-service analytics company Alteryx, and conducted by IDC, surveyed 400-plus individuals performing data functions across North America and Europe. It finds data analysts spend 60 percent of their time generating insights, but just 27 percent of that time is spent on actual analysis. The remainder is spent searching for and preparing data. These data workers… [Continue Reading] -

Arcserve launches affordable cloud disaster recovery service
Publié: janvier 30, 2018, 12:22pm CET par Ian Barker
Disaster recovery has often been a choice between maintaining system availability at high cost, or choosing a cheaper solution at the expense of longer recovery times. Now data protection and recovery specialist Arcserve is launching a new direct-to-cloud disaster recovery as a service (DRaaS) and backup as a service (BaaS) solution aimed at mid-sized businesses. Arcserve UDP Cloud Direct offers sub five minute recovery time objectives (RTOs) and sub 15-minute cloud recovery point objectives (RPOs). Multiple automated backup validations ensure data is fully recoverable and error-free. It transfers directly to and from cloud storage without the need for an appliance,… [Continue Reading] -

Moving to 'intelligent operations' will help businesses thrive
Publié: janvier 29, 2018, 4:00pm CET par Ian Barker
Organizations that can harness the combination of innovative talent, diverse data, and applied intelligence will be best placed to use data-driven insights to improve business outcomes and enhance the customer experience, according to new research. The study conducted by HfS Research for professional services company Accenture shows that 80 percent of those surveyed are concerned with disruption and competitive threats, especially from new digital-savvy entrants. It also shows that most organizations are currently not able to make data-driven decisions due to a lack of skills and technology to process data. Nearly 80 percent of respondents say that 50 to 90… [Continue Reading] -

New solution delivers universal threat intelligence
Publié: janvier 29, 2018, 3:06pm CET par Ian Barker
Threat intelligence is becoming an essential part of protecting systems. But this information often comes from many different sources, making it hard to see the big picture and limiting flexibility and effectiveness. To address this issue, Recorded Future is launching a new product providing centralization, collaboration, and customization of intelligence. Called Fusion, it's powered by machine learning and allows users to centralize and customize proprietary and internal threat data with external threat intelligence. "There are many threat intelligence vendors and solutions today that offer everything from feeds, to reports, to platforms," says Matt Kodama, vice president of product at Recorded Future. "We… [Continue Reading] -

Why consumers love shopping online
Publié: janvier 29, 2018, 11:53am CET par Ian Barker
While the majority of shopping is still done offline, it's the internet retailers that are growing at a three times faster rate. Online retail portal Shopping.fm has produced an infographic comparing the online and bricks and mortar shopping worlds. It looks at what people buy where and what factors drive their decision to shop online. It shows that while offline sales are currently 10 times those of online, 51 percent of Americans now say they prefer to shop online and this figure is higher for certain age groups. North America is second only to Asia in the number of online… [Continue Reading] -

Corporations seen as a bigger threat to data privacy than cyber criminals
Publié: janvier 26, 2018, 12:33pm CET par Ian Barker
Ahead of this Sunday's (January 28) Data Privacy Day, enterprise cyber security company Tripwire has conducted a poll of Twitter users asking who they were most concerned about collecting their private information. Of the more than 300 people who took part, 40 percent say they would be most worried about corporations stealing their information. While nearly a third (27 percent) say they are most concerned about the government gathering their critical data. However, only 21 percent gave identity theft by criminals as being their main concern. Just 12 percent were concerned about online stalkers and harassers storing their private information.… [Continue Reading] -

UK should lead the world in safe, ethical AI
Publié: janvier 25, 2018, 5:26pm CET par Ian Barker
Speaking at the World Economic Forum in Davos the UK Prime Minister Theresa May says she wants the country to lead the world in deploying artificial intelligence in a safe and ethical manner. A new advisory body -- Centre for Data Ethics and Innovation -- will be set up to co-ordinate the UK's efforts with other countries, and the UK will join the Davos forum's own council on artificial intelligence. She says she believes we have only seen the beginning of what AI can achieve and that a new AI startup has been created in the UK every week over… [Continue Reading] -

Shippable opens up OS support for DevOps teams
Publié: janvier 25, 2018, 4:20pm CET par Ian Barker
Most CI and DevOps vendors are focused on Linux-based applications, which means supporting Windows or iOS requires multiple platforms, or managing their own instances of Jenkins. This can lead to an inefficient, expensive and inconsistent experience. Automation platform Shippable is addressing this issue with the launch of support for applications built on Mac OS X, iOS, and Windows, plus new analytics tools. "Shippable is a consistent DevOps platform across all types of applications, regardless of tools, architecture, language used to develop or deployment target used to run," says CEO Avi Cavale. "With today's release we have expanded beyond Ubuntu-based applications… [Continue Reading] -

Data threats are the new reality as organizations embrace transformative technologies
Publié: janvier 25, 2018, 3:34pm CET par Ian Barker
With 99 percent of organizations using big data, 94 percent Internet of Things devices, and 91 percent using or working on mobile payments, there are more attack surfaces than ever and new risks that need to be addressed. A new study from systems and cyber security company Thales e-Security finds the extent and impact of increased threats clearly shown in levels of data breaches and vulnerability. Some 67 percent of respondents report having been breached, with 36 percent breached in the last year -- a marked increase from 2017's report, which saw 26 percent breached in the last year. Consequently,… [Continue Reading] -

Record ransomware volumes seen in 2017
Publié: janvier 25, 2018, 2:48pm CET par Ian Barker
The latest annual State of Malware Report from Malwarebytes shows that ransomware had a bumper year in 2017, though it began to trend downwards towards the end of the year. Ransomware launched against consumers was up more than 93 percent and ransomware against businesses up 90 percent. As the year end approached though many avenues known for ransomware drops were seen diversifying their payloads with banking Trojans and cryptocurrency miners instead. The report shows an increase of 40 percent in hijackers and 30 percent in spyware detections in 2017. The second half of the year also marked an average of… [Continue Reading] -

How GDPR will affect your email archiving [Q&A]
Publié: janvier 25, 2018, 11:15am CET par Ian Barker
The arrival of GDPR is set to impact on many aspects of commercial operation, not least email. But what about old emails that are stored or archived? We spoke to Marc French, chief trust officer at cloud email specialist Mimecast to find out more about GDPR and an aspect that organizations may have overlooked. BN: How does email archiving factor into GDPR risk management strategy? MF: Emails often contain personal data -- and that means organizations must manage backup and archived copies of them with rigor. In May 2018 when GDPR goes into effect, organizations must be able to access… [Continue Reading] -

Lack of soft skills holds IT staff back from leadership roles
Publié: janvier 24, 2018, 5:32pm CET par Ian Barker
The importance of interpersonal skills has increased in recent years according to a new report, but companies aren't training their technology teams in these abilities. The study from business and technology consultancy West Monroe Partners looks at soft skills, including communication, collaboration, conflict resolution, and leadership in relation to technology and IT hiring decisions West Monroe surveyed 1,250 individuals made up of 600 HR and recruiting professionals, and 650 full-time employees who regularly work with their company's technology teams. Findings include that 98 percent of HR leaders say soft skills are important in landing a technology position -- so important… [Continue Reading] -

UK organizations urged to get ready for tougher data protection laws
Publié: janvier 24, 2018, 3:52pm CET par Ian Barker
New research released today by the UK government shows that fewer than half of all businesses and charities are aware of new data protection laws with just four months to go before they come into force. Knowledge varies by industry, businesses in the finance and insurance sectors have the highest awareness of the changes to be brought in through the EU's General Data Protection Regulation (GDPR), which is to be implemented in UK law via the Data Protection Bill in May 2018. Businesses in the construction industry have the lowest awareness, with only one in four aware of the coming… [Continue Reading] -

Official app stores targeted by malicious Bitcoin apps
Publié: janvier 24, 2018, 3:14pm CET par Ian Barker
With increasing interest in cryptocurrency it's inevitable that cyber criminals will see the potential to make money from investors and users. Threat management company RiskIQ has found that hackers are targeting the Apple, Google Play, SameAPK, APKPlz and other app store users with malicious cryptocurrency apps aiming to steal money and personal data. In analysis of 18,408 apps across 20 app stores, the firm's researchers uncovered over 600 blacklisted Bitcoin-themed apps in total. Monitoring for 10 of the popular Bitcoin exchanges in the app title, RiskIQ found 661 apps to be blacklisted by official cyber security vendors but still available… [Continue Reading] -

Organizations blame their own staff for cloud security incidents
Publié: janvier 24, 2018, 1:49pm CET par Ian Barker
When systems are in the cloud, 45 percent of organizations perceive their own employees to be the biggest security risk, according to a new report. According to user behavior specialist Netwrix, even though the majority of attacks they experienced over the year were external, organizations blame their own IT staff (39 percent) and business users (33 percent) as much as or more than their cloud providers (33 percent). The report shows the most common cloud security concerns are the risk of unauthorized access (69 percent), the risk of malware infiltration (50 percent) and companies’ inability to monitor the activity of… [Continue Reading] -

How moving inventory to the cloud can streamline your business [Q&A ]
Publié: janvier 24, 2018, 11:23am CET par Ian Barker
A major trend we've been seeing in inventory management (and business, in general) is for companies to move from a desktop solution to a cloud solution. This has profound implications for the nature of how businesses manage their inventory, and we thought it would be interesting to get the low down on this trend from an industry expert. Christy Hair is an inventory solution specialist with Boxstorm, an online inventory management specialist. We asked her a series of questions about cloud inventory management and how moving a company's inventory to the cloud can help it streamline its processes in new… [Continue Reading] -

Fewer than five percent of enterprise apps will move to the cloud in 2018
Publié: janvier 23, 2018, 5:28pm CET par Ian Barker
A new study of over 160 IT directors and chief technology officers at companies with more than 1,000 employees shows that while 78 percent are planning to upgrade their enterprise applications, the cloud doesn't feature in many plans. The survey by digital experience platform Sapho reveals that fewer than five percent of enterprise apps will migrate to the cloud from on-premises in 2018, mainly because of security and compliance issues, but also because many of these apps are so ingrained in daily business processes, they can't be moved. When looking at tools to modernize these enterprise applications and systems, survey… [Continue Reading] -

State-sponsored attacks expected to dominate 2018 threat landscape
Publié: janvier 23, 2018, 4:44pm CET par Ian Barker
With 1.9 billion records stolen in the first six months, more than in the whole of 2016, 2017 proved a bumper year for cyber crime. According to cyber security company Venafi, this trend is set to continue into 2018, with state-sponsored attacks to the fore. "In 2017, attackers working for nation-states focused on efficiency and return on investment, and they were very successful," says Jing Xie, senior threat intelligence analyst at Venafi. "As a result, we should expect to see escalations and variations of similar attack vectors this year." Xie also expects to see the trust models used to control… [Continue Reading] -

Organizations could face up to $19 billion in losses if a cloud provider is hacked
Publié: janvier 23, 2018, 3:39pm CET par Ian Barker
If a hacker were to gain control of a cloud provider for over three days, businesses could face losses up to a whopping $19 billion, with SMBs carrying the largest economic and insurance losses, according to a new report. In partnership with the American Institutes for Research (AIR), insurance market Lloyd's of London is unveiling a new report detailing the financial impact of a cyberattack on a US cloud provider. Fortune 1000 companies will carry 38 percent of the losses (and 46 percent of insured losses) arising from a three to six day downtime event. However, smaller companies might be… [Continue Reading] -

Corporate cultural issues hold back secure software development
Publié: janvier 22, 2018, 3:18pm CET par Ian Barker
As the digital economy expands and software becomes more critical, security worries grow. In a new survey, 74 percent of respondents agree that security threats due to software and code issues are a growing concern. The study of over 1,200 IT leaders, conducted by analysts Freeform Dynamics for software company CA Technologies, finds 58 percent of respondents cite existing culture and lack of skills as hurdles to being able to embed security within processes. In addition, only 24 percent strongly agree that their organization's culture and practices support collaboration across development, operations and security. On top of cultural limitations, less… [Continue Reading] -

New API sheds light on the dark web
Publié: janvier 19, 2018, 3:32pm CET par Ian Barker
Gaining threat intelligence from the dark web can be a difficult task for security providers due to its unstructured nature. Similarly, when data breaches occur, companies often face the problem of knowing exactly which data has been exposed on underground marketplaces. Data feed service Webhose is launching a new feed of dark web data, Dark Web API, that shines light into the dark web. It enables cyber security companies, public institutions and researchers to identify relevant information, within content extracted from .onion domains, including market places, hidden forums and message boards. "Often hidden behind multiple levels of encryption, the greatest… [Continue Reading] -

Hackers gear up to target Winter Olympics
Publié: janvier 19, 2018, 11:53am CET par Ian Barker
With the 24th Winter Olympics due to start in Pyeongchang, South Korea in a few weeks, athletes are not the only ones preparing for the event. A report from security analytics platform Cybereason shows that hackers and cyber criminals are gearing up too, the scale and cost of the event making it a prime target. The greatest cyber risks are likely to come from the third-party ecosystem and the access to networks that TV stations, journalists and sub-contractors require to run and cover the games. The report also looks at potential threat actors including nation states, non-state actors and organized… [Continue Reading] -

New platform integrates Windows file servers with the cloud
Publié: janvier 18, 2018, 4:41pm CET par Ian Barker
Although businesses are keen to move to the cloud and IaaS solutions, most still have files stored on in-house servers. Enterprise file sharing and sync platform FileCloud is launching a new product called ServerSync that integrates Microsoft Windows file servers with any IaaS cloud. "Over 80 percent of businesses still run on-premise Microsoft Windows file servers to store their files," says Madhan Kanagavel, CEO of FileCloud. "There is no easy way for team members to access these files remotely, greatly inhibiting the speed at which business can be conducted. With FileCloud’s ServerSync, customers can access their data locally from the… [Continue Reading] -

How behavioral analytics help to fight insider threats
Publié: janvier 18, 2018, 3:46pm CET par Ian Barker
In the increasingly complex threat landscape faced by businesses, insiders continue to be a problem, accounting for around half of data breaches, according to a recent Forrester report. One way that companies are combating this threat is with the use of User and Entity Behavior Analytics (UEBA). This detects abnormal behavior, adds contextual information to confirm the behavior is abnormal, and then prioritizes the riskiest insiders for analysts to investigate. Security and risk management firm Bay Dynamics has put together an infographic highlighting some of the things UEBA can detect. These include attacks that try to slip below the radar… [Continue Reading] -

New AI platform helps companies with GDPR compliance
Publié: janvier 18, 2018, 1:26pm CET par Ian Barker
At the heart of the forthcoming GDPR legislation is the protection of personal data. For businesses this means being able to identify data that’s covered, including where it’s held and how it’s processed. California-based Algorithmic IT Operations (AIOps) specialist Loom Systems is launching a new platform and virtual IT data analyst that helps users maintain GDPR compliance with just a click of a button. Designed with data protection and privacy in mind, Loom's platform uses AI to analyze logs and unstructured machine data for immediate visibility into IT environments, highlighting and anonymizing sensitive log data to ensure companies can more easily… [Continue Reading] -

New SDK helps deliver best practice privileged account management
Publié: janvier 17, 2018, 4:25pm CET par Ian Barker
The idea of security by design is something we'll hear much more of as GDPR implementation looms. But many organizations still struggle when it comes to implementing a least privilege security model. Access management specialist Thycotic is launching a new command line interface for its Secret Server privileged account management solution, enabling DevOps teams to bring best practice privileged account management to their code, build scripts, and configuration files. Secret Server SDK enables software developers and operations professionals to use Secret Server as part of their application development and deployment process. DevOps teams can rely on Thycotic's military-grade security capabilities… [Continue Reading] -

AI is moving into the enterprise mainstream
Publié: janvier 17, 2018, 3:28pm CET par Ian Barker
Artificial intelligence is often seen as being a technology of the future, but a new study from natural language processing company Narrative Science reveals that 61 percent of businesses are already using AI. Interest and investment in the technology is increasing too, 71 percent of respondents say their company has an 'innovation strategy' to drive investments in new technologies like AI. A majority of companies say they have budget dedicated to enabling innovation (59 percent) and expect that outlay to increase in 2018 (62 percent). Business intelligence and finance are the areas where there’s most interest in the benefits of… [Continue Reading] -

Half of companies suffer financially motivated cyber attacks
Publié: janvier 16, 2018, 4:21pm CET par Ian Barker
Cyber attacks driven by ransom demands are on the increase as criminals seek to cash in on the soaring values of crypto currencies according to a new report. The 2017-2018 Global Application and Network Security Report from cyber security company Radware finds that reported ransom attacks surged in the past year, increasing 40 percent from the 2016 survey. Half of companies surveyed suffered a financially motivated attack in the past year. "The rapid adoption of cryptocurrencies and their subsequent rise in price has presented hackers with a clear upside that goes beyond cryptocurrencies' anonymity," says Andrew Foxcroft, regional director for… [Continue Reading] -

New study shows wide gaps in attitudes to cloud security
Publié: janvier 16, 2018, 3:23pm CET par Ian Barker
While a majority of businesses around the world have adopted cloud services, a study released today reveals a wide gap in the level of security precautions applied by companies in different markets. The study from digital security company Gemalto finds that German businesses are more cautious when it comes to sharing sensitive information in the cloud (61 percent) than British (35 percent), Brazilian (34 percent) and Japanese (31 percent) organizations. Germany's lead continues when dealing with information at rest. 61 percent of German organizations say they secure sensitive or confidential information while being stored in the cloud environment, ahead of… [Continue Reading] -

New platform improves visibility of online services
Publié: janvier 16, 2018, 1:11pm CET par Ian Barker
As enterprises move more data to the cloud one of the problems they have is understanding where everything is and how it integrates with existing workflows. Cyber security and breach analytics specialist Eastwind Networks is launching a new Eastwind for SaaS platform that offers complete visibility for companies using online services, such as G Suite, Office 365, Dropbox, Box and Salesforce. Benefits of the platform include getting a clearer picture of what's happening in SaaS applications, from office suites to file storing and sharing apps. In addition, it offers increased understanding of activity outside the corporate network to evaluate which… [Continue Reading] -

Getting a good Google ranking is a long game
Publié: janvier 15, 2018, 3:28pm CET par Ian Barker
Whenever a business gets a new website it wants to see it ranking highly in search results. But getting to the top in Google and other search engines is a long game, according to SEO company Ahrefs. UK web design company The Website Group has produced an infographic based on the Ahrefs research. It shows that -- based on random keywords -- the top 10 ranking pages on Google are on average more than two years old. Of two million randomly selected pages, just 5.7 percent rank in the top 10 for at least one keyword within a year. The… [Continue Reading] -

More than half of UK businesses still unaware of GDPR
Publié: janvier 11, 2018, 3:18pm CET par Ian Barker
With GDPR implementation only a few months away, a worrying new survey shows that 55 percent of UK businesses are still unaware of the GDPR regulations. The study by compliance solution PORT.im also reveals that only 27 percent of businesses believe GDPR applies to them, despite 73 percent saying that they collect personal data on their customers -- a strong indication that GDPR does apply. The results show only 35 percent of businesses have a record of consent to store their customers' data, seven percent never ask for consent, and 19 percent say they have sought permission but have no… [Continue Reading] -

Only one in 10 employees is aware of IT security policies
Publié: janvier 11, 2018, 12:18pm CET par Ian Barker
A new survey from Kaspersky Lab reveals that there is a major disconnect between employees and their employer's IT security guidelines. In a survey of almost 8,000 full-time employees, 49 percent of those employees surveyed consider protection from cyber threats to be a shared responsibility, but only 12 percent of respondents are fully aware of their organization’s IT security policies and rules. In addition, a worrying 24 percent of employees believe there are no established policies in their organizations at all. This lack of awareness tends to be a particular problem for SMBs where there is no dedicated IT security… [Continue Reading] -

Cisco solution prevents malware from hiding in encrypted traffic
Publié: janvier 10, 2018, 3:24pm CET par Ian Barker
As businesses increasingly turn to cloud solutions they rely more on encryption to protect their data. Gartner predicts by 2019, 80 percent of web traffic will be encrypted, but that leads to a problem as it can allow malware to travel undetected. Detecting malicious content in encrypted traffic is difficult without decrypting it, forcing network operators to choose between privacy and security. A new solution from network specialist Cisco solves this conundrum by allowing traffic to be scanned without decrypting it. Encrypted Traffic Analytics (ETA) has been in early field trials with customers around the world since June last year and… [Continue Reading] -

Security and business continuity top IT spending plans for 2018
Publié: janvier 10, 2018, 12:39pm CET par Ian Barker
Security is the top initiative companies plan to pursue in the next 24 months with investments in virus and malware protection, patch management, and intrusion detection and prevention. According to a new State of Resilience report by big data company Syncsort, 49 percent plan to spend on these areas, with 47 percent planning to spend on business continuity and high availability. The report also finds that while almost two-thirds of companies perform security audits on their systems, the most common schedule is annual (39 percent). Another 10 percent conduct audits only every two years or more, which, given an ever-changing… [Continue Reading] -

Cloud workloads at risk from compliance, security and management failings
Publié: janvier 9, 2018, 5:13pm CET par Ian Barker
Security, management and compliance challenges are hitting the benefits businesses are getting from using the cloud as their infrastructures become more complex, according to new research. The study from security and compliance specialist WinMagic reveals that 39 percent of respondents report their infrastructure is more complex since using the cloud, and 53 percent spend more time on management tasks than they have done previously. Of the 1,029 IT decision makers surveyed, 98 percent report using the cloud, with an average 50 percent of their infrastructure on cloud systems. Around a third (33 percent) of respondents report that their data is… [Continue Reading] -

New tool helps enterprises root out shadow IT
Publié: janvier 9, 2018, 3:35pm CET par Ian Barker
Shadow applications -- where employees use their own cloud and other software that isn't approved by the IT department -- is a growing problem for many enterprises as it leaves data exposed outside the corporate firewall. Cloud Access Security Broker (CASB) specialist Bitglass is launching a new Shadow IT Discovery tool as part of its Zero-day CASB Core product to help businesses to get a handle on the problem. "The only constant in the enterprise cloud footprint is change," says Anurag Kahol, Bitglass' CTO. "Bitglass Next-Gen CASB is designed from the ground up to automatically adapt to changes in applications… [Continue Reading] -

Alert fatigue can allow cyber threats to slip through the net
Publié: janvier 8, 2018, 3:51pm CET par Ian Barker
Businesses are increasingly turning to software to allow them to spot cyber threats. But this can lead to a problem in the form of alert fatigue, where there are just too many warnings to allow them to be properly investigated. Network threat detection specialist Bricata has put together an infographic to highlight the problem of alert fatigue. It shows that large enterprises can face up to 1.3 million vulnerabilities every 30 days while 64 percent of threat alerts are not addressed every day. It also reveals that over half (54 percent) of security professionals ignore threats that should merit a… [Continue Reading] -

McAfee launches protection against identity theft
Publié: janvier 8, 2018, 3:05pm CET par Ian Barker
Given the high number of data breaches in the past year and the number of records involved, many consumers now rank identity theft as one of their top concerns with 66 percent of Americans saying it's the crime they most worry about. Security company McAfee is using this week's CES to move beyond its traditional antivirus products and launch its own Identity Theft Protection. The new product allows users to take a proactive approach to protecting their identities with personal monitoring, financial monitoring and recovery tools needed to keep identities personal and secured. "Data breaches are increasing in volume and… [Continue Reading] -

Malicious flashlight apps found on Google Play store
Publié: janvier 5, 2018, 3:17pm CET par Ian Barker
Whether you need to put your key in the lock on a dark night, or explore the depths of the cupboard under the stairs, having a flashlight app on your phone can prove useful. But researchers at Check Point have discovered more than 22 different flashlight and utility apps harboring adware called, appropriately, 'LightsOut'. The code, which generates illegal ad revenue for its perpetrators at the expense of unsuspecting users, is believed to have had more than 1.5 million downloads. Some users reported that they were forced to press on ads to answer calls and perform other day-to-day activities on… [Continue Reading] -

Targeted attacks on industry are on the increase
Publié: janvier 5, 2018, 12:08pm CET par Ian Barker
Cyber attacks on industrial organizations are a growing problem, with 28 percent admitting they faced an attack in 2017, compared to only 20 percent in 2016. This is among the findings of a new survey by Kaspersky Lab which also shows that many attacks are going unnoticed with organizations taking an average of several days (34 percent) to several weeks (20 percent) detecting a cyber attack. 87 percent of industrial companies say the informational technology/operational technology security events they experienced over the previous year were complex. The survey also reveals that 48 percent of industrial businesses have insufficient insight into… [Continue Reading] -

Dashlane's Project Mirror aims to kill off the password in 2018
Publié: janvier 4, 2018, 3:28pm CET par Ian Barker
Most digital services still rely on passwords for security, but recent breaches have shown that they are far from a perfect solution. Password management specialist Dashlane has set an ambitious goal to kill off the password in 2018 with the launch of its Project Mirror. The goal of Project Mirror is to put Internet users in control of their login and digital data, and allow them to control their identities more easily. Passwords have widespread adoption and could exist well into the future with current technologies, but Dashlane sees Project Mirror as a year-long effort to eliminate users’ dependence on… [Continue Reading] -

McAfee grabs Skyhigh to boost cloud security
Publié: janvier 4, 2018, 11:52am CET par Ian Barker
With more and more businesses storing data in the cloud, protecting and controlling it as it travels back and forth has become a major concern. To address this McAfee is acquiring Skyhigh Networks, one of the pioneers of the cloud access security broker (CASB) model of protection. "Today's announcement marks a new milestone for the future of our company," says Chris Young, chief executive office of, McAfee. "With two industry leaders coming together under one company, we will make cybersecurity an enabler to the transformative power of our digital age. We are focused on securing customers from their devices to the… [Continue Reading] -

'Alexa, nick him!' -- Amazon Echo joins the fight against crime
Publié: janvier 3, 2018, 3:06pm CET par Ian Barker
We're used to digital assistants controlling more and more aspects of our daily lives, but a UK police force is looking at how Amazon Echo could help in fighting crime. Police in Lancashire, north west England, are looking at how Alexa could relay information about missing persons or updates on local crime to citizens. It could also be used in the reporting of minor offenses, freeing up police call centers to deal with more serious issues. Rob Flanagan, Lancashire Constabulary's innovation lead, told the College of Policing conference, "If we can reduce demand into our call centers via the use… [Continue Reading] -

2017: Year of the data breach
Publié: janvier 3, 2018, 11:12am CET par Ian Barker
Barely a week seemed to go by in 2017 without news of a new data breach exposing customer or commercial data. But just how bad was it? File transfer specialist Ipswitch has put together an infographic looking at the year in breaches. In terms of the number of records compromised, 2017 didn’t break any records. 2013 still occupies the top slot there when the Yahoo breach alone exposed some three billion sets of credentials. Data breach activity was high in 2017 though, with 1,202 breaches in the 11 months to November, according to a report from the Identity Theft Resource… [Continue Reading] -

John McAfee and the strange Twitter hack
Publié: décembre 29, 2017, 12:45pm CET par Ian Barker
In a cautionary tale for the festive season, unorthodox security guru John McAfee claims to have had his Twitter account hacked. The account sent out a number of 'coin of the day' Tweets on December 27th encouraging followers to buy some lesser known crypto currencies. Nothing especially strange in that as McAfee has himself sent this type of message in the past. However, the messages were swiftly followed by a tweet from McAfee saying the account had been hacked and the messages were fake. Urgent: My account was hacked. Twitter has been notified. The coin of the day tweet was… [Continue Reading] -

Security concerns and a move to edge computing, 2018 predictions for the IoT
Publié: décembre 22, 2017, 4:09pm CET par Ian Barker
In 2017 we've see Internet of Things devices enter many more areas of our lives. We've also seen them exploited to launch cyber attacks. So, how do industry experts think the IoT will develop in 2018? The security aspect of IoT devices is still a concern for many. Larry Cashdollar, senior engineer, security intelligence response team at Akamai says, "As manufacturers develop new internet-connected devices, they must make software security a top concern. Not only can vulnerable devices be leveraged for attacks, but the consumers privacy is also at stake. Ignoring this threatens the security and stability of the internet… [Continue Reading] -

Greater transparency and digital transformation, what 2018 holds for artificial intelligence
Publié: décembre 22, 2017, 12:41pm CET par Ian Barker
One of the most interesting trends we've seen in 2017 is the spread of artificial intelligence into areas like marketing and security. Is this set to continue into next year, and are there new fields where AI is set to make a significant impact? Here are the views of some industry experts. AI isn't yet ready to go mainstream, but more businesses will be laying the ground work to use it in future, says Couchbase SVP of engineering and CTO Ravi Mayuram. "Today AI is more of a trendy buzzword than practical reality, and it’s difficult to execute because AI… [Continue Reading] -

Challenging costs and greater portability -- 2018 cloud predictions
Publié: décembre 21, 2017, 4:45pm CET par Ian Barker
The shift of systems towards the cloud has showed no signs of slowing down this year, and industry experts still see a bright future for the technology in 2018, although not without challenges along the way. Hybrid systems could see the fastest growth. "I expect hybrid to experience the largest growth spurt, because most companies have a legacy IT department and they can’t just change the business and systems to operate only on public cloud services. On the other hand, I believe net new companies will operation mostly in the public domain with only private/hybrid systems based on security and… [Continue Reading] -

Amazon pulls the plug on uploading your own music to its cloud
Publié: décembre 21, 2017, 3:44pm CET par Ian Barker
As well as being a handy way of storing items you've bought from the site, Amazon Music also allowed you to upload your own tracks and stream them from its cloud. Now though the company is quietly pulling the plug on this aspect of its service. Previously you could store 250 tracks for free, or 250,000 if you paid an annual subscription. But the ability to upload new songs is now being withdrawn. Free users lost the ability to upload on December 18th. Existing paid subscribers will still be able to upload tracks as long as the subscription is active. However,… [Continue Reading] -

An AI arms race and attacks on cryptocurrency among cyber security predictions for 2018
Publié: décembre 21, 2017, 12:16pm CET par Ian Barker
It's the time of year when industry experts like to dust off their crystal balls, examine the pattern of tea leaves in the bottom of their cups and try to predict what the coming year is going to hold. As far as security is concerned most commentators think we can expect the increase in numbers and sophistication of attacks we've seen in 2017 to continue, but there are some new things to worry about too. "The scope and pace of information security threats is jeopardizing the veracity and reputation of today’s most reliable organizations. In 2018, we will see increased… [Continue Reading] -

Ransomware dominates the 2017 threat landscape
Publié: décembre 20, 2017, 3:46pm CET par Ian Barker
Cyber attacks have been on the rise throughout 2017. According to endpoint security specialist Carbon Black, from January to December there has been a 328 percent jump in attacks against endpoints. This means a business with 10,000 employees seeing about 1,000 attacks every single day. It's ransomware that continues to be a main attack vector for criminals though. Not only is it proliferating in underground markets on the dark web, it also cost global businesses an estimated $5 billion in 2017. The company's latest threat report shows that in 2017 ransomware most often targeted tech companies, government organizations, and law… [Continue Reading] -

Android users more likely to work over Christmas
Publié: décembre 20, 2017, 3:07pm CET par Ian Barker
In many businesses Christmas is seen as a quiet time when things slow down and staff get the chance to relax. But according to enterprise file sharing company Egnyte that's not necessarily the case. The company analyzed over three billion activities from thousands of business around the world and found that, contrary to popular opinion, overall business productivity only decreased by only five percent over Christmas week (60M activities the week of Christmas against 63M activities on average for the year). In some industries -- business services, healthcare, media and entertainment, and education -- productivity actually goes up by more… [Continue Reading] -

Currency mining Android Trojan can kill your phone
Publié: décembre 19, 2017, 1:46pm CET par Ian Barker
Researchers at cyber security company Kaspersky Lab have discovered a new Android mobile Trojan called Loapi. It uses a modular architecture, allowing functions to be added to the software so it can be used for anything from crypto currency mining to DDos attacks. Crucially though Loapi can create such a heavy workload on an infected device that the battery overheats and destroys the phone. The Trojan is being spread through advertising campaigns under the guise of antivirus solutions or adult apps. Once installed, applications request device admin rights and then discreetly initiate communications with command and control servers to install additional… [Continue Reading] -

Big data delivers higher revenue and faster growth
Publié: décembre 19, 2017, 12:24pm CET par Ian Barker
Almost 60 percent of enterprises adopting big data cite both increased productivity across the organization and improved efficiency leading to reduced costs as their biggest gains. This is among the findings of a survey by enterprise software company Syncsort, which finds that the most dramatic increase in reported benefits was higher revenue and accelerated growth, which 55 percent named as a benefit this year compared with only 37 percent last year. Big data is becoming more mainstream too, Hadoop and Spark, which had high interest but low adoption at the time of Syncsort's first survey in 2014, are now in… [Continue Reading] -

Mobile ads shift to using video as spending doubles
Publié: décembre 18, 2017, 4:13pm CET par Ian Barker
With consumers spending more of their smartphone time in apps worldwide, in-app advertising continued to be the main growth area in worldwide mobile ad spending and video ads are increasingly dominant. Data from real-time advertising platform Smaato reveals in-app ad spend taking at least 85 percent of mobile ad spending in each of the top 20 mobile advertising markets worldwide. The data also shows that mobile video ad spending growth continues to outpace that of all other mobile ad formats. Video ad spending has almost doubled, showing more tha 90 percent growth in one quarter alone. Ad spaces that played… [Continue Reading] -

Consumers lack data breach awareness
Publié: décembre 18, 2017, 3:08pm CET par Ian Barker
New research from cyber exposure company Tenable reveals a widespread lack of consumer awareness surrounding the impact of data breaches. The results based on an online Harris Poll of more than 2000 US adults show that only 12 percent think their data has been stolen over the past year. But given the Equifax breach exposed up to 143 million Americans, that number is statistically impossible. Although 94 percent of those polled have heard about the security breaches that have taken place in the last year, they have taken little action to protect themselves from further exposure. Only 25 percent have… [Continue Reading] -

Why moving to the cloud can help boost security and compliance [Q&A]
Publié: décembre 18, 2017, 11:13am CET par Ian Barker
Although the adoption of cloud services has increased over the past few years, many organizations are still unwilling to make the move to the cloud due to security and compliance concerns. But Jim Hansen, VP of product marketing at security management firm AlienVault argues that companies with limited resources and budget should actually consider moving to the cloud in order to benefit from stronger security and compliance, in addition to other business benefits. We spoke to him to find out more. BN: What are the business advantages of moving to the cloud? JH: Cloud computing has proven to be more cost-effective… [Continue Reading] -

Why the IoT needs wireless power
Publié: décembre 15, 2017, 4:30pm CET par Ian Barker
With a predicted 200 billion connected devices in use by 2020, the Internet of Things is leading to a massive growth in the number of powered devices. While this is a massive opportunity for manufacturers it's also a problem as all of those devices have to be kept powered up. Batteries are the current solution, but they're expensive, limit the design and life of a device, and contain nasty substances that are difficult to dispose of when they reach the end of their life. Power technology company Ossia reckons that wireless power transmission is the answer and has produced an… [Continue Reading] -

Using AWS for data protection -- where barriers can also be benefits
Publié: décembre 15, 2017, 12:53pm CET par Ian Barker
Cloud data protection and management specialist Druva has released the results of its 2017 AWS Cloud Data Protection Survey, which shows that the three biggest barriers for moving data to AWS for cloud storage are cost, security and lack of control. But for respondents already in the cloud those same barriers are identified as the top benefits. One of the biggest benefits seen from those who have already moved their data to the cloud is cost savings (59 percent). Yet 49 percent of respondents who are considering a move cite cost as the number one barrier. "Although cloud migration has… [Continue Reading] -

The value of personal data to companies and cyber criminals
Publié: décembre 14, 2017, 3:53pm CET par Ian Barker
Businesses rely more and more on data, but a new study shows up significant differences in the value that is placed on confidential data around the world and in different industries. The research from cyber security firm Trustwave involved more than 500 IT decision makers in the United States, Canada, United Kingdom, Australia and Japan, examining attitudes towards the value of confidential data. It finds that US professionals value their personally identifiable information (PII) data more than twice as much as their UK counterparts. The average per capita value (PCV) of PII in the US is $1,820 versus $843 in the… [Continue Reading] -

Over 90 percent of security pros worry about cyber criminals using AI
Publié: décembre 14, 2017, 3:10pm CET par Ian Barker
While machine learning and artificial intelligence are becoming key to cyber security, a new survey shows that a majority of security professionals worry that the technology could be used against them. The study by cyber security company Webroot reveals that 91 percent are concerned about hackers using AI against companies in cyber attacks. Among other findings is that the US is an early adopter of AI for cyber security, with 87 percent of US professionals reporting their organizations are currently using AI as part of their security strategy. Three quarters of cyber security professionals in the US believe that, within… [Continue Reading] -

FileCloud launches GDPR support for private clouds
Publié: décembre 14, 2017, 1:15pm CET par Ian Barker
With GDPR coming into effect in may 2018, the complex requirements of the legislation may leave many companies struggling to comply. Enterprise file service platform FileCloud is adding new features to its platform to deliver compliance support for organizations using private cloud enterprise file sharing. The FileCloud platform provides a set of easy-to-use features that help enterprise organizations to adhere to the wide impact of GDPR. These include complete EU data-residency and support of GDPR compliance across both private and public cloud deployments. In addition, FileCloud is introducing the ability to manage multiple policies across users, including GDPR, which means… [Continue Reading] -

ForeScout integrates with IBM to protect IoT devices
Publié: décembre 13, 2017, 1:34pm CET par Ian Barker
The increase in the number and variety of connected devices has made enterprise IT environments much more complex. Maintaining security and compliance is a tricky problem and IoT security specialist ForeScout is integrating with IBM Security solutions to offer users stringer endpoint protection and automated risk mitigation. ForeScout Extended Module for the IBM BigFix endpoint management platform delivers real-time endpoint visibility and control beyond BigFix-managed endpoints to include unmanaged devices such as BYOD, IoT, network infrastructure and operational technology systems. It verifies the presence and operation of BigFix agents on supported corporate endpoints using ForeScout and can enroll, restart, or… [Continue Reading] -

Email is still the preferred channel for marketers
Publié: décembre 12, 2017, 5:03pm CET par Ian Barker
Despite digital disruption and the emergence of newer technologies, email is still the preferred channel for marketers according to a new report. Email marketing brand Campaigner has released the results of its Digital Marketing Industry Report which shows that past year, 59 percent of marketers reported their top challenge as increasing open rates, up eight percentage points from last year. To combat this challenge, marketers are expected to incorporate additional tools and tactics into their current marketing programs with 31 percent believing email landing pages would be the greatest return on investment boost. While email still leads, social media is… [Continue Reading] -

Bad office habits increase the chance of a data breach
Publié: décembre 12, 2017, 4:17pm CET par Ian Barker
A new study of over 1000 US office workers finds that 99 percent of those surveyed admit to conducting at least one potentially dangerous security action, from sharing and storing login credentials to sending work documents to personal email accounts. The survey by cloud business solutions provider Intermedia finds that 24 percent of office workers reuse the same login credentials for their work and personal accounts. Nearly all 96 percent automatically save work passwords on their work computer, instead of routinely entering login credentials. More than half (57 percent) of office workers admit to storing work files on their desktop… [Continue Reading] -

Poor USB security leaves enterprises at risk
Publié: décembre 12, 2017, 3:37pm CET par Ian Barker
Security polices for USB devices are frequently outdated and inadequate, and enterprises are often failing to monitor their use, according to a new survey. The study by encrypted drive specialist Apricorn reveals that while nine out of 10 employees rely on USB devices today, only 20 percent of them are using encryption on those devices. Eight out of 10 employees use non-encrypted USBs, such as those received for free at conferences, trade events or business meetings. Apricorn surveyed over 400 employees across a range of industries. It discovered that USB drives are seen as an important tool, with roughly 70… [Continue Reading] -

Malicious mobile apps fool consumers by imitating leading brands
Publié: décembre 12, 2017, 1:17pm CET par Ian Barker
By impersonating brands and fooling consumers, malicious mobile apps are on the increase, according to digital threat management leader RiskIQ in its latest Q3 mobile threat landscape report. Apps available outside of official stores are most likely to be malicious. Google’s percentage of malicious apps decreased to a low of four percent in Q3 after reaching a high of eight percent in Q2. However, one of the most prolific creators of malicious apps worked exclusively in the Play store. Secondary store AndroidAPKDescargar more than doubled its number of malicious apps to 20,907, making up about one-third of its total app count… [Continue Reading] -

70 percent of UK consumers have not heard of GDPR
Publié: décembre 12, 2017, 11:43am CET par Ian Barker
The General Data Protection Regulation (GDPR) is set to extensively change data privacy rules in the EU in May, yet a new survey from compliance solution PORT.im shows 70 percent of consumers are completely unaware of their new rights and haven't even heard of the legislation. The study also finds that 78 percent of consumers have recently had unsolicited contact from UK-based businesses. There's also a good deal of suspicion about how personal data is used. 40 percent of respondents believe that more than 200 organizations currently hold their personal data. Worryingly, for businesses ahead of the implementation of GDPR,… [Continue Reading] -

World's biggest botnet delivers new ransomware threat
Publié: décembre 11, 2017, 5:31pm CET par Ian Barker
The latest Global Threat Index from cyber security specialist Check Point reveals that the Necurs spam botnet -- reckoned to be the largest in the world -- is being used to distribute one of the latest ransomware threats. During the Thanksgiving holiday in the US, Necurs sent over 12 million emails in just one morning, distributing the relatively new Scarab ransomware, first seen in June 2017. "The re-emergence of the Necurs botnet highlights how malware that may seem to be fading away doesn't always disappear or become any less of a threat," says Maya Horowitz, threat intelligence, group manager at… [Continue Reading] -

'New Mafia' cyber attacks on businesses up 23 percent in 2017
Publié: décembre 8, 2017, 11:52am CET par Ian Barker
A new report from anti-malware specialist Malwarebytes says that the volume and sophistication of cyber attacks is growing thanks to an increase in organized cyber crime it dubs the 'New Mafia'. Ransomware attacks up to the end of October have surpassed total figures for 2016 by 62 percent. In addition, there has been an almost 2,000 percent increase in ransomware detections since 2015 -- rising to hundreds of thousands in September 2017 from less than 16,000 in September 2015. "The 'New Mafia', identified by our report, is characterized by the emergence of four distinct groups of cyber criminals: traditional gangs,… [Continue Reading] -

Three quarters of retail organizations lack a breach response plan
Publié: décembre 7, 2017, 4:07pm CET par Ian Barker
As online retailers gear up for their busiest period of the year, how prepared are they to face the threat of cyber attacks? A new study from cyber security company Tripwire reveals that just 28 percent of respondents say they have a fully tested plan in place in the event of a security breach. A worrying 21 percent say their organization doesn't have a plan at all, and the same proportion of respondents say they don't have the means to notify customers of a data breach within 72 hours, a requirement specified by GDPR. "Considering the amount of high-profile data… [Continue Reading] -

Financial services organizations fail to properly secure SSH keys
Publié: décembre 7, 2017, 3:05pm CET par Ian Barker
Secure Shell (SSH) provides a secure channel for communication over unsecured networks and is therefore a popular technology in the financial services sector. But a new study for machine identity protection company Venafi shows that even though SSH keys provide the highest levels of administrative access, they are routinely untracked, unmanaged and poorly secured. According to the findings 69 percent of respondents from the financial services industry admit they don't actively rotate keys, even when an administrator leaves their organization. This allows the former employee the potential for ongoing privileged access to critical and sensitive systems. "Cyber criminals can leverage… [Continue Reading] -

'Doppelgänging' attack hides malware from security tools
Publié: décembre 7, 2017, 12:41pm CET par Ian Barker
Endpoint protection company enSilo has used this week's Black Hat Europe conference in London to reveal how Microsoft Windows features can be used to slip malicious ransomware and other threats past most updated, market-leading AV products. enSilo researchers demonstrated how, by manipulating how Windows handles file transactions, they could pass off malicious actions as benign, legitimate processes, even if they use known malicious code. In addition to blinding Windows' embedded defense mechanisms and third-party AV and next generation AV security products to incoming threats, Process Doppelgänging gives attackers the further advantage of leaving no traceable evidence behind -- making this… [Continue Reading] -

Organizations not in control of their public cloud spending
Publié: décembre 6, 2017, 4:44pm CET par Ian Barker
Companies don't have an understanding of their public cloud spend, with 75 percent either overspending relative to their budget, or simply not knowing how much they are spending. A study by cloud optimization service Densify shows while the majority of organizations have budgeted spend for public cloud, most don't know how much their company spends monthly on these services. The amounts involved are significant, with half of organizations spending more than $300,000 per year and 20 percent spending more than $1.2 million per year. Yet only 50 percent believe that they are being charged the right amount for what they… [Continue Reading] -

Low code platforms lead to a rise in 'citizen developers'
Publié: décembre 6, 2017, 3:12pm CET par Ian Barker
The introduction of low code platforms has led to more and more applications being developed outside of the IT department. A new report from development platform company Kintone reveals that one in five executives say more than 50 percent of their applications were developed outside their IT department. 76 percent claim a portion of applications are developed outside of their IT department, while at least 32 percent of respondents' organizations actively encourage non-IT employees to develop programming or app development skills and provide training and tools for them to do so. Citizen developers get their applications out faster than large… [Continue Reading] -

60 percent of organizations aren't ready for GDPR
Publié: décembre 6, 2017, 11:55am CET par Ian Barker
With the deadline of May 2018 looming closer, a new survey shows 60 percent of respondents in the EU and 50 percent in the US say they face some serious challenges in being GDPR compliant. The study by data protection specialist Varonis polled 500 cyber security professionals in organizations with over 1000 employees in the UK, Germany, France and the US and finds more than half (57 percent) of professionals are concerned about compliance with the standard. 38 percent of respondents report that their organizations do not view compliance with GDPR by the deadline as a priority. 74 percent believe… [Continue Reading] -

New tools speed up enterprise DevOps adoption
Publié: décembre 5, 2017, 3:18pm CET par Ian Barker
Many businesses are turning to DevOps to speed up application deployment, but it's easy to become overwhelmed by the new tools, specialized skills, and cultural shifts needed to make it work. Customer engagement specialist Pegasystems is tackling this with the launch of a new tool allowing organizations to jump start their stalled DevOps initiatives to reduce time to market. Pega Deployment Manager is a no-code, model-driven tool that enables businesses to accelerate the deployment of new applications and software updates. It provides a built-in DevOps pipeline that automates CI/CD for organizations starting out with DevOps. Developers can check-in, test, and… [Continue Reading] -

How cyber crime could be improving the internet
Publié: décembre 5, 2017, 11:28am CET par Ian Barker
War always sparks innovation, and over the years conflict has led to improvements in technology and the acceleration of development in things like radar and the jet engine. So, is the war against cyber crime driving technologies that will improve the internet? Security education site Cyber Security Degrees thinks so and has produced an infographic to prove it. In 2016, cyber crime cost the global economy over $450 billion -- yet some experts have claimed trying to secure the internet is more trouble than it's worth. Part of this is down to laziness which means people don’t follow security protocol… [Continue Reading] -

New tool offers an affordable anti-ransomware solution for enterprises
Publié: décembre 4, 2017, 3:23pm CET par Ian Barker
Over the last year attacks like WannaCry and Petya have brought ransomware into the public eye like never before. Security intelligence platform CyberSight is launching a new solution to predict, detect and stop ransomware attacks. RansomStopper uses proprietary technology and machine learning to provide a multi-layered defense against ransomware for home and business use. It offers an affordable solution for business users and is being made available free for home users. "We've seen the largest ransomware attacks in history this year, and cybercriminals are showing no signs of slowing down," says Hyder Rabbani, chief operating officer at CyberSight. "Too often,… [Continue Reading] -

How the healthcare sector is waking up to phishing threats [Q&A]
Publié: décembre 1, 2017, 5:51pm CET par Ian Barker
The healthcare sector is a popular target for phishing attacks, yet it's failing to adopt simple measures like DMARC that could offer protection to both patients and staff. A new report from cyber security company Agari reveals that fewer than 10 percent NHS Trusts and Boards in the UK have self-certified as using DMARC. Globally 77 percent of healthcare organizations don't have a DMARC policy. Agari analyzed the DMARC policy status of 40 UK healthcare organizations, including hospital groups and healthcare insurers, and 5000 known NHS domains. It finds, worryingly that 92 percent of domains are carrying fraudulent email. We… [Continue Reading] -

Almost half of businesses think their leadership is digitally illiterate
Publié: novembre 30, 2017, 4:31pm CET par Ian Barker
Digital transformation is increasingly critical to business success, yet a new survey of technology professionals shows that 47 percent lack confidence in the digital literacy of their leadership. The study by technology association ISACA shows less than 25 percent of organizations believe their senior leadership is very receptive to adopting emerging technologies, while 20 percent are believed to be not receptive at all. Big data analytics is ranked highest in the chance of delivering transformational value to organizations (38 percent), easily besting AI/machine learning/cognitive (20 percent), public cloud (18 percent), IoT (14 percent), blockchain (seven percent) and AR/VR (two percent). Technologies… [Continue Reading] -

Ivanti inventories and protects enterprise endpoints
Publié: novembre 30, 2017, 3:28pm CET par Ian Barker
Endpoint systems continue to be the weakest point for most organizations, allowing a potential route for hackers to penetrate networks and steal data. IT and security operations specialist Ivanti is launching a new version of its Endpoint Manager and Endpoint Security aimed at simplifying endpoint management and security with an integrated console and workflows. Ivanti Endpoint Manager combines device discovery and inventory capabilities with secure configuration management to build an organization’s defense strategy. Ivanti Endpoint Security for Endpoint Manager extends prevention support with capabilities including device and application control and, in this release, provides new features to automate device isolation… [Continue Reading] -

Lost time on conference calls costs businesses $34 billion a year
Publié: novembre 29, 2017, 3:17pm CET par Ian Barker
Business people waste an average of 15 minutes on each conference call they make simply getting started or dealing with distractions throughout the call. This wasted time costs US and UK businesses over $34 billion/£26 billion according to a new report. Online meeting company LoopUp surveyed 1000 professionals in the US and UK and finds the cost of wasted call time is up by 46 percent since 2015. Dial-in remains the main way business people participate in conference calls, regardless of whether they have access to web or video conferencing tools. 61 percent of people (68 percent in bigger companies)… [Continue Reading] -

'Unknown' antivirus tool tops independent tests
Publié: novembre 29, 2017, 12:44pm CET par Ian Barker
German independent testing institute AV Test has released the results of its latest test of Windows home user antivirus programs. In a surprise result, Kaspersky Internet Security shares first place in the test with relative unknown AhnLab V3 Internet Security. Both achieved an 18/18 rating, the only two programs in the test to do so. Kaspersky just shades the detailed test scores with its 100 percent detection rating (opposed to 99.9 percent for AhnLab's product), and zero false positives (as opposed to one). Looking at previous tests AhnLab has had good ratings for a while but this is the first… [Continue Reading] -

Over 90 percent of cryptocurrency mobile apps contain vulnerabilities
Publié: novembre 29, 2017, 11:38am CET par Ian Barker
In the week when cryptocurrency values have reached new levels some worrying research from web security firm High-Tech Bridge reveals that more than 90 percent of the most popular cryptocurrency mobile apps on Google Play have common vulnerabilities and weaknesses. The company used its free Mobile X-Ray service to test apps for security flaws and design weaknesses that can endanger the user, data stored on the device or sent and received via the network, or the mobile device itself. Of the top 30 applications with over 500,000 installations, 94 percent contain at least three medium-risk vulnerabilities, and 77 percent contain… [Continue Reading] -

Most people would stop dealing with companies following a data breach
Publié: novembre 28, 2017, 5:03pm CET par Ian Barker
If a company suffered a data breach, 70 percent of consumers would stop doing business with it, according to a new survey of 10,000 people worldwide. The study carried out for digital security company Gemalto also reveals that 37 percent now believe that they could be a victim of a breach at any time, compared to those surveyed in 2016 (35 percent) and 2015 (27 percent). In addition 58 percent of consumers believe that the threat to their personal information increases during high profile commercial events like Black Friday, Amazon Prime Day or Cyber Monday. Two thirds of respondents (67… [Continue Reading] -

The strangest ways of stealing data
Publié: novembre 28, 2017, 3:56pm CET par Ian Barker
Most data thefts are down to relatively simple techniques, like phishing, in order to get hold of login credentials. But even where systems are well protected, hackers can find ingenious ways of breaching security. VPN advice site Top 10 VPN has compiled information from research and from real world attacks to highlight some of the more innovative ways of stealing data in an infographic. Fairly obvious approaches include accessing IoT devices like smart coffee machines, and setting up fake access points to steal network login credentials. More ingenious techniques include using the motion sensors of a smartphone placed close to… [Continue Reading] -

Number of stolen credentials at top UK companies triples in 2017
Publié: novembre 28, 2017, 11:47am CET par Ian Barker
A new study from threat intelligence platform Anomali reveals that the volume of credential exposures among FTSE 100 companies in the UK has dramatically increased to 16,583 from April to July 2017, compared to 5,275 in last year’s analysis. According to the findings 77 percent of the FTSE 100 -- the 100 largest companies listed on the London stock exchange -- were exposed, with an average of 218 usernames and passwords stolen, published or sold per company. In most cases the loss of credentials occurred on third party, non-work websites where employees reuse corporate credentials. In May 2017, more than… [Continue Reading] -

The role of education in fighting security breaches [Q&A]
Publié: novembre 23, 2017, 3:50pm CET par Ian Barker
When securing systems most people's thoughts turn to the technology of firewalls, anti-virus programs and so on. What’s often neglected is the human aspect. Many breaches are down to poor password practices or falling for phishing emails, things which can be prevented with better education. We spoke to Stephen Burke, founder and CEO of security awareness specialist Cyber Risk Aware to get his views on how awareness training can be used to drive better behavior and make businesses more secure. BN: What's the starting point for awareness training? Do you need to audit the data and who has access? SB:… [Continue Reading] -

UK government pledges cash to boost the digital economy
Publié: novembre 22, 2017, 5:45pm CET par Ian Barker
In today's budget speech the UK Chancellor, Phillip Hammond, has announced a number of measures aimed at boosting the tech sector. These include £500m of support for 5G mobile networks, full fiber broadband and artificial intelligence and £540m to support the growth of electric cars, including more charging points. A further £2.3bn is allocated for investment in research and development and £30m to develop digital skills distance learning courses. Digital economy royalties relating to UK sales which are paid to a low-tax jurisdiction -- hello Amazon, Apple, etc -- are to be subject to income tax as part of a… [Continue Reading] -

Half of UK adults want to stop using the Uber app following breach
Publié: novembre 22, 2017, 3:14pm CET par Ian Barker
The news that ride hailing service Uber has suffered, and covered up, a major hack means that millions of people could unknowingly have had their data put at risk. Data security company Egress Software Technologies ran a flash survey of 500 UK adults this morning to find their reactions to the story. Over half admitted that they weren't aware of the situation prior to being asked by Egress, however, having been made aware of the fact that Uber tried to cover up the breach, more than half (53 percent) of respondents say it has made them want to stop using… [Continue Reading] -

Adwind remote access Trojan makes a comeback and it's got smarter
Publié: novembre 21, 2017, 4:07pm CET par Ian Barker
The Adwind cross-platform, malware-as-a-service Trojan has been around since 2012. Spread by phishing emails claiming to be invoices, purchase orders, and requests for quotations, it's aimed at high value targets like finance departments. While it never completely disappeared in recent years the number of attacks did die down. However, security awareness training company KnowBe4 has noted an upsurge in Adwind emails during October of this year. "In early October we noticed an uptick in the number of phishing emails reported by customers that were sporting .JAR (Java) attachments -- a hallmark of Adwind/AlienSpy," says Stu Sjouwerman, CEO of KnowBe4. "Occasional… [Continue Reading] -

New platform helps companies gain value from data
Publié: novembre 21, 2017, 3:00pm CET par Ian Barker
Data is the lifeblood of businesses and many companies are now turning to DataOps methodology to create an agile, self-service workflow that fosters collaboration and boosts creativity, while respecting data governance policies. Data platform specialist MapR Technologies is launching its latest Converged Data Platform 6.0, offering new advancements to help organizations achieve greater value from all of their data through DataOps teams. "DataOps is an important movement, ultimately letting organizations turn their data into value as quickly as possible," says Anoop Dawar, vice president product management and marketing at MapR. "We continue to evolve the MapR Platform to accommodate the… [Continue Reading] -

How Black Friday conquered the UK
Publié: novembre 21, 2017, 11:54am CET par Ian Barker
There are various stories surrounding the origins of Black Friday, the most common being that it was the day retailers turned the corner from loss to profit and the figures in the ledger changed from red to black. Whatever its roots, Black Friday was a purely American phenomenon. That is until 2010 when Amazon first brought Black Friday deals on more than 500 products across to the UK. Since then it's caught on in a big way on that side of the pond. Loans company UK Credit has created an infographic charting the rise of Black Friday in the UK.… [Continue Reading] -

Cryptocurrency mining a growing threat to businesses
Publié: novembre 17, 2017, 4:33pm CET par Ian Barker
The CoinHive malware, designed to mine the Monero cryptocurrency when a user visits a web page -- without the user's approval -- was the sixth most common malware during October. The latest Global Threat Impact Index by Check Point released this week shows the RoughTed ad-blocker malware and Rocky ransomware are still the top two threats. However, there's a new trend toward sneakier programs with Seamless -- which redirects the victim to a malicious web page -- at number three. CoinHive can have a particularly severe impact on systems. It implants JavaScript, which then grabs high levels of the end-users'… [Continue Reading] -

100 percent of enterprises have suffered mobile malware attacks
Publié: novembre 17, 2017, 3:06pm CET par Ian Barker
A new study of over 850 organizations around the world shows that all of them have experienced a mobile malware attack. The research by cyber security company Check Point shows an average of 54 mobile malware attacks per business with Android and iOS platforms both proving vulnerable. Other findings include that 89 percent of businesses have experienced a man-in-the-middle attack over Wi-Fi. Also 75 percent of respondents averaged 35 rooted or jailbroken devices on their networks. Looked at by industry financial services (29 percent) and government (26 percent) experience the most mobile malware attacks. Both offer attractive targets for hackers with… [Continue Reading] -

Fake Black Friday apps look to steal consumer details
Publié: novembre 16, 2017, 4:06pm CET par Ian Barker
As many as one in 25 Black Friday apps could be fakes looking to steal logins and credit card information according to a new report. Digital threat management company RiskIQ has used internet reconnaissance and analytics to identify digital threats against the top five eCommerce brands during the Black Friday shopping season. It finds that more than 32,000 malicious mobile apps are using the branding of the top-five online retailers. These apps seek to trick shoppers into entering credit card information, giving up Facebook and Gmail credentials, or downloading malware that steals personal information or locks devices until ransoms are… [Continue Reading] -

Enterprises put at risk by employees' poor security habits
Publié: novembre 16, 2017, 3:24pm CET par Ian Barker
According to a new study, 25 percent of employees have tried to look at data at work that they weren't supposed to, and 60 percent were successful at accessing that data. The survey by adaptive threat prevention company Preempt also reveals widespread bad habits, with 41 percent of employees using the same password for both personal and work accounts. In addition, 20 percent of employees were aware that their passwords had been compromised in a breach, but of those 56 percent say they only changed their passwords for the account that was breached, showing they are not aware of the… [Continue Reading] -

Malware goes global with every nation affected
Publié: novembre 15, 2017, 3:01pm CET par Ian Barker
Malware is a worldwide problem affecting every nation state on the planet according to the latest Comodo Threat Research Labs report. Comodo detected almost 400 million malware incidents around the globe in the third quarter of this year, with even the tiny island nation of Kiribati in the central Pacific being affected. The top five malware hit countries are, Russia, the US, Poland, the UK and Germany. The top 20 countries accounted for nearly 319 million detections, or over 80 percent of the global total. Most nations have Trojans as their number one threat, indeed Trojans with 13.7 million detections… [Continue Reading] -

90 percent of organizations vulnerable to insider threats
Publié: novembre 14, 2017, 4:38pm CET par Ian Barker
Most enterprises and government organizations fell vulnerable to insider threats and around half have experienced an insider attack in the last year, according to a new report. Commissioned by Cybersecurity Insiders, the study is based on a comprehensive online survey of 472 cyber security professionals. Among the main factors are too many users with excessive access privileges (37 percent), an increasing number of devices with access to sensitive data (36 percent), and the increasing complexity of information technology (35 percent). 52 percent of respondents confirmed insider attacks against their organization in the previous 12 months (typically fewer than five attacks),… [Continue Reading] -

Experimentation platform aims to streamline software delivery
Publié: novembre 14, 2017, 3:47pm CET par Ian Barker
Development teams have turned to continuous delivery to help them adapt software features whilst rolling them out to customers. At the same time project management teams have used feedback mechanisms to get information on how well the software is working. The problem is that in many businesses these two operations are separate, which leads to delays and duplication of efforts. California-based Split wants to empower enterprises to make smarter product decisions with the launch of its Split Feature Experimentation Platform, a unified solution for continuous delivery and full-stack experimentation. "Today's digital transformation -- where software is core to every business… [Continue Reading] -

New platform aims to protect connected medical devices
Publié: novembre 14, 2017, 3:20pm CET par Ian Barker
Healthcare providers are spending a lot of money on connected devices. But this comes at a time when cyber attacks on healthcare targets are increasing with medical devices a prime target. Israeli start up Medigate has secured backing for a technology platform, that lets security teams defend networked medical devices from cyber attacks. It combines knowledge and understanding of medical workflow and device identity and protocols with the reality of today's cyber security threats. SEE ALSO: A quarter of UK healthcare IT pros not confident in response to cyber attacks Medigate aims to provide visibility into all medical devices connected… [Continue Reading] -

A quarter of UK healthcare IT pros not confident in response to cyber attacks
Publié: novembre 14, 2017, 1:15pm CET par Ian Barker
According to a new report, one in four UK healthcare IT professionals aren't confident in their organization's ability to respond to cyber attacks. Research from network intelligence company Infoblox finds that disruption caused to the NHS by WannaCry in May 2017 means many healthcare organizations are preparing themselves for further ransomware attacks. However, a disturbing quarter of participating healthcare IT professionals in both the UK and the US report that their organization would be willing to pay a ransom in the event of a cyber attack. Of these, 85 percent of UK respondents and 68 percent of US have a… [Continue Reading] -

New Kubernetes certification program helps deliver consistency in the cloud
Publié: novembre 13, 2017, 7:12pm CET par Ian Barker
Over the last three years open source container platform, Kubernetes has been adopted by a diverse community of providers including some of the biggest names in the cloud. Now the Cloud Native Computing Foundation (CNCF) is launching a Kubernetes Software Conformance Certification program, which ensures Certified Kubernetes products deliver consistency and portability. "The new Kubernetes Software Conformance Certification gives enterprise organizations the confidence that workloads that run on any Certified Kubernetes Distribution or Platform will work correctly on any other version," says Dan Kohn, executive director at the CNCF. "The interoperability that this program ensures is essential to Kubernetes meeting… [Continue Reading] -

Companies will waste over $10 billion in cloud spending in the next year
Publié: novembre 13, 2017, 4:27pm CET par Ian Barker
Wasted cloud spend over the next year could top $10 billion according to cloud management company RightScale. Complexity in pricing and billing is a key reason for wasted cloud spend. A typical cloud bill can contain millions of items that represent tens of thousands of different resource types and price points. AWS alone has more than 70,000 price points for compute instances. Cloud providers are also constantly changing their pricing and discount models. A further cause of waste is a decentralised approach, where departments and business units are able to set up their own cloud instances with no need to… [Continue Reading] -

Survey highlights disconnect between security expectations and reality
Publié: novembre 13, 2017, 4:15pm CET par Ian Barker
A new survey of IT decision makers shows that 89 percent are confident their organizations are in a good position to protect themselves from attacks, but four out of 10 are not taking steps to lock down information, putting themselves at risk of data loss. The study from security software company Varonis polled 500 IT decision makers in the UK, Germany, France and the US. Fifty-four percent of respondents believe their company will face a major attack in the next year. Data theft and data loss are seen as the top concerns, with 26 percent reporting that their organizations have… [Continue Reading] -

New container firewall solution speeds up enterprise integration
Publié: novembre 13, 2017, 1:16pm CET par Ian Barker
Containerization is increasingly a part of enterprise IT strategy, and like any other systems it needs to be properly secured. Container security specialist NeuVector is releasing a new version of its container firewall security solution with key security, integration, and UI additions, along with a version aimed specifically at enterprises. NeuVector 1.3 enhances critical protection across several fronts, including the ability to detect attacks that rely on tunneling. The new release also adds automatic forensic capture on every detected threat, and makes it simple for security teams to safeguard connections to and from external and legacy networks. The NeuVector solution… [Continue Reading] -

Almost half of consumers are in the dark about AI
Publié: novembre 10, 2017, 3:33pm CET par Ian Barker
According to a new study, 43 percent of consumers in the US and 46 percent in then UK say they have 'no idea what AI is about.' The research by business management software specialist Sage looks at major public concerns about AI and reveals what consumers and the tech community believe to be the greatest areas of potential impact. The majority of respondents are optimistic about the potential for AI to manage both personal and professional tasks. However, the data demonstrates the need for more education on the new opportunities AI can create to increase productivity and help build businesses.… [Continue Reading] -

Gmail accounts make up 30 percent of marketing databases
Publié: novembre 10, 2017, 1:03pm CET par Ian Barker
The number of Gmail users subscribed to marketers' email programs has increased from 17 percent in 2014 to 30 percent today, according to new data released by Yes Lifecycle Marketing. The company analyzed more than 7 billion emails sent through its cross-channel communications platform Yesmail360i. According to the findings, Gmail users make up nearly half (49 percent) of new subscribers -- those who opted into a brand's email program within the last 90 days -- and 38 percent of subscribers who opted in over the last year. The report also finds that users of the 'Big Four' mail services --… [Continue Reading] -

New self-service tool helps unlock customer data across ad platforms
Publié: novembre 9, 2017, 6:00pm CET par Ian Barker
Advertising via platforms like Google and Facebook is popular, but any insights gained from using these services are difficult to apply elsewhere. Identity management company Drawbridge is launching a new Self Service Graph dashboard that gives marketers transparency into their cross-device data by letting them tap into the service, without requiring any engineering on the client side. It applies large-scale AI and patented machine learning technology to datapoints, such as resettable device identifiers, that Drawbridge receives. The company then creates a Connected Consumer Graph of customers and touchpoints, which brands can use to build more personalized experiences for their customers.… [Continue Reading] -

84 percent of enterprises plan to move workloads to the cloud
Publié: novembre 9, 2017, 3:49pm CET par Ian Barker
The need for greater scalability and flexibility, and a desire to avoid capital expenditures are driving enterprises to move more of their workloads to the cloud. A survey by hybrid cloud operations company OpsRamp of IT professionals in organizations with over 500 employees reveals that 84 percent are planning to move more work to the cloud in the next two years. The rapid pace of change is indicated by the fact that over 40 percent say their organization only moved to the cloud in the past two years. 50 percent say their organization's cloud adoption level is still developing, while… [Continue Reading] -

Comodo launches free service to remove website malware
Publié: novembre 9, 2017, 3:17pm CET par Ian Barker
Many recent security breaches have been caused by poor website safety, allowing hackers to exploit vulnerabilities to steal data. Cyber security company Comodo is launching a free malware removal service for websites to help businesses stay secure. Once a business submits a request Comodo's security operations center analysts will instantly remove all malware, perform hack repairs, including checking the files, databases and any malicious code running to remove infection from the site, and keep the customer fully updated. The free service is powered by Comodo's cWatch platform, which is paired with security operation centers (SOCs) globally to help fight malware… [Continue Reading] -

How machine learning is set to shake up marketing
Publié: novembre 9, 2017, 12:39pm CET par Ian Barker
Artificial intelligence and machine learning are expanding their reach into many areas of business, and marketing is no exception. B2B marketing specialist Engagio has produced an infographic looking at how marketers can incorporate the latest technology into their own account based marketing strategies. Among its key points are that machine learning will have a $15.3 billion total market value by 2019, and while only 27 percent of marketers currently use AI, 51 percent plan to use it in the future. In addition 30 percent say automation saves them time and 25 percent say it provides insights into big data. More… [Continue Reading] -

Enterprises are risking an IoT technology time bomb
Publié: novembre 8, 2017, 4:59pm CET par Ian Barker
The increased use of connected devices leads to significant security challenges for 77 percent of enterprises, according to a new survey. The study conducted by Forrester for IoT security company ForeScout Technologies also reveals that 82 percent struggle to identify all of their network-connected devices, and when asked who is primarily responsible for securing IoT, IT and line of business (LoB), leaders don't have a clear answer or measure of ownership. 54 percent of respondents say that they have anxiety due to IoT security, with LoB leaders showing more concern (58 percent) compared to their IT counterparts (51 percent). Budget… [Continue Reading] -

90 percent of IT pros worry about public cloud security
Publié: novembre 8, 2017, 4:15pm CET par Ian Barker
New research commissioned by network testing, visibility, and security vendor Ixia reveals that more than 90 percent of respondents are concerned about data and application security in public clouds. In addition nearly 60 percent report that public cloud environments make it more difficult to obtain visibility into data traffic. The study carried out by Dimensional Research among 350 IT professionals responsible for cloud deployments and management in companies larger than 1,000 employees also finds that 88 percent have experienced a business related issue from a lack of visibility into public cloud traffic. The three top challenges presented by this lack… [Continue Reading] -

New endpoint protection platform aims to stop targeted attacks
Publié: novembre 8, 2017, 3:04pm CET par Ian Barker
Increasingly attacks against businesses and government organizations are targeted against a specific entity. The latest platform from endpoint protection specialist Endgame uses enhanced attack mapping and automated guidance to empower users of any skill level to stop even the most aggressive attacks. Endgame realized that security technologies fail to protect organizations from targeted attacks for three reasons -- they lack sufficient scope of attack coverage, they're too slow to detection, and they lack the required guidance and skills to uncover malicious activity in time to stop it. With this new release, Endgame aims to solve those challenges by giving security… [Continue Reading] -

More than seven billion records exposed in 2017 data breaches
Publié: novembre 8, 2017, 12:09pm CET par Ian Barker
The first three quarters of 2017 have seen 3,833 breaches reported, exposing over seven billion records, according to a new report. But the study by Risk Based Security reveals that 78.5 percent of all records exposed came from just five breaches. Compared to the same period in 2016, the number of reported breaches is up 18.2 percent and the number of exposed records is up 305 percent. The number of breaches confirmed to have exposed a million or more records now stands at 69 for the year. Inadvertent online disclosure remains the leading cause of records compromised in 2017, accounting… [Continue Reading] -

Public cloud and SaaS monitoring added to security operations platform
Publié: novembre 7, 2017, 4:48pm CET par Ian Barker
The use of SaaS applications and cloud infrastructure is becoming more widespread, but robust cyber security operations policies are often lacking for these environments. The proliferation of these services has blurred the traditional security perimeter of the enterprise, creating a growing need to unify the security and operational policies of on-premises, SaaS and public cloud infrastructure to ensure visibility into systems and data. Security operations center (SOC) as a service company Arctic Wolf Networks is meeting this need by adding SaaS application and public cloud infrastructure monitoring to its CyberSOC platform. This addition will help ensure customers stay secure and… [Continue Reading] -

One in five security professionals still uses paper to manage privileged passwords
Publié: novembre 7, 2017, 3:57pm CET par Ian Barker
A new study from identity management company One Identity reveals a worrying level of mismanagement of privileged accounts. The survey of over 900 IT security professionals carried out by Dimensional Research finds 18 percent of respondents admit to using paper-based logs, and 36 percent are using equally inadequate spreadsheets for tracking privileged accounts. The survey also finds that two-thirds (67 percent) of companies are relying on two or more tools to manage these accounts -- indicating widespread inconsistency in privileged access management (PAM). A majority (57 percent) admit to only monitoring some privileged accounts, or not monitoring privileged access at… [Continue Reading] -

Threat intelligence platform adds analyst assessments to machine learning
Publié: novembre 7, 2017, 3:10pm CET par Ian Barker
Companies are increasingly turning to AI and machine learning solutions to combat cyber threats, but sometimes there is no substitute for the insight that comes with human analysis. Threat intelligence specialist Recorded Future recognizes this and is expanding its platform to give security operations centers access to analyst-originated intelligence to offer relevant expert insights and analysis needed for operational improvements and targeted risk reduction. "To effectively combat the risks of cyber attacks, defenders need intelligence from the widest range of sources in real-time," says Dr Christopher Ahlberg, CEO and co-founder at Recorded Future. "The direct access to analyst insights combined… [Continue Reading] -

New partner program lets service providers offer erasure as a service
Publié: novembre 7, 2017, 12:57pm CET par Ian Barker
One of the areas that can often be overlooked when companies are formulating data protection strategies is what happens to information at the end of its life. It's important to dispose of unneeded information securely and data erasure specialist Blancco Technology Group is offering a new erasure as a service (EaaS) process. It's making this available through a partner program so that managed service providers can integrate it into their IT service offerings. Since launching the EaaS program, the company has signed deals with 14 global and regional partners, some of which are the world's most respected IT service providers,… [Continue Reading] -

New router-based solution protects home IoT devices
Publié: novembre 6, 2017, 4:04pm CET par Ian Barker
As we bring more and more smart devices into our homes, we potentially open ourselves up to a variety of new risks with devices opening back doors into networks or falling prey to botnets. German antivirus company Avira is launching a new approach to home security which needs no new infrastructure on the domestic network and no configuration done by the user. SafeThings sits within the home router and works with cloud-based machine learning. Avira licenses the product to router manufacturers and internet service providers, enabling them to protect networks from misuse and to deliver value-added IoT security services directly… [Continue Reading] -

Solix launches free GDPR readiness tool
Publié: novembre 6, 2017, 3:13pm CET par Ian Barker
With the GDPR implementation date of May 18th 2018 drawing ever nearer, organizations are looking to review their data management processes in order to avoid being hit with fines. Big data application provider Solix Technologies is launching a range of new data governance capabilities and assessment services to address GDPR readiness and compliance, in addition to a free online GDPR readiness grading tool. The Solix Common Data Platform (CDP) is an application framework for data-driven enterprises. Key capabilities include uniform data collection of structured and unstructured data, data governance and retention management, data security and access control, enterprise archiving, and… [Continue Reading] -

70 percent of European IT decision makers see Brexit as a business opportunity
Publié: novembre 6, 2017, 12:19pm CET par Ian Barker
Britain's decision to leave the European Union has sparked mixed emotions in the business world, but a new survey of over 800 IT decision-makers across Europe reveals that most see Brexit as an opportunity. In the survey of over 800 European IT decision-makers by cloud and network provider Interoute, 70 percent overall believe that Britain leaving the EU is an opportunity for their company. Business confidence surrounding Britain leaving the EU was highest in France (83 percent) and Belgium (78 percent) but lowest in Sweden (49 percent). While the outlook surrounding Brexit was generally positive across Europe, 63 percent of… [Continue Reading] -

One in four UK workers maliciously leaks business data via email
Publié: novembre 6, 2017, 11:53am CET par Ian Barker
New research into insider threats reveals that 24 percent of UK employees have deliberately shared confidential business information outside their company. The study from privacy and risk management specialist Egress Software Technologies also shows that almost half (46 percent) of respondents say they have received a panicked email recall request, which is not surprising given more than a third (37 percent) say they don’t always check emails before sending them. The survey of 2,000 UK workers who regularly use email as part of their jobs shows the biggest human factor in sending emails in error is listed as 'rushing' (68 percent).… [Continue Reading] -

Data protection and edge computing in the Industrial Internet of Things [Q&A]
Publié: novembre 3, 2017, 11:57am CET par Ian Barker
As the Industrial Internet of Things (IIoT) takes hold across multiple industries, buzz around edge computing is growing in parallel as operators evolve to push more and more computing power to the edge of their networks, where IIoT functions really live. The data being generated, however, is now becoming more and more critically important, requiring new levels of protection. We spoke to Jason Andersen, VP of business line management at Stratus Technologies, a provider of availability solutions for edge computing, IIoT and critical infrastructure. Jason offers his insights on the evolution of data criticality and protection as well as unified… [Continue Reading] -

All you need to know about IoT Botnets [Q&A]
Publié: novembre 2, 2017, 4:06pm CET par Ian Barker
Connected devices like smart TVs and webcams aren't new -- but since their inception 30 years ago, the number of humans connected to the internet has been surpassed by the number of devices connected to it. In fact, industry analysts estimate the number of connected devices will reach 50 billion by 2020. And as the number of connected devices increases exponentially, so the number of security risks grows as well. We spoke with Steinthor Bjarnason, network security research engineer for DDoS and advanced threat protection provider Arbor Networks' Security Engineering and Response Team (ASERT), to get a clear understanding of… [Continue Reading] -

One in four organizations use only passwords to secure BYOD
Publié: novembre 2, 2017, 12:21pm CET par Ian Barker
Allowing employees to access corporate data via their own devices is increasingly popular, but it does present risks if not implemented correctly. A new report from data protection company Bitglass finds one in four organizations do not have multi-factor authentication methods in place to secure BYOD -- a well-known enterprise security gap. This is despite the fact that single-factor authentication, via passwords to control user access to corporate data, has resulted in several high-profile data breaches in recent months, including Zomato, Deloitte and Microsoft. "Enterprises often misjudge the effectiveness of traditional security solutions, many of which are readily bypassed," says… [Continue Reading] -

IBM launches container-driven private cloud platform
Publié: novembre 1, 2017, 4:19pm CET par Ian Barker
While public cloud adoption continues to grow, organizations, especially in regulated industries like finance and health care, are continuing to use private clouds to quickly launch and update applications. To tap into this market IBM is launching a new Cloud Private software platform, designed to enable companies to create on-premises cloud capabilities similar to public clouds to accelerate app development. The new platform is built on open source Kubernetes-based container architecture and supports both Docker containers and Cloud Foundry. This allows integration and portability of workloads as they evolve to any cloud environment, including the public IBM Cloud. Features include… [Continue Reading] -

IT pros predict a long term future for the mainframe
Publié: novembre 1, 2017, 3:17pm CET par Ian Barker
In spite of trends towards decentralization and the cloud, the mainframe remains a relevant and growing data center hub for many businesses according to a new report. In the 12th annual Mainframe Research Report from IT solutions company BMC 91 percent of respondents predict mainframe workloads will continue to grow, and 51 percent say more than half of their data resides on a mainframe. "Results from the 2017 BMC Mainframe Research Report provide a good indicator on the future health and viability of the mainframe," says Bill Miller, president of ZSolutions at BMC. "The survey shatters a prevailing variety of… [Continue Reading] -

Misuse of spreadsheets costs European businesses €55 billion a year
Publié: novembre 1, 2017, 1:44pm CET par Ian Barker
Spreadsheets like Excel were never designed to handle complex analytics and big data tasks, but a growing demand for data insights is leading many businesses to waste effort manually handling data in spreadsheets. A study commissioned by self-service analytics company Alteryx and carried out by IDC reveals that advanced spreadsheet users spend on average nine hours a week on repeat effort manually manipulating data, wasting €10,000 per year. Across Europe this represents, on average, two billion hours of duplicate work, costing an eye-watering €55bn per year (around $64bn). According to the findings there are 30 million advanced spreadsheet users worldwide,… [Continue Reading] -

Why the cloud doesn't work for all businesses [Q&A]
Publié: novembre 1, 2017, 11:52am CET par Ian Barker
As more and more applications move to the cloud there's an increasing assumption that it's the right approach for everyone. Indeed we've seen recently that many cloud investments are being made out of fear of missing out. But this one size fits all approach isn't necessarily the right one, and can put companies in a difficult position. We spoke to Michael Hiskey, Chief Strategy Officer from intelligent data management company Semarchy, to find out what businesses should consider before moving to the cloud and how they can avoid being forced down that route. BN: Are companies adopting the cloud for… [Continue Reading] -

Security worries delay migration to the cloud
Publié: octobre 31, 2017, 5:34pm CET par Ian Barker
Nearly a third of enterprises plan to increase their public cloud usage in the next 12 to 18 months, but the majority harbor significant concerns about cyber attacks and breaches in their hybrid environments. An international survey of 450 senior security and network professionals by security vendor AlgoSec reveals the greatest concerns about applications in the cloud are cyber attacks (cited by 58 percent) and unauthorized access (53 percent), followed by application outages and mis-configured cloud security controls. The biggest security management challenges in hybrid clouds are lack of visibility (cited by 63 percent of enterprises) and managing security policies… [Continue Reading] -

Illicit code signing certificates worth more than passports on the dark web
Publié: octobre 31, 2017, 4:45pm CET par Ian Barker
Code signing certificates are used to verify the authenticity and integrity of software and are a vital element of internet and enterprise security. By taking advantage of compromised code signing certificates, cybercriminals can install malware on enterprise networks and consumer devices. A study for machine identity protection company Venafi by the Cyber Security Research Institute shows that digital code signing certificates are changing hands on the dark web for up to $1,200, making them worth more than credit cards, counterfeit US passports and even handguns. "We've known for a number of years that cyber criminals actively seek code signing certificates… [Continue Reading] -

Process mining and robotic automation combine to drive digital transformation
Publié: octobre 31, 2017, 4:06pm CET par Ian Barker
Enterprises face many challenges when automating their processes, not least in identifying which have the most potential to benefit from the process. A new collaboration between robotic process automation (RPA) platform company, UiPath and leader in process mining, Celonis, lets customers automatically visualize and screen their processes for areas with highest automation potential, and subsequently, build, test, and deploy RPA in an accelerated and structured fashion. "UiPath is committed to delivering the most capable, agile and scalable RPA platform in the market," says Daniel Dines, CEO and founder of UiPath. "Working with Celonis, our vision is to dramatically accelerate process… [Continue Reading] -

Analysis uncovers more than 3,200 unique phishing kits
Publié: octobre 31, 2017, 3:22pm CET par Ian Barker
The people behind phishing attacks are always looking for ways to improve their profitability. They quite often re-use material by bundling site resources into a phishing kit, uploading that kit to a server and sending a new batch of emails. Sometimes though they get careless and leave the kits behind allowing them to be analyzed. Trusted access specialist Duo Security carried out a month-long experiment to track down these abandoned kits. Over the course of the study it found more than 3,200 unique phishing kits, tracked the actors behind the kits, identified kit re-use across sites and more. To create… [Continue Reading] -

Top American banks have significant gaps in GDPR website compliance
Publié: octobre 31, 2017, 1:10pm CET par Ian Barker
GDPR affects all companies that engage with EU citizens, even if they have no physical presence in the EU, but a new study reveals that some major US firms still have websites that don’t comply. The research by digital threat management company RiskIQ looks at 25 of the 50 largest banks in the US (as of 2017) and finds significant security gaps in personally identifiable information (PII) collection. Per organization, RiskIQ has identified an average of 1,891 insecure login forms, 1,663 pages collecting PII insecurely, 1,326 EU first-party cookie violations and 1,265 EU third-party cookie violations. "PII discovery, inventory, and… [Continue Reading] -

Open source developers make progress in adopting secure practices
Publié: octobre 31, 2017, 11:26am CET par Ian Barker
Secure software development practices are increasingly being adopted by open source software (OSS), and are underscoring the importance of managing OSS risk. The latest report from development platform Synopsys uses results from the free Coverity Scan static analysis solution to assess the quality of development practices and the overall maturity of the OSS ecosystem. "Due to the ubiquity of open source and the vital role it plays in virtually all types of software, understanding and managing its risks can no longer be optional," says Andreas Kuehlmann, senior vice president and general manager of the Synopsys Software Integrity Group. "The Coverity… [Continue Reading] -

Password cracking tool helps admins test security
Publié: octobre 30, 2017, 4:56pm CET par Ian Barker
Weak or reused passwords are a common cause of security breaches but are something that it’s hard for administrators to police. Intelligence-led security company FireEye is releasing a new password cracking tool to enable security professionals to test password effectiveness, develop improved methods to securely store passwords, and audit current password requirements. The main program is installed on a server, but a further 'worker' component means GoCrack is able to distribute its processing across CPUs and GPUs on networked machines via a simple to use web-based interface to create, view, and manage tasks. In order to protect sensitive password data,… [Continue Reading] -

Four in five companies aim to change the way they manage IT security in the next year
Publié: octobre 30, 2017, 4:09pm CET par Ian Barker
According to a new study, 80 percent of businesses across the US and UK will change how they deal with security in the coming 12 months. The survey of more than 400 SMEs and enterprises by service management company SolarWinds MSP finds that 17 percent of companies intend to switch their current service provider in the next 12 months, 10 percent want to cease outsourcing in favour of in-house management, and 49 percent planning to outsource their security for the first time. For service providers this presents an opportunity. Businesses currently handling security internally but now wanting to outsource their… [Continue Reading] -

UK hosting firm launches free GDPR guide
Publié: octobre 27, 2017, 11:48am CEST par Ian Barker
With GDPR coming into force in May next year, worrying numbers of businesses are still unprepared for the impact of the new legislation which represents a major shake up in data protection. UK hosting firm UKFast wants to help get businesses on the right track and is launching a free pocket guide to GDPR along with a downloadable toolkit. The guide is broken down into sector-specific chapters and offers actionable advice, covering everything businesses need to get up to speed on GDPR compliance. It includes specialist advice for the retail, hospitality and leisure, professional services, not-for-profit, IT and public sectors.… [Continue Reading] -

HomeHack vulnerability could allow your LG robot vacuum to spy on you
Publié: octobre 26, 2017, 4:56pm CEST par Ian Barker
Researchers at threat prevention specialist Check Point have uncovered a vulnerability which could allow hackers to gain control of the LG Hom-Bot robot vacuum cleaner's video camera. The camera normally sends live video to the associated LG SmartThinQ app as part of its HomeGuard Security feature. Once in control of a specific user's LG account, any LG device or appliance associated with that account could be controlled by the attacker -- including the robot vacuum cleaner, refrigerators, ovens, dishwashers, washing machines and dryers, and air conditioners. Dubbed HomeHack, the vulnerability in the SmartThinQ mobile app enabled Check Point's researchers to… [Continue Reading] -

82 percent of security professionals worry about nation-state attacks
Publié: octobre 26, 2017, 4:54pm CEST par Ian Barker
Nation-state attacks and hacktivists are among the biggest worries for IT security professionals according to a new study. The report by AI security company Cylance and the Enterprise Strategy Group shows that 82 percent of respondents are concerned or extremely concerned by the threat posed by nation-states, and 79 percent are by the threat of hacktivists. Cyber criminals are still seen as concerning by 99 percent and insider threats concern 78 percent. Interruptions to standard business operations are seen as the top impact of compromised endpoints (32 percent), followed by impeding the productivity of knowledge workers (31 percent), and delays… [Continue Reading] -

Traditional antivirus fails to protect 40 percent of users
Publié: octobre 26, 2017, 2:56pm CEST par Ian Barker
Conventional antivirus solutions are failing to protect users from attacks according to a Malwarebytes report. The study is based on real-world clean up scans performed by Malwarebytes. Nearly 40 percent (39.18percent) of all malware attacks cleaned on endpoints with an AV installed occurred on endpoints that had two or more traditional AV solutions registered. In addition 39.16 percent of attacks on endpoints with a non-OS bundled AV installed occurred on an endpoint running one of the four leading traditional AV solutions. "The results of these scans clearly indicate the ineffectiveness of today's traditional AV solutions and, more importantly, the unknown risks… [Continue Reading] -

New cross-channel tool helps businesses understand customers
Publié: octobre 25, 2017, 6:46pm CEST par Ian Barker
While it's easier than ever to collect information about customers, businesses often struggle to extract meaningful information from it in order to drive sales. The latest tool from customer data platform Segment lets enterprises build a record of their entire relationship with a customer, and use it to create personalized experiences everywhere they interact with their users. Called Personas, it allows a retail businesses to understand the complete history of each user across all channels, in one centralized record. These records can then be made available in tools that the company uses to interact with its customers. For example, Personas… [Continue Reading] -

Virtual reality could attract new talent to security careers
Publié: octobre 25, 2017, 5:10pm CEST par Ian Barker
The cyber security industry continues to face a skills crisis, but a new study from security vendor ProtectWise and analyst ESG suggests that the adoption of new technologies could be instrumental in attracting new talent. The survey of over 500 16 to 24 year-olds finds that 74 percent say that the use of gaming and VR technology in the fight against cyber crime would increase the likelihood of them pursuing a cyber security career. Just one percent of employed respondents are working in cyber security and only nine percent of all respondents show an interest in pursuing a career in… [Continue Reading] -

Cyber criminals turn to messaging apps following dark web crackdown
Publié: octobre 25, 2017, 1:21pm CEST par Ian Barker
The recent crackdown on popular dark web markets AlphaBay and Hansa is driving cyber criminals to migrate to messaging apps like Discord, ICQ, Skype, Telegram and Whatsapp, according to a new report. The study from threat management company IntSights analyzed thousands of black markets, text storage/paste sites, hacking forums, IRC channels, apps and social media pages, and uncovers a steady increase in threat actors inviting cyber crime forum users to join their chat groups. The company estimates that hundreds of thousands of users of prominent mobile messaging apps may be using them to trade stolen credit cards, account credentials, malware… [Continue Reading] -

Gender divide opens up as mobile apps become the preferred way of booking travel
Publié: octobre 24, 2017, 6:02pm CEST par Ian Barker
The latest annual Mobile App Engagement Index from app marketing platform Liftoff shows that travel reservation bookings on mobile have finally hit critical mass adoption. Users are becoming accustomed to doing more on mobile and reservation apps are increasingly popular. This year's data shows that for businesses the cost-per-first-booking has dropped. In 2017, the peak cost to acquire a mobile user who made a reservation was $36.95, nearly half of last year's peak cost of $61.09. What's more, the average cost-per-reservation in 2017 ($27.98) was $16 less than the 2016 average ($43.88). There is a divide between the sexes when booking… [Continue Reading] -

CyberScout launches one-stop marketplace for identity management
Publié: octobre 24, 2017, 5:24pm CEST par Ian Barker
Recent breaches like that at Equifax have highlighted the importance of supporting victims with identity management services in the aftermath of an attack. Identity and data defense firm CyberScout is launching a comprehensive marketplace for identity management, privacy, and cyber security education products and services, aimed at providing individuals with a one-stop-shop solution for all services relating to cyber protection. Aimed primarily at insurers, CyberScout HQ is designed as an online marketplace that delivers everything needed to combat cyber crime. Brokers and insurers can add their own branding and configure it to address multiple audience segments and prioritized threats for… [Continue Reading] -

Industrial and infrastructure networks are prime targets for attackers
Publié: octobre 24, 2017, 4:28pm CEST par Ian Barker
Operational technology networks are used with specialized Industrial Control Systems (ICS) to monitor and control physical processes such as assembly lines, mixing tanks, and blast furnaces. These networks are ripe targets for adversaries according to a new study from industrial cyber security company CyberX. Many of these networks are exposed to the public internet and easy to crack using simple vulnerabilities like plain-text passwords. Lack of even basic protections like antivirus can enable attackers to quietly perform reconnaissance before sabotaging physical processes. Once attackers get into an OT network it's relatively easy for them to move around and compromise industrial… [Continue Reading] -

One in three businesses can't keep up with cloud security
Publié: octobre 24, 2017, 3:50pm CEST par Ian Barker
Maintaining security in the cloud and container environments is an increasing problem according to a new survey. The study by intrusion detection platform Threat Stack finds that 31 percent of those interviewed say they are unable to maintain security as their cloud and container environments grow. As a result, 62 percent say that they’re seeking greater visibility into their public cloud workloads. 57 percent of those surveyed report significant delays in the sales cycle due to trouble meeting customer security requirements. In addition 59 percent report the same issue around meeting customer compliance requirements. This sees nearly one in three of… [Continue Reading] -

Mention of bugs in reviews puts half of users off downloading apps
Publié: octobre 24, 2017, 3:14pm CEST par Ian Barker
Half of app users are likely to be dissuaded from downloading an app based on customer reviews that mention bugs and glitches, according to a new survey. The study conducted by independent software testing company QualiTest Group, shows users aged 45 to 54 are the least likely to download an app with negative customer reviews, and are the age group least convinced that companies do enough to ensure UX and update apps to have fewer bugs. Only 10 percent of app users are 'very likely' to download an app despite customer reviews referencing bugs and glitches. Just 35 percent of… [Continue Reading] -

New endpoint protection platform guards against nation state attacks
Publié: octobre 23, 2017, 4:03pm CEST par Ian Barker
Endpoint security company Endgame has become the first protection platform that measures its effectiveness not just against malware but against nation-state level attacks. It has worked with MITRE Corporation to validate protections against MITRE's ATT&CK Matrix, a framework for adversarial tactics and techniques that enterprises encounter daily. Using this approach provides a far more realistic understanding of protection against targeted attacks compared to other testing regimens. The results illustrate Endgame’s ability to detect and protect against nation-state level attackers before data theft or damage. "The industry must redefine the scope of endpoint protection to ensure their technologies are truly effective against… [Continue Reading] -

Successful DevOps implementation needs a clear plan
Publié: octobre 20, 2017, 11:23am CEST par Ian Barker
Businesses are reporting strong success in transitioning to DevOps, provided there is careful upfront planning and an honest assessment of resources, according to a new study. The survey, by development and testing services firm KMS Technology, finds that among the 200+ IT professionals questioned, 43 percent report having a 'very positive' impression of DevOps prior to their transitions. When these transitions were completed, 51 percent report a very positive impression, and 79 percent say they have achieved their desired goals. There are some challenges though, the most significant being the limited skill set and knowledge of DevOps among in-house IT… [Continue Reading] -

McAfee introduces advanced analytics to protect endpoints and the cloud
Publié: octobre 18, 2017, 6:01pm CEST par Ian Barker
Security teams face ever larger and more complex amounts of data which can hinder their ability to defend against threats. McAfee is introducing new solutions that make use of the automation, reasoning and data duration provided by advanced analytics technologies, allowing security teams to easily discover and assess data and root out threats. McAfee Investigator uses both machine learning and artificial intelligence, to increase accuracy and confidence of investigations by automating data collection and empowering security analysts of varied experience to fully assess threats in less time. It allows analysts to focus on the most significant threats by using advanced analytics… [Continue Reading] -

Security professionals say the need for soft skills has increased
Publié: octobre 18, 2017, 3:26pm CEST par Ian Barker
According to the results of a new survey, the need for soft skills like communication and critical thinking has increased in the IT security sector. The study conducted by Dimensional Research for security and compliance specialist Tripwire finds that 72 percent of security professionals say the need for soft skills is now greater. 21 percent believe soft skills are actually more important than technical skills when hiring staff, and 17 percent expect to hire people without security-specific expertise over the next two years. The most important soft skills cited are analytical thinking (selected by 65 percent), good communication (60 percent)… [Continue Reading] -

SailPoint launches updated identity governance platform
Publié: octobre 18, 2017, 1:10pm CEST par Ian Barker
Identity management company SailPoint is announcing enhancements to its open identity platform, designed to enable identity to be woven throughout the IT operations and security fabric of organizations. IdentityIQ version 7.2 enables a unified approach to identity governance that shares identity information across all IT and security investments. It allows identity governance to be extended as a shared service across global enterprise infrastructures. Key to this are newly expanded open identity platform capabilities. In addition, there are expanded APIs so critical identity governance processes can easily be shared or invoked from both proprietary and legacy IT solutions. Other enhancements include integration… [Continue Reading] -

Windows 10 Fall Creators Update -- what's in it for IT pros?
Publié: octobre 18, 2017, 12:16pm CEST par Ian Barker
As the latest update for Windows 10 begins its roll out, many professional users will be wondering about its impact and whether it will make their lives easier or harder. Fall Creators Update has a number of changes which should prove useful for IT pros including streamlined deployment, enhanced analytics and new security features. Admins can use the Windows Store for Business to set up AutoPilot deployment profiles so that when someone in the organization installs a new PC and attaches it to the company network, AutoPilot sets up Windows based on the profile settings assigned. There's also a new… [Continue Reading] -

Are your employees snooping on your corporate network?
Publié: octobre 17, 2017, 4:38pm CEST par Ian Barker
A new survey of IT security professionals reveals that 92 percent of respondents say employees at their organizations try to access information that is not necessary for their day-to-day work. The study from identity management company One Identity also shows that IT security professionals themselves are among the worst offenders for corporate data snooping. One in three respondents admit to having accessed sensitive information that is not necessary for their day-to-day work -- showing an ongoing abuse of elevated rights given to the IT security role. More than one in three (36 percent) of IT pros admit to looking for… [Continue Reading] -

Microsoft launches its most powerful Surface Book yet
Publié: octobre 17, 2017, 4:01pm CEST par Ian Barker
Microsoft is set to begin shipping its second generation Surface Book in November and says it wants to offer the power of a desktop with the versatility of a tablet. Surface Book 2 will be available in both 13 and 15-inch versions, weighing in at 3.38lbs and 4.2lbs respectively, both will have a PixelSense Display with multi-touch, plus Surface Pen, and Surface Dial on-screen support. The 15-inch version will have nearly seven million pixels -- 45 percent more than a MacBook Pro. Surface Book 2 is based around the eighth generation Intel Core i7 processor with NVIDIA GeForce GTX 1050… [Continue Reading] -

Companies overlook risks in open source software
Publié: octobre 17, 2017, 3:14pm CEST par Ian Barker
Open source code helps software suppliers to be nimble and build products faster, but a new report reveals hidden software supply chain risks of open source that all software suppliers and IoT manufacturers should know about. The recent Equifax breach for example exploited a vulnerability in a widely used open source web framework, Apache Struts, and the study by software monetization specialist Flexera points out that as much as 50 percent of code in commercial and IoT software products is open source. "We can't lose sight that open source is indeed a clear win. Ready-to-go code gets products out the… [Continue Reading] -

Russia set to take on Bitcoin with its own 'CryptoRuble'
Publié: octobre 16, 2017, 5:40pm CEST par Ian Barker
Having earlier called for crypto currencies to be banned, Russian President Vladimir Putin has now officially stated that Russia will issue its own CryptoRuble using Blockchain technology. According to communications minister Nikolay Nikiforov, CryptoRubles will be exchangeable for conventional Rubles and will be accepted by Russian banks. However, holders will need to pay 13 percent tax if they don't provide proof of origin, a measure intended to combat money laundering. The idea behind the introduction seems to be to boost the country's online economy in a way that doesn't need dependence on foreign money markets or third party transaction brokers.… [Continue Reading] -

AsTech offers Qualys Cloud Platform with a $1 million breach cost guarantee
Publié: octobre 16, 2017, 3:19pm CEST par Ian Barker
The Qualys Cloud Platform is designed to give customers a continuous, always-on assessment of their global security and compliance posture across all global IT assets, wherever they reside. Cyber risk management company AsTech is boosting its attractiveness further for its Managed Qualys Service customers by offering a $1 million guarantee for securing perimeter networks. AsTech Vigilance for Managed Qualys Services implements, configures and manages Qualys to ensure all vulnerabilities it is capable of finding for perimeter assets are found and presented in a prioritized report. "Throughout our 20 year history, no AsTech customer has ever experienced a data breach, and… [Continue Reading] -

Almost half of UK infrastructure will have moved to the cloud in six months
Publié: octobre 16, 2017, 12:47pm CEST par Ian Barker
A new survey of UK IT decision makers by cloud and network provider Interoute shows the cloud is increasingly seen as the best platform for providing scalable infrastructure. The results reveal that businesses plan to move on average just under half (46 percent) of their infrastructure to the cloud over the next six months. Businesses are looking for ways to remain competitive whilst managing costs and ensuring stability, but integrating digital and legacy technologies remains a priority too. Nearly four in 10 (38 percent) citied this as a key consideration. Over half (56 percent) of businesses named their ability to… [Continue Reading] -

Enterprises not confident they can protect mobile data traffic
Publié: octobre 13, 2017, 12:28pm CEST par Ian Barker
While companies are becoming increasingly dependent on mobile workers and distributed offices, a new survey reveals that IT staff are not confident they can protect remote workers. The study by distributed gateway platform supplier iboss also finds that senior (CEO, CIO, CISO, and CTO) respondents are more confident in their organizations' ability to secure mobile traffic than more junior IT executives. 56 percent of CIOs, CISOs, and CTOs were not confident they could secure mobile traffic compared to 80 percent of subordinate IT executives. Among other findings are that 43 percent of business-to-business (B2B) IT executives are not confident they… [Continue Reading] -

80 percent of enterprises are investing in AI but a third think they need to spend more
Publié: octobre 12, 2017, 3:01pm CEST par Ian Barker
Although 80 percent of enterprises are investing in AI today, one in three business leaders believes their company will need to invest more over the next three years to keep pace with competitors. This is one of the findings of a survey of 260 large, global organizations, conducted by research firm Vanson Bourne for data and analytics specialist Teradata. The industries where respondents expect to see the most impact from AI are IT, technology and telecoms (59 percent), business and professional services (43 percent), with customer services and financial services tied for third on 32 percent. The areas where AI… [Continue Reading] -

Free online service tests mobile app security and privacy
Publié: octobre 12, 2017, 11:43am CEST par Ian Barker
When you download a mobile app you sometimes get more than you bargained for, Uber's app that tracked iPhone users for example. It can be hard to know exactly what apps on your phone are up to. Now though, application security testing company High-Tech Bridge is launching a free 'Mobile X-Ray' service for developers that analyses native and hybrid iOS and Android apps and detects the most common weakness and vulnerabilities. According to High-Tech Bridge at least one Open Web Application Security Project (OWASP) top ten vulnerability is found in 97 percent of Android and 85 percent of iOS apps.… [Continue Reading] -

Ransomware economy grows 2500 percent since 2016
Publié: octobre 11, 2017, 4:40pm CEST par Ian Barker
We all know that ransomware is a big problem, but a new report from cyber security company Carbon Black reveals that it's increasingly big business too. According to the report, there are currently more than 6,300 dark web marketplaces selling ransomware, with over 45,000 product listings. Between 2016 and 2017 to date ransomware sales on the dark web have grown from $249,287 to $6,237,248, a growth rate of just over 2,500 percent. According to the FBI, ransom payments extorted total about $1 billion in 2016, up from $24 million in 2015. Successful ransomware authors can earn $163,000 or more annually.… [Continue Reading] -

The 10 phishing subject lines you're most likely to click
Publié: octobre 11, 2017, 3:37pm CEST par Ian Barker
Phishing is still a key tool for cyber criminals as they seek to insert malware onto machines and to get hold of personal details. Although most people are aware of the threat there are still some subject lines that are much more likely to deliver results for the phishermen than others, according to security awareness training specialist KnowBe4, which has released its Top 10 Global Phishing Email Subject Lines report for the third quarter of 2017. The company looked at tens of thousands of email subject lines used in simulated phishing tests to uncover just what makes a user want… [Continue Reading] -

Endpoint data is increasingly critical for organizations
Publié: octobre 11, 2017, 2:59pm CEST par Ian Barker
In a world where more systems are in the cloud or virtual environments, you’d expect the importance of endpoint data to decline, but a survey conducted at this year’s VMworld US suggests this is not the case. The survey by data security and recovery company Code42 reveals that 42 percent of organizations are storing between 50 and 100 percent of their data on endpoints. In the higher education sector it's noticeably higher, with 81 percent storing half or more of their data on endpoints. The majority of companies (65 percent) are using their endpoint data for tasks beyond just backup,… [Continue Reading] -

73 percent of CFOs trust the cloud for financial data
Publié: octobre 11, 2017, 1:12pm CEST par Ian Barker
Chief finance officers are becoming more confident about the use of the cloud to store their company's data according to a new survey. The study from cloud performance management company Adaptive Insights finds that just three years ago only 33 percent of CFOs trusted the cloud for their financial data, but today 73 percent do so. "The cloud enables a level of data access that Finance teams need in order to meet the demand for accurate, real-time information from across the enterprise," says Robert S Hull, founder and chairman at Adaptive Insights. "This quarter’s report validates that CFOs are embracing… [Continue Reading] -

New cloud platform offers faster app development
Publié: octobre 9, 2017, 4:26pm CEST par Ian Barker
There's increasing demand from businesses to produce apps quickly, but at the same time ensure that they are robust and reliable. Open source web portal company Liferay is launching a cloud platform that gives developers the infrastructure, services and hosting capabilities they need to quickly build, launch and scale their applications. Called WeDeploy, it removes common backend obstacles so that application developers can focus their time and resources on the differentiating features of their products. Businesses creating an application need a fast, reliable deployment method and WeDeploy provides application hosting through the cloud with just a few lines of code.… [Continue Reading] -

IT departments and users are out of step on password security
Publié: octobre 6, 2017, 12:49pm CEST par Ian Barker
A new survey reveals that 76 percent of employees say they experience regular password usage problems and more than a third need password-related help desk support at least once every month. According to the study from password manager LastPass and business intelligence company Ovum nearly three-quarters say they would want to use a tool to help store and access passwords without needing to remember each one if their company offered such a solution. Other findings show that 61 percent of IT executives rely exclusively on employee education to enforce strong passwords. Employees are therefore left on their own, with no… [Continue Reading] -

Three-quarters of Brits worry about risks from connected homes
Publié: octobre 5, 2017, 4:24pm CEST par Ian Barker
Despite their potential to reduce bills and make life easier, 76 percent of British consumers are worried about the impact of smart technology and connected homes. A study by price comparison site MoneySuperMarket polled more than 2000 people and reveals many are fearful of the smart homes concept, with unapproved data collection cited as the greatest worry. Other concerns include the technology being hacked by criminals (51 percent), being made unusable by a virus (43 percent) and recording you without your knowledge (42 percent). While 77 percent of Brits have heard of a 'connected' home, only six percent claim to… [Continue Reading] -

Most organizations aren't sure where their data is stored
Publié: octobre 5, 2017, 3:14pm CEST par Ian Barker
The modern IT landscape means that information can be stored across a number of platforms and locations. It's perhaps not surprising then that only 47 percent of organizations know where their data is stored at all times according to a new study. The survey by McAfee of 800 business decision makers looks at how enterprises are looking after their data in the light of legislation including GDPR. The findings reveal that nearly half (48 percent) of organizations surveyed will migrate their data to a new location because of regulations like GDPR. A similar amount will migrate their data because of… [Continue Reading] -

Cost and complexity are top barriers to DevOps adoption
Publié: octobre 4, 2017, 4:43pm CEST par Ian Barker
While DevOps seems to be flavor of the month with many organizations, the path to adoption is not necessarily a smooth one. Intelligent SaaS specialist Pensa has conducted a survey of more than 200 IT decision makers with a view to identifying the biggest challenges they face in the adoption of DevOps practices. Limited budgets are cited as the top barrier to DevOps success by 19.7 percent of respondents. This is followed closely by the constraints of legacy systems (17.2 percent), application complexity (12.8 percent), difficulty managing multiple environments (11.3 percent), and company culture (9.4 percent). Other barriers for DevOps… [Continue Reading] -

New platform delivers relevant, risk-based threat intelligence
Publié: octobre 4, 2017, 4:12pm CEST par Ian Barker
Keeping on top of the latest threats can be a major task, so it's no surprise that many businesses are turning to automated solutions to help ease the workload. Threat intelligence provider Recorded Future is launching a new machine learning based platform called Threat Views which enables the delivery of relevant threat intelligence in real-time based on analysis of billions of data points in every language. It uses a combination of dynamic risk scores, updated in real time, reflecting analysis of known risks associated with IP addresses, hashes, domains, and vulnerabilities, plus organization-specific priorities based on an enterprise’s environment including… [Continue Reading] -

59 percent of business processes could be automated by 2022
Publié: octobre 4, 2017, 12:15pm CEST par Ian Barker
According to a new survey of IT decision makers in the US and UK, 59 percent of business processes could be automated within the next five years, with 70 percent believing that robotics have become more of a priority. The study from robotics specialist Redwood Software identifies the key benefits of automation as speed of process and reduction of manual effort, while the key risks are security and cost. "Companies are rapidly unlocking the potential of robotics and automation, and transforming their entire businesses in the process," says Dennis Walsh, president of Americas and Asia-Pacific for Redwood Software. "The acceleration of… [Continue Reading] -

Art for data's sake -- pop-up shop takes personal information as payment
Publié: octobre 3, 2017, 4:15pm CEST par Ian Barker
Cyber security company Kaspersky Lab has been running an interesting experiment in London with a shop that only accepts personal data as payment. The Data Dollar Store provided shoppers with the opportunity to get their hands on exclusive prints and artwork by street artist Ben Eine. The difference came at the checkout where the only way to pay was with Data Dollars -- a new currency created by Kaspersky Lab that consists of a customer's personal data held on smartphones such as images, video or texts. "We see the Data Dollar mainly as a means to raise awareness for the… [Continue Reading] -

Conversational interface helps insider threat detection
Publié: octobre 3, 2017, 3:30pm CEST par Ian Barker
Lack of visibility into endpoints poses a major issue for enterprises as IT administrators can be left in the dark about where data is and how it's being used. This means that when data breaches occur it can take longer to detect the source. A new tool from ThinAir aims to shorten this detection time by analyzing interactions and making information available via a conversational interface. "ThinAir helps CISOs and security analysts become 10 times faster and more effective, by automating many of the tasks that consume much of their time and effort every day," says Tony Gauda, founder and… [Continue Reading] -

Cyber risks are being created by departments outside IT
Publié: octobre 3, 2017, 1:24pm CEST par Ian Barker
More risks are being created by departments outside of IT, but it's still the IT department's problem according to a new survey. The study by identity platform SailPoint shows that 55 percent of respondents believe one of the key reasons that non-IT departments introduce the most risk is that they often lack the understanding of what actions and behaviors are potentially hazardous. Using insecure mobile devices and adopting unmonitored SaaS applications are two examples of such risky behavior. According to the survey, seventy percent of organizations have embraced BYOD and SaaS application adoption, while less than half have formal policies in place… [Continue Reading] -

66 percent of SMBs could go out of business following a breach
Publié: octobre 2, 2017, 4:07pm CEST par Ian Barker
Today's threat landscape is becoming increasingly more complex and sophisticated, And all sizes of business are at risk. VIPRE Security has released the results of a survey of 250 SMB IT managers which shows that 66 percent say they would either go out of business or shut down for a day or more if their systems and/or data were compromised. In addition almost a quarter of respondents (23 percent) reported that they experience cyberattacks daily. 68 percent of SMB IT managers say they are tasked with generating security reports, yet 47 percent have to manually collect data from various sources… [Continue Reading] -

Compuware brings mainframe development to the cloud
Publié: octobre 2, 2017, 3:57pm CEST par Ian Barker
Many larger enterprises still rely on older, legacy systems developed in COBOL that don’t lend themselves to the latest Agile and DevOps development techniques. Mainframe development specialist Compuware is deploying its Topaz flagship solution for mainframe Agile/DevOps on Amazon Web Services (AWS). This gives cloud access to modern mainframe development, enabling enterprises to deploy agile tools for COBOL and other legacy code bases fast. Using Topaz on AWS, which uses Amazon AppStream 2.0 technology, enterprises can provide their global development, test and ops teams with immediate and secure cloud access to Compuware’s entire mainframe Agile/DevOps solution stack. AppStream 2.0 offers… [Continue Reading] -

Strategies for dramatically cutting public cloud costs [Q&A]
Publié: septembre 29, 2017, 5:24pm CEST par Ian Barker
IT teams are increasingly moving to the public cloud for its supposed low cost and high agility. However, once implemented in their environments, people are finding public cloud to be expensive and fairly complex to manage. We spoke to Andrew Hillier, CTO of cloud optimization analytics service provider Densify, who is all too familiar with the struggles that IT organizations face as their public cloud costs rise through the roof. Read on for his insights into strategies that organizations can implement when looking to reduce cost, risk and complexity in the public cloud. BN: Many organizations today are finding issues… [Continue Reading] -

Failed updates leave Mac computers at risk from targeted attacks on firmware
Publié: septembre 29, 2017, 3:11pm CEST par Ian Barker
The Extensible Firmware Interface (EFI) has steadily replaced BIOS in recent years as means of booting and controlling hardware devices. Mac systems have used EFI since 2006 but an analysis by Duo Labs, the research arm of Duo Security, of more than 73,000 Mac systems finds that in many cases the EFI is not receiving security updates, leaving users vulnerable to attacks. In 2015 Apple began to bundle software and firmware updates in order to ensure systems had the most current firmware security. Duo Labs' analysis looked at the updates released in the last three years and compared the actual… [Continue Reading] -

Edifier e235 Luna E -- solid sound meets deep-sea vibe [Review]
Publié: septembre 29, 2017, 1:14pm CEST par Ian Barker
For people who have invested in a large screen TV with a view to enjoying a home cinema experience, one of the most common complaints is the quality of the built-in speakers. The latest flat-screen TVs lack the big wooden cabinets of old for sound to resonate around in and so the audio quality from their on-board speakers tends to be a bit weedy. Most therefore look to add a soundbar or external speaker system to improve the experience. Edifier is a company that always seems to manage to produce interestingly styled speakers at the same time as delivering decent sound… [Continue Reading] -

Inadequate processes for managing accounts and access create major security risks
Publié: septembre 28, 2017, 4:27pm CEST par Ian Barker
Poor management of user accounts is leaving organizations open to security and compliance risks according to a new report. Identity and access management specialist One Identity surveyed over 900 IT security professionals, in conjunction with Dimensional Research, and finds that what should be security best practices -- such as swift removal of access to corporate data and applications, dormant account identification, and role administration -- continue to be a challenge for many enterprises. A lack of confidence that all former employees (and employees changing roles) are fully deprovisioned -- or have their accounts changed or removed -- in a timely enough manner… [Continue Reading] -

Attackers impersonate bank emails to cash in on post-Equifax fears
Publié: septembre 28, 2017, 3:52pm CEST par Ian Barker
In the wake of the recent breach at credit agency Equifax it's only natural that people are keeping a close eye on their bank statements and credit reports. Of course the bad guys know this too and a new report by Barracuda Networks looks at an email attack that is impersonating a 'secure message' from financial institutions. Emails appearing to come from legitimate organizations like Bank of America instruct the recipients to either download an attached document or reply back to the sender. The criminals behind the messages appear to be targeting mainly private banking clients as they are high… [Continue Reading] -

New DevOps toolkit automates database changes to remove bottlenecks
Publié: septembre 28, 2017, 2:51pm CEST par Ian Barker
DevOps is a popular choice with companies looking to streamline software delivery, but it often encounters a road block when changes to databases are needed. In businesses databases are often historically developed and need to be managed differently due to their complexity and their sometimes sensitive nature. Systems management and security company Quest Software is launching a new toolkit to help organizations automate database changes within their existing DevOps processes. Toad DevOps Toolkit integrates database changes with and the Continuous Integration and Continuous Delivery aspects of DevOps processes. It allows the functionality of code to be tested during the build… [Continue Reading] -

IT maturity improves in small and medium sized businesses
Publié: septembre 28, 2017, 1:00pm CEST par Ian Barker
A new study by IT management specialist Kaseya looks at IT department practices and for the second year in a row finds a growing level of maturity in SMBs and mid-market companies. Kaseya uses an IT Management Maturity Model that divides companies into five levels, from the lowest 'Reactive' through 'Efficient', 'Proactive' and 'Aligned' up to the highest 'Strategic'. While 83 percent of respondents classify their IT organization as being at one of the first three, less mature levels on the model; Reactive, Efficient, or Proactive, at the other end of the scale, when compared a survey in 2016, the… [Continue Reading] -

BullGuard rolls out its next generation anti-malware engine
Publié: septembre 27, 2017, 5:38pm CEST par Ian Barker
The cyber security market doesn't stand still for long and there's a constant arms race between the good and bad guys. Security company BullGuard is doing its bit to keep up by launching its next-generation anti-malware engine that's capable of detecting the latest zero-day threats. It will be rolled out across a range of BullGuard endpoint protection products. The engine is underpinned by cloud-based machine learning systems that will ensure products using it can continuously learn from and improve their cyber attack detection and remediation capabilities. At the same time the company is also introducing a real-time Home Network Scanner into… [Continue Reading] -

Phishing attacks reduce but more companies are targeted
Publié: septembre 27, 2017, 4:08pm CEST par Ian Barker
Threat detection company RiskIQ has released the latest of its quarterly reports into threat trends, this one looking at phishing. It finds that in the second quarter of 2017 there were 39,320 unique phishing domains, down from 45,025 back in the first quarter. However, there were 316 targeted phishing brands in Q2 -- up 15.7 percent from the 273 brands targeted in Q1. "Threat actors are always innovating, creating new methods to lure victims into gaining access to their financial information, PII, and user accounts," says RiskIQ's Andrew Geiger writing on the company’s blog. "Any angle they can play to… [Continue Reading] -

New platform adds self-managing storage to Azure and AWS
Publié: septembre 27, 2017, 2:47pm CEST par Ian Barker
It's important for enterprises to correctly size their public clouds in order to control costs and optimize performance. Cloud management company Turbonomic is using this week's Microsoft Ignite conference to announce a new version of its platform that delivers dynamic optimization and allocation of storage and relational database services. Turbonomic 6.0 expands an organizations' ability to automatically make the right tradeoffs between cost and performance while maintaining compliance. In addition it delivers further cost and performance benefits with the new ability to make the best use of pre-paid capacity and provide visibility for spot instances as well as enabling suspension… [Continue Reading] -

Security Serious Week aims to help UK businesses tackle the skills gap
Publié: septembre 27, 2017, 12:59pm CEST par Ian Barker
As part of the European Cyber Security Awareness Month, the first week of October in the UK marks Security Serious Week. This not-for-profit event set up by Eskenzi PR will present five panel-style webinars for participants from UK businesses on the theme of Bridging the Cyber Skills Gap through Diversity and Creativity. The week is supported by industry experts who are offering their time, wisdom and free advice to help UK companies protect as well as educate themselves. The events will cover topics including how companies can take advantage of UK schemes and programs to make the country a thriving… [Continue Reading] -

DDoS attacks continue to target IoT networks
Publié: septembre 26, 2017, 4:49pm CEST par Ian Barker
The second quarter of this year has seen DDoS attacks continue to target IoT networks according to attack protection specialist Nexusguard. Nexusguard gathers DDoS attack data through botnet scanning, honeypots, ISPs and traffic moving between attackers and their targets, so the data is unbiased by any single set of customers or industries. It finds that UDP-based (user datagram protocol) attacks increased by 15 percent in the second quarter, targeting hijacked devices connected to the Internet of Things, and overtaking SYN, HTTP Flood and other popular volumetric attacks in popularity. A new botnet, Persirai, attacked more than 1,000 different models of IP… [Continue Reading] -

Organizations unprepared for the ransomware onslaught
Publié: septembre 26, 2017, 4:07pm CEST par Ian Barker
A new study shows that companies and government agencies are being overwhelmed by frequent, severe ransomware attacks that have become the number one threat organizations face. The 2017 Ransomware Report from Crowd Research Partners, commissioned by Cybersecurity Insiders is based on the responses of over 2,200 cybersecurity professionals. "In many respects, ransomware is a game changer. It is incredibly easy and inexpensive for cyber criminals to execute highly profitable attacks on a global scale," says Holger Schulze, CEO and founder of Cybersecurity Insiders. "Many organizations are alarmingly unprepared for the ransomware onslaught. We predict the ransomware problem will get significantly… [Continue Reading] -

Comodo launches IoT security platform
Publié: septembre 26, 2017, 2:57pm CEST par Ian Barker
We all know we need to protect our computer systems when they're connected to the internet, but there’s generally less awareness of the threat posed by the latest generation of Internet of Things devices. Cyber security company Comodo wants to make these devices more secure with the launch of a new IoT Security Platform that will allow device manufacturers and network providers to issue and manage PKI and SSL certificates for private ecosystems. "Too many devices are coming to market with weak or no security pre-installed," says Damon Kachur, head of IoT solutions at Comodo. "Comodo's platform will help to… [Continue Reading] -

Microsoft mixes AI and cloud to drive business transformation
Publié: septembre 25, 2017, 4:20pm CEST par Ian Barker
Microsoft is using its annual Ignite event this week to show how technology can be used to help customers innovate and transform their business processes. Announcements have covered Office 365, Windows 10, Microsoft Azure, Dynamics 365 and Microsoft AI as well as a look at how quantum computing may help solve some major challenges. "Digital technology is impacting all aspects of our society and economies, creating unprecedented opportunity for organizations of all sizes," says Satya Nadella, CEO of Microsoft. "I'm optimistic and inspired by the ingenuity of customers, partners and developers everywhere that are pushing the frontiers of what’s possible… [Continue Reading] -

Maintaining Windows 10 tops list of enterprise security challenges
Publié: septembre 25, 2017, 3:05pm CEST par Ian Barker
Keeping Windows up to date with the latest fixes is a major challenge for enterprise IT teams and can leave endpoints vulnerable, according to a new report. The study from systems management company Adaptiva reveals that 59 percent of companies take up to a month or longer to complete Windows OS updates. In addition, 48 percent of respondents say that third-party patching is also difficult to accomplish company-wide. 32 percent of respondents identify keeping up with 'the pace of policy changes to defend against newly discovered vulnerabilities or cyberattack methods' as the most difficult ongoing challenge that IT teams address.… [Continue Reading] -

Americans see criminal hacking as the top threat to their health, safety and prosperity
Publié: septembre 22, 2017, 5:04pm CEST par Ian Barker
Hacking outranks other threats including climate change, nuclear power, hazardous waste, and government surveillance in Americans' perceptions according to a new survey. The study by cyber security company ESET asked randomly selected adults to rate their risk perception of 15 different hazards. Six of the hazards were cyber-related while the rest were other forms of technology hazard. The results show that criminal hacking is rated the top risk, just ahead of air pollution. Another cyber-related risk, the theft or exposure of private data, is rated fourth, after hazardous waste disposal. Government data monitoring ranks only eighth. "To be honest, I… [Continue Reading] -

New version of GitLab adds extra features for developers
Publié: septembre 22, 2017, 3:15pm CEST par Ian Barker
Popular open source development platform GitLab is launching its latest release aimed at helping developers reap the full benefits of DevOps, in particular continuous integration (CI) and deployment (CD), and Kubernetes based application development. GitLab 10.0 has been put together with input from enterprise customers as well as a worldwide community of over 1,800 developers. It reduces the amount of time developers must spend on tooling, freeing them to focus on software development. The addition of Auto DevOps brings best practices to projects by automatically configuring software development lifecycles by default, providing out-of-the box templates to automatically enable and configure… [Continue Reading] -

Cloud migration is more difficult than cloud adoption
Publié: septembre 21, 2017, 6:00pm CEST par Ian Barker
Adopting the cloud is one thing, but migrating to it is a much harder task according to a new report. The study by cloud company Virtustream and research firm Forrester reveals that moving to the cloud is often an application-by-application process, and only 32 percent of those surveyed rely on a single cloud vendor for migration, signaling a preference for multi-cloud. Despite the difficulties, migration of apps to the cloud continues to grow. On average, organizations engaged in active cloud projects today have migrated 44 percent of their apps, and by 2019, this figure is expected to reach 62 percent.… [Continue Reading] -

Cyber Monday is the new Black Friday
Publié: septembre 21, 2017, 3:42pm CEST par Ian Barker
New research shows that as we move towards the holiday season, shoppers are more excited about the prospect of Cyber Monday than that of Black Friday. A study by retail analytics company Euclid finds that Cyber Monday leads the way in consumer excitement (72 percent) followed by Black Friday and the day after Christmas (62 percent and 55 percent, respectively). The findings also show that eCommerce continues to build momentum, but also that physical stores maintain a key role in the buying process. In fact, 75 percent of consumers aged 18 to 34 visit a store on a regular basis… [Continue Reading] -

New tool offers developers cross-platform cloud access
Publié: septembre 21, 2017, 2:59pm CEST par Ian Barker
As businesses turn to the cloud they often find themselves adopting multiple different platforms to solve specific problems. This creates a problem for developers who need to deal with multiple tools and systems. Developer services start-up Manifold is aiming to ease this issue with the launch of a new cross-platform tool. The Manifold system allows developers to easily find, buy, and manage their favorite services -- from email to logging -- without being locked into a single cloud platform. Using Manifold, developers are no longer restricted by the confines of any particular cloud, allowing them to create stacks tailored specifically for their project… [Continue Reading] -

New security platform uses live attacks to evaluate risk
Publié: septembre 20, 2017, 4:56pm CEST par Ian Barker
One of the hardest things for security teams to do is accurately evaluate the level of risk that their organization is facing. Cyber security firm Nehemiah Security is launching the latest version of its AtomicEye RQ (Risk Quantifier) platform that can calculate a system's exploitability and generate comprehensive risk reports. It works by deploying live attacks on a simulation of a real network. It's thus able to assess a network's resiliency to being attacked by any combination of hundreds of thousands of exploits, and provide actionable intelligence that prioritizes what actions to take to make it more secure. "When designing… [Continue Reading] -

New enterprise password management tool eases administrator workload
Publié: septembre 20, 2017, 3:56pm CEST par Ian Barker
Effective password management is essential in helping to control data breaches, but employees often use the same passwords for both work and personal use, leaving corporate data potentially exposed. Password management company Dashlane is launching its new Dashlane Business 2.0 enterprise password solution. "CEOs, senior IT executives, and their Boards realize they do not have the ability nor the desire to oversee 100 percent of all cloud applications used by employees," says Dashlane CEO Emmanuel Schalit. "Dashlane Business is a quick, reliable way to educate and on-board non-technical users, while leveling up security and improving password practices across their entire… [Continue Reading] -

Office workers fall victim to phishing attacks despite training
Publié: septembre 20, 2017, 3:18pm CEST par Ian Barker
Despite training and other efforts to combat the problem, phishing is still proving a remarkably effective tactic for cyber criminals according to a new report. The study by cloud business applications company Intermedia shows that while 70 percent of office workers say that their organization regularly communicates with employees about cyber threats as a means of prevention, there are significant gaps between confidence and effectiveness. The problem isn't restricted to entry level staff either. Owners/executives (34 percent) and even IT workers (25 percent) report being victims of a phishing email more often than any other group of office workers. "Today's… [Continue Reading] -

DigitalOcean launches developer-friendly object storage
Publié: septembre 20, 2017, 1:08pm CEST par Ian Barker
Businesses are dealing with larger quantities of data than ever before, and this means an increase in the scale and complexity of storage required. Developer cloud company DigitalOcean is launching a new storage product called Spaces which provides a scalable and cost-effective way to address complex storage needs within a developer-friendly and easy-to-use UI. Developed in response to requests from DigitalOcean's developer community, Spaces is suited to hosting web assets, acting as the origin for CDNs, storing user-generated content such as images and large media files, archiving backups in the cloud and storing logs. Developers can easily manage all of… [Continue Reading] -

Twitter proves better than the Dark Web for assessing vulnerability risk
Publié: septembre 19, 2017, 5:53pm CEST par Ian Barker
The latest report from risk management and cyber security company Nopsec looks at the use of social media in risk analysis. Twitter in particular seems to be becoming the go-to resource for security researchers and attackers looking to disseminate proof-of-concept exploits. While some vulnerabilities have thousands of Twitter interactions -- counted by tweets mentioning their CVE identifier -- most vulnerabilities are never tweeted about or are tweeted only once. The most tweeted CVEs reflect interactions focused on well-publicized, dangerous vulnerabilities. Trying to locate similar risk indicators on the Dark Web yields mixed results, partly because it only shows what is visible from… [Continue Reading] -

Open source tool aims to deliver more efficient web development
Publié: septembre 19, 2017, 4:02pm CEST par Ian Barker
Websites are essential for businesses in the modern world, which puts web development teams under pressure to deliver results. Open source tool specialist DRUD Tech is launching a new tool called ddev which is designed to do away with the complicated steps and disparate components of website development. Using a simple interface, ddev manages many complex technologies, including industry standard components like MySQL, NGINX, and PHP, with the ability to extend to include Redis, Apache Solr, memcache, Varnish, and more. For experienced development teams this means ddev can eliminate unnecessary delays, errors, and inefficiencies common throughout the traditional development to… [Continue Reading] -

'App mapping' gives enterprises improved visibility into systems
Publié: septembre 19, 2017, 3:10pm CEST par Ian Barker
The shift to containers and as-a-service delivery models introduces blind spots for many enterprises as they struggle to see the whole picture and can't determine the health of their apps and APIs. Netsil, a new startup, is launching an innovative solution to this problem in the form of its Application Operations Center (AOC), a universal observation and monitoring platform for modern cloud applications. It uses an 'app mapping' technique to allow DevOps teams to gain complete visibility into all their services and their dependencies, with no code changes required. It automatically discovers every Docker container, Kubernetes pod, host and service endpoint,… [Continue Reading] -

Mobile network flaws could open Bitcoin wallets to hackers
Publié: septembre 18, 2017, 5:31pm CEST par Ian Barker
An architecture flaw in mobile networks could allow hackers to intercept SMS one-time passwords and access Bitcoin wallets. The vulnerability uncovered by enterprise security specialist Positive Technologies means that with just a person's first name, last name, and phone number, researchers were able learn the email address linked to the wallet, obtain control over it, and gain access to the wallet itself including withdrawing funds. The attack is made possible due to a flaw in the Signaling System No 7 (SS7) protocol used by most of the world's telephone networks. SS7 was developed in 1975 and has made the news… [Continue Reading] -

Majority of enterprise cloud services still not ready for GDPR
Publié: septembre 18, 2017, 2:48pm CEST par Ian Barker
With the EU's General Data Protection Regulation set to come into force in May next year, companies are rushing to ensure that their systems will comply with its rules. Yet a new report from cloud security company Netskope finds that almost three-quarters of cloud services still lack key capabilities needed to ensure compliance with the GDPR regulations. The study finds that the average enterprise has deployed 1,022 cloud services, down slightly from last quarter's average of 1,053. Of those cloud services in use, only 24.6 percent received a GDPR-readiness rating of 'high', based on attributes like the location where data… [Continue Reading] -

First half of 2017 sees more mobile vulnerabilities than for the whole of 2016
Publié: septembre 18, 2017, 12:27pm CEST par Ian Barker
A new report into mobile threats reveals that in the first half of 2017, there were more common vulnerabilities and exposures (CVEs) registered for Android and iOS than in all of 2016. The study by mobile threat defense company Zimperium, based on data from its z3a app analysis tool, also shows that many devices aren't running the latest operating systems, leaving them vulnerable. It finds that 94 percent of Android devices are not running the latest software version available, compared to 23 percent of iOS devices. The most concerning risks associated with iOS devices were malicious configuration profiles and 'leaky… [Continue Reading] -

Hurricanes lead to drop in malware infections
Publié: septembre 15, 2017, 3:02pm CEST par Ian Barker
An interesting side effect of the recent hurricanes Harvey and Irma is that malware infections in the Florida and Texas areas have seen a dramatic fall. Data released by Enigma Software Group, makers of the SpyHunter anti-malware software, shows that infections in the Houston area showed a 52.5 percent drop from the average on August 29th. In the week before Harvey hit infections dropped 26.2 percent from the average number of infections. In Miami infections began dropping from their usual levels starting on September 6th, as Irma was declared a Category 5 hurricane near Puerto Rico. Infections on the 6th… [Continue Reading] -

Intelligent data platform drives digital transformation
Publié: septembre 14, 2017, 5:21pm CEST par Ian Barker
Businesses are more keen than ever to unlock the power of their data, but often struggle to come up with a strategic approach. Cloud data management company Informatica is launching its latest Intelligent Data Platform driven by the CLAIRE engine which uses metadata-driven AI to deliver faster insights. "Successful digital transformations are data-driven and require a strategic approach to data management that catalogs and governs all data that matters, secures data that needs protection, ensures the quality of trusted data, scales for big data workloads and real-time processing across hybrid architectures, and brings it together for an actionable 360-degree view… [Continue Reading] -

Criminals hijack browsers to mine cryptocurrency
Publié: septembre 14, 2017, 4:33pm CEST par Ian Barker
Cyber criminals supplementing their income by mining cryptocurrencies like Bitcoin is nothing new. Usually this has been done by installing malware or PUPs on the machines of unsuspecting users. But now researchers at ESET have discovered a new method of mining cryptocurrencies, which can be done directly within your web browser, using JavaScript. This gives attackers the potential to reach a greater number of victims, by infecting websites, rather than by targeting individual machines. Knowing that the default settings of most browsers include activated JavaScript, attackers simply need to insert the mining script in websites that receive large amounts of… [Continue Reading] -

User feedback solution helps companies build brand loyalty
Publié: septembre 14, 2017, 3:15pm CEST par Ian Barker
Companies want people to use their apps, but it can be hard to obtain feedback on what is and isn't working, and understand what customers want. Digital experience company Applause is launching its Customer Journeys solution which delivers authentic user feedback from a range of sources including apps, marketing materials, websites, in-store, IoT devices and more. It can be used to understand what customers like or dislike about products at any stage of the software development lifecycle from prototype to production. Results can be viewed through a real-time dashboard. Customer Journeys includes Applause Platform, a software-as-a-service offering that provides an… [Continue Reading] -

Mobile apps still the 'Wild West' of online security
Publié: septembre 14, 2017, 12:17pm CEST par Ian Barker
Most app stores are still failing to adequately protect their users from malicious and fraudulent app downloads. This is one of the findings of a new report by threat management company RiskIQ which analyzed 120 mobile app stores and more than 2 billion daily scanned resources. The major marketplaces are still a source of blacklisted apps, with Google Play jumping to the #2 source for blacklisted apps in the second quarter of this year. But it's a secondary store, AndroidAPKDescargar, that holds the #1 spot for the second-straight quarter. A bright spot though is that blacklisted app downloads fell by… [Continue Reading] -

McAfee launches new range of consumer security products
Publié: septembre 13, 2017, 4:53pm CEST par Ian Barker
With internet threats showing no signs of slowing down, it's vital to keep all of your devices protected and this applies in the home as much as the workplace. With the launch today of its latest consumer products, McAfee is aiming to protect against threats as well as offering online privacy and safety for the whole family. McAfee's core security suite includes McAfee AntiVirus Plus, McAfee Internet Security, McAfee Total Protection and McAfee LiveSafe. The company says it now delivers even more efficient and effective protection from digital threats as the engine's cloud-based behavioral analytics and machine learning capabilities expand.… [Continue Reading] -

IT professionals are an underused resource for cyber security
Publié: septembre 13, 2017, 4:07pm CEST par Ian Barker
It's widely accepted that there is a shortage of people with cyber security skills, yet a new study shows that companies are failing to give IT professionals -- the people implementing and operating security strategies for most organizations -- the training and responsibility they need to take on a more proactive cyber security role. The study, from security training company (ISC)2 also reveals that many IT professionals feel their security guidance is being ignored by business leadership. More than 3,300 IT professionals participated in the survey and the findings show that almost half of IT organizations don't provide adequate resources for IT… [Continue Reading] -

New data platform accelerates application development and deployment
Publié: septembre 13, 2017, 3:15pm CEST par Ian Barker
One of the things that can hold back development of business applications the reliance on extract, transform, and load (ETL) infrastructures to move data between applications and platforms. Platform specialist InterSystems is launching a new platform built around a high-performance database that eliminates the need for ETL. InterSystems IRIS provides all of the critical capabilities for rapidly developing data-intensive and mission-critical applications, including advanced data management, interoperability, transaction processing, and analytics. "We created InterSystems IRIS Data Platform with solution creators in mind with all of the critical capabilities for building applications that face the future," says Paul Grabscheid, vice president… [Continue Reading] -

Bill Gates says Britain can be a world technology leader after Brexit, but CBI demands certainty on data
Publié: septembre 13, 2017, 11:48am CEST par Ian Barker
Before the UK's referendum on leaving the EU last year, Bill Gates warned that a vote to leave could jeopardize the country’s position in the science and technology sector. But in an interview with the Daily Telegraph (paywalled) the Microsoft founder says that Britain can remain a world leader if care is taken. Gates has invested £750 million in UK research institutions including universities in Liverpool, Edinburgh, London, Cambridge, and Oxford, "because they're the best at doing lots of this important work." However, Gates warns that there will be some challenges to overcome to ensure that the UK retains its… [Continue Reading] -

Free analytics tool lets developers troubleshoot app performance
Publié: septembre 12, 2017, 4:25pm CEST par Ian Barker
Businesses are increasingly keen to take advantage of mobile apps, but consumers are quick to drop apps that fail to perform as expected. The problem is that once an app is released it's difficult for developers to get feedback on how it's working in the real world. App acceleration company PacketZoom is addressing this with the launch of a free analytics tool that enables app developers to analyze, troubleshoot and control app performance in real-time. Called Mobile IQ, it offers developers real-time alerts on app throughput, transfer time and error rates, detects issues such as slow response times and disconnects,… [Continue Reading] -

Container use in the cloud continues to grow
Publié: septembre 12, 2017, 3:21pm CEST par Ian Barker
A new report reveals the continuing popularity of container systems in the cloud, with AWS Docker adoption up by six percentage points over last year and AWS Lambda almost doubling. The 'State of Modern Applications in the Cloud' report from analytics platform Sumo Logic shows that businesses of all sizes are transforming at an unprecedented pace in order to compete in the digital era. However, they are often being hampered by legacy technologies and inefficient siloed processes and tools that are ill-equipped to handle today's volume of data. Among other findings are that Linux is now the dominant operating system in… [Continue Reading] -

UK companies look overseas to bridge the IT skills gap
Publié: septembre 11, 2017, 3:57pm CEST par Ian Barker
With digital transformation projects currently flavor of the month, businesses are facing increasing difficulties in finding the talent needed to carry them out. A new study of UK IT leaders by cloud and networking company Interoute finds 96 percent believe that the cost of professionals with expertise in digital transformation is higher than for other IT initiatives, and nearly half (48 percent) see the skills shortage as a problem. Many are using contractors with 87 percent reliant on them to support projects on an interim basis. What's interesting though is that many of these skills come from overseas. On average,… [Continue Reading] -

Carbon Black launches streaming protection against ransomware
Publié: septembre 11, 2017, 3:16pm CEST par Ian Barker
Ransomware remains one of the most serious threats to organizations of all sizes, but traditional signature-based detection methods can struggle to identify the latest attacks. Endpoint security company Carbon Black is launching its latest Cb Defense next-generation anit virus (NGAV) solution using 'Streaming Ransomware Protection' designed to detect and prevent attacks, even if the ransomware employs fileless techniques or unknown tactics. The software makes use of event-stream processing, which is the same technology that has revolutionized algorithmic day-trading, to continuously update risk profiles based on a stream of computer activity. When multiple, potentially malicious events occur in a cluster, Cb… [Continue Reading] -

Poor security design and how not to handle a cyber attack -- lessons from Equifax
Publié: septembre 8, 2017, 4:36pm CEST par Ian Barker
The data breach at credit agency Equifax looks to be one of the biggest in recent times. Industry experts have been quick to criticise both the company's security and its response to the breach. Once again we've seen a breach exploiting a web app vulnerability that has managed to go undetected for several months. There has also been criticism of Equifax executives actions in selling $1 million worth of stock before going public about the breach. "This breach is totally inexcusable," says Mike Shultz, CEO of Cybernance, a cyber governance company. "This wasn't a technical assault -- this was a… [Continue Reading] -

US schools are uniquely vulnerable to cyber attacks
Publié: septembre 8, 2017, 3:50pm CEST par Ian Barker
A new study by application delivery and security company Radware reveals that US schools are uniquely vulnerable to the threat of cyber attacks. The study of 1,000 US consumers shows that 15 percent of respondents think a 1-6 grade student easily disrupt school or university operations through a cyber attack, while 57 percent believe the same is true for high school students. Despite this pessimism, however, 76 percent of respondents say they are not aware of any schools or universities being affected by a cyber attack. Part of the problem is that schools' security budgets are 50 percent lower than those… [Continue Reading] -

IBM offers free cyber security training to military veterans
Publié: septembre 8, 2017, 11:55am CEST par Ian Barker
We've seen quite a bit recently about the difficulties of recruiting cyber security personnel, and how the skills needed for the role have changed. In a new initiative, IBM in the UK is teaming up with ex-forces employment specialist SaluteMyJob and non-profit education body the Corsham Institute to offer a free cyber security training course for military veterans. The certification in IBM security and analytics solutions teaches cyber security software skills to former and transitioning military personnel, and 100 veterans are expected to complete the course by 8th September. Designed to facilitate employment into cyber security roles, this IBM Corporate… [Continue Reading] -

SentinelOne's new Deep Visibility capability enhances endpoint protection
Publié: septembre 7, 2017, 4:55pm CEST par Ian Barker
When looking to protect their systems from attack most companies focus on the protection of endpoints, but it can prove hard for admins to gain visibility into individual systems. Endpoint protection specialist SentinelOne is launching a new Deep Visibility module for its SentinelOne Endpoint Protection Platform, aimed at providing better visibility at all levels. Deep Visibility extends the company's current endpoint suite abilities to provide full visibility into endpoint data. It uses kernel-based monitoring for complete, autonomous, and in-depth search capabilities across all endpoints -- even those that go offline. This enables customers to fully automate their detection to response… [Continue Reading] -

50 percent of employees believe their businesses aren't ready for GDPR
Publié: septembre 7, 2017, 3:33pm CEST par Ian Barker
With the EU's GDPR legislation less than a year away from coming into force, a new study reveals that half of employees believe their companies aren't ready for it. The survey, carried out by Usurv for Storage Made Easy asked 200 employees a simple question on whether they believe their company is ready for the upcoming data protection law. "The General Data Protection Regulations are the most stringent update of data privacy and protection regulations for many years," says Jim Liddle, Storage Made Easy CEO. "They affect all businesses whether large or small and potentially could have the effect of putting… [Continue Reading] -

Skills required for a cyber security career have changed
Publié: septembre 7, 2017, 12:59pm CEST par Ian Barker
As we saw earlier this week, the cyber security industry is looking for new blood in order to solve the skills crisis. Another study this week by security and compliance firm Tripwire underlines this, with 81 percent of existing security professionals believing that the skills required for the job have changed in the past few years. This shows in the fact that 20 percent of respondents say that their organizations have hired people with expertise not specific to security over the past two years, and another 17 percent say they plan to do the same in the next two years.… [Continue Reading] -

Why your business is a target for hackers
Publié: septembre 7, 2017, 11:44am CEST par Ian Barker
Although cyber attacks regularly make the headlines, it's easy to fall into the trap of thinking that it can’t happen to your business. You might think that you’re well protected or that you’re too small to worry about. A new infographic from communications and cloud company CBTS reveals why everyone is potentially at risk. It looks at the risks of malicious mail and weak passwords, as well as the top threats including spear phishing and ransomware. It also points out that 43 percent of data losses are due to internal incidents. Far from being immune, smaller companies suffer more attacks,… [Continue Reading] -

Emerging threats encourage cooperation among security professionals
Publié: septembre 6, 2017, 5:27pm CEST par Ian Barker
According to a new survey of attendees to this year’s Black Hat USA conference, concerns around emerging threats like ransomware and polymorphic malware have sparked a significant increase in collaboration by the cybersecurity industry. The study by security management specialist AlienVault spoke to over 600 participants at the conference and found that for 43 percent, ransomware is their biggest security concern. The second largest group, 31 percent, is most worried about polymorphic malware, which is able to adapt its appearance to avoid detection. In terms of ransomware, the biggest fear for most participants (38 percent) is being unable to prevent… [Continue Reading] -

Avast launches new security solution for SMBs and MSPs
Publié: septembre 6, 2017, 3:00pm CEST par Ian Barker
Following Avast's acquisition of rival firm AVG last year the two companies' products have largely continued side by side. Today sees the launch of one of the first fruits of the union in the form of Avast Business, combining technology from AVG and Avast, and aimed at smaller businesses and managed service providers. Kevin Chapman, senior vice president and general manager of Avast's SMB business says, "Since last year, our focus has been on combining the best of both business product portfolios, partner programs, tools, and systems to eliminate the complexity around protecting businesses, while delivering the most powerful security… [Continue Reading] -

New technology platform helps secure business devices
Publié: septembre 6, 2017, 1:21pm CEST par Ian Barker
Thanks to increased use of mobile and BYOD devices, there's a significant risk to business networks from un-managed and uncontrolled devices which could offer a route for security breaches. Israeli startup company Axonius is looking to solve this problem with a new platform designed to eliminate blind spots on the network and provide a single place to understand, manage and control the security of all end user, compute and IoT devices. The company has raised $4 million in seed funding to develop the platform which standardizes the interface for devices and incorporates existing standalone tools and controls. This allows Axonius to… [Continue Reading] -

Ransomware is the top threat to business data
Publié: septembre 5, 2017, 2:50pm CEST par Ian Barker
New research from research organization the SANS Institute reveals that frontline IT professionals consider ransomware to be the top overall threat to data availability. Insider threats and denial of service are also considered top threats to sensitive data. While the majority of respondents indicate that they escaped actual compromise of sensitive data in the last year, enough respondents did lose data to provide valuable lessons from these events. Of the respondents, 78 percent report two or more threats occurring in the past 12 month, while 68 percent report the same threat occurring multiple times over that same period. User credentials… [Continue Reading] -

New blood needed to solve the cyber security skills crisis
Publié: septembre 5, 2017, 11:26am CEST par Ian Barker
Senior figures in IT security see enticing staff from non-IT backgrounds and encouraging young people into the industry as vital to addressing the cyber security skills shortage. A new study commissioned by MWR InfoSecurity and carried out by security discussion and networking group RANT shows respondents feel the core skills needed in cyber security are curiosity (46 percent) or on-the-job experience (34 percent), with no respondents saying a university IT degree is crucial. Experienced security professionals are in high demand which makes attracting such staff notoriously difficult and businesses need to look at ways to attract them. Company culture is… [Continue Reading] -

47 percent of UK teens have been cyber bullied
Publié: septembre 4, 2017, 12:43pm CEST par Ian Barker
According to a new study of 1,000 UK teenagers, 47 percent have been cyber bullied with 70 percent experiencing it on social media and Facebook being the most common platform. The survey by McAfee reveals part of the problem appears to be that teens are not getting proper guidance at home or at school about staying safe online. Teenagers are spending a lot of time online. Twenty-seven percent of British girls and 20 percent of boys say they spend over five hours a day online. Yet, just 31 percent of parents speak to their offspring about what they do on… [Continue Reading] -

30 percent of Americans would leak private data for $1,000
Publié: septembre 1, 2017, 3:00pm CEST par Ian Barker
As we carry out more of our day-to-day transactions online, so the amount of information about us that exists out on the internet grows. That means there are more and more opportunities for data to be leaked or stolen, but a new study by IT staffing company Modis reveals that people still aren't taking their privacy seriously. If $1,000 were on offer over 41 percent of respondents say they would leak personal photos, while nearly 39 percent are willing to part with their browser history. Most are more protective about their financial information though, with only 10.9 percent ready to… [Continue Reading] -

New blockchain platform helps cut online ad fraud
Publié: août 31, 2017, 4:17pm CEST par Ian Barker
While digital advertising is increasingly popular, it suffers from a lack of trust due to fraud and, despite predictive technology, has relatively low accuracy. As a result, a high percentage of spend gets wasted. Advertising ecosystem Papyrus, launching today, aims to bring together users, publishers, advertisers and developers of decentralized applications in a new way that permits them to interact in an environment with built-in fraud prevention and which offers an unprecedented level of control. It works using a "trustless" environment powered by blockchain technology. Using blockchain, participants rely on decentralized consensus and universal transparency and incentives for fair and… [Continue Reading] -

DMARC -- rebuilding trust in email [Q&A]
Publié: août 31, 2017, 2:01pm CEST par Ian Barker
Email has become the default means of communication for both businesses and individuals, but as we saw yesterday it isn't without its problems. A major issue email has is that of security, cyber criminals are getting better at creating phishing and other messages that accurately spoof commercial organizations. But there is a technology in the form of Domain-based Message Authentication, Reporting and Conformance (DMARC) which has the potential to restore faith in email communication. We spoke to Patrick Peterson, founder and executive chairman of email trust specialist Agari, to find out more. BN: How did DMARC come about? PP: For… [Continue Reading] -

New authentication methods help companies to ditch passwords
Publié: août 30, 2017, 5:34pm CEST par Ian Barker
Most people now recognize that passwords alone are flawed as a means of securing systems. The problem is that there are lots of options when it comes to finding a better way of doing things. Access control specialist SecureAuth is helping the move towards a passwordless world with the introduction of additional multi-factor authentication (MFA) methods, including Link-to-Accept via SMS or email, and YubiKey, the FIDO Universal Second-Factor (U2F) security key by Yubico. These methods mean users aren't required to have a phone or smartphone application in order to authenticate without passwords. This allows organizations to go passwordless without having to… [Continue Reading] -

How enterprises are using data to get work done
Publié: août 30, 2017, 4:51pm CEST par Ian Barker
A new study by content management and collaboration specialist Egnyte has analyzed 25 Petabytes of customer data and four billion of the activities they performed. This has been used to uncover unique insights about the way businesses are managing their data and how their employees are collaborating on it. Among the findings are that hybrid content has grown by 83 percent year-on-year, while 41 percent of content resides in on-premises storage. New types of content are affecting storage use too and this trend is likely to continue as video is expected to claim 80 percent of web traffic by 2019.… [Continue Reading] -

Sophisticated phishing attacks target Office 365
Publié: août 30, 2017, 4:17pm CEST par Ian Barker
With over 100 million monthly subscribers, it's not surprising that Office 365 is a popular target when it comes to attempting to steal credentials. A new report from Barracuda Networks looks at how phishers are sending out authentic-looking emails purporting to be from Microsoft asking users to reactivate their accounts. "Cybercriminals have a long history of designing attacks to reach the largest number of eyeballs possible," says Asaf Cidon VP of content security services, writing on the Barracuda blog. "From the early days of traditional spam, to search or trending topics on social platforms, criminals follow the users -- and… [Continue Reading] -

Happy 35th birthday email, you've changed our lives
Publié: août 30, 2017, 3:29pm CEST par Ian Barker
On August 30th 1982, Dr VA Shiva filed the first copyright for an email system. That means email turns 35 today, but though it's all grown up it's proved to be a bit of a problem child. A new survey released to coincide with the anniversary by Edison Software, makers of an AI mail app, finds that email has grabbed a dominant role in many of our lives and this shows no signs of abating. The study shows that 74 percent of Americans feel overwhelmed by the number and frequency of emails they receive. What's more, nearly half (44 percent)… [Continue Reading] -

Improving the measurement of cyber threats before they turn into attacks
Publié: août 30, 2017, 12:35pm CEST par Ian Barker
Cyber attacks are a major problem for companies and they can be made all the more devastating if a long time elapses before they're discovered. A new report by the Cloud Security Alliance looks at helping enterprises develop metrics and processes to measure threats before they become cyber attacks. The paper introduces two key metrics -- Elapsed Time to Identify Failure (ETIF) and Elapsed Time to Identify Threat (ETIT) -- and proposes that the responsibility for measuring and reporting each be transferred from companies whose systems encounter cyber attacks to those in the Intrusion Detection System (IDS) space. Researchers suggest that… [Continue Reading] -

New cloud solution allows multi-factor authentication across the enterprise
Publié: août 29, 2017, 5:01pm CEST par Ian Barker
Data breaches can often be traced back to weak or stolen credentials, add in a proliferation of systems in the cloud and increasing levels of mobile access, and protecting business systems becomes a major headache. Independent identity provider Okta is launching its latest cloud-based Okta Adaptive Multi-Factor Authentication (AMFA) that makes two-factor authentication standard for every user. Okta AMFA provides a comprehensive set of authentication factors and a robust policy framework that supports contextual access management and adaptive, risk-based authentication. Because it uses context, Okta AMFA gives the right users access only to the data and application permissions they need,… [Continue Reading] -

Intel's 8th-gen processors help deliver secure payments
Publié: août 29, 2017, 3:05pm CEST par Ian Barker
Earlier this month we saw Intel launch its new 8th-generation Core processors. As well as improved performance, these chips offer added security with Intel Software Guard Extensions (Intel SGX) technology. Thanks to a collaboration with authentication specialist Nok Nok Labs (NNL) the new chips with SGX are able to deliver standards-based authentication to enable stronger, simpler, and more secure payments for computer users. The NNL S3 Authentication Suite is certified by the Fast IDentity Online (FIDO) Alliance which was founded to solve the problems that users face creating, remembering and relying on multiple usernames and passwords. "Passwords are a problem.… [Continue Reading] -

Why are so many organizations struggling to patch? [Q&A]
Publié: août 25, 2017, 11:49am CEST par Ian Barker
Many recent cyber attacks like WannaCry have succeeded by exploiting vulnerabilities that, although known, have gone widely unpatched. Why do some organizations find it so difficult to keep their systems up to date and what can they do to better protect themselves? We spoke to Wendy Nather, principal security strategist at Duo Security to find out. BN: Despite the industry evangelizing the importance of updating software and patching, it's evident that it's not always happening -- why is this? WN: There are lots of reasons why organizations may be struggling to update software and patch systems. Many organizations simply don't… [Continue Reading] -

Government organizations lag behind in implementing latest security practices
Publié: août 24, 2017, 3:42pm CEST par Ian Barker
Cyber attacks are becoming more complex and intense. In addition, many hackers are interested in the types of sensitive data held by government bodies. Yet a new study shows that these organizations are lagging behind in dealing with IT risks. The study by data visibility platform Netwrix reveals that while 57 percent of government entities focus on endpoint protection, 72 percent experienced security incidents in 2016, the most common reasons being human errors and insider misuse. It's not surprising then that 100 percent of respondents from the government sector see employees as the biggest threat to security. In addition, 75… [Continue Reading] -

Non-Windows platforms increasingly at risk from malware
Publié: août 24, 2017, 1:17pm CEST par Ian Barker
Where it was once the case that damaging malware attacks were aimed solely at Windows devices, a new study shows that strategic attacks on both Mac and Android devices are rapidly rising. The report by Malwarebytes reveals that Android ransomware was up by more than 100 percent in the second quarter of 2017. In addition, Mac malware this year is already at the highest it has ever been. Both platforms are vulnerable to malicious applications, with many still making it past app store review processes, and both are continually plagued by potentially unwanted programs (PUPs). However, the tactics that attackers use… [Continue Reading] -

AI-powered analytics unlock commercial relationship data
Publié: août 23, 2017, 4:47pm CEST par Ian Barker
Details of the deals that a business has with other organizations are usually locked up in contracts or other documents such that valuable information is either not readily available or easily overlooked. California-based Pramata is launching a suite of analytic applications that can identify critical information in existing contracts and combine it with data from business systems such as CRM and billing to benefit commercial relationships. "Most software products give you tools and then ask you and your teams to do all the work populating the tools with your data," says Justin Schweisberger, Pramata's chief product officer. "Pramata is the… [Continue Reading] -

New portal helps developers integrate payment solutions
Publié: août 23, 2017, 3:30pm CEST par Ian Barker
One of the keys to monetizing apps is to have an effective and easy to use payments solution built in. Payment solutions company Qualpay is aiming to make this process easier by offering a portal to make the selection of systems easier. Qualpay for Developers allows developers looking for easy-to-implement payment APIs to use the portal to evaluate and deploy multiple payment solutions or work with Qualpay to tailor the platform for specific environments. Qualpay's payments platform accommodates a variety of solutions, from marketplaces, shopping carts, customer relationship management (CRM) systems, to invoicing and accounting solutions. Qualpay offers a personalized… [Continue Reading] -

Enterprises not confident security can keep up with digital transformation
Publié: août 23, 2017, 12:26pm CEST par Ian Barker
Businesses are increasingly turning to digital transformation to accelerate their online presence, to enrich products, deepen customer relationships, and boost their brand. But the bad guys have gone digital too, taking advantage of the digital ecosystem and user trust to make more sophisticated attacks. A new study sponsored by digital threat management company RiskIQ finds that for many businesses digital transformation and the changing external threat landscape are outpacing enterprise security capacity. The research conducted by IDG Connect finds that an average of 40 percent of organizations experienced five or more significant security incidents in the past 12 months. Among most… [Continue Reading] -

SaaS solution analyzes user credentials to help prevent data breaches
Publié: août 22, 2017, 5:41pm CEST par Ian Barker
Data breaches arising from misuse of credentials can often be made worse by users having excessive or inappropriate entitlements. A new solution from One Identity allows companies to analyze and compare user entitlements, and pinpoint situations where they deviate from the norm and thus pose an elevated risk. One Identity Starling Identity Analytics & Risk Intelligence (IARI), is an SaaS-based solution that ensures an individual's access rights are appropriate, used actively and present the lowest risk. It quickly identifies dormant or inappropriate entitlements, and fixes high-risk roles before they can be used in harmful ways. Using a pool of data source… [Continue Reading] -

New platform speeds up enterprise digital transformations
Publié: août 22, 2017, 4:55pm CEST par Ian Barker
While enterprises are keen to push forward with digital transformation projects, they're often held back by legacy applications and siloed data which are difficult to integrate. Business consultancy Janeiro Digital is aiming to overcome these problems and boost digital transformation with the launch of its latest XFORM platform. It's made up of two parts, XFORM Foundation and XFORM Bridge. XFORM Foundation includes all of the key components needed for modular development and to establish a clean, scalable, secure, and flexible enterprise application architecture. This is complemented by XFORM Bridge which is a lightweight API mediation layer to connect the different… [Continue Reading] -

New solution aims to cut mobile app fraud
Publié: août 22, 2017, 4:20pm CEST par Ian Barker
One of the ways developers can boost the popularity of their mobile apps is via pay-per-click advertising. But this leaves them open to fraud where bots can be used to generate large numbers of hits. Mobile advertising technology firm AppLift is launching a new Fraud Buster tool, which combats app install fraud in real time to ensure users are genuine and deliver increased return on advertising spending. "As fraudsters game mobile app installs to their benefit, the trust upon which the online advertising ecosystem is built erodes at an expedited rate," says Maor Sadra, CRO of AppLift. "The Fraud Buster arrests… [Continue Reading] -

IBM launches blockchain collaboration to improve food safety
Publié: août 22, 2017, 3:31pm CEST par Ian Barker
According to the Centers for Disease Control and Prevention, one in ten people in the US falls ill each year from contaminated food. The source of such problems can be hard to identify due to a lack of traceability. Blockchain is an ideal technology to help address these challenges because it establishes a trusted environment for all transactions and IBM is launching a collaboration with major industry players to strengthen consumer confidence in the global food system. The consortium includes Dole, Golden State Foods, Kroger, McCormick and Company, Nestlé, Tyson Foods and Walmart, all of whom will work with IBM… [Continue Reading] -

Verizon boosts software defined networking with Cloud IP Platform
Publié: août 22, 2017, 12:05pm CEST par Ian Barker
Businesses are moving more of their systems to the cloud and that includes infrastructure projects like networking and provision for branch offices. Telecoms provider Verizon is updating its software defined networking (SDN) platform with a new Software Defined Secure Branch (SD-Branch) managed service powered by Versa Networks' Cloud IP platform. The Versa solution will be integrated into Verizon's Virtual Network Services offering that allows customers to reduce complexity and control costs by virtualizing multiple components of a branch office. These include public and private network connectivity management, wireless connectivity, multi-site network support, application based quality of service and multi layered… [Continue Reading] -

How network segmentation can help contain cyber attacks
Publié: août 21, 2017, 1:07pm CEST par Ian Barker
Cyber crime continues to be a major problem globally and companies are seeking new ways of combating it. However, there are some older technologies that remain an effective defense. One of these is network segmentation, and network security specialist Tufin Technologies has produced an infographic explaining how segmentation works and how it can help keep organizations secure from today’s sophisticated cyber attacks.. It explains why organizations need the ability to visualize and enforce segmentation from a single console across multiple vendors and platforms. This level of visibility and control enables enterprises to maintain compliance with industry regulations, tighten the overall… [Continue Reading] -

Customer service is key to a good app experience
Publié: août 18, 2017, 3:43pm CEST par Ian Barker
A new survey reveals that 89 percent of Americans will recommend an app based soley on a customer service experience, but 47 percent will simply delete apps that are frustrating and don’t provide any customer support. The research from customer support company Helpshift surveyed over 2,000 18+ adults in the US and finds that 81 percent use mobile apps. Checking social media is the most popular activity, carried out by 66 percent, 44 percent read the news, 44 percent play games, 35 percent order food via apps, and 22 percent handle work-related tasks. However, there are findings that should give app… [Continue Reading] -

Ransomware attacks almost double in first half of 2017
Publié: août 17, 2017, 5:48pm CEST par Ian Barker
The percentage of ransomware attacks almost doubled in the first half of 2017 compared to the first half of 2016, from an average of 26 percent to an average of 48 percent of the main attack categories worldwide. This is according to a mid-year cyber attack trends report from threat prevention company Check Point. It also finds that 23.5 percent of organizations were impacted by the RoughTed malvertising campaign, and 19.7 percent of organizations were impacted by the Fireball malware over the same period. The report's authors also note that the leaking and consequent availability of key nation-state hacking tools,… [Continue Reading] -

Fastly adds the power of edge computing to Google BigQuery
Publié: août 17, 2017, 4:37pm CEST par Ian Barker
Companies continue to be keen to exploit the power of big data analytics, and one of the most popular platforms for doing this is Google's BigQuery. Edge cloud platform Fastly is announcing a new integration that allows the real-time streaming of logs to BigQuery. This, the first of a number of planned integrations with Google's Cloud Platform, aims to deliver better performance and faster real-time insights. Fastly provides private interconnects with Google at 14 strategic locations around the world. By connecting directly with Google's network backbone, bypassing the public internet, it can reduce the latency to GCP data. Compared to… [Continue Reading] -

90 percent of organizations will adopt VMware in the cloud by 2018
Publié: août 17, 2017, 3:41pm CEST par Ian Barker
A new study from cloud data management company Druva shows a strong trend among businesses towards moving virtual workloads to the cloud. It reveals that in the VMware market 90 percent of companies are aiming to migrate their workloads by 2018, with a clear preference for AWS (47 percent), followed by Microsoft Azure (25 percent). Disaster recovery is cited as a critical reason to move to the cloud by 82 percent of those surveyed. This reflects a changing of perceptions as professionals come to understand how the cloud reduces the possibility of costly downtime and promotes productivity. More than half of… [Continue Reading] -

72 percent of security pros say encryption backdoors won't stop terrorism
Publié: août 17, 2017, 3:02pm CEST par Ian Barker
A new survey of information security professionals carried out at last month's Black Hat conference suggests that the majority think encryption backdoors are ineffective and potentially dangerous. The study carried out by machine identity protection company Venafi finds that 72 percent of respondents don't believe encryption backdoors would make their nations safer from terrorists. This follows an earlier study from Venafi into consumer attitudes to encryption and government powers which showed that people have mixed feelings about the effect it would have on them personally. This new study shows that only 19 percent of professionals believe the technology industry is doing… [Continue Reading] -

On-premises workloads have more security incidents than those in the public cloud
Publié: août 16, 2017, 4:14pm CEST par Ian Barker
According to a new survey, workloads run on in-house systems suffer 51 percent more security incidents than those on public cloud services. The study from cloud security and compliance company Alert Logic analyzed more 2 million security incidents captured by its intrusion detection systems over 18 months. It finds customers running applications on public cloud platforms experienced an average 405 security incidents over the period while on-premises customers experienced 612. Hosted private cloud had a 69 percent higher incident rate (684) and hybrid cloud a worrying 141 percent higher (977). But while the public cloud is relatively safe, the results… [Continue Reading] -

Enterprises still struggle with password policies
Publié: août 16, 2017, 2:54pm CEST par Ian Barker
Passwords and their effectiveness is a subject that continues to come under the spotlight, particularly with the publication of a recent United States National Institute for Standards and Technology (NIST) document recommending a move to passphrases. Security awareness training specialist KnowBe4 has carried out a survey of 2,600 IT professionals to look at how organizations are managing passwords and determine how the proposed passphrase concept stacks up against methods currently in use. The findings reveal that 44 percent of respondents overall, (large organizations with 1,000+ employees and small to mid-size businesses), think a passphrase of around 25-characters could work, compared… [Continue Reading] -

Over a third of IoT medical device organizations suffer security incidents
Publié: août 15, 2017, 4:20pm CEST par Ian Barker
As the internet of things spreads into more and more areas, increasing numbers of medical devices are now connected, making them vulnerable to cyber attacks that could shut down medical processes, expose critical hospital and patient data, and ultimately put patient safety at risk. Many medical devices are not built with cybersecurity in mind, yet a survey by Deloitte Cyber Risk Services of over 370 professionals organizations operating in the medical device/IoT arena shows that 36.5 percent have suffered a cyber security incident in the past year. Indeed, 30.1 percent of respondents say identifying and mitigating the risks of fielded… [Continue Reading] -

Companies are losing ground against cyber threats
Publié: août 15, 2017, 3:20pm CEST par Ian Barker
Businesses are struggling to keep pace against the rising level of cyber security threats, according to a new study. The Threat Monitoring, Detection and Response Report from Crowd Research Partners -- produced in partnership with a number of leading cyber security vendors -- finds that the biggest concern is dealing with advanced threats in three key areas, ransomware (48 percent), phishing attacks (48 percent) and attendant data loss (47 percent). The level of concern with these threat categories has grown significantly over the past six months and 62 percent of respondents indicate that their most significant challenge is being able… [Continue Reading] -

Why hackers love privileged accounts
Publié: août 15, 2017, 1:22pm CEST par Ian Barker
Accessing privileged accounts is the hacker's number one choice of the easiest and fastest way to get access to critical data according to a new study. Privileged account solutions specialist Thycotic carried out a survey of more than 250 hackers at 2017's Black Hat conference and found that 32 percent of respondents see privileged accounts as the best way of getting hold of sensitive data, with 27 percent preferring access to user email accounts. Among other findings are that 73 percent of hackers believe the traditional security perimeter of firewalls and antivirus are irrelevant or obsolete. Also 85 percent blame… [Continue Reading] -

New platform looks to plug gaps in enterprise security
Publié: août 14, 2017, 4:41pm CEST par Ian Barker
When enterprises have a range of different IT systems and integrated supply chains it can lead to gaps in security coverage which are easily overlooked. Fortress Information Security is launching a new Emerging Security Risk Management platform to provide an enterprise-wide visualization capability allowing organizations to spot and address gaps. It creates a visual map across a company's information technology (IT), operational technology (OT) and their external supply chain connections to give a complete view of their cyber security vulnerability. Organizations can then mitigate vulnerabilities before they become points of attack. "There is a cyber security challenge facing most companies… [Continue Reading] -

Fear of missing out is driving cloud investments
Publié: août 14, 2017, 3:19pm CEST par Ian Barker
Businesses are increasingly keen to move ahead with cloud strategies and, according to a new survey, one of the reasons may be simply that they don’t want to miss out. The study from backup and archiving company Commvault with CITO Research finds that 81 percent of C-level and other IT leaders are either extremely concerned or very concerned about missing out on cloud advancements. It’s perhaps not surprising then that 93 percent of respondents say they are moving at least some of their processes to the cloud. In addition, 56 percent say they have moved or intend to move not… [Continue Reading] -

McAfee launches virtual security platform for AWS
Publié: août 14, 2017, 11:11am CEST par Ian Barker
Workloads on AWS can be vulnerable to a number of different threats including cross-site scripting, SQL injection and botnets, and if one virtual server is compromised malware has potential to move to a customer's other machines. To secure this McAfee is launching its Virtual Network Security Platform for AWS to provide advanced security in the public cloud. Instead of taking a traditional approach by monitoring an entire network segment to effect protection for a single workload, McAfee vNSP protects at the individual workload level. This guarantees visibility of inter-segment traffic, eliminating a single point of failure for an entire network… [Continue Reading] -

Phishing is the top threat faced by organizations
Publié: août 11, 2017, 3:21pm CEST par Ian Barker
Both users and their endpoint devices are the primary target for cyber criminals with phishing being the most prevalent threat according to a new report. The study from research and education specialist the SANS Institute finds security professionals rate phishing at 72 percent, spyware at 50 percent, ransomware at 49 percent, and Trojans at 47 percent as being the top threats today. Phishing has the biggest impact, with 40 percent of survey respondents having experienced phishing attacks, including spearphishing and whaling in the last year. "Users and their endpoints are still in the cross hairs," says Lee Neely, SANS analyst,… [Continue Reading] -

The top five cloud security myths debunked
Publié: août 11, 2017, 11:42am CEST par Ian Barker
Increasingly businesses are moving their data and applications to the cloud. But there are always concerns about how secure the information is. Network security company Portnox has put together an infographic looking at some of the myths surrounding cloud security and explaining why they're ill-founded. The top five cloud security myths are that the cloud is inherently insecure, that it's too new to be trusted, that it's good for productivity but not for network security, that security solutions require re-education of teams, and that cloud solutions are unable to help with compliance. The graphic debunks all of these and you… [Continue Reading] -

One in five people put corporate data at risk via unsecured Wi-Fi hotspots
Publié: août 10, 2017, 4:19pm CEST par Ian Barker
Employees are putting corporate data at risk by using unsecured hotspots and over sharing on cloud services, according to a new report. The study from cloud security specialist Bitglass set up Wi-Fi hotspots in random public spaces for two hour time slots, and captured and analyzed traffic, finding that of the 834 people in the public spaces, 187 unique devices (around 20 percent) connected. Of that 20 percent, 21 people accessed enterprise cloud applications over the unsecured Wi-Fi hotspot, including Office 365, Salesforce, Adobe Marketing Cloud, ADP, Slack, and Asana -- putting corporate data at risk. Two connected devices also… [Continue Reading] -

Enterprises lack resources to respond to targeted attacks
Publié: août 10, 2017, 3:38pm CEST par Ian Barker
The number one priority for security executives is achieving complete breach intolerance according to a new study from endpoint security company Endgame in conjunction with Forrester Research. The study of over 150 security decision makers in large US enterprises also finds 64 percent of executives are concerned that the next breach or attack they experience could be severe, a fear that is heightened by the fact that decision makers don’t know the system or the vector that will be attacked next. Security teams are also being hamstrung by complexity, 71 percent of respondents are using five or more technologies in… [Continue Reading] -

Managed service providers face cyber security talent shortage
Publié: août 10, 2017, 12:47pm CEST par Ian Barker
Many businesses rely on outsourcing some or all of their IT to managed service providers (MSPs), but a new study from Kaspersky Lab reveals that two out of three MSPs are suffering from a shortage of qualified cyber security staff. Among the findings are that cyber security is no longer seen as a separate or optional function among MSPs with 92 percent now including it as part of their portfolio of services. More than half (51 percent) cite security as essential to their customers' operational continuity in the next three to five years. Cyber security is expected to boost MSP… [Continue Reading] -

New platform improves visibility and control of endpoints
Publié: août 9, 2017, 4:03pm CEST par Ian Barker
Traditional methods of securing endpoints rely on installed agents and are affected by network dependencies. Endpoint security specialist Absolute is launching a new version of its solution that's always connected to every endpoint. Absolute 7 uses Persistence technology that’s embedded in the firmware of many popular endpoint devices, to deliver always-connected visibility and control with a tether to every device both on and off the corporate network. It can protect both Widows and Mac devices and also has a new Reach feature that delivers the ability to create and execute custom query and remediation scripts. This allows it to eliminate… [Continue Reading] -

Almost half of popular consumer websites have poor password requirements
Publié: août 9, 2017, 3:30pm CEST par Ian Barker
Although other forms of authentication are gaining traction, the password is still the most common method of identifying yourself to websites. Levels of password security should therefore be an important consideration for online businesses, especially in eCommerce. But a Password Power Rankings survey out today from password manager Dashlane shows that 46 percent of consumer sites, including Dropbox, Netflix, and Pandora, and 36 percent of enterprise sites, including DocuSign and Amazon Web Services, are failing to implement the most basic password security requirements. Some of the most popular sites provide the least guidance when it comes to secure password policies.… [Continue Reading] -

Brand influence of Snapchat declines while Instagram increases
Publié: août 9, 2017, 1:30pm CEST par Ian Barker
Marketers are keen to take advantage of the latest social channels to boost their profiles, but it can be a bit of a lottery for brands to know which have the most influence on customers. A new study by marketing platform Snaplytics has analyzed over 800 influencers in depth over the last quarter, to identify how many updates contain brand mentions, which brands are being mentioned and who mentions them on what platform. It finds that Snapchat has been going down in terms of influencer activity, while Instagram Stories is gaining more traction, especially among larger brands. There is a… [Continue Reading] -

New solution helps secure privileged accounts
Publié: août 8, 2017, 3:19pm CEST par Ian Barker
Privileged accounts allow access to all aspects of a company's IT infrastructure, so if they fall into the wrong hands the consequences can be disastrous. A new hardware appliance solution from identity management specialist One Identity aims to make it easy for businesses to deploy, operate and maintain their privileged password systems. One Identity Safeguard 2.0 includes new features that enable user flexibility and add redundancy while helping secure of today's hybrid infrastructures, including both on-premise and cloud-based applications. "Since privileged account management solutions have been around for a long time, they tend to be stale and lag behind the… [Continue Reading] -

New independent organization launches to promote data sanitization
Publié: août 8, 2017, 12:15pm CEST par Ian Barker
With security breaches and theft of sensitive data on the increase, enterprises are searching for ways of keeping their information secure. One technique that can be used is data sanitization but it's still relatively unknown and often misunderstood within the technology and IT security industry. To try to change this a new independent network, known as the International Data Sanitization Consortium (IDSC), is launching to champion and promote data sanitization best practices. The IDSC's mission is to eliminate ambiguity around data sanitization, including terminology, standards and guidelines. A recent survey of IT professionals worldwide found that 64 percent failed to… [Continue Reading] -

Want your emails read? Send them on Thursday at 4pm
Publié: août 8, 2017, 11:20am CEST par Ian Barker
Email marketing has always been something of a hit and miss affair, you're sending messages off knowing that many of them will simply disappear into the black hole of the internet. A new study by marketing platform GetResponse looks to shed some light on the most effective strategies to get your emails read by analyzing almost two billion messages. Among the findings are that emails sent on Thursdays have a higher open rate (23.13 percent) and a higher click-through rate (3.52 percent). Yet most companies are sending their messages on Wednesday. Messages sent between 9am and 11am, and between 3pm and… [Continue Reading] -

Delphix partners with Azure to ease cloud migration
Publié: août 4, 2017, 3:28pm CEST par Ian Barker
Microsoft Azure is increasingly popular as a business cloud platform, but migrating to Azure often means bringing together data from a range of sources. Lack of access to this data can hinder development and slow delivery. Data management specialist Delphix is launching a new Dynamic Data Platform for Azure, which offers enterprises the ability to streamline cloud migration projects, accelerate development and testing, and significantly reduce cost and complexity. "Delphix enables fast, secure migration of data to the cloud and a platform to access the right data at the right time," says Chris Cook, CEO of Delphix. "Through this collaboration… [Continue Reading] -

Security teams lack the right endpoint detection tools
Publié: août 2, 2017, 5:08pm CEST par Ian Barker
A new survey of IT and security professionals reveals that many teams lack the appropriate endpoint detection and response tools to quickly and efficiently deal with security alerts without the need to take endpoints offline to re-image them. The survey of 385 North American professionals by forensic security specialist Guidance Software reveals that 95 percent of respondents say advanced software functionality for malware removal and system recovery -- without the need to re-image a system -- is important in an endpoint security suite. Perhaps no surprise then that 23 percent of respondents cite re-imaging endpoints as one of their organization's top… [Continue Reading] -

Malicious SSL content more than doubles in six months
Publié: août 2, 2017, 4:17pm CEST par Ian Barker
As the overall percentage of encrypted traffic increases, hackers are increasingly using SSL to conceal device infections, and hide their other activities. A new study from Zscaler finds that an average of 60 percent of the transactions in the Zscaler security cloud have been delivered over SSL/TLS. "Hackers are increasingly using SSL to conceal device infections, shroud data exfiltration and hide botnet command and control communications. In fact, our study found that the amount of phishing attempts per day delivered over SSL/TLS has increased 400 percent from 2016," says Deepen Desai, senior director, security research and operations at Zscaler. "SSL… [Continue Reading] -

The return of the long-lasting DDoS attack and the rise of RDoS
Publié: août 2, 2017, 12:13pm CEST par Ian Barker
The latest DDoS intelligence report from Kaspersky Lab shows that long-lasting attacks are making a comeback. The longest attack in the second quarter of this year was active for 277 hours (more than 11 days) -- which is a 131 percent increase compared to the first quarter and a current record for the year. It shows that the geography of incidents has changed too, organizations with online resources located in 86 countries were targeted, compared to 72 countries in Q1. The top 10 most affected countries are, China, South Korea, US, Hong Kong, UK, Russia, Italy, the Netherlands, Canada and… [Continue Reading] -

Attacks from unknown threats increase by 40 percent
Publié: août 1, 2017, 4:44pm CEST par Ian Barker
The second quarter of this year has seen two of the largest recorded cyber attacks in WannaCry and NotPetya, and the latest quarterly report from Panda Security reveals there's been an increase in unknown threats too. PandaLabs analyzed attack data collected from all devices protected by one of Panda Security's solutions and discovered a 40 percent increase in attacks from unknown threats from the previous quarter. Among other trends identified is that ransomware is still on the rise, and will continue to do so as long as there are victims willing to pay. Also lost or stolen data is a problem… [Continue Reading] -

New storage platform offers data protection and seamless scaling
Publié: août 1, 2017, 3:44pm CEST par Ian Barker
In the past companies have relied on different secondary storage solutions for backup and recovery, and for archiving large amounts of structured and unstructured data. But as businesses need to store larger amounts of more diverse data this creates headaches for administrators as the same information collects on both solutions and may need to be handled via different interfaces. Storage company Cohesity is aiming to eliminate these inefficiencies with the launch of Orion 5.0, a platform for data protection and archiving that seamlessly spans on-premises and cloud infrastructure and can be managed through a simple, single-pane-of-glass user interface. It offers… [Continue Reading] -

71 percent of SMBs are not prepared for cyber security risks
Publié: août 1, 2017, 2:53pm CEST par Ian Barker
Small and medium sized businesses increasingly feel that they're vulnerable to cyber threats but most aren't prepared to meet them. A new survey from endpoint security specialist Webroot finds that 96 percent of businesses with 100 to 499 employees in the US, UK and Australia believe their organizations will be susceptible to external cybersecurity threats in 2017. But although they recognize the threats, 71 percent admit to not being ready to address them. Among other findings are that IT decision makers (ITDMs) at SMBs are most worried about new forms of malware infections (56 percent), mobile attacks (48 percent), and… [Continue Reading] -

How Amazon Echo could be used to spy on you
Publié: août 1, 2017, 1:05pm CEST par Ian Barker
As we acquire more voice activated smart devices, there's always the risk that they could be eavesdropping on day-to-day conversations. We've already seen reports of spying TVs, and now MWR InfoSecurity has exposed a vulnerability in Amazon Echo that can turn it into a listening device without affecting its functionality. Exploiting the vulnerability does require physical access to the device. By removing the rubber base at the bottom of the Echo, the research team was able to access the 18 debug pads and directly boot into the firmware of the device, via an external SD card, and install persistent malware… [Continue Reading] -

Cyber criminals target mortgage transactions as they phish for a big catch
Publié: juillet 31, 2017, 5:14pm CEST par Ian Barker
Buying a house is the biggest purchase most people make, with large amounts of money involved it’s not surprising that these transactions are attractive to cyber criminals. Security specialist Barracuda Networks has released an analysis of a recent mortgage spear phishing attempt where an attacker attempted to divert a payment. The scam works by sending an email, supposedly from the buyer's mortgage company, notifying a switch of banks and requesting payment be wired to a different account. In the stress of organizing a house purchase it's easy to see how people could fall victim to this type of attack. Though… [Continue Reading] -

Samsung launches new platform to monetize IoT data
Publié: juillet 31, 2017, 3:45pm CEST par Ian Barker
The IoT can represent a cultural shift for hardware makers as they move from just selling hardware to providing a connected digital experience. But supplying applications and supporting an ecosystem of third-party devices, apps and services has a cost which either needs to be absorbed or factored into the price of the product. Samsung is addressing this problem with the launch of its ARTIK Cloud Monetization, a new service to monetize the data shared by IoT devices and enable an IoT data economy. ARTIK Cloud Monetization provides a complete brokering, metering and payments system. It gives device manufacturers an easy… [Continue Reading] -

Data capture techniques fail to keep pace with demands for real-time analysis
Publié: juillet 31, 2017, 3:08pm CEST par Ian Barker
Organizations using extract, transfer and load (ETL) and Changed Data Capture (CDC) technologies are struggling to keep up with today's demand for real-time data analysis, with negative effects on their business opportunities and efficiency. This is one of the findings of a new study by IDC, sponsored by software company InterSystems which highlights a growing need for reliable real-time data analytics in today's enterprise. More than 75 percent of respondents believe untimely data has inhibited business opportunities and 27 percent indicate it has negatively affected their productivity or agility. Untimely data is also slowing the pace of business, with 54… [Continue Reading] -

Amazon Prime Day boosts other shopping apps
Publié: juillet 28, 2017, 1:25pm CEST par Ian Barker
Amazon's Prime Day, although it's only been happening for three years, has already become a sort of Black Friday for the summer season. But a new report shows that it's having a positive benefit for other retailers too. The study by mobile app marketing specialist Liftoff analyzed the install and purchase rates over a seven day period -- three days leading up to Prime Day, Prime Day itself, and the three days following. The company then compared 'Prime Week' to the previous six week period in order to establish benchmarks for shopping app install rates and purchase rates. While shopping… [Continue Reading] -

The future of enterprise flash storage [Q&A]
Publié: juillet 28, 2017, 11:10am CEST par Ian Barker
The all-flash storage market is predicted by Gartner to be worth $9 billion by 2020. But while flash offers speed advantages it's also expensive so it seems likely that the foreseeable future will see a mix of storage. We spoke to Lazarus Vekiarides, CTO and co-founder of ClearSky Data, which offers enterprise storage, backup and DR as a fully managed hybrid cloud service, to find out more about flash storage and how best to exploit it. BN: Is there really a shortage of flash storage and what does this mean for enterprises? LV: The data center world has been buzzing about all-flash… [Continue Reading] -

UK ransomware victims most likely to pay up
Publié: juillet 27, 2017, 4:05pm CEST par Ian Barker
A new study from anti-malware specialist Malwarebytes reveals that UK users are most likely to pay up if hit by ransomware. The study of over 1,000 companies across the US, France, UK, Germany, Australia, and Singapore reveals that 56.9 percent of UK businesses surveyed opted not to pay the ransom, and 46.2 percent lost files by not paying. In comparison, 84.1 percent of French businesses surveyed opted not to pay the ransom, and only 24.5 percent lost files. This could be because the UK is the least confident when it comes to combating ransomware. While the global average of businesses… [Continue Reading] -

Two-thirds of consumers suspect governments abuse their powers to access data
Publié: juillet 27, 2017, 3:08pm CEST par Ian Barker
According to a new study 51 percent of people don’t believe their government can protect their personal data, and nearly two-thirds (65 percent) suspect their government already abuses its powers to access the data of citizens. Identity protection company Venafi surveyed 3,000 consumers in the US, UK and Germany about initiatives that would grant governments more access to private, encrypted data. 68 percent of respondents say they believe governments shouldn't force private companies to hand over encrypted personal data without consumer consent. But despite these concerns 41 percent believe laws that provide government access to encrypted personal data would make… [Continue Reading] -

More than half of companies fail to measure the effectiveness of their cyber security
Publié: juillet 27, 2017, 1:19pm CEST par Ian Barker
With businesses spending increasing amounts on cyber security, a new survey reveals that many of them are failing to measure the effectiveness of their investments. The study from privileged account management specialist Thycotic found 58 percent of its 400 respondents scored a failing grade on a benchmark survey when evaluating their efforts to measure their cybersecurity investments and performance against best practices. 32 percent, of companies are making business decisions and purchasing cyber security technology blindly, without any way to measure their value or effectiveness. In addition, more than 80 percent of respondents fail to include business users in making… [Continue Reading] -

Brexit negotiations could be hit by DDoS attacks
Publié: juillet 27, 2017, 11:57am CEST par Ian Barker
Hackers could use DDoS to disrupt the Brexit negotiations for the UK's leaving the European Union, or use attacks as a distraction technique while they seek to steal confidential documents or data, according to new research. The study by Corero Network Security polled 100 security professionals at the Infosecurity Europe conference in London and found 57 percent believe Brexit negotiations will be disrupted by DDoS attacks. Many in the industry expect to see a significant escalation of DDoS attacks generally during the year ahead, with 38 percent predicting that there could even be worldwide internet outages during 2017. On a… [Continue Reading] -

New AI system helps overcome the cyber security skills gap
Publié: juillet 26, 2017, 5:14pm CEST par Ian Barker
Enterprises are under constant attack from increasingly sophisticated cyber adversaries, but they are struggling to recruit people with cyber security skills. Automation is the answer that many are turning to and cyber defense specialist DarkLight is launching its latest software which has AI that is trained to think and act like a human analyst. DarkLight 3.0 can implement known strategies from the best defenders and analysts in the form of playbooks to discover and identify attacks made against protected networks, and act to mitigate those threats to combat the most determined adversaries. "Most of the AI cyber defense solutions on… [Continue Reading] -

Exploring the psychology of ransomware
Publié: juillet 26, 2017, 4:35pm CEST par Ian Barker
In recent months we've seen high profile ransomware attacks target many businesses, and we've seen cyber criminals making greater efforts to target their victims. A new study from endpoint protection company SentinelOne and De Montfort University has been looking at how social engineering tactics are used by cyber criminals to manipulate and elicit payments from victims. "We noticed that there's a wide range of techniques used in the splash screens that we see and we thought it would be interesting to understand the things that went into them, the icons and so on," says Tony Rowan chief security consultant of… [Continue Reading] -

Threat hunting becomes critical to defeating cyber crime
Publié: juillet 26, 2017, 1:34pm CEST par Ian Barker
Security company McAfee is using this week's Black Hat conference to release a new report examining the role of cyber threat hunting and the evolution of the security operations center (SOC). Among its findings are that on average, 71 percent of the most advanced SOCs closed incident investigations in less than a week and 37 percent closed threat investigations in less than 24 hours. Novice threat hunters only determine the cause of 20 percent of attacks, compared to leading hunters who are able to verify 90 percent. Threat hunters in more mature SOCs spend 50 percent more time on actual… [Continue Reading] -

Organizations expect to fail if digital transformation is unsuccessful
Publié: juillet 26, 2017, 12:28pm CEST par Ian Barker
Enterprises are investing heavily in digital transformation projects, with 83 percent of senior IT leaders spending up to $10 million on them in the past year. Yet, 54 percent believe their company will be out-innovated and may fail in under five years according to the findings of a new survey from NoSQL data platform Couchbase. The survey of 450 heads of digital transformation for enterprises across the US, UK, France and Germany finds 80 percent feel they are at risk of being left behind by digital transformation. IT leaders themselves also feel at risk, with 73 percent believing they could… [Continue Reading] -

90 percent of consumers think security should be built into IoT devices
Publié: juillet 26, 2017, 11:37am CEST par Ian Barker
With increasing numbers of connected devices entering our homes and workplaces, their security is becoming a major concern as they can offer hackers an attractive backdoor into networks. A new survey from digital platform security company Irdeto shows that 90 percent of consumers across six countries think security should be built in, and 78 percent are aware that smart devices connected to their networks have the potential to be targeted. The study of almost 8,000 consumers across Brazil, China, Germany, India, the UK and the US finds millennials less aware of the risks, with 72 percent aware that any smart… [Continue Reading] -

How tech companies stack up for pay and corporate culture
Publié: juillet 25, 2017, 5:42pm CEST par Ian Barker
Technology companies are some of the biggest players in the business world, yet many still like to see themselves as being 'cool' places to work. A new study from compensation data specialist PayScale looks at a number of factors across 52 of the world's largest technology companies, comparing compensation, tenure, job satisfaction, and intent to leave, with some surprising results. The five tech companies with the most satisfied employees are: Box.com (91 percent), Zendesk (89 percent), LinkedIn (82 percent), Google (81 percent), and Workday (75 percent). On the other side of the coin, the highest levels of stress are experienced… [Continue Reading] -

New enterprise file platform helps overcome storage limitations
Publié: juillet 25, 2017, 4:38pm CEST par Ian Barker
With the rise of public and private clouds, enterprise file storage has become much more complex in recent years. Aimed at simplifying storage and removing capacity limitations, the latest Enterprise File Services Platform from CTERA Networks allows users to securely access, share and protect an unlimited number of files in the cloud as if they were stored locally on their desktop or on shared network drives. Version 6.0 of the platform provides unified modern file services for endpoints, offices and servers with the highest levels of security and with full IT control over data migration, governance, and choice of cloud.… [Continue Reading] -

AI-based platform improves security teams' response
Publié: juillet 25, 2017, 4:02pm CEST par Ian Barker
With risks showing no signs of declining, and security skills in short supply, companies are increasingly looking at machine-driven solutions to protect their networks. AI security company JASK is launching a new platform called JASK Trident which uses AI to facilitate machine driven alert triage, malicious behavior detection, and investigations into those behaviors. "With millions of cybersecurity jobs going unfilled, CISOs and managers of security operations centers across industries like financial, manufacturing, healthcare, and retail are looking for ways to improve their teams' abilities to mitigate cyberattacks," says Greg Martin, CEO and co-founder at JASK. "Trident accelerates the rate at… [Continue Reading] -

New analytics platform unlocks mobile data for marketing
Publié: juillet 25, 2017, 3:18pm CEST par Ian Barker
Businesses are increasingly offering mobile apps to their customers and these have the potential to deliver a great deal of valuable information. Turning that data into something useful though can be a challenge. Mobile marketing specialist Swrve is launching a Premium Analytics add-on to its existing Swrve Mobile Engagement Platform, aimed at giving improved insights, reporting and analytics capabilities. The platform hosts all of an organization's mobile data, giving data scientists capabilities for data-mining, reports and predictive modeling to deliver strategic insights about their mobile performance. The platform allows users to gain deeper understanding of their mobile apps to improve… [Continue Reading] -

New intelligence service allows companies to protect their digital identity
Publié: juillet 25, 2017, 12:24pm CEST par Ian Barker
Hackers often seek to imitate well-known companies in order to cash in on events as we saw in the wake of the recent WannaCry attacks. It’s therefore important for companies to be aware of their digital presence and know if they are being impersonated online. Threat management company RiskIQ is launching a Digital Footprint Snapshot to provide an on-demand intelligence report of a firm's internet-facing digital assets. "RiskIQ Digital Footprint allows organizations to more effectively discover, map, and monitor their internet-facing digital assets that may be susceptible to exploitation or compromise," says Steve Ginty, senior product manager at RiskIQ. "Now… [Continue Reading] -

Zoho launches one-stop cloud business suite for SMBs
Publié: juillet 25, 2017, 11:51am CEST par Ian Barker
Productivity software company Zoho has long offered packages for CRM, business email and more. It's now going after the SMB market with the launch of Zoho One, an all-in-one cloud business suite offering straightforward pricing and centralized control. Zoho One offers businesses all the applications they need to acquire and serve customers (marketing, sales, and support apps); run operations (finance, recruiting, and related HR apps); and provide all the tools for employees to work collaboratively (office suite, mail, personal productivity, and collaboration apps). They can also build custom apps for unique business needs and put them under the same umbrella.… [Continue Reading] -

New app framework delivers better visibility into cloud infrastructure
Publié: juillet 24, 2017, 5:23pm CEST par Ian Barker
Cloud workloads are increasing their share of data center traffic, but they give admins a headache when it comes to security and visibility. Security and compliance specialist Qualys is addressing both these issues with the launch of CloudView, a new app framework for its Cloud Platform that delivers a single pane view across cloud infrastructures. CloudView augments the existing Qualys view of host-related vulnerability, compliance and threat intelligence with a real-time inventory of all an enterprise’s cloud services. This helps security teams monitor, assess and deliver reports from within the DevOps pipeline. It ensures that cloud workloads throughout the Continuous… [Continue Reading] -

57 percent of internet users are worried about malvertising
Publié: juillet 21, 2017, 12:55pm CEST par Ian Barker
According to a new survey by advert filtering company AdGuard, 57 percent of internet users have either fallen prey to advert scammers, or are worried about malicious and phishing advertising. In addition 48 percent of respondents have experienced privacy issues with tracking requests hidden in online ads, leading to the email spam, unwanted incoming calls and IM chats. "We expect the volumes of malware distributed by hijacked ad networks to rise, since online advertising remains largely unregulated and prone to scammer abuse," Adguard's CTO Andrey Meshkov says. "Ad blocking as we know it these days must be viewed as web… [Continue Reading] -

How ransomware is going manual to target victims [Q&A]
Publié: juillet 21, 2017, 12:07pm CEST par Ian Barker
The ransomware attacks that make the news are the ones like WannaCry and NotPetya that spread rapidly and affect many businesses. But there's a new breed of manual ransomware attack happening that seeks to pick its victims much more selectively with a view to causing maximum disruption. We spoke to Roy Fisher, incident investigator at cyber security company MWR to find out more. BN: What makes manual ransomware different? RF: Traditional ransomware comes through some form of phishing attack or other 'spray and pray' technique. Manual ransomware requires much more time and effort from the attackers. They're trying to break… [Continue Reading] -

Elementary, my dear Watson -- IBM's cognitive system learns to spot differences in tone
Publié: juillet 20, 2017, 4:15pm CEST par Ian Barker
Human conversations are littered with subtle indicators, like tone of voice or slang, which can make the meaning of the dialog very different from what the words actually say. Online the situation is made more complex still by the increasing use of emojis. All of this can leave automated chatbots and customer service systems floundering when interacting with unhappy or frustrated individuals. IBM Watson is seeking to tackle the issue by making a new Tone Analyzer feature available from today. Trained specifically using customer support conversations on Twitter, the new feature is optimized to help companies monitor agent/customer communications, detect anomalies,… [Continue Reading] -

Data breaches are down but retailers still think they’re vulnerable
Publié: juillet 20, 2017, 3:28pm CEST par Ian Barker
US retail data breaches have dropped from 22 percent last year to 19 percent this, but 88 percent of retailers still think they’re vulnerable according to a new report. The latest retail edition data threat report from cyber security specialist Thales e-Security, in conjunction with 451 Research, shows that 52 percent of retailers have suffered a data breach in the past. However, retailers may not be learning from past mistakes, with more than half of the 19 percent that were breached this year having also experienced a breach previously. "First, the good news. Only 19 percent of US retail respondents… [Continue Reading] -

New solution streamlines IoT connectivity
Publié: juillet 19, 2017, 5:14pm CEST par Ian Barker
The IoT presents a challenge for organizations as they have to configure, secure and manage massive numbers of devices. A new product suite from productivity specialist Helium is aimed at streamlining the ability to prototype, deploy and scale a long-range wireless network that connects thousands of end devices, giving companies a simple way to intelligently and securely deliver data from devices to the cloud and application layer. Helium allows companies to manage and update their systems from a central console, the Helium Dashboard, eliminating the need to visit every sensor in the field. This also serves as a central point… [Continue Reading] -

Online courses train the next generation of credit card criminals
Publié: juillet 19, 2017, 4:21pm CEST par Ian Barker
E-learning courses costing under $1,000 are giving aspiring cyber criminals the potential to make $12k a month, based on a standard 40-hour working week according to new research. The study from digital risk management company Digital Shadows finds the courses, available to Russian speakers only, last for six weeks and comprise 20 lectures with five expert instructors. The course includes webinars, detailed notes and course material at a cost of RUB 45,000 ($745), plus $200 for course fees. With the average Russian earning under $700 a month, it's easy to see why the potential to earn 17 times as much… [Continue Reading] -

How healthcare providers are getting IoT security wrong
Publié: juillet 19, 2017, 3:51pm CEST par Ian Barker
More than 90 percent of healthcare IT networks have IoT devices connected to them, but those devices may not be properly protected according to a new study. The survey by IoT security solutions company ZingBox shows that over 70 percent believe that the traditional security solutions used to secure laptops and servers are sufficient to secure IoT connected medical devices. "The survey results demonstrate the current state of confusion and misconceptions abound in the healthcare industry on how best to secure connected medical devices. The need to gain a deeper understanding of the unique individual personalities of IoT devices remains a… [Continue Reading] -

Most Americans reuse passwords, with millennials the worst culprits
Publié: juillet 19, 2017, 2:00pm CEST par Ian Barker
A new survey of over 1,000 US adults reveals that 81 percent of people surveyed admit to using the same password for more than one account. Among millennials where 92 percent say they use the same password across multiple accounts. More worrying still, more than a third (36 percent) report that they use the same password for 25 percent or more of their online accounts. Yet despite these poor habits, the study for access control company SecureAuth, conducted by Wakefield Research shows Americans are much more likely to be concerned about their online personal information being stolen (69 percent) than… [Continue Reading] -

Is your software-defined storage truly software-defined? [Q&A]
Publié: juillet 19, 2017, 11:14am CEST par Ian Barker
It's no secret that today's technology sector is interested in software-defined storage (SDS) -- you'll often hear talk of its ability to reduce costs and increase simplicity. But while many companies are pointing to their technology as SDS, most only have a portion of what’s necessary to be considered truly software-defined. In order to fix this confusion, we need to agree on a concrete definition of SDS in order to get the best use of the technology and understand how organizations can use it as a cost effective data management solution. We spoke to Ashok Rajagopalan, head of products at… [Continue Reading] -

iOS and its effect on enterprise security
Publié: juillet 18, 2017, 4:12pm CEST par Ian Barker
Over the past decade, iOS devices have found their way into many businesses. According to a new report this has led to an increase in the number of attacks and incidences of malware on the platform. Mobile threat defense company Skycure analyzed the security impact of iOS on the enterprise over the past ten years and found that the percentage of enterprise iOS devices that have malicious apps installed today has more than tripled since the third quarter of 2016. In comparison, the rate of Android malware infections has stayed relatively flat. While Apple does an effective job of keeping… [Continue Reading] -

Symantec and Bay Dynamics partner to fight insider threats
Publié: juillet 18, 2017, 3:17pm CEST par Ian Barker
Insider threats are a major problem for all types of organization and more than ever firms are looking for data loss prevention strategies. Cyber security specialist Symantec is integrating Bay Dynamics' Risk Fabric analytics platform with its data loss prevention and other technologies, to create a central point of behavioral analytics that dynamically delivers mitigation actions to keep malicious insiders from stealing sensitive data. "The perimeter is gone, sensitive data is everywhere, and corporate and personal devices access critical data constantly," says Nico Popp, senior vice president of Product Management and Development for Information Protection at Symantec. "Through our partnership… [Continue Reading] -

Half of ex-employees still have access to corporate applications
Publié: juillet 18, 2017, 12:51pm CEST par Ian Barker
Businesses aren't doing enough to guard against the security risks presented by ex-employees, according to new research from identity management firm OneLogin. The study finds that nearly half (48 percent) of respondents are aware of former employees who still have access to corporate applications, with 50 percent of IT decision-makers ex-employee's accounts remaining active once they have left the company for longer than a day. In addition 44 percent of respondents don't have confidence that former employees have been removed from corporate networks at all. According to 20 percent of the respondents, failure to de-provision employees from corporate applications has… [Continue Reading] -

New CRM product integrates with Outlook to boost productivity
Publié: juillet 17, 2017, 4:03pm CEST par Ian Barker
Legacy CRM suites often involve slow, cumbersome interfaces, are frustrating for users and consequently don't achieve wide adoption. According to a Forrester survey, 47 percent of respondents encounter user adoption struggles when implementing their CRM initiative. CRM specialist Insightly is launching the latest version of its product with deep Microsoft Outlook integration, as well as a redesigned technical architecture and user interface to help sales teams in mid-sized businesses improve their productivity. Users can view contact details and account history from Insightly CRM directly in their Outlook inbox prior to contacting prospects or customers, and then automatically link those emails… [Continue Reading] -

DevOps practices help improve the quality of open source components
Publié: juillet 17, 2017, 3:24pm CEST par Ian Barker
The use of open source components can help speed up the software development process, but it comes with a risk if poor quality code leads to vulnerable applications being released. The latest State of the Software Supply Chain Report from DevOps tools specialist Sonatype reveals that organizations which actively manage the quality of open source components flowing into production applications realize a 28 percent improvement in developer productivity, a 30 percent reduction in overall development costs, and a 48 percent increase in application quality. "Companies are no longer building software applications from scratch, they are manufacturing them as fast as they… [Continue Reading] -

IBM announces breakthrough in encryption and data protection for enterprises
Publié: juillet 17, 2017, 11:36am CEST par Ian Barker
With data breaches a problem that shows no signs of going away, businesses are increasingly seeking to protect their information with encryption. But with large volumes of information this can be time consuming and costly. To address the problem, IBM is announcing a breakthrough encryption engine that, for the first time, makes it possible to encrypt all data associated with any application, cloud service or database all the time. Mainframe-based IBM Z is capable of running more than 12 billion encrypted transactions per day. The system’s advanced cryptographic capability now extends across any data, networks, external devices or entire applications… [Continue Reading] -

The US states with the highest malware infection rates
Publié: juillet 14, 2017, 4:44pm CEST par Ian Barker
Computer users in New Hampshire are three times more likely than those elsewhere in the US to get a malware infection on their computers according to a new report. The study from Enigma Software Group (ESG), the company behind SpyHunter, analyzed over 1.5 million infections detected by SpyHunter across all 50 states in the first six months of this year. The top five states are: New Hampshire -- with infection rates 201 percent higher than the national average Colorado -- 143 percent higher Virginia -- 80 percent higher New Jersey -- 64 percent higher Oregon -- 25 percent higher Tennessee,… [Continue Reading] -

Kaspersky brings protection to business Macs
Publié: juillet 14, 2017, 12:55pm CEST par Ian Barker
There has long been a perception that Macs are somehow immune to cyber attacks, but as the security landscape has changed they've become an attractive target for hackers looking to gain access to corporate networks. Kaspersky Lab is launching a new edition of its Kaspersky Endpoint Security Cloud to give corporate Macs cloud-based multilayered protection. Aimed at small and medium businesses and managed service providers, it also brings more automation and management capabilities. Kaspersky detected 11.8 million cyber-attacks against Mac users in 2016. MacOS-specific malware, OS-agnostic phishing and 'man in the middle' type attacks can put paid to the false… [Continue Reading] -

New solution prevents bots from accessing API servers
Publié: juillet 13, 2017, 3:37pm CEST par Ian Barker
Bots are often the culprits behind web scraping, brute force attacks, online fraud, account hijacking, data theft, and more. Often these attacks are made through the API servers that power public-facing websites and mobile applications. A new solution from bot detection specialist Distil Networks is aimed at protecting these servers by determining whether a human is using a verified browser or mobile device to gain access. Capabilities of Bot Defense for Mobile App APIs include what is called 'Hi-Def Fingerprint' identification, based on over 200 unique markers present in the OS and browser (things like plugins, screen, interface, fonts, WebGL,… [Continue Reading] -

A third of security professionals are unprepared for dealing with cyber threats
Publié: juillet 13, 2017, 12:45pm CEST par Ian Barker
One in three security professionals lack effective intelligence to detect and action cyber threats, according to a new survey from threat intelligence platform Anomali. In addition 24 percent believe they are at least one year behind the average threat actor, with half of this sample admitting they are trailing by two to five years. Among other findings are that 17 percent of respondents haven't invested in any threat detection tools such as SIEM, paid or open threat feeds, or User and Entity Behavior Analytics (UEBA). Two-thirds of respondents maintain fewer than 200 days of log data online for analysis and… [Continue Reading] -

Digital transformation poses major network challenges for business
Publié: juillet 12, 2017, 4:29pm CEST par Ian Barker
As enterprises strive to take advantage of the world of digital business, they face a number of issues surrounding the operation and control of their networks. Network traffic intelligence company Kentik surveyed over 200 IT professionals attending Cisco Live 2017 to discover the network challenges raised by digital transformation. The results show cloud adoption is still the most concerning factor in increased network complexity, according to 36 percent of respondents. This puts it ahead of the IoT (21 percent), SDN (12 percent), and NFV (3 percent). Only 20 percent of survey respondents think their organizations are doing an excellent job… [Continue Reading] -

Shopping cart attack provides insight into criminal operations
Publié: juillet 12, 2017, 3:55pm CEST par Ian Barker
The Magecart attack which injects JavaScript into unpatched eCommerce sites in order to capture payment information first appeared in October last year. Researchers at threat management specialist RiskIQ have been following a new strain of Magecart and found that it offers a rare insight into the operations of the actors behind digital threats. By logging consumer keystrokes, Magecart captures large quantities of payment card information from unsuspecting shoppers. This stolen data typically gets packaged and sold as CVV dumps, on websites where transactions involving stolen credit card data take place. But RiskIQ's research shows that there are other ways in… [Continue Reading] -

How the authentication landscape is changing [Q&A]
Publié: juillet 12, 2017, 10:56am CEST par Ian Barker
Recently there has been much talk of the death of the password and a switch to other forms of authentication, like biometrics, which are seen as more secure. But is biometric security a complete answer, and do we risk swapping usability for security? We spoke to Perry Chaffee, vice president of strategy at password-less security company WWPass to find out about the latest trends in authentication. BN: How is the security market changing its outlook with regard to authentication? PC: Authentication tends to either improve security at the cost of convenience, or improve convenience at the cost of security. Very… [Continue Reading] -

Two new vulnerabilities found in Windows NTLM security protocols
Publié: juillet 11, 2017, 7:10pm CEST par Ian Barker
Researchers at behavioral firewall specialist Preempt have discovered two vulnerabilities within the Microsoft Windows NT LAN Manager (NTLM) security protocols. The first involves unprotected Lightweight Directory Access Protocol (LDAP) from NTLM relay, and the second discovery impacts Remote Desktop Protocol (RDP) Restricted-Admin mode. Both vulnerabilities can result in unauthorized credential use, risk of password cracking and potentially domain compromise. "Today's threat landscape continues to expand, highlighting weaknesses in existing security protocols, and these two vulnerabilities are no different," says Ajit Sancheti, CEO and co-founder of Preempt. "NTLM puts organizations and individuals at risk of credential forwarding and password cracking, and… [Continue Reading] -

DigitalOcean launches high performance cloud servers for compute intensive applications
Publié: juillet 11, 2017, 5:13pm CEST par Ian Barker
Although cloud-based server infrastructure is becoming more common, it's not usually suited to applications that need very high levels of CPU performance. Developer-focused cloud platform DigitalOcean wants to change this with High CPU 'Droplets' featuring the latest Intel Xeon Scalable processors. These provide ideal support for applications such as ad exchanges, game servers, highly active front-end application servers, and batch processing. "High CPU is our sixth new offering in twelve months and it's a response to developers who need access to newer and higher performing CPUs," says Julia Austin, CTO of DigitalOcean. "These Droplets are backed by Intel's most powerful… [Continue Reading] -

Rapid response software helps companies recover from ransomware attacks
Publié: juillet 11, 2017, 4:14pm CEST par Ian Barker
Recent high profile ransomware attacks including WannaCry and NotPetya have highlighted the fact that often the time organizations take to recover is just as damaging as the attack itself. Network visibility firm Portnox is aiming to tackle this with the launch of Rapid Ransomware Response and Control as part of its suite of network access control (NAC) systems. Rapid Ransomware Response and Control allows for fast recovery by automatically disconnecting infected devices, as well as any that may be prone to infection or missing necessary patches, preventing the lateral spread of the ransomware throughout the network. By providing full visibility… [Continue Reading] -

Enhanced firewall integrates with Azure and DevOps tools
Publié: juillet 11, 2017, 3:48pm CEST par Ian Barker
Cloud security specialist Barracuda Networks is announcing enhancements to its firewall products to help customers speed up Microsoft Azure adoption and become cloud ready. Barracuda NextGen Firewall and Barracuda Web Application Firewall (WAF) both now integrate with Microsoft Operations Management Service (OMS). A Barracuda WAF specific dashboard is now available in the Azure Marketplace, making it easy for administrators to take advantage of this integration. NextGen Firewall also includes advanced SD-WAN capabilities to provide secure, optimized WAN connectivity from on-premises locations to cloud-based networks. New enhancements include a comprehensive REST API that helps DevOps teams to include web application security… [Continue Reading] -

New version of Parallels RAS helps remove barriers to adopting virtual applications
Publié: juillet 10, 2017, 4:49pm CEST par Ian Barker
Delivering virtual applications and virtual desktop infrastructure can be a complex and expensive business. Parallels Remote Application Server (RAS) has been a leader in application delivery for some time and is using this week's Microsoft Inspire conference to launch its latest update. Parallels RAS 16 includes new features like PowerShell API, white labeling for managed service providers (MSPs) and independent software vendors (ISVs), Touch ID for iOS clients, linked clones for virtual desktop infrastructure (VDI), Turbo.net integration for an easy way to manage multiple application versions, use of Microsoft Windows Server for VDI deployments for MSPs), and more. It features enhanced support for the… [Continue Reading] -

Microsoft 365 delivers a complete solution for businesses
Publié: juillet 10, 2017, 4:32pm CEST par Ian Barker
As the workplace evolves to become more diverse and teams are more widely distributed, businesses are looking to technology to empower their staff. Microsoft CEO Satya Nadella used his speech today at Inspire to announce the launch of Microsoft 365 which incorporates Office 365, Windows 10 and Enterprise Mobility + Security, to deliver a complete, intelligent and secure solution for employees. It comes in two versions: Microsoft 365 Enterprise and Microsoft 365 Business. The Enterprise version brings together Office 365 Enterprise, Windows 10 Enterprise and Enterprise Mobility + Security to empower employees to be creative and work together securely. Writing… [Continue Reading] -

New biometric authentication platform eliminates the need for passwords
Publié: juillet 10, 2017, 3:33pm CEST par Ian Barker
Passwords are increasingly being seen as inadequate for securing systems and developers are seeking better alternatives. A new SaaS platform from Pramati Technologies is aimed at providing strong authentication for mobile and web-based applications using existing device capabilities. ThumbSignIn enables enterprises and service providers to deploy strong authentication solutions that reduce reliance on passwords and protect against a range of attacks. It uses public key cryptography to securely transfer authentication information over the internet. But unlike password-based systems, the authentication takes place entirely on users' devices, and the biometric information is never transmitted to, nor stored on, the server. This… [Continue Reading] -

Gender discrimination harms tech industry growth
Publié: juillet 7, 2017, 3:15pm CEST par Ian Barker
According to new analysis by Sopra Banking Software, men still dominate senior roles in the tech sector and this is harming the industry’s growth. A study by McKinsey Global Institute finds that 38 percent of women in the technology field feel that gender discrimination staggers growth and chances for progressing their career in the future. What's more, 60 percent of these women attribute not wanting to be a top executive to excessive stress and pressure. The same study finds that in an ideal scenario, where female roles are identical to those of men, "as much as $28 trillion, or 26… [Continue Reading] -

Younger consumers return to more traditional shopping habits
Publié: juillet 7, 2017, 12:00pm CEST par Ian Barker
New research reveals that younger consumer groups are increasingly turning to traditional face-to-face shopping habits alongside digital. Amsterdam-based payment solutions company Acapture has been looking at the preferences of the youngest and largest sets of digital native consumers -- millennials and generation Z. It finds that although both groups have grown up with constant Internet connectivity, and are competent online shoppers, generation Z consumers (those born after 1995) value face-to-face interaction as much as digital, and prefer to combine different platforms and channels. Over half choose to communicate in-person despite their use of connected technology, and over two thirds prefer… [Continue Reading] -

Plugins and social media links leave websites more open to compromise
Publié: juillet 6, 2017, 11:58am CEST par Ian Barker
Adding extra features like plugins and social media links makes websites more likely to be compromised according to a new report. The study by website security company SiteLock finds that sites with between one and five plugins have 1.5 times more chance of being compromised than the average site. More plugins leads to more risk, with 10 to 20 plugins increasing the chance of compromise to 2.5 times and 20 plus plugins leads to three times the risk. Linking to social media adds to the danger of being hacked too. Sites that link to Facebook and Twitter accounts have 1.5 times the… [Continue Reading] -

Ukraine police raid accounting software company as part of NotPetya investigation
Publié: juillet 5, 2017, 5:38pm CEST par Ian Barker
Police in the Ukraine have seized the servers of Intellect Service, a company supplying accounting software, as part of their investigation into the NotPetya ransomware attack. A malicious update to Intellect's MeDoc accounting package is believed to have been responsible for some of the initial NotPetya infections. The head of Ukraine's cyber police, Serhiy Demedyuk, says the software was subject to a supply chain attack. This would have involved gaining access to the source code in order to add a back door which gives access to a remote access Trojan. A police spokesman says that MeDoc was preparing to send… [Continue Reading] -

Protecting hybrid apps from attackers [Q&A]
Publié: juillet 4, 2017, 12:00pm CEST par Ian Barker
In order to speed up development times and roll out their apps across multiple platforms without the need to create entirely new code, companies are increasingly turning to hybrid apps. The problem is that these rely on HTML and JavaScript code which is relatively easy to reverse engineer. How can businesses prevent this and keep their apps and the data they handle safe from hackers? We spoke to Andrew Whaley VP of engineering for Europe at application protection specialist Arxan Technologies to find out. BN: What makes hybrid apps uniquely vulnerable? AW: Companies have to put their apps out there… [Continue Reading] -

Windows 10 Fall Creators Update will simplify enterprise device deployments
Publié: juin 29, 2017, 4:30pm CEST par Ian Barker
We've already seen that with the Windows 10 Fall Creators Update Microsoft is aiming to strengthen security. The company has today revealed a number of other new features aimed at business users. The flagship among these is Windows AutoPilot Deployment, a cloud service designed to simplify the deployment and management of new Windows 10 PCs. AutoPilot is designed to allow end users to set up their own PCs but still get the out of box experience (OOBE) defined by the IT department. The user powers up the machine, selects a language, chooses a keyboard layout and connects to a network.… [Continue Reading] -

Enterprises gear up to face the inevitability of cyber attacks
Publié: juin 29, 2017, 3:21pm CEST par Ian Barker
A new study finds that while attacks increase and financial losses continue to mount, a growing number of companies are preparing to respond to breaches The research from forensic security company Guidance Software finds that 54 percent of organizations feel well prepared to respond to a major breach in the coming year (up from 51 percent in 2016). Additionally, 25 percent of respondents say they're looking to build a formal security and incident management team within the next year up from 12 percent in 2016. 35 percent of respondents say assessing risk is the biggest IT security challenge, up from… [Continue Reading] -

Information security and the generation gap
Publié: juin 29, 2017, 12:51pm CEST par Ian Barker
Cyber attacks are becoming a regular feature of everyday life and it's more important than ever to be aware of the risks and take steps to protect yourself. But, according to a survey of 1,000 people across the US by password management company LastPass, different age groups have very different attitudes to security. Interestingly, it's the younger generation that's least concerned about safeguarding their security. Generation Z (aged between 13 and 22) have poor password habits, 32 percent don't put much effort into choosing passwords and 25.6 percent use only one or two passwords across all their accounts. A worrying… [Continue Reading] -

Half of organizations hit by ransomware will suffer more than one attack
Publié: juin 28, 2017, 5:08pm CEST par Ian Barker
With ransomware hitting the headlines at the moment thanks to the Petya/NotPetya attack, a timely new report from cloud data protection specialist Druva reveals it's becoming a ubiquitous global threat affecting enterprises large and small and devices of all types. The survey of more than 800 companies shows that over 80 percent of respondents report ransomware attacks are on the rise and that half of businesses hit by ransomware have been attacked multiple times. "It's no longer a question of if an organization will be the victim of a ransomware attack, but when. Druva's Ransomware Report underscores the importance of… [Continue Reading] -

Cloud-based governance solution identifies breaches in real time
Publié: juin 28, 2017, 3:59pm CEST par Ian Barker
All organizations have valuable data which they need to protect, but as their digital footprint gets larger it becomes harder to keep track of and guard all their information. Content collaboration and governance specialist Egnyte is launching a cloud-based governance solution, Egnyte Protect to provide real-time analysis of all content within an organization and deliver insights to help administrators prevent potential data breaches. Egnyte Protect continuously analyzes the customer's entire content environment and classifies the most sensitive information, like credit card numbers or social security numbers. In real-time it can identify vulnerabilities, alert administrators and offer actions that can immediately fix… [Continue Reading] -

IBM and Lightbend collaborate on AI platform
Publié: juin 28, 2017, 3:24pm CEST par Ian Barker
IBM is announcing a collaborative development initiative with Lightbend, the provider of the world's leading Reactive Application Development Platform, to help advance the development of artificial intelligence (AI) and cognitive solutions in the enterprise. The collaboration will create new code, tools and documentation that will be designed to help developers build Java- and Scala-based applications on the Lightbend Reactive Platform. Joint solutions will provide a complete toolchain for Java and Scala developers to easily build and deploy AI and cognitive applications in both on-premise and cloud environments. Lightbend's current Reactive Platform is powered by an open source core and brings… [Continue Reading] -

New software aims to make employees central to the workplace
Publié: juin 28, 2017, 1:36pm CEST par Ian Barker
With automation and artificial intelligence becoming increasingly important for business, many employees are worried about what that means for their careers and future as part of a human workforce. IT solutions specialist BMC is launching its new Digital Workplace, a cloud-based service that enables IT, HR, legal, facilities management, and any other line-of-business groups to offer employees a one-stop-shop for the tools and information they need to do their work. With millennials expected to make up 75 percent of the workforce by 2025, organizations must adapt to meet the influx of digital natives and their workplace expectations. They need to… [Continue Reading] -

Less than one percent of UK charities are protected against email fraud
Publié: juin 28, 2017, 12:40pm CEST par Ian Barker
Charities, just like other organizations, rely heavily on email for their communications, but a new study reveals that in the UK most are not protected against the risks of fraudulent emails and phishing attacks. The study by platform-as-a-service provider Red Sift analyzed the email domains of over 78,000 charities and found that under one percent have adequate protection using DMARC authentication. The Top 100 Charities fare a little better with five percent adoption, however, none are blocking unauthorized email. This is despite a UK government report earlier this year showing the most common attacks are delivered via fraudulent emails. To… [Continue Reading] -

Petya ransomware goes global -- what's happening and how to protect yourself
Publié: juin 28, 2017, 11:20am CEST par Ian Barker
The ransomware attack we reported yesterday may have begun in the Ukraine, but it spread rapidly across Europe and has now hit companies in Australia and the US including pharmacy giant Merck. A variant of the Petya ransomware now being dubbed 'NotPetya', it spreads initially by phishing emails and once on a system the ransomware demands $300 in bitcoin. When it's installed on one system behind a firewall it's able to spread rapidly to others on the same network. The attack uses the same delivery method as last month's WannaCry attack, an exploit known as 'EternalBlue' within the Microsoft Server… [Continue Reading] -

Major ransomware attack spreads rapidly across Europe
Publié: juin 27, 2017, 6:03pm CEST par Ian Barker
Companies, government departments and airports in the Ukraine have been hit by ransomware this afternoon and the attack now appears to be spreading across Europe. In Ukraine, government departments, the central bank, a state-run aircraft manufacturer, Kiev airport and the metro network have all been hit. In the UK, the advertising company WPP says its systems have also been taken down, and Danish transport company Maersk reports sites and business units shut down by the attack. Ukranian media also reports that systems at the Chernobyl nuclear plant have been affected by the attack. Details are still emerging but it appears… [Continue Reading] -

New service helps enterprises buy and manage software
Publié: juin 26, 2017, 3:54pm CEST par Ian Barker
As enterprises grow in size it becomes harder for them to manage their software assets. Systems get decentralized and employees aren't always sure what tools are available, which can lead to the adoption of shadow IT. Leading systems integrator World Wide Technology (WWT) is launching a new service called EA+ which guides enterprise buyers through the entire process of defining, choosing and implementing a complete software stack. EA+ manages every part of the software buying process, from initial purchase, to implementation, to renewal. Clients get access to WWT's $150 million Advanced Technology Center, a dedicated testing environment where proposed software… [Continue Reading] -

New platform aims to speed up digital transformation
Publié: juin 26, 2017, 3:11pm CEST par Ian Barker
Companies are increasingly competing to transform their IT infrastructure to take advantage of the cloud, containers and other technologies that offer greater agility. California-based appOrbit is launching a new application platform that will allow customers to automate the modeling, delivery, and management of enterprise software onto any modern infrastructure. "We founded appOrbit with the vision to simplify the holistic management of applications regardless of whether three-tier or microservice, cloud-native or legacy enterprise, across any cloud," says Rahul Ravulur, co-founder and CEO at appOrbit. "All applications should be on-demand, self-healing, scalable, composable, secure and completely portable to any environment, not the… [Continue Reading] -

UK parliament cyber attack highlights the shortcomings of passwords
Publié: juin 26, 2017, 1:26pm CEST par Ian Barker
As we reported over the weekend the UK parliament's email system was subject to a brute force attack using passwords stolen in the 2012 LinkedIn breach. Security experts have been quick to point out the inherent weakness in large organizations and government departments relying on passwords to protect highly sensitive data. "A simple brute force attack can normally be detected and blocked within a minute," says Ilia Kolochenko, CEO of web security company, High-Tech Bridge. "This incident highlights once again that cybersecurity fundamentals are ignored even by the governments of leading countries. Today, two-factor authentication (2FA), advanced IP filtering and… [Continue Reading] -

Cloud-native workloads gain momentum
Publié: juin 23, 2017, 12:08pm CEST par Ian Barker
A new survey shows that 18 percent of organizations now have more than half of their workloads in cloud-native environments. In addition many are moving from on-premises and self-hosting toward shared environments, distributing workloads across multiple providers. The study by cloud security and network software firm Cohesive Networks also finds 57 percent of respondents say that cloud-native workloads make up at least 20 percent of applications in Infrastructure-as-a-Service (IaaS). In addition 64 percent strategically use multiple cloud providers for development, testing, and production workloads. The speed and lack of friction in the cloud allows more experimentation and flexibility. Cloud IaaS… [Continue Reading] -

The value of information on the dark web
Publié: juin 22, 2017, 3:22pm CEST par Ian Barker
We're all familiar with the concept of the dark web where information gained from hacks and data breaches is traded amongst cyber criminals. But just how much are your identity and account credentials worth? Password manager and digital vault app Keeper Security has produced an infographic looking at how much various pieces of information trade for. An email address and password is worth between £0.60 and £1.80 ($0.75 to $2.25), PayPal account credentials £1.20 ($1.50), a medical record from a large scale attack between £1.20 and £8 ($1.50 to $10), and a complete medical record as much as £800 ($1,000).… [Continue Reading] -

Facts you didn't know about email marketing
Publié: juin 22, 2017, 1:50pm CEST par Ian Barker
Despite newer developments like social media and mobile, email remains a powerful and effective marketing tool. Website tool comparison site WebsiteBuilder has put together an infographic looking at why email marketing works, the techniques used, and more. Among the highlights are that 77 percent of consumers prefer to receive marketing communication by email. In addition 44 percent have bought at least one item as a result of a promotional email, giving email marketing three times the conversion rate of social media. The most used techniques are automated emails (74 percent), personalization (58 percent), social media integration (33 percent) and location-based… [Continue Reading] -

UK consumers want an end to misleading 'fibre' broadband advertising
Publié: juin 22, 2017, 12:23pm CEST par Ian Barker
Using the word 'fibre' to describe broadband services which are partly delivered using copper cable is misleading consumers according to the UK's Advertising Standards Authority (ASA). Conducted by specialist research agency Opinion Leader, using focus groups and in depth interviews with residential and business broadband users, the research shows that adverts using the word fibre don't enable people to make an informed choice. The majority of UK households and businesses receive their broadband over networks that are only partially fibre. Fibre terminates at a street cabinet with the final connection to the consumer being delivered over copper phone wire or… [Continue Reading] -

Mobile employees are willing to place security above privacy
Publié: juin 21, 2017, 5:02pm CEST par Ian Barker
Given the recent increase of violent incidents around the world, in addition to everyday risks and natural disasters, businesses are naturally concerned about protecting their staff. New research by enterprise safety application company Everbridge shows that mobile workers expect that their companies will be able to provide safety information to them should something happen or should they be in the proximity of a serious event. It also shows staff are willing to sacrifice privacy to achieve this. 81 percent of companies report that their employees expect the organization to help protect them while they are mobile, traveling or working remotely.… [Continue Reading] -

Top websites struggle to guard against sophisticated bot attacks
Publié: juin 21, 2017, 3:15pm CEST par Ian Barker
A report released today shows that, while an average of 16 percent of websites across all industries can thwart simple bot attacks, only five percent are able to properly protect against sophisticated attacks. The study from bot detection specialist Distil Networks, in conjunction with the Online Trust Alliance (OTA), evaluated the top 1,000 websites in retail, banking, consumer services, government, news media, internet service providers and OTA members. The report divides bots into four categories: Sophisticated Bots -- coming in slowly from dozens of IP addresses, using browser automation tools that can hold cookies and maintain state Moderate Bots --… [Continue Reading] -

Personalization can add up to six percent to ecommerce revenues
Publié: juin 21, 2017, 12:16pm CEST par Ian Barker
Effective personalization of marketing messages can have a significant effect on generating sales according to a new report. The study by marketing technology specialist Qubit shows that ecommerce businesses could add six percent to their revenues by focusing on the most effective optimization and personalization techniques. The most effective techniques identified by the report include scarcity, highlighting items that are low in stock; social proof, using the behavior of other users to indicate trending products; and urgency, imposing a deadline for consumers to act. These are much more effective in terms of increasing revenue per customer than other methods such… [Continue Reading] -

Mobile commerce grows as cost of acquiring new customers falls
Publié: juin 20, 2017, 7:00pm CEST par Ian Barker
A new report from mobile app marketing specialist Liftoff reveals that the cost of acquiring new customers for mobile shopping apps is falling. The cost of getting someone to install an app is just $4.45, though converting that into a purchase costs considerably more (over $75), with an install-to-purchase rate of just 5.9 percent. The study which analyzed 26.9 billion ad impressions across 4.8 million app installs between April 2016 and April 2017 also shows that September is the best month to pick up new users. Those who register in September are more likely to complete a purchase ahead of… [Continue Reading] -

Microsoft Stream rolls out to Office 365 Enterprise customers
Publié: juin 20, 2017, 5:53pm CEST par Ian Barker
Last year Microsoft announced the preview of its Stream enterprise video service, intended to make it easy to share and discover business-relevant video content. Today Stream becomes available as a stand alone product and is being rolled out to Office 365 Enterprise customers around the world. At the same time it's announcing new intelligent features for the platform. These include turning transcribed audio into searchable text. Simply by typing in keywords users can jump to any point in a video where they are spoken. Face detection lets viewers see where each person in the video is shown throughout and a… [Continue Reading] -

New vulnerability manager aims to prevent the next WannaCry
Publié: juin 20, 2017, 3:09pm CEST par Ian Barker
When the WannaCry attack hit last month, a patch was already available to prevent it. Its victims were those who had failed to deploy it. Software management company Flexera is aiming to help companies close the risk window between patches and attacks with the launch of its new Software Vulnerability Manager. According to Flexera's research, 81 percent of vulnerabilities recorded in 2016 had patches available on the same day as the disclosure, but companies have taken on average 186 days to completely install those patches. The Vulnerability Manager allows companies to quickly identify, prioritize and patch vulnerabilities used as entry points… [Continue Reading] -

Retail industry leads the way in data breaches
Publié: juin 20, 2017, 1:33pm CEST par Ian Barker
The largest share of data breach incidents involved the retail industry, closely followed by food and beverages, according to a new report. The 2017 Global Security Report from Trustwave shows that 22 percent of incidents involved the retail industry, followed by food and beverages at 20 percent. Incidents involving point of sale (POS) systems also increased from 22 percent in 2015 to 31 percent in 2016. POS breaches are more common in North America which has been slower than the rest of the world to roll out the EMV chip and pin standard, suggesting that hackers are keen to exploit… [Continue Reading] -

One in three consumers has a separate email account for marketing messages
Publié: juin 16, 2017, 11:55am CEST par Ian Barker
People are increasingly looking to separate marketing messages from their other emails by having them sent to a separate account. According to a new survey of consumer email habits from Yes Lifecycle Marketing, 36 percent have opened separate email accounts solely for brand communication. For millennials that number jumps to more than half (58 percent). While you might assume this would be bad news for marketers, the findings show that those with separate marketing accounts check in more frequently for promotions compared to consumers who only use one primary account. Which suggests that consumers want promotions but don't want to… [Continue Reading] -

SecureAuth launches improved Office 365 protection
Publié: juin 15, 2017, 4:40pm CEST par Ian Barker
Office 365 is the world's most popular cloud service, but widespread use of the platform also makes it a primary target for cyber attacks. Breaches tied to phishing email scams and lack of strong identity security are accelerating. Adaptive access control specialist SecureAuth is launching a new enhanced security solution aimed at protecting Office 365 from attack by improving authentication. SecureAuth's solution delivers adaptive authentication for all Office 365 mail clients -- including Microsoft Outlook and third-party applications, such as Apple Mail. It provides identity protection and detection using advanced adaptive authentication and risk analysis capabilities, and features SecureAuth's portfolio… [Continue Reading] -

Threat intelligence fails to deliver on its promise
Publié: juin 15, 2017, 3:54pm CEST par Ian Barker
A new study by the Information Security Forum (ISF), an independent authority on cyber security and information risk management, reveals that threat intelligence isn't delivering the expected business objectives. While 82 percent of ISF Members surveyed have a threat intelligence capability, with the remaining 18 percent planning to implement one in the next twelve months, only 25 percent of those surveyed believe their capability is fully delivering. "While organizations continue to rely on well-established security practices, many are seeking additional ways to keep pace with the increasing torrent of attacks," says Steve Durbin, managing director of ISF. "To efficiently manage… [Continue Reading] -

Businesses still struggle with web application quality issues
Publié: juin 15, 2017, 2:52pm CEST par Ian Barker
Software bugs have been a problem since the very earliest days of computing, and as we move towards more data-intensive applications and a more sophisticated and flexible user experience, QA and testing remains as vital as ever. Development platform company Sencha has released the results of a new survey carried out by Dimensional Research, looking at current attitudes and common experiences surrounding the testing of web applications. The findings make clear that quality remains a major issue, with 98 percent of respondents reporting quality issues that impact their business, and 53 percent saying these issues occur at least monthly. 99 percent… [Continue Reading] -

Attacks on online services cost banks over $1.7 million
Publié: juin 15, 2017, 12:13pm CEST par Ian Barker
A cybersecurity incident involving a bank's online banking services costs the organization $1,754,000 on average, around double the price of recovering from a malware incident. This is among the findings of Kaspersky Lab's Financial Institutions Security Risks survey released today, which shows that 61 percent of cybersecurity incidents affecting online banking come with additional costs for the institution targeted. These include data loss, loss of brand or company reputation, confidential information leaks, and more. Recovering from a DDoS attack is also more expensive for banks ($1,172,000) to recover from than non-financial organizations ($952,000). The report shows that when organizations are attacked… [Continue Reading] -

New development environment helps bridge the gap between Dev and Ops
Publié: juin 14, 2017, 5:12pm CEST par Ian Barker
As the development cycle evolves, things like testing, monitoring and compliance need to be delivered earlier in order to speed up service delivery. Enterprise software solutions firm BMC is launching a new development environment to help organizations compete in the digital economy. Control-M Workbench is a no-cost, self-service, standalone development environment. It expands on the capability of the Control-M Automation API introduced in 2016. The API offers a set of programmatic interfaces that allow developers and DevOps engineers to automate application workflows in a self-service environment within the agile application release process. Control-M Workbench can be deployed quickly, giving developers… [Continue Reading] -

Enterprise users still relying on weak passwords
Publié: juin 14, 2017, 4:06pm CEST par Ian Barker
Despite moves towards other methods of verification, most enterprises are still using passwords to secure their systems. But based on results from its password assessment tool Preempt Inspector, behavioral firewall company Preempt shows that many enterprise users are still relying on compromised or poor quality passwords. The findings show that 7.34 percent of users have very weak passwords that have appeared in previous security breaches such as those of public cloud services. In addition 13.9 percent of users share passwords with others. Password quality issues beset 19.1 percent, meaning that there's the potential for around one in five enterprise passwords to… [Continue Reading] -

Intelligent chatbot helps boost endpoint security
Publié: juin 14, 2017, 3:33pm CEST par Ian Barker
It's vital to protect endpoints within the enterprise, but often the level of alerts generated by conventional solutions can prove overwhelming for security analysts. Cyber security platform Endgame is introducing new features to simplify attack detection, threat hunting, and response, including the use of an intelligent chatbot. Called Artemis, the bot employs natural language understanding (NLU) to allow users of any skill level to ask simple yet powerful questions and receive the definitive answers required to stop targeted attacks before data theft or damage occurs. Endgame's NLU engine combines machine learning with security domain expertise to identify analyst intent and guide… [Continue Reading] -

SailPoint brings AI to identity management
Publié: juin 14, 2017, 2:51pm CEST par Ian Barker
Enterprise identity management company SailPoint is using the Navigate '17 event to preview its new identity analytics solution, IdentityAI. By adding analytics to SailPoint's existing open identity platform it will enable customers to improve their identity governance and mitigate potential threats. The new platform will allow organizations to manage risk by detecting and alerting on anomalous behaviors and potential threats, using artificial intelligence technology to perform peer group analysis, behavioral pattern matching and statistical analysis. The machine learning engine is able to scan massive amounts of identity data to identify risks without having to rely on teams of security experts.… [Continue Reading] -

AI-driven platform improves sales forecasts and visibility
Publié: juin 13, 2017, 4:19pm CEST par Ian Barker
Success in a sales environment increasingly needs access to accurate real-time data on which to base decisions. To provide companies with better information, sales forecasting specialist Aviso is launching its latest Aviso Sales Vision, an AI-based platform that provides accurate sales forecasts, detailed pipeline visibility, and actionable insights to drive sales performance. Sales Vision works with Salesforce, Microsoft Dynamics CRM, and other data sources. It delivers AI-driven visibility into pipeline health, forecast changes, and sales performance from a PC or mobile device. It provides multi-dimensional sales forecasts and insights, making it easy to pinpoint deals and identify trends that will… [Continue Reading] -

New platform helps integrate big data across the cloud
Publié: juin 13, 2017, 3:30pm CEST par Ian Barker
As enterprises continue to move their data to the cloud, they often find themselves using multiple different services. But a multi-cloud approach brings problems when it comes to managing and integrating information. To tackle this issue, cloud and big data integration company Talend is releasing a new version of its Talend Data Fabric integration platform that is optimized to manage multi-cloud, enterprise IT environments. Talend Summer '17 helps businesses seamlessly manage information across AWS, Microsoft Azure, Google, Snowflake and Cloudera platforms. This means customers can integrate, cleanse and analyze data to drive innovation and gain a competitive edge, while reducing… [Continue Reading] -

Enterprises overwhelmed by endpoint alerts
Publié: juin 13, 2017, 2:56pm CEST par Ian Barker
Organizations receive an average of more than 600 endpoint alerts in a typical week according to a new report. These represent a severe drain on an organization's financial resources and IT security personnel and the cost can average $1.4 million annually. The study by endpoint security company Absolute and the Ponemon Institute reveals that, of all alerts, 45 percent (277 alerts) are considered reliable and an average of 115 are investigated. An average of 61 percent or 369 of these alerts involve malware infections. The study also shows that organizations are finding it increasingly difficult to identify off-line or 'dark'… [Continue Reading] -

Malicious antivirus apps prey on ransomware fears
Publié: juin 13, 2017, 12:02pm CEST par Ian Barker
Recent weeks have seen a rise in fake WannaCry protectors on mobile app stores, even though this particular infection doesn't target mobile devices. But using the fear of high profile infections to get users to download potentially unwanted programs or malware is nothing new according to threat management company RiskIQ. Using its mobile database, hundreds of examples of apps that claim to help defend mobile phones were found, instead, to be preying on unsuspecting users by pushing adware, trojans, and other malware. Using a title search for 'antivirus' resulted in 6,295 total apps, past and present, claiming to either be an… [Continue Reading] -

Collaboration cloud services lead to a rise in data violations
Publié: juin 13, 2017, 11:05am CEST par Ian Barker
Almost 10 percent of data loss prevention (DLP) violations come from collaboration services according to a new report. The study from cloud security company Netskope shows that as cloud services like HipChat and Slack have increased in popularity enterprises need to put policies in place to protect the information that’s shared. "Collaboration services are quickly displacing more traditional ways of communication and collaboration like email, and with that means that more data is being shared inside of those services," says Sanjay Beri, founder and CEO, Netskope. "It's critical that organizations implement solutions that afford real-time visibility and control, data loss… [Continue Reading] -

Microsoft integrates with Zimperium to guard against zero-day mobile threats
Publié: juin 12, 2017, 3:15pm CEST par Ian Barker
Cyber attacks aren't limited to desktop systems, mobile endpoints are equally at risk and for enterprises this is something else that needs protection. Mobile threat defense specialist Zimperium is announcing an integration with Microsoft Enterprise Mobility + Security to integrate its product with the Microsoft Intune mobile device and application management product. Zimperium's on-device detection protects users in real-time, without the delays and limitations of cloud-based detection, and then provides threat intelligence directly to Microsoft Intune. The integration adds the capability to control access to corporate resources and data based on comprehensive analysis. Andrew Conway, general manager of product marketing… [Continue Reading] -

Patch management is a major issue for enterprises
Publié: juin 9, 2017, 3:04pm CEST par Ian Barker
We already know that outdated systems are a major problem for enterprises as they increase the risk of data breaches. But a new study by enterprise security specialist Bromium reveals that the act of patching is a big problem for many companies too. The study of over 500 CISO in companies with more than 1,000 employees, shows over half (53 percent) of CISOs say crisis patch management is a major disruption to their IT and security teams. Enterprises have to issue an emergency patch an average of five times a month, with each crisis patch taking an average of 13… [Continue Reading] -

New Android malware uses code injection to control devices
Publié: juin 9, 2017, 12:20pm CEST par Ian Barker
Researchers at Kaspersky Lab have released details of a new trojan being distributed via the Google Play store that is able to inject malicious code into the system runtime libraries. Named Dvmap, the trojan is believed to have been downloaded from Google Play more than 50,000 times since March this year. The addition of code injection makes a worrying new development in mobile malware. It means it becomes possible to execute malicious modules even with root access deleted. In addition any security solutions and banking apps with root-detection features that are installed after infection won’t be able to spot the… [Continue Reading] -

Majority of vulnerabilities appear online before official databases
Publié: juin 7, 2017, 4:24pm CEST par Ian Barker
New research from threat intelligence company Recorded Future reveals that of 12,500 disclosed Common Vulnerabilities and Exposures (CVEs), more than 75 percent were publicly reported online before they were published to the NIST's centralized National Vulnerability Database (NVD). Sources reporting include easily accessible sites such as news media, blogs, and social media pages as well as more remote areas of the internet including the dark web and criminal forums. This disparity between the unofficial and official communication of CVEs is placing a greater onus on CISOs and security teams, leaving them open to potential exploits and unable to make strategic… [Continue Reading] -

Healthcare industry most targeted by cyber attacks
Publié: juin 7, 2017, 11:56am CEST par Ian Barker
A new report into cyber security trends shows healthcare to be the most frequently targeted industry, with 164 threats detected per 1,000 host devices. Next most targeted are education and media, which had 145 and 123 detections per 1,000 host devices, respectively. By comparison, the food and beverage industry came in as the least targeted industry with just 17 detections per 1,000 hosts. The study from Vectra Networks revealed at this week's Infosecurity Europe event also reveals that attack rates are increasing with the average number of reconnaissance, lateral movement and exfiltration detections all up by more than 265 percent.… [Continue Reading] -

Cloud developer platform launches free firewall protection
Publié: juin 6, 2017, 5:16pm CEST par Ian Barker
DigitalOcean, the cloud platform for software developers is launching a free Cloud Firewalls service to reduce the potential attack surface. Developers can deploy the service quickly without installing or configuring any software, and are able to define what ports are visible on their cloud servers -- known as Droplets -- to minimize risk. "We are committed to helping developers build great software. This includes offering a simple and automated way to secure their infrastructure," says Julia Austin, CTO of DigitalOcean. "Teams of engineers depend on DigitalOcean to stay true to our commitment to simplicity, and Cloud Firewalls ensures they can… [Continue Reading] -

Globalscape delivers stronger data governance and improved visibility
Publié: juin 6, 2017, 4:43pm CEST par Ian Barker
With businesses under pressure to secure their data and control who accesses it, there’s increased demand for visibility into where information is going. Information security company Globalscape is launching a a new reporting platform called EFT Insight. This uses a combination of business and operational intelligence to ensure information exchanges are functioning properly and securely, alerting network administrators to any conditions that could compromise security or violate service level agreements. It gives users the ability to gather and analyze data and to view trends over time for business and operational intelligence purposes. They can investigate issues with granularity or drill… [Continue Reading] -

New file system brings added security to the public cloud
Publié: juin 6, 2017, 2:59pm CEST par Ian Barker
With growing numbers of data breaches and increasing pressure from regulations like GDPR, companies need to enact stricter security policies. Object and cloud storage specialist Scality is addressing this with the launch of Scality RING7, a new software-defined, multi-site file system and object storage solution. Scality RING7 allows concurrent user access across sites and parallel writers to increase throughput. It also seamlessly unites the worlds of file and object data, enabling users to access the same data from either file or object protocols. It features data encryption, Write Once Read Many (WORM) change control, data-restorative versioning, extended location control for… [Continue Reading] -

Workplace stress driven by AI and pressure to master new skills
Publié: juin 6, 2017, 12:45pm CEST par Ian Barker
Stress at work is on the rise and it’s driven by factors both inside and outside the workplace according to a new study of 1,000 US office staff. The report by online learning company Udemy reveals the number one stress factor outside of work is the current political climate (50 percent), while inside it's the fear of losing jobs to AI or new technology (43 percent). Of those surveyed, 52 percent say they feel more stressed today than they did one year ago, and 23 percent believe their work stress has increased significantly over the past year. 60 percent of… [Continue Reading] -

Predictive breach-risk platform helps enterprises stay secure
Publié: juin 6, 2017, 12:17pm CEST par Ian Barker
Companies face the possibility of security breaches from many different sources, which means they must constantly react to new threats. New player in the security field Balbix aims to put security professionals ahead of the game with the launch of its predictive breach-risk platform. It can be used to predict top breach scenarios, prioritize security fixes and provide risk insights to prevent security incidents before attacks happen. The platform makes use of predictive analytics and AI to automatically measure breach risk. Specialized sensors deployed across the enterprise continuously discover and monitor all devices, apps and users across hundreds of attack… [Continue Reading] -

DevOps automation boosts performance
Publié: juin 6, 2017, 11:06am CEST par Ian Barker
The highest performing organizations have automated 72 percent of all configuration management processes. And those same high performers spend much less time (28 percent) in manual configuration processes that stall innovation and deployments. In comparison, low performers are spending almost half of their time (46 percent) on manual configuration. These are among the findings of the latest State of DevOps Report by Puppet Labs, which surveyed 3,200 respondents from organizations of all sizes and across multiple industries. For the first time, the report also considered leadership types and how they affect performance. The results show that high-performing teams have leaders… [Continue Reading] -

How to protect your company from third-party data breaches
Publié: juin 5, 2017, 5:42pm CEST par Ian Barker
It's becoming increasingly clear that data breaches can happen to any company and at pretty much any time. Protecting your company's data isn't just about securing your own systems, it also means ensuring that any third-parties you contract out services too are taking appropriate care too. Mailing and document management company United Mail has put together an infographic focusing on how to combat a breaches by using best practices and how to decide which third-parties can be trusted. The graphic reveals the average cost per record of a breach in various industries. These range from $335 in healthcare to $80… [Continue Reading] -

App developers want better feedback during coding and debugging
Publié: juin 2, 2017, 3:37pm CEST par Ian Barker
The ability of developers to do their jobs effectively is crucial to delivering reliable apps on time. App development company Perfecto has released the results of a new survey which asked developers how they focus their resources. Among the findings are that 50 percent of user interface and user experience developers want better feedback during the coding and debugging process. Less than 25 percent say they actually get the timely feedback they need. It also finds that the average developer spends less than 50 percent of their time writing code. While high-performing dev teams do not spend any more or… [Continue Reading] -

Major UK companies at risk of breaking key GDPR principle on collecting PII
Publié: juin 1, 2017, 4:33pm CEST par Ian Barker
New research shows that more than a third of all public web pages of FTSE 30 companies capturing personally identifiable information (PII) are in danger of violating the GDPR regulations by doing so insecurely. The FTSE 30 is made up of the 30 most influential companies listed on the London Stock Exchange. The study by RiskIQ looking at the sites of these organizations finds that more controls on outward facing web assets are needed. The study found 13,194 pages on sites owned by these companies that collect PII, an average of 440 pages per organization. Of these, 34 percent of… [Continue Reading] -

Healthcare sector accounts for 43 percent of all UK data breaches
Publié: juin 1, 2017, 3:43pm CEST par Ian Barker
Data security services company Egress has released data from the UK's Information Commissioner's Office (ICO) which shows that the health sector accounts for nearly half (43 percent) of all data breaches. It also shows that human error, rather than external threats, is the main cause of incidents across every sector. Staff mistakes accounted for 49 percent of all breach incidents in the last quarter of 2016. UK healthcare organisations suffered 2,447 data breaches between January 2014 and December 2016. This is almost four times more than the second highest sector (local government). The number of incidents is also rising, with… [Continue Reading] -

IT analytics platform uses machine learning to improve VMware efficiency
Publié: mai 31, 2017, 5:11pm CEST par Ian Barker
Maintaining performance of business systems is essential, particularly as more applications move to virtual environments. IT analytics specialist SIOS Technology is expanding the capabilities of its SIOS iQ platform to optimize VMware environments. A new flexible, API-driven integration architecture enables SIOS iQ to integrate data from a range of sources. These include application monitoring tools and data aggregation systems such as Splunk, Hadoop and Elasticsearch. By providing a more comprehensive view of the IT infrastructure, SIOS iQ empowers IT to automatically and quickly identify and correct the root causes of application performance issues, and to predict future application performance. "The… [Continue Reading] -

Cloud-native controller streamlines web app delivery
Publié: mai 31, 2017, 4:08pm CEST par Ian Barker
Getting the best performance, and thus return on investment from their app projects is essential for an increasing number of organizations. But in traditional delivery models the optimization layer is either separate from the application servers in the form of a content delivery network (CDN), or requires constant manual management and operation. Web application control specialist Webscale is launching a cloud application delivery controller (ADC) for web applications that delivers access to essential, real-time capabilities for application performance, availability, and security. "In our core markets of e-commerce, e-learning, and financial services, where application delivery is mission-critical, customers' needs vary dramatically,"… [Continue Reading] -

Majority of CEOs are not engaging with social media
Publié: mai 31, 2017, 3:57pm CEST par Ian Barker
A new study into the social media habits of Fortune 500 CEOs reveals that only 40 percent were active on one of the six major social networks (Twitter, Facebook, Google+, Instagram, LinkedIn and YouTube) in 2016. The study from business cloud platform Domo and CEO.com also shows that despite 75 chief executive changes occurring in this group in 2016 there's been no significant impact on social media use. Only 40 Fortune 500 CEOs (eight percent) have a Facebook page, down from 57 in 2015. Of those, 32 were inactive for the last quarter of 2016. LinkedIn, which was acquired for $26.2… [Continue Reading] -

Unsecured IoT devices pose major security risk
Publié: mai 31, 2017, 1:31pm CEST par Ian Barker
New research from the Ponemon Institute and risk assurance body Shared Assesments reveals a high level of concern among organizations about the security of IoT, yet a gap in understanding of how to mitigate and communicate the risks, especially as it relates to third parties. The study of 553 individuals in industries such as financial services and healthcare reveals that 76 percent say a DDoS attack involving an unsecured IoT device is likely to occur within the next two years. In addition, 94 percent of those surveyed say that a security incident related to unsecured IoT devices or applications could… [Continue Reading] -

MicroStrategy enterprise analytics platform comes to AWS
Publié: mai 30, 2017, 4:24pm CEST par Ian Barker
Businesses are collecting more information than ever before, and they need a reliable and accessible way of analyzing it. Enterprise analytics specialist MicroStrategy is making its business intelligence platform available on AWS, giving users an on-demand solution that can be up and running fast. What it's offering is a version of its MicroStrategy 10 platform built specifically for deployment on AWS. It includes a provisioning portal for administrators to create and deploy dedicated cloud environments with MicroStrategy 10 on to AWS infrastructure. Administrative tools deliver automation and scheduling of routine tasks, making it easy to start, stop, resize, and terminate… [Continue Reading] -

Judy malware could affect over 36 million Android devices
Publié: mai 30, 2017, 3:17pm CEST par Ian Barker
Millions of Android devices could have been affected by a new auto-clicking adware program found in apps developed by a Korean company. Uncovered last week by security company Check Point malicious apps included a series of casual cooking and fashion games under the 'Judy' brand. They were able to evade the Play store's screening checks because the malware payload is downloaded from a non-Google server after the programs are installed. The code then uses the infected phone to click on Google ads, generating fraudulent revenue for the attacker. Once notified by Check Point, Google removed the apps. The apps have seen… [Continue Reading] -

WannaCry was most Americans’ first experience of ransomware
Publié: mai 26, 2017, 3:54pm CEST par Ian Barker
Although ransomware in some form has been around since 2005, a new survey of 5,000 US consumers reveals that for 57 percent the recent WannaCry attack was their first exposure to how it works. The study by endpoint security company Carbon Black also shows that seven out of 10 consumers would consider leaving a business if it were hit by ransomware. Financial institutions and healthcare providers are most trusted to keep data safe (70 percent), but only half (52 percent) trust retailers. This is slightly at odds with trends which show the financial services sector was the most attacked industry… [Continue Reading] -

Dynamically generated whitelists help stop hackers
Publié: mai 26, 2017, 1:11pm CEST par Ian Barker
Whitelists have traditionally been used as a way of limiting what users can do, but they're time consuming to maintain and keep up to date. Florida-based Terra Privacy is addressing this with a system where destinations are continually inserted and removed from the whitelist in real-time, in concert with the user's activities. Hacker Deterrent Pro's system provides effective protection against browser-injected trojans. It uses a Transient Whitelist that only contains the addresses of open webpages and their declared additional connections. All other browser traffic remains blocked. This means browser-injected trojans are blocked from connecting to their command and control servers.… [Continue Reading] -

83 percent of security staff waste time fixing other IT problems
Publié: mai 25, 2017, 5:13pm CEST par Ian Barker
A new survey of security professionals reveals that 83 percent say colleagues in other departments turn to them to fix personal computer problems. The study by security management company FireMon shows a further 80 percent say this is taking up more than an hour of their working week, which in a year could equate to more than $88,000. For organizations, eight percent of professionals surveyed helping colleagues out five hours a week or more could be costing over $400,000. Organizations are potentially paying qualified security professionals salaries upwards of $100,000 a year and seeing up to 12.5 percent of that… [Continue Reading] -

One year from GDPR, organizations are struggling to get compliant by the deadline
Publié: mai 25, 2017, 11:50am CEST par Ian Barker
The EU General Data Protection Regulation (GDPR) comes into force on May 25th 2018, but a new survey by data protection company Varonis shows companies are struggling to meet the deadline and are pessimistic about its effects. The results from 500 IT decision makers in the UK, Germany, France and the US, reveal that 75 percent of organizations say they will struggle to be ready for the deadline. In addition 42 percent say that it's not a priority for their businesses, despite the threat of fines which could cost companies up to four percent of global turnover or €20 million… [Continue Reading] -

New digital assistant answers data-related questions
Publié: mai 24, 2017, 5:18pm CEST par Ian Barker
In our private lives we're used to getting answers quickly from digital assistants. So far though this is something that hasn't really taken off in business environments. That could be about to change as data search specialist Knoema launches Yodatai, a bot that's designed to answer data-related questions. Working with public data as well as internal business intelligence data, Yodatai's AI interface works with existing chat platforms Slack, Facebook Messenger, and Skype. Users can instantly get answers to questions regarding both public data on markets and industries, as well as private corporate data, without leaving their messaging tool. "Companies can now easily get… [Continue Reading] -

HP software helps turn old PCs into thin clients
Publié: mai 24, 2017, 4:14pm CEST par Ian Barker
As software moves towards the cloud, many companies are opting for thin client architecture on the desktop. But this involves an investment in new hardware that may strain restricted budgets. HP has used this week's Citrix Synergy event to launch its Thin Client Conversion Suite, allowing old PCs to be turned into a thin client solution at low cost. The solution supports a wide variety of backend systems while maintaining the existing OS, reducing risk, and lowering costs for training and hardware. For IT administrators, the software provides the peace-of-mind that comes with the ability to confidently secure and control… [Continue Reading] -

Kaspersky launches Threat Intelligence Portal for businesses
Publié: mai 24, 2017, 3:11pm CEST par Ian Barker
Companies have to deal with an increasing number of cyber threats. To allow them to stay in touch with this ever evolving landscape they need up to date intelligence. With the launch of its Threat Intelligence Portal, Kaspersky Lab is enabling security operation center operators to be able to work more efficiently while facing hundreds and thousands of threat alerts. The portal will give enterprises immediate access to both the very latest and historical threat intelligence to help them combat cyber-attacks before they impact their organization. This will help improve incident response times and forensic capabilities by giving security teams… [Continue Reading] -

Credential stuffing tools help hackers break into accounts
Publié: mai 24, 2017, 12:23pm CEST par Ian Barker
With thousands of stolen account details available for sale on the web, cyber criminals are turning to new methods using them efficiently to try to break into accounts. According to a new report by risk analysis specialist Digital Shadows, 'credential stuffing' tools are the latest technique being used to automate attempts at account takeover. Credential stuffing -- not as you might think the latest alternative to sage and onion -- is a type of brute force attack where large sets of credentials can be automatically inserted into login pages until a match with an existing account is found. The most… [Continue Reading] -

Emails beat social media in the battle for consumer engagement
Publié: mai 23, 2017, 4:39pm CEST par Ian Barker
It's easy to believe that marketing to younger generations would be best conducted via social media, but a new survey shows that email is still a more effective tool. The study from email marketing brand Campaigner looks at the preferences of online shoppers and revealed insights into how to most effectively market to different consumer generations. Despite social media's large and growing presence in many consumers’ lives, the survey reveals that it isn’t the ideal platform for brand interaction. In fact, less than a quarter (24 percent) of online shoppers in general name social media as one of their preferred channels… [Continue Reading] -

New open source database designed for enterprise users
Publié: mai 23, 2017, 3:55pm CEST par Ian Barker
Businesses are looking for database technology that increases their agility, scalability, security, and supports a range of different use cases, at the same time keeping down costs. On the other hand developers want a database that is open and extensible, and lets them easily develop many different types of application. Open source specialist MariaDB Corporation is looking to meet these conflicting demands with MariaDB TX 2.0, an open source transactional database solution for modern application development. "For too long, there has been a gap between the high-cost functionality of proprietary databases, and the affordable, modern architectures of open source databases,"… [Continue Reading] -

New software adds secure authentication to any enterprise application
Publié: mai 23, 2017, 12:32pm CEST par Ian Barker
Increased numbers of phishing and other cyber attacks are putting companies under greater pressure to secure their applications. Conventionally this requires re-coding or other work to achieve, but new software from behavioral firewall specialist Preempt lets organizations add secure authentication to any enterprise application. The software, called Any App, is vendor agnostic and allows customers to obtain more value out of their existing investments in multi-factor authentication (MFA) solutions such as SecureAuth, Duo and Google Authenticator. Preempt builds secure authentication at the network layer and works for both Windows and Linux environments. When a user first connects to an application,… [Continue Reading] -

Phishers cash in on WannaCry attack
Publié: mai 23, 2017, 11:14am CEST par Ian Barker
The UK's ActionFraud cyber crime reporting center is warning customers of BT’s internet services of a phishing scam claiming to protect against WannaCry-style attacks. The emails claim that BT has launched preventative measures to protect data on an international scale and try to get recipients to click on a link to a 'security upgrade'. The attack uses convincing-looking branding and domain names which appear very similar to genuine BT addresses and so could catch out the unwary who are concerned about the security of their data after the global attack. Mike Wyatt, threat researcher at threat management company RiskIQ says,… [Continue Reading] -

Digital assistants set to outnumber people by 2021
Publié: mai 19, 2017, 12:50pm CEST par Ian Barker
The number of digital assistants installed is on track to exceed 7.5 billion by 2012, which is more than the world population. According to technology research company Ovum, Google Assistant will dominate the voice AI–capable device market with 23.3 percent market share, followed by Samsung's Bixby (14.5 percent), Apple's Siri (13.1 percent), Amazon's Alexa (3.9 percent), and Microsoft's Cortana (2.3 percent). Ovum's study finds that smartphones and tablets are leading the market for voice AI, with 3.5 billion active devices in 2016, most of which use Google Now and Apple Siri. However, the use of AI in conjunction with other… [Continue Reading] -

Cyber crime is a $6 trillion a year industry
Publié: mai 19, 2017, 11:42am CEST par Ian Barker
Last week's WannaCrypt attack infected over 200,000 devices and is estimated to have made its perpetrators $72,000. Increasingly scammers and criminals are seeing the internet as a means of making financial returns. Cyber crime has become a serious business and no business or information is safe from attack. Threat detection company Pwnie Express has produced an infographic analyzing the cyber crime industry. Among the highlights are that more than 159 million records containing sensitive information were compromised in 2015. Over 300 million new pieces of malware were released in 2014, and 60 percent of small businesses cease operating six months… [Continue Reading] -

New free plugin filters bot data from Google Analytics
Publié: mai 18, 2017, 3:21pm CEST par Ian Barker
Google's own bot filtering catches only a small percentage of the bot traffic that hits most sites, leading to traffic analysis data being skewed. Bot detection specialist Distil Networks is launching a free tool designed to remove the bad data created by bots. Bots can be used by competitors, hackers and fraudsters and are the key culprits behind web scraping, brute force attacks, competitive data mining, online fraud, account hijacking, data theft, spam, digital ad fraud and downtime. "Bot activity is so prevalent today, that if you run a website of any shape or size, there is a good chance… [Continue Reading] -

European political parties left open to email-based cyber attacks
Publié: mai 18, 2017, 12:58pm CEST par Ian Barker
None of the political parties in the UK, Germany and Norway, all of whom have upcoming elections, have email authentication or protection against spear phishing in place, according to new research. The study by secure email company Agari shows that while eight percent have published an email authentication policy, they've left the door wide open by setting their policy to 'none', which will not stop malicious emails from reaching intended victims. This lack of security is leaving voters, supporters and the parties themselves wide open to targeted email attacks using identity deception and social engineering methods. As demonstrated in the… [Continue Reading] -

Are your devices listening to you?
Publié: mai 18, 2017, 12:17pm CEST par Ian Barker
Increasingly we're surrounded by devices that have microphones. Not just our computers and smartphones, but smart home devices like Alexa and Echo and even our TVs. The problem is these mics are not just accepting commands, they're listening to what's going on in the background too. Panda Security has put together an infographic that looks at what devices might be listening in to our conversations and what steps we can take to protect ourselves. Among its findings are that 88 percent of Americans say it's important that they not have someone watch or listen to them without their permission, and… [Continue Reading] -

Updated EnCase software enhances endpoint protection
Publié: mai 16, 2017, 4:21pm CEST par Ian Barker
The weakest point in any network is usually the endpoint, so effective protection measures are essential to fend off cyber attacks. Security specialist Guidance Software is launching an updated version of its EnCase Endpoint Security solution aimed at providing enhanced endpoint detection and response (EDR) capabilities for businesses. EnCase Endpoint Security Version 6 provides conditional detection and embedded threat intelligence with a focus on automation. It allows users to more rapidly detect hidden threats before they lead to a breach. It also has integrated threat intelligence which adds a deeper layer of context to security alerts, this includes numeric threat… [Continue Reading] -

Huddle simplifies bulk document collection
Publié: mai 16, 2017, 3:07pm CEST par Ian Barker
In any organization teams often waste valuable time requesting, tracking and chasing documents. In the process they can run up against file size and mailbox limitations as well as trying to track who holds and has sent which files. To help with all this, collaboration specialist Huddle is launching a new File Request feature designed to make the collection of files more secure, and up to 80 percent more efficient. File requests can be created from within Huddle, adding one or more assignees, specifying the upload location and setting a due date. Requests for multiple files (up to 500 per… [Continue Reading] -

Cray partnership delivers supercomputing-as-a-service
Publié: mai 16, 2017, 12:56pm CEST par Ian Barker
The latest generation of supercomputers are able to deliver unparalleled processing power, but their cost puts them beyond the reach of many businesses and researchers. A new partnership between cloud computing and data center specialist Markley and leading supercomputer brand Cray is offering supercomputing-as-a-service to make it easier and more affordable for research scientists, data scientists, and IT executives to access dedicated, powerful computing and analytic capability. "The need for supercomputers has never been greater," says Patrick W. Gilmore, chief technology officer at Markley. "For the life sciences industry especially, speed to market is critical. By making supercomputing and big… [Continue Reading] -

Is WannaCry linked to the Lazarus Group?
Publié: mai 16, 2017, 12:02pm CEST par Ian Barker
As last Friday's WannaCry (WannaCrypt) ransomware attack continues to cause ripples around the globe, links have emerged between the malware code and the infamous Lazarus Group. Lazarus is the group responsible for attacks on the Bangladesh Central Bank last year, Sony Pictures Entertainment in 2014, and more financial attacks in at least 18 countries. Yesterday, a Google researcher, Neel Mehta, posted a code sample on Twitter that hints at a similarity between WannaCrypt and malware samples used by Lazarus in 2015. Researchers at Kaspersky Lab's GReAT team analyzed the information and identified and confirmed clear code similarities between the malware samples. However,… [Continue Reading] -

Three out of five companies expect to be breached in 2017
Publié: mai 16, 2017, 11:08am CEST par Ian Barker
As cyber attacks and security breaches continue to make the headlines, a new study suggests that three out of five companies expect to suffer a breach this year. The latest Market Pulse survey from identity management company SailPoint also reveals that 33 percent believe they may not even know they’ve been breached. Of the 67 percent who reported being breached in 2016, the average material impact to the business was $4 million. The survey also finds that 51 percent of companies suffered two or more breaches in the last twelve months. The study also looked at areas of risk and… [Continue Reading] -

OS vulnerabilities up -- Patches down
Publié: mai 15, 2017, 4:20pm CEST par Ian Barker
If the WannaCrypt ransomware attack of the last few days has taught us anything it should be the importance of patching systems to guard against attack. Yet a study released today suggests the message isn't getting through. The latest US country report from Flexera Software reveals the percentage of US PC users with unpatched Windows operating systems was 9.8 percent in Q1, 2017, up from 7.5 percent last quarter and 6.5 percent in Q1, 2016. The percentage of vulnerabilities originating in operating systems in the US was 36 percent in Q1, up from 33 percent in Q4, 2016 and 21… [Continue Reading] -

The WannaCrypt attack -- what we know and how to protect yourself
Publié: mai 15, 2017, 3:31pm CEST par Ian Barker
What seemed to have begun as just another ransomware attack hit the headlines last Friday (May 12th) when it began to attack hospitals and healthcare services in the UK. It became clear pretty quickly that this was in fact something much bigger however, with problems reported at businesses and government bodies around the world. Infections by the malware known as WannaCrypt or WannaCry, began in Spain with the Telefonica telecommunications giant one of the first to be hit. It then quickly spread to the United Kingdom, Russia, Japan, Taiwan, the United States, and many others. In total, over 150 countries… [Continue Reading] -

NHS hospitals hit by ransomware attack [Update: Now spreading globally]
Publié: mai 12, 2017, 5:21pm CEST par Ian Barker
Hospitals and doctors' surgeries across the UK have been hit by what is being described as a large scale ransomware attack. The attack is believedto have begun at around 1:30 pm today. Areas affected include East and North Hertfordshire, North Cumbria, Blackpool, and Barts Health in London. Computers in some hospitals and other centers have been taken offline as a precaution. Patients are being advised to avoid attending A&E departments and GP surgeries 'unless absolutely necessary' and should instead call the 111 telephone service for triage and medical advice or 999 in emergencies. Existing patient appointments are being honored but… [Continue Reading] -

Is multi-cloud architecture just a fad? [Q&A]
Publié: mai 12, 2017, 11:16am CEST par Ian Barker
Enterprises often find themselves working with more than one cloud provider. This multi-cloud approach is a lot like hybrid cloud, yet many companies today may not consider this type of environment. If they have, they are more than likely wondering how to manage and govern the data held in separate clouds. They want to know how to find the best use of different architectures in a multi-cloud world. We spoke to Lief Morin, CEO of infrastructure solutions and managed services company Key Information Systems, to discuss what he's hearing from his clients on multi-cloud strategies and when organizations should skip this… [Continue Reading] -

British voters concerned about the impact of fake news on elections
Publié: mai 11, 2017, 3:12pm CEST par Ian Barker
With the UK's general election campaign now in full swing, a new study of 2,000 adults finds that 68 percent are concerned that fake news could influence the outcome. In addition, 26 percent are not confident in their ability to identify a fake story and a further 39 percent were unsure if they had ever seen one. This makes Facebook’s decision to publish tips on spotting fake news timely. The research by comparison site BroadbandGenie along with polling company OnePoll shows respondents believe the Conservatives would benefit the most from fake news, whilst Labour would be most negatively affected. The… [Continue Reading] -

Newsletter bombs are the new DDoS
Publié: mai 11, 2017, 12:03pm CEST par Ian Barker
So called 'newsletter bombs' are increasingly being sent to the publicly known email addresses of journalists, companies, and also dot-gov email addresses. These attacks send thousands of fake newsletter sign-up emails to targeted email addresses rendering the attacked mailbox useless. According to German secure email service Tutanota, which had its own main contact address targeted, these attacks are easy to execute because most newsletter sign-up forms have no protection against malicious bot sign-ups. "Being a secure email service, the irony of not being able to use our main mailbox was particularly depressing", says Matthias Pfau, co-founder and developer of Tutanota.… [Continue Reading] -

New app aims to streamline hospitality industry payments
Publié: mai 10, 2017, 6:19pm CEST par Ian Barker
Traditional payment systems can be somewhat cumbersome in a hospitality environment, leading to increased risk of fraudulent transactions or customers failing to pay. Payment platform Rooam is launching a new app that allows users to open and pay for restaurant and bar tabs from their smartphones. Initially introduced to bars and restaurants in the Washington D.C. area in October 2016, Rooam's technology platform has since been adopted by several major restaurant groups. It allows users to quickly pay for food and drinks directly from their smartphones, eliminating the need to wait or catch a staff member's attention. Guests mention they… [Continue Reading] -

Ransomware continues to dominate the cyber threat landscape
Publié: mai 10, 2017, 5:54pm CEST par Ian Barker
A new report from Panda Security's PandaLabs research arm reveals that real time attacks that involve direct interaction with the victim are on the rise. It also shows the increasing professionalism of cyber criminals. Highly specialized groups are forming in fields like the creation and distribution of malware and exploits. An example covered by PandaLabs is the RDPatcher attack, the purpose of which is to put the victim’s computer up for sale on the black market for use in a bot network. Ransomware is still lucrative too, estimated to have earned criminals over a billion dollars in 2016. Attacks in… [Continue Reading] -

Ransomware remains profitable as 47 percent fall victim to attacks
Publié: mai 9, 2017, 4:04pm CEST par Ian Barker
Ransomware is one of the most successful and profitable weapons in the cyber criminal's armory, partly because it leverages an old-fashioned crime in a new digital format. A new study by Barracuda Networks reveals that 92 percent of people surveyed are concerned about ransomware hitting their organization, and 47 percent of respondents have been a victim of ransomware themselves. Of those that were attacked, 59 percent were unable to identify the source of the ransomware. Of those that did identify the source, 76 percent found that it entered the organization through email. Most interesting are the results relating to SaaS… [Continue Reading] -

New solution aids forensic investigation of mobile devices
Publié: mai 9, 2017, 2:54pm CEST par Ian Barker
Whether it's due to a specific cyber attack, theft of data, or a wider criminal investigation, it's increasingly necessary to be able to capture evidence from mobile devices. Forensic investigation software specialist Guidance Software is launching a new version of its EnCase product aimed at safely gathering data from mobiles. EnCase Mobile Investigator allows corporate and law enforcement investigators to use the visibility of EnCase to collect and analyze data from all major smartphones, tablets, and many other mobile device types. "The number of mobile devices investigated each year has increased nearly tenfold over the past decade," says Ken Basore,… [Continue Reading] -

Comodo launches free enterprise threat analysis
Publié: mai 9, 2017, 1:37pm CEST par Ian Barker
Data breaches not only cost businesses money in the short term, they can cause long term reputational damage as stolen details turn up for sale in dark corners of the internet. Cyber security company Comodo is offering enterprises with more than 1,000 employees a free 'Company Threat Analysis' to determine if their sensitive information is for sale on the Dark Web and, if so, how to prevent compromises from happening again. It creates a personalized report to identify if an enterprise's information has been stolen and dive into how this data became available to cyber criminals in the first place… [Continue Reading] -

How secure operating systems can help protect endpoints [Q&A]
Publié: mai 8, 2017, 3:40pm CEST par Ian Barker
Endpoints are often the weakest links in any IT system, but protecting them effectively now means much more than simply guarding against malware. As businesses rely more on the cloud and on web-based applications, the endpoint provides a gateway that can be vulnerable to attack. Data security specialist Becrypt is taking an innovative approach with the use of a secure operating system to verify the integrity of devices. We spoke to Bernard Parsons, CEO of the company, to find out more. BN: What are the key areas that protection is now focusing on, is it mainly encryption? BP: Part of… [Continue Reading] -

More than half of people believe using spyware to snoop on family members is legal
Publié: mai 5, 2017, 2:51pm CEST par Ian Barker
A new study shows that 53 percent of people believe it's legal to install a program on a family member's phone to snoop on their activity. The survey of more than 2,000 people in the US and UK by software comparison service Comparitech.com also finds 57 percent would consider spying on their children's phone conversations and messages. "Spy apps can cost less than $100. While they're often officially marketed to private investigators, there's nothing stopping a spouse or parent from buying one," says Paul Bischoff, privacy advocate at Comparitech.com writing on the company’s blog. "Once purchased, the buyer can download… [Continue Reading] -

One in four banks struggle to identify customers online
Publié: mai 5, 2017, 11:53am CEST par Ian Barker
Around a quarter of banks are struggling to identify their customers when delivering digital and online banking services, according to Kaspersky Lab. The latest findings from its Financial Institutions Security Risks survey show that 38 percent of financial institutions surveyed confirm that balancing prevention techniques and customer convenience is one of their specific concerns. Growth in online and mobile banking means customers are not only becoming victims of financial fraud, but also a major entry point for attacks on banks' digital channels. According to the research, in 2016, 30 percent of banks suffered security incidents affecting banking services delivered via… [Continue Reading] -

'Fatboy' ransomware uses a location-based charging model
Publié: mai 5, 2017, 11:01am CEST par Ian Barker
A new ransomware-as-a-service product named 'Fatboy' has been advertised on Russian language forums. What makes it different is the way it uses a sliding scale to charge its victims. Threat intelligence company Recorded Future has revealed that Fatboy uses the Economist's Big Mac Index -- designed to explain exchange rates -- to ensure victims in areas with a higher cost of living will be charged more to decrypt their data. The business model is also interesting in that purchasers deal directly with the author of the malware and not through a third party as many other cyber criminals prefer. These partners… [Continue Reading] -

DDoS attacks could cost enterprises over $2.5 million in revenue
Publié: mai 4, 2017, 4:41pm CEST par Ian Barker
A new report from information services specialist Neustar looks at the frequency and cost of DDoS attacks and what is being done to counter the threat. In terms of revenue loss, three percent of organizations report average revenue loss of at least $250,000 per hour, with 51 percent taking at least three hours to detect an attack and 40 percent taking at least three hours to respond, that means an attack could cost over $2.5 million. Attacks are getting larger too, with 45 percent of DDoS attacks delivered at more than 10 gigabits per second (Gbps), and 15 percent of… [Continue Reading] -

Two-thirds of Americans think internet access is a privilege
Publié: mai 4, 2017, 3:21pm CEST par Ian Barker
President Trump's signing of bill overturning the FCC's planned internet privacy protections, allowing ISPs to track and sell consumers' online information to third parties with greater ease has generated a storm among privacy advocates. It also prompted AnchorFree, the company behind the Hotspot Shield VPN, to carry out a survey of over 2,000 US consumers to gauge sentiment toward the internet and privacy. Among key findings are that over two-thirds of Americans (68 percent) belive internet access is a privilege while only 32 percent think it's a human right. Of those that think access is a privilege, 42 percent say… [Continue Reading] -

Consumer tips for World Password Day
Publié: mai 4, 2017, 12:02pm CEST par Ian Barker
Almost everything has its own day these days and May 4th is -- along with all the Star Wars puns -- World Password Day. Cyber security firm Kaspersky Lab is keen to help people avoid common password problems and is calling for a standardization of password criteria. Tips for creating a good password include making it at least 15 characters long; combining letters, numbers and symbols; not using personal details that could be gleaned from your social media profiles; and making passwords unique for every account. If it's too hard to remember all of your passwords, use a password manager. If… [Continue Reading] -

Cyber squatters target UK bank domains
Publié: mai 3, 2017, 4:41pm CEST par Ian Barker
Part of the art of making a phishing attack successful is having a domain name that looks sufficiently similar to a legitimate one not to arouse suspicion in the target. Research by threat intelligence specialist DomainTools has uncovered over 300 registered domains using the names of five of the UK's top high street banks. Using its PhishEye tool, the company analyzed domains mimicking Barclays, HSBC, Natwest, Lloyd's and Standard Chartered. Addresses including hsbc-direct.com, barclaya.net, barclays-supports.com and lloydstsbs.com were all uncovered as being owned by third parties rather than the banks themselves. "Imitation has long been thought to be the sincerest… [Continue Reading] -

Healthcare breaches down following 2016 peak
Publié: mai 3, 2017, 3:39pm CEST par Ian Barker
Healthcare data breaches hit an all-time high in 2016 resulting in the records of almost 16.6 million Americans being exposed as a result of hacks, lost or stolen devices, and unauthorized disclosure. But the latest Healthcare Breach Report from data protection company Bitglass shows a sharp decline in breaches over the first quarter of 2017. Key findings of the report are that 328 US healthcare firms reported data breaches in 2016, up from 268 in 2015. However, the volume of leaked records fell in 2016, and is on track to fall further in 2017. Unauthorized disclosures are now the leading cause… [Continue Reading] -

Assembly line robots vulnerable to hacking
Publié: mai 3, 2017, 3:09pm CEST par Ian Barker
Industrial robots make many of the things that we use in our everyday lives, from cars to domestic appliances. If the world isn't to descend into chaos therefore, it's imperative that robots follow their programming. But a new report from the TrendLabs research arm of cyber security company Trend Micro reveals just how easily industrial robots can be hacked. The spread of the industrial Internet of Things makes these devices more vulnerable to hackers. While the robots themselves may not be inherently insecure, the controllers used to operate and program the machines are often connected to the internet, and those… [Continue Reading] -

Free tool allows Active Directory users to test for weak passwords
Publié: mai 2, 2017, 4:18pm CEST par Ian Barker
While security is still heavily reliant on passwords, they represent a target for hackers and weak or reused choices offer an easy way into systems. Security awareness training company KnowBe4 is releasing a free Weak Password Test (WPT) tool for organizations that use Active Directory, allowing them to check for multiple types of threats related to weak passwords. Checks carried out by the tool include looking for the most common passwords and dictionary passwords, finding passwords shared among multiple accounts, and identifying accounts with no requirement to regularly change the password. It can also find accounts that store passwords using… [Continue Reading] -

IBM ships malware infected flash drives to Storwize customers
Publié: mai 2, 2017, 3:44pm CEST par Ian Barker
IBM is warning customers of its Storwize hybrid enterprise storage solutions that it has accidentally sent out some malware infected USB sticks. Companies ordering the Storwize V3500, V3700 and V5000 Gen 1 flash storage solutions may have been sent the infected sticks. The malware is contained in the directory for the initialization tool and when the tool is run it gets copied to a temporary directory on the computer’s hard drive. The malware doesn't target the storage system itself and it doesn't run automatically but, if launched, it will try to infect the Windows system it's on and may download… [Continue Reading] -

New integration delivers improved security analytics for mainframe users
Publié: mai 2, 2017, 2:48pm CEST par Ian Barker
Many enterprises still rely on logs and data from a range of different security products to get a picture of user behavior, particularly where legacy mainframe systems are involved. A collaboration between data analytics company Syncsort and application audit specialist Compuware is aimed at improving an organization's ability to detect threats against critical mainframe data, correlate them with related information and events and satisfy compliance requirements. Compuware's Application Audit captures start-to-finish user session activity data in real time -- including all successful logins, session keyboard commands and menu selections, specific data browsed, and more. Syncsort Ironstream users can then receive… [Continue Reading] -

ESET launches free security awareness training
Publié: mai 1, 2017, 3:09pm CEST par Ian Barker
Cyber attacks are a big problem for businesses and since many of them are caused by human error training employees to spot the signs of an attack is vital. Yet many companies lack the resources to carry out the level of education needed, which is why security software company ESET is launching a new, free cyber security awareness training program. "It was concerning to hear about stories from our customers, like an IT manager who had to choose to either outfit their office with new printers or buy cybersecurity training videos," says Andrew Lee, CEO of ESET North America. "We… [Continue Reading] -

Security skills need to evolve to cope with cyber threats
Publié: avril 28, 2017, 12:39pm CEST par Ian Barker
Securing systems is essential, but many businesses continue to take a reactive approach to protection using dated tools and techniques. A new report by technology trade association CompTIA highlights the need for companies to adopt proactive measures to identify weak links before they are exploited, broaden the security skills of their technology professionals, and implement top to bottom security training throughout the organization. The study shows a shifting focus from defense to offense. In CompTIA's survey of business and technology executives at 350 US companies, 29 percent of firms say they are highly proactive in their security posture, emphasizing detection… [Continue Reading] -

34 percent of US government agencies have had data breaches in the last year
Publié: avril 27, 2017, 4:07pm CEST par Ian Barker
According to a new report from systems security specialist Thales e-Security and 451 Research, US federal agencies are facing threats caused by legacy systems, spending and staffing issues. 65 percent have experienced a data breach at some stage in the past with 34 percent having one in the last year. Almost all agencies (96 percent) consider themselves 'vulnerable', with half (48 percent) stating they are 'very' or 'extremely' vulnerable. This number is higher than any other US sector polled for the 2017 Data Threat Report. Pressures to adopt advanced technologies (cloud, Big Data, IoT, and containers) are only making the… [Continue Reading] -

New approach protects IoT devices via a secure network
Publié: avril 27, 2017, 3:49pm CEST par Ian Barker
Up to now the security model for protecting IoT devices has been similar to that used for PCs, relying on patches which need to be installed by the user. Now though internet security and performance company Cloudflare is launching a new service called Orbit which streamlines patching and adds an additional layer of security thanks to the use of a secure global network. Using Orbit, IoT manufacturers can restrict their devices so they only connect to the internet through Cloudflare's network. Then, if there is a security vulnerability, the IoT manufacturer can perform a 'virtual patch,' across all of their… [Continue Reading] -

Attackers shift away from file-based techniques
Publié: avril 27, 2017, 1:08pm CEST par Ian Barker
Cyber attack methods are becoming more sophisticated in order to bypass traditional file-scanning protection systems according to a new study. Endpoint protection specialist SentinelOne has used filtered data from more than one million SentinelOne Enterprise Platform agents deployed worldwide to carry out behavioral analysis of malware programs that bypassed firewalls and network controls to infect devices. This data has been used to create the company's first Enterprise Risk Index which focuses on three risk categories. These are, attacks from document-based files, largely associated with Microsoft Word or Adobe PDF, attacks detected from traditional portable executable-based files, and attacks detected only… [Continue Reading] -

Uncontrolled user access is a weak link in corporate governance
Publié: avril 27, 2017, 12:07pm CEST par Ian Barker
Correct handling of corporate data is important not just to guard against security threats and data breaches, but to avoid the risk of regulatory fines and lawsuits too. But a new report from secure erasing specialist Blancco Technology Group shows the two weakest links in a company's data governance program are uncontrolled user access to data (53 percent) and managing where data is stored (43 percent). Data protection and regulatory compliance are further complicated by the fact that organizations are often too lenient in allowing employees to transfer data both inside and outside their organizations. For instance, 69 percent of the… [Continue Reading] -

New developer kit helps secure IoT devices
Publié: avril 26, 2017, 5:11pm CEST par Ian Barker
The rapid growth in numbers of IoT devices has seen them become a favored attack route for cyber criminals. This has left companies looking for a way to integrate strong security into millions of devices. To address this problem, security platform Mocana is launching a new developer kit that provides businesses, who may not have deep cybersecurity or cryptography expertise, with a way to simplify the integration of hardware-based security features into IoT devices. The Mocana IoT Security Developer Kit (DevKit) includes Mocana’s IoT security software modules integrated with an Infineon Technologies OPTIGA TPM (Trusted Platform Module) chip on a… [Continue Reading] -

New platform uses behavioral science to cut cyber security risks
Publié: avril 26, 2017, 2:56pm CEST par Ian Barker
With the right training and knowledge, many cyber attacks can be avoided. Addressing this human aspect of security is the idea behind a new platform from British start-up CybSafe. Human error is a major cause of data breaches and security training needs to be able to positively change user behavior. Using intelligent software and proprietary analytics, CybSafe's cloud-based platform learns an individual's knowledge level and their behavior patterns to deliver a personalized e-learning program. Delivered through a mobile app or online, the GCHQ-accredited e-learning platform is aimed at saving businesses money, not just by reducing their risk of falling victim… [Continue Reading] -

Arcserve launches new email archiving technology for businesses
Publié: avril 26, 2017, 1:15pm CEST par Ian Barker
Businesses of all sizes are under increasing pressure to protect corporate email records and make them easily accessible for audits and legal discovery. Data protection and recovery specialist Arcserve has acquired email archiving technology FastArchiver and is making it available through its Arcserve UDP solution portfolio. UDP Archiving efficiently stores archived on-premise, public or private cloud email in a location independent of the primary mail system. It allows businesses to reduce the risk of email service outages or malfunctions, and access archive email 24/7, plus meet legal requirements with features like full text search, tagging, hit highlighting, save search, search… [Continue Reading] -

77 percent of British consumers have worries about new payment methods
Publié: avril 26, 2017, 12:48pm CEST par Ian Barker
This week South Korea takes the first steps towards becoming a coinless society as shoppers will be handed pre-paid cards instead of change in a country-wide trial. If the trial is successful, bank officials will allow change to be transferred straight into the shoppers' bank accounts by next year. But a new report from global law firm Paul Hastings shows that security fears are preventing many British consumers embracing new payment technologies. The study of over 2,000 consumers finds 77 percent are worried about using new payment methods. The risk of fraud is cited as the main reason (59 percent)… [Continue Reading] -

How deception-based technology is turning the tables on hackers [Q&A]
Publié: avril 26, 2017, 11:18am CEST par Ian Barker
Cyber attacks are constantly evolving and consequently businesses are always seeking new ways of defending themselves. This is as much about understanding the nature of attacks as about preventing them. One of the latest developments is the use of deception, employing camouflaged traps and tokens to throw the attackers off balance by detecting and understanding the nature of the attack and their plans. We spoke to Kev Eley, VP at TrapX to find out how a new approach to security, based on deception techniques, is helping organizations to turn the tables on attackers. BN: What is deception-based technology and how… [Continue Reading] -

Overexposure of data leaves organizations at risk
Publié: avril 25, 2017, 3:26pm CEST par Ian Barker
Excessive employee permissions are exposing organizations to insider threats, ransomware and other risks according to the findings of a new report. Using its Data Security Platform, threat prevention specialist Varonis conducted over a thousand risk assessments for customers and potential customers on a subset of their file systems totaling over 236 million files and 3.79 petabytes of data. The study reveals that 47 percent of organizations have at least 1,000 sensitive files open to every employee, while 22 percent have 12,000 or more sensitive files exposed to every employee. An average of 20 percent of folders in all organizations are… [Continue Reading] -

Firms worldwide say GDPR could harm their business
Publié: avril 25, 2017, 1:00pm CEST par Ian Barker
With implementation of the EU's General Data protection Regulation less than a year away, a new study reveals that many firms are worried about the effect it could have on their bottom line. The survey from information management company Veritas shows 38 percent of companies think they could lose customers or go out of business as a result of non-compliance. UK firms are expected to spend $1.4 million on GDPR compliance by 2018, but only 37 percent are ready now. These concerns aren't confined to the UK, the survey talked to 900 decision makers in eight countries, and finds that… [Continue Reading] -

68 percent of consumers think brands put personal data at risk
Publié: avril 25, 2017, 11:42am CEST par Ian Barker
Customers are coming to expect a more personalized service, but that means exposing more of their information to businesses. But a new survey from identity management company Gigya reveals that many still don’t trust brands with their personal information. The findings show 68 percent of consumers are concerned about how brands use their personal data. A similar number (69 percent) have concerns about security and privacy risks surrounding the increased adoption of Internet of Things devices, such as fitness trackers, smart watches and connected cars. This shows up a dilemma for businesses as they balance customer expectations and new privacy requirements… [Continue Reading] -

New platform simplifies securing cloud workloads
Publié: avril 24, 2017, 4:04pm CEST par Ian Barker
The cloud is a dynamic environment and the threats it faces are equally fluid, whether they're sophisticated cyber attacks or insider threats. Cloud security company Lacework is launching a new tool called Polygraph that detects breaches, manages insider threats, delivers insights into workloads, and offers graphical investigation tools for public, private and hybrid cloud workloads. It's been developed to provide end-to-end visibility, so security professionals can connect and visualize elements of an attack or insider threat enabling them to respond more quickly and effectively. Complex cloud data center architectures typically feature thousands of similar machines, processes, users, containers, and applications… [Continue Reading] -

New service gives enterprises self-service identity management
Publié: avril 24, 2017, 3:19pm CEST par Ian Barker
Increasing workforce mobility and the shift of systems to as-a-service models has meant greater need for a reliable means of controlling access and identifying legitimate users. Identity management specialist SailPoint is launching a new service called IdentityNow Access Request that provides a simple, mobile-ready interface for delivering a self-service access request process to employees, contractors, and business partners. It's aimed at improving IT efficiency and reducing the risk of inappropriate access by consistently enforcing organizational access policies. The service uses the company's existing IdentityNow governance platform, but allows IT departments to securely delegate the responsibility of managing access to other… [Continue Reading] -

Dell flips its lid to create the XPS 13 2-in-1 [Review]
Publié: avril 21, 2017, 12:19pm CEST par Ian Barker
News of Dell's upcoming convertible version of the XPS 13 leaked back in January, now it's here and we’ve got our hands on one. Dell has essentially taken its XPS 13 laptop and turned it into a convertible whilst maintaining most of the conventional system's features. First impressions are that it feels solidly made with a machined aluminum chassis, carbon fiber composite palm rest and a gorilla glass screen. It has a smart silver/gray finish but what strikes you most on first acquaintance is the compact size. There are two screen options: a Quad HD UltraSharp and a standard 1080p.… [Continue Reading] -

Malware backdoors still the biggest threat to enterprises
Publié: avril 20, 2017, 4:29pm CEST par Ian Barker
New data from cloud security specialist Netskope shows that companies are still struggling to prevent network breaches and protect themselves at all points of entry. Backdoors made up the bulk of cloud malware detections, at 37.1 percent, down from 43.2 percent last quarter but still the biggest single threat. Following backdoors is adware at 14.3 percent, and Microsoft Office macros at 6.0 percent. Other threats include Javascript making up 5.8 percent of detections, ransomware 4.2 percent, mobile 1.5 percent, and PDF exploits one percent. The percentage of malware-infected files is 9.3 percent, down from 26.5 percent last quarter. Webmail now outstrips… [Continue Reading] -

Enterprises want mobile apps that can improve productivity
Publié: avril 20, 2017, 3:32pm CEST par Ian Barker
Most businesses have adopted some kind of mobile strategy and the focus now is on the positives that mobility programs can deliver. New research for mobile application management provider Apperian finds that 43 percent of respondents listed improved productivity as their primary goal of enterprise mobile apps -- a 20 percent jump over 2016. In addition, 22 percent of those surveyed cited new revenue or service delivery opportunities -- a 17 percent increase from last year. These findings suggest enterprises expect mobility to have a positive impact on the bottom line, not just improve business processes or employee satisfaction. Expansion… [Continue Reading] -

ShadowPlex delivers cost-effective deception technology
Publié: avril 20, 2017, 12:31pm CEST par Ian Barker
Deception technology intended to catch out attackers by deploying decoys that mimic business systems is gaining in popularity. The market for deception is expected to exceed $2 billion by 2021. Threat defense specialist Acalvio Technology is launching a new product called ShadowPlex which offers the scale and depth of a dynamic deception environment, and integrated intelligence built on a cloud-first infrastructure that makes it easy and cost-effective to deploy. "With its patented DeceptionFarms technology, ShadowPlex supports organizations in and from the cloud to quickly and easily, deliver high fidelity, cost effective and early detection of malicious activity," says Ram Varadarajan,… [Continue Reading] -

Karmen ransomware gives cyber criminals a user-friendly attack tool
Publié: avril 19, 2017, 5:54pm CEST par Ian Barker
Researchers at threat intelligence specialist Recorded Future have uncovered a new strain of ransomware called Karmen that’s designed for use by people with limited technical expertise. The ransomware-as-service has been developed by Russian and German hackers and is notable for its user-friendly approach. It comes equipped with a dashboard that allows the tracking of computers infected with the virus, including the status of any ransom that’s been paid. The standard version is small in size to help it evade detection. There's also a larger, self-protecting, version that will delete its own decryptor if it detects that it’s in a sandboxed… [Continue Reading] -

Almost half of UK business hit by cyber crime
Publié: avril 19, 2017, 1:32pm CEST par Ian Barker
UK-based businesses of all sizes are being urged to protect themselves against cyber crime after new government statistics showed nearly half of all UK businesses suffered a cyber breach or attack in the past year. The Cyber Security Breaches Survey 2017 reveals nearly seven out of 10 large businesses identified a breach or attack, with the average cost to large businesses of all breaches over the period being £20,000 and in some cases reaching millions. The survey also shows that personal data is still a lure for criminals, with businesses holding electronic personal data on customers much more likely to… [Continue Reading] -

Managing compliance in the hospitality industry [Q&A]
Publié: avril 19, 2017, 11:14am CEST par Ian Barker
Even for businesses in sectors like finance and healthcare where compliance and security is ingrained in the culture, protecting sensitive information is a major challenge. For other sectors where it's incidental to the main business, compliance can be a major headache. With new payment card security requirements and other regulations like GDPR coming into force, businesses in sectors like hospitality need to up their game. We spoke to Geoff Milton, security strategist at data protection company ShieldQ to find out how the hospitality industry can overcome the headaches associated with compliance. BN: What effect will the changes to PCI-DSS regulations… [Continue Reading] -

New edge platform delivers faster digital experiences
Publié: avril 18, 2017, 4:11pm CEST par Ian Barker
A great deal of today's data is generated by users at the edge of corporate networks. It therefore makes sense to process and serve this information closer to where it originates. San Francisco-based Fastly is unveiling its new edge cloud platform, which allows popular businesses to deliver consistently secure, fast and personalized digital experiences as close to end users as possible. "Our goal is to help the world’s leading digital businesses operate fully at the edge for the best possible performance," says Artur Bergman, CEO and founder of Fastly. "We will continue to support our customers' growth, enable continuous development… [Continue Reading] -

New Samsung Places tool makes it easier to call businesses
Publié: avril 18, 2017, 3:17pm CEST par Ian Barker
While people often search for businesses on the web, the most popular way of actually getting in touch is still by phone. But that means getting the details from your browser and switching to the dialer app to make the call. Caller profiling and phone spam protection company Hiya is launching the first implementation of its Hiya Business Profiles product for the Samsung Galaxy S8, which allows users to find and call businesses from within the dialer. Samsung Places will replace the Favorites tab in the native dialer and provide users with an integrated search and discovery experience. It delivers… [Continue Reading] -

New tool offers flexible feature delivery for mobile developers
Publié: avril 18, 2017, 1:44pm CEST par Ian Barker
Businesses are clamoring for up to date mobile apps, but in the past the approach has tended to be all or nothing, with no real way of testing new features on some users before rolling them out to everyone. Mobile developer tool specialist Rollout.io is launching a new ROX by Rollout tool that gives mobile app developers the ability to selectively deliver new features to subsets of users and monitor the performance of those features, making intelligent, data-driven recommendations about further deployment. "Data-driven deployment is the future of mobile app development," says Erez Rusovsky, co-founder and CEO of Rollout. "With… [Continue Reading] -

Businesses are unprepared for the Industrial IoT
Publié: avril 18, 2017, 1:03pm CEST par Ian Barker
Many companies are unprepared for the Industrial Internet of Things (IIoT), even though most executives at those companies realize that the future of their business could depend on it, according to a new study. The research from the Business Performance Innovation Network finds that 52 percent of executives at large enterprises -- and 41 percent of executives at all companies -- expect the IIoT to have a significant or major impact on their industry within three years. IIoT adoption is gaining ground according to 55 percent of respondents, yet just 1.5 percent of executives at large companies say they have a… [Continue Reading] -

Over 70 percent of companies using AWS have serious security misconfigurations
Publié: avril 18, 2017, 11:29am CEST par Ian Barker
A high percentage of companies using AWS cloud services have at least one critical security misconfiguration according to a new survey. Cloud security company Threat Stack has analyzed more than 200 companies using AWS and found number of well-documented security misconfigurations. Among the most serious are AWS Security Groups configured to leave SSH wide open to the internet in 73 percent of the companies analyzed. This simple configuration error allows an attacker to attempt remote server access from anywhere, rendering traditional network controls like VPN and firewalls ineffective. Threat Stack also observed SSH traffic from the internet using the root account,… [Continue Reading] -

Twistlock delivers enhanced security and compliance for container environments
Publié: avril 17, 2017, 3:04pm CEST par Ian Barker
In recent years containerization has seen increased popularity thanks to its ability to deliver an agile, flexible environment in which software can be reliably moved from development to testing to live, or from in-house to the cloud. But the use of containers also throws up new challenges, particularly when it comes to keeping data secure. Container security specialist Twistlock is using this week's DockerCon to launch an updated product with new features, improved performance and a revised user interface. "Container security needs to be truly application aware and based upon developer intent," says John Morello, chief technology officer at Twistlock.… [Continue Reading] -

Are bots set to replace apps for mobile commerce?
Publié: avril 17, 2017, 1:00pm CEST par Ian Barker
As the world has moved more towards using mobile platforms for eCommerce and accessing the web, many companies have been looking to shift away from apps towards more responsive technology delivered by bots. But is this model the future? Mobile development company ROKO Labs has produced an infographic looking at the pros and cons of both approaches. Among key findings are that while apps currently take the lion's share of funding, early-stage bot funding has increased by a massive 129 percent year-on-year. Also bot funding surpassed apps in August 2016, reaching a high of $20.49 million. The increased use of… [Continue Reading] -

New platform uses machine learning to find the next big thing in entertainment
Publié: avril 14, 2017, 3:21pm CEST par Ian Barker
Anyone involved in writing books or TV and film scripts knows that whilst the entertainment and publishing sectors are constantly on the look out for the next blockbuster, nobody is quite sure what one actually looks like. A new AI platform called AUTHORS is looking to use machine learning technology to recognize critical insights in original, creative work, to identify its mass audience appeal. The AUTHORS platform analyzes the content, predicts success, and then connects the creator with the appropriate publishers or agents. Though still in its early stages, the platform currently has about 40 publishers and agents who use… [Continue Reading] -

GDPR and what it means for businesses
Publié: avril 14, 2017, 12:58pm CEST par Ian Barker
The EU's General Data Protection Regulation (GDPR) comes into force in just over a year's time, but what impact will it have on business data protection efforts? GDPR is one of the toughest pieces of data protection legislation in the world and will impose heavy penalties for non-compliance for any business around the world that collects or processes EU resident data -- even if the company is based outside the EU. Threat defense specialist Digital Guardian has produced an infographic detailing how GDPR has been developed and what it means for businesses. It covers the key requirements of the legislation,… [Continue Reading] -

Solving the puzzle of hybrid cloud [Q&A]
Publié: avril 14, 2017, 12:27pm CEST par Ian Barker
Many enterprises are moving towards hybrid cloud environments, but they face a challenge when it comes to working out how to control their cloud use effectively. If they fail to do this and govern their cloud use properly, then any gains in agility they achieve will come with high costs and operational risks. We spoke to Andrew Hillier, CTO of Cirba, the company behind the Densify.com SaaS hybrid capacity analytics software, to find out how enterprises can bridge the gap between cloud hype and reality. BN: What are the main factors driving the move towards cloud use? AH: There are numerous… [Continue Reading] -

Employees in the dark about data retention policy
Publié: avril 12, 2017, 4:12pm CEST par Ian Barker
Enterprises are increasingly bound by legal and compliance requirements to retain information and communications. Yet a new study reveals that over half of office-based employees say their companies don't have written policies on data retention or personal use of work devices, or if they do, they aren’t aware of them. The study conducted by Harris Poll for e-discovery company kCura reveals communication habits that could put organizations at risk of incurring increased data retention and discovery costs in today's increasingly litigious business environment. "With so much data to organize, risk and costs can -- and do -- get out of… [Continue Reading] -

New cloud platform enables cost-effective data engineering
Publié: avril 12, 2017, 3:21pm CEST par Ian Barker
Businesses encounter a variety of challenges in building systems on and around Spark to meet the needs of data engineering. Often engineers need to perform mission-critical data cleansing, transformations, and manipulations, to make business activities real-time dashboards or fraud detection possible. Mastering data engineering is therefore an essential step to automating systems and making data-driven decisions. Spark-based data science platform Databricks is launching a new edition of its cloud platform optimized specifically for data engineering workloads. Databricks for Data Engineering enables more cost-effective data engineering using Spark while empowering data engineers to easily combine SQL, structured streaming, Extract, Transform, Load… [Continue Reading] -

Preventing cyber attacks -- this time it's personal
Publié: avril 12, 2017, 12:09pm CEST par Ian Barker
Security professionals are putting pressure on themselves to secure their organization's systems according to the findings of a new report. The 2017 Security Pressures Report from managed security specialist Trustwave surveyed over 1,600 security decision makers around the world and finds that while 53 percent of respondents report increased pressure in trying to secure their organization, that pressure is becoming more personal as 24 percent say they put the most pressure on themselves, up from 13 percent last year. The findings also show that pressure from the boardroom and from c-level executives has decreased significantly as it's shifted to IT… [Continue Reading] -

Software-defined sensor technology improves cloud visibility
Publié: avril 11, 2017, 4:28pm CEST par Ian Barker
While companies are keen to benefit from the agility and cost savings of using the cloud, there are still concerns about the ability to monitor and secure systems to an enterprise standard. Ireland-based network analysis specialist Corvil is addressing this with the launch of a software-defined solution for packet-level instrumentation of virtual machines in public, private and hybrid cloud infrastructures. Corvil Sensor uses a Smart Streaming architecture optimized for real-time, reliable and always-on monitoring and analysis of business-critical workloads in the cloud. It allows customers to extend the operational, security and business analytics solution already provided by Corvil to public,… [Continue Reading] -

New platform delivers crowd insights into consumer preferences
Publié: avril 11, 2017, 3:36pm CEST par Ian Barker
A combination of big data and the web means that there's more opportunity than ever for companies to study and understand the habits of consumers. Online lists and voting site Ranker is using its wealth of polling data to launch a new Ranker Insights platform for marketers to uncover details of consumer behavior. Aiming initially at the entertainment sector, Ranker has used millions of data points to create B2B partnerships with a range of networks, production companies, movie studios and music labels across all platforms. Ranker Insights generates comprehensive data profiles of thousands of actors, movies, celebrities, TV series, musicians,… [Continue Reading] -

Why technology is key to managing mobile workforces
Publié: avril 11, 2017, 1:00pm CEST par Ian Barker
Workforces are increasingly mobile, but that presents a problem for businesses when it comes to controlling workloads. Scheduling software specialist Skedulo and marketing company Column Five have produced an infographic showing how technology is key to managing field workers. Key findings are that in 2020, the mobile workforce is projected to make up 70 percent of the total workers in the United States, with the healthcare industry leading the way. Ensuring mobile workers are at optimal efficiency and productivity is a top concern of 57 percent of field service organisations. In addition, by 2018, 70 percent of field service workers… [Continue Reading] -

New rating system measures national cyber security risk
Publié: avril 7, 2017, 3:43pm CEST par Ian Barker
Although governments need to secure their nation's critical infrastructure from cyber attack, they can often lack the context in which to assess risk. Security ratings specialist BitSight is addressing this with the announcement of its Sovereign Security Ratings, the first objective measurement of national cybersecurity risk. As part of the BitSight Security Ratings Platform, the Sovereign Security Ratings portal allows analysts to benchmark the security and risk posture of multiple countries and industries in one view. With this information, government organizations gain intelligent and actionable insights into threats and can initiate action with the appropriate parties. It also allows the… [Continue Reading] -

CTERA delivers automated cloud backup for AWS users
Publié: avril 6, 2017, 3:14pm CEST par Ian Barker
In the dash to move systems to the cloud many organizations neglect the need to safely backup their information. Secure file services specialist CTERA Networks is addressing this problem for Amazon cloud users by making its Cloud Server Data Protection Platform available on the AWS Marketplace. It allows organizations to back up any number of Windows and Linux Amazon Elastic Compute Cloud (Amazon EC2) instances hosted on AWS, and to use AWS as a backup target for applications running on any cloud or object storage-based solution. It addresses both the architectural and operational considerations for protecting cloud-based data with a… [Continue Reading] -

Inateck adds to its range of laptop protection [Review]
Publié: avril 6, 2017, 11:31am CEST par Ian Barker
Inateck has for a long time been producing good quality, reasonably priced sleeves and cases for laptops and tablets. It's now added to its selection with two new offerings. There's not a great deal to say about the Inateck LC1302, it's a simple neoprene sleeve designed to fit 13-inch laptops and notebooks or larger tablets like the Surface Pro. A wide opening zipper allows for easy access, waterproof material keeps the contents safe from rain and spillages, and three layers of fabric protect from shocks. Our review sample came in a nice navy blue with the maker's name subtly printed… [Continue Reading] -

Criminals able to empty ATMs using remote admin attacks
Publié: avril 5, 2017, 4:12pm CEST par Ian Barker
Back in February of this year researchers at Kaspersky Lab uncovered a series of mysterious fileless attacks against banks where criminals were using in-memory malware to infect banking networks. A recent investigation into a Russian bank ATM, where there was no money, no traces of physical interaction with the machine and no malware, has thrown further light on this activity. The bank's forensics specialists recovered two files containing malware logs from the ATM's hard drive. These were the only files left after the attack and while it wasn't possible to recover the malicious executables -- because after the robbery cybercriminals… [Continue Reading] -

New software helps companies control cloud spending
Publié: avril 5, 2017, 3:20pm CEST par Ian Barker
The speed at which companies have adopted cloud services has led in many cases to difficulties understanding and controlling the costs involved. Enterprise cloud management company RightScale has a solution to this issue with a new stand-alone collaborative cloud cost management and optimization solution. RightScale Optima delivers cost-saving recommendations to the appropriate resource owners, enabling them to take automated actions, and tracking optimization progress across the entire organization. "RightScale Optima is the first cloud expense solution designed as a collaborative platform that integrates cost-saving recommendations and automated action with extensive cost reporting to help enterprises ensure that they can realize… [Continue Reading] -

Intelligent MDM puts data in the hands of business users
Publié: avril 5, 2017, 12:36pm CEST par Ian Barker
Enterprise information management (EIM) and master data management (MDM) have in the past been complex tasks that have meant tight control of data by the IT department. Now though MDM specialist Semarchy is launching a new intelligent solution called xDM, designed to deliver control of data to the business user. "Traditionally, the MDM user experience has been so complex, that it has lived solely within the IT department. This is not the intelligent way to present such a crucial enterprise tool," says Salah Kamel, CEO and founder of Semarchy. "Today we're unveiling the industry's most significant breakthrough in MDM. Our… [Continue Reading] -

Intel Security becomes McAfee (again)
Publié: avril 5, 2017, 11:43am CEST par Ian Barker
It always seemed a little odd that, having acquired McAfee in 2010, Intel chose to drop what was a well established brand in the security field in favor of Intel Security. Well, now things have come full circle and Intel Security will now be known as McAfee, operating as a standalone business, though still with investment from Intel. The news follows from last year's announcement that the chip maker was selling part of its stake in the security business to private equity firm TPG. Intel, which retains a 49 percent stake in the company, will also have its senior vice… [Continue Reading] -

New solution applies data science to understanding consumers
Publié: avril 4, 2017, 4:11pm CEST par Ian Barker
Data science company Protagonist (previously called Monitor 360) is launching a new platform that is designed to analyze complex, cross-platform data sets in order to reveal the underlying beliefs and motivations of consumers. Using advanced natural language processing and machine learning it can uncover and measure the narratives that impact a given market, while the company's team of narrative experts apply high-level evaluation to give actionable meaning to the findings. "For the past ten years, Protagonist has rigorously observed and analyzed the way that beliefs function in the world, and we were never content with the inherent biases and limits of… [Continue Reading] -

New solution integrates software asset and security management
Publié: avril 4, 2017, 3:13pm CEST par Ian Barker
Keeping track of software licenses and ensuring that products are kept up to date with the latest patches can prove a chore for businesses. Software management specialist Flexera Software is launching a new product that integrates asset and security management for better vendor, financial and risk management, as well as operational efficiency and optimization. Flexera's Software Asset Management (SAM) solution enables enterprises to gain visibility and control of IT assets, reduce ongoing software costs and maintain continuous license compliance. As part of this process, FlexNet Manager Suite helps companies discover and inventory their software assets, rationalize and consolidate their portfolio… [Continue Reading] -

Downtime is a key cost of ransomware attacks
Publié: avril 4, 2017, 1:29pm CEST par Ian Barker
The cost of downtime due to lack of access to systems for customers and employees was the biggest business impact of a ransomware attack according to 59 percent of respondents to a new survey. The study from cyber security company Imperva also shows that 32 percent of respondents say their company has been infected with ransomware with 11 percent taking longer than a week to regain access to their systems after an attack. "Whether companies choose to pay the extortion or not, the real cost of ransomware is downtime and lost productivity," says Terry Ray, chief product strategist at Imperva.… [Continue Reading] -

Small and medium enterprises are underfunding IT security
Publié: avril 4, 2017, 11:50am CEST par Ian Barker
While large enterprises have the resources to tackle security issues, smaller organizations can struggle. A new survey of more than 150 IT security professionals at small to medium-sized businesses shows a significant drop in respondents' confidence in the security technologies they've deployed. The study by security as a service specialist EiQ Networks reveals that 86 percent of respondents say their organizations have underfunded IT security initiatives. Less than 15 percent report confidence that currently deployed technologies will be successful in detecting and responding to cyber attacks. This compares to 26.8 percent in 2015. In addition 56 percent say that their organizations are… [Continue Reading] -

New SaaS platform delivers gateway security for the cloud
Publié: avril 3, 2017, 5:25pm CEST par Ian Barker
Organizations are increasingly faced with the need to support a more distributed environment, with employees accessing data on mobile devices and information stored both in-house and in the cloud. Keeping these systems secure places a strain on traditional gateway security models, but cyber security company iboss is launching a new Distributed Gateway Platform is purposefully designed and packaged to offer today’s distributed organizations advanced gateway security capabilities. Delivered as a SaaS solution, features include include malware detection and response, content filtering, behavioral analytics and risk scoring, mobile device management, and sandboxing in one comprehensive, modular platform. It uses an elastic,… [Continue Reading] -

Teradata delivers portable database licensing for the hybrid cloud
Publié: avril 3, 2017, 5:09pm CEST par Ian Barker
Whilst cloud and hybrid models offer undoubted flexibility, they can lead to problems when it comes to keeping track of software licenses. Analytics solutions company Teradata is looking to cut through the confusion with the launch of a new simplified licensing model. This aims to deliver portability for deployment flexibility, subscription-based licenses and simplified tiers with bundled features. With portable database licenses, Teradata customers can now have the flexibility to choose, shift, expand, and restructure their hybrid cloud environment by moving licenses between deployment options as their business needs change. "The Teradata Database continues to be recognized as the leading… [Continue Reading] -

New audit solution fights insider threats against core enterprise systems
Publié: avril 3, 2017, 4:14pm CEST par Ian Barker
Many enterprises still rely on mainframes, while these are inherently secure, audits of user activities have historically been limited to scans of disparate logs and SMF data that don’t specifically capture start-to-finish user session activity. Mainframe software specialist Compuware is launching a new cybersecurity and compliance solution that enhances the ability of enterprises to stop insider threats by fully capturing and analyzing start-to-finish mainframe application user behavior. Compuware Application Audit provides a superior approach to analyzing logs by directly capturing complete, rich start-to-finish user session activity data in real time -- including all access attempts, session keyboard commands and menu selections,… [Continue Reading] -

Poor social network password habits put business data at risk
Publié: avril 3, 2017, 3:03pm CEST par Ian Barker
In an increasingly connected world few aspects of our lives exist in isolation. As a result, bad password habits on social networks can put work accounts at risk. A new study by account management solutions company Thycotic reveals that 53 percent of users haven’t changed their social network passwords in more than a year -- with 20 percent having never changed their passwords at all. This not only means their social network accounts are at risk but if the same password is being used elsewhere, other accounts are vulnerable too. "As we know, social networks give away a lot of… [Continue Reading] -

Pay-as-you-go cloud platform offers fast, convenient web design
Publié: avril 3, 2017, 12:36pm CEST par Ian Barker
It's a rare business that doesn't have a website these days, but for smaller companies the process of building a site and keeping it up to date can be costly and time consuming. Texas-based startup Snaplitics is aiming to fix this with the launch of an affordable tool for creating professional websites and landing pages without having to hire developers. "A professional website that looks less than three years old and tells a story is a crucial component of a business's success," says co-founder Sean Hynes, "We wanted to make the process widely approachable to even non-tech-savvy users without inflated,… [Continue Reading] -

CloudBerry offers free licenses to celebrate World Backup Day
Publié: mars 31, 2017, 12:34pm CEST par Ian Barker
Backups aren't something that you should be doing only once a year, even so like most things these days backup has its own day and has had since 2011. World Backup Day is designed to raise awareness among consumers and businesses of the importance of keeping an up to date backup of your data. Cloud backup specialist CloudBerry Lab is doing its bit by offering free licenses for its Windows, Linux, and macOS products for a limited period. The company has also released the results of a survey of more than 700 internet users aimed at finding out what steps… [Continue Reading] -

Security professionals still struggle with the cloud and IoT
Publié: mars 30, 2017, 1:26pm CEST par Ian Barker
Organizations are using multiple cloud services and security staff are worried about the visibility problems this presents as well as the risks presented by IoT devices. These are the findings of a survey of RSA attendees, carried out by security management and threat intelligence specialist AlienVault. A third of respondents to the survey describe the state of security monitoring within their organization as 'complex and chaotic'. More than 10 different cloud services are used within their organization according to 39 percent of respondents, and an additional 21 percent don't actually know how many cloud applications are being used. No surprise… [Continue Reading] -

Daptly's smart display is a digital assistant for your home
Publié: mars 30, 2017, 11:34am CEST par Ian Barker
More and more of us are using voice operated personal assistants like Siri and Alexa, but a voice only interface can prove frustrating as it offers no visual cues. Technology startup Daptly is aiming to build a better assistant with a smart, gesture and voice controlled display that manages your life and seamlessly blends technology into your home or office. Built into a picture frame or a mirror, the Daptly Display recognizes who's in front of it and shows a personal dashboard that only displays information relevant to that person. So in the morning it can show you news and… [Continue Reading] -

Consumers are ready for chatbots but companies aren't using them
Publié: mars 29, 2017, 3:24pm CEST par Ian Barker
The majority of consumers are comfortable talking with a chatbot yet only a fraction have engaged with one, according to a new report. The study by mobile engagement specialist Vibes shows that over 60 percent of consumers would feel comfortable talking with a chatbot, yet only 22 percent have actually done so. "Consumers are open to engaging with brands on mobile in a way that is unlike any other channel," says Jack Philbin, co-founder and CEO of Vibes. "While consumers carefully control how brands can engage with them on these personal devices, they are highly receptive to new and emerging… [Continue Reading] -

New enterprise platform streamlines getting business intelligence from big data
Publié: mars 29, 2017, 1:30pm CEST par Ian Barker
Although big data is currently all the rage, extracting meaningful business intelligence from it can prove costly and time consuming. Data acceleration company Jethro is launching its latest platform offering an all-in-one enterprise solution that combines the power of indexing architecture with 'auto-cubes' to accelerate extracting business intelligence from big data. Jethro 3.0 eliminates costly and labor-intensive data engineering tasks such as pre-aggregating tables, manually building cubes, or keeping up with new and changing applications. Instead, Jethro automatically creates cubes based on real-world user queries, fully-indexes all table columns, and manages an intelligent query result cache. Unlike SQL-on-Hadoop engines that full-scan… [Continue Reading] -

Almost 40 percent of industrial computers face cyber attacks
Publié: mars 29, 2017, 12:15pm CEST par Ian Barker
In the second half of 2016 Kaspersky Lab products around the world blocked attempted attacks on 39.2 percent of protected computers that it classifies as being part of industrial enterprise technology infrastructure. The study from the Kaspersky Lab Industrial Control Systems Cyber Emergency Response Team (ICS CERT) also reveals that the top three sources of infection were the internet, removable storage devices, and malicious e-mail attachments and scripts embedded in the body of e-mails. The danger of infected removable storage devices shows the internet is not the only thing businesses have to worry about. During the period of research, 10.9… [Continue Reading] -

Non-malware attacks pose greater risk to business
Publié: mars 28, 2017, 4:04pm CEST par Ian Barker
Non-malware attacks pose more of a business risk than commodity malware attacks according to 93 percent of cybersecurity researchers. The study by endpoint security company Carbon Black interviewed more than 400 cyber security researchers and finds that 64 percent say they’ve seen an increase in non-malware attacks, such as remote logins and in-memory attacks, since the beginning of 2016. Attitudes to artificial intelligence and machine learning are also explored in the survey. AI is considered by most cybersecurity researchers to be in its nascent stages and not yet able to replace human decision making in cybersecurity. 87 percent of the… [Continue Reading] -

Comodo launches no-cost DNS security for businesses
Publié: mars 28, 2017, 3:21pm CEST par Ian Barker
Malicious websites provide a haven for malware and other threats to lurk, waiting for users to click links in emails or on other sites to contract an infection. Cyber security specialist Comodo is helping to combat this problem by making its DNS- and cloud-based web security offering, Dome Shield, available free of charge to both individuals and enterprises. Comodo Dome Shield provides a baseline level of web security by blocking access to known sites where malware resides. It offers a first layer of protection that prevents users from accessing malware sites. If users cannot access the site where a malware… [Continue Reading] -

IKEA launches affordable smart lighting range
Publié: mars 28, 2017, 12:04pm CEST par Ian Barker
Love it or hate it, Swedish home furnishing brand IKEA has a strong track record of providing affordable, well-designed home wares with unpronounceable names. The company is now moving into smart lighting with a range of remotely controlled energy-efficient LED bulbs, lighting panels and doors. There's also an app which allows you to personalize and control your lighting from your smartphone. IKEA is aiming to make smart lighting affordable and accessible to the masses. The new range is a plug-and-play solution, meaning that there is no need for hardwiring as customers can simply switch their traditional lightbulbs for a TRÅDFRI… [Continue Reading] -

European information security execs face major challenge from insider threats
Publié: mars 27, 2017, 4:35pm CEST par Ian Barker
New research shows that 35 percent of employees across the UK, France, Germany and Italy admit to have been involved in a security breach. This presents CISOs with a significant challenge when it comes to protecting company data, particularly in light of the forthcoming European General Data Protection Regulation (GDPR) which comes into effect in early 2018. The study from cyber security company Forcepoint surveyed over 4,000 office workers across the UK, France, Germany and Italy to better understand attitudes toward data protection and the number of insider threats, malicious and accidental, facing organizations across these countries. The findings show… [Continue Reading] -

How consumers are using AI and how they see its future
Publié: mars 27, 2017, 3:34pm CEST par Ian Barker
AI is starting to worm its way into our homes and workplaces, but a new study reveals that many consumers are currently unaware of the role it already plays in their lives. The survey of almost 2,000 US consumers by predictive sales platform InsideSales.com shows that in both their personal and work lives, people are split in their use of AI. Outside the office, more than half (55 percent) report that they have used AI before, but only about 10 percent can be considered early adopters, using AI on a regular basis. Interestingly use of AI seems to equate to lower… [Continue Reading] -

Three-quarters of organizations not confident in dealing with SSL-based attacks
Publié: mars 24, 2017, 3:51pm CET par Ian Barker
Despite 39 percent of businesses suffering an SSL-based attack in 2016, only 25 percent feel confident in their ability to deal with one according to a new study. The report from cyber security company Radware shows that cyber attacks are becoming the norm, with 98 percent of organizations experiencing some form of attack in 2016. SSL attacks though are of particular concern. SSL provided the backbone of eCommerce, though the Heartbleed attacks of three years ago have led many companies to switch to alternatives like TLS. For attackers though SSL offers a way to mask attack traffic and thwart malware detection… [Continue Reading] -

Uncovering the cost and profitability of DDoS attacks
Publié: mars 24, 2017, 12:29pm CET par Ian Barker
DDoS attacks are a popular cyber criminal technique, used either to cause a distraction for a different crime or demand a ransom for calling off or not launching an attack. New research from Kaspersky Lab reveals how profitable this activity can be. Researchers studied the DDoS services on offer on the black market and looked at how far the illegal business has advanced, as well as the extent of its popularity and profitability. The findings show that DDoS attacks can cost anywhere from $5 for a 300-second attack to $400 for a 24-hour attack. Based on the research, the average price… [Continue Reading] -

New generation of cyber highwaymen could threaten parcel drones
Publié: mars 23, 2017, 5:14pm CET par Ian Barker
Robbing the mail has a long and dishonorable history dating back to the days of the stagecoach. But UK-based online parcel broker ParcelHero is warning that automated delivery drones and droids could see the rise of a new breed of high-tech highwaymen. The development of devices that alter the drone or droid's instructions, or simply stop them dead, is seen as inevitable. With UK online retail sales now worth more than £130 billion a year, if deliveries are to become largely automated and just one percent of items are waylaid using new technology, that's over £1bn of goods stolen a… [Continue Reading] -

New platform protects industrial IoT devices
Publié: mars 23, 2017, 3:48pm CET par Ian Barker
Internet of Things devices are the latest threat vector that businesses have to deal with, introducing a potential extra weakness into corporate networks and leading experts to warn of increased risk. To help guard against the threat, Mocana Corporation is introducing a new security platform designed to protect IoT devices and associated device-to-cloud communications. It's also announcing capabilities that allow industrial manufacturers to make use of the newest hardware-based security technologies, automate digital certificate management to harden devices and effectively scale their IoT deployments. The Mocana platform provides a full-stack solution for securing IoT systems from the endpoint, to the… [Continue Reading] -

71 percent of Android phones on major US carriers have out of date security patches
Publié: mars 23, 2017, 1:20pm CET par Ian Barker
Slow patching of security flaws is leaving many US mobile users at risk of falling victim to data breaches according to the findings of a new report. The study from mobile defense specialist Skycure analyzed patch updates among the five leading wireless carriers in the US and finds that 71 percent of mobile devices still run on security patches more than two months old. This is despite Google releasing Android patches every month, indeed six percent of devices are running patches that are six or more months old. Without the most updated patches, these devices are susceptible to attacks, including rapidly… [Continue Reading] -

Malware campaign targets users in Latin America
Publié: mars 22, 2017, 5:10pm CET par Ian Barker
A modified version of a threat that first appeared in 2014 is successfully targeting users in Latin America according to the SPEAR research team at threat prevention specialist Cylance. Attackers using the El Machete malware -- first identified by Kaspersky -- have moved to new C2 (command and control) infrastructure, based largely around dynamic DNS domains, in addition to making some minimal changes to the malware in order to evade signature-based detection. SPEAR has been able to identify just over 300 unique victims over the past month as well as over 100GB worth of data that was successfully extracted and… [Continue Reading] -

How the best companies avoid downtime costs
Publié: mars 22, 2017, 3:25pm CET par Ian Barker
On average downtime costs an enterprise $686,000 per hour, leading to lost revenue across the economy of more than $26 billion. Hosting and disaster recovery specialist Sungard Availability Services has put together an infographic looking at the threat of downtime and how the best companies are better placed to deal with it. The best prepared businesses report 75 percent fewer downtime incidents and a massive 90 percent less downtime per event. They're also able to recover faster, averaging 1.13 hours as opposed to 5.18 hours for other businesses. Part of being prepared is that firms are more likely to have recovery… [Continue Reading] -

The hidden impact of DNS on internet users
Publié: mars 22, 2017, 11:09am CET par Ian Barker
According to a new report, 92 percent of UK companies have limited visibility into the impact DNS performance is having on their internet users and visitors to their online resources. The study by cyber security company Neustar and research firm Quocirca shows that although DNS is a fundamental utility supporting the internet, and relied on by all businesses, visibility is hampered by complexity with 45 percent of organizations having as many as eight different ways of provisioning their DNS infrastructure. Based on interviews with 100 senior IT decision makers at UK-based businesses in a variety of sectors, the report reveals that 72… [Continue Reading] -

DevOps adoption changes approach to application security
Publié: mars 21, 2017, 4:19pm CET par Ian Barker
New research from software supply chain automation company Sonatype reveals that the adoption of DevOps is leading businesses to adopt a different approach to security. The survey shows that mature development organizations are ensuring automated security is woven into their DevOps practice, early. But the results reveal that IT organizations continue to struggle with breaches as a nearly 50 percent increase was recorded between Sonatype's 2014 and 2017 surveys. DevOps is steadily gaining in maturity with 67 percent of survey respondents describing their practices as very mature or improving in maturity. Where traditional development and operations teams see security teams and… [Continue Reading] -

Jamf gives admins zero day support for the latest Apple OS releases
Publié: mars 21, 2017, 3:26pm CET par Ian Barker
New releases always present a challenge for system admins and that applies to Apple just as much as other systems. Device management specialist Jamf is offering zero day support for the latest spring releases of iOS (10.3), macOS (10.12.4), and tvOS (10.2). "As usual, Apple's new functionality for iOS, macOS and tvOS coupled with Jamf's zero-day support will help organizations empower people with technology that puts the user first," says Dean Hager, CEO of Jamf. "Specifically, the new management support for Apple TV opens up tremendous potential for transformation in education, healthcare, hospitality and boardrooms around the world. We have… [Continue Reading] -

Organizations remain vulnerable to brute force attacks
Publié: mars 20, 2017, 4:54pm CET par Ian Barker
Gaining access to accounts is often done the old-fashioned way, using brute force guesses, but a new report reveals that many devices and accounts still have default usernames and passwords. The study from visibility and testing company Ixia shows the top five username guesses as root, admin, ubnt, support, and user -- ubnt being the default username for AWS and other cloud services based on Ubuntu. Among other things the report reveals are the top five phishing targets as being Google, Paypal, Facebook, Microsoft, and Alibaba. Over the summer of 2016 ransomware attacks outpaced conventional phishing. Fake Adobe updates are… [Continue Reading] -

Archiving partnership aids financial services compliance
Publié: mars 20, 2017, 3:19pm CET par Ian Barker
For the financial services industry, compliance is a major issue as there's a need to archive communication from many different sources. To provide a solution to the industry's unique demands, financial services software specialist IPC Systems has announced a collaboration with communications compliance and archiving company Actiance. This will use Actiance's Alcatraz solution to offer IPC's financial services customers a holistic archival solution across a range of digital communications, including voice. Alcatraz can archive over 80 different types of digital communications, ranging from email to enterprise social networks, financial networks, and public social media. Thanks to the collaboration, IPC will… [Continue Reading] -

Microsoft Teams vs Slack -- how do they compare?
Publié: mars 20, 2017, 1:21pm CET par Ian Barker
Last week Microsoft rolled out its Teams collaboration app to Office 365 users. Teams has been widely billed as a competitor for Slack, but how do the two big players in this space measure up against each other? Internet marketing company TechWyse has put together an infographic giving an easy-to-follow overview of how the features of Teams and Slack compare. Slack is the more expensive option for paid users, but it does offer a Freemium model which Teams lacks. The comparison is about more than cost though. The graphic looks at numbers of users, features like alerts and the availability… [Continue Reading] -

How big data is being used and what's holding it back
Publié: mars 17, 2017, 4:37pm CET par Ian Barker
Big data has been something of a buzz word in IT and in enterprises in recent years, but while many people are enthusiastic about its potential there are fewer examples of its tangible benefits. Canadian printing company Colourfast has produced an infographic looking at what benefits big data is actually bringing to companies. Among the findings are that 40 percent of companies worldwide use big data analytics. Organizations that quantify their gains from big data analytics reported an eight percent increase in revenues and a 10 percent reduction in cost as a result of doing so. The most popular uses… [Continue Reading] -

Storm Stella leads to spike in malware infections
Publié: mars 17, 2017, 1:08pm CET par Ian Barker
Earlier this week, Storm Stella not only left parts of the North East US with up to three feet of snow, it led to an increase in malware infections too. According to data released by Enigma Software, the company behind SpyHunter, infections jumped by between 15 and 90 percent in some areas hit hard by the storm. "Any time we see a large number of people change their online habits, we see a change in infections," says Enigma spokesperson Ryan Gerding. "On Tuesday you had millions of people who stayed home from school and work. When they were snowed in,… [Continue Reading] -

The security threats that businesses will face in 2019
Publié: mars 16, 2017, 4:03pm CET par Ian Barker
The cyber security landscape is a constantly evolving one. The organizations best able to cope with it are the ones that can look beyond today's threats to those they'll face in future. London-based Independent security body the Information Security Forum has released its Threat Horizon 2019 report which is developed for business leaders who need to rapidly grasp emerging information security threats and assess the potential business impacts. Threat Horizon 2019 balances today's realities with forecasts that push the limits of present thinking. The latest report highlights nine major threats, broken down into three themes, that organizations can expect to… [Continue Reading] -

Malware hidden deeper in installer packages to evade detection
Publié: mars 16, 2017, 3:15pm CET par Ian Barker
Microsoft's Malware Protection Center has identified a new wave of NSIS (Nullsoft Scriptable Install System) installers that seek to evade detection by burying malware deeper in the code. The changes have been seen in installers that drop ransomware like Cerber, Locky, and others. The installers try to look as normal as possible by incorporating non-malicious components that usually appear in legitimate installers. Components include more non-malicious plugins, in addition to the installation engine system.dll, there's also a .bmp file that serves as a background image for the installer interface, to mimic legitimate ones, and a non-malicious uninstaller component uninst.exe. The… [Continue Reading] -

People who identify as 'tech savvy' are 18 percent more likely to suffer ID theft
Publié: mars 16, 2017, 1:59pm CET par Ian Barker
Identity theft is a growing problem, but who is falling victim to online ID fraud, why is it still happening, and how can you protect yourself? IT training specialist CBT Nuggets has carried out some research among more than 2,000 people in the US to find out, with some intriguing results. They discovered that people who self-identified as 'tech savvy' are 18 percent more likely to be victims of online identity theft than those who didn't. Additionally, respondents with PhDs are more frequently victims than high school graduates. Plus Apple users are 22 percent more likely than Windows users to be victims… [Continue Reading] -

Businesses deploy sensitive data to new environments without adequate security
Publié: mars 16, 2017, 1:02pm CET par Ian Barker
According to a new report, 93 percent of enterprises will use sensitive data in advanced technology environments (such as cloud, SaaS, big data, IoT and container) this year. But 63 percent of those respondents also believe their organizations are deploying these technologies ahead of having appropriate data security solutions in place. These are the findings of the latest Data Threat Report from Thales e-Security and 451 Research. While concerns about data security in cloud environments are still high, they've lessened since last year. In 2016, 70 percent of respondents voiced worries about security breaches from attacks targeting cloud service providers… [Continue Reading] -

Women still underrepresented in information security
Publié: mars 15, 2017, 4:40pm CET par Ian Barker
Women make up only 11 percent of the cyber security workforce according to the latest report from the Center for Cyber Safety and Education -- formerly the (ISC)² Foundation -- and the Executive Women's Forum (EWF). The survey of more than 19,000 participants around the world finds that women have higher levels of education than men, with 51 percent holding a master’s degree or higher, compared to 45 percent of men. Yet despite out qualifying them, women in cybersecurity earned less than men at every level and the wage gap shows very little signs of improvement. Men are four times more… [Continue Reading] -

The challenges of adopting DevOps
Publié: mars 15, 2017, 3:46pm CET par Ian Barker
DevOps has become enormously popular as a means of speeding up tech projects, but a new study reveals the challenges that organizations face in adopting it. The survey from sandbox specialist Quali finds the top barriers to DevOps success include the respondent's company culture (14 percent), challenges of testing automation (13 percent), legacy systems (12 percent), application complexity (11 percent), and budget constraints (11 percent). Other barriers to implementing DevOps include limited IT skills, difficulty managing multiple environments, a lack of DevOps plans and tools, and a lack of executive buy-in. Complex applications also make the transition to cloud and… [Continue Reading] -

Sleeper accounts wait for at least a week before launching cyber attacks
Publié: mars 15, 2017, 3:05pm CET par Ian Barker
Sleeper cell accounts which appear normal and hide among normal users, waiting for long periods of time to age the account before striking, are the latest technique being used by cyber attackers. These accounts are often used for testing or carrying out the attack in stages, according to fraud and financial crime detection service DataVisor. According to the DataVisor Online Fraud Report, 44 percent of fraudulent accounts sleep for at least seven days before an attack. In addition 37 percent of malicious accounts have still to attack even after three months. Fraudsters are using cloud hosting providers to create armies… [Continue Reading] -

Secret Double Octopus eliminates enterprise passwords
Publié: mars 15, 2017, 2:44pm CET par Ian Barker
No, we're not talking about the James Bond of the cephalopod world getting his tentacles on your security. Secret Double Octopus is an intriguingly named Israeli company that’s launching a new authenticator app for enterprises. Authentication systems have traditionally relied on a single layer of protection, such as SMS, tokens, push notifications and biometrics. Secret Double Octopus uses a multi-shield authentication process for users to verify or reject a login attempt, payment or transaction. Based on algorithms originally developed to protect nuclear launch codes, the company has developed a solution that applies keyless authentication and data-in-motion protection for cloud, mobile,… [Continue Reading] -

Microsoft Teams rolls out to Office 365 users around the world
Publié: mars 14, 2017, 5:25pm CET par Ian Barker
As we reported last week, Microsoft is today launching its own business collaboration tool in an effort to fend off the challenge from Slack. Teams is now available to Office 365 users in 181 markets and 19 languages. Where Teams is likely to score over its competitors is in its close integration with other Office products and with Skype for Business. Microsoft Teams provides threaded, persistent chat to keep all users engaged. The company has added many new communication features since the preview version, including audio calling from mobile devices, plus video on Android, which is coming soon to iOS… [Continue Reading] -

IT security pros expect a rise in Industrial Internet of Things attacks
Publié: mars 14, 2017, 4:29pm CET par Ian Barker
The Industrial Internet of Things (IIoT) is used in many businesses, including critical infrastructure sectors such as energy, utilities, government, healthcare and finance. No surprise then that it's a likely target for attack. A new survey from security and compliance specialist Tripwire of more than 400 IT security professionals shows that 96 percent expect to see an increase in security attacks on the IIoT in 2017. 51 percent say they don't feel prepared for security attacks that seek to abuse, exploit or maliciously use insecure IIoT devices. In addition 64 percent say they already recognize the need to protect against… [Continue Reading] -

Traditional endpoint protection ineffective in fighting ransomware
Publié: mars 14, 2017, 2:56pm CET par Ian Barker
Ransomware continues to be the most lucrative business model for cyber crime, and a new study indicates that existing endpoint protection methods may not be enough to guard against it. The survey from security awareness training organization KnowBe4 questioned more than 500 organizations about the current state of their ransomware protection, whether they were a victim of ransomware, the impact of a successful breach and their remediation tactics. It finds that 33 percent of respondents have experienced a ransomware attack in the past 12 months. More concerning is that 53 percent of organizations that had deployed multiple solutions against ransomware… [Continue Reading] -

Decrease in patch rates points to broken software supply chain
Publié: mars 13, 2017, 4:54pm CET par Ian Barker
Vulnerabilities in software are at the heart of many security problems, providing a foothold for hackers that they can use to gain access to systems. The latest Vulnerability Review from the Secunia Research arm of Flexera Software maps the security threat presented to IT infrastructures and explores vulnerabilities in the 50 most popular applications on private PCs. The study finds that in 2016, 81 percent of all vulnerabilities, and 92.5 percent of applications, in what it identifies as the Top 50 Software Portfolio, that were impacted by vulnerabilities had patches for those vulnerabilities available on the day of disclosure. However,… [Continue Reading] -

63 million LinkedIn users have weak passwords
Publié: mars 13, 2017, 3:30pm CET par Ian Barker
Last year's highly publicized Yahoo and LinkedIn breaches exposed millions of users' passwords to the public and saw them for sale on the dark web. Researchers at behavioral firewall company Preempt have analyzed the leaked LinkedIn passwords to find out how many were weak before the breach occurred. The findings show that 35 percent of leaked LinkedIn passwords -- over 63 and a half million -- were already known from previous password dictionaries, making them vulnerable to cracking offline by reference to a word list of known or previously used passwords. In addition 65 percent could be easily cracked with brute… [Continue Reading] -

Mint SIM delivers mobile for the cord-cutting generation -- 20 percent discount for BetaNews readers
Publié: mars 13, 2017, 11:15am CET par Ian Barker
Choosing the right mobile plan can be a minefield, requiring you to balance your needs for voice, texts and data against the performance of the service provider and the monthly costs. US company Mint SIM is seeking to shake things up with a phone service for today's agile, digitally savvy generation. It offers a model that is platform agnostic and not tied to a particular phone or OS. With Mint's pay-up-front, multi-month plans, users get bigger discounts against the fastest voice and 4G LTE network. You can choose to pay for your phone plan up front for a year, and not… [Continue Reading] -

Kaspersky brings you the smell of malware
Publié: mars 10, 2017, 12:02pm CET par Ian Barker
When your job is writing about technology you get used to receiving the somewhat off the wall ways companies come up with to promote their products. Kaspersky's latest endeavour though had us scrambling for the calendar to check whether it was April 1st, as the company is launching a fragrance. Described as 'threatening yet provocative' the rather disturbingly named Threat de Toilette comes, like all the best scents, in pour femme and pour homme versions. "Fear awakens our senses," says David Emm, Kaspersky Lab's principal security researcher and face of the new scent. "The men and women who wear Threat… [Continue Reading] -

Better consumer education could help cut video piracy
Publié: mars 9, 2017, 3:26pm CET par Ian Barker
A new survey reveals that education could have a big impact on piracy, cutting the numbers who illegally share video content. The study by digital platform security specialist Irdeto of more than 25,000 adults across 30 countries finds that despite the high number of consumers around the world watching pirated video content (52 percent), almost half (48 percent) would stop or watch less illegal content after learning the damage that piracy causes to the media industry. An industry-wide education initiative could have the most impact in the Latin America and Asia Pacific regions. 59 percent of consumers who watch pirated… [Continue Reading] -

Check Point adds advanced security to the Google Cloud Platform
Publié: mars 8, 2017, 5:40pm CET par Ian Barker
Businesses often have security concerns surrounding moving their data to the cloud. For users of the popular Google Cloud Platform, Check Point is offering additional security with the launch of a new product. The release of vSEC for Google Cloud Platform delivers advanced security that is built for agile and scalable cloud environments. The software extends advanced, multi-layered security to protect workloads in the cloud from external attacks while enabling secured connectivity from on-premise enterprise networks to the Google Cloud Platform. In addition, it prevents the lateral movement of threats between servers hosted inside the cloud. Designed for the dynamic security… [Continue Reading] -

Generation Z finds products online but prefers to shop in-store
Publié: mars 8, 2017, 4:14pm CET par Ian Barker
The Gen Z population -- those born between the late 1990s and the mid-2000s -- still value the in-store experience even though they're likely to search for products online. This is among the findings of a study into shopping habits by retail analytics specialist Euclid Analytics. It reveals that this age group like to see, hold and try on products before buying and 28 percent of Gen Z shoppers want to engage with store associates while shopping, the most of any generation. Other interesting findings are that only 47 percent of Gen Z shoppers like to browse stores (tied with… [Continue Reading] -

Over 60 percent of organizations hit by ransomware in 2016
Publié: mars 8, 2017, 3:15pm CET par Ian Barker
Ransomware continues to be a major problem, a new report reveals that more than 60 percent of organizations suffered some form of ransomware attack in 2016. The good news is that 54 percent successfully retrieved their data without resorting to paying the ransom. These are among the findings of the fourth-annual Cyberthreat Defense Report from security research firm CyberEdge Group. Among other findings are that nearly four in five respondents' organizations were affected by a successful cyberattack in 2016, with a third being breached six or more times in the space of a year. Despite this, however, there are signs… [Continue Reading] -

IT executives believe service management is key to digital transformation
Publié: mars 8, 2017, 1:31pm CET par Ian Barker
A new survey reveals that a majority of IT executives believe investment in IT service management (ITSM) is important to gain the agility needed to compete in an era of global, cross-industry disruption and digital transformation. The study of more than 250 IT executives for enterprise management specialist BMC conducted with Forbes Insights reveals that 88 percent of respondents say ITSM is important to their digital transformation efforts. In addition 86 percent see ITSM as important to related initiatives around cloud computing, 83 percent to mobility and 83 percent to big data. Also 75 percent believe the time, money, and… [Continue Reading] -

New reporting tool helps businesses unlock key product data
Publié: mars 7, 2017, 4:17pm CET par Ian Barker
The importance of data to business decisions is well understood, however, too often companies are relying on outdated intelligence tools which mean they waste time creating reports. Analytics specialist Mixpanel is looking to help companies unlock their data with the launch of Mixpanel Dashboards. Dashboards allows users to create and explore unlimited sets of reports so they can view and share their key product metrics in one place. People can access their Dashboards anywhere, from mobile apps and laptops or even on HD displays mounted around the office. "We created Dashboards so people can get the right information at the… [Continue Reading] -

Apple adoption in enterprises is on the increase
Publié: mars 7, 2017, 3:11pm CET par Ian Barker
Over 90 percent of enterprises have some Mac usage and 99 percent have iPads and iPhones according to the results of a new survey of IT professionals by Apple device management specialist Jamf. Almost all of the organizations surveyed in 2016 report an increase in both Mac and iOS device adoption over the previous year and much of this is driven by employee choice. Nearly half of organizations surveyed (44 percent) give their employees a choice between Mac and PC, with the majority (71 percent) offering a choice between different mobile devices (Apple, Android, etc). This choice is happening in all sizes… [Continue Reading] -

IBM and Salesforce partner to help businesses make smarter decisions
Publié: mars 7, 2017, 11:19am CET par Ian Barker
Although artificial intelligence has been around for some time, it's generally been beyond the reach of most businesses. A new collaboration between industry giants IBM and Salesforce aims to put AI-enabled technologies into the hands of millions of users to help them make better informed decisions. With the partnership, IBM Watson, the leading AI platform for business, and Salesforce Einstein, AI that powers the world's number one CRM system, will seamlessly connect to enable a new level of intelligent customer engagement across sales, service, marketing, commerce and more. New insights from Watson will be brought directly into the Salesforce Intelligent Customer Success… [Continue Reading] -

Docker launches new enterprise platform
Publié: mars 2, 2017, 5:17pm CET par Ian Barker
Containerization specialist Docker is releasing a new commercial platform for enterprise development and IT ops teams that build, run, and operate business-critical applications. Docker Enterprise Edition (EE) is made up of a container runtime with integrated and multi-tenant orchestration, security and management, in addition to an ecosystem of certified technologies. EE gives enterprises an open container platform that ensures a simplified yet rich user experience. The new modular platform makes it easy to install, configure and upgrade Docker on certified infrastructure (operating systems and cloud providers). Docker EE is available in three versions: Basic comes with the Docker platform, support and… [Continue Reading] -

Hidden backdoor discovered in Chinese IoT devices
Publié: mars 2, 2017, 3:27pm CET par Ian Barker
Researchers at Trustwave have uncovered a backdoor in IoT devices from a Chinese manufacturer that could leave them open to exploitation. The backdoor is present in almost all devices produced by VoIP specialist DBLTek, and appears to have been purposely built in for use by the vendor. It uses a simple challenge and response mechanism to allow remote access. However, Trustwave's investigation has shown this scheme to be fundamentally flawed in that it is not necessary for a remote user to possess knowledge of any secret or password, besides the challenge itself and knowledge of the protocol/computation used. The issue… [Continue Reading] -

Mobile app use could boost charity giving
Publié: mars 2, 2017, 1:29pm CET par Ian Barker
We're all spending more and more via mobile apps, and giving to charity could be the next area to benefit from the shift to mobile payments. A new study carried out by social payment app Moneymailme finds that 72 percent of 18-25 year-olds would give to charity via a mobile app if given the chance. 48 percent of this generation believe physical money will be obsolete within 20 years so the ability to donate via apps will become key. The survey of 1,000 18-25 year-olds in the UK finds that 74 percent of young people give to charitable causes. This… [Continue Reading] -

Companies need to work together to combat malvertising
Publié: mars 2, 2017, 12:24pm CET par Ian Barker
Advertising agencies, search engines and cybersecurity specialists should work collectively to tackle the security threat from rising malvertising. According to Ben Williams, head of operations and communications at Adblock Plus unless this happens more users will be exposed to potential security compromises such as malware and phishing, and this will drive further adoption of adblockers as a solution to these threats. A study from digital threat management firm Risk IQ shows total malvertising rose at a startling 132 percent between 2015 and 2016. Among the most notorious ads in the previous year were fake software at 70 percent, scams at 845 percent,… [Continue Reading] -

New security offering to guard against account take overs
Publié: mars 1, 2017, 6:00pm CET par Ian Barker
Data breaches caused by account take overs (ATOs) are a growing problem, partly due to people reusing passwords so that when a high profile breach -- such as the recent one at Yahoo -- occurs other accounts are put at risk. User behavior specialist Sift Science is taking on this threat and expanding into the cyber security market with a new tool to detect ATOs. Sift ATO Prevention assesses customer data as well as anonymized data from Sift's global network of customers to flag accounts that raise suspicions of having been taken over. Accounts are flagged using algorithms that automatically apply… [Continue Reading] -

Informatica uses behavioral analytics to spot and protect high risk data
Publié: mars 1, 2017, 5:01pm CET par Ian Barker
With increasing amounts of sensitive data stored in the cloud and accessed on mobile devices, protecting that information presents a major challenge. Data management specialist Informatica is adding to its Secure@Source platform with behavioral analytics to detect high risk data and ensure it's properly protected. Key features include automated and integrated sensitive data discovery, proliferation analysis, detection of anomalous user activities, multi-factor data risk analytics, and automated orchestration of remediation in a single platform. It covers cloud, Hadoop and legacy environments, and can support diverse and complex data classifications, proliferation and risk analytics, user access and activity correlation, user behavior… [Continue Reading] -

Database-as-a-service platform introduces encryption-at-rest
Publié: mars 1, 2017, 3:18pm CET par Ian Barker
While storing data in the cloud is undoubtedly convenient it also introduces risks and encryption is increasingly seen as a way of helping combat them. Database-as-a-service company mLab is introducing encryption-at-rest as an opt-in data security measure for customers of its most popular plans, at no additional cost. The mLab platform currently manages nearly 500,000 MongoDB deployments across Amazon Web Services, Google Cloud Platform, and Microsoft Azure. Encryption-at-rest will be available to mLab's Database-as-a-Service customers on Dedicated Standard and High Storage plans, covering deployments across both Amazon Web Services and Google Cloud Platform. The company already offers customers in-transit encryption… [Continue Reading] -

Why the cloud needs a new approach to security
Publié: mars 1, 2017, 12:12pm CET par Ian Barker
With more and more organizations moving their operations to the cloud, old approaches to security are put under strain and struggle to cope with the new way of working. Network security specialist Observable Networks has put together an infographic looking at the current state of cybersecurity and how old approaches don’t adapt to the cloud. It points out that perimeter-based detection is failing to respond to modern threats and also looks at the most common data breaches. Observable believes that a new active method of detection is required such as endpoint modeling, to provide behind the perimeter security via analytics-driven… [Continue Reading] -

Advertising Trojans become top mobile malware threat
Publié: février 28, 2017, 4:05pm CET par Ian Barker
Mobile malware detection almost tripled in 2016 and advertising Trojans exploiting super-user rights became the top threat. These are among the findings of Kaspersky Lab's 2016 Mobile Threat report released today, which looks at reports generated by the company's mobile products. The company recorded nearly 40 million attack attempts by mobile malware last year, with over four million users of Android-based devices protected (compared to 2.6 million in 2015). There were over 260,000 detections of installation packages for mobile ransomware Trojans (an increase of almost 8.5 times, year-on-year). More than 153,000 unique users were targeted by mobile ransomware (an increase… [Continue Reading] -

Performance issues and high failure rates continue to plague iPhones
Publié: février 28, 2017, 3:22pm CET par Ian Barker
We reported back in August that failure rates of iOS devices had overtaken those of Android for the first time. The latest State of Mobile Device Performance and Health report from Blancco Technology Group shows that this trend is continuing with the iOS failure rate at 62 percent in the final quarter of last year. The iPhone 6 has been the worst performing iOS device consecutively for four quarters with the highest failure rate compared to other models -- 25 percent in Q1 2016, 29 percent in Q2 2016, 13 percent in Q3 2016 and 15 percent in Q4 2016.… [Continue Reading] -

New solution guarantees 100 percent uptime for private cloud storage
Publié: février 28, 2017, 2:19pm CET par Ian Barker
Whether public or private, one of the key factors businesses consider in choosing a cloud service is to ensure maximum availability. Cloud storage specialist Scality is announcing its new HALO Cloud Monitor, a 24/7 solution to provide customers continuous uptime for their managed private cloud storage environments. Designed to work with the Scality RING object storage platform, HALO continuously monitors customer environments in real time and provides predictive analytics to ensure storage systems are performing optimally. Comprehensive dashboards offer diagnostic metrics, monitoring system level statistics, component processes, memory, disk and many other key elements. It provides, user-friendly visualization of events,… [Continue Reading] -

New IT management platform aimed at higher education sector
Publié: février 28, 2017, 1:13pm CET par Ian Barker
Higher education bodies face a range of challenges including restricted funding and increasing competition for students. The increasing digitization of the education sector adds an additional worry. To address the latter, IT management solutions specialist Kaseya is launching a new platform aimed specifically at higher education institutions. IT Complete for Higher Education offers a comprehensive toolkit to cut IT costs and maximize resources, while delivering a rich user experience to support students, faculty and administrators. It gives university system administrators a single pane of glass view into agent architecture, discovery and reporting, as well as cross-platform support. In addition there are… [Continue Reading] -

Telco data is an untapped source of customer information
Publié: février 27, 2017, 4:11pm CET par Ian Barker
Brands often turn to sources like Google and Facebook to find information about consumers, but a new report suggests that telecom carriers could be a valuable source of customer data. The study of over 300 brands in the US, UK and France by Ovum for mobile technology company Synchronoss Technologies finds that 67 percent of brands consider telecoms operators to be a better original source of data insights than Google, Apple and Samsung. Google (59 percent) and Facebook (52 percent) remain the dominant brand partners for data insights and digital advertising. 26 percent of brands say they do currently partner… [Continue Reading] -

Parallels on Azure helps streamline remote desktop delivery for SMBs
Publié: février 27, 2017, 11:40am CET par Ian Barker
An increasingly mobile and flexible workforce means greater demand for virtual desktops that can be delivered to any device. But complex and expensive to achieve, putting it beyond the reach of smaller organizations. Cross platform solutions specialist Parallels is aiming to simplify things with the launch of its Parallels Remote Application Server on the Microsoft Azure Marketplace. "Microsoft Azure brings even more cost savings and simplicity to our solution, enabling SMBs to install Parallels RAS and deploy virtual desktops and apps to any device around the world in record time, so IT admins and end users can experience the simplicity… [Continue Reading] -

New DDoS capabilities uncovered in Necurs botnet
Publié: février 24, 2017, 12:35pm CET par Ian Barker
The Necurs botnet is one of the largest around at the moment and is principally known for sending spam including the Locky ransomware. However, new research from BitSight's Anubis Labs has uncovered a new component being loaded in infected systems that allows it to use bots to enable proxy communications and perform DDoS attacks. The module has a compilation date in August 2016, although there's no evidence that these new capabilities have yet been used in anger. A botnet the size of Necurs, if used for DDoS attacks, is likely to cause severe disruption wherever it hits, being very capable of… [Continue Reading] -

PCs still at risk from end-of-life programs
Publié: février 23, 2017, 1:11pm CET par Ian Barker
The latest software vulnerability report from Secunia Research at Flexera Software reveals that the average US private PC user has 75 installed programs on their PC, 7.4 percent of which are no longer patched by the vendor. More detailed analysis of the findings shows that 7.5 percent of users had unpatched Windows operating systems in the final quarter of 2016, up from 6.1 percent in Q3 of 2016 and down from 9.9 percent in Q4, 2015. In addition 14 percent of users had unpatched non-Microsoft programs in Q4, 2016, up from 13.8 percent in Q3 of 2016 and 12.2 percent… [Continue Reading] -

Half of 2016’s phishing attacks aimed to steal money
Publié: février 23, 2017, 11:03am CET par Ian Barker
Almost half (47.48 percent) of all phishing attacks in 2016 were aimed at stealing victim's money, and the amount of financial phishing attacks increased by 13.14 percent according to a new report. The study by Kaspersky Lab analyzed attacks registered in 2016 by the company's heuristic detection technologies. Kaspersky's anti-phishing technologies detected almost 155 million user attempts to visit different kinds of phishing pages last year. Of those, almost half of detections were attempts to visit a financial phishing page, where the aim was to obtain valuable personal information from users -- such as their account numbers for banking, credit… [Continue Reading] -

Americans at risk of identity theft as they file their tax returns
Publié: février 22, 2017, 4:17pm CET par Ian Barker
As we move into the tax return season a new study reveals that attitudes to identity theft and a pattern of poor practices are leaving much of the public vulnerable. Data security and ID theft protection company CyberScout has carried out its second annual Tax Season Risk Report and finds 58 percent of Americans are not worried about tax fraud in spite of federal reports of 787,000 confirmed identity theft returns in 2016, totaling more than $4 billion in potential fraud. Among other findings are that only 35 percent of taxpayers demand that their preparers use two-factor authentication to protect their… [Continue Reading] -

CloudBees platform helps enterprises speed up software deployment
Publié: février 22, 2017, 3:25pm CET par Ian Barker
In order to address businesses' continuing dependence on software, development teams are turning to continuous delivery and automated software pipelines to speed up deployment. To address these needs CloudBees is launching Jenkins Enterprise to help companies accelerate their software delivery and meet the rapidly growing volume of software development. Jenkins Enterprise Enterprise delivers the manageability and operations capabilities to enable teams to quickly distribute, set up and share project assets and infrastructure. It includes authentication and access control for enterprise level security. Docker containers to enable Jenkins Enterprise to be deployed on native and virtualized environments, as well as on… [Continue Reading] -

New container platform speeds up Docker deployment
Publié: février 22, 2017, 2:28pm CET par Ian Barker
Containerization has seen a big increase in popularity in recent years, but companies are keen to ensure they're able to deploy containers quickly and keep control of the costs. Container infrastructure specialist Diamanti is launching a new purpose-built appliance for containerized applications, allowing businesses to deploy Docker containers quickly with guaranteed service levels and at a lower cost than traditional data center infrastructure. The Diamanti D10 appliance ships pre-integrated with all of the container software, compute, networking and storage resources necessary to deploy and operate high-performance containerized applications at production scale. In addition Diamanti's network and storage API contributions to popular… [Continue Reading] -

Manners maketh the smartphone user
Publié: février 22, 2017, 12:58pm CET par Ian Barker
The smartphone has revolutionzed the way we communicate and access information, but what about the effect it's had on our wider society? New research from business technology company Pitney Bowes looks at the tricky topic of smartphone e-etiquette -- and no, that doesn't mean sticking out your little finger as you use your phone. The research carried out among more than 1,100 people in the UK identifies a list of digital behaviors that most people consider to be rude. The worst offenses are being disturbed by someone talking on a phone in a public area (71 percent of us feel… [Continue Reading] -

Healthcare organizations boost spending on cyber security
Publié: février 21, 2017, 5:06pm CET par Ian Barker
Faced with increased requirements to digitize their records, healthcare organizations around the world are boosting their cyber security budgets according to a new report. The study from Thales e-Security finds 81 percent of US healthcare organizations and 76 percent of those globally will increase information security spending in 2017. In the US, government regulations such as the HITECH Act's Electronic Patient Care Reporting (ePCR) requirements are driving healthcare organizations to digitize their data. While this creates efficiency, it means individual healthcare data is exposed to more people, in more places and on more devices, including smartphones, laptops and increasingly, IoT… [Continue Reading] -

The top three barriers to digital transformation
Publié: février 21, 2017, 4:15pm CET par Ian Barker
To stay competitive in an increasingly digital world, companies are looking to transform their digital environment to improve collaboration and maintain their edge. But a new study by Intralinks and the Cloud Security Alliance reveals that digital transformation strategies are being hindered by three main barriers. These are data privacy and compliance fears, data siloed in specific departments and locations, and outmoded enterprise content management (ECM) systems. Of particular concern on the privacy front is the European Union's General Data Protection Regulation (GDPR), which will greatly tighten existing EU rules on data protection and privacy, and add new requirements beginning… [Continue Reading] -

Sapho integrates its app platform with IBM Domino
Publié: février 21, 2017, 3:17pm CET par Ian Barker
There's increasing demand from companies to build apps that integrate with their existing enterprise systems. Specialist in consumer-like micro apps Sapho is announcing new integration with the IBM Domino social business platform, that will simplify developer access to information and workflows used by employees. The Sapho Micro App Platform delivers apps that provide personalized information and one-click tasks via a Facebook-like newsfeed available to employees on their channel of choice. These include a native mobile app, browser, intranet, plus email and messenger clients like IBM Watson Workspace. "The Sapho Micro App Platform helps provide IBM Domino customers the ability to… [Continue Reading] -

New certification to verify cyber threat detection skills
Publié: février 20, 2017, 1:13pm CET par Ian Barker
Cyber security is an increasingly essential skill set, but it can be hard for businesses to verify that they're employing people with the right abilities. The Computing Technology Industry Association (CompTIA) is launching a new, vendor-neutral certification. CompTIA Cybersecurity Analyst (CSA+) is the first of its kind to bring behavioral analytics to the forefront of assessing cyber threats. The CSA+ certification will offer a broad-spectrum validation of the knowledge and skills required to configure and use cyber-threat detection tools, perform data analysis and interpret the results to identify vulnerabilities, threats and risks to an organization. It certifies knowledge of a… [Continue Reading] -

Businesses rely on managed services providers to move to Azure
Publié: février 17, 2017, 2:07pm CET par Ian Barker
While Microsoft's Azure cloud service is gaining popularity with businesses, many of them are relying on a managed services provider (MSP) to implement it successfully. According to a new survey by cloud and IT services company NetEnrich, 67 percent are 'very likely' to engage an MSP in the next year to migrate to Azure or to manage their cloud and/or on-premises environment. The survey also underlines Azure's popularity with 46 percent of respondents running at least half of their IT infrastructure and workloads on the service. The top benefit of working with a MSP to manage Azure is seen as… [Continue Reading] -

Businesses fail to take full advantage of data science
Publié: février 16, 2017, 3:54pm CET par Ian Barker
The benefits of data science are widely recognised according to a new survey, but 22 percent of users are failing to take full advantage of the data available. The study by Continuum Analytics, the company behind the Anaconda open source data platform, surveyed 200 data science and analytics decision makers at US organizations of all sizes and industries, as well as more than 500 data scientists to uncover similarities and disparities between the two groups. Among the findings are that 73 percent of respondents rank data science as one of the top three most valuable technologies they use. However, a… [Continue Reading] -

Americans more concerned about online privacy and security than a year ago
Publié: février 16, 2017, 3:08pm CET par Ian Barker
New data released today shows that Americans are increasingly concerned about their online privacy and security, including apprehension about increased government surveillance in the new presidential administration. The survey by secure access specialist AnchorFree of over 1,000 users of the company's Hotspot Shield personal VPN application reveals 84 percent say they are more concerned about their online privacy and security today than they were a year ago. Among other findings are that 64 percent say they are more concerned about keeping personal information private today because of the new presidential administration. Also, 50 percent are more concerned about online privacy… [Continue Reading] -

How will 3D printing affect your life?
Publié: février 16, 2017, 2:24pm CET par Ian Barker
3D printing is one of those technologies that’s been hovering on the edge of public consciousness for a few years without ever hitting the mainstream. But as the technology has matured and the machines become cheaper, 3D printing is set to affect all of us. UK electronics supplier RS Components has put together an infographic showing how 3D printing will develop over the next few decades. In the short term it predicts that by 2020 many aircraft parts will be 3D printed, saving weight and leading to more efficiency. In 2025 we could be 3D printing replacement human organs using modified… [Continue Reading] -

Is ransomware in decline or just evolving?
Publié: février 16, 2017, 1:07pm CET par Ian Barker
According to a new report from the Microsoft Malware Protection Center, the volume of ransomware being encountered is reducing. Data from Windows Defender Antivirus shows that after peaking in August, when 385,000 encounters were registered, ransomware encounters dropped almost 50 percent in September, and have continued to decline. But this doesn't mean we’re seeing the end of the menace. The attack vectors being used, the number of new ransomware families being released and the sophistication of the code suggests it isn't going away any time soon. Microsoft's monitoring of ransomware over the last year reveals that every quarter, more than… [Continue Reading] -

IBM and The Weather Company use edge computing to issue vital alerts
Publié: février 15, 2017, 5:15pm CET par Ian Barker
Communicating news of severe weather events or natural disasters is something mobile phones are well suited to, but if there's limited or disrupted network coverage the message may fail to get through. IBM and The Weather Company have developed a new app that will use peer-to-peer connections within the mesh network to send alerts to individuals via their smartphone devices. The mesh network technology links other nearby phones to extend the signal to help keep citizens connected and informed, and in the most severe conditions, might even help save a life. This is especially important in emerging markets, as well… [Continue Reading] -

New challenger takes on US inter-carrier mobile messaging duopoly
Publié: février 15, 2017, 4:11pm CET par Ian Barker
In the US a duopoly exists between SAP and Syniverse for inter-carrier mobile messaging. Carriers and other communication service providers are forced to choose between these two vendors to exchange messages across networks. This makes the carriers vulnerable to price hikes and sub-par quality of service. New provider tyntec is seeking to disrupt the market and create more competition with its new Inter Carrier Messaging Service (ICMS). The company is aiming to build on its experience in application to person (A2P) messaging to offer enterprises and operators one simple connection to billions of SMS and MMS users, on multiple mobile… [Continue Reading] -

Optimizing costs is top priority among corporate cloud users
Publié: février 15, 2017, 3:33pm CET par Ian Barker
Cloud management company RightScale has released the results of its sixth annual State of the Cloud Survey, the largest survey of corporate cloud users. Among the findings are that optimizing cloud costs is the top initiative across all cloud users (53 percent) and especially among mature cloud users (64 percent). Respondents estimate 30 percent of cloud spend is wasted, while RightScale has measured actual waste at between 30 and 45 percent. Despite an increased focus on cloud cost management, only a minority of companies are taking critical actions to optimize their cloud costs, such as shutting down unused workloads or… [Continue Reading] -

Businesses are being held back by enterprise software
Publié: février 15, 2017, 2:30pm CET par Ian Barker
Businesses and IT executives are frustrated by their current software and more than 80 percent of executives have had to change a part of their daily operations to match the way their software works according to a new report. The survey of over 500 executives carried out by development platform provider TrackVia finds that integration or compatibility with other software and applications is cited as the top priority by 32 percent, yet also the biggest challenge (31 percent) for executives. But existing enterprise software is failing as a solution, 76 percent say they have replaced enterprise software programs, because they… [Continue Reading] -

89 percent of consumers don't pay for mobile malware protection
Publié: février 15, 2017, 1:14pm CET par Ian Barker
A new survey reveals that a large majority of mobile users do not currently pay for malware protection. However, 61 percent say they do want, and are willing to pay for, protection services from their service provider. The study from security solutions company Allot Communications shows that rather than independently seek out, evaluate and download security apps for each of their mobile devices, consumers would like a one-stop-shop for online protection for themselves and their families. This presents communication service providers (CSPs) with an opportunity to sell an extra service, which many of them are not taking advantage of. "CSPs have… [Continue Reading] -

New platform helps enterprises comply with privacy regulations
Publié: février 14, 2017, 3:50pm CET par Ian Barker
Privacy regulations like the EU General Data Protection Regulation (GDPR) mean that enterprises can face substantial fines for non-compliance. As 2016 saw a record number of personal record data breaches this is something all businesses need to take seriously. At RSA today, privacy specialist BigID is announcing the general availability and pricing for its new enterprise privacy management platform. This looks to help companies protect their customers' personal data through the application of machine learning and identity intelligence to data privacy. "It has become increasingly difficult for companies to stay ahead of data breaches. As a reaction to this, many… [Continue Reading] -

Logtrust launches real-time integrated threat analytics
Publié: février 14, 2017, 2:46pm CET par Ian Barker
Big data analytics specialist Logtrust is using RSA to launch a new solution for delivering real-time, integrated threat analytics. The program enables companies to build solutions that analyze the historical behavior of systems and attackers in order to detect, understand and eliminate potential threats in real-time -- even those that are coming from multiple sources, across multiple devices. Key features of the Logtrust solution include the ability to continuously ingest multiple log formats, and conduct searches and queries on live and historical data via simple point-and-click interface without complicated coding. Fast historical analysis can be carried out, allowing analysts to… [Continue Reading] -

Majority of enterprises use more than 10 mobile business apps
Publié: février 14, 2017, 11:54am CET par Ian Barker
Almost 80 percent of companies are using more than 10 mobile apps for business, according to a new report. The third edition of the Mobile Security and Risk Review by MobileIron also finds that 18 percent of companies use Apple's Volume Purchase Program (VPP) to streamline their app deployment. The rate of VPP use is significantly higher in the healthcare (29 percent) and government (25 percent) sectors. In addition, 13 percent of organizations use Device Enrollment Program (DEP), which offers more control over corporate mobile fleets. With DEP, enterprises can enforce tighter restrictions on corporate-owned, supervised devices. Nearly a quarter… [Continue Reading] -

IBM brings the power of Watson to cyber security
Publié: février 13, 2017, 5:31pm CET par Ian Barker
The technology industry is having to contend with ever more sophisticated cyber security threats. With a growing shortage of security analysts and masses of data to process this throws more emphasis on the use of AI techniques. This week at RSA Conference, IBM Security will be demonstrating what the "cognitive security operations center" of the future will look like, including new Watson-powered tools for investigating security events, new services for building these SOCs and breakthrough research that allows customers and analysts to interact with Watson through voice and chat. According to IBM research, security teams sift through more than 200,000 security… [Continue Reading] -

Breach analytics platform speeds up incident response
Publié: février 13, 2017, 4:24pm CET par Ian Barker
It's increasingly said by experts that data breaches are now a matter of when rather than if. Being able to respond quickly is therefore vital for companies to minimize damage and disruption. Cybersecurity solutions and breach analytics cloud platform Eastwind Networks is launching an enhanced Breach Analytics Cloud platform to provide complete visibility across the entire attack surface. It works by collecting telemetry from hybrid environments, traditional and non-traditional networks, cloud software and infrastructure providers, and off-premise users. Using machine learning it can identify where an entity became an outlier and use that model to retrospectively analyze an entire dataset… [Continue Reading] -

2016: 'The year of ransomware'
Publié: février 10, 2017, 3:46pm CET par Ian Barker
Ransomware attacks aren't new, but 2016 saw them increasing in frequency and sophistication as cyber criminals see a lucrative revenue opportunity. UK-based Technology Services Group has produced an infographic that looks at ransomware’s rapid rise. Among the highlights are a 3,500 percent rise in attacks during 2016, there’s also been a 600 percent increase in the number of new ransomware families between December 2015 and April 2016. Overall 41 percent of businesses have been hit by ransomware, but in the UK the figure is 54 percent, with ransomware accounting for a quarter of all attacks on businesses. A worrying 37… [Continue Reading] -

8 out of 10 Brits feel misled by advertised broadband speeds
Publié: février 10, 2017, 3:03pm CET par Ian Barker
The way broadband speeds in the UK are advertised is misleading according to 80 percent of respondents to a new survey. Broadband comparison site Cable.co.uk interviewed 2,000 consumers with 58 percent finding advertised speeds "very misleading" and 22 percent saying they are "somewhat misleading". Current guidelines allow broadband providers to advertise 'up to' speeds, but these are achievable by only around 10 percent of customers. Consumers feel that at least 66 percent of users should be able to get the top speed in order for it to be legitimately used in advertising. Older people are more likely to find advertised… [Continue Reading] -

Microsoft teams up with Skycure to fight mobile threats
Publié: février 10, 2017, 11:49am CET par Ian Barker
Cyber threats to enterprises aren't confined to the desktop, mobile systems are at risk too and businesses are looking for solutions that can combine security with ease of management. Mobile threat defense company Skycure has announced that it's working with Microsoft to integrate its Skycure platform with Microsoft Enterprise Mobility + Security (EMS). Skycure's integration with EMS delivers mobile device threat intelligence directly to Microsoft Intune, providing additional inputs into Intune's device compliance settings. The integration allows Intune to dynamically control access to corporate resources and data based on Skycure's real-time analysis. The combination allows IT administrators to set rules… [Continue Reading] -

The secrets of top performing information security officers
Publié: février 9, 2017, 5:09pm CET par Ian Barker
A new study based on two years of work by IANS Research looks at the work of chief information security officers (CISOs) and their role in enterprises. The report identifies concrete actions CISOs should consider taking to progress their programs from where they are today to the next level. Among the findings of the CISO Impact report are that high-performing CISOs know the value of engaging to drive change. In the data three out of four of high performers embrace this approach, compared to one in 20 of the low performers. All the highest performers have followed the route of… [Continue Reading] -

Popular Windows development UI library goes open source
Publié: février 9, 2017, 4:08pm CET par Ian Barker
User interface controls are important to creating applications for use across different devices as they need to retain the native look and feel of the OS. To make life easier for .NET developers development company Progress is making its Telerik UI for Universal Windows Platform (UWP) open source. Telerik UI offers developers a set of native UI controls for building Windows apps. As well as reducing coding and time to market, it enables developers to remove the repetitive, tactical elements of development to focus on solving business challenges. By making Progress Telerik UI for UWP open source and part of… [Continue Reading] -

Next generation email security addresses advanced threats
Publié: février 9, 2017, 3:28pm CET par Ian Barker
Despite other developments in malware, email remains a favourite route for attackers because it's easy for people to fall victim to phishing and other threats. Network security company SonicWall is launching a new next-generation email security platform to help guard against ransomware, zero-day and advanced threats. SonicWall Email Security 9.0 integrates with the Capture Advanced Threat Protection (ATP) service and uses cloud-based sandboxing technology to detect advanced threats by scanning a range of email attachment types. It then analyzes them in a multi-engine sandbox, blocking them until reviewed by an administrator, and rapidly deploying remediation signatures. The solution incorporates anti-spam,… [Continue Reading] -

Invisible malware targets financial information
Publié: février 9, 2017, 12:01pm CET par Ian Barker
Researchers at Kaspersky Lab have uncovered a series of targeted attacks that use legitimate software to avoid detection. The attacks employ widely available penetration-testing and administration tools as well as the PowerShell framework for task automation in Windows. They drop no malware files onto the hard drive, but hide in the memory. This combined approach helps to avoid being detected by whitelisting technologies, and leaves forensic investigators with almost no artifacts or malware samples to work with. The attackers stay around just long enough to gather information before their traces are wiped from the system on the first reboot. The… [Continue Reading] -

Enterprise change management goals are out of sync with strategy
Publié: février 8, 2017, 6:06pm CET par Ian Barker
The results of a new study to be released tomorrow, but seen exclusively by BetaNews, reveal a severe misalignment between the way IT leaders talk about change management and the strategies they have in place to execute these initiatives. The survey of more than 320 IT leaders by document productivity company Nitro shows that change management strategies vary between organizations, but many fall short. Three out of four respondents state that a vendor's level of change management support has played a role in their decision to sign an agreement. 87 percent rank customer support resources as an important factor in… [Continue Reading] -

Security consultancy offers $1 million guarantee against breach-related costs
Publié: février 8, 2017, 5:17pm CET par Ian Barker
One of the biggest worries for businesses is the cost of suffering a major cyber attack in terms of both money and business reputation. San Francisco-based independent security consultancy AsTech is so confident of its track record that it's offering a $1 million warranty against breach-related costs if an organization using its Paragon Security Program suffers unauthorized access to non-public information through a vulnerability that AsTech fails to discover. AsTech joins SentinelOne, WhiteHat Security, Cymmetria and a few others in offering some form of financial guarantee to customers in the event of successful cyber attacks on their applications and networks… [Continue Reading] -

DDoS tactics shift towards a blended approach
Publié: février 8, 2017, 4:25pm CET par Ian Barker
The world of cyber security is a constant arms race with attackers and defenders constantly on the lookout for an edge. Cyber security company NexusGuard has released its latest threat report for the final quarter of 2016, and notes a shift towards blended DDoS attacks combining multiple vulnerabilities with the intent of overloading targeted monitoring, detection and logging systems. Attacks rose by more than 150 percent between November and December 2016, which researchers attribute to the outbreak of the Mirai botnet source code. Financial and government institutions were the primary industry focus of hybrid attacks in Q4 2016. Nexusguard analysts… [Continue Reading] -

The problems facing the app development industry
Publié: février 8, 2017, 3:49pm CET par Ian Barker
The app development business is being plagued by long development times, skills gaps and large backlogs according to a new report. The study from low-code development platform supplier OutSystems identifies the critical issues that the industry needs to address if it’s to avoid missed opportunities and lost revenue. Well over half of IT professionals (62 percent) report having a backlog of mobile apps, some with more than 10 apps waiting to be developed. Although 88 percent of respondents say that mobile functionality is either a requirement or very important, 37 percent of organizations report facing a shortage of mobile developers… [Continue Reading] -

Duo Security launches fast, simple alternative to VPN
Publié: février 8, 2017, 3:13pm CET par Ian Barker
Enterprise users increasingly want access to their data while they're out of the office. This generally requires a VPN or Network Access Control (NAC) solution but these can be time consuming and complex to set up and administer. To make things faster and simpler, trusted access specialist Duo Security is launching a major commercial implementation of Google's BeyondCorp framework that drastically improves and simplifies management of how employees and devices access critical corporate applications. According to Duo a third of access requests to a corporate network come from outside the firewall, increasing the risk for unauthorized remote access to sensitive… [Continue Reading] -

Threat hunting gains in popularity to combat cyber threats
Publié: février 8, 2017, 2:33pm CET par Ian Barker
The use of threat hunting techniques to combat cyber attacks is increasing according to a new report. The study by Crowd Research Partners of cybersecurity professionals in the 350,000 member Information Security Community on LinkedIn reveals that threats are rising dramatically and that deployment of sophisticated threat hunting platforms can significantly accelerate the time needed to detect, investigate and fix threats. "Following the unprecedented wave of cybersecurity attacks, threat hunting is emerging as a new line of defense and the latest innovation for security operations centers (SOCs) to combat advanced security threats," says Holger Schulze, founder of the Information Security… [Continue Reading] -

Druva launches improved ransomware protection for enterprises
Publié: février 7, 2017, 5:49pm CET par Ian Barker
Ransomware is a big problem for today's enterprises, the US Department of Justice reports an average of 4,000 ransomware attacks occur in the US every day. This means detection and fast action is more important than ever. Cloud data protection company Druva is launching an enhanced version of its platform to manage the ransomware threat from detection right through to recovery. It works by continually assessing the characteristics of file changes and their types. For example abnormal deletions, unusual file modifications and updates, and identifying an unusually large number of file creations, all of which could be a sign of… [Continue Reading] -

New product delivers 'self-healing' endpoint security
Publié: février 7, 2017, 5:03pm CET par Ian Barker
Increasing numbers of companies are coming to accept that it's only a matter of time before they become the victim of some form of data security breach. This means they need to be able to detect and respond to threats more quickly. Cloud-based security platform Absolute is launching a new Application Persistence product to provide embedded, self-healing capabilities to third-party endpoint controls such as VPN, anti-virus, encryption, systems management and other critical controls that are too easily compromised. Application Persistence allows enterprises to harden their security, giving all of the agents on their endpoints the ability to self-heal or reinstall… [Continue Reading] -

New solution cuts risk from unstructured data
Publié: février 7, 2017, 3:30pm CET par Ian Barker
Businesses understand the need to look after sensitive data, but a problem often arises in knowing where that data is. Unstructured information held in folders and documents is just as valuable to hackers as database records and is harder to protect. Identity management company SailPoint is launching its latest data governance solution, allowing enterprises to guard sensitive files wherever they reside. SecurityIQ 5.0 gives enterprises the ability to discover where sensitive data is stored in files and folders, eliminate overexposed permissions, and apply centralized management and access controls over unstructured data in systems running on-premises or in the cloud. It also… [Continue Reading] -

Unified security management comes to the cloud
Publié: février 7, 2017, 3:23pm CET par Ian Barker
Implementing effective security can be time consuming, complex and costly, more so given the adoption of cloud-based systems. Unified security management (USM) specialist AlienVault is aiming to simplify things with the release of USM Anywhere, an all-in-one Software-as-a-Service (SaaS) security monitoring platform. USM Anywhere is designed to centralize threat detection, incident response and compliance management of cloud, hybrid cloud, and on-premises environments from a single cloud-based console. "AlienVault has been rethinking cybersecurity and meeting the needs of resource-constrained organizations for nearly a decade with our USM Appliance and Open Threat Exchange offerings," says Denny LeCompte, senior vice president of products… [Continue Reading] -

ZTE leads the way in unwanted call protection
Publié: février 7, 2017, 1:24pm CET par Ian Barker
Phone spam from robot calling systems is a major issue in the US and around the world, prompting regulators to look at controlling the problem. Smartphone maker ZTE is taking a proactive approach and teaming up with caller profile service Hiya to integrate caller identification, spam detection and call blocking into its latest Axon 7 handset. This makes ZTE the first mobile manufacturer to provide free caller ID and spam protection for consumers in the US to protect themselves from unwanted callers the moment they turn on their device. "The rise of robocalls is staggering, with more than 10 billion of… [Continue Reading] -

'Streaming Prevention' technology takes a new approach to stopping cyber attacks
Publié: février 6, 2017, 5:33pm CET par Ian Barker
Traditional security techniques can be effective in fending off cyber threats, but a new generation of non-malware attacks try to gain control of computers without downloading malicious software. Instead, they use trusted, native operating system tools, such as PowerShell, and exploit running applications, like browsers. Endpoint security specialist Carbon Black is launching a new tool which can combat both types of threat. Called Streaming Prevention it uses event stream processing to continuously update a risk profile based on a steady stream of activity. Where legacy AV solutions and static, machine-learning approaches focus on detecting malware at the point-in-time it is written… [Continue Reading] -

Democracy 'threatened' by the social media echo chamber
Publié: février 6, 2017, 2:40pm CET par Ian Barker
In the wake of Donald Trump's election in November, we looked at the phenomenon of social media bubbles and the effect they have on political discourse. Research released by UK political think tank Demos reveals some of the extent of the echo chamber effect in political discussions on Twitter. Demos looked at 2,000 users of Twitter all of whom expressed open support for either the Conservative Party, the Labour Party, The UK Independence Party (Ukip) or the Scottish National Party (SNP). A further 500 acted as a control group expressing no party allegiance. The results show, perhaps not surprisingly, that… [Continue Reading] -

Democracy 'threatened' by the social media echo chamber
Publié: février 6, 2017, 2:40pm CET par Ian Barker
In the wake of Donald Trump's election in November, we looked at the phenomenon of social media bubbles and the effect they have on political discourse. Research released by UK political think tank Demos reveals some of the extent of the echo chamber effect in political discussions on Twitter. Demos looked at 2,000 users of Twitter all of whom expressed open support for either the Conservative Party, the Labour Party, The UK Independence Party (Ukip) or the Scottish National Party (SNP). A further 500 acted as a control group expressing no party allegiance. The results show, perhaps not surprisingly, that… [Continue Reading] -

The US cities with the highest malware infection rates
Publié: février 3, 2017, 3:44pm CET par Ian Barker
Computers located in Tampa, Orlando, and St. Louis are more likely than those in other US cities to be infected with malware. This is according to a new report from ESG, the company behind the SpyHunter anti-spyware program. It compiled its results from SpyHunter detection data across the 100 largest cities in the United States in 2016. The same three cities came top of the list of infection rates in 2015 too. In 2016 Tampa had infection rates 540 percent higher than the national average, Orlando 525 percent higher and St. Louis 520 percent higher. This could be down to… [Continue Reading] -

Threat hunting and why combating cyber attacks needs a human element [Q&A]
Publié: février 3, 2017, 11:09am CET par Ian Barker
The threat landscape facing businesses is more complex than ever and it's rapidly changing. No surprise then that traditional approaches to security are struggling to cope. This has led some security companies to turn to a more dynamic approach of seeking out threats rather than simply responding to attacks. We spoke to Adam Bateman Managing Director of Countercept at specialist information security company MWR Info Security to find out more about threat hunting, what it does and how it can be implemented, plus why we can't afford to ignore the human angle. BN: Why are traditional security techniques no longer… [Continue Reading] -

Enterprises fear brand damage more than data breaches
Publié: février 2, 2017, 3:54pm CET par Ian Barker
The biggest fear for organizations is long-term damage to brand and reputation, yet despite this three quarters lack a comprehensive risk management strategy. This is one of the findings of a survey for risk intelligence company RiskVision carried out by the Ponemon Institute, it reveals that 63 percent of organizations are worried about reputation and brand damage. This is followed by security breaches (51 percent), business disruption (51 percent) and intellectual property loss (37 percent). But despite these fears 76 percent say they either don't have a clearly defined risk management strategy in place or the one they do have… [Continue Reading] -

Speed of fixing bugs holds back software deployment
Publié: février 2, 2017, 12:34pm CET par Ian Barker
Developers want to deploy software releases faster, but the time taken to fix bugs is holding them back according to new research. A survey for cloud testing platform Sauce Labs carried out by Dimensional Research reveals that 28 percent of those surveyed say they want to deploy hourly (up from 18 percent in 2016). Last year only eight percent said they were not deploying as fast as they wanted to, but that percentage has nearly doubled to 14 percent this year. However, the survey also reveals the ability to fix bugs once they've been identified is holding things back. No… [Continue Reading] -

IT teams fall behind in automation
Publié: février 1, 2017, 4:47pm CET par Ian Barker
While businesses are focused on digital transformation to deliver greater efficiency and higher profits, IT teams themselves are falling behind the curve according to a new report. The survey from IT services and solutions provider Dimension Data shows that IT staff only spend 14.5 percent of their time on innovation and new projects. Automation is seen as a key enabler for optimized IT operations, but only 20 percent of surveyed companies say their IT operations are fully automated. Nine percent of organizations say they have no automation, 13 percent have limited automation, 32 percent have a medium level of automation… [Continue Reading] -

New database release enables data-driven decisions in real time
Publié: février 1, 2017, 3:56pm CET par Ian Barker
Many organizations rely on databases to support their decision making processes, but the process of importing, analyzing and then acting on the data can inhibit fast action. In-memory SQL database specialist, VoltDB is releasing version 7.0 of its to offer increased scalability for managing transactions and generating analytics while ensuring high availability and strict data consistency. Features of the new release include more power and data security for geographically-dispersed datacenters. VoltDB v7.0 includes powerful multi-site/cluster, multi-version cross-datacenter replication (XDCR), this lowers application latency and improves availability and disaster recovery for geographically-distributed workloads across multiple datacenters. In addition it offers enhanced… [Continue Reading] -

Exploit acquisition program aims to patch mobile vulnerabilities faster
Publié: février 1, 2017, 3:03pm CET par Ian Barker
Even after new mobile threats have been identified the number of devices in use means it can take time for patches to be rolled out to all users. Mobile threat defense company Zimperium is hoping to tackle this problem with the launch of a $1.5 million bounty program to purchase N-day exploits which have been identified but are still usable on unpatched devices. The Exploit Acquisition Program focuses on N-day vulnerabilities for Android and iOS devices. While most bug bounty programs purchase zero-days, or unknown vulnerabilities, and then develop a patch, millions of users remain at risk due to poor… [Continue Reading] -

Survey reveals the true cost of data breaches
Publié: février 1, 2017, 12:19pm CET par Ian Barker
More than a third of organizations that experienced a data breach in 2016 reported substantial customer, opportunity and revenue loss of more than 20 percent. This is a key finding of the latest Cisco Annual Cybersecurity Report which also shows that after attacks, 90 percent of these organizations are improving threat defense technologies and processes. Steps being taken include separating IT and security functions (38 percent), increasing security awareness training for employees (38 percent), and implementing risk mitigation techniques (37 percent). The survey of 3,000 chief security officers and security operations leaders from 13 countries reveals budget constraints, poor compatibility… [Continue Reading] -

Slack sets its sights on large enterprises
Publié: février 1, 2017, 11:31am CET par Ian Barker
The Slack team collaboration tool has proved popular with many businesses since it first launched in 2013. Now Slack is aiming to carry its success into larger organizations with the launch of Slack Enterprise Grid, offering the adaptability to create communication structures which mirror how teams already collaborate. Grid has already been tested in big companies including PayPal, Capital One, and IBM that have been providing feedback on how it works. "Whether physical or digital, our teams expect workspaces that empower them to communicate efficiently, connect and ideate easily, and build new products quickly -- wherever they are -- and… [Continue Reading] -

2016's top malware threats show a shift in attack patterns
Publié: janvier 31, 2017, 4:51pm CET par Ian Barker
The methodology of malware and cyber attacks has shown a significant shift in 2016, according to the State of Malware report from Malwarebytes. Although ransomware is the favorite attack method used against business, ad fraud malware is growing fast and poses a substantial threat to both consumers and businesses. The report shows ransomware distribution between January 2016 and November 2016 increased by 267 percent. In the fourth quarter of 2016 nearly 400 variants of ransomware were cataloged by Malwarebytes. Ransomware detections accounted for 12.3 percent of all enterprise threats, but only 1.8 percent of consumer threats, and 81 percent of… [Continue Reading] -

New intelligence platform aims to cut credential-based risks
Publié: janvier 31, 2017, 4:12pm CET par Ian Barker
Many cyber attacks are made using stolen or abused credentials. One of the ways to combat this is to collect activity data and use it to spot anomalous behavior patterns. Leader in this field Exabeam is launching its new Security Intelligence Platform, designed to decrease the risk of cyber threats for organizations of any size. It addresses the need to collect more data than ever before, to make better connections across that data to detect threats, and to augment human analysts during incident response. "Data breaches are now affecting national political and economic systems, and the technologies that have been… [Continue Reading] -

Comodo extends endpoint protection to Mac and Linux
Publié: janvier 31, 2017, 3:37pm CET par Ian Barker
Businesses are increasingly aware of the need to protect their endpoint systems. However, they tend to concentrate most of their efforts on Windows which can leave other platforms vulnerable. Cyber security specialist and digital certificate provider Comodo is launching a new version of its Advanced Endpoint Protection (AEP) product that extends availability of its default-deny endpoint security to Mac and Linux platforms, in addition to Windows. Comodo AEP offers a complete endpoint protection platform using multiple security technologies, including anti-virus, host-based intrusion prevention system (HIPS), web filtering, personal firewall, white/blacklisting and Secure Auto-Containment. It also provides management and reporting in… [Continue Reading] -

Tenable launches cloud-based vulnerability management
Publié: janvier 31, 2017, 1:11pm CET par Ian Barker
Increased adoption of virtualization, the cloud, and the accelerating use of web applications and short-lived assets like containers has led to changes in how and when companies need to assess vulnerabilities. Cyber security firm Tenable Network Security is launching a new cloud-based vulnerability management platform to enable enterprises to secure the full range of assets in modern elastic IT environments. Called Tenable.io it offers asset tracking using an advanced fingerprinting algorithm to pinpoint the true identity of each resource -- even dynamic assets like laptops, virtual machines and cloud instances. This allows customers to better understand the true state of… [Continue Reading] -

The Big Shift in IT Leadership -- free ebook from Wiley
Publié: janvier 31, 2017, 11:51am CET par Ian Barker
The IT world has undergone some major changes in recent years, but in many cases management hasn't kept up with what's happening, leaving enterprises struggling to keep up with the competition. IT leaders need to understand how they can use resources effectively to drive business growth, find the right talent and ultimately increase profitability. A new ebook, The Big Shift in IT Leadership from Wiley, is aimed at helping managers lead their teams and ensure they use technology effectively for business growth. BetaNews readers can get hold of a copy (worth $30) for free by visiting this page and entering… [Continue Reading] -

Kaspersky and ESET top the security charts
Publié: janvier 30, 2017, 5:11pm CET par Ian Barker
The way people access the internet is changing, with a shift towards portable devices, and that in turn has led to a shift in the software they use. Independent testing company AV-Comparatives has conducted its annual survey focusing on which security products (free and paid) are employed by users, along with their OS and browser usage. The results show that Kaspersky Lab and ESET are the two most popular desktop security products worldwide. They also feature in the top four products on every continent. In addition, Kaspersky is the most popular mobile security solution worldwide, while ESET and Avast make… [Continue Reading] -

Vulnerabilities could leave thousands of NETGEAR routers exposed
Publié: janvier 30, 2017, 4:38pm CET par Ian Barker
New vulnerabilities discovered in 31 models of NETGEAR router are reckoned to leave at least 10,000 devices at risk and could affect many more. Cyber security company Trustwave has released details of the vulnerabilities which allow an attacker to discover or completely bypass any password on a NETGEAR router, giving them complete control of the router, including the ability to change configuration, turn infected routers into botnets or even upload entirely new firmware. The vulnerability can be used by a remote attacker if remote administration is set to be internet facing. By default this is not turned on. However, anyone… [Continue Reading] -

New platform offers holistic risk assessment for enterprises
Publié: janvier 30, 2017, 3:21pm CET par Ian Barker
The proliferation of cloud services and diverse platforms in modern enterprises makes guarding against risk and protecting data a major challenge. Cyber risk assurance company TechDemocracy is addressing this problem with the launch of a new platform to analyze the effectiveness of existing cyber risk and compliance solutions and offers a consolidated view of enterprise risk posture. Called Intellicta it's designed to help boards of directors and senior management teams bridge the visibility gaps across their compliance, security, risk, and governance functions. Using a single dashboard, the Intellicta platform presents situational awareness for the overall cyber risk across the enterprise,… [Continue Reading] -

The future of home technology
Publié: janvier 30, 2017, 12:11pm CET par Ian Barker
Technology tends to creep up on us and before we know it is an essential part of our lives. In the home we're already seeing increasing numbers of smart devices like thermostats and light bulbs, but what else is on the horizon? Electronics company RS Components has produced an interactive graphic showing some of the things we can look forward too. Among its predictions are that by 2020 smart windows will be available that will turn opaque with the touch of a button, eliminating the need for blinds and curtains. By 2030 your bed will nudge you to improve your… [Continue Reading] -

40 percent of British children use the internet unsupervised
Publié: janvier 27, 2017, 12:55pm CET par Ian Barker
Connected devices are a big part of all our lives and that goes for younger members of the family too, but of course connecting to the internet means risk. A new survey from Intel Security shows 40 percent of British parents do not keep track of their children's online activity, so they don't know when their children are online or what websites and content they're accessing. According to the survey of 13,000 people, 79 percent are concerned about their children interacting with a social predator or cyber criminal online, and 23 percent of parents say they've found their children visiting… [Continue Reading] -

Mid-market enterprises are too confident of their cyber security
Publié: janvier 26, 2017, 5:27pm CET par Ian Barker
Mid-market enterprises have very high confidence in their cyber security defenses, but in reality they struggle to defend against malicious activity which has become more sophisticated, more targeted and more severe. Security operations-as-a-service company Arctic Wolf Networks along with research firm Vanson Bourne, surveyed IT decision makers at 200 companies with between 500 and 3,000 employees and uncovered a disparity between what IT professionals believe versus the reality of their security posture. It finds a large majority (95 percent) of IT professionals believe their cybersecurity posture is above average to great, yet 100 percent of these same respondents report that their organization's… [Continue Reading] -

Bot traffic takes back the web
Publié: janvier 25, 2017, 4:04pm CET par Ian Barker
Just over a year ago we reported that, for the first time in five years, human web traffic had overtaken bot traffic. It seems, however, that human dominance was short lived. The latest Imperva Incapsula Bot Traffic Report shows that in 2016 the bots were back on top with 51.8 percent of online activity, although it's an increase in good bot activity that has driven the trend. Good bots now account for 22.9 percent of all activity, up from 19.5 percent in the last report. Feed fetchers were the most active good bot in 2016, responsible for 12.2 percent of… [Continue Reading] -

New platform brings enterprise-grade eCommerce to smaller businesses
Publié: janvier 25, 2017, 1:27pm CET par Ian Barker
Doing business on the internet is deceptively simple, but for start-ups and smaller businesses, having the resources to do it well can prove elusive. UK-based website conversion and digital advertising company Ve Interactive is launching a new self-service platform aimed at giving smaller companies full control of their online marketing and generate more online sales. The platform will give users instant access to Ve's consumer-centric onsite engagement panel as well as its intelligent email marketing solution. Both of these aim to increase customer engagement, prevent needless abandonment and turn more online browsers into buyers. All of the technology is mobile-friendly, fully… [Continue Reading] -

Cyber criminals develop service to protect themselves from scammers
Publié: janvier 24, 2017, 4:38pm CET par Ian Barker
Cyber crime is a competitive business, particularly for those who buy and sell their dubious services via online marketplaces. But that competition can lead to the scammers being scammed. So called 'rippers' seek to defraud other criminals by selling dumps of fake social media credentials or invalid credit card details, or taking money without delivering the promised goods. Needless to say this doesn't go down all that well in the criminal fraternity and experts at cyber security company Digital Shadows have discovered and mapped a fast-growing service called Ripper.cc that cybercrime backers have created to blacklist the frauds and fakers… [Continue Reading] -

Aegis launches new generation secure flash drive
Publié: janvier 24, 2017, 4:11pm CET par Ian Barker
Last year we reviewed the Aegis Secure Key 3.0 encrypted flash drive. Apricorn, the company behind it, has now launched a new 3z version delivering even more security. The Secure Key 3z offers top-level security innovation (FIPS 140-2 level 3 validation pending) at a lower cost and in a smaller form factor than before. It's accompanied by Aegis Configurator, a Windows-based software package that allows 10 or more compatible Aegis Secure Devices to be set up and configured simultaneously. Combined with the Aegis Configurator, the Aegis Secure Key 3z flash drive provides a seamless workflow for secure storage rollouts. This… [Continue Reading] -

93 percent of organizations have technical challenges protecting data
Publié: janvier 24, 2017, 3:06pm CET par Ian Barker
Data breaches can be extremely damaging for enterprises, leading to loss of consumer confidence, loss of revenue and even regulatory fines. But despite the importance of data security a new study by Forrester Consulting on behalf of data protection specialist Varonis Systems, finds that organizations are often focused on threats rather than their data and don't have a good handle on understanding and controlling sensitive information. Although making heavy investment in a variety of data security tools as part of their strategy, 93 percent of respondents report persistent technical challenges in protecting their data. In addition 96 percent believe a unified approach… [Continue Reading] -

Let there be light (and sound) -- Inateck Tomons DL1101 [Review]
Publié: janvier 24, 2017, 11:17am CET par Ian Barker
Is it a lamp? Is it a speaker? Is it a media player? Is it a radio? Actually the DL1101 is all of these things rolled into one. It can connect to a sound source via Bluetooth or play music from a Micro SD card, there's a built-in FM receiver and it lights up, all of this for around $20. The on-board battery needs to be charged through its USB connection. It can deliver up to eight hours of life on a full charge but this obviously depends on volume levels and how bright you have the light. Power and playback… [Continue Reading] -

AI-powered chatbot helps combat cyber attacks
Publié: janvier 20, 2017, 3:09pm CET par Ian Barker
The key to defeating cyber attacks lies in being able to make the correct response in a timely manner, but frontline security staff may lack the skills or resources to spot problems early. Endpoint security company Endgame is launching an intelligent assistant built to automate security operations analyst actions and guide users of any skill level to detect and respond to advanced attacks. Called Artemis, the software uses machine learning and natural language processing techniques that enable it to anticipate priorities for security teams and detect patterns in malicious behavior before the analyst knows to look for it. The company… [Continue Reading] -

Data breaches up by 40 percent in 2016
Publié: janvier 20, 2017, 11:51am CET par Ian Barker
The last year has seen fewer of the large scale breaches that made the headlines in 2014 and 2015, but that doesn’t mean the problem has gone away. A new report from CyberScout and the Identity Theft Resource Center (ITRC) has found a 40 percent increase in the US with a total of 1,093 data breaches in 2016, up from 780 in 2015. The leading cause of data breach incidents was hacking/skimming/phishing attacks, accounting for 55.5 percent of the overall number of breaches, an increase of 17.7 percent over 2015 figures. This type of attack also accounted for 72 percent… [Continue Reading] -

Consumers are starting to get the message on phishing
Publié: janvier 19, 2017, 5:54pm CET par Ian Barker
According to a new report from security awareness training company Wombat Security, people are starting to get the message on phishing. When asked, 'What is phishing?', 65 percent of those surveyed in the US answered correctly. Ransomware remains a bit of a mystery for many, however, 52 percent were not even able to hazard a guess in response to 'what is ransomware?' Despite an increase in awareness of the concept of phishing, end users continue to make their organization vulnerable through risky behaviors like checking personal email on work devices and keeping work data on their personal devices. There's also… [Continue Reading] -

Work and personal app usage blurs as enterprise users change their habits
Publié: janvier 19, 2017, 5:04pm CET par Ian Barker
The use of the cloud and as-a-service software models is having a big impact on the way businesses operate, but just how is this shift playing out? Identity management specialist Okta has collected anonymized data from its customers' networks around the world to create the third edition of its Businesses @ Work report looking at how organizations and the people who work for and with them get work done. Among its findings are that the role of IT is expanding and that the distinction between corporate apps and personal apps is fading away. It's also seeing early signs of a… [Continue Reading] -

Why advertisers need to wake up to mobile games
Publié: janvier 19, 2017, 3:06pm CET par Ian Barker
Mobile devices are increasingly used for many aspects of our lives and that includes playing games. But what does this mean for enterprises looking to promote their brands? New research from mobile engagement platform Tapjoy suggests that consumers are twice as likely to say they feel relaxed when playing mobile games than they are when using social apps and that means more potential for advertisers to get their message across. The survey of over 5,500 smartphone and tablet users shows respondents say they feel more focused (35 percent vs 11 percent), happier (34 percent vs 21 percent), and more engaged… [Continue Reading] -

Taxi drivers, cashiers and other jobs facing extinction by technology
Publié: janvier 19, 2017, 12:02pm CET par Ian Barker
One of the challenges facing developed economies is that increased use of technology is set to wipe out many jobs. This is leading politicians to explore schemes like national basic incomes so that people can support themselves in a world where work is less certain. But which jobs are most at risk of disappearing? UK services marketplace Bidvine has conducted a survey to find out how the public think advances in technology are changing the job market. The results make sobering reading for people in some occupations (if you're a taxi driver you may want to look away now). 36… [Continue Reading] -

Businesses not prepared for the risk from mobile and IoT apps
Publié: janvier 18, 2017, 5:01pm CET par Ian Barker
Despite widespread concern about the security of mobile and IoT applications, organizations are ill-prepared for the risks they pose, according to new research. The study from threat prevention company Arxan Technologies, IBM Security and the Ponemon Institute reveals that 60 percent of respondents believe it’s either certain or likely their organization has experienced a material data breach or cyber attack over the past 12 months that was caused by an insecure mobile app. In addition 46 percent believe the same is true as the result of an insecure IoT app. Despite this though only 32 percent say their organization urgently… [Continue Reading] -

Many consumers don't care about the impact of piracy
Publié: janvier 18, 2017, 3:55pm CET par Ian Barker
Almost a third of consumers watch pirated content even though they know it's illegal to do so and that it deprives the content creators of revenue. The study for platform security company Irdeto conducted by YouGov finds that 74 percent of US consumers know that sharing pirated content is illegal and 69 percent that downloading it is. Despite this, 32 percent of respondents admit to watching pirated content. When told that pirated video content can result in studios losing money, meaning they can’t invest in creating content, 39 percent say that this knowledge has no effect on the amount of… [Continue Reading] -

New Flock plug-in targets fake news -- you'll never guess what happens next
Publié: janvier 18, 2017, 3:31pm CET par Ian Barker
Fake and misleading stories plague the internet and there's always a risk that if not spotted they can influence decisions within an organization. Enterprise collaboration platform Flock is aiming to stop the spread of unreliable news, especially within business environments with the launch of a Fake News Detector plug-in. Flock FND identifies and flags content from sources deemed misleading, unverified or false when users share it on the Flock messaging and collaboration platform. When users unknowingly share suspect URLs into Flock chat boxes, Flock FND cross-references the link within a database of more than 600 verified fake news sources. When… [Continue Reading] -

Businesses missing out by not engaging customers with SMS
Publié: janvier 17, 2017, 5:24pm CET par Ian Barker
Consumers want to communicate with businesses using SMS according to a new study, but companies are failing to grasp the opportunity this offers. The research from mobile engagement specialist OpenMarket unveils a missed opportunity for financial service providers, retailers and hospitality companies that don't make use of SMS-powered chatbots to more effectively engage with customers. The research, which polled over 1,500 mobile users in both the US and UK, finds that despite 49 percent of consumers wanting to engage more conversationally with businesses through SMS, enterprises aren't meeting their needs. The results show 50 percent are not currently receiving SMS notifications… [Continue Reading] -

UK health trusts hit by ransomware attacks
Publié: janvier 17, 2017, 3:31pm CET par Ian Barker
The UK's National Health Service is being targeted by ransomware according to a new study which shows that 30 percent of NHS Trusts have suffered an attack, potentially placing patient data and lives at risk. The findings come from a Freedom of Information Act study conducted by endpoint security company SentinelOne. It submitted FOI requests to 129 NHS Trusts, of which 94 responded. All but two NHS trusts -- Surrey and Sussex, and University College London Hospitals -- have invested in AV security software on their endpoint devices to protect them from malware. But, despite installing a security solution, Leeds Teaching… [Continue Reading] -

Even ransomware stops for Christmas
Publié: janvier 16, 2017, 4:08pm CET par Ian Barker
An 81 percent drop recorded in Locky ransomware infections in December is thought to be down to the cyber criminals behind the malware taking a Christmas break. Threat prevention company Check Point recorded the big drop in Locky infections as part of an eight percent overall decrease in the number of recognized malware attacks on organizations in December. December saw ransomware purveyors getting into the festive spirit by offering a discount, but it seems they like to take a break over the holiday too. Check Point recorded a similar decrease last December with nine percent fewer attacks than in previous months… [Continue Reading] -

RockJaw Resonate -- clever design combined with quality audio [Review]
Publié: janvier 16, 2017, 3:30pm CET par Ian Barker
We've looked at earphones from RockJaw in the past and they've always offered a good compromise between reasonable price and a quality listening experience. The company's latest Resonate model is more expensive than its other offerings but it does combine clever design touches with a tuneable listening experience. The Resonate design makes use of removable filters like RockJaw's Alpha Genius model, so you can adjust the listening experience depending on your tastes. Useful touches continue in the way you can remove the cable from the ear pieces -- they attach via MMCX (Micro-Miniature Coaxial) connectors -- a useful feature should you ever… [Continue Reading] -

Marketers divided on the importance of analytics
Publié: janvier 13, 2017, 3:19pm CET par Ian Barker
Technology means that marketers are able to collect more information on customers and their purchasing habits than ever before. But a new study shows that there's a divide on how important using that information is going to be. The survey by marketing software company Marketo reveals that while 57 percent of all respondents in the US believe predictive analytics will be the primary technology they use to engage with their customers, only 11 percent of international marketers think the same. The survey of respondents from Australia, France, Germany, the United States, and the United Kingdom identifies the internet of things… [Continue Reading] -

Android overtakes iOS in mobile ad revenue
Publié: janvier 12, 2017, 7:27pm CET par Ian Barker
Analysis of data from billions of mobile ad impressions served during the third quarter of 2016 shows that for the first time Android has passed iOS in terms of revenue generated. The report from real-time advertising platform Smaato shows that based on eCPM (effective cost per thousand impressions) in the third quarter of 2016, Android accounts for 55 percent of global mobile ad revenue generated by publishers compared to 41 percent for iOS, the share of which is eroding. Since Android has the lion's share of the market, accounting for 88 percent of shipments in the quarter, you might expect… [Continue Reading] -

Social apps dominate mobile activity
Publié: janvier 12, 2017, 3:51pm CET par Ian Barker
Yahoo's mobile analytics arm Flurry has released its State of Mobile report for 2016, looking at mobile app activity and trends from the last year. Over the last year, Flurry tracked more than 940,000 applications, across 2.1 billion devices, in 3.2 trillion sessions. Compared to 2015 overall app usage grew by 11 percent and time-spent in apps grew by 69 percent. Growth in some app categories, however, has been at the expense of other apps rather than traditional media. Messaging and social applications for example saw year-on-year growth at 44 percent, while the personalization category lost 46 percent in session… [Continue Reading] -

New platform detects and blocks attacks using behavior patterns
Publié: janvier 12, 2017, 11:59am CET par Ian Barker
Traditional security solutions rely on detecting an attack based on existing information, which allows zero-day threats to slip through the net. Israel-based Nyotron is launching a new generation of its PARANOID security platform designed to block attacks before they occur, regardless of threat type or method used to access the network. It works by mapping and understanding what normal computer behavior looks like and what to do when suspicious behavior tries to damage data on an endpoint. Once implemented, the software can monitor system calls for normal, suspicious or malicious behavior attempts. This means that regardless of the type of… [Continue Reading] -

Unsanctioned cloud use remains a problem for enterprises
Publié: janvier 11, 2017, 4:30pm CET par Ian Barker
A new report from cloud security company Netskope reveals that while enterprise cloud adoption continues to rise, unsanctioned use of services remains a problem. The results show that half of all users of officially sanctioned cloud storage services like Box and Dropbox also have a personal instance of the same service. This can make detection of unauthorized copying of data more difficult. "Until very recently, organizations had to take an all-or-nothing approach to allowing cloud services. If they sanctioned a cloud storage service for corporate use, they also needed to accept any additional personal instances of that cloud storage service… [Continue Reading] -

Complaints about two-factor authentication are on the rise
Publié: janvier 11, 2017, 3:49pm CET par Ian Barker
Of companies that use two-factor authentication, 74 percent admit that they receive complaints about it from their users -- and nearly 10 percent of them just ‘hate it.’ This rather surprising information comes from a studty by access control company SecureAuth, carried out in conjunction with Amplitude Research, which surveyed 300 IT decision makers and cybersecurity professionals on industry perspectives and concerns over 2FA. The result is a turn around from a similar survey last year which showed that 99 percent of IT departments believed 2FA was the best way to protect an identity and its access. "It's not surprising… [Continue Reading] -

Public cloud has the greatest security implications say execs
Publié: janvier 11, 2017, 3:05pm CET par Ian Barker
A new survey reveals that 65 percent of senior IT and security executives think that the biggest security risks for business come from public clouds. The study from IT solutions company BMC in conjunction with Forbes Insights also shows that 69 percent of respondents say digital transformation is forcing fundamental changes to existing cybersecurity strategies. Financial and customer information, brand reputation, intellectual property, and employee information are all listed as critical assets still exposed and with potential for massive reputation damage. "Make no mistake, cybersecurity is a critical initiative across the board. Every company, government and society are seeking new… [Continue Reading] -

Modeling and analytics and their role in business [Q&A]
Publié: janvier 11, 2017, 10:55am CET par Ian Barker
Businesses are collecting more data about their operations and their customers than ever before. But data in itself is only part of the story. For it to be useful it's necessary to spot patterns and gain insights. At this point most businesses turn to analytics, but this can only tell you what's happened in the past. To predict future trends means using algorithms to build models of what may be complex systems. So, is it time to abandon analytics and turn to modeling? Or do businesses really need to embrace both? We spoke to Michel Morvan, co-founder and executive chairman… [Continue Reading] -

Ransom is the #1 motivation behind cyber attacks
Publié: janvier 10, 2017, 3:59pm CET par Ian Barker
A new report from cyber security and application delivery company Radware reveals that almost half of businesses (49 percent) say they’ve been the subject of a cyber-ransom campaign in 2016. Ransom was the top motivation behind cyber-attacks they had experienced according to 41 percent, followed by insider threats (27 percent), political hacktivism (26 percent), and competition (26 percent). In addition 55 percent say that IoT complicates their detection or mitigation requirements as it increases the surface of the attack landscape. While massive DDoS attacks made headlines in 2016, Radware's research shows that attacks of more than 50 Gbps made up… [Continue Reading] -

Insiders or outsiders, which is the greater threat?
Publié: janvier 10, 2017, 11:19am CET par Ian Barker
Historically, the idea of a hacker has always conjured up images of the outsider trying to gain access to government or corporate systems. But in recent years it's become clear that insiders can present just as big a threat, whether from malicious intent or just careless use of systems. Data protection company Digital Guardian has produced an infographic examining the different types of threat, the methods they use and the motivation behind them. Among the highlights are that finance or espionage are among the major motives for attacks, accounting for 89 percent of outsider and 59 percent of insider incidents… [Continue Reading] -

Security and the Internet of Things [Q&A]
Publié: janvier 9, 2017, 5:04pm CET par Ian Barker
Last year saw the Mirai botnet harness routers and other IoT devices to launch DDoS attacks against internet services. Is this type of attack something we’re going to see more of in 2017, and what can companies and individuals do to protect themselves? We spoke to Sam Rehman, chief technology officer at attack prevention specialist Arxan Technologies to find out more about security and the Internet of Things. BN: Let's start with last year and the Mirai botnet, how significant was that attack? SR: Mirai was mostly about taking advantage of flaws in routers and doing that wasn't an easy… [Continue Reading] -

Many businesses are are relying on others to fight DDoS attacks
Publié: janvier 5, 2017, 3:16pm CET par Ian Barker
With large scale cyber attacks constantly hitting the headlines, businesses ought to be aware of the need to protect themselves. But a new study by Kaspersky Lab shows that 40 percent of businesses are unclear on how to protect themselves against targeted attacks and DDoS. Many believe that someone else will protect them and therefore don't take their own security measures. 40 percent think their ISP will provide protection and 30 percent think data center or infrastructure partners will protect them. Moreover, the survey finds that 30 percent fail to take action because they think they are unlikely to be… [Continue Reading] -

Many businesses are relying on others to fight DDoS attacks
Publié: janvier 5, 2017, 3:16pm CET par Ian Barker
With large scale cyber attacks constantly hitting the headlines, businesses ought to be aware of the need to protect themselves. But a new study by Kaspersky Lab shows that 40 percent of businesses are unclear on how to protect themselves against targeted attacks and DDoS. Many believe that someone else will protect them and therefore don't take their own security measures. 40 percent think their ISP will provide protection and 30 percent think data center or infrastructure partners will protect them. Moreover, the survey finds that 30 percent fail to take action because they think they are unlikely to be… [Continue Reading] -

Managed SIEM brings threat protection to multi-site businesses
Publié: janvier 5, 2017, 1:29pm CET par Ian Barker
Data breaches are bad news for companies not just in terms of potential losses but in damage to reputation. Larger enterprises are realising that they need to protect not just their central locations but also their remote and franchise locations in order to guard their brand. Network security company Netsurion is launching a managed SIEM (security information and event management) solution called SIEM-at-the-Edge, designed specifically to protect multi-location businesses, along with a Breach Detection Service to augment other security measures. Powered by the EventTracker security management platform, these services give businesses an affordable level of protection from cyberthreats that was… [Continue Reading] -

New solution uses machine learning to protect against botnet attacks
Publié: janvier 4, 2017, 4:09pm CET par Ian Barker
The Mirai botnet is thought to have affected more than 1.5 million smart devices over the past few months. Router manufacturer Securefi is aiming to combat this problem with the launch of a new IoT device security service. Initially available for the company's Almond 3 routers, Securifi's solution protects connected home devices like DVRs, IP cameras, and smart thermostats from a number of key online threats. The Almond 3 router has a built-in home automation hub, giving a holistic view of both Wi-Fi and smart home devices, and can monitor traffic without resorting to dubious techniques like ARP poisoning. It… [Continue Reading] -

Ransomware set to increase in 2017
Publié: janvier 4, 2017, 3:24pm CET par Ian Barker
Ransomware has been one of the major threats faced by both businesses and individuals in 2016 and many security analysts don't see it going away any time soon. Threat intelligence specialist Recorded Future echoes that view and believes we’ll see more attacks aimed at shaming the victims. Allan Liska, an intelligence analyst at Recorded Future cites November's San Francisco Muni attack as something hackers will seek to copy by targeting public facing systems like self-checkout systems at grocery store chains, bank ATMs and digital billboards. "Basically, any organization that has a kiosk-type system exposed to the public and running on… [Continue Reading] -

Dashlane teams with Intel to improve password protection
Publié: janvier 3, 2017, 6:08pm CET par Ian Barker
Security breaches have been one of the major themes of 2016, so going into the new year it’s no surprise that companies are keen to try to make things more secure. Password manager Dashlane is announcing enhancements to its software to make use of Intel Software Guard Extensions, a powerful security technology built into the latest Intel Core processors. "Dashlane is committed to staying on the cutting edge of security," says Emmanuel Schalit, CEO of Dashlane. "The new Intel Core processors provide a powerful new way to protect your passwords. Dashlane is taking full advantage of Intel’s built-in hardware security… [Continue Reading] -

69 percent of businesses experience data loss due to employee turnover
Publié: janvier 3, 2017, 5:16pm CET par Ian Barker
A new report from IT research and consulting company Osterman Research reveals that employee turnover and attrition is the number one data protection concern for enterprises. Of the organizations surveyed, 69 percent indicate that they have suffered significant data or knowledge loss resulting from employees who had left the business. The report explains that while there are generalized problems associated with the loss of corporate knowledge and expertise when employees leave, many of these problems are related to employees actually taking data with them when they depart, or leaving it in locations that are unknown or inaccessible to corporate data… [Continue Reading] -

Finding your inner superhuman -- 2017 and beyond according to Samsung
Publié: décembre 29, 2016, 3:54pm CET par Ian Barker
2017 will be the year in which technology transforms our everyday lives and the way we communicate with others, according to electronics giant Samsung. Among the company's predictions is machines set to become smart coaches based on what they understand from our behaviour. As our lives continue to be tracked or quantified by technology, smart machines will coach us based on the data they collect, suggesting things like changes to our diet based on our daily energy levels. This will be enabled by a new generation of wearables incorporating seamless sensors that can detect mood and conditions, as well as… [Continue Reading] -

Inateck KTU3FR 4-port USB 3.0 card and HB4101 4-port USB 3.0 hub [Review]
Publié: décembre 28, 2016, 1:17pm CET par Ian Barker
The USB 3.0 standard has been around for a while, first appearing on consumer devices in 2009. It's likely therefore that any new PC purchased in the last few years will have USB 3.0 built in. If you have an older machine, or you need more ports, then you can add a PCIe card to add extra USB 3.0 capability. Inateck's KTU3FR 4-port card is an easy way to boost your USB 3.0 options. It's easy to install though it does need more power than the PCIe slot can provide so it comes with SATA and Molex cables, one of… [Continue Reading] -

Internet of Things risks and what to do about them
Publié: décembre 28, 2016, 11:50am CET par Ian Barker
In the past year we’ve already seen the Internet of Things used to carry out cyber attacks, and many experts are predicting that this is a problem that will grow in coming months. Given that many people may have acquired new IoT devices over the holiday period, financial advice website RefiGuide has put together a timely infographic looking at the risks IoT devices can pose and what you can do to protect yourself. It looks at past problems like the 2014 Jeep Cherokee hack and 2015's Samsung smart fridges leaking users' email details. It also covers the reasons why IoT… [Continue Reading] -

Data lakes and brick walls, big data predictions for 2017
Publié: décembre 23, 2016, 11:29am CET par Ian Barker
There's been a lot of talk about big data in the past year. But many companies are still struggling with implementing big data projects and getting useful results from their information. In this part of our series on 2017 predictions we look at what the experts think will affect the big data landscape in the coming year. Steve Wilkes, co-founder and CTO at Striim believes we'll see increasing commoditization, with on-premise data lakes giving way to cloud-based big data storage and analytics utilizing vanilla open-source products like Hadoop and Spark. He also believes that security concerns will mean that we'll… [Continue Reading] -

Facebook is the preferred holiday marketing tool of smaller businesses
Publié: décembre 22, 2016, 4:33pm CET par Ian Barker
Smaller businesses are increasingly recognizing the importance of digital marketing and Facebook is their platform of choice for the holiday period. This is among the findings of a report by marketing platform GetResponse which reveals that 60 percent of SMBs increased their digital marketing budget for this year’s holiday season. Among the 200 SMB decision-makers surveyed, 33 percent say Facebook advertising is the digital marketing channel they primarily use to promote or increase holiday sales. Their own website is the choice of 17 percent, email 11 percent, YouTube eight percent, and Google Pay-Per-Click advertising seven percent. "Facebook has proven to… [Continue Reading] -

Ransomware gets into the Christmas spirit with a festive discount
Publié: décembre 21, 2016, 11:45am CET par Ian Barker
Christmas is a time of goodwill and it seems that the people behind the CryptXXX ransomware aren't immune as they're offering a seasonal discount for victims who intend to pay up. Researchers at data security company Forcepoint have discovered that where previously, victims infected with CryptXXX, also known as UltraCrypter were asked for a payment of 1.2 Bitcoin, in keeping with the season of goodwill, the cyber criminals are now offering decryption at a Christmas discount. Victims paying their ransom demands can now unlock their files for only 0.5 Bitcoin. The 0.5 Bitcoin rate -- around $395 at the current exchange… [Continue Reading] -

Flock guns for Slack with its 'chat operating system'
Publié: décembre 20, 2016, 4:15pm CET par Ian Barker
Slack came from nowhere to be one of the leaders of the collaboration market in just two years. But being a leader means other people are keen to take a share of your business and team messenger application Flock is the latest to be eyeing up Slack's market. Today Flock is launching a development platform, FlockOS. It describes this as a chat operating system, that allows developers to build customized apps, bots and integrations. These can either be used within their own organizations, or published on the Flock Appstore, making them available for all Flock users. "Messaging and collaboration platforms… [Continue Reading] -

Changing infrastructure and new job roles among 2017 Internet of Things predictions
Publié: décembre 20, 2016, 3:46pm CET par Ian Barker
Continuing our series of expert predictions for the coming year, today we turn our attention to the Internet of Things which has begun to take off in a serious way in 2016. Although the IoT may already be pretty big it's set to get much, much bigger. Figures earlier this year from Machina Research predict the number of IoT connections will grow from 6 billion in 2015 to 27 billion in 2025. So what opportunities and challenges is this going to present to businesses? Steve Wilkes, co-founder and CTO at Striim, sees network infrastructures having to adapt to cope with… [Continue Reading] -

Lack of talent and compliance worries among cloud predictions for 2017
Publié: décembre 19, 2016, 4:28pm CET par Ian Barker
This is the time of year when industry experts like to come up with predictions for the coming 12 months. Last week we looked at some of their security forecasts, today it's the turn of the cloud to get the crystal ball gazing treatment. So, what do experts think are going to be the cloud trends of 2017? "In 2017, enterprises will be transitioning IT workloads to the cloud at a significant pace that will drive the biggest growth in hybrid cloud infrastructure, along with a significant increase of SaaS service offerings from vendors that address niche needs," says Curtis… [Continue Reading] -

When Things attack and other security predictions for 2017
Publié: décembre 16, 2016, 4:05pm CET par Ian Barker
The past year has been a pretty turbulent one for IT security with high profile data breaches, Apple and the FBI wrangling over encryption, persistent threats from ransomware and more. So as industry experts begin to roll out their predictions for 2017, what can we look forward to, or what do we need to beware of, in the security field? Stephen Cobb, senior security researcher at ESET sees increased potential for cross-pollination attacks, as ransomware will begin to seep into IoT devices, what he calls 'Ransomware of Things'. "In order to prevent RoT, a number of things need to happen… [Continue Reading] -

Still got a Yahoo mail account? You need to start telling lies
Publié: décembre 16, 2016, 11:48am CET par Ian Barker
As we reported earlier this week Yahoo has suffered yet another major security breach. This will have sent many users scurrying to change their passwords, but what else can you do to protect your account? Adam Levin, chairman and founder of identity protection specialist IDT911 suggests that users need to start telling lies. He doesn't mean lying about the fact that you have a Yahoo account -- though given the severity of breaches it has suffered that might save you some embarrassment. No, he means telling lies in the answers to your security questions. "Users should lie when providing new answers,"… [Continue Reading] -

IT leaders look to the cloud for backup and recovery
Publié: décembre 15, 2016, 3:48pm CET par Ian Barker
A new survey of over 250 senior IT executives reveals that 89 percent of IT leaders are planning on implementing more cloud based disaster recovery in the next year. The study by disaster recovery and business continuity specialist Quorum also reveals that 80 percent of IT leaders say it takes more than an hour for them to recover from a server failure, with more than 25 percent saying they need more than two hours. The problem is that 98 percent of IT leaders believe that speed of recovery plays an important role, with over 70 percent claiming it's extremely critical… [Continue Reading] -

Why enterprises are struggling with WAN management
Publié: décembre 15, 2016, 3:08pm CET par Ian Barker
Companies are struggling to manage and secure their WANs, especially at branch locations, according to the findings of a new report. The study, conducted by Dimensional Research for Versa Networks, finds almost all participants state that maintaining security policies, network devices and complexity due to cloud and mobile applications are the most difficult aspects of managing the WAN. 97 percent say they face multiple challenges to managing their WAN and the three most common ones involve branch offices. Managing network and security devices at branch locations was cited by 52 percent, mitigating information security risks at branch locations (50 percent),… [Continue Reading] -

November saw a spike in ransomware attacks
Publié: décembre 13, 2016, 5:11pm CET par Ian Barker
Ransomware remains a major threat with attacks using Locky and Cryptowall both increasing by 10 percent in November compared with the previous month. The latest report from threat prevention specialist Check Point based on its Global Threat Index shows the number of active malware families and number of attacks remain close to an all-time high thanks to continued relentless attacks on business networks. Conficker retained its position as the world’s most prevalent malware, responsible for 15 percent of recognized attacks. Second-placed Locky, which only started its distribution in February of this year, was responsible for six percent of all attacks… [Continue Reading] -

The biggest high-profile password blunders of 2016
Publié: décembre 13, 2016, 1:19pm CET par Ian Barker
Weak or reused passwords are one of the main causes of security breaches and nobody is immune from the problem. Password manager company Dashlane is seeking to raise awareness of the issue with the release of what it calls its P@ssholes List, highlighting the celebrities and high profile organizations that have fallen victim to poor password habits in the past year. Those named and shamed include pop stars Katy Perry, Harry Stiles and Jack Johnson, actor Tom Hiddleston, and technology leaders including Facebook's Mark Zuckerberg. Organizations include the National Football League and tech companies like LinkedIn and Dropbox. You can… [Continue Reading] -

Office 365 adoption surges ahead across the EMEA region
Publié: décembre 13, 2016, 11:32am CET par Ian Barker
Microsoft's Office 365 suite and Google's G Suite are deployed in 66 percent of organizations in the EMEA (Europe Middle East and Africa) region, but Office 365 on 44 percent is outpacing G Suite on 22 percent. This is one of the findings of a new EMEA cloud report from data protection company Bitglass which shows that adoption of cloud suites is higher than in any other region. In Europe, France and the Netherlands have the highest rates of cloud adoption at 82 percent and 78 percent. Slack has also taken off in the region and is now used in… [Continue Reading] -

Points mean prizes in gamified DDoS platform
Publié: décembre 9, 2016, 4:00pm CET par Ian Barker
Gamification is increasingly used by business as a means of enhancing the usability of software. But now it seems hackers are exploiting the technique too. Researchers at threat protection company Forcepoint have uncovered a DDoS package being shared on Turkish hacking forums employing a gamified approach. The hacking group lures its participants to join its DDoS platform, known as Sledgehammer, by gamifying the attack and offering hackers the chance to compete with peers in order to earn redeemable points. Users are rewarded with one point for every 10 minutes that they attack one of the 24 listed targets (which include… [Continue Reading] -

Companies miss basic precautions that could prevent data breaches
Publié: décembre 8, 2016, 5:02pm CET par Ian Barker
Public awareness of data security issues has never been higher. Not only have data breaches made the news but the FBI's battle with Apple has put encryption in the headlines too. Yet despite the high profile of threats a new survey of IT security professionals from secure browser company Authentic8 shows that businesses aren't taking basic steps to protect themselves. Over 57 percent of respondents admit to the reuse of passwords for different websites when it's "not important" and nearly 30 percent use at least one personal password for a work account. In addition 40 percent of respondents don’t use a… [Continue Reading] -

DreamObjects improves enterprise cloud storage
Publié: décembre 8, 2016, 3:32pm CET par Ian Barker
The cloud is becoming the first place many businesses turn to when looking to increase their storage capacity. Web hosting and cloud services company DreamHost is looking to give enterprises more scalable, reliable, and high performing cloud storage with the launch of its latest DreamObjects storage hosting service. Based on the latest jewel release of the open source Ceph software defined storage platform, DreamObjects can be used to build cloud-ready applications and to store documents, photos, songs and backup, taking advantage of its Amazon S3 API compatibility. An easy-to-use console lets users see how much storage they're using and what… [Continue Reading] -

New platform simplifies integration of business systems
Publié: décembre 7, 2016, 3:58pm CET par Ian Barker
Businesses increasingly rely on a range of systems. But getting those systems to work smoothly together can prove to be something of a challenge. Integration specialist Jitterbit is announcing what it calls a Citizen Integrator, a cloud based integration platform. This integration-platform-as-a-service (iPaaS) approach combines a do-it-yourself integration experience for everyday business users with a powerful design experience for developers. A simple integration interface allows everyday users to accomplish basic integration functions quickly across a variety of cloud and on-premise systems, these include Salesforce, NetSuite, Oracle, SAP, Box, and Slack. Integration can be carried out without special training or IT… [Continue Reading] -

Automated phishing boosts profits for hackers
Publié: décembre 7, 2016, 12:34pm CET par Ian Barker
Phishing has proved to be one of the most profitable techniques for hackers. A new report from cyber security company Imperva reveals that the availability of turnkey services is making it even more effective. Imperva researchers explored the darknet marketplace to estimate the cost of phishing campaigns and to get a clear picture of the hackers' business model. They discovered phishing-as-a-service (PhaaS) campaigns were easy to buy and low cost. In addition, they saw that hackers were easily able to hijack compromised webservers for their campaigns, which further lowers the investment needed. Based on the researchers' analysis of costs, PhaaS… [Continue Reading] -

100 percent of holiday retailers vulnerable to cyber security issues
Publié: décembre 6, 2016, 4:11pm CET par Ian Barker
With more of us than ever doing our shopping online over the holiday period we want to feel that we can do so safely. But a new report from security ratings company SecurityScorecard exposes cyber security vulnerabilities across 48 of the biggest US retailers. The company studied the 48 largest retailers as indicated by the National Retail Federation. It finds that more than 50 percent may have failed to meet the Payment Card Industry’s Security Standards (PCISS). It also uncovered issues including malware infections, use of end-of-life products, weak network security and low security awareness among employees. Overall 100 percent… [Continue Reading] -

New platform gives businesses control of SaaS
Publié: décembre 6, 2016, 3:25pm CET par Ian Barker
The switch to as-a-service models for delivering software gives organizations a wide range of providers to choose from, but it can lead to a proliferation of different solutions and a challenge for management. Cloud management specialist BetterCloud is launching a new unified software-as-a-service (SaaS) management platform to give IT departments powerful automation and governance capabilities. "The rise of the SaaS-powered workplace is transforming the role of IT," says David Politis, CEO of BetterCloud. "What was once a behind-the-scenes department is now becoming deeply integrated into the business. But the explosion of SaaS offerings from thousands of providers brings a new and significant set… [Continue Reading] -

The key cyber threats to businesses in 2017
Publié: décembre 6, 2016, 1:22pm CET par Ian Barker
The past year has been a pretty eventful one for many reasons, not least in the area of cyber security which has seen attacks gaining in sophistication and persistence. If you were expecting 2017 to be an improvement you may be in for a disappointment according to the Information Security Forum (ISF) which is today publishing its outlook for the threats businesses will face in the next year. The four key threats it identifies will come from the Internet of Things, crime syndicates, end users, and an over reliance on government and regulators. These it says are are not mutually… [Continue Reading] -

Are remote workers happier?
Publié: décembre 6, 2016, 11:35am CET par Ian Barker
Thanks to technology, remote working is easier and more popular, with both workers and employers, than ever before. But does being able to work remotely lead to a happier workforce? Time management specialist Time Doctor has produced an infographic based on research by employee engagement company TINYpulse into remote working habits. Among the findings are that 91 percent of those surveyed say that they get more work done outside the office. 41 percent enjoy the freedom that remote working offers, and 28 percent say that they do it because it fits the needs of their family. Interestingly those that work… [Continue Reading] -

Consumers ignore security risks and turn to mobile for their holiday shopping
Publié: décembre 5, 2016, 3:11pm CET par Ian Barker
Mobile is expected to be the most popular online shopping route this holiday season with 71 percent planning to use it. Next-generation mobile security company Trustlook has carried out a survey of Android users to dig deeper into the expected mobile shopping behaviors for the 2016 holiday season. Smartphone proliferation, faster network speeds, and slick shopping apps have combined to provide a far better experience for mobile shoppers and 40 percent of those surveyed prefer shopping on their mobile devices, compared to 18 percent who prefer shopping in a store. The results show that 43 percent of users will spend… [Continue Reading] -

The state of SharePoint and Office 365 development
Publié: décembre 2, 2016, 4:48pm CET par Ian Barker
SharePoint is the most widely used hub for modern businesses, while Office 365 is increasingly the first choice for cloud productivity. With these two platforms forming the bedrock of many companies' IT environments, business leaders need to understand how the platforms are changing and the needs of the employees who work with them. SharePoint customization specialist Rencore has surveyed over 1,200 SharePoint and Office 365 developers and other professionals to get a picture of how the community is evolving. Among the findings are that businesses are gradually phasing out older versions of SharePoint and increasingly adopting later versions of the… [Continue Reading] -

Half of IT professionals more concerned about internal threats than external ones
Publié: décembre 1, 2016, 3:05pm CET par Ian Barker
Hackers and cyber criminals are often seen as the biggest threat to company IT systems, but a report from behavioral firewall company Preempt shows that insiders, including careless or naive employees, are now viewed as an equally important problem. The survey carried out for Preempt by Dimensional Research finds that 49 percent of IT security professionals surveyed are more concerned about internal threats than external threats. Malware installed unintentionally by employees was the top concern of respondents (73 percent), ahead of stolen or compromised credentials (66 percent), stolen data (65 percent), and abuse of admin privileges (63 percent). The majority… [Continue Reading] -

Most enterprise attempts at email authentication fail
Publié: décembre 1, 2016, 1:07pm CET par Ian Barker
A new study shows that 75 percent of large businesses attempting implementation of the DMARC email authentication standard are not presently capable of using it to block unauthorized email. This means that enterprises are putting their own security, compliance, and brand protection at risk. Automated mail authentication specialist ValiMail looked at email authentication policies for more than a million business domain names, including those of Fortune 1000, NASDAQ 100, and FTSE 100 businesses. "Our investigation showed that using email authentication to monitor and control unauthorized email is extremely difficult for the majority of global companies," says ValiMail's CEO Alexander García-Tobar.… [Continue Reading] -

70 percent of smaller IT businesses don't see Brexit as a threat
Publié: décembre 1, 2016, 12:49pm CET par Ian Barker
Despite the widespread predictions of Armageddon that preceded June's vote on the UK leaving the European Union, new research reveals that a majority of companies in IT and computing don't see Brexit as a threat. The research by commercial insurer RSA shows that 70 percent of small and medium businesses in IT and computing don't see Brexit as a risk. Of those surveyed 43 percent say that leaving the EU will have no impact at all, and 27 percent say it will have a positive effect on their business. There are regional differences too, eight out of 12 regions are… [Continue Reading] -

Symbol-to-accept strengthens multi-factor authentication
Publié: novembre 30, 2016, 5:26pm CET par Ian Barker
One of the more popular ways of securing logins in recent times has been the use of push-to-accept technology, sending a verification message to a user's mobile device. However, this runs the risk of users inadvertently approving login requests that they didn't initiate. Adaptive access company SecureAuth is launching its new Symbol-to-accept technology to boost security without sacrificing convenience. The way it works is that a push message is still sent to the user's mobile, but using Symbol-to-accept, the user is presented with several 'accept' buttons displaying single, randomly-selected symbols. To successfully log in, the user selects the symbol that matches one… [Continue Reading] -

60 percent of enterprises have fallen victim to social engineering in 2016
Publié: novembre 30, 2016, 4:28pm CET par Ian Barker
A new study from cyber security company Agari reveals the scale of social engineering attacks on industrial organizations across the US. Of over 200 security leaders surveyed 60 percent say their organizations were, or may have been, victim of at least one targeted social engineering attack in the past year, and 65 percent of those who were attacked say that employees' credentials were compromised as a result. In addition, financial accounts were breached in 17 percent of attacks. Among other findings are that 89 percent of respondents have seen either a steady pace or an increase in spear phishing and… [Continue Reading] -

New Android malware breaches over a million Google accounts
Publié: novembre 30, 2016, 3:27pm CET par Ian Barker
Researchers at cyber security company Check Point have uncovered a new malware variant that has breached more than a million accounts and is infecting over 13,000 Android devices a day. Called Gooligan, the malware roots Android devices and steals email addresses and authentication tokens stored on them. With this information, attackers are able to access users' sensitive data from Gmail, Google Photos, Google Docs, Google Play, and G Suite. It also generates revenue for the criminals by fraudulently installing apps from Google Play and rating them on behalf of the victim. Gooligan is installing 30,000 apps daily on breached devices,… [Continue Reading] -

Sentiment analysis helps sales teams measure customer reaction
Publié: novembre 30, 2016, 1:28pm CET par Ian Barker
One of the problems sales teams face is knowing how their pitches, presentations and marketing materials are perceived by the customer. Cloud-based sales and content management platform Pitcher is hoping to offer teams better insight with its newly patented Sentiment Analysis Module (SAM). SAM allows sales representatives working in the field to seamlessly gauge and analyze customer reactions to sales and marketing materials, presentations and pitches in real-time. It gives front-line teams the ability to engage their customers and collect sentiment reactions to pitch materials, which are expressed either verbally or through gestures. While sharing content that highlights product offerings,… [Continue Reading] -

Digital transformation is top strategic priority for half of execs
Publié: novembre 29, 2016, 5:27pm CET par Ian Barker
Digital transformation is at the top of the strategic agenda for enterprises, and half of executives surveyed believe the next two years will be critical for their organizations. These are among the findings of a new report by Forbes Insights, in association with Hitachi Data Systems, which surveyed 573 senior executives worldwide as well as holding one-on-one conversations with top executives. Among the findings are that investing in new technologies to enable digitization is the top investment priority for 51 percent over the next two years, along with increasing data and analytics capabilities also cited by 51 percent. Drivers for… [Continue Reading] -

Sophisticated social engineering attacks target hotel chains
Publié: novembre 29, 2016, 3:45pm CET par Ian Barker
In the run up to one of the hospitality industry's busiest periods, cyber criminals are targeting hotel chains with a series of targeted attacks. Cyber security company Trustwave has investigated the attacks, which combine social engineering with sophisticated malware, against a number of its clients in the past month. Believed to originate from the prolific Carbanak crime group, the attacks start with a phone call to customer services staff claiming to be having trouble making an online booking and asking permission to email a document containing travel details. The attackers are careful to research their targets beforehand so that they're able… [Continue Reading] -

Scality improves security for enterprise cloud
Publié: novembre 28, 2016, 3:08pm CET par Ian Barker
As organizations store more of their information in the cloud increased focus is placed on keeping it secure from breaches and other threats. Cloud storage specialist Scality is launching a new version of its RING software defined storage technology to provide extended security features and a trusted, compliant and secure storage infrastructure. "Data is a business critical asset but we are increasingly seeing more data breaches, security attacks and malware threats on businesses," says Giorgio Regni, CTO at Scality. "Organizations today need to reduce risk, assure compliance, securely store data and implement strict access controls and governance. We designed Scality… [Continue Reading] -

If you're going to San Francisco be sure to travel free with ransomware
Publié: novembre 28, 2016, 12:46pm CET par Ian Barker
The Muni public transport system in San Francisco has been hit by a major ransomware attack over the weekend that left the network having to give passengers free travel. It's estimated that around 2,000 systems have been affected by the attack, which began on Friday, including ticket machines, servers and Windows workstations. The software used in the attack is believed to be a variant of HDDCryptor. This uses freeware and open source tools to encrypt hard drives and network-shared files, as well as overwriting the master boot record on infected systems. Locked machines displayed a message reading, "You Hacked, ALL… [Continue Reading] -

North American businesses suffer twice as many cyber attacks
Publié: novembre 25, 2016, 1:12pm CET par Ian Barker
A new report from Kaspersky Lab finds that businesses in North America are significantly less protected against cyberattacks compared to those worldwide. According to the study 20 percent of global enterprises suffered four or more data breaches in the past year, while 44 percent of North American businesses suffered a similar number of attacks. Two of the top causes of serious data breaches are careless or uninformed employee actions (59 percent) and phishing or social engineering (56 percent). The survey shows that cybercriminals are successfully hacking their way into corporations through uninformed employees. In addition the results reveal that 52 percent of… [Continue Reading] -

Consumers want to know more about how their data is used
Publié: novembre 23, 2016, 4:05pm CET par Ian Barker
The world is ever more reliant on data, but consumers are becoming increasingly concerned about where their personal details are stored and who has access to them. Professional technology standards body IEEE has carried out a survey of 1,000 UK adults which finds that 81 percent believe the public should be better educated on how their data is being used online. In addition more than half of respondents would like to see clarity from individual websites on their specific use of personal data. Worryingly for online companies, 65 percent are able to cite a negative experience as a result of a… [Continue Reading] -

Free tool helps consumers check online security ahead of Black Friday
Publié: novembre 23, 2016, 3:05pm CET par Ian Barker
On this year's Black Friday and Cyber Monday, more Americans will be shopping online than ever before, but a new study reveals that the majority are concerned about the potential to have their personal and financial information hacked. The survey from cybersecurity company UpGuard shows that almost 95 percent of consumers are concerned about the security of their information online, and more than half would break with their favorite brands if they knew their information was at risk. Roughly 92 percent of respondents say they think consumers should be moderately to extremely concerned about cybersecurity. 74 percent report they are… [Continue Reading] -

Druva launches pay-as-you go disaster recovery on AWS
Publié: novembre 22, 2016, 5:45pm CET par Ian Barker
Disaster recovery is something that all businesses need but few like to contemplate. It's tempting therefore to think that storing data in the cloud makes the problem go away, but of course it doesn't. You need to look after your data wherever it's stored and to help AWS users with this, data protection specialist Druva is launching its Phoenix cloud-native solution for backup, archive and disaster recovery on the AWS Marketplace. Using a single dashboard for backup, availability and governance, Druva Phoenix is designed for today’s distributed enterprise server infrastructure. It reduces the risk, effort and cost of protecting and… [Continue Reading] -

OneDrive for Business accounts used to spread malware
Publié: novembre 22, 2016, 4:49pm CET par Ian Barker
Malware purveyors have been making use of cloud services for some time, sending cloud-storage links that host malware to victims is an efficient way for cyber criminals to operate. In a new twist to the technique, Forcepoint Security Labs has discovered that cybercriminals have been utilizing compromised Microsoft OneDrive for Business accounts to host malware since at least August of this year. Criminals are exploiting the 'MySite' feature which allows work-related files to be uploaded and shared, even with external parties. Download links are sent to prospective victims as part of social engineering mass-mailing campaigns. The links lead to a… [Continue Reading] -

56 percent of Brits want to move to the Moon
Publié: novembre 22, 2016, 3:31pm CET par Ian Barker
Whether it's a result of Brexit or they're simply sick of the weather, a new survey reveals that 56 percent of British people would like to move to the Moon. If money were no object 19 percent also say they would buy a holiday home on Mars. Product development company Arconic surveyed 1,000 people in the UK to find out how they thought technology would develop over the next 50 years. Almost half (46 percent) expect space travel for the average person will be possible in the next 50 years and 43 percent would like to inhabit an undiscovered planet… [Continue Reading] -

What you need to know about GDPR
Publié: novembre 21, 2016, 7:17pm CET par Ian Barker
The concept of data protection has been around for many years, since the UK first implemented a Data Protection Act in 1984. The general data protection regulation is a piece of legislation drawn up by the European Commission to unify data protection within the EU and to govern the export of personal data beyond the EU’s boundaries. GDPR is due to come into force across the EU in May 2018 following a two year transition period. Being a regulation rather than a directive, it doesn’t require enabling laws to be passed by member states. Why Data Protection Matters Businesses and… [Continue Reading] -

How seasonal tech gifts could be risking your data
Publié: novembre 21, 2016, 5:06pm CET par Ian Barker
In the run up to the holiday season many of us will be buying internet connected devices. But new research from Intel Security shows that technology bargains and gifts could be putting consumers' data at risk. The survey among UK consumers shows smartphones and tablets come top of many seasonal shopping lists, with 42 percent planning to upgrade gadgets to the latest models. Yet 60 percent say they have no plans to ensure security software is installed. "An underlying issue is that consumers simply don't know which products need protecting," says Nick Viney, VP consumer at Intel Security. "A fifth of… [Continue Reading] -

How secure are online retailers?
Publié: novembre 21, 2016, 3:22pm CET par Ian Barker
With Black Friday, Cyber Monday and the holiday season on the horizon, many people are going to be shopping online. But how much do you trust the sites you’re dealing with? Password management company LastPass has released a report looking at each site's password requirements, how much information they store, and how much effort they put into helping customers follow good password security practices. It has identified the top online retailers based on e-commerce sales in 2015 and analyzed each website on a set of six criteria. It then ranks each on a scale of zero to 10 points, depending… [Continue Reading] -

How businesses should respond to unplanned downtime
Publié: novembre 21, 2016, 12:41pm CET par Ian Barker
Today's businesses face a wave of challenges when it comes to protecting their data. Securing data in the cloud, a rise in ransomware attacks, and increases in unstructured data all make it hard to plan operations effectively and can lead to unscheduled downtime. Cloud data protection company Arcserve, however, sees this as an opportunity for organizations to re-assess their ability to cope with problems. The company has released a report setting out five strategies to help organizations prepare for and respond to unplanned downtime. These include improving risk management and making more effective use of the cloud. By applying Arcserve's strategies… [Continue Reading] -

IBM launches new services to help enterprises with cloud migration
Publié: novembre 18, 2016, 5:08pm CET par Ian Barker
Businesses are turning to the cloud as a way of coping with ever larger amounts of data. But moving to the cloud at the same time retaining control of where data resides and how it’s accessed is a challenge. To help enterprises migrate and more easily generate business insights, IBM is announcing a range of new services on its Bluemix cloud platform. IBM Decision Optimization on Cloud is capable of ingesting large amounts of data including predictions, master and transactional data, business goals, and business rules to prioritize and rank business decisions such as plans and schedules. It includes the… [Continue Reading] -

Almost half of businesses have suffered a ransomware attack in the last year
Publié: novembre 18, 2016, 3:39pm CET par Ian Barker
A new survey of over 500 businesses in the US, UK, France and Germany shows that in the last 12 months, 48 percent have fallen victim to a ransomware campaign, with 81 percent having suffered three or more attacks. The study from endpoint security company SentinelOne reveals employee information (42 percent), financial data (41 percent) and customer information (40 percent) are the types of data most often affected by these attacks. Respondents identified the most likely motives of their attackers as financial gain (54 percent), operational disruption (47 percent) and cyber espionage (42 percent). In 81 percent of cases respondents… [Continue Reading] -

Cloud use could be putting businesses at risk
Publié: novembre 17, 2016, 4:01pm CET par Ian Barker
According to a new study, 69.7 percent of cloud applications do not specify whether the customer keeps ownership of uploaded data, just 8.7 percent commit to not sharing data with third parties, and only 16 percent delete data immediately after contract termination. All three of these things could leave businesses open to non-compliance files under the EU's GDPR requirements. The report from cloud security company Skyhigh Networks analyses real life cloud usage data from 30 million cloud users worldwide to assess the risk the cloud presents. What businesses upload is important too, 18.1 percent of files uploaded to cloud-based file sharing… [Continue Reading] -

Almost 40 percent of Americans would give up sex for cyber security
Publié: novembre 17, 2016, 3:08pm CET par Ian Barker
According to an online survey of over 2,000 adults, 39 percent of Americans would sacrifice sex for one year if it meant they never had to worry about being hacked, having their identity stolen, or their accounts breached. Women are more likely than men to be willing sacrifice a year of sex in exchange for online peace of mind (44 percent vs 34 percent), and sex isn't the only thing people would give up to remove cybersecurity headaches. Four in 10 (41 percent) would rather give up their favorite food for a month than go through the password reset process… [Continue Reading] -

iOS apps three times more likely to crash than Android
Publié: novembre 17, 2016, 1:30pm CET par Ian Barker
With iOS and Android waged in a long term battle for smartphone market share every quarter, device performance can often play a role in shaping the final results. According to a report released today by Blancco Technology Group, Apple is losing the app performance battle to Android with its iPhones and iPads failing at a rate of 62 percent worldwide, compared to the 47 percent failure rate of Android devices. Pokémon GO has highlighted problems, with users spending a lot of time on the game. The app ranked as one of the most unstable iOS apps with five percent experiencing… [Continue Reading] -

What you need to know about fog computing
Publié: novembre 17, 2016, 12:18pm CET par Ian Barker
You could be forgiven for thinking it’s something to do with improving weather forecasts, but in fact fog computing is a type of decentralized infrastructure. In a fog computing -- sometimes referred to as edge computing -- model, computing resources and applications are placed at the most logically efficient point, whether that’s in the data center or in the cloud or somewhere in between. The idea of this is to boost efficiency, return faster responses and to minimize the amount of data that has to be moved around. It is a key part of implementing the Internet of Things as… [Continue Reading] -

Cyber crime affects 40 percent of manufacturing companies
Publié: novembre 16, 2016, 5:53pm CET par Ian Barker
In an increasingly interconnected world, all organizations are at risk from cyber attacks and manufacturing businesses are no exception. A new study conducted by Deloitte and the Manufacturers Alliance for Productivity and Innovation (MAPI) reveals that 40 percent of manufacturing companies were affected by cyber incidents in the past 12 months, and 38 percent of those impacted suffered damages in excess of $1 million. Other findings are that four of the top 10 cyber threats facing manufacturing organizations are directly attributable to internal employees. Intellectual property tops the list of data protection concerns for 36 percent of manufacturing executives, and… [Continue Reading] -

How storage can help fight malware [Q&A]
Publié: novembre 16, 2016, 1:40pm CET par Ian Barker
We tend to think of storage as being a target when it comes to malware attacks with cyber criminals seeking to steal data or encrypt it to demand a ransom. But in fact technology can make storage part of the solution. Hybrid storage specialist Reduxio believes innovative storage can be used to fight and defeat ransomware and malware. We spoke to Reduxio's Jacob Cherian (VP of product strategy) and Mark Grandinetti (chief marketing and corporate strategy officer) to find out how. BN: How much of an impact can ransomware have on a business? MG: Ransomware is a top concern for… [Continue Reading] -

What you need to know about federated identity
Publié: novembre 16, 2016, 10:40am CET par Ian Barker
As we conduct more and more of our work and personal lives using information technology, we have to sign in to lots of different systems. That can mean many different sets of credentials which can be hard to manage. Federated identity is a way of streamlining this by linking an electronic identity and attributes across several identity management systems. This is related to single sign-on (SSO), which involves sharing authentication between systems -- such as signing onto other websites using your social network ID -- but federated identity goes much deeper. Background At its simplest federated identity means having a not… [Continue Reading] -

Time tracking tools aren't keeping up with mobile workforces
Publié: novembre 15, 2016, 5:38pm CET par Ian Barker
Modern businesses are increasingly concerned with agility and efficiency and this leads them to seek more mobile solutions. But a new report shows that workforces are struggling with outdated processes that don't adequately support this new world. The study by performance management specialist Changepoint shows that organizations using time and task data to guide business decisions are relying on old-fashioned methods including Excel spreadsheets (28 percent) and even pen and paper (36 percent). The company surveyed more than 800 global project managers, executives, and IT professionals and found that 77 percent aren't confident in the accuracy of the timesheets they… [Continue Reading] -

Comodo launches new certificate management platform
Publié: novembre 15, 2016, 5:38pm CET par Ian Barker
Digital certificates are an essential part of online security and as the number of Internet of things devices continues to grow they'll become more important still. But as we rely more on certificates so managing them becomes more complex. Cyber security solutions company Comodo, the world's leading certificate authority, is launching the latest release of its Comodo Certificate Manager (CCM), a full-lifecycle digital certificate management platform which makes it easier for enterprises to manage their certificates. CCM allows businesses to self-administer and instantly provision Comodo certificates and to auto-discover and manage all certificates, from any certificate authority, throughout the organization. The… [Continue Reading] -

35 percent of cloud spend is wasted through inefficiency
Publié: novembre 15, 2016, 4:47pm CET par Ian Barker
In the dash to the cloud it's easy to lose sight of the fact that it isn't necessarily always the answer to spending your IT budget in the most efficient way. New data released by cloud management company RightScale reveals that cloud users could reduce their spend by an average of 35 percent by making better use of resources. Based on three months of data from RightScale's Cloud Cost Optimization Service it finds that compute resources represent 76 percent of cloud spend and database services account for only 15 percent. Cloud spending continues to rise overall, up 76 percent from… [Continue Reading] -

Office 365 and G Suite now in 59 percent of organizations worldwide
Publié: novembre 15, 2016, 3:46pm CET par Ian Barker
Cloud adoption has hit an all time high in 2016, largely driven by productivity packages like Microsoft Office 365 and Google's G Suite, according to a new report. Data protection company Bitglass scanned the cloud use of more than 120,000 companies to identify the primary cloud productivity suite used. It finds 59 percent of organizations worldwide now use one of these two apps, up from 48 percent in 2015. Office 365 continues to edge ahead of G Suite and is deployed in more than a third (34.8 percent) of organizations while G Suite is used by 25 percent. Public companies… [Continue Reading] -

What causes networks to fail?
Publié: novembre 15, 2016, 1:25pm CET par Ian Barker
Network outages are a major source of pain for businesses, so understanding what causes them is an important part of preventing them in the first place. A new survey from Veriflow reveals that complexity and human error are high on the list as contributing to network problems. Of 300 plus network professionals responding to the survey, 97 percent admit that human factors cause network outages. Yet despite this 69 percent of respondents still rely on manual processes, such as inspecting devices via the command line interface (CLI), inspecting configurations and performing manual traceroutes or pings, as one of their main solutions.… [Continue Reading] -

New security solution protects Office 365 customers
Publié: novembre 15, 2016, 11:33am CET par Ian Barker
More and more companies are moving their office applications to the cloud and Microsoft Office 365 is one of the most popular options with around 85 million subscribers. One of the major concerns with this trend is keeping information secure, to address this IT management solutions provider Kaseya is launching its latest AuthAnvil. An identity and access management solution, this provides single sign on (SSO), multifactor authentication (MFA) and automated user provisioning for Office 365. AuthAnvil gives end users the simplicity and time saving of securely signing in once to access all applications without having to remember multiple sets of… [Continue Reading] -

What you need to know about network function virtualization
Publié: novembre 15, 2016, 10:32am CET par Ian Barker
We’re seeing more and more technology functions being virtualized in order to streamline operations and cut costs. Networking is no exception to this trend, though it has been slower to adopt it than some other areas, there are good reasons for this which we’ll look at later. A shift is beginning to occur though. Network function virtualization allows network tasks to be performed by software running on commodity hardware, replacing expensive, dedicated hardware appliances. This promises easy scaling of functions and should help in the automation of service delivery. The Background to NFV In the telecommunications sector products have generally… [Continue Reading] -

HoneyNet delivers deception technology for all sizes of enterprise
Publié: novembre 14, 2016, 2:55pm CET par Ian Barker
Data breaches can be hard to detect and are often missed by traditional cyber security approaches, allowing attackers to spend a long time inside a network. One way of combating this is to catch attackers out by deploying decoys that mimic desktops, servers, printers and other technology present in a network. But until recently this approach was only available to large organizations. But now security information specialist EventTracker is launching a "deception-as-a-service" product called HoneyNet. This provides a managed security service that enables any size of enterprise to add a deception network layer to its cyber security defenses. HoneyNet uses… [Continue Reading] -

What you need to know about Hadoop
Publié: novembre 14, 2016, 1:18pm CET par Ian Barker
Unless you’ve been hiding away from the world of computing for the last few years, you’ll have come across Hadoop. Apache Hadoop, to give it its full name, is an open source framework designed to handle the storage and processing of large amounts of data using low-cost commodity hardware. Since its initial release in 2011, it has become one of the most popular platforms for handling big data. How Does It Work? Hadoop grew out of Google File System, and it’s a cross-platform program developed in Java. It has four core components: Hadoop Common, which holds all of the libraries… [Continue Reading] -

The five most common social engineering attacks
Publié: novembre 11, 2016, 3:09pm CET par Ian Barker
However much technology you throw at protecting your organization's systems the weakest link is still the person sitting in front of the endpoint. No surprise then that social engineering is increasingly the attacker's weapon of choice for gaining access to sensitive systems. Security rating and risk monitoring company SecurityScorecard has put together an infographic showing the five most common attacks and their impact on enterprises. The attacks identified are 'pretexting' -- assuming another identity to obtain sensitive information, 'tailgating' -- following a person with legitimate access into a secure location, 'quid pro quo' -- offering some incentive in exchange for… [Continue Reading] -

What you need to know about business process automation
Publié: novembre 10, 2016, 9:49pm CET par Ian Barker
Automation means many different things, in the context of business it usually involves streamlining processes in order to reduce costs. Applied across the whole organization it means restructuring resources and integrating the applications used across the enterprise to save time and money. Business process automation (BPA) automation is aimed at those tasks that involve a series of processes which follow a predictable pattern with a series of repeated operations. As research specialist Gartner puts it, "It focuses on 'run the business' as opposed to 'count the business' types of automation efforts and often deals with event-driven, mission-critical, core processes. BPA… [Continue Reading] -

Why you need to know who owns your encryption keys [Q&A]
Publié: novembre 10, 2016, 4:58pm CET par Ian Barker
As companies move more of their data to the cloud it's not surprising that they’re turning to encryption in order to keep their data safe. But if you're using a third-party cloud provider, who owns and controls the keys to your encrypted data? Rui Biscaia, director of product management at data classification specialist Watchful Software believes it's vital for companies to know. BN: Why has encryption become such an important tool? RB: Encryption technology is a fundamental, underlying part of protecting sensitive data. It ensures that the wrong people don't have access to your information and can't leverage it for… [Continue Reading] -

What you need to know about converged infrastructure
Publié: novembre 10, 2016, 4:46pm CET par Ian Barker
Information technology infrastructure is made up of many components, servers, storage, networking hardware, systems management software, and more. This can lead to a complex system being built up of components from several different suppliers. What converged infrastructure does is to bring together all of these things into a single, integrated package. For businesses this means that they can centralize the management of all their IT resources with a view to increasing use and cutting costs. Converged infrastructure is often associated with the cloud and outsourcing, but it can work just as well applied internally within large organizations too. Origins and… [Continue Reading] -

Malicious spam levels hit two year high
Publié: novembre 10, 2016, 3:28pm CET par Ian Barker
A new report from Kaspersky Lab reveals that its products blocked 73,066,751 attempts to attack users with malicious attachments during the third quarter of this year. This represents the largest amount of malicious spam since the beginning of 2014 and is a 37 percent increase compared to the previous quarter. The majority of the blocked attachments were ransomware trojan downloaders. "Spam is often just unwanted advertising, but it has a darker side too," says Daria Gudkova, acting head of content analysis and research at Kaspersky Lab. "Criminals use spam to distribute malware and exploit users' vulnerability, convincing them to hand… [Continue Reading] -

What you need to know about enterprise connectivity
Publié: novembre 9, 2016, 7:31pm CET par Barclay Ballard, Ian Barker
Connectivity is vital for all businesses. Whether you need to communicate with customers, clients or employees, or simply rely on it to deliver your service, the importance of connectivity cannot be overstated. What’s more, this importance is clearly growing. In the always-on, cloud-based, mobile-first digital world that we inhabit, enterprise connectivity is not merely desirable -- it is expected at all times. Connectivity, of course, means different things to different businesses and the level of connectivity that you are able to provide is likely to depend on a number of factors. Do you have the technology required, including the hardware… [Continue Reading] -

A closer look at the OpenStack platform
Publié: novembre 9, 2016, 7:07pm CET par Ian Barker
Providing an open source platform for cloud computing, OpenStack allows the use of multi-vendor commodity hardware in a data center to process and store data, and deliver networking resources. It’s managed through a dashboard or an API and is used by many major companies around the world to manage their IT infrastructure. OpenStack grew out of a joint project between NASA and Rackspace Hosting and launched in 2010. It’s currently managed by the not-for-profit OpenStack Foundation created in 2012. More than 500 companies are now members of the OpenStack project. OpenStack has a six-month release cycle with each release planned… [Continue Reading] -

IBM launches experimental platform to embed Watson into any device
Publié: novembre 9, 2016, 4:22pm CET par Ian Barker
IBM's Watson project has been a leader in cognitive computing, enabling machines to understand the world in a similar way to humans. Today the company is unveiling the experimental release of Project Intu, a new, system-agnostic platform designed to allow developers to embed Watson functions into various end-user device form factors, offering a next generation architecture for building cognitive-enabled experiences. Using Project Intu developers can simplify and integrate Watson services, such as Conversation, Language and Visual Recognition, with the capabilities of the 'device' to, in essence, act out the interaction with the user. Instead of a developer needing to program… [Continue Reading] -

Business needs a 'connectivity-first' approach
Publié: novembre 9, 2016, 3:24pm CET par Ian Barker
Many companies are realizing that traditional integration approaches no longer satisfy business requirements and are not designed for the digital age, according to a new report. The State of Salesforce Connectivity survey from cloud integration company Jitterbit looks at integration trends and needs from 300 companies from 33 different industries running Salesforce. The findings reveal that IT is increasingly being cut out of the software purchasing process. More than 70 percent of new software and technology purchases are made or influenced by the operating department, and around one in four new software purchases are made without involvement from IT at… [Continue Reading] -

What you need to know about data warehousing
Publié: novembre 7, 2016, 7:58pm CET par Ian Barker
Data warehouses are at the core of many information driven business initiatives. They’re used to store large volumes of historical data which can then be used in business intelligence projects to create knowledge-based reporting. But a data warehouse isn’t just a single, huge repository of data, they come in a number of different types. What they all have in common is that they’re separate from day-to-day operational systems. Data is uploaded to a warehouse after it has served its primary purpose, so that it can be used for statistical analysis and decision support, once out of date for this purpose… [Continue Reading] -

Employees feel pressure to use personal devices for work
Publié: novembre 7, 2016, 4:02pm CET par Ian Barker
Of employees in the US who use their personal smartphones for work, 45 percent are required to do so by their employers and 55 percent do so voluntarily. However, of those voluntary users 42 percent feel pressured to use their phone for business use outside of work. This is among the findings of a new survey by platform services company Syntonic which reveals mounting pressure on employees to use their personal devices for work even if not required by their employer. This is coupled with a growing reluctance by individuals to use their personal data plans. Half of employees postpone… [Continue Reading] -

What you need to know about enterprise collaboration
Publié: novembre 7, 2016, 2:48pm CET par Barclay Ballard, Ian Barker
Enterprise collaboration, sometimes abbreviated to EC or ECS for enterprise collaboration systems, is becoming an increasingly vital tool for many businesses. Essentially, it comprises various forms of hardware and software used to enable the seamless and efficient sharing of information and resources within a particular company. Enterprise collaboration systems can simply be relatively common communication tools such as email and instant messaging. Increasingly though businesses are turning to more bespoke solutions that combine these functions with project management and document management software. It is also worth noting that enterprise collaboration can prove beneficial for teams based in the same office,… [Continue Reading] -

How biometrics are addressing privacy concerns [Q&A]
Publié: novembre 7, 2016, 10:55am CET par Ian Barker
As traditional password security methods become increasingly discredited, enterprises are turning to other technologies to secure systems and transactions. Though many of the technologies are still in their infancy, others are becoming mainstream. We spoke to David Gerulski, vice president of fingerprint device specialist Integrated Biometrics to find out more about then latest technologies and how they're being used to address privacy concerns. BN: Will biometrics ever completely replace passwords or will they always be part of a two-factor model? DG: The current consensus heard at major identity conferences around the globe, and within biometrics industry advocacy groups, including the… [Continue Reading] -

The common causes of IT stress and how to deal with them
Publié: novembre 4, 2016, 4:13pm CET par Ian Barker
Anyone who works in IT knows that there are times when it can be an extremely stressful occupation. Especially when you’re expected to drop what you’re doing and fix a problem. Meeting technology specialist Highfive has put together an infographic looking at some of the most common causes of stress and how they can be managed. From low stress tasks like troubleshooting and implementing BYOD to more stressful issues like connectivity and highly stressful ones like rollouts and security breaches, it offers tips for staying on top of things whilst keeping your blood pressure under control. A lot of this… [Continue Reading] -

What you need to know about blockchain
Publié: novembre 4, 2016, 3:52pm CET par Ian Barker
For all the recent buzz surrounding the cloud and big data, it remains a fact that at the heart of much business computing there is still some form of database. In particular the operation of digital currencies like Bitcoin relies on databases that are able to track large volumes of transactions and keep them secure. The solution used by digital currencies -- though it’s increasingly finding other applications too -- is the blockchain. First implemented in 2009, blockchain technology consists of blocks that hold batches of timestamped transactions, each block is linked to the previous one, thus forming a chain.… [Continue Reading] -

You can use your phone, just shut up about the election!
Publié: novembre 4, 2016, 3:37pm CET par Ian Barker
Smartphone use at family dinners used to be something of a frowned on activity. But a new survey reveals that people are becoming more tech tolerant. The study from connected experience agency Sequence shows that while 35 percent of those surveyed say smartphone use at the holiday table creates tension, far more (65 percent) are bothered by discussing politics. In fact, 59 percent of consumers feel their family and friends are good about keeping their smartphones away during the holidays, which is a 20 percent increase from 2015. Nearly half of millennials (47 percent) say smartphones at the holiday table… [Continue Reading] -

App developers spend too much time debugging errors in production systems
Publié: novembre 3, 2016, 5:12pm CET par Ian Barker
According to a new study 43 percent of app developers spend between 10 and 25 percent of their time debugging application errors discovered in production, rather than developing new features. The survey carried out by ClusterHQ found that a quarter of respondents report encountering bugs discovered in production one or more times per week. Respondents were also asked to identify the most common causes of bugs. These were, inability to fully recreate production environments in testing (33 percent), interdependence on external systems that makes integration testing difficult (27 percent) and testing against unrealistic data before moving into production (26 percent).… [Continue Reading] -

Mobile devices set to influence holiday shopping habits
Publié: novembre 3, 2016, 4:43pm CET par Ian Barker
We're increasingly reliant on our mobile devices for many aspects of our lives and that includes our shopping. As we move towards the holiday season advertising platform Opera Mediaworks has surveyed 800 mobile users to find out how they intend to use their mobile devices for their seasonal shopping. Among the findings are that 40 percent of shoppers have made mobile purchases directly from an advertisement and 57 percent would make a mobile purchase if the product was relevant. In addition nine out of 10 shoppers find value in having their mobile devices with them while shopping in-store. There are… [Continue Reading] -

New solution aims to stop phishing attacks in their tracks
Publié: novembre 3, 2016, 3:26pm CET par Ian Barker
We know that phishing is on the increase and that attacks are becoming ever more sophisticated. The Anti-Phishing Working Group (APWG) found more than 460,000 unique phishing sites in the second quarter of 2016 alone, up 61 percent over the previous quarter and almost three times the number observed in the fourth quarter of 2015. Doamin name and threat intelligence company DomainTools is launching a new security solution that helps to prevent phishing attacks before they happen by spotting phishing domains. Called PhishEye -- see what they've done there? -- it automates the process of identifying look-alike domains that spoof… [Continue Reading] -

Off-the-shelf Android spyware targets high level executives
Publié: novembre 3, 2016, 1:14pm CET par Ian Barker
The increasing commoditization of malware means that you no longer need to be a technical expert to launch an attack. You can simply buy the tools off the shelf. Researchers at Skycure Research Labs have uncovered just such an off-the-peg spyware attack targeting senior company executives. The app called Exaspy is a commercial Android spyware package that gives an attacker access to much of the victim's data. It was found on an Android device belonging to the vice president of a global technology company. The software disguises itself as an app called 'Google Services' and uses the package name 'com.android.protect'. This… [Continue Reading] -

What you need to know about deep learning
Publié: novembre 2, 2016, 7:12pm CET par Ian Barker
The concept of machine learning has been around for some time. Deep learning is an area of research aimed at taking things further still and getting closer to an artificial intelligence system by using neural networks in a way that imitates the human brain. Sometimes also referred to as hierarchical learning or deep structured learning, it seeks to model data in order to solve problems like object and facial recognition, natural language processing and speech recognition. It’s called deep learning because the data is processed through a number of layers, usually in a neural network, the output from one layer… [Continue Reading] -

Datto launches new ransomware protection for SMBs
Publié: novembre 2, 2016, 5:18pm CET par Ian Barker
We already know that ransomware is a lucrative business for the attackers. But for the victims, especially smaller businesses, it can prove devastating. A new solution offering enterprise-class ransomware protection for small and mid sized companies is being launched by data protection specialist Datto. In the event of an attack it aims to shorten downtime, save money and reduce the impact to business, giving companies an effective and reliable alternative to paying hackers' ransoms. The software guards against malicious encryption in the company's Backupify, Datto NAS and Datto Drive offerings, as well as providing ransomware detection within its flagship SIRIS… [Continue Reading] -

Developers prefer open source tools
Publié: novembre 2, 2016, 3:53pm CET par Ian Barker
New research shows that 98 percent of developers use open source tools at work, with 56 percent revealing that more than half of their development tools are open source, and 18 percent using only open source tools. The study from code collaboration platform GitLab also shows that more than half of developers (55 percent) are able to choose the tools they work with. When asked about the tools and techniques that are most important to them, 92 percent say distributed version control systems (Git repositories) are very or extremely important for their everyday work followed by continuous integration (77 percent),… [Continue Reading] -

New platform aims to deliver personalized communications to any device
Publié: novembre 2, 2016, 2:53pm CET par Ian Barker
In order to retain customers businesses need to be responsive to their needs and send them relevant communications. Mobile growth platform company Urban Airship is making it easier for marketers to do this with a service that lets them deliver individualized messaging to any platform, device or marketing channel and use real-time customer data from any system. It uses a two-pronged approach with what it calls Open Channels and Open Profiles. Open Channels, allows companies to reach customers with rich notification-style messaging on any channel -- from chat messaging services and email, to intelligent personal assistants and in-car information systems.… [Continue Reading] -

New platform improves accuracy of behavioral attack detection
Publié: novembre 2, 2016, 1:15pm CET par Ian Barker
As cyber attacks get more sophisticated, so being able to spot them requires a different approach from simply looking for signatures. Behavioral detection company LightCyber is launching a new version of its Magna platform that increases the precision and speed of detecting an in-progress attack from either a malicious insider or external bad actor. "Detecting and thwarting an active attack requires highly precise detection of the attacker’s operational activities," says Jason Matlof, executive vice president of LightCyber. "The historic problem endemic to security has been the inability to parse out the most relevant attacker signals, which has resulted in overwhelming… [Continue Reading] -

What you need to know about enterprise resource planning
Publié: novembre 1, 2016, 8:24pm CET par Sam Pudwell, Ian Barker
We’ve already covered what businesses need to know about enterprise content management (ECM), so now it’s time to move on to another popular business tool: enterprise resource planning (ERP). ERP is business process management software -- typically consisting of a suite of integrated applications -- that allows an organization to manage its entire business and automate many back-office functions. It is designed to be used by larger enterprises -- often requiring dedicated teams to customize and analyze the data -- and integrates various facets of an operation, including sales and marketing, product planning, manufacturing and inventory management, making sure everything… [Continue Reading] -

AdWords malvertising targets macOS users
Publié: novembre 1, 2016, 6:10pm CET par Ian Barker
Researchers at threat prevention company Cylance have discovered a malvertising campaign on Google AdWords for the search term "Google Chrome", where unsuspecting macOS users were being tricked into downloading a malicious installer. The installer, identified as "OSX/InstallMiez" (or "OSX/InstallCore"), ultimately downloads a malicious file named "FLVPlayer.dmg". The malware hash changes on each download, making it difficult to detect and track. Once the installation is completed, the browser is redirected to a scareware page. Clicking on the link leads to another page offering a potentially unwanted program (PUP) claiming to cleanup OS X computers as well as starting a download for… [Continue Reading] -

British empire strikes back with new cyber security strategy backed by £1.9 billion investment
Publié: novembre 1, 2016, 4:20pm CET par Ian Barker
The UK government has today launched a new National Cyber Security Strategy, setting out decisive action to protect the nation's economy and the privacy of British citizens, and strike back against attackers, while encouraging industry to up its game to prevent damaging cyber-attacks. The strategy sets out how the UK will use automated defenses to safeguard citizens and businesses against growing cyber threats, support the UK's growing cyber security industry, develop a world-class cyber workforce, and deter cyber-attacks from criminals and hostile actors. The announcement also promised £1.9 billion (around $2.3 billion) of investment for action in three key areas,… [Continue Reading] -

Enterprises put themselves at risk by running outdated Microsoft products
Publié: novembre 1, 2016, 3:46pm CET par Ian Barker
According to a new report 65 percent of Windows systems are still running Windows 7, and a small percentage of devices are still running Windows XP. The survey from trusted access specialist Duo Security analyzed more than two million endpoints and found 63 percent of them running Microsoft operating systems. Yet only 24 percent are running Windows 10. Windows 7 remains the most popular despite there being over 600 vulnerabilities affecting unpatched versions. The unloved Windows 8.1 is on eight percent of surveyed systems. Although only one percent of systems are still running XP that still accounts for tens of thousands of… [Continue Reading] -

70 percent of organizations are swamped by threat data
Publié: novembre 1, 2016, 1:05pm CET par Ian Barker
New research from threat intelligence platform Anomali and the Ponemon Institute shows that 70 percent of security industry professionals believe threat intelligence is often too big and/or complex to provide actionable insights. It also shows that they often fail to share essential threat data with board members and C-level executives, despite the fact that security is now a business priority. In addition the study finds that security teams within organizations aren't optimized to deliver on threat intelligence. Less than half (46 percent) of those polled say incident responders use threat data when deciding how to respond to malicious activity, which… [Continue Reading] -

What you need to know about enterprise content management
Publié: octobre 28, 2016, 8:00pm CEST par Sam Pudwell, Ian Barker
Thanks to the likes of smartphones, the internet and big data, we now have access to more information in various shapes and sizes than ever before. In most cases, having more information is a good thing for businesses, but there comes a point where there is simply too much to keep track of. This is especially true in large enterprises, where invoices, word documents, receipts and purchase orders are in abundance and could be needed by anyone at any time. Keeping on top of all of this would be a challenge for even the most organized individuals, so that’s where… [Continue Reading] -

The changing face of the enterprise storage market [Q&A]
Publié: octobre 28, 2016, 4:20pm CEST par Ian Barker
The growth of cloud usage, increasing volumes of information and a switch towards software defined systems based on commodity hardware have all had an impact on the storage market. About a year ago we spoke to Mark Lewis, Chairman and CEO of storage specialist Formation Data Systems to get his views on the future of enterprise storage. This week we caught up with Mark again to find out how much the market has changed in just a short time. BN: What have been the big changes in the storage industry over the past year? ML: It's been an interesting year… [Continue Reading] -

Comodo offers companies free forensic analysis to fight zero-day malware
Publié: octobre 26, 2016, 5:12pm CEST par Ian Barker
Because it isn't detected by traditional, signature based anti-virus solutions, zero-day malware has the potential to wreak havoc in businesses of all sizes. Cyber security company Comodo is launching a new, free forensic analysis service to help enterprises discover previously unknown and undetected malware that could cause serious security issues or data breaches. "Underpinned by Comodo's industry-leading Default Deny Platform, this is the only forensic analysis that can examine 100 percent of all files, including unknown ones, and determine if they are good or bad," says John Peterson, vice president and general manager, Comodo Enterprise. "We are offering this forensic… [Continue Reading] -

New software simplifies BYOD management
Publié: octobre 26, 2016, 3:50pm CEST par Ian Barker
The US mobile workforce is set to grow to 105.4 million workers by 2020 according to IDC and this creates a challenge for businesses trying to control and secure deployments. In a bid to make things easier, networking solutions company Brocade is launching its latest Ruckus Cloudpath platform to enable IT organizations of any size to easily establish secure, policy-based access for wired and wireless devices. Features of Cloudpath ES 5.0 include a faster, better end-user experience. It takes users as little as 10 seconds to onboard a device and users don't need to remember passwords, with no re-login necessary… [Continue Reading] -

Traditional retailers need to engage customers via mobile or lose them to online sellers
Publié: octobre 26, 2016, 3:28pm CEST par Ian Barker
As we approach the holiday season retailers will be looking forward to the annual boost in sales that it brings. But a new survey from Euclid Analytics reveals that if retailers don’t employ digital strategies to engage shoppers they risk losing them to online merchants like Amazon. Mobile and social media adoption means a different shopping experience for consumers who are looking to make holiday purchases. They could be shopping at a physical store, while at the same time comparing prices and looking for coupons via Facebook on their smartphones. Among the study's findings are that 83 percent of consumers say… [Continue Reading] -

Millennial behavior puts federal IT systems at risk
Publié: octobre 25, 2016, 5:59pm CEST par Ian Barker
The security habits of the millennial generation could be putting federal IT systems at risk, if agencies don't adjust their cyber defenses in time. This finding comes from a new study by cyber security company Forcepoint, which examines how members of the millennial generation use technology. Millennials currently make up about 25 percent of federal employees and are expected to represent nearly 75 percent of the workforce by 2025. But while baby boomers are more cautious online, the survey data shows that millennials (those born between 1977 and 1994) are more likely to abandon caution for digital expediency. Federal organizations face… [Continue Reading] -

The seven IoT devices that could be putting your business at risk
Publié: octobre 25, 2016, 5:08pm CEST par Ian Barker
We've already seen concerns about the threats Internet of Things gadgets may pose in the home, with hackable Barbie dolls and snooping Smart TVs. Not to mention that the latest Dyn DDoS attack was carried out using unsecured IoT devices. IoT devices are starting to become commonplace in businesses too so the potential for problems can only grow. Security company ForeScout, along with leading ethical hacker Samy Kamkar, has been investigating the risks these devices pose. The research looked at seven common enterprise IoT devices: IP-connected security systems, smart climate control systems and energy meters, video conferencing systems, connected printers, VoIP phones,… [Continue Reading] -

IT executives are out of step with their teams
Publié: octobre 25, 2016, 4:53pm CEST par Ian Barker
A new report finds that there's a disconnect between IT executives and their staff on critical issues, including control over SaaS applications. The report from cloud specialist BetterCloud shows that non-executive IT staff, when compared to IT executives, are 29 percent more likely to say their team lacks complete control over their SaaS applications and 56 percent more likely to feel like their IT team lacks complete visibility into them. "IT executives often struggle to see many of the critical issues their departments face. As a result, many are unaware of the cracks in their IT environment that are forming… [Continue Reading] -

New tool offers SWIFT network protection through deception
Publié: octobre 25, 2016, 4:05pm CEST par Ian Barker
Attacks on the inter-bank SWIFT system have been making the headlines this year, proving lucrative for the hackers and worrying for the industry. Help is on the way though as Cyber security company TrapX is launching a deception-based security solution, DeceptionGrid, specifically designed protect SWIFT. "In the past year, SWIFT has been under attack by persistent cyber attackers, which have resulted in the theft of more than $100 million dollars from banks worldwide," says Greg Enriquez, CEO of TrapX. "These attacks demonstrate a broad knowledge of bank operations as attackers combine them with sophisticated tools and techniques to penetrate target… [Continue Reading] -

Thycotic launches free tool to expose endpoint threats
Publié: octobre 25, 2016, 3:16pm CEST par Ian Barker
We're seeing attacks on endpoint systems becoming more common and increasingly clever. Yet for administrators knowing what's happening on their endpoints presents a challenge. Privileged account management specialist Thycotic is launching a new, free Endpoint Application Discovery Tool to automatically discover and reports on applications installed on Windows endpoints. Using this new tool, IT security professionals can gain visibility over their entire network and understand any risks that are involved with applications running on their systems. The software helps security professionals discover applications installed, report on those applications to raise awareness of vulnerabilities in the network, flag potential applications with high security… [Continue Reading] -

What you need to know about hybrid cloud
Publié: octobre 24, 2016, 6:44pm CEST par Barclay Ballard, Ian Barker
In terms of industry buzz and discussion, it is unlikely you’ll find a technological concept that’s more popular at the moment than cloud computing. Since it burst on to the scene a few years ago, cloud computing has proven its utility within a huge range of business and consumer markets. With the flexibility, productivity and cost advantages being delivered by the cloud, it can truly claim to have had a profound impact on the way that we live our lives. However, although "cloud computing" is often spoken about in relatively generalized terminology, it is far from a homogeneous resource. Public,… [Continue Reading] -

Enterprises struggle to manage cloud complexity
Publié: octobre 24, 2016, 4:06pm CEST par Ian Barker
Businesses are looking to transform their IT services by moving to the cloud, but a new report reveals that they’re increasingly struggling to manage its complexity. The study from cloud automation company Embotics and 451 Research surveyed 166 US-based enterprise IT organizations regarding their use of cloud infrastructure and the management and automation of the associated processes. It finds that more than 75 percent of enterprises are using multiple clouds, including public and private. In addition 65 percent of respondents with more than one cloud are using a cloud management platform and 54 percent are using tools from multiple providers. Meanwhile… [Continue Reading] -

Adding facial recognition to mobile helps reduce fraud
Publié: octobre 24, 2016, 3:21pm CEST par Ian Barker
Doing more of our day to day transactions online increases the risk of falling victim to some kind of fraud. Increasingly therefore companies are turning towards biometrics to ensure users are who they say they are. Digital verification company Jumio is adding biometric facial recognition to its Netverify product to verify users on mobile devices. The use of biometrics aims to reduce fraud within the banking, finance, travel, and online gaming industries by ensuring a user is a live human rather that a photograph. Netverify performs a face match but also completes a 'liveness' check, which takes no more than… [Continue Reading] -

What you need to know about DevOps
Publié: octobre 20, 2016, 8:18pm CEST par Sam Pudwell, Ian Barker
The term DevOps is being thrown around a lot in the IT industry at the moment, but what exactly does it mean and, more importantly, how can it help an enterprise? As a combination of developer and operations, DevOps looks to bring these two different areas of digital business together to provide the perfect combination of innovation and user-focused processes during software development. Continuous deployment and continuous delivery are both important aspects of this and, when adopting DevOps, it is vitally important that businesses assess which one is right for them. It also looks towards the automation of delivering changes to… [Continue Reading] -

What you need to know about quantum computing
Publié: octobre 20, 2016, 6:49pm CEST par Ian Barker
Most people will be familiar with Moore’s Law which states that the number of transistors it’s possible to get on a microprocessor doubles every 18 months. If this holds true it means that some time in the 2020s we’ll be measuring these circuits on an atomic scale. You might think that that’s where everything comes to a juddering halt. But the next step from this is the creation of quantum computers which use the properties of atoms and molecules to perform processing and memory tasks. If this all sounds a bit sci-fi, it’s because practical quantum computers are still some… [Continue Reading] -

New automation tool helps businesses deploy Docker containers
Publié: octobre 20, 2016, 6:16pm CEST par Ian Barker
Automated software delivery specialist Puppet is launching a new Docker Image Build tool, which automates the container build process to help organizations as they define, build, and deploy containers into production environments. It adds to existing Puppet functionality for installing and managing container infrastructure, providing a standard, consistent way to install Docker operating environments as well as building and deploying containers. "For the last decade Puppet has enabled organizations to adopt the latest technologies and everything running on top of it, including virtualization, public and private clouds, and now containers," says Deepak Giridharagopal, CTO at Puppet. "Over the last year… [Continue Reading] -

New platform guards against in-memory endpoint attacks
Publié: octobre 20, 2016, 3:29pm CEST par Ian Barker
Cyber attackers know that the weakest point of an organization's security is usually the endpoint and they'll increasingly try to hide malware's presence from security tools by running it only in memory. Endpoint security specialist Endgame is releasing an update to its platform which expands coverage of the attacker lifecycle to anticipate innovations. Today's release enhances in-memory attack detection and malicious persistence detection capabilities, building on Endgame's pre-exploit prevention, signature-less malware detection, early-stage attacker technique detection, and automated investigations. Endgame can detect all known and unknown techniques used by adversaries to hide in-memory. Its patent-pending technology detects in-memory-only adversaries by… [Continue Reading] -

What you need to know about cognitive computing
Publié: octobre 20, 2016, 2:27pm CEST par Ian Barker
The ability to think is one of the things that marks us out as human, "I think therefore I am", as the philosopher René Descartes put it. But what if machines were able to mimic human thought processes? This is the basic premise behind cognitive computing. In order to replicate human thought processes, cognitive computing uses techniques like pattern recognition, data mining and natural language processing. The ultimate goal is to be able to make computer systems that are capable of solving complex problems without needing human assistance to prompt them in the right direction. Computing giant IBM, which is… [Continue Reading] -

New cloud platform streamlines enterprise digital transformation
Publié: octobre 20, 2016, 12:00pm CEST par Ian Barker
If you only have a few websites and mobile apps to handle looking after them is a fairly straightforward task. But businesses that need to handle multiple digital properties with proper governance and security -- at the same time delivering a consistent, personalized customer experience -- face a major challenge. To help companies face these challenges, application development company Progress is launching a new DigitalFactory platform. This is a cloud-based digital transformation solution built for developers, IT administrators and marketers to allow them to collaborate on and deliver engaging customer experiences that meet the needs of business at a global… [Continue Reading] -

What you need to know about IT infrastructure library
Publié: octobre 20, 2016, 11:16am CEST par Ian Barker
Bringing information technology into line with the needs of the business is frequently a problem. ITIL -- originally known as Information Technology Infrastructure Library -- is aimed at resolving this by establishing a set of rules for IT service management (ITSM). The ITIL framework is geared to standardizing the choosing, planning, delivery and support of business IT services. The intention is to deliver greater efficiency and predictable service levels. Published as a series of five core volumes, each of which covers a part of the ITSM lifecycle, the current version of ITIL (ITIL v3) first appeared in 2007 and received… [Continue Reading] -

What you need to know about IT service management
Publié: octobre 19, 2016, 9:03pm CEST par Ian Barker
In the early days of business computing, the technology was seen as a supporting tool to help speed up processes like preparing accounts or controlling stock. But as information technology has found its way into more and more areas of business, it’s become increasingly important that IT should be aligned with the needs of the business and be able to deliver added value. For this to be effective businesses need to have policies and procedures in place to plan, deliver, control and operate the IT services they offer either internally or to outside customers. All of these activities can be… [Continue Reading] -

What you need to know about CRM
Publié: octobre 19, 2016, 8:47pm CEST par Barclay Ballard, Ian Barker
For the vast majority of organizations, customers should be the number one priority. Without their support, revenue streams dry up and businesses quickly fail. For small businesses that have a face-to-face relationship with their clients keeping them happy is straightforward, but in larger organizations ensuring that the relationship between business and customer is as positive as it can be is not always easy. Imagine being in charge of a global, multi-national company with thousands of customers in disparate locations. Each of these customers has their own specific needs and businesses can’t afford to treat them all as a single homogeneous… [Continue Reading] -

What you need to know about product lifecycle management
Publié: octobre 17, 2016, 6:20pm CEST par Ian Barker
In any kind of production process, whether the end product is a washing machine or a piece of software, there are a number of stages to go through. From the initial idea, through design to manufacturing, service and support, and end of life and disposal, all products go through a similar lifecycle. Product lifecycle management is about integrating the staff, data, processes and business systems that go to produce a product. This in turn provides a fund of information surrounding the creation of the product which can be used to streamline the development of future products. PLM software allows this… [Continue Reading] -

How incentives are key to driving mobile wallet use
Publié: octobre 17, 2016, 4:13pm CEST par Ian Barker
Mobile wallets are gaining in popularity, according to a new survey by loyalty platform Points almost 64 percent of consumers say they've used a mobile wallet in the past year. However, some consumers are still reluctant to make mobile payments for a variety of reasons. 47 percent are concerned about security and privacy, 45 percent say that credit and debit cards and/or cash are enough, and 20 percent say it’s too complicated. When opting for a mobile wallet, 84 percent want ease of payment, 79 percent payment security and 61 percent integrated loyalty programs. Asked about the improvements they'd like… [Continue Reading] -

Netskope expands its Threat Protection product to cover ransomware
Publié: octobre 17, 2016, 3:17pm CEST par Ian Barker
Ransomware is increasingly big business and more than 43 percent of malware types are used to deliver it. It can also be unwittingly spread via the use of cloud services. To protect against the threat, cloud security company Netskope is adding ransomware detection and recovery capabilities to its Netskope Threat Protection product. It uses a proprietary method of detection using machine learning to monitor file operations. In addition it has the ability to scan sanctioned cloud services, including Office 365, Box and Dropbox, for unauthorized encryption due to a ransomware infection and quickly fix the effects of an attack without… [Continue Reading] -

What you need to know about martech
Publié: octobre 14, 2016, 6:28pm CEST par Barclay Ballard, Ian Barker
We’ve already covered fintech, and now it’s time to have a look at another technology portmanteau: martech. Short for marketing technology, it refers to innovative new approaches to campaigns and other marketing tactics, driven by software and hardware developments. It is an area that is experiencing rapid growth, with worldwide martech spending expected to reach $32 billion by 2018, up from $22.6 billion in 2015. Because many of the tools behind the growth of martech are relatively new, such as customer relationship management software and big data analytics, they are generating both opportunities and challenges for many marketers. The test facing businesses… [Continue Reading] -

New endpoint solution protects privileged access credentials
Publié: octobre 13, 2016, 5:46pm CEST par Ian Barker
Credentials for privileged access accounts are a prime target for cyber attackers and they can often be stolen from vulnerable endpoints. Privileged account management specialist Thycotic is tackling this problem by launching Privilege Manager for Windows, which allows IT admins to implement a wide array of policies and controls that best match their needs. With a simple process of policy matching, contextual evaluation, and applying actions, the software provides a flexible, powerful, and easy to use solution for protecting endpoints. When an application is launched Privilege Manager identifies it, checks it against security policies and then applies appropriate actions. Actions… [Continue Reading] -

Healthcare companies are facing a cyber security crisis
Publié: octobre 13, 2016, 3:55pm CEST par Ian Barker
Many industries have found that the rapid expansion in demand for digital information has outpaced efforts to keep the data secure. This is a particular issue for healthcare organizations which handle confidential records yet have seen some headline breaches in recent years. UpGuard, the company behind the CSTAR security preparedness score for enterprises, has released a new report which provides fresh data on the security failings of companies in the healthcare industry. The company evaluated 500 healthcare companies across various sectors -- from health insurers to pharmaceutical companies and hospitals -- and gave them each a CSTAR score, a single measure of… [Continue Reading] -

Most businesses haven't inspected cloud services for malware
Publié: octobre 12, 2016, 4:24pm CEST par Ian Barker
Echoing the findings we reported earlier that companies leave cloud protection to third-parties, a new study from cloud security company Netskope reveals most companies don't scan their cloud services for malware either. The study conducted with the Ponemon Institute shows 48 percent of companies surveyed don't inspect the cloud for malware and 12 percent are unsure if they do or not. Of those that do inspect 57 percent of respondents say they found malware. It also shows that while 49 percent of business applications are now stored in the cloud, fewer than half of them (45 percent) are known, officially sanctioned or approved by IT.… [Continue Reading] -

New camera technology makes video conferencing a snap
Publié: octobre 12, 2016, 3:21pm CEST par Ian Barker
With increasingly distributed workforces, video conferencing is more than ever an essential business tool. But in conference rooms the size and shape of the space can make it difficult for conventional cameras to include everyone. Video conferencing technology company Lifesize is launching a new camera with a smart-framing sensor that intelligently adjusts its wide-angle lens to automatically capture and include everyone in the meeting. The Lifesize Icon 450 pairs with the company's cloud-based video communication program to create a collaboration hub that's simple for end users to operate and easy for IT administrators to support. "For most businesses the conference… [Continue Reading] -

Enterprises leave protection of cloud data to third-party providers
Publié: octobre 12, 2016, 3:02pm CEST par Ian Barker
Businesses are increasingly moving their systems to the cloud, but 62 percent rely on the cloud provider to back up applications running on their platform. New research from secure cloud services company CTERA Networks reveals that 67 percent of organizations deploy more than 25 percent of their applications in the cloud, and 37 percent plan to grow their cloud use by at least 25 percent, if not more. In addition, 54 percent of organizations are embracing a hybrid cloud strategy that uses both on-premises and cloud services. However, 66 percent strongly or somewhat agree that there is less focus on… [Continue Reading] -

Lack of visibility leads to cloud storage security issues
Publié: octobre 12, 2016, 12:05pm CEST par Ian Barker
A lack of visibility into an organization's use of cloud providers can lead to unauthorized access to data, improper handling and storage of data and unauthorized data removal. As a result, organizations are left exposed and vulnerable to a data breach. This is among the findings of a new report from the Blancco Technology Group. Based on a survey of almost 300 IT professionals around the world it finds that 26 percent of organizations are either 'not confident' or only 'somewhat confident' about their IT teams' knowledge of the use of all cloud storage providers. This is despite the fact… [Continue Reading] -

What you need to know about software-defined networking
Publié: octobre 12, 2016, 10:56am CEST par Ian Barker
As more and more systems move to the cloud, so we’re becoming increasingly used to accessing all systems on an as-a-service model. Networking is no exception to this and by using software-defined networking businesses can break away from the restrictions imposed by old, inflexible static network architecture. SDN allows companies to master the complex nature of their networks and have a single point of control. At the same time it opens up the possibility of automating network management to allow it to cope with fluctuations in traffic and demand. Origins of SDN The idea of software-defined networking isn’t new, it… [Continue Reading] -

What you need to know about Docker
Publié: octobre 11, 2016, 8:17pm CEST par Barclay Ballard, Ian Barker
Considering it only came into existence in 2013, Docker has experienced a monumental rise in both the consumer and business markets. From such humble beginnings, (the earliest version of the technology was developed by founder Solomon Hykes in his mother’s basement), Docker has managed to secure a number of high-profile partners and in 2015 received a valuation in excess of $1 billion. But what exactly is Docker? According to the company itself, "Docker allows you to package an application with all of its dependencies into a standardized unit for software development". The way in which Docker does this is through… [Continue Reading] -

Shopping apps targeting women generate better profits
Publié: octobre 11, 2016, 6:16pm CEST par Ian Barker
Marketers must target women if they are looking to succeed and make profits in the mobile sector, according to a new report. The Mobile App Engagement Index from performance based marketing platform Liftoff analyzed 7.3 million app installs across five sectors to unearth key app trends from the first half of this year. It finds that female customers are not only more likely to make a purchase in both mobile e-commerce and gaming apps, they are also less expensive to acquire compared to their male counterparts. Liftoff found that women were nearly 34 percent more likely to make a purchase… [Continue Reading] -

Enterprises increase reliance on public key infrastructures
Publié: octobre 11, 2016, 11:26am CEST par Ian Barker
A new report released by data protection company Thales and the Ponemon Institute shows that the use of cloud services and the IoT has led to greater dependence on public key infrastructures (PKIs) in today's businesses. The survey of more than 5,000 companies across 11 countries shows that PKIs -- used to create, distribute, store, and revoke digital certificates and manage public-key encryption -- are increasingly relied on to support applications. On average PKIs support eight different applications within a business, up one from 2015, but in the United States the number is up by three applications. Cloud-based services are seen as… [Continue Reading] -

How connected cars are vulnerable to attack
Publié: octobre 10, 2016, 10:59am CEST par Ian Barker
It's reckoned that by 2020 three-quarters of new cars shipped globally will have some form of internet connectivity. But while this brings benefits in terms of practicality and ease of use it also adds cars to the list of IoT devices that are vulnerable to attack. We've already seen Fiat Chrysler recalling cars to fix a vulnerability and this could be just the tip of the iceberg. Mobile protection specialist Arxan has put together an infographic highlighting some of the ways connected cars could be attacked. These include intercepting communication between mobile apps used to unlock or immobilize the vehicle.… [Continue Reading] -

Free disaster recovery for businesses in the path of Hurricane Matthew
Publié: octobre 7, 2016, 11:30am CEST par Ian Barker
Hurricane Matthew is already the most powerful Atlantic tropical storm in almost a decade and has caused devastation in Haiti. Homes and businesses in Florida are now bracing themselves for its impact. In response to the storm, disaster recovery as a service specialist Axcient is offering complimentary, no commitment disaster recovery services to businesses potentially affected by Matthew's approach. This offer will allow businesses to protect their applications and data using Axcient's cloud-based IT resilience platform, Fusion, to minimize any IT downtime that might result from the storm. Fusion setup takes less than 15 minutes and Axcient has staff on… [Continue Reading] -

TalkTalk fined £400,000 for security breach
Publié: octobre 5, 2016, 5:45pm CEST par Ian Barker
UK ISP TalkTalk hit the headlines last year for a data breach that resulted in the theft of personal data relating to over 150,000 customers. Today the Information Commissioner's Office announced that it has issued the company with a record £400,000 (around $510,000) fine for what it called a failure to implement basic security measures. "In spite of its expertise and resources, when it came to the basic principles of cyber-security, TalkTalk was found wanting," says Information Commissioner Elizabeth Denham. "Today's record fine acts as a warning to others that cyber security is not an IT issue, it is a… [Continue Reading] -

SaaS makes our jobs more difficult say IT pros
Publié: octobre 5, 2016, 3:30pm CEST par Ian Barker
There is a perception in the IT business that adopting software-as-a-service models will make life easier for tech teams and end users alike. But a new study by cloud specialist BetterCloud suggests that in fact SaaS is making IT jobs harder. According to the survey of over 900 IT professionals, 56 percent of Google Apps and 62 percent of Office 365 IT pros believe their jobs are becoming more difficult due to rising SaaS adoption. For these respondents, adopting SaaS means dealing with more vendors, more dashboards, more data, and having less control over cloud IT systems. "Many IT professionals… [Continue Reading] -

Intel Security launches new McAfee lineup harnessing the power of the cloud
Publié: octobre 5, 2016, 12:49pm CEST par Ian Barker
As we use more devices to access the internet protecting all of them from the latest threats becomes something of a chore. Intel Security is addressing this with the launch of a new 2017 range of McAfee security products at the heart of which is a next-generation anti-malware engine that offers more efficient and effective threat detection by offloading analysis to the cloud. McAfee AntiVirus Plus, McAfee Internet Security, McAfee Total Protection and McAfee LiveSafe offer cross-device protection for PCs, Macs, smartphones and tablets. Features include Real Protect, a next generation anti-malware engine that combines proven detection methods with an… [Continue Reading] -

How ransomware threatens government agencies [Q&A]
Publié: octobre 5, 2016, 11:10am CEST par Ian Barker
Ransomware is an increasingly severe threat to all organizations and government agencies are not exempt. The Federal Trade Commission recently labeled ransomware as "among the most troubling cyberthreats". But why are government agencies such an attractive target and what can they do to combat the threat? We spoke to Andrew Hay, chief information security officer of data security specialist DataGravity to find out. BN: Ransomware isn't a new danger, but it seems to be on the rise. Why is the FTC just now recognizing it as a cybersecurity threat? AH: Although the threat isn't new, people are aware of ransomware… [Continue Reading] -

IBM and Carbon Black announce new endpoint security solution
Publié: octobre 4, 2016, 5:38pm CEST par Ian Barker
Addressing endpoint vulnerabilities is a major challenge for businesses, often compounded by a lack of visibility into which devices are being actively exploited. According to Gartner 99 percent of vulnerabilities exploited are ones that professionals have known about for a year, but have lacked the solutions to address. To tackle this IBM and Carbon Black have got together to design a new integrated offering, which links Carbon Black's endpoint activity data with public Common Vulnerabilities and Exposures (CVE) databases to deliver a prioritized list of actively exploited vulnerabilities that's tailored to each organization. By combining IBM BigFix and Carbon Black… [Continue Reading] -

Self-service solution improves the quality of Salesforce data
Publié: octobre 4, 2016, 4:24pm CEST par Ian Barker
Thanks to the explosion in cloud applications and the increasing number of IoT devices, enterprises have more data than ever. But there's no easy way to ensure its quality. Data management specialist Informatica is launching its Cloud Data Quality Radar a self-service data quality solution for business. Salesforce users will be the first to benefit. The cloud-based solution is designed to easily identify, fix and monitor the quality of data within and across applications, whether in the cloud or on-premise. By offering self-service it means data owners and users can be actively involved in keeping data clean, regardless of where… [Continue Reading] -

New platform provides coaching insights for sales managers
Publié: octobre 4, 2016, 3:14pm CEST par Ian Barker
In recent times many CRM platforms have tended to focus on using machine learning to boost sales. Sales capabilities company Qstream, however, is keen to address the human side of improving sales performance. At this week's Dreamforce '16 conference it's announced that its expanding its Sales Capabilities Platform with a Coaching Hub, which allows managers to identify gaps in their team's required knowledge or behaviors and address them faster. The data-driven Coaching Hub brings together a number of metrics, observed sales skills and confidence ratings at the individual or team level in a single click. It shows a graphical coaching activity… [Continue Reading] -

How to avoid falling victim to phishing attacks
Publié: octobre 4, 2016, 11:26am CEST par Ian Barker
Phishing attacks are becoming increasingly sophisticated. The old days of badly written emails are largely behind us, making today’s attacks much harder to spot. To mark the fact that October is National Cyber Security Awareness Month in the US and European Cyber Security Month, data loss prevention company Digital Guardian has released an infographic to help users recognize and avoid phishing attacks. It covers the different types of phishing including 'whaling' -- targeting senior people within a company. It also looks beyond email at voice phishing (vishing), SMS phishing (smishing), and social media phishing (make up your own cute name… [Continue Reading] -

Actiance seeks to scoop up HP Autonomy customers
Publié: septembre 30, 2016, 3:19pm CEST par Ian Barker
HP Enterprise's announcement earlier this month that it was spinning off its 'non-core' software business, including the Autonomy big data solution to Micro Focus, has left many customers worried about the future. Archiving, analytics and compliance specialist Actiance is hoping to attract these users with the launch of an Autonomy Safe Landing Program, letting users easily transition to its Alcatraz archiving product. Alcatraz is a web-scale cloud archive designed from the ground up to store email and social communications in context. With fast search, high-performance import and exports, and robust APIs it lets companies discover insights while ensuring supervisory and surveillance workflows,… [Continue Reading] -

IP shielding enables secure voice and video conferencing
Publié: septembre 28, 2016, 6:58pm CEST par Ian Barker
There's a great deal of emphasis on securing data and email, but essential business communication via voice and video tends to get ignored. Yet these communications are vulnerable, partly because devices constantly release metadata, telling the network where and how to route communications. To address this, Privacy-as-a-Service platform specialist Dispel is launching a secure voice and video conferencing service, a single application designed to provide enterprises and individuals with impenetrable private communications on their smartphones and mobile devices. "Parallel with the increased use of encryption, big data analysis and behavioral inference have become the techniques of choice for technically sophisticated… [Continue Reading] -

Does your personality make you more likely to get hacked?
Publié: septembre 28, 2016, 4:53pm CEST par Ian Barker
LogMeIn the company behind the LastPass password manager has released the results of a survey looking at consumer psychology, behavior and attitudes when it comes to managing personal passwords. Among the findings are that 61 percent of respondents use the same or similar passwords across accounts, and 55 percent of them do it even though they understand the risk. Also more than a third (39 percent) create more secure passwords for their personal accounts than their work accounts. Only five percent of respondents didn't know the characteristics of a secure password, with the majority of respondents understanding that passwords should… [Continue Reading] -

Board members say they need cyber security experts
Publié: septembre 28, 2016, 4:13pm CEST par Ian Barker
Three out of five board members believe that they need to have cyber security experts on their boards, yet only one in six claim to have substantial expertise in understanding the implications of cyber security. These are among the findings of a report from risk analytics specialist Bay Dynamics which looks at why boards of directors are making cyber security a top priority and the challenges they face in reducing risk. The need for compliance is driving many decisions, in the past two years, there has been an 11-fold increase in the number of organizations citing increased regulation from government… [Continue Reading] -

New service helps enterprises secure legacy applications
Publié: septembre 28, 2016, 3:05pm CEST par Ian Barker
Many companies rely on legacy applications, but while they're keen to get maximum return on their investment and avoid the costs of moving to a new system, they may be opening themselves to security threats. Information risk management consultancy AsTech Consulting is launching its Legacy Application Security Evaluation and Remediation (LASER) guided security improvement program to help companies uncover hidden security issues. "LASER is first fully scalable, productized service focused exclusively on large legacy applications allowing companies to tailor the level of investigation they want focused on their application, and the type of help they need to address the vulnerabilities in the… [Continue Reading] -

The security risks of migrating legacy applications to the cloud [Q&A]
Publié: septembre 27, 2016, 5:29pm CEST par Ian Barker
Enterprise use of the public cloud is taking off in a big way and it's estimated that by 2018, half of the applications running in public cloud environments will be considered mission-critical by the organizations that use them. But migrating legacy applications to the cloud can lead to new security risks as how the application is used and hosted could differ from the original deployment. We spoke to Drew Kilbourne, Managing Director at application security specialist Cigital to find out more about the risks and how to manage them. BN: What are the risks of taking legacy applications into a… [Continue Reading] -

New cloud services aim to increase adoption of Skype for Business
Publié: septembre 27, 2016, 4:33pm CEST par Ian Barker
Cloud-based unified communications are an attractive option for businesses, but a lack of effective management and monitoring tools is holding back many from deploying the technology. Managed cloud services company Unify Square is addressing this with the launch of an extended lineup of Skype for Business (SfB) cloud and hybrid services to help enterprises transition from on premise, to hybrid or full cloud deployments. The new release takes the company's existing PowerAssurance hybrid managed services system and adds some additional services. These include a Site Transformation Accelerator, a subscription-based service that handles site-by-site deployments of Modern Voice for SfB, supporting… [Continue Reading] -

CipherLoc aims to fix 'broken' encryption
Publié: septembre 27, 2016, 3:17pm CEST par Ian Barker
Companies are turning to encryption in order to protect their sensitive data, but many of the systems used can be cumbersome and don't necessarily offer total protection. CipherLoc Corporation is launching a suite of data security solutions that eliminate the flaws and inadequacies in today’s encryption algorithms, adding an extra layer of protection to existing products, services, and applications. "Modern day encryption algorithms are broken," says Mike Salas, VP of sales and marketing at CipherLoc. "Conventional wisdom states that well-known encryption algorithms -- such as AES -- are safe due to the fact that it would take thousands of years… [Continue Reading] -

Updated DRM platform helps protect sensitive enterprise data
Publié: septembre 27, 2016, 2:37pm CEST par Ian Barker
Leakage of data, whether due to the action of hackers or simple error by insiders is a major problem for enterprises. File security specialist FinalCode is launching a new version of its DRM platform to help businesses secure data both inside and outside the organization. FinalCode 5.11 provides strong encryption, entitlement settings and traceability controls with the ability to remotely delete files even after they have been shared. Users can define file permission settings and respective recipients themselves, or have controls applied automatically using corporate templates. Once protected, these files can be securely stored and shared, as they can only… [Continue Reading] -

Microsoft takes security to the Edge with Windows Defender Application Guard
Publié: septembre 26, 2016, 6:10pm CEST par Ian Barker
With many cyber attacks now initiated through the browser, endpoint security is something all businesses need to take seriously. Among today's announcements at Ignite, Microsoft trailed security enhancements across a range of its products, including the Edge browser. Windows Defender Application Guard will be available to Windows 10 Enterprise users from next year and aims to make Edge the most secure business browser. With Windows Defender Application Guard mode enabled, the Edge browser will protect enterprises from advanced attacks that can infiltrate networks and devices via the Internet, creating a safer, worry-free browsing experience for customers. It's powered by virtualization-based… [Continue Reading] -

Failed projects prompt companies to move to cloud analytics
Publié: septembre 26, 2016, 3:18pm CEST par Ian Barker
While there is huge interest in data analytics among the business community many organizations are struggling with failed projects according to a new study which reveals 88 percent of respondents have suffered failures with recent initiatives. Reasons for the failure of analytics projects include low end-user adoption, projects going over budget, systems not providing the analytics users were expecting, and too many initiatives evolving into 'zombie' projects that were almost completed but not ready for end-users. Cloud data warehousing company Snowflake Computing commissioned the survey from Dimensional Research, the results show that more than half of data professionals believe their… [Continue Reading] -

Benchmark report reveals effectiveness of marketing emails
Publié: septembre 23, 2016, 4:41pm CEST par Ian Barker
Email is still among the most popular ways of delivering marketing messages to customers, but it can be hard to measure how well it works. A new study from delivery platform SendGrid measures the engagement numbers for the average percentage of male and female recipients, the percentage of emails that are opened on mobile and non-mobile devices, open rates, click rate, click-to-open rates and monthly send rates across 10 industries. The report combines engagement statistics across all senders, establishing the benchmarks for the average monthly send rate of 9.8 emails with a unique open rate of 14.2 percent, open rate… [Continue Reading] -

More than half of IT pros don't erase data properly
Publié: septembre 22, 2016, 5:39pm CEST par Ian Barker
A new study reveals that 53 percent of IT professionals use common, but ineffective, methods to erase data on corporate computers, external drives and servers. The survey by Blancco Technology Group of over 400 professionals worldwide found that 31 percent report dragging individual files to the Recycle Bin and 22 percent reformat the entire drive. "Over the last several years, we’ve worked with businesses in the finance, healthcare and government sectors to help them understand the need to permanently and verifiably erase data from IT equipment and devices," says Richard Stiennon, a former Gartner analyst and now chief strategy officer… [Continue Reading] -

Marketers lose $100 million to mobile app advertising fraud
Publié: septembre 22, 2016, 4:27pm CEST par Ian Barker
App marketers will lose up to $100 million in 2016 due to mobile app install and engagement advertising fraud according to a new study. The research from mobile analytics company AppsFlyer shows that the losses come from fraudulent click data, paid installs from fraudulent devices, and fraudulent and simulated in-app events. While the study found the US to be the region most targeted by fraudsters, the countries with the highest rates of app install and engagement ad fraud -- when taking account mobile population -- are, Germany, Australia, China, Canada and the UK, followed by the US, Russia and France.… [Continue Reading] -

Enterprises are learning from cyber attacks but bad habits persist
Publié: septembre 22, 2016, 1:10pm CEST par Ian Barker
A majority of enterprises (79 percent) say they have taken action to improve their security in response to major cyber attacks. However, 40 percent of organizations still store privileged and admin passwords in a Word document or spreadsheet, while 28 percent use a shared server or USB stick. This is among the findings of the 10th annual Global Advanced Threat Landscape Survey from cyber security company CyberArk which looks at whether organizations are learning lessons from cyber attacks. The results also raise concerns about overconfidence. Three out of four IT decision makers now believe they can prevent attackers from breaking… [Continue Reading] -

Data lake management solution helps stop companies drowning in big data
Publié: septembre 21, 2016, 5:04pm CEST par Ian Barker
While businesses are keen to get the benefits of big data, analysts find it hard to harness information across the enterprise and find relationships between data sets. This can result in labor-intensive manual processes and a pool of unmanageable data that soaks up more and more resources in the quest for something useful. Data management solutions company Informatica is offering businesses a comprehensive, self-service approach that gives businesses cloud ready data lakes out-of-the-box. Informatica's Data Lake Management solution enables data analysts to easily find, prepare, govern and protect data of any size and velocity to more efficiently and confidently drive… [Continue Reading] -

Adaptiva launches serverless software distribution from the Azure cloud
Publié: septembre 21, 2016, 4:00pm CEST par Ian Barker
Deploying software and updates to computers across a global enterprise from the cloud can be slow and expensive using traditional methods. Systems management specialist Adaptiva is launching OneSite 6.0, a serverless option for distributing software from the cloud using Microsoft System Center Configuration (ConfigMgr) and Microsoft Azure. OneSite 6.0 eliminates barriers to cloud adoption by allowing content to be downloaded only once from the cloud. It then shares the content locally using peer-to-peer technology to efficiently minimize network bandwidth usage. "Enterprises clearly want to move their systems management activities to the cloud, but are concerned about the demands and costs… [Continue Reading] -

Malware attacks are declining but getting cleverer
Publié: septembre 21, 2016, 3:09pm CEST par Ian Barker
In the first six months of 2016 users were twenty percent less likely to encounter malware than in the same period last year. But although attacks are decreasing they’re getting more sophisticated and often disappear within hours having achieved their aims. These are the key findings of the latest Webroot Quarterly Threat Report, based on information collected from millions of endpoints, released today. "The report data demonstrates that, while malware encounters may be on a downturn, the business of cybercrime is indeed alive and well," says Tyler Moffitt, senior threat research analyst at Webroot. "As attack timelines accelerate and polymorphism… [Continue Reading] -

Education and government suffer most from ransomware
Publié: septembre 21, 2016, 12:38pm CEST par Ian Barker
The highest rates of ransomware are now found in the education and government sectors according to the findings of a new report from BitSight. The report looks at how ransomware is impacting almost 20,000 companies in six major industries: finance, retail, healthcare, energy/utilities, government and education. The findings show that the rate of new ransomware strains, such as Locky and Cryptowall, has spiked over the last couple of years, and numerous industries are beginning to fall victim to these ransomware attacks. The report reveals that educational institutions have over three times the rate of ransomware found in healthcare and more… [Continue Reading] -

Information Security Forum helps businesses guard their 'crown jewels'
Publié: septembre 20, 2016, 5:28pm CEST par Ian Barker
Traditional approaches to deploying security controls don't always provide appropriate or sufficient protection for mission-critical information assets. Aiming to support enterprises in guarding this information, the Information Security Forum (ISF) is launching 'Protecting the Crown Jewels', a series of reports based on the ISF Protection Process, to help organizations formulate a structured, methodical process to deliver comprehensive, balanced protection. The ISF Protection Process helps organizations identify mission-critical information assets, based on value and risk to the organization and the potential business impact if compromised. It also assists in assessing the threats to these assets, such as a competitor stealing trade… [Continue Reading] -

US businesses overspend by $2.6 billion a year on BYOD
Publié: septembre 20, 2016, 5:01pm CEST par Ian Barker
Enterprises in the US are overspending by an average of almost $287 per employee each year, due to compliance concerns, confusion in the executive suite over BYOD policy ownership, and lack of visibility into employee mobile usage. This adds up to a total overspend of $2.6 billion across the country. These are among the findings of a new survey by mobile platform provider Syntonic and Information Solutions Group on BYOD use in the enterprise. Almost 60 percent of respondents say they have a formal BYOD policy, and of those, 69 percent are actively reimbursing employees for work-related usage of their… [Continue Reading] -

New launch offers data loss prevention for American SMBs
Publié: septembre 20, 2016, 4:42pm CEST par Ian Barker
The potential for data loss is there for all businesses, but smaller organizations often don’t have the resources to guard against it as effectively as larger ones. Safetica, an established European data loss prevention company, is launching in North America and aiming its software at small and medium businesses. It's easy to use, helps businesses of all sizes comply with regulations, and Safetica provides support before and after deployment at no charge. Using a contextual approach, Safetica protects files based on how they're used. It can spot risky employee behaviors and prevent sensitive data from being accidentally or deliberately shared.… [Continue Reading] -

Duo launches single sign on for easy, secure cloud access
Publié: septembre 20, 2016, 3:38pm CEST par Ian Barker
Businesses are increasingly recognizing that passwords are no longer an adequate way of protecting systems. But users still need a means of access that is easy to use, secure and doesn't get in the way. Cloud-based access provider Duo Security is today announcing that it's combined its flagship two-factor authentication and device insight with single sign-on (SSO) capabilities to create a trusted access platform. This allows organizations to verify that users are who they say they are, that their devices are secure enough to access business applications and networks, and check where they're logging in from -- all with one single… [Continue Reading] -

Secure messaging environment delivers safe online collaboration
Publié: septembre 20, 2016, 3:11pm CEST par Ian Barker
With workforces being increasingly mobile and decentralized, they need effective tools to aid collaboration. Whilst email is commonly used it lacks the rich feature set and security features of dedicated applications. A newcomer to the collaboration market, real time messaging company Riot is today publicly launching its secure messaging environment that aims to bring all your online collaboration into one workspace. Riot enables teams to easily share data and collaborate on projects across different communication apps and third party tools. By using Matrix-powered bridging to external networks such as Slack, IRC, Twitter and Gitter, Riot frees users from closed silos… [Continue Reading] -

Kentik launches network performance monitoring for the cloud era
Publié: septembre 20, 2016, 2:02pm CEST par Ian Barker
Migrating systems to the cloud leads to a shift in network traffic patterns that can present a performance challenge for businesses. Network analytics company Kentik is launching its new Network Performance Monitoring (NPM) aimed at meeting the needs of modern, digital businesses. It builds on Kentik Detect, a big data-based, SaaS network analytics platform and also includes the nProbe host-based and sensor monitoring agent software from ntop. This can be deployed into hybrid data center and cloud environments, and monitors network performance factors such as latency, retransmits, out of order packets, and packet fragments based on actual application traffic flows,… [Continue Reading] -

Altify brings augmented intelligence to B2B sales
Publié: septembre 19, 2016, 3:41pm CEST par Ian Barker
The internet means that buyers are armed with more information than ever before which can make life more challenging for salespeople. Sales transformation company Altify is looking to give sales teams the edge with the launch of its latest enterprise B2B sales platform with augmented intelligence capabilities that prompt sales professionals of the next best action to progress a sale. Altify Max uses some traditional AI techniques, but extends their benefits by amplifying the sales knowledge in the system first. This lets salespeople apply their experience and expertise, augmented by the best practices and machine algorithms in the software. Max… [Continue Reading] -

Windows Safe Mode attack could put your passwords at risk
Publié: septembre 19, 2016, 11:45am CEST par Ian Barker
Because it allows only the essential elements of the Windows operating system to run, Safe Mode is a useful tool for diagnosing and fixing problems. But according to researchers at CyberArk Labs it could also be exposing you to risk. Safe Mode stops a lot of third-party software from running at startup and that can include many security solutions. Attackers who have gained remote access to a machine may therefore be able to reboot it into Safe Mode to launch attacks. "Sure, the attacker can arbitrarily force a restart, but this will likely look suspicious to the user and prompt… [Continue Reading] -

Students need better data security education
Publié: septembre 15, 2016, 5:38pm CEST par Ian Barker
As students head back to university, a survey by Intel Security reveals that, in the UK at least, half of them are failing to protect their phones, tablets and laptops from online threats. The survey of more than 1,000 UK-based students carried out in conjunction with The National Student finds that despite a quarter of teenagers reporting that they are 'almost constantly' online, only 50 percent of students ensure they have the necessary security software installed to keep their devices and data safe. In addition more than 90 percent log on to public Wi-Fi on their campuses and in bars… [Continue Reading] -

Millennials prefer to deal with companies by text
Publié: septembre 15, 2016, 5:04pm CEST par Ian Barker
Of all the communication channels available for dealing with businesses, 60 percent of millennials prefer two-way text engagement, because it’s convenient, fast, and easy to use. This is one of the findings of a new survey by mobile engagement specialist OpenMarket of 500 US millennials (18 to 34-year-olds) on their use of SMS communications. While 72 percent of millennials say they text 10 or more times a day, and 31 percent more than 50 times a day, the leading factor in millennials' preferences for texting is its ability for two-way communication with businesses. The results make interesting reading for businesses… [Continue Reading] -

How cyber security professionals see insider threats
Publié: septembre 15, 2016, 3:29pm CEST par Ian Barker
Whilst the popular view of hackers tends to be of outsiders, there's been increasing emphasis in recent years on the threat to enterprise data posed by those inside the organization. Behavior analytics company RedOwl carried out a survey at last month's Black Hat conference, asking almost 300 security professionals for their views on insider threats, and the results are released today. Among the findings are that almost half of respondents (47 percent) say their organization has experienced an insider incident within the past year. Nearly half also say that their C-level executives and board of directors are now concerned with… [Continue Reading] -

CloudBees brings enterprise-strength reliability to Jenkins
Publié: septembre 14, 2016, 6:33pm CEST par Ian Barker
The Jenkins open-source automation server is popular with businesses, and is easily extended by community contributions. But these contributions don't always receive the rigorous testing that enterprises require. Until now that is, Jenkins specialist CloudBees is launching CloudBees Jenkins Enterprise, a verified Jenkins distribution aimed directly at enterprise users. Announced at this week's Jenkins World conference in Santa Clara, the distribution has undergone a new comprehensive testing and verification process called the CloudBees Assurance Program. This ensures a stable and certified distribution of Jenkins, along with curated extensions from the community and third parties, all of which are now certified… [Continue Reading] -

Ping Identity partners with Microsoft to deliver secure application access
Publié: septembre 14, 2016, 5:38pm CEST par Ian Barker
Many large enterprises use Azure Active Directory (Azure AD) as their identity platform for managing users and providing secure access to thousands of cloud SaaS and on-premises applications. Secure access company Ping Identity is announcing a collaboration with Microsoft to deliver integrations that will expand secure remote access and single sign-on (SSO) from any device to more on-premises web applications for Microsoft Azure AD customers. Azure AD handles over a billion authentications daily to more than nine million directories. However, connecting the full set of legacy and custom on-premises apps to these environments can be challenging. This integration with Ping… [Continue Reading] -

GCHQ plans Great British Firewall to protect web users
Publié: septembre 14, 2016, 4:44pm CEST par Ian Barker
The UK's cyber intelligence agency GCHQ is planning what has been labelled a 'Great British Firewall' to protect individuals and companies against cyber attacks. The idea emerged in a speech delivered by the head of GCHQ's national cybersecurity centre, Ciaran Martin, at the Billington Cyber Security Summit in Washington DC. "The great majority of cyber attacks are not terribly sophisticated. They can be defended against. And even if they get through their impact can be contained. But far too many of these basic attacks are getting through. And they are doing far too much damage," says Martin. "They're damaging our… [Continue Reading] -

American Express customers phished using phishing prevention scam
Publié: septembre 14, 2016, 3:08pm CEST par Ian Barker
In a rather ironic twist on traditional phishing attacks, customers of American Express are being targeted by a campaign promising them an identity theft and phishing prevention tool. The phishing emails offer SafeKey use as bait. This is a legitimate program that Amex offers its customers as an additional layer of security to guard against ID theft and phishing. The scam uncovered by Comodo Labs plays on deep-seated identity theft concerns to actually perpetrate large scale identity theft. The hackers have taken a great deal of care in the design of the messages employed to make them look, feel and… [Continue Reading] -

One in five companies fail to test for security vulnerabilities
Publié: septembre 14, 2016, 12:25pm CEST par Ian Barker
Many businesses don't carry out frequent security testing despite believing that it's critically important to securing their systems and data, according to a new survey. The study from managed security services company Trustwave and Osterman Research finds that one in five businesses surveyed don't do any security testing, despite the fact that 95 percent of respondents reported encountering common security issues associated with security vulnerabilities. Among other findings are that when organizations do conduct testing, most do it using a combination of in-house resources and third-party testing services, although two in five organizations manage security testing only in-house. Among the… [Continue Reading] -

New partnership aims to improve threat detection
Publié: septembre 13, 2016, 4:12pm CEST par Ian Barker
The problem with many security solutions is that the number of alerts they generate leads to a good deal of time in investigations, some of which will turn out to be false positives. Real-time analytics company Corvil is partnering with endpoint security specialist Carbon Black to offer customers unified cyber threat detection, analysis, and response. The combined solution provides visibility and context, allowing security teams to seamlessly track and correlate activity across their networks and endpoints. This enhanced visibility helps security teams accelerate detection times and streamline forensic investigations. This means faster response to both internal and external attacks, as… [Continue Reading] -

New solution prevents loss and corruption in big data environments
Publié: septembre 13, 2016, 3:29pm CEST par Ian Barker
The pressure to move towards using big data can often lead to management practices lagging behind. While storage is managed often data flows aren't, which leads to breakdowns and corruption of the data. The bigger and more complex the data, the greater the problem becomes. To address this, San Francisco-based StreamSets is launching its Dataflow Performance Manager (DPM), a solution that makes it possible to manage the operations of a company's end-to-end dataflows within a single pane. StreamSets DPM unifies visibility and control of dataflows, which reduces management costs, improves data quality and enables IT agility. Customers can map dataflows… [Continue Reading] -

New software applies machine learning to contract reviews
Publié: septembre 13, 2016, 1:13pm CEST par Ian Barker
When contracts need to be reviewed, renewed or revised, the process tends to be labor intensive and time consuming. Contract delivery and analytics specialist Seal Software is launching version 5.0 of its contract analysis software, which uses machine learning to speed up the process. It also includes a new add-in which allows contract data extraction and review capabilities to be used within Microsoft Word. Analyze This Now (ATN) pulls existing contracts directly into Word, converting all documents -- including PDF and TIFF images -- into MS Word format. From there, business users can review text, update terms, change metrics, and create… [Continue Reading] -

Niche software vulnerabilities leave enterprises open to attack
Publié: septembre 9, 2016, 4:15pm CEST par Ian Barker
News of software vulnerabilities often centers on products from well-known companies that potentially put large numbers of end users at risk. But a new report from software solutions company Flexera Software reveals that the niche products used by specialist industries can be just as much of a problem. It reveals that the product with the highest number of vulnerability issues between May and July this year was Philips Xper Connect, a hospital information system, which had 272 vulnerabilities. This underscores the need to extend software vulnerability management diligence across all software assets found on corporate or personal systems -- not… [Continue Reading] -

New cloud suite aims to eliminate passwords
Publié: septembre 8, 2016, 5:19pm CEST par Ian Barker
Passwords are old technology and were never really designed to protect public access to sensitive information like bank and healthcare details. Yet despite the introduction of new technologies like two-factor authentication, biometric recognition and others, the password continues to cling on. Identity and authentication platform Trusona wants to hasten the death of the password with the introduction of its Cloud Identity Suite, offering three tiers of identity-proofing and authentication, and making the basic level available for free. "A technology invented more than fifty years ago is not built to handle the modern cyber attack landscape. Trusona is proud to lead… [Continue Reading] -

More than half of malware infected files in cloud apps are shared with others
Publié: septembre 8, 2016, 4:36pm CEST par Ian Barker
The latest report on enterprise cloud usage and trends from cloud security specialist Netskope reveals that 55.9 percent of malware-infected files found in cloud apps are shared publicly. It also finds that ransomware is now one of the most common threats, with 43.7 percent of malware infections found in enterprise cloud apps having delivered ransomware. These include Javascript exploits and droppers, Microsoft Office macros and PDF exploits. Whilst attacks are often initially delivered through phishing and email, within cloud environments, infected and encrypted files can quickly spread to other users through cloud app sync and share functionality in what is… [Continue Reading] -

New solution helps identify security blind spots
Publié: septembre 8, 2016, 3:54pm CEST par Ian Barker
One of the biggest problems companies have in keeping their system secure is a lack of integration and coordination between security and operations. This can lead to security blind spots and processes that are isolated from protection solutions. IT solutions provider BMC is announcing extensions to its BladeLogic Threat Director product that allow for the rapid identification of unsecured assets, and provide visibility into application dependencies. This means operations teams will be better able to anticipate the impact of actions on end users. "There is a real disconnect in enterprise security between the identification of issues and taking action. Most… [Continue Reading] -

Pilot-as-a-Service platform connects enterprises to software vendors
Publié: septembre 8, 2016, 3:04pm CEST par Ian Barker
While companies are often keen to have their own custom built applications, the process of coming up with a proof of concept and selecting a developer can be complex and time consuming. Israel-based prooV wants to make the process easier with the world's first Pilot-as-a-Service platform that seamlessly connects enterprises to independent software vendors. It offers a user-friendly platform which enables enterprises and ISVs to easily discover, and be discovered by, potential customers, suppliers, and partners, and then seamlessly execute on proof of concept (PoC) opportunities. PoC pilots run on prooV's dedicated cloud-based testing environments that emulate the enterprise’s internal… [Continue Reading] -

Limelight launches web application firewall
Publié: septembre 7, 2016, 3:48pm CEST par Ian Barker
Increased reliance on the Internet means businesses face a number of different security threats aimed at bringing down websites, impacting performance or stealing information. Many of these attacks are aimed at the application layer. Content delivery specialist Limelight Networks is adding to its Cloud Security services with the launch of a new Web Application Firewall (WAF). This is a new cloud-based security service that detects and stops application attacks in real-time, protecting websites and web applications from both common threats and specialized attacks. The Limelight WAF service eliminates HTTP application threats by identifying and blocking common attacks such as Cross-Site… [Continue Reading] -

New alliance of security companies aims for a holistic approach to data breaches
Publié: septembre 7, 2016, 3:15pm CEST par Ian Barker
One of the biggest problems organizations have in staying secure is a lack of visibility across the whole enterprise, giving hackers the opportunity to exploit gaps between security solutions. Access control specialist SecureAuth is taking the lead in the creation of a Connected Security Alliance with the aim of building a reference architecture that will help organizations address every stage of the attack lifecycle from initial penetration, to lateral movement, to escalating privileges. The alliance will initially be composed of SecureAuth and cybersecurity solution providers CyberArk, SailPoint and Exabeam. It's designed to better protect organizations and reduce the time it… [Continue Reading] -

What enterprise workloads are right for the cloud? [Q&A]
Publié: septembre 7, 2016, 11:33am CEST par Ian Barker
The question many businesses are asking themselves is, 'should we be moving to the cloud?' The public cloud is clearly a success, as shown by the significant adoption of Amazon Web Services (AWS). Companies are benefiting from the pay-as-go nature of the cloud, as well as from the ability to turn up services as needed without the traditional hardware spend. Gartner recently reported that cloud computing will affect more than $1 trillion in IT spending by 2020. But even with this growing popularity, corporate IT departments are still struggling with how to integrate public clouds into their data center initiatives. One of… [Continue Reading] -

Icertis partners with Box to offer smoother enterprise contract management
Publié: septembre 6, 2016, 3:26pm CEST par Ian Barker
Contracts are among the most sensitive documents that many enterprises handle. When storing them in the cloud therefore firms need to be sure that they’re secure and properly managed. Contract lifecycle specialist Icertis is partnering with cloud storage supplier Box to integrate with the latter's enterprise content management platform, empowering users to collaborate with internal stakeholders and seamlessly share documents and contract drafts during negotiation. "Working with Icertis enables seamless enterprise contract management workflows,” says Roger Murff, vice president of Business Development and Technology Partnerships at Box. "We are happy to have Icertis in our ecosystem of partners to provide our… [Continue Reading] -

Automatic lovers -- conference explores the sex lives of robots
Publié: septembre 5, 2016, 11:33am CEST par Ian Barker
Robots and technology are invading more and more areas of our lives, but there are some places they have yet to... ahem, penetrate. A conference in Salford, UK this week organized by the TC9 group of the International Federation for Information Processing (IFIP) is set to explore issues of technology and intimacy. This is an area which divides experts. David Levy's 2008 book, 'Love and Sex with Robots' suggests that humans will fall in love with and even marry social robots in the not too distant future. However, robotics ethicist, Kathleen Richardson, is campaigning to ban sex robots because she… [Continue Reading] -

Kaspersky launches cloud security for smaller businesses
Publié: septembre 2, 2016, 3:29pm CEST par Ian Barker
Although there are many different security solutions on the market, smaller businesses often struggle to find a solution that's affordable and easy to implement. Kaspersky Lab is targeting this SMB market with its new Endpoint Security Cloud. It's a software-as-a-service solution offers advanced functionality and proven protection but can be managed easily via simple cloud-based console with an intuitive and user-friendly interface. The solution can protect Windows workstations, file servers, Android and iOS mobile devices, all through the same console. Based on advanced, multi-layered security technologies, Kaspersky Endpoint Security Cloud uses industry leading protection features, including Kaspersky Security Network and System… [Continue Reading] -

End users struggle to identify security threats and put enterprises at risk
Publié: septembre 2, 2016, 11:24am CEST par Ian Barker
There's a reason why cyber attacks use social engineering techniques, it's because the person sitting in front of the screen is usually the weakest link in the security chain. This is confirmed by the findings of a new report from Wombat Security Technologies which shows that in the last year, the number of organizations that reported being a victim of phishing has increased 13 percent, and 60 percent of enterprises say the rate of phishing attacks has increased overall. The report used responses to questions to find how well end users are able to identify and manage security threats within… [Continue Reading] -

Forty percent of enterprise networks show evidence of DNS tunneling
Publié: août 31, 2016, 3:32pm CEST par Ian Barker
DNS tunneling is a significant security threat that can enable cybercriminals to insert malware or pass stolen information into DNS queries, creating a covert communication channel that bypasses most firewalls. A new report released by network control company Infoblox reveals that 40 percent of the enterprise files it tested in the second quarter of this year show evidence of DNS tunneling. "In the physical world, burglars will go to the back door when you've reinforced and locked the front door. When you then secure the back door, they'll climb in through a window," says Rod Rasmussen, vice president of cybersecurity… [Continue Reading] -

New service allows secure connection to APIs
Publié: août 30, 2016, 6:21pm CEST par Ian Barker
The rate of change required for business software has increased dramatically in recent years. In order to keep up many firms rely on APIs but these introduce their own problems, especially in regard to security. Identity and device management company Okta is launching a new service that secures the connections between applications, services and APIs. Okta API Access Management is based on the user, making it easy to centrally maintain one identity and one set of permissions for any employee, customer, or partner across every point of access, regardless of location or device type. "As global enterprises undertake reinvention, they… [Continue Reading] -

Application-defined WAN improves remote cloud working
Publié: août 30, 2016, 3:07pm CEST par Ian Barker
Moving applications to the cloud and distributing work to remote offices places new strains on networks. According to Microsoft's guidelines for Office 365 adoption, enterprises should plan for up to four times increase in WAN bandwidth, and enable direct-to-cloud access from the remote office to avoid sub-optimal performance. Software-defined WAN pioneer CloudGenix is addressing this problem with the launch of its Instant On (ION) 3000v application-defined fabric, an SD-WAN platform for virtualizing remote offices. ION 3000v allows enterprises to deploy applications anywhere based on app-SLAs, enforcing security, performance and compliance requirements. This approach establishes a new defense-in-depth security model for… [Continue Reading] -

New platform seeks to automate risk management
Publié: août 29, 2016, 3:07pm CEST par Ian Barker
Identifying and prioritizing cyber threats is a problem for large organizations and it's easy to become overwhelmed with information. This is why, increasingly, they're turning to solutions to automate the process. Risk analysis specialist Bay Dynamics is launching a new version of its analytics platform, Risk Fabric, that helps companies measure, communicate and reduce cyber risk. It automatically delivers prioritized threat and vulnerability information, based on the value of assets at risk, to the business leaders who are responsible for those assets. "Risk Fabric has proven to be the leading platform in helping large, Fortune 500 companies prioritize and combat… [Continue Reading] -

GoDaddy users hit by clever phishing scam
Publié: août 26, 2016, 3:21pm CEST par Ian Barker
Phishing attacks continue to get cleverer as the people behind them refine their social engineering techniques. The latest attack uncovered by Comodo Labs targets users of the popular GoDaddy web hosting service. The scam sends out email from what appears to be support@godaddy.com. Within the body of the phishing email, the user is notified that their email account storage has been maxed out and that incoming emails are being rejected. Having sparked a momentary panic it then tells the recipient they must upgrade within 24 hrs or their account will be suspended. To fix it, all they have to do… [Continue Reading] -

Responding to the changing threat landscape facing enterprises [Q&A]
Publié: août 26, 2016, 12:01pm CEST par Ian Barker
Not so many years ago corporate IT security involved installing a firewall and antivirus solution. But the threat landscape has now become much more complicated and is changing faster than ever. Companies need to be aware of these changes and make sure their security arrangements can keep up. We spoke to Shai Gabay, the chief innovation officer of security operations and advanced threat detection specialist CYBERBIT, to find out more about the risks and solutions. BN: What is changing in the way bad actors are targeting IT organizations? SG: Five years ago, an attacker could write a virus from a… [Continue Reading] -

One in four breaches in the financial sector are from lost or stolen devices
Publié: août 25, 2016, 4:20pm CEST par Ian Barker
New research from data protection company Bitglass into breaches in the financial services industry reveals that leaks nearly doubled between 2014 and 2015, and that lost and stolen devices are the most common cause. While hacking remains a major fear, only one in five leaks were caused by it. Other breaches were the result of unintended disclosures (14 percent), malicious insiders (13 percent), and lost paper records (8.1 percent). In 2015, 87 breaches were reported in the financial services sector, up from 45 in 2014. In the first half of 2016, 37 US banks have already disclosed breaches. In addition… [Continue Reading] -

Cloud platform lets marketers deliver personalized Google Ads
Publié: août 25, 2016, 3:17pm CEST par Ian Barker
Google Ads has proved itself an effective tool for gaining new business, but it's a rather less useful way of targeting existing customers. Now though, marketing cloud specialist Optimove is launching a new integration with Google Ads. This allows businesses to target existing customers with personalized ads on google.com and across the Google Display Network, based on recent and predicted behavior patterns. "Google Ads is known as a great user acquisition channel, but there has not been a scalable and effective way to use it to target existing customers based on their personal preferences and activity patterns -- until now," says… [Continue Reading] -

iOS device failures overtake Android for the first time
Publié: août 25, 2016, 1:43pm CEST par Ian Barker
In the ongoing smartphone performance and reliability battle, Apple has lost its leading position to Android for the first time in the second quarter of 2016. Plagued by crashing apps, WiFi connectivity and other performance issues, the iOS failure rate more than doubled to 58 percent, compared to a 25 percent failure rate in the previous quarter, according to the research by mobile device diagnostics company Blancco Technology Group. Of the iOS devices that failed, the iPhone 6 had the highest failure rate (29 percent), followed by iPhone 6S (23 percent) and iPhone 6S Plus (14 percent). The main issues encountered included… [Continue Reading] -

How the Industrial Internet of Things is set to change the world
Publié: août 25, 2016, 12:33pm CEST par Ian Barker
We're all aware of the Internet of Things and its likely effect on our homes, but there's another side to it which is its impact on industry. Electronics supplier RS Components has put together an interactive graphic looking at how the Industrial IoT is going to change everyday functions from streetlighting to agriculture. Smart street lighting for example could cut energy costs by around 35 percent by automatically dimming when no activity is detected. Smart logistics could ensure that perishable items and medicines are delivered in peak condition. It's estimated that this could save European businesses up to 300 billion… [Continue Reading] -

Hate the software you have to use at work? You are not alone
Publié: août 24, 2016, 6:24pm CEST par Ian Barker
Are you frustrated with clunky workplace systems? Do you wish that you could work with a more modern streamlined solution? You're in good company, a new study by app platform specialist Sapho in conjunction with research firm Forrester reveals that 91 percent of employees agree simplified enterprise apps would increase their efficiency and productivity. In addition 75 percent of employees say they have a hard time accessing information in their enterprise systems and applications. Other concerns surround the number of systems in use. In just two years the number of applications that employees use has grown by 25 pecent. To make… [Continue Reading] -

Most US IT practitioners earn $100k annual salaries
Publié: août 24, 2016, 5:13pm CEST par Ian Barker
Automated software delivery specialist Puppet has released the result of its latest DevOps Salary Report which shows that most IT practitioners in the US earn a $100,000 annual salary. It also finds that 43 percent of IT managers earn $150,000 or more, up from 26 percent last year. The report is based on data gathered from more than 4,600 respondents to the survey. Respondents were asked to report on the number of servers and employees in their organization. The results reveal that organizations with more than 10,000 servers pay the highest percentage of salaries that are $150,000 a year or… [Continue Reading] -

Cloud-based identity service streamlines SaaS adoption
Publié: août 24, 2016, 4:03pm CEST par Ian Barker
SaaS application adoption is growing fast and with it comes increasing expectations to be able to access any application from anywhere on any device. Consequently organizations want login solutions that can help them reduce risks in their environment, deliver a better experience for their end-users, and adapt to the complexities of existing infrastructure and new applications. Access control specialist SecureAuth is launching a new release of its Cloud Access product, delivering adaptive and multi-factor authentication, single sign-on (SSO), and automated account management for thousands of applications. SecureAuth Cloud Access has SSO support for over 8,000 apps and sites, so organizations… [Continue Reading] -

Report shows wide variation in privileged access management practices
Publié: août 24, 2016, 3:05pm CEST par Ian Barker
As we reported yesterday, privileged users can represent a significant risk to enterprise security. A new report from cyber security company BeyondTrust underlines this with findings that show organizations adhering to best practices for privileged access management are much better at mitigating the risks of a data breach. The survey of more than 500 IT, IS, legal and compliance experts split its overall scores into top- and bottom-tier groups and finds that top-tier companies were much more likely to have a centralized password management policy -- 92 percent in contrast with just 25 percent of bottom-tier organizations. Regular password changes are… [Continue Reading] -

New tool helps cut Agile software project delays
Publié: août 23, 2016, 4:39pm CEST par Ian Barker
Delays to software projects are frequently blamed on missed or misunderstood requirements. As companies look to ensure the successful delivery of Agile IT projects, they need tools that help ensure business needs are met. Toronto-based Blueprint Software is launching a new Storyteller add-on for the JIRA bug tracking tool, that allows developers to automatically generate user stories, acceptance criteria and tests, ensuring that user requirements are properly addressed. Ruth Zive, vice president of marketing at Blueprint Software, says, "Transitioning from Waterfall to Agile can cause many issues for organizations. A critical issue here is that business stakeholders and analysts don't… [Continue Reading] -

The hidden security risk of privileged users
Publié: août 23, 2016, 3:39pm CEST par Ian Barker
All businesses are aware of the danger posed by insider threats, but those threats are multiplied when they involve privileged user accounts. Damage caused by privileged users is the most extensive, the hardest to mitigate and the hardest to detect as it involves authorized users doing things they are authorized to do. A new report from access management specialist Forcepoint in conjunction with the Ponemon Institute looks at the gap between organizations' awareness of the problem and their ability to solve it. The study conducted among more than 700 operations and IT security managers finds that 91 percent think that… [Continue Reading] -

New Huddle release improves security and control
Publié: août 23, 2016, 12:48pm CEST par Ian Barker
Business collaboration tools are increasingly essential in the enterprise, but they need to keep content secure, especially in professional services environments that handle sensitive client data. Collaboration specialist Huddle is tackling this with the launch of its Unified Authentication Portal. Using a single sign on, this lets account managers apply policies across Huddle's web, desktop and mobile apps in one step, simplifying the process of keeping content secure. "Security is a top concern for most enterprises; however this is especially true of professional services firms who are collaborating with internal and external stakeholders on a regular basis" says Stuart Cochran,… [Continue Reading] -

New tool helps developers streamline release management
Publié: août 22, 2016, 6:58pm CEST par Ian Barker
As the importance of software to almost all businesses has grown, so the competition to bring new releases to market and ensure they're error free is fierce. Open source code collaboration specialist GitLab is addressing this issue with a new tool that enables developer teams to improve the software release management process, providing real-time visibility of project issues across an organization. Called Issue Board it allows developers to visualize and manage issues from within GitLab, streamlining the release and deployment process, and eliminating the need to use an external tool. Free to all GitLab users, the Issue Board builds on… [Continue Reading] -

Hackers play the fame game to boost business
Publié: août 22, 2016, 12:19pm CEST par Ian Barker
Hacking by its very nature tends to be an activity that takes place in the shadows. However, analysts at security awareness specialist Digital Shadows have identified a growing trend of some hackers actively seeking the limelight to promote their businesses. Just as in the legitimate commercial world, reputation is important and players without one are less likely to be trusted. In order to boost their profiles therefore some cyber criminals have been using publicity to add to their credibility. "While cybercriminals engaging with journalists is not a new phenomenon, a recent trend has been observed of previously unknown actors using the… [Continue Reading] -

Traditional malware falls as mobile malware rises in July
Publié: août 19, 2016, 12:39pm CEST par Ian Barker
The number of active malware families attacking businesses fell by five percent in July, but mobile malware now accounts for nine percent of the total -- up 50 percent from June. These figures come from threat prevention company Check Point based on intelligence drawn from its ThreatCloud World Cyber Threat Map. During July, Check Point detected 2,300 unique and active malware families attacking business networks, the first time in four months it has seen a drop in the number of unique malware families. However, the total number seen still matches the second all-time highest number recorded in a calendar month… [Continue Reading] -

Besiter Eclipse: A nicely designed power bank [Review]
Publié: août 18, 2016, 3:18pm CEST par Ian Barker
As we become more and more reliant on our portable devices, running out of battery power at a crucial moment is always a risk. Fortunately there are plenty of USB power banks on the market to give your device a boost. The latest to come our way is the Besiter Eclipse from UK company Kavson. It claims to have one of the most powerful batteries available, making it able to charge an iPhone 6S up to 5 times and a Samsung Galaxy S7 up to 3 times over. Out of the box, first impressions are that it has a weighty,… [Continue Reading] -

New spear-phishing attacks seek out industrial and engineering targets
Publié: août 18, 2016, 12:14pm CEST par Ian Barker
Researchers at Kaspersky Lab have uncovered a new wave of targeted attacks against the industrial and engineering sectors in 30 countries around the world. Named 'Operation Ghoul' by Kaspersky's researchers, the attacks use spear-phishing emails and malware based on a commercial spyware kit to seek out valuable business-related data stored in their victims' networks. The campaign appears to have been organized by a cybercriminal group which has been tracked by researchers since March 2015. The latest attacks appear to be the most recent operation conducted by this group. The malware is delivered as an attachment and is based on the… [Continue Reading] -

Management underestimates the time and cost needed for the cloud
Publié: août 17, 2016, 4:00pm CEST par Ian Barker
While 96 percent of US enterprises expect to increase their investment in cloud management over the next five years, the majority of IT decision makers are not using those services to their fullest potential according to a new study. The survey findings from Wakefield Research and cloud automation specialist Logicworks show that 80 percent of the 400 surveyed IT decision makers believe that their company's leadership team underestimates the time and cost required to maintain resources in the cloud. In addition 50 percent report that they are only somewhat confident that their organization could immediately address an issue that led… [Continue Reading] -

Intelligent connectors help integrate enterprise data and applications
Publié: août 17, 2016, 3:15pm CEST par Ian Barker
Enterprise data can have multiple elements which makes it difficult to map to different systems and can prevent businesses from getting the most from their information. Data integration specialist SnapLogic is introducing a new release of its Elastic Integration Platform with new additions to its library of more than 400 intelligent connectors called Snaps. These include connections for Apache Hive, Teradata and Hadooplex, making for simpler integration of big data into enterprise systems. Building on SnapLogic's existing ease of use and self-service, the latest release introduces new automated data transformation capabilities that take an expression from a source system, evaluate… [Continue Reading] -

HMA! aims to bring VPN to the masses
Publié: août 17, 2016, 11:30am CEST par Ian Barker
Virtual private networks (VPNs) are an effective way of masking your internet activity when using public networks. However, they've always seemed a bit geeky, which puts many everyday internet users off using them. VPN specialist Hide My Ass! (HMA!) is aiming to change that with a new version of its product aimed at people who haven't previously used a VPN. HMA! Pro VPN v3 offers a streamlined, friendlier interface to make using a VPN as simple as possible. It's been developed to encourage those who have never used or considered using a VPN to control how and when they share personal… [Continue Reading] -

Ransomware-as-a-service tool generates $195,000 profit in July
Publié: août 16, 2016, 3:55pm CEST par Ian Barker
There are a number of high profile ransomware programs doing the rounds at the moment and we know that it can generate lucrative returns for the people behind it. But just as in the legitimate commercial world, the as-a-service model is starting to gain traction with attackers. Security vendor Check Point is releasing details of Cerber, which it believes is the world's biggest ransomware-as-a-service scheme. Cerber operates as a franchise, with its developer recruiting affiliates who then spread the malware further for a cut of the profits. In July 2016 alone, Cerber had over 160 active campaigns, targeting 150,000 users… [Continue Reading] -

Over 30 percent of employees put their companies at risk by responding to phishing attacks
Publié: août 16, 2016, 3:08pm CEST par Ian Barker
Phishing is one of the major security threats that enterprises now face, but according to new research from Duo Security users are putting 31 percent of organizations at risk of a data breach due to phishing attacks. Based on feedback from the Duo Insight phishing simulation tool, the company finds that 31 percent of users clicked the link in a phishing email and worse still 17 percent entered their username and password, giving an attacker in a real-world scenario the keys to corporate data. The goal of Duo Insight is to offer organizations of all sizes a free internal phishing drill… [Continue Reading] -

The increasing role of AI in cyber security [Q&A]
Publié: août 15, 2016, 11:01am CEST par Ian Barker
As attacks become more frequent and sophisticated, conventional security techniques and human analysis struggle to keep pace. As a result many companies are turning to artificial intelligence methods to help them defend their systems effectively. We spoke to Peter Gyongyosi product manager of security intelligence specialist Balabit to find out more about how AI is increasingly the future of cyber security. BN: Why is AI becoming more popular in the security space? PG: AI is able to create software that's capable of intelligent behavior. This intelligence can take many shapes, like suggesting to music to you to being able to… [Continue Reading] -

North American businesses reluctant to adopt Windows 10
Publié: août 12, 2016, 1:49pm CEST par Ian Barker
A year on from the release of Windows 10 most businesses are still reluctant to adopt the OS, according to research by solutions and managed services company Softchoice. Based on an evaluation of more than 400,000 Windows-based computing devices between January and May this year, across 169 organizations in the US and Canada using the TechCheck asset management solution, the study reveals less than one percent were running Windows 10. It finds the vast majority of North American businesses adopted Windows 7 as the corporate platform-of-choice since moving away from Windows XP, and have yet to move in significant quantities… [Continue Reading] -

Predictive risk technology helps fight phishing
Publié: août 11, 2016, 5:23pm CEST par Ian Barker
Phishing attacks are on the increase and are becoming increasingly sophisticated. This means that older technologies such as blacklisting known phishing sites are struggling to keep up with the threat. The Anti Phishing Working Group detected a 250 percent jump in phishing sites between October 2015 and March 2016. Fraud protection company Easy Solutions is helping to combat the problem with the public beta launch of its Swordphish predictive phishing and malware risk assessment technology. Swordphish is an API-based tool that helps organizations use the power of prediction to combat 'alert fatigue' and to detect phishing, malware and ransomware attacks in the… [Continue Reading] -

Over half of security pros say cloud vendors shouldn't give governments data access
Publié: août 11, 2016, 4:35pm CEST par Ian Barker
There are a number of concerns that companies have over migrating to the cloud, but one of the key ones is who else might have access to the data. Cloud security company Bitglass has released the results of its latest Mitigating Cloud Risks survey in conjunction with the Cloud Security Alliance, which shows that potential government access to encrypted data is an issue. According to the findings, 35 percent of IT security professionals believe cloud app vendors should be forced to provide government access to encrypted data while 55 percent are opposed. In the US there's more opposition with 64… [Continue Reading] -

SecureAuth launches training program to cut security skills gap
Publié: août 11, 2016, 4:06pm CEST par Ian Barker
Shortage of skills is one of the main reasons businesses give for not achieving their objectives according to Gartner and this is especially true in the cybersecurity field. Access control specialist SecureAuth is aiming to address this with the launch of its SecureAuth University, a continuing education program for customers, partners and employees. Through a combination of eLearning and instructor-led courses, SecureAuth University offers certification for cybersecurity professionals at three levels, administrator, advanced administrator and developer. This can deliver return on investment by delivering a greater understanding of current methods used in cyberattacks, and how to recognize the early stages… [Continue Reading] -

New solution detects enterprise data at risk on shadow IT
Publié: août 10, 2016, 6:22pm CEST par Ian Barker
Shadow IT is an increasingly major concern for businesses, the use of public cloud services offers convenience for workers but risks confidential information being exposed outside the organisation. Canadian endpoint security company Absolute is launching new functionality for its Absolute Data and Device Security (DDS) product that detects data at risk on endpoints associated with cloud storage applications. With the latest release of DDS, admins can determine which cloud applications are being used in the organization and what information is being stored. It includes Absolute's Endpoint Data Discovery capability which allows the discovery of sensitive data on devices associated with cloud… [Continue Reading] -

New platform allows integration of VMware and public cloud
Publié: août 10, 2016, 4:06pm CEST par Ian Barker
Many businesses are turning to virtualization technologies and to public cloud services like AWS, but bringing these technologies together can be tricky. Hybrid IT specialist HotLink is launching a new Cloud-Attach platform that enables customers to quickly, easily and holistically incorporate public cloud resources into their existing production data centers. Cloud-Attach offers out-of-the-box interoperability between VMware management infrastructure and Amazon Web Services, without adding operational or integration complexity. In addition, new managed services allow customers to deploy 'cloud-attached' data centers efficiently and without public cloud expertise on staff. "Public clouds like AWS have been growing at an aggressive rate for the… [Continue Reading] -

ThousandEyes delivers improved network visibility for enterprises
Publié: août 10, 2016, 2:50pm CEST par Ian Barker
The internet and the cloud are now a key part of the infrastructure for many enterprises. But the advantages of scale, flexibility and cost can come at a price of complexity, reliability, and vulnerability. Network intelligence company ThousandEyes is releasing Endpoint Agent, which provides a way to measure end-user experience and network behavior for every network that employees use to access critical services. ThousandEyes Endpoint Agent extends network intelligence to employee laptops and desktops, as well as the enterprise network access infrastructure. It enables IT teams to troubleshoot and resolve end-user performance issues for any application, whether it's deployed on-premise… [Continue Reading] -

Are you spending too much of your life using technology?
Publié: août 9, 2016, 12:26pm CEST par Ian Barker
We all spend more time using computers, mobiles and other devices, but exactly how much of your life is devoted to using technology? UK technology rentals chain BrightHouse has done some research which shows that 37 percent of Brits spend more than two hours every day browsing the web. What’s more the average 18-year-old spends 343 hours a year checking social media. Other findings include that for the average male 50 percent of their day is spent using a computer, mobile phone, console or in front of the TV. On average three hours and 28 minutes are spent daily on… [Continue Reading] -

New browser management suite helps businesses improve security and cut costs
Publié: août 8, 2016, 3:11pm CEST par Ian Barker
The move to software-as-a-service models has meant that the humble browser is now the key endpoint software for many enterprises. Yet this reliance on browsers can make it hard for IT teams to exercise the levels of control they need. Browser management specialist Browsium is launching a new version of its management suite to give administrators the right tools to improve security and reduce costs. "Enterprise organizations have struggled to adapt software management tools, built for native desktop applications, to the web applications that now run businesses," says Matt Heller, Browsium’s founder and chairman. "The management, security, and configuration challenges for packaged client… [Continue Reading] -

Latin America set to see major mobile growth
Publié: août 5, 2016, 4:42pm CEST par Ian Barker
Until now the Latin America region has been slow to adopt mobile apps, partly because of limited availability of high-speed data connections. But as the Rio Olympics kick off and the world focuses on the region, Yahoo's analytics arm Flurry is releasing its first-ever report analyzing mobile activity across Latin America. Flurry has tracked 10 percent year-on-year growth in active devices between June 2015 and June 2016, up from 230 million to 252 million. It has measured 70 million more active devices in the region in June 2016. When broken down by manufacturer, Samsung has gained six percent market share… [Continue Reading] -

Casting a light on shadow IT -- turning threat into opportunity [Q&A]
Publié: août 5, 2016, 4:11pm CEST par Ian Barker
Today's climate of digital transformation (DX) is giving rise to a variety of intriguing cloud and software-as-a-service based offerings. In the case of public cloud, instant access to infrastructure and platforms for developing new services off-premise may be extremely attractive to some organizations. The modern world of free cloud services and easily installable apps makes it all too easy for employees to bypass the IT department and use whatever systems they want. Virtually unlimited elasticity and pay-as-you-go cost models with no capital expenditure make these offerings an ideal solution to lines-of-business . Add to this a wealth of SaaS offerings… [Continue Reading] -

66 percent of IT professionals admit to delaying migrations
Publié: août 5, 2016, 3:28pm CEST par Ian Barker
According to a new study carried out by cloud migration specialist Vision Solutions, migrations are one of the major headaches faced by IT professionals. So much so that 66 percent say they've delayed a migration. Plus, nearly 75 percent of all companies who performed a migration in 2015 say they were offline or experienced downtime for 48 hours or more. Of the 935 professionals surveyed, 35 percent say that they lack the experience or the expertise to confidently perform a system migration. No surprise then that a worrying 44 percent of businesses experienced a migration failure in 2015. In addition,… [Continue Reading] -

OpenYOLO API project set to enhance user security and make login easier
Publié: août 4, 2016, 3:18pm CEST par Ian Barker
Google and online identity and password management company Dashlane are announcing the upcoming launch of a new, open-source API project to enhance user security. The collaboration between Dashlane and Google, plus other leading password managers, will develop OpenYOLO (You Only Login Once), an open API that will enable app developers to access passwords stored in password managers to easily and securely log users into their Android applications. "This is an important initiative for our industry and for the state of user security," says Emmanuel Schalit, CEO of Dashlane. "Collectively, we are committed to increasing user security and believe that the… [Continue Reading] -

New solution lets enterprises transfer sensitive data securely
Publié: août 4, 2016, 12:39pm CEST par Ian Barker
Businesses in industries like healthcare, financial services, insurance, retail and government hold sensitive data and need to be able to keep it safe at all times. Compliance with regulations like PCI and HIPAA often requires new layers of security between the public internet and protected data. Network management software company Ipswitch is tackling this with the launch of Ipswitch MOVEit 2016. The product gives IT teams the ability to ensure secure and compliant internal and external file transfers, automate workflows and automatically generate reports while ensuring zero downtime and no data loss. In addition, MOVEit 2016 contains an all new… [Continue Reading] -

82 percent of Brits use the internet every day
Publié: août 4, 2016, 11:49am CEST par Ian Barker
Adults in Great Britain are using the internet more than ever before according to new figures released by the government's Office for National Statistics (ONS). The internet was used daily or almost daily by 82 percent of adults (41.8 million) in Britain in 2016, up from 78 percent (39.3 million) in 2015 and 35 percent (16.2 million) in 2006 when statistics were first collected. Mobile internet use is up too, overall 75 percent of adults used the web 'on the go' on a smartphone, portable computer or hand held device in 2016. This figure is much higher at 97 percent… [Continue Reading] -

More than 60 percent of Windows users would switch to Mac for more privacy
Publié: août 3, 2016, 10:52am CEST par Ian Barker
Concerns over Windows 10 and the amount of data it collects via the Windows Store could prompt users to switch to Mac according to a new survey. The study conducted by OnePoll on behalf of security and privacy advice and comparison website Comparitech.com finds that 61 percent of the US public who regularly use Windows would at least consider switching to Mac. In the UK the figure is even higher at 67 percent, with 15 percent saying they would definitely consider swapping. Only 33 percent in the UK and 39 percent in the US say that they would not contemplate… [Continue Reading] -

CheckPoint launches real-time zero day browser protection
Publié: août 2, 2016, 3:33pm CEST par Ian Barker
The most common way for malware to get onto a PC is via files downloaded from the web. According to Exploits at the Endpoint: SANS 2016 Threat Landscape Study, 41 percent of people suffered their worst security events from drive by downloads and 80 percent suffered phishing attacks. Threat protection specialist CheckPoint is launching a new anti-malware and anti-phishing extension for web browsers to address this growth in web-based malware and social engineering attacks. SandBlast Agent for Browsers is an extension for Internet Explorer and Chrome (a Firefox version will be coming later) which stops zero day web-based malware, phishing… [Continue Reading] -

New subscription service offers flexible threat intelligence
Publié: août 2, 2016, 3:13pm CEST par Ian Barker
Depending on their size and the sector they operate in, businesses need to respond to threats of different types and require intelligence to suit. Endpoint protection specialist CrowdStrike is launching a tiered eCrime subscription that will allow customers to choose the option that best meets their needs to gain new capabilities and insights into the entire eCrime adversary ecosystem, and orchestrate detection and response options in a more effective manner. It allows users to access automated and integrated eCrime threat intelligence through CrowdStrike’s Falcon Intelligence Standard, which provides tactical threat intelligence for both nation-state actors and eCrime actors. They can… [Continue Reading] -

New security solution offers anytime, anywhere user protection
Publié: août 2, 2016, 12:38pm CEST par Ian Barker
As growing numbers of devices are connected to the internet, security and privacy concerns grow. Businesses are looking for solutions that provide protection for both the endpoint and the network. Israel-based Allot Communications is announcing a new collaboration with Intel Security to introduce McAfee Unified Security Powered by Allot, providing complete end-to-end security capabilities. The solution blends advanced threat detection technologies in the network and at the endpoint with customer intelligence and comprehensive personalization capabilities to deliver a scalable platform that simplifies security service activation, service awareness, operation and management. Deployed by communication service providers (CSPs) as a value-added security service… [Continue Reading] -

The rise of the Linux botnet
Publié: août 2, 2016, 12:00pm CEST par Ian Barker
A new report from Kaspersky Lab on botnet-assisted DDoS attacks shows a steady growth in their numbers the second quarter of this year. SYN DDoS, TCP DDoS and HTTP DDoS remained the most common attack scenarios, but the proportion of attacks using the SYN DDoS method increased 1.4 times compared to the previous quarter and accounted for 76 percent. This is due to the fact that the share of attacks from Linux botnets almost doubled (to 70 percent) -- and Linux bots are the most effective tool for SYN-DDoS. This is the first time that Kaspersky DDoS Intelligence has registered… [Continue Reading] -

Arxan guards against application layer threats
Publié: août 1, 2016, 5:08pm CEST par Ian Barker
Cyber attacks are increasingly happening at the mobile and IoT application layer. This allows hackers to bypass server-level security and go straight for the binary code, to steal IP, credentials and other sensitive information. Attack prevention company Arxan Technologies is launching new features to help guard against this type of threat. These include new and enhanced support for major operating systems and languages, including QNX (a subsidiary of Blackberry) and Apple's Swift programming language, as well as new white-box cryptographic schemes including SHA-3. "As more attacks occur at the mobile and IoT application layer, binary code protection has become a critical… [Continue Reading] -

Windows 10 Anniversary update is not driving enterprises to switch
Publié: août 1, 2016, 3:46pm CEST par Ian Barker
Although 64 percent of enterprises are planning to move to Windows 10 in the next year, tomorrow’s expected Windows 10 Anniversary release from Microsoft isn't proving to be a huge motivator for upgrading. According to the survey from systems management specialist Adaptiva, 76 percent say the anniversary update is not increasing their sense of urgency to move to Windows 10. Key motivators for migration, according to the survey, are access to the newest Windows 10 security features, such as enterprise data protection, Device Guard, Credential Guard, and security auditing, as key drivers for the migration. "These survey results show that… [Continue Reading] -

New platform detects mobile threats at the app level
Publié: juillet 29, 2016, 11:15am CEST par Ian Barker
Increased reliance on mobile devices opens enterprises up to a new range of threats. While mobile management solutions can do a good job of protecting the device, it's harder to guard against attacks on individual apps. Mobile security company Appmobi is launching a new solution that detects and resolves attacks at the app level. Appmobi Protection Center uses machine learning coupled with an IT-defined rules engine to analyze and process millions of events per minute. It compares behavior to existing profiles, and recognizes attacks in real time to automatically remedy any potential threat. This provides IT teams with visibility into… [Continue Reading] -

New solution helps enterprises guard against chat-based phishing
Publié: juillet 28, 2016, 4:09pm CEST par Ian Barker
Slack is the largest enterprise chat platform in the world with more than 2.7 million daily active users who spend an average of 140 minutes per day using it. Not surprising then that alert attackers see it as an opportunity to expand their social engineering campaigns. The fact than many people use Slack without the IT team's knowledge creates a further security issue. Cloud security specialist GreatHorn is announcing its Collaboration and Chat Security product which provides security operations, analytics, and reporting for Slack deployments, as well as expanding security controls for cloud systems like Google Apps and Office 365. "Employees… [Continue Reading] -

What new tech will you see in your lifetime?
Publié: juillet 28, 2016, 3:31pm CEST par Ian Barker
Technology has already shaped the world we live in. Things like television, the jet engine and the first computers have made major changes to the way we live our lives. But what can we expect in the future? The pace of change is faster than ever and there are innovations on the horizon that will change our lives just as radically as those of the past. Electronics supplier RS Components has produced an interactive graphic that lets you see how old you’ll be when these new technologies arrive. It predicts the first robot pharmacists dispensing drugs by 2021 for example… [Continue Reading] -

61 percent of Americans fear having their cars or home security cameras hacked
Publié: juillet 28, 2016, 12:56pm CEST par Ian Barker
As more and more devices get connected to the Internet of Things, so their susceptibility to hacking increases too. New research from enterprise data protection company Vormetric in conjunction with Wakefield Research shows that this is a concern for many people. Most feared is the hacking of cars and home security cameras, both cited by 61 percent. In addition 52 percent thought a virtual personal assistant such as Amazon Echo would be vulnerable to hacking, and 45 percent were concerned about the potential to hack smartwatches. Although security of healthcare systems has received a lot of attention, medical monitors register… [Continue Reading] -

The easy way to become a cyber criminal
Publié: juillet 27, 2016, 5:24pm CEST par Ian Barker
You might think that becoming a cyber criminal required some hard work and dedication to your task, maybe even some form of apprenticeship where you learn the craft at the side of a more experienced hacker. But new research has identified a one-stop, outsourced online shop, providing hosting, design and payment solutions for cyber criminals looking for a low-cost of entry method to sell their ill-gotten assets. Cyber attack prevention specialist Digital Shadows conducted research into deer.io, a Russian-language site that hosted darkside.global. The service appears to have been active since at least October 2013 and, at the time of… [Continue Reading] -

DDoS attacks increase by over 80 percent
Publié: juillet 27, 2016, 4:41pm CEST par Ian Barker
In the second quarter of this year DDoS attacks increased by 83 percent to more than 182,900, according to the latest threat report from security solutions company Nexusguard. The report shows that Russia has become the number one victim country. Starlink -- a Russian ISP supporting small, medium and large enterprises -- received more than 40 percent of the DDoS attacks measured over a two-day period. This targeted DNS attack also pushed the mean average DDoS duration to hours instead of minutes, as measured in the previous quarter. Nexusguard's researchers attributed this increase to nationalist hactivists organizing a targeted attack… [Continue Reading] -

Zoho lets salespeople access CRM straight from their inbox
Publié: juillet 27, 2016, 3:58pm CEST par Ian Barker
Salespeople spend a lot of their time in communication with customers and prospects, so time spent updating CRM systems can often be seen as unproductive. Business cloud platform Zoho aims to change that with the launch of its latest CRM product which incorporates SalesInbox, an email client designed exclusively for salespeople. Zoho SalesInbox works with Gmail, Exchange, Yahoo! Mail, Zoho Mail and other standard email hosting services. It's part of Zoho CRM Enterprise and will also work with Salesforce. What it does is to organize emails according to how important they are for a salesperson, enabling them to prioritise and… [Continue Reading] -

Every piece of sensitive data could have 1,000 unnecessary copies
Publié: juillet 27, 2016, 3:22pm CEST par Ian Barker
Data risk reduction specialist Identity Finder has rebranded itself as Spirion and has released the results of long-term sensitive data audits at three of its largest enterprise sites. During the audits, the company discovered that if left unchecked, every legitimate piece of sensitive data will create up to 1,000 unnecessary copies. What's more, the company found that if left unmanaged, for every legitimate user of sensitive data, up to 100 additional users will end up having access to it. These assessments are based on before and after audits of the implementation of Spirion’s Data Platform. "To eliminate the risks associated… [Continue Reading] -

Aegis Secure Key 3.0 [Review]
Publié: juillet 27, 2016, 1:27pm CEST par Ian Barker
There are a number of secure flash drives on the market, but most of them rely on a software lock that requires you to enter a PIN on the computer after you've plugged in the drive. Apricorn takes a different approach with its Secure Key which has a keypad on the device itself, allowing you to lock and unlock it independently. At 95.5 mm it's about half as long again as a normal flash drive and fits snugly into an aluminum slip case so you can't accidentally press buttons in your pocket. The keys are small but have a positive… [Continue Reading] -

SafeDNS uses machine learning to detect malicious internet resources
Publié: juillet 27, 2016, 11:07am CEST par Ian Barker
However careful you are online it's always possible to get caught out by a maliciously coded website or advert that leads to malware ending up on your machine. Online safety service SafeDNS is launching a new system for detecting malicious internet resources, which it claims blocks close to 100 percent of them for better online protection. Using continuous machine learning and user behavior analysis, the new SafeDNS system takes a step forward from static lists of categorized resources to dynamically created databases. The SafeDNS research team has produced a technology able to detect malicious internet resources with 98 percent precision.… [Continue Reading] -

New platform aims to cut mobile ad waste
Publié: juillet 26, 2016, 6:15pm CEST par Ian Barker
There's a famous quote from 19th century British soap magnate Lord Leverhulme which goes, "Half the money I spend on advertising is wasted, and the problem is I don't know which half". Despite the array of technology and analytics tools available today, it’s still true that a good deal of advertising spend is simply thrown into the dark. Real-time mobile advertising platform Smaato is aiming to cut waste with the launch of its Smaato Demand Platform (SDX) that allows more accurate targeting of ads. Aimed at mobile publishers and app developers, SDX brings powerful targeting and QPS (query per second)… [Continue Reading] -

88 percent of all ransomware is detected in the healthcare industry
Publié: juillet 26, 2016, 4:24pm CEST par Ian Barker
According to the findings of a new report, companies in the healthcare industry have the most ransomware present, accounting for 88 percent of all detections in the second quarter of this year. The report from managed security provider Solutionary shows other affected industries include education (six percent) and finance (four percent), with eight other industries combining for less than two percent of detections. "Healthcare has been a target for ransomware campaigns because the industry has often paid ransom to retrieve vital customer data quickly. Furthermore, healthcare organizations use an abundance of systems and devices that are crucial pivot-points for an… [Continue Reading] -

Real-time outage detection delivers insights into online performance
Publié: juillet 26, 2016, 3:29pm CEST par Ian Barker
As businesses come to rely increasingly on the cloud, the impact of downtime in any part of the network infrastructure is felt more keenly. Network intelligence company ThousandEyes is launching a new Internet Outage Detection product, providing a way for enterprises to reliably detect outages across ISPs. It delivers better insights into internet performance by detecting patterns of anomalies in network data generated by global users of the ThousandEyes platform. These capabilities provide actionable information about when and how network and routing outages are affecting application and service delivery. "All kinds of companies are using ThousandEyes to gain critical visibility… [Continue Reading] -

SentinelOne offers customers a $1 million ransomware guarantee
Publié: juillet 26, 2016, 2:53pm CEST par Ian Barker
Ransomware is one of the biggest threats that companies face and it can have severe consequences if important files are corrupted or lost. Endpoint security specialist SentinelOne is underlining its confidence in its product by launching a threat protection guarantee to provide customers with financial protection in the event of ransomware attacks on their networks. SentinelOne's cyber threat protection guarantee program provides its customers with financial support of $1,000 per endpoint, or up to $1 million per company, securing them against the financial implications of a ransomware attack, if the company suffers an attack and SentinelOne is unable to block… [Continue Reading] -

Email is still king despite the threats it poses
Publié: juillet 25, 2016, 5:49pm CEST par Ian Barker
Email is often cited as the technology that made the internet essential for businesses. You would have thought by now that something else would have come along to replace it in our affections, but the popularity of email shows no sign of waning. A new infographic from email authentication company ValiMail shows that 98.5 percent of people check their email daily and spend as much as six hours doing so. What's more 74 percent prefer email for business communication, and 82 percent of consumers sign up for emails from websites. It's no surprise then that 66 percent of consumers buy… [Continue Reading] -

Dashlane streamlines password management for BYOD
Publié: juillet 25, 2016, 3:14pm CEST par Ian Barker
Weak passwords can put business data at risk, but if employees are using their own devices, poor security practices from their home life can spill over into the workplace. Password manager app Dashlane has a solution to this issue in the form of a new Spaces feature for its Business version, which allows employees to manage both their business and personal passwords on mobile devices. Users can toggle between dedicated work and personal Spaces so making employees more secure and empowering businesses to improve password security and access management. "Password management blurs the line between home and work. If an employee… [Continue Reading] -

Fighting the threat of social hacking [Q&A]
Publié: juillet 22, 2016, 11:08am CEST par Ian Barker
Often the weakest link in an enterprise’s cyber security is the person behind the endpoint. Although technology solutions can offer a high degree of protection, there’s no substitute for making users aware of the potential threats. Social engineering attacks are increasingly used to try and catch out employees. Education on cyber security is therefore something that's being taken seriously by businesses of all sizes. We spoke to Scott Youngs, CIO of infrastructure solutions and managed services company Key Information Systems to find out more about the threat and how education can help beat it. BN: Is security a major factor… [Continue Reading] -

New solution tackles ransomware at source
Publié: juillet 21, 2016, 3:04pm CEST par Ian Barker
Ransomware is one of the biggest cyber threats businesses and individuals face and tackling it requires a customized approach. Israel-based illusive networks is launching a new Advanced Ransomware Guard product that uses deception techniques to spot threats across the entire network, endpoints and servers and neutralize ransomware activity at the source hosts. "Ransomware requires a dedicated solution," says illusive networks CEO Shlomo Touboul. "Unlike other malware types, ransomware immediately takes sensitive information hostage and ransom demand timelines are tight, so proactive and accurate detection and response is imperative. The market's initial responses have yielded solutions based on behavioral analytics and… [Continue Reading] -

Why it's time for a new approach to Agile security [Q&A]
Publié: juillet 21, 2016, 11:11am CEST par Ian Barker
Security is often something that gets left until late in the development cycle and as Agile development takes off, security can be an inhibiting factor. Since many security breaches now target the endpoint, there's more emphasis on building secure software which means it's something that needs to be integrated into the development process. Fixing security flaws late in the day can prove costly and time consuming. Software security firm Cigital has recently released its latest Agile Security Manifesto offering principles for building security into the development process. We spoke to Meera Subbarao, director of secure development practice and a principal… [Continue Reading] -

LogMeOnce adds features to track and wipe mobile devices
Publié: juillet 20, 2016, 5:07pm CEST par Ian Barker
The increasing use of mobile devices and spread of BYOD means that there’s a risk of data falling into the wrong hands if a device is lost or stolen. Mobile identity and password management company LogMeOnce is adding new features to its app making it simpler to manage, track and wipe personal and business data from devices. LogMeOnce's Kill-Pill and Mobile Device Management (MDM) features enable individuals, businesses and IT administrators to easily enroll and manage devices, verify compliance and wipe data stored in LogMeOnce if necessary. Additionally, LogMeOnce BYOD enhances office productivity and security of sensitive data by giving… [Continue Reading] -

New solution delivers compliance for business Instagram users
Publié: juillet 20, 2016, 3:51pm CEST par Ian Barker
Businesses are increasingly adopting Instagram within the enterprise as a tool for building brand awareness and connecting with prospects and customers. But as with any form of business communication it's subject to regulatory control. Regulators may classify Instagram posts as advertisements and exchanged comments as business records. To address this, compliance specialist Actiance is adding Instagram support to its Actiance Socialite platform, which enables companies to capture social media posts in context and retain data, including the images, for instant search and retrieval. "Forward-thinking companies are increasingly using Instagram and other social channels to connect with digital audiences. Yet as they… [Continue Reading] -

New identity platform delivers passwordless authentication
Publié: juillet 20, 2016, 3:32pm CEST par Ian Barker
We regularly hear stories about the imminent death of the password. Add in thousands of Internet of Things devices needing to authenticate and it’s clear that the time has come for a better system. Identity management company ForgeRock is launching the latest edition of its ForgeRock Identity Platform, with advanced new capabilities that will enable organizations to employ passwordless login. ForgeRock Identity Platform is an end-to-end open source identity management solution that supports passwordless login as well as frictionless second factor authentication capabilities to provide continuous security. It can invoke two factor authentication if an anomaly occurs, for example if a… [Continue Reading] -

Euclid Connect delivers personalized in-store experiences via Wi-Fi
Publié: juillet 19, 2016, 4:34pm CEST par Ian Barker
Part of the reason for the success of online retailers is the ability to gather information on customers so that they can be targeted with appropriate offers. Retail analytics and engagement specialist Euclid Analytics is launching a new platform that aims to give brick and mortar retailers some of the same advantages. Euclid Connect uses Wi-Fi to let retailers market more effectively and personalize in-store experiences. Through the use of smartphones and existing on-site Wi-Fi, the platform delivers customer insights across physical locations, enabling brands to have a unified view of the customer's journey. By allowing smartphone users to opt-in to… [Continue Reading] -

New platform offers enterprises complete endpoint security
Publié: juillet 19, 2016, 2:52pm CEST par Ian Barker
Endpoint security company Carbon Black already offers application control, incident response, and threat-hunting products. Today it's announced the acquisition of next generation antivirus supplier Confer allowing it to offer a complete endpoint protection platform. The new platform, called Cb Endpoint Security, provides organizations with the flexibility they need to cope with growing and evolving security needs. Confer's cloud-based analytics engine will become part of a 'Cb Collective Defense Cloud,' adding depth to the platform. Cb Endpoint Security combines behavior-based prevention techniques with integrated detection and response capabilities to stop cyber attacks. Its cloud-based, deep-analytics approach blocks both malware and increasingly… [Continue Reading] -

More than half of companies fail to protect privileged credentials
Publié: juillet 15, 2016, 3:05pm CEST par Ian Barker
Details of privileged accounts represent a major prize for hackers because they unlock the access required to exploit virtually any part of an organization's network and data. Yet according to a new report many companies are failing to adequately protect them. The study by privileged account management (PAM) specialist Thycotic and research firm Cybersecurity Ventures benchmarked the PAM performance of more than 550 organizations and found that 52 percent received a failing grade. While 80 percent of respondents consider PAM security a high priority and 60 percent say that PAM security is required to demonstrate compliance with government regulations, the… [Continue Reading] -

Rock Jaw Clarito earphones: Stylish, budget-priced audio [Review]
Publié: juillet 15, 2016, 12:21pm CEST par Ian Barker
Last year we reviewed the Rock Jaw Alfa Genius V2 earphones and they impressed with their adjustable filters, offering a premium listening experience at a mid-range price. Even so, not everyone is prepared to spend more than $60 on a pair of earphones, so now British company Rock Jaw is targeting more frugal listeners with the new Clarito. Like the company's more expensive offering these come in a smart package containing the aluminum bodied earphones, three different sizes of silicone ear piece, a cable clip and a soft carrying pouch. The 90-degree jack plug is gold plated and the whole… [Continue Reading] -

'Happy Birthday' messages drive around 10 percent of email order revenue
Publié: juillet 14, 2016, 4:24pm CEST par Ian Barker
Although they account for only two percent of all emails sent, triggered marketing messages -- those sent to mark birthdays and other events -- generate 10.2 percent of email-driven revenue and 9.7 percent of email-driven orders. This is among the findings of a study by Yes Lifecycle Marketing, the company behind marketing and analytics platform YesMail360, which shows that people are twice as likely to open triggered messages as they are general marketing emails. "As email volume continues to increase, it becomes more and more difficult for marketers to stand out from the noise and effectively engage consumers", says Michael… [Continue Reading] -

New partnership extends reach of beacon advertising
Publié: juillet 14, 2016, 3:20pm CEST par Ian Barker
Beacon advertising is becoming increasingly popular as a means of targeting consumers in specific locations with relevant messages. It's now set to spread further as Freckle, the world's largest beacon technology company, announces a partnership with one of North America's largest mobile platform companies for publishers and media companies AirKast. AirKast customers include Cumulus Broadcasting, ESPN, CBS News Radio and Fox News Radio. The company has over 2,000 individual apps that are launched more than 20 million times per month. With the Freckle SDK in AirKast's applications, clients can now benefit from Freckle's thousands of beacons placed in stores and… [Continue Reading] -

Web users would rather filter ads than block them completely
Publié: juillet 14, 2016, 2:20pm CEST par Ian Barker
Blocking online adverts is a controversial subject -- yes, adverts can be annoying but they also represent the only revenue stream for many sites. A new survey from Adblock Plus in conjunction with HubSpot Research reveals that 83 percent of users just want to block the most intrusive ads and 77 percent would rather filter ads than block them completely. The survey questioned 1,055 respondents from the US, UK, Germany and France, with 70 percent of respondents being users of an ad blocker (not just Adblock Plus). Of the 30 percent non-users, 63 percent say that ad blocking has a positive… [Continue Reading] -

How businesses are missing out on data analytics
Publié: juillet 13, 2016, 5:15pm CEST par Ian Barker
Analytics is something that many enterprises are keen to make use of, but a new report finds that many businesses are approaching it in the wrong way. The report from decision science and big data specialist MuSigma identifies gaps and shortcomings in traditional approaches to analytics and problem solving but also highlights that a majority of senior leadership believes analytics is affecting company strategy and results in positive ways. "This report shows that many businesses are still misguidedly prioritizing data and technology needs over the need for better decision making," says Tom Pohlmann, head of values and strategy, Mu Sigma. "Changes… [Continue Reading] -

New self-phishing tool helps companies measure attack risks
Publié: juillet 12, 2016, 4:01pm CEST par Ian Barker
Protecting against data breaches is always better than dealing with their aftermath. And since phishing is still one of the most popular attack methods businesses and employees need to be alert to the risks. Authentication specialist Duo Security is launching a new, free tool to let IT teams run internal phishing simulations and assess their vulnerability to such attacks. Using Duo Insight, administrators can identify potential security weaknesses and make the case for investing in stronger security solutions. It produces easy-to-read reports that make it straightforward for administrators and security teams to present the relevant findings to management. "Unfortunately, many organizations… [Continue Reading] -

Skype for Business use on mobile expected to double by 2018
Publié: juillet 12, 2016, 3:06pm CEST par Ian Barker
While Skype remains the most popular VoIP tool, the Skype for Business mobile client has been dogged by ongoing quality and technical issues that have slowed its rollout. A new survey by Unify Square and Osterman Research finds that 30 percent of IT teams' total time spent troubleshooting the Skype platform is devoted to the mobile client. Despite this, most organizations are happy with Skype for Business Mobile Client with 54 percent satisfied or very satisfied. Only 16 percent are somewhat dissatisfied or very dissatisfied due to technical issues. Respondents identified mobile battery life and the inability to see application… [Continue Reading] -

Malware attack targets European energy companies
Publié: juillet 12, 2016, 2:59pm CEST par Ian Barker
The Labs team at malware protection company SentinelOne has discovered a sophisticated malware campaign that's specifically targeting at least one European energy company. The malware, called SFG, is the mother ship of an earlier malware sample called Furtim, which targets the industrial automation control systems with sophisticated malware and acts as dropper to deliver a payload which could be used to extract data or potentially shut down the energy grid. The malware has been developed to work on devices running any version of Microsoft Windows and has been carefully designed to bypass traditional antivirus software and firewalls -- including those… [Continue Reading] -

Microsoft Finnished!
Publié: juillet 11, 2016, 6:05pm CEST par Ian Barker
As gifts to headline writers go, Microsoft's acquisition of Finland's Nokia mobile phone company keeps on giving. We already did the Finnish line gag when the deal to buy Nokia was announced in 2014. Today the company confirmed that as part of the shedding of 1,850 jobs from its smartphone business, announced back in May, it's closing its Nordic subsidiary. This will lead to the loss of 1,350 jobs in Finland. "We are focusing our phone efforts where we have differentiation -- with enterprises that value security, manageability and our Continuum capability, and consumers who value the same," said Satya Nadella, chief executive… [Continue Reading] -

New solution offers one-stop cyber security for SMBs
Publié: juillet 11, 2016, 3:24pm CEST par Ian Barker
For smaller organizations, managing their systems can present enough of a challenge without the additional need to worry about different aspects of security. Now a new three-way collaboration between underwriters Victor O Schinnerer & Company, SaaS data protection company Spanning, and Microsoft, is designed to help small and mid-size organizations safeguard their business and data. It offers a suite of risk management and data protection solutions including the Schinnerer Cyber Protection Package, Microsoft Office 365, Microsoft Enterprise Mobility Suite, and Spanning Backup for Office 365. The solution includes Schinnerer's Cyber Protection Package, offering insurance cover for digital crime, breach liability,… [Continue Reading] -

New migration program helps enterprises move big data to the cloud
Publié: juillet 11, 2016, 12:45pm CEST par Ian Barker
Many companies are keen to gain from the power of big data but struggle with the expense and operational complexity of expanding their on-premise systems. Moving data to the cloud is the obvious solution but that too leads to issues surrounding migration. Big data-as-a-service company Qubole has partnered with software solutions specialist WANdisco to make the move easier with the launch of a Cloudera Migration Program. "The big data industry is shifting from on-premise to cloud as the preferred deployment model, but many early Cloudera customers are stuck with a system that wasn't designed for the cloud." says Ashish Thusoo,… [Continue Reading] -

New network monitoring tool offers better visibility and control
Publié: juillet 11, 2016, 10:53am CEST par Ian Barker
Owing to the growth of cloud and hybrid environments, IT teams are faced with increasingly complex networks that are a challenge to control and monitor. IT management solutions specialist Ipswitch is launching a new product that allows teams to visualize, troubleshoot and monitor networks, servers, virtual machines and applications from a single piece of software. WhatsUp Gold 2017 provides a comprehensive and interactive view of the entire network. This enables IT teams to discover, visualize and interact with their IT environment via advanced visualization technology, troubleshoot faster with intuitive maps, workflows and dashboards, and monitor their entire environment with one… [Continue Reading] -

New security tool addresses Android app collusion threat
Publié: juillet 7, 2016, 4:51pm CEST par Ian Barker
As we reported last month app collusion, where apps work together to extract sensitive data, now represents a very real security risk to mobile devices. To address this emerging threat, component technology firm Formaltech, today is releasing FUSE, a DARPA-funded tool that detects inter-application collusion and other vulnerabilities in Android apps. The FUSE platform identifies potential security vulnerabilities and tracks information flow through multiple apps, revealing potential collusion between apps. The tool uses static binary analysis to detect vulnerabilities without requiring the source code of the apps, allowing security professionals to analyze third party apps without the need for vendor cooperation.… [Continue Reading] -

90 percent of security events are caused by bots
Publié: juillet 7, 2016, 11:18am CEST par Ian Barker
Bots account for 49 percent of all internet traffic, most of which is from malicious 'bad bots' according to website security company Incapsula. Of course there are good bots too, such as the crawlers used by major search engines, but according to Incapsula’s figures 90 percent of all security events are caused by bots, and 66 percent of all bot activity is malicious. It splits bad bots into four categories, The Impersonator -- which poses as a regular visitor to spy on, steal from or bring down a website. The Hacker -- which seeks to steal valuable data (such as… [Continue Reading] -

Employees put corporate networks at risk
Publié: juillet 6, 2016, 5:03pm CEST par Ian Barker
Digital device practices among US employees are exposing their employers to increased security risks according to a new study. Identity management company OneLogin along with Arlington Research surveyed 1022 respondents in the US and found that 13 percent let their colleagues use a device that can access their employer's network. In addition nine percent allow their partners to access such a device, and one percent even permit their children to use it. Password sharing is widespread too, with 20 percent of employees sharing their work email password, and 12 percent sharing passwords to other work applications. Nearly half of all… [Continue Reading] -

New partnership delivers cloud solution for the insurance industry
Publié: juillet 6, 2016, 2:08pm CEST par Ian Barker
Insurance companies have slightly different software needs from other businesses. They need to expand accounts, drive renewals, streamline the new policy acquisition process and manage claims. Now cloud specialist Vlocity and insurance solution provider Insurity are announcing a partnership that will deliver a cloud solution for insurance businesses. "Insurity is focused on driving insurers' modernization and transformation initiatives -- and we work with more than 100 insurers. Providing targeted, effective and efficient policy and plan service interactions across all channels is what strengthens customer relationships," says Lani Cathey, senior vice president at Insurity. "Our work with Vlocity will bolster our… [Continue Reading] -

Identity fraud in UK targets under 30s
Publié: juillet 5, 2016, 10:51am CEST par Ian Barker
New figures reveal a 52 percent rise in young identity fraud victims in the UK. In 2015, just under 24,000 people aged 30 and under were victims of identity fraud. This is up from 15,766 in 2014, and more than double the 11,000 victims in this age bracket in 2010. The figures from fraud prevention service Cifas -- which is calling for better education about fraud and financial crime -- are released alongside a new short video designed to raise awareness of ID fraud among younger age groups. "Fraudsters are opportunists", says Simon Dukes, Cifas chief executive. "As banks and lenders… [Continue Reading] -

More than half of Android phones are vulnerable to encryption bypass
Publié: juillet 4, 2016, 1:03pm CEST par Ian Barker
A newly revealed vulnerability on Android phones is able to bypass the full disk encryption on over half of devices. The attack, demonstrated by Israeli security researcher Gal Beniamini, can allow an attacker to break through the levels of trust and privileges that are intended to ensure only legitimate code can access secret material, such as DRM keys or disk encryption keys. Although the attack was patched in the May security update, two-factor authentication specialist Duo Security says that only 43 percent of Android devices are patched and safe from this type of attack, leaving 57 percent still at risk.… [Continue Reading] -

SaaS market is set to reach $55 billion by 2026
Publié: juillet 1, 2016, 5:07pm CEST par Ian Barker
A new study by software selection site Better Buys shows that the shift to SaaS solutions is growing apace, expected to increase from just $8 billion in 2015 to $55 billion by 2026. It also reveals that more than 1,400 new SaaS companies have sprung up in the last five years, taking a large volume of market share from major competitors like Adobe, Cisco, IBM, and Salesforce, and accounting for 57 percent of the SaaS market. While SaaS is growing globally, the US still has more than half the market. Based on recent job listing data from Indeed, top states… [Continue Reading] -

Is the Internet of Things the next Industrial Revolution?
Publié: juillet 1, 2016, 12:02pm CEST par Ian Barker
The Industrial Revolution changed society and led to the growth of towns and cities with consequent mass production and movement of population. Electronics retailer RS Components has produced an infographic looking at how the Internet of Things is leading a move to create a new industrial internet, powered by intelligent machines. The move is being driven by the availability of low-cost sensors and the introduction of long range wireless technology. It predicts that the Industrial Internet will lead to greater productivity and higher living standards as it makes it easier to add value. It will also make possible smart cities,… [Continue Reading] -

New cloud platform gives companies insight into channel sales
Publié: juin 30, 2016, 5:24pm CEST par Ian Barker
Companies selling IT solutions via channel partners can easily find that they spend all their time dealing with resellers and distributors, and consequently lose touch with their end users. Channel management company Zyme is launching a new cloud platform that helps global B2B and B2C enterprises monitor and optimize the performance of their distribution channels through timely, actionable intelligence. The zyme cloud platform 3.0 takes raw partner data and transforms it into intelligence using proprietary technologies and rich content libraries. This is then made available through analytics dashboards and seamless integration with customers’ business systems. "The zyme cloud platform 3.0… [Continue Reading] -

New startup aims to help solve the shortage of data scientists
Publié: juin 30, 2016, 4:02pm CEST par Ian Barker
Whilst the use of big data is gaining traction around the world, one of the things that’s likely to hold back development is a shortage of qualified data scientists. By 2018, the demand for data scientists is predicted to exceed supply by about 50 to 60 percent according to a recent McKinsey study. Austrian startup company Knoyd is aiming to disrupt the process of training and hiring data scientists by launching BaseCamp, a data science bootcamp. It will allow prospective data scientists to learn and train on real companies' problems and will prepare them for an exciting data science career. During… [Continue Reading] -

At least one mobile device in every large enterprise has a malware infection
Publié: juin 30, 2016, 3:24pm CEST par Ian Barker
A new report focusing on malware in the enterprise, finds that large organizations (those with more than 200 iOS or Android mobile devices) are almost guaranteed to have at least one malware-infected device. The report, by mobile threat defense specialist Skycure finds that four percent of all mobile devices have malware installed, regardless of whether they are managed by an enterprise or an individual. Among the detailed findings are that three percent of all enterprise iOS devices have malware installed, and nearly twice as many (5.7 percent) of all enterprise Android devices are infected. Android devices have a greater variety… [Continue Reading] -

Microsoft cloud changes are overwhelming its customers
Publié: juin 30, 2016, 1:01pm CEST par Ian Barker
Microsoft partners are witnessing Office 365 technology updates, refreshes and changes outpacing their customers' ability to keep up with them. This is according to a new study by customer experience specialist harmon.ie which surveyed more than 200 Microsoft partners worldwide. Thanks to the complexity and rate of change, partners are seeing new opportunities to step in and provide the much needed bridge to help companies keep up. "As Microsoft continues to innovate in the cloud, its rapid release of new capabilities is overwhelming its customers who are struggling to make sense of them," says Yaacov Cohen, CEO of harmon.ie. "This… [Continue Reading] -

72 percent of companies plan to ditch passwords by 2025
Publié: juin 29, 2016, 5:00pm CEST par Ian Barker
Security professionals increasingly believe that usernames and passwords provide insufficient security, and 72 percent think they will be phased out within nine years. This is among the findings from mobile identity company TeleSign which also shows that security professionals are increasingly turning to effective, easy to implement technologies such as behavioral biometrics and two-factor authentication to secure user accounts. "The vast majority of security professionals no longer trust the password to do its job," says Ryan Disraeli, co-founder of TeleSign. "Thankfully, most companies aren't resigning themselves or their users to password-only account security. They are implementing two-factor authentication in droves and… [Continue Reading] -

Use of encryption in enterprises is at all time high
Publié: juin 29, 2016, 1:19pm CEST par Ian Barker
The use of encryption in global organizations is now at an all-time high, with 41 percent using it extensively today -- a seven percent rise over last year. This is among the findings of a Global Encryption report from Thales e-Security and the Ponemon Institute which shows that businesses are taking action to guard their sensitive data. Database encryption has risen from 42 percent to 61 percent in the past year among companies with a mature encryption strategy in place. Following Heartbleed and other SSL vulnerabilities, internet communications (SSL/TLS) have also seen a huge increase in the use of encryption,… [Continue Reading] -

75 percent of IT pros lack visibility into their hybrid clouds
Publié: juin 29, 2016, 11:42am CEST par Ian Barker
A majority of organizations lack visibility into their cloud infrastructure, file shares, user activity and mobile devices, according to a new survey. The study from cloud governance specialist Netwrix reveals that almost 65 percent of organizations do not have complete visibility into user, IT and third-party activity in their IT infrastructure. In addition 75 percent of respondents have partial or no visibility into their cloud and hybrid IT environments. The survey of over 800 people across 30 industries worldwide shows a large majority of respondents (78 percent) saying they are unaware or only partly aware of what is happening across their unstructured… [Continue Reading] -

New solution allows intelligent management of data growth
Publié: juin 28, 2016, 6:04pm CEST par Ian Barker
The amount of data companies have to deal with is getting bigger and bigger, it's expensive to store and time consuming to manage. Little wonder then that businesses are looking for solutions that can automate the process. Komprise, emerges from beta today with a solution that lets companies automate the management of enterprise data with analytics and insight -- across both cloud and on premise. With no hardware to deploy, no storage agents, no changes to the hot data path, no complex configurations or proprietary interfaces, Komprise seamlessly works across storage environments, both on-premise and in the cloud. The solution… [Continue Reading] -

67 percent of used drives for sale contain sensitive data
Publié: juin 28, 2016, 4:41pm CEST par Ian Barker
An analysis of 200 second-hand hard disks and solid state drives purchased from eBay and Craigslist in the first quarter of 2016 reveals that 67 percent of them contained personally identifiable information. In addition 11 percent held sensitive corporate data, including company emails, CRM records and spreadsheets containing sales projections and product inventories. The study comes from mobile diagnostics and secure erasure specialist Blancco Technology Group. "With the Ashley Madison hack, in particular, users who wanted to make sure all of their data was erased from the dating site put all of their trust into the site’s $20 'Full Delete'… [Continue Reading] -

Almost a third of IT professionals ignore cyber security alerts
Publié: juin 28, 2016, 4:01pm CEST par Ian Barker
Just over 30 percent of IT professionals admit to sometimes ignoring security alerts because of high volumes of false positives. This is among the findings of a new survey from Skyhigh Networks conducted along with the Cloud Security Alliance which also reveals that 20 percent of companies have more than ten security tools that generate alerts. Incident response will be the most important new skill in the next five years according to 80.4 percent of respondents. In addition 62.1 percent of businesses have security concerns about public cloud platforms such as AWS and Azure, 40.5 percent believe that they can't secure… [Continue Reading] -

Cohesity adds protection for physical servers
Publié: juin 28, 2016, 3:33pm CEST par Ian Barker
As demand for data grows, companies often struggle to stay in control of a range of different secondary storage solutions. Californian company Cohesity has pioneered hyper-converged secondary storage and today announces new releases of its DataProtect and DataPlatform products that expand data protection to physical servers, enable faster recovery times, and double performance levels. Cohesity DataPlatform 3.0 delivers improved VMware backup performance as well as doubling IOPS and throughput performance for file access. Cohesity is also introducing a new proactive monitoring service that will analyze and recommend preventative maintenance actions for DataPlatform installations. DataProtect 3.0 extends its data protection coverage… [Continue Reading] -

New cloud platform delivers IT resilience
Publié: juin 28, 2016, 1:33pm CEST par Ian Barker
Economic pressures means IT departments need to provide high levels of service whilst cutting costs and using fewer resources. Legacy infrastructure not only gets in the way of this it limits IT's ability to quickly respond to incidents, outages and security breaches. Disaster recovery specialist Axcient is launching Fusion, a cloud-converged platform for IT resilience and agility that will allow enterprises to reduce infrastructure overhead and cost, regain valuable IT staff time and deliver a more reliable and high-performing service to their end users. "Until now, IT departments have been caught in a vicious cycle of buying more hardware and… [Continue Reading] -

First impressions matter in email marketing
Publié: juin 28, 2016, 12:38pm CEST par Ian Barker
We all know that first impressions are important and it seems that the same is true when it comes to email marketing. According to a survey by email marketing company Campaigner 39 percent of marketers say that the first email content new subscribers see from their brand is a thank-you-for-subscribing message. And those messages work, with almost half reporting that 21 percent or more of new subscribers engage with them. "It takes just seconds within meeting someone to form a lasting impression", says EJ McGowan, general manager of Campaigner. "Unsurprisingly, first impressions for brands are just as critical and time-sensitive. Marketers who… [Continue Reading] -

Free performance health check for Hadoop clusters
Publié: juin 27, 2016, 5:17pm CEST par Ian Barker
Hadoop is one of the most popular frameworks for creating distributed processing environments using commodity hardware. This makes it the first choice for many when implementing big data. However, the nature of this type of system means there are inherent performance limitations. Distributed systems performance specialist Pepperdata is launching Hadoop Health Check, a complimentary, expert assessment that evaluates and diagnoses Hadoop clusters of 100 nodes or more, and provides full visibility into current cluster conditions. When a company signs up for the Health Check program, the Pepperdata software is installed on a production cluster for up to 72 hours. Over that… [Continue Reading] -

New version of CryptXXX ransomware is harder to decrypt
Publié: juin 27, 2016, 3:39pm CEST par Ian Barker
Researchers at endpoint protection specialist SentinelOne have uncovered a new variant of the CryptXXX ransomware family which is being spread via spam and possibly other means. The latest version fixes previous flaws in its file encryption methods which prevents use of free decryption tools and makes it impossible to decrypt files without paying the ransom. As with earlier versions of the ransomware this one hides by copying details from a legitimate .dll file -- in this case one related to CyberLink PowerDVD Cinema. Previous versions used details from a Microsoft dll. It's likely that the cybercrime team behind this variant is… [Continue Reading] -

New platform offers self-service data preparation
Publié: juin 27, 2016, 3:04pm CEST par Ian Barker
Companies are keen to gain the edge that big data can offer, but collecting and analysing information and getting it to a point where it's useful takes time and resources. Cloud integration and big data specialist Talend is launching the latest version of its Talend Data Fabric, a platform designed to meet the integration needs of both developers and business users whether their applications are on-premises or in the cloud. "It's well understood that companies must become data-driven in order to compete, yet there are still several major barriers preventing businesses from making data an organization-wide core competency," says Ciaran… [Continue Reading] -

UK tech industry reacts to Brexit
Publié: juin 24, 2016, 6:07pm CEST par Ian Barker
As the UK awoke this morning -- at least those parts of it that hadn't been glued to the poll results through the early hours -- to find that it had voted to leave the European Union, there was plenty of reaction. While the pound fell and the stockmarket shuddered, technology companies have been quick to add their take on the news. Some were keen to highlight the risks of leaving. Matt Hunt, CEO of Apadmi Enterprise, a leading UK app developer says, "The UK and EU are markets that have continued to offer tech businesses huge growth potential and the… [Continue Reading] -

37 percent of Americans would prefer better automation at work to a better sex life
Publié: juin 24, 2016, 11:16am CEST par Ian Barker
Whether it says more about their work lives or home lives is unclear, but it seems that more than 1 in 3 working Americans would prefer having a better way to automate all their routine work tasks, such as booking meetings, than have a better sex life. What's also interesting is that 44 percent of those were women and 30 percent were men. This is among the findings of a survey by automation specialist Built.io carried out in conjunction with Wakefield Research. It also finds that Americans are willing to give up some personal information in exchange for a more… [Continue Reading] -

How mobile device management could be invading your privacy
Publié: juin 23, 2016, 3:21pm CEST par Ian Barker
Many companies now turn to mobile device management (MDM) to control and monitor their employees' mobile use. But a new study from data protection company Bitglass reveals that MDM itself represents a threat to privacy. Bitglass researchers configured MDM software to route mobile data traffic through a corporate proxy and installed corporate-issued certificates on employee devices to decrypt SSL traffic. This, a common configuration in enterprise MDM deployments for inspecting traffic for malware, enabled researchers to see the contents of employees' personal email inboxes, social networking accounts and even banking information. More of a problem is that the usernames and passwords… [Continue Reading] -

Crypto-ransomware attacks increase five fold
Publié: juin 23, 2016, 12:30pm CEST par Ian Barker
Ransomware has become a big problem in recent years, particularly crypto-ransomware, which encrypts data on users' systems. New research by Kaspersky Lab looking at how it’s evolved over the last two years points to just how big. Among the findings are that the number of users attacked with crypto-ransomware rose 5.5 times, from 131,111 in 2014-2015 to 718,536 in 2015-2016. The total number of users encountering any type of ransomware between April 2015 and March 2016 also increased by 17.7 percent compared to the period April 2014 to March 2015. The share of users encountering ransomware at least once as… [Continue Reading] -

Microsoft launches data protection tool for enterprises
Publié: juin 22, 2016, 5:10pm CEST par Ian Barker
As businesses rely more on mobile and cloud systems, greater emphasis is placed on protecting their information while retaining the productivity benefits. Microsoft is launching a new service to help businesses guard their data as it travels between devices and servers. Azure Information Protection builds on both the existing Microsoft Azure Rights Management (Azure RMS) and the company's acquisition last year of information protection business Secure Islands. The service will allow enterprises to use policies to classify and label data in intuitive ways based on the source, context and content of the data. Classification can be fully automatic, user-driven or based… [Continue Reading] -

Enterprises struggle to manage big data flows
Publié: juin 22, 2016, 4:22pm CEST par Ian Barker
Enterprises of all sizes are facing challenges on a range of data performance management issues from stopping bad data to keeping their data flows operating effectively. This is a finding of a survey by data performance management specialist StreamSets which finds that nearly 90 percent of respondents reported flowing bad data into their data stores, while only 12 percent think themselves good at the key aspects of data flow performance management. Data quality is cited as the most common challenge when managing big data flows (selected by 68 percent). In addition to bad data flowing into stores, 74 percent of… [Continue Reading] -

Strong DevOps performance pays off for businesses
Publié: juin 22, 2016, 11:36am CEST par Ian Barker
High-performing DevOps organizations are widening their lead against lower-performing ones according to a new report. Compared to low performers, high-performing organizations deploy 200 times more frequently, have 2,555 times faster lead times, and recover 24 times faster from failed changes. The findings come from software automation specialist Puppet, which has announced the findings of its latest State of DevOps Report looking at return on investment, how building quality and security into the development cycle affects business outcomes, the role of lean product management, and the relationship between employee engagement and organizational success. Compared to last year, the high performers have… [Continue Reading] -

Lookout uses network layer security to expand mobile protection
Publié: juin 21, 2016, 4:15pm CEST par Ian Barker
The shift towards a mobile and cloud focused workplace has brought a great deal of flexibility but it's also added new risks. How do you protect data when employees can access it at any time and from any device? Lookout, a specialist in securing mobility, has expanded expanded Mobile Threat Protection with the introduction of Network Protection, an automatic on-device analysis of network connections to defend against man-in-the-middle attacks and ensure information is being securely transmitted. Lookout's approach focuses on the risks that are the most relevant to enterprises, namely attempts to intercept, and decrypt data in transit. This allows… [Continue Reading] -

SMBs lack the resources to combat ransomware
Publié: juin 21, 2016, 3:33pm CEST par Ian Barker
Owners of small and medium businesses in the US recognize the potential of ransoware to disrupt their operations, but 84 percent say they wouldn't pay cyber criminals in the event of an attack. Yet the survey by data security company IDT911 also shows that company assets and business operations are left highly vulnerable as nearly 75 percent don't have cyber insurance, or are unsure if their policy includes cyber protection. "Ransomware is the Zika virus of the business world and there is absolutely no telling how far and wide this will spread," says Adam Levin, founder and chairman of IDT911,… [Continue Reading] -

Professional services companies lose thousands to poor document management
Publié: juin 21, 2016, 1:58pm CEST par Ian Barker
You might think that a small amount of time spent looking for documents each day is insignificant. But according to a new survey of accounting, advisory and consultancy firms it could be costing US firms almost $4,000 per employee each month. The study from enterprise collaboration specialist Huddle finds that US respondents work on an average of 26 documents per day spending an average of 89 seconds looking for each one. With an average hourly billing rate of $265, that comes to $3,747 per employee each month. In the UK it's even worse, respondents work on an average of 25… [Continue Reading] -

New release brings on-demand scheduling to field services
Publié: juin 21, 2016, 12:46pm CEST par Ian Barker
The field services industry has already benefited from mobile technology that allows workers to receive new jobs and file reports on the move, reducing the need for returns to base. A new release from mobile workforce management specialists Skedulo takes things further by allowing customers a self-service scheduling ability along with job tracking. Skedulo Lens incorporates APIs and web/mobile SDKs that make real-time scheduling and availability information accessible to end customers on public websites, portals and branded mobile applications. "With today's technology, you can order a car via your mobile device and know exactly who is driving and when they… [Continue Reading] -

Improving data center efficiency [Q&A]
Publié: juin 21, 2016, 11:11am CEST par Ian Barker
With the growth of the cloud, data centers have become big business. In fact, it's estimated that they now use around 10 percent of the world's energy. It's not surprising then that companies are looking to increase the efficiency of their IT operations, cut their energy use and reduce their carbon footprints. However, the solution to finding more efficiency may be closer than they think. Jeff Klaus, general manager of Data Center Solutions at Intel argues that enterprises need to look to home grown solutions before turning elsewhere. We spoke to him to find out more. BN: Is energy efficiency… [Continue Reading] -

USB devices still represent a major security threat for enterprises
Publié: juin 20, 2016, 4:41pm CEST par Ian Barker
With the increasing move to the cloud, it may seem that USB storage devices are becoming obsolete. However, research by endpoint protection company CoSoSys suggests that USB still has a place. The survey of 2016 Infosecurity Europe visitors looks at the use of USB storage devices in the enterprise and the policies governing them. The research found that 74 percent of respondents' organizations allow employees to use USB devices in their networks, yet only 35 percent of companies force employees to use encrypted USB devices. What's surprising in the age of cloud is that 65 percent of employees still use USB… [Continue Reading] -

CCleaner Business Edition: A useful tool for companies with limited support resources [Review]
Publié: juin 20, 2016, 12:59pm CEST par Ian Barker
You’re probably familiar with the free version of the CCleaner system clean up tool. What you might not know is that there’s also a Business Edition aimed at ensuring small and medium business endpoints run efficiently. Like the standard version it can remove unneeded files, recovers hard drive space, speed up Windows, reduces crashes and helps protect privacy and security. Business Edition adds the ability to clean multiple user profiles, it updates itself automatically, supports scripting, and comes with priority technical support. In use When installed CCleaner creates a desktop icon, it also adds itself to the right-click context menu… [Continue Reading] -

The human element still matters in marketing
Publié: juin 17, 2016, 5:18pm CEST par Ian Barker
Marketers are constantly trying to find new ways of engaging with consumers with their message. But although technology is important there still needs to be a human angle. Content creation specialists Ceros and Column Five have taken a look at the ways in which brands are experimenting with their content and using technology to help drive home their message. Among their findings are that 70 percent of marketers believe interactive content is an effective way to engage audiences and that 61 percent of customers feel better about a brand after interacting with custom content. Businesses therefore need to work on… [Continue Reading] -

Why organizations need a risk-based approach to securing payment card data [Q&A]
Publié: juin 16, 2016, 5:13pm CEST par Ian Barker
The Payment Card Industry Data Security Standard (PCI DSS) has done much to cut credit card fraud by ensuring that businesses comply with the rules. But Charles White founder and chief executive of UK-based risk consultancy Information Risk Management (IRM) argues that it has now become little more than a tick box activity which enterprises go through to gain accreditation. Charles spoke to BetaNews about PCI DSS, how businesses need to be doing more to improve their security profiles, and why there are tough times ahead. BN: Why do you feel that the way PCI DSS operates needs to change?… [Continue Reading] -

Most countries unprepared for General Data Protection Regulation
Publié: juin 15, 2016, 4:08pm CEST par Ian Barker
The EU's General Data Protection Regulation (GDPR) intended to strengthen data protection is due to come into force in May 2018, yet new research from content management company Metalogix shows IT professionals in many countries aren't prepared for it. Among the top IT considerations for a cloud archiving solution, GDPR readiness ranked only fourth, named by 26 percent, behind security (79 percent), administrative control (50 percent), and service level agreements (44 percent). IT professionals in the DACH (Deutschland, Austria and Switzerland) region are three times as aware and concerned (77 percent) about the implications of the GDPR as other regions… [Continue Reading] -

New solution helps enterprises keep track of data
Publié: juin 15, 2016, 3:10pm CEST par Ian Barker
Data growth presents a number of problems for enterprises. Aside from the obvious ones like the need for extra storage, there's the risk that employees often unwittingly store sensitive data in unsafe locations within local and network storage, professional email accounts and the cloud. Security software company Ground Labs is launching a new data discovery solution that scans for 100 different data points and personally identifiable information (PII), so organizations can protect critical information at every endpoint without relying on traditional perimeter security methods. Enterprise Recon 2.0 offers accurate and intuitive scanning capabilities that are compatible with a wide array of… [Continue Reading] -

Retailers aren't spending on the right areas to protect data
Publié: juin 15, 2016, 12:28pm CEST par Ian Barker
The retail sector has been the subject of some of the most high profile data breaches in recent years. Add to this the willingness of customers to switch allegiance in the event of a breach and it's clear the industry needs to take security seriously. A new survey from enterprise data protection specialist Vormetric in conjunction with 451 Research focuses on retail companies, detailing IT security spending plans, perceptions of threats to data, rates of data breach failures and data security stances. Among the findings are that 89 percent of IT executives feel vulnerable to data threats and 51 percent… [Continue Reading] -

New automation capabilities help keep IT in control of SaaS
Publié: juin 15, 2016, 11:33am CEST par Ian Barker
Business IT is undergoing a major shift as many organizations get closer to adopting a fully cloud-based approach. But this means that IT departments inevitably give up some degree of control over data governance, security and overall data management. Security automation specialist BetterCloud is launching a new automation engine called Workflows that orchestrates critical, complex processes to ensure accuracy, precision, and compliance across SaaS applications. The first solutions available on Workflows are User Onboarding, User Offboarding, and User Lifecycle Management. These automate the provisioning, deprovisioning and user access within Google for Work applications, giving IT greater control over data, costs and… [Continue Reading] -

IoT has too many devices and not enough security
Publié: juin 14, 2016, 5:33pm CEST par Ian Barker
As Internet of Things devices expand their reach into the enterprise, they make greater demands on security. New research from cyber security specialist ForeScout Technologies reveals that while IT professionals acknowledge the growing number of IoT devices on their networks, they are unaware of how to properly secure them. The survey indicates a lack of visibility into networks. 70 percent of survey respondents don’t have confidence in their ability to see connected devices as soon as they joined their networks, and almost a quarter say that they aren't confident at all. By leaving connected devices out of the security sphere,… [Continue Reading] -

More than half of board members are willing to sack security execs for poor reporting
Publié: juin 14, 2016, 4:17pm CEST par Ian Barker
The decisions that board level executives make on cyber security are very dependent on the quality of the reports they receive from front line management. A new report from cyber risk analysis specialist Bay Dynamics, carried out in conjunction with Osterman Research, looks at how boards of directors see cyber security reports. Among its findings are that 59 percent of board members say that one or more IT security executives will lose their job as a result of failing to provide useful, actionable information. Cyber risks are a high priority among board members compared to other areas such as financial,… [Continue Reading] -

Portworx launches enterprise-class storage for containers
Publié: juin 14, 2016, 3:47pm CEST par Ian Barker
The use of containers has done much to transform the deployment of applications. However, storage hasn't kept pace as it's difficult to scale up to cope with increased workloads. Data storage specialist Portworx is launching new purpose-built, enterprise-class storage solution for containers. PX-Enterprise will enable IT to match the agility of application developers and deliver lower costs compared to legacy solutions. By taking a fundamentally distributed approach, Portworx turns commodity X86 hardware into a converged storage node that can be scaled across a cluster of nodes and automatically provisioned with any Docker-ready scheduler. PX-Enterprise ensures data persistence across nodes, and… [Continue Reading] -

SailPoint extends open identity management platform
Publié: juin 14, 2016, 1:12pm CEST par Ian Barker
Since threats to enterprise systems often come from stolen or compromised credentials, managing user identity is a vital part of modern security. Access control specialist SailPoint is announcing a plugin framework for its SailPoint IdentityIQ platform that will allow customers and partners to develop extensions to the core product features, so they can move towards a more identity-aware organization. It's also unveiled a series of beta plugins, including a privileged account management (PAM) interface designed to extend integrations with leading PAM vendors, as well as plugins from other companies including ColumnIT, Identropy, KOGIT and Regatta. "Our vision for an open… [Continue Reading] -

27 percent of apps connected to corporate environments are risky
Publié: juin 13, 2016, 4:10pm CEST par Ian Barker
As organizations move more of their data to the cloud the risk from shadow IT in the form of connected third-party apps grows greater. New research from CloudLock CyberLab, the security intelligence part of the CloudLock security platform, finds that 27 percent of third-party apps are classified as high risk. This means cyber criminals could gain programmatic access to corporate platforms and impersonate end users. With a 30x increase in apps from 5,500 to nearly 160,000 between 2014 and 2016, this represents a large number of potential backdoors through which hackers can infiltrate and steal sensitive corporate assets. The report… [Continue Reading] -

New application uses behavioral analytics to fight ransomware
Publié: juin 13, 2016, 3:24pm CEST par Ian Barker
Ransomware is one of the most important security threats for business to deal with as it has the potential to cause serious damage and financial loss. User behavior specialist Exabeam is launching its Analytics for Ransomware, a new application designed for early detection across the corporate network. Unlike other security products, Exabeam can detect ransomware movement and activity in the network, servers, workstations, BYOD devices, and cloud services. "Ask any CISO about their biggest challenge today, and ransomware will almost certainly be the response," says Nir Polak, CEO of Exabeam. "It's bypassing security tools and overwhelming already-overburdened security analysts. Exabeam… [Continue Reading] -

Behavioral firewall helps guard against data breaches
Publié: juin 13, 2016, 12:12pm CEST par Ian Barker
When a data breach is just as likely to originate from inside the organization as outside, protecting an enterprise can be a difficult task. Californian company Preempt is launching a new proactive approach that allows organizations to spot threats in real-time without engaging already overwhelmed security teams. Preempt Behavioral Firewall protects enterprises from security breaches and malicious insiders with an approach that couples User and Entity Behavior Analysis (UEBA) with Adaptive Response to provide the most effective solution for both detecting and responding to threats. "According to Verizon's DBIR, in 60 percent of breaches, attackers are able to compromise an… [Continue Reading] -

Collective defense helps security professionals collaborate against cyber crime
Publié: juin 10, 2016, 3:48pm CEST par Ian Barker
To be effective in fighting cyber crime it's important that businesses are able to share intelligence effectively. Endpoint security company Carbon Black is enabling this with its new Detection eXchange, a collective defense ecosystem which will enable thousands of security professionals to collaborate against hackers and prevent cyber attacks. Through the Detection eXchange, Carbon Black customers and partners can collaborate and share 'Patterns of Attack' (POA), threat intelligence encompassing the specific series of behaviors attackers use to compromise systems. These patterns include the root causes of attacks -- such as exploits or vulnerabilities -- and are far more expensive for… [Continue Reading] -

Progressive threat detection guards against attacks from anonymous networks
Publié: juin 10, 2016, 1:01pm CEST par Ian Barker
Cyber attackers use a variety of anonymity techniques to avoid detection. Many attacks come from anonymous proxies and anonymity networks are often use valid, but compromised, credentials. Access control specialist SecureAuth is launching a new Threat Service product to stop suspicious logins even if attackers have valid credentials and even if they are logging in from an anonymous network. SecureAuth Threat Service combines multiple information feeds to protect against today's multifaceted threat landscape including Advanced Persistent Threats (APT), as well as cyber crime and hacktivism. It uses accurate IP geo-location data to map all routable IP addresses worldwide. It enhances a… [Continue Reading] -

The evolution of cloud in the enterprise [Q&A]
Publié: juin 10, 2016, 11:15am CEST par Ian Barker
Over the past few years the cloud has significantly changed the way all of us store data, and in many cases how we run software too. But from an enterprise perspective what impact has the cloud had on traditional data centers, and how is it continuing to evolve? We spoke to Saviz Izadpanah, chief technology officer of HighQ -- which provides cloud collaboration and content publishing services to the world's leading law firms, corporate legal teams and banks -- to find out. BN: What has been the biggest impact of the cloud on enterprises? SI: It has meant that a… [Continue Reading] -

Intel improves its Unite conference room technology
Publié: juin 9, 2016, 4:42pm CEST par Ian Barker
With businesses becoming more geographically dispersed and employees often working on different platforms, conferencing is a vital tool. But the challenge of getting equipment to cooperate can result in loss of time and productivity. Chip maker Intel had this issue in its own business and came up with an in-house solution to solve the problem. Intel Unite improved the company's meeting set-up time by 70 percent and was made available to other businesses. Now it wants to make Unite more attractive with some new enhancements to the product. Intel Unite allows any PC to wirelessly connect to existing monitors, whiteboards and projectors… [Continue Reading] -

Partnership deal aims to help businesses transform using big data
Publié: juin 9, 2016, 4:07pm CEST par Ian Barker
Many businesses are keen to exploit the advantages of big data, but they struggle to find the resources needed to do so. A new partnership between management consultancy Boston Consulting Group (BCG) and analytics specialist Mu Sigma aims to let clients exploit cutting-edge big data and analytics solutions to transform the way they do business. The partnership will enable organizations across all industries to gain a powerful set of capabilities to pursue business transformation supported by waves of data analytics. It will allow companies to make data-driven decisions and adds the ability to build a sustainable capacity for analytics and decision… [Continue Reading] -

New solution adds machine learning analytics to VMware environments
Publié: juin 9, 2016, 3:13pm CEST par Ian Barker
With virtualized environments performance issues can be hard to pinpoint. IT departments can find it difficult to spot whether the cause is in the application, network, storage, or virtualization layer of the infrastructure. Software optimization specialist SIOS is bringing machine learning to bear on this problem with the latest release of SIOS iQ, its analytics software for VM environments. The new release integrates SIOS iQ with SQL Sentry Performance Advisor, bridging a critical gap between IT infrastructure administrators and SQL Server administrators. For the first time, IT staff can easily identify and resolve the root causes of performance issues based on analysis… [Continue Reading] -

New breed of 'super hunters' earn thousands from bug bounty programs
Publié: juin 8, 2016, 5:08pm CEST par Ian Barker
With data breaches still making headlines and security teams facing increased pressures it's not surprising that companies are looking for innovative ways to find flaws in their systems. Crowdsourced security specialist Bugcrowd has released the results of its second annual State of Bug Bounty Report which shows that the number of bug bounty programs hosted on its platform is up by an average of 210 percent year on year since January 2013. Among its other findings are that larger enterprises are increasingly adopting bug bounties. Companies with 5,000+ employees accounted for 44 percent more of the total companies launching bug bounty… [Continue Reading] -

More than half of enterprises believe cloud apps are as secure as on-premise
Publié: juin 8, 2016, 4:18pm CEST par Ian Barker
In the past there's tended to be a perception that running applications in the cloud is less secure than keeping them in-house. However, a new study by data protection company Bitglass suggests that this view is changing as cloud apps mature. 52 percent of organizations are now confident that cloud apps are as secure as premises-based apps, up from 40 percent a year ago. Among the report's other findings are that Google continues to lose market share to Microsoft within the enterprise. Now 61 percent of organizations have existing or planned Office 365 deployments, up from 45 percent last year.… [Continue Reading] -

New enterprise collaboration platform uses social network technology
Publié: juin 8, 2016, 3:40pm CEST par Ian Barker
There are lots of business collaboration tools on the market, but a new offering from UK-based Connectik aims to combine productivity features with the ease of use of a social network. Connectik's newly launched hub allows enterprises to create a social network with their customers, staff and business partners, while also serving as an internal collaboration and productivity tool. Designed to be a social-first network, Connectik offers engagement features that allow businesses to create groups, publish updates, run polls, distribute messages and analyze engagement data. The collaboration features in the hub also include project administration and productivity monitoring, as well as… [Continue Reading] -

New platform enables faster delivery of smart apps
Publié: juin 8, 2016, 10:07am CEST par Ian Barker
New technologies like big data and machine learning are beginning to revolutionize business, but they place increasing demands on the technical expertise needed to exploit them. Development platform Mendix is launching its latest version, Mendix 7, that will allow businesses to build Smart Apps to improve operations, deliver differentiated services and create new business models. Using Mendix's open platform ecosystem, the software provides drag-and-drop connectors to leading IoT, big data and machine learning platforms and services including AWS and IBM Watson. Without writing any code, developers can use these component services to make connected things and insights actionable, and deliver… [Continue Reading] -

New free security scanner checks Internet of Things devices
Publié: juin 7, 2016, 5:34pm CEST par Ian Barker
Protecting yourself online is no longer just about your PC and your mobile phone. There are now a whole host of other devices which are potentially vulnerable. Internet security specialist BullGuard is launching a new, free tool for consumers that reveals connected devices which could be vulnerable to hackers. If a user's smart device is flagged as being vulnerable, details about the specific security issues are provided. BullGuard's IoT Scanner uses data from Shodan.io, the first search engine for internet connected devices, to scan for vulnerable smart devices and presents results in a straightforward way that anyone can understand. It can… [Continue Reading] -

Lookout and Microsoft partner to protect enterprise mobile
Publié: juin 7, 2016, 4:55pm CEST par Ian Barker
The world is becoming increasingly mobile first and businesses need to ensure that their data is protected however it’s accessed. Mobile security specialist Lookout has announced that it's partnering with Microsoft to deliver integration of its Lookout Mobile Threat Protection with Microsoft's Enterprise Mobility Suite. When mobile threats are detected, the integration between Lookout and Microsoft EMS will enable companies to take action to protect data across users, devices and applications. Companies will have the ability to incorporate threat intelligence from Lookout into the conditional access policies that they have set up in Microsoft EMS, to manage and secure access… [Continue Reading] -

Enterprises struggle to evaluate security risks
Publié: juin 7, 2016, 4:24pm CEST par Ian Barker
Many organizations rely on the Common Vulnerability Scoring System (CVSS) to evaluate cyber risks, but a new report suggests that relying on the score alone is not enough. NopSec, a provider of cybersecurity precision threat prediction and remediation solutions, has released its 2016 State of Vulnerability Risk Management report. This suggests that in addition to CVSS, subscores combined with other factors such as context, social media trend analysis, and data feeds deliver a better risk evaluation and prioritization. "Relying only on the CVSS score to drive prioritization for applying patches needs to change. Organizations need to align the patching methodology… [Continue Reading] -

82 percent of IT pros think Windows 10 would make their company more secure
Publié: juin 7, 2016, 2:51pm CEST par Ian Barker
Security is an ongoing struggle for businesses and many data breaches can be traced back to the use of out of date software. A new survey from systems management company Adaptiva asked more than 150 IT pros their feelings about their enterprises' security, and found that the majority were concerned about potential vulnerabilities. Among the key findings are that 82 percent of IT pros think moving to Windows 10 would make their company more secure. 70 percent of respondents are concerned about potential security vulnerabilities in their Microsoft SCCM environment and almost two-thirds (65 percent) of respondents plan to conduct… [Continue Reading] -

The software-defined data center goes mainstream
Publié: juin 7, 2016, 12:35pm CEST par Ian Barker
The software-defined data center is gaining widespread adoption across a range of industries according to a new report. The survey of 500 industry executives by security controls specialist HyTrust finds that many areas of operation including mission critical systems are now moving to a virtualized delivery model. "Without much fanfare, this critical technology advance has become woven into the basic fabric of businesses large and small," says Eric Chiu, president of HyTrust. "The potential of virtualization and the cloud was always undeniable, but there was genuine concern over security and skepticism regarding the processes required. What we find in this… [Continue Reading] -

Inateck BH1101 and BH1105 earphones [Review]
Publié: juin 3, 2016, 1:49pm CEST par Ian Barker
Over the past few years Inateck has made a name for itself with good value audio kit including headsets and Bluetooth speakers. Its latest offerings are in the closely-contested earphone market, so how well do they measure up to more established players? The BH1105 is the budget option and, a little unusually these days, just a set of headphones, there's no in-line mic to use with a smartphone. The design is a little different too, with the body of the phones being made of wood. Zebrawood to be precise -- if you thought zebras were made of meat you're correct,… [Continue Reading] -

Mobile workforces put businesses at increased risk
Publié: juin 3, 2016, 12:13pm CEST par Ian Barker
A more and more mobile workforce is leaving US businesses vulnerable to increased risk of data breaches and theft of information. This is highlighted in a survey of executives and small business owners by secure data destruction company Shred-It. Among the findings are that 92 percent of C-Suite Executives have at least some employees using a flexible or off-site working model, but only 31 percent of these executives say they have an information security policy for both off-site work environments and flexible working areas in place. Small businesses by comparison have at least some employees using a flexible/off-site working model… [Continue Reading] -

Five tips to avoid becoming a ransomware victim
Publié: juin 2, 2016, 3:48pm CEST par Ian Barker
Ransomware is one of the major threats computer users now face, even though recent reports suggest that many people don't actually know what it is. Delivered via spam or phishing emails that trick users into clicking on malicious links, ransomware renders computer systems, devices or files inaccessible and holds the victim hostage until payment is made, usually in the form of bitcoins. "Victims are faced with the choice of paying up or losing all their valuable data forever. Unfortunately, this approach works for cybercriminals, because consumers and businesses are unprepared for their data -- whether it's a business' intellectual property… [Continue Reading] -

Oukitel’s K4000 gets maxed out
Publié: juin 2, 2016, 3:10pm CEST par Ian Barker
When we reviewed the Oukitel K4000 Pro toughphone last month it came with a pretty standard Android UI. Latest versions of the K4000 though will come with a new 'max' interface that puts fewer but larger icons on each screen. It also offers a bigger dial pad, so the phone should appeal to older users and to others who struggle to cope with smaller icons. The main screen puts three fixed apps at the bottom of the screen for phone functions and displays six more of the user's choice above. Users can set eight frequently used numbers too, each with… [Continue Reading] -

SWIFT attacks date back more than a year
Publié: juin 2, 2016, 11:57am CEST par Ian Barker
We reported a few days ago on banks using the SWIFT inter-bank transfer system being hacked, resulting in $81 million being stolen from the Bangladesh Central Bank. Now Luis Corrons, technical director of PandaLabs, has released more information on other banks affected, with attacks that stretch back more than a year. In addition to the Bangladesh attack in February, Vietnamese Tien Phong Bank suffered a similar attack in the last Quarter of 2015, where cybercriminals also tried to make transfers through SWIFT, although the bank realized in time and halted the million dollar transfers already en route. A few months… [Continue Reading] -

Revealing the security habits of cyber criminals
Publié: juin 1, 2016, 3:41pm CEST par Ian Barker
Cyber crime is big business and that means the people behind it face many of the same challenges as legitimate organizations. This includes operational security (OPSEC), a key tactic used by commercial and military organizations to protect privacy and anonymity. Research from cyber situational awareness specialist Digital Shadows reveals that criminals are using OPSEC as a means to an end -- avoiding detection, maintaining availability of their attack infrastructure, and retaining access to environments they have compromised. Just as with other enterprises, criminals stand to lose from poor OPSEC. For example, Dridex botnet operator Andrey Ghinkul associated his nickname --… [Continue Reading] -

HP Enterprise launches new application lifecycle management tool
Publié: juin 1, 2016, 12:55pm CEST par Ian Barker
In order to keep up with a rapidly changing market landscape and deliver better customer experiences, organizations are building and enhancing software and mobile applications at a rapid rate. This is leading businesses to rethink their internal software development processes in order to support development methodologies like Agile, Lean, and DevOps. To help customers accelerate their DevOps processes, Hewlett Packard Enterprise is launching HPE ALM Octane, an Application Lifecycle Management (ALM) solution that leverages widely-used developer toolsets like Jenkins and GIT to bring continuous quality to lean, Agile, and DevOps-focused teams. HPE ALM Octane aims to provide insights to developers… [Continue Reading] -

Security vulnerabilities in top UK companies exposed
Publié: juin 1, 2016, 12:14pm CEST par Ian Barker
Cyber security affects all of us, but it only makes the headlines when it's big companies that are the target of attacks. Threat intelligence provider Anomali has produced a new study focusing on vulnerabilities in businesses on the UK's FTSE 100 list of the largest companies. Among the findings are that over the last three months, 81 companies in the FTSE 100 had potentially malicious domain registrations against them, enabling cyber criminals to create dummy websites that can be used to trick users into supplying private data. The report also discovered that 5,275 employee email and clear text password combinations… [Continue Reading] -

The challenge of creating high performance, fault tolerant storage [Q&A]
Publié: mai 31, 2016, 5:56pm CEST par Ian Barker
The growth of the Internet of Things, increased reliance on analytics to support decision making, and greater use of video means businesses are storing more and more data. That data has become a crucial asset and storing it so that it's accessible and safe is a major challenge. Solutions from major vendors are costly but data storage operating system specialist RAIDIX has come up with a product that can offer fault tolerance on commodity hardware. We spoke to Sergey Platonov, product owner at RAIDIX to find out more about the solution and why data storage is now a major challenge.… [Continue Reading] -

Research finds critical out-of-the-box vulnerabilities on big name laptops
Publié: mai 31, 2016, 4:58pm CEST par Ian Barker
When you buy a new PC it inevitably comes with a range of extra software -- bloatware if you will -- ranging from the maker's own updater tools to trials of antivirus and other products. Trusted access provider Duo Security has carried out some research into how this extra software could be making users more vulnerable and invading their privacy. It tested a total of 10 new laptops from Acer, Asus, Dell, HP and Lenovo and found that all the vendors had at least one vulnerability that allowed for a complete compromise of the affected machine. Most of the vulnerabilities… [Continue Reading] -

Updated solution to improve control over enterprise data use
Publié: mai 31, 2016, 3:03pm CEST par Ian Barker
As organizations rely more and more on data, so keeping it secure and making sure it can only be accessed by the appropriate people becomes increasingly important. To address this, identity and access management company SailPoint is launching an updated version of its SecurityIQ solution that provides an integrated and comprehensive approach to governing all data in the enterprise. SecurityIQ will allow enterprises to manage unstructured data that exists in many different formats and locations. This allows them to meet new challenges to both controlling and governing access to information. For example, compliance with the European General Data Protection Regulation (GDPR) which… [Continue Reading] -

The need for change in combating ransomware and other threats [Q&A]
Publié: mai 27, 2016, 3:50pm CEST par Ian Barker
The security landscape is one that is constantly changing and old-style signature-based detection systems are struggling to keep up. But what are the main threats today and how can companies and individuals combat them? We spoke to Tomer Weingarten CEO of next-generation security specialist SentinelOne about ransomware and what the LinkedIn hack means for the future of password security. BN: Why is ransomware so hard to tackle? TW: It's one of the most common problems in security today, the main reason is not because it's complicated but mostly because it's lucrative to cyber criminals. Ransomware is a very effective mechanism to… [Continue Reading] -

Control of usage and costs is biggest challenge to public cloud
Publié: mai 27, 2016, 12:15pm CEST par Ian Barker
A new survey by cloud analytics company Cloud Cruiser and Dimensional Research shows that the top challenge with public cloud consumption is the ability to proactively manage usage and costs across the business. The survey among almost 200 professionals who attended the Amazon Web Services (AWS) Global Summit in April also reveals that nearly one third of organizations are doing nothing to track, manage and allocate cloud consumption costs. "The survey results show that, despite significant investment in public cloud, IT continues to struggle with technologies that will help them analyze public cloud usage," says David Gehringer, principal at Dimensional… [Continue Reading] -

Better online security or faster internet, which would you choose?
Publié: mai 26, 2016, 3:05pm CEST par Ian Barker
Your answer probably depends on how old you are. According to a new survey 57 percent of Americans would take the better security. However, where millennials are concerned 54 percent would rather improve their internet speed. This is among the findings of a new survey by adaptive access control company SecureAuth Corporation and Wakefield Research. Gender and education make a difference too, while men are split fairly evenly between personal online security (51 percent) and speed (49 percent) significantly more women care about online security (62 percent). When it comes to education, 63 percent of college graduates care about security,… [Continue Reading] -

Brazil a major cyber security risk ahead of Olympics
Publié: mai 26, 2016, 12:26pm CEST par Ian Barker
There have been plenty of concerns in the news over Brazil's readiness to host this year's summer Olympics, ranging from the Zika virus and political unrest to poor ticket sales. A new report from BitSight Technologies highlights cyber security concerns too with security performance of companies in Brazil among the worst in the developed nations, meaning business dealings in this region could come with serious risk. BitSight researchers analyzed the security performance of a random sample of 250 companies per country from the United States, the United Kingdom, Singapore, Germany, China and Brazil. They used this information to create a… [Continue Reading] -

Malwarebytes extends enterprise endpoint detection system to include Macs
Publié: mai 26, 2016, 11:32am CEST par Ian Barker
Although Macs have been relatively immune to malware, they have faced nuisance apps like adware and PUPs for years, and new threats are appearing, including ransomware like KeRanger. Experts believe it's only a matter of time before the next big attacks against Macs surface. With more companies turning to Macs and a rising number of new threats, concern about the possibility of widespread Mac vulnerabilities is on the rise. Malware protection specialist Malwarebytes is responding to this by extending its Breach Remediation platform to cover Mac systems. "The idea that Macs are inherently safe and immune to malware and other… [Continue Reading] -

The container market is about more than just Docker
Publié: mai 25, 2016, 5:51pm CEST par Ian Barker
When containers are mentioned, Docker is probably the system that comes to mind. But in fact the container market is much bigger than that with over 100 products that use containers to amplify the benefits of agile development for their users. Of those, 20 come from public companies and over 70 from private companies, which collectively represent $1.7 billion in venture capital funding. 88 percent of enterprises say they're shifting to a DevOps strategy, and containers are changing the nature of DevOps and transforming infrastructure. It's an important and complex market then, and developer tools company Codenvy has produced its… [Continue Reading] -

Ransomwhat? 43 percent don't know what ransomware is
Publié: mai 25, 2016, 12:36pm CEST par Ian Barker
A new report shows that 43 percent of consumers in the US and Canada don't know what ransomware is. A similar number (44 percent) say they don’t know what data or information could be stolen in a ransomware attack. The study by Kaspersky Lab surveyed 4,000 US and 1,000 Canadian consumers aged over 16 and found that only 16 percent mentioned ransomware as a cyber threat they were worried about, compared to their concerns about viruses, spyware and Trojans. Even among the supposedly tech-savvy millennial generation only 13 percent said they were worried about ransomware in general. Also, many respondents… [Continue Reading] -

People want safer alternatives to passwords and they want them now
Publié: mai 25, 2016, 12:18pm CEST par Ian Barker
As the recent leak of LinkedIn data shows, passwords are an increasingly vulnerable and flawed way of securing systems. A new survey from identity management specialist Gigya reveals that consumers are beginning to recognize this and that 52 percent would choose anything but a traditional username and password account registration when given the option. The survey of 4,000 people split between the US and UK finds that 29 percent prefer using two-factor authentication and 20 percent prefer biometric authentication. Biometrics is belived by 80 percent of those expressing a preference to be more secure than traditional methods. "Within the next… [Continue Reading] -

Putting the 'twit' in Twitter? Will changes flood your feed with unwanted messages?
Publié: mai 24, 2016, 5:10pm CEST par Ian Barker
Over the decade since it launched, Twitter has evolved from simple 140 character text messages to incorporate photos, videos and more. It can also justifiably lay claim to introducing and popularizing the hashtag. In an effort to keep the service up to date the company is rolling out some changes in the coming months. While some of these are useful, others are set to prove unpopular, especially for those who follow business accounts. First the good news, for the first time you'll be able to retweet and quote yourself, allowing you to draw attention to messages you think may have… [Continue Reading] -

Druva releases pay-as-you-go disaster recovery
Publié: mai 24, 2016, 4:32pm CEST par Ian Barker
Disaster recovery solutions have usually been a fixed cost for business, involving paying for a fixed amount of storage whether you actually used it or not. Data protection specialist Druva is launching new usage-based pricing for its Phoenix public cloud solution for backup, archive and disaster recovery. There are no additional hardware or software costs and enterprises will now pay only for the actual storage they consume. "As organizations move more and more compute to the cloud, they are discovering innovative ways to better leverage their data to increase business value. With Phoenix we continue to drive this innovation --… [Continue Reading] -

Brits are willing to compromise their online security to get fit for the beach
Publié: mai 24, 2016, 3:49pm CEST par Ian Barker
With the approach of summer, many people are looking for diet and fitness solutions to get themselves ready for the beach. But research into the practices of 1,000 British internet users by Intel Security finds a willingness to compromise online security to achieve a dream body. Among the findings are that 34 percent are willing to sacrifice online safety to get a flat stomach, clicking on potentially malicious websites offering to help 'lose belly fat' specifically. Promotional sites offering to help with weight loss are the number one site Brits admit they would click on to help achieve their goals.… [Continue Reading] -

New healthcare platform addresses communications compliance challenges
Publié: mai 24, 2016, 3:08pm CEST par Ian Barker
The healthcare and pharmaceutical industries are highly regulated and need to constantly keep up with changing demands and regulations. California-based Actiance, specialists in communications compliance, analytics and archiving, has launched a new cloud-based platform aimed at the health sector which addresses new and existing regulatory retention, security and privacy requirements, while reducing the risk and expense of costly eDiscovery and compliance activities. As new communications channels and networks become available to the healthcare and pharmaceutical industries, records management responsibilities become even more critical. Implementing new communications and social channels without safeguards and processes in place exposes firms to non-compliance with… [Continue Reading] -

Medical devices targeted by cyber attacks
Publié: mai 20, 2016, 12:37pm CEST par Ian Barker
Hacking and cyber attacks are no longer confined to computers. Thanks to the Internet of Things they affect a whole lot of other equipment too and that includes medical devices. Application protection specialist Arxan has produced an infographic looking at the growing threat landscape surrounding connected medical devices. Among its findings are that a worrying 94 percent of healthcare organizations have been victims of a cyber attack. Vulnerabilities include patient data theft, manipulation of therapy with the potential to harm patients, and malware infections that can spread throughout a healthcare network. Headline attacks include a patient who was able to… [Continue Reading] -

How can enterprises streamline the migration of data? [Q&A]
Publié: mai 20, 2016, 11:12am CEST par Ian Barker
Businesses are under increasing pressure to replace legacy storage with cloud and hybrid options in order to modernize their infrastructure and cut costs. Migrating data presents a number of challenges and IT teams are turning to automation in order to address them. We spoke to Jonathan Huberman, CEO of specialist in the hybrid enterprise file sync and share market, Syncplicity, to find out more about how enterprises can move their data smoothly and make it available across a number of devices. BN: How can you guarantee integrity when data is drawn from multiple sources? JH: Data sync tools need to be… [Continue Reading] -

Brands fail to meet mobile communication expectations
Publié: mai 19, 2016, 5:00pm CEST par Ian Barker
Brands aren't doing enough to meet their customers' expectations for mobile communication, according to a new survey. The study, by web convergence company tyntec and technology research specialist Ovum, of 1000 people in the US and Germany finds that customers prefer to interact with customer service agents using different communication channels depending on where they are in the transaction process, and that they expect service providers to be effective using mobile. New IP-based communication channels like OTT chat apps (over-the-top apps that bypass carrier charges for texting, WhatsApp for example) are identified as a significant untapped opportunity, with 50 percent… [Continue Reading] -

Compliance struggles to keep pace with new communications channels
Publié: mai 19, 2016, 3:51pm CEST par Ian Barker
Compliance professionals need to supervise all types of business communications, but a new survey shows that they're struggling to keep pace with the volume and variety of electronic channels. Hosted archiving specialist Smarsh has released its sixth annual Electronic Communications Compliance Survey Report. The survey, of compliance professionals in the financial services industry, highlights that supervision practices aren't sufficiently addressing the compliance implications of ongoing trends, like increased regulatory scrutiny and the challenge of adapting to channels like social media and text messaging. Among the findings are that over 40 percent of firms that enable employees to use LinkedIn and… [Continue Reading] -

The challenge of securing smart buildings from cyber attack [Q&A]
Publié: mai 19, 2016, 12:39pm CEST par Ian Barker
As more and more devices get added to the Internet of Things the risks they present get larger. A recent report from the BBC has highlighted the fact that buildings and their systems for heating, lighting and even security may be at risk. We spoke to Péter Gyöngyösi, product manager of Blindspotter at contextual intelligence specialist Balabit, to find out more about the risks smart buildings present and how landlords and tenants can guard against them. BN: How big a problem is security for smart buildings and is it going to get worse? PG: I believe it is indeed a… [Continue Reading] -

Four-year-old LinkedIn IDs go up for sale online
Publié: mai 18, 2016, 5:06pm CEST par Ian Barker
Cast your mind back to 2012 and the LinkedIn hack that had the grown up's social network scurrying to advise its users to change their passwords. It was thought at the time that the 6.5 million sets of credentials posted on a Russian password forum was the extent of the breach. However, four years on a hacker under the name of 'Peace' is offering for sale a database of millions more LinkedIn accounts. The data on offer includes the email addresses, plus hashed -- and in some cases already cracked -- passwords of 117 million users. Details of the sale,… [Continue Reading] -

Peephole attack could leave more than a billion Android devices open to clickjacking
Publié: mai 18, 2016, 12:46pm CEST par Ian Barker
Earlier this year we reported on the risk Android devices faced from a technique called Accessibility Clickjacking which would allow attackers to monitor all of a user's activity. At the time of that story the company that uncovered the vulnerability, Skycure, thought that it could affect around half a billion devices. It now believes that despite additional protection being added from Android Lollipop, more than a billion devices may be at risk. Android Accessibility Services provide interface enhancements to help users interact with their devices. It offers the ability to draw over apps which allows graphical overlays to programs that… [Continue Reading] -

Birst delivers enhanced analytics capabilities
Publié: mai 17, 2016, 6:00pm CEST par Ian Barker
Companies are increasingly turning to analytics to gain a competitive advantage and help with customer retention. But a recent study from cloud analytics specialist Birst reveals that half of the companies surveyed that attempted to create in-house analytics products reported being unsatisfied with the results. To meet demand for reliable analytics products, Birst has announced new capabilities that boost time-to-market and deliver improved user experiences. Features include new JavaScript APIs which enable third-party applications to interact with Birst using bi-directional data filters. This means applications can dynamically update based on events and data signals that happen in Birst, but also… [Continue Reading] -

Dell launches zero-day protection for thin clients and virtual desktops
Publié: mai 17, 2016, 3:53pm CEST par Ian Barker
Endpoint protection is still vital for enterprises of all sizes. Dell is launching new security products aimed at giving businesses advanced threat prevention for Windows Embedded thin clients and virtual desktops. Using IP from its award-winning Dell Data Protection portfolio of security solutions, Dell is applying its endpoint security expertise beyond the PC to the thin client and virtual machines. The company claims this will give customers an industry-first approach to comprehensively securing their data. "While other vendors depend on a 'detect and remediate' approach that alerts IT staff to an attack after the damage has been done," says Jeff… [Continue Reading] -

Cloud security concerns rise as investment grows
Publié: mai 17, 2016, 10:56am CEST par Ian Barker
Industry predictions suggest that the world cloud market will exceed $250 billion by 2020, but a new report shows that as cloud investment grows so do security concerns. Crowd Research Partners has released the results of its 2016 Cloud Security Spotlight Report, created in conjunction with leading cloud security vendors Alien Vault, Bitglass, Cato Networks, CloudPassage, Dell Software, Dome9 Security, IMMUNIO, (ISC)2 and Randtronics. Among the findings are the main barriers to cloud adoption, led by general security concerns (53 percent, up from 45 percent in last year's survey), legal and regulatory compliance concerns (42 percent, up from 29 percent), and… [Continue Reading] -

The UK's year in business continuity disasters
Publié: mai 16, 2016, 5:19pm CEST par Ian Barker
All businesses should worry about how they'll keep going in the event of a disaster. But those disasters aren't always internal, they can be due to outside forces and can be hard to predict. As part of this week's Business Continuity Awareness Week 2016 organized by the Business Continuity Institute, managed services company IT Specialists (ITS) has produced a list of the top 10 UK business continuity disasters of the last year. These include the Holborn fire, which burned in an underground service duct and left 5,000 London properties without power. Other problems were caused by storms and floods affecting power… [Continue Reading] -

More than half of businesses are in digital denial
Publié: mai 16, 2016, 12:34pm CEST par Ian Barker
Businesses are under increasing pressure to improve their customer experiences and make more effective use of their digital communication channels. Yet new research from apps, data development and integration company Progress shows that 62 percent of respondents believe their business is in denial about the need to transform digitally. What's more 70 percent of UK-based respondents think that reliance on the IT team is the biggest barrier to delivering a good customer experience. Globally 72 percent think IT is most likely to be the final decision maker for digital initiatives. Better collaboration between IT and marketing is needed to deliver… [Continue Reading] -

New solution targets threats to containerized apps
Publié: mai 12, 2016, 3:44pm CEST par Ian Barker
Running applications in containers is increasingly popular, but whilst it offers benefits in terms of the flexibility to run apps anywhere, it raises fresh challenges for keeping them secure. A new set of automated capabilities that defend against active threats targeting container environments is being launched by security solutions company Twistlock. Twistlock Runtime is fully automated and designed to detect and stop sophisticated runtime attacks -- including APTs and zero-day exploits. It uses a 'declarative' security model to build runtime protection. It performs static and dynamic analysis of container images and derives a set of declarative 'DNA' profiles for the containers.… [Continue Reading] -

New Webroot solution uses threat intelligence to secure IoT gateways
Publié: mai 12, 2016, 3:01pm CEST par Ian Barker
As the Internet of Things takes off, gateways are increasingly being used to connect legacy and next generation devices, but they often don't have the security features to protect critical infrastructure. Endpoint security specialist Webroot is launching a new threat intelligence solution for IoT gateways to secure them against advanced and persistent network based threats. Called BrightCloud Threat Intelligence for IoT Gateways, the service will enable IoT Solution providers, platform providers, and managed security service providers (MSSPs) to secure their systems. By utilizing tens of millions of threat sensors around the world, it can analyze new threats and exploits as… [Continue Reading] -

90 percent of financial services IT security pros fear security breaches
Publié: mai 12, 2016, 11:21am CEST par Ian Barker
A new survey of IT security professionals working in the financial services sector reveals that 90 percent feel vulnerable to security breaches and 44 percent have actually experienced one -- 19 percent in the last year. These findings come from enterprise data protection specialist Vormetric which, in conjunction with 451 Research, has issued a financial services edition of its 2016 Data Threat Report. Meeting compliance requirements was named as the top IT security spending priority at 56 percent, but preventing data breaches at 50 percent and best practices, also at 50 percent, were close followers. The main barriers to adoption… [Continue Reading] -

Businesses want advanced analytics but have low confidence in their data
Publié: mai 10, 2016, 4:37pm CEST par Ian Barker
A new report from data quality management company Blazent and 451 Research shows a disconnect between businesses' desire to pursue machine learning analytics and the quality of their data. The poll, of 200 C-level and senior IT leaders, reveals that despite the 67 percent of respondents that have a strong appetite for advanced analytics technologies, 60 percent have low confidence in their organization's data quality management practices. The findings show the pace of adoption for more sophisticated algorithmic analysis is accelerating more quickly than originally anticipated, with 22 percent of respondents already having a program in place and 42 percent… [Continue Reading] -

Outdated software on BYOD devices puts business data at risk
Publié: mai 10, 2016, 3:34pm CEST par Ian Barker
When people used office workstations managed by the IT department it was relatively easy to manage security because there was a defined perimeter. In the modern era of mobile devices and BYOD though security becomes much harder. Authentication specialist Duo Security has released a new report on the security health of user devices, based on data gathered from more than two million devices used by businesses worldwide. Among its findings are that a quarter of all Windows devices are running outdated and unsupported versions of Internet Explorer. Around two percent of Windows devices are running versions of the OS which… [Continue Reading] -

Brands are not ready to meet consumer mobile expectations
Publié: mai 10, 2016, 12:59pm CEST par Ian Barker
New research shows that a majority of brands are unprepared when it comes to implementing a mobile strategy and aren't allocating enough resources to improve the mobile experience to meet consumer expectations. The study by experience management software company Sitecore shows that although 97 percent of brands believe a good mobile experience impacts customer loyalty, 41 percent of respondents have either no mobile strategy in place at all, or have a mobile strategy that has yet to be implemented. In addition, 70 percent of these brands believe that their organization will not deliver on a mobile experience strategy for at… [Continue Reading] -

Cyber criminals love to attack hotel chains
Publié: mai 9, 2016, 4:27pm CEST par Ian Barker
Hotels represent rich pickings for cyber criminals. There's the potential to steal information from large numbers of customers with consequent financial gains. Researchers at Panda Security have issued a report showing the major attacks targeted against hotel chains in 2015. These attacks are against chains of all sizes and have resulted in the theft of credit card data from thousands of customers. In many cases this has been carried out using malware-infected POS terminals. In a recent instance spear phishing has been used to target one of Panda's Adaptive Defense 360 luxury hotel clients. "We know that, in most cases,… [Continue Reading] -

Open source framework enables native mobile app development
Publié: mai 6, 2016, 1:01pm CEST par Ian Barker
Although HTML5 has allowed apps to work across platforms, there's still demand for companies to develop native apps for the major mobile platforms. Progress Software is launching the latest version of NativeScript, an open source framework on the Telerik platform, enabling developers to use JavaScript to build native mobile apps running on the major mobile systems. With the release of NativeScript 2.0, developers using Google's Angular 2 JavaScript framework can now write native mobile applications for iOS and Android. They can reuse existing skills and code from the web and achieving time and cost-efficiencies. "Angular integration first shipped with our popular… [Continue Reading] -

Looker launches analytical apps for business
Publié: mai 5, 2016, 5:29pm CEST par Ian Barker
Data is the lifeblood of most areas of business, but often companies end up with isolated analytics tools used by different departments and no central overview. Analytics specialist Looker is launching a range of new apps that can meet the needs of individual departments but which all deploy on the Looker Data Platform, so an entire company can use Looker to understand each aspect of their business with up-to-the-minute data to make data-driven decisions. "Data should be transformative for businesses, but outdated tools and inflexible out-of-the-box solutions often handcuff business users from access to the valuable insights they want and… [Continue Reading] -

The rise of the virtual CIO [Q&A]
Publié: mai 5, 2016, 5:16pm CEST par Ian Barker
The role of chief information officer has become entrenched in large organizations, but smaller businesses often can't afford to employ one. This means that they miss out on the expertise a CIO can bring, but also lack representation of IT at board level. In some cases businesses are getting around this by outsourcing the role to a 'virtual CIO' who may only be needed for one or two days a month, so they can also work across multiple organizations, and from different locations. We spoke to Dean Coleman, head of service delivery at service management specialist Sunrise Software to find out… [Continue Reading] -

Attack researchers are top target of DDoS activity
Publié: mai 5, 2016, 11:30am CEST par Ian Barker
We all know that the cyber security world is a constant war of attrition, but it seems that DDoS attackers are targeting those firms which represent a direct threat to their business model. According to a new report from cyber security company Nexusguard, an attack research group, Loryka LLC, was the number one target in the first quarter of this year, with 90 DDoS attacks. "Researchers and their related groups are becoming high-valued targets for digital criminals. We have seen this in the past, but never as a primary target for a whole quarter, making the findings in this quarterly… [Continue Reading] -

Having a 5-incher means you spend more time in apps
Publié: mai 4, 2016, 4:14pm CEST par Ian Barker
It seems that size really does matter -- at least when it comes to the size of the screen on your smartphone. New research shows that people spend more time in apps if they have a larger screen. The study from mobile engagement platform Localytics shows that 5-inch devices show 23 percent more app engagement than smaller screens. They also show 3.53 percent higher average session length than 4-inch screens. On 5-inch screens people spend 66 minutes in each individual app per month, as opposed to 52 minutes a month in each app on 4-inch screens. Also users launch apps… [Continue Reading] -

New platform uses machine learning to streamline mobile development
Publié: mai 4, 2016, 3:18pm CEST par Ian Barker
Businesses are under increasing pressure to create mobile apps, but often lack the resources to do so effectively. Workplace mobility specialist PowWow Mobile is launching a new platform that lets users build apps faster and with less code. SmartUX Studio is designed to easily transform functional web-based or Windows business applications into intuitive, modern mobile app experiences. Using a machine-learning engine it adds the legacy application's features and UI components to a drag-and-drop menu so users can quickly assemble mobile applications, saving on design and re-development time. It includes a SmartStudio, enabling the use of mobile-first features that consumers are used to,… [Continue Reading] -

Why automation and artificial intelligence are essential to cyber defense [Q&A]
Publié: mai 4, 2016, 11:11am CEST par Ian Barker
With the ever increasing complexity and volume of cyber attacks, companies are increasingly turning to automated solutions and artificial intelligence in the quest for more effective protection. But how effective is an automated approach and will it become the norm in future? We spoke to Eran Barak, CEO of incident response specialist Hexadite to find out. BN: Are we nearing the end of traditional approaches to security? EB: Without a doubt. Until very recently, companies have been spending their security time, resources, and dollars on products that gather information that is then handed to a person to act upon. However,… [Continue Reading] -

Spanning launches backup for OneDrive business users
Publié: mai 3, 2016, 6:18pm CEST par Ian Barker
Just because your data is stored in the cloud is no reason to stop backing it up. While cloud service providers are responsible for making your data available, they’re not responsible for managing and protecting customers' data from accidental or malicious behavior. As a recent survey showed accidental deletion by users is a major source of data loss from the cloud. Now the company behind that survey, Spanning, is launching a solution for Microsoft Office 365 OneDrive for Business users. Features of Spanning Backup for Office 365 include automated and on-demand backup for all files that are stored by an… [Continue Reading] -

New free solution helps developers create better mobile software faster
Publié: mai 3, 2016, 4:02pm CEST par Ian Barker
Developing mobile apps often involves common components. But it's all too easy for developers to either fall into the trap of reinventing the wheel, or using components sourced from elsewhere that have no guarantee of quality. San Francisco-based WalkMe is launching a new, free, applet store which will provide programmers and developers with ready-made and easily integrated components. Its aim is to help programmers and app developers get their product to market earlier and to take it to the next level. WalkMe Apps enables app developers to focus their attention on the development of core software while providing them with the… [Continue Reading] -

Oukitel K4000 Pro -- a smartphone for a life of hard knocks [Review]
Publié: mai 2, 2016, 4:09pm CEST par Ian Barker
At the top end of the smartphone market the likes of Apple and Samsung are competing to offer the latest technology. But down at the lower priced end of things, for people who want a smartphone on a budget, there are a swathe of Chinese makers competing for your cash. Set aside your techno-snobbery and many of these phones turn out to be surprisingly good for the price. The latest to come our way is the Oukitel K4000 Pro. It's a 64-bit, quad-core, 4G phone with a five-inch screen, running last-but-one Android 5.1 Lollipop and costing less that $150. Its key… [Continue Reading] -

New service helps small businesses sync and share files
Publié: mai 2, 2016, 3:04pm CEST par Ian Barker
Enterprises of all sizes have become increasingly reliant on file syncing and sharing services. But for smaller companies business focused services can be expensive, leaving them reliant on free consumer services that offer limited space and functions. Backup and storage specialist Datto is launching and new inexpensive yet powerful file sync and share (FSS) service leveraging the low cost basis of the company's 200 petabyte (PB) private cloud, coupled with a global license agreement with ownCloud, an established open-source leader in the FSS industry. It allows employees to access files from any device in any location and share them with… [Continue Reading] -

Lack of data is a roadblock to account-based marketing
Publié: avril 29, 2016, 4:26pm CEST par Ian Barker
The idea of account-based marketing (ABM), treating B2B customers as individual marketing targets, has been around for a while. Technology has made it more practical approach in recent years, but a new survey reveals there are still factors holding back its use. Business insights specialist Avention has carried out a survey of 100 B2B sales and marketing practitioners about their use of ABM techniques and strategies. While more than 90 percent of those surveyed believe ABM is relevant to their businesses, respondents say that their number one roadblock to starting an ABM program is lack of access to the right… [Continue Reading] -

85 percent of people won't pay ransoms to recover data
Publié: avril 29, 2016, 12:01pm CEST par Ian Barker
As we've seen in recent reports, ransomware is an increasingly big problem. But how much do people know about it and methods to protect themselves? Security researchers at ESET surveyed over 3,000 people across the US and Canada to gauge their understanding of ransomware and unearthed some interesting findings. One in three of those surveyed say they are unaware of what ransomware is. More worryingly younger people are less likely to understand the concept than older ones. 85 percent say they would prefer to lose their files rather than pay a ransom, while the remaining 15 percent would be willing… [Continue Reading] -

Financial services lead the way in BYOD adoption despite security concerns
Publié: avril 28, 2016, 3:04pm CEST par Ian Barker
BYOD is becoming increasingly popular across all industries, but it's the financial sector that's leading the way according to a new report. The findings come from data protection company Bitglass which surveyed more than 800 cybersecurity professionals across five major industries, including financial services, technology, healthcare, government and education. It finds that 72 percent of all organizations support BYOD for all or some employees, but the figure is 74 percent for the financial sector. However, relatively few organizations are able to control access to corporate data, with only 14 percent having successfully deployed mobile application management (MAM) solutions. "The threat of data leakage… [Continue Reading] -

9 out of 10 office workers suffer technology stress in meetings
Publié: avril 28, 2016, 12:36pm CEST par Ian Barker
A new survey of office workers in the UK shows that a majority suffer stress in meetings when struggling with tasks like sharing screens and finding the right cables in order to give presentations. The study by visualization specialist Barco finds that for 93 percent, this meeting stress has serious knock-on effect on every aspect of their work. Presentations were of a poorer quality, time was wasted, deadlines were missed, and for 12 percent, it even resulted in lost promotions and lost business. People's heart rates reached 179bpm when struggling with technology during a meeting, compared to resting heart rates… [Continue Reading] -

New partnership helps boost eCommerce platform performance
Publié: avril 27, 2016, 2:59pm CEST par Ian Barker
In order to get a competitive advantage, retailers are increasingly looking to deliver a rich, interactive eCommerce experience for their customers. The problem with this is that it can lead to platforms being loaded down with extra functions that result in a drop in performance. Application delivery specialist InstartLogic has announced that it's partnering with IBM to help retail clients accelerate the performance of their eCommerce platforms. Instart Logic's Application Delivery Platform brings a fundamental new approach to website delivery and security to users of the IBM WebSphere Commerce platform and IBM Commerce on Cloud. It uses software and machine… [Continue Reading] -

Free online service helps uncover malicious domains
Publié: avril 27, 2016, 12:29pm CEST par Ian Barker
Phishing sites that use domain names similar to a legitimate company’s, along with cybersquatting are a major problem. Open DNS recently claimed that cyber squatters have become more active during the US election campaign. Web security solutions company High-Tech Bridge is launching a new, free, online service that will allow anyone to instantly detect typosquatted, cybersquatted or phishing domains targeting their domain or brand name. Called Domain Security Radar, the service is simple to use -- just enter a URL and results include details on cybersquatted domains, typosquatted domains and phishing websites. It also shows the latest trends and alerts… [Continue Reading] -

New Bamboo Server features help businesses manage growth
Publié: avril 26, 2016, 5:11pm CEST par Ian Barker
Growth is the goal of most businesses, but it can create problems for IT teams as they hit resource limits, lose track of processes, and struggle with inefficient collaboration, security risks and user management problems. Development tools company Atlassian is announcing the release of its latest version of Bamboo Server continuous integration and deployment tool that manages the roll out of automated software builds. Key features of Bamboo 5.11 are an increase in the number of remote agents from 100 to 250, improved diagnostics and better integration. It's now possible to use REST APIs to trigger deployments for continuous delivery.… [Continue Reading] -

Cloud native networking helps businesses exploit public clouds
Publié: avril 26, 2016, 3:24pm CEST par Ian Barker
As more businesses turn to the use of public cloud services, they're keen to find ways to gain more visibility into their deployments and make them more secure. Cloud native networking pioneer Aviatrix Systems is addressing this with the launch of its Cloud Native Networking 2.0. The solution combines a software-defined network controller and software gateways to enable businesses using a combination of public, private and hybrid clouds to quickly and easily roll out virtual private clouds. It enables cloud operations teams to set up, securely connect and centrally manage their entire cloud network, connecting users, sites and instances across regions… [Continue Reading] -

Rackspace improves compliance handling for mixed infrastructures
Publié: avril 26, 2016, 1:18pm CEST par Ian Barker
When businesses have specific compliance requirements -- because of the industry they're in for example -- managing them across cloud and hybrid infrastructures can be a tough challenge. Managed services specialist Rackspace is addressing this by adding CloudPassage Halo as the underlying security and compliance platform behind its Rackspace Compliance Assistance service, targeting companies that prefer to outsource the management of their compliance initiatives. "CloudPassage is one of the leading providers in workload-focused security," says Jarret Raim, director, managed security at Rackspace. "Halo has enabled Rackspace to provide a new service to our customers, helping us to define, manage and… [Continue Reading] -

Angel investors prefer science and technology startups
Publié: avril 25, 2016, 4:31pm CEST par Ian Barker
It's easy to assume that investors are only interested in making money and adopt a follow-the-leader approach to getting the best returns. However, a new report from online startup investment platform Propel(x) shows that the top reasons for investing are: the management team, cited by 75 percent, ability to understand the technology (52 percent), and the potential return on investment (42 percent). "The results of our survey dispel a common misconception that angel investors are driven by a follow-the-leader mentality," says Swati Chaturvedi, CEO and co-founder of Propel(x). "Our data shows that access to both management and independent industry experts is… [Continue Reading] -

Choosing asset management software
Publié: avril 22, 2016, 4:20pm CEST par Ian Barker
Asset management is often seen as something as a chore and something that's relegated to a few hours work with an Excel spreadsheet. But that makes it hard to keep up to date and may not deliver all of the information needed to effectively keep track of equipment and software. Wasp Barcode Technologies has developed its AssetCloud software to give companies a cloud and subscription-based service that helps organizations efficiently track, maintain and collect data on the materials they own. It's also put together an infographic highlighting the features companies need to look for when choosing an asset management system.… [Continue Reading] -

Social ad spending rises by 86 percent
Publié: avril 22, 2016, 12:52pm CEST par Ian Barker
Spending on social media advertising has increased by 86 percent in the first quarter of this year compared with the same period in 2015. It's also up eight percent when compared to last year's final holiday shopping quarter. These findings come from agile marketing specialist Kenshoo based on data managed by its platform for over 3,000 advertiser and agency accounts. It attributes the growth to the appeal of new ad types like Facebook Dynamic Product Ads and increased inventory through Instagram. Paid search spend increased by 13 percent year-on-year, buoyed by increased spend on mobile ads (up 77 percent) and product ads… [Continue Reading] -

More than a third of enterprises don't backup business data
Publié: avril 21, 2016, 4:53pm CEST par Ian Barker
The results of a new survey show that many organizations continue to demonstrate a complacent, lax attitude toward backups, leaving them vulnerable to evolving threats. The study from cloud-based backup provider CloudBerry Lab finds that almost half of respondents (49 percent) have only one copy of their business data, which could cause major operational disruption in the event that data becomes inaccessible. Around 36 percent of enterprises backup their business data completely. But while this finding is encouraging, it's offset by the fact that an equal number do no backups at all. Also 27 percent of respondents admit to having lost… [Continue Reading] -

New technique allows Trojans to remain in memory to evade detection
Publié: avril 21, 2016, 4:19pm CEST par Ian Barker
Remote access Trojans (RATs) have been used for many years to allow attackers to gain access to and take control of user’s systems. Usually RATs are delivered when a user opens an email attachment or downloads a file from a website or peer-to-peer network. This involves direct delivery of the payload which makes detection easier. Researchers at security company SentinelOne have uncovered a more sophisticated delivery technique that ensures that the payload file remains in memory through its execution, never touching the disk in a de-encrypted state. This lets the attack stay hidden from conventional antivirus technologies. Samples analyzed also… [Continue Reading] -

Taking the pulse of cyber security in healthcare
Publié: avril 21, 2016, 3:34pm CEST par Ian Barker
Large hospitals often have thousands of workstations used by multiple employees to access confidential patient data, so securing them can be a major challenge. Endpoint security specialist Duo Security has compared its customers in healthcare with those in other industries to determine how the sector differs in its security requirements. Among the findings are that healthcare customers are logging into twice as many applications as the average user, widening the attack vector. Twice as many healthcare endpoints have Flash installed and three times as many healthcare customers have Java installed on their devices, again, putting them at greater risk of… [Continue Reading] -

Oukitel aims to shake up the budget smartphone market with the sub-$50 C3
Publié: avril 21, 2016, 12:02pm CEST par Ian Barker
Not everyone wants or can afford a premium smartphone and Chinese makers have been busy carving out a niche at the lower end of the market with a whole raft of models that provide smartphone features at dumbphone prices. Launching next week the Oukitel C3 is the latest entry into an increasingly crowded market. What makes it stand out is that unlike most cheaper phones which rely on older versions of Android, the C3 runs the latest 6.0 Marshmallow. The phone comes with a 5-inch HD display that has a 720 x 1280 resolution, an MT6580 quad-core chip set, a 1GB… [Continue Reading] -

Digital divide is holding back the UK economy
Publié: avril 21, 2016, 11:21am CEST par Ian Barker
New research by business organization the CBI in conjunction with IBM shows that a digital divide is opening up across the British economy, with just over half (55 percent) of 'pioneer' firms adopting digital technologies and processes, while the remaining 45 percent are falling behind. Despite the UK taking top place globally for e-commerce and fifth place for the availability of technology, it ranks only fourteenth in the world for company-level adoption of digital technology, with many companies struggling to digitize their businesses at the rate of peers in other countries. Reasons for this are given as a lack of… [Continue Reading] -

Frustration with conventional password management leads to risky behavior
Publié: avril 20, 2016, 3:46pm CEST par Ian Barker
One in three Americans indulges in some form of risky password practice, such as writing them down, according to the results of a new survey. The report from access control specialist SecureAuth finds that Americans are exasperated with conventional online password management. It reveals that 74 percent rely on means other than memory to manage their online passwords, 35 percent write passwords down and 25 percent use the same password across several accounts. When asked what they found most frustrating about password management, 29 percent named keeping up with different password requirements across accounts, 18 percent meeting complex password requirements,… [Continue Reading] -

Businesses need to use text messages to reach millennials
Publié: avril 20, 2016, 3:09pm CEST par Ian Barker
Millennials have an overwhelming preference for texting according to new research. In fact, when given the choice between only being able to text or call on their mobile phones, 75 percent of millennials would rather lose the ability to talk. Respondents to the survey from enterprise mobile specialist OpenMarket say texts are preferred because they're more convenient and on their own schedule (76 percent), texts are less disruptive than a voice call (63 percent), they prefer to text rather than call in general (53 percent) and because they never check voicemails (19 percent). With millennials making up nearly a quarter… [Continue Reading] -

New analytics platform aims to transform mental healthcare
Publié: avril 20, 2016, 1:03pm CEST par Ian Barker
Healthcare costs for people diagnosed with mental illness and common chronic health conditions are 75 percent higher than for those without a mental health diagnosis according to the Centers for Medicare and Medicaid Services (CMS). This is because there’s often a lack of coordination between multiple care providers, different state policies and diverse payment structures which can result in poor health outcomes and higher costs across health systems. To address the problem behavioral health analytics provider ODH and IBM Watson Health are announcing the launch of Mentrics, a population health management platform designed to help care organizations transform the quality… [Continue Reading] -

77 percent of companies don't have the capability to respond to cyber attacks
Publié: avril 19, 2016, 4:18pm CEST par Ian Barker
Only 23 percent of organizations are capable of responding effectively to a cyber incident. This leaves the remaining 77 percent often having to purchase support services after an incident has occurred. This is among the findings of the latest Global Threat Intelligence Report from security company Solutionary. The report is made up of information from 24 security operations centers, seven R&D centers, 3.5 trillion logs, 6.2 billion attacks and nearly 8,000 security clients across six continents. Among other findings are that spear phishing attacks accounted for approximately 17 percent of incident response activities supported in 2015. In many cases, these… [Continue Reading] -

US hosts more malicious websites than any other country
Publié: avril 19, 2016, 3:42pm CEST par Ian Barker
According to a new report from German security company G DATA, more malicious websites were hosted in the US in 2015 than in any other country, originating around 57 percent of recorded attacks. China, Hong Kong, Russia and Canada are also major hosts of malware, though Europe is little in evidence, only Germany and Italy making the top seven and accounting for just six percent between them. Overall, the number of websites categorized as being 'evil' has risen by 45 percent, emphasizing how attacks from the web represent one of the biggest and growing threats facing computer users. It also shows… [Continue Reading] -

How the cyber crime business model is changing
Publié: avril 19, 2016, 12:22pm CEST par Ian Barker
Cyber crime is an increasingly serious business and a new report released today by Trustwave looks at the top trends from the past year based on real-world data from data breach investigations. Key findings from the report include that 97 percent of applications tested by Trustwave in 2015 had at least one vulnerability. In addition 10 percent of the vulnerabilities discovered were rated as critical or high risk. Retail is the industry most commonly targeted by criminals, accounting for 23 percent of Trustwave investigations, followed by hospitality at 14 percent and food and beverage at 10 percent. The findings show… [Continue Reading] -

Facebook video scam targets Chrome users
Publié: avril 15, 2016, 3:06pm CEST par Ian Barker
Researchers at security company ESET have released details of a new piece of malware that spreads disguised as video posts on Facebook. Malicious links appear as a video post you were tagged in on a timeline, or as a message sent to you via Facebook Messenger by a friend. They use the titles, 'My first video', 'My video', 'Private video' or a string of randomly generated characters. Clicking on the link tells you that a plugin is needed in order to play the video. If this is installed your Facebook wall will be flooded with fake video posts tagging various friends.… [Continue Reading] -

Threat hunting technique helps fend off cyber attacks
Publié: avril 14, 2016, 8:50pm CEST par Ian Barker

With data breaches making the news ever more frequently, businesses are on the look out for new ways to identify and guard against threats.
Cyber threat intelligence company DomainTools has released the results of a new survey conducted by the SANS Institute on the effectiveness of using threat hunting to aggressively track and eliminate cyber adversaries as early as possible.
According to the survey, adopters of this model reported positive results, with 74 percent citing reduced attack surfaces, 59 percent experiencing faster speed and accuracy of responses, and 52 percent finding previously undetected threats in their networks.
"With cyberattacks increasing exponentially each year, it's no surprise enterprises are attracted to threat hunting as a proactive multi-layered approach to discovering and mitigating cyber threats as early as possible," says Tim Chen, CEO of DomainTools. "As the findings note, successful threat hunting isn't necessarily about overhauling an existing cybersecurity program, it's about using the third-party data and technologies that most organizations already possess in order to maximize the chances of proactively finding, attributing and eliminating an adversary before the damage is done".
Though it's a relatively new approach to the early identification of cyber threats, 85 percent of enterprises say they are currently involved with some level of threat hunting. There are barriers to using the technique effectively though, 40 percent cite the need for a formal program and 52 percent a lack of skilled staff.
The top seven data sets that support threat hunting are IP addresses, network artifacts and patterns, DNS activity, host artifacts and patterns, file monitoring, user behavior and analytics, and software baseline monitoring. The most common trigger for launching a hunt is an anomaly or anything that deviates from normal network behavior according to 86 percent of respondents.
However, the survey also reveals that only 23 percent of businesses have hunting processes that are invisible to attackers, meaning that the majority of organizations are at risk from exposing internal hunting procedures in a way that benefits the attacker.
You can learn more in the full report which is available from the DomainTools website.
Image Credit: alphaspirit / Shutterstock
-

Are old customers more important to online businesses than new ones?
Publié: avril 14, 2016, 2:56pm CEST par Ian Barker

For businesses, particularly online ones, there will always be a mix of new and old customers. But what does the ratio between them tell you about the health of the company?
Cloud marketing company Optimove has studied data from millions of online customers and more than 180 brands to help companies understand if their ratio of new-to-existing customers indicates a state of growth, stagnation or decline.
It finds that online retailers with a new to old customer ratio of 90:10 are unhealthy, with a five-year compound annual growth rate (CAGR) lower than two percent and customer churn rates 100 percent higher than average. These are classed as 'running in place.'
Those with a new-to-existing customer ratio between 70:30 and 40:60 are typically early stage companies (less than seven years old). These are 'rockets' and are growing very fast, with a five-year CAGR over 100 percent and churn rates 50 percent lower than the average.
Businesses with new:existing ratios between 40:60 and 20:80 can be considered as 'healthy grown ups,' as they're typically more than 7 years old and have a five-year CAGR between 20 percent and 60 percent, with the lowest churn rates of any companies in the study.
A ratio of 10:90 or worse is bad news, these businesses, 'old cash cows,' are practically dying, showing declining revenues over the last three to five years.
"Two companies with the same revenue mix may tell very different stories and drive growth in very different ways," says Shauli Rozen, head of professional services at Optimove. "A quick example might be two companies that both derive 75 percent of revenue from existing customers. One might be acquiring many new customers and converting only a small portion of them to active and loyal customers, while the other may choose a more focused acquisition strategy, acquiring a smaller number of new customers, but turning a larger portion of them into loyal, long-time customers".
You can read more about the findings on the Optimove blog.
Photo credit: mtkang / Shutterstock
-

Watch out for phishing as US tax deadline day approaches
Publié: avril 14, 2016, 1:45pm CEST par Ian Barker

As the April 18 deadline for submitting individual and company tax returns in the US approaches, many people will be rushing to submit their information and this makes it a major opportunity for cyber criminals.
The run up to the deadline is likely to see millions of phishing emails sent to consumers and businesses. These will be trying to grab social security numbers, paycheck stubs, bank accounts, passwords, IDs and other key pieces of personal and professional information, using fake web sites and fraudulent emails that masquerade as official government collection agencies.
Fatih Orhan, director of technology for Comodo and the Comodo Threat Research Labs says, "In this age of sharing and collaborating in an online world, being exposed to phishing is an eventuality for virtually every company, well-known or not. It may not be the most groundbreaking attack method cyber criminals use -- but there's no denying that cyber criminals are becoming more clever when crafting their messages. More frequently, they're using well-known applications or social platforms and also action-oriented language in the subject lines to entice recipients to open the emails, click the links or attachments and get the information they want".
Comodo advises users to carefully check the address and domain name of email senders. While it may appear to be official, closer inspection will most likely reveal that the actual address is not linked with the domain name of the company.
In addition check the URL and domain of the website the mail is linking to. Chances are the URL and domain are also not affiliated with the company they’re purporting to represent. It also advises users to check with their IT department before opening or clicking on a link that seems suspicious.
Image Credit: wk1003mike / Shutterstock
-

Dell Venue 8 Pro 5855 is an attractive business tablet [Review]
Publié: avril 14, 2016, 11:08am CEST par Ian Barker
The first generation of Dell’s Venue 8 tablet hit the market back in 2013. In January of this year the company launched the updated version that we have here, which comes with a faster Intel Atom X5 processor and 64-bit Windows 10 as standard.
So, how does this latest version measure up, and is it a good option for business users?
In the Box
The Venue 8 Pro is available as Wi-Fi only or you can have a mobile data connection too. It’s powered by a 2.4GHz Intel Atom X5 Z8500 -- the old model had the 1.8GHz Z7340. You get 2GB of DDR3 RAM, a 64GB solid state hard drive and Wi-Fi as standard. Our review unit came with 4GB of RAM and the mobile data option, if you need more space, storage can be further expanded with a microSD card of up to 128GB. It’s worth noting that Dell uses eMMC storage -- which is basically a built-in SD card -- rather than a faster SSD disk.
The tablet measures 130 by 216mm and is only 9.45mm thick. At 377 g it gives an impression of solidity without feeling too weighty to carry around. The tablet has an 8-inch 1280 x 800 screen, a 5MP rear camera and 2MP front. The 5855 supports Miracast so you can wirelessly connect to compatible peripherals like screens and keyboards. The battery is a 19.5 WHr single cell unit.

You get a USB C cable and a mains adaptor in the package and, an attractive feature for business users, Microsoft Office Mobile is included in the price, and you can upgrade to the full version with an Office 365 subscription. Security is taken care of with the Dell Data Protection software.
Business Features
The Dell has a reassuringly solid feel and it should stand up well to the rigours of everyday business life. It comes with the Bamboo Paper digital notebook software that allows you to write and draw on the screen either with your finger or the optional stylus.
The fact that MS Office Mobile is included means you can start work almost as soon as you take it out of the box. You also get Dell’s Data Protection software which offers encryption and anti-malware features to keep your tablet and data secure. The Venue 8 Pro is also compatible with the Dell Client Command Suite, allowing IT departments to centrally manage BIOS and hardware configurations.
In addition you get access to Dell ProSupport Plus as an option, which helps identify and resolve problems and keep your hardware running smoothly. There’s the option of Protected Workspace too, this opens applications likely to be targeted by malware in a sandbox environment to guard against attacks.
There are a number of accessories that will be attractive to business users too, including a docking, station that supports keyboard, mouse and dual displays, a case called "Folio" that converts into a hands free stand, plus an active pen stylus for writing and drawing on the screen. You can also get an adaptor that gives access to HDMI, VGA, Ethernet and USB 3.0 via the USB-C port. Software options include Adobe Create Cloud, Photoshop Elements and Acrobat.
In Use
There’s a power switch on the top along with a headphone socket. The bottom edge has a USB C socket and speaker grille. On the right are the volume control and a hard Windows button plus a slot for SIM and memory cards. Because it’s USB C it’s less fiddly to connect as you don’t have to get the plug the right way around, but you’ll need to get an adaptor if you want to attach a flash drive or other standard USB peripheral.

The back has a ridged finish which makes it pleasant to grip, though it does tend to show finger marks. While the Venue 8 is nicely weighty it isn’t too heavy to hold one-handed. The rear camera is in a slightly raised panel in the centre of the back towards the top. You do tend to place your fingers over this if you’re holding the tablet landscape, so you’ll need to wipe it clean before taking photos. The back of the machine does get warm in use, but not uncomfortably so. The performance of this tablet isn’t going to set the world on fire. but it’s perfectly adequate for everyday tasks.
The screen has quite a wide bezel -- especially on the short edges -- but the viewing area itself is a good size. The screen itself offer 283 ppi pixel density (an improvement on the 189 ppi of the previous generation). What this means in practice is that it has crisp colors, good contrast and delivers smooth video playback. Viewing angles are good too so its possible for two people to watch the screen at the same time. It isn’t quite bright enough to cope with outdoor use on sunny days but that’s a minor quibble. There’s only a single speaker but it delivers decent sound quality.
The number of megapixels doesn’t tell the whole story with the rear camera, as although it’s "only" 5MP it actually delivers pretty impressive results. There’s no flash, but it takes good pictures in both daylight and artificial light. It uses the standard Windows 10 Camera app which is basic but functional. The 2MP front camera is good enough for VoIP calling.
The most disappointing aspect of the Venue 8 Pro is its battery life. Even in relatively light use, like visiting websites or viewing documents you’ll struggle to get more than five or six hours on a charge. Watch videos or play games and you’ll eat through the power reserves much faster.
Conclusion
At £366 for the 64GB version with mobile data as tested -- you can get the 2GB Wi-Fi only version for £259 -- the Venue 8 Pro may seem a little pricey. As a business machine though it looks like an attractive package. It’s solidly constructed, has a good range of practical hardware and software options, and it looks smart in an understated way.
If you can live with the rather disappointing battery life and you value reliability over performance, it’s well worth considering.
Pros
- Impressive display
- USB C
- Good range of business friendly features
Cons
- Disappointing battery life
- Non-SSD storage
- Pricey
ITProPortal Review: 7/10
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Crowdsourcing platform creates insights from unstructured data
Publié: avril 13, 2016, 5:54pm CEST par Ian Barker

Getting useful information from unstructured data is a notoriously difficult and time consuming task, but the launch of a new intelligent crowdsourcing platform could be about to change that.
The Spare5 platform uses a known community of specialists to accomplish custom micro-tasks that, filtered for quality, allow product owners to train powerful artificial intelligence models, improve their search and browse experiences, augment their directories and more.
According to IDG, unstructured data is growing at the rate of 62 percent annually and by 2022, 93 percent of all data will be unstructured. The Spare5 platform applies a combination of human insights and machine learning to solve the increasingly complex problem of using unstructured data, including images, video, social media content and text messages. Among the company's first wave of customers are Avvo, Expedia, Getty Images, GoPro, and Sentient Technologies.
"The old adage that a picture is worth a thousand words is true, but it's just the beginning. Spare5 is providing us breakthrough value by delivering nuanced human insights into our photos, at a value and scale that was unthinkable just a year ago," says Steve Heck, CTO of Getty Images.
Recognizing that all people have some expertise, valuable interests and free time, Spare5 has amassed a community of subject matter specialists across a wide range of skills and demographics, and built a library of game-like tasks. This approach enables Spare5 to ensure the right task goes to the right person. In order to continuously improve accuracy its Reputation Engine applies machine learning to rate each individual's performance.
As customers use the platform over time, the process becomes faster, smarter and better. Using a variety of SDKs and APIs, processed data can be easily integrated into existing data workflows and exported to produce top-line business reports.
"Our mission is to tap the world's potential brainpower," says Matt Bencke, founder and CEO of Spare5. "Businesses need specialized human insights to solve complex data problems. It used to be somewhere between impossible and impractical to crowdsource specialized insights at scale, with confidence and speed. Not any more. We love seeing our customers get the help they need to interpret unstructured data, while freeing up their employees to focus on their core competencies. There is a profound difference when the right human intelligence powers machine learning. And we've just begun".
Spare5 uses a subscription model allowing companies to easily make use of the platform. To find out more about it you can take a look at the company's website.
Photo Credit: photobank.kiev.ua/Shutterstock
-

New sales platform combines human and machine intelligence
Publié: avril 13, 2016, 4:53pm CEST par Ian Barker

Much of the sales process is about making effective use of information about existing and potential customers. But often that knowledge isn't easily accessible and therefore not used effectively.
A new platform from sales transformation specialist Altify aims to give B2B sales teams real-time visibility into the process based on stored knowledge and its built-in contextual insight engine.
Called Altify Max it monitors what is happening in the opportunity, the account, and the pipeline and forecast, assesses the impact, and notifies the salesperson to act with a suggested measure. Max has 30 years of deep sales knowledge and insights built in to the software, and customers can extend and customize the knowledge with their own insights. This real-time coaching solution is aimed at making the sales team more effective and delivering better results.
"Altify's ongoing mission is to help salespeople provide more value for their customers, and become true business partners," says Donal Daly, CEO of Altify. "We have always embedded knowledge, insight and context into the applications on the Altify Platform, but what makes Max so exciting is that we have poured a lot more knowledge into the system, added contextual notifications, and given our customers the capability to add their own knowledge and insights. This is really augmented intelligence for everyone who uses Salesforce. It is the perfect platform to enable companies to take their sales organizations to a higher level of performance and professionalism".
Benefits of the Max platform include increased engagement and effectiveness, with sales teams able to work more productively. Max can identify warning signs, so salespeople can address risk earlier in the sales process.
Max has been developed using 30 years of sales knowledge and packaged as a set of 'business rules' or insights that can help guide salespeople as they are working their opportunities or accounts. Organizations can personalize Max by customizing or extending the supplied knowledge and by creating insights specific to their own business.
Max will be generally available from next month and you can find out more on the company's website.
Image Credit: Tatiana Shepeleva / Shutterstock
-

Employees opt for Apple when given a technology choice
Publié: avril 13, 2016, 3:52pm CEST par Ian Barker

It's becoming increasingly common for companies to offer their employees a choice of technology devices. And according to a new survey when they do have a choice people are more likely to choose Apple devices.
The study by device management company JAMF Software shows that ease of use is the main reason given by people for selecting Mac (75 percent) and iOS (79 percent) as their work device of choice.
The findings also show a generation gap in computer choice. Employees between the ages of 18 and 54 overwhelmingly choose Mac, while those 55 and over are more comfortable using PCs. However, when given a mobile device choice, nearly 80 percent of all age groups select iOS compared to just 18 percent who choose Android. Regardless of age, when staff are given the technology they want, employers are rewarded with more productive and appreciative employees.
"Employees today not only want -- but expect -- the ability to choose the devices they are most comfortable with for work," says Dean Hager, CEO of JAMF Software. "Because Apple builds technology that puts people first, people prefer Apple. When employers combine the freedom of choice with Apple, employees are happier and are empowered to be more productive -- offering a huge business advantage".
Among other findings are that 61 percent of respondents say their company has a choice program and 72 percent claim that the ability to select their device of choice makes them more productive in the workplace. Choice programs are important to the well being of an organization according to 73 percent, and 70 percent of those who currently lack user choice say their organization should give them the right to choose the device that best empowers them to do their job.
More detail is available in the full report which you can find on the JAMF website.
Photo credit: Blablo101 / Shutterstock
-

Security is a top priority when installing identity solutions
Publié: avril 13, 2016, 3:10pm CEST par Ian Barker

According to a new survey 78 percent of organizations say that security outweighs cost savings and user experience when choosing identity management solutions.
The survey by access control specialist SecureAuth used responses from over 230 IT security professionals in the US and UK.
When asked why their company has initiated new identity projects in the past, 55 percent of respondents across small, medium and large companies say the deployment of new applications -- including both on-premises and cloud-based -- was the top driver. Board and senior management's drive for increased security is also cited by 50 percent of respondents as a chief reason for new identity project initiation, underscoring that cyber security has become a board-level concern.
Other drivers for installing identity management include compliance and audit requirements at 49 percent, cost savings (44 percent), security breaches at another company (36 percent), increased use of stolen or misused credentials (34 percent) and the company itself experiencing a security breach (25 percent).
"It's no secret that security has become a board room-level imperative," says Craig Lund, CEO of SecureAuth. "A decade ago, it was a nice to have; today, it's a must have. Accordingly, organizations across the globe are abandoning their laissez-faire approaches to cybersecurity and significantly increasing security spending for the coming years. Worthwhile cybersecurity endeavors may require some redirection of budget, but in this day and age, proactivity is just as important as reactivity".
When asked about their plans for identity and access management, 79 percent of respondents say that plans are underway for IAM of externally focused applications, including vendor, partner and customer applications, portals and mobile apps. In addition 47 percent say that IAM investment is a currently funded priority, 32 percent will invest in the next year, and 13 percent will invest in IAM, but don't have a specific time frame.
For more information you can visit the SecureAuth blog.
Photo Credit: Maxx-Studio/Shutterstock
-

New service helps service providers deliver cloud-based security
Publié: avril 13, 2016, 12:32pm CEST par Ian Barker

Security is a key concern for all enterprises, so it's not surprising that it's something managed service providers are keen to offer their customers in order to add value and differentiate their service.
Network breach detection company Eastwind Networks is launching a Managed Service Provider (MSP) and Managed Security Service Provider (MSSP) program. The new program is designed to help service providers stand out and grow their business with a simple cloud-based breach detection solution that ensures that customer data and assets are secure.
"In today's competitive security industry, MSPs are looking for value-added, easy to deploy and manage solutions that help ensure their customer’s success," says Paul Kraus, president and CEO of Eastwind Networks. "With our new MSP program, we are able to offer our partners services that provide an additional level of security expertise, a strong security platform offering and complete visibility to threats, security gaps, application usage, and overall network awareness".
Available via the Eastwind Cloud or in the customer's private cloud, the platform uses rich data, behavioral analytics, and threat intelligence to pinpoint anomalous behaviors even before they're classified as breaches. It's been designed to catch hackers during the weeks and months that they spend in the network before they take action. Storing and mining more than a year's worth of rich network metadata, Eastwind examines not only current network conditions, but continually analyzes historical data against updated threat sources to find breaches that would have otherwise gone unnoticed.
You can find out more about Eastwind breach detection and the MSP program on the company's website.
Photo credit: allepu / Shutterstock
-

Jewelery meets gadgetry in the Oukitel A8
Publié: avril 13, 2016, 11:44am CEST par Ian Barker

Bluetooth tracking devices to help stop you forgetting your phone have been around for a while, but they've generally been quite functional in design, looking like a remote car key.
Chinese smartphone maker Oukitel is launching its own take on the lost phone finder with a new gadget that looks like a piece of jewelry but also functions as more than just an alarm to tell you you've left your phone behind.
The Oukitel A8 lets you answer and hang up calls so you can appear a bit strange on the train by talking to your pendant -- it could be a good way of getting a seat. It can also control music playback and act as a shutter button to control the phone's camera so it’s handy for taking selfies too.
It has a 280mAh battery which the company says takes only 30 minutes to charge and will give you 15 hours of connected standby or five hours of talk time. It's compatible with both Android and iOS, so it should work with most smartphones on the market and it comes in a choice of blue or black.
Normal price of the A8 is $24.99 but until April 29 it's available for $19.99 from the Tomtop.com site. More details of the gadget are available on the Oukitel website.
-

New platform speeds up development of intelligent search apps
Publié: avril 12, 2016, 6:22pm CEST par Ian Barker

One of the problems with big data is that creating applications to access the information inevitably introduces a time lag and this leads to frustration for the end user.
Search and analytics software company Lucidworks is aiming to cut out this bottleneck with the launch of Lucidworks View, which allows companies to quickly and easily create custom search-driven applications built on Apache Solr and Apache Spark.
"Data lives everywhere, across a growing set of formats and locations. Even the most mature companies struggle to not only wrangle it in high volumes but expose it in a meaningful way," says Will Hayes, CEO of Lucidworks. "We built Lucidworks View to give our users the ability to rapidly create sophisticated applications for customers and, for the first time, truly plug and play with Big Data. Our aim is to eliminate the costly, time consuming complexities usually associated with the front- and back-end development of intelligent apps, moving companies quickly from the question, 'What do I do with my data?' to the statement, 'Data drives every part of the business'".
Lucidworks View lets companies build custom user interfaces that use the power of the popular Apache Solr and Apache Spark database engines. Using the platform can give customers individualized access to essential information while equipping their workforce with the tools they need to make informed business decisions.
Capabilities include simple configuration and workflow so that developers and admins at any level of expertise can start building and deploying intelligent apps with just a few keystrokes and no code. There are out-of-the-box connectors for over 60 systems including MySQL, databases, JIRA, Slack, Logstash, local file systems, and the web.
The product also allows tracking and continual improvement of search results based on user signals like clicks, social, device and geolocation for a contextually relevant data experience powered by machine learning. Developers can easily and quickly customize the interface to meet user expectations and present data in an intuitive, valuable way.
Lucidworks View is available from today and you can find out more on the company's website.
Image credit: Angela Waye/Shutterstock
-

Kingston launches new hardware encrypted flash drives
Publié: avril 12, 2016, 5:18pm CEST par Ian Barker

One of the best known names in the flash memory market, Kingston acquired the IronKey brand from Imation in February of this year.
IronKey has long been one of the leading brands in encrypted Flash drives and today we see the first fruits of the new partnership with Kingston's launch of two new managed and 256-bit AES hardware encrypted USB drives.
The DataTraveler 4000G2 with Management (DT4000G2DM) and DataTraveler Vault Privacy 3.0 with Management (DTVP30DM) solve the requirements of organizations that need to meet Federal Information Processing Standards (FIPS) and protect data at the highest level across their mobile workforce. Both devices can be used as a managed solution via the SafeConsole Encryption Management Platform from DataLocker, Kingston's partner for encrypted USB drive management.
Both new drives are 256-bit AES hardware encrypted and FIPS certified (the DT4000G2DM is FIPS 140-2 Level 3 validated; the DTVP30DM is FIPS 197 certified) to ensure maximum corporate and personal data security. Additionally, SafeConsole is the only secure USB management platform for secure USB drives with true password management at both remote and local level. The platform enables secure reset of forgotten passwords, activation of full audit trails, geolocation and geofencing to ensure cross-border compliance, automatic inventory, plus a 'remote kill' feature in the event the device is lost.
"Human error, malicious attacks and technical failures can place employee and corporate data at risk. Companies, agencies and organizations need to implement a security policy well before anything goes wrong as it's critical to prevent non-compliance, fines and even financial loss," says Ken Campbell, Flash business manager, Kingston. "Our latest encrypted managed USB drives, the recent IronKey acquisition and growing DataLocker partnership all demonstrates Kingston's commitment to providing the most secure and largest family of encrypted USB solutions on the market".
The DT4000G2DM and DTVP30DM are available in 4GB, 8GB, 16GB, 32GB and 64GB capacities, and are backed by a five-year warranty and free technical support. More information and details of where to buy can be found on the Kingston website.
-

Attack by cyber terrorists feared by 63 percent of US security professionals
Publié: avril 12, 2016, 3:17pm CEST par Ian Barker

Key concerns of information security executives include the growing threats of global cyber terrorism, the current state of security within the US and the ability of organizations to prevent such attacks.
These are among the findings of a new study by account management solutions provider Thycotic of more than 200 security industry attendees at RSA.
Cyber terrorism needs to be be taken more seriously as 63 percent of respondents feel terrorists are capable of launching a catastrophic cyber-attack on the US within one year. In addition, 92 percent of respondents believe that a majority of US companies either need more security or are behind the security curve in their ability to defend against cyber terrorism attacks.
"Some may say the whole discussion surrounding the threats associated with cyber terrorism is hyped; however, our findings show that 72 percent actually feel that the topic isn't hyped enough and that more needs to be done to protect companies and country as a whole from these types of vulnerabilities," says Jonathan Cogley, founder and CTO at Thycotic. "Re-examining the type of security technology used to protect both the US government and private sectors is essential to keeping our country safe".
There's a fairly even split on whether public or private sector systems are more at risk, 50 percent of respondents believe US private companies are more vulnerable than government agencies, while 42 percent believe the government is more vulnerable. An overwhelming 89 percent of survey respondents believe that both the military and businesses need to focus more on developing capabilities to defend against terrorist inspired cyber attacks.
You can find out more about the results on the Thycotic blog or register for an upcoming webinar which will discuss the findings.
Photo credit: Kletr / Shutterstock
-

Flexera extends software asset management to the cloud
Publié: avril 12, 2016, 1:46pm CEST par Ian Barker

While it's important for companies to manage their software licensing effectively, with the shift of many systems to the cloud doing so has become more difficult.
Software asset management specialist Flexera is riding to the rescue with the launch of a new solution addressing the management of cloud Infrastructure-as-a-Service.
FlexNet Manager for Cloud Infrastructure gives organizations centralized visibility into their cloud services use and allows them to optimize utilization and control costs. This first release focuses on optimization of Amazon Web Services (AWS) -- the most widely adopted cloud infrastructure service.
"The cloud services industry is growing more than five times faster than other IT categories as organizations shift away from internal hardware to greater use of public cloud infrastructures. This shift in spend means having the ability to track, manage and optimize cloud services usage is essential for responsible governance and cost management," says Jim Ryan, president and CEO of Flexera Software. "With FlexNet Manager for Cloud Infrastructure as part of FlexNet Manager Suite for Enterprises, Flexera Software enables companies to manage and optimize cloud infrastructure services and the software running in the cloud, along with traditional on-premises software".
FlexNet Manager for Cloud Infrastructure can automatically import usage and billing data from multiple accounts to deliver a centralized view of all AWS accounts and instances across the business. A cloud dashboard provides an executive-level view of the organization's use of cloud resources, showing consumption patterns and total spend across all AWS cloud subscriptions.
Cloud usage analysis and reporting enables organizations to eliminate waste and optimize spend. Users can analyze data and view consumption reports and breakdowns based on AWS instance types, both On-demand and Reserved instances, view consumption rates by departments and perform trending analysis.
You can find out more about the product and its features on the Flexera website.
Photo Credit: kentoh/Shutterstock
-

SQL Server 2005 support reaches the end
Publié: avril 12, 2016, 11:05am CEST par Ian Barker

We've known for some time that SQL Server 2005 was reaching the end of its extended support period and Microsoft has been busy encouraging users to move to newer software such as SQL Server 2014.
Today is the day when its support finally ends, so users still running the system will no longer receive hotfixes and security updates from Microsoft.
Ali Din, CMO at cloud infrastructure company dinCloud says, "Migrating your infrastructure can seem daunting, but it's imperative for organizations to upgrade to a modern data platform before the support deadline in order to maintain security and compliance. There are a lot of enhancements from SQL Server 2005 to SQL Server 2012, but if you are going to go through an upgrade, I suggest taking advantage of the technology with a proven methodology".
Din recommends that enterprises make the move to the latest version on SQL Server (SQL Server 2014), so that they can take advantage of the latest features and functionality available. In addition they should use an SQL database expert to help with the planning, migration, and optimization of their systems.
The Enterprise edition of SQL Server allows users to take advantage of In-Memory to improve database performance, along with AlwaysOn for high availability. The robust features of SQL Server 2014 should allow companies to save by not having to buy multiple smaller or less feature-rich databases.
More about end of support for SQL Server 2005 and migration options can be found on the Microsoft website and on the dinCloud blog.
Photo credit: 360b / Shutterstock.com
-

The future of developer recruitment [Q&A]
Publié: avril 11, 2016, 6:05pm CEST par Ian Barker

Recruiting developers is often a problem for organizations as the skills required are different from those in other sectors and can be hard to assess. Development often has a great deal in common with more creative fields, where suitability for a job is not so much about qualifications but about what you can do and how you can communicate.
So what can companies do to discover the developer talent they need? We spoke to Mike Bartlett, CEO of developer community site Gitter to get his perspective.
BN: What's wrong with the traditional approach where you simply advertise a job and wait for applications to roll in?
MB: Very seldom is great talent looking for a new job. The best engineers will be highly in demand and can effectively pick and choose where they work and what they work on. If you want the best, as you should, not only do you have to go out and find them, but you're also going to have to convince them why they should be working for you. Higher salaries, better free lunches and more ping-pong tables just won't cut it any more.
You need to start building relationships far in advance of hiring, building trust and an understanding of why working for you is better than working for someone else.
If you're just placing ads on traditional jobs boards or using regular recruiters, you’re probably going to get a large number of CVs through the door and spend a huge amount of time trying to figure out if the candidate is any good. This is hugely time consuming not only for the hiring manager, but will also take time out of your existing development team's schedule as they are generally the ones having to dig into each applicant individually.
BN: Do companies sometimes fail to effectively assess technical skills as part of the recruitment process?
MB: The most common failure is assessing how the candidate works with your particular technology stack, the code you've already written and -- most important -- with the team.
We've seen, and even used, a lot of developer testing techniques. There are particular exercises that will test competency, for example with a particular algorithm and understanding if the candidate truly understands computer science, logic and reasoning and these can weed out some of the obvious bad hires.
What we've found really effective is doing pair programming tests where the applicant will come and spend three or four hours sitting with one of your existing developers and working together on a real problem within your own environment. This will not only test software development skills, but communication skills, team work and a you'll get a really good sense of how that person behaves in real working conditions.
BN: What can businesses do to look for candidates rather than waiting for them to appear?
MB: The whole team should always be hiring. Make sure your developers are always on the look out for great people to hire. This means going to meetups and not just listening to the presentations, but socializing with the other attendees and getting to know one another. It means actively contributing to open source projects and hanging out in the online communities such as our own developer network, Gitter, and building relationships with the people who stand out.
There are great tools such as Workable or Lever where you can give your whole team access and help keep a list of prospective future candidates in a centralized place.
BN: What can developers themselves do to make them more attractive to prospective employers?
MB: Get stuck into the online communities and contribute back to open source projects. Pretty much every technology stack used in software development today is open source; rather than just reporting bugs back to the project maintainers, if you can roll up your sleeves and get stuck into the code, find the bug and send a proposed fix back to the project, you'll immediately gain a lot of credibility and be seen as contributing back to the ecosystem.
BN: Developer recruitment is a bit like online dating really, isn't it?
MB: Oddly enough, I met my wife on Match.com. If she reads me comparing our relationship to hiring developers, I think I might find myself in a lot of trouble!
Photo Credit: sokolovsky/Shutterstock
-

New cloud platform streamlines Android app development
Publié: avril 11, 2016, 12:51pm CEST par Ian Barker

Businesses have ever more demand from consumers to deliver services via mobile, so they're looking for ways to produce apps quickly and efficiently.
To address this need, Android solutions provider Genymobile is cloud-based platform that allows enterprises to build, test, show off and service Android applications across the entire application lifecycle while streamlining the development process.
Genymotion Cloud is a cloud-based emulator that combines collaboration and automation features. It enables developers, QA, UI/UX designers, sales and marketing, help desk teams and business decision-makers to easily evaluate apps at any stage of development on more than 3,000 virtual device configurations instantly via any web browser.
"There is mounting pressure for every business to be mobile-powered. It is imperative that mobile development does not become a burden. Our SaaS solution maximizes efficiencies across the whole mobile application value delivery chain," says co-founder and co-CEO of Genymobile, Arnaud Dupuis. "Everyone involved in the project gets the information they need exactly when they need it. This not only means faster time to market. It also means better quality, reliability and improved customer satisfaction".
Collaboration features include the ability to demo the app's functionality on any Android device via any web browser, allowing sales and marketing to gather market feedback before the application is complete. Customized virtual device configurations can be remotely shared, allowing developers working on the same project to share an identical local development environment. The most up-to-date application under-development can also be shared for review, meaning developer teams and UX or UI engineers can collaborate more easily throughout the project. Sales teams can expedite cycles by allowing potential customers to use and test an app under development without requiring additional engineering support.
Genymotion Cloud also offers automation features including continuous integration support, compatible with on-premise CI infrastructures such as Jenkins, Bamboo, Buildbot and TeamCity. Code testing is simplified too with standard HTTPS REST and Java APIs that allows developers to create a testing device, install an application, run and test it against multiple device configurations without leaving the development environment. In addition, it's compatible with industry standard integrated development environments, including Android Studio and Eclipse.
You can find out more about Genymotion Cloud on the company's website.
Image Credit: Alex Mit / Shutterstock
-

The Internet of Things gets its own day (and lots more Things)
Publié: avril 8, 2016, 3:11pm CEST par Ian Barker
The idea of connected devices is nothing new, the University of Cambridge had a connected coffee pot, to save on trips down the corridor to see if it had finished brewing, as early as 1991.
But as more and more devices go online we've come up with the idea of the Internet of Things. This, apparently, is such a good idea that it also now has its own day on April 9.
To mark this year's Internet of Things Day, electronics supplier RS Components has produced an infographic looking at how the IoT has developed and what it means for our day-to-day lives.
By 2020 it's reckoned that there will be about 13 billion household Things like toasters, fridges, TVs and thermostats connected to the internet. To put that into perspective in 2016 there are around two billion mobile phones online.
There will also be around 3.5 billion Things in Cars online by 2020, 411 million wearables and 646 million Things in Hospital, like heart monitors and body implants. In addition 9.7 billion Things in the Street like traffic lights, parking meters and buildings will be online too.
You can see more detail in the full graphic below, but just remember, a connected Thing is for life not just April 9.
Image Credit: Ahmetov_Ruslan / Shutterstock
-

Why it's vital for retailers to have a mobile strategy [Q&A]
Publié: avril 8, 2016, 10:57am CEST par Ian Barker

We already know that having a mobile friendly site is important to search rankings, and with Google's announcement in March that it will start to rank mobile-ready sites even higher, companies are likely to focus even more on the mobile experience.
It's particularly important for retailers to connect with millennial shoppers who are more likely to research or buy using their mobile devices. We spoke to Aaron Shook, executive software architect of digital transformation specialist PointSource, to find out why a mobile strategy and good design are key to success.
BN: How important is it for shopping sites to deliver a positive mobile experience?
AKS: Very. Not only does mobile friendliness now affect SEO holistically (desktop included), but it also is a huge driver in determining mobile conversion rate and overall traffic numbers. A poor mobile user experience will send users directly to competitors who offer better experiences on the customer's device.
BN: Does a move towards more mobile friendly sites risk alienating older users?
AKS: No. E-comm sites can be mobile friendly without being flashy. Mobile friendliness simply means that you cater to the device that your user is viewing your page on; older users have a similar need for mobile pages to be easily viewable when using mobile devices. Design differences around flashiness, button sizes, etc. can be driven by analyzing your user demographics, but mobile friendliness is a must regardless of age group.
BN: Are we seeing a trend towards accessing retails sites using apps rather than browsers and what impact does this have?
AKS: For every-day retail shopping, I don't think that retail-branded apps will outpace mobile web in the foreseeable future. When users have simple purchases to make, their go-to is still going to be a web browser rather than downloading a retail-specific app. That said, apps are very valuable because they allow retailers to occupy real estate on users' phones and thus every day lives and continually engage the user. The most loyal customers who are spending the most with your brand are also the ones who will keep brand-specific apps installed, so providing these customers with additional value-adds through an app to reward them for loyalty is definitely a revenue driver. A solid mobile strategy needs to account for both mobile web and apps.
BN: How can mobile be used to enhance the physical in-store experience?
AKS: Newer technologies are making it possible to track user journeys through stores in ways that we couldn't have imagined prior to smartphones. Beacon technologies can allow retailers to track user movements through the store in order to optimize shopping patterns, send promotions, and gain a firm understanding of the user journey in a brick-and-mortar setting.
BN: Surveys have shown that surfers visit fewer pages of a site on mobile devices than they do on desktops. How can retailers adapt to this?
AKS: Our belief is that a big part of the reason for this pattern is twofold, and the reasons are heavily intertwined. Firstly users often pull out mobile phones to research a specific item rather than to browse e-comm storefronts since browsing is easier on a desktop device. Second, user experiences on retail mobile sites are still not up to par with desktop experiences, making it more difficult to shop on the majority of sites. We've seen huge gains in overall traffic, page views per user, average usage time, etc. by designing mobile websites with experiences specifically catering to the needs of mobile users. Designing an experience specifically for your mobile users is a must in order to truly unlock an e-comm mobile site's full potential.
BN: Will we see numbers of mobile shoppers continuing to increase or are we reaching a plateau?
AKS: Numbers continue to rise and don't show signs of stopping any time soon. 2015's holiday period mobile numbers set record numbers for mobile across the board, as did 2014, 2013, and so on. While 2013 and 2014 mobile transaction numbers were still relatively low compared to desktop counterparts, 2015 saw a rise of customers checking out and completing purchases on mobile. According to IBM, more than 36 percent of e-commerce sales during the 2015 holiday period took place on mobile devices, up from 27 percent the year before. The numbers may eventually plateau, but we are not anywhere close to that point yet.
Image Credit: Slavoljub Pantelic / Shutterstock
-

Startup company launches solution to protect connected cars from cyber attacks
Publié: avril 7, 2016, 3:33pm CEST par Ian Barker

In our increasingly connected world it isn't just your computer or smartphone that can fall victim to attack. The Internet of Things is producing a whole new generation of vulnerable devices.
Not least of these are connected cars where attackers can potentially infiltrate and take control over car systems, even killing the engine as you drive.
A new Israeli startup company Karamba Security has produced a purpose-built ECU solution that protects a car's externally connected components. It can identify attack attempts and block exploits from infiltrating the car's network to ensure drivers' safety.
Security detection and enforcement capabilities can be embedded directly on the ECU to ensure only explicitly allowed code and applications can be loaded and run on the controller. Karamba blocks any foreign code, which means the controller is safe from attackers, regardless of how they entered (via the internet, USB drive, service port, etc), with no false alarms.
"Customers have been very excited about our ECU endpoint approach," says Ami Dotan, CEO of Karamba Security. "By stopping attacks at the ECU, attackers can't make it inside the car's network, which means the car's ongoing operations are safe. Our early warning and malware prevention capabilities allow car companies to provide drivers smart vehicles that will get them where they want to go, safely."
The solution can be used to protect existing as well as new cars, manufacturers are able to retro fit protection to older models as part of an ECU software update.
Karamba has received $2.5 million in seed funding from YL Ventures and from the GlenRock private investment company. "We were impressed with Karamba's unique focus on developing an unobtrusive solution to the cybersecurity problems of the automotive industry," says Yoav Leitersdorf, managing partner of YL Ventures. "The experience of the team gave us confidence they could take a unique, shrink wrapped, approach and make it a reality."
You can find out more about the risks and how Karamba's protection works on the company's website.
Photo Credit: ssguy/Shutterstock
-

Basic API security measures are often overlooked
Publié: avril 7, 2016, 2:58pm CEST par Ian Barker

APIs are the glue that holds much of the digital world together, connecting systems, apps and data. But a new survey reveals that many organizations are failing to place enough emphasis on API security.
Research company Ovum in partnership with bot detection and mitigation firm Distil Networks, surveyed 100 IT and security professionals. They found that 30 percent of APIs are planned out with no input from the IT security team and 27 percent of APIs proceed through the development stage without the IT security team weighing in.
Other findings include that 87 percent of respondents were running an API management platform, with 63 percent using a platform developed in-house. However, rate limiting, considered to be a basic API security practice, was employed by less than half of respondents.
Of those surveyed 53 percent feel security teams should be responsible for API security, while 47 percent think the developer teams should hold responsibility.
It's clear that APIs have taken hold, with 20 percent of respondents saying they're maintaining, building, or publishing more than 50, while at the other end of the scale, 32 percent are working on between one and 10. The remainder are running somewhere between 11 and 50 APIs, but Ovum expects to see the number grow over the next few years.
A significant proportion are using public APIs that are exposed to developers outside their own companies. 51 percent say that at least part of the rationale for their APIs was to enable an external developer community/ecosystem, while 67 percent say that partner connectivity is a driving factor.
The report's authors note, "Our survey finds that most respondents are at least concerned with the issue of API security, which is as it should be. Furthermore, most of them are using some form of API management platform, and the majority of platforms in use provide some level of security capability. However, there is by no means blanket coverage of all aspects of API security by all platforms."
You can read more about the findings on the Distil Networks site.
Image Credit: Profit_Image / Shutterstock
-

New platform streamlines enterprise software deployment
Publié: avril 7, 2016, 2:00pm CEST par Ian Barker

Modern software is often complex, perhaps running services on multiple machines. This can make deployments complex and prone to errors.
Software deployment specialist Puppet Labs is launching the latest version of its Puppet Enterprise platform which gives development teams control over and insight into the changes they want to push out.
At the same time the company is launching a software operations platform called Blueshift. It engages with products like Docker to give organizations the tools they need to build and operate modern software.
"We're driven by a belief that software can make people more powerful," says Luke Kanies, founder and CEO of Puppet. "To make that a reality, we're focused on building the standard platform for automating delivery and operation of the software that powers everything around us. Puppet gives organizations a common language to deliver and operate modern infrastructure and to adopt whatever comes next -- simply, securely, and consistently".
Puppet makes it possible to push out any change on demand and manage ordered deployments of applications and infrastructure. It's also possible to possible to schedule change in a specific time window, and push change through tools like HipChat, Git, Jenkins or directly with Puppet Enterprise.
Operators gain visibility into deployments and can manage them as required. Thanks to an an interactive dependency graph, teams can visualize dependencies across all the resources they manage with Puppet.
There's also integration with the Splunk operational intelligence platform. This allows users to analyze their infrastructure and get performance metrics for Puppet Enterprise services with data sent direct to Splunk Enterprise.
You can find out more on the Puppet Labs website.
Image Credit: Rafal Olechowski / Shutterstock
-

Microsoft releases Cloud App Security to protect SaaS apps and data
Publié: avril 6, 2016, 5:56pm CEST par Ian Barker

Back in September of last year we reported that Microsoft had announced its purchase of cloud security firm Adallom to help its customers protect their cloud-based data and applications.
In February it teased that a new Cloud App Security offering based on Adallom's technology would be released in April. Well, today the wait is over and the product becomes generally available as a cloud-delivered service to help IT and security teams gain visibility and control over cloud apps.
Writing on the company's blog back in February, Bret Arsenault, Microsoft's chief information security officer says, "Microsoft Cloud App Security brings the same level of visibility and control that IT departments have in their on-premises network to their SaaS applications including apps like Box, SalesForce, ServiceNow, Ariba, and of course Office 365".
Cloud App Security identifies all cloud applications on a network -- from all devices -- and provides risk scoring and ongoing risk assessment and analytics. It allows admins to set granular controls and policies for data sharing and loss prevention (DLP), leveraging API-based integration. Users can opt to use out-of-the box policies or build and customize their own. Cloud App Security also provides threat protection for cloud applications using user behavioral analytics and anomaly detection.
As a first step network logs are uploaded to the service. These are analyzed and admins can then choose which apps are sanctioned and need to be connected to the service. Once that's done data control policies can be set up and admins start to receive alerts. You can read more about how it works on the Microsoft Cyber Trust Blog.
It's available on a subscription basis at $5 per user per month. If you're interested in finding out more you can visit the Cloud App Security product page to request a trial.
Photo credit: Maksim Kabakou / Shutterstock
-

The best mobile apps for business users
Publié: avril 6, 2016, 3:07pm CEST par Ian Barker

Useful apps tend to embed themselves deeply into people's work lives and stay installed on their devices for the long term. As a result it can be hard to get a definitive list of the best apps at any one time.
To try to remedy this, app quality company Applause has produced a report that ranks 130 business apps based on what people feel about them. Categories of apps ranked include communication, organization, work productivity, security and weather.
To qualify for the report, apps needed to have a minimum of 1,000 reviews combined in the Android and iOS app stores. Ranking is based on a sentiment score of 0-100 as determined by Applause's analytics platform for attributes including usability, security, privacy, interoperability and more.
The average score of all 130 apps was 61 out of 100 (the average score of apps across all categories is 67). Organization apps were the highest ranked at an average score of 68/100. Communication and security apps received average scores of 55 and 53, respectively.
In the communication category, Slack (64.5) scored ahead of Google Hangouts (47), HipChat (42.5) and Skype for Business (22). In organization, Box (64.5) scored ahead of Google Drive (61), Dropbox (60) and Microsoft OneDrive (58). Of security apps, Norton Mobile Security (79) scored ahead of Kaspersky Internet Security (77) and Avast Mobile Security (75).
Ten apps earned above average scores based on more than 100,000 reviews. These include ColorNote (93), Duolingo (88.5), CamScanner (85) and Evernote (78). The report's authors note that, "Consumers value apps with elegant user interfaces and simple navigation, accurate information, relevant notifications, quick launch times, fast performance and engaging and fun experiences".
At the other end of the scale the worst scores were received by enterprise mobile management apps such as Good, Mobile Iron and AirWatch, all of which ranked at the bottom with scores under 20.
You can find out more about how Applause measures app sentiment and access the full report on the company's website.
Image Credit: Syda Productions / Shutterstock
-

The doctor will lose your data now -- 1 in 5 doctors' mobile devices could be at high risk
Publié: avril 6, 2016, 11:35am CEST par Ian Barker

More than 27 million Android devices running medical apps are likely to have high risk malware installed according to a new report.
The Mobile Threat Intelligence report from threat defense company Skycure is focused on healthcare and finds that doctors who use mobile devices to assist their day-to-day practice are exposed to network threats, and that these significantly increase over time.
In a single month, one in five (22 percent) of mobile devices will be at risk of a network attack. This figure nearly doubles to 39 percent after four months. In addition to network threats, mobile devices continue to be plagued by malware. More than four percent of all Android devices were found to be infected with malicious apps. Medical app users need to be particularly wary, as the report shows 27.79 million devices with medical apps installed might also be infected with high-risk malware. The Skycure mobile threat defense platform conducted 51 million network tests in 2015, and detected the installation of nearly 13,000 malicious apps.
"Mobile is a huge attack target for cyber criminals who are after sensitive personal data like patient records," says Adi Sharabani, CEO of Skycure. "Unlike desktop and network security, mobile security is often the weakest link in the security chain. Healthcare is one place where it is clear that one compromised device puts more than just the device owner’s data and identity at risk".
Among other findings are that 80 percent of doctors use their mobile devices to assist in their day-to-day practice and 28 percent store patient data on their mobile device, making their devices prime targets for cyber criminals.
Eleven percent of mobile devices running an outdated operating system with high-severity vulnerabilities might have stored patient data on them. In addition fourteen percent of mobile devices containing patient data likely have no passcode to protect them.
There is some good news, for example, the percentage of devices with passcodes enabled rose slightly to 52 percent in the last quarter of 2015 from 48 percent in Q3 2015. This may be due to the adoption of new devices featuring biometric passcodes. However, it still leaves nearly half of devices completely unprotected.
The report also shows that users of iPhones and iPads are more protected because they are much more likely to have the most current version of their device's operating system. At the end of 2015, 88 percent of iOS users had upgraded iOS 9. By contrast, only three percent of Android users were using Android 6.0, Marshmallow, at the end of the year.
You can find more about the findings by registering for an on-demand webinar, and there's a summary of the findings in infographic form below.
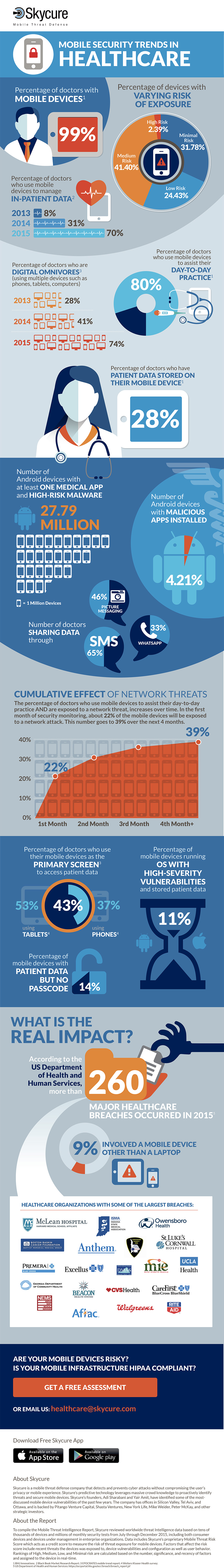
Image Credit: Rob Hyron / Shutterstock
-

Open source database targets the big data analytics market
Publié: avril 5, 2016, 4:12pm CEST par Ian Barker

Leader in open source databases MariaDB is announcing the release of its new big data analytics engine, MariaDB ColumnStore.
It unifies transactional and massively parallelized analytic workloads on the same platform. This is made possible because of MariaDB's extensible architecture that allows the simultaneous use of purpose built storage engines for maximum performance, simplification, and cost savings. This approach sets it apart from competitors like Oracle, and removes the need to buy and deploy traditional columnar database appliances.
"I've seen first-hand how traditional columnar appliances arose as reactions to the cost and complexity of Oracle," says Michael Howard, CEO of MariaDB, "But these reactions have only increased complexity and cost further, and most importantly, over-looked critical features. In contrast, MariaDB ColumnStore is ACID compliant, blazingly fast, massively parallelized, and uses a distributed storage engine. What's equally important is its front end -- MariaDB, which provides the same interface, same security, same SQL richness simplifying management, reducing operating costs".
ColumnStore is a columnar storage engine for massively parallel distributed query execution and data loading. It supports a vast spectrum of use cases including real-time, batch, and algorithmic. It can perform complex aggregation, joins, and windowing functions at the data storage level to increase performance. MariaDB ColumnStore is an Open Source GPL2, a fork based on InfiniDB and open source community contributions.
The company is also announcing new data streaming capability in MariaDB MaxScale that will simplify real-time data propagation to external data lakes or data warehouses. This feature allows transactions in MariaDB to be replicated in real time to Hadoop or any other data store. It enables MaxScale and MariaDB to handle replication in mission critical applications without impacting performance. At the same time it includes all necessary metadata so that any program can read it, with no per-value overhead.
MariaDB ColumnStore will be available for beta testers next month, you can sign up for more information on the release on the company's website.
Image Credit: Tashatuvango / Shutterstock
-

Behavior ID strengthens mobile and web security
Publié: avril 5, 2016, 3:09pm CEST par Ian Barker

Whether it's down to stolen credentials, weak passwords or bot-based attacks, the threat of an account takeover is one of the major worries for most users.
Mobile identity company TeleSign is launching Behavior ID, a new offering that enables web and mobile applications to measure and analyze a user's behavioral patterns to provide continuous authentication, even after the user has been verified with traditional security measures like passwords.
It provides an additional, transparent layer of security for every type of online account or mobile application, ensuring they are protected them from fraud, without the need for user interaction. Behavior ID delivers a 'similarity score' based on a set of behavioral biometric traits that are collected, analyzed and rated as users go about their everyday tasks, from initial account creation through ongoing access and usage of an account. This profile is then used to calculate a similarity ratio between the user's current behavior and their historical, expected behavior. It can therefore streamline the user experience for known good users, while providing a basis for challenging potentially bad or fraudulent users by asking for re-verification, or two-factor authentication.
No user interaction is required to enroll, enable, and start protecting an account from compromise. Users simply continue to use their web or mobile application as normal with no change to their workflow or behavior.
"With Behavior ID, our customers can immediately increase the level of identity assurance for every user account they have, without adding friction," says Steve Jillings, CEO at TeleSign. "The power of Behavior ID is its ability to adapt to the user, transparently producing a digital fingerprint from a user's behavior to confirm their identity and develop an ongoing authentication without requiring the consumer to do anything. Best of all, these unique biometric patterns are extremely accurate, from the way we move our hand on a mobile device screen or with a mouse, it is virtually impossible to precisely imitate another person's behavior".
Behavior ID SDKs for web and mobile applications are available from today for developers to embed into new or existing web and mobile app platforms. More information can be found on the TeleSign website.
Image Credit: Kirill Wright / Shutterstock
-

Use of next generation databases hindered by backup technology
Publié: avril 5, 2016, 2:05pm CEST par Ian Barker

Businesses are showing increased interest in developing their infrastructure to support distributed, scale-out databases and cloud databases, but a lack of robust backup and recovery technologies is hindering adoption.
Backup and recovery is cited by 61 percent of enterprise IT and database professionals as preventing adoption. However, 80 percent believe that deployment of next-generation databases will grow by two times or more by 2018.
These are among the findings of a new report from data protection specialist Datos IO which looks at the concerns of IT leaders and the benefits they cite surrounding the rising demand for distributed applications and adoption of scale-out databases.
Other findings are that 75 percent of respondents predicted that next-generation databases will influence their organizational growth in the coming 24 months. The majority of apps (54 percent) deployed on next-generation databases sit in the analytics category, with business management, IoT and security apps coming close behind.
MongoDB and Cassandra lead the way in distributed database deployment, followed by cloud-native databases from Microsoft and Amazon. Some 89 percent of enterprise IT database professionals say that backup and recovery (as a function of storage) is critical for production applications.
"This survey shows IT application and database professionals clearly understand that for organizations to ride this unprecedented tide of data agility, they also need to innovate data storage, specifically for distributed backup and recovery," says Tarun Thakur, co-founder and CEO of Datos IO. "To deploy and scale next-generation applications, enterprises must be sure that data can be managed and recovered over its lifecycle at scale. To unlock the full potential of data, it is imperative that businesses fill data their protection gaps now".
There's a summary of the findings in infographic form below and you can find out more at the Datos IO site.
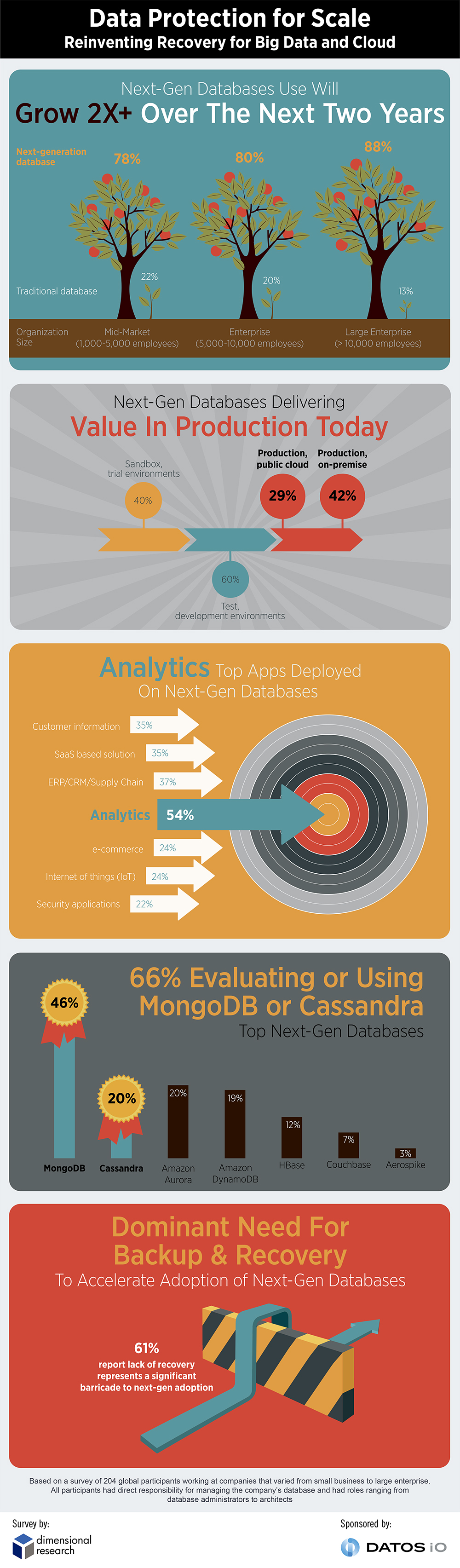
Image Credit: Oleksiy Mark / Shutterstock
-

New capabilities help drive application release automation
Publié: avril 4, 2016, 5:00pm CEST par Ian Barker

Digital transformation strategies are often held back by complex IT systems that have been built over the years and represent significant investment. This may lead to departments seeking their own solutions, placing yet more pressure on back office systems.
Business automation specialist Automic is launching new capabilities to its DevOps release automation product, Automic Release Automation, to allow companies to deliver greater agility, scalability, and speed in order to drive competitive advantage.
"We are simplifying how our customers execute on their DevOps journey by specifically targeting all of the applications across an enterprise with the goal of driving the digital transformation required by our clients", says Chris Boorman, chief marketing officer at Automic. "Our experience in automation, expertise in production IT environments, and industry recognized technology are key differentiators that position us and our clients for success. The Automic Blueprint for Continuous Delivery provides a practical approach that an enterprise can employ to scale continuous delivery across both back-office applications and the new digital front-office. This blueprint provides a clear and structured approach for all enterprises to use in driving their digital transformation".
Features include a new cloud-based sandbox, and visualization of the delivery pipeline of all applications to better understand the impact and time implications of multiple concurrent releases throughout the organization.
Automic Release Automation enables enterprises and service providers to serve multiple departments and clients in isolation from each other on a single shared platform, simplifying operations and maintenance, and making scaling easier.
It also integrates with the Automic marketplace allowing developers to contribute and utilize new content seamlessly. There's a new online assessment service too that will benchmark an enterprise against key indicators of maturity. By answering a set of simple questions, enterprises can benchmark themselves against the Automic standard, against their peers, their industry or their region.
You can find out more about Automic Release Automation, which is available now, on the company's website.
Image Credit: Stokkete / Shutterstock
-

Work-life balance gains importance as tech worker salary expectations fall
Publié: avril 4, 2016, 3:24pm CEST par Ian Barker

What are the trends driving the careers of tech professionals? A new report based on information gathered from the Woo platform, which allows workers to find jobs with companies that offer the things they really want, reveals what has changed in the first quarter of 2016.
The Woondex (Woo Index) shows there has been a 12.6 percent drop in salary expectations compared to the final quarter of last year. However, there's an 8.2 percent increase in the number of workers looking for a better work-life balance over the same period.
The San Francisco Bay Area is still the most popular location for tech workers in the US, but its appeal could be waning as there's a 6.9 percent increase in the number of Bay Area workers who say they are willing to relocate. The most popular choice for those who want to move on is New York, followed by Seattle.
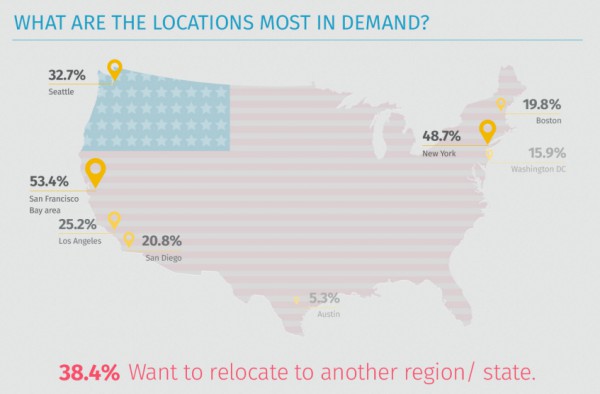
It seems that size matters too, at least for businesses, with 82.6 percent wanting to work at larger companies compared to only 76.5 percent willing to work at startups.
The most in demand technologies are Java (18.2 percent), NodeJS (15.2 percent) and AngularJS (14 percent). When it comes to sectors big data/cloud is still most popular, followed by health and finance.
You can find out more about how Woo helps gauge their worth and find fulfilling roles on the company's website.
Photo Credit: wavebreakmedia/Shutterstock
-

LookingGlass releases new threat intelligence platform
Publié: mars 31, 2016, 3:57pm CEST par Ian Barker

Using threat intelligence helps enterprises to improve decision making when it comes to managing security incidents and enforcing policy.
Threat defense specialist LookingGlass Cyber Solutions is looking to improve the way analysts and security operators interpret threats targeting their organizations with the launch of its new ScoutPrime threat intelligence management platform.
"We are excited to announce the availability of ScoutPrime and the other enhancements to the broadest portfolio of threat intelligence and risk management products in the market," says Chris Coleman, CEO of LookingGlass Cyber Solutions. "These latest additions ensure our customers stay ahead of the rapidly changing threat landscape targeting their organizations and the companies they do business with".
ScoutPrime allows users to customize threat levels to match their organizational risk tolerance. With configurable threat indicator confidence scoring, along with an internet intelligence‐based foundation allos it to apply context using the largest collection of proprietary and third party threat data available in a single product. The result is relevant, actionable intelligence. By allowing organizations to visualize threats ScoutPrime reduces the risk they face from new and emerging threats.
LookingGlass has also enhanced its Cyber Threat Center which now includes a case management enhancement that allows customers to enrich the intelligence to sync with their internal processes and track each vetted issue from delivery to resolution. In addition Cyber Threat Center now has the ability for administrators to enable two‐factor authentication on user accounts.
Improved too is the company's Cyveillance Malicious C2 data feed which monitors over 60,000 domains known to be associated with active malicious command and control servers. Its daily updates now include support for internationalized domain names and additional metadata on the botnet, variant, category, and criticality score.
You can find out more on the LookingGlass website.
Image Credit: Mopic / Shutterstock
-

New study finds strong demand for service-based messages
Publié: mars 31, 2016, 3:00pm CEST par Ian Barker

Over the last few years consumers have increasingly come to expect to receive messages keeping them up to date with appointments and transactions.
Mobile marketing company Vibes has announced the results of a study of over 1,000 people which finds that mobile phones are the number one preferred device for service-based messages with 70 percent preferring to receive service-based messages this way.
Good news for businesses is that service-based messages are seen to create a competitive advantage, with 84 percent of consumers saying that service-based messaging has an impact on their decision to choose one company over another.
Conveying basic information such as time, date and tracking information, is one of the most important features of service-based messages in terms of positively impacting customer satisfaction. Most consumers (78 percent) say that a text message is the fastest way to be reached for important service updates on purchases.
Alongside the survey results, Vibes is launching a new transactional messaging solution to enable enterprises to deliver automated service messaging programs across mobile channels. Using the company's Catapult platform, it enables enterprises to power automated service messaging programs across mobile channels, including text, push and mobile wallet (Apple Wallet and Android Pay).
"With the enterprise shift to mobile, mobile messaging has become a top priority and complement to email strategies to provide the best experience possible for customers", says Jack Philbin, co-founder and CEO of Vibes. "Transactional messaging on mobile provides an immense opportunity to gain a non-marketing mobile touch point, drive cost savings and innovate your brand. We’re already seeing large enterprises turn to Vibes to capitalize on the immediacy of mobile and power transactional messaging programs to reach consumers on their most trusted and heavily used device in a way that is easy for them".
Key features include user-friendly transactional messaging templates and logic that allow technical and non-technical users to create actual message templates, update content and set up message logic. Sophisticated reporting capabilities can conduct deep cross-channel analysis to help business users understand transactional messaging’s impact on the customer experience.
The full Transactional Messaging Consumer Report is available from the Vibes website where you can also find more about the transactional messaging service.
Image Credit: Rido / Shutterstock
-

The 3-2-1 rule and other backup tips
Publié: mars 31, 2016, 11:55am CEST par Ian Barker

It may not have escaped your notice that today is World Backup Day, which aims to raise awareness of the importance of looking after your data.
To mark the event Dark Bear Web Solutions has produced an infographic offering facts and tips about backups.
It reveals that 64 percent of people globally would be more worried about losing their data than about losing the device it was held on. Also that 37 percent of small businesses have had to restore lost data from a backup at some point.
Among the tips it offers are how to spot what isn't a backup, for example saving to another folder or leaving pictures in your camera's memory. It also recommends the 3-2-1 rule for data you care about -- taking three copies, using two formats, for example the cloud plus a hard drive, and having one off-site backup.
It looks at the differences between cloud storage and cloud backup too, and at the various physical media types that can be used, as well as offering tips for small businesses.
You can see much more in the full graphic below.
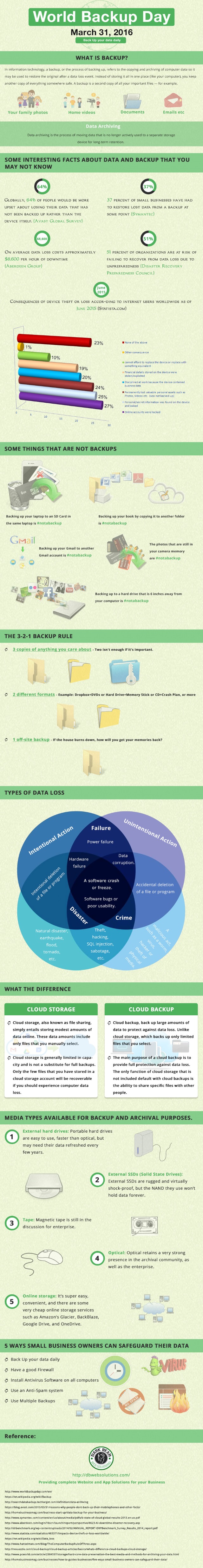
Image Credit: Oleksiy Mark / Shutterstock
-

New program ensures enterprises are prepared for cyber attacks
Publié: mars 30, 2016, 3:34pm CEST par Ian Barker

If a data breach happens customers expect a fast and reassuring reaction from the company affected. It's therefore crucial for businesses to have an incident response plan, but often those plans are only tested when a breach occurs.
According to an upcoming survey from customer security company AllClear ID the two most common challenges during a breach response are people related, with 66 percent citing internal politics and 60 percent "too many cooks in the kitchen".
To address the need for a proactive security plan and enable enterprises to act swiftly and decisively, the company is launching its AllClear Reserved Response program. This is aimed at ensuring a successful customer response after a cyberattack by pairing expert planning with guaranteed response capacity.
"Cyberattacks are a very real part of doing business today and we've repeatedly seen the devastating impacts that poorly managed breach responses have on a company. CEOs get fired, customer loyalty and retention tank, and companies experience significant financial losses", says Bo Holland, founder and CEO of AllClear ID. "Reserving the response capacity you need in advance is the most effective way to mitigate the response risk and restore customer confidence after a breach".
Using Reserved Response, businesses are given the confidence and capacity they need to execute critical business decisions immediately following a breach, something which can make or break customer trust and loyalty. They can begin executing their response plans as soon as a breach occurs, reducing the chances of negative publicity and damage to business reputation.
"Planning is not enough. If you don’t have the operational capacity to communicate to all of your customers and resolve their problems during an emergency, you will fail", Holland adds. "It's the Titanic problem -- the captain had an evacuation plan, but he was caught short on lifeboats".
You can find out more about AllClear Reserved Response on the company's website.
Photo credit: Imillian / Shutterstock
-

The changing role of the firewall in network security
Publié: mars 30, 2016, 1:38pm CEST par Ian Barker
The firewall is still at the center of most network security strategies, but it needs to evolve as cloud technology, software defined networks and next generation firewalls take hold.
This is among the conclusions of the latest State of the Firewall Report from network security specialist FireMon, which finds that 91 percent of IT security professionals believe firewalls are still as critical or more critical than ever to their security architecture.
Two-thirds of respondents also say that firewalls are somewhat or highly valuable to the cloud services they manage. This represents a 10 percent increase over 2015. Next generation firewalls (NGFWs) represent at least 50 percent of current firewall infrastructure in almost half of the organizations surveyed compared to 34 percent in 2015. NGFWs can add complexity to security management, but despite this only 6.7 percent of organizations say they have no NGFWs.
Software defined networking (SDN) is also seen as being a major factor, with 90 percent of respondents recognizing that it has impacted or will impact networking to some degree.
"We're seeing small shifts in IT professionals' perceptions of the firewall as new technologies enter the market", says Jody Brazil, co-founder and chief product strategy officer at FireMon. "Adoption of SDN and network virtualization in general won't decrease the need for firewalls, but it may open the door to advancements or a new category of network protection. It will be more of a continuous evolution rather than a complete upheaval as so many are quick to claim".
The report is based on a November 2015 survey of approximately 600 IT security practitioners from a range of organizations, a full copy can be downloaded from the FireMon website.
Photo Credit: Andrea Danti/Shutterstock
-

How enterprises can benefit from archiving in the cloud
Publié: mars 30, 2016, 12:52pm CEST par Ian Barker

Most businesses have information they need to keep for compliance and other reasons. Traditionally this has been in the form of paper archives, but the availability of low-cost cloud storage offers an attractive alternative.
Data management company Solix Technologies has produced an infographic looking at the advantages of cloud archiving.
It reckons that for 1.6 terabytes of data -- around five million sheets of paper -- there are substantial savings in production and archiving costs, with a figure of less than $1,000 a year for cloud storage compared to $140,000 or more for paper.
There are also benefits in convenience and ease of access to stored data. Also 65 percent of people see password protected documents of secure compared to only 45 percent for papers locked in a filing cabinet.
You can see the full infographic below.

Image Credit: Bedrin / Shutterstock
-

New service addresses security concerns in Microsoft SCCM environments
Publié: mars 29, 2016, 4:17pm CEST par Ian Barker

Potential security vulnerabilities in Microsoft SCCM (System Center Configuration Manager) environments are a concern for 70 percent of IT professionals, according to a new survey, with 65 percent planning to conduct an SCCM security review in the next year.
The results of the study of more than 150 professionals by security company Adaptiva have been released to coincide with its launch, along with Windows Management Experts, of a new security auditing service for SCCM users.
As part of the service, security experts will conduct a series of interviews and system checks in order to validate processes, procedures, and configurations against a list of more than 100 security best practices.
They will also document where a company can improve SCCM security, and highlight the security areas where an IT department is doing things right. In addition they'll deliver a security action plan with specific fixes that should be applied to address identified vulnerabilities.
In addition customers have the option to implement Adaptiva solutions like its Client Health endpoint security engine or OneSite content distribution system, to automate system checks and support the ongoing deployment of security patches and updates. They can also schedule follow-up reviews to ensure progress is made as planned, and validate that recommended security best practices are maintained on an ongoing basis.
"Security is a huge concern for everyone in IT, from admins to CIOs, who see locking down their SCCM environments as a crucial part of the solution", says Jim Souders, COO of Adaptiva. "With the new SCCM Security Audit service, Adaptiva and WME team up to provide companies with protection and peace of mind. For organizations that want to upgrade their SCCM security program, we offer advanced security management capabilities with our OneSite and Client Health products".
More information on SCCM security audits is available on the Adaptiva website.
Photo Credit: watcharakun / Shutterstock
-

The biggest barriers to adopting BYOD
Publié: mars 29, 2016, 3:17pm CEST par Ian Barker

Thanks to the benefits that it offers in terms of productivity and employee satisfaction, BYOD remains a popular option for many companies and the market is predicted to be worth $360 billion by 2020.
But a new report from Crowd Research Partners in conjunction with some leading data security vendors -- including Bitglass, Blancco Technology Group, Check Point Technologies, Skycure, SnoopWall and Tenable Network Security --provides a conflicting portrayal of BYOD security barriers and adoption trends in the workplace.
The biggest factors inhibiting BYOD adoption are revealed as security (39 percent) and employee privacy (12 percent). In contrast, management opposition (three percent) and user experience concerns (four percent) rank much lower.
The survey results also show that one in five organizations suffered a mobile security breach, primarily driven by malware and malicious Wi-Fi. It’s not too surprising then that security threats to BYOD are a burden on organizations' IT resources (35 percent) and help desk workloads (27 percent).
Despite increasing mobile security threats, data breaches and new regulations, only 30 percent of organizations surveyed say they are increasing security budgets for BYOD in the next 12 months. Meanwhile, 37 percent have no plans to change their security budgets.
"BYOD can be a tough nut for organizations to crack", says Pat Clawson, CEO of Blancco Technology Group. "Despite its many benefits, our study found that 21 percent of organizations have experienced a data breach resulting from BYOD or corporate-owned mobile devices. This often creates a chicken-or-egg scenario -- where organizations contemplate whether to push forward with BYOD without having complete security controls in place, or to postpone until they can be absolutely certain data won't be leaked. To change this, we need to educate businesses on the full scope of mobile security risks and technology solutions that can help them protect data across the entire lifecycle -- and get the C-suite to understand the impact on overall business growth".
The complete report is available to download from the Blancco Technology website and there’s a webinar to discuss the findings on April 14.
Photo credit: Sarawut Aiemsinsuk/Shutterstock
-

Cubot X17 -- a premium smartphone at a budget price? [Review]
Publié: mars 28, 2016, 3:36pm CEST par Ian Barker

Cubot is a name you may not have heard of, but the Chinese company is seeking to make an impact on the smartphone market with the X17, offering premium features at a more down market price of around $170 (£130).
First impressions are positive, the phone comes in a box with a textured bronze colored finish. In the package you get a USB cable, mains adaptor, SIM tray opening tool, a clip-on protective cover for the back, a spare screen protector -- there's one pre-installed -- and a printed quick start guide. You also get a couple of cleaning wipes which is a nice touch.
The technical spec is impressive too. The phone uses a 1.3 GHz quad-core, 64bit processor (Mediatek 6735A) and has 3GB of RAM. There's 16GB of onboard storage though you can expand this with a microSD card. The 5-inch screen has a 1920 x 1080 resolution and 441 ppi, there's 4G support along with Bluetooth and Wi-Fi, though no NFC, and it runs Android 5.1 Lollipop. Cameras are 16MP rear -- with an LED flash -- and 8MP front.
The X17 is dual SIM and, usefully, the two slots are different sizes so you can use a standard Micro SIM and/or the smaller Nano SIM. Note though that the Micro SIM and SD card use the same slot so you can't have both at once. The phone is powered by a non-removable 2500mAh battery.
You can find the full spec on the Cubot website.

Out of the Box
The phone itself feels and looks like a quality item. It's nicely weighty and has a shiny metal edge, the glass front curves into this which gives it a premium look. The 5-inch screen has white sections above and below it housing the front camera, speaker grille and fixed menu buttons. The back echoes this with a silver coloured metal centre panel between two white plastic sections. Power and volume buttons are on the right edge with the SIM and SD card slot on the left.
The rear camera lens is slightly raised above the phone body, though if you have the clear clip-on cover in place it sits flush. A slight oddity is that the permanent menu and back buttons are the other way around from most Android phones which takes a bit of getting used to.
With the phone switched off the screen appears to go right up to the sides of the device, but switch on and you realise that there's narrow black border so the actual usable area is slightly smaller. The part that you can use though is bright with strong colors and good viewing angles.

In Use
The X17's performance is perfectly acceptable in everyday tasks, accessing the net and playing videos, though the processor isn't quite up to the most intensive games. It does seem to get through the battery quite quickly, but you should manage around a day of normal use on a full charge. There is a battery saver mode that you can set to activate at 15 percent or five percent of remaining power to eke out the remaining life. The phone gets a little warm when you've been using it for a while, but not uncomfortably so.
You can swipe to the left from the lock screen to activate the camera without unlocking the phone first. Using the rear camera there's a bit of a lag when focusing, and when you have got it focused the photos aren't great with colors that look a little over saturated. Sharpness and detail is good though. Video can be shot in full HD at 30fps, but there's no image stabilization so you can end up with rather shaky results.
The front camera has a wide angle lens making it good for taking group selfies (groupies?), and you can enable a gesture mode for timer shots which detects a V sign to start a countdown. Again pictures are adequate rather than outstanding.
As we noted above there's no NFC on the X17, you do get something called HotKnot, which is similar but only works with other Mediatek-based kit so its usefulness is rather limited.
Software is pretty much standard Android. The phone does come with Opera Mini installed, but otherwise is commendably free of bloatware. There are air gesture options for scrolling through the gallery, changing radio stations and switching the screen on and off, but these are a bit hit and miss in use.
Conclusion
If you're looking for a phone that offers 4G on a budget, there's quite a bit to like about the X17. It's well made with the feel of a pricier device, the screen in particular being the equal of some much more expensive phones.
There are some compromises, the camera in particular isn't great and the lack of NFC may be a deal breaker for some. Also the battery life is no more than adequate. Those things aside the X17 is a decent all-rounder and will suit people who are looking to take their first leap into 4G without breaking the bank.
-

New research helps isolate real threats from suspicious activity
Publié: mars 28, 2016, 12:23pm CEST par Ian Barker

Security teams often spend a lot of their time investigating anomalies and suspicious behavior, leaving them less time to focus on true threats.
Cloud security specialist CloudLock is tackling this problem with research into what it calls a Cloud Threat Funnel. Based on analysis of user behavior patterns it can isolate truly malicious threats from the noise of other potentially suspicious or unusual behaviors.
As the report's authors note, "Analyzing user behavior for signs of a breach is like searching for a needle in a haystack. Anomalous behaviors may be simply accidental missteps by careless users, or typical work-related actions that in the right (or wrong) context can become dangerous".
The funnel approach is based on research into the daily behavior of 10 million users, 1 billion files and 140,000 cloud apps. It reveals that 99.6 percent of users access cloud platforms from just one or two countries per week. Establishing this as the norm, the team was then able to isolate and reveal anomalies.
By adding user activity to third-party threat intelligence the algorithms reduce the likelihood of false positives. The Threat Funnel then moves into anomalies, recognizing outliers that do not conform to expected patterns. Because it's a self-learning model, it reduces the number of alerts being generated to improve the signal-to-noise ratio and visibility. Using this approach allows security professionals to focus their efforts on true malicious threats.
In order to make use of the Cloud Threat Funnel, organizations need to deploy an adaptive security model that can provide security teams with predictive, preventive, detective and responsive capabilities. By narrowing the focus on top offenders and user activities that are the most indicative of a true threat, security teams can make confident decisions much faster and avoid costly breaches with less effort.
The findings and methodology behind Cloud Threat Funnel are available in a report which you can download from the CloudLock website.
Image Credit: Andrea Danti/Shutterstock
-

Software vulnerabilities are up -- but it's not Microsoft's fault
Publié: mars 25, 2016, 3:28pm CET par Ian Barker

The number of software vulnerabilities has increased over the last year, but the majority of them are in non-Microsoft products.
This is a key finding of the latest Vulnerability Review from Flexera Software, which in 2015 recorded 6,081 vulnerabilities in 2,484 products from 263 vendors. This compares to 2014's figures of 15,698 vulnerabilities in 3,907 products from 514 vendors.
"The substantial 36 percent drop in number of products and 49 percent drop in vendors primarily reflects an adjustment in focus from Secunia Research to only monitor the systems and applications in use in the environments of customers of Flexera Software's Software Vulnerability Management product line", says Kasper Lindgaard, director of Secunia Research at Flexera Software. "This change is caused by a continuous rise in the number of vulnerabilities reported in recent years, and we are currently seeing other research houses choosing similar strategies -- CVE Mitre, for example".
Looking at the 50 most popular applications on private PCs -- identified using Flexera's Personal Software Inspector -- the split between vulnerabilities in Microsoft and non-Microsoft products shows 21 percent for Microsoft and 79 percent for other vendors. This is despite Microsoft products making up 67 percent of the top 50.
In 2015, 1,114 vulnerabilities were discovered in the five most popular browsers: Google Chrome, Mozilla Firefox, Internet Explorer, Opera and Safari. That represents a four percent increase from 2014.
Over the same period 147 vulnerabilities were discovered in the five most popular PDF readers: Adobe Reader, Foxit Reader, PDF-XChange Viewer, Sumatra PDF and Nitro PDF Reader.
There's some good news in the fact that 84 percent of vulnerabilities in all products had patches available on the day of disclosure in 2015. The number of zero day vulnerabilities at 25 was the same as in 2014.
For more detail and to download a copy of the full report you can visit the Flexera website.
Photo Credit: Sergey Nivens/Shutterstock
-

UK start up seeks to make online software research easier
Publié: mars 25, 2016, 1:37pm CET par Ian Barker

According to Google's Consumer Barometer Report 53 percent of people compare products, prices and features online before buying.
This is even more true of B2B buyers, with 89 percent saying they use the web as part of their research process.
When it comes to buying business software it isn't surprising that it can take days if not weeks to shortlist software options. Even then information regarding different product choices is fragmented across multiple locations -- emails, spreadsheets, PDF proposals, online meetings and many more.
This is bad news for software vendors too, as due to the slow and fragmented nature of the research process, they have to wait a long time to understand purchase decisions. Since most research is done online the space is dominated by a few large software companies. Most smaller software vendors have to rely on traditional marketing channels which drive up cost of customer discovery and customer acquisition.
London based start-up Comparesoft is looking to solve this problem. Using a data-driven algorithm, Comparesoft provides unbiased and vendor neutral software comparisons. Users can review usability, implementation, pricing and case studies within minutes and get an immediate practical software comparison. They can then chat online with prospective vendors and book instant meetings with their favorites. All of the information related to their software selection is in one convenient place.
John de Robeck, marketing manager at asset management specialist FMIS says, "Comparesoft is exactly what FMIS was looking for. Unlike other providers we use, Comparesoft is specifically geared to the UK market and so covers a key sector in our target market".
Currently in beta, you can discover more and try out the software comparison tool from the Comparesoft website.
Image Credit: alphaspirit / Shutterstock
-

Docker comes to Mac and Windows
Publié: mars 24, 2016, 5:44pm CET par Ian Barker

Today is the third birthday of the Docker containerization system and to celebrate the company is launching a beta program for Mac and Windows versions of its software.
It offers an integrated, easy-to-deploy environment for building, assembling, and shipping applications from Mac or Windows as well as having many improvements over Docker Toolbox.
Docker for Mac and Windows doesn't need a dedicated machine, making life easier for developers and providing easy access to running containers on a local host network. It includes a DNS server for containers, and is integrated with the Mac OS X and Windows networking system. On a Mac, Docker can be used even when connected to a corporate VPN.
Docker for Mac can be used at the same time as Docker Toolbox on the same machine, allowing developers to continue using Toolbox as they evaluate Docker for Mac. On Windows systems you need to stop Toolbox before using Docker for Windows.
"The Docker for Mac product has addressed all of these issues for us, installation has been significantly smoother thanks to the native Mac application and autoupdater. Official images now 'just work' with the Mac and the new development workflow allows engineers to quickly spin up new versions of services and develop software natively on the Mac against them, with everything just working", says Mat Clayton, Co-founder of Mixcloud, one of the few companies to have tried the software in private beta.
If you're interested in joining the beta program you can sign up to receive an invitation on the Docker website. Docker for Mac and Docker for Windows are at different stages of development, although they do share a significant code base. Docker for Windows will initially be rolled out to users at a slower pace but will eventually have the same functionality as Docker for Mac. Docker for Windows currently only ships on Windows 10 editions that support Hyper-V.
-

The rise of the advanced persistent bots
Publié: mars 24, 2016, 4:30pm CET par Ian Barker

Overall bad bot activity is decreasing, but the number of advanced persistent bots is up according to a new report.
The 2016 Bad Bot Landscape Report from Distil Networks reveals that 88 percent of all bad bot traffic has one or more characteristics of an advanced persistent bot, one that's able to mimic human activity and evade detection.
"When we dug into the bot activity in 2015, we identified an influx of Advanced Persistent Bots (APBs)", says Rami Essaid, co-founder and CEO of Distil Networks. "ABPs can mimic human behavior, load JavaScript and external assets, tamper with cookies, perform browser automation, and spoof IP addresses and user agents. The persistency aspect is that they evade detection with tactics like dynamic IP rotation from huge pools of IP addresses, use Tor networks and peer to peer proxies to obfuscate their origins, and distribute attacks over hundreds of thousands of IP addresses. A whopping 88 percent of 2015 bad bot traffic were APBs. This shows that bot architects have already taken note of traditional bot detection techniques and are finding new sophisticated ways to invade websites and APIs, in an effort to take advantage of critical assets and impact a business's bottom line".
Among the main findings of the report are that 46 percent of all web traffic originates from bots, with over 18 percent coming from bad bots. Medium-sized websites (those with a 10,001 to 50,000 Alexa ranking) are at greater risk, as bad bot traffic made up 26 percent of all web traffic for this group.
Chrome has edged out Firefox as the browser of choice for bad bot creators with over 26 percent of all user agents now using the Google browser. In addition 53 percent of bad bots are now able to load external resources like JavaScript meaning these bots can show up falsely attributed as humans in Google analytics and other tools.
The report finds that 39 percent of bad bots are able to mimic human behavior, so tools such as WAFs, web log analysis, or firewalls, which perform less detailed analysis of clients and their behavior, will likely result in large amounts of false negatives.
It also finds that 36 percent of bad bots disguise themselves using two or more user agents, and the worst APBs change their identities over 100 times. Multiple IP addresses are used by 73 percent of bad bots to rotate or distribute their attacks, and of those, a surprising 20 percent used more than 100 IP addresses.
While six out of the top 20 ISPs with the highest percentage of bad bot traffic originated from China, Amazon has appeared in the top five bad bot originators three years in a row. It's still the US that's the largest originator of bots, with over 39 percent of bot traffic, while India and Israel moved up to the two and three spots.
You can find more information by downloading the full report from the Distil Networks website.
Photo Credit: Gunnar Assmy/Shutterstock
-

Zero day OS X flaw can bypass System Integrity Protection
Publié: mars 24, 2016, 3:33pm CET par Ian Barker

Security company SentinelOne has released news of a major flaw in Apple OS X systems that can allow the bypassing of the latest System Integrity Protection security feature.
This zero day vulnerability is present in all versions of Apple's OS X operating system. It has been reported to Apple and patches will be available soon. SentinelOne’s lead OS X security expert, Pedro Vilaça, is presenting the full findings on this vulnerability today at SysCan360 2016 in Singapore.
System Integrity Protection is intended to limit the ability of a root account to access protected parts of iOS and OS X. But some programs, such as those that update the operating system, retain privileges. It's this that is being exploited by the flaw which allows programs to run arbitrary code on the device and bypass SIP.
To exploit the vulnerability, an attacker must first compromise the target system, which could be done via a spearphishing attack, or by an exploit in the user's browser. The vulnerability is said to be reliable and stable, and won't cause systems to crash. It's also able to avoid detection using techniques that traditional detection mechanisms, looking for more obvious warning signs, would miss. The good news is that, up to now, there's no evidence of it being used in the wild.
You can find out more about the threat and see a full copy of Vilaça's presentation on the SentinelOne blog.
Photo credit: studioVin / Shutterstock
-

User error is the leading cause of data loss in SaaS applications
Publié: mars 24, 2016, 11:10am CET par Ian Barker

Accidental deletion of information is the leading cause of data loss from SaaS applications, responsible for 43 percent in the US and 41 percent in the UK, ahead of data loss caused by malicious insiders and hackers.
This is among the findings of a new survey of IT professionals in the US and UK from cloud backup specialist Spanning which also has insights into who is responsible for SaaS data protection, organizational confidence in SaaS data protection, and the top concerns surrounding moving data to the cloud.
Among the report's other findings are that a gap exists between perception and reality of SaaS data protection responsibility. Security is the top concern when moving critical business applications to the cloud. But 80 percent of respondents have suffered some type of SaaS data loss and have similar fears related to future cloud data security.
In light of the EU-US Privacy Shield being put in place, IT professionals in the UK are taking a more cautious approach to data sovereignty than their US counterparts. However, the US leads UK in SaaS data protection confidence and the two countries differ most on security when it comes to SaaS adoption.
On both sides of the Atlantic, organizations are moving to the cloud by deploying similar types of SaaS applications. When given a choice of 14 common types of SaaS applications, the top two for both the US and UK were the same -- email/messaging and financial applications are either deployed in a public cloud now, or will be deployed in one in the next 12 months.
In the UK, HR software -- containing some of the most sensitive personal data about employees -- was the third-most chosen option, while in the US, it was IT infrastructure management. Both regions had customer relationship management and sales force automation software as their fourth-most implemented.
The report concludes, "The security of SaaS data is critical -- and Americans (80 percent) are more confident than British respondents (45 percent) in their organization’s ability to secure cloud data. This confidence may shift, however, as organizations continue to see SaaS data loss incidents occur -- almost 80 percent of all respondents experienced some sort of SaaS data loss. And, while 78 percent of US respondents, and 73 percent in the UK, are aware of standalone services that allow them to backup and restore SaaS information separate of the provider/application, only 37 percent in the US utilize them, and 31 percent in the UK".
More detail can be found in the full report which is available to download from the Spanning website.
Image Credit: Maksim Kabakou / Shutterstock
-

90 percent of US federal agencies are vulnerable to data threats
Publié: mars 24, 2016, 10:15am CET par Ian Barker

According to new research 90 percent of IT security leaders in US federal agencies say they feel vulnerable to data threats.
In addition 61 percent have experienced a past data breach, with nearly one in five indicating a breach in the last year. This is among the findings of the US Federal Government Edition of the 2016 Vormetric Data Threat Report from enterprise data protection company Vormetric and 451 Research.
The top barriers to adopting better security are named as skill shortages at 44 percent, and budgets at 43 percent. Despite news stories highlighting the threat of nation state hacking, the top external threat actors identified were cybercriminals at 76 percent, with nation state hackers coming a distant fourth at 47 percent.
Bright spots in the report include that 58 percent are increasing spending to offset threats to data, and 37 percent are increasing spending on data-at-rest defenses this year. The top categories for increased spending over the next 12 months are network defenses at 53 percent, followed by analysis and correlation tools at 46 percent.
Network defenses are "very" effective at safeguarding data, according to 60 percent of respondents, more than any other vertical and well above the US average of 53 percent. With data-at-rest defenses seen as the most effective tools for protecting data once other defenses have failed, surprisingly these were ranked last in terms of US federal spending plans, with just 37 percent planning to increase their spending on data-at-rest defenses, compared to the US average of 45 percent.
However, many respondents are planning to implement "newer" security tools that are more effective at protecting data even when other defenses have been compromised. These include cloud security gateways (40 percent), application encryption (34 percent), data masking (31 percent) and tokenization (27 percent).
"Albert Einstein's oft-used quote is fitting -- if doing the same thing over and over and expecting a different result isn't the definition of insanity, it is certainly a recipe for placing our nation’s critical assets at risk", says vice president of Marketing for Vormetric, Tina Stewart. "Public sector organizations need to realize that doing more of the same won't help us achieve an improved data security posture. More attention must be paid to techniques that protect critical information even when peripheral security has failed, and data-at-rest security controls such as encryption, access control, tokenization and monitoring of data access patterns are some of the best ways to achieve this".
More information is available in the full report which you can download from the Vormetric website.
Image Credit: Brian A Jackson / Shutterstock
-

Data scientists spend lots of time doing stuff they don't enjoy, but they still love their jobs
Publié: mars 23, 2016, 4:02pm CET par Ian Barker

Data scientists spend a lot of time doing things they don't like, such as sorting out problems with unprocessed information, but they still love their jobs according to a new survey.
The second annual Data Science report from data enrichment platform CrowdFlower shows that there’s a perceived shortage of data scientists, with 83 percent saying there aren’t enough to go around, up from 79 percent last year.
The results of asking how data scientists spend their time are revealing to. They spend 60 percent of their time acting as "digital janitors" cleaning and organizing data prior to processing. Only nine percent of their time is spent mining for patterns and only four percent building algorithms, the sort of tasks that we think of data scientists performing.
When asked which part of the job they enjoyed least, 57 percent named the data wrangling aspect of cleaning and organizing information. Collecting data sets was cited by 21 percent. The tasks they do the most are therefore the ones they get least enjoyment from.
Yet despite this data scientists overwhelmingly happy in their work. When asked to rank how happy they felt in their current position on a simple five point scale, 35 percent gave it a five and 47 percent a four, meaning that over 80 percent like their jobs.
The survey also asked respondents if they felt they had the right tools to do their jobs. Just 14 percent disagreed, indicating that enterprises are committed to giving data scientists what they need to succeed.
When asked about the skills that are most in demand, SQL came out top on 56 percent, followed by big data favorite Hadoop on 49 percent, Python on 39 percent and Java on 36 percent.
The report concludes, "As more and more organizations adopt data as a key driver of decision making, the importance of streamlined, well-oiled data science teams is going to remain paramount. But the current status quo probably isn't sustainable. On the one hand, we see a shortage of data scientists while on the other, they’re spending too much time cleaning and munging data. This is time that could be much better served doing predictive analysis and building out machine learning practices".
You can find out more about the report's findings on the CrowdFlower blog.
Photo Credit: Sergey Nivens / Shutterstock
-

Sitefinity delivers improved content management and customer analytics
Publié: mars 23, 2016, 1:21pm CET par Ian Barker

In modern fast-moving business environments, marketers need to be able to respond quickly to changes and deliver appropriate content.
To help deliver this ability, business transformation specialist Progress is releasing new versions of its Telerik Sitefinity platform for content management and customer analytics.
The new release, Telerik Sitefinity 9.0, provides new features, enhancements and architectural improvements to help digital marketers, and the departments that support them, achieve better agility with their online campaigns.
It allows marketing, development and IT to work more effectively together to increase digital marketing agility. New features, including improved personalization, multilingual asset support, multipage forms and a 360-degree customer view, enable marketers to be more effective in driving customer engagement. At the same time, Sitefinity 9.0 provides developers with greater extensibility that’s critical for achieving competitive advantage.
"To deliver the real-time, hyper-personalized, responsive content customers expect, marketing organizations have no choice but to become more agile, as agility can mean the difference between being a leader or laggard", says Svetozar Georgiev, senior vice president of Application Platforms at Progress. "Relying on IT and development for day-to-day tasks impedes digital marketing agility and hurts a team's ability to rapidly deliver innovative, personalized customer experiences. Spanning development, administrative and marketing capabilities, Sitefinity 9.0 delivers a powerful platform that supports rapidly changing business initiatives and messaging -- helping marketers respond more nimbly in today’s fast-paced, multichannel world".
Key features for marketers include improved personalization so campaigns can segment the audience and make use of behavioral and demographic data. A 360-degree customer view brings together all customer interactions within the organization, from website page visits to defined conversions, for dynamic decision-making using extended contact profiles. Multilingual asset support ensures appropriate content is delivered to global audiences, and multipage forms support cuts abandonment rates resulting from long, cumbersome forms and enables marketers to split long forms into smaller steps, improving the end-user experience.
For developers continuous delivery allows roll out of new website functionality with minimum effort, new APIs make deployment easier, and simplified widget creation improves performance for precompiled views, and increases developer productivity. There's also an integrated mobile solution to create easy-to-integrate, content-driven mobile apps with Telerik Platform.
You can find out more about the latest release on the Sitefinity website.
Photo credit: ra2studio / Shutterstock
-

Thycotic plans $100 million security software giveaway
Publié: mars 22, 2016, 5:24pm CET par Ian Barker

Privileged accounts exist in all areas of business IT and if compromised they can provide an external attacker or dishonest insider access to sensitive data.
Account management company Thycotic wants to help businesses protect themselves and so is giving away a no-cost version of its Secret Server package to guard against attacks that target privileged accounts.
Secret Server Free will provide customers with a package valued at $5,000, at no-cost, to protect their privileged account credentials. By the end of the year, the company plans to protect more than 20,000 global organizations against cyber-attacks giving away a total of total $100 million worth of free privileged account security software.
"At Thycotic, we are on a global mission to help IT teams worldwide protect their organizations from hackers and have already done so for more than 3,500 organizations", says James Legg, CEO of Thycotic. "With the introduction of Secret Server Free, we will continue towards accomplishing this undertaking by making it easier, and more affordable, for IT teams to prevent cyber-attacks leveraging our industry-leading PAM security software at no cost to them".
Features of the free package include support for up to 100 users, protecting up to 1,000 privileged account passwords, integration with Active Directory, Remote Desktop tunneling with PuTTY, and password storage using military-grade encryption.
You can find out more and sign up for a copy of Secret Server Free on the Thycotic website.
Photo Credit: Mmaxer/Shutterstock
-

New platform aims to break down barriers to big data adoption
Publié: mars 22, 2016, 4:22pm CET par Ian Barker

Big data deployments are increasingly shifting from lab settings to full production environments. But there are a number of security and QoS (quality of service) challenges that can slow this process.
Big data company BlueData is launching the latest release of its EPIC software platform, introducing several security and other upgrades to provide a smoother Big-Data-as-a-Service experience as well as support for new applications and frameworks.
Complexity remains a major barrier to adoption for big data technologies like Hadoop and Spark. BlueData's software makes it easier to deploy big data infrastructure and applications. It uses Docker containers to provide a self-service BDaaS experience on-premises together with the highest levels of security and performance for big data analytics in the enterprise.
"BlueData is working with customers in every industry and at all stages of their big data journey, from early experimentation and lab environments for dev/test to enterprise-wide production implementations", says Kumar Sreekanti, CEO of BlueData. "Our solution is highly flexible and scalable, supporting any big data use case and accelerating our customers’ deployments as they move through each stage of their journey. This new spring release is another key milestone for us, solidifying BlueData's position as the leading infrastructure platform for Big-Data-as-a-Service in the enterprise".
The latest release incorporates many features and functionality enhancements requested by BlueData's customers across multiple industries -- including financial services, pharmaceutical, healthcare, technology, telecommunications, energy, government, and education.
The enterprise version of BlueData's platform now provides additional security and governance capabilities to meet enterprise-class auditing and regulatory compliance requirements. Other new functionality includes more granular resource management controls, QoS-based allocation, performance optimizations, and quota enforcement for multi-tenant big data deployments. In addition there’s extended support for applications and tools including Cloudera Navigator and Ranger for data governance and security administration; HAWQ for massively parallel processing analytics; and Geode (Gemfire) as well as Cassandra and Kafka for real-time analytics.
The Spring release is available now and will be featured at the Strata + Hadoop World event in San Jose, California next week.
Image Credit: Maksim Kabakou/Shutterstock
-

Kyvos brings big data to Microsoft Azure
Publié: mars 22, 2016, 3:46pm CET par Ian Barker

Many organizations are looking at the benefits they can gain from big data but are put off by the infrastructure costs involved.
Analytics company Kyvos Insights is aiming to make big data more accessible by making its scalable, self-service online analytical processing (OLAP) solution available to users of Microsoft Azure HDInsight.
"Supporting a cloud platform like Azure HDInsight that you don’t have to manage and can get up and running in minutes with our solution is very appealing to our customers", says Ajay Anand, vice president of products at Kyvos Insights. "Now, through this relationship, Azure HDInsight users can analyze their data very quickly with Kyvos and the other BI tools they use. In addition, they benefit from not having to wait for IT data groups to provision hardware, making it easy to perform activities such as creating a cluster faster than ever before".
Kyvos helps business users to visualize, explore and analyze big data interactively using 'cubes on Hadoop' technology. By providing greater levels of scalability and interaction directly on Hadoop -- with no need for programming -- Kyvos helps users gain insights that can lead to better business decisions, increased understanding of customers, more accurately targeted marketing and greater profitability.
"Microsoft is focused on simplifying big data and advanced analytics to give organizations the fastest way to achieve business transformation," says Tiffany Wissner, senior director of data platform marketing at Microsoft. "By giving users the ability to do OLAP analysis with Kyvos on top of data in Hadoop with Azure HDInsight, our collective customers can achieve insights faster and easier to positively impact their business."
You can find out more about big data solutions from Kyvos Insights on the company's website.
Photo Credit: T.L. Furrer / Shutterstock
-

Webscale offers a fast track to delivering web applications
Publié: mars 22, 2016, 2:36pm CET par Ian Barker

Running an application or server in the cloud has many advantages, but it doesn't guarantee scalability. It can be hard to predict demand, leading to infrastructure having to play catch up at peak periods.
Application delivery specialist Webscale Networks is aiming to improve things with the launch of its new platform offering mid-market e-commerce and enterprise companies a fast track to the cloud.
Webscale features predictive auto-scaling, multi-cloud, performance optimization, security and manageability. Based on nine years of research into predictive analytics, Webscale's patented, dynamic resource allocation IP sets it apart from traditional application delivery or load balancing solutions. Its ability to look ahead at demand and automatically take whatever action is needed to ensure a website stays fast and available, makes it easy to use by anyone within an organization.
"Mid-market businesses, especially e-commerce companies competing in tough markets that want to grow while they manage spend, need to be looking to the cloud as their infrastructure of choice -- Webscale gets them there", says Sonal Puri, CEO of Webscale. "Webscale provides complete control over a web application, offering predictive auto scaling, single-screen monitoring, self-healing and multi-cloud support. With the addition of free cloud migration services for qualifying customers, Webscale is now the fastest, most powerful and affordable path to the cloud".
Features include predictive auto-scaling technology that looks ahead of traffic surges and scales out, and back, with greater accuracy, so customers only pay for what they use. Webscale is cloud-agnostic, so it can be used by businesses deploying a multi-cloud strategy. Built and delivered as-a-service, it works across all public, private or hybrid cloud infrastructures, as well as static hosting environments.
It also offers a PCI-DSS 3.1 certified web application firewall that provides comprehensive functionality with support for security policies including SSL/TLS encryption support, DDoS attack mitigation, and more.
Webscale is available in four versions (Free, Lite, Pro and Enterprise), you can find out more and request a free trial on the company's website.
Image Credit: Chaiyapop Bhumiwat / Shutterstock
-

New platform delivers scalable account-based marketing
Publié: mars 21, 2016, 5:19pm CET par Ian Barker

Account-based marketing (ABM) is one of the most effective approaches to B2B marketing, but historically users of the technique have struggled to scale it beyond a few accounts.
San Francisco-based YesPath is using the MarTech marketing technology conference to launch its new ABM offering using algorithms to select the right content and get it to the right person at the right time.
"Every day, companies are missing out on revenue because marketing and sales are not coordinated", says YesPath CEO Jason Garoutte. "When Sales learns something about a prospect's goals, that information does not get used in content or campaigns. Conversely, when Marketing collects data from digital campaigns, that information is not used by Sales. The problem affects every stage of the revenue cycle, from new business to renewals and upsells".
YesPath is a SaaS platform that constantly monitors a sales team's list of target accounts. It builds account profiles using massive amounts of data culled from the web. Based on these profiles, an engagement engine matches the right content to each account.
For example, if a marketing team wants to tell different stories for different use cases, YesPath can monitor a list of target accounts, watching for interest in those cases. When an account shows interest, YesPath can trigger an email to share appropriate content. It can also queue up a special offer for when that account visits the website. YesPath can also alert sales staff that it's time to place a call to a customer.
YesPath uses an Intent Network, which analyzes signals of interest across the broader web. This gives marketers insight into the activity of potential customers who may not even have visited their website or otherwise shown direct interest.
The Intent Network uses data from partner Bombora, which tracks consumption of content across 3,000 b2b publisher sites, to detect changes in account interests. Based on these signals, YesPath learns which accounts are "in market" and whether they’re finding their way to the marketer's content. By combining this intent data with marketers' existing data it generates a more complete picture of the account and can power real-time content recommendations.
You can find out more YesPath on the company's website.
Image Credit: donskarpo / Shutterstock
-

US companies still struggle with innovation
Publié: mars 21, 2016, 3:17pm CET par Ian Barker

Businesses in the US have been struggling with innovation for the past three years and things show no signs of improving according to a new survey from professional services company Accenture.
The survey of managers and executives in 500 companies across the US reveals that 60 percent say their companies don't learn from past mistakes. This is nearly double the 36 percent who admitted to this three years ago in a similar survey.
In addition 72 percent say that their firms often miss opportunities to exploit underdeveloped areas or markets versus 53 percent three years ago. Sixty-seven percent also believe their companies are risk averse, a large increase from 46 percent in the previous survey.
The survey shows that 82 percent admit they don't distinguish their innovation approaches between incremental and large-scale change -- meaning they use a single one-size-fits-all approach to achieve different goals. Most respondents say they have big innovation ideas but are missing an organizational home with the company, as a result their ideas often go nowhere.
"A significant gap exists between what US companies want to achieve in the innovation arena versus what they are able to do", says Adi Alon, a managing director with Accenture’s Strategy practice. "They want to innovate yet they need to take different and bolder actions to achieve transformational, major revenue-generating innovation. True innovation requires aggressive changes in technologies, operating models and talent".
Despite their companies' innovation shortcomings, respondents are more bullish about disruptive innovation than they were three years ago. For example, 84 percent say they believe innovation is key for their long-term success compared with only 67 percent in the earlier survey. The same number of respondents say they're looking for the "next silver bullet", in terms of a market-defining innovation, rather than incremental changes to the same products. Creating new products is a priority for almost half (47 percent) of respondents, an increase of 20 percentage points from three years ago.
You can find out more about the report's findings, as well as recommendations for how business can improve their approach to innovation, on the Accenture website.
Photo Credit: xavier gallego morell/Shutterstock
-

20 percent of employees would sell their passwords
Publié: mars 21, 2016, 11:04am CET par Ian Barker

According to new research from identity management company SailPoint one in five employees would be willing to sell their work passwords to another organization, up from one in seven last year.
Of those who would sell their passwords, 44 percent would do it for less than $1,000, and some for less than $100. This is made worse by the fact that 65 percent admit to using a single password among applications and 32 percent share passwords with their co-workers.
Other findings include the worrying fact that more than two in five employees still have corporate account access after they leave their job. In addition 26 percent uploaded sensitive information to cloud apps with the specific intent to share data outside the company. Also one in three employees purchased a SaaS app without IT's knowledge, a 55 percent increase from last year. Reasons for not involving the IT department include because it's faster (49 percent), because IT adds too much process (40 percent), and IT over complicating things (21 percent).
The data comes from a survey of 1,000 office workers at large organizations (with at least 1,000 employees) across the US, UK, Germany, France, the Netherlands and Australia. It reveals a disconnect between employees' growing concern over the security of their personal information and their negligence over data security practices in the workplace.
"This year's Market Pulse Survey shines a light on the significant disconnect between how employees view their personal information and that of their employer, which could also include personal information of customers", says Kevin Cunningham, president and founder of SailPoint. "Today's identity governance solutions can alleviate the challenge of remembering several passwords and automate IT controls and security policies, but it's imperative that employees understand the implications of how they adhere to those policies. It only takes one entry point out of hundreds of millions in a single enterprise for a hacker to gain access and cause a lot of damage".
More information is available in the full report which can be downloaded from the SailPoint website.
Image credit: Gunnar Pippel/Shutterstock
-

Communifire makes building an intranet easier for smaller businesses
Publié: mars 18, 2016, 4:38pm CET par Ian Barker

The use of an intranet helps businesses promote engagement in teams and enable staff to become more productive. But often intranets are seen as the preserve of large corporations.
Software company Axero is launching the latest version of its Communifire intranet platform aimed at small and medium enterprises.
Communifire 5.2 offers an array of new features that improve the user experience for administrators, enabling organizations to unlock the value of the platform and improve employee communication, collaboration and performance.
The main new feature is Page Builder, an easy-to-use, drag-and-drop interface that administrators can use to create page layouts. It turns elements into visual building blocks that allow anyone to understand and edit the layout and content of their pages without touching any code.
The latest Communifire also offers gamification capabilities that allow users to recognize other users by granting them badges. Badges can be earned by completing a customized series of actions within the community.
"Axero's mission is to empower organizations and employees with all the tools and features they need to perform their best," says the company's cofounder and President Tim Eisenhauer. "Communifire has always grown and evolved based on the voice of our customers, and version 5.2 reflects our ongoing commitment to delivering the best, most effective intranet software on the market".
Other updated feature include search enhancements to allow users to find content more easily, these include a 'fuzzy search' feature that tries to predict what users are looking for and accounts for typos and misspellings. There's also the ability to receive more focused digest emails, and an updated chat and messaging interface.
For more information and a 14-day free trial you can visit the Axero website.
Image Credit: alphaspirit / Shutterstock
-

Off-the-shelf BYOD systems bring privacy and security risks
Publié: mars 18, 2016, 3:56pm CET par Ian Barker

When companies allow staff to use their own systems to access corporate data, the devices used can often be outside of IT department control.
But how much of a security and privacy hazard is presented by a new off-the-shelf laptop? Security company Duo Labs set out to discover the risks by buying a number of OEM Windows 10 machines in the US, Canada and the UK and testing them for vulnerabilities.
All of the systems tested were found to have privacy issues, some were more serious than others and many of them affected all the machines. Network protocol-related security issues affected all the laptops, starting as soon as the laptop appeared on the network during initial boot.
Following the application of Patch Tuesday updates, some privacy settings were reset to their default values, without the user being notified that they'd changed. Default laptop settings and protocols make it easier for an attacker to sniff, grab, view and redirect an unsuspecting user’s traffic especially on public networks.
Bloatware and trial software was at the root of questionable traffic on some of the systems too. The OEM Microsoft Signature Edition machine tested came in for praise here as it had less unnecessary software installed. It did, however, still have some of the Windows 10 privacy concerns identified elsewhere.
Systems with McAfee security trials installed were found to contain web bugs that could be used to track and serve advertising to users. "We observed web bugs which are used typically by advertisers to track surfing habits. You'd expect to see this in web browsers as they're a reality of internet advertising today. It seems curious to us that a security company would do this, because as an attacker if I were to compromise a third-party advertising company I would then have the ability to feed my content out to all the systems using that platform," says Steve Manzuik Director of Research at Duo. "I don't think there's anything nefarious going on, they're using it to track their trial versions and get people to buy the software, but it seems odd that this would be the route they decided to use".
More information and the full report, along with recommendations for making out-of-the-box machines more secure, is available from the Duo website.
Image Credit: Maslowski Marcin / Shutterstock
-

Druva extends data protection to popular enterprise cloud apps
Publié: mars 17, 2016, 5:08pm CET par Ian Barker

The increasingly decentralized world of work means that data can be in many different places, on desktops, mobile devices, or in the cloud.
This creates challenges for security and governance, especially if there's a need to adhere to legal and compliance rules. Data protection company Druva wants to guard information wherever it's stored and is extending its inSync offering to cover Box, Google Apps for Work and Exchange Online.
Druva inSync provides a single access point for viewing, monitoring and managing end-user data without having to manually access separate data sources through different solutions. In addition it automates and unifies backup, archive and governance capabilities across multiple cloud applications. New Microsoft Exchange Online support helps companies meet their hosted email and message-based governance needs. Cloud applications support also protects data shared via online file sharing and content management service Box -- which Druva has entered into a recent partnership with -- and the Google Apps suite of cloud computing productivity and collaboration software tools including Gmail, Google Drive and Google Docs.
"A user-centric approach to data protection and governance is key to a company’s managing data throughout its entire lifecycle, and across, among and between various devices, endpoints and the cloud," says Jaspreet Singh, CEO of Druva. "Today's businesses need a single solution for data availability and corporate governance -- eDiscovery, audit, search and compliance management covering data on cloud apps and endpoints -- and that's what Druva is delivering. This expanded data protection follows the user, something that is imperative as enterprises make use of new cloud services while working to adhere to data availability and corporate governance policies".
Key features include automated compliance management powered by full text search capabilities and built-in compliance templates for the likes of HIPAA. There's built-in legal hold workflow for eDiscovery to quickly collect and preserve data in place for investigative or litigation needs. Forensic-based collection and chain of custody reporting to ensure legal admissibility and remove the risk of information being corrupted.
A federated search facility can quickly locate files across the organization and all services. Tamper-proof audit trails give full data and user tracking for investigation and compliance audits, and automated compliance alerts enable visibility into latent data risks so they can quickly address them.
Druva inSync for Box and Office 365, including OneDrive and Exchange Online, is available now, Google Apps is in limited availability, becoming generally available next month. You can find out more on the Druva website.
Photo Credit: Slavoljub Pantelic / Shutterstock
-

Enterprise data platform integrates with Slack
Publié: mars 17, 2016, 4:14pm CET par Ian Barker
All too often business communication and data are separate. This means that if you need to refer to something while chatting with a colleague you have to break off and open another application to do so.
In order to make data more accessible and collaboration easier, business analytics specialist Looker is announcing a new data platform that integrates with the popular Slack communication tool.
Called Lookerbot, it seeks to make enterprise collaboration more efficient by bringing real-time data into any conversation in Slack, eliminating the need to shuffle through applications looking for information.
"Data has been something people do out-of-cycle. Data needs to be part of the conversation, no matter where it's happening," says Frank Bien, CEO of Looker. "The world is moving on from the current swath of business intelligence tools that simply report a view of the past in a kludgy user interface. Accessing current data in collaboration tools like Slack helps everyone make better business decisions, faster. Looker's data platform makes these conversations possible".
Lookerbot is built using Looker's API and SDK and is one of many integrations built on the data platform. Users enter a simple command in Slack and Lookerbot returns the answer within the Slack conversation. The data is displayed in Slack as it appears in Looker with a complete array of visualization types (charts, maps, and tables), including custom visualizations and colors.
Michael Erasmus, Data Analytics Lead at Buffer says, "Buffer is a distributed company so Slack is basically our office. The majority of our work lives in Slack. Having Looker, one of our most critical tools, integrate into every conversation in Slack is incredibly powerful. It means that when decisions are being made at every stage of our process, we have data at our fingertips, improving transparency and collaboration".
More information about using Looker with Slack is available on the company's website.
-

Consumers believe retailers don't understand them
Publié: mars 17, 2016, 3:20pm CET par Ian Barker

Retailers have long depended on email marketing as an affordable and effective way to reach their customers, maintain loyalty and drive purchases.
On average, consumers opt-in to receive emails from two retailers and this can lead to them receiving around 13 emails a week. But a new survey reveals that 82 percent of people feel that this constant flow of offers means that the retailers they are loyal to don't understand them.
The survey from sales solution company First Insight shows that two-thirds of shoppers feel that receiving six or more emails a week from retailers is too many. Consumers only open one in four of the emails they receive, and feel that 95 percent of the messages they get are not at all relevant to them. Several consumers surveyed say they have taken action, with 44 percent reporting that they've unsubscribed from a retail email list in the past six months, and 40 percent saying that they would go out of their way to shop at a store that doesn't waste their time with irrelevant email offers.
"Right now we're seeing a huge disconnect in the conversation that retailers think they are having with customers through email marketing efforts," says Jim Shea, Chief Commercial Officer of FirstInsight. "The communications are not only too frequent but are basically meaningless to consumers. What consumers really want is for retailers to take the time to know them and make recommendations about clothing or products that are in line with their personal taste".
A lighter touch and more personalized approach with email marketing seems like the best way to generate business. Their favorite retailers only send them one or two emails a week according to 61 percent of those surveyed, and 43 percent say they would be more likely to open emails from retailers if they knew those messages contained personalized suggestions of products or clothing that aligned with past purchases, rather than simply promoting products that were generally available or reduced.
The survey polled over 1,100 people across the US and you can download the full report from the First Insight website.
Image Credit: Balefire/Shutterstock
-

Javelin attack simulator spears security gaps
Publié: mars 17, 2016, 2:49pm CET par Ian Barker
Web gateways remain one of the most attractive attack routes for hackers, and many of the most commonly used gateways remain vulnerable.
According to attack detection specialist Seculert popular gateways have allowed more than 40 percent of malicious communications to succeed in 2015. To combat this the company is launching a new outbound attack simulator called Javelin.
While it doesn't use actual malware, the Javelin simulator replicates the latest and most dangerous attacks on an organization's gateway through individual attack communication simulations. It provides instant results, and then allows users to acquire a gateway update package. This package contains details about the simulated attacks, a license to run unlimited attack simulations, and fixes to update the enterprise's gateway solutions in order to contain the attacks should live attacks present themselves.
"In today's threat landscape, the ability to simulate the latest, real-world attacks and measure the efficacy of web gateway response is one of the keys to maintaining an effective security posture," says Richard Greene, Seculert's CEO. "With Javelin, enterprises will know, for the first time ever, how their perimeter defenses will perform in the face of the most malicious attacks we see in the wild each day".

Javelin has been in a closed beta test for two months. As well as highlighting their own security exposures, it gives enterprises a tool to assess how well their business partners are protecting their intellectual property.
Available now, Javelin needs no hardware or software to be installed. You can find out more and request a trial on the Seculert website.
Image Credit: rosedesigns / Shutterstock
-

IT teams choose between performance and security
Publié: mars 16, 2016, 4:04pm CET par Ian Barker

Although security breach stories regularly make the headlines, a new survey shows that the biggest worry IT teams have with current security solutions is that they slow down the system.
The study from endpoint security specialist Barkly also reveals that while only half of respondents are confident in their current endpoint solution, 80 percent believe that effective endpoint security is possible.
When asked about the downfalls of their security solutions, 41 percent of respondents say they are dissatisfied with their current solution because it slows down their system. If security products are slowing systems, and by extension lowering productivity, it may be that users are taking insecure shortcuts to improve efficiency, such as using unauthorized third-party apps or connecting unsanctioned devices to the network. In addition the survey reveals that the other major issues IT teams have with current solutions are that they require too many updates (36 percent), are too expensive (33 percent) and provide no protection against zero-day attacks (33 percent).
In spite of increased spending on security, only 50 percent of respondents say they are confident in their current solution. More than half of respondents (54 percent) don’t believe their organization can effectively measure security return on investment, and only 25 percent have confidence in their colleagues’ cybersecurity awareness.
The research also shows a difference of opinion between IT pros and the C-suites on security. Respondents indicated that they believe IT teams prioritize security higher than the C-level, with nearly 40 percent of respondents saying that IT teams believe it to be an essential priority, compared to only 27 percent of C-level executives. There's also a disconnect between IT teams and the C-level when it comes to their biggest concerns -- while the C-level is more worried about insider threats, IT teams feel that careless, uninformed employees are a higher risk. When asked how they would improve security within their organizations, C-suite respondents say they would rather buy new software while front-line IT pros would prefer to educate their colleagues.
"This report proves that from the CISO to the entry-level IT pro, organizations must be better aligned when it comes to security. When there's a disconnect in priorities, level of understanding and measurement, even a seemingly strong security initiative is destined to fail," says Jack Danahy, co-founder and CTO of Barkly. "Once teams understand each other's priorities and concerns around security, they can implement the tools they really need, that will best protect their endpoints from ever-increasing, complex threats".
The full 2016 Cybersecurity Confidence Report can be downloaded from the Barkly website.
Photo credit: dencg / Shutterstock
-

Most IT professionals believe current privacy and consent tools are inadequate
Publié: mars 16, 2016, 3:11pm CET par Ian Barker

The regulatory environment for data is in a state of change at the moment with many countries introducing legislation to control the flow of information. This combined with growth of the IoT and digital economy is posing major challenges for business.
A new survey by identity management company ForgeRock finds 96 percent of surveyed IT professionals agree that there is an increasing need for dynamic and flexible privacy tools. And that these need to be adaptable to future borderless regulatory requirements and consumer expectations.
The study of more than 300 IT professionals across 38 countries also finds that only nine percent believe current privacy and consent methods are adequate. Emerging European regulations for data protection are creating a need for better tools and standards for ensuring personal data protection, privacy and consent according to 96 percent.
In the US 84 percent of respondents (and 87 percent of Asia Pacific and Japan-based respondents) believe the US will eventually adopt similar personal data protection regulations to Europe. However, only 66 percent of EMEA-based respondents believed that the US will eventually adopt similar personal data protection regulations.
95 percent of respondents agree that individuals are becoming more concerned about their personal data privacy and their ability to control, manage and share data about themselves online. They also agree that organizations want to build trust by giving customers the ability to consent to data sharing and control over where their personal data is shared.
"As our survey illustrates, coping with regulation -- privacy or otherwise -- is no longer just a cost center for organizations. As connected devices and technologies take on a greater role in public and private life, there are massive business benefits to building in new identity and data privacy solutions that can scale over time," says ForgeRock's CEO, Mike Ellis. "Organizations clinging to legacy identity management technologies -- which are currently inadequate -- will be at a major disadvantage".
You can read more about the survey's findings on the ForgeRock blog.
Photo credit: Ivelin Radkov / Shutterstock
-

The most disruptive business technologies
Publié: mars 16, 2016, 11:40am CET par Ian Barker

You'll quite often hear talk of how technology can disrupt business. A survey carried out at Microsoft's 2015 Global CIO Summit in October suggests that CIOs believe 47 percent of their company's revenues will be under threat from digital disruption in the next five years.
But what does this disruption really mean? Microsoft has produced an infographic looking at the five major technologies that are doing most to disrupt the business world.
These include mobile computing, with 5G and other developments expected to boost growth in coming years. Additional automation is expected to provide timelier access to information, leading to faster decision making.
Big data is expected to make a major difference to business intelligence and become a driving force in the global economy. This will be supported by the Internet of Things which is expected to grow five fold to 250 billion devices over the next decade.
Finally although the cloud has been around for may years it's still a major disruptive force and its economic influence is expected to rise to $6.2 trillion.
You can see the full infographic below or on the Microsoft website.
Image Credit: Peshkova / Shutterstock
-

BetterWorks expands its business suite with performance development and strategic planning
Publié: mars 15, 2016, 4:43pm CET par Ian Barker

Enterprises thrive on being able to set and manage goals. BetterWorks software provides the tools to do this and the company is now expanding its offering by adding performance development and strategic planning modules to its operational suite.
This means it now provides a comprehensive business operating platform combining planning, strategic execution and people development across a single system.
"The modern workforce is demanding a more frequent, open and collaborative solution to workplace operations," says Kris Duggan, CEO of BetterWorks. "We believe the future of work requires a business operating system that connects the dots between operationalizing the business and developing its employees".
The performance development module enables frequent, lightweight, two-way conversations between managers and their employees. Performance conversations can be built around the employee’s goals and top work priorities. Over the coming quarters, BetterWorks will roll out additional 360-feedback tools focused on individual work as well as contributions to company values.
Strategic planning via the Plans module lets users create multi-period views of goals to support agile, long term operational planning, and turn strategy into an actionable plan. This allows organizations to break annual plans into sizable, quarterly goals, update and communicate strategy as priorities of the company shift and allocate resources and planning more effectively.
"When asked to identify the single greatest challenge to executing their company’s strategy, 30 percent cite failure to coordinate across units, making that a close second to failure to align (40 percent)," says Donald Sull, Researcher at MIT. "Aligning on strategic objectives is crucial for businesses striving for operational excellence. BetterWorks Plans will help organizations overcome one of their most difficult challenges: connecting strategy with execution".
Both new modules are available now for an additional monthly fee, visit the BetterWorks website for more information.
Image Credit: Syda Productions / Shutterstock
-

Registration-as-a-service makes for easier customer authentication
Publié: mars 15, 2016, 3:23pm CET par Ian Barker

With so much choice available online, if a business doesn't deliver on meeting customer expectations then it's likely to lose out. One of the main challenges in keeping customers happy is delivering effective authentication while maintaining security.
Identity management company Gigya is releasing a new registration-as-a-service (RaaS) offering to enable enterprises to more effectively authenticate consumers with consistent cross-device experiences.
The system provides a flexible set of REST APIs that support the integration of end-to-end user registration systems across web properties, mobile applications and connected devices. These are complete with identity validation, progressive profiling and responsive design. The new features allow businesses to minimize development and maintenance costs, build fully-customized registration forms and maximize conversion rates.
"Great customer experience has become the new market requirement for growing acquisition rates and expanding relationships, with customer identity and access management (CIAM) technologies at the core," says Troy Abraham, Gigya's SVP of Global Services. "With the ultimate goal of enabling our clients to exceed their end-users' expectations, the GigyaWorks program has been created to help global enterprises capture, manage and leverage customer data while educating them around key market trends and processes every step of the way".
Capabilities of Gigya's RaaS include risk-based authentication (RBA) which takes account of a combination of IP address and device-based information. Using this enterprises can implement additional layers of identity validation when certain anomalies occur. For example, if a user logs in from a different country.
It includes password-less mobile authentication using one-time codes sent via SMS, eliminating the need to remember username and password combinations. It's designed to work and look good on any mobile application or connected device. An upgraded UI builder allows brands to easily edit registration screens using a simple drag-and-drop interface, as well as giving them the ability to simulate how registration flows will look on different devices with the click of a button.
More information about RaaS is available on the Gigya website.
Image Credit: Kirill Wright / Shutterstock
-

Smartsheet delivers greater visibility into collaborative projects
Publié: mars 15, 2016, 2:00pm CET par Ian Barker

Enabling efficient collaboration on projects is key to success in business and there are many platforms to enable it. But it can sometimes be hard to fully understand what's happening inside a particular task.
One of the leading collaboration platforms, Smartsheet is addressing this by launching Sights, a new product that delivers visibility into the work being done within Smartsheet environments.
By putting important information in front of the right audiences at the right times, Sights aims to deliver positive business impact by enhancing organizational speed and performance. Its ease of use and flexibility enables users to configure the product themselves, and gives teams the ability to customize how they visualize and derive insight from their work.
"Sights is a game-changer for our customers, giving them the power to amplify the value of the important work they’re doing on our platform," says Mark Mader, president and CEO of Smartsheet. "The valuable insights they derive from Sights go well beyond a surface-level look at productivity -- they enable individuals and teams to work smarter and make smarter decisions, driving enhanced organizational speed and performance".
Features of Sights include a drag and drop layout that makes it simple for any Smartsheet user to create a Sight by selecting widgets and dragging them into position. Sight widgets display data sources in visual styles including metrics, rich text, lists, grids and more. The look can be customized too using colors, fonts, sizing and text.
Sights can include any information held in Smartsheet plus links to information outside the package, so it can deliver a complete view of projects and processes. Sharing permissions can be set specific to each Sight so only the right set of viewers see it, and only people with administrative rights can change it.
More information on Sights is available on the Smartsheet website.
Photo Credit: nmedia/Shutterstock
-

New cloud tool links big data to business intelligence
Publié: mars 15, 2016, 1:14pm CET par Ian Barker

Big data can provide a useful source of insights for business analysis. But providing access to it can mean significant IT effort and the use of expensive, off-the-shelf solutions.
Altiscale the big data as a service specialist is launching a new Insight Cloud self-service analytics solution to provide a bridge between big data and business users.
It aims to simplify the connection between big data and the end user, as well as bypassing the need for costly, proprietary solutions. Altiscale Insight Cloud should make it faster and easier for business analysts to benefit from the rich, detailed data held in the Hadoop data lake.
Using a converged architecture, it eliminates the need for a separate relational data store for aggregated data. This reduces the cost and management burden on the organization, while allowing easier scalability from tens of terabytes up to petabytes. The converged architecture also minimizes data movement and replication across environments.
"Our enterprise customers first wanted to have a powerful, affordable solution to solve their Big Data challenge, which we provided with the Altiscale Data Cloud," says Raymie Stata, CEO and founder, Altiscale. "Today we are introducing the Altiscale Insight Cloud, which solves the challenge of bringing Big Data to a broader range of users, so that enterprises can quickly develop new offerings, better target customers, and respond to shifting market or operational conditions. It's a faster and easier way to get from Big Data infrastructure to insights that drive real business value".
Insight Cloud will be on display at the Strata+Hadoop World conference from March 29-31 in San Jose, or you can find out more on the Altiscale website.
Image Credit: Tashatuvango / Shutterstock
-

SIOS updates its machine learning solution for virtual environments
Publié: mars 15, 2016, 11:17am CET par Ian Barker
Since the launch of its machine learning tool for IT analytics last year, SIOS Technology Corp has released regular updates to help maximize the availability and efficiency of virtualized environments.
New features in SIOS iQ 3.5 deliver greater accuracy and precision in capacity utilization and performance analysis for VMware environments. It also includes dashboard enhancements for improved usability and a 'graphical topological impact' view to enable faster identification and resolution of issues.
"Legacy monitoring tools provide data about individual objects, such as CPU or capacity utilization). When a performance problem arises they leave IT staff to compare data points to make educated guesses about both the root cause and potential solution," says Jerry Melnick, president and CEO of SIOS. "SIOS iQ not only eliminates this guesswork by precisely identifying the cause, it recommends specific steps to resolve it".
Key features of the latest release are capacity forecasting analysis, this allows SIOS iQ to understand capacity utilization pattern and forecast how many days remain before data stores run out of free space. This allows enterprises to optimize infrastructure without risking costly emergencies. It can be used with the existing SIOS iQ Snapshot Waste analysis feature to optimize storage and maintain a predictable budget.
In addition enhanced root cause analysis adds symptom analytics and graphically describes the topology of the impacted objects, visually displaying the infrastructure issue to the user. It can provide a deep understanding of issues by employing advanced topological behavior analysis to get to the root cause of performance issues without the need to manually analyze data logs or compile and compare charts.
SIOS iQ 3.5 is available now, more information and a free trial is available on the company's website.
-

How APIs are key to digital success
Publié: mars 4, 2016, 12:25pm CET par Ian Barker

In the digital world it's increasingly APIs that hold everything together, allowing information to be easily shared between applications.
A new study from SmartBear Software gathered responses from over 2,300 software professionals around the world to paint a picture of the current state of the API industry.
Among the findings are that demand for APIs is still growing, one in five respondents only began developing APIs in the last two years. They're being used by a wide spectrum of enterprises too, with 70 percent of financial organizations and 59 percent of government bodies saying they’re developing APIs. Much of this growth is driven by demand for mobile and Internet of Things access, 54 percent of API providers expect mobile to drive the most growth with 44 percent expecting it to be the IoT.
Security is cited as the number one challenge API providers want to see solved, cited by 41 percent of respondents. Quality is a key factor too, with 85 percent of respondents saying that API quality is either very important or extremely important to their organization. Performance matters too, with 61 percent of API providers saying they regularly do performance testing to ensure the quality of their output.
The full report is available from the SmartBear website and there's also a summary of the findings in infographic form below.

Image Credit: totallyPic.com / Shutterstock
-

'Accessibility Clickjacking' malware could impact 500 million Android devices
Publié: mars 3, 2016, 6:58pm CET par Ian Barker

Researchers at threat defense company Skycure have uncovered an Android proof of concept malware that uses accessibility services to allow attackers to spy on and even control a device.
It can monitor all of a victim's activity and allow attackers to read, and possibly compose, corporate emails and documents via the victim's device, as well as elevating their permissions to remotely encrypt or even wipe the device.
Accessibility APIs, which were introduced in Android 1.6 and significantly enhanced in Android 4.0, allow Accessibility Services to have access to the contents of the interfaces that a user interacts with, when reading or composing an email, browsing or working on a document for example. They can also perform actions on the behalf of the user. They're intended to help users with disabilities, by allowing the creation of system-wide text to speech tools, for example. But while having legitimate uses, these capabilities are also extremely attractive to malware writers.
Using Accessibility Clickjacking could allow malicious applications to access all text-based sensitive information on an infected Android device, as well as take automated actions via other apps or the operating system itself, all without the device user's consent. This would include access to both personal and work emails, SMS messages, data from messaging apps, sensitive data on business applications such as CRM software, marketing automation software and more.
More detail on the threat is available on the SkyCure blog there's also a video demonstration of how it works below.
Image Credit: Palto / Shutterstock
-

Real-time messaging is displacing email
Publié: mars 3, 2016, 3:02pm CET par Ian Barker

According to a new report, 56 percent of respondents believe that real-time messaging will displace email as their organization's primary workplace communication and collaboration tool.
The latest Trends in Cloud IT Research survey from BetterCloud surveyed over 800 people split between IT professionals and end users. The results show that while real-time messaging is gaining popularity, 27 percent of end users and 23 percent of IT professionals say some employees are less productive because of it.
The other side of that coin is that 80 percent of Skype for Business users, 84 percent of Google Hangouts users, and 95 percent of Slack users say their communication has improved because of real-time messaging.
Small and medium businesses are most likely to use the 'big three' messaging apps -- Google Hangouts, Skype for Business and Slack -- with Slack in particular having 92 percent SMB users. A majority of organizations (57 percent), however, use two or more real-time messaging applications. Bigger businesses are likely to use even more, over 20 percent of large enterprises (5,001+ employees) use five or more real-time messaging apps.
It seems that the telephone is under threat from this trend towards messaging too, 71 percent of small-to-medium sized businesses (1-1,000 employees) say they will not invest in another phone system at all or will not increase their investment.
The trend towards messaging is also partly driven by shadow IT. Nearly a quarter of respondents (22 percent) admit they either don’t know or don't care whether the real-time messaging application they use is approved by their IT department. Seven percent say they aren’t sure if the tool they use is outside IT’s control.
You can find more in the full report which is available via the BetterCloud blog.
Photo credit: Pavel Ignatov/ Shutterstock
-

What makes a typical information security chief?
Publié: mars 2, 2016, 3:53pm CET par Ian Barker

Major data breaches continue to highlight how essential it is for businesses to secure their systems, and as a result many organizations are looking to recruit information security officers.
But what should they be looking for? What are the traits that the top information security professionals share? Data loss prevention specialist Digital Guardian has produced an infographic based on research into the CISOs and security leaders at Fortune 100 companies which throws up some interesting results.
Information security seems to be an overwhelmingly male profession, with only 11 of security leaders being female. Although most are qualified to at least bachelor's degree standard, qualifications in information security and indeed computer science are less common than those in business. However, 59 percent did begin their careers in IT or IT security.
CISSP (Certified Information Systems Security Professional) qualifications are held by more than half of Fortune 100 security leaders. The dynamic nature of the industry is also underlined by the fact that a large majority of CISOs have only been in their jobs for between one and five years.
You can see more details in the full infographic below.
Infographic by Digital Guardian
-

New query tool makes life easier for .NET developers
Publié: mars 2, 2016, 3:13pm CET par Ian Barker

Standard query tools can often lack the flexibility required to deliver precise results which results in the need for further processing and adds to data traffic.
To address this problem ScaleOut Software is announcing a new computational query tool that combines Microsoft's LINQ query with the company's own data-parallel computing technology to offer more powerful and flexible query tools for grid-based applications. Available with ScaleOut Software's suite of in-memory data grid products, including ScaleOut StateServer and ScaleOut ComputeServer, computational query makes it easy for .NET developers and architects to harnesses the full power of the grid's data-parallel compute engine and dramatically accelerate query processing. It's available for use with Java on both Linux and Windows systems.
"We are excited to add computational query to our distributed LINQ query support based on customer feedback asking for even richer query capabilities," says Dr William L Bain, founder and CEO of ScaleOut Software. "We see a growing need for computational query in e-commerce, finance, and IoT applications that depend on in-memory data grids to track fast-changing data. These applications require powerful query tools to make informed, timely decisions before the moment is lost. We see this as an easy but important step that .NET developers and architects can take towards harnessing the full power of data-parallel computing".
ScaleOut's computational query enhances LINQ query thanks to a user-defined filter method which allows applications to extend query semantics by analyzing all properties of an object with a user-defined computation. It provides automatic, data-parallel computing that analyzes data in place, thereby reducing both networking traffic and client workload. User code is automatically shipped to grid servers, which manage its execution. By harnessing the power of the in-memory data grid to perform advanced query analysis, computational query accelerates query processing.
You can find out more about computational query and how it works on the ScaleOut website.
Image Credit: alphaspirit / Shutterstock
-

Cyber threats could overwhelm the healthcare industry
Publié: mars 1, 2016, 5:24pm CET par Ian Barker

Healthcare organizations average about one cyber attack per month and almost half say they have experienced an incident involving the loss or exposure of patient information during the last year, leaving patients at risk of identity theft.
These are among the findings of a survey by security company ESET and the Ponemon Institute into cyber security in the healthcare sector.
According to 78 percent of respondents, the most common security incident is the exploitation of existing software vulnerabilities greater than three months old. Advanced persistent threats are a problem too, respondents experienced an APT attack about every three months during the last year. The primary consequences of APTs and zero-day attacks were IT downtime (63 percent) followed by the inability to provide services (46 percent). Yet despite these attacks only half of respondents say they have an incident response plan in place.
Attackers are most interested in patient's medical records according to 81 percent of respondents. Also a majority (52 percent) say that legacy systems and new technologies to support cloud and mobile implementations, big data and the Internet of Things, increase security vulnerabilities for patient information. Respondents also expressed concern about the impact of employee negligence (46 percent), and the ineffectiveness of business associate agreements mandated by HIPAA which are designed to ensure patient information security (45 percent).
"The concurrence of technology advances and delays in technology updates creates a perfect storm for healthcare IT security," says Stephen Cobb, senior security researcher at ESET. "The healthcare sector needs to organize incident response processes at the same level as cyber criminals to properly protect health data relative to current and future threat levels. A good start would be for all organizations to put incident response processes in place, including comprehensive backup and disaster recovery mechanisms. Beyond that, there is clearly a need for effective DDoS and malware protection, strong authentication, encryption and patch management".
More information is available in the full report which can be downloaded from the ESET website.
Image Credit: Rob Hyron / Shutterstock
-

New platform helps mid-sized organizations respond to cyber threats
Publié: mars 1, 2016, 3:52pm CET par Ian Barker

Cyber attacks don't discriminate when it comes to the size of the organization. But smaller enterprises can lack the resources needed to effectively deal with them.
Incident response specialist Resilient Systems -- which is in the process of being acquired by IBM -- has designed its latest Resilient Commercial Incident Response Platform (IRP) to meet the needs of mid-sized organizations.
It offers a foundation for incident response planning, management, orchestration, and mitigation. In addition it provides immediate improvement in security teams’ ability to have an expert, consistent, repeatable, and measurable process.
"Organizations of all sizes face serious cyber threats every day. While these threats seem daunting, security teams can successfully navigate them by preparing and provisioning for incident response," says John Bruce, Co-Founder and CEO of Resilient Systems. "With the launch of our mid-market platform, we've made it easier for companies with fewer resources or a smaller footprint to transform their security posture immediately, and be better prepared to respond quickly and effectively to any threat".
The platform can be delivered as a service or installed in-house. Features include more than 18 different response plans or playbooks that are based on the latest industry standards and best practices -- ensuring that response plans are consistent, proven, and repeatable.
Fast and easy incident creation and tracking is available, providing greater visibility and helping organizations ensure that incidents are captured, tracked, and fully resolved. Commercial IRP has incident workflow capabilities that allow for an orchestrated process and response, allowing security teams to move faster with more intelligence.
The platform also has collaboration tools to ensure all potential stakeholders in an organization, such as IT, legal, marketing, HR, and the executive team, can work together to define their roles and act quickly and decisively when an incident occurs.
More information can be found on the Resilient Systems website.
Image Credit: underverse /Shutterstock
-

New solution aims to eliminate passwords in the workplace
Publié: mars 1, 2016, 3:19pm CET par Ian Barker

Passwords are increasingly seen as insufficient to protect sensitive systems and companies are looking for more secure alternatives.
Digital identity company Intercede is introducing new software that works with Intel's latest Intel Authenticate technology with the aim of eliminating workplace passwords entirely.
Intercede software, running on the 6th generation Intel Core vPro processor, works in combination with Intercede's MyID credentials management solution to replace password-based access control for networks, applications and services with certificate-based, secure and convenient hardware-backed protection.
"Intel Authenticate is a solid technology built to intelligently help secure Windows based platforms in today's enterprise environments," says Richard Parris, CEO of Intercede. "We are proud to be working with Intel to provide differentiating technology that works with their new generation solution. Intel Authenticate, coupled with MyID, enables end-user companies to focus on their business and to protect their workforce and assets with a more highly secure solution that is cost-effective, easy to deploy and manage across a global enterprise".
Currently available in preview, Intel Authenticate is a hardware-enhanced, multifactor authentication solution that strengthens identity protection on the PC, making it less vulnerable to identity breaches and security credential attacks. Intercede will complement Intel Authenticate by making hardware-backed credentials available for Windows and domain logons, as well as making it easier to issue and manage credentials. Enterprises will be able to use Intercede's technology with Intel Authenticate to remove the need for usernames and passwords and provide higher levels of user authentication.
"We're excited to advance our work on Intel Authenticate, working with premier security companies like Intercede," says Tom Garrison, vice president and general manager for the Intel Business Client Division. "Together, we're empowering enterprise to not only dramatically improve identity security, but to do so in a way that improves the ease of use and experience for the business professional".
The technology will be previewed at this week's RSA conference.
Photo Credit: Maxx-Studio/Shutterstock
-

Microsoft announces Windows Defender Advanced Threat Protection
Publié: mars 1, 2016, 1:30pm CET par Ian Barker
Cyber attacks are becoming more sophisticated and can be costly for businesses. Microsoft has recognized that it needs to offer stronger protection for its enterprise customers and is announcing a new service to help them detect, investigate, and respond to advanced attacks.
Windows Defender Advanced Threat Protection adds a new post-breach layer of protection to the Windows 10 security stack. Using a mix of client technology built into Windows 10 and a cloud service, it will help detect threats that have made it past other defenses.
It will also provide enterprises with information to investigate the breach across their endpoints, and offer response recommendations. It can provide key information on attacks thanks to sophisticated cloud-based threat intelligence.
Windows Defender Advanced Threat Protection uses a combination of Windows behavioral sensors, cloud based security analytics, threat intelligence, as well as tapping into Microsoft’s intelligent security graph which uses big data analytics to identify anomalies. It allows admins to examine the state of machines and their activities over the last six months to maximize historical investigation capabilities and provides information on a simple attack timeline.
Writing on the Windows blog Terry Myerson, the head of Microsoft's Windows and Devices Group says, "Just like we developed Windows 10 with feedback from millions of Windows Insiders, we worked with our most advanced enterprise customers to address their biggest security challenges, including attack investigations and day-to-day operations, to test our solution in their environments. Windows Defender Advanced Threat Protection is already live with early adopter customers that span across geographies and industries, and the entire Microsoft network, making it one of the largest running advanced threat protection services".
SEE ALSO: How to activate Windows Defender Offline in Windows 10
Windows Defender ATP will be built into Windows 10, allowing it to be kept continuously up-to-date, so offering businesses lower costs and zero deployment effort. Using a cloud back end means no on premise server infrastructure or ongoing maintenance is required either.
It's likely that ATP will be made available via the Windows Insider program and eventually the public but as yet there's no word on the timescale.
-

Kaspersky launches new platform to detect targeted attacks
Publié: mars 1, 2016, 11:40am CET par Ian Barker

While conventional security technologies are good at protecting against generic threats, targeted attacks are more difficult to handle.
Kaspersky Lab is looking to combat this type of attack with new offerings including the Kaspersky Anti Targeted Attack Platform, a sophisticated solution designed to detect targeted attacks, and a range of Security Intelligence Services, offering penetration testing, cybersecurity training and threat intelligence sharing.
The Kaspersky Anti Targeted Attack Platform enables businesses to detect targeted attacks and other malicious actions through the careful monitoring of network activity, including web and email. Based on the company's security intelligence and expertise in discovering cyber threats, the platform utilizes network and endpoint sensors and a sandbox technology to detect abnormal and potentially malicious activity within a highly integrated system.
The platform analyzes data collected from different points of the corporate IT infrastructure. Its sensors cover data acquisition over network traffic, web and email, as well as endpoints. This allows the solution to detect complex attacks at any stage, even when no malicious activity is taking place, like data exfiltration. Suspicious events are then processed via different engines, including an Advanced Sandbox and a Targeted Attack Analyzer for a final verdict.
"As we developed our Anti Targeted Attack Platform, we understood that a working solution cannot stand apart from well-known and highly efficient security approaches," says Nikita Shvetsov, Kaspersky Lab's Chief Technology Officer. "At the same time, new corporate threats demand new technology and intelligence an order of magnitude more complex than our existing solutions. The result of two years’ extensive investment of resources, expertise and talent is this premium product that helps enterprises to achieve new levels of security for their IT infrastructure".
In addition the company is launching its Security Intelligence Services to meet the needs of larger businesses. These include a Security Assessment service to carry out penetration testing and application security assessment, plus access to threat intelligence data from Kaspersky Lab through threat data feeds and botnet tracking. Kaspersky is also offering training in security awareness and in digital forensics and malware analysis.
You can find out more about Kaspersky Anti Targeted Attack and Security Intelligence Services on the company's website.
Image Credit: Jirsak/Shutterstock
-

IT security executives tell boards what they want to hear
Publié: février 29, 2016, 3:20pm CET par Ian Barker

A new report reveals that just four out of 10 IT and security executives feel the information they provide to the board of directors is actionable and that they often tell them what they want to hear.
The report from threat intelligence company Bay Dynamics also shows that only 39 percent believe they are getting the help they need from the board to address cyber security threats.
Based on a study conducted by Osterman Research among IT and security executives in 136 US companies, the report shows manual reporting methods still dominate. Manually compiled spreadsheets are used to report data to the board by 81 percent, a process which can lead to incorrect reporting and oversight of important data, whether due to intentional manipulation or to human error.
Boards have a strong preference for qualitative information, according to 53 percent of respondents, with 38 percent saying their boards prefer quantitative information.
"The report reveals that both the board and security professionals are not doing their jobs when it comes to security reporting," says Feris Rifai, co-founder and CEO at Bay Dynamics. "The board isn't holding IT and security executives accountable for providing accurate, traceable and actionable information and security executives are failing to report information that is accurate, traceable and actionable. Both parties must do better if they want to make the right decisions that minimize their cyber risk".
Among other findings are that the most common type of information reported about cyber security issues is known vulnerabilities within the organizational systems, followed by recommendations on cyber security program improvements and specific details on data loss incidents. Information about the cost of cyber security programs and details about expenditures on specific projects or controls are not as commonly reported.
The most common criteria used to determine which type of intrusion to report is the type of data affected -- cited by 84 percent of respondents. This includes whether the data breached or attacked was sensitive or confidential, such as customers’ financial data or personal information, or corporate financial data.
"Security is now everyone's problem -- from the IT team to the C-suite and the boardroom. As a result, reporting the right type of information with the right context, in addition to making it actionable, has never been more critical," says Michael Osterman, Principal Analyst at Osterman Research. "It is imperative that security executives reconsider how they’re getting their information, the type of information they're reporting, and how they’re reporting it, so that the board can effectively take action to make smart security decisions".
The full report is available to download from the Bay Dynamics website.
Photo Credit: EmiliaUngur/Shutterstock
-

82 percent of company boards are concerned about cyber security
Publié: février 29, 2016, 2:01pm CET par Ian Barker

According to a new study, data security is now on the agenda in most boardrooms. Yet only 14 percent of information security chiefs report to the CEO.
The report by the Information Systems audit and Control Association (ISACA) and the RSA Conference also reveals that 74 percent of security professionals expect a cyberattack in 2016 and 30 percent experience phishing attacks every day.
"While there are signs that C-level executives increasingly understand the importance of cybersecurity, there are still opportunities for improvement," says Jennifer Lawinski, Editor-in-Chief, RSA Conference. "The majority of CISOs still report to CIOs, which shows cybersecurity is viewed as a technical rather than business issue. This survey highlights the discrepancy to provide an opportunity for growth for the infosec community in the future".
The study also identifies a 12-point decline in the percentage of security professionals who are confident in their team's ability to detect and respond to incidents, dropping from 87 percent in 2014 to 75 percent in 2015. Among that 75 percent, six out of 10 don't believe their staff can handle anything beyond simple security incidents. In addition, the number who say that fewer than half of job candidates were considered 'qualified upon hire' has risen from 50 percent to 59 percent in a year. Also 27 percent say they need six months to fill a cybersecurity position, up three points from 2014.
"The lack of confidence in current cybersecurity skill levels shows that conventional approaches to training are lacking," says Ron Hale, Chief Knowledge Officer of ISACA. "Hands-on, skills-based training is critical to closing the cybersecurity skills gap and effectively developing a strong cyber workforce".
The study also examined emerging trends towards artificial intelligence and the Internet of Things. Rather than the accepted view of AI as an aid to detecting threats, it found that respondents believe that AI will increase risk in both the short (42 percent) and long (62 percent) term. Less surprising is that more than half (53 percent) of respondents are concerned or very concerned that the Internet of Things will expand attack surfaces further and exacerbate cyber risk.
The full State of Cybersecurity study is available to download from the ISACA website.
Image Credit: Manczurov / Shutterstock
-

New service helps organizations visualize and prioritize security threats
Publié: février 29, 2016, 12:57pm CET par Ian Barker
Active vulnerabilities can present a serious threat to organizations, which is why many are turning to intelligence solutions to spot and manage security issues.
Cloud-based security and compliance specialist Qualys is announcing a new service as part of its Cloud Platform. Called Qualys ThreatPROTECT, it provides customers with an interactive dashboard to help them understand security threats at-a-glance.
ThreatPROTECT's dashboard uses vulnerability scan data gathered via Qualys scanners or Cloud Agents in real-time and correlates this with Real-time Threat Indicators (RTI) from multiple industry sources. It then provides customers with an easy-to-understand display offering clear insights into what vulnerabilities to fix first based on the level of threat seen in the wild.
"In today’s rapidly changing threat landscape, the most effective way for companies to protect themselves is to accurately identify assets, identify vulnerabilities, and ensure that systems are properly configured," says Philippe Courtot, chairman and CEO for Qualys. "Our goal is to continuously expand and improve our cloud-based offerings so customers can raise the bar when securing their assets. Qualys ThreatPROTECT is another example the demonstrates the power and agility of our cloud platform to introduce new services that can help customers improve their overall security without the cost and complexity associated with deploying enterprise software".
Qualys is also announcing the extension of its Cloud Agent platform, with the availability of agents for Linux and Mac OS, adding to the platform's existing support for Windows. The Cloud Agent platform gives organizations the ability to conduct real-time asset inventory searches on a global scale, to effectively address the security and compliance of their IT assets.
Cloud Agent augments the company's Cloud Platform. It automatically collects vulnerability and configuration data and securely transfers it to the Qualys Cloud Platform, where it is analyzed and correlated to identify risks and eliminate vulnerabilities.
Courtot adds, "IT and security professionals have the daunting task of ensuring that all assets are up-to-date, compliant and secure. With the availability of the Cloud Agent on all major computing environments, companies can now inventory all their IT assets, get the visibility needed to secure them against cyber attacks on a continuous basis and take action with Qualys' new patching capabilities".
More information on these developments can be found on the Qualys website and they'll be on display at the company's RSA stand.
-

Comodo Dome offers cloud-delivered security solution
Publié: février 26, 2016, 3:13pm CET par Ian Barker

Cloud and hybrid environments along with mobile access bring lots of challenges surrounding securing networks.
One way of addressing these is to provide security from the cloud which is what Comodo is doing with its new cloud delivered secure web platform, Comodo Dome.
Comodo Dome takes a modular approach, allowing system administrators and IT directors to layer in just the modules they need across their networks as they grow. These include advanced threat protection (ATP), web security, portable containment, sandboxing, antispam, data loss prevention (DLP), next-generation firewall, bandwidth management and a secure VPN service. Individual modules can be easily added to provide total security and compliance to corporate policies, regardless of the end user, device or location.
"Every best-of-breed Web security solution today leaves significant gaps in securing mobile first, cloud-centric and borderless networks. Having large security content filters and backhauling traffic from remote offices is quickly becoming cumbersome and costly for IT departments of all sizes," says John Peterson, vice president of Enterprise Products at Comodo. "With Comodo Dome, companies can use the platform by itself or layer it with their existing security gateways as an additional and highly critical piece of security, which prevents patient zero infections and unknown file types from being executed on internal networks and devices -- solving the malware problem".
Comodo Dome is built on the company's next-generation default-deny platform, which places emphasis on allowing known good applications, while denying everything else until a verdict on those applications is reached. This is the opposite of the traditional industry method of default-allow, and thus ensures uninterrupted business productivity across an enterprise, while protecting users from zero-day attacks.
Dome inspects all Internet traffic and blocks zero-day malware and malicious files in real time, even if they are currently undetected by other antivirus engines. It also acts as a Web proxy that blocks known bad files and then identifies unknown files and wraps them in a portable container in flight, ensuring that end users are free to open, execute and use the files with zero risk of infection. Even sophisticated targeted attacks and the newest emerging threats are contained and blocked in real time.
Comodo Dome will be on display at next week's RSA conference in San Francisco.
Image Credit: alphaspirit / Shutterstock
-

IBM and Check Point team up to offer threat prevention
Publié: février 26, 2016, 12:45pm CET par Ian Barker

Cybercrime is big business, netting $445 billion in annual profits according to the United Nations. To combat it enterprises need to be able to detect risks and have the tools to prevent attacks.
Check Point Software and IBM Security have announced an expanded alliance which will allow the two companies to share threat intelligence, as well as a broad set of product integrations and expanded investment across IBM's consulting and managed security services.
"The sharing of intelligence and expertise is how the security industry will take our defensive capabilities to the next level", says Caleb Barlow, vice president of strategy at IBM Security. "Cybercriminals are not new to this concept of sharing and our industry needs to step up to the challenge. Having a partner the quality of Check Point validate this approach is a big win for our joint customers".
The alliance focuses on four key areas. IBM X-Force and Check Point's security research team will directly collaborate through the sharing of threat identification and analysis using IBM X-Force Exchange (XFE), IBM's threat intelligence sharing platform. This intelligence may be integrated into each company's products, to help deliver protection to customers of both companies.
Check Point will be launching a new SmartConsole application in the IBM Security App Exchange for integration with the IBM Security QRadar Intelligence Platform. The app will deliver network data and security events from Check Point devices to QRadar to enable operators to view threat information in real-time directly from the QRadar console.
Integration within IBM Maas360 enterprise mobility management (EMM) will allow customers to easily deploy and manage Check Point Mobile Threat Prevention to limit compromised devices from accessing enterprise networks and data, based on real-time insights. This will allow automated protection against advanced threats across mobile devices, apps and networks, while simplifying the implementation and ongoing monitoring of mobile security technology.
IBM Managed Security Services (MSS) will continue to deepen its expertise in delivering and managing Check Point solutions for IBM customers. The deployment and management of a broader range of Check Point network security offerings will be supported through new lab equipment and ongoing training of IBM SOC analysts and solution architects. This will give customers cost-effective access to resources and expertise as their security requirements change.
You can find more about the partnership on the Check Point blog.
-

Ping Identity offers flexible real-time access for digital enterprises
Publié: février 25, 2016, 5:21pm CET par Ian Barker

Legacy identity management solutions can struggle to keep up with the current interconnected world where systems may be both local and in the cloud.
Security company Ping Identity is launching a new Federated Access Management product designed to offer lightweight, open and hyper-connected identity technology for the modern digital enterprise.
Key benefits include automatic scaling to match AWS and OpenStack environments, which delivers cost and resource savings. It has context-sensitive, risk-based multi-factor authentication to ensure users receive proper access based on their location, role or other criteria set by administrators. The product can trigger 2FA for users attempting to access applications from outside their network, from public Wi-Fi or after hours. There are also time savings for admins thanks to a simplified partner administration and integration interface.
"Demand for secure access across the entire digital enterprise will only rise in the years ahead," says Andre Durand, CEO and founder, Ping Identity. "Increasingly, identity and access management helps companies realize the benefits cloud has to offer, including enhanced security and better user experiences. With the Ping Identity Platform, we aim to help our customers make the leap to digital transformation quickly, without sacrificing security".
By analyzing constant streams of contextual data, it allows split-second decisions to be made about user identities and permissions. There are thousands of pre-integrated applications, along with flexible cloud and software deployment options, which allows Ping Identity to leapfrog legacy vendors and offer an extensible, open platform and advanced integration capabilities.
More information about Federated Access Management can be found on the Ping Identity website.
Photo credit: Pakhnyushcha / Shutterstock
-

New platform offers endpoint protection for Linux servers
Publié: février 25, 2016, 4:33pm CET par Ian Barker

Most of the internet is powered by Linux servers, so it's not surprising that they’re increasingly a target for attack. In particular recent attacks have focussed on using compromised systems to distribute malware to other systems.
Many Linux systems rely on traditional signature-based threat detection which leaves them vulnerable to zero-day attacks. Endpoint security company SentinelOne is announcing a new solution aimed at protecting enterprise data centers and cloud providers from emerging threats that target Linux servers.
"As we have seen, Linux endpoints, whether they are servers or other devices, are not immune to malware and other forms of attack," says Tomer Weingarten, CEO of SentinelOne. "To address this new threat plane, SentinelOne EPP now provides the same exceptional level of integrated threat detection, prevention and remediation for Linux machines as it does for Windows and OS X devices".
SentinelOne uses a lightweight autonomous agent to monitor all activity in both kernel and user space (including files, processes, memory, registry and network) on the protected device. Each agent leverages the SentinelOne Dynamic Behavior Tracking (DBT) Engine which uses sophisticated machine learning to predict threats across any vector against the background of normal application behavior. Once malicious activity is detected SentinelOne immediately employs a series of automated mitigation and quarantine processes to eliminate the threat in real-time. SentinelOne also maintains a detailed audit trail of activity for forensic analysis and reporting which is delivered to the management console in real-time.
The SentinelOne EPP platform with support for Linux is available now, you can find more information on the company's website.
Image Credit: rosedesigns / Shutterstock
-

Netskope launches threat protection for enterprise cloud apps
Publié: février 25, 2016, 3:59pm CET par Ian Barker

Use of cloud apps, including unauthorised 'shadow' IT, is booming, but it leaves a gap in the protection provided by traditional perimeter security.
To plug this gap cloud access security broker Netskope is launching a threat protection solution for the cloud. Netskope Active Threat Protection combines threat intelligence, static and dynamic analysis, and machine-learning based anomaly detection to enable real-time detection, prioritized analysis, and handling of threats that may originate from cloud apps.
It gives a 360-degree view into sanctioned and unsanctioned cloud app usage, even if the user is accessing the app remotely or from a mobile device. It also understands the context of the usage, such as who is uploading, downloading and sharing data -- information that can prove critical when thwarting an attack or limiting its effects.
Active Threat Protection is designed to prioritize potential threat dangers during scanning without sacrificing the comprehensiveness of the scans performed. This is done at high-speed and in real-time before presenting forensic analysis in a single Netskope dashboard or via a customer's existing SIEM solution.
"With the constantly evolving landscape of malware, ransomware and other threats to the enterprise, IT need not only 'rip the blindfold off' when it comes to shadow IT, but to be able to react immediately to ensure the safety and security of sensitive data," says Sanjay Beri, co-founder and CEO, Netskope. "With Netskope Active Threat Protection, customers can now take advantage of the Netskope deep cloud app visibility and granular policy enforcement capabilities in tandem with the benefits of a complete threat protection suite. We have collaborated with a number of leading enterprise security companies to offer this service to our customers and ensure that we are one step closer to safer enterprise cloud app usage."
You can find more details on the Netskope website and the product will be demonstrated at the RSA conference next week.
Image Credit: Maksim Kabakou/Shutterstock
-

New platform can use any data source to gain visibility into attacks
Publié: février 25, 2016, 3:05pm CET par Ian Barker

A security breach can involve many different elements, this means that analyzing attacks can be a complex and difficult task.
Security analytics specialist Niara is launching a new version of its security analytics platform that can analyze any data source and supports the customization of behavioral analytics modules, providing organizations with complete visibility into attacks and risky behaviors inside their environments.
"By making behavioral analytics modular and data-agnostic, Niara enables data sources, machine learning models and features to be easily combined to better isolate attacks and identify risky behaviors," says Sriram Ramachandran, CEO and co-founder of Niara. "That flexibility results in much richer Entity360 risk profiles, allowing attacks to be detected with greater precision and dramatically reducing the time and skill needed to investigate and respond to security events".
It allows organizations to derive security insights from data sources by combining Niara's built-in behavioral analytics with custom modules unique to a particular environment. As a result, organizations can benefit from more comprehensive risk profiles and extensive information about attacks due to the breadth of Niara's multi-dimensional analytics. Analysis includes factors like privilege escalation, password sharing, credential violations, lateral movement, internal reconnaissance, abnormal access to high-value resources, command and control and exfiltration activities.
You can find out more on the Niara website or at the company's stand at next week's RSA conference.
Photo credit: sommthink/Shutterstock
-

Pawn shop phones contain left over personal data
Publié: février 25, 2016, 1:48pm CET par Ian Barker

If you buy a used mobile phone you could be getting more than you bargained for according to security software company Avast. It seems that some phone owners are inadvertently pawning their porn.
Avast purchased 20 used smartphones from pawn shops in 4 cities -- New York, Paris, Barcelona and Berlin. The goal being to see if used phones are regularly being sold with previous owners’ personal information still retrievable on them.
After buying the phones it used widely available free data recovery software to see what was on them. It discovered that 12 of the phones hadn't been wiped clean, even though shop owners assured the buyers they had been. On them were more than 1,200 photos, more than 200 photos containing adult content, 149 pictures of children, over 300 emails and text messages, identity details of two previous owners and what is described as a 'very adult' video.
Of the phones that were factory reset, 50 percent still contained personal data as they were running an outdated version of Android that had an improperly functioning factory reset feature. Some of the previous owners had only deleted their files without doing a factory reset, which meant they could be recovered.
"Through our research, we noticed that some people simply forget to delete their personal data and perform the factory reset before selling the device," says Gagan Singh, president of mobile at Avast Software. "To ensure that all data is removed, a user needs to overwrite the phone’s files. Without this, a user’s personal data could easily end up in the hands of the next owner of the phone. In the end, users are responsible for cleaning all sensitive and personal data from their devices prior to sale, and they should never rely on a shop owner to remove remaining data prior to reselling the phones".
To find out more about the findings along with tips on how to dispose of an old phone safely on the Avast blog. You can also see an infographic of the findings below.
Photo credit: Africa Studio / Shutterstock
-

CrowdStrike improves ability to combat breaches
Publié: février 24, 2016, 5:13pm CET par Ian Barker

Effective cyber security is all about seeing threats and being able to respond to them quickly and effectively. Increasingly this means using the cloud to deliver intelligence.
CrowdStrike, a specialist in cloud-delivered protection, is launching a new version of its Falcon platform to deliver endpoint, detection and response functions along with advanced antivirus capabilities.
CrowdStrike's fully cloud-based Threat Graph model analyzes and correlates billions of events in real-time, spots anomalies, and detects behavioral patterns to track and stop both known and unknown threats. This model allows Falcon Host to act like a 'DVR,' providing retrospective visibility and unlimited cloud-recall capabilities. This forensic capacity helps cut the time and cost of incident response, while increasing the chances of containing and mitigating damage by allowing customers to search and query all endpoints in seconds.
Extension of the platform's APIs means customers can integrate existing third party intelligence and so don't waste their current security investments. Falcon Connector can also transmit Threat Graph information to a customer's preferred SIEM system.
There's a new ransomware blocking feature too, and added protection for Linux systems with Linux-specific behavioral defenses based on indicators of attack.
"Our enhancements of CrowdStrike's Falcon Platform reflect our core customer value for redefining next generation endpoint protection to stop breaches," says Dave Cole, CrowdStrike's chief product officer. "Continuing to advance IoA-based prevention with ransomware exploit blocking and machine learning capability are just a couple of the new features that we are announcing today. Expanding CrowdStrike Falcon’s sensor coverage to Linux platforms, combined with our established support for Windows and Mac, is another significant market-leading accomplishment that allows us to provide protection across all mainstream endpoint operating systems. We are committed to continuing to build new innovative capabilities to change the game in endpoint security and ensure that CrowdStrike customers are able to protect themselves against all threats, known and unknown, in the most effective and efficient manner possible".
You can find out more about the latest release on the CrowdStrike website.
Image Credit: Balefire / Shutterstock
-

Identifying users with behavioral biometrics
Publié: février 24, 2016, 4:22pm CET par Ian Barker

As we're regularly being told, passwords on their own are no longer sufficient to ensure our security. Businesses are therefore on the lookout for new ways to identify users without making the sign in process overly complicated.
Adaptive authentication specialist SecureAuth is launching the latest version of its product that includes behavioral biometrics, a new risk analysis technology that performs keystroke analysis and mouse movement analysis to determine a user's legitimacy and build a completely unique behavior-based profile on each user device.
These profiles are compared to subsequent login attempts and if they don't match, SecureAuth IdP v9.0 will ask for multi-factor authentication (MFA) for that login to proceed. SecureAuth is the first identity management vendor to offer this capability as part of a comprehensive risk-based authentication process.
"Think of SecureAuth IdP as a bullet proof vest," says Craig Lund, SecureAuth's CEO. "It has multiple layers of protection, which creates a strong bulwark against cyber attacks. It’s harder to break through multiple layers of authentication compared to just one. In this case, one of those layers is created by behavioral biometric technology, which is unique in that it is influenced by social and psychological attributes. This makes it nearly impossible to copy or imitate somebody else’s behavior when using a device".
As well as using behavioral biometric technology to determine risk, SecureAuth IdP also uses device recognition, IP reputation, directory lookup, geo-location and geo-velocity. Features include a tailored login process so that organizations can adjust security requirements for different groups of users.
IdP only requires multifactor authentication when it detects that risk factors are present -- such as a mismatched behavioral profile. It offers more than 20 authentication methods ranging from SMS, telephony, and e-mail one-time passwords to push notifications, so an appropriate method can be matched with each use.
SecureAuth IdP will be on display at the RSA Conference in San Francisco next week or you can learn more on the company's website.
Photo Credit: JMiks/Shutterstock
-

New platform improves efficiency of security operations
Publié: février 24, 2016, 3:55pm CET par Ian Barker

Security teams often have to spend a lot of their time investigating incidents, which is time consuming and can distract from other tasks.
To improve the efficiency of security operations centers (SOCs), Israel-based SECDO is launching a new platform aimed at managed security service providers (MSSPs).
It provides advanced alert validation, investigation and remediation capabilities. The platform dramatically improves the efficiency of the SOC by automatically validating alerts from security event and information management (SIEM) systems, using unique thread-level endpoint activity data to identify false positives and prioritize true positives. Using SECDO, MSSPs will be able to handle the thousands of alerts that they receive each day, while meeting ever-more competitive SLAs for their customers.
"SECDO is a valuable platform for MSSPs who want to offer their customers advanced services while improving the efficiency and response times of their own SOC," says Shai Morag, CEO and Co-Founder of SECDO. "With SECDO's endpoint analytics, MSSP SOC teams can now understand the full context of every alert, visually investigate, and reduce the time and resources needed to identify and eradicate a breach".
The platform’s interactive data visualization technology enables SOC analysts to understand the 'who, what, where, when, and how' of every incident by showing the entire attack chain timeline back to the root cause. This enables first and second tier analysts to easily investigate and respond to threats without having to escalate to the next level. When an in-depth investigation is required, SECDO provides multi-dimensional, interactive search capabilities that can reduce hundreds of manual queries into a single visual search.
It uses SECDO's disruptive thread-level endpoint intelligence and causality analysis technologies to give service providers visibility into their customer’s environment. This allows MSSPs to offer the advanced threat protection, incident investigation and forensics services that are necessary to stay ahead in the security marketplace.
The platform has been in use for three months, with customers reporting positive results, you can find out more and request a demo on the SECDO website.
Photo credit: Alex Mit / Shutterstock
-

85 percent of enterprises keep sensitive data in the cloud
Publié: février 24, 2016, 12:51pm CET par Ian Barker

According to a new report by enterprise security specialist Vormetric, 85 percent of senior IT security executives worldwide say they are using sensitive data in the cloud, up from 54 percent last year.
But even as they move to adopt cloud services, and in some cases believe that cloud environments are more secure than their local IT infrastructure, enterprises remain concerned about the security of their information.
When respondents are asked about the top data security concerns for cloud services, 70 percent (75 percent in the US) name security breaches or attacks at the service provider. 66 percent cite increased vulnerabilities from shared infrastructure, 66 percent say lack of control over the location of data, and 65 percent select lack of a data privacy policy or privacy service level agreement.
When asked about changes that would increase their willingness to adopt cloud services, 48 percent asked for encryption of data with enterprise key control on their premises. 36 percent wanted detailed physical and IT security implementation information, 35 percent selected encryption of their organization's data within the service provider's infrastructure, and 27 percent also wanted exposure of security monitoring data for their information.
"Security is still an afterthought when it comes to adopting new technologies, often taking a back seat amidst the rush to stake a claim in a promising new market," says Garrett Bekker, senior analyst, information security, at 451 Research and the author of the report. "We found that enterprises are storing sensitive data in just these types of environments -- 85 percent in cloud, 50 percent in big data, and 33 percent in IoT. Many have strong concerns about the security of their data as a result".
With half of all respondents planning to store sensitive information within big data environments (up from 31 percent on last year), these become a much greater concern for enterprises as a possible point of compromise, and as a focus for compliance efforts. The biggest worries are the Security of the reports produced -- as they may include sensitive data, named by 42 percent of respondents, and that sensitive information may reside anywhere within the environment (41 percent).
The IoT raises similar concerns over the protection of sensitive data and privacy issues. Plus the overlap of IoT with big data has the potential to create a new class of risks.
You can find more information in the full report which is available to download from the Vormetric website.
Photo Credit: Jirsak/Shutterstock
-

New platform enables real-time in-app support
Publié: février 24, 2016, 11:55am CET par Ian Barker

The pace of modern app development often means that support can be something of an afterthought. New startup RevTwo is launching a platform that allows support to be built in to any app on any device.
The RevTwo In-App Support Platform modernizes the in-app support model by enabling users to connect with app evangelists and users from across the world for real-time support.
Typically, when app users encounter an issue they can't solve, they are forced to leave the app, search online, trawl through message boards and hope that someone else encountered the same problem. RevTwo flips that model on its head, enabling people to connect with other users, in-app, with the push of a button.
"Our in-app, community-based support will completely transform the user experience," says Jim Hansen, co-founder and chief technology officer of RevTwo. "From a teacher in Alabama helping a student in California solve a math problem to a professional gamer in Japan providing tips and tricks to a player in Holland, for the first time ever, users can get the help they need from their peers without ever leaving their apps".
As well as the community model, the RevTwo platform provides universal support at all stages of the app lifecycle. It includes free tools for developer support throughout testing that provide insight into problems at the software level -- preventing issues before production. In-app professional help desk support services are also available to connect users to a help desk within the app through audio, video and screen share, driving faster problem resolution.
To see inside an app, a developer simply bundles the RevTwo library into any iOS-based app (Android support on the way). Following the integration the app can open support sessions, initiate and respond to voice calls and interact with diagnostic tools like screen sharing, logging, database inspector and file browser.
Developers can use RevTwo for free with developer support through testing and community support for production. To discover more visit the company's website.
Image Credit: Rido / Shutterstock
-

Think your mobile device is faulty? You're probably not using it right
Publié: février 23, 2016, 5:59pm CET par Ian Barker

A new report shows that almost three-quarters of mobile devices returned with problems to mobile network operators and manufacturers in Europe and North America have 'No Trouble Found'.
The quarterly trend report from Blancco Technology Group also finds that in Europe device failures soared during the second half of 2015 -- rising from 14 percent during the third quarter to 29 percent during the fourth quarter.
The company has used data collected from millions of iOS and Android smartphones and tablets that underwent testing on its SmartChk diagnostic platform. The report argues that user behavior is the cause of a substantial number of device performance problems, failures and 'NTF' returns, rather than hardware.
"The quantity and types of apps being used, app notification settings, location services settings and battery charging habits are just some examples of how user behavior impacts the day-to-day performance and long-term health of devices," says Pat Clawson, CEO of Blancco Technology Group. "Take Asia, for example, where app adoption is high and the most frequently used apps are in the social networking and messaging categories. When these users fail to close the 40+ apps installed on their devices, it eats into the performance, memory and battery life. And all the while, users presume hardware is to blame when behavior is actually the culprit. It's a paradoxical situation and it happens very often".
Among other findings are that of issues found during the fourth quarter of 2015, 85 percent were on Android devices, compared to just 15 percent for iOS devices. Samsung tops the list of Android device manufacturers with the highest failure rate (27 percent), followed by Lenovo (21 percent), Motorola (18 percent), Xiaomi (11 percent) and Asus (8 percent). The most common causes of device failures worldwide are camera, touch, battery charging, microphone and performance. In Asia, frequent use of social networking apps and messaging applications, such as Facebook, WhatsApp, WeChat and Line, affected device performance in the region. The increasing usage of emoji and productivity apps in Europe played a contributing role in the increase in device failure rates during the second half of 2015.
Clawson adds, "Being able to detect with certainty the causes and types of device problems to determine if they are fixable is important. For mobile network operators and manufacturers, it allows them to automate and scale the device diagnostics and repair process to deliver a consistent customer experience. It also helps enterprise businesses support the needs and increase the productivity of their mobile workforce".
More information on SmartChck and Blancco's other mobile solutions can be found on the company's website -- where you can also download the report -- or at its booth at MWC in Barcelona this week.
Image Credit: Bevan Goldswain / Shutterstock
-

New platform helps protect enterprise Android use
Publié: février 23, 2016, 5:27pm CET par Ian Barker

Allowing the use of mobile devices and BYOD in the enterprise has led to new challenges for IT teams. Not lease of these is controlling which apps employees can access and how they can use them.
Security solutions provider OptioLabs is launching a new platform that will allow enterprises to create policies that control each of the 3,300 system methods in Android to provide targeted security protections.
Called OptioInsight, it allows IT staff to deploy a situationally-aware policy to achieve HIPAA, or FISMA compliance for their mobile devices. These sophisticated situational policies apply controls automatically, based on time, location, network and other factors -- enforcing strict controls only when they are needed, and still preserving an optimal mobile experience for the user. Being cloud-based it can be managed from any browser and can be hosted by OptioLabs or in a private cloud.
"The increasing speed and sophistication of mobile security threats can easily overwhelm even the best enterprise cybersecurity teams and put sensitive and critical data at risk," says Bill Anderson, Chief Product Officer of OptioLabs. "OptioInsight puts enterprise cybersecurity teams in control, giving them the ability to enforce -- based on policy – how specific applications are used throughout their environment".
Other features include context-sensitive security policies across Optio-ready devices. This means an enterprise can define security policies that adapt as the mobile user moves through different environments -- ensuring strong security when enterprise resources are used, but allowing the user full access at other times.
OptioInsight synchronizes with Active Directory to inherit user accounts and group assignments and will automatically update device policies for registered Enterprise users. It can also track system, application, device and user behavior for all Optio-ready devices to produce data analytics for emerging threats.
You can find out more about OptioInsight on the company's website.
Photo credit: Kirill__M / Shutterstock
-

Endpoint specific malware renders signature detection useless
Publié: février 23, 2016, 4:46pm CET par Ian Barker

Signature-based security could be virtually useless as 97 percent of malware is unique to a specific endpoint says a new report.
This is among the findings of the latest annual Webroot Threat Brief which shows that today's threats are truly global and highly dynamic. Many attacks are staged, delivered, and terminated within a matter of hours, or even minutes, having harvested user credentials and other sensitive information.
Among other findings are that around 50 percent of Webroot users experienced a first contact with a zero-day phishing site, compared to approximately 30 percent in 2014. This indicates that zero-day phishing attacks are becoming the hacker’s choice for stealing identities.
Interestingly technology companies, including Google, Apple and Facebook, were targeted by more than twice as many phishing sites as financial institutions, such as PayPal, Wells Fargo, and Bank of America. These companies are targeted because the same login credentials are often used to access other websites, resulting in multiple compromised accounts with each phishing victim.
Criminals are using more IP addresses too, with 100,000 new addresses created per day in 2015, a significant increase from the 2014 average of 85,000 a day. This shows cybercriminals are relying less on the same list of IPs, and are expanding to new ones to avoid detection. The US continues to have the most malicious IP addresses of all countries. In 2015, it accounted for over 40 percent of all malicious addresses, a significant increase from 31 percent in 2014. Top countries hosting 75 percent of malicious IPs include the US, China, Japan, Germany, and the UK.
As with IP addresses, malicious URLs are largely hosted in the US (30 percent), followed by China (11 percent). The US is also by far the largest host of phishing sites, with 56 percent of sites within its borders.
"2015 was yet another record year for cybercrime, during which more malware, malicious IPs, websites, and mobile apps were discovered than in any previous year," says Hal Lonas, chief technology officer at Webroot. "It comes as no surprise to those of us in the Internet security industry that the cybercrime ecosystem continues to thrive, given new innovations and little in the way of risk for those who choose to participate. The continued onslaught of hacks, breaches, and social engineering scams targeting individuals, businesses, and government agencies alike has caused many in the security field to ask if it's truly possible to defend against a persistent attacker. We conclude that we can only succeed by being more innovative than our criminal opponents".
Webroot suggests that organizations need to bolster their security posture with next-generation endpoint protection and real-time, accurate, dynamic threat intelligence to protect themselves, their users, and their customers from cybercriminal activity.
The full Threat Brief is available to download from the Webroot site and you can see an infographic summary of the findings below.
Image Credit: wavebreakmedia / Shutterstock
-

90 percent of Android devices are running an outdated OS
Publié: février 23, 2016, 3:05pm CET par Ian Barker

According to new research over 90 percent of Android devices are running an out of date version of the OS. In addition, 32 percent of those in use in enterprises today are running version 4.0 or older of the operating system, leaving them highly susceptible to vulnerabilities like Stagefright.
The study by cloud based access provider Duo Security analyzed data from its installed base of over a million mobile devices. It reveals that the problem isn't just with Android, only 20 percent of iPhones run the latest Apple operating system version, iOS 9.2. Outdated iOS devices have well-known vulnerabilities such as Ins0mnia and Quicksand that make these devices susceptible to attacks.
Duo estimates that over 20 million mobile devices connected to enterprise networks are no longer supported by the device manufacturer and therefore can't be upgraded to the latest versions of the software, which would fix their vulnerabilities. In fact, there are many devices still on the market that can't receive updates, meaning that even a brand-new device may be a security concern for the enterprise.
"IT administrators need to gain visibility into the health of all devices accessing their critical applications so that they can better protect these apps and at the same time improve the overall hygiene of all the devices," says Ash Devata, VP of Product at Duo Security. "Our new functionality will enable IT admins to understand what devices are out of date regardless of what type of device it is. We can then give admins the power to restrict out of date systems from accessing corporate data, and all of this is done without having to install anything on the end user device".
Full findings of the report are available on the Duo website. Duo has also made available a free X-Ray app for Android to allow users to detect serious vulnerabilities.
Image Credit: Palto / Shutterstock
-

The cost of mobile data breaches in big companies
Publié: février 23, 2016, 12:24pm CET par Ian Barker

A mobile data breach could cost a large enterprise over $25 million (£18 million) according to a new report.
The study of security and IT leaders in Global 2000 companies, carried out by mobile security specialist Lookout and the Ponemon Institute, examines the risk introduced by employees accessing increasing amounts of corporate data via their mobile devices.
The report finds that for an enterprise, the economic risk of mobile data breaches, including direct operational costs, as well as potential maximum loss from non-compliance and reputational damage, could be as high as $25.7 million (£18.2 million).
It also shows that mobile data breaches are more common than many may think. Two-thirds (67 percent) of organizations report having had a data breach as a result of employees using their mobile devices to access the company's sensitive and confidential information. With an average of three percent of employees' mobile devices infected with malware at any point in time, that could be more than 1,700 mobile devices, in a typical large organisation, connecting to an enterprise network everyday.
"The mobile workforce is dragging companies into a world where 24/7 access to cloud-based services from any location is a basic requirement. Employees demand flexibility. They want simultaneous access to work apps like Salesforce and personal apps like Facebook," says Gert-Jan Schenk, Vice President of Lookout EMEA. "When you talk to IT and security leaders, their number one concern is balancing mobility with security. It is critical that they get mobile security right from the outset, particularly in light of the financial and reputational consequences if they don't".
Another issue highlighted by the report is IT and security leaders’ underestimation of how mobile their employees have become. For example, on average IT believes that only 19 percent of employees can access customer records via mobile while 43 percent of employees say they have access. With the risk of mobile data breaches this visibility gap introduces unacceptable risk.
More details of the study are available on the Lookout website.
Image Credit: Minerva Studio / Shutterstock
-

Android banking and payment apps at risk from Acecard Trojan
Publié: février 22, 2016, 5:37pm CET par Ian Barker

A new Android banking Trojan is now bypassing Google Play security measures -- the Acecard Trojan is capable of attacking users of nearly 50 different online financial applications and services.
During the last quarter of 2015 researchers at Kaspersky Lab detected an unusual increase in the number of mobile banking attacks in Australia. The suspicious activity was discovered to be the result of a single banking Trojan called Acecard.
The company describes Acecard as one of the most dangerous Trojans it's ever seen. It uses almost every malware functionality currently available -- from stealing a bank's text and voice messages to overlaying official app windows with false messages that simulate the official login page in an attempt to steal personal information and account details. The most recent versions of the Acecard family can attack the client applications of some 30 banks and payment systems. Considering that these Trojans are capable of overlaying any application on command, the overall number of attacked financial applications may be much higher.
Acecard is also able to overlay phishing windows on other applications including IM services WhatsApp, Viber, Instagram and Skype, social networks including Facebook and Twitter, the Gmail client, Google Play and Music, and the PayPal mobile app.
"This cybercriminal group uses virtually every available method to propagate the banking Trojan Acecard. It can be distributed under the guise of another program, via official app stores, or via other Trojans. The combination of Acecard's capabilities and methods of propagation make this mobile banker one of the most dangerous threats to users today," says Roman Unuchek Senior Malware Analyst at Kaspersky Lab USA.
Kaspersky Lab experts believe that Acecard was created by the same group of cybercriminals that was responsible for the first TOR Trojan for Android and the first mobile encryptor/ransomware. The reasoning for this is based on similar code lines and the use of the same command and control servers.
To prevent infection by Acecard, Kaspersky recommends not downloading applications you don't trust, not clicking suspicious links, installing a reputable security application and keeping it up to date.
You can find more details on the Securelist blog.
Image credit: wk1003mike / Shutterstock
-

Huawei and Nexusguard partner to offer DDoS protection
Publié: février 22, 2016, 5:14pm CET par Ian Barker

DDoS attacks are one of the most worrying threats that enterprises face. Chinese hardware company Huawei and security specialist Nexusguard are launching a new joint solution that offers enterprises and internet service providers state-of-the-art DDoS protection using software-defined networking (SDN).
The companies will combine Nexusguard's cloud-enabled Origin Protection and Huawei's DDoS Protection System Appliances, giving customers low latency and multi-layered protection that can accurately and quickly defend their systems with hybrid implementations.
In the past, differing customer sizes and requirements meant different ISPs had to set up appliances and build their own DDoS mitigation solutions from the ground up. For service providers overwhelmed by DDoS attack traffic, Nexusguard’s Hybrid Cloud approach will mitigate smaller attacks locally with on-premise appliances, which will be followed by failover to the cloud once inbound traffic exceeds the local network capacity to handle the attack.
"Businesses look for advantages in technology that can support real-time traffic monitoring and protection with low latency, which is where we believe SDN will be the ultimate model for technology and solution providers in the future," says Liu Lizhu, general manager of the Firewall and Gateway Domain at Huawei. "With Nexusguard's purpose-built cloud DDoS mitigation expertise and our on-premise appliance protection, we can ensure customers enjoy the lowest latency and the quickest recovery from cyberattacks with a hybrid approach".
Benefits of the combined solution include low false-positives, keeping end user experiences intact, and mitigation capabilities for DDoS attacks of any size, using excess cloud capacity. It offers immediate protection, triggered by real-time attack monitoring, along with security across multiple layers safeguarding against all types of DDoS attack.
Both companies will be showcasing the joint solution at next week's RSA 2016 conference in San Francisco.
Image Credit: sibgat / Shutterstock
-

New tool uses machine learning to personalize emails
Publié: février 22, 2016, 1:16pm CET par Ian Barker
Most marketing email gets personalized using a static template which limits the amount of information that can be tweaked for each recipient.
Marketing automation company Boomtrain is launching a new platform, Boomtrain Editor, that adds advanced machine learning personalization regardless of email provider. It predicts the optimal email content for each recipient, and can then be applied by simply dragging and dropping it into a customizable template.
Rather than displaying the same message for all subscribers, content can be personalized with recommendations for each individual user, regardless of the number of recipients. It can turn existing HTML newsletters into a dynamic, 1:1 personalized template, without needing software specialists to help.
"You can go out and run predictive models on IBM's Watson or Google's TensorFlow, but if you don't have a team of engineers on staff, you won't be able to use it for practical marketing applications," says Nick Edwards, CEO of Boomtrain. "Boomtrain has bridged that gap to make advanced machine learning personalization accessible for marketers everywhere to leverage this new wave of data and technology".
In order to create a seamless process for executing email campaigns, Boomtrain has also announced a partnership with Iterable, a user engagement platform that powers marketing across email, mobile and web, to serve dynamic, personalized content to individual consumers through the Iterable email platform. Through this partnership, Boomtrain will create content within the email, while Iterable will be responsible for sending the actual message.
More information on Boomtrain Editor is available on the company's website.
Image Credit: Sarah Holmlund / Shutterstock
-

Dark data and why you should worry about it
Publié: février 19, 2016, 4:56pm CET par Ian Barker

How much of your company's data do you actually use? According to search technology specialist Lucidworks, businesses typically only analyze around 10 percent of the data they collect.
The rest becomes what the company calls 'dark data' -- information that lurks unused. Much of this data is unstructured and doesn't fit into any convenient database format. This means that companies don't have the tools to make sense of it or simply find they have too much to handle.
Lucidworks reckons that 7.5 septillion (7,700,000,000,000,000,000,000) gigabytes of data are generated worldwide each day and a large proportion of that will go dark. This data may contain sensitive information or details that could be used to commit crime, so it needs to be looked after. But it also has the potential to uncover details of undetected fraud, or boost business by revealing patterns in consumer habits, or finding untapped sources of revenue.
There's an interactive graphic on the issue of dark data on the Lucidworks site. You can see a short extract from it below to give you a flavor.

-

Streamlining home network security [Q&A]
Publié: février 19, 2016, 11:22am CET par Ian Barker
Whilst businesses can call on expert resources to secure their systems, for many home users protecting a home network and the devices attached to it can be something of a dark art.
Finnish security company F-Secure is aiming to make securing systems simple even for the non-technical with its forthcoming SENSE product. We spoke to Mika Majapuro, F-Secure's director of product management, to find about more.
BN: Can you give us an overview of what SENSE is?
MM: We've been building F-Secure SENSE for around one and a half years, the reason we started the project was we know that people have more and more connected devices. With the Internet of Things they'll have many more in future thanks to technology like smart TVs and smart thermostats.
The bad news is that all of these connected devices are hackable and there are worries that maybe your TV or your child's toy could be spying on you. We wanted people to be able to run a connected home but stay safe, secure and private.
BN: How does it work?
MM: SENSE is a combination of a Wi-Fi router, endpoint security and cloud service. You take the sense device home and connect it to your existing router, it then creates a new Wi-Fi network to which you move all of your connected devices. SENSE can then monitor all of the traffic going in and out of your home. If it sees something suspicious it can send information to the cloud for analysis. If there's a problem then action can be taken to block the connection and notify the user that maybe their connected toaster is trying to send traffic to China or receiving traffic from a malicious website. It's a behavior and reputation based service.
For devices like PCs and phones we also install an endpoint app which provides security for when they are taken out of the home. This provides antivirus protection, blocks tracking attempts and so on.
BN: Once you've bought that SENSE hardware is there an ongoing subscription?
MM: Yes, you buy the hardware which should be about $199 and that includes 12 months of subscription. After that you pay $8 per month but that’s for an unlimited devices so it doesn't matter whether you have 20 devices or 200 it's the same price. Since it also replaces your traditional antivirus product the cost becomes very competitive.
BN: How easy is it to set the system up?
MM: For home users, setting up security can be a painful process. With SENSE we really wanted to make it easy to use so we've used focus groups and redone the setup process more times than I like to remember. The app also gives you valuable information about your connected home, how many devices you have, where they're connecting, how they're behaving and so on. There's also a simple display that tells you when your home is secure and which will alert you if something is going wrong.
BN: Tell us a bit more about the SENSE gadget?
MM: If you look at traditional routers it's safe to say they're not the best looking devices and are something which you probably want to hide. We've tried to make the SENSE hardware something that you'd be proud to own and keep visible. The display will show if attention is needed so you can then go to the app to find out what's happening.
There's nothing special in the hardware, it has a 1GHz dual-core CPU and 512MB of RAM, the real magic is in the software and the cloud service.
BN: Does it replace your existing wireless router?
MM: No, it's an add-on. You attach the SENSE device to the router you received from your ISP, either with Wi-Fi or Ethernet. It then sets up a new wireless network to which you'll need to move all of your devices, network attached storage and so on.
BN: When will it be available?
MM: We announced SENSE at a startup event in Helsinki last November. We’re still in the final stages of development but in Europe and North America you can pre-order the product on the website and it will start shipping in early summer.
-

Prelert brings behavioral analytics to Elasticsearch
Publié: février 18, 2016, 5:39pm CET par Ian Barker

Increased use of big data in IT management and other areas means that companies are on the look out for new tools to give them better insights from their information.
Behavioral analytics company Prelert is making it easier for Elasticsearch users to automate the analysis of large data sets with the launch of Behavioral Analytics for the Elastic Stack.
It's powered by Prelert's machine learning algorithms and capabilities, which have been proven in the company’s other analytics products including its widely deployed Anomaly Detective solution. Prelert’s analytics create accurate, always up-to-date statistical baselines of normal behaviors. From these baselines the software is able to detect, score and link unusual activity that could indicate IT operations problems, IT security incidents, or business interruptions.
Since the automated analysis flags real issues as they're happening, it eliminates the need for traditional data monitoring rules and thresholds that return false positives if set too strictly, miss activity if set too loosely, and become outdated over time. Prelert's analytics include new statistical influencer tracking, which provides contextual data for each detected anomaly, so the root cause of issues can be identified and resolved quickly.
"There's a whole new world of possibilities for the way users extract value from their data that’s being driven by combining the power of analytics with the speed of search," says Tanya Bragin, Director of Product Management at Elastic. "Prelert's automated behavioral analytics are a powerful addition to the Elastic Stack and further demonstrates how developers can build an application using Kibana’s UI framework".
Behavioral Analytics for the Elastic Stack is expected to be available for download next month but in the meantime you can get more information on the Prelert website.
Photo Credit: Sergey Nivens / Shutterstock
-

Vertafore and Microsoft launch first custom CRM solution for the insurance industry
Publié: février 18, 2016, 4:39pm CET par Ian Barker

CRM systems have become essential tools for sales and marketing teams, giving them the ability to organize and automate the processes that build good customer relationships.
But off-the-shelf solutions don't always meet the needs of specialist industries. Insurance technology specialist Vertafore is launching its new Agency SalesTrack solution, built on Microsoft Dynamics CRM to cater specifically for the insurance sector.
"Built on Dynamics CRM, Vertafore's Agency SalesTrack solution addresses the key challenges insurance agents face today," says Tom Feher, US Financial Services Industry Director at Microsoft Corporation. "Working with the rich features and capabilities of Dynamics CRM, Vertafore's SalesTrack Solution provides a 360 view of their production pipeline as well as the details needed to service clients. This increases agent productivity by eliminating duplicate data entry, enabling agents to not only meet their sales quota, but also provide exemplary service to their clients".
SalesTrack integrates with Vertafore's existing AMS 360 product to to centralize customer information and increase visibility into the key performance indicators affecting insurance sales. It offers a comprehensive view of the entire customer journey, eliminating the need for duplicate data entry and the associated delays and errors.
"We evaluated the major software providers in the CRM space, and we are really excited to partner with Microsoft Dynamics," says Greg Wright, SVP, Agency and Carrier Solutions at Vertafore. "Together, we're developing solutions for the independent insurance channel at incredible speed. The launch of Vertafore Agency SalesTrack helps independent agencies adapt and meet the evolving need of consumers and the insured so producers can focus on what they do best: selling insurance".
For more information on Agency SalesTrack and to register for a webinar explaining how it works you can visit the Vertafore website.
Photo Credit: Mikko Lemola / Shutterstock
-

95 percent of US consumers share their passwords
Publié: février 18, 2016, 4:06pm CET par Ian Barker

It seems that convenience trumps security when it comes to passwords. Although 73 percent of US consumers believe sharing login details is risky, 95 percent do share between one and six of their passwords with other people.
A new survey by LastPass also reveals that only 19 percent of respondents say they don't share passwords that would jeopardize their identity or financial information, leaving a scary 81 percent of people who would share them.
The study explored the password sharing habits of more than 1,000 US consumers of 18 or older. Among the key findings were that 59 percent use the same password on multiple sites, which means people are potentially exposing more online accounts than they realize through password sharing.
"Nearly all aspects of our lives have some online component and when you bring password sharing into the mix, all of that sensitive information is instantly compromised," says Joe Siegrist, VP and GM of LastPass. "We realize that at times, people and teams need access to the same accounts, so we created a new LastPass Sharing Center in our 4.0 version, allowing users to easily and securely share their passwords, giving them the peace of mind knowing their passwords are protected".
Other findings include that only 27 percent of respondents reset a password after sharing it with others. Younger generations are more trusting too, those aged 18-29 are the most likely to share passwords with friends. In fact, 40 percent said they’d shared a password with a friend as opposed to 15 percent of those aged 30-44, only 6 percent aged 45-59 and 8 percent aged 60+.
Password sharing isn't limited to personal accounts either. One in four respondents admit to sharing business passwords, classified as any password associated with their workplace. Additionally, 61 percent of respondents say they are more likely to share their work passwords than personal passwords.
You can find more details of the survey's findings in the infographic below.
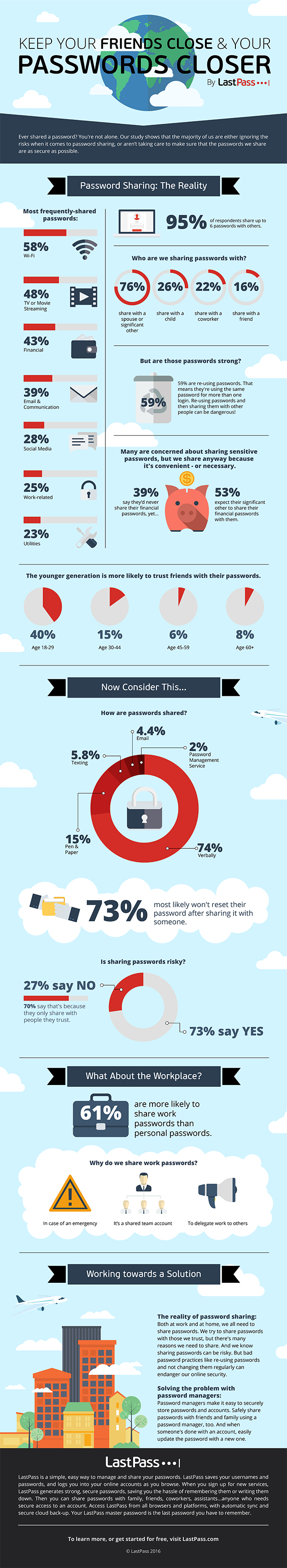
Photo credit: shutteratakan / Shutterstock
-

Are you Digitally Enlightened or an Online Nudist?
Publié: février 18, 2016, 3:51pm CET par Ian Barker

According to the results of a new survey, while two thirds of US respondents say they would like extra layers of online privacy and security, their actions prove otherwise as few even use currently available tools.
The study by VPN provider Hide My Ass! has been used to categorize people into five different approaches to online life:
* Old School Sharers are hesitant to share personal information or participate regularly on social media and lack confidence that they are protected from threats.
* Cautious Contributors are apprehensive about new technology, but are more socially inclined and learn from the mistakes of the past.
* Online Nudists seek out and bare everything to their online community, craving a high amount of interaction with their peers through social media.
* Social Savvy Butterflies are active in and seek interaction from online communities, but have stepped up their game and take precautions to ensure their personal information stays safe.
* The Digitally Enlightened employ the highest levels of security, which enables them to safely maintain their highly active digital lives.
Among the survey's findings are that 63 percent of respondents have experienced online security issues, but, of those, only 56 percent have made permanent behavior changes afterwards. Nearly one in four people (24 percent) use unsecured public Wi-Fi, leaving their information open to prying eyes, quite often or all the time.
Take up of existing security tools is depressingly low, only 16 percent utilize privacy-enhancing browser plug-ins, just 13 percent use two-factor authentication and a mere 11 percent use a VPN. In fact 44 percent are not at all familiar with VPNs and a mere four percent use anonymity software (such as Tor).
While 70 percent say that the risk of exposing personal information online reduces their level of social media use and presence, only a quarter have strict privacy restrictions in place on their social media accounts. Also while two thirds say they are likely to shred physical documents containing personal information they are happy to post details online including their email addresses (51 percent), home addresses (26 percent) and personal phone numbers (21 percent).
"Even with the NSA revelations and a seemingly endless onslaught of celebrity hacks and public data breaches, Americans still turn a blind eye to their vulnerability online," says Danvers Baillieu, the chief operating officer of Hide My Ass! "While many people say they want to protect themselves online, it is difficult for them to sacrifice things like their level of social presence. For too many, the gratification of a ‘like’ severely outweighs the investment in building a digitally secure life. When it comes to choosing either security or convenience, the latter almost always wins".
You can find a summary of the findings in infographic form below.
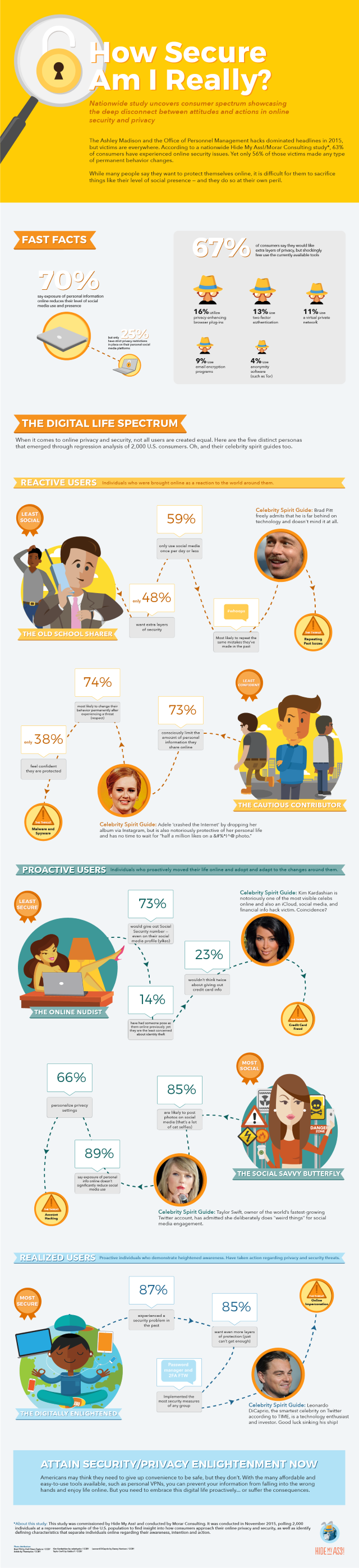
strong>Image Credit: jurgenfr / Shutterstock
-

IT professionals' bad security habits exposed
Publié: février 18, 2016, 3:17pm CET par Ian Barker

Many IT personnel don't follow the same security protocols they’re expected to enforce according to the results of a new survey of over 500 professionals working in IT security roles.
The study by Absolute Software Corporation shows that 45 percent of IT professionals admitted to knowingly circumventing their own organization's security policies. In addition 33 percent of respondents admitted to successfully hacking their own or another organization.
"Given that IT is the security gatekeeper for an organization, it was alarming to see such high incidents of non-compliant behavior by IT personnel," says Stephen Midgley, vice president, Global Marketing at Absolute. "Even if these actions are being performed to validate existing infrastructure, senior leadership should be aware that this activity is occurring. It may also be worthwhile to consider third-party audits to ensure adherence with corporate security policies".
Security remains at the top of the IT spending list, with 87 percent of respondents expecting increased investment in security this year. Despite prioritizing security and increasing budgets, IT departments believe that employees represent the greatest security risk to an organization (46 percent). This may be related to the fact that on average, 33 percent of all security protocols are not being followed by staff. It may also explain the high incidents of security breaches, with 38 percent of respondents experiencing a data breach within the past year.
Younger professionals are also likely to show a more casual attitude to security according to the findings. Among IT professionals aged 18-44, 41 percent are likely to hack their own organization compared to just 12 percent of those in the 45+ age group. 92 percent of 18-44 year-olds say they are confident in containing a data breach, compared to 79 percent of 45+ professionals.
"Despite marked improvements, businesses are still very susceptible to attack," adds Midgley. "The gaps in current data breach response plans and in upholding general best practice policies must be addressed".
The full report is is available to download from the Absolute website.
Photo Credit: Alexander Kirch/Shutterstock
-

Malwarebytes launches new endpoint detection platform for enterprises
Publié: février 17, 2016, 6:20pm CET par Ian Barker
Traditional endpoint security often ends up generating lots of false alerts which take up valuable support time to investigate and resolve.
Anti-malware specialist Malwarebytes is aiming to make things easier for businesses with the launch of its latest Breach Remediation product, a platform that improves organizations' ability to remove advanced threats from their endpoint systems.
It uses a scanning engine that detects and removes infections and related artifacts simultaneously across all endpoints on the network. Malwarebytes Breach Remediation scans network endpoints looking for suspicious files or anomalies and, when found, pieces together all of the threat traces allowing it to automatically fix other compromised systems on the same network.
"Traditional breach remediation involves an incident responder running to each computer to put out cyber fires, one at a time," says Marcin Kleczynski, CEO of Malwarebytes. "Three hours later the same security team member runs to put out another fire. This inefficient way of 'solving' the issue hasn't evolved for decades. Now, Malwarebytes and our integration partners are creating an automated sprinkler system that enables the whole enterprise to put out fires as they appear across thousands of endpoints".
In addition using its own behavioral rules to identify compromised endpoints, Malwarebytes Breach Remediation can read custom indicators of compromise (IOC) from third party sources, including Mandiant, Lastline and Fidelis, as well as the Open Indicators of Compromise (OpenIOC) framework, to hunt for new and undetected threats.
The product is available now from authorized resellers and will be shown at the RSA Conference in San Francisco from 29 February to 4 March. For more information you can visit the Malwarebytes website.
Photo Credit: Palto/Shutterstock
-

ID as a Service solution helps to secure digital access
Publié: février 17, 2016, 4:23pm CET par Ian Barker

Identity and access management (IAM) is a growing field, expected to be worth around $18 billion by 2019 according to a recent report.
This is partly down to cloud growth creating the need for a secure solution that can scale quickly, in on-premise environments and across cloud applications, without additional costs for installation and extra hardware.
IAM solutions company IDdriven is entering this market with its new Identity as a Service (IDaaS) solution. This aims to offer an easy-to-implement and cost-effective way for companies of all sizes to secure and manage their digital access points.
"My team and I spent 24 months engineering a product that we felt encompassed and addressed all of the technical elements currently missing from IDaaS solutions on the market," says Arend Verweij, CEO of IDdriven. "This is reflected in the core features and delivery of IDdriven. We offer scalable pricing, access control based on company role and location, along with analytics and reporting on use and threats. These features, among others, give our company a massive competitive edge in a crowded marketplace".
IDdriven is subscription-based, so that businesses of all sizes can secure their digital access, cost-effectively. It also integrates seamlessly with existing ID management systems, to add new functionality while getting the most out of existing investments.
It has a robust and secure back end running an easy-to-use UI, specifically designed to be accessible to all users, regardless of their experience level. Role and zone-based access control delivers the ability to manage the identities and access rights of employees based on their company role and precise location, anywhere in the world and on all devices. A self-service feature gives added flexibility, without risking security, by enabling employees to request access to applications from a central service desk as their job roles evolve.
You can find out more and request a demo on the IDdriven website.
Image Credit: Kirill Wright / Shutterstock
-

Threat Stack launches integrated cloud security suite
Publié: février 17, 2016, 3:28pm CET par Ian Barker

Keeping systems secure has become more complicated as companies adopt cloud and hybrid environments for their systems.
To eliminate the need for multiple different security products and give users a single-pane view into workloads, infrastructure monitoring, vulnerability management, threat intelligence and compliance reporting, Threat Stack is launching a new Cloud Security Platform.
Threat Stack CSP gives users the immediate visibility and vital insights needed to operate efficiently, prevent data loss and identify and verify threats, while keeping data secure and compliant.
"We recognized an opportunity to evolve with the many companies looking to move into or expand within the cloud. Today’s security needs go beyond singular point solutions, so we have answered the market's requests with a complete security platform which will not only scale, but meet all of the immediate and future needs of our customers," says Brian M Ahern, chairman and CEO of Threat Stack. "This integrated platform approach will save our clients money, as well as organizational effort to manage security and compliance initiatives".
Key features include workload insights to help organizations verify whether their environments have been compromised by insider threats and/or data loss by tracking suspicious user activity, tracking connections to command and control servers and tracking access to secret configuration files. Tracking changes to infrastructure in real-time and generating infrastructure alerts based on user, event name, counts of events, and source IP means changes to a software-defined infrastructure won’t occur without security teams knowing about them.
Threat Stack CSP examines package information and tells the user if there is anything vulnerable. It then organizes workflows around what’s important based on common vulnerabilities and exposure (CVEs). Threat Intelligence lets companies know when workloads are communicating to known bad hosts, and receive granular alerts about who servers are talking to.
There's also real-time visibility, detailed audit trails and built-in compliance reporting provide the historical record companies need to meet compliance regulations and ensure data and infrastructure are protected.
Threat Stack CSP is available now and you can find out more on the company's website.
Photo Credit: Marynchenko Oleksandr / Shutterstock
-

Store your personal data in a HAT to keep it safe
Publié: février 16, 2016, 3:45pm CET par Ian Barker

As we use the internet we give away information to lots of sites from shopping portals to search engines. The growth of the Internet of Things is likely to see a further boost in the amount of data held and shared about us.
The Warwick Manufacturing Group (WMG) at the University of Warwick in the UK is working on £1.2 million HAT (Hub-of-all-things) research project to develop a platform technology where individuals can keep all their personal data in one place.
Funded by the Research Councils UK Digital Economy Programme and working in conjunction with industry and commercial partners, the research project has developed a personal data platform to perform all four key operations on personal data: collect, control, re-combine, contextualize and share.
"Now is the time to wake people up to just how much personal data they pour online and empower them to use that data to benefit them as much as its benefiting the businesses that are harvesting it," says Professor Irene Ng of WMG. "With the internet of things growing as a concept people need to get as much utility out of their own data as the product providers and utilities that will increasingly be taking that data".
A HAT Foundation will develop the next phase of the technology, taking over from the HAT research project team in WMG to roll-out the HAT globally in 2016. The Foundation will scale-up the HAT ecosystem and build a community of HAT users, to promote widespread take-up of HATs by individuals.
"The data on your HAT is owned by you and can be recombined by you so that you can make it meaningful and useful for decision-making. The HAT is also a fully scalable personal data platform for firms to offer you services for your data in a privacy-preserving way, as well as allowing you to track and creatively organize your data for better informed decisions in your lives," adds Professor Ng. "Most importantly, I believe that the HAT will start a movement for individuals to claim our personal data, as we believe it is now time for us to gain control of our digital lives and put ourselves, as individuals, at the center of the growing data exchange in the sharing economy".
You can find out more about the project on the HAT Foundation website.
Photo Credit: jazzerup/Shutterstock
-

New solution protects enterprise websites from attack
Publié: février 16, 2016, 3:06pm CET par Ian Barker

Some of the latest cyber attacks seek to steal information using man-in-the-browser (MITB) attacks. These represent a dangerous trend because they circumvent even the strongest authentication techniques by hijacking the session after the user has authenticated a bank or other site.
Threat intelligence start up buguroo is looking to combat this with its new online fraud detection solution that can detect hijacked sessions in real time and stop them before any money leaves the bank.
The company's new bugFraud Defense technology is entirely host- and cloud-based and doesn't require any action, such as installing software or an agent, by an end-user client in order to be protected. The buguroo software is transparent to the user, requires minimal resources and doesn't degrade the user experience or performance.
"Any online fraud detection solution that still relies on signatures or requires users to take action is based on a failed model," says Pablo de la Riva Ferrezuelo, CTO and founder of buguroo. "Industry research shows that 'opt-in' models that require installing client-side software at best get low single digit percentage participation. Study after study shows users expect their service providers to protect them, and they are not willing to help. Period. That's what we do".
The solution is implemented at web server level for both development and security teams. It then requires only a lightweight modification in regular server content to link online sessions to the cloud-based fraud detection engine.
Available immediately in the US, Europe and Latin America, buguroo bugFraud Defense can be bought as a standalone product or as part of bugThreats, the company's comprehensive threat intelligence platform, also announced today. The company is targeting those sectors most commonly attacked by cyber criminals, banking, social networking and e-commerce. More information is available on the buguroo website.
Photo credit: Lichtmeister / Shutterstock
-

IBM unveils new mainframe for secure hybrid clouds
Publié: février 16, 2016, 12:15pm CET par Ian Barker

More and more organizations are seeing the benefits of adopting the hybrid cloud, but they don’t want to risk sacrificing the security advantages of more traditional systems.
To help businesses tap into hybrid cloud without sacrificing security, IBM is announcing a new mainframe, the z13s. Building on the mainframe’s world-class performance and security profile, the z13s features new embedded security technologies, enhanced data encryption and tighter integrations with IBM Security solutions.
The z13s provides the foundation for a more secure, end-to-end hybrid cloud environment, allowing organizations to protect their most sensitive data without sacrificing performance. Features include a new cryptographic co-processor and hardware-accelerated cryptographic coprocessor cards provide encryption up to two times faster, so users can increase workload security without compromising throughput and response time.
The new z13s has up to 4TB of memory (eight times more than previous single-frame mainframes) along with faster processing speeds and sophisticated analytic capabilities. IBM Multi-factor Authentication (MFA) for z/OS has been integrated into the operating system, adding to overall security by requiring users to enter a second form of identification, such as a PIN or randomly generated token, to gain access to the system.
It also has IBM's Security Identity Governance and Intelligence software which helps prevent data loss by governing and auditing device access. Integrated into the mainframe, QRadar and Identity Governance use real-time alerts to focus on identified critical security threats, while Security Guardium uses analytics to help ensure data integrity by providing intelligent data monitoring.
"Fast and secure transaction processing is core to the IBM mainframe, helping clients grow their digital business in a hybrid cloud environment," says Tom Rosamilia, senior vice president, IBM Systems. "With the new IBM z13s, clients no longer have to choose between security and performance. This speed of secure transactions, coupled with new analytics technology helping to detect malicious activity and integrated IBM Security offerings, will help mid-sized clients grow their organization with peace of mind".
New z13s systems will be available from next month and you can find out more about IBM's z Systems portfolio on the company's website.
-

New report reveals in-game purchase habits
Publié: février 15, 2016, 3:29pm CET par Ian Barker

Only around two percent of free to play game users spend money making in-game purchases. A new report into buying habits from gaming analytics specialist SOOMLA reveals the -- perhaps unsurprising -- information that those who made an in-app purchase in one game are six times more likely to do so in another.
Yaniv Nizan, Co-founder and CEO of SOOMLA, says, "Attracting payers to your game is like finding a needle in a haystack, but when crossing in-app purchase data from thousands of other games, our payer prediction technology reveals which user segments will eventually convert and what they're likely to buy".
Other insights from the report include the fact that quick payers (those who make a first in-app purchase within 24 hours of install) are nine times more likely to pay in another game. Plus over 40 percent of users who paid $25 or more in one game, will also pay in another game.
For each in-game item users purchase with real currency, an average of 18 additional items are purchased with virtual currency. And while 71 percent of in-game purchases are for 'single use' items, like extra time or ammunition, it's 'lifetime' items such as characters, level packs or advert removal, that account for 65 percent of revenue.
Looking at usage patterns, daily active users increase by as much as 33 percent at weekends, and this occurs primarily on phones, although sessions on tablets are often longer in duration. Patterns differ across game genres as well, with strategy games boasting the highest average session duration of 11 minutes -- 2.6 times more than for other genres. Seasonal factors are at work too with developers who market their apps in time for the holiday season achieving an average revenue per paying user increase in December of 83 percent above the annual average.
If you want more information the full report is available to download from the SOOMLA website.
Photo credit: Mmaxer / Shutterstock
-

Better customer experience can turn travel searchers into bookers
Publié: février 12, 2016, 4:09pm CET par Ian Barker

When people are booking travel, companies like travel agencies, hotel chains and airlines have an opportunity to gain a loyal customer.
But a new survey of more than 500 travelers from data science specialist Boxever suggests that the window to turn searchers into bookers and beat the competition is a narrow one.
While you might think that price is a driving factor, only 47 percent of those surveyed say they prefer airlines and online travel agencies to present the cheapest flights first in online search results. The results show that almost a third of travelers want the best, most relevant options presented first, those that take into account a range of key elements including price, timing, duration, personal preferences, past travel history and needs.
A personalized booking experience is important too, 85 percent say they would value travel websites that remember their personal preferences and automatically present the best and most relevant options.
There's also a demand for a more connected experience, 54 percent of frequent travelers would like airlines, hotels, ground transportation providers and other travel companies to automatically share their travel information. People say they are willing to provide more information about themselves if it leads to a better travel experience.
The opportunity to sell extras is there but it's important that it’s presented early in the booking process. 48 percent of travelers who purchase extras or services do so when booking, but just 16 percent will add extras -- like Wi-Fi or a seat upgrade -- in the days before a flight, and even fewer wait until they actually arrive at the airport.
Respondents also displayed a reluctance to respond to promotional messages. 38 percent say they almost never check the promotions or adverts tab in their personal email, nine percent only check it a few times a year and 13 percent a couple of times a month. However, 33 percent say they would consider moving a company’s mail to their main inbox if the content was consistently targeted to their needs and preferences, and not the marketing priorities of the company.
The full report is available to download from the Boxever website.
Photo Credit: Ilin Sergey/Shutterstock
-

Social engineering tops the hacking pops
Publié: février 12, 2016, 12:45pm CET par Ian Barker

Hackers are constantly seeking new ways to attack systems and gain insider access to data. A new survey from IT security company Balabit reveals the 10 most popular hacking methods to help companies understand how to protect themselves.
The survey of almost 500 IT security practitioners reveals that social engineering is the most popular means of attack. Hackers aim to get a 'low level' insider user account by means of phishing and escalate its privileges.
"Traditional access control tools and anti-malware solutions are necessary, but these only protect companies’ sensitive assets while hackers are outside of the network," says Zoltán Györkő, CEO at Balabit. "Once they manage to break into the system, even gaining a low level access, they can easily escalate their rights and gain privileged or root access in the corporate network. Once it happens, the enemy is inside and poses a much higher risk as they seem to be one of us".
Compromised accounts, such as those with weak passwords, is the second most popular route. If users have the same password on work and personal accounts the attacker only needs to discover one, from a social network account say, to open up corporate systems.
Third place is taken by web-based attacks such as SQL injections. The quality of code in many applications is still questionable from a security point of view, and there are many automated scanners from which attackers can easily detect vulnerable applications.
"The highest risk to corporations is when outside attackers gain insider access, as they can stay undetected within the network for months," says Györkő. "Balabit aims to support organizations to know their enemy by knowing who is behind their user accounts, and determining whether it is a legitimate user or a masked hacker. This should be the fundamental priority in every kind of organization's IT security strategy".
You can see the full top 10 in the infographic below.
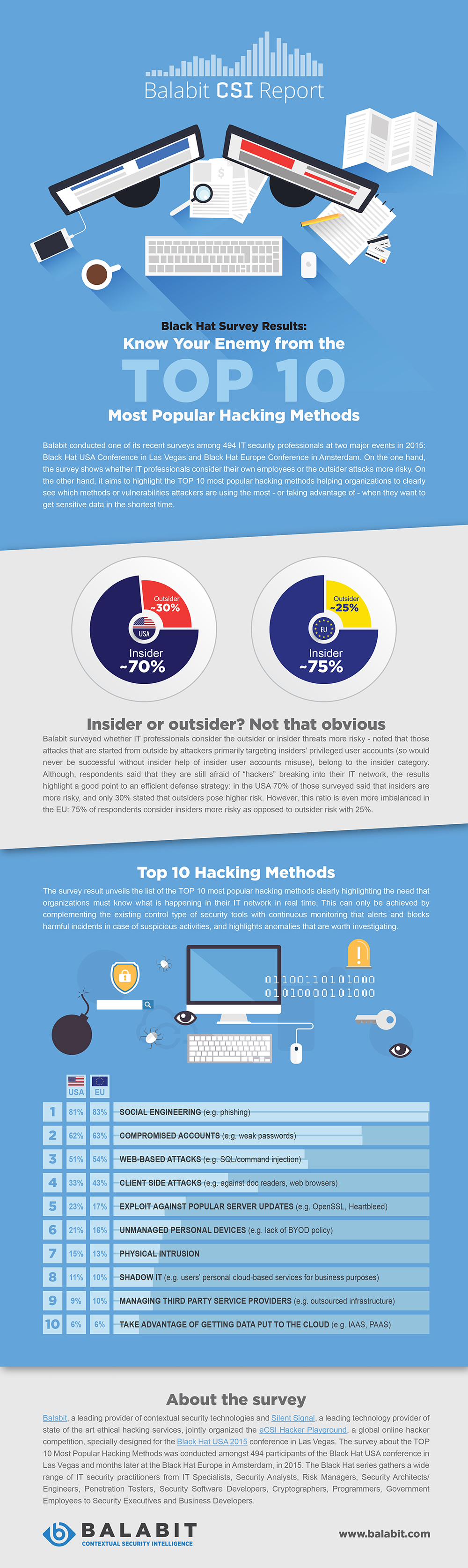
Photo Credit: igor.stevanovic/Shutterstock
-

ISP filters could be harming UK users’ love lives
Publié: février 12, 2016, 12:15pm CET par Ian Barker

Content filters are supposed to protect you from bad stuff, but they can have unexpected side effects and block things you want to access.
As we approach Valentine's Day a new survey by UK broadband comparison site Broadband Genie has discovered that filters may be preventing Brits from finding love by blocking online dating sites.
As part of prime minister David Cameron's bid to protect children from adult content, ISPs are now required to have 'family-friendly' web filters automatically enabled. The filters can block a wide array of sites, from online dating to pornography, but there is skepticism about their effectiveness and concerns about how sites are classified.
The company revealed last year that 46 percent of users may have their filters activated, meaning many could struggle to access online dating services. But these latest results show that 73 percent of people surveyed wouldn't know how to access online dating websites if they'd been blocked by their ISP's content filter.
"Not only are there questions on the effectiveness of the filters, but the sheer amount of confusion they're causing is very worrying indeed," says Rob Hilborn, Head of Strategy at Broadband Genie. "The opt out nature of the filters means ISPs now have a much bigger responsibility to provide users with accessible information and simple processes to make a decision on opting out if they should want to".
Respondents to the survey are divided on whether dating sites should be blocked. A majority (60 percent) say online dating websites shouldn't be blocked by default, however, 29 percent think dating sites don't do enough to stop children from accessing them, and 54 percent believe dating sites pose a threat to children.
Hilborn concludes, "It's incredibly important we put the correct measures in place to protect children online, whether that's through web blocking tools or better education. However, we shouldn't be damaging legitimate businesses through poorly executed and confusing blanket filters which ignore how people actually use the internet".
You can read more on the report's findings on the Broadband Genie blog.
Photo Credit: SueC/Shutterstock
-

The top threats to watch for in 2016
Publié: février 11, 2016, 4:01pm CET par Ian Barker

Messaging and infrastructure security specialist Cloudmark has released its Annual Global Threat Report for 2015 which reveals the biggest current threats based on its crowd sourced security platform, which analyses user behavior from more than a billion subscribers.
Top of the list is the Swizzor malware which delivers unsolicited ads, modifying browser settings without user permission. This silent threat delivers booby-trapped emails to unsuspecting users with varying subject lines. Each email contains a zip file carrying the malware payload, this uses a simple domain generation algorithm for command and control synchronization to create a large number of domains that then clash with legitimate websites and make it difficult for them to be taken down.
Senior marketing consultant Pam Strayer writing on Cloudmark's blog says, "This under-the-radar malware uses novel URL naming conventions with common, simple words to disguise itself as normal traffic. Appearing as normal email traffic, the malware attempts to subvert typical email security and character distribution analysis".
Shortened links were another major concern in 2015 with 25,000 different malicious links detected, of which 97 percent are email spam. Spammers are using this method as an easy way to generate an unlimited number of call-to-action URLs that redirect to a server hosting storefronts and spam content. By using multiple links it's harder for spam filtering to detect them all. This activity also reflects badly on major brands, the CNN.it URL shortener for example has been abused, peaking at 8,800 malicious URLs in a single day on 11th Jan 2016.
Cloudmark reports that 91 percent of firms have experienced a spear phishing attack and that this is costing companies $1.6m annually. In a surprising development the report also shows that Germany has become the biggest spammer in Europe, sending more junk email than Russia, India and China.
Cloudmark expects that as the Internet of Things creates more uses for connected devices and intelligence, criminals will find a way to take advantage for malicious purposes. For example a home security system could be hacked and instructed to unlock a door to allow a thief to enter -- or perhaps lock a victim in. Other possibilities include, spying on conversations, or filming people in the privacy of their homes using smart TVs connected to webcams.
Other predictions are that zero day exploits will become so valuable that they may be deliberately introduced by developers so that friends can claim the bug bounty. The report also forecasts that the UK's Investigatory Powers Bill will cause other major Internet companies to follow Yahoo's lead and move their operations out of the UK to avoid being subject to this law.
The full report is available to download from the Cloudmark website.
Image Credit: underverse /Shutterstock
-

Dating apps -- the good the bad and the ugly
Publié: février 11, 2016, 12:47pm CET par Ian Barker

It's coming up to Valentine's Day, so inevitably the IT industry turns its thoughts towards dating apps. Two new reports show that the apps may not be living up to expectations, and that users of them could be revealing more than they intend to.
New research from app quality researcher Applause shows that consumers are more dissatisfied with dating apps than any other type.
The research looked at 97 apps, with a minimum of 2,000 app store reviews, which received a quality score based on consumer sentiment on a 0-100 point scale (100 being the best score). Overall, the dating apps lagged all other apps in quality by 23 points.
Just 11 dating apps earned quality scores of 50 or more with more than 10,000 app store reviews, including OKCupid and GROWLr by Initech. Tinder dropped by over 10 points in the last year, since Applause's first report on the category last February.
Consumers have high expectations when it comes to their dating app's style, privacy and security. The report concludes that, "Brands looking to improve their app quality in the eyes of users would be wise to invest in usability and security audits to prioritize product improvements". The full version is available on the Applause website.
As if that wasn’t bad enough news for the industry, software management specialist Flexera has issued a report which shows that many popular dating apps could present a security risk for enterprises when installed on BYOD devices.
Of the 25 popular Apple iOS dating apps tested 88 percent, including Grindr, OKCupid and Tinder, are capable of accessing a device's location services. 76 percent support ad networks and 60 percent are capable of accessing the device's social networking apps as well as SMS/Texting functions.
36 percent, including Grindr, Lovestruck and OKCupid, are capable of accessing the device's calendar, and 24 percent, including Blendr, Hinge and Tinder, are capable of accessing the address book.
The full report is available on the Flexera website and there’s an infographic summary of the findings below.
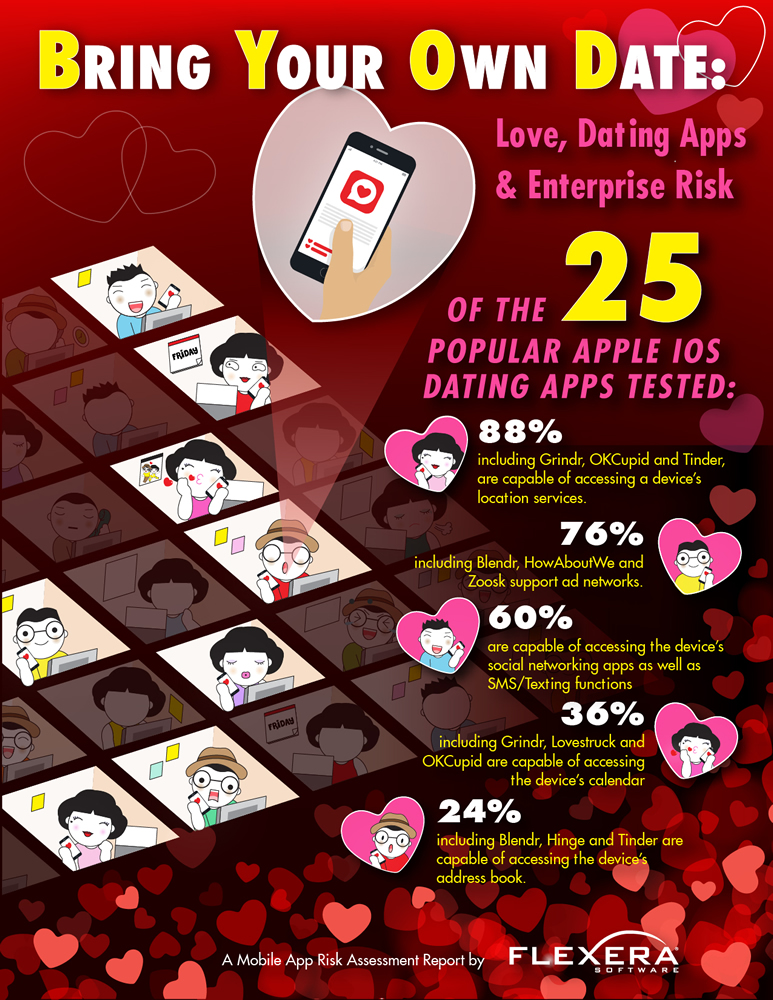
Photo Credit: JoeyBear/Shutterstock
-

Dridex botnet hacked to deliver free antivirus software
Publié: février 5, 2016, 3:14pm CET par Ian Barker

Widely used by cyber criminals to introduce malware onto systems, the Dridex banking trojan has been subject to a number of high profile investigations, and a takedown by US authorities last year.
These things don't stay dead for long, however, and Dridex is back in business. But in an interesting new twist it seems that the Dridex botnet has been hijacked to deliver the free Avira antivirus program rather than its more usual malicious payload.
Dridex is spread by spam, usually using a Word document with malicious macros. Once the file has been opened, the macros download the payload from a remote server, and the computer is infected. In the latest version though the links have been modified to deliver Avira instead.
"The content behind the malware download URL has been replaced, it's now providing an original, up-to-date Avira web installer instead of the usual Dridex loader," says Moritz Kroll, malware expert at Avira.
The company denies that it's behind the modification itself. "We still don't know exactly who is doing this with our installer and why -- but we have some theories," says Kroll. "This is certainly not something we are doing ourselves".
Explanations as to why this is happening include that it's an attempt to confuse detection processes. It could also be the work of white hat hackers who want their identities to remain secret. "While what they are doing is fundamentally helpful, it is also technically illegal in most countries, so they probably don't want to be known or identifiable," adds Kroll.
You can find out more about this unusual development on the Avira blog.
Image Credit: Julien Tromeur/ Shutterstock
-

New UK homes to get superfast broadband -- maybe
Publié: février 5, 2016, 2:38pm CET par Ian Barker

The UK government has today announced that it will work with Openreach -- BT's local access network business -- and the Home Builders Federation (HBF) on an agreement to deliver superfast broadband connectivity to new build properties in the UK.
The deal will mean that fibre-based broadband is offered to all new developments either for free or as part of a co-funded initiative.
Openreach will offer an online planning tool for homebuilders. This will tell them whether properties in any given development can be connected to fibre for free, or if a contribution is needed from the developer to jointly fund the deployment of the local fibre network. Openreach says it will make a 'significant contribution' to the installation costs before seeking funds from developers.
"This is an important step towards bringing fibre broadband to as many new build properties as possible," says Clive Selley, CEO of Openreach. "We recognise that high speed broadband connectivity is a major factor for homeowners when deciding to buy a house. That's why we’re offering to deliver fibre to all new build developments either for free or as a co-funded model".
The announcement has met with a luke warm response in some quarters, however. Dan Howdle, consumer telecoms expert at broadband and TV advice site Cable.co.uk says, "What is the purpose of a network provider making it easier for developers to install proper broadband infrastructure if it still remains the homebuilder’s choice as to whether or not to take action? These measures are arbitrary and unlikely to have any effect. They comprise neither legislative enforcement of superfast for new builds, nor any obligation for homebuilders to inform buyers they face years of broadband misery".
Howdle continues, "Today's announcement allows homebuilders to continue to do exactly what they have been doing: to sell homes with little or no broadband connectivity and without forewarning their buyers. As such, it is unlikely to appease the many thousands of families forced to choose between living with little or no connectivity, or selling up and moving on".
More details of the announcement can be found on the UK government's website.
Image Credit: Peter Bernik / Shutterstock
-

Managing risk in the digital supply chain [Q&A]
Publié: février 4, 2016, 12:42pm CET par Ian Barker

You may be aware of risks and problems in your own business, but increasingly it's possible to be exposed to issues by other organizations that you deal with, particularly if you're buying in IT services.
How can enterprises deal with these threats and ensure that their data and that of their customers is kept safe at all stages of the supply chain? We spoke to Dean Coleman, head of service delivery at service management and support specialist Sunrise Software, to find out.
BN: How difficult is it for larger organizations to manage problems that might occur further down the supply chain?
DC: It can be quite difficult, historically most organizations have a handle on risk in terms of what's going on in the business, financial targets and so on. But when it comes to IT risks and the supply chain providing IT they don't have the same visibility. These days IT is everywhere and businesses depend on it so IT problems have a larger impact. The understanding of risk needs to be something that key decision makers are more aware of.
BN: Is this a particular problem when dealing with smaller companies who might not have resources in house?
DC: Yes, from the supplier side of the fence we see that smaller organizations often don't have the skills in house to deal with security, infrastructure, and so on. They rely heavily on these services but don't see them as a core part of their business. Because they don't have the skills and resources they will often turn to third parties to manage these things for them. However, in some cases the third parties also don't do a very good job, they’ll be providing reactive services rather than the proactive ones that are really needed to predict problems based on risk.
BN: Is this something larger companies need to address in their service agreements with smaller ones?
DC: Definitely, it's essential that they do. They should be offering services that highlight back to their customers what the potential risks are and what the impact of those risks could be. They also need to highlight where changes and improvements are needed and where investments will be most effective. Information from service providers can allow businesses to make effective decisions.
BN: Is it about more transparency at all levels?
DC: Not only does the customer benefit from having better information to make decisions, it helps the service providers themselves because they're highlighting the risks of, say, a server failure. While service providers might be responsible for keeping systems up and running they don’t necessarily have direct control of the hardware and infrastructure involved. This can leave them in a position where they can highlight a risk -- like a server running short of disk space -- but it's down to the customer to take action.
BN: How much emphasis should there be on education since the human factor is often the weakest link?
DC: There is an element of that, education is always key when it comes to IT. People need to be aware of issues like phishing, although services like filtering are now very effective there’s always a risk of things like fake invoices getting through and catching users unawares.
BN: What challenges will service providers face in future?
DC: One of the struggles for service providers is how they manage risks, keep track of them and make sure their customers are aware of them. They need to regularly report back to customers with risk assessments and the potential impact they can have, plus recommended courses of action. Most providers will now have very good tools to ensure that systems are kept up to date rather than relying on spreadsheets and older methods. they’re now able to link risks not only to infrastructure but to specific services or people they could directly affect.
BN: Does this ultimately lead to providing a better service because you have a more resilient system?
DC: Yes, if you're aware of and managing the risks and have plans to mitigate problems then the services you provide should improve. The availability should increase because you’re taking a more proactive approach, and as a service provider it also leads to opportunity for more revenue, selling services, technology, project management and so on. Greater transparency leads to a better relationship with the customer and the opportunity to quote for more business.
Image Credit: jannoon028 / Shutterstock
-

OnePlus 2: Impressive mid-range smartphone [Review]
Publié: février 3, 2016, 4:53pm CET par Ian Barker

OnePlus may not be a name that springs instantly to mind when you think of smartphones, but it really should be. It is a Chinese company that is fast developing a reputation for turning out quality handsets at something of a bargain price.
The company's latest OnePlus X model starts at around £200 which is only about £40 below the price of its flagship, the better specified OnePlus 2 model, so does it live up to the company’s claims that this is an affordable phone with premium features?
In the Box
You get a nicely presented package which makes it feel like you’re getting a quality product from the off. Lift off the lid and you find the phone sitting on top of a red box which contains the charger, instructions, a clear screen protector and a rubber sleeve.
The phone itself looks smart with milled edges that catch the light and a shiny glass black back panel -- though this does show every fingerprint. It’s just under 7mm thick and weighs a relatively lightweight 138 grams. There’s a limited edition Ceramic version of the phone available too, but in appearance it’s not too different from the black glass of our review unit and its functionality is the same.

Power and volume switches are on the right-hand edge; again, these have a machined finish that makes them feel a cut above the plastic buttons on, say, a Nexus 5X. The combined SIM card and memory card slot, accessed in the usual way by poking a tool into a little hole, is also on the right.
On the left is a three position Alert Slider; this is a novel touch that lets you quickly set the phone to silent, priority or tell-me-everything modes in a single action. It’s handy for when you’re going into meetings for example allowing you to quickly silence the phone without having to access the screen. On the bottom edge are the speaker grilles and a standard microUSB port, the headphone socket is at the top left. Unlike the OnePlus 2 the X lacks a fingerprint scanner.

There are hardware buttons at the base of the screen for the usual back, home and recent apps functions. These are very faint and quite hard to see, but you can opt to use soft buttons instead; these nibble away a bit of your screen space. Like the Nexus 5X, the phone is a nice size to hold and operate one-handed thanks to a 5-inch screen.
Under the skin is a Qualcomm Snapdragon 801 quad-core processor, 3GB of RAM, 16GB of storage and an Adreno 330 graphics processor. If you need more space you can add a microSD card to expand the storage up to 128GB.
There’s a 13MP rear camera and an 8MP front and the display offers 1,920 x 1,080 resolution. It’s all powered by a 2,525mAh battery which, depending on how you use it, should get you a couple of days between charges. It’s a dual-SIM phone too, connectivity is via 4G, Wi-Fi and Bluetooth, but you don’t get NFC.
The OnePlus X runs the previous generation Android 5.1.1 Lollipop, and it has OnePlus’ Oxygen user interface. This doesn’t make many changes to stock Android other than adding light and dark menu options, shortcuts to apps you use frequently and some tweaks to app management. It’s largely free of bloatware though, with the only installed apps being the SwiftKey keyboard, a custom file manager, Google Office apps and a OnePlus Radio app.
Business Features
The Alert Slider is a clever extra for busy executives who don’t want to be interrupted by their phone in meetings -- or perhaps when entertaining clients at the opera. Move the switch to one of its three positions and the phone just gives a little buzz and displays a message on the screen to acknowledge the instruction.
The dual-SIM feature is useful if you want to have access to separate business and personal networks on the same handset. However, one of the SIM slots doubles as a microSD card slot; a neat design, but it means you can’t have more storage and two SIMs installed at the same time.
The Oxygen UI’s app management feature gives you the ability to control permissions for individual apps, something that’s standard in Android Marshmallow, but not in Lollipop. This helps prevent data leaks by keeping your information private, limiting what information and hardware features each app is allowed to access without preventing you from using its features.
The Oxygen skin also lets you assign shortcuts to the physical home, back and recent apps buttons. You can have up to two shortcuts on each one, useful for apps that you use on a regular basis. Google Office apps for Docs, Sheets and Slides are pre-installed allowing you to work when you’re out of the office and access your data stored in the cloud.
In Use
The OnePlus X is a good size for ease of one-handed use and is nicely weighted without being too heavy. It also looks and feels like a much more expensive piece of kit, using it back-to-back after the Nexus 5X there’s no doubt that in a blind test you’d say the OnePlus was a much costlier device.
The phone feels nice in your hand too and the machined edges make it easy to grip. It does lack some hardware options you’ll find on pricer models, a fingerprint scanner and NFC communication being the main missing features.
Having a standard USB port means you’re more likely to already have adaptors, car chargers, etc that will fit, but on the other hand you miss out on USB-C features like faster file transfers. The supplied plastic cover feels a bit tacky, but it does help protect the edges and back of the phone from knocks and scratches and helps you to grip the handset. A selection of other covers is available from the OnePlus website if you fancy something a bit more stylish.
The OnePlus X’s Snapdragon 801 processor spec is one you’d have seen in the priciest flagship phones just a year or so ago. But despite the fact that it isn’t the very latest in CPU technology it feels easily fast enough to cope with day-to-day tasks. It streams video smoothly, opens apps fast and never feels like it’s struggling.
The display is a real high point of this phone, you often get LCD screens at this price point but the OnePlus uses AMOLED. What this means on a technical level is that the individual pixels are illuminated rather than the screen being cross lit as with an LCD display. In practice this translates to a display that delivers bright, vibrant colors and superb contrast, which means deep blacks. This combined with the black of the handset really seems to have colors zinging out from the screen.
Combine this with 440ppi pixel density that delivers nice sharp text and images and you have what is probably one of the best displays of any phone in this price bracket. In fact the display here is rather better than that on the more expensive OnePlus 2.
The physical buttons below the screen on the other hand are very faint and there’s no illumination option so you may well find yourself sacrificing some screen space to the soft buttons for the sake of ease of use. The screen has an auto brightness setting, but it does seem to make things a little too bright indoors; you’ll probably end up finding a comfortable setting for most conditions and turning the automatic option off.
Of course you’ll want to use headphones for serious listening, but the speaker -- yes, speaker, although there are two grilles on the bottom of the phone there is only one -- on the OnePlus is actually pretty good, delivering a clear sound at everyday volume levels.
It begins to sound a bit harsh if you crank things up higher, but that’s carping as few phones offer hi-fi speaker quality. The OnePlus Radio app lets you receive FM stations, it uses the headphone cable as an antenna so you can’t listen via the speakers when using it.
The Oxygen interface doesn’t mess too much with the Android user experience. As standard it has a dark theme which nicely shows off the capabilities of the phone’s screen. Probably the most useful feature it offers is frequently used shortcuts which can be found by swiping right from the home screen.
This gets automatically populated with apps and contacts according to use, rather like the frequently visited sites on your Google home page, you can also take control yourself and add widgets here for specific apps making it a good aid to everyday use.
Oxygen does have some odd omissions too, there’s no Gallery app, for example, meaning you have to find your photos and videos via the Files app. Oxygen is quite tweakable, however, so you should have no problem customizing it to fit in with the way you want to work.
Out of the box the OnePlus X comes with a number of gesture controls enabled. You can draw an "O" to launch the camera app for example or slide two fingers down the screen to pause playback of music or videos. You can turn these gestures on and off according to taste.
The rear camera delivers okay results though there’s no image stabilization and the f2.2 lens is slower than the one on its OnePlus 2 brother. You simply tap on the screen to focus, this also brings up a little gear wheel icon which you can drag around to adjust the exposure.
In low light it automatically cranks up the ISO level, this delivers clear images -- without using flash on many occasions -- but at the expense of some graininess. You also get some extra shooting modes built in including HDR for balancing detail and shadow, and a Beauty mode for enhancing portraits.
There’s also something called Clear Image which creates a higher res picture by stitching 10 images together. This takes just a couple of seconds to do and although it sounds gimmicky it delivers surprisingly good results.

There’s no 4K on offer, but you can capture video at 720P or 1080P. The 8MP front camera is not brilliant, but is fine for selfies and video calls. You do get a selection of basic editing functions which allow you to carry out simple fixes like adjusting brightness and cropping images, as well as adding some effects. It’s never going to get keen photographers excited, but the OnePlus X camera delivers perfectly good everyday snapshots.
Conclusion
Although it only costs £199/$249, the OnePlus X pulls off the trick of looking and feeling like a much more expensive phone, a result of the glass back and nicely machined metal components. There are no plasticky budget overtones here and the quality of the screen adds to the overall good impression too.
That said it’s not perfect, having to sacrifice the dual-SIM capability for extra storage is a bit frustrating, and the lack of NFC means no using Android Pay or quickly swapping data with other handsets. Other more minor frustrations include the hard to see hardware buttons below the screen and the fact that the back quickly becomes covered in fingerprints making the phone look rather scruffy.
There’s no doubt that this is an impressive phone for the price and one that you won’t be ashamed to whip out in high-level meetings -- or for that matter in the pub. Whether you buy one really depends on how you’re going to use it.
Given that the OnePlus 2, which does come with a fingerprint scanner and has a better camera, but still no NFC, only costs £40 more you might want to weigh up which is the better option depending on which features really matter to you.
Pros
- Excellent screen
- Smart design
- Well made
Cons
- No NFC
- Faint hardware buttons
- Second SIM/SD card trade-off
ITProPortal Review: 7/10
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

OnePlus X: Impressive mid-range smartphone [Review]
Publié: février 3, 2016, 4:53pm CET par Ian Barker

OnePlus may not be a name that springs instantly to mind when you think of smartphones, but it really should be. It is a Chinese company that is fast developing a reputation for turning out quality handsets at something of a bargain price.
The company's latest OnePlus X model starts at around £200 which is only about £40 below the price of its flagship, the better specified OnePlus 2 model, so does it live up to the company’s claims that this is an affordable phone with premium features?
In the Box
You get a nicely presented package which makes it feel like you’re getting a quality product from the off. Lift off the lid and you find the phone sitting on top of a red box which contains the charger, instructions, a clear screen protector and a rubber sleeve.
The phone itself looks smart with milled edges that catch the light and a shiny glass black back panel -- though this does show every fingerprint. It’s just under 7mm thick and weighs a relatively lightweight 138 grams. There’s a limited edition Ceramic version of the phone available too, but in appearance it’s not too different from the black glass of our review unit and its functionality is the same.

Power and volume switches are on the right-hand edge; again, these have a machined finish that makes them feel a cut above the plastic buttons on, say, a Nexus 5X. The combined SIM card and memory card slot, accessed in the usual way by poking a tool into a little hole, is also on the right.
On the left is a three position Alert Slider; this is a novel touch that lets you quickly set the phone to silent, priority or tell-me-everything modes in a single action. It’s handy for when you’re going into meetings for example allowing you to quickly silence the phone without having to access the screen. On the bottom edge are the speaker grilles and a standard microUSB port, the headphone socket is at the top left. Unlike the OnePlus 2 the X lacks a fingerprint scanner.

There are hardware buttons at the base of the screen for the usual back, home and recent apps functions. These are very faint and quite hard to see, but you can opt to use soft buttons instead; these nibble away a bit of your screen space. Like the Nexus 5X, the phone is a nice size to hold and operate one-handed thanks to a 5-inch screen.
Under the skin is a Qualcomm Snapdragon 801 quad-core processor, 3GB of RAM, 16GB of storage and an Adreno 330 graphics processor. If you need more space you can add a microSD card to expand the storage up to 128GB.
There’s a 13MP rear camera and an 8MP front and the display offers 1,920 x 1,080 resolution. It’s all powered by a 2,525mAh battery which, depending on how you use it, should get you a couple of days between charges. It’s a dual-SIM phone too, connectivity is via 4G, Wi-Fi and Bluetooth, but you don’t get NFC.
The OnePlus X runs the previous generation Android 5.1.1 Lollipop, and it has OnePlus’ Oxygen user interface. This doesn’t make many changes to stock Android other than adding light and dark menu options, shortcuts to apps you use frequently and some tweaks to app management. It’s largely free of bloatware though, with the only installed apps being the SwiftKey keyboard, a custom file manager, Google Office apps and a OnePlus Radio app.
Business Features
The Alert Slider is a clever extra for busy executives who don’t want to be interrupted by their phone in meetings -- or perhaps when entertaining clients at the opera. Move the switch to one of its three positions and the phone just gives a little buzz and displays a message on the screen to acknowledge the instruction.
The dual-SIM feature is useful if you want to have access to separate business and personal networks on the same handset. However, one of the SIM slots doubles as a microSD card slot; a neat design, but it means you can’t have more storage and two SIMs installed at the same time.
The Oxygen UI’s app management feature gives you the ability to control permissions for individual apps, something that’s standard in Android Marshmallow, but not in Lollipop. This helps prevent data leaks by keeping your information private, limiting what information and hardware features each app is allowed to access without preventing you from using its features.
The Oxygen skin also lets you assign shortcuts to the physical home, back and recent apps buttons. You can have up to two shortcuts on each one, useful for apps that you use on a regular basis. Google Office apps for Docs, Sheets and Slides are pre-installed allowing you to work when you’re out of the office and access your data stored in the cloud.
In Use
The OnePlus X is a good size for ease of one-handed use and is nicely weighted without being too heavy. It also looks and feels like a much more expensive piece of kit, using it back-to-back after the Nexus 5X there’s no doubt that in a blind test you’d say the OnePlus was a much costlier device.
The phone feels nice in your hand too and the machined edges make it easy to grip. It does lack some hardware options you’ll find on pricer models, a fingerprint scanner and NFC communication being the main missing features.
Having a standard USB port means you’re more likely to already have adaptors, car chargers, etc that will fit, but on the other hand you miss out on USB-C features like faster file transfers. The supplied plastic cover feels a bit tacky, but it does help protect the edges and back of the phone from knocks and scratches and helps you to grip the handset. A selection of other covers is available from the OnePlus website if you fancy something a bit more stylish.
The OnePlus X’s Snapdragon 801 processor spec is one you’d have seen in the priciest flagship phones just a year or so ago. But despite the fact that it isn’t the very latest in CPU technology it feels easily fast enough to cope with day-to-day tasks. It streams video smoothly, opens apps fast and never feels like it’s struggling.
The display is a real high point of this phone, you often get LCD screens at this price point but the OnePlus uses AMOLED. What this means on a technical level is that the individual pixels are illuminated rather than the screen being cross lit as with an LCD display. In practice this translates to a display that delivers bright, vibrant colors and superb contrast, which means deep blacks. This combined with the black of the handset really seems to have colors zinging out from the screen.
Combine this with 440ppi pixel density that delivers nice sharp text and images and you have what is probably one of the best displays of any phone in this price bracket. In fact the display here is rather better than that on the more expensive OnePlus 2.
The physical buttons below the screen on the other hand are very faint and there’s no illumination option so you may well find yourself sacrificing some screen space to the soft buttons for the sake of ease of use. The screen has an auto brightness setting, but it does seem to make things a little too bright indoors; you’ll probably end up finding a comfortable setting for most conditions and turning the automatic option off.
Of course you’ll want to use headphones for serious listening, but the speaker -- yes, speaker, although there are two grilles on the bottom of the phone there is only one -- on the OnePlus is actually pretty good, delivering a clear sound at everyday volume levels.
It begins to sound a bit harsh if you crank things up higher, but that’s carping as few phones offer hi-fi speaker quality. The OnePlus Radio app lets you receive FM stations, it uses the headphone cable as an antenna so you can’t listen via the speakers when using it.
The Oxygen interface doesn’t mess too much with the Android user experience. As standard it has a dark theme which nicely shows off the capabilities of the phone’s screen. Probably the most useful feature it offers is frequently used shortcuts which can be found by swiping right from the home screen.
This gets automatically populated with apps and contacts according to use, rather like the frequently visited sites on your Google home page, you can also take control yourself and add widgets here for specific apps making it a good aid to everyday use.
Oxygen does have some odd omissions too, there’s no Gallery app, for example, meaning you have to find your photos and videos via the Files app. Oxygen is quite tweakable, however, so you should have no problem customizing it to fit in with the way you want to work.

Out of the box the OnePlus X comes with a number of gesture controls enabled. You can draw an "O" to launch the camera app for example or slide two fingers down the screen to pause playback of music or videos. You can turn these gestures on and off according to taste.
The rear camera delivers okay results though there’s no image stabilization and the f2.2 lens is slower than the one on its OnePlus 2 brother. You simply tap on the screen to focus, this also brings up a little gear wheel icon which you can drag around to adjust the exposure.
In low light it automatically cranks up the ISO level, this delivers clear images -- without using flash on many occasions -- but at the expense of some graininess. You also get some extra shooting modes built in including HDR for balancing detail and shadow, and a Beauty mode for enhancing portraits.
There’s also something called Clear Image which creates a higher res picture by stitching 10 images together. This takes just a couple of seconds to do and although it sounds gimmicky it delivers surprisingly good results.

There’s no 4K on offer, but you can capture video at 720P or 1080P. The 8MP front camera is not brilliant, but is fine for selfies and video calls. You do get a selection of basic editing functions which allow you to carry out simple fixes like adjusting brightness and cropping images, as well as adding some effects. It’s never going to get keen photographers excited, but the OnePlus X camera delivers perfectly good everyday snapshots.
Conclusion
Although it only costs £199/$249, the OnePlus X pulls off the trick of looking and feeling like a much more expensive phone, a result of the glass back and nicely machined metal components. There are no plasticky budget overtones here and the quality of the screen adds to the overall good impression too.
That said it’s not perfect, having to sacrifice the dual-SIM capability for extra storage is a bit frustrating, and the lack of NFC means no using Android Pay or quickly swapping data with other handsets. Other more minor frustrations include the hard to see hardware buttons below the screen and the fact that the back quickly becomes covered in fingerprints making the phone look rather scruffy.
There’s no doubt that this is an impressive phone for the price and one that you won’t be ashamed to whip out in high-level meetings -- or for that matter in the pub. Whether you buy one really depends on how you’re going to use it.
Given that the OnePlus 2, which does come with a fingerprint scanner and has a better camera, but still no NFC, only costs £40 more you might want to weigh up which is the better option depending on which features really matter to you.
Pros
- Excellent screen
- Smart design
- Well made
Cons
- No NFC
- Faint hardware buttons
- Second SIM/SD card trade-off
ITProPortal Review: 7/10
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

New analytics solution helps retailers protect revenues
Publié: février 3, 2016, 3:01pm CET par Ian Barker

Accurately modeling consumer behavior and the events that drive and inhibit sales is a tricky problem for retailers.
Specialist in IT operation and security analytics Prelert, has turned its expertise on the problem and is launching a new Retail Order Analytics solution. It's aimed at helping online and multichannel retailers to identify technical and operational issues as they're happening in order to stem losses and protect revenue streams.
Built using unsupervised machine learning technology, Prelert's solution automates data analysis and detects the periodic nature of daily and weekly order cycles. It adapts to changing data patterns that may result over time due to factors like a new product becoming available or current events that cause a spike in product interest.
"A significant drop in the number of orders taken by an e-commerce site during a particular day might be obvious in retrospect, but can be very difficult to catch in near real time without automated machine learning. Static thresholds and even moving averages can’t reliably identify issues," says Mark Jaffe, CEO of Prelert. "Our anomaly detection algorithms have been proven to work and provide significant ROI within hundreds of progressive IT organizations around the globe. We can provide the same value now for retail and e-commerce organizations, with a solution tailored specifically for them".
Unlike other solutions which require data to be moved or batch uploaded, Prelert is designed to be easy to deploy, bringing analytics to where an organization's data already resides and analyzing it in near real time. In addition, an open API allows developers to use Prelert in their own products or environments.
For more information on Prelert's Retail Order Analytics you can visit the company's website.
Image credit: iQoncept/Shutterstock
-

How communication tools are being used in the workplace
Publié: février 3, 2016, 11:22am CET par Ian Barker

Interaction at work has been changed in recent years thanks to tools like Slack, but what do IT managers look for when sourcing communication tools?
According to the results of a new survey of 250 IT managers by West Unified Communications more than half believe that relying on best-of-breed communication and collaboration tools is more important than adopting solutions from the same vendor.
Other findings are that the adoption of video technology is on the rise. More than one-third of IT managers (36 percent) expect to implement or expand their video capabilities in the next three years, but cite it as one of the most difficult technologies for IT departments to maintain.
The top reason for delaying unified communication deployment, according to 52 percent of respondents, is not cost or budget, but that a technology isn't a ‘must have’ priority. The top technology is still audio conferencing, used by 79 percent, followed by web conferencing (76 percent) and instant messaging (73 percent).
More on the survey's findings is available on the westUC website and there's a summary in infographic form below.
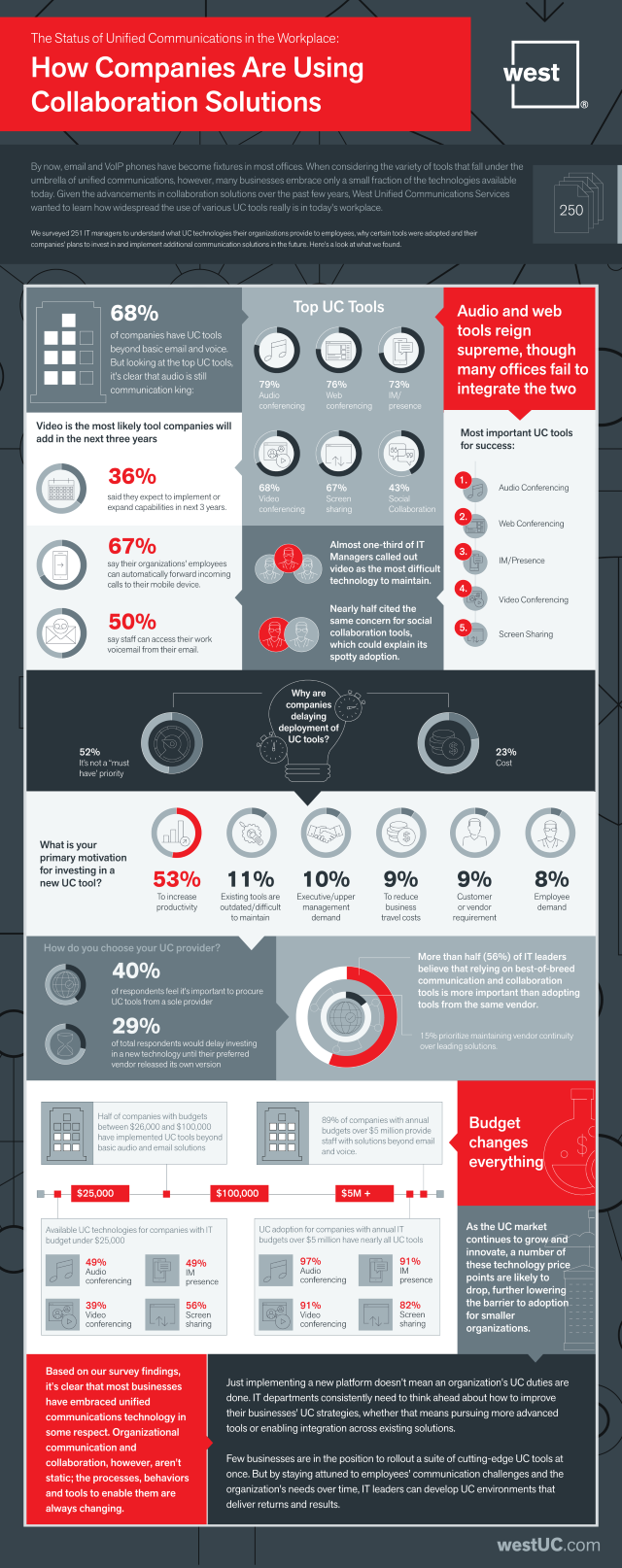
Photo credit: Everett Collection / Shutterstock
-

New cloud solution offers one-stop backup, archive and recovery
Publié: février 2, 2016, 5:31pm CET par Ian Barker

As businesses adopt the cloud for increased flexibility and reliability, public cloud services are increasingly being used as a protection platform to provide backup, archiving and disaster recovery.
Data protection specialist Druva has recognized the importance of this market and is adding disaster recovery capability to its Phoenix product to offer a converged cloud solution.
Druva Phoenix is built on Amazon Web Services and makes use of the public cloud’s elasticity, global presence and security, meaning companies can store, protect and manage large volumes of data simply, efficiently and effectively.
"Companies have been forced to juggle multiple hardware and software resources -- including on-site tape, secondary disk hardware and backup software -- to manage, protect and secure data. This has created organizational silos and significant expense. Phoenix has been designed as a one-stop-shop for on-demand, infrastructure data protection services," says Jaspreet Singh, CEO, Druva. "By adding DR to Phoenix's existing public cloud backup and archival capabilities, these silos are eliminated saving enterprises money and resources".
Phoenix's new DR capability allows organizations to continuously back up their VMware environments. They can automatically recover and spin-up their virtual machines in the AWS public cloud when disaster strikes, ensuring business continuity. It helps save on costs too by eliminating the need for additional dedicated on premise software, storage or hardware. Thanks to advanced configuration settings, Phoenix users can set up detailed polices to automate network and security failover to a DR environment, significantly reducing downtime. In addition, administrators can create multiple copies of virtual machines across geographies and accounts for test and development.
More details on the latest capabilities in Phoenix are available on the Druva website.
Photo Credit: Andreas Weitzmann/Shutterstock
-

New cloud service helps organizations meet document preservation requirements
Publié: février 2, 2016, 3:27pm CET par Ian Barker

Companies increasingly face demands to keep documents in order to satisfy legal and compliance requirements. This can present problems in deciding what to keep but also in keeping up with the latest regulations.
The latest EU/US Data Transfer negotiations for example are causing businesses to re-think their current business processes and data governance strategy in order to address these changes.
Compliance and archiving specialist Actiance is launching a new version of its Alcatraz product offering on-demand preservation capabilities so that organizations can hold, capture, search, and review content across more than 70 communications channels.
This allows legal departments to effectively manage eDiscovery requirements, while mitigating risks that may arise during the critical collection and preservation steps, as well as complying with new Federal Rules of Civil Procedure (FRCP) regulations.
"The standards for legal preservation have become better defined, posing greater challenges for customers who face frequent, unpredictable legal discovery," says Kailash Ambwani, president and CEO, Actiance. "Actiance's On-Demand Preservation capabilities provide a gold standard in proving that a firm has taken the reasonable steps required by the Federal rules to collect and preserve all information that may be relevant for litigation".
The software uses a modern, tamper-proof data store so that legal teams can upload content from communication and social channels to automatically place under legal hold when required for eDiscovery. Electronically stored information is then immediately available for legal teams to conduct searches, filter unneeded content, and export data for review. With built-in, easy-to-use eDiscovery features, legal teams are able to manage collection and preservation tasks without relying on IT staff.
Alcatraz and its enhanced features will be showcased at LegalTech in New York this week and you can find out more on the Actiance website.
Image Credit: Constantine Pankin / Shutterstock
-

New risk management software helps companies handle sensitive data
Publié: février 2, 2016, 12:35pm CET par Ian Barker

Endpoint security and digital investigations specialist Guidance Software is launching a new solution to help organizations identify and classify confidential data.
EnForce Risk Manager allows organizations to reduce their surface area of risk, limiting the potential damage from breaches and improving their ability to comply with global data protection rules.
The software allows enterprises to identify the most commonly compromised data anywhere it's stored, including file shares, email sources, servers, databases and all types of endpoints. They can then categorize that data for review and validation, and automatically address issues through digital removal and other control actions.
"The amount of data stored on electronic systems today is growing at an exponential rate. And as we've learned from high-profile breaches that compromised sensitive information, including health records and credit card information, the ability to mitigate risk remains challenging," says Ken Basore, senior vice president of product engineering, Guidance Software. "In conversations with our customers, the need to combine data management, e-discovery, privacy and security, as well as policies, into proactive, corporate-wide information governance has repeatedly arisen. With EnForce, Guidance Software is committed to reducing business risks, decreasing storage and information technology costs, and providing greater peace of mind to our customers".
EnForce Risk Manager better equips organizations to comply with external data privacy regulations and polices such as HIPAA (Health Insurance Portability and Accountability Act) and PCI DSS (Payment Card Industry Data Security Standard), as well as with internal policies.
By identifying and systematically deleting data that is old, no longer needed or has no current business value, organizations can also reduce current and future storage costs. Removing old data will leave businesses with higher quality information to help them make more accurate and better informed business decisions.
Guidance Software will be previewing EnForce Risk Manager at LegalTech, from February 2-4, in New York. The product will be generally available later this year, for more information visit the company's website.
Photo credit: Olivier Le Moal / Shutterstock
-

Lenovo ThinkPad 10: A viable laptop substitute [Review]
Publié: février 1, 2016, 8:10pm CET par Ian Barker

The majority of tablets are aimed at consumers and, therefore, business features can sometimes feel a little tacked on. Some manufacturers take a different approach, however, and there is little doubt that latest second generation of ThinkPad 10 from Lenovo is not aimed squarely at business users.
It runs 64-bit Windows 10, has Trusted Platform Module encryption and other features and options that will make it an attractive corporate choice. Add in the fact that it is solidly built and has lots of accessories available to improve its usefulness as a business tool and it looks even more impressive, and even more similar to the Microsoft Surface. So, is this a better option for serious tablet users than a device based around a mobile OS, like Android?
In the Box
The ThinkPad 10 comes in both 2GB and 4GB memory versions, and both are powered by the quad-core Intel Atom x7-Z8700 Processor with 2MB of cache and integrated HD graphics.
The 2GB versions come with 64GB of on-board storage while 4GB models have 128GB; in either case you can extend this by adding a microSD card. The 4GB versions are available with or without mobile web access, although it is only 3G; if you do opt for the mobile version you also get Windows 10 Pro installed as opposed to the Windows 10 Home version on the other models.
The front camera is 1.5MP and the rear is 5MP and it comes with auto-focus and flash; it is capable of recording 1080p video too. The tablet has a 10.1 inch multi-touch Gorilla Glass screen with 1920 x 1200 resolution. Connectivity is via 802.11 a/c Wi-Fi, Bluetooth 4.0, and, in the top versions, 3G mobile.
There is a built in Swipe fingerprint reader on all versions. Optional extras on offer include a built-in SmartCard reader, NFC, and the ThinkPad Pen Pro with WRITEit allowing you to use stylus input.
As standard you do not get a lot in the box other than the tablet itself and a mains charger. This does not have a standard USB connection but uses a proprietary plug so you will need to make sure you have the charger with you if you are out and about and likely to run short of juice. Talking of which the battery should be able to deliver up to 10 hours of life on a full charge.

As to the design of the tablet itself, there is a power switch on the top edge, on the right are volume controls, microSD and SIM card slots plus ports for HDMI, USB 3.0, headphones and power. On the left-hand side is a Kensington lock slot, and on the bottom edge are the connectors for a case/keyboard or docking station. The fingerprint sensor is on the back and is positioned so that it falls neatly under your right forefinger when you are holding the device in landscape format.
Business Features
The ThinkPad will attract business users for a number of reasons. Most obviously because it runs the familiar Windows platform, so compatibility with MS Office documents is assured and users can easily sync system settings via their Windows ID.
Trusted Platform Module encryption ensures that your data stays secure and for those wanting even more protection there is the option of a smart card reader to augment the standard fingerprint scanner. Other attractive add-ons for business users include the Folio Keyboard, which is a keyboard, touchpad and case combined, allowing you to use the device like a conventional laptop.
There is also the option of the Pen Pro stylus, plus a desktop dock that offers keyboard, mouse, USB, HDMI and audio ports as well as an Ethernet connector so you can use the machine in the office. The Pen Pro comes with a holder to keep it safe but this attaches to the USB port thus denying you access to it for other purposes. You can see from this collection that Lenovo is serious about cracking the business market -- though of course all of these things ramp up the cost of the device.

There are a couple of useful pre-installed apps too. REACHit allows you to search for files across all of your devices and cloud storage from a single screen, and SHAREit which is a cross-platform file transfer tool.
Order direct from the Lenovo website and you can mix and match the options you want, and add software, upgrading from Windows 10 Home to Windows 10 Pro, for example, or adding Office. The problem is that once you have built it up you could have bought a decent laptop for the same money.
In Use
The back of the ThinkPad has a smooth matt finish which feels nice to the touch, though it does tend to show marks and fingerprints. It has a red power LED that forms the dot over the "i" in the ThinkPad logo, which is a pleasing design feature. There is also a subtle red highlight around the rear camera lens.
The back does look a bit busy though, with copyright information and an Intel Inside and Lenovo logos printed on it, plus the fingerprint scanner, NFC touchpoint and speaker recesses. There is a slight design quirk in that the top corners are rounded, while the bottom ones are square; this, presumably, is to aid docking, attaching keyboards, etc, but it does make the tablet look a little odd, as though it is part of something else.
It may not be the best looking tablet in the world then, but there is no doubt that it feels rugged and is likely to survive the day-to-day rigors of corporate life. Lenovo’s website makes much of its premium construction, stress testing and reliability. The buttons for power and volume are plastic, but they do not feel cheap.
The ThinkPad is a relatively heavy beast compared to, say, a Galaxy Tab. It weighs almost 600 grammes (1 pound 5 ounces in old money) and you would not want to hold it one-handed for long. It also gets quite warm in operation at around the bottom right corner, particularly when it is charging, and this is just the spot at which you hold it.

The tablet boots up and shuts down very quickly and it copes well with most everyday tasks, including music and video streaming, without breaking a sweat. It also switches between open apps with minimal lag. The ThinkPad 10 copes well with legacy Windows programs too, which can sometimes be rendered uncomfortably small on tablet screens. When you turn it from landscape to portrait, however, there is always a slight delay before the screen decides to reorient itself.
It has a wide black bezel around the screen, which makes the tablet feel rather larger than it needs to be, but you quickly get used to this and, on the flip side, it does make it easy to hold without accidentally triggering functions. The Windows logo below the screen is not there just for show; it also acts as a Windows Start button, which is a neat touch.
You get the advantage of a full-sized USB 3.0 connector; however, it is hidden under a little rubber cover which is quite fiddly to open and is not tethered to the chassis, so you will no doubt end up losing it. If you have an NFC enabled version, the touch point is just below the camera and is marked with a small label for ease of location.
The screen itself is one of the ThinkPad’s most impressive features; it is bright and responds well and accurately to touch inputs. It delivers smooth video playback too and if you are apt to play Candy Crush under the table during boring meetings it will not disappoint there either. The resolution is good and the size feels just about right, making use of the on-screen keyboard comfortable with minimal risk of mistyping.
The speakers are on the back, down towards the bottom edge, which makes them easy to cover with your hand when you are holding the device. Sound quality is okay, though it is not room-filling, but it has enough bass response to allow you to feel a slight vibration through your fingers.

Although it is only 5 megapixel, the ThinkPad’s rear camera captures pictures that are sharp and bright with good levels of detail and accurate colors. It is at least as good as most tablet cameras, though it does not compare to those found on the latest smartphones. Things can be a bit grainy in low light if you opt not to use use the flash, and this is even more pronounced on the rear camera, but it is good enough for video calling.
It comes with some Lenovo programs pre-installed, including Companion, Lenovo ID, and the REACHit and SHAREit apps mentioned above. There is also a trial of McAfee LiveSafe installed, but otherwise the ThinkPad is commendably free of bloatware. You can opt for various software packages when ordering, including Office -- or an Office 365 subscription -- Photoshop Elements and various security options.
One of the attractions of the ThinkPad is that it allows you to operate in the familiar home comfort of Windows, but that is also a source of some of its frustrations. The on-screen keyboard, for example, has big buttons, but to access numbers you either need to switch to numeric mode or use a less than intuitive press and hold technique.
Also, when you press on an input field the keyboard does not automatically appear as it does on Android, you have to start it manually. The Camera app too feels rather underdeveloped compared to those on other platforms. You can address some of these issues with a visit to the Windows Store, but even so there is not the choice of alternatives that you get on iOS or Android.
There is a wide selection of accessories available for the ThinkPad, mostly aimed at business use as we noted above. For more general users -- particularly those who use the camera a lot -- there is a Quickshot cover that has a neat fold-down corner, which exposes the camera lens and launches the camera app. It also has a magnetic closure that automatically puts the tablet into sleep mode when closed and wakes it again when opened.
Conclusion
As a tablet in its own right the ThinkPad 10 has a lot to like, but is let down by one or two minor niggles; but, to be fair, some of those are down to Windows rather than the device itself. It is an attractive business proposition though, thanks to the compatibility of its Windows OS, its security features and the availability of accessories that allow you to effectively bridge the laptop/tablet gap.
The 2GB version costs £459.99, while the top of the range 4GB smart card version is £709.99. This makes the Lenovo look a bit pricey against Android tablets, especially of you start adding keyboards and styluses, but then it is not really a direct competitor. It is a machine that is more likely to be bought by companies to equip their employees, rather than by BYOD or personal users.
Looked at in that light, the ThinkPad 10 is a robust device that offers an alternative to the Microsoft Surface. It lacks the Surface Pro 4’s faster Core CPU, but otherwise offers a similar spec at a slightly lower price point, though with either machine you will pay extra if you want to add a keyboard. Even so, if you are looking for a tablet that can serve as a viable laptop substitute, the ThinkPad 10 is worth adding to your shortlist.
That said, there are plenty of alternatives in the form of laptops that use 360 degree hinges or detachable screens to give similar functionality, plus, up at the top of the ThinkPad’s price range, you are getting close to the Surface Pro 4 with its larger screen and faster Core CPU.
Pros
- Security features
- Build quality
- Impressive screen
Cons
- Heavy
- Pricey
- Limited app choice
8/10
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Threat of cyber crime drives higher salaries for security professionals
Publié: janvier 29, 2016, 4:18pm CET par Ian Barker

Employers are offering salaries up by 14 percent on average for IT security specialists in the light of the growing threat posed by cyber crime.
A Global Salary Survey by UK specialist recruitment company Robert Walters also sees salaries for developers increasing as major employers look to overhaul their online presence.
Developer salaries are set to grow nine percent this year as against five percent for the industry as a whole, thanks to digital transformation projects in large companies, many of them driven by a new emphasis on data security.
It's security roles that see the biggest increases though with heads of cyber security and security analyst roles seeing 18 percent increases. Even junior security support positions are set to have seven percent growth.
"Over the last year we've seen a massive increase in both permanent and interim cyber security roles due largely to the ongoing threat around IT and cyber crime. The challenges facing companies continue to grow in volume and complexity as cyber security threats constantly evolve," says Steve Corbett, Associate Director, IT recruitment at Robert Walters. "The impact of high profile IT security breaches involving attacks on major companies has served to bring this emerging threat into the public eye, increasing pressure from regulators and legislators on companies to have a dedicated cyber security representative and to meet specific standards of security".
More detail on the survey results is available to download from the Robert Walters website.
Photo credit: beeboys / Shutterstock
-

How technology is ruining your mind
Publié: janvier 29, 2016, 11:48am CET par Ian Barker

Do you find that you don't remember facts any more because you know you can easily look them up online? Or does using phones and gadgets late at night make it harder for you to sleep?
According to an infographic from London-based support specialist Conosco these are just some of the ways in which technology is harmful to our minds.
Everyday mobile phone use for example can lead to stress, depression and anxiety, and holding the handset close to your ear increases activity in the brain region nearest the antenna. Use of tech by children leads to a shorter attention span and socializing via online media affects the way they form relationships in the real world.
Carrying out tasks online affects learning because information is no longer delivered in a linear way. Information overload is damaging our capacity for reflection and it also discourages deliberation, so that we're likely to make decisions faster, and make mistakes in the process.
Technology can also create dangerous distractions. Satellite navigation for example can make drivers less able to concentrate on what's going on around them.
The full infographic is below. If your attention span is sufficient to let you read to the end, let us know how technology has affected your life. Now, what was I doing...?
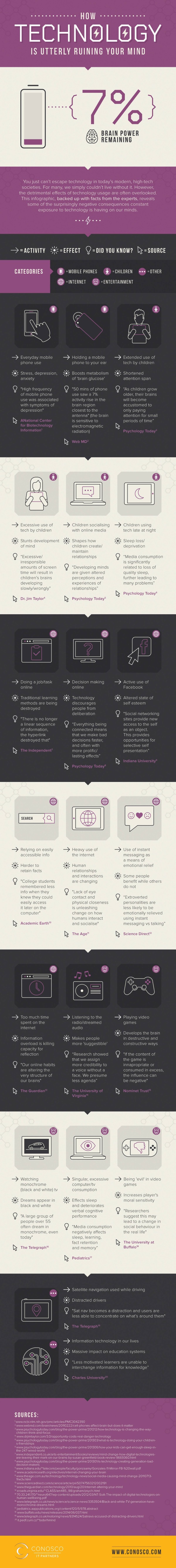
Photo Credit: CREATISTA/Shutterstock
-

Intel aims to make life easier for small businesses
Publié: janvier 29, 2016, 10:57am CET par Ian Barker
Small businesses make up around 17 percent of the total PC market, yet often they don’t have dedicated resources to manage their systems.
Chip maker Intel has spotted an opportunity here and is launching its Small Business Advantage program, offering a blend of systems management and business collaboration.
SBA automates PC maintenance tasks to keep systems up to date with minimal interruption. It also enhances security by monitoring software for compromise and offering a USB blocker to help keep out viruses and stop unauthorized file transfers.
It helps staff work together too with built-in chat, file sharing and screen sharing for instant collaboration. This offers a more secure solution than using consumer tools. There's an optional Companion App -- supported on Windows, Android, and iOS platforms -- which keeps mobile users connected when they are on-the-go.
"Small businesses are very focussed on their own business, not on the latest technology and they're not buying PCs all the time. We tried to build something that was very easy to use and that integrated all of the tools they need," says Chad Constant Director of Business Client Marketing at Intel. "If they buy a PC that's SBA capable from one of our OEM partners they get this solution which can then be downloaded to other machines in the business".
SBA runs on Core i3 and above systems. It can also be added to a network in the form of a headless appliance that can relay traffic across the internet, allowing mobile users to access their work data, and will be able to deliver future small business capabilities.
SBA is available though Intel's OEM channel partners with no ongoing cost once installed. You can find out more on the Intel site.
-

Enterprises want to run databases in containers
Publié: janvier 28, 2016, 3:54pm CET par Ian Barker

More than three out of four IT decision makers are interested in running stateful applications like databases within containers, according to a recent survey.
Silicon Valley-based containerized data platform specialist Robin Systems conducted the survey in December 2015 with more than 200 respondents from industries including retail, banking and finance, manufacturing, and Internet infrastructure.
The results show that 81 percent of respondents expect their companies to increase investment in container-based technology. Workload consolidation and lower performance overhead, as compared to traditional virtualization, are the key motivation for 78.5 percent of those who expressed interest in running databases within containers. Performance was cited by more than half (53 percent) of respondents.
Among other findings are that enterprise container adoption continues to grow, with 35 percent of respondents already using containers in production while 26 percent are experimenting with them. A majority of respondents reported deploying both stateful and stateless applications within their containers.
Containers are emerging as the preferred platform for running databases too, with approximately half of respondents doing so. About 40 percent of respondents say they have deployed big data applications such as Hadoop and Spark within containers.
Docker is being adopted quickly, but LXC and LXD remain as the preferred containerization technology for data-centric applications, with 60 percent citing their use. AWS EBS is the most popular storage backend for containers at 30 percent, reflecting widespread container adoption for cloud-native applications.
When it comes to on premise storage infrastructure, respondents were essentially split between Storage Area Network (SAN) and Direct Attached Storage (DAS), both of which are used by about 20 percent of respondents.
"Containers are a natural platform for running performance sensitive applications such as databases, as they enable consolidation without compromising performance or predictability", says Partha Seetala, chief technology officer at Robin. "This aligns perfectly with our vision of providing enterprises a high-performance and elastic containerized platform for stateful and mission-critical applications".
More information on database containerization is available on the Robin Systems website.
Image Credit: wavebreakmedia / Shutterstock
-

New SharePoint intranet platform helps Office 365 users collaborate
Publié: janvier 28, 2016, 3:07pm CET par Ian Barker

Intranets are increasingly common, even in smaller companies, allowing employees easy access to shared resources
For Office 365 users wanting to exploit the power of intranets, Florida based MessageOps is launching ROOT, a SharePoint intranet platform. ROOT is a feature-rich intranet portal that gives customers an opportunity to create a more collaborative working environment, and give their employees a central access point to important company information and apps.
"We designed this portal to make it easier for businesses to unify messaging and access the tools they need to be more productive," says Chris Pyle President and CEO of Champion Solutions Group and MessageOps. "The platform modernizes the workplace and allows companies to think with one mind and speak with one voice regarding corporate and departmental goals, marketing, and social messaging. All these capabilities not only drive results, but also employee satisfaction".
ROOT boosts productivity by enabling employees to obtain the tools they need to perform their daily tasks, such as a sophisticated search feature (by people, department or skillset), access to company goals and objectives, corporate events calendar, and departmental requests. The departmental request widget improves transparency and streamlines workflows by tracking the status of requests and enabling managers of the department to see open, in progress, and closed requests by category and person.
It also includes a recognition feed for shout-outs, employee anniversaries, and birthdays to drive loyalty and engagement. There are widgets for social networking (LinkedIn, Twitter, Facebook), blogs, weather, tip of the day, application feeds, and more.
ROOT is scalable across any sized enterprise, works across different devices and can be up and running quickly. You can find out more and take a tour of the product on the MessageOps website.
Image Credit: Tischenko Irina / Shutterstock
-

Canonical and Oracle team up to boost enterprise cloud use
Publié: janvier 28, 2016, 12:05pm CET par Ian Barker

Canonical, the company behind Ubuntu Linux, has announced a collaboration with Oracle to make Ubuntu images available on Oracle Cloud.
Under the deal, Certified Ubuntu images will be available on the Oracle Cloud Marketplace, providing Oracle enterprise customers with increased choice and new and innovative ways to manage and scale their enterprise workloads, using the number one cloud operating system.
Certified Ubuntu images are continually maintained and tested by Canonical and the latest versions are made available on the Oracle Cloud Marketplace within minutes of their official release.
Udi Nachmany, head of Certified Public Cloud at Canonical says, "Aside from the obvious cost savings inherent in open source cloud development, one of the key benefits of using official Ubuntu images is that customers use the same operating system at scale in production as in development, at no additional cost -- which dramatically simplifies cross-substrate management, migration and re-engineering. Organizations may want to deploy their servers on-premises, develop their own private cloud in-house, or use the Oracle Cloud. Ubuntu offers this flexibility".
For enterprise cloud customers Ubuntu brings the benefit of regular updates to ensure they're running the latest features, compliance accreditations and security updates. There are archive mirrors for faster retrieval of updates and access to Canonical for support.
"This relationship signifies our strategy to broaden the range of options for enterprise customers, giving them more choice and flexibility when choosing cloud technologies," says Sanjay Sinha, vice president, Platform Products at Oracle. "We recognise there is a growing demand for innovative new cloud solutions and we are excited to have Canonical offer certified Ubuntu images in the Oracle Cloud Marketplace".
Canonical is a Gold level member of Oracle PartnerNetwork and Ubuntu is available now on the Oracle Cloud Marketplace.
-

Phishing attacks grow in volume and complexity
Publié: janvier 27, 2016, 4:00pm CET par Ian Barker

According to a new report from security awareness specialist Wombat Security phishing attacks are on the rise and are supported by increasingly aggressive social engineering practices that make them more difficult to prevent.
Organizations surveyed indicated they have suffered malware infections (42 percent), compromised accounts (22 percent), and loss of data (4 percent) as a direct result of successful phishing attacks.
"Phishing continues to be a highly effective attack vector that is increasingly responsible for a significant percentage of data breaches in the market today," says Trevor Hawthorn, CTO of Wombat. "In spite of continued investments in a number of popular security technologies, phishing messages continue to reach end users and can result in serious damages to a company’s critical data and reputation. Our methods have shown that a Continuous Training Methodology which educates end users on cybersecurity threats changes employee behavior and reduces risk within an organization".
The survey reveals that the most popular phishing attack templates with the highest click rates include items employees expected to see in their work email such as an HR document, or a shipping confirmation. For example, the survey found that employees were more cautious when receiving 'consumer' emails on topics like gift card notifications, or social networking accounts. However, an 'urgent email password change request' had a 28 percent average click rate.
Other findings show that spear phishers often go to great lengths to gather information on key people within an organization. Emails personalized with a first name had click rates 19 percent higher than those with no personalization. Click rates also vary between industries. Telecommunications and professional services workers click phishing emails more than those in other industries.
To find out more you can download the full 2016 State of the Phish report from the Wombat Security site.
Image Credit: Maksim Kabakou / Shutterstock
-

One in three Americans are victims of healthcare data breaches
Publié: janvier 27, 2016, 2:59pm CET par Ian Barker

In the last year there have been a number of data breaches involving the healthcare industry. These included high profile attacks such as those on Premera Blue Cross and Anthem compromising millions of records.
According to the 2016 Healthcare Breach Report from cloud access specialist Bitglass more than 111 million individuals' data was lost due to hacking or IT incidents in the US alone.
According to the findings 98 percent of record leaks were due to large-scale breaches targeting the healthcare industry. These high-profile attacks were the largest source of healthcare data loss and indicate that cyber attackers are increasingly targeting medical data.
"The 80 percent increase in data breach hacks in 2015 makes it clear that hackers are targeting healthcare with large-scale attacks affecting one in three Americans," said Nat Kausik, CEO, Bitglass. "As the IoT revolution compounds the problem with real-time patient data, healthcare organizations must embrace innovative data security technologies to meet security and compliance requirements".
The reason for the surge in attacks is that protected health information (PHI) -- which includes sensitive information such as social security numbers, medical record data, and date of birth -- has a high value on the black market.
When credit card breaches occur, issuers can simply terminate all transactions and individuals benefit from laws that limit their liability. However, victims have little recourse when subjected to identity theft via PHI leaks, and many are not promptly informed by providers that their data has been compromised. While criminals often make use of healthcare data for the purposes of identity theft, they can also leverage it to access medical care in the victim's name or to conduct corporate extortion.
More information can be found in the full report which is available to download from the Bitglass website.
Image Credit: Rob Hyron / Shutterstock
-

Continuous security helps protect consumer data
Publié: janvier 27, 2016, 1:03pm CET par Ian Barker

As individuals, the amount of personal data we have online has grown thanks to social networking and the number of organizations that encourage us to do business via the internet.
It's set to grow still more as the Internet of Things takes off, and this presents problems when it comes to sharing information. Conventional solutions rely on checkboxes or cookies, but these struggle to cope with current demands.
Access management specialist ForgeRock is launching its new Identity Management Platform, which includes the industry's first use of continuous security and consumer-facing privacy protection to guard data.
"In an era of very public data breaches and heightened consumer awareness, 'fostering trusted digital relationships' can't be considered a buzz phrase. Privacy strategy must include a consent-to-share strategy that looks after the top line of the business," says Mike Ellis, CEO of ForgeRock. "The UMA (User Managed Access) standard was created to give an individual a unified control point for authorizing who and what can get access to their digital data, content and services, no matter where all those things live. The new ForgeRock Identity Platform enables private and public organizations to quickly deploy secure identity services based on UMA principles".
The platform uses 'continuous security' which enables organizations to apply contextual identity, adaptive risk and multi-factor authentication at the time a user authenticates as well as at any point during a digital session. This ensures the authenticity of users, devices, things and services at all times and cuts the risk whenever an anomaly is detected.
By employing the UMA standard it makes it possible for organizations to comply with shifting privacy regulations and establish trusted digital relationships. The new software capabilities make it easy for businesses to comply with data privacy regulations, such as Safe Harbor and the forthcoming EU General Data Protection Regulation (GDPR).
More information on the platform is available on the ForgeRock website.
Photo Credit: Pavel Ignatov/Shutterstock
-

Free tool launches to evaluate privileged password management
Publié: janvier 26, 2016, 4:56pm CET par Ian Barker

It's easy to set rules for handling privileged account passwords, but harder to ensure that they're being followed and that they meet best practice and security guidelines.
IT security specialist Thycotic is aiming to help organizations by launching a free online tool that demonstrates how companies compare to other, similarly-sized, organizations when meeting password management practices.
Privileged accounts have become valuable tools for hackers. In a study conducted in conjunction with the 2015 Black Hat Conference, 75 percent of attendees surveyed revealed that privileged accounts are easier to compromise today than they were two years ago. These accounts, used by system administrators, third-party and cloud service providers, along with application and business users, exist in nearly every connected device, server, hypervisor, operating system, database, application and industrial control system in operation today. Therefore, businesses of all sizes need to take their privileged account management (PAM) seriously.
"Many IT executives and security professionals have documented and trained their employees on how to protect personal passwords. However, in spite of the even higher vulnerability of privileged account passwords, not all IT professionals have knowledge of privileged account best practices," says Thycotic Founder and CTO Jonathan Cogley. "Furthermore, organizations that understand privileged account best practices often have no idea if those practices are being followed or if their current practices enable them to restore normal business operations within SLAs should a breach occur. Additionally, they have no understanding of how their practices compare to companies in their peer group".
The tool can be accessed on the Thycotic website and provides users with an immediate grade (from A to F) based on how well their privileged password security practices match up against PAM best practices. Participants are able to quickly understand how and where to focus their time, money and resources in order to improve privileged account defenses.
Photo credit: Ai825 / Shutterstock
-

Under half of executives are confident in their organization's data quality
Publié: janvier 26, 2016, 3:50pm CET par Ian Barker

According to new research from data intelligence specialist Blazent there's a major disconnect between executive attitudes to data quality and the effect that bad data can have on the business.
Based on a study by 451 Research of 200 C-level and senior IT leaders, the report reveals that fewer than half (40 percent) of C-level executives and data scientists are 'very confident' in their organization's data quality. Yet a majority (94 percent) recognize the impact poor data quality has on business outcomes.
Areas that can be affected by poor quality data include lost revenue (42 percent) and bad decision-making (39 percent). When asked about the root causes for poor data quality, nearly half (47 percent) of respondents cited data migration as a leading cause.
In large enterprises it's IT which still bears the burden of keeping data clean (79 percent) despite the introduction of data scientists (26 percent). In cases where costly data scientists are involved, one-third report spending up to 90 percent of their time on cleaning up raw data. In addition, the challenge of maintaining data quality is exacerbated by conventional methods used to ensure data quality. 41 percent rely on applications to validate data, 38 percent manually cleanse data and a worrying 10 percent either don't know what they're doing or employ a 'hope for the best' approach.
"After listening to customers for over 15 years, we've developed an acute understanding of the pain and loss poor quality data can have on a business," says Gary Oliver, CEO at Blazent. "While data scientists became one of the most coveted roles in IT this past year, the reality is that CIOs and IT leaders still carry the burden of maintaining the proper checks and balances for data quality, and it will be incumbent on them to solve this unwieldy problem as data volumes continue to escalate".
Despite the problems maintaining quality, the importance of good data is widely recognized. 81 percent of respondents say they use data analytics to uncover new revenue opportunities, and it's perceived as having a direct impact on increased revenues (51 percent) and lower costs (49 percent). The amount of data is growing too, with 95 percent expecting data sources and volumes to triple in the next 12 months.
More information on the findings can be found on the Blazent website.
Image Credit: alphaspirit / Shutterstock
-

HotLink launches disaster recovery as a service
Publié: janvier 26, 2016, 3:04pm CET par Ian Barker

With more and more systems moving to cloud delivery models it's not surprising that disaster recovery services should follow suit.
California-based HotLink is joining the trend with the launch of its new HotLink Managed DRaaS (Disaster Recovery as a Service) using Amazon Web Services (AWS) to provide VMware data protection and cost-effective business resiliency.
Recent research from the Disaster Recovery Preparedness Council shows that 73 percent of companies are failing in terms of disaster readiness, and that 58 percent rarely or never test their DR plans because it's too difficult and expensive. HotLink's new Managed DRaaS is designed to provide IT organizations with the technology, skilled resources, cloud knowledge, hybrid IT experience, methodology and continuous service delivery needed to ensure their environments are protected -- whether the disruption is a security breach, networking failure, software issue, human error or other unexpected condition.
"HotLink Managed DRaaS provides an affordable and accessible insurance policy that ensures customers' environments can be seamlessly restored and readily managed in the event of a failure, using IT's existing VMware management tools and methodologies. This is a first in the industry," says Lynn LeBlanc, CEO of HotLink. "Companies want a 'set it and forget it' solution for DR/BC (Disaster Recovery/Business Continuity), and that's exactly what our new service provides. Most importantly, the new HotLink Managed DRaaS solution is dramatically more affordable than other fully-managed DR/BC options because HotLink leverages the public cloud economics of AWS as the DR/BC infrastructure".
Product features include continuous monitoring and testing to ensure systematic validation of the DR/BC site. This includes the status of all protected workloads by restore point so that recovery plans are deployed as expected and are fully functional.
It delivers easy-to-understand reporting on the entire DR/BC site status, as well as notification of any irregularities that need customer attention. Protected workloads, file servers and database servers can all be recovered from AWS within minutes of a failure.
A unified management platform extends customers' existing VMware infrastructure to the AWS DR/BC site in the event of a failure. It also allows recovery plans to be built using VMware vCenter-compatible tools.
Customers can select the optimal service level to meet their business needs and budgetary requirements. Options are available spanning weekly, daily and 24/7 service level delivery.
For more information and pricing you can visit the HotLink website.
Photo Credit: Olivier Le Moal/Shutterstock
-

Turkey becomes top target for DDoS attacks
Publié: janvier 26, 2016, 12:26pm CET par Ian Barker

The final quarter of last year saw Turkey suffer an onslaught of denial of service attacks, the number growing ten-fold to more than 30,000 events per day, according to security company Nexusguard.
The company's Q4 2015 Threat Report shows that 81 percent of the top 10 attack destinations were Turkish-based IP addresses. It's thought that the spike in attacks could be related to rising tensions between Russia and Turkey.
Observed attacks against Turkey started on November 13 and peaked on December 27. The widespread shutdown for IPs in Turkey contributed to a large spike in domain name system (DNS) attacks measured between September 30 and December 31, 2015. Of the 216,102 attacks measured, more than 69 percent were DNS attacks, overtaking other reflection methods like network time protocol (NTP) and CHARGEN vulnerabilities. DNS amplification attacks can overload IP addresses with requests, resulting in outages for the target. Nexusguard’s research shows that countrywide attacks could result in collateral damage to other customers or even whole municipalities that may share domains with the victims.
"As warfare among countries and other opposing organizations blurs the lines between physical and cyber security, companies with online presences can be caught in the crosshairs," says Bill Barry, executive vice president of global strategy at Nexusguard. "With DDoS attacks escalating and diversifying in 2016, we’re finding that websites can be affected by geopolitical events even if they're not part of the feud. Businesses must have continuity plans in place with a mitigation approach to plan for this type of collateral damage".
More information on the latest DDoS trends is available on the Nexusguard website.
Photo Credit: Fabio Berti/Shutterstock
-

IBM adds hybrid cloud capability to LinuxONE
Publié: janvier 26, 2016, 10:57am CET par Ian Barker

Back in August last year we reported on IBM's bid to take a slice of the enterprise Linux market with the launch of a range of dedicated mainframes.
Today the company is announcing an expansion of its Linux ecosystem along with new hybrid cloud capabilities to allow organizations to develop, deploy and manage applications for the cloud more easily and with robust security.
IBM is optimizing its Cloudant NoSQL database and StrongLoop API development technologies into LinuxONE to enable clients to develop, deploy and manage applications for the cloud quickly and easily. The new features don't require developers to convert languages, improving time taken for development and deployment.
In addition Big Blue is expanding its supported software and capabilities for LinuxONE. It recently ported the Google developed Go programming language, designed for building simple, reliable and efficient software. IBM will begin contributing code to the Go community in the summer.
It's also been working with SUSE to collaborate on technologies in the OpenStack space. SUSE tools will be employed to manage public, private and hybrid clouds running on LinuxONE. In addition, IBM has proved that its LinuxONE Emperor system is capable of supporting up to one million Docker containers -- enabling businesses to unlock insights from massive volumes of data generated by the Internet of Things.
Canonical is offering its Ubuntu Linux distribution and cloud tool sets to LinuxONE clients too. In coming months this will enable them to take advantage of LXD, a hypervisor designed for Docker and full system containers. With the addition of Ubuntu to the existing SUSE and Red Hat distributions, enterprises now have a third option for acquiring the LinuxONE system.
"IBM is strengthening its expansion into the open community, providing developers more choice and flexibility with LinuxONE," says Ross Mauri, general manager, IBM z Systems and LinuxONE. "The platform's broadened ecosystem and new hybrid cloud capabilities underscore the security, efficiency and performance that clients need, while delivering the flexibility and possibilities of open source they love".
More information on the IBM LinuxONE portfolio of products is available on the company's website.
-

Inateck BR1002 Bluetooth transmitter/receiver [Review]
Publié: janvier 25, 2016, 4:46pm CET par Ian Barker

We live in a world where we increasingly expect everything to interface with everything else. New cars come with Bluetooth and wireless connections for example to access information from your phone, and audio systems are able to stream music around your home.
But what if you have an older car, or if you want to link a smartphone to your non-smart home Hi-Fi? Inateck has an answer in the form of the BR1002, a neat little gadget that can turn your older devices into Bluetooth enabled ones.
It's about the size of the sort of remote plipper that you use to lock and unlock a car. Controls are simple, a switch on the side to change between transmit and receive modes and a red button on the front for pairing. On top are a USB port for charging and a 3.5mm jack for connecting to your audio device. There's a printed -- although rather badly translated in places -- instruction leaflet that explains how it works.
Plug it into a USB port and a white ring around the button lights up to show it's charging. A full charge takes around two hours and will give you roughly six hours use as a receiver or eight as a transmitter. It'll beep to tell you the battery is running low. Pairing is simple, hold down the red button for a few seconds until two white LEDs flash and it should be visible to other devices. It'll automatically pair to the last used device when powered on. You can only pair one device at a time, however.
So what can you do with it? Basically the BR1002 lets you turn any device with a 3.5mm audio connector into a Bluetooth enabled one. In receiver mode you can stream music to your car from your phone, or turn an old pair of headphones into wireless ones, or in transmitter mode send sound from your old Walkman to your PC.
It works well in practice with a stable connection and only a very occasional glitch in the audio stream. The audio cable is very short but that shouldn't be a problem for the type of use the device will be put to. That and the fact you can only pair one device at a time are the only real drawbacks to the BR1002. At $21.99 on Amazon it's an inexpensive, versatile and easy to use gadget.
More information is available on the Inateck website.
-

DDoS attacks and how they work
Publié: janvier 25, 2016, 3:31pm CET par Ian Barker

DDoS attacks are one of the greatest threats that companies face and can lead to financial losses and damage to customer relationships.
But how exactly do these attacks work? Cloud delivery security company Incapsula has put together an infographic explaining the anatomy of an attack.
It looks at the victims of attacks as well as those who facilitate them. These include the 'arms dealers' who supply the software and tools to launch attacks, and also the types of cyber criminals who use them, ranging from hacktivists trying to make a political point -- hello Anonymous -- to script kiddies mounting attacks just for the fun of it.
The graphic also looks at the costs of attacks both in financial terms and in disruption to the business.
You can see the full infographic below.
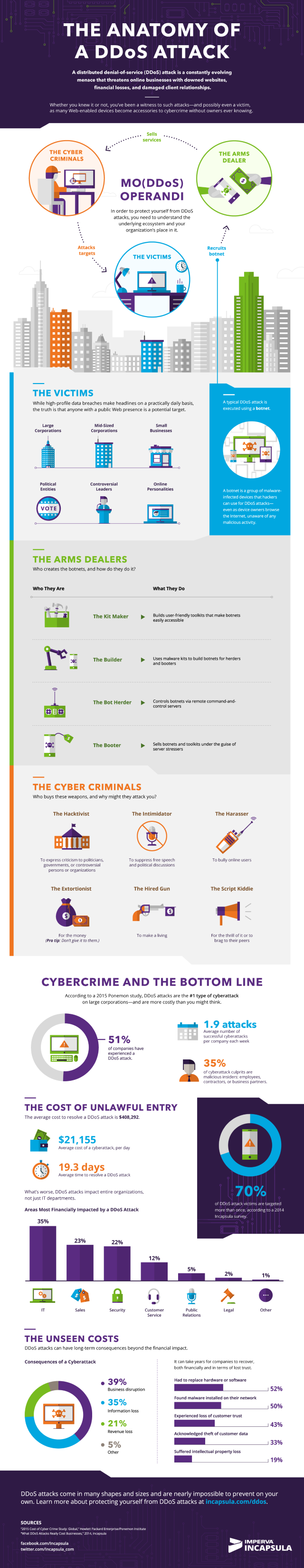
Photo Credit: Duc Dao / Shutterstock
-

SMEs and the Internet of Things
Publié: janvier 25, 2016, 1:41pm CET par Ian Barker
The Internet of Things is usually thought of in terms of its impact on consumers, but it has an impact on business users too.
UK support company Supreme Systems has produced an infographic looking at what the IoT can do for smaller businesses.
It looks at the areas where the IoT can benefit businesses including customer satisfaction, financial performance and overall efficiency. The graphic also covers how the IoT can open up new opportunities for research and product development.
The factors to consider when deploying the IoT are considered too, including security, open source and proprietary standards and more.
You can see more in the full infographic below.
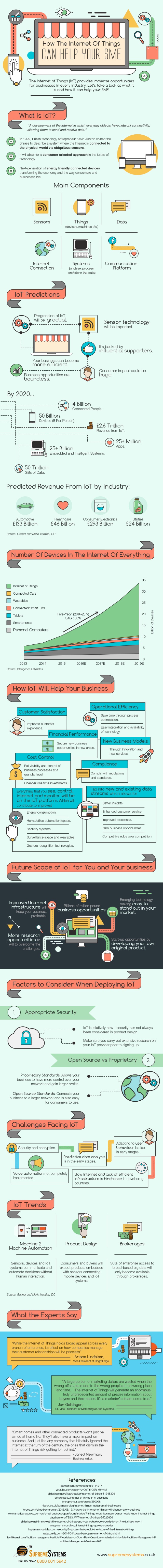
-

Humans get frozen out of frontline security
Publié: janvier 22, 2016, 4:43pm CET par Ian Barker

A new report from application delivery and cyber security specialist Radware suggests that the human element will increasingly be excluded from security as 2016 brings a 'battle of the bots'.
It finds that throughout 2015, no industry was immune to cyber attacks, and few were prepared for them. In 2016, attacks are predicted to become even more aggressive with the arrival of Advanced Persistent Denial of Service (APDoS) attacks and an increase in volume and scope of sophisticated bot-generated assaults against web application infrastructure.
"The front lines of information security will not include humans," says Carl Herberger, vice president of security solutions at Radware. "As defenses continue to succumb to an endless flood of sophisticated, automated attacks and an infinite number of new attack techniques, the idea of humans having the ability to deploy detection technologies and choreograph responses in real-time will disappear. We are approaching the fall of human cyber defenses and the rise of cyber botted-defense".
Other findings include the likelihood of an increase in frequency of ransom demands as attackers focus their demands toward service providers and leverage both DDoS and SSL flood attacks when payment is not made. New techniques like burst attacks, APDoS attacks, an increase in volumetric pipe attacks, and dynamic IP attacks will make it harder to defend using mostly manual solutions.
The report also shows that many companies are still ill-prepared for cyber attacks. While more than 60 percent say they are extremely or very well prepared to safeguard against unauthorized access and worm and virus damage, the same proportion of respondents say they're somewhat or not very prepared against advanced persistent threats and information theft. For DDoS attacks results split almost evenly between prepared and not prepared.
"In 2015, cyber-attacks became the new normal, as 90 percent of organizations surveyed experienced them in varying degrees," adds Herberger. "Organizations should prepare for the challenges that will lie ahead in 2016, laying the groundwork now to fight back against new methods and motivation".
The full report, including recommendations on how companies can protect themselves, is available to download from the Radware site and there's a summary of the findings in infographic form below.

Photo Credit: Vladru/Shutterstock
-

Only 45 percent of organizations are confident in their security
Publié: janvier 22, 2016, 1:50pm CET par Ian Barker

According to a new report 92 percent of executives believe regulators and investors will expect companies to manage their cyber security risk exposure, yet only 45 percent are confident in their security posture.
This is among the findings of the Cisco 2016 Annual Security Report which looks at the challenges businesses have in the face of a growing number of cyber threats.
Among other highlights of the report are the problems of an ageing infrastructure. Between 2014 and 2015, the number of organizations that said their security infrastructure was up-to-date dropped by 10 percent. The survey also discovered that 92 percent of internet devices are running known vulnerabilities. Worse than that, 31 percent of all devices analyzed are no longer supported or maintained by the vendor.
Cisco also identifies the risk that SMBs present to the supply chain. From 2014 to 2015 the number of SMBs that used web security dropped by more than 10 percent. This presents a potential risk to larger enterprises due to structural weaknesses. SMBs often lack the resources for an effective security posture, they are improving their security approach, in part, by outsourcing, which is up to 23 percent in 2015 over 14 percent the previous year.
Malicious browser extensions are identified as a potential source of major data leaks, although they’re often viewed by security teams as a low-level threat. This threat affects more than 85 percent of organizations. Adware, malvertising, and even common websites or obituary columns have led to breaches for those who don't regularly update their software.
"Security is resiliency by design, privacy in mind, and trust transparently seen," says John N Stewart, senior vice president, chief security and trust officer at Cisco. "With IoT and digitization taking hold in every business, technology capability must be built, bought, and operated with each of these elements in mind. We cannot create more technical debt. Instead, we must meet the challenge head on today".
The full report has much more information and is available to download from the Cisco website.
Photo Credit: watcharakun / Shutterstock
-

Managed service providers succeed by offering security products
Publié: janvier 20, 2016, 3:39pm CET par Ian Barker

A new survey from IT management specialist Kaseya reveals a continued surge in overall growth for managed service providers (MSPs), especially for those offering security services.
Kaseya's Global Pricing Survey gathers data from more than 400 MSPs across 30 countries and offers unique visibility into the IT services they offer their clients. It finds that the majority of MSPs have experienced more than 20 percent growth over the past three years.
The results reveal that high growth MSPs offer more emerging services than their lower growth counterparts, including cloud monitoring and hosting services for customer owned equipment. In addition almost all high growth MSPs deliver a strong portfolio of services such as cloud, backup and recovery, and desktop and server management.
High-growth MSPs rate services such as security as a key competitive advantage in the coming year, as heightened security risks came in as the top client demand for 2016. However, only slightly more than a third of respondents are offering one of the faster growing security segments, identity and access management (IAM) technology. The respondents that do offer IAM, though, report a double-digit annual growth rate over the past three years.
"As the leading provider of IT management, security and automation technology to MSPs, Kaseya is in the enviable position of being the vendor that others look to for information on what separates a successful MSP from the pack. Having been on both sides (MSP and vendor), I know first hand that successful MSPs have bolder strategies and put their customers' concerns first," says Miguel Lopez, Kaseya’s SVP and GM of MSPs. "At Kaseya, we base our own customer success model on our customers’ year-over-year growth rather than our own company’s sales. It turns out that the most successful MSPs follow the same model for their users. Kaseya's annual MSP pricing survey provides the industry with a tool to use to evaluate what company success looks like, and highlights the areas the most successful thrive at".
Other findings include that high growth MSPs are able to charge more for their technicians and have a higher variance of what they charge for level one, two and three technicians. Higher growth MSPs also charge more on average for ongoing server support and maintenance per month. They're also more than twice as likely to offer cloud monitoring services than lesser growth providers.
In addition 85 percent of high growth MSPs are more likely to provide hosting services for customer-owned equipment. Plus almost three quarters of high growth MSPs offer desktop security services.
More information and analysis of the report's findings can be found on the Kaseya blog.
Image Credit: Manczurov / Shutterstock
-

Birst expands its networked BI platform
Publié: janvier 19, 2016, 6:52pm CET par Ian Barker

Cloud analytics specialist Birst is releasing new capabilities for its Networked BI Platform aimed at empowering end users in the enterprise to work with data effectively.
New features include Birst Mobile for Android, Collaboration, and End-User Data Preparation. The networked BI Platform is aimed at creating a network of interwoven BI instances that share a common analytical fabric, eliminating data silos to ensure collaboration and accelerate the delivery of BI across the enterprise.
End-User Data Preparation gives users the ability to rapidly refine their own data, analyze it by itself, or blend it with data from other people in the BI network. Individuals can glean insights on their own while also staying networked and connected to other users. This eliminates the silos that emerge from analyzing data on a desktop and ensures one seamless connection.
Birst's Collaboration capability enables any user in the network to collaborate through in-context discussion threads that mimic their daily social media interactions. User posts, within Birst, capture the data in context, ensuring that users can see the data as it was when the original posts were created.
Additionally, Birst Mobile for Android enables users anywhere to access the same data whether on a desktop, laptop or mobile. Offline capabilities automatically sync data and content so business users are able to view mobile analytics even when not connected.
"Birst's revolutionary approach to BI allows for agility, so business users can operate in their own personal BI sandbox while staying connected across the entire enterprise," says Brad Peters, Chief Product Officer, Birst. "Unlike traditional approaches, Birst’s Networked BI Platform helps business leaders empower users to work freely with data, while delivering trust, governance and agility at scale".
More information about the latest platform can be found on the Birst website.
Image Credit: Syda Productions / Shutterstock
-

Enterprises keen to adopt Windows 10
Publié: janvier 19, 2016, 3:17pm CET par Ian Barker

A new survey of IT professionals from large organizations reveals higher than anticipated momentum for the adoption of Windows 10, with 63 percent of respondents expecting to run Windows 10 on a significant number of systems this year. The study from systems management specialist Adaptiva shows that of those IT departments that piloted Windows 10, nearly half (40 percent) have now deployed it on 50 percent or more of their systems, indicating strong confidence levels and unprecedented adoption of the new operating system.
The large scale movement to Windows 10 is fueling high demand for the new version of Microsoft Systems Center Configuration Manager (ConfigMgr), software used to distribute and update operating systems and other software. Roughly two-thirds (65 percent) of those moving to the new ConfigMgr released in December cited deployment, updating, and management of Windows 10 as their biggest motivators for upgrading. The announcement earlier this month that Windows 8 will no longer receive security patches is also thought to be accelerating the drive to Windows 10.
"The survey results underscore the surge in Windows 10 interest we are seeing from enterprises as well as the concerns they have about keeping pace with the frequent updates," says Jim Souders, chief operating officer at Adaptiva. "The new Microsoft ConfigMgr and Windows 10 releases are ushering in a need for a more automated, intelligent approach to systems management that reduces the time and complexity necessary to keep software and systems secure and up to date".
Photo credit: XiXinXing / Shutterstock
-

61 percent of new organizations are born in the cloud
Publié: janvier 19, 2016, 3:02pm CET par Ian Barker

The cloud is changing the way businesses and IT teams operate and a new survey from industry specialist BetterCloud reveals the extent of the shift.
Based on a survey of 1,500 IT professionals it shows that of organizations started in the last two years 61 percent have begun their operations in the cloud. In addition 59 percent of IT professionals say the cloud has changed the structure and responsibilities of their team in the past year.
Smaller businesses with less than 1,000 employees are heading the dash skywards, with 51 percent reporting that they expect to have all of their systems in the cloud by 2020. This compares to 32 percent of mid-market businesses and only 21 percent of enterprises.
The report also shows up some interesting facts on the path companies have taken to the cloud. Before moving to Google Apps 49 percent of customers came from Exchange, 35 percent had no previous platform, seven percent came from Lotus Notes, five percent from Office 365 and four percent from Novell Groupwise.
Comparing this to Office 365, 70 percent of current customers came from Exchange, 13 percent came from Google Apps, eight percent had no previous platform, six percent came from Lotus Notes and three percent came from Novell Groupwise.
It can take up to a year to choose and move to a cloud system and there are some surprising factors in adoption rates, including the age range of employees. Companies with an average employee population aged between 18 and 20 had on average three cloud apps in 2015 and are expected to have five by 2017. Those with more experienced employees in the 35 -- 44 age range however had six cloud apps in 2015 but are expected to have 15 by 2017.
You can find much more information in the full 2016 State of Cloud IT report on the BetterCloud blog.
Image Credit: ND Johnston/Shutterstock
-

Google overtakes Facebook in advertising spend
Publié: janvier 15, 2016, 8:33pm CET par Ian Barker

A new report from marketing technology company IgnitionOne reveals the latest trends in digital advertising spend for the final quarter of 2015.
Among its key findings are that Google passed Facebook in growth and conversions, seeing an increase of 37 percent in programmatic display advertising spend and a 34 percent increase in conversions. In comparison, Facebook saw an increase of 22 percent in growth and 17 percent in conversions.
Other findings are that in the US paid search has continued the consistent growth seen over the past several years, with an 18 percent increase year on year. In addition following steady drops seen in the past three out of four quarters, impressions are on the rise, with a year on year increase of 7 percent. This is somewhat unexpected after Q3 2015, which saw them down by 21 percent.
"The overall increase is due in part to the rise in both Google Partner Network activity and impressions from Google shopping ads", says IgnitionOne’s Marketing Content Manager Rachel Peterson writing on the company’s blog. "Google’s shift to shopping ads in a carousel format has led to an overall increase in impressions, but a decrease in CPC (Cost per Click) growth, particularly in mobile, which saw CPCs down by 21 percent".
Cyber Monday continues to drive Thanksgiving shopping trends, seeing an impressive 107 percent increase in spend compared to normal baseline activity. Automotive advertising was strong in the final quarter too, with a 66 percent increase in spend and 58 percent increase in clicks over the previous year.
The full report is available to download from the IgnitionOne website.
Photo Credit: mtkang / Shutterstock
-

Almost a quarter of companies are willing to pay $1m ransom to hackers
Publié: janvier 13, 2016, 3:06pm CET par Ian Barker

We all know that cyber attacks can be enormously disruptive, but how far would companies go to prevent an attack?
A new survey by the Cloud Security Alliance and Skyhigh Networks reveals that 24.6 percent of companies would be willing to pay a ransom to hackers to prevent a cyber attack and 14 percent would pay more than $1 million.
The report also shows a high level of confidence in the cloud which is seen as being more secure than on-site systems. That said, a lack of skilled security professionals is seen as being a barrier to companies seeking to prevent cloud data loss.
"It's shocking that so many companies are willing to pay even a penny’s ransom, and would trust hackers not to follow through with an attack. The idea that some would pay more than $1m is downright staggering. There are no guarantees at any price, and there is no way back once the payment is made," says Nigel Hawthorn, Skyhigh Networks' Chief European spokesperson. "Examples of companies refusing to pay up, such as Meetup.com, are few and far between. As such, hackers are increasingly confident they can hold businesses over a barrel, that they can execute crippling cyberattacks and that most businesses would rather pay up than put up. There will be several high profile examples of ransomware in 2016, and countless unreported incidents on top of that".
The European Cloud Adoption and Risk report also reveals that by the end of 2015, for the first time ever, the average European enterprise now uses more than 1,000 cloud applications -- with some companies using as many as 6,000. It shows a rise in EU-based cloud services too, which nearly doubled over a six month period (from 14.3 percent to 27 percent of services). Worryingly though only 8.1 percent of the 16,000 services analysed met enterprise requirements for data and privacy.
More information is available in the full report which can be downloaded from the Skyhigh website.
Photo credit: Fabio Alcini / Shutterstock
-

The future of enterprise storage [Q&A]
Publié: janvier 11, 2016, 2:17pm CET par Ian Barker

Storage has undergone some major changes in recent years. The growth of cloud usage, the Internet of Things and the exploitation of big data have all meant increased demand and a shift towards different solutions. But how has this affected the storage industry and and what further changes can we expect to see?
We spoke to Mark Lewis, Chairman and CEO of storage specialist Formation Data Systems to get his view on how the industry is evolving.
BN: How much has the rapid growth of cloud computing affected the storage business?
ML: Cloud computing represents a major disruption in how infrastructure is delivered and clearly represents a model of what enterprises need to do in order to remain competitive. If you look closely at how Google, Amazon, LinkedIn and the other cloud leaders built their massive cloud infrastructures you’ll note that they didn't use any proprietary storage technology from the traditional enterprise vendors like EMC, NetApp or Hitachi. The reason behind this is pretty simple; all you have to do is to look at the economics of trying to deliver web-scale infrastructure that provides the agility, flexibility and performance needed to deliver enterprise-grade infrastructure. Existing storage technologies couldn't deliver anything even close to what is needed to be competitive. The cloud service providers knew that the only way they could achieve these goals was to write their own custom software that will run on industry standard compute infrastructure. Enterprise IT is faced with the same challenges today, but they clearly don't have the resources to build their own storage software stack, so a software-defined solution like Formation is very attractive.
BN: How will the increase in unstructured data from the IoT and other sources impact storage demands?
ML: Unstructured data from multiple sources has already been placing incredible pressure on Enterprise IT managers for years, and this will only increase with the onset of a completely new class of devices and applications that will generate massive amounts of unstructured data. IoT is a good example, but there are many more that are relevant in the enterprise. So, in order to manage this new class of unstructured data in the enterprise, it must be classified, stored, protected and analyzed as part of their normal business processes. This means that the data should be replicated, backed up and subjected to the same standards that structured data has been subjected to for decades. Here's the problem -- how can an IT manager continue to build out more silos of data storage using traditional technologies with flat or declining budgets. The short answer is that you can't. An entirely new method is needed to be able to support multiple data types on the same platform, apply enterprise grade functions such as replication, snapshots and backup, but do so using industry standard hardware and intelligent software-defined storage platforms. Enterprises need to approach the problem the same way that the cloud guys did in order to survive. Otherwise, they'll drown in all the data being generated.
BN: Can enterprises save on costs by optimizing their storage use?
ML: Optimizing existing storage platforms can provide only incremental benefits, but won’t solve the problems that we discussed earlier. We keep hearing from our customers that they don't need 10 percent cost savings; they are looking for a 10X order of magnitude in TCO reduction. This is why many have shifted newer workloads over to AWS, Google or Microsoft, because as we discussed, this is where a lot of the growth will come from. But the problem that is being created is that you’re managing legacy workloads in your data center and newer workloads in the cloud. It's not very streamlined and creates even higher levels of inefficiency and complexity. Formation has performed very detailed analysis on TCO reduction on our software-defined storage solution as compared to traditional storage arrays and we've proven that an enterprise can realize anywhere between four to seventeen times (4-17x) TCO reduction using our platform versus traditional storage technologies. This level of cost reduction means that users can run on-premise storage for less than what it would cost to manage the same amount of storage in the cloud. As the capacities increase, so do the savings
BN: Isn't there a danger of introducing greater complexity?
ML: It's actually the exact opposite. When done correctly, consolidation of multiple workloads on a single system will remove complexity, simplify operations and provide higher levels of efficiency. Rather than having four or five ways to provision, manage, report and protect your data, you now have a single way to do it. Because we've built the FormationOne platform using cloud and web-scale methodologies, the system is extremely simple to operate and scales seamlessly to support very large environments.
BN: What do you think will be the major trends in storage in 2016?
ML: Software based infrastructure will move from trials and labs into mainstream production, especially in storage. As we discussed, the growth in data are there and the economic are too compelling to not take advantage. We’re seeing evidence of this in the field and many of the customers that we're working with now are looking at how to deploy true software-defined storage.
Photo Credit: wavebreakmedia/Shutterstock
-

Penclic R3: Not your typical mouse [Review]
Publié: janvier 11, 2016, 11:03am CET par Ian Barker

Using a mouse for long periods can be uncomfortable and in severe cases may even lead to repetitive strain injury.
There are various pieces of kit on the market to help you avoid this including ergonomically designed mice and wrist rests. Taking a slightly different and more innovative approach to the problem is the Penclic which is a sort of fusion of mouse and pen.
It looks rather like one of those pens you find chained to the counter in banks, but is attached to its base with a ball joint. The base, which is shaped like a small mouse, houses a rechargeable battery and has an LED that glows green to indicate it’s charging and changes to red when it needs charging. On the underside are an on/off switch a button to sync with reciever and a +/- button to adjust the DPI setting for sensitivity.
The base and the top are shiny plastic with the bit where you hold it and click the buttons in a smooth matt finish. A slim chrome band between the top and bottom sections of the pen adds a touch of bling.
In the smart plastic package you get the Penclic itself, a USB receiver for wireless operation, a retractable cable for charging and a cloth pouch to carry it all around in. There are some basic multilingual instructions that explain how to get started. It will work with Windows, Mac and Linux systems and there’s no driver installation required.
In Use
The base of the Penclic works like a normal infra red mouse, the difference being that the scroll wheel and left and right buttons are relocated to the pen. You hold it just like you would a normal writing implement and it can be used either left or right-handed.
The charger cable has a microUSB connector at the mouse end and this is a bit fiddly to attach, you’re also not quite sure if you’ve pushed it home far enough. Once you’ve charged the battery, setting up is easy: plug the receiver into a USB port on your PC, press the button on top, press the corresponding button under the mouse, the LED flashes red for a few seconds and you’re good to go, there’s no need to install any software as it uses the standard mouse drivers.
After rebooting or recovering from sleep mode you need to press the mouse’s connect button again to re-establish a link. The +/- switch lets you change from the standard 1200 DPI setting to 800 or 1600.
Using the Penclic feels a little weird at first and you need to take some time to find a comfortable way of holding the device and moving it without pressing buttons by accident. With a normal pen-like grip your index finger sits over one button and your thumb over the other with your first finger on the scroll wheel. It’s slightly confusing, however, as on the standard setup the right button left-clicks and the left button right-clicks.
You can of course reverse this from the Windows settings, but -- for right-handed users at least -- the way Penclic does it actually makes sense after a while as the index finger click to select text or press on-screen buttons feels like a more natural action.

Once you get used to it you’ll find the Penclic is nicely sensitive. It does feel very light though which means it’s easy to move it more than you intend even on the lower sensitivity setting. It’s also quite easy to squeeze the pen and click both buttons together until you adapt to using it. The scroll wheel’s middle button click action is a bit stiff which means it’s easy to move the mouse by accident when you select it.
The physical advantage to using the Penclic is that your arm and wrist adopt a more natural angle and you can rest the base of your palm on the desk to provide support. It’s fine to use for long periods with no resulting aches and pains.
Depending on how much you use the R3 you can get up to a month on a full battery charge, the LED flashes red to warn you when it’s running low. If you get caught out you can use a standard AAA battery to power the device temporarily until you can recharge it.
Conclusion
It takes time to adapt to how the Penclic works and build up your levels of accuracy. Once you do it works perfectly well allowing you to accurately position the cursor. The unorthodox button arrangement takes a little longer to get used to but it makes sense once you’ve been using it for a while.
It does only have the standard buttons so it won’t replace your sophisticated gaming mouse, but then that isn’t the market here. For standard office use it’s perfectly fine and comfortable to use. It’s also quite good for use with graphics programs too as it has a natural, pencil-like, feel.
The Penclic R3 isn’t cheap at £59.99 but if it saves you from RSI it could be well worth the money.
Pros
Easy to set up
Accurate movement
Long battery lifeCons
Unorthodox button layout
Very light
Fiddly charge cableITProPortal Review: 8/10
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

New malware attack targets WhatsApp users
Publié: janvier 7, 2016, 3:10pm CET par Ian Barker

A new malware campaign is aiming specifically at businesses and consumers using the WhatsApp mobile messaging service.
Uncovered by researchers at Comodo Labs the campaign uses emails masquerading as WhatsApp content. These have an attached zip file containing a malware executable.
The emails have a variety of subject lines including, "You have obtained a voice notification," and "An audio memo was missed," each followed by a short string of random characters which are probably used to identify the recipient.
If the zip file in the email is opened and executed, the malware is installed on the PC. It's a variant of the 'Nivdort' family. When run it replicates itself into different system folders, as well as adding itself into an auto-run in the computer's registry.
"Cybercriminals are becoming more and more like marketers - trying to use creative subject lines to have unsuspecting emails be clicked and opened to spread malware," says Fatih Orhan, Director of Technology for Comodo and the Comodo Antispam Labs. "As a company, Comodo is working diligently in creating innovative technology solutions that stay a step ahead of the cybercriminals, protect and secure endpoints, and keep enterprises and IT environments safe".
More details of the attack are available on the Comodo blog.
Photo Credit: Balefire/Shutterstock
-

Enterprise Crowdfunding will help big companies pilot and launch products
Publié: janvier 6, 2016, 11:31pm CET par Ian Barker

Crowdfunding has become a popular way for smaller businesses and independent designers to gain backing for their projects. Now though funding platform Indiegogo is turning its sights on bigger business.
It's launching a new Enterprise Crowdfunding service to provide large corporations with specific services for engaging with Indiegogo's audience of early adopters, entrepreneurs and makers. This will allow enterprises to validate and optimize product concepts, as well as source new innovations.
"We created Indiegogo to empower anyone, anywhere to raise funds for their ideas, from the inventor working out of her garage to the largest Fortune 500 companies looking to create innovative new products that line up with what customers really want," says Indiegogo CEO Slava Rubin. "Some of the world's most successful companies are already using Indiegogo for product development, market research, and to support causes important to them. Now we’re taking that a step further with Enterprise Crowdfunding".
A number of large companies have announced milestone Indiegogo campaigns. Among these are games maker Hasbro which selected the family-friendly card game 'Irresponsibility' as the winner of its first campaign and is planning future challenges for 2016.
Harman International Industries will launch an Indiegogo campaign to evaluate the market potential for a new selective noise cancellation technology for its line of JBL headphones. Also Shock Top helped pioneer Indiegogo's enterprise platform with its 'Shock the Drought' initiative, launched in August 2015 to identify, fund and bring new water-saving technologies to market in response to the California drought.
"We set out to help California during one of the worst droughts in history, and Indiegogo proved to be a great partner and resource for inventions with the potential to make a big impact on water conservation," says Jake Kirsch, Vice President of Shock Top.
You can find more about the Indiegogo program for enterprises on the company's website.
Photo credit: Andrey_Popov / Shutterstock
-

Vulnerability puts users of privacy-focused Blackphone at risk
Publié: janvier 6, 2016, 3:30pm CET par Ian Barker

Blackphone is marketed as the most secure Android phone available so it's bad news that researchers at endpoint protection specialist SentinelOne have uncovered a vulnerability in the Blackphone One that would allow some of the phone’s protection features to be bypassed.
The vulnerability means that apps could be installed without asking for permissions, so they could access features and information on the phone without the user’s knowledge.
Among things the vulnerability would permit are, sending and receiving text messages without the user’s knowledge, checking the state of phone calls silently (what number the call is connected to and was it incoming or outgoing), and forcing conference calls with other numbers.
SentinelOne's director of mobile research Tim Strazzere says, "The issue lets you talk directly to the modem at the firmware level, so Android doesn't know what's going on. This also means that the user wouldn't know if, for example, call forwarding had been set up".
The vulnerability arises through a socket that has been left open and accessible on the Blackphone. Although it hasn't been seen in the wild it could be exploited using a malicious app.
Once SentinelOne had validated its findings it reported them to SilentCircle, Blackphone's parent company, and it has now been fixed via SilentCircle’s bug bounty program.
Strazzere notes on the SentinelOne blog, "This vulnerability illustrates the breadth and depth of the attack surface on this and other devices. It also raises some important considerations for security professionals. First, even the most 'secure' systems can be vulnerable to attacks. Second, the increasing proportion of third party technology (hardware, drivers, software libraries, etc.) used in today’s devices makes detecting and remediating flaws more difficult than ever. And finally, virtually all vulnerabilities require some form of malware in order to be remotely exploited. Monitoring processes on a device can provide an important layer of detection and response when apparently legitimate requests to perform system functions originate from anomalous sources".
Image credit: Brilliant Eye/Shutterstock
-

Messaging, productivity and shopping apps drive Flurry of mobile growth
Publié: janvier 5, 2016, 4:20pm CET par Ian Barker

Overall mobile app usage grew by 58 percent in 2015 according to the latest figures from Flurry, Yahoo's mobile advertising and analytics platform, which tracked over 3.2 trillion sessions over the course of the year.
With the exception of games, which showed a one percent drop, every app category posted year-on-year growth. Personalization leads the way, up 322 percent, news and magazines are up 135 percent, and productivity also shows triple-digit growth up 125 percent.
Writing on the Flurry Tumblr, Simon Khalaf, SVP, Product and Engineering, Publisher Products at Yahoo says, "What was even more impressive is the majority of that growth rate came from existing users versus new users. In fact, in 2015, we estimate that 40 percent of the 58 percent total growth in sessions came from existing users, compared to 20 percent in 2014 and 10 percent in 2013".
Looked at by devices, news and magazine apps, sports apps, and music, media, and entertainment apps all saw faster growth on phablets -- a spectacular 721 percent in the case of news and magazines.
Time spent using mobile devices is up too, increased by 117 percent overall. Once again phablets lead the way with a 334 percent growth in usage as compared to 85 percent on medium phones and 81 percent on small tablets.
More details on the findings can be found on the Flurry Tumblr blog.
Photo Credit: 3Dstock / Shutterstock
-

No backdoors thanks, we're Dutch
Publié: janvier 5, 2016, 3:25pm CET par Ian Barker

Unlike other countries, notably the UK and China, that have been busy passing laws to allow them to snoop on encrypted communication, the Dutch government has decided that strong encryption is vital to the health of its digital economy and the privacy of its citizens.
The country's minister of security and justice Ard van der Steur writes in an official statement that the Dutch executive cabinet endorses, "...the importance of strong encryption for Internet security to support the protection of privacy for citizens, companies, the government, and the entire Dutch economy. Therefore, the government believes that it is currently not desirable to take legal measures against the development, availability and use of encryption within the Netherlands".
The minister points out the weakened encryption won't make the world a safer place as it will give criminal organizations easier access to sensitive data, adding, "Confidence in secure communication and storage data is essential for the future growth potential of the Dutch economy, which is mainly in the digital economy".
The move has been welcomed by security professionals. "The decisive announcement from the Netherlands to maintain strong encryption and avoid implementing back-door access sets a powerful example that other world governments should follow," says Dr Nithin Thomas, Co-Founder and CEO of secure data transmission specialist SQR Systems. "Creating back doors in encryption technology would just as readily create access for hackers as it would intelligence services, leaving everything from individual financial data to national secrets at risk".
Whether other governments will be willing to adopt the Netherlands' enlightened approach to encrypted communication we'll have to wait and see, but we're not holding our breath.
Photo Credit: Kutlayev Dmitry/Shutterstock
-

Google Nexus 5X: An Android Marshmallow smartphone worthy of your attention [Review]
Publié: janvier 5, 2016, 11:12am CET par Ian Barker

Phones have been gradually getting bigger in the past few years. That makes for better displays for watching videos and viewing documents and web pages, but there’s a downside too.
For many people it makes them more awkward to carry around and can mean they’re harder to use as a phone because you need two hands to operate them.
Bucking the trend somewhat the latest Nexus 5X is at the compact end of Google’s smartphone range, with a 5.2-inch display. It would be easy to dismiss this phone as a budget option, but in fact although it’s small it isn’t short of features and it has a lot to offer for business and personal users alike, so let’s take a closer look at its features and how it works.
In the Box
Although it’s sold under the Google name, the Nexus 5X is actually manufactured by South Korean electronics giant LG and it has that company’s subtle branding on the back. The package is pretty minimalist and contains just the phone itself plus a mains charger and USB cable. Note though that the cable is USB-C at both ends rather than the more usual standard USB to microUSB that you get on Android phones. So if you want to connect it to your PC you’ll need an adaptor, Google will sell you one for an extra £10.99.

There are no printed instructions included, just a card with graphics explaining how to insert a SIM card and connect the charger. You do get a little tool in the pack to allow you to open the nanoSIM slot.
The design of the phone is quite smart with an all-glass front that has no physical buttons and is pierced by speaker and mic grilles top and bottom. Its slim at just under 8mm, slightly more if you take into account the bulge around the camera lens. There’s a thin black plastic surround which has power and volume buttons on the right-hand edge and the SIM card slot on the left. USB and headphone connectors are on the bottom edge. The back, white (quartz in Google speak) on our review unit but blue and black versions are available too, has a slightly raised area around the camera lens and below that a ring surrounding the fingerprint sensor.
The back is plastic but it has a smooth matt finish which is pleasant to touch and has rounded edges so it’s comfortable to hold too. Viewed from the edge the black and white combination makes it look like a thin Liquorice Allsort.

The screen has a 1920 x 1080 resolution (1080p) and narrow edges at the sides which provide a good usable area. Under the skin there’s a 1.8GHz hexa-core processor (Qualcomm Snapdragon, with four cores at 1.4Ghz and two at 1.8GHz, for people who like to know these things), plus an Adreno GPU, you get 2GB of RAM and either 16 or 32GB of storage. Our review unit was the 32GB version, note though that there’s no SD card slot so you can’t add extra storage later.
It has 12.3MP rear and 5MP front cameras, a 2,700 mAh battery and a variety of sensors including an accelerometer, gyroscope, barometer and proximity sensor. Connectivity is via 4G, Wi-Fi (up to 802.11 a/c) and Bluetooth 4.2, plus NFC. It runs the latest Android 6.0 Marshmallow and comes unlocked so it can be used on any mobile network.
Business Features
The Nexus 5X isn’t really aimed at business users but it does nonetheless have a number of features that would make it attractive to them. It offers good battery life that will get you through a full day of moderately heavy use and if you do need to charge it you can do so quickly, allowing people on the move to take advantage of quick pit stops -- provided they remember the USB-C charger.
The fact that it’s unlocked is useful too as you can use your preferred network and take advantage of whatever contracts you may already have in place. The inclusion of a fingerprint reader makes for better security and the fact that it comes with standard Android gives you a blank canvas for your business apps. Marshmallow’s app permissions feature lets you tell an app it can access stuff like location only when it actually needs it, rather than you granting blanket access at installation. This should help prevent unintended data leaks through badly written apps.
The downside for serious business use is that memory is limited and storage is not expandable so if you want to carry large amounts of business data around with you you’re going to need to look elsewhere.
In Use
With its plastic back and relatively light weight -- only 136 grammes -- it’s hard to get away from the fact that the Nexus 5X looks and feels a bit cheap at first, the power and volume buttons don’t help this impression as they have hard edges and lack positive feel. Don’t let that put you off, however, because there’s quite a lot to like.
The 5.2-inch screen means it’s comfortable to hold in one hand, with everything no more than a thumb’s span away, in this respect it’s easier to use than the larger 5.7-inch Nexus 6P. It’s also easy to slip into a pocket without it feeling too bulky or spoiling the line of your expensive tailoring.

That screen works well too with bright colors, strong contrast and good touch response though the slight vibration you get when typing to tell you a press has registered is so subtle as to be almost unnoticeable. The Nexus 5X has an Ambient Display feature that wakes the screen in greyscale when the phone is picked up or a notification message arrives. It also has adaptive brightness that optimizes the screen brightness settings to suit the available light levels. Turning this off gives you a brighter display most of the time but at the expense of battery life.
What you enjoy in vision you miss out on in sound. The single speaker is just about acceptable for ring tones or making phone calls but if you want to listen to music or watch videos you will need to use headphones in order to get decent audio quality.
Whilst it may be inconvenient in terms of what you can connect it to just at the moment -- until the standard becomes more commonplace -- one of the advantages of using USB-C is that there’s no ‘wrong way’ to connect it. The plugs work either way around so it’s less fiddly to hook things up. Its other big advantage is it enables fast charging. With the supplied charger you can plug the phone in for around 15 to 20 minutes and it gives you about a quarter of the battery capacity back, enough for three hours or so of use. Under two hours charging time will give you a completely full battery. There’s no wireless charging option though which represents a step back from the older Nexus 5.
Unusually the fingerprint sensor is located on the back rather than the front of the device, but this actually works very well being perfectly positioned to rest your index finger on when you’re using the phone. It also has that raised ring around it making it easy to locate just by touch and it unlocks the phone fast with a single press. Training it to accept new prints is also quick and easy and you can set a backup pin, gesture or password just in case.
The 12.3MP rear camera is quite impressive and takes some decent pictures even in relatively poor lighting conditions, there is a built-in flash too. You can shoot 4K video as well, though that will eat up your available storage pretty quickly at 300MB a minute, and it’s easy to switch to video mode by swiping the screen. The camera lacks features like image stabilization and burst mode that are present on the larger Nexus 6P though. The camera app too is rather limited with just a few features like lens blur, panorama and photosphere, plus an HDR mode. A useful function is that double pressing the power button when the screen is off will immediately put the phone straight into camera mode so you can quickly grab a shot. The front camera is only 5MP, but fine for making video calls, taking selfies and the like.
If you haven’t used Android Marshmallow before you won’t find it too much of a culture shock over earlier versions of the OS. It does have some nice touches though, in particular the app screen that scrolls vertically rather than sideways, making it easier to find things and better to use one-handed, and the app permissions system which makes for improved security by only allowing app access to hardware features when they’re actually required. It also has a clever ‘Now on Tap’ function that lets you Google whatever it is you’re currently looking at on screen, in any app, simply by holding down the phone’s home button. This is handy for looking up how to use a function of the settings menu for example.

You might expect that with only 2GB of RAM on board, performance would be the Nexus 5X’s Achilles heel, but in fact it’s pretty good. Moving around the interface is fluid and fast and you never feel that you’re having to wait for the phone to catch up. It does take a little while to boot up after it’s been powered off but that’s a minor niggle. That said, whilst 2GB of RAM may be okay now, plenty of other phones are coming with 4GB or more as standard and app developers will soon start to take advantage of the extra. This may not, therefore, be a phone to buy for the long term.
The battery will give you around eight hours of continuous use on a full charge so it should be fine for a working day. Standby time is more impressive though, Google quotes up to 420 hours, in part due to Marshmallow’s Doze feature which puts apps into sleep mode when it detects that the phone is stationary for a time, thus reducing power usage.
Conclusion
Overall the Nexus 5X is a bit of a mixed bag. With its plastic back and light weight it does look and feel rather cheap, particularly the power and volume buttons, but it’s actually quite robust and the smooth plastic back resists fingerprints well. It also has some good features, the screen for example is impressive and the well placed fingerprint reader makes for ease of use.

Camera performance is good too and overall it’s a nice size, balancing usability and portability. Plus of course it has the latest Marshmallow version of Android and being from Google you get it in its pure form with no bloatware and no re-skin. Perhaps the biggest drawback is the 2GB memory which limits future proofing, you’ll almost certainly want to spend the extra £40 to get 32GB of storage too.
Using USB-C only for charging is no doubt good for the long term, though a bit annoying at the moment if you’re caught with a low battery and don’t have the supplied charger with you. It’s a shame they didn’t provide an adaptor to let you use a standard USB socket rather than only offering it as an extra.
The Nexus 5X Starts at £304 for the 16GB version, the 32GB as tested is £344. That makes it competitively priced if not especially cheap. There’s a lot of competition at this end of the market and phones like the Moto X Play and OnePlus X offer similar feature sets for slightly less money.
However, the Nexus 5X is well worth including on your shortlist and with no network restrictions and an unmolested version of Android it’s a blank canvas for you to personalize to your own taste.
Pros
Quick charging
Good battery life
Android MarshmallowCons
Only 2GB of RAM
No SD card slot
USB-C onlyITProPortal Review: 7/10
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

The challenge of managing the cloud in the enterprise [Q&A]
Publié: janvier 4, 2016, 3:10pm CET par Ian Barker

It's an increasingly rare business today that has all of its IT on its own premises. The cloud has led to many systems being moved off site and also contributed to the growth of shadow systems.
How can business manage these challenges and make sure that they're not putting their information at risk? We spoke to John Purrier, cloud visionary and CTO of business automation company Automic Software to find out.
BN: Is there an increasingly blurred boundary between private and public clouds?
JP: We are definitely seeing an accelerated convergence between traditional on-premises data centers and multi-tenant public clouds, giving rise as well to managed single tenant hosting and single tenant isolation on public cloud infrastructures. Private data centers are increasingly being managed and consumed through cloud and DevOps technologies, and the public clouds have made great strides in security, data protection, and the ability to isolate tenants from one another for both security and performance considerations. Over time, this convergence will provide greater choice to enterprise IT organizations in allowing them to place workloads and data where it makes most business sense rather than being forced by the technology architectures.
BN: We're seeing more and more analytics solutions aimed at systems management. Is this the future and can we expect more automation?
JP: This is one of the most exciting aspects of the digital transformation taking place. We are moving toward more dynamic and real-time analytic feedback into the automation processes controlling IT workflow and management. This allows the control systems to make decisions on workload placement, environment creation/destruction, data storage, network routing, etc. based on the actual state of the entire IT environment rather than following statically defined scripts. As we increasingly instrument our networks and environments, such as with the Internet of Things (IoT), we will increasingly use this real-time data to continually improve business efficiency through automation.
BN: What are the biggest challenges for companies considering a shift to the cloud?
JP: As enterprises look to make their own digital transformations there are a few critical questions to be answered:
1. Adopting cloud technologies and potentially moving applications and data outside of the corporate firewall is a technical challenge, but the larger challenge is cultural. The move to the cloud requires process and procedures that need to be made integral to the IT and company culture to be successful. The internal evangelism and adoption of cultural change is probably the biggest challenge.
2. A realistic inventory of existing systems and processes needs to be done, and decisions made as to whether current applications and data systems a) stay where they are and are maintained, b) moved to cloud architecture and frameworks, perhaps through PaaS or other application tooling, c) sunsetted and retired, or d) re-implemented as cloud-native applications. Orchestration automation is a valuable tool in making the existing systems continue to run seamlessly while investing development and operational resources toward the cloud-based systems.
3. In working with Enterprises on their application journey to the cloud common patterns for best practices have emerged. Taking significant, but non-business critical applications such as marketing sites, brochure sites, and short lived campaigns initially and running these as pilots gives teams a good feel for new cloud-based processes and tools. These pilots also allow for simultaneous deployment of DevOps tooling and processes. Through an iterative cycle of develop/deploy/retrospective-learning organizations find their own rhythm and cadence for cloud-based deployments.
After the pilot period then the processes can be scaled up to rapidly move more applications, moving from non-business critical to mission critical. At this point it is critical to have a solid DevOps and Operational automation strategy and implementation to ensure repeatable and reliable deployment pipeline processes.
4. Understand that cloud system management, orchestration, and automation tooling will increasingly allow multiple data centers and multiple cloud infrastructures to be part of an overall Enterprise IT solution. This will allow truly level playing fields amongst the providers, preventing lock-in and giving the Enterprises the governance, insight, and control they need to accelerate their business.
BN: What do IT managers need to look for in potential cloud providers?
JP: It is key that IT managers understand the network security, tenant isolation, and data security models of the cloud providers they are thinking of engaging with. Additionally, if applicable, CSP policies allowing data sovereignty and regulatory compliance should be explored. These are the big concerns many Enterprises have with going outside of their own firewalls. Next up would be performance and uptime SLA agreements, along with support policies and issue escalations.
BN: How should providers address legitimate concerns over the security of data and meeting compliance requirements?
JP: These are, and have been, the focus of cloud providers for several years. The fact is that CSP's at any kind of scale have more network engineers, security engineers, compliance experts, and operational personnel than most companies that run their own data centers. The providers should be able to walk through their policies, technology, and remediation systems in detail to any customer who wants assurance that the infrastructure meets their requirements.
There may always be some combination of requirements that make a company invest in their own data centers and operational teams. This is OK, not everything needs to be run outside the firewall. However, in order to make this truly viable the automation and orchestration systems that provide the governance and points of control to the business need to be architected to be multi-DC and multi-cloud capable.
BN: Do we need to see board level management getting more in touch with how their companies handle IT requirements?
JP: Senior management need to be a strong advocates toward the cultural, procedural, and technological shifts that the digital transformation of their business will require. In order to be competitive going forward all businesses need to accelerate their internal IT operations in order to bring more value to the business. The enterprise IT path forward will increasingly be collaborations between business requirements, development, and operational teams facilitated through automation, analytics, and distributed computing and cloud infrastructures.
Photo Credit: nopporn/Shutterstock
-

Global eDiscovery market passes $10 billion
Publié: janvier 4, 2016, 12:24pm CET par Ian Barker

The eDiscovery process of extracting data for regulatory or legal purposes is generally seen as a bit of a niche in the IT field.
However, a new study by research specialists IDC forecasts that the market for worldwide eDiscovery services reached $8.2 billion at the end of 2015. This combined with an eDiscovery software market of just over $2 billion means the global eDiscovery market has passed the $10 billion threshold.
"Increased litigation and regulation coupled with expanding use cases for eDiscovery software will continue to drive moderate growth in the worldwide eDiscovery market," says Sean Pike, Program Director in IDC's Security Products group and leader of IDC's eDiscovery and Information Governance research program. "The data solution market, however, is maturing rapidly as buyers search for automation to solve well-defined problems. To meet maturing needs, eDiscovery solution and service providers are already creating robust strategies to use existing search and analytics competencies to compete in the white hot content analytics and cognitive solution markets".
The Americas region is still the largest market for eDiscovery, and is expected to remain so, but there's been a growth in international demand over the past year. Europe and Asia are both seeing an uptick in demand for eDiscovery services. By 2019, IDC expects Europe to make up almost 23 percent of the market and Asia just over seven percent.
There's also been some consolidation in the market with service providers and technology solution companies pairing off. In addition solution providers are buying capabilities as bolt-on functionality for existing products or services, in an effort to gain or hold onto market share. Software and service provider companies see analytics companies as posing the largest threat to existing market opportunity.
The full Worldwide eDiscovery Services Forecast is available from the IDC website.
Image credit: sommthink/Shutterstock
-

The future of data center infrastructure management [Q&A]
Publié: décembre 29, 2015, 12:01pm CET par Ian Barker

Recent research from Intel suggests that, despite the availability of automated solutions for data center infrastructure management (DCIM), many businesses are still using manual procedures to do their capacity planning and forecasting.
To get an insider perspective on how managers can better exploit the benefits of DCIM products to streamline their operations we spoke to Jeff Klaus, General Manager of Intel Data Center Solutions.
BN: According to your recent research, 40 percent of data center managers still use manual processes to conduct capacity planning and forecasting. Why is this number so high?
JK: This number is indeed high, however data center managers are not happy with using manual methods today but are doing so because of a lack of good and simple solutions that can provide them accurate data to help them automate their manual processes. Among main barriers for DCIM adoption, current solutions are expensive, complex, and not easy to use by the end users, which all contribute to why this number is still very high.
BN: Does this show that the benefits of DCIM solutions are failing to get across?
JK: DCIM adoption appears to be slower than predicted and this should be a wake-up call for the solutions providers. We all would like to see broader DCIM adoption by end users in 2016, but for that to happen, DCIM vendors will need to listen to their customers, address their key concerns, including power and thermal management, and ways to automate manual processes, and do a better job in articulating and proving DCIM solution value and ROI for the end user. The vendors will also need to address general concerns related to their solutions, like lower costs, simplifying the solutions, and investing in its ease of use. We're still very optimistic about DCIM as the data center managers clearly say they need such tools, it’s just a matter of listening to them and providing them the right solution that will help them better manage their infrastructure and help them automate the manual processes that currently take up 40-60 percent of their time.
BN: Why should companies consider DCIM if they haven't already?
JK: Companies' need for DCIM is still there and challenges in managing the complex infrastructure today are not going to disappear. They will actually get more complex as IT devices continue to add telemetry. Thus, companies still need to evaluate tools and solutions that will help them better manage their infrastructure, automate manual processes, improve their capacity planning and provisioning process, improve their agility, improve thermal profile in their datacenters, identify and predict power and thermal issues, and improve datacenter efficiency. DCIM vendors are also aware to the slow adoption of their solutions and better understand the customers’ needs and concerns today. They’re constantly improving their solutions, ensuring they solve their customers’ problems, making them simpler and easier to use and maintain, and even lowering the solution cost.
BN: Are you seeing DCIM moving into new industries and how are they benefiting from the technology?
JK: I think that most DCIM vendors realize the importance of granular and accurate data as part of their solution, regardless of the industry. The solution can have great 3D layout and strong analytics features, however, if the data it visualizes or analyzes is not accurate then the result is not good or compelling for the customer. Luckily, the hardware vendors realized their customers’ needs 5-7 years ago, and since then we see more and more intelligent devices that can report accurate metrics related to their power consumption, thermals, utilization, airflow, and more. I expect that this year we'll see more DCIM vendors listen to their customers and integrate such technologies as part of their solutions, provide accurate data and analytics to their customers, and allow them to automate their current manual processes which will help the technology penetrate new industries and obtain broader adoption.
BN: What changes will we see in the DCIM marketplace in 2016?
JK: We will continue to see some consolidation in this market and expect to see a few exits and merges occur. The vendors who will stay are the ones that react to their customers' requirements and make the required changes in their solutions to fit their customers’ needs. We will also see continued price decline and, hopefully, simplified solutions that are easier to deploy, use, and maintain.
Photo Credit: dotshock/Shutterstock
-

2016 will see the rise of DDoS-as-a-service
Publié: décembre 28, 2015, 4:00pm CET par Ian Barker

We've already seen a big increase in DDoS attacks in the past year and according to the latest predictions these are set to continue and become more sinister in nature as we move into 2016.
Security specialist Corero foresees a rise in 'Dark DDoS' attacks used as various smokescreens to distract victims while other attacks infiltrate corporate networks to steal sensitive data.
Dave Larson, COO at Corero Network Security, says, "The highly sophisticated, adaptive and powerful Dark DDoS attack will grow exponentially next year as criminals build on their previous successes of using DDoS attacks as a distraction technique. The Carphone Warehouse attack in August was interesting because it was one of the first publicly reported cases of Dark DDoS in the public domain. This is a new frontier for DDoS attacks and a growing threat for any Internet-connected business that is housing sensitive data, such as credit card details or other personally identifiable information".
It also predicts a rise in DDoS-as-a-service cyber crime business models, where it's possible to pay to have victims hit for as little as $6.00 per month. This means less sophisticated cyber crime actors can readily become DDoS adversaries.
During October 2015, 10 percent of Corero's customer base was faced with extortion attempts, which threatened to take down or to continue an attack on their websites unless a ransom demand was paid. If the volume of DDoS attacks continues to grow at the current rate of 32 percent per quarter, according to Corero’s latest Trends and Analysis Report, the volume of Bitcoin ransom demands could triple to 30 percent by the same time next year.
Corero also anticipates 2016 will see ISPs come under pressure to provide DDoS mitigation services to their customers. In a survey conducted this autumn, Corero revealed that three quarters of enterprise customers would like their ISP to provide additional security services to eliminate DDoS traffic from entering their networks.
"The current status quo allows malicious traffic carrying DDoS threats to flow freely over most provider networks," says Larson. "As a result, most customers end up paying their provider for bandwidth that delivers potentially dangerous Internet content. But the technology exists for ISPs to turn this problem into a business opportunity. By providing DDoS mitigation tools as a service, deployed at the Internet edge, they can defeat this problem before it enters their customers’ networks".
More information on the changing DDoS landscape and lessons learned fron 2015’a attacks is available on the Corero blog.
Photo Credit: Duc Dao / Shutterstock
-

Expect faster adoption and more localization in a cloudy 2016
Publié: décembre 23, 2015, 4:06pm CET par Ian Barker

The growing maturity of the cloud has been one of the major trends of the past year and this is something that looks set to continue into next year.
There will be new challenges, however, and we've looked at what some of the industry's experts think the cloud will have in store for 2016.
Rohit Gupta, founder and CEO of cloud security specialist Palerra thinks APIs will gain in importance, "We expect to see cloud vendors selling APIs as new revenue streams. SaaS, PaaS, and IaaS vendors will be pressured to provide rich sets of APIs, enabling security vendors and application vendors to provide value added services".
The cloud may become more localized says Blazent's CTO, Michael Ludwig, "Increasing cloud adoption will push major cloud providers to consider regionalized service approaches due to network bandwidth concerns among enterprise customers". He also believes that self-service big data as a service (BdaaS) portals are going to make information and insights more readily available across the enterprise.
According to application performance specialist Riverbed, "More and more IT assets will be pushed into the cloud, and more users will work outside premises. We'll see more companies operate exclusively in the cloud, but enterprises will continue to leverage the hybrid cloud model with overall cloud usage increasing across the network". This will mean that organizations will need to look for solutions that provide greater visibility into performance, security and end-user experience for applications.
Marc Crespi, CEO and co-founder of OneCloud Software, expects the hybrid cloud to gain in importance, "In 2016 we are going to see accelerated adoption of hybrid cloud deployments because we will see more technologies that remove the barriers to leveraging public cloud. For example, these technologies will bring a simplified approach to creating a unified hybrid cloud management platform from disparate tools. The outcome will be a secure and scalable architecture that makes it possible for IT to add the public cloud to their 2016 plan".
Crespi also believes the cloud will change the disaster recovery industry, "With the cloud, disaster recovery doesn't take up any room and can be done affordably, simply and quickly. With the cloud, DR becomes a no brainer".
"The cloud office wars between Google and Microsoft will continue, but partners are going to need to support both suites in order to be successful, because it will become clear that both platforms serve specific market segments better than the other," says David Politis, CEO of BetterCloud. He also predicts that 2016 could become a golden age of IT. "This is the year when shadow IT will actually be embraced and seen as an opportunity to truly affect change in an organization. CIOs will be pushed to the cloud by their user populations, by their CEOs, and even by their boards as the market continues to produce success stories of organizations transforming the way they work by moving to the cloud".
Of course security issues impact on the cloud too and cyber security association ISACA predicts that, "Hackers will increasingly have cloud providers in their crosshairs, as organizations move more pervasively to cloud. This year we saw cloud providers take more responsibility for storing customer data. Because more data is shifting outside of organizations, 2016 will bring with it more attempts from cyber criminals to gain direct access to that pool of information".
Jeff Denworth, SVP of Marketing at cloud storage company CTERA expects that security concerns will have a positive effect, "IaaS will become more secure than an average private data center -- Amazon and AWS will elevate 'all-in' deal making to a feverish high. But in the meantime, just as organizations had dual-vendor strategies for IT hardware and software, this will emerge as a risk management policy for cloud operations".
The cloud then will continue to be a major factor in IT provision and we're likely to see more businesses moving away from running their own data centers to embrace an all-cloud future.
Image Credit: leolintang/Shutterstock
-

Weaponization, iOS attacks and biometrics – the security landscape for 2016
Publié: décembre 23, 2015, 12:30pm CET par Ian Barker

It's the time of year when companies inevitably turn to their crystal balls and try to predict what the coming year will have in store.
Where security is concerned there's a focus across the board on the evolving threat landscape and the tools needed to deal with it. We've brought together predictions from some of the leading industry experts.
Andrzej Kawalec, CTO for HPE Security Services at Hewlett Packard Enterprise says, "2016 will bring a shift in how organizations protect their data. New cybersecurity tools and techniques will focus on applying big data analytics and automation to the threat landscape, as well as internal users and operations. Additionally, new methods for managing user identity will cross into biometrics and across cloud platforms, and we will see the increasing adoption of advanced consumer security and identity products and services".
But whilst new techniques are used old threats will continue to be a problem. Kawalec adds, "A large and worrying proportion of attacks will continue to prey on old vulnerabilities in standard software and operating systems versions that are poorly managed and updated. New vulnerabilities in mobile devices, operating systems and applications will outstrip more traditional areas of focus".
Mobile security will continue to be a problem too. Zimperium's Joshua Drake, VP of platform research and exploitation, thinks that iOS will be targeted more in the coming year, "iOS security will take center stage with more iOS kernel exploits and jailbreaks for iOS 9.2 and 9.3. We'll also see another Airdrop-esque attack, potentially through AirPlay or Continuity/Handoff".
He also predicts that Android's continued lack of timely updates will be a problem and that more exploits will take advantage of the shared address space ASLR weakness to gain system privileges. On a brighter note Drake believes, "More vulnerabilities will be publicly disclosed due to the expansion of bug bounty programs as more companies realize the value and build the internal acumen to digest the results. Legislative changes will also have a positive impact."
The IoT is also likely to become more of an attack target for cyber criminals. "Adversaries will exploit the influx of connected devices -- everything from watches to cars to critical national infrastructure -- to obtain personal and sensitive information. IoT represents the next battleground as we move towards smarter environments and adversaries advance their tactics to take advantage of new vulnerabilities that arise," says HP Enterprise's Kawalec.
Dmitri Alperovitch, CTO and Co-founder of Crowdstrike and RSA Conference Advisory Board member, believes data will be increasingly weaponized, "Use of data as weapon will be a major problem in 2016. In the past, data has been taken, destroyed or encrypted, but increasingly we’re seeing breaches during which data is leaked publicly in order to cause significant damage to a business, reputations, or even the government (eg, Sony, Ashley Madison, etc.). Criminals and hacktivists are now stealing data and threatening to place it on public websites for others to see. In conjunction with this, hackers are building massive databases that include multiple types of data (insurance, health, credit card) to present a 'full picture' of an individual. It's one thing to have your data stolen and another to have it used against you. We'll continue to see individuals', corporations' and public entities' info used against them as a weapon in 2016".
To help combat threats Stephen Cox, chief security architect at SecureAuth believes we'll see changes in authentication methods, "Biometrics will take a larger role as a second factor as organizations grow more and more distrustful of the password. The ubiquity of personal devices with biometrics sensors will make this possible. Open standards friendly to biometric privacy, such as FIDO, will help adoption".
Cox also says that 2016 will be the year of adaptive authentication, "In many attacks we saw in 2015, attackers were not using malware, they were simply using stolen credentials to log into the environment. With organizations moving to the cloud, there will be an increasing number of authentication touch points in an organization, and those will need to be protected with technology that can rapidly identify and respond to threats".
HP's Kawalec also predicts that senior managers will become more involved in security issues, "In light of the frequent and destructive data breaches we've seen over the last two years, CEOs will be at the forefront in leading the response to a cyber breach. Increasingly we will see these breaches fought in courtrooms and newsrooms, as well as on laptops and networks. Cyber risk will be top-of-mind for boards, elevating the CISO beyond traditional IT. And with this, enterprises will be increasingly responsible for the information security of consumer data".
Steve Lowing, the Director of Product Management at Promisec shares this view and adds that, "The Endpoint Detection and Remediation Market will grow as companies try to stay ahead of threats, and companies will place an importance on encrypting sensitive data due to the rise in ransomware. Companies will have to make sure their remote employees aren't working with confidential corporate data on old, vulnerable OS releases".
Whatever the experts predict you can be sure that security threats aren't going away and that something will come along to make new headlines.
Photo Credit: Anneka/Shutterstock
-

Managing mobile apps in large enterprises [Q&A]
Publié: décembre 22, 2015, 11:54am CET par Ian Barker

More and more businesses are rushing to embrace mobile apps, but in large companies where hundreds of apps need to be rolled out this can present major headaches for administrators.
We spoke to Chris Isbrecht of IBM Security's MaaS360 team to find out about some of the challenges of scaling mobile to large enterprises, as well as how they can be addressed.
BN: Has mobile become a key part of driving greater productivity in enterprises?
CI: Mobile has become the primary way organizations communicate with employees, partners and customers. In this digital age, organizations are increasingly embracing mobile apps as a way to improve productivity and meet employee requests to seamlessly work anywhere.
Given the "app overload" with today's mobile devices, there's a well-defined need for businesses to leverage apps that stand out from the crowd. There's an appetite for mobile apps that are tailored to respective businesses, optimized for end-user engagement, integrated with enterprise and third-party data and designed for dependable access.
BN: How easy is it for large scale mobile app deployments to go wrong?
CI: Since most organizations aren't properly educated on the fundamentals of app scaling, it's particularly easy for missteps to occur. Unfortunately, organizations don't prioritize the user experience for deployments, which leads them to ignore the importance of user self-service. IT assumes that they need to be the ones always pushing the button. Businesses also tend to deploy a solution to a small pilot group and mistakenly think that will scale and support their entire population of users, but it’s far from the case.
I would recommend organizations formally poll users -- or use asset inventory -- to understand the apps their users are utilizing. For corporate sponsored apps, they should advertise them to users and customize descriptions, so employees understand the importance of apps in their specific catalogs. IT should also ensure they have group-based deployments to target specific users and enable administrators to target users with predefined bundles of applications that can be installed with a single click.
BN: What tools can businesses use to manage large scale app roll outs?
CI: When a customer starts managing a significant amount of apps, it's critical that their management tools scale for both the IT administrator and end-user. This means a company cannot get by without implementing an enterprise mobility management solution (EMM), which provides Mobile Application Management (MAM) capabilities. Attempting to do it with other tools might work with fewer apps but, not at scale.
EMM provides administrators with the ability to create a corporate app catalog, distribute corporate apps and leverage volume purchase programs. With larger deployments, supporting user groups -- through Active Directory -- drastically improves management and providers a better user experience.
With IBM MaaS360, we have customers that are successfully managing close to 1,000 applications in their corporate app catalog. It’s not just one operating system, there are companies managing over 500+ iOS and 500+ Android apps for their businesses and users.
The end-user needs a top-notch experience. When they enroll their device for EMM, they should instantly get the apps they need to be productive. If the admin leveraged Active Directory groups, apps are usually pushed down to the user automatically and they do not need to request them. If they don’t see the app they need, they need a one-stop shop to get them.
That is why a corporate app store is essential for success. Having an app store where users can search for corporate authorized apps -- while being able to review the app's rating and co-worker comments -- is a powerful, self-service tool. This keeps users happy and simplifies how they get supported apps.
BN: What role does user self-service have to play?
CI: Self-Service is vital because it increases efficiency -- by saving your support team day-to-day tasks -- and keeps users engaged and educated on the apps available to them. When a user understands what apps are available and grasps how to get them immediately, it's going to positively impact the business by saving IT a tremendous amount of time. Otherwise, IT support would be overwhelmed with hundreds of daily tasks around large scale deployments.
BN: How do user groups fit into the process?
CI: It's important to limit users' access to application catalogs because the objective is to maintain user productivity with the applications provided via the catalog. For example, we manage 75,000 devices for a large company with an application catalog that spans 1,000 public and private applications. The key for implementation is to limit the scope of apps to users based on employee function and then provide them with the tools to search, sort and filter apps that bolster productivity. Otherwise, pushing 1,000 apps to a device leads to end-user confusion, frustration and a loss in productivity.
BN: What can we expect to see in the enterprise mobile landscape in 2016?
CI: On a completely separate note, I think the industry will have to closely monitor the growth of mobile malware in 2016. This past year, we witnessed a significant uptick in mobile security incidents -- Stagefright, KeyRaider , XcodeGhost and YiSpecter just to name a few -- and it's eerily similar to the benign viruses that threatened PCs in the '90s before rocking the IT world in the early 2000's.
Remember when the ILOVEYOU virus infected millions of unsuspecting users, resulted in billions of dollars in economic damage and transformed PC security?
While the rise of mobile malware has been predicted for years, it's nearly certain that we’ll experience a mobile malware problem in the coming year. Businesses will need protection and it's crucial that they employ the appropriate, mobile threat management solution, which ties to a broader enterprise mobility management product. This will allow for the immediate detection and remediation of mobile malware -- before it's too late.
Image Credit: Sergey Nivens / Shutterstock
-

Bvckup 2 is a hassle-free backup tool [Review]
Publié: décembre 21, 2015, 9:36pm CET par Ian Barker

Let’s face it, backups are pretty boring, which is probably the reason why they often get overlooked and people find themselves staring into the abyss of lost data. Part of the reason why so many of us hate backups is that the software used often seems to overcomplicate things with lots of options that many people never use.
Bvckup 2 aims to change all of this with a backup solution that’s clean, simple to use, elegant and fast. Produced by Swiss company Pipemetrics, Bvckup 2 is small -- the installer is less than 2MB in size - but packs in a surprising amount of sophistication.
Getting Started
On installation it automatically detects whether you have a 32 or 64-bit system and proceeds accordingly. The ease of use continues on the first run when the only option you get is Add new backup. Click this and you can choose a source and destination for your save. If you want to you can stop there and simply run the backup job -- it’s as easy as that -- but there are other options if you need them.
It’s designed to be fast and starting from scratch in our tests it saved 1.3GB of files to an external USB 2.0 drive in just two minutes. After the initial backup of course it’s quicker still as it will only save changes. It uses multiple read/write requests in parallel to speed up the transfer process and is able to run intensive tasks on multiple CPU cores, but scale back its activity when the PC is under load. This means you can leave it running in the background while still using your PC for other tasks.
One of the other reasons it’s so fast is its single-minded approach. It creates a mirror from one location to another, it doesn’t do anything clever like a two-way sync or a system backup and it doesn’t encrypt or compress data along the way.
You can have it run tasks on a regular timed schedule or it can continually monitor files and folders for changes in real time. It also uses what’s called Delta copying which means it will save only the parts of a file that have changed rather than copy the whole thing each time, further improving performance. A backup can be pinned to a specific removable destination -- it tracks drives by their unique hardware ID not just the Windows-assigned drive letter -- so that it will only run when the target is available, and of course you can save to networked or cloud storage.
Business Features
All of this simplicity might make you think that Bvckup 2 is mainly for home users. However, it has a lot of features that make it attractive for enterprise users too. It can cope with multi-million item backups making it suitable for large systems and it can run multiple jobs in sequence or all at once.
When running a job it creates a backup plan, you can do a simulated run and view this without actually executing it, so it’s good for satisfying compliance requirements. It uses Windows’ shadow copy service to allow it to save locked files. Saves of deleted items don’t have to remain cluttering up the main backup, they can be moved to an archive folder from where they can be retained for compliance or deleted after a period of time.
You can set the program to run a command before and/or after the backup, so you could shut the machine down after saving for example. You can also get it to send an email on completion allowing admins to see that remote systems are being properly backed up.
As we pointed out above there’s no encryption or compression so it may not be suitable for handling sensitive data, unless of course the files you’re saving are already encrypted in which case they’re simply mirrored as they are. Lack of compression of course means your backup storage needs to match the size of the original.
Conclusion
Licences for Bvckup 2 start at $39.95 (around £26.50) for the professional version and discounts are available for volume orders. For $19.95 (£13.23) you can buy it to protect your home PC too. If you want to try it out there’s a fully functional two-week trial available to download from Bvckup2.com. Currently it’s only available for Windows and will run on XP or later.
There are more complex backup programs out there, but that’s not really the point. What Bvckup 2 does is focus on doing a single task and doing it well with minimal hassle. It’s almost enough to make backing up your system a pleasure.
Pros
- Small footprint
- Easy to use
- Very fast
Cons
- No encryption
- No compression
Review: 8/10
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Photo credit scyther5 / Shutterstock
-

Samsung Galaxy Tab S2 9.7 is a great iPad Air 2 alternative [Review]
Publié: décembre 21, 2015, 6:12pm CET par Ian Barker

Tablets are often seen as a consumer device, allowing you to update Facebook from the sofa while you watch TV, or catch up with iPlayer in bed. But they’re increasingly finding a place in the business world too, allowing mobile workers to catch up with emails or update documents on the move. They can also be a viable laptop replacement for tasks like making sales presentations.
The iPad remains popular, since it popularized the tablet format, but of late, Android devices have been catching up in terms of quality and capability. Samsung has long been one of the biggest players in the Android tablet market and its latest premium tablet, and the Galaxy Tab S2 is clear evidence of the company’s intention to park its tank on the iPad’s lawn. But how well does it succeed and what does it have to offer to tempt business users away from buying the Apple device?
In the Box
The package is fairly minimal, you get a white cardboard box and it just contains the tablet itself, with a USB cable and a mains power adaptor. Both of these are white too -- far be it from us to suggest that there’s an attempt to make this like like an Apple device here. It has a clever mains adaptor design which reduces in bulk by means of sliding down the earth pin and which makes it easier to slip into a bag or pocket. Documentation is limited to a brief Quick Start leaflet that explains the position of the main controls and how to charge the device.

First impressions when you lift it out of the box are that the tablet is nicely weighty and our review unit, in the Gold color option, looks smart with a light grey/beige surround to the Gorilla Glass screen and a shiny metal bezel around the edge. The back is smooth and has a metallic finish, which just about looks gold in the right light, though it is in fact plastic which lets down the premium feel a little bit.
What you do notice is that it’s a svelte 5.6mm thick which makes it easy to slip into a satchel or pouch. It also means it’s almost 2mm thinner than an iPad Air and 0.5mm thinner than an iPad Air 2, it also weighs over 70 grams less than the Air and 45 grams less than the Air 2. First blood to Samsung in terms of the size of the device then. The right-hand edge has the power button at the top and the volume control below it, plus a Micro SD card slot -- you need a paper clip or the little tool provided in the box to open this. On the front below the screen are the Home button, that also wakes the screen from standby and acts as a fingerprint reader, which is flanked by touch sensors for the back and recent apps functions. On the bottom edge are the USB and headphone connectors and the speakers.

The Galaxy Tab S2 is powered by an octa-core chipset with 1.9 and 1.3 GHz quad-core CPUs and has 3GB of RAM. You get 32GB of onboard storage as standard, expandable by up to 128GB via an SD card. 64GB versions are available too. Our review unit was the 9.7-inch version, though a smaller 8-inch model is also on offer. The star of the show is undoubtedly the impressive Super AMOLED HD screen which has 2048 x 1536 resolution. Other hardware features include 802.11 a/b/g/n/ac Wi-Fi which has MIMO ability for better signal reliability, plus Bluetooth 4.1 with the BLE low-energy function to prevent it from taking too much out of the battery life. You can also get a 4G version should you need connectivity when your out and about with no Wi-Fi access. It has a 5,870MAh battery which promises a decent amount of use between charges. The battery is not removable, however, so it will mean a return to the supplier should it ever need replacing.
The Galaxy Tab S2 has a pair of cameras, the rear one being 8MP -- the same as, you guessed it, the iPad Air 2 -- and the front 2.1MP -- better than the Air 2’s 1.2MP.
Start it up and you find it’s running the not-quite-latest Android 5.0.2 Lollipop, though an update to Marshmallow should be on the horizon. It has Samsung’s TouchWiz user interface rather than the standard Android one and there’s a minimum of bloatware installed. Useful apps that are included are Microsoft’s Office suite, plus Samsung’s Smart Manager to help optimize the device, and a handy multi-window feature. The latter is similar to the Windows’ Snap feature, allowing you to display two windows side by side and therefore make full use of that big screen. You also get a Briefing app that displays the latest news stories, weather, etc in an easy to access format. Most of the pre-installed stuff can be uninstalled if you don’t require it.
Business Features
The fingerprint scanner obviously makes for good security. You can store up to three prints allowing you a choice of fingers to use and there’s a password backup option should all of your chosen digits be out of action. It takes a little time to train the scanner for each print as you have to stroke your finger across the sensor several times to ensure it sees all areas of the print. Once it’s set up though the scanning generally works well, though it is sensitive to moisture, struggling to authenticate after you’ve washed your hands or been out in the rain and not thoroughly dried your finger tips for example.
The S2 comes with access to Samsung’s KNOX enterprise security suite which allows users to access confidential email and apps securely. It also allows the separation of enterprise and personal information on the device making mobile and BYOD management easier. There are a range of KNOX certified apps available via a separate store, ensuring that users can access the latest tools in a safe, secure environment.
KNOX works with most popular mobile device management (MDM) solutions so IT staff can manage devices remotely and even have the ability to wipe them in the event of theft or loss. KNOX allows the use of VPN connections to protect data in transit too.
The Microsoft Office package gives you access to 100GB of One Drive storage free for two years. This makes the S2 an attractive business tool, allowing you to access your documents from the cloud, making it easy to work from anywhere you have an internet connection and ensuring that you’re never left without a vital file.
The multi-window feature is a handy tool for business users too, making it easy to refer to documents side by side, or have a browser window open for reference while you edit a document for example. The Smart Manager app scans and optimizes the device, ensuring the best battery life and memory usage as well as cleaning up storage. It also scans for security issues, helping to protect the tablet from malware and ensure that it’s up to date with the latest patches.
All of this is configurable so you can, for example, disable optimization for certain apps that you want to get maximum performance from. The downside of this is it can be a bit of a pest, constantly nagging you with notification messages and sounds.
In Use
Powering up takes a slightly longer press of the power button than feels strictly necessary, but once the screen lights up the actual boot process is fast giving you a usable tablet in just a few seconds.
The Galaxy Tab has rounded corners, although the edges are flat rather than curved which makes it easy to hold. The 9.7-inch version does feel a bit too big to comfortably hold in one hand for long periods, the 8-inch would be better here, so you end up resting it against something. The screen is impressive and offers crisp images and good colors. It uses Adaptive Display technology that adjusts the brightness and other levels according to the ambient lighting, this means you can easily see it in bright light. It delivers smooth video playback too. There’s also a Reading Mode which lowers the brightness and makes it easier on the eyes if you’re reading long documents or eBooks.

The Adaptive Display does a reasonable job and most of the time you don’t notice it at work, though it doesn’t always get it quite right sometimes making brightness adjustments to little effect. The TouchWiz interface is nice to use with smart icons and an intuitive layout, it’s easy to live with and it doesn’t come as too much of a culture shock if you’re used to standard Android. The downside of course is that you have to wait slightly longer for operating system updates than on a system running vanilla Android. Most importantly the screen is nicely responsive to inputs and that large size screen does mean that it’s easy to use the on-screen keyboard and not worry about hitting the wrong character all the time even if you have less than delicate digits.
Sound quality is acceptable, if a little tinny, however, because the speakers are on the bottom edge they’re all too easy to muffle if, for example, you’re resting the tablet on your lap, or with your hand if you’re holding it sideways. Having the headphone socket on the bottom edge is also a bit awkward if you’re holding the S2 in portrait orientation.
Overall there are no performance issues in everyday use, apps load quickly and we didn’t experience any crashes. Battery life is around 12 or 13 hours continuous use, so with casual operation you should be able to go two or three days between charges. It also retains its battery life well when on stand-by.
Tablet cameras aren’t usually about serious photography, the size of the device means it’s not really snapshot friendly anyway, however, the S2’s are reasonably good. The rear camera produces sharp images and good color reproduction in natural light, pictures that are more than good enough to post online. There are also some clever modes including the ability to take 360 degree panoramas. It has the Pro mode found on Galaxy phones too, that lets you adjust contrast, white balance and so on. It does struggle in low light, even if you activate the HDR mode you end up with images that look a little pixellated.
This is disappointing by smartphone standards, but for a tablet it’s probably acceptable. The front camera produces slightly grainy results, especially in artificial light, but it’s good enough for video calling, which is what most business users will want it for, and the odd selfie.

Conclusion
With the 32GB Wi-Fi only version costing £399 direct from Samsung, the Galaxy Tab S2 9.7 is priced on a par with the 16GB 9.7-inch iPad Air 2. It has the same screen resolution in a lighter and thinner package, and of course more storage, so it’s clear to see what the target is here. The Samsung offers good performance in everyday use and is likely to deliver better battery life than the iPad as well.
Features like the ability to use KNOX and the inclusion of Microsoft Office make it an attractive option for enterprise users. The plastic back panel doesn’t detract too much from the quality feel of the device, and obviously it contributes to the Galaxy Tab’s light weight. The cameras are good by tablet standards and it isn’t overloaded with bloatware.
Overall Samsung has delivered a well thought out package with this device and if you were thinking of buying an iPad Air 2 it’s well worth considering the Galaxy Tab S2 as an alternative. It offers you more for your money, good performance and you won’t find yourself feeling that you’ve ended up with second best.
Pros
- Excellent screen
- Long battery life
- Fast processor
Cons
- Plastic back
- Not the latest Android
- Nagging Smart Manager
Review: 8/10
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

The enterprise trends of 2015
Publié: décembre 21, 2015, 3:32pm CET par Ian Barker

Businesses tend to be quite conservative in their approach to technology, so it's always interesting to look at what's been sparking their interest.
Identity and mobility management specialist Okta has released a new report, based on analysis of its customers, looking at the big winners and losers in the enterprise over the past year.
The fastest growing apps of 2015 are; Slack, Greenhouse, Envoy, Zapier, Windows Azure Public Cloud Services, Bamboo HR, Wrike and Lucidchart, all seeing usage across Okta's customer base grow at over 200 percent. Slack in particular has seen run away adoption levels, growing 667 percent in 2015.
The report also shows strong cloud growth in the recruitment industry, with the number of Okta customers using recruiting apps up by 99 percent, beating the growth in project management and messaging apps. Greenhouse in particular has seen 580 percent usage growth in the 12 months from November 2014.
Multi-factor authentication is gaining ground too, with traditional security questions like mother's maiden name in decline. Instead providers are turning to devices like phones and smartwatches as well as biometric identification. Okta's data suggests an increase in the use of both hard and soft tokens too.
In addition it finds that responsibility for security is moving away from IT, with a 30 percent growth in the number of identity management purchase decisions where chief security officers were involved. Away from software it seems that enterprise tablet use has plateaued, declining slightly over the last year. Okta suggests that 2016 will be a make-or-break year for enterprise tablets. The report says, "In order for them to survive, manufacturers need to seek out and invest in strategic partnerships to add more computing power, better apps and features designed for productivity."
Finally the report suggests we may be entering an age of bring your own business (BYOB), where by using public loud services it's possible to run a small to mid-sized business with no infrastructure, no physical locations, no warehouses, no servers and no software. The company's data shows that shows that the median number of off-the-shelf cloud apps at companies has grown by 33 percent year-on-year, Amazon Web Services has grown at 123percent, and Microsoft Azure Cloud Services at 216 percent.
More information on the report is available on the Okta blog.
Photo Credit: Sergey Nivens/Shutterstock
-

Human behavior is the biggest threat to company security
Publié: décembre 21, 2015, 12:10pm CET par Ian Barker

A new survey of cyber security professionals from information management company Nuix shows that businesses are placing greater emphasis on insider threats.
The report reveals that 71 percent of respondents report that they have an insider threat program or policy, and 14 percent say that they allocate 40 percent or more of their budget to insider threats.
"The findings in this report are of no surprise -- they represent the same issues and concerns that we're advising our customers on every day," says Keith Lowry, Nuix's Senior Vice President of Business Threat Intelligence and Analysis. "First, there's greater awareness of insider threats thanks to the public profiles of Chelsea Manning and Edward Snowden. It’s also easier to steal information; for example, you can copy key files onto a thumb drive in seconds. And finally, sadly enough, theft of internal records has become culturally more acceptable".
People were reported to be 'almost universally' the biggest weakness in information security, ahead of technology and processes. Of the respondents that reported to have an insider threat or policy, 70 percent offer employee training to minimize risk. "The company employs intelligence teams that study different aspects of communications, user activity, social media, suspicious activity and other details," said one respondent.
Worryingly, 31 percent of respondents say that they don't know what people who have access to crucial data actually do with it. The cloud is an area of concern too, with 86 percent of respondents agreeing that it creates unique concerns including loss of visibility into the management of data and lack of regulatory compliance.
The full report is available to download from the Nuix website.
Image Credit: Brian A Jackson / Shutterstock
-

Survey reveals managers and developers split on real time data analysis
Publié: décembre 18, 2015, 12:14pm CET par Ian Barker

According to the results of a new survey, 84 percent of CIOs believe their organization can analyze data in real-time, however, only 42 percent of developers agree with that statement.
This difference of opinion is one of the findings of the study by in-memory data platform specialist VoltDB. Where 91 percent of CIOs, IT managers and developers do agree is that real-time streaming data analysis can have a positive impact on their company's bottom line.
Other findings are that 48 percent of developers believe the biggest obstacles to responding and acting in real time are budget and internal resource constraints, compared to only 18 percent of CIOs that feel the same way.
Only 35 percent of respondents define real-time as actions occurring in less than a second or in milliseconds, compared to 32 percent of respondents that define it in minutes or lack a real-time standard altogether. In addition 56 percent of respondents believe real-time streaming data applications have different requirements from big data applications.
"While there's increasing recognition that competitive advantage depends on how quickly you can use data to make your business smarter, more engaging, responsive and interactive, there's a gap in understanding how to effectively deploy the solutions that will have the most impact," says Peter Vescuso, vice president of marketing at VoltDB. "With the industry’s only purpose-built architecture for fast data, VoltDB powers mission-critical applications with new levels of features, functionality and performance, helping customers realize more value from the enormous amounts of live data entering their organizations".
More information on the results is available on the VoltDB blog and there's a summary of the findings in infographic form below.
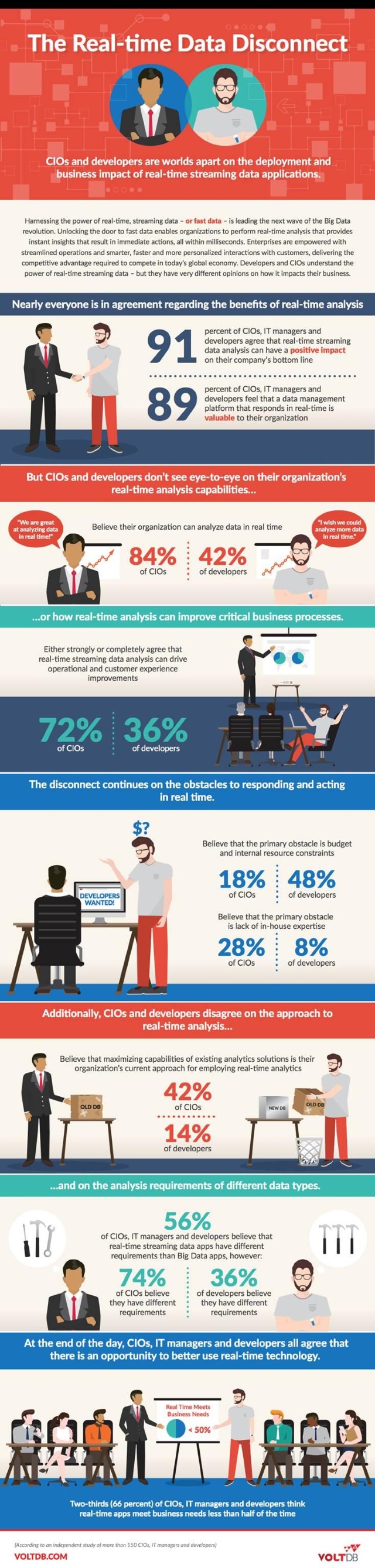
Image Credit: watcharakun /Shutterstock
-

The Internet of Things is becoming part of consumer's daily lives
Publié: décembre 17, 2015, 5:54pm CET par Ian Barker

According to the latest Digital Trends Report from Adobe Digital Index (ADI) the Internet of Things is gaining a foothold in more and more people's lives.
The report is based on 22 billion visits to branded websites and over 20 million social engagements across Facebook, Twitter, Instagram and other sites. Also included in the report is survey data based on 400 US consumers who own either a smartphone or tablet.
The survey finds that 50 percent of respondents have interacted with home IoT devices, and that 15 percent own a smart device such as a thermostat, smart home system or smart smoke alarm. Social buzz indicates that ‘Google On Hub’ is the most popular IoT device.
"Mobile, and specifically larger-screen smartphones, are enabling a lot of behaviors," says Joe Martin, senior analyst at ADI. "People are really happy with how they're working. It's definitely making things easier. It also leads to the kind of data-driven world we live in now. You can look up your Nest thermostat and see how it’s being used, and you adjust it with your mobile phone and collect data about how things are working within your home".
Other findings are that browsing and searching are increasingly being done via personal assistant applications. Facebook M is expected to take the lead here, despite its limited beta, it's receiving four times more social buzz than any other digital assistant available today. Siri is currently ranked as the number one virtual assistant, but Facebook M is expected to overtake it once it’s broadly available.
Despite the move to digital assistants, the browser wars go on and Microsoft Edge is expected to gain traction with tech enthusiasts. Although only 1.4 percent of browser visits currently come from Microsoft Edge, with Chrome and Safari dominating browser visits, positive social media buzz for Microsoft’s browsers has increased by 75 percent. Edge has the highest adoption rate and is expected to gain traction with tech enthusiasts, especially as businesses roll out Edge to employees.
ADI also predicts that with nearly 40 percent of consumers likely to buy a smartwatch in the next six months, smartwatches are expected to overtake fitness trackers as the most common wearable technology. Social buzz indicates that the Apple Watch is the smartwatch most likely to be purchased.
You can find out more about the report's findings on the Adobe blog.
Photo credit: Odua Images / Shutterstock
-

Desktop and mobile habits of employees revealed
Publié: décembre 17, 2015, 4:49pm CET par Ian Barker

Do you know how your employees are accessing content within your business? Enterprise file sharing specialist Egnyte has analyzed all of the unstructured data from its customers, no matter what device, storage, or apps they use, to discover the latest trends.
Having looked at this data over the last 12 months, they uncovered some interesting facts about the diversity of employee interactions with their company content.
Findings include that only 15 percent of users utilized both desktop and mobile apps to access content. This suggests that employees are highly specialized, using mobile or desktop according to their roles in the company. Workers in the field likely to only use apps on their mobile devices (24 percent), whereas office-based employees are likely to only use apps on desktop (61 percent).
What is perhaps more surprising is that 63 percent of users utilized two or more operating systems (Mac, Windows, Linux, etc.) when accessing content. This indicates a willingness and ability to work with a variety of tools and devices and that employees need to have choices for how they get their work done and what tools they can use.
Google Chrome dominates the business sector with a whopping 60 percent of activities done via the browser. Internet Explorer trails at only 20 percent and Safari unloved at only five percent. However, 40 percent of employees actually use two or more browsers when accessing their content.
You can find out more about the results on the Egnyte blog and there's a summary in infographic form below.
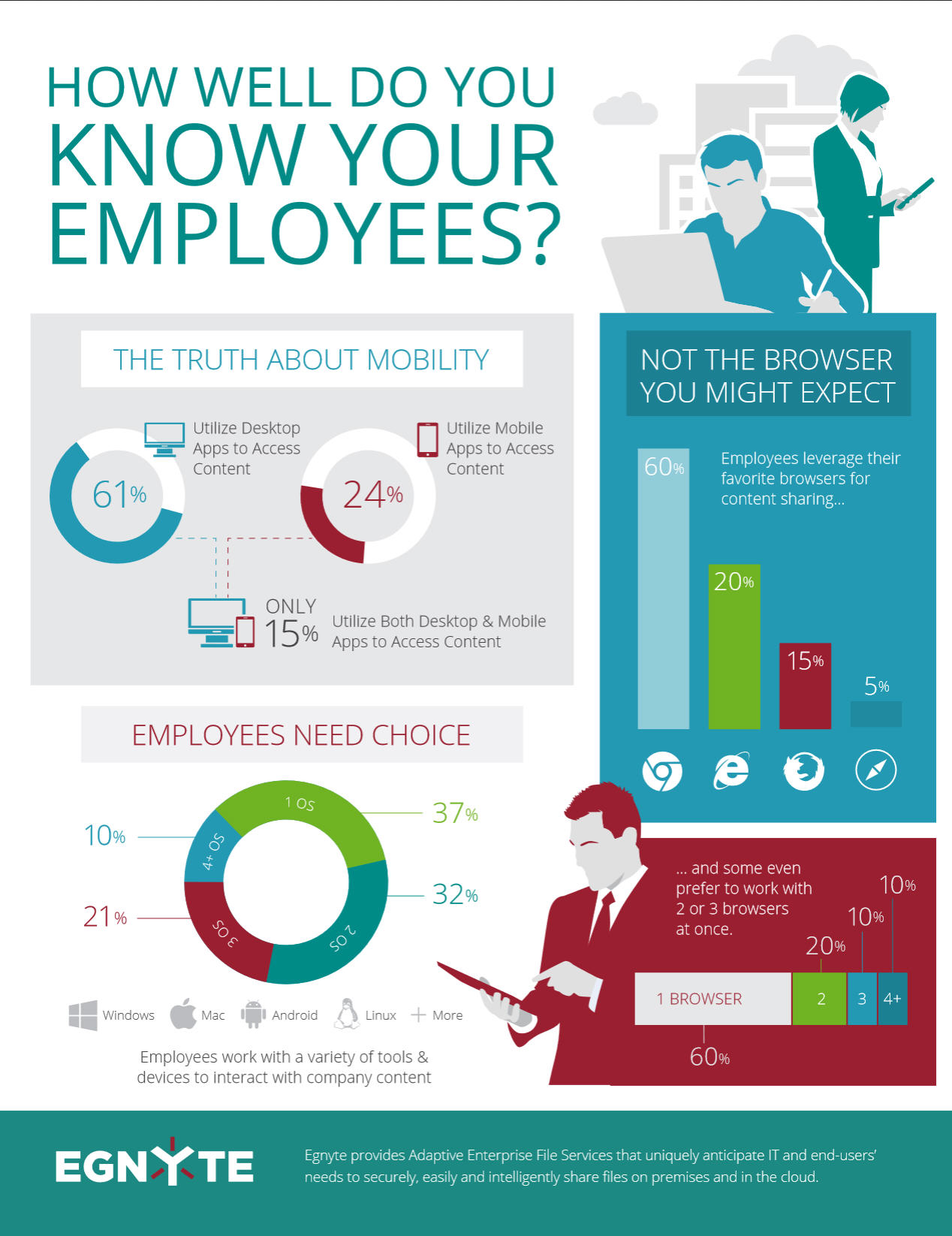
Image Credit: Goodluz / Shutterstock
-

New survey reveals global Android usage trends
Publié: décembre 17, 2015, 4:12pm CET par Ian Barker

Mobile marketing company Celltick has mined its user interaction data to produce an Android Usage Trends report revealing insights on how users around the world use their mobile phones.
Among the key findings are that the vast majority of smartphones in Asia (71 percent) and the Middle East and Africa continue to be configured with English. Facebook might be ubiquitous, however, Facebook Messenger is only popular on low-end phones, amongst higher-end handsets, Skype is the most common application installed.
Other interesting findings are that smartphone users in India interact with their phones more than twice as often as their European counterparts. Indian users unlock or glance at their phone up to 36 times an hour, compared to a peak of 16 times an hour in the US.
New versions of Android often take time to expand in key mobile growth regions, with only six percent of users in South Asia currently deploying it. Brazilians spend almost three-quarters of their time on Wi-Fi networks, which is a reflection of their urban lifestyle. By contrast, the Japanese use cellular connections 65 percent of the time, thanks to cheap and fast cellular data network investments alongside slow Wi-Fi deployment.
Interestingly Americans aren't as addicted to Wi-Fi as they appear, spending only 55 percent of their time using Wi-Fi and the rest on cellular networks.
"Analyzing Celltick's rich behavioral data was a productive exercise, leading to some fascinating conclusions about how, and why, people are using Android smartphones today," says Ramgopal Vidyanand, VP Marketing and Business Development at Celltick. "With these insights, players across the mobile ecosystem will be better empowered to reach and engage mobile users more meaningfully, creating new revenue streams while helping to maximize existing ones".
The full report is available to download from the Celltick website.
Photo credit: Bloomua / Shutterstock
-

P2P file sharing and its impact on business
Publié: décembre 17, 2015, 12:22pm CET par Ian Barker

When you think of peer-to-peer file sharing you probably bring to mind services like Kazaa and Limewire that were among the early sites allowing users to share media, or of more recent operations like Pirate Bay.
But while it's easy to think of P2P in terms of individuals downloading music or movies, a new report from security rating company BitSight reveals that it’s a problem for businesses too.
BitSight looked at 30,700 organizations and observed file sharing activity in 23 percent of companies using the BitTorrent protocol. Much of this activity is likely against corporate policies -- although there are no published metrics on what percentage of companies prohibit P2P file sharing, many companies do have explicit rules against it.
Among the findings are that 43 percent of application files and 39 percent of games files shared contained malicious software. Grand Theft Auto V and Adobe Photoshop lead the respective lists of top torrented games and applications, the top five in each category being:
Top Torrented Games:
1 Grand Theft Auto V
2 The Sims 4
3 Mortal Kombat X
4 FIFA 15
5 The Witcher 3Top Torrented Applications:
1 Adobe Photoshop
2 Microsoft Office
3 Microsoft Windows 8.1
4 Microsoft Windows 7
5 Microsoft Windows 10The report also finds that there's a correlation between botnet activity and file sharing activity. And it reveals that more than a quarter of companies in the government, energy/utilities, and education industries have observed BitTorrent file sharing activity in the last six months.
"While the sharing and downloading of copyrighted or pirated content and applications over peer-to-peer typically violates most corporate policies, the behavior continues to occur at a high rate. Movies and games often come to mind when organizations think about P2P file sharing; however, the majority of infected applications that we uncovered were either Adobe Photoshop, Microsoft Office or various versions of the Microsoft Windows operating system," says Stephen Boyer, co-founder and CTO of BitSight Technologies. "Our analysis found a high degree of correlation between organizations participating in P2P activity and system compromises via malware infections. The high malware infection rates suggest that organizations with file sharing activity are more susceptible to machine takeover. File sharing activity can serve as one of many key risk indicators and should be considered not only internally, but also when assessing vendor risk, conducting M&A due diligence, and underwriting cyber insurance".
You can get more detail in a full copy of the report from the BitSight website.
Photo credit: Imagentle / Shutterstock
-

Hillstone adds extra security layer for AWS customers
Publié: décembre 16, 2015, 5:01pm CET par Ian Barker

When moving applications to the cloud it's easy to fall into the trap of believing that security can safely be left to the provider.
For Amazon Web Services customers there's now an extra layer of security on offer from Hillstone Networks. Hillstone CloudEdge is deployed as an Amazon Virtual Private Cloud (Amazon VPC) gateway to provide an additional layer of security protection.
It integrates with multiple security services, including firewall security, application visibility and identification, VPN, IPS, QoS, SLB, and attack protection, to ensure security for cloud deployments.
"Hillstone CloudEdge provides strong security protection for various cloud environments," says Lingling Zhang, Vice President of Marketing & Business Development of Hillstone Networks. "Our customers want easy-to-use solutions that are available for immediate purchase and deployment. The introduction of Hillstone's CloudEdge demonstrates our focus on offering comprehensive security solutions that power and promote the customer business".
Features include dedicated cloud security isolation, all traffic flowing across the Amazon VPC is inspected and unauthorized access attempts are prevented based on user and application identification and control.
Hillstone supports Amazon VPC service maintenance through the integration of a snapshot backup of CloudEdge, enabling rapid restoration of virtual firewall services with the most current configuration, in the event of an appliance failure or system crash. It also provides control based on applications, offers comprehensive reports on Amazon VPC traffic, and helps AWS users achieve the lowest cost for network security.
Firewall protection includes north-south traffic inspection to provide the VPC network with dedicated security isolation via policy and granular access control, plus QoS, VPN, IPS and server load balancing to guarantee business continuity.
Standards-based site-to-site VPN connections can be established between the corporate local network, branches and the AWS virtual service. In addition server load balancing helps businesses establish an Amazon Elastic Compute Cloud (Amazon EC2) instance.
You can find more information about CloudEdge on the Hillstone website.
Image Credit: Maksim Kabakou/Shutterstock
-

New breach detection solution alerts enterprises to insider threats
Publié: décembre 16, 2015, 4:28pm CET par Ian Barker

For enterprises and government departments the biggest threats can often come from within the organization rather than outside it.
Detecting these insider threats can be difficult which is why security company Eastwind Breach Detection is launching a new platform that uses rich data, behavioral analytics, and threat intelligence to pinpoint anomalous behaviors even before they're classified as breaches.
"Government and enterprise IT professionals today fight a complicated battle," says Paul Kraus, CEO and founder of Eastwind Breach Detection. "Between API-driven apps, distributed work teams, and a global army of hackers that never sleeps, black hats constantly find new and creative ways to break into networks. Eastwind arms security teams with an intelligent defense: a way to reliably detect hackers in the network before they act".
By storing and mining more than a year's worth of rich network metadata, Eastwind can examine not only current network conditions, but continually analyze historical data against updated threat sources to find breaches that would have otherwise gone unnoticed.
A customizable set of dashboards displays suspicious activity, such as pings by known malicious IPs, while a brief weekly summary of activity and network health saves users the time needed to compile the big picture themselves.
It can be deployed on private clouds with custom data enrichments, lookup rules, and custom application scanning. It can also monitor network activity for other purposes, such as acceptable use policy enforcement and compliance. Eastwind can also detect the possible transmission of stolen data such as payment details. Smart alerts mean fewer false positives allowing admins more time to investigate real issues.
Gregg Frohman, VP of Business Development at Eastwind points out, "Protecting the perimeter remains critical to a defense-in-depth strategy. However, we read daily how these solutions alone are getting thwarted by ever-changing tactics. Pre-breach prevention and post-breach detection go hand-in-hand, and we are partnering with a growing number of end-point protection providers to increase each other's overall effectiveness".
You can find more information on Eastwind Breach Detection and sign up for a free trial on the company's website.
Image Credit: Andrea Danti/Shutterstock
-

BUFFERZONE launches advanced threat protection for Windows 10
Publié: décembre 16, 2015, 3:12pm CET par Ian Barker

Employee use of email and web browsers is still one of the most common ways that businesses suffer from cyber attacks, which underlines the need for effective protection.
Endpoint security specialist BUFFERZONE is announcing its product's support for Windows 10 to protect organizations upgrading to the latest OS from advanced threats, zero-day attacks, drive-by downloads and phishing scams.
BUFFERZONE's technology works by isolating internet applications in a secure, virtual container which prevents employees from inadvertently downloading malware and putting the organization at risk. It prevents malware from reaching the endpoint by running browsers, email and other internet applications, as well as removable media, in their own virtual environment. Threats are contained rather than relying on detection process that may not be 100 percent accurate, protecting the endpoint from infection and helping to guard the rest of the network.
"The most vulnerable party in information security today is the user endpoint, making the extra layer of protection increasingly necessary," says Israel Levy, CEO of BUFFERZONE. "We are happy to provide BUFFERZONE support for Windows 10 to meet the pressing need for advanced protection from malware, including ransomware, drive-by downloads, and phishing scams".
More information on BUFFERZONE's endpoint solutions for business is available on the company's website.
Photo credit: Anton Watman / Shutterstock
-

New DaaS platform aims to boost B2B marketing performance
Publié: décembre 16, 2015, 1:05pm CET par Ian Barker

Marketers are always keen to understand customer purchase intentions. But whilst there are many tools aimed at building consumer intelligence can business to business organizations benefit too?
Washington DC based True Influence thinks so and is launching a new data-as-a-service solution called InsightBASE, which monitors and curates online behavioral signals. It aims to allow B2B marketers to engage with prospects even before they directly identify themselves as being in the market.
"The B2B buying journey begins with online research," says Brian Giese, CEO of True Influence. "With InsightBASE, marketers now have the entirely new B2B capability of monitoring visits to third-party B2B websites. It provides a new view and a new opportunity that marketers never had access to before, and marketers are enjoying an average improvement of 400 percent in campaign conversion results".
InsightBASE works by monitoring online activity by individuals visiting business websites from their corporate domains, capturing the web pages visited and the content of those pages. Comparing the activity level of target companies over time allows the software to identify surges in interest using select keywords.
The intelligence can be integrated with a company's existing CRM or marketing automation systems such as Oracle Eloqua, Marketo, and Salesforce, allowing marketers to launch campaigns automatically and target companies that meet a certain interest level criteria.
The information can be used to accurately target display advertising on websites and in trade publications. It can also enable the sending of timely, targeted email marketing.
InsightBASE uses a subscription pricing model based on the number of accounts monitored. More information is available on the True Influence website.
Image Credit: donskarpo / Shutterstock
-

Removing the IT roadblock to selecting business technology [Q&A]
Publié: décembre 16, 2015, 11:09am CET par Ian Barker

Choosing software and cloud solutions for business is a difficult task and getting it wrong can have serious consequences. We've all heard horror stories about money being wasted on systems that either don't deliver or are left unused.
So, how can organizations make better decisions on systems purchases? We spoke to Venkat Devraj, CEO of technology selection specialist, SelectHub, to find out.
BN: There's a perpetual tug-of-war between business managers and IT departments when it comes to technology selections -- who should take the lead?
VD: Your question highlights a key issue for IT in many organizations: are they seen as a helpful, strategic partner or just a roadblock? How many end-users and business unit leaders view IT as a trusted advisor -- someone who understands their pain and more importantly, is ready to do something about it in a reasonable time frame? Engaging with IT often means imposing a drawn-out process comprising service desk tickets, questionnaires--and sitting through meetings with IT personnel who rarely share the sense of business urgency.
BN: So you're saying avoid the IT department whenever possible?
VD: For the sake of your technology investments, it's not advisable to bypass your IT department. However, regardless of who's initiating the selection or leading the project, for IT to be brought into the loop early and often, it needs to act as a strategic facilitator rather than a control group.
Rather than being obsessed with arcane concepts such as architectural compatibility and relying on archaic selection tools such as Word docs and Google spreadsheets, they need to evolve the underlying process with a prescriptive workflow which can be driven by end-users in self-service mode. This involves a major rethinking of the way IT typically operates -- if they want to remain relevant and provide real business value to their organizations.
BN: How does IT reinvent itself to become more relevant?
VD: IT needs to be relentless in eliminating administrative overhead and make its presence felt as an agile service broker and a provider of relevant market context to help the business units make the right decision. Some progressive organizations are already going down this path via a disciplined Technology Selection Management (TSM) methodology.
In our experience working with over 2,000 IT selection projects across a variety of industries and company sizes, any notion of cookie-cutter selection approach does not work. In these complex events, the overall process needs to be separated into a sequence of steps such as functional requirements gathering, technical requirements gathering, vendor/product short-listing, and all validation steps -- right through to financial due diligence, and contract negotiation. Each step should be viewed discretely and led by project managers from IT or end-user business units, depending on the scope of that step and the net beneficiaries.
Expecting a single group to represent and lead the entire process results in various incorrect assumptions and compromises being made, which ultimately jeopardize the success of that investment.
BN: Has the rise of the cloud changed the procurement landscape, allowing line managers to bypass IT for example?
VD: Yes, and we are seeing it grow at a non-linear pace. In 2013, when we first launched, we saw over 90 percent of our users were IT personnel. Now that percentage has come down to 50 percent, with over 40 percent of projects completely bypassing IT -- IT is not even a passive stakeholder in the process!
BN: How can the process ensure that security and compliance requirements are met?
VD: When offering technology selection as a service within their organization, IT should seed the TSM workflow with their security, compliance and architectural requirements upfront so it doesn't become an afterthought.
Other control groups such as finance and procurement can do the same thing by incorporating vendor due diligence and contractual requirements based on specific parameters such as scope of purchase, departments being impacted and size of budget.
BN: With all these pre-set requirements, aren't we back to IT being a roadblock?
VD: Quite the opposite. By building those requirements right into the process backbone, end-users are not held hostage to IT and finance personnel not being available to vet the process thus eliminating latency and re-work. Any selection event initiated by end-users would seamlessly encompass relevant functional and technical criteria that are uniformly applicable to a project of that kind.
BN: Do senior managers need to adjust their mindset to take account of hybrid and cloud environments?
VD: End users primarily care about functionality and time to value. Cloud-based deployments shrink implementation time lines and operational costs significantly. So there is a great deal of migration happening to the cloud. Gartner has predicted that on-premise software will decline from 34 percent last year to 18 percent by 2017. Given that the cloud has become the first choice for deploying applications, it will continue to disrupt the traditional stodgy technology selection processes that IT and procurement managers have relied on, creating a greater urgency to evolve towards an agile TSM practice.
Image Credit: wavebreakmedia / Shutterstock
-

Ergotron WorkFit-T: An affordable alternative to a standing desk [Review]
Publié: décembre 15, 2015, 7:03pm CET par Ian Barker

Sitting down, so medical professionals tell us, is bad for you. As a species we’re designed to stand up and move about rather than sit in front of a screen. The trouble is, modern office-based work doesn’t really lend itself to this hunter/gatherer lifestyle.
The answer for some people is to have a standing desk so that you can bash away at your keyboard from a vertical position. It may not match the thrill of the hunt, but at least it gets you off your backside. The trouble is, purpose built standing desks can be eye-wateringly expensive, especially some of the sophisticated motorized models, and you have the problem of where to accommodate an extra piece of furniture.
The latest product from Ergotron provides a solution, the WorkFit-T sits -- or rather stands -- on top of your existing desk or table and allows you to choose whether to work from a sitting or standing position.
What Is It?
It comes in a choice of black or white finishes with a built-in keyboard tray and has the option of a monitor riser so that you can adjust the height of your screen separately. Risers are available for both single and dual monitor set ups and screens up to 30-inches in size, compatible with the VESA MIS-D mounting standard with 75 or 100mm hole centres.
The first thing to note about the WorkFit-T is that it’s no flimsy flat pack. It’s a serious, heavyweight (our review unit was delivered on a pallet) piece of kit with engineering Brunel would be proud of. The riser is a chunky piece of kit too, weighing an extra 3.6Kgs on top of the 26Kgs of the WorkFit-T itself -- don’t go standing this on your auntie’s old card table with the wobbly legs!
It comes pre-assembled so you’re ready to go once you’ve liberated it from the packaging. It’s supplied with some braided cable sheathing to keep things neat and tidy and keep stray wires away from the lifting mechanism. Fitting the optional monitor riser requires a little bit of screwdrivering but nothing too strenuous. There’s a maximum weight limit for equipment of 35lbs (around 16Kgs), which should be more than enough for everyday use.
It uses a counterbalanced mechanism that moves up and down but stays within the footprint of your desktop. There’s minimal effort involved in changing the height, you simply release the brakes at either side and lift gently then it rises until it hits the top of its travel or you put the brakes on again. Lowering it is equally easy, just a gentle downward pressure once the brakes are off, so you can switch easily between sitting and standing. There’s 15-inches (38cm) of total movement, so most people should be able to find a comfortable working height.
In Use
Once in position, whatever height you have it set at, it provides a solid, stable work surface that you can lean on while working without it tipping or dropping in height. Adjustment is simple and quick, it’s a two-handed job as you have to release both brakes simultaneously, but that’s no hardship and it helps keep your fingers away from the moving parts. You need to make sure your cables are long enough so that they’re not stretched taut when the Ergotron is at the top of its travel. You’ll probably need to invest a few pounds in USB and maybe video cable extensions.
The optional monitor riser gives you an extra five inches (13cm) of height adjustment on the screen, as well as allowing you up to 30 degrees of tilt so you should be able to find a comfortable working position. The mount can be rotated too if you like to switch between portrait and landscape modes.
There’s plenty of space on the work surface so you have room for phones, papers, cuddly toys and whatever else you choose to surround yourself with when working. The surfaces themselves have a lightly grained finish rather than being completely smooth which makes for a good mousing environment. The keyboard tray is a generous size so there’s room to place a small mouse mat next to your keyboard if you wish.
It does raise the height of your work surface slightly when you’re sitting down so you’ll need to fine tune your seating position to get the recommended 90 degree elbow bend. Working standing up takes a bit of getting used to, so it’s good that the Ergotron lets you quickly switch between sitting and standing as you can gradually wean yourself away from your chair for longer periods. A word of warning for open plan office users here, if you listen to music while working you’re much more inclined to move to the beat when standing up!

Conclusion
At £310 (ex VAT) for the basic unit in black, plus an extra £68 for a monitor riser kit, the WorkFit-T isn’t cheap, however it’s less than a complete new standing desk. It has a 5-year warranty but you get the impression it’s built to last several lifetimes, and what price do you put on your -- or your employees -- health?
You can find out more about the benefits of standing desks on the JustStand.org website and more about Ergotron products on the company’s website.
Pros
- Easy adjustment
- Solid build
- Range of monitor options
Cons
- Pricey
- May require longer cables
- Tends to make you dance in the office
Company Release
PriceITProPortal
ReviewErgotron £310 9/10 Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Addressing new challenges in enterprise mobile management [Q&A]
Publié: décembre 14, 2015, 5:25pm CET par Ian Barker

Although many enterprises are keen to deploy mobile apps for their workforce and to support BYOD and extended working, they've often been held back by traditional app distribution options. Historically this has required IT organizations to bring devices under management -- for corporate owner, corporate liable, and BYOD devices -- which can put a brake on enterprise mobile app deployments.
To find out how new approaches can allow data to be secured at the app level, we spoke to Mark Lorion, Chief Product and Marketing Officer at mobile app management and security company, Apperian.
BN: Is a lack of flexibility in app distribution holding back the implementation of mobile strategies?
ML: In the past, Enterprise Mobility Management (EMM) platforms were the go-to for enterprise mobility initiatives. But because they typically require that a Mobile Device Management (MDM) 'profile' be installed onto a users' device, it requires IT to bring the device under management before any apps or content can be deployed to the user. This isn't really an issue for corporate-owned devices, but with the move to BYOD many users are not willing to allow the IT organization to install MDM profiles and control their personal devices. Similarly, many organizations want to enable their business partners, contracted workers, dealers, and other non-employees with mobile apps and those users often will not -- or cannot -- have their devices under management. In other cases, a mobile device may be under management by another IT organization (could be another company or another agency in the public sector) and therefore can only receive enterprise apps from one source (because mobile devices can be under management from one MDM profile.) These scenarios reflect users who are unreachable using traditional EMM platforms.
A big shift that has occurred in the mobility industry is the move toward app-level security and management. This best-of-breed mobile app management (MAM) approach applies policy to each app and enables the app to be deployed with appropriate security and management controls so that MDM is not required to ensure the safe delivery and use of the app. When policy is applied at the app level, instead of directly on the device, enterprises can maintain security and management control without having to issue corporate devices, or install policies on users’ personal devices.
BN: How does applying security policy via the app rather than the device help?
ML: Applying security policies to apps enables fine-grained levels of control, security and management capabilities, without requiring that device be under management. A truly effective approach to applying the policies to each app can be done via a dynamic 'wrapper' that will apply desired policies directly to the app itself and without requiring that developers make code changes or use SDK's. For example, app-level policies can allow IT to lock access to an app, or wipe data on a specific app, or require two-factor authentication for app access, and more – without MDM being on the device.
One huge benefit of this approach is that the app can be deployed anywhere -- with or without MDM being on the device. This means those unreachable users highlighted above are now within reach of corporate mobile apps. Another benefit is that it allows the organization to apply many additional layers of security and control over the app, making the app suitable for deployment in highly secure settings.
All of this increases the number of potential users who can be served and drives the adoption of mobile apps while reducing the burden on app administrators. This allows organizations to focus on what matters most – building critical apps for their employees and getting them into the hands of 100 percent of users.
BN: Does this improve the experience for employees too?
ML: Yes. Modern workers tend to move back and forth between personal and work activities on one device. By allowing them to do so without encroaching on their personal device and data is becoming an expectation, especially with the proliferation of BYOD. Employees can feel confident in their ability to work from any location, without giving their employers access to the entirety of their personal information.
The app-level approach to security and management is less intrusive, but it also creates a more secure app and one that offers a smoother user experience. If an app is updated on the back-end, policy can push that update to a user directly, without them having to proactively go look for a download. IT can also gain remote access to help troubleshoot any challenges with the app. There’s no learning curve, or foreign platform users need to access apps through. It really creates a more native experience, similar to the way users experience consumer apps.
BN: Is this only for larger enterprises or does it scale to smaller businesses too?
ML: If an organization has an app that is important to securely get into the hands of all possible users, then a MAM-based approach to app security and deployment should be considered -- regardless of company size. In the past, larger organizations tended to be the early adopters of this approach, mainly because they were the early developers of mobile apps for enterprise use. With the costs and complexity of developing mobile apps decreasing while expectations of mobile-enablement by workers increasing, organizations of all sizes will face these requirements.
Virtually every worker has a smartphone today -- and many of them are doing work in places other than a traditional office where they'd have access to more business technologies. Apps that streamline workflows that can have a significant impact at SMBs, too, when it comes to business-critical processes such as sales teams closing deals or writing contracts on-the-go.
BN: What safeguards are in place to deal with lost devices, employees leaving the company, etc?
ML: The app-level security and management offered by a best-of-breed MAM platform should provide a number of controls to handle these scenarios -- all without requiring the use of MDM on the device. There are a variety of access controls, such as passcode access or 2-factor authentication that can be activated to keep an app from launching. There are 'data wipe' policies that allow centralized administrations or security personnel to remotely delete all data contained in the app or they can force updates to the app, which render it useless. These approaches and others can be activated remotely and without requiring that the devices are under management. This provides tight security controls over just the organization's apps without affecting a user's personal apps or data.
Image Credit: Sergey Nivens / Shutterstock
-

Will 2016 be the year of Windows 10 in the enterprise? [Q&A]
Publié: décembre 14, 2015, 11:34am CET par Ian Barker

Businesses are notoriously reluctant to make the leap to a new operating system. But by the start of 2016 Windows 10 will have been around for six months, so can we expect next year to be the start of its taking off in the enterprise?
We spoke to Deepak Kumar, Founder and CTO of configuration management specialist Adaptiva to get his views on the march of Windows 10 and more.
BN: Will we see Windows 10 adopted by enterprises in a big way next year?
DK: Yes, we will. We've already witnessed Windows 10 take off quickly, surpassing both Windows XP and OSX. Consumers are adopting Windows 10 extremely rapidly as they generally have no revenue stream at risk, IT costs to budget, compatibility testing to conduct, regulation compliance to consider, security policy to enforce, etc. Enterprises have to calculate all of those factors, and determine if the time and cost of migrating right away is worth it. Microsoft took their eye off the ball with Windows 8, but with Windows 10 they got it right. Not only have they paved a much smoother upgrade path, but they've made a great OS that delivers business-critical capabilities. Enterprises want to upgrade because of what Windows 10 can do for them in terms of integration, security, compliance, productivity and other new capabilities. I've been running Windows 10 since beta and it's rock solid.
BN: Is this going to drive demand for migration solutions to streamline deployments?
DK: Absolutely. IT directors are struggling to figure out how they’re going to deploy Windows 10 on thousands -- or hundreds of thousands -- of computers without breaking the budget or taking forever. Traditional enterprise deployment methods require global infrastructure, expensive consultants, and massive administrator effort. Even with those resources, migrations can take years as evidenced by the fact that some enterprises are still running Windows XP. That is no longer acceptable. The pace of business has accelerated dramatically. Global businesses are demanding new technologies that allow rapid, high-volume deployments that don't require a vast server infrastructure, additional WAN capacity, or massive professional services expenditures. Enterprises will seek infrastructure-free solutions that protect the WAN and automate nearly everything. This will help them cut years off their Windows 10 migration timelines, and realize enormous cost savings as well.
BN: Will this provide a boost to the overall PC market?
DK: This is something we'll see more visibly in the enterprise market specifically. Mobile devices are changing the world, there's no doubt about it. However, most of what people do in the enterprise requires a dedicated system. Have you ever tried to create a complicated spreadsheet on your phone? You can do it, but not very fast. Most people need keyboards and full-size screens to be productive. Also, the cost of laptops and PCs is unbelievably low. In some cases, you can get a highly functional computer for nearly the price of a cell phone. With the epic failure of Windows 8, many companies have held back from migrating off the aging Windows 7 on a widespread basis. With Windows 10, enterprises feel certain they have a modern OS that is a safe investment for the future. Microsoft said Windows 10 will be the last version of Windows and has moved to service branches giving businesses additional confidence. As Windows 10 grows in the enterprise, so will enterprise PC sales.
BN: We keep hearing about how big data analytics is going to revolutionize system management, is this just hype?
DK: It's not hype. Current integrations of big data analytics solutions are often unwieldy, leaving perishable business insights undiscovered in disconnected data silos. The solutions are complex and require enormous resources just to set up. This leaves a huge door open for vendors to provide big data solutions that are more cost effective and practical. Systems management vendors are particularly well positioned to do this, because they already have access to distributed data and key pieces of platform to conduct big data analysis. Where companies can't cost-justify a pure-play big data technology, this type of solution could provide a viable option for getting actionable intelligence from globally disparate big data.
BN: With higher demand for data can we expect to see bandwidth usage become more regulated in order to control costs?
DK: According to IDG, the average enterprise network will expand bandwidth at a 28 percent compound annual growth rate through 2017 due to a variety technologies including cloud computing, mobile everything, and video. IDG reports that by 2017, enterprises that do not control network use risk requiring up to 3 Mbps per user of bandwidth, more than 20 times the average needed in 2012. This sets the stage for companies to find ways to limit bandwidth use. Businesses won’t cap user data on a broad scale like cellular companies do, but they will develop policies and processes to curtail bandwidth use. At the same time, enterprises will seek to deploy more bandwidth-efficient technologies to reduce the amount of bandwidth needed.
Photo credit: rvlsoft / Shutterstock
-

The challenges of endpoint management in a hybrid environment [Q&A]
Publié: décembre 11, 2015, 11:53am CET par Ian Barker

As the IT world is changing it's not uncommon for companies to be using a mix of cloud and on-premise solutions. These hybrid environments offer a best of both worlds option but do present problems when it comes to managing resources.
To find out how managers can address these challenges and what tools they can use to help, we spoke to Dana Epp, CTO of IT management specialist Kaseya.
BN: The cloud is meant to make things easier, but do hybrid environments inevitably lead to greater complexity?
DE: A lot of the complexity comes from the fact that when people start adopting the cloud IT isn't always involved. CRM systems like Salesforce can make life easier for the sales team but it becomes complex for IT if they're not part of the decisions. Over the last five years or so there are so many new tools available in the cloud and they're easy to buy with just a credit card so you don't have to be in IT to get hold of cloud services.
This growth of 'shadow IT' means that you end up needing to implement tools and strategies to watch for these behaviors and take back control. The most important part of this is not so much the systems as the data they hold which is a corporate asset and needs to be protected. The complexity comes from understanding how you can get visibility and control, whatever tools you’re using. You also need to ensure that you have the ability to recover when things go wrong.
BN: What do businesses need to be aware of when selecting cloud partners?
DE: The most important thing is to realize that not all cloud partners are the same. It's vital to look at a potential partner's data center management to ensure they're providing redundancy, security, backup, and that they have the right staffing to handle the management of the systems. But having the ability to run a data centre doesn't necessarily make you a good cloud partner. Things like being able to maintain the data and have access to it are vital to companies looking at cloud services.
You need to look for providers that have geographical redundancy, but you also need to be aware of any compliance restrictions on where data can be stored. If you’re in Europe for example you may not want your data stored in the US. Some cloud providers will have multiple data centres around the world, but it’s important to understand what happens when the system fails over, does geographical redundancy mean your data may end up somewhere it shouldn't be?
You also need to look at what due diligence providers carry out on their systems and infrastructure. The big three, Google, Microsoft and Amazon, spend a lot of time and have dedicated staff to make sure they meet compliance obligations of different standards. One of the values of going to the cloud is that you can leverage that expertise.
BN: How much of the move to hybrid environments is about changing the management mindset?
DE: It's difficult for some organizations, especially at board level, to be willing to give up control. What they don't always understand is that you're not abdicating responsibility, you're delegating it to a service that can provide you with a better, more flexible and more efficient service than you could run in-house.
You can also spin up more resources quickly when needed, so it becomes an operational expense rather than a capital one. That mind shift needs to happen and it allows you to get the job done better and faster. For example mining companies are able to use public cloud for a short period of time to do an intense amount of work, but if those servers were on-premise they would sit idle for nine or ten months of the year. In many ways cloud is just an extension of your infrastructure management. The key is to make sure the right people have access when they need it regardless of where the data is located.
BN: Is it possible to get a 'single pane' solution that allows enterprises an overview of all their systems?
DE: To accomplish that your technology selection and infrastructure have to be well aligned. If you're picking solutions that don't integrate and don't allow information to be shared you'll never get that single pane. At Kaseya we make sure we follow the standards that are there so that we can communicate with the devices, the data and the people so that we have that visibility.
But of course the world is always shifting, you have IoT devices all of which have IP addresses and which need to be managed so that there's no risk to the organization. Managing everything from a single pane, therefore, is a constant challenge.
BN: Can we expect to see more focus being placed on analytics and automation in systems management?
DE: The more data that's available the more we can make informed decisions about what's going on. We can create a holistic report that can show business owners what type of applications they're running. The next stage is to automate that so that if, for example 13 percent of employees are using Dropbox, management can decide if that's an activity they want to permit and, if it's not, disable and uninstall the software automatically. You can also automate the ability to sign in to applications like Salesforce and manage the users.
It helps when employees leave the organization too because you can automate the provisioning of cloud applications, reassign licenses and so on. Similarly with new starters, if the HR system is talking to other systems then an employee can automatically be added to the right groups and given access to the apps and cloud services needed to do their job, so IT doesn't have to be involved in manual provisioning.
BN: Does that also mean companies can save on licensing costs?
DE: Yes, if you have that visibility into applications you can de-provision licenses and reassign them. That's a potentially huge cost saving in larger organizations, by managing software and cloud use effectively they could be saving thousands of dollars every month.
Whilst it's possible to do everything in the cloud, in reality most enterprises will have a hybrid approach. Companies should be able to use the same governance and policies to deal with all of their systems. That can save them money and deliver a better experience for the user.
Image Credit: jannoon028 / Shutterstock
-

UK software engineer salaries lag behind those in the US
Publié: décembre 10, 2015, 5:17pm CET par Ian Barker

London has long been a global tech hub, but a new study indicates that salaries for software engineers in the UK capital are lagging behind those of major tech centers in the US.
The study of salary data from tech marketplace Hired shows that, compared to San Francisco and New York, UK companies actually offer the lowest average salaries for software engineers.
When adjusted for cost of living, an engineer earning an average salary in San Francisco would make the equivalent of £86,000 ($130,000) a year, while an engineer earning an average salary in New York would make an equivalent of £81,000. By contrast, in London the average developer salary is £54,000 a year, making San Francisco and New York salaries are 37 percent higher and 33 percent higher respectively.
"Our data science team spent many hours digging into this information to find out not only how different tech hubs like New York, San Francisco and London stack up against one another in terms of salary, but also how that translates into quality of life in those markets", says Lindsey Scott, Director of Communications writing on the Hired blog. "While most people know that software engineer salaries are particularly high in San Francisco, they often don’t fully understand how the cost of living impacts those figures".
Perhaps unsurprisingly the data reveals that, generally speaking, the larger the company the greater the salary offered. For early stage startups that can't compete with larger companies on salary, perks like flexible working hours or the ability to work remotely are an important part of the overall package to help attract candidates. Many of the companies featured in the report cite additional perks, with 18 percent offering flexible working hours, while 16 percent free lunches.
The report also shows that although London businesses are hiring talent in the UK, they are also very willing to recruit from across Europe. Some 28 percent of UK job placements were from other parts of Europe or from the US, with San Francisco-based candidates receiving the highest number of offers from London companies. European candidates were drawn primarily from Spain, Sweden, and France.
More information can be found in the full report which is available to download from the Hired site.
Image Credit: Duc Dao / Shutterstock
-

Humans reclaim the web from the bots
Publié: décembre 10, 2015, 12:44pm CET par Ian Barker
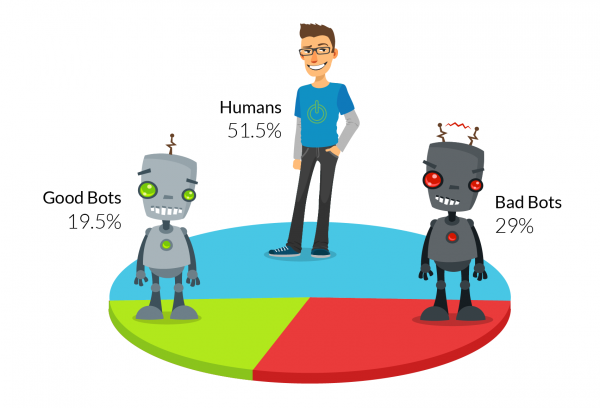
For the first time in five years, humans were the ones responsible for the majority (51.5 percent) of all online traffic, up from just 38.5 percent in 2013.
This is according to the latest Imperva Incapsula Bot Traffic Report which shows that good bot traffic decreased, from 31 percent in 2013 to 19.5 percent in 2015, while bad bot traffic remained static, at around 30 percent.
What's the difference between good and bad bots? Good bots assist the web's evolution and growth. Their owners are legitimate businesses who use bots to assist with automated tasks, including data collection and website scanning.
Bad bots are the malicious intruders that swarm the internet and leave a trail of hacked websites and downed services. Their masters are the bad actors of the cyber security world, from career hackers to script kiddies. In their hands, bots are used to automate spam campaigns, spy on competitors, launch DDoS attacks or execute vulnerability scans to compromise websites on a large scale.
The decline in good bot traffic isn't simply due to greatly reduced activity by a few groups of bots. The report shows that it's across the board, with 442 of 484 good bot clients displaying negative growth or an extremely low growth of less than 0.01 percent. Individually, none of them declined by more than two percent. Moreover, out of 42 good bots that displayed increased activity, only one displayed an increase of more than one percent.
Another interesting finding is that bot traffic to small and medium sized websites is increasing while that to larger and more popular sites is down. Human traffic on the other hand is up thanks to an increase in the number of people able to access the web and the fact that we're staying online for longer.
Analysis of bad bot traffic shows that while 'impersonators' -- bots designed to bypass security solutions -- are up, other types are down. This includes a decline in spam bots, put down to the fact that Google penalizes hosts and sites that benefit from spam links.
You can see more of the report's findings in infographic form below.
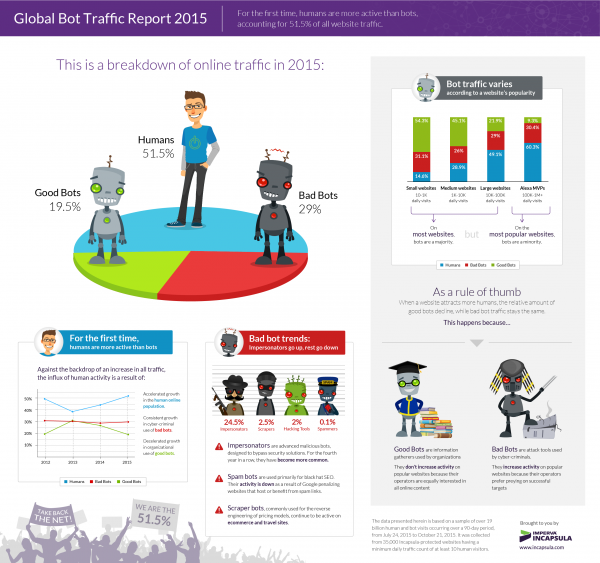
-

Retail data breaches threaten customer loyalty
Publié: décembre 10, 2015, 11:53am CET par Ian Barker

A high percentage of Americans would change their shopping habits if their favorite retailer was hit by a data breach according to a new study.
Data security specialist Vormetric commissioned the survey over 1000 US adults from Wakefield Research which found that for 85 percent of respondents the significant personal consequences that can result from a breach would cause them to find a new place to shop.
Factors that would cause them to take their business elsewhere are, if money was taken from their checking account (67 percent), unauthorized charges appearing on their credit card (62 percent), leakage of personal information (57 percent), and damage to their credit score (54 percent).
"It's been two years since major retail attacks made 'data breach' a household word", says Tina Stewart, VP of marketing at Vormetric. "The revelation of a major data breach following the Black Friday weekend in 2013 was the starting point for two record years of data breaches that have followed. Events since then have demonstrated just how much financial and reputational havoc a data breach incident can wreak on beloved brands".
The results underline the fact that retailers need to take security seriously or risk losing their customers. Protecting data by meeting minimum compliance requirements is no longer sufficient to guard sensitive data. Many recent retail breaches have occurred at organizations that were certified compliant with highly ranked standards like PCI-DSS.
"The time has come for retailers -- and indeed all organizations -- to embrace a data-centric mindset and change their approach to how their data is protected", says Sol Cates, CSO at Vormetric. "With attackers now using multi-phase approaches to breach organization's perimeters and networks, a stronger focus on better securing company data where it is stored is required. Encryption and access controls are now front-line defenses for defending data at rest. With encryption becoming increasingly easier to implement, there is no excuse for not protecting your organization’s sensitive data, regardless of where it resides".
More information on how retailers can protect themselves is available in the 2015 Insider Threat Report on Vormetric's website.
Image Credit: Sergey Nivens / Shutterstock
-

Bringing business intelligence to big data
Publié: décembre 9, 2015, 6:03pm CET par Ian Barker

Extracting useful information from business data used to mean waiting for the IT department to run reports. Increasingly though there's demand for users to be able to extract information themselves.
The latest company to join this trend is Israel-based Anodot which is aiming to disrupt the static nature of today's BI using patented machine learning algorithms for big data.
Anodot's Anomaly Detection solution is data agnostic and automates the discovery of outlying events in all business and operational data. The platform isolates issues and correlates them across multiple parameters to find and alert on incidents in real time.
"I experienced the data analysis lag problem first hand as CTO for Gett", says Anodot's founder and CEO David Drai. "As a mobile taxi app, SMS text orders were dropped by the carrier but it could take up to three days to spot critical issues and fix them, costing tens of thousands of dollars per incident. That's where I got the idea for Anodot -- to employ the latest advances in machine learning to detect performance problems automatically and in real time, eliminating the latency".
Features of Anodot Anomaly Detection include real time operation, and the ability to work with any type of metric or KPI and scale to any big data volume. Using proprietary patented machine learning algorithms it correlates different metrics to help identify the root causes of problems and eliminate alert overload.
Its simulation capability optimizes alert planning and reduces false positive alerts as well as cutting out the need for time-intensive manual analysis. As a result non-specialists can gain the insights they want with clear visualizations that help any user to understand what the data is showing them.
The company has received $3 million of venture capital funding to accelerate its product roadmap and expand its sales activity, focusing on the ad tech, e-commerce, IoT and manufacturing industries in the US and EMEA. You can find out more and request a trial of the software on the Anodot website.
Image credit: David Gaylor / Shutterstock
-

All businesses share the same cloud security concerns
Publié: décembre 9, 2015, 4:19pm CET par Ian Barker

All organizations have the same key concerns regarding the security of their data in the cloud, according to a new report.
The study by security-as-a-service specialist CloudLock reveals that every organization shares five primary cloud cyber security concerns, regardless of industry. These are: account compromise, cloud malware, excessive data exposure, over-exposed personally identifiable information (PII) and payment card industry (PCI) data, and collaboration.
Excessive sharing is the main worry, with 83 percent of technology organizations concerned with ensuring access permissions to sensitive data are granted appropriately. This is followed by the K-12 education sector (77 percent), financial services (75 percent), healthcare (72 percent) and manufacturing (70 percent). Notably less focused on excessive sharing are retail (66 percent), government (60 percent) and higher education (59 percent).
Manufacturing industry shows the least concern for ensuring access permissions are granted appropriately for PII such as users' IDs, dates of birth, etc, (27 percent) and PCI (39 percent). Only 10 percent of technology firms are focused on protecting PII, but 41 percent are concerned with PCI. Higher education is the most concerned with protecting PII (77 percent) and PCI (61 percent), with the huge database of student records, as well as credit card and banking information tied to large spending areas such as tuition, administrative and research funds.
"While all industries are certainly evolving to make security a priority, each industry faces different risks and concerns that need to be addressed in a very specific and nuanced manner", says CloudLock CEO and Co-Founder Gil Zimmermann. "We're hoping this latest data will provide guidance for those who are wondering how they stack up against their peers, and possibly make them take notice of where they are falling behind when it comes to protecting critical information and assets."
The full report, with more information on specific industry sectors, is available to download from the CloudLock website.
Image Credit: Maksim Kabakou/Shutterstock
-

Apple hardware gains popularity in the enterprise
Publié: décembre 9, 2015, 3:07pm CET par Ian Barker

Apple devices are becoming an integral part of today's enterprise environment, with nearly all enterprise IT professionals saying that their internal teams provide support for Mac, iPhone and iPad devices.
This is among the findings of a survey amongst IT professionals by Apple device management company JAMF Software. It shows that 96 percent of teams support Macs, 84 percent iPhones and 81 percent iPads.
The survey shows that user preference is the number one reason for the increased adoption of Mac (81 percent) and iOS devices (84 percent). As organizations continue to implement user choice programs, more and more employees are choosing Apple devices for work because they're what they prefer in their everyday lives. Secondary factors driving Apple adoption in the enterprise include security advantages and increased productivity features, among others. IT professionals surveyed also agree that Mac (75 percent) and iOS (82 percent) devices offer more security compared to other computer platforms.
There have been increases in the usage of Mac (68 percent), iPhone (46 percent), and iPad (36 percent) devices in 2015. Macs are easier to manage than other computer platforms according to 64 percent, and 67 percent say that Mac will cut into the PC's market share over the next three years. In addition 78 percent of those surveyed say that the iPhone and iPad are easier to manage than other mobile device platforms
Big companies are seeing the effect of using Apple hardware on their bottom lines too. “Every Mac that we buy is making and saving IBM money,” says Fletcher Previn, IBM's VP of Workplace-as-a-Service, speaking at the 2015 JAMF Nation User Conference.
"This research highlights what we at JAMF have been seeing for some time: user preference is driving the rise of Apple in enterprise and education", says Dean Hager, CEO of JAMF Software. "While a lot of the attention of Apple's success has been on its iOS devices, the survey results also show that Mac will continue to replace the PC at an unprecedented rate because it empowers users to be creative, productive, and happier in their jobs".
The full Managing Apple Devices in the Enterprise survey report for 2015 is available to download from the JAMF website.
Image Credit: rvlsoft / Shutterstock.com
-

SMBs lack the resources to protect themselves from cyber attacks
Publié: décembre 9, 2015, 1:05pm CET par Ian Barker

Only 37 percent of SMBs believe that their organizations are fully equipped to handle IT security according to a new survey.
The study by security company Webroot reveals that in most small to medium businesses, IT teams are expected to handle all cyber security management and concerns. IT employees at almost one in three companies (32 percent) juggle security along with their other IT responsibilities, which leaves them limited time to cope with security tasks.
Lack of budget is an issue too, with 60 percent of respondents believing their organization is more vulnerable to attacks because they don't have the resources to properly defend themselves. Almost half of respondents (48 percent) think their company is vulnerable to insider threats, from employees for example. In addition, 45 percent believe they are unprepared for threats from unsecured internal and external networks, such as public Wi-Fi, and 40 percent for unsecured endpoints, such as computers and mobile devices.
There is evidence that businesses are aware of the problem, 81 percent of respondents say they plan to increase their annual IT security budget for 2016, by an average of 22 percent. They're also very open to other strategies for improvement, with an overwhelming 81 percent agreeing that outsourcing IT solutions (including cyber security) would increase their time available to address other areas of their business.
"SMBs play a pivotal role in helping drive the economies of all the countries polled, but past experiences have taught them they face an uphill battle when it comes to cybersecurity", says George Anderson, director of product marketing at Webroot. "This perception must change. A viable alternative to the 'go at it alone' standard is an outsourced approach in combination with Smarter Cybersecurity solutions that are easy to install and manage remotely, and provide real-time protection against modern threats".
You can read the full report on the Webroot website.
Imaged Credit: soliman design / Shutterstock
-

Panda Internet Security 2016: Good protection, small performance impact [Review]
Publié: décembre 8, 2015, 5:34pm CET par Ian Barker
We already know the importance of defending endpoints to keep business systems secure. The latest release of Panda Internet Security offers protection for PC, Mac, iOS and Android devices, and aims to provide a wide spectrum of security in an easy-to-use package.
For businesses looking to help staff protect their BYOD devices or smaller organizations looking for desktop protection, what does it have to offer?
Features
There are the main elements you’d expect to see in any internet security package, namely antivirus and firewall protection. With Panda you also get a Process Monitor which keeps an eye on other software for suspicious activity, and a Safe browsing feature to block suspicious URLs.
In addition there’s USB protection to scan flash drives when they’re attached, and Wi-Fi protection that can warn you if you’re about to access an insecure network. Data Shield can protect selected files and folders by granting programs permission to access them. When you install new software a wizard will prompt you to set what it’s allowed to access, this helps protect against ransomware type malware that seeks to deny access to data.
There’s also Application Control which allows you to control which programs are allowed to run, and parental control allows you to block specific websites or categories for certain users.
The program has a Rescue Kit feature that you can use to create a bootable flash drive to recover an infected system. It lets you run an advanced virus scan too and access Panda’s Cloud Cleaner. A virtual keyboard lets you enter sensitive information like banking passwords on the screen if you’re worried about keyloggers.
There are various licence options allowing you to protect one, three or five devices and there are versions for Windows, Mac, Android and iOS systems. What you don’t get in this version of the product is online backup, encryption, file shredding or system tune-up tools. If you want those you need to spend a bit more on Panda Global Protection.
In Use
So, lots of features on offer, but what’s it like to use?
Installation is fast on a Windows PC, taking just a few minutes, and it doesn’t require a reboot. If you have Windows Defender running it automatically gets deactivated as part of the process. Panda does run a scan of your system after installing but this happens in the background and has minimal impact on the system’s performance.
It installs a Panda toolbar to your browser to help protect your surfing. A minor irritant is that it wants to set Yahoo as your default search engine and MyStart as your home page. You can uncheck the boxes to opt out, but whilst this might be acceptable in shareware it doesn’t sit well in a commercial product that you’ve put down hard cash for.
You’re prompted to set up an online account as part of the installation. This lets you review your licence information, see which products you have active and download the software for other devices.
Once up and running, click the subtly panda-shaped taskbar icon and you’re presented with a smart, tiled interface that’s evidently Windows 10 inspired. This is friendly and simple to operate, if you need to dig deeper -- to set firewall rules for example -- there are Settings buttons on screens where more options are available.
In operation Panda is mostly unobtrusive, the firewall pops up asking for a decision occasionally -- such as when a new program tries to connect to the web -- which is not something you see so often with security packages theses days. Otherwise it will only bother you when installing new programs, plugging in flash drives, or if it detects a problem.
The antivirus module lets you perform a full scan of the system, this takes a while but is probably worth doing the first time you use the software. You can also choose to do a Critical Areas scan which looks at memory, Windows folders, etc, or a Custom scan which lets you select what to examine. You have the option to shut down the PC after a scan has finished so you can use it as part of your end of day routine. The Critical Areas scan took around 20 minutes on our Windows 10 test system.
 The Android app includes a useful Privacy Auditor which tells you which of your apps are allowed to access media files, SMS messages, the device camera and so on, useful for spotting potentially unwanted behaviour. Mobile versions also have anti-theft protection that allows you to lock or wipe the device remotely via your online account.
The Android app includes a useful Privacy Auditor which tells you which of your apps are allowed to access media files, SMS messages, the device camera and so on, useful for spotting potentially unwanted behaviour. Mobile versions also have anti-theft protection that allows you to lock or wipe the device remotely via your online account.Conclusion
Panda Internet Security 2016 costs £49.99 to protect three devices for a year, which is on a par with the BullGuard product we looked at a couple of weeks ago. It’s pretty comparable in terms of the features it offers too. It lacks BullGuard’s rating of online search results but that’s not a huge loss. It ranks slightly better in recent independent protection tests too.
As with most consumer-oriented security solutions the scary options are hidden away in the name of ease of use, but they’re available if you need them. Panda Internet Security 2016 delivers a straightforward endpoint solution and won’t significantly harm system performance.
Pros
- Fast installation
- Minimal system impact
- Clean interface
Cons
- Unwanted options on installation
- Slightly intrusive firewall
Company Release
PriceReview Panda Security £49.99 7/10 Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

ThoughtSpot gives companies a self-learning search capability
Publié: décembre 8, 2015, 4:58pm CET par Ian Barker
Enterprises have lots of data that could be used to improve their operations and profitability, but it can often prove hard to access. By contrast, users are accustomed to being able to instantly find information on search engines like Google with minimal effort.
Business intelligence company ThoughtSpot aims to bridge this gap with the launch of ThoughtSpot 3, a major update to its search-driven analytics platform.
The software has three key components, DataRank is a machine learning algorithm that sorts and presents data recommendations as you type. It guides users to the right results based on data properties and the collective intelligence in the company, helping people to get answers faster.
AutoJoins automatically graphs data sources and joins tables in real-time to calculate answers across previously siloed databases. Finally PopCharts creates instant graphs and charts as you type in ThoughSpot's search box. PopCharts chooses from over a dozen new chart types and automatically presents the best one for each search. These results can be saved to a dashboard for future reference.
"People want to make smart data-driven decisions as quickly as possible. They have come to expect it in their personal lives. Two billion people use search everyday to get instant answers when it comes to booking travel, trading stocks, and finding jobs -- activities previously managed by experts. With ThoughtSpot 3 we’re providing the same service to business professionals looking to make smarter decisions every day at work," says Ajeet Singh, co-founder and CEO of ThoughtSpot. "With the release of ThoughtSpot 3, every human now has the power to search to analyze all of their company data as easily as they use search in their personal lives".
ThoughtSpot 3 is available now and you can find more information on the company's website.
-

New application delivers predictive personalization for Oracle users
Publié: décembre 8, 2015, 4:08pm CET par Ian Barker

Marketing organizations are always keen to understand more about their customers so they can accurately target their efforts.
Machine intelligence-based marketing platform Boomtrain is launching a new application on the Oracle Marketing AppCloud offering predictive personalization to help businesses form better relationships with their customers.
Oracle Marketing Cloud provides data-driven solutions to simplify marketing resources and deliver more personalized customer-centric experiences. Combined with Boomtrain's platform users can easily develop deeper understandings of individual consumers based on how they interact with website and email campaigns. By applying this first-party data to Boomtrain’s predictive algorithms, companies can recommend the content or product that each individual user is most likely to engage with.
"Forward looking companies are moving away from mass marketing to develop stronger, more meaningful relationships with individual consumers," says Nick Edwards, co-founder and CEO of Boomtrain. "Boomtrain provides a strong complement to Oracle Marketing Cloud and will help mutual customers automatically predict the optimal content or product recommendation across any marketing channel".
Boomtrain is available now from the Oracle Cloud Marketplace.
Image Credit: iQoncept / Shutterstock
-

Retailers aren't doing enough to protect their data in the holiday season
Publié: décembre 8, 2015, 3:42pm CET par Ian Barker

Retailers believe they're doing a good job of protecting their sensitive data, but may in fact be ignoring major security holes.
This is among the findings of a retail risk report from threat protection company Bay Dynamics, based on a survey of IT decision makers in 125 large US retail organizations.
Problems include employees, particularly temporary seasonal staff, using shared accounts. While a majority of respondents say they know everything their permanent and temporary employees are doing on their corporate systems, 21 percent say their permanent retail floor workers and 61 percent say their temporary floor workers do not have unique login credentials for corporate systems. This means those workers are using shared accounts -- which include the same login credentials. As a result, IT and security teams don't know everything their employees are doing on their corporate systems.
More than a quarter of respondents said they don’t know if their temporary employees have ever accessed or sent data they shouldn't have. Also 37 percent of respondents say they can't identify which systems their temporary employees have accessed.
Almost half (47 percent) of respondents acknowledge that temporary workers are somewhat risky to their organization and more than a third view them as a high risk. 66 percent also view their permanent workers as somewhat risky.
In spite of these worries, the majority of retailers gave themselves a 6 or higher -- on a scale of 1 to 7, with 7 being the most proactive -- for identifying critical assets that must be protected, detecting theft or data leakage, and controlling employee access to critical assets.
The report concludes, "Decision makers may think they are securing the enterprise, but as our survey reflects that is not the case. In today's cybercrime era, where criminals are highly organized and will take extraordinary measure to commit crime -- whether that's landing a job as a temporary holiday worker simply to get access to a retailer's network or attacking the retailer through a third party vendor by posing as a legitimate vendor employee -- retailers need 100 percent visibility into what each employee and insider is doing when accessing key corporate systems and data assets".
The full report is available on the Bay Dynamics website.
Photo Credit: mtkang/Shutterstock
-

New solution helps businesses offer single sign ons
Publié: décembre 8, 2015, 1:52pm CET par Ian Barker

As businesses grow and expand their online presence, they can end up with customers needing lots of different logins for blogs, support portals, forums and more. This can lead to frustration among users and mean that businesses lose sight of their system interactions.
Software company Inversoft is launching a solution to this problem in the form of Passport. This not only allows a single sign-on between applications, games, forums, help desks, user accounts and other offerings, but also gives companies a comprehensive view of user activity.
Implemented via an API and made for use on desktops, tablets, smartphones and other devices, Passport is based on OAuth 2.0, the most advanced authorization standard, and adds a number of proprietary features. Among these is the ability to mute, ban or suspend users if necessary, or reward them with special offers or promotions. It also lets customers specify their preferred language so companies can respond with appropriately translated emails and messages.
"For years, companies have been dealing with the limitations of SAML and LDAP protocols for single sign-on. Passport moves the industry forward dramatically," says Brian Pontarelli, founder and CEO of Inversoft. "It offers features and capabilities most other solution providers would never dream of. Best of all, Passport requires only one database to drive a company’s entire user management function".
Passport also features native integration with CleanSpeak, Inversoft's tool for profanity filtering and content/user moderation. A full menu of auditing and analytics tools supports deep-dive queries and pre-set reports are also available for critical performance metrics.
To maximize security, Passport supports two-factor authentication. As an on-premise solution it conforms to internal security protocols, avoiding the risk presented by hosted, multi-tenant alternatives.
Passport is available now and there's a free developer plan that can handle up to 50 users, allowing businesses to try it out. More information is available on the Inversoft website.
Image Credit: Gunnar Pippel/Shutterstock
-

MapR launches global streaming for big data
Publié: décembre 8, 2015, 1:17pm CET par Ian Barker

The growth of the Internet of Things is providing businesses with ever larger volumes of data, that in turn places ever greater demands on the technology needed to process it.
Big data specialist MapR is launching its MapR Streams solution which connects data producers and data consumers across shared topics of information and across the globe.
It offers a converged data platform that integrates file, database, stream processing, and analytics to accelerate data-driven applications and address emerging IoT needs. This allows organizations in any industry to continuously collect, analyze and act on streaming data.
With the continuous analysis of big data businesses can improve their responsiveness to critical events. It can, for example enable advertisers to provide relevant real-time offers, help healthcare providers improve personalized treatment, or retailers optimize their inventories.
"Bringing together world-class Apache Hadoop and Apache Spark with a top-ranked NoSQL database and now continuous, reliable streaming with global scale is a huge step forward in enabling enterprise developers to create the next-gen apps using big data," says Anil Gadre, senior vice president, product management at MapR Technologies. "MapR continues to execute on its vision of making it easy for enterprises to get the competitive edge from big data by bringing together all of the essential components".
Unlike other approaches that create data silos across multiple systems and lack enterprise-grade features and global replication, MapR natively integrates data-in-motion and data-at-rest in one converged platform. As a result, it enables developers to create new, innovative applications that reduce data duplication and movement, lower the cost of integration and maintenance associated with multiple platforms, and deliver faster business results.
More details are available on the MapR site and you can sign up to a webinar on December 10 which will demonstrate the power of the platform.
Image Credit: bleakstar / Shutterstock
-

Businesses are in the dark on cloud costs and usage
Publié: décembre 8, 2015, 12:24pm CET par Ian Barker

Whilst there are increasing levels of trust in running critical applications in the public cloud, many organizations struggle when it comes to providing details of their cloud costs and consumption.
This is according to a survey for analytics specialist Cloud Cruiser, carried out by Dimensional Research, which interviewed almost 350 IT professionals who attended the Amazon Web Services re:Invent shows in 2014 and 2015.
It finds that 85 percent of respondents believe it's valuable to share cloud consumption metrics with the business. Unfortunately, 42 percent continue to find it difficult to properly allocate public cloud usage and costs.
"The public cloud is delivering measurable business benefits as companies find ways to manage and mitigate security and compliance requirements. This drives more organizations to place business applications in the cloud, expanding public cloud usage beyond development and test to that of a flexible business asset," says David Gehringer, Principal, Dimensional Research. "However, IT is expected to provide reliable services and ensure cost transparency so the business can make fact-based decisions about the ROI on services. In 2016, we expect to see more business applications in the cloud and an increased focus on cost transparency comparing those of internal resources and external public cloud services".
In the past the public cloud has been used mainly for sandboxing and development. The survey shows that this is still the case, with 62 percent of respondents using it for this in 2015, but use for enterprise applications is growing and has increased from 38 percent last year to 46 percent this year.
Plans to use alternative clouds are also down. In 2014 only 27 percent planned to use no other cloud apart from AWS, this figure is up to 43 percent in 2015.
More information on the survey and on how businesses can take better control of their cloud usage is available on the Cloud Cruiser website.
Image Credit: Brian A Jackson / Shutterstock
-

Barbie says hello to more security flaws
Publié: décembre 4, 2015, 12:28pm CET par Ian Barker

Hot on the heels of last Friday's news of the potential of the Wi-Fi enabled Hello Barbie doll to be hacked, new research has uncovered security issues with the mobile app associated with the doll and with its connections to cloud servers.
Application security specialist Bluebox working with independent researcher Andrew Hay has revealed that the app can be modified to reveal confidential information including passwords.
It also finds that the app will connect a mobile device to any unsecured Wi-Fi network as long as it has 'Barbie' in the name, allowing for a network spoofing attack to be carried out by an attacker impersonating the Barbie network to steal data.
The app also utilizes an authentication credential that can be re-used by attackers, and it shipped with unused code that serves no function but increases the overall attack surface.
On the server side client certificate authentication credentials can be used outside of the app by attackers to probe any of the Hello Barbie cloud servers to look for more vulnerabilities. In addition the research found that the ToyTalk server domain was on a cloud infrastructure susceptible to the POODLE attack, allowing attackers to downgrade connection security and listen in on communications to the server such as uploaded conversation from the doll.
Bluebox Labs has disclosed all critical security issues to Mattel partner ToyTalk and a number of the problems have already been resolved.
Writing on the Bluebox blog, security research engineer Andrew Blaich says, "All of the issues discovered point to the need for more secure app development, as well as the need for integrating self-defending capabilities into not only stand-alone mobile apps, but also the apps that power IoT devices like Hello Barbie. Ultimately, this research demonstrates the security of the mobile apps associated with IoT devices must be a higher priority".
-

Data discovery solution made available free on MS Office
Publié: décembre 3, 2015, 4:49pm CET par Ian Barker

Businesses are increasingly keen to unlock the insights contained within their data. But the tools to do this are often expensive and complex, putting them beyond the reach of smaller organizations.
Analytics specialist BeyondCore has announced a collaboration with Microsoft to make its data discovery solution available to Office users for free.
The new BeyondCore Analyst for Office provides single‐click analysis and detailed story‐based explanations of insights directly integrated into the familiar Office suite. It allows business users to analyze all data, without the need to formulate sophisticated questions or design complex queries, cut through the clutter to identify and act on the most relevant, statistically‐validated patterns, and visualize, understand, share and act on the results.
"Microsoft Office is the preferred analytics environment for most businesspeople. We congratulate BeyondCore on the way its Analyst for Office is empowering many more people around the world to extract powerful insights from big data," says Kirk Koenigsbauer, Microsoft corporate vice president, Office 365 Client Apps and Services.
There are limits to the free version of course, it lets users conduct up to ten analyses a month on smaller datasets in Excel or Microsoft SQL Server. Users can upgrade to paid versions of BeyondCore Analyst for Office to conduct more analyses, analyze larger datasets or access Big Data sources such as Hadoop.
Users can also try BeyondCore's enterprise solutions for 15 days free. This offers additional features including the ability to schedule analyses to automatically run each day, week or month, secure collaboration, audit and monitoring capabilities, and predictive and prescriptive analysis.
"BeyondCore's mission has always been to dramatically simplify the complexity of analytics, making it instantly available for business users," says BeyondCore Founder and CEO Arijit Sengupta. "But users often feel 'this is too good to be true.' Now with the free version of BeyondCore Analyst for Office, they can just try for themselves and see that analytics has changed forever. After using BeyondCore, users will no longer equate pretty graphs with actionable analysis".
More information can be found on the BeyondCore website. For the remainder of 2015 it's also offering an Implement on Our Dime deal where BeyondCore will conduct the first analysis or schedule the first dynamic dashboard on the clients' data, at no risk.
Image Credit: alphaspirit / Shutterstock
-

New privacy platform protects enterprise communication
Publié: décembre 3, 2015, 4:04pm CET par Ian Barker

Enterprise customers are increasingly concerned about the security of their mobile communications, as well as the ability to deliver auditing and compliance information.
Silent Circle, the Swiss company behind the privacy focused Blackphone, is launching its Enterprise Privacy Platform a set of secure software, services and devices designed to deliver privacy to business and government organizations of all sizes.
Features of the platform include a new Silent Manager which gives designated administrators a simple and easy way to oversee their organization's use of the Silent Circle platform through a web-based interface. It provides overviews of current users, groups, and plans, as well as a news feed showing relevant information like updates to Silent Circle apps.
The company's Silent Phone app, which encrypts VoIP and messaging services for any iOS or Android device, is now available in two subscription levels -- Basic and Plus. Silent Phone Basic allows unlimited member-to-member encrypted voice calling and text messaging for an annual membership fee of $5. Silent Phone Plus provides full functionality to include conference calling, file transfers, attachments, voice mail and direct customer support for $9.95 per month.
Silent World offers enhanced security and flexibility on any mobile device (iOS or Android). It extends the reach of Silent Phone's encrypted calling to regular mobile and landline numbers in 439 destinations, allowing for private conversations to effectively anyone in the world -- even to people who don't currently use Silent Phone.
"Building on the momentum of our Blackphone 2 launch, I’m proud to unleash all the work we have done on rebuilding our software and cloud-based Enterprise Privacy Platform," says Bill Conner, President and CEO of Silent Circle. "Our platform delivers unprecedented secure communications with the enterprise management controls necessary for auditing and general oversight. Now governments and global enterprises have a new choice in secure communications that didn't exist before, across any Android or iOS device".
More information can be found on the Silent Circle website and the Silent Phone app is available now on Google Play and the Apple App Store.
Image Credit: Sergey Nivens / Shutterstock
-

Instart Logic and Verisign team up to fight DDoS attacks
Publié: décembre 3, 2015, 2:58pm CET par Ian Barker

DDoS activity is at its highest for two years according to Verisign's Q3 2015 DDoS Trends Report, and as the number and sophistication of attacks increases, companies are recognizing the need for better security.
Application delivery specialist Instart Logic has announced a partnership with Verisign to offer customers an advanced DDoS scrubbing capability.
"In an ever changing cyber threat landscape, this technology integration will provide customers the combined benefit of a CDN through Instart Logic's application delivery platform and DDoS protection through Verisign’s DDoS Protection Service," says Ramakant Pandrangi, vice president of technology at Verisign.
The collaboration combines Verisign's DDoS protection services with Instart Logic's cloud security suite to effectively and efficiently combat some of the world’s largest attacks. When a DDoS event is detected, a customer’s internet traffic will be redirected to Verisign's DDoS Protection Services in the cloud, sending attack traffic to Verisign before it can harm their network. The DDoS traffic is then scrubbed through the use of Verisign's Athena mitigation platform and massively-scaled global network designed to handle advanced application and volumetric attacks. Filtered traffic is then sent to the customer’s network, so they can sustain normal business operations.
"Our ability to provide speed, security and scale can only happen with meaningful, strategic partnerships throughout the world that enable us to accelerate our go to market within the various regions," says Samrah Khan, head of business development and partnerships at Instart Logic. "Collaborating with organizations that share our vision allow us to provide more customers with the best solutions for delivering web and mobile applications".
The DDoS scrubbing service is available from today as an add-on to the Instart Logic's cloud security suite. You can find out more on the company's website.
Photo Credit: Duc Dao / Shutterstock
-

Application developers struggle to adapt to changing licensing models
Publié: décembre 2, 2015, 5:46pm CET par Ian Barker

Application producers are aware of rapid change impacting their ability to make money from their software products, but they're not adopting the automated licensing and entitlement management systems that would protect them from those changes and enable them to be more agile, and grow revenues and profits.
This is the conclusion of a new report by Flexera Software which shows that producers are aware that rapid technology changes are impacting the business climate, creating new opportunity and risk.
Among the changes identified are the Internet of Things, cited by 32 percent of producers as having a high impact on customer satisfaction. Within one to two years, 16 percent say that the IoT will have a major effect on supporting new business models.
The impact of new technologies on security is important too, 38 percent of respondents say the cloud has a high impact on security concerns. Others list virtualization, 29 percent, and mobile computing, 33 percent.
The way people buy software is shifting too. Within two years, the number of producers who claim all their revenues are derived from a perpetual software license model will be almost halved from 26 percent to 14 percent. By contrast the number who say half or more of their software revenues come from SaaS-based software subscriptions will rise from 14 to 21 percent.
Whilst the changes are widely recognized, the survey suggests application producers have not yet built sufficient agility and flexibility into their businesses to adapt. 58 percent report difficulty allowing customers to manage their own software entitlements. 38 percent find it difficult to quickly package and bundle features to create different product versions in order to accommodate changing market needs or unique customer demands, and 33 percent find it hard to support trial and/or evaluation licensing. Only 35 percent are using a purpose-built commercial licensing technology.
"Application producers lag far behind non-software industry counterparts that have long since automated critical operations with ERP, CRM and other mission critical systems. Many producers wrongly assume that because their ranks include software engineers and programmers, they can easily develop their own licensing and entitlement management systems in house," says Mathieu Baissac, Vice President of Product Management at Flexera Software. "But Software Monetization is a highly specialized field that is constantly changing, which makes it virtually impossible for non-licensing and monetization experts to adapt and scale as the business climate changes. The result, as the report findings illustrate, is that most producers are leaving money on the table because they aren’t sufficiently agile and the customer experience is being negatively impacted".
The full report is available from the Flexera website.

Image Credit: Stokkete / Shutterstock
-

Popular free mail services still use vulnerable versions of SSL
Publié: décembre 2, 2015, 4:04pm CET par Ian Barker

New research from information security company High-Tech Bridge reveals that the security of some of the most popular mail services, including Gmail, Outlook and Yahoo is lacking.
The company used its SSL checker service to test the popular email services for 31 different criteria, including the most recent SSL/TLS vulnerabilities and weaknesses, compliance with PCI DSS requirements, and compliance with NIST guidelines.
Almost all the tested email providers still support the old SSLv3 standard. Earlier this year, the Internet Engineering Task Force declared that SSLv3 shouldn't be used as it's insecure and threatened the confidentiality of encrypted communication. The Task Force recommended moving to the more secure TLS 1.2 instead.
Fastmail gained the highest score of A+ in the tests and is the only email service provider that meets PCI DSS compliance requirements for SSL/TLS. Hushmail, which describes itself as 'a privacy-oriented email service' with 'built-in encryption', has the weakest configuration of SSL/TLS, and scored an F in the SSL test.
Despite gaining a B+ grade, Gmail has one of the most flexible SSL/TLS configurations to ensure its compatibility with old and outdated email clients. Based on results from High-Tech Bridge's test, Outlook.com -- which gained a B- score -- does not visibly have a centralized SSL/TLS configuration of its email servers, potentially delaying and over-complicating update processes, and slowing down patch management.
"With the new functionality of our SSL testing service we aim to enable anyone to verify how well his or her data is being encrypted in transit," says Ilia Kolochenko, High-Tech Bridge's CEO. "With the increasing growth of wireless networks strong encryption becomes very important. However, many people tend to think that SSL can be applicable to HTTPS only, as they use HTTPS websites every day. Now they can test their SSL connection to their email and any other SSL-services as well".
You can read more about the test results for each of the services on the High-Tech Bridge blog.
Photo Credit: Balefire/Shutterstock
-

Two-thirds of companies don't regularly test their disaster recovery plans
Publié: décembre 2, 2015, 3:10pm CET par Ian Barker

More than 60 percent of companies in the UK and Germany say that they either test their disaster recovery plan either less than once a year, or don't test it at all.
This is among the findings of research conducted by data recovery specialist Kroll Ontrack which finds that a mere nine percent of companies test their plan every one to five months and another 29 percent every six months to a year.
Half of the companies surveyed hadn't experienced an IT disaster in the previous three years, but more than a third had needed to invoke their disaster recovery plan. While the majority of these companies had to invoke their plan between one and five times, an unfortunate minority were forced to undertake disaster recovery measures more than 10 times during the last three years.
A further issue raised by the survey is that even though employees' mobile devices are now an important element of corporate IT infrastructure, this hasn't been accounted for by most disaster recovery plans. Almost half (48 per cent) of respondents say that their plans don't cover mobile devices used by employees to access corporate systems.
"These findings are a clear indication that many companies still face significant risks in terms of data security, data loss and data recovery," says Paul Le Messurier, Programme and Operations Manager at Kroll Ontrack. "They also lack a thought-out disaster recovery plan that is tested regularly and is bullet-proof when a real disaster strikes the company and it is faced with system failure and data loss. Without an effective plan in place, companies face the prospect of a loss of business continuity plus reputational and financial damage. It's important that disaster recovery plans are in place, but it’s just as important to ensure that they are tested regularly and updated accordingly".
In a separate poll undertaken in the UK, almost 46 percent of respondents say that they don't have a disaster recovery plan in place at all, while a worrying 24 percent were unaware whether they had a plan or not.
"Even though the cost of downtime for a small to medium sized company may not be as high as for a Fortune 1000 one, it can still have an impact that threatens the existence of the company. It pays to have a disaster plan in place that is tested regularly and that can be invoked quickly and efficiently," adds Le Messurier.
Kroll Ontrack has developed a free template that smaller enterprises can use to develop their own disaster plans, including advice on what should be included and what testing is necessary.
Image Credit: Oleksiy Mark / Shutterstock
-

How DDoS attacks have evolved in 2015
Publié: décembre 1, 2015, 5:06pm CET par Ian Barker

As with most other cyber threats, the world of DDoS attacks seldom stands still, with new techniques constantly evolving to make them more effective and harder to defeat.
Security strategist Andrew Lemke, writing on the IBM Security Intelligence blog, has taken a look at some of the most significant DDoS developments of the past year.
April saw a major attack on the GitHub code sharing site. The attack originated in China and used a technique that unwittingly recruited users of Baidu -- the world's fourth largest website -- by injecting script into their browser sessions. This gave the hackers a large population of web users to boost their attack.
A similar amplification technique involves the use of BitTorrent to engage in distributed reflective denial-of-service (DRDoS) attacks. This has a number of advantages for the attackers, it's anonymous, plus it can be initiated by a single computer but still generate a large amount of traffic coming from multiple sources on the BitTorrent network. It also amplifies the original packet very well. The researchers who discovered the attack method state that the amplification factor can be as much as 120.
A potential form of attack that isn't yet in the wild is "temporal lensing" which sends packets by different routes but times them to arrive simultaneously in order to overwhelm the target system.
You can read more, along with tips for defending against DDoS attacks on the Security Intelligence blog.
Photo Credit: Fabio Berti/Shutterstock
-

WAFS allows simple, secure file sharing and collaboration across the world
Publié: décembre 1, 2015, 4:15pm CET par Ian Barker

Secure information exchange specialist GlobalScape has used this year's Autodesk University in Las Vegas to launch an upgraded version of its Wide Area File Services collaborative software platform, WAFS 5.
WAFS 5 simplifies enterprise collaboration, eliminates errors, and decreases bandwidth usage, providing secure, near real-time data access to both on-premises and cloud-based files located anywhere in the world.
The software uses intelligent byte-level differencing technology to instantly update changes to files by multiple remote users with minimal impact on network bandwidth. It also ensures that files are never overwritten, even if opened by other remote users.
"As work environments become increasingly distributed, real-time collaboration on large, critical files such as spreadsheets, CAD drawings, engineering blueprints, or MRI images is an ever-more vital business imperative," says Greg Hoffer, Vice President of Engineering at Globalscape. "Working with colleagues and partners distributed across the globe -- without frustrating slowness, costly delays, consistency errors, or versioning problems -- is a huge advantage to employee efficiency and productivity. With WAFS 5, distance and file size is not an issue. Complex files can be sent over a WAN at LAN speeds and are accessible to end users across multiple offices around the world".
WAFS 5 has a number of improvements including, up to eight times faster upload performance, up to 10 times faster download performance, and copy speed performance which is up to 90 times faster. It has increased transparency of file replication activities between servers and desktops to check for errors and ensure delivery success, along with increased system reliability, especially during periods of network instability.
Reduced bandwidth utilization ensures data transfers don't prevent mission-critical traffic from flowing in and out of the network, and an enhanced synchronization engine to offer easy, secure file collaboration.
More information about WAFS 5 is available from the GlobalScape website.
Image Credit: Chiran Vlad / Shutterstock
-

In-memory platform delivers faster operational intelligence
Publié: décembre 1, 2015, 3:45pm CET par Ian Barker

Until recently big data tools have been used to provide detailed analysis of large, stored data sets, but there's now increasing demand from industries such as eCommerce and financial services to have instant analysis on live data.
To meet this demand, in-memory computing specialist ScaleOut Software is launching a new version of its StateServer product which offers continuous and instant access to fast-changing data for large enterprises with ever increasing application workloads.
"In today's increasingly competitive marketplace big data isn't enough. To stay in the game, enterprises across many industries must constantly attain full value from their fast-changing data as well, incorporating these insights around the clock for real-time feedback," says Dr William L Bain, founder and CEO of ScaleOut Software. "ScaleOut StateServer 5.4 makes this possible by raising the bar in advancing in-memory computing technology and delivering powerful performance that offers enterprises unprecedented capabilities for operational intelligence in their live systems".
With this latest release ScaleOut StateServer can handle access requests in parallel, offers a comprehensive set of APIs, patented high availability, and new performance updates. Features include performance enhancements for multi-core processors, including IBM POWER8 systems, the ability to quickly sort and visualize very large object collections, and AppFabric Caching APIs to help customers preserve legacy application code when switching to StateServer.
ScaleOut is already employed by over 35 Fortune 500 companies, which use its fast, scalable, in-memory data grid technology to support mission-critical applications where high availability and low latency processing are key.
More details are available on the ScaleOut website.
Image Credit: Peshkova / Shutterstock
-

New platform seeks to integrate business communication
Publié: décembre 1, 2015, 3:15pm CET par Ian Barker

In large organizations you'll often find employees using multiple different platforms to work on and exchange files, making integration of activity difficult.
Israel-based Fastee is looking to solve this problem with the launch of a new platform which allows business team members, service providers and customers to quickly communicate in one place and provides them secure access to any shared material.
Fastee is tailored to business needs and the platform is integrated with a broad range of enterprise software including Salesforce, Asana and Yammer. Files and emails can be shared thanks to integration with Gmail, Exchange 365, Dropbox, Box, Onedrive and Google Drive. Everything is accessible within the platform via group or direct chat, allowing any group member to have access to shared files or linked folders, even if they aren't subscribed to a given service.
Chats, files and emails are all fully searchable. Fastee is accessible through iOS and Android, and on the major browsers, with notifications that can be enabled for both mobile and desktop. The platform's integration reduces the need to search across platforms for files, conversations or to-do lists.
All files and chats are protected with 256-bit AES encryption. The app generates a unique key for each item and securely stores each key in a separate location. There's also a private groups feature which ensures that all content shared within groups is limited to group members only. Users can preview files, images and emails through Fastee, without the need to download to a local device.
"We are proud to launch our company and our platform, offering an agile, fully comprehensive communication platform to the business community," says Guy Eisdorfer, Co-Founder and CEO of Fastee. "Our app provides business teams with one place to interact with their customers and colleagues, giving them quick, secure access to a project’s entire lifetime of files and chats. We see our app quickly becoming the go-to communication tool of choice for business users".
You can find more information on the Fastee website and the app is available from Google Play and the Apple App Store.
Image Credit: Syda Productions / Shutterstock
-

The benefits of disaster recovery in the cloud
Publié: novembre 30, 2015, 12:52pm CET par Ian Barker

As more systems are moving to the cloud it's leading to an evolution in requirements for disaster recovery.
Irish IT solutions company ERS Computer Solutions has produced an infographic looking at how companies can benefit from disaster recovery in the cloud.
It looks at the cost of downtime in various industries, as well as its most common causes. It also reveals that 59 percent of companies say they choose cloud backups for cost reasons, 52 percent cite ease of use and 48 percent compatibility.
Cloud users are able to recover more quickly from disasters though, with 20 percent able to be back up and running in a couple of hours, compared to only nine percent of non-cloud users.
There's much more, including issues to consider before adopting cloud-based recovery and what questions to ask providers, in the full graphic below.
Photo Credit: Olivier Le Moal/Shutterstock
-

Wi-Fi Barbie could be putting your kids at risk
Publié: novembre 27, 2015, 4:40pm CET par Ian Barker

The latest Wi-Fi enabled Hello Barbie dolls could be putting your children at risk according to security researchers.
Using a combination of speech recognition technology and wireless connection Hello Barbie provides, "...an engaging and unique Barbie experience," according to manufacturer Mattel.
That experience may be rather more engaging than you bargained for according to security researcher Matt Jakubowski, who has managed to hack the Hello Barbie operating system. He says he's been able to extract information including Wi-Fi network names, account IDs and MP3 files.
Talking to NBC he warns that the information he was able to access could be used to find someone's house or business, to access their home network and everything that the doll had recorded. He says, "It’s just a matter of time until we are able to replace their servers with ours and have her say anything we want".
However, Martin Reddy, Co-founder and CTO of ToyTalk which designed the Hello Barbie operating system says, "...we are not aware of anyone who has been able to access your WiFi passwords or your kid's audio data".
Writing on the company's blog Reddy says, "Mattel and ToyTalk have invested a lot of effort to build the safest experience possible for parents and their children. As part of that commitment, we are actively engaging the security community to address any concerns. We have initiated a security bug bounty program where security researchers are rewarded for responsibly disclosing potential vulnerabilities to us. This lets us fix any issues as they are discovered and keep the doll as safe as possible for you".
This seems to cut no ice with the Campaign for a Commercial-Free Childhood which has launched a #HellNoBarbie campaign urging parents to boycott the toy.
-

Do dropped phones really always land screen side down?
Publié: novembre 26, 2015, 6:19pm CET par Ian Barker

It always seems to be the case that if you drop your phone it lands screen side down and gets cracked.
A survey by Motorola suggests that one in three of us in the UK is using a smartphone with a cracked screen so this would seem to be true, but can it be proved scientifically?
As with the laws of physics causing toast to land butter side down, a similar phenomenon can be applied to your handset. A theory developed by physicist and Aston University visiting professor, Robert Matthews, explains why it's not just down to bad luck.
Professor Matthews' study notes that smartphones are often held loosely in one hand, with the user's fingers below the phone's center of gravity. This makes the phone both more at risk of being dropped, and more likely to pivot about the fingers. Once the phone leaves the hand, it spins at a rate dictated by the various forces acting on the phone as seen in the diagram below.
The forces acting on the phone at this point can be represented by a formula:
This where L is the length of the smartphone, g is the acceleration due to gravity, p = 2δ/L is the 'overhang parameter', δ is the overhang distance, and θ is the angle of the smartphone when it starts its descent. Don't worry if you haven't got all that, there won't be a test at the end.What this means in practice is that a dropped phone is unlikely to break contact with the fingers before it's achieved a high enough spin-rate to attain a safe, screen-up landing.
Professor Matthews says, "People might think it's just their bad luck when a fumbled phone lands screen-down and smashes. In fact, physics is to blame, making screen-down landings more likely. It seems we’re all at risk of experiencing this manifestation of Murphy’s Law: 'If something can go wrong, chances are it will'. People who are naturally clumsy and often fumble their phones are clearly particularly at risk".
Image Credit: VDex / Shutterstock
-

Fake Amazon app targets Black Friday shoppers
Publié: novembre 26, 2015, 3:43pm CET par Ian Barker

Hoards of shoppers hunting for the best Black Friday deals and perhaps not paying full attention to online safety makes this a time of year when cyber criminals are also keen to cash in on moneymaking opportunities.
Internet security company Zscaler has uncovered a widespread malware campaign whose authors are scamming large numbers of people by creating fake Android apps offering early access to Amazon's Black Friday and Cyber Monday sales.
Once installed it masquerades as a legitimate Amazon app. When launched it starts a child app that asks for admin privileges and other risky permissions including sending SMS and dialing phone numbers. This app registers itself as a service so it will stay on the device even if the original app is removed.
It has code for harvesting the user's personal data including call logs and received inbox messages, collecting sender's numbers, SMS body text, received incoming call numbers and contact names.
Zscaler warns users to, "Always install applications from legitimate app stores and websites. Be aware of the permissions asked by the application during installation. Shopping apps should not be asking for access to your contacts or SMS".
More information on the attack is available on the Zscaler blog.
Photo credit: Stuart Miles / Shutterstock
-

BullGuard Internet Security 2016 offers good value for home users [Review]
Publié: novembre 26, 2015, 11:05am CET par Ian Barker
Recent reports have highlighted that it’s security at the endpoint which often leaves businesses exposed. This applies not just to machines in the office but also to mobile and BYOD devices, so some sort of security solution is essential.
BullGuard has released its latest Internet Security suite this month which is fully Windows 10 compatible and includes a number of things that make it an attractive option for business users. New features like Dropbox compatible backup and storage ensure that business data is properly protected.
The suite also has tune up options to help optimize system performance; this includes duplicate file detection and clean up to help free disk space, and a boot manager to control which applications are launched when Windows boots.
Of course the main thing you buy these suites for is virus protection and BullGuard has beefed up this area too. An enhanced behavioural detection engine offers more protection and an improved safe browsing module helps guard against malicious websites. Improved quarantine provides protection without user intervention, and specific exploit detection includes malicious URLs and executable image files. In addition there’s improved detection of malware at Windows start-up to combat rootkit attacks and help to protect against the rise of ransom ware.
An impressive collection of features then, but how does it all work in practice?
Installation
Installation from a download on a fibre connection took under five minutes including a brief initial scan. You need a reboot to activate the firewall which takes a little longer than normal -- actually it took a lot longer than normal on our test system and required a shutdown and another boot. It was fine after that though so we’ll put that down to a one-off glitch.
Once installed you’re presented with BullGuard’s neat tiled interface. You don’t get the option to choose modules as part of the install, you have to load the whole package, but afterwards you can control which ones you use. On the Settings menu each module has a simple on/off switch. You can set the protection level of the Antivirus module with a slider, for anything more complex you need to switch to Advanced mode.
In Use
BullGuard Internet Security is designed to offer a decent level of protection, but not to frighten the horses, so straight after installation everything is very simple and used friendly. Things like control of firewall rules is there if you need it, but you need to switch to Advanced mode in order to access them.
The Antivirus and Firewall modules work unobtrusively enough, you can also get it to scan for vulnerabilities which warns you about things like missing Windows updates and insecure network connections. We’d have preferred to see a bit more depth here, such as checking commonly installed programs like Flash for patches too. BullGuard generally performs well in independent virus detection tests.
The program’s impact on performance is negligible compared to an out-of-the box Windows 10 system running Windows Defender. By default the Tune Up module keeps browser caches and temp folders clean, you have the option to let it delete broken registry entries, clean up downloads and empty the Recycle Bin too. You also have the option to manage startup entries to improve boot times, programs can be disabled altogether or delayed so that you can get started more quickly.
The safe browsing option means search engine results are automatically scanned and safe links are shown with a green tick. You can hover your cursor over this to find out more about the site. However, this works with popular search engines, Google, Yahoo, and Bing as well as links on Facebook, but others like Lycos (yes, it is still going) and DuckDuckGo aren’t covered.
Spam filtering works with Outlook, Windows Live Mail and Thunderbird and you can manually configure safe and unsafe senders if you need to. It won’t trouble many business users but there is a parental control module which lets you control selected content based on age group profiles and set an access schedule.
You get 5GB of cloud storage as part of the package which you can use for backups with the built-in tool or for general storage. You have the option to share files from the cloud as you can with other storage services. Backup works constantly in the background for whatever folders you’ve selected, rather than run on a set schedule, so when something is changed it will automatically be saved. You can set a schedule if you prefer and you can also change where the backup is saved with the option to use an external or network drive, or your Dropbox storage.
Conclusion
The only things that are really missing are password management and identity protection, though the latter can be added with an upgrade. Although there are some minor niggles BullGuard works well overall. It won’t scare off inexperienced users, but more sophisticated options -- to allow you to tunnel through the firewall for a VPN for example -- are there if you know where to look.
At just under £50 to protect three PCs it’s also reasonably priced. Large companies will doubtless want to roll out their own solutions for BYOD, but for smaller enterprises looking for an endpoint solution to recommend or supply for their staff BullGuard Internet security is worth considering.
BullGuard Internet Security costs £49.95 to protect three PCs for a year. If you want to road test it before buying there’s a 60-day trial available on the BullGuard website.
Pros
- Minimal performance impact
- Easy to install
- Day-to-day options simple to use
Cons
- Limited vulnerability scanning
- No password management
- Safe browsing limited to popular sites
Company Release Price ITProPortal Review BullGuard £49.95 7/10 Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Popular mobile payment apps leave consumers and businesses exposed
Publié: novembre 24, 2015, 12:10pm CET par Ian Barker

It's likely that this year's holiday season will mark the first time that online purchases made on mobile devices will overtake those on desktop systems.
This makes mobile payment systems a prime source of risk and a new study by mobile app security company Bluebox Security highlights poor security across consumer mobile payment apps, including some of the most popular solutions for both Android and iOS.
Bluebox examined 10 mobile payment apps expecting to find that security would be robust for apps directly handling financial transactions. However, in every app reviewed it found security was remarkably basic. 98 percent of developers polled by Bluebox have reported most mobile apps are moderately to highly vulnerable. Yet consumers are naively placing their trust and their cash in these apps, as 69 percent of those polled say they're confident that the apps they use are safe from attack.
Bluebox took a close look at the top two peer-to-peer payment apps that are used to send monetary gifts to family and friends, along with the top three one-click merchant apps from leading retailers. The analysis showed that these five apps lack the enterprise-grade protections needed to safeguard financial transactions and that they harbor vulnerabilities that require immediate attention to protect against hackers.
Problems found include every app examined being vulnerable to tampering that would allow rerouting of funds from a consumer's account to a hacker's account, without the consumer's knowledge. On average, 75 percent of the code in the apps was from third-party code libraries, which are used by enterprises to speed up mobile app development. When not properly secured and vetted, these code libraries could easily contain the next widespread exploit like Heartbleed or Stagefright -- exposing payment apps to possible breaches.
None of the five apps encrypted data written to disk, meaning authentication info, transaction history and other personal information is fully visible to attackers once they’ve gained access to a device or app.
Additionally, all of the apps investigated were vulnerable to hacking via a compromised device, by replacing the legitimate app with a modified version without the user’s knowledge, or by intercepting the app’s interactions with cloud services over Wi-Fi or cellular networks.
"Our starting hypothesis was that mobile apps handling financial information would have more rigorous security compared to other mobile apps, but our research uncovered the opposite. As enterprises rush to get apps to market, we are discovering the same security errors from industry to industry," says Andrew Blaich, lead security analyst at Bluebox Security. "Enterprises need to ensure their apps can defend themselves and make security a seamless step in the development process."
More information on the study's results can be found on the Bluebox blog.
Photo Credit: Slavoljub Pantelic/Shutterstock
-

Inateck MP1305 iPad Pro/MacBook sleeve [Review]
Publié: novembre 23, 2015, 6:08pm CET par Ian Barker

If you’re suffering a touch of deja vu looking at the photo above it's probably because my colleague Mark Wilson reviewed Inateck's similar sleeve for the Surface Pro earlier this year.
This one is designed for the iPad and MacBook fraternity and features a neat fold over design that allows it to act as a stand for the device as well as a sleeve to protect it. It has a smaller pouch in front of the main one and here are a couple of pockets on the back, one of which is big enough to take CDs. It also comes with a separate little pouch containing a cleaning cloth and which is big enough to take a mouse. It's not really suited to carrying bulky mains adaptors around though, so you’ll need to charge your device before you go out.
The outside is a pleasingly tactile soft, thick felt and the inside is lined with a sort of velvety grey cloth to prevent your screen from getting scratched. It feels and looks well made with even stitching and subtle Inateck logos on a leather-style patch on the front and on a tab sewn onto one of the edges.
The main flap is held closed by Velcro which is also used to turn the case into a stand so you can watch videos or run through presentations at a comfortable viewing angle, there are two positions depending on your preference.

It's a neat design, but its slimline style means that carrying anything bulky in one of the pockets is going to look a bit like a snake that's swallowed a rabbit as well as risking damaging your kit.
Though it's aimed at MacBooks and iPads there's nothing to stop you using it for other pieces of kit up to 13-inches in size -- we won't tell anyone if you don't.
It currently costs $23.99 from Amazon (£18.99 in the UK). More details can be found on the Inateck website.
-

Bringing machine learning to the masses [Q&A]
Publié: novembre 23, 2015, 12:35pm CET par Ian Barker

Big businesses are increasingly recognizing the potential of data science and machine learning. Until recently, however, it hasn't been readily available to smaller organizations and individuals.
But now companies like Amazon and Google are beginning to make machine learning available more widely. Is this the start of a new trend? What will it mean for businesses, and will we see the rise of a new generation of ‘citizen data scientists’?
We spoke to Mike Weston, CEO of data science specialist Profusion to find out more.
BN: Isn't machine learning something that's only for techies and big organizations?
MW: No. This is a common misconception. You do not have to be a big organization to benefit from machine learning, you just have to be willing to invest time.
Machine learning is a branch of data science which focuses on using a form of artificial intelligence to help solve problems. Initially, a data scientist will train a computer with questions and answers relevant to a business' issues and the computer will then learn how to answer similar questions in the future. This training can be tailored to a business' needs and characteristics -- including its size.
BN: Are we seeing a move towards data science being available to all?
MW: Most definitely -- large tech companies are starting to take notice of machine learning and data science, and developing tools to make this more accessible to 'non-techies'. You have Amazon and Microsoft integrating machine learning tools within their AWS and CRM platforms while Google has recently released Tensorflow. This trend is only going to increase as more companies become aware of the importance and potential of data science.
I also expect that as these machine learning tools become more commonplace, we’ll see an increase in the number of 'citizen data scientists' within companies. These are people who are embedded in different departments and who have enough knowledge to understand the value and applications of data science and who can undertake rudimentary analysis. It will be these people who become data science’s greatest cheerleaders.
BN: Thanks to smart devices and the Internet of Things enterprises are collecting more data than ever. Is there a risk that much of this is being wasted?
MW: At the current time I am pretty certain that many businesses are wasting their data. This is only going to grow as smart devices and the IoT becomes more mainstream. The main issue is that many businesses do not see the full potential of the mountain of data they are sitting on and they do not know how to use it.
BN: What opportunities can machine learning bring to businesses?
MW: There are a great many opportunities. For example, a supermarket retailer could look at all their transactional data and see that eggs, milk, vanilla pods and flour are often bought in the same basket. Overlaying information on common recipes along with seasonal and weather data may then tell that retailer that all these items are commonly used to bake a cake, that baking increases when the weather is overcast and is highest in winter. The supermarket could then use this information to predict demand for certain items of stock, along with recommending baking goods and recipe books.
The advantage of using a machine learning algorithm for this is that the computer constantly learns and improves. Although a retailer may have many different products and millions of transactions, using an algorithm saves the time it would take a team of human beings to sift through all this data. As the algorithm learns from its mistakes, it gets increasingly accurate over time.
Data science can also be applied to other problems and industries. It has the potential to streamline an organization's supply chain, inform public services and infrastructure, be used for pharmaceuticals and in clinical trials and be used for employee wellness. Data science's potential is game-changing.
BN: On the other side of the coin what concerns is it likely to raise?
MW: Whenever businesses work with personal data, there are always concerns over the security and use of that data. It is important that organizations consider how they store their data, along with who has access to it. Companies will have to make some difficult decisions regarding how far they go in using their consumers' and staff data. I recommend that businesses create guidelines informing others on how the data will be used, and why.
If businesses fail to use data in an ethical way, they could face a backlash and loss of trust from their consumers and staff. This would be damaging to the entire tech industry and is definitely something we wish to avoid.
BN: Will we see simplified data science opening the door for more complex projects?
MW: Simplified data science will almost certainly open the door to more complex projects.
The machine learning platforms offered through Amazon and Microsoft have made data science more accessible, but only for a limited number of applications. With Amazon, the emphasis is on e-commerce and targets the users of Amazon Web Services. Meanwhile, Microsoft's system targets marketing and CRM.
Users of these systems will be able to detect fraud and fake reviews, predict if a customer is likely to leave and tailor a marketing strategy. However, these users will not be able to do more complicated data science. They will lack the technical knowledge required to write algorithms, clean data or know what technique to use to solve particular problems. In this way, businesses which see the benefits of using the simpler data science tools, may then turn to data scientists for more complex work.
Image Credit: Sarah Holmlund / Shutterstock
-

69 percent of users would bypass security controls to win a big deal
Publié: novembre 20, 2015, 1:14pm CET par Ian Barker

When faced with the chance of clinching a major deal people are willing to throw security controls out of the window.
This is according to research by contextual security company Balabit which asked over 380 European IT executives, CIOs, CISOs, auditors and other IT professionals about their thoughts on IT security and business flexibility.
When asked about their preference if they needed to choose between IT security and business flexibility, 71 percent of respondents said that security should be equally or more important than business flexibility.
But show them the money and things change, when the same people were asked if they would take the risk of a potential security threat in order to achieve the biggest deal of their life, 69 percent of respondents say they would take the risk.
"These results show that organisations have a long way to go to balance security and business," says Zoltán Györkő, CEO at Balabit. "They demonstrate that while security overload may be tolerated during normal business, when it comes to big deals the respondents would not hesitate to bypass security to win business. It is important that this is recognised as an issue and dealt with accordingly".
Since insiders cause many data breaches according to Ponemon, companies need to achieve a balance between IT security and business flexibility.
"Today's static control solutions can only go so far," adds Györkő. "Security teams must have visibility of the context of user actions to be able to respond effectively, and any additional tools must be transparent to the business workflow. We believe that a monitoring based approach that enables companies to respond to suspicious activities in real time can make IT security more business friendly; that is why we developed our Contextual Security Intelligence Suite".
More details of the survey are available from the Balabit website.
Photo credit: wk1003mike / Shutterstock
-

Want higher pay? Get some DevOps skills
Publié: novembre 17, 2015, 4:58pm CET par Ian Barker

DevOps skills are increasingly sought after and as a result salaries for DevOps engineers are higher than for other IT job titles according to new research.
IT automation software provider PuppetLabs has released its 2015 DevOps Salary Report based on data gathered from its 2015 State of DevOps Report.
Among the findings are that DevOps engineers make noticeably higher salaries than most other practitioner job titles in the 2015 survey and report. 55 percent of US DevOps engineers make $100,000 per year or more; this share is surpassed only by architects (with 75 percent making $100,000-plus), a group that includes the distinct job titles of architects, cloud or infrastructure architects, and systems architects.
Where managers in the rest of the world typically make at least one salary increment more than practitioners, most managers in the US make at least two salary increments more. The report also shows that in the US you're more likely to make a better salary if you are a tech practitioner in technology, web software or education.
These salaries come at the expense of long hours, however. Seventy-one percent of practitioners report working 40 or more hours per week. Most respondents (52 percent) reported working 41-50 hours per week. More DevOps engineers reported working in excess of 50 hours per week than any other job title. More systems engineers reported working 41-50 hours per week, and more system administrators reported working 40 or fewer hours per week.
There's a gender divide too. Most surveyed women reported making $50,000 to $100,000 (59 percent of women, compared to 47 percent of men), while more men reported making $100,000 or more (47 percent of men, compared to 36 percent of women).
"The 2015 State of DevOps Report showed that high-performing IT organizations are more agile, more reliable, and ultimately drive real business value," says Nigel Kersten, CIO at Puppet Labs. "Now that organizations are learning of the benefits of DevOps, we're seeing additional salary data that reveals just how much demand there is around the world for highly qualified IT and DevOps practitioners. It's encouraging to see these positions continue to grow, and we look forward to watching the market evolve and adapt to the growing urgency around making IT a competitive advantage".
You can see more detail on the results in the infographic below or on the PuppetLabs blog.
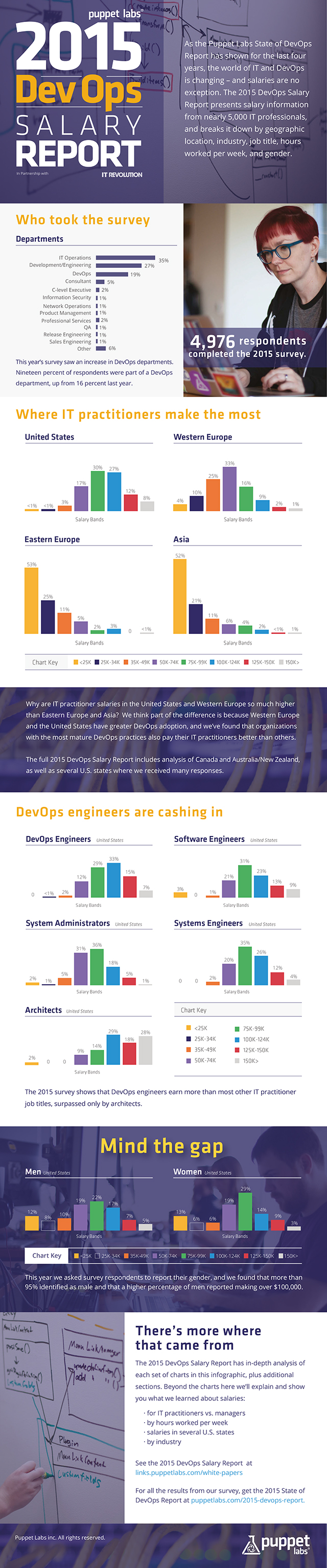
Photo Credit: Pavel L Photo and Video / Shutterstock
-

New solution uses data to improve IT service quality
Publié: novembre 17, 2015, 4:49pm CET par Ian Barker

Businesses generally want IT management solutions that offer a complete overview regardless of the underlying platforms that produce it.
Atlanta-based OpsDataStore is addressing this need by launching its new big data back end for all IT management data.
Features of OpsDataStore include open data collection architecture which can handle management data from any platform and any management software product. The solution includes connectors for the VMware vSphere data center virtualization platform, Dynatrace APM, AppDynamics and the ExtraHop wire data platform. Users can also add new connectors for other products.
Unlike simple metrics stores or log databases, OpsDataStore relates items to each other as they're ingested and maintains a continuously updated topology map of the entire environment. Any object can be queried for its end-to-end topology at any point in time. The model is continuously and automatically updated, eliminating the need for periodic discovery.
OpsDataStore is built on state of the art open source, low latency, and big data technologies, including Cassandra (time series database), Spark (stream processing engine), and Kafka (message bus). These technologies enable OpsDataStore to scale to any size environment and process large amounts of data in real time.
An open query architecture makes for easier access and reporting along with support for leading business intelligence tools so data can be easily published to those who need it.
"Service quality issues affect the revenue, reputation, and customer retention of global enterprises that rely upon online services," says Bernd Harzog, CEO of OpsDataStore. "Through our work with hundreds of enterprises over the last several years, we saw the urgent need to glue together IT management data into an easily consumable solution. By creating a central repository for all IT operations data, we enable enterprises to keep up with an unprecedented rate of innovation while delivering superior online service quality".
More information on the launch is available on the company's blog.
Image Credit: jannoon028 / Shutterstock
-

IT pros welcome the rise of their new machine overlords
Publié: novembre 17, 2015, 3:13pm CET par Ian Barker

Until recently the idea of machines and computers taking over from humans has been the stuff of sci-fi. But recent developments in automation have brought the reality of a machine takeover of many tasks much closer.
New research from smart automation specialist arago reveals that, amongst IT workers at least, more automation leads to greater job satisfaction. 85 percent not only welcome smart automation, but also identify concrete benefits from it.
According to the study 85 percent say that intellectually stimulating activities are most important to their job satisfaction, 88 percent want to use automation to free up their time so they can focus on more strategic initiatives, 93 percent believe automated IT tools do not put their jobs at risk, and 91 percent realize automated IT tools are not the beginning of an AI takeover.
When asked what they'd prefer to do instead of the menial tasks that take up much of their time, the two most preferred tasks are innovating technology/solutions (72 percent) and modernizing existing technology (63 percent).
"IT pros know that smart automation technology frees up their time, reduces the need for menial tasks and allows them to concentrate on innovative endeavors that are much more strategic to their employers and their own future. That shows the common narrative stating that IT Pros find smart automation a threat to their jobs, and that they are afraid of a machine takeover, are overblown. The reality is quite the opposite." says Chris Boos, CEO for arago. "Forward thinking CEOs, CIOs and HR executives need to be aware of the positive impact smart automation will have on their companies".
You can see more of the survey's findings in infographic form below.
Image Credit: Tatiana Shepeleva / Shutterstock
-

How reviews can help online retailers can stand out in the crowd [Q&A]
Publié: novembre 17, 2015, 11:35am CET par Ian Barker

As we approach Cyber Monday, Black Friday and the holiday season, online retailers are keen to make the most of the opportunity to boost their business.
But what can they do to make themselves stand out? Reviews from customers are a crucial part of the process. We spoke to Jonathan Hinz, director of strategic partnerships and business development at online review community Trustpilot to find out how companies can use them to their advantage.
BN: What can e-commerce brands do to attract customers during the holiday buying season?
JH: In 2013, Nielsen reported that 84 percent of consumers trusted recommendations from people they know and 68 percent trusted the opinions of those online. These figures are up 6 percent and 7 percent respectively, from 2007. What's clear from these figures is that brands need to change their traditional marketing approaches to ones that relate better to consumers. As social creatures, we have the need to act like others. We tend to weigh our regular decisions, and sometimes major decisions, on those around us. So why should making a decision about what to purchase and who to purchase from be any different? Companies need to use pictures, reviews and feedback from their existing customers to entice new customers. Consumers need to hear and see from their peers, putting information into context in order to make a purchase decision. It’s the only way brands can stand out from competition.
BN: What and where are the best places to display online reviews on an eCommerce site?
JH: The reality is that it's not simply about conversion on the site any more. Consumers are bombarded by messages from brands across all kinds of media and devices these days. It's just not a linear path any longer as customers are interacting with brands an average of 4.3 times in two days before a purchase. No one location (like your website) is enough to encourage a consumer to buy a product or service. Committing yourself to being a consumer-focused company and understanding consumer behavior is critical in addressing the encouragement of a purchase.
Once you understand who your consumers are, and how they purchase, you can then address where your brand needs support throughout the customer journey. This all depends on the consumer research you conducted. Do you need to increase your visibility in search? Convert better in search ads, landing pages or on your website? Does your website have drop-off points, or worse, shopping cart abandonment challenges? I know all the brands I’ve ever consulted with would simply say they need help with 'all of the above.' That's why it's critical to engage with a company like Trustpilot that provides a range of solutions, from free to enterprise, to promote the reviews and feedback of your existing customers to any sales prospects in your future.
BN: How can social media help boost purchases and increase trust in a company?
JH: Social media is a great outlet for companies to build trust and increase consumer consideration of purchase, and the proof is that 89 percent of consumers say interaction with a brand on social media has an impact on their purchase. How brands use social media is what makes the difference. Social media platforms perform best in building trust and creating an environment where consumers can share experiences to spread awareness of brands. Giving your existing consumers a platform to help inform your prospective consumers through posting authentic and verified consumer reviews is key here. Consumers need to know you're a credible place to buy from and that you can handle the inevitable negative situations that occur.
BN: Other than price, what helps a buyer decide where to purchase a product?
JH: 'Where' is an interesting concept in our omnichannel world. Where can mean from whom they purchase, and also from which device they purchase. More consumers are on their mobile devices than any other device. The research and purchases they make on mobile are increasing as well. Brands need to ensure their sites and content are mobile optimized to ensure visibility on the devices consumers are using the most. Additionally, 86 percent of consumers will pay more for a better customer experience, which means brands need to invest in a consumer review solution that can help them collect customer feedback and analyze the data to improve customer relations and service.
Image Credit: Rawpixel / Shutterstock
-

DHL customers targeted by new phishing scam
Publié: novembre 16, 2015, 1:52pm CET par Ian Barker

With the approach of the holiday season there's a spike in online shopping which means many people will be expecting the delivery of packages.
This of course is a window of opportunity for cyber criminals looking to steal personal information. It's perhaps not surprising then that Comodo Antispam Labs has identified a new global phishing threat, targeted at businesses and individuals who use DHL shipping.
The fake emails appear to come from DHL Worldwide and have the subject line 'DHL Shipping Delivery Tracking Number.' The tell tale give away is that the sender's email address is not on a DHL domain. The messages imitate the corporate style and logos of DHL, and are designed to capture logins and passwords to DHL accounts and package tracking information.
The phishing email headed 'DHL Capability Tool' asks recipients to click a link to obtain a tracking number for their delivery. If clicked the link leads to a site that will capture the user’s DHL ID and password.
"Through specific IP and URL analysis -- as well as the Comodo Antispam Labs' continuous monitoring and scanning of data from the users of Comodo's Internet security systems, our team was able to identify this specific phishing email scam and alert the public to it," says Fatih Orhan, Director of Technology for Comodo and the Comodo Antispam Labs. "As a company, we work diligently in creating innovative technology solutions that stay a step ahead of the cyber criminals, and keep enterprises and IT environments safe".
There are around 2.5 million users of DHL worldwide so the campaign has the potential to net those behind it a good number of unwary victims. You can find more information about the scam on the Comodo blog.
Image Credit: Maksim Kabakou / Shutterstock
-

HP Enterprise launches new Docker solutions for business
Publié: novembre 16, 2015, 12:19pm CET par Ian Barker

Docker has been widely adopted by enterprises looking for tools that allow for fast development, testing and management of applications.
HP Enterprise (HPE) is using this week's DockerCon Europe to introduce a new line up of solutions for the Docker ecosystem. These encompass cloud, software, storage and services to allow businesses to use Docker to help them move to a hybrid infrastructure in a scalable, secure and trusted manner.
"Containers are changing the way applications are developed and managed, bridging the gap between IT and developers and helping organizations accelerate their pace of innovation," says Martin Fink, EVP and CTO at HPE. "Hewlett Packard Enterprise is embracing and extending Docker capabilities by providing a comprehensive set of enterprise class tools and services to help customers develop, test and run Docker environments at enterprise scale".
Solutions on offer include the HPE Helion Development Platform 2.0 with support for Docker, which enables developers and IT operators to deploy microservices, a way of designing applications as independently deployable services, packaged as Docker containers.
HPE StormRunner and HPE AppPulse for Docker let developers and IT operations test, deploy and monitor Dockerized applications with confidence, providing full application lifecycle management. Remote Docker Swarm cluster monitoring with HPE Sitescope manages and monitors a complete Docker Swarm cluster using HPE Sitescope, an agentless application monitoring software solution.
HPE Codar for Docker allows continuous deployment of hybrid workloads, part traditional and part containerized, with the click of a button. Docker Machine plugin for HPE Composable Infrastructure automates the deployment of Docker container hosts from HPE OneView, enabling IT and DevOps to rapidly provision bare metal infrastructure for Docker environments within an organization's own datacenter and on their own secure networks.
There's also persistent storage for Docker containerized apps using flash-optimized HPE 3PAR StoreServ Storage arrays and the HPE StoreVirtual software-defined storage solutions. Enterprise-grade container support delivers expanded support for containers in alignment with HPE's technology solutions roadmaps, with a single point of contact for access to a global network of specialists round the clock.
Erez Yaary, HPE Software Chief Technologist EMEA says, “These announcements cover a wide spectrum from development through to managing workloads and management of the data center, all with enterprise grade services”.
HPE solutions for Docker are available now, for more information you can visit the HP Enterprise Grounded in the Cloud blog.
Image Credit: Hewlett Packard Enterprise
-

Are ad-blockers killing marketing efforts?
Publié: novembre 13, 2015, 4:38pm CET par Ian Barker

Ad-blocking on both desktop and mobile devices is becoming more and more common. But does this mean advertisers are increasingly wasting their time?
A new survey of over 500 consumers by consumer intelligence and predictive marketing company Boxever reveals that 70 percent of consumers surveyed say they're likely or extremely likely to use ad-blocking apps, and another 15 percent said they'd consider it.
When asked the reasons why they wanted to block ads, 61 percent say the mobile ads typically received are completely irrelevant, 61 percent also say mobile ads impede the mobile experience. 56 percent say the mobile ads they typically receive never add any value, and 51 percent say they've never taken action on a mobile ad presented to them.
Email doesn't seem to be better channel for marketers either, particularly since recent filtering advancements rolled out by Gmail, Yahoo, Microsoft and others. Only 22 percent of consumers say they check their clutter/promotions folder each day.
"The issue is a lack of relevance, value and context", says Boxever CEO Dave O'Flanagan, "In fact, an earlier Boxever survey from this year found that for more than 50 percent of consumers, three out of four sales offers received are irrelevant to their needs and preferences".
You can read more about the effect of ad blocking on the Boxever blog and there's a summary of the findings in infographic format below.
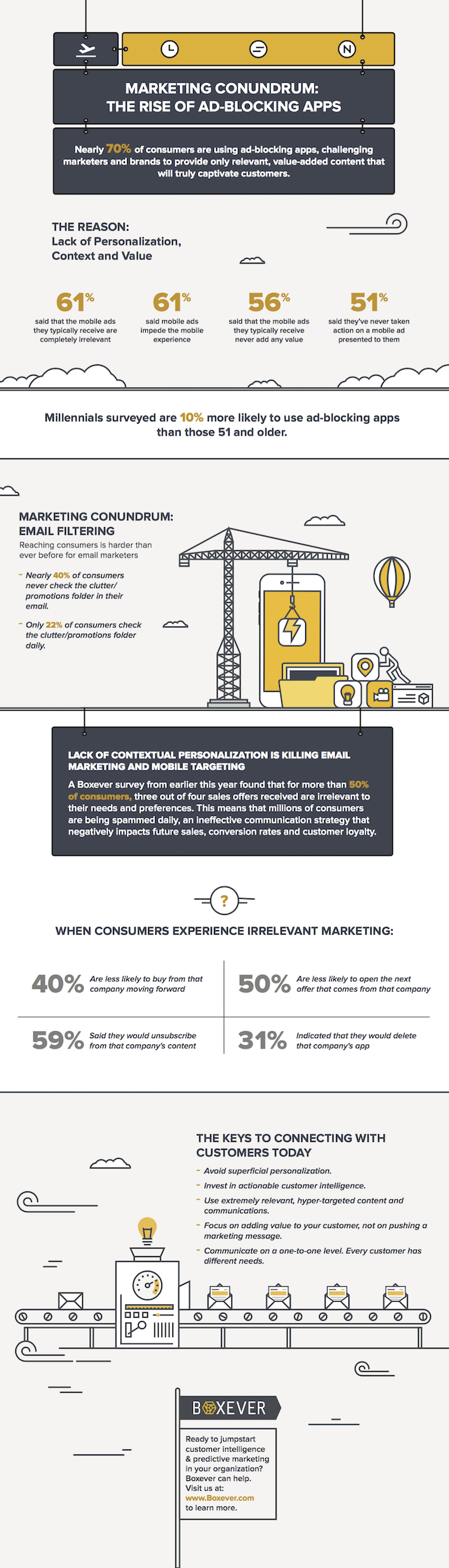
Photo Credit: Quka/Shutterstock
-

How BSIMM improves security by letting developers compare security practices [Q&A]
Publié: novembre 13, 2015, 3:34pm CET par Ian Barker

Every organization believes that it's making its systems secure, but because they usually work in isolation from competitors and other businesses they have no way of knowing how they compare.
The Building Security In Maturity Model (BSIMM) aims to quantify security practices and present them in a measurable way to allow companies to compare their performance.
We spoke to Paco Hope Principal Security Evangelist of application security specialist Cigital to find out more about BSIMM and how it works.
BN: Where did the idea for BSIMM come from?
PH: Around seven years ago Cigital decided that rather than preaching to people about security we should take a step back and ask them what they do. So we went to big companies like Adobe and asked them how they spent their security budgets. We then developed a model that described all of the things they told us they were doing. Since then we’ve gone on to measure over 100 firms, however, the model only contains data from those who’ve been measured recently.
BN: How does it work?
PH: What we're trying to do is observational science around software security; we’re not interested in the desktop IT, anti-virus, network operations areas. We're talking about people who build software and apply it around the enterprise. Over time we've settled on around 112 activities that we've seen these people doing. From this we’ve built a scientific model that lets us score companies based on what they do. There’s no perfect score, it’s about what stuff companies are doing and whether that’s right for them. The activities are broken into five categories, including penetration testing, version control, risk and compliance.
BN: How is the information used?
PH: We publish a report every year which is all creative commons and out in the open. We do charge people to be measured so there is a commercial aspect, but anyone can look at the BSIMM report and self-assess. The scores for any particular firm are kept secret, we don’t share what we found at particular businesses.
BN: So it's a bit like an audit?
PH: No really, it's typically done over a few days of interviews, we'll sit down with the heads of development, support, operations and testing. We have a pretty good set of questions having done this hundreds of times, but it’s not an accounting audit where we ask to see deliverables that demonstrate what’s being done.
BN: What advantage does it have for businesses and does it scale to smaller and medium enterprises?
It overcomes the difficulty of getting to grips with security. You don't have to go it alone and make it up, you can learn from what other people have done. We have interviewed some smaller companies but below a certain size -- say you have a mobile apps company with only 20 people -- this doesn't make sense for them. But any decent sized enterprise, especially one that's pulling software from lots of vendors and building many different apps, BSIMM works really well.
BN: Do some sectors benefit more than others?
PH: We don't talk about specific sectors very much until we have enough people in that sector to show results without revealing details about a particular member. So, we have 20 plus financial services companies for example so we can show an average for that sector without revealing anything about a particular company.
Financial services, independent software vendors, consumer electronics and healthcare are the areas where we have most data. What surprised us at first was how similar some sectors are -- financial services and software vendors for example. It's only as we’ve started to get into other verticals that we've started to see more differences. Healthcare for instance tends to have a lower score than other industries, this is because some industries tend to think of themselves as hardware based when today it's not true. Car makers too these days are increasingly in the software business because a modern car is a big computer with a petrol-based power supply.
The advantage BSIMM brings is that companies adapting to a changing business model can learn from others who have already analyzed what they do.
BN: What could companies that have suffered major data breaches learn from the BSIMM model?
PH: That list of 112 activities hasn't been the same over the years; it's changed. A couple of years ago we stared to see an activity called 'simulating a software crisis' where mature firms will test their procedures for dealing with a problem like a software breach. They'll involve all of the relevant departments including legal, PR and so on and work through how they’d deal with the problem.
A good example is Saleforce.com which is a member of BSIMM, a couple of months ago a cross-site scripting bug was discovered in a Saleforce admin panel. 30 days after this was reported the whole thing was fixed and Saleforce acknowledged the problem, they delivered the kind of response you’d expect from a mature organization. It’s not about being perfect and producing perfectly secure software every time, it’s about knowing what to do and how to handle the problem. By contrast the recent TalkTalk breach was handled quite badly as they took a long time to get out a coherent message.
BN: Is there a cost involved?
PH: In a sense it's a bit like ISO9001, you can go and read the standard and do everything yourself, but at some point you need a third-party to come along and verify what you've done. So yes, there is a nominal cost if someone wants to be measured by us, but it's not expensive.
A further advantage of joining is that we've created a community that brings together people from companies who've been measured and they can compare notes and realize that often they have the same problems.
Image Credit: Manczurov / Shutterstock
-

Top 50 UK websites expose your browser to unknown scripts
Publié: novembre 13, 2015, 12:02pm CET par Ian Barker

How much risk are you facing just by visiting a website? Do you know what scripts are running and which other sites they're pulling data from?
Malware prevention company Menlo Security scanned the Alexa top 50 UK websites to find out what their users were being exposed to. The findings show that on average, when visiting a top 50 UK site, your browser will execute 19 scripts.
It found that eight percent of the top 50 sites executed more than 50 scripts and that the top UK website ran a startling 125 unique scripts when requested. 72 percent of the top 50 sites executed fewer than 20 scripts, and one of the top 50 used just a single script. Two of the top three sites on the list are news websites.
What's also interesting is the amount of data being downloaded. 62 percent of sites downloaded less than 1MB of code, however, one media site downloaded 4.9MB. Media sites hold the top two places for the amount of downloaded code followed by social media sites making up the top five.
In addition the scan looked at the back end code of the sites and found 15 of the top 50 sites were running vulnerable versions of web-server code. Microsoft IIS version 7.5 was the most prominent vulnerable version reported, with known vulnerabilities going back more than five years.
"There are many legitimate reasons why developers use scripts to enhance the user experience of a website today, but similarly attackers can use scripting capabilities for iframe redirects and malvertising links to compromise browsers", Jason Steer, Menlo Security solutions architect of EMEA says, writing on the company's blog. "The main takeaways show that going to any popular website is now associated with some risk, as we see play out in numerous media stories every week. Knowing that visiting a top 10 site means that I'm allowing my browser to execute more than 25 scripts according to our data (that’s 25 scripts that may or may not be well written and/or secure), is a concern. What's more is that going to a top 25 UK website exposes my browser to more than 100 scripts without any knowledge of how good or bad they may be, and from over 50 unique websites in the background".
Tests were carried out against the Alexa Top 50 UK sites on October 15th using a 64-bit version of Chrome.
Image Credit: spaxiax / Shutterstock
-

Vormetric adds encryption and access control capabilities for Docker
Publié: novembre 12, 2015, 4:01pm CET par Ian Barker

Businesses are turning to encryption as a means of meeting compliance and data storage requirements and to guard against breaches and data loss.
But with the rapid evolution of enterprise IT data may be stored in a variety of environments in-house, in the cloud, which presents new security challenges.
Enterprise security company Vormetric is announcing an expansion of its Data Security Platform, with new capabilities that expand protection for sensitive data within datacenter, cloud, big data and application environments.
The latest platform offers encryption and access control capabilities for Docker, Hadoop, NoSQL and SQL as well as enhanced automation capabilities. It enables advanced protection against data breaches, while also helping organizations to meet strict compliance and regulatory requirements.
"The many advances in functionality and features added to the Vormetric Data Security Platform will help our customers deploy more easily, as well as protect data more completely, in more environments, and with minimal business impact," says Vice President of Product Management for Vormetric, Derek Tumulak. "We believe that Vormetric's rapid implementation and support of new environments and use cases gives our customers great investment protection, empowering them to safely adopt new technologies and platforms without having to disrupt operations or implement costly new security infrastructure sets".
New features include protection for data at rest in Docker containers. The solution's encryption, access controls, and security intelligence logs can now be used to safeguard and control container images and backups, ensuring that they only run in authorized environments.
It allows easier deployment of database field-level encryption by ensuring that the encrypted data size matches the existing database field size, avoiding database schema changes. Extension of data security access controls for Hadoop allows a higher level of security and policy-based isolation within Hadoop environments, delivering granular per-user or per-group access policies to encrypted files or folders within the Hadoop Distributed File System (HDFS) namespace.
The new capabilities will be available in the first quarter of 2016, you can find out more on the Vormetric blog.
Image Credit: Maksim Kabakou / Shutterstock
-

Predictive analytics help guide the sales process
Publié: novembre 12, 2015, 3:00pm CET par Ian Barker

Sales teams are often saddled with outdated analytics and reporting which means that they lack a clear understanding of what's needed to drive the sales process forward.
Smart sales specialist TAS Group is launching a new Sales Performance Manager as part of its Dealmaker platform, which is aimed at helping sales leaders and their teams manage every aspect of their sales pipeline and performance with built-in knowledge and insights to help guide their decisions.
"Dealmaker Sales Performance Manager is exactly what sales leaders need to cut out ambiguity and take real, substantial steps forward," says Donal Daly, CEO of The TAS Group. "Our software is informed by 30 years of experience and over 200 enterprise customers who are drawing billions of dollars of revenue every month. These insights go beyond analytics; they offer total visibility into the pipeline with all of that industry expertise for context. We wanted our customers to have accurate forecasts and explosive pipelines. With Dealmaker Sales Performance Manager, we’re giving them the understanding and guidance they need to get them".
Dealmaker Sales Performance Manager is built natively on the Salesforce platform. Key features include a specially developed system of key performance indicators (KPIs) for measuring sales success, plus real-time visibility into a sales organization’s current state, so teams can constantly access a complete, accurate understanding of their performance.
Informed pipeline management allows teams to create a strategy, tailored to each sales team’s specific needs and challenges. This also allows for instant performance reviews, highlighting the challenges and successes and illustrating best practices for even better results in the coming quarter.
Sales Performance Manager is available on any internet-connected mobile device, meaning actionable intelligence and sales tools are available at any time. More details can be found on the TAS Group website.
Image Credit: Syda Productions / Shutterstock
-

Built-in safety measures create a false sense of security
Publié: novembre 12, 2015, 1:06pm CET par Ian Barker

It's increasingly common for hardware manufacturers and software developers to build in various security measures to protect users.
However, a new survey by cloud encryption company Alertsec reveals that these standard security precautions may be creating a false sense of security for PC and mobile users.
The Alertsec SMB 2015 Encryption Study, carried out among 1,255 small-to-medium businesses reveals that 68 percent believe auto-saved passwords are not secure. Nearly half (48 percent) believe never logging out of user profiles decreases security. Over one in five SMB executives (23 percent) believe lock down -- when functionality of the system is restricted -- is not secure, while 16 percent believe that locking out systems following multiple failed password attempts is also insecure.
"The real problem is the false sense of security these 'security precautions' create," says Ebba Blitz, President of Alertsec. "Computer manufacturers and software vendors offer a variety of built-in solutions that seem to protect you, but they are no match for the run-of-the-mill cybercriminal. That's why encryption is so important. Losing data could cause a problem of catastrophic proportions for any individual and any company".
87 percent of those surveyed say they fear data breaches. When pressed further most cited physical security fears, with 40 percent of respondents saying they fear leaving their laptop in the car and consequently having their identity stolen, 37 percent fear having their laptop stolen while working at a coffee shop, 30 percent fear burglars breaking into their homes and obtaining online banking information and 27 percent worry about having their laptop stolen at airport security and having their cloud storage and photo files breached.
Perhaps no surprise then that 68 percent say the problems they have seen at work have made them encrypt their personal computers. An impressive 90 percent say that work computers should be encrypted, followed by smartphones (61 percent), personal computers (58 percent) and tablets (55 percent).
More about how encryption can be used to secure devices is available on the Alertsec website.
Image Credit: Sergey Nivens / Shutterstock
-

Companies vulnerable to cyber attack as defenses lag behind threats
Publié: novembre 12, 2015, 11:39am CET par Ian Barker

Security solutions are lagging behind and failing to provide protection or detection levels adequate to protect against today's security threats.
This is according to a new survey from security and compliance solutions company Promisec. The results point to increased security gaps and vulnerabilities in spite of widespread fear of security breaches.
The survey spoke to over 150 IT decision makers and 74 percent said traditional anti-virus defenses no longer address advanced targeted threats, with only 26 percent believing they will play a vital role in the future. This compares to 58 percent and 19 percent respectively, in last year’s survey, which illustrates a continued trend away from traditional anti-virus defenses.
Yet despite this recognition and the fact that 73 percent of respondents say endpoints are most vulnerable to attack, fewer companies today (32 percent) say they have advanced endpoint security protections in place, down from 39 percent last year.
"Results from our survey indicate that for many companies, endpoints remain highly vulnerable to a cyber-attack as threat levels continue to rise," says Dan Ross, CEO of Promisec. "We continue to see new breed of more complex and sophisticated threats, where traditional blocking and prevention mechanisms, such as firewall, anti-virus and anti-malware software, are no longer enough to keep our networks safe. Companies need to aggressively fortify their endpoint security infrastructure as a critical part of their total security portfolio in order to keep pace with the rapid evolution of today’s most severe threats".
The survey also finds that 82 percent of IT professionals are either 'highly' or 'moderately' concerned about a potential security breach in the next year but only 31 percent say they are 'well prepared' for a cyber-attack.
You can read more about the survey on the Promisec blog and there's a summary of the findings in the infographic below.
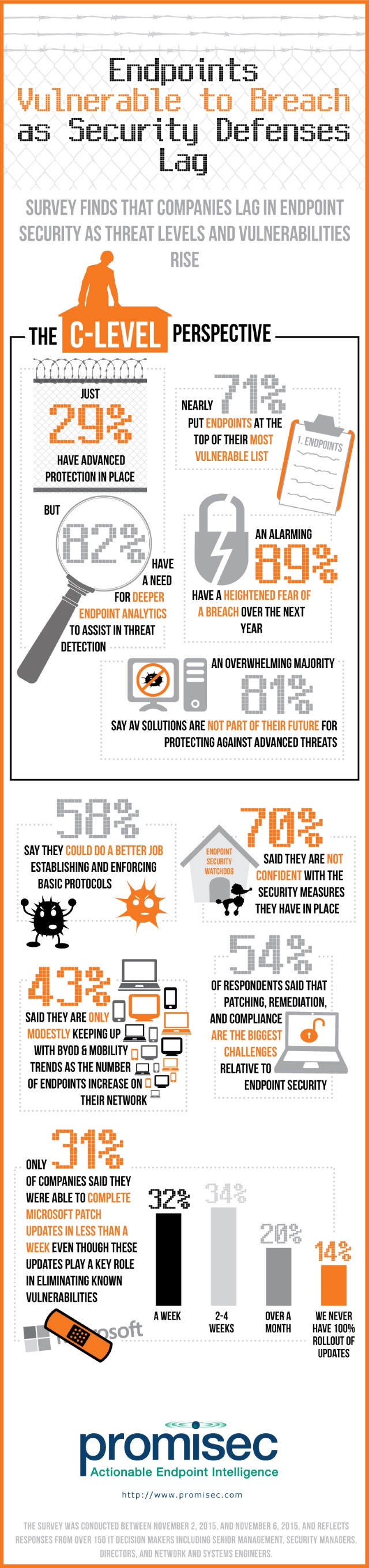
Image Credit: underverse /Shutterstock
-

New Clarizen release delivers simpler collaboration and improved visibility
Publié: novembre 11, 2015, 3:38pm CET par Ian Barker

Work management software company Clarizen is announcing its latest release which delivers new options for viewing work and integration with the JIRA development workflow package.
Major features include an interactive Gantt view gives users visual representation of the workplan, on which they can take action, such as rescheduling work by dragging and dropping or creating dependencies by linking tasks. Users can also display key attributes -- for example percentage complete or dates -- on the Gantt bars, and share the Gantt as a widget with internal and external stakeholders.
A new real-time calendar display allowing users to view and manage all their work. This can be color-coded to focus on status, priority, or manager for improved visibility.
Analytic snapshot apps enable trend analysis on project performance to identify problem areas. Administrators can track daily active users on the application and identify where user adoption is low or where users may need extra training. They can capture information for daily trend snapshots, plus track actual, remaining and expected progress over time.
JIRA v2 integration strengthens connections between teams. When one part of a team uses JIRA for software coding and bug tracking while the rest of the project is managed in Clarizen, all stakeholders can be kept in sync as key JIRA data is reflected in Clarizen and vice versa. The flexible, out-of-the-box integration features best practice mappings and events, with an easy-to-use administration layer designed for business users.
Other new features include the ability to have multiple managers on all work objects, view project cases in separate panels, and push notifications for Clarizen's iPhone app.
"Teams are empowered when workers at all levels within an organization can view, manage and collaborate on their work," says Avinoam Nowogrodski, CEO of Clarizen. "Our Fall Release further expands our customers’ visibility into their businesses, so they can make decisions in real time".
The new release is available at no charge to existing Clarizen users, with the exception of JIRA integration which requires an extra license. A webinar showcasing the product's features will be held on 23 November.
Image Credit: Tischenko Irina / Shutterstock
-

The performance impact of internet security products
Publié: novembre 11, 2015, 12:46pm CET par Ian Barker
Many people cite performance issues as a reason why they're reluctant to run or end up uninstalling internet security products.
Independent testing organization AV-Comparatives has released the results of its latest studies on a range of security products, focussing on how they impact system performance.
It tested 19 products on an HP 350 G1 system running Windows 10 Home 64-bit and measured the impact on file copying, archiving and unarchiving, installing and uninstalling applications, launching applications, downloading files, and the PC Mark 8 testing software.
Using a system with no security software as a baseline it came up with an impact score for each product. An 'out of the box' system with Windows Defender installed scored 16.2, least impact was recorded by Avira on 2.3 and Avast on 2.7 with Kaspersky third on 5.4.
At the other end of the scale there's a tie for most impact recorded, with ThreatTrack Vipre and Fortinet FortiClient both with an impact score of 27.5. Lavasoft on 16.3 and BullGuard on 16.7 both have similar impact to a standard Windows Defender system.
The report points out that other factors, such as the age of the machine, the amount of RAM available, the contents of the hard drive and whether other software is up to date can also have an impact on performance.
The full report can be downloaded from the AV-Comparatives site with details of all the products tested and charts showing how they compare for different functions.
Image Credit: alexmillos / Shutterstock
-

The future for enterprise mobility [Q&A]
Publié: novembre 11, 2015, 11:32am CET par Ian Barker

The shift towards mobile computing and BYOD has been the big story in enterprise IT over the past couple of years.
But has the trend towards mobile peaked? Can we expect BYOD to move into smaller organizations and what effect will legal and regulatory frameworks have? We spoke to Gary Greenbaum, CEO of BYOD billing specialist Syntonic to find out.
BN: Are we seeing a slow down in enterprise mobile adoption and if so is this a long-term trend or just a blip?
GG: The big trend at work is less about enterprise mobility adoption, that's already happened en masse. It's more about the consumerization of IT, whereby IT is adopting consumer-driven technologies brought into the work environment by employees, a trend that has been active for over five years and that shows no signs of abating. Increasing reliance on mobile devices in the enterprise is driven by ever more powerful mobile computing devices and employee preferences for consumer applications that can also be used for business, such as Outlook or Skype. The consumerization of IT trend has mutual benefits for the employer and the employee. The enterprise has enjoyed tremendous productivity gains as consumers bring increasingly powerful smartphones and other mobile devices into the workplace. Employees have achieved greater flexibility to work from anywhere and use the apps and tools they’re familiar with. The line between work and personal life has blurred. Work is no longer a geographic location where employees go: it's what employees do. BYOD is enabling this new way of working.
BN: What will be the effect of the class action lawsuits for BYOD employee reimbursement in California and Massachusetts? Can we expect these to spread elsewhere?
GG: What happens in California doesn't stay in California. The conclusion of Cochran v. Schwan's Home Services class action lawsuit was noteworthy because it simply reasserted existing labor law and didn't introduce any new law. BYOD reimbursement is fair work practice that is similar to other forms of business reimbursement. Similar labor laws are active in many other states and we expect to see on-going employee lawsuits seeking fair compensation.
BN: How will smaller businesses be able to cope with demands for BYOD and the associated regulatory pressures?
GG: The industry has been remiss about building solutions for SMBs. The same California law that requires employers to reimburse employees for mobile phone use applies to both enterprises and SMBs. Small and medium size businesses require a split billing solution, just as much as the large enterprise. Split billing helps SMBs remain compliant by ensuring accurate reimbursement for mobile usage. To date, Enterprise Mobility Management (EMM) vendors have focused their offerings on large enterprises with solutions that aren’t well suited to the needs of SMBs.
SMBs are left with four options:
1. Force employees to fill out time-intensive expense reports
2. Estimate reimbursement amounts
3. Don’t reimburse employees
4. Adopt a split billing solution to accurately segment mobile usageOptions 1, 2, and 3 are not tenable. Forcing employees to fill out expense reports is costly and fraught with guesswork since mobile bills only list the date, time and megabytes used, with no tie-back to actual business usage. Estimating reimbursement amounts doesn't provide accurate accounting and leads to over-generous stipends that inflate company BYOD costs. Finally, the recent enforcement of existing labor law in California requires employers to reimburse employees when they use their mobile devices for business use.
Adopting a split billing solution, is the most cost-effective option since it not only allows employers to reimburse and remain compliant, but it also provides analytics insights to understand how employees are using mobile devices so businesses can better forecast and budget. Today's split billing also provides turnkey solutions that are easy to manage with minimal IT resources.
BN: Can we expect to see Apple making more efforts to take on Android in the workplace?
GG: Android has had tremendous success with BYOD outside of the US, while Apple has enjoyed the lion's share of the US BYOD market. It's not a birthright to have the dominant mobile OS, as Blackberry's past mobile ventures clearly demonstrate. Apple will do what's necessary to maintain their position, pursuing business feature parity with Android, and if the past is indicative of the future, they’ll provide differentiated value with their iOS enterprise offering.
There's also a channel need that hasn't been addressed. Consumers don't currently choose a phone by evaluating how well it meshes with their work environment, such as separating business use from personal use. A phone that makes it easy to get reimbursed by your employer opens up new opportunities for handset manufacturers, mobile operators, and solution providers to deliver new, differentiated value to consumers.
BN: Where is enterprise mobility expanding fastest?
GG: Core business services are pivoting to mobile due to the confluence of ubiquitous employee smartphone adoption, cloud services, and the growth of mobile business applications, Employers and employees now expect work to be conducted on mobile devices. The big drivers behind this growth are business productivity and employee flexibility. The landscape has changed: gone are the voice-only phones of the past. Business apps and services are now available online. The new opportunity for businesses is to efficiently grow employee mobile services while reducing Capex.
BN: Will we see further consolidation of enterprise mobility management providers in 2016?
GG: Yes. The IBM acquisition of Fiberlink's MaaS360, VMWare's acquisition of AirWatch, and Blackberry's acquisition of Good Technology are part of an overall EMM consolidation trend, aggregating functionality and services to single vendor solutions. Dell has become a one-stop destination for enterprise solutions with storage, network, cloud services, virtualized hardware, and device management. Consolidation is also an indication that the BYOD market is maturing and going mainstream.
Image Credit: Max Griboedov/Shutterstock
-

One in 10 Brits believe AI is evil
Publié: novembre 10, 2015, 5:41pm CET par Ian Barker

Most people in Britain believe that artificial intelligence is a force for good according to a new survey, with only one in 10 thinking that it’s evil.
This is one of the findings of research by marketing technology company Rocket Fuel which finds broad public optimism about AI across the UK.
A large majority (92 percent) claim some understanding of what AI is and almost half (48 percent) believe AI is a force for good or mostly good. 42 percent of Brits are excited by AI or think it will solve big world problems. However, 21 percent see AI as a threat or are scared by it.
There is a greater awareness of the uses of AI in everyday life among men than women, with women more likely to perceive AI as a thing of science fiction or limited to laboratories (21 percent), compared to men (13 percent).
When it comes to the workplace 45 percent don't believe AI will impact their job, 10 percent think it will have a positive effect and nine percent believe their job will be under threat. Interestingly those on the lowest incomes are more likely to see AI as changing their job for the better.
Perhaps surprisingly it's younger age groups who are most suspicious of the technology, with 20 percent of 18-24 year olds citing AI as a force for evil, double the percentage of any other age group. Also 18 percent of 18-24 year olds believe that AI will threaten their jobs, again double the number of any other age group.
"Artificial intelligence continues to hit the headlines and there has been a lot of discussion about the negative impact this technology could have on our lives. As a company that uses AI to power our business and drive better, more efficient outcomes for our clients' marketing campaigns, we were interested to understand just what the British public’s perception of AI is," says Dominic Trigg, Rocket Fuel’s SVP and MD Europe and emerging markets. "We were pleasantly surprised by the findings, with the overall sentiment towards AI being very positive amongst a well-informed British public. We believe AI is already making a positive impact in a number of industries and we believe that it is more likely to continue to offer practical improvements, innovation and efficiency to the UK, rather than any danger".
More information about AI and its role in marketing can be found on the Rocket Fuel website.
Image Credit: Mopic / Shutterstock
-

Looker makes Google BigQuery available across the enterprise
Publié: novembre 10, 2015, 5:11pm CET par Ian Barker

Whilst most organizations recognize the importance of big data, the tools needed to obtain value from it are often complex and unweildy.
To make it easy for companies to build an organization-wide data analytics platform, business analytics specialist Looker is launching Looker Blocks for the Google BigQuery cloud analytics service.
BigQuery, unlike other databases, never runs out of storage and never gets slow, Looker claims its offering is the only tool that lets users harness the power of the underlying database with its unique in-database architecture. Looker operates on the data directly in BigQuery, never extracting subsets of data, making for incredibly fast queries against all of the data available to everyone.
"Looker and BigQuery are compatible because both technologies are, at the core, architected to scale. Whether you have 250GB or Petabytes of data, Looker makes data exploration easy and accessible to everyone at a company." says Frank Bien, CEO of Looker. "We aren't just a visualization tool that only analyzes subsets of the data, we are a reliable data platform for organization-wide analytics and business metrics".
Specific Looker Blocks and additional features to connect with the Google Cloud include Table Date Range Analytics which makes BigQuery's unique approach to data partitioning seamless for end users and optimizes query performance, making it easy to understand event data over time, and gain insight into every aspect of consumer behavior.
A Query Size Estimator lets data analysts determine the size of a query directly within Looker’s data platform -- before it's run -- giving data analysts greater insight for database management. The Google Analytics Premium Looker Block comes pre-built with a full suite of web analytics metrics such as funnels, bounce rates, and attribution analysis. Once up and running with the GA Premium Block, users can then layer on additional custom analysis to understand the metrics that drive their business.
More information on using Looker with Google BigQuery can be found on the company's website.
Photo Credit: Sergey Nivens / Shutterstock
-

RoboForm boosts security with two-factor authentication
Publié: novembre 10, 2015, 4:36pm CET par Ian Barker

Two-factor authentication is increasingly common as a way of verifying logins to websites so that you’re not relying on just a password.
Now Siber Systems maker of the popular RoboForm password manager is adding 2FA to allow users to receive a password via text message to verify trusted desktop, laptop and mobile devices for repeat use with the software.
"People are rightly concerned about the security of their sensitive personal information and financial accounts," says Bill Carey, Siber Systems VP of Marketing. "Hackers are becoming more sophisticated all the time, causing a record number of data breaches that can affect hundreds of millions of people. Our multifactor authentication option improves security by ensuring that only registered computers and mobile devices can access a user's RoboForm Everywhere account. By limiting the possibility of outside access to a user's account, we've created one of the strongest security solutions on the market today".
RoboForm Everywhere subscribers can use multifactor authentication protection for free on an opt-in basis. This enables them to expand the trusted environment for their passwords by verifying their personal laptops, PCs and mobile devices before accessing their RoboForm information.
Once a user has opted in, the feature will send a one-time password either via text message or to the user's registered email account the first time they log on from an unregistered computer or mobile device. The message will contain a code the subscriber can use to verify the device. Once the device is registered, it's approved for repeat use with the user name and log-in password. Users can also delete devices from the approved list any time.
For more information on using the software and 2FA you can visit the RoboForm site.
Photo Credit: JMiks/Shutterstock
-

Twistlock strengthens container security for enterprises on Google Cloud
Publié: novembre 10, 2015, 3:40pm CET par Ian Barker

More and more businesses are adopting a container strategy but this leads to problems for operations and security staff seeking to maintain control and visibility.
Container security specialist Twistock released its Container Security Suite in beta back in May and has now announced general availability of the product along with its participation in the Google Cloud Platform partner program.
"Containers bring unprecedented speed and agility that allow DevOps to quickly respond to changing business needs. But organizations are concerned about the robustness of policy management and the ability to support organizational compliance needs," says Ben Bernstein, CEO and co-founder of Twistlock. "This integration is significant because Google Cloud Platform users can use Twistlock technologies to have the visibility and controls they need to maximize business efficiency and potential for innovations".
Integration with Google Cloud Platform (GCP) provides container image scanning, access control functions, and the ability to enforce runtime security policies to protect containerized applications running on GCP.
Twistlock allows users to scan images in Google Container Registry for CVE (Common Vulnerabilities and Exposures) and for policy compliance. They can also detect anomalies in a running container engine cluster and take automated corrective actions, such as raising an alert or disconnecting the container’s network access. In addition it can generate reports of policy violations in both Container Registry and Container Engine.
For users there are three parts to Twistlock for GCP, a Registry Scanner that performs vulnerability scanning for container registries, and the Twistlock Console which is both a policy configuration portal and a central dashboard for all Twistlock tasks. Plus there's Twistlock Defender which runs on the same host as protected container workloads and monitors container health, applies configuration policies, and reports container information back to the console.
More information is available on the Twistlock blog and users can request a free trial of the platform on the company's site.
Image Credit: VERSUSstudio / Shutterstock
-

New compliance solution helps developers tackle software piracy
Publié: novembre 10, 2015, 3:07pm CET par Ian Barker

A recent study by the Business Software Alliance estimated that 43 percent of software installed today is not properly licensed, which equates to more than $63 billion in lost revenue.
SmartFlow Compliance Solutions is launching an innovative solution designed to help companies combat intellectual property theft and establish effective in-house compliance programs.
"Software piracy is becoming a rampant global epidemic with significant impacts on businesses and the economy," says Ted Miracco, CEO of SmartFlow. "We've developed a turnkey solution that allows businesses to start seeing ROI immediately. Armed with SmartFlow, our clients proactively take charge of the situation by tracking down pirated versions of their software and compiling the data to take necessary action against IP theft. We streamline the compliance enforcement process, so it’s simple and effective for companies to recover this valuable source of revenue, while protecting their paying customers from unfair competition".
SmartFlow is built in at the development stage and works a bit like an 'Easter egg' in an application, allowing the developer to determine where it's being used and whether it's properly licensed.
SmartFlow's data collection capabilities can be fine-tuned to comply with specific information regulations across the globe. This makes for comprehensive data reporting, so developers can build a stronger case against blatant IP thieves as well as alerting companies that may be unintentionally non-compliant.
Available now, the SmartFlow product suite includes a SmartFlow Software Development Kit (SDK), which monitors applications to ensure they are being used in compliance with licensing terms, and SmartFlow Professional or SmartFlow Enterprise programs, which provide everything a company needs to establish an in-house compliance program.
For more information and pricing you can visit the SmartFlow website.
Image Credit: Feng Yu / Shutterstock
-

Addressing the mobile app trust gap
Publié: novembre 10, 2015, 12:02pm CET par Ian Barker

According to a new survey 80 percent of consumers would stop being a customer if there were a security breach in a company's mobile app. But app developers admit in the same study that many apps are not secure due to pressure to release them to market before they are ready.
These findings come from mobile security and analytics company Bluebox Security which talked to over 400 consumers and approximately 300 developers.
The results reveal that 69 percent of consumers are somewhat to very confident that the apps they use are safe from hackers. However, this confidence is misplaced as the developers of those apps confess they are not secure. In fact, 74 percent of developers believe most mobile apps are moderately vulnerable and 24 percent say they are highly vulnerable.
Almost half of all developers admit that they have rushed an app to market, despite it not being completely ready. Also 53 percent of developers admit that they have taken shortcuts or put temporary solutions in place in order to get their app out on time. Developers are using unsecured third party frameworks too, 96 percent say they use third party frameworks that may or may not be safe to build their apps. Only 32 percent said that they would prefer to develop their own code.
To address these issues Bluebox is launching a new solution for enterprises to secure their consumer-facing apps and fight back against mobile threats that are placing consumers and businesses at risk. Bluebox for Consumer Apps allows enterprises to turn their consumer mobile apps -- those available on the Apple App and Google Play stores -- into self-defending apps that secure, detect and respond to mobile threats, and provide mobile threat intelligence data with a single click.
"Companies have underinvested in mobile security in a rush to become mobile first, and now the bill is due. With mobile threats being discovered almost daily, and enterprises losing control over consumer devices, it's only a matter of time before a mobile hack is the root of the next major breach," says Pam Kostka, CEO of Bluebox. "Our goal is to enable businesses to have confidence in the security posture of the apps that they build and distribute. Our security and threat analytics are easily embedded with the click of a button, transforming any app into a self-protecting island that can intelligently defend itself in real-time when it is in a hostile environment or actively under attack".
The complete survey findings are available on the Bluebox blog and Bluebox for Mobile Apps will be available in December.
Image Credit: LovePHY / Shutterstock
-

New machine learning solution delivers insight into VMware environments
Publié: novembre 10, 2015, 10:49am CET par Ian Barker

As many businesses have shifted their systems to VMware environments they have a need for real-time insights into application and server performance, efficiency, and reliability.
To meet this need SIOS Technology is announcing the latest release of its SIOS iQ machine learning analytics software. This offers new features to deliver accuracy and precision in performance analysis for VMware environments.
"By putting all key information about an organization's infrastructure at their fingertips, SIOS iQ enables IT managers to ensure their applications are operating efficiently, that issues are identified and resolved quickly, and that VMware resources are not being wasted," says Jerry Melnick, president and CEO at SIOS Technology. "These newest enhancements further simplify the understanding of IT operations and help resolve issues in dynamic virtual environments".
Highlights of SIOS iQ 3.3 include a best practice analysis feature which enables SIOS iQ to provide insights on performance, efficiency, reliability, and capacity utilization immediately after implementation. Using event injection it enables VMware vRealize Operations Manager 6.0 (vROps) to display high availability cluster health, host-based caching configuration recommendations, undersized VMs, idle resources and more, making it easier to stop and fix performance issues.
Version 3.4 will include a Topology Impact Analysis View -- a visual map of the VMware infrastructure showing interrelated objects (VMs, network, storage, and applications) and their relationships, highlighting current status and anomalous behavior. Drill down screens will enable IT staff to explore the detailed root causes of performance issues and recommendations for improvement.
IT staff will be able to augment SIOS iQ's understanding of both normal and anomalous infrastructure behavior by adding extra parameters for increased precision and accuracy. It will also offer a SIOS PERC Dashboard reliability indicator, showing the number of host failures that a cluster has sustained over time and indicating when there are not enough hosts to sustain future failures.
SIOS iQ 3.3 is available now, version 3.4 will be released by the end of the year, for more information and pricing visit the SIOS website.
Image Credit: art4all / Shutterstock
-

New incident response platform aims to improve cyber resilience
Publié: novembre 9, 2015, 3:10pm CET par Ian Barker

According to a recent study by the Ponemon Institute, more than 90 percent of organizations recognize cyber resilience as an essential part of protecting their core assets and business interests.
Part of creating that protection is to have an effective plan for when things go wrong and incident response solutions specialist Resilient Systems is releasing version 24 of its Incident Response Platform (IRP). The release features strategic integrations with IBM X-Force's threat intelligence feed and HP ArcSight, enabling organizations to gain insight more quickly and respond more intelligently to cyber threats and attacks of all types.
"Effective response starts with strong context and intelligence, which is why we've partnered with IBM X-Force, strengthened our integration with HP ArcSight, and introduced custom threat feeds to empower our customers with the best information about the latest threats," says John Bruce, co-founder and CEO of Resilient Systems. "And in response to increasing demand from larger organizations, we've added features that make their deployments even easier".
The new IRP release also incorporates features aimed at large enterprises to speed up deployments. These include LDAP (Lightweight Directory Access Protocol) support to allow security teams to manage and authenticate users of Resilient Systems from within Active Directory. Configuration migration provides customers with large and complex systems the flexibility to easily move configurations across environments, from development and testing into production.
For customers with Resilient Systems installed on-premise it also provides new documentation to help them maintain high availability by using capabilities within their virtual infrastructure.
"Over the last five years, we've pioneered the incident response space by creating the first-ever Incident Response Platform. We have deployed this platform globally for more than 100 on-premise and SaaS customers, evolving in each release to meet their critical IR requirements," says Bruce. "Now in version 24, the platform reflects this evolution with even more enhancements. It’s fast becoming the industry standard for organizations in need of a response solution that will improve their resilience -- today and in the future".
You can find more on the Ponemon resilience study and details of the latest release on the Resilient Systems website.
Photo Credit: Sergey Nivens/Shutterstock
-

Apple IDs targeted in global phishing scam
Publié: novembre 9, 2015, 1:42pm CET par Ian Barker

A new phishing threat is targeting businesses and consumers with Apple IDs in an effort to steal IDs, passwords and credit card information.
The attack has been identified by Comodo Antispam Labs and looks like an official Apple email. It has the Apple logo and includes Apple's physical address, as well as an email address that, at a quick glance, appears to to be from Apple -- giving the recipient the illusion of the message being authentic.
The messages claims that limitations have been placed on the user's account and that they need to provide additional verification information by clicking a link.
They don't have the usual tell tale poor spelling and grammar that identify phishing attacks. If the link is clicked it leads to pages with a similarly authentic Apple look and feel that ask for passwords and billing information including payment card details.
The Comodo Antispam Labs team identified the Apple phishing email through IP, domain, and URL analysis, along with the Labs' continuous monitoring and scanning of data from the users of Comodo's internet security systems.
"The Comodo Antispam Lab is an expert resource of engineers and computer science professionals, who use innovative and proprietary Comodo cybersecurity technology to protect and secure the online world," says Fatih Orhan, Director of Technology for Comodo. "We will continue to work diligently in creating and implementing innovative technology solutions that stay a step ahead of the cyber criminals, and keep enterprises and IT environments safe".
More details of the scam can be found on the Comodo blog.
Image Credit: wk1003mike / Shutterstock
-

Post-Stagefright analysis shows Android users remain indifferent to attacks
Publié: novembre 9, 2015, 12:05pm CET par Ian Barker

In the past few months, Android users have seen a series of attacks by hackers exploiting bugs, collectively putting more than a billion devices at risk worldwide.
In late July, Stagefright hit the news as a weakness in the system that was being exploited by hackers. This was followed by Stagefright 2.0 and Kemoge, making for massive malware attacks on Android phones in three out of the last four months.
360 Mobile Security has used analytics to determine the response of its 24 million US users in the wake of Stagefright. It found that junk files cleaned saw a 62.6 percent increase, viruses found were up by 2.8 percent in the first week and an additional 11 percent the following week. The number of antiviruses installed saw a 13 percent increase and weekly new users also saw a 13.4 percent increase.
These findings echo 360's previous report in July which found that there's a disconnect between the mobile security threats that exist, and users' willingness to protect themselves and their devices from them.
The report recommends that in order to stay safe users should, only install apps from trusted official app stores and avoid using third party sources, never click links from suspicious emails and texts, always have their device upgraded to the newest version of the operating system, and use a trusted antivirus app. It concludes, "Preventing a virus from infecting your phone through the use of a security app is much simpler than trying to cure it after it appears and infiltrates a mobile device".
You can learn more about how to protect your Android device on the 360 Security website.
Image Credit: Christos Georghiou / Shutterstock
-

Poor management of admin accounts puts businesses at risk
Publié: novembre 9, 2015, 11:07am CET par Ian Barker

Login details for an administrator or other privileged account falling into the wrong hands can have serious consequences for a business.
But a new global security survey from Dell reveals that organizations have haphazard processes for managing administrative or other privileged accounts, making them vulnerable to security breaches.
Among the findings are that 76 percent of IT security professionals believe better control of privileged accounts would reduce the likelihood of a breach. Nearly 80 percent of respondents have a defined process for managing privileged accounts, but admit they aren't diligent about following it. In fact, almost 30 percent say they still use manual processes such as Excel or other spreadsheets to manage privileged accounts. Not only are these processes prone to error and easily compromised, they can impede quick resolution in time-critical situations.
The three most critical account management issues are listed as, default admin passwords on hardware and software not being consistently changed (37 percent), multiple admins sharing a common set of credentials (37 percent), and an inability to consistently identify individuals responsible for administrator activities (31 percent).
Although over 75 percent say they have a defined process for changing the default admin password on hardware and software as new resources are brought into the organization, only 26 percent say they change admin passwords monthly on mission critical systems and devices.
"Privileged accounts really are the 'keys to the kingdom,' which is why hackers seek them out and why we've seen so many high-profile breaches over the past few years use these critical credentials," says John Milburn, executive director and general manager, Identity and Access Management at Dell Security. "To alleviate this risk and ensure these accounts are controlled and secured, it's absolutely crucial for organizations to have a secure, auditable process to protect them. A good privileged account management strategy includes a password safe, as well as least-privileged control to protect organizational assets from breaches. Dell Security solutions cover the entire range of customer needs, including privilege safe, delegation/least-privileged access, and audit and monitoring, along with significant, integrated adjacent technologies for Active Directory bridge and multifactor authentication".
More about the report and best practices for securing privileged accounts is available on the Dell Security website.
Image Credit: Africa Studio / Shutterstock
-

Location is key to app experiences but users are reluctant to share it
Publié: novembre 6, 2015, 12:56pm CET par Ian Barker

According to a new survey 83 percent of app users say location is crucial to their app experiences, but nearly 40 percent are hesitant to share their location.
These are part of the findings of a study by Skyhook Wireless which looks at the extent to which people turn location services on or off for their apps and tries to understand why many smartphone users choose not to take advantage of the benefits sharing location can bring.
The results reveal that nearly 40 percent of app users hesitate to share location data, with 18 percent turning location services off for all apps. 50 percent of those users name privacy concerns as the top reason to turn off location, 23 percent don't see the value of location data and 19 percent cite battery drain concerns.
Out of the nearly 20 percent of app users who turn off location services for all of their apps, 63 percent have done so because of battery drain concerns, 45 percent privacy concerns, 23 percent don't see the value of giving their location data and 20 percent switch location services off in an effort to avoid advertising.
Consumers expect real benefits from their apps in exchange for turning location on. Half of all app users expect an accurate location, relevant app content and targeted offers or coupons once their location data is shared. 34 percent of smartphone users expect personalized communications and 25 percent keep location services on in order to get offers and notifications.
"This data suggests that there's a huge and largely untapped opportunity to create value from location services that many app publishers and advertisers could be taking full advantage of," says Skyhook CEO Jim Crowley. "Ultimately, it's all about the payoff to consumers. Users need to be informed about the ways in which location services add meaningful value to their app experience, and educated about how their privacy is being managed -- so that the critical benefits outweigh any attendant concerns".
You can see a summary of the research findings in infographic form below, and there's a look at techniques for getting users to turn on location services on the Skyhook blog.
Image Credit: Ralwel / Shutterstock
-

Linux Foundation teams with big industry players to launch Open API Initiative
Publié: novembre 5, 2015, 5:01pm CET par Ian Barker

As we've seen with IBM's announcement earlier today, APIs are flavor of the development month at the moment.
Now the The Linux Foundation, a non-profit organization dedicated to accelerating the growth of Linux and collaborative development, is announcing the launch of an Open API Initiative to promote and facilitate the adoption and use of an open API standard.
The initiative is supported by some big names including Capital One, Google, IBM, Microsoft and PayPal. It will extend the Swagger specification, created in 2010, which is a description format used by developers to design and deliver APIs that support a range of connected applications and services.
"Swagger is considered one of the most popular frameworks for building APIs. When an open source project reaches this level of maturity, it just can’t be managed by one company, organization or developer," says Jim Zemlin, executive director at The Linux Foundation. "The Open API Initiative will extend this technology to advance connected application development through open standards".
Downloads of Swagger and Swagger tooling have almost tripled over the last year, and it's considered the most popular open source framework for defining and creating RESTful APIs. SmartBear recently acquired the Swagger API open source project from Reverb Technologies and today is working with its industry peers to ensure the specification and format can be used and developed for years to come.
"Across industries, Swagger has gained incredible adoption for its expressiveness, comprehensive toolchain and vibrant community alike," says Tony Tam, VP of Products, Swagger at SmartBear and founder of the Swagger open-source project. "Working with both API vendors and consumers, SmartBear sees the value in open governance around the specification which will allow for even more rapid growth and adoption across the API industry, and is honored to donate the Swagger Specification into the Open API Initiative under The Linux Foundation".
More information on this and other collaborative projects is available on the Linux Foundation website.
Image Credit: Profit_Image / Shutterstock
-

New solution helps track hybrid mobile app performance
Publié: novembre 5, 2015, 4:38pm CET par Ian Barker

Gartner predicts that by 2016 more than 50 percent of mobile apps will be hybrid, combining elements of both native and Web applications.
This allows apps to benefit from the portability of HTML5 Web apps along with a container that allows access to a device's native features. For businesses they offer faster development with easier updating and management.
To help realize these benefits, mobile app intelligence company Crittercism is launching a new extension to its iOS and Android SDKs that tracks the real-time user experience, performance issues and diagnostic data of hybrid apps.
"We've seen tremendous activity in hybrid app development among our customers in recent years, and the challenge has always been understanding user experience," says Robert Kwok, chief technology officer and co-founder of Crittercism. "Many times performance issues can arise as users transition between the static, native side of an app and the more dynamic Web side. Historically, two separate agents, one on the mobile device and the other on the server, have been used to attempt to monitor hybrid, but this approach is cumbersome and offers an incomplete picture of user experience. Crittercism's new single mobile agent unifies the monitoring of the disparate parts of a hybrid app so that companies can better understand and optimize their customers' journey".
The new hybrid solution can be combined with Crittercism's Business Transactions feature, which allows customers to focus on mission-critical user work flows. For hybrid apps these work flows may span both the native and Web portions so there's a need for unified intelligence.
More information on hybrid support can be found on the Crittercism blog.
Image Credit: talitha_it/Shutterstock
-

New survey reveals what drives mobile shopping habits
Publié: novembre 5, 2015, 3:51pm CET par Ian Barker

Clean sites with low load times and fewer pages to navigate are more likely to get consumers to spend money according to new research.
The survey by Instart Logic of 2,000 US consumers also shows that consumer confidence in a brand is tied to their quality of experience while online shopping.
Among the findings are that 62 percent say they use their mobile phones for the entire shopping process from discovery, to research, to the purchasing of an item. As part of the shopping process 77 percent use mobile phones for the initial research and 73 percent to read reviews and product information.
More than three quarters of respondents find shopping on their mobile beneficial, 73 percent say they like mobile shopping because it's more convenient, while 72 percent find it useful because it's available 24 hours a day.
Half of the respondents say they would make the same purchases on their phone that they made in a bricks and mortar shop. For 74 percent the deciding factor in whether they would make purchases from their mobile device or a physical store is price.
Site experience is key to the shopping experience, with 59 percent saying they would buy more often if sites loaded faster and 43 percent if purchases were more secure. Barriers to purchasing are the site being too complicated (58 percent) and the mobile screen being too small (57 percent).
You can read more about the findings on the Instart Logic website or there's an infographic summary below.

Image Credit: Slavoljub Pantelic / Shutterstock
-

More than half of CIOs favor cloud-first strategies
Publié: novembre 5, 2015, 3:12pm CET par Ian Barker

Business information leaders are keen to adopt the benefits of the cloud according to a new study by data protection company Bitglass.
The company surveyed nearly 100 CIOs and IT leaders attending the Gartner Symposium IT Expo in Orlando, to better understand their top challenges for 2016 and how they plan to address them.
Among the key findings are that 55 percent of CIOs stated that their organizations will adopt a 'cloud-first' strategy, and nearly 90 percent plan on increasing spending on security for their organization in 2016.
"Progressive CIOs understand the powerful advantages that a cloud-first, security-now strategy can bring to their business," says Nat Kausik, CEO of Bitglass. "As we get ready to turn the page on a year plagued by epic data breaches and other nefarious activity, the increased focus on cloud and on security by IT leaders is encouraging for 2016 and beyond".
Other highlights are that 34 percent of respondents expect to increase spending on cloud security by more than 20 percent in 2016 and, 87 percent will increase their security spend overall. 50 percent of survey respondents reported cost savings in 2015 as a result of their SaaS applications, and Cloud Access Security Broker (CASB) adoption is rising fast, with 55 percent of CIOs planning to deploy a CASB in the future.
Controlling downloads to external devices was named as the largest cloud security challenge heading into 2016 by 36 percent of executives, followed by evaluating security of cloud app vendors (24 percent) and external sharing (21 percent). Shadow IT, a major concern from previous years is now a top concern for only 13 percent of CIOs.
The full report is available to download from the Bitglass website.
Image Credit: Ferbies / Shutterstock
-

IBM announces new solutions for the API economy
Publié: novembre 5, 2015, 1:06pm CET par Ian Barker

APIs are the glue which allow different parts of systems data and logic to connect and they’re changing the way businesses and IT departments work.
But whilst they make life easier for the user, they present new challenges for enterprises and developers who need to ensure security and management of APIs at the back end, while maintaining a dynamic consumer experience at the front end.
IBM estimates that the API Economy is estimated to become a $2.2 trillion market by 2018 and it's launching new services and solutions to help its clients navigate it. These include an API Economy Journey Map, which uses consultants who are part of the company's new cognitive practice to help clients identify key opportunities and gauge their readiness on their journey in the API Economy.
For the first time, IBM has built machine-learning capabilities into its API Harmony technology to help developers use intelligent search technology to quickly and easily find APIs and choose the combinations that will be most effective for a given application.
IBM is also collaborating with the Linux Foundation and leading industry standards organizations to provide an open platform for building, managing, securing and integrating open APIs.
"The API Economy opens up new opportunities for innovation in both business model and technology strategy when enterprises participate with digital business services," says Marie Wieck, General Manager at IBM Middleware. "To succeed in the API Economy and reach new clients, enterprises need an open ecosystem for trusted exchange and a differentiating strategy for how they monetize those services. IBM is helping guide clients every step of the way into this API Economy as they start their journey to becoming cognitive businesses".
To help clients begin to make the most of the API Economy, IBM will offer workshops and digital transformation services to help clients quickly develop and adopt an API strategy. Starter workshops will allow developers to leave with a functioning API after spending just four days in one of IBM's Bluemix Garage venues.
To boost the development of industry standards around open API development, Big Blue is also announcing its participation in two key standards organizations to allow clients to quickly and easily integrate APIs into their digital services. It's working with the Banking Industry Architecture Network (BIAN) to create common IT standards for the banking industry, including the creation of common banking API definitions which will standardize application components and simplify and accelerate the creation of APIs.
It's also working with the HL7 standards organization on the Fast Healthcare Interoperability Resources (FHIR) API standard for exchanging healthcare information electronically, aiming to simplify implementation without sacrificing information integrity.
For more information on IBM and the API economy you can visit the company's website.
Image Credit: Tomasz Bidermann/Shutterstock
-

How behavioral biometrics can help secure systems
Publié: novembre 5, 2015, 12:42pm CET par Ian Barker

Increasingly the security industry is looking for alternatives to the hard to manage and all too easily compromised password.
Biometrics like fingerprints and retinal scans are starting to make ground, but California-based two-factor authentication specialist SecureAuth has announced a new partnership with BehavioSec which aims to use behavioral analysis as a security tool.
An individual's unique behavioral biometric pattern is influenced by social and psychological factors -- such as if a person is a native speaker of the language they write -- making it nearly impossible to copy or imitate somebody else's behavior in front of the computer. By incorporating behavioral biometric technology into authentication platforms, organizations can strengthen their defenses against cyber adversaries.
"This is a truly sophisticated technology, in that the end user’s experience is only impacted if their keyboard, mouse, or touch interactions raise a red flag," says Keith Graham, CTO of SecureAuth. "Combining BehavioSec's patented approach with SecureAuth’s Adaptive Authentication will further help businesses stay ahead of advanced threats. The marriage of SecureAuth and BehavioSec's technology provides an unrivaled approach to helping organizations not only better protect themselves, but also provides the means to help them detect human attackers who may have breached their network".
To give an example of the way it works, an internet banking application would have the capability to spot unauthorized access to a customer's on-line account by recognizing the behavioral biometric interactions of the user while they are typing or moving the mouse. On spotting any irregular behavior, the banking application will prompt the user for a second factor of authentication. If the user is unable to provide the second factor, they will be prevented from accessing the account any further.
The new feature is set for inclusion in SecureAuth IdP 9.0, which is targeted for release in early 2016. Meantime there are a series of technology previews taking place in major US cities this month.
Photo Credit: ra2studio / Shutterstock
-

Microsoft and Red Hat announce enterprise cloud partnership
Publié: novembre 4, 2015, 3:49pm CET par Ian Barker

Microsoft Azure is set to become a Red Hat Certified Cloud and Service Provider as part of a new partnership announced today.
The tie up between Microsoft and the leading open source provider means Red Hat Enterprise Linux will be offered as the preferred choice for enterprise Linux workloads on Azure.
The two companies are also working together to address common enterprise, independent software vendor (ISV) and developer needs for building, deploying and managing applications on Red Hat software across private and public clouds.
Writing on the Red Hat blog, Paul Cormier, president, Products and Technologies says, "Today, it is incredibly likely that where you once found 'Red Hat shops' and 'Microsoft shops,' you'll find heterogeneous environments that include solutions from both companies. We heard from customers and partners that they wanted our solutions to work together -- with consistent APIs, frameworks, management, and platforms. They not only wanted Red Hat offerings on Microsoft Azure, they wanted to be able to build .NET applications on infrastructure powered by Red Hat Enterprise Linux, including OpenShift, Red Hat Enterprise Linux Atomic Host, and Red Hat Enterprise Linux OpenStack Platform".
Other fruits of the partnership will include cross-platform, cross-company support spanning the Microsoft and Red Hat offerings. Support teams will be located on the same premises, enabling them to offer a simple, seamless and fast experience to customers.
Red Hat's CloudForms IaaS offering will operate with Microsoft Azure and Microsoft System Center Virtual Machine Manager, giving CloudForms customers the ability to manage Red Hat Enterprise Linux on both Hyper-V and Azure. Support for managing Azure workloads from Red Hat CloudForms is expected to be added in the next few months, extending the existing System Center capabilities.
In addition developers will have access to .NET technologies across Red Hat offerings, including Red Hat OpenShift and Red Hat Enterprise Linux, jointly backed by Microsoft and Red Hat. Red Hat Enterprise Linux will be the primary development and reference operating system for .NET Core on Linux.
"This partnership is a powerful win for enterprises, ISVs and developers," says Scott Guthrie, executive vice president for Microsoft's Cloud and Enterprise division. "With this partnership, we are expanding our commitment to offering unmatched choice and flexibility in the cloud today, meeting customers where they are so they can do more with their hybrid cloud deployments -- all while fulfilling the rigorous security and scalability requirements that enterprises demand".
More information about the partnership can be found on the Microsoft blog and the companies will be holding a joint webcast at 11am ET (8am PT) today.
Image Credit: Lightspring / Shutterstock
-

Human element is key to effective use of analytics
Publié: novembre 4, 2015, 2:56pm CET par Ian Barker
While most organizations are primarily focused on technology and tools, it's people who translate data and insights from analytics into business outcomes.
This is a key finding of a new report by Forbes Insights and professional services organization EY which shows that people and culture are critical to realizing business value from data and analytics.
"For a lot of companies, the bottleneck to creating value is not data, technology or advanced analytics skill sets," says Forbes Insights' Bruce Rogers, Chief Insights Officer. "It's a question of, once we have the insights from analytics, what are we doing with it? At the end of the day, success still involves people making different decisions and changing business processes".
The global survey of 564 senior executives reveals that 54 percent of executives with leading analytics organizations report that analytics is central to their overall business strategy, compared to only 10 percent in the remaining enterprises.
Change management is an important component of the top 10 percent of enterprises' overall data analytics initiatives. Almost three in five leaders embrace change management as 'extremely' important, versus about one-third of the rest.
The top 10 percent in the survey also say they've been able to organize and establish governance around their data analytics efforts. A majority indicate that they have enterprise, department and lines-of-business data, and analytics groups and that these are well aligned.
"This report illustrates the need for organizations to develop an effective business strategy to compete in today's data-driven world," says Chris Mazzei, Principal, Ernst & Young LLP and EY Chief Analytics Officer. "Technology is no longer a strong enough differentiating factor among organizations -- companies must invest in people and recognize the importance of the human element if they are to reap the benefits of their analytics initiatives".
The full report is available to download from the Forbes Insights site, there's also an assessment tool that you can use to see how your organization stacks up against the analytics leaders.
Image Credit: Rawpixel / Shutterstock
-

CloudCenter platform simplifies application deployments
Publié: novembre 3, 2015, 5:41pm CET par Ian Barker

Managing development projects across an enterprise can be a complex process, involving tracking multiple phases and teams.
Cloud management company CliQr's latest CloudCenter platform introduces features that help developer and operations teams simplify and streamline deployment of any application to any data center, public or private cloud.
CloudCenter uses an integrated continuous integration / continuous delivery (CI/CD) Project Board which unifies the management of users, deployments and environments across multiple pipeline phases -- from development, test and quality assurance to staging and production.
"True CI/CD can only be achieved with automation, but -- until now -- continuous deployment across multiple environments has been problematic," says Tenry Fu, co-founder and CTO of CliQr. "CliQr's new CloudCenter update marks an industry milestone as the first cloud management platform to integrate end-to-end project management with underlying infrastructure and application deployment automation. New features help DevOps teams automate and standardize deployment in any data center or cloud environment and visualize and manage each project’s end-to-end process that crosses those environments".
In addition to the Project Board where developers and the project manager can see the health and status of deployments at any stage, key features of CloudCenter 4.2 include Project Definitions that enable project managers to set lifecycle phases, link to cloud accounts, add users and then launch projects with defined budgets and built-in cost controls.
Because a single platform manages project setup, execution and integrated application and infrastructure deployment automation across all phases of the CI/CD pipeline, project managers have complete transparency of overall project flow, current health and status, as well as control and reporting against allocated budget. For DevOps teams CloudCenter eliminates cloud lock-in and hard coding of the deployment. Users can simply promote deployments from one phase to another across cloud environments with no detailed knowledge of underlying services.
More details of CloudCenter 4.2's features are available on the CliQr blog.
Photo Credit: Sakonboon Sansri/Shutterstock
-

Druva extends its protection to Azure
Publié: novembre 3, 2015, 5:09pm CET par Ian Barker

The increasing demands of compliance and legal requirements are forcing companies to retain more and more data as well as having to comply with local regulations. Many organizations see the public cloud as an attractive option for storing this information but that in itself raises additional security issues.
For Azure users the headaches are about to be reduced as data protection specialist Druva is extending its cloud solutions to Microsoft's public cloud and infrastructure platform.
"Druva has always taken a proactive approach to help our customers address their data availability and governance needs -- and that involves offering customers strong data protection and security in the cloud for their sensitive workloads," says Jaspreet Singh, CEO of Druva. "Our work with Microsoft Corp. underscores our commitment to broadening our cloud-related options and giving customers additional choice for deploying in the cloud securely and conveniently. Druva has quickly grown to become the defacto standard for data protection workloads in the public cloud".
Druva inSync integrates secure, scalable, high-performance backup, file sync across all user data, remote file access, data loss prevention, eDiscovery and automated compliance monitoring. The new Azure tie up provides increased flexibility of inSync deployments, new go-to-market channels and offers more regions to store customer sensitive data.
Additional benefits of Druva on Azure include the ability to meet a broad set of international and industry-specific compliance standards including ISO 27001 and HIPAA, as well as country-specific standards including Australia's IRAP, and the UK's G-Cloud. Microsoft's data center locations provide 21 storage regions around the globe, including Canada and China, so Druva customers can meet the data residency needs of regional data privacy regulations. Enterprise customers who have standardized on the Microsoft platform can use their Microsoft Customer Advantage contract license credits towards their Druva purchase.
"The Microsoft Azure Marketplace delivers direct access to the cloud-ready applications and services customers are asking for," says Steve Guggenheimer, Corporate Vice President and Chief Evangelist at Microsoft. "Druva built natively to the public cloud to take advantage of its elasticity, global presence and security to handle petabytes of customer data efficiently, which are also foundational elements of our Azure offering. Our mutual customers will reap the benefits of our joint efforts with cloud scalability and flexibility, always-on reliability, and international compliance support".
Azure support will be generally available in 45 days, in the meantime you can find out more about Druva's public cloud support on the company's website.
Photo Credit: jörg röse-oberreich/Shutterstock
-

New predictive content solution helps drive customer relationships
Publié: novembre 3, 2015, 3:22pm CET par Ian Barker

To stay competitive companies have to understand their customers, in the modern data-driven world that means adopting a more personalized approach and abandoning old mass marketing techniques.
San Francisco-based Boomtrain is announcing the integration of its predictive personalization platform with the Marketo marketing software to offer companies deeper understanding of individual customers and help them build stronger relationships.
With a combination of Boomtrain's next-generation machine learning algorithms and Marketo's automated campaign delivery, brands can create unique relationships with each of their customers. By analyzing how individual users interact with the brand's content and products, Boomtrain can answer questions about each person, including what their interests are, how they behave, and what compels them to take action.
"Mass marketing is becoming obsolete, and marketers need to realize that if they want to stay competitive, they have to put individuals first," says Nick Edwards, co-founder and CEO of Boomtrain. "Our vision at Boomtrain is to make every step of the entire audience journey more personal and relevant for every user. With Marketo, we're able to optimize the delivery of these experiences across channels, putting us both in a perfect position to transform how marketers do their jobs and propel excellence in brand communications".
Boomtrain's personalization uses predictive algorithms so its recommendations improve over time. Joint customers can then use the Marketo system to use relevant recommendations in their email and on-site campaigns.
"Regardless of the size of their company and industry, every marketer in the world can now market specifically to a person’s unique behavior and deliver the right message at the right time for maximum returns," says Mike Stocker, Director of Business Development at Marketo. "Our partnership with Boomtrain allows us to provide a smarter engagement marketing platform. We're excited that Boomtrain is part of our LaunchPoint ecosystem and look forward to driving success for many more customers through the partnership".
The joint solution is available through Marketo's LaunchPoint solutions ecosystem and you can find out more about it on the company's website.
Image Credit: iQoncept / Shutterstock
-

Metalogix launches real-time protection for SharePoint content
Publié: novembre 3, 2015, 1:33pm CET par Ian Barker

With security breaches becoming more common the need to secure all aspects of an organization’s data is greater than ever.
Microsoft's SharePoint is one of the most popular content collaboration tools and needs protecting just as much as anything else. Up to now, however, SharePoint security solutions have been passive, using a mix of permissions management and compliance-driven reporting functions.
System management software company Metalogix is launching its latest ControlPoint 7.0 software which can deliver real-time situational awareness into suspicious SharePoint user activity to help prevent costly data breaches and leakages.
The software uses machine learning to analyze and detect suspicious patterns of activity in SharePoint and prevent unauthorized access to content. The technology monitors SharePoint around the cloud and alerts on suspicious behavior, tracking behavior anomalies and unauthorized access based on geo-location to protect against both internal and external threats. By letting admins see which content users are accessing, including when, where, what time and how often, ControlPoint can help organizations avoid unauthorized access and usage.
"We've seen SharePoint mature to the point where a host of Fortune 500 companies and governments all over the world use it. As a result it's used to store more sensitive data, the corporate lifeblood of companies that could do serious damage if exposed," says Jay DeWalt, Senior Vice President Global Alliances and Channels at Metalogix. "Companies have to balance the risk of adding security against inhibiting the productivity of their users. ControlPoint 7.0 uses behavioral analytics to address the need for more intelligent and more accurate security of content that conventional permissions management simply doesn't provide".
The analytics element is integrated with Sensitive Content Manager, launched earlier this year, which uses machine learning to locate, classify and act on sensitive content within SharePoint. It pinpoints unauthorized access and alerts on suspicious behavior up to, and including locking users out of SharePoint.
More information on ControlPoint 7.0 and Sensitve Content Manager is available on the Metalogix website.
Imaged Credit: soliman design / Shutterstock
-

ExtraHop brings the power of search to network data
Publié: novembre 3, 2015, 12:16pm CET par Ian Barker

IT teams are able to collect more real-time data than ever before, but there's a difference between gathering information and being able to do something useful with it.
Wire data analytics specialist ExtraHop is launching the fifth generation of its big data analytics platform, complete with a new search appliance aimed at giving businesses fast, reliable insights into their operations.
"The incredible rate of technology adoption in the enterprise is ushering in a new era, transforming IT from a support center to a force multiplier for business," says Jesse Rothstein, CEO of ExtraHop. "The fifth generation of the ExtraHop platform is designed to empower this transformation, enabling for the first time truly data-driven operations. Our platform allows organizations to discover, explore, and take command of their network, client, application, and business data in a single platform, delivering unprecedented insights that drive collaboration, understanding, and value".
ExtraHop 5.0 delivers turnkey stream analytics for wire data. Combined with the ExtraHop Explore appliance it can deliver sophisticated historical search and multi-dimensional analysis of all wire data, allowing network and IT security teams to spot anomalous and disruptive behavior from any device or user. By speeding insight into how that behavior is impacting the performance, availability, and security of the infrastructure it can reduce the time taken to fix problems and ensure greater reliability.
Other features include Dynamic Discovery which allows for the automatic discovery of any device in the environment (including IoT connected devices), understands device dependencies, and tracks activity without instrumentation. A new user interface makes IT data available to all users with features including a visual query language, dynamic tables for rapidly building comparisons of any transaction attribute, and selective dashboard sharing including the ability to handpick eligible users.
You can find out more about the latest release and request an interactive demo on the ExtraHop site.
Photo Credit: Palto/Shutterstock
-

Mobile threats continue to grow with banking Trojans still a major concern
Publié: novembre 2, 2015, 5:11pm CET par Ian Barker

Security company Kaspersky Lab has released its latest quarterly threat evolution report for the third quarter of this year which shows over 300,000 new mobile malware programs detected, a 10.8 percent increase over Q2.
Displaying intrusive advertisements to consumers remained the main method of profiting from mobile threats. Mobile adware has continued to increase and accounts for more than half of all detected mobile threats in the quarter.
Some mobile attack methods are using superuser privileges (root access) to conceal their presence in the systems folder, making them hard to combat. Some good news is that SMS Trojans have decreased, accounting for only 6.2 percent of mobile threats during the quarter.
Attacks on mobile banking remain a major problem despite being down slightly, 5.68 million notifications compared to 5.9 million in the previous quarter. Kaspersky Lab solutions blocked almost 626,000 attempts to launch malware capable of stealing money via access to consumers' online banking, 17.2 percent lower than in the previous quarter. Users in Austria were most likely to be attacked by banking Trojans with five percent of Kaspersky users in the country facing the threat during the quarter. Trojan-Downloader.Win32.Upatre is the most most common threat, used in 63.1 of attempts to steal payment details.
"The developments in Q3 demonstrate that the global threat landscape is continuing to evolve at a fast pace. Malicious mobile programs are on the rise and in countries where online banking is popular, people are at considerable risk from Trojans looking to target them. With 5.6 million cases of attempted theft from online bank accounts, and cybercriminals continually developing sophisticated attacks, the use of high quality cybersecurity products has never been more important. It's vital that all those using the Internet -- both individuals and organizations -- protect themselves from these growing threats," says David Emm, Principal Senior Security Researcher at Kaspersky Lab's Global Research and Analysis team.
Kaspersky Lab also says it's been investigating a number of targeted cyber attacks including Turla which uses satellite communication to manage its command and control servers, the Darkhotel APT which infiltrates hotel Wi-Fi networks to place back doors on target computers, and the Blue Termite APT which focuses on stealing information from organizations in Japan.
Much more information is in the full report which is available to download from Kaspersky's Securelist website.
Image Credit: DeiMosz / Shutterstock
-

89 percent of Americans fail to recognize the threat posed by stolen health records
Publié: novembre 2, 2015, 4:38pm CET par Ian Barker

Most people worry about the risk of their financial information being stolen, but a new survey from data security platform supplier Vormetric reveals that many are unaware of their vulnerability to medical data theft.
Of over 1,000 US adults polled by Wakefield Research on behalf of Vormetric, only 11 percent included medical records in their top three selections for personal data they would be most concerned to have lost in a data breach.
"Healthcare data sets contain extremely detailed personal information. Enough to not only apply for credit cards or loans, but also to generate huge sums from fraudulent medical charges," says Tina Stewart, vice president of marketing for Vormetric. "The public's lack of awareness of their potential exposure to this is troubling. Few seem to realize that having their medical data lost is much more dangerous to their financial health than a stolen credit card number and address".
Top concerns are social security numbers (84 percent), credit card data (73 percent) and financial account information (71 percent). Other categories of information people were concerned about using are, personal contact information (24 percent), social media usernames and passwords (11 percent), home Wi-Fi or internet login information (10 percent) and fingerprint information (9 percent).
The survey also shows a lack of understanding of the benefits of encryption. A surprising 91 percent of respondents would still be worried if their personal data was stored in an encrypted file that was stolen as a result of a hack.
"Our survey with Wakefield also shows that there is a disconcerting lack of understanding among the general public about how encryption works," adds Stewart. "Essentially, it makes data totally inaccessible to those without the key required to decode it. Without the key, encrypted data is meaningless to hackers, and when combined with strong access controls, encryption is one of the best tools available for safeguarding sensitive data in this environment".
More information on the findings can be found on the Vormetric blog.
Image Credit: Rob Hyron / Shutterstock
-

Inateck BH1001 Wireless Sport Headset [Review]
Publié: novembre 2, 2015, 12:50pm CET par Ian Barker

Bluetooth headsets with Sport in the title usually feature a plastic band which goes around the back of your neck. This not only makes you look a bit strange it can also be uncomfortable.
Inateck's headset does away with this and just has a thin wire between the two earpieces. There's a control unit on the right-hand side to allow you to adjust the volume, accept calls, pair with your phone, etc, and this also houses the built-in mic.
The earpieces are magnetic, so when you're not listening to them you can attach the two together and carry them safely around your neck, which also avoids the cable getting tangled. They come with a soft fabric carrying pouch, a USB charging cable and a couple of spare silicon ear buds.
On the technical side they feature Bluetooth 4.1 and a 100mAh battery. A three hour charge gives you up to 8 hours of listening time. Overall they have a quality feel and the design is nicely thought out, so how well do they work?
Pairing is straightforward, press the power button until the LED flashes red and blue and you're good to go. The unit can only pair to one device and will automatically reconnect to the last one used when turned on. Sound quality is very good with decent bass response and clear higher frequencies too. They also do a reasonable job of shutting out other sounds. Taking the ear buds out and snapping the magnetic ends together automatically pauses the music which is a neat touch.
There are a few niggles, the cover over the USB port seems a bit flimsy, and the earpieces are rather bulky compared to wired units so they don't feel particularly secure -- that could be a fault of my ears but for something that's aimed at sports use it's not reassuring.
At $32.99 from Amazon (£30.99 in the UK) the BH1001 offers decent value, if you have the right sized ears, more information can be found on the Inateck website.
-

2014 still leads the way for data breaches
Publié: octobre 30, 2015, 5:19pm CET par Ian Barker

There have been some significant data breaches in 2015, and with two months still to go there may yet be more to come, but so far the numbers of people and businesses affected haven't approached the scale of last year's attacks.
The Top Ten Reviews comparison service has been looking back at the major breaches that marked 2014.
In terms of numbers last May's eBay breach affecting around 145 million people, plus breaches at JPMorgan Chase, affecting 76 million, and Home Depot, affecting 56 million, make 2015's biggest breaches like the Office of Personnel Management attack affecting around 21 million and even the 80 million records exposed by Anthem Health Care look pretty small.
The cost is significant too, with the Home Depot breach alone estimated to have cost $62 million and the total cost of the eBay and JPMorgan Chase attacks still to be revealed. The average cost of a data breach last year is put at $3.5 million and the total cost to the US economy at $525 million.
You can see more details of 2014's security breaches on the Top Ten Reviews site or in the infographic below.
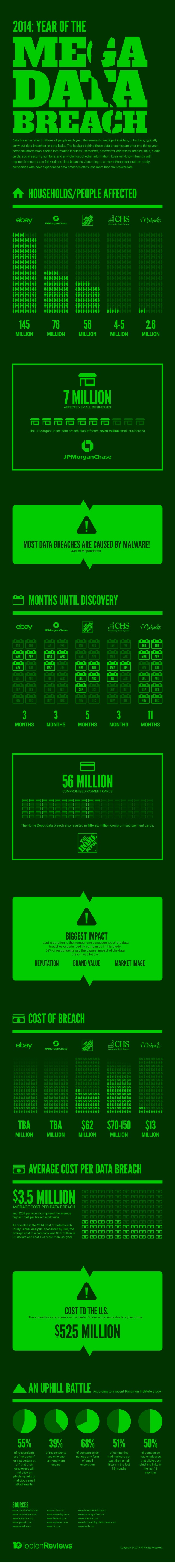
Image Credit: Sergey Nivens / Shutterstock
-

Mobile threats are on the rise and more than 40 percent of devices are at risk
Publié: octobre 30, 2015, 12:31pm CET par Ian Barker

Mobile threat defense specialist Skycure has released its Mobile Threat Intelligence Report, which finds a frightening increase in threats to both enterprise and personal mobile devices.
Using analysis of worldwide mobile data from Skycure and outside sources, the report found 41 percent of mobile devices are at medium to high risk on the Skycure risk scale. Nearly two in every hundred are high risk devices that were already compromised or were under attack.
Skycure ranks devices according to a proprietary Mobile Threat Risk Score, which takes into account recent threats the device was exposed to, device vulnerabilities and configuration, and user behavior.
The report reviewed data from devices with Skycure either installed by enterprises on employees' mobile devices or by security-aware consumers. Despite having this protection, the report found that the majority (over 52 percent) of all devices do not even have a simple passcode enabled, and 30 percent of devices were running an out of date operating system.
Among the findings are that one in three Android devices is still vulnerable to one of the recent high-profile Android attacks, with an out-of-date operating system. Nearly three percent of Android devices are infected with malicious apps with medium to high severity and 27 percent of Android devices have third-party app installation enabled, meaning they can install apps outside the official Google Play store. Interestingly, 33 percent of enterprise-managed devices have this possible vulnerability enabled, compared to 20 percent of personal devices, because some enterprises use it to install third-party enterprise apps.
In addition more than 15 percent of Android devices have USB debugging enabled, an easy way for a malware application to make it to the mobile device from a computer. The report shows that iOS devices have their problems too with 26 percent having an out-of-date operating system.
Enterprise-managed devices do remove some of the risk though, the findings show that more than five times more personal Android devices are rooted than enterprise-managed devices. The report also found very few jailbroken iOS devices in enterprises.
"Witches and vampires might not be real", says Adi Sharabani, CEO of Skycure, just in case you hadn't noticed it's Halloween. "But threats to mobile devices are and based on what we’re seeing in this report people aren’t doing enough to protect themselves. Skycure brings invisible mobile threats to the surface, so that enterprises can fight the bad guys on a level playing field".
You can see more of the report's findings in the infographic below.
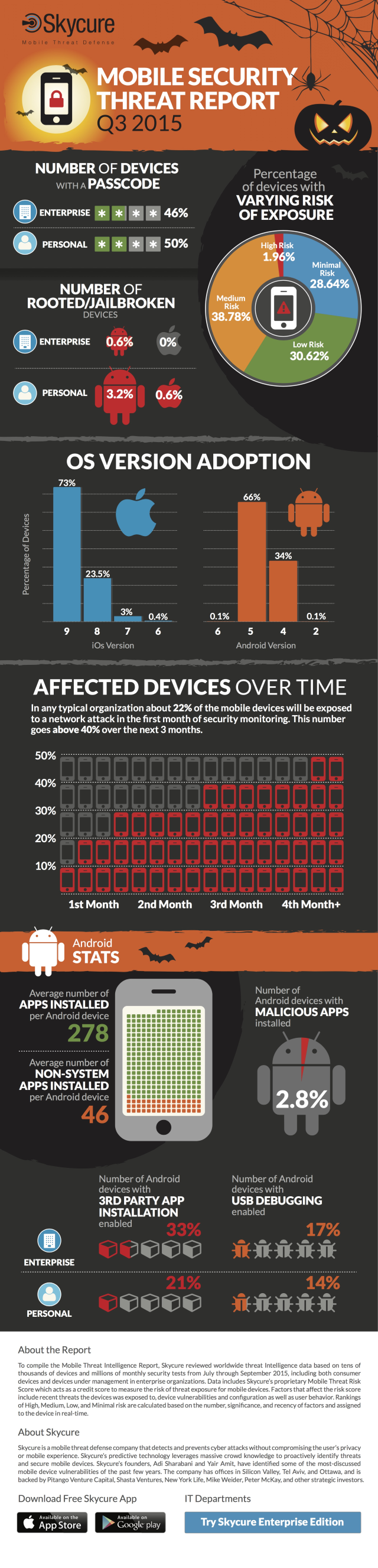
Photo Credit: lucadp/Shutterstock
-

How your social media habits could be putting your security at risk
Publié: octobre 30, 2015, 11:48am CET par Ian Barker

The biggest risk to your data or that of your company could stem from the way you use social media. Despite headline-hitting hacking attacks social media remains a favorite tool of cyber criminals.
Data protection specialist Digital Guardian has produced an infographic warning of the risks of over sharing on social media.
It highlights the amount of data you may be revealing and how attackers can use that to their advantage. For example by using the names of your co-workers to make phishing emails seem more authentic. Information gathered from social media, such as your mother's maiden name or your pet's name can be used to guess passwords. At its most extreme details can be used to steal your identity or open fake accounts for criminal activity.
The graphic also offers some useful tips to stay safe, these include using your privacy settings to limit who you share data with, and weighing the possible implications of any information before you click the post button.
You can see more in the full infographic below.
Infographic by Digital Guardian
Image Credit: Oleksiy Mark / Shutterstock -

Major utilities leaving website vulnerabilities un-patched
Publié: octobre 29, 2015, 4:00pm CET par Ian Barker

Hard on the heels of last week's TalkTalk breach, another British utility company, British Gas, has contacted over 2,000 customers to warn them that their email addresses and passwords have been posted online.
Yet according to information security company High-Tech Bridge many large companies could be leaving customer data at risk via their websites.
The company ran its free SSL checker tool on both the TalkTalk and British Gas sites and in each case revealed a lack of compliance with PCI DSS and NIST guidelines.
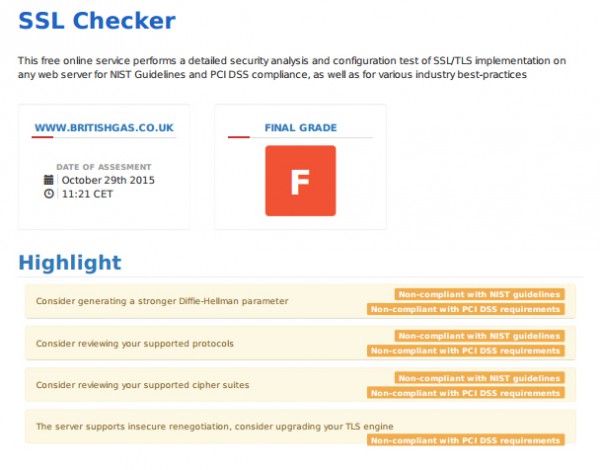
It has published a report on scans of web servers of 161 companies from the Forbes Global 2000 list. Among its findings are that 19.4 percent of the servers supporting HTTPS have an untrusted certificate, 34 percent have Always-On SSL enabled and 26 percent have an Extended Validation (EV) certificate. In addition 18.5 percent are still vulnerable to POODLE over SSL, and only 12 percent have configurations compliant with PCI DSS requirements 2.3 and 4.1.
"Appropriate data encryption is becoming a vital part of our everyday life," says Ilia Kolochenko, CEO of High-Tech Bridge. "Many security standards and federal laws require implementing strong data encryption to protect customers’ data. This is why at High-Tech Bridge we decided to launch a free service to enable anyone to test his or her server security in simple, fast and reliable manner. We are collaborating with many globally-recognized security organizations, such as OTA and ITU, to deliver the best quality of testing, and we are open to collaborate with the industry and individuals to continuously improve the service".
Full details of the scan results can be found on the on the High-Tech Bridge blog.
Photo Credit: Yuriy Boyko/Shutterstock
-

Cloud-based app security – the consumer view
Publié: octobre 29, 2015, 3:14pm CET par Ian Barker

More than half of consumers don't believe that cloud-based apps and services are keeping their data secure, according to a new survey.
Cloud security specialist Radware has released the results of a study of over 2,000 people which reveals that consumer perceptions and expectations are dramatically shifting with frequently reported hacks, which will have a major impact on how businesses secure their services, communicate with consumers and go to market.
Among the findings are that 54 percent of those surveyed say they would stop using a cloud-based app if it was hacked, and 43 percent of those claiming to have experienced personal data compromise indicate that they often opt out of certain security features of the apps they use.
There's widespread belief that companies need to take more responsibility too, 85 percent say providers of cloud-based apps should offer compensation or identity theft protection to customers affected by a breach.
The survey also highlights confusion about what is and isn't in the cloud. Although the results indicate that 33 percent of people are using cloud-based apps, of those surveyed 53 percent of 18-34 year-olds say they use them, but only 15 percent of those over 65 say they do. The report points out that, "Many of the most commonly used and popular mobile applications are little more than a client-side browser with a custom interface created for application use, with all data and logic sitting server side in the Internet. This is why relatively few modern mobile applications work when smartphones are offline".
There's a summary of the key findings in infographic form below or the full report is available from the Radware website.

Photo Credit: Slavoljub Pantelic/Shutterstock
-

The secret life of lost smartphones
Publié: octobre 29, 2015, 12:31pm CET par Ian Barker

Have you ever lost a mobile phone and wondered where it went? Security company Avast had the same thought and deliberately 'lost' 20 phones to find out what happened to them.
Avast installed three security apps on all the phones, the free Avast Anti-Theft app, Lookout Mobile Security, and Clean Master. It then randomly placed 10 phones in San Francisco and 10 in New York. Each phone was marked with contact information on where to return the device if found.
Of the 20 phones only four were returned, so what happened to the rest? Avast analysts used the Avast Anti-Theft app to track the devices and find out. They discovered that the majority of lost devices were wiped clean using the factory reset feature, Avast Anti-Theft was the only security app that survived the reset.
Using this app they found that one device appears to have traveled via a transatlantic cargo ship before settling in India where the phone is currently being used. One flew to the Dominican Republic, one arrived in a pawn shop, and one seems to be with a taxi driver meandering the streets of San Francisco.
"More than 3 million phones are lost each year," says Gagan Singh, president of mobile at Avast, "Fortunately with Avast Anti-Theft, users have the means to track and recover a lost phone -- or remotely wipe the data on it if it's not recoverable. With all the personal data we store on our phones today, it's a good idea to have a way to either find your phone or delete the content if you lose it".
The small bright spot in all this is that four people did return the phones they found to Avast. One of the finders, Quiana W from Brooklin, says, "I know how it feels like to lose things -- wallet or phone -- so I was trying to pay it forward".
Image Credit: cunaplus / Shutterstock
-

77 percent of Brits think the internet is getting more dangerous
Publié: octobre 28, 2015, 4:59pm CET par Ian Barker

It may not be entirely surprising in the wake of recent high-profile attacks like that on TalkTalk, but a new survey of almost 3,500 users from UK broadband comparison site Broadband Genie reveals that we're losing trust in the internet.
Among the findings are that 75 percent of Brits believe companies aren't doing enough to secure their personal data, and 15 percent said they had their personal data exposed by a leak or a hack.
Of those surveyed 77 percent think the internet is getting more dangerous, with 35 percent saying they don't feel safe online. It also reveals that while most (80 percent) have anti-virus software, only 53 percent have added further protection by installing anti-spyware/malware software, while 57 percent use firewalls and just 23 percent use an anti-spam program.
"More than ever we need to be aware of the threats out there and the tools available to stay safe and secure. As well as arming users with the right software and knowledge, all organizations need to have rigorous security procedures to combat threats and manage the aftermath of a leak," says Rob Hilborn, Head of Strategy for Broadband Genie. "It's also important for users to consider what protection they’ve got on the other devices they own. It's not uncommon for users to access their personal information from laptops, phones and tablets, so it's important to make sure these devices which are often overlooked are also secure".
How businesses respond to leaks is important too. The poll found that while 41 percent say they would not continue to use a service if private information was exposed, 57 percent say their continued use would depend on how an incident was handled.
The full survey results can be found on the Broadband Genie blog.
Photo credit: Yuriy Vlasenko / Shutterstock
-

New clothing company aims to make geeks chic
Publié: octobre 28, 2015, 3:41pm CET par Ian Barker

The popular image of male IT workers with pens in their top pockets or wearing crumpled T-shirts maybe about to change.
Seattle-based Ya Joe is launching a new online direct-to-consumer clothing line aimed specifically at tech guys. Its website explains why each item was created and how it can be worn in real-life situations, with realistic fitting guides that are true to size.
The company analyzed tech staff in their day-to-day lives to better understand the clothing features that would make their lives easier, such as pockets that easily fit a work badge and mobile device, or pockets that guys can comfortably place their hands in.
"Since we wanted to make the process for our shoppers as easy and streamlined as possible, we decided to offer select options and colors," says chief creative officer Aaron Hicks. "We use high-quality materials, breathable fabrics and customize the pieces to fit within our customers' lives. The clothing is interchangeable, allowing the casual yet professional pieces to easily transition from day to night. This allows our customers to purchase a range of clothing items that all look good together".
By adopting a direct-to-consumer business model, Ya Joe avoids typical retail and advertising markups, allowing the company to offer good value, high-quality clothing. The website is also designed to provide a convenient, easy to navigate shopping experience by grouping together items for specific occasions, taking the stress out of deciding what to wear.
"In our market research, we found that our guys often had a hard time analyzing a look or style to find something that worked for them, as how do you analyze a look, feel or trend?" says Joe Boldan, Ya Joe founder and former CEO of adventure clothing brand ExOfficio. "I teamed up with Aaron to design the first-ever clothing line using an analytic approach with our tech guys in mind. Our primary goal is to alleviate the stress and anxiety these guys often experience while shopping and provide them with an alternative that has them in mind and gives them the fashion they deserve".
Do male IT staff deserve their poor fashion image? Do let us know what you think. Meanwhile if you believe your tech guys could do with some sprucing up you can point them to the Ya Joe website.
-

Half of IT security pros think their organizations are unlikely attack targets
Publié: octobre 28, 2015, 2:00pm CET par Ian Barker

According to a new study published by the Ponemon Institute and sponsored by behavioral analytics specialist Prelert, half of IT security practitioners in the US view their organization as an unlikely target for attack.
The report also reveals a lack of cyber-preparedness with 61 percent of respondents admitting a lack of confidence in their organization's ability to detect advanced threats.
When asked about the type of attacks that cause the greatest concern, the most common answer is advanced persistent threats (67 percent), followed by zero-day attacks (57 percent) and login attacks (37 percent).
Yet despite worrying about these threats respondents showed a lack of urgency in adopting changes to deal with them. Asked how their use of advanced threat detection technologies would change 12 months from now, 49 percent said their usage would either not change or decrease.
"This research reveals some major disconnects that IT professionals seem to have between perception and reality. While even circumstantial evidence points to the increasing volume and severity of cyberthreats, it's shocking to learn that half of security pros don’t even view themselves as a target," says Dr Larry Ponemon, chairman and founder of the Ponemon Institute. "We're also seeing discrepancies in the way teams are viewing and reacting to advanced persistent threats. Overall, they're not confident in their ability to detect advanced threats, but they’re not doing much about it. It's clear that new solutions are needed".
Only 36 percent of respondents say that they're using security analytics, but there's high recognition of its importance. 90 percent believe security analytics is either essential (19 percent), very important (45 percent) or important (26 percent) to their organization's ability to maintain strong security.
The importance of machine learning is recognized by 83 percent as part of a security policy. Spotting the difference between abnormal and normal behavior is said by 59 percent of respondents to be important to identifying suspicious artifacts that could verify potential intrusions. However, only 38 percent say their IT security team can do this.
More findings are available in the full report which is available to download from the Prelert website and the findings will be discussed at a webinar on November 11.
Photo Credit: Jirsak/Shutterstock
-

Killer smart devices and other cyber threats you'll face in 2016
Publié: octobre 27, 2015, 4:27pm CET par Ian Barker

The world of online security never stands still, and if the past year has shown us anything it's that you don't need sophisticated technology to launch a successful cyber attack.
Security company Trend Micro has released its annual security predictions report outlining the threats it expects to be facing next year. It forecasts continued growth in online extortion, hacktivism and mobile malware, as well as a shift towards an offensive cybersecurity posture for government entities and corporations.
"We anticipate 2016 to be a very significant year for both sides of the cybercrime equation," says Raimund Genes, CTO of Trend Micro. "Governments and enterprises will begin to see the benefit of cybersecurity foresight, with changes in legislation and the increasing addition of cybersecurity officers within enterprises. In addition, as users become more aware of online threats, attackers will react by developing sophisticated, personalized schemes to target individuals and corporations alike".
The report predicts that 2016 will also mark a significant turning point for malvertising. In the US alone, there has been a 48 percent increase in users who use ad blocking software, with a 41 percent increase in global use this year. As a result, advertisers will seek to alter their approach to online ads, and cybercriminals will attempt to find other ways to obtain user information.
Online extortion is expected to grow too, with more sophisticated psychological analysis and social engineering techniques used to lure victims. It also predicts that hacktivists will be driven to expose more incriminating information and may try to systematically destroy targets with high-profile data breaches.
Other key predictions are that variants of mobile malware will grow to 20 million, primarily affecting China, while targeting new mobile payment options globally. Even scarier is the prediction that as more consumer-grade smart devices are used in day-to-day activities, at least one device failure will prove to be be lethal in 2016. This will lead to calls for regulation of device production and usage.
Despite all this, less than 50 percent of organizations are expected to have cyber security experts on staff by the end of 2016. On the government side though we can expect to see legislation expanding to create a global cyber defense model, allowing for more successful arrests, prosecutions and convictions.
You can read more about the predictions on the Trend Micro site. Meantime if you think that your smart device is trying to kill you do let us know.
Photo Credit: vinzstudio/Shutterstock
-

Real-world Docker adoption up five fold in the past year
Publié: octobre 27, 2015, 3:46pm CET par Ian Barker

The adoption of containerization platform Docker has been one of the big infrastructure trends in the past year. But while it's much talked about, what effect is it having in the real world?
Infrastructure tracking specialist Datadog has released the results of a survey, based on the real Docker usage of 7,000 companies, revealing a 5x growth in Docker adoption since September 2014.
It also shows that from almost no market share a year ago, Docker is now running on six percent of Datadog's monitored servers. Perhaps surprisingly, larger companies are proving to be early adopters, with more than half of those with 500 or more hosts having tried Docker.
Although some eventually abandon it, the report shows that two-thirds of those that try Docker go on to adopt it. In fact most companies who will adopt have already done so within 30 days of their initial production usage, and almost all the remaining adopters convert within 60 days. Once adopted the average company triples its Docker usage within the first five months.
The three most widely used technologies in Docker are, Registry used by 25 percent of companies, presumably instead of Docker Hub. NGINX comes next as Docker is being used to contain a lot of HTTP servers. Third most popular is Redis, the in-memory key/value data store often being used as an in-memory database, message queue, or cache.
Most companies adopting Docker run four containers simultaneously on each host. This finding seems to indicate that Docker is commonly used as a lightweight way to share computing resources.
Docker containers have a short lifespan, three days on average, compared to traditional and cloud-based VMs which have an average lifespan of 12 days. This, Datadog points out, has a significant impact on the number of things that need to be monitored and that solutions which are host-centric, rather than role-centric will become unusable.
You can read more about the findings and the methodology used to produce the report on the Datadog site.
Image Credit: Oleksiy Mark / Shutterstock
-

New analytics platform helps detect internal attacks
Publié: octobre 27, 2015, 2:55pm CET par Ian Barker

Security analysts can struggle to cope with the large volumes of alerts generated by multiple security tools. This can make it hard to distinguish anomalies from genuine malicious actions.
To provide organizations with additional context and more accuracy to detect malicious attacks, even those that originate internally, security analytics specialist Niara is launching a new version of its platform to deliver user and entity behavior analytics (UEBA) on network packet and flow data, in addition to log data.
"Most analytics tools today only look at log data. While this is a critical part of identifying attacks on the inside, it's only part of the puzzle," says Sriram Ramachandran, CEO and co-founder of Niara. "To get the most accurate information for attack detection, you must be able to analyze relevant security data from any source, regardless of volume, including log, flow, packet and threat intelligence sources. Having this higher fidelity picture allows you to drastically reduce the volume of alerts that security analysts have to sort through and validate, making them quicker and much more effective".
By profiling a range of behaviors including authentication, remote access, resource access, file, protocol, and peer-to-peer analytics, Niara can deliver a spectrum of analytics to not only detect anomalous behaviors, but more reliably spot those with malicious intent.
These analytics are combined with deep forensics, integrating them into a single system that provides analysts with a closed loop workflow from detection and investigation through to fix. Niara also integrates with third-party security information and event management (SIEM) systems, such as Splunk and HP ArcSight, to enable analytics-driven intelligence and improved visibility into attacks.
Deployable on premise or in the cloud, you can find out more about the latest Niara platform on the company's website.
Image Credit: Manczurov / Shutterstock
-

Code42 releases new endpoint protection platform
Publié: octobre 27, 2015, 12:05pm CET par Ian Barker

Backing up data is increasingly important, not just to guard against system failures but because of the need to retain information for legal purposes, and for migrating information between devices.
Endpoint data protection and security specialist Code42 is launching its fifth generation CrashPlan platform to strengthen its backup and restore capabilities.
The new version includes a new legal hold app which makes it easier for litigation support staff to identify, preserve and collect electronically stored information. Instead of relying on IT teams to serve up end-user data during eDiscovery, the legal hold web app empowers legal departments to run the process themselves, significantly reducing litigation expenses.
There are also new data migration features to ensure that files and folder structures move seamlessly across platforms. Individual device settings and preferences can be transferred automatically with the Windows User State Migration Tool (USMT), reducing time spent on reconfiguration by end users and IT staff.
"Our business is to ensure our customers' endpoint data is protected and secure -- so they can easily recover, search and analyze it," says John Durant, senior vice president of product at Code42. "In our 5.0 release we responded to customer requests for streamlined legal holds, faster data migrations and an elegant user interface -- and we nailed it. These enhancements strengthen the platform’s core backup functionality while building bridges between the IT department and other areas of the enterprise, solving a whole new set of problems for our customers".
In addition Code42 5.0 has a new user interface offering simplified workflow and faster, self-service backup and file recovery, making it easier to use and more appealing to end users, accelerating enterprise-wide adoption.
For IT admins it also offers integration with the Splunk reporting tool to provide insights on the flow of data and status of operations.
You can find more information about the latest CrashPlan and request a 30-day free trial on the Code42 website.
Image Credit: Oleksiy Mark / Shutterstock
-

New platform simplifies OpenStack cloud networking
Publié: octobre 26, 2015, 3:05pm CET par Ian Barker

OpenStack is a popular open source tool for creating public and private clouds and is used by big companies around the world.
To make running OpenStack systems easier, open source network specialist Akanda is launching a new version of its Astara platform that radically simplifies the complexity and scale of implementations.
"Astara's first release as an official OpenStack project is an exciting one for OpenStack operators," says Henrik Rosendahl, CEO, Akanda. "The goal of Astara is to make Networking and DevOps’ lives easier. With tremendous community support and momentum for the platform throughout its first year, Astara is the answer for massively simplified OpenStack networking stack that can replace traditional -- and expensive -- single vendor lock-in".
The latest Astara release is compatible with the latest 'Liberty' OpenStack release and includes a new load balancer driver which allows OpenStack operators to configure the platform to load and manage only the resources they choose. Neutron virtual network resources are now much more quickly provisioned onto appliance VMs via a new service that manages pools of hot-standby appliance VMs.
The new release also offers integration and support for Dynamic Lightweight Network Virtualization which gives OpenStack operators a complete, OpenStack-ready stack. There are active high availability and scaling improvements, plus syncing to Liberty’s global requirements, ensuring smooth installation into system namespaces shared by other OpenStack projects. For clouds running OpenStack Kilo or Juno releases the new Astara release can be completely back ported.
More information about the latest release is available on the Akanda blog.
Image Credit: Chaiyapop Bhumiwat / Shutterstock
-

Behind the big names, the first hires of major tech companies
Publié: octobre 26, 2015, 11:47am CET par Ian Barker

We've all heard of Bill Gates, Steve Jobs and Mark Zuckerberg, but what about the people they hired in the early days of their fledgling businesses?
You probably don’t know anything about Marc McDonald's role at Microsoft or Shel Kapha'’s at Amazon, but these were among the first people hired by those companies and had a significant effect on their growth.
Recruitment search engine Adzuna has produced an infographic highlighting the roles of the lesser known people behind the success of some tech giants.
You can find out more about the lesser known names at Google, eBay, Dropbox, Tumblr, Yahoo and more in the graphic below.
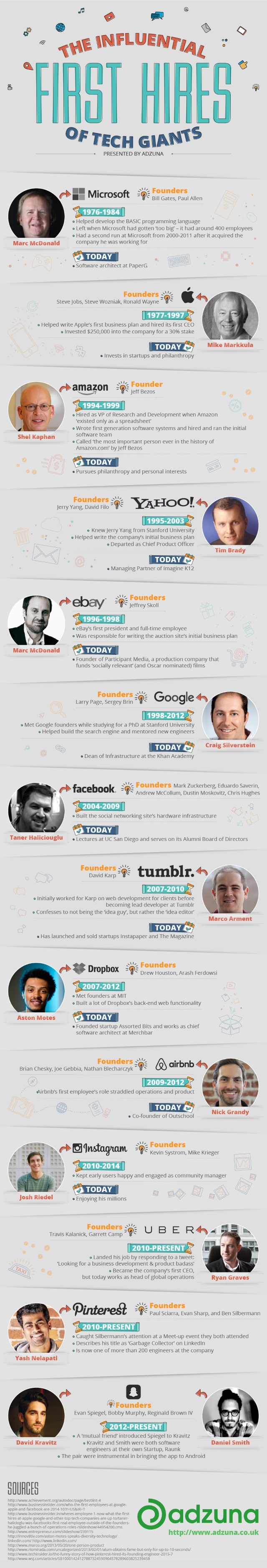
Photo Credit: EDHAR/Shutterstock
-

How spam and botnets have become big business [Q&A]
Publié: octobre 23, 2015, 3:02pm CEST par Ian Barker

Botnets are not a new problem, but they remain a key part of the cyber criminal's armoury. The Messaging, Malware and Mobile Anti-Abuse Working Group (M3AAWG), a global industry forum dedicated to promoting best practices in cyber security, has issued its first report looking at the level of botnet infection. Based on information provided by ISPs covering over 43 million subscribers in the US and Europe it concludes that around one percent of consumers are infected by a bot. The good news is that notification rates are high with between 94 and 99.82 percent of those infected being notified of the problem by their ISP.
Even on those numbers botnets are a major problem. We spoke to Ken Simpson CEO of outbound traffic security company MailChannels and co-chair of M3AAWG's Botnet Subcommittee to find out about how botnets and spam have become big business.
BN: What is the M3AAWG?
KS: It was founded about 10 years ago by a group of international ISPs. The mission of the organization is to bring together all of the people involved in transacting the world’s email so that they can create standards and work together to fight back against very well-funded criminal networks.
BN: Can you give us an overview of the current state of the spam industry?
KS: A lot of internet users aren't aware that there's actually a huge amount of spam going on. They have spam filters and most of the time the filter keeps spam out.
These days a large proportion of the spam that's sent around the world is not trying to sell you something. What cyber criminals have realized is that trying to sell you some Viagra pills doesn't make as much money as it used to. What they're doing now is focusing on exploitation, financial information and private identity information that they can use to steal money from your bank account or get you to participate in some fraud.
This is a massive problem, the scale of fraud and cyber crime being spread over email has to be in the tens of billions per year. It's not just individuals being targeted either it's institutions of all sizes. What we try to do at MailChannels is provide software and services to help the ISPs who originate the mail traffic protect their users. We help them identify the bad stuff as it goes out onto the internet so that they can block it and protect the rest of the web.
BN: Why would service providers care about providing protection?
KS: If they don't do something the global reputation of their email will suffer and their network will get blocked. This means their users wouldn't be able to send email any more because it would be blocked everywhere else.
BN: How important are botnets in all of this?
KS: One of the leading botnet researchers recently told me that the world of botnets has never been more interesting. There are more sophisticated botnets than ever before and they’re engaging in a wider array of bad behavior. There's a whole eco-system of players who are running these botnets, renting time on them and selling them for different services. If you wanted to carry out some cyber crime yourself you could go to an internet forum and rent time on a botnet to do whatever you wanted -- distribute malware, send spam or run a denial of service attack. It's also very cost effective because it's a competitive marketplace.
BN: There seems to have been a shift in the type of spam recently, towards sending fake invoices for example, is this significant?
KS: There's a move away from traditional spamming, which has an extremely low return per email message, to more concentrated financial fraud. If you get a Viagra spam email then maybe you spend $50 on purchasing pharmaceuticals, but the spammer makes only a tiny slice because he has to source the product and send it out, he may make only $3 or so on the transaction.
But if I manage to convince you that your company owes $5,000 to my fictitious organization and I get you to wire transfer that, then I get $5,000. I don't have to hit as many victims to make that pay off pretty quickly. This isn’t just a few spammers, it's criminal networks with some very nasty people behind them.
BN: Does this activity originate only in failed states or is it a global issue?
KS: There are spammers operating in every country, but the ones operating in places like the US, UK and Canada tend to be the string pullers. They'll develop the infrastructure and they tend to be involved more in traditional spamming, selling products. The actual dirty work will be subcontracted elsewhere.
Countries like the Ukraine have little regulation because the country is so broken by war and corruption. They literally have call centers taking support inquiries for extortion schemes. Government is effectively neutralized by criminal interests, so if you pay off the right people things like ransomware scams can operate pretty much in the open.
BN: So the whole operation has become very professional rather than the common idea of a hacker working from his bedroom?
KS: It ranges across the spectrum, one of the things that my company offers is an outbound protection service for service providers who don't want to spend time trying to maintain their email reputation.
Around two thirds of the attempted signups for this come from spammers and phishers and most of the phishing signups come from northern Africa and Indonesia. They're very open because in their countries there's zero chance of any enforcement finding them. They will phish services like PayPal and even though individually they might not do a lot of damage, collectively they do a lot and they're very difficult to find. They may be committingng all of their cyber crime from a laptop in an internet cafe.
So, while there's sophistication there are also thousands of people operating at a lower 'street smart' level to attempt to extort users of online services. They often work within their own language area, so you get phishers working in Morocco or Algeria targeting customers of French banks for example.
BN: Is phishing cyclical? Do scammers target PayPal one week, Barclays the next, a French bank the week after?
KS: I get the sense that it is because it takes time to develop a campaign, you have to replicate the target website so they do tend to hit one at a time. Because there's lots of these guys working on the same thing many institutions are being hit in parallel but it's not like one person is hitting all of the institutions. Smaller financial institutions see periodic waves where their customers will see nothing for months then get hit by thousands of email messages. Larger ones like PayPal are being phished 24 hours a day, domain names similar to PayPal are being constantly registered, it's like a tidal wave.
You can find out more about the botnet report on the MM3AAWG blog.
Image credit: Gunnar Assmy/Shutterstock
-

TalkTalk breach puts details of four million customers at risk
Publié: octobre 23, 2015, 11:47am CEST par Ian Barker

UK telecoms provider TalkTalk says it's been hit by a "significant and sustained" cyber attack which could have exposed the personal information of its four million customers.
In an official statement the company says that data including names, addresses, dates of birth, phone numbers and payment details may have been accessed.
TalkTalk says it's working with cyber crime experts and the police to find out what happened and the extent of information accessed. A Russian jihadist group has claimed responsibility for the attack online although this has yet to be verified.
The Metropolitan Police says it's aware of speculation surrounding the perpetrators but that its enquiries are ongoing and no arrests have been made.
This is the third attack TalkTalk has suffered in the past year. In February customers were warned about the theft of thousands of names and account numbers, and in August its mobile sales site was breached.
The latest breach appears to have started with a DDoS attack which may have been used to distract the company's security team while the data theft took place.
Dido Harding, TalkTalk's CEO, says, "TalkTalk constantly updates its systems to make sure they are as secure as possible against the rapidly evolving threat of cyber crime, impacting an increasing number of individuals and organisations. We take any threat to the security of our customers’ data extremely seriously and we are taking all the necessary steps to understand what has happened here. As a precaution, we are contacting all our customers straight away with information, support and advice around yesterday’s attack".
If you're a TalkTalk customer the company should be getting in touch, however, it warns people to beware of scammers and says it won't email or phone asking for bank details or passwords, or ask people to download software onto their machines.
In the meantime you're advised to change your passwords and monitor your bank accounts for unusual activity. Anything suspicious should be reported to Action Fraud via www.actionfraud.police.uk or on 0300 123 2040.
TalkTalk's share price dropped 10 percent when the London Stock Exchange opened this morning.
-

UK companies suffer from innovation inertia
Publié: octobre 22, 2015, 5:43pm CEST par Ian Barker

If businesses don't keep pace with digital innovation they're likely to lose out on opportunities for long term growth and risk being displaced by more agile competitors or road-blocked by security and compliance barriers.
Yet new research from Hitachi Data Systems suggests that a lack of consensus about where to make intelligent investments is leaving UK organizations in a state of 'innovation inertia' and putting business growth at risk.
Headline findings are that 81 percent of IT leaders say their companies aren't set up for the digital age, and 75 percent can't make informed investment decisions due to a lack of clarity in business strategy and access to business data. A worrying 90 percent of IT leaders believe their organization isn't agile enough to respond rapidly to industry change, putting them at risk of being outpaced by more digitally-aware brands.
"Technology plays an integral role in helping UK organizations transform to thrive in a digital economy, but only if there is consensus about which technologies are relevant to future growth and about the ability to adapt to these known priorities," says Richard Gadd, UK managing director at Hitachi Data Systems. "This isn't about innovating for innovation’s sake, it's about UK organizations having the ability to garner valuable business insights to make informed technology investments that will drive future growth and enable UK organizations to redefine business agility. The pace of business change will never be this slow again, and to stay relevant for the long term, organizations need to know their business inside out so they can quickly capitalise on new revenue opportunities before their competition do".
The report also reveals some of the barriers to technological innovation. 91 percent of IT leaders recognize that effectively storing, retrieving and analyzing data can identify future revenue streams, yet 87 percent are facing barriers to using big data.
Compliance is seen as a major barrier to future technology investments by 83 percent of UK organizations. Organizational culture and legacy IT systems are seen by respondents as major barriers to business agility too, 97 percent of IT leaders feel that their organizations could improve how they use technology, with potential business benefits including increased staff efficiency, improved customer service, and faster delivery of internal projects.
"The key to overcoming this innovation inertia is understanding that businesses can't transform everything at once," says Bob Plumridge, EMEA CTO at Hitachi Data Systems. "The research shows that nearly all IT leaders (96 percent) believe legacy IT systems provide risk to future growth, however when implementing new technology, a complete overhaul of current technology isn't always necessary. Instead IT leaders need to successfully identify and drive the innovations that matter the most, connecting the technology they need today with the technology that will be integral to future success. It is by aligning with the business and employing informed insights, derived from their organization's data, that businesses can start cutting through the trees and understanding which innovations are most important to driving business growth".
The survey targeted 200 IT decision-makers at UK organizations with over 1,000 employees in September and October this year.
Image Credit: Duc Dao / Shutterstock
-

Digital services benchmark reveals winner and loser regions in global eCommerce
Publié: octobre 22, 2015, 4:38pm CEST par Ian Barker

Digital services provide real-time indicators into buyer behavior and tend to reflect the overall health of global markets. Understanding these patterns gives online services companies the opportunity to redirect efforts to different regions or target their campaigns to where the opportunity is emerging.
Digital commerce solutions company Avangate today released findings from its first Digital Services Benchmark. The new report tracks global consumption of digital services to identify regions with the fastest growth and greatest contraction.
The report reveals that Kuwait, Vietnam, Slovenia, Pakistan, Saudi Arabia and India are seeing the most digital growth, with positive increases in buyer purchasing from Q2 to Q3 2015. One of the countries that showed consistent growth, Vietnam, has a booming tech scene, which has been reported as the nation’s most successful private industry.
At the other end of the scale the regions with the slowest growth are Kazakhstan, Serbia, Namibia, Greece, Ecuador and China. After dropping significantly at the top of Q3, Greece saw a 56 percent increase in purchases during August 2015 which may be evidence of recovery. China also saw a slight surge of seven percent during this time period, likely due to interest rate cuts employed by banks.
"Our mission is to support and stimulate global commerce for digital services from global payment processing, tax and compliance to automated billing, renewal and customer engagement," says Michael Ni, CMO and SVP of Products at Avangate. "We believe that by identifying patterns and drawing correlations from the data to current events, we can help our clients make smart decisions that deepen relationships with existing customers and extend services where new opportunities arise".
The report concludes that the opportunity for online commerce is fluid across the globe. As a result online service providers need to ensure they're supporting a strong foundation for digital commerce, regardless of the market they're targeting.
More information is available on the Avangate website and there's a summary of the findings in infographic form below.
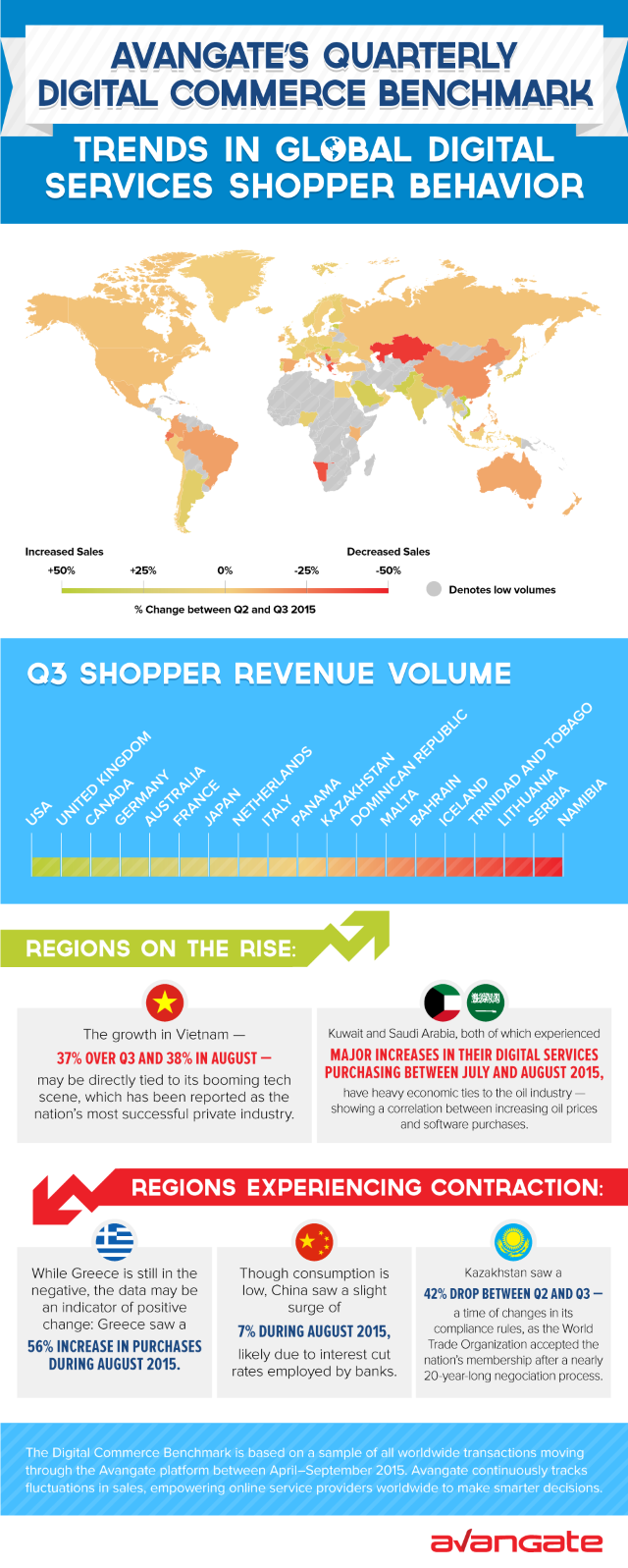
Photo Credit: Nonnakrit/Shutterstock
-

How data is changing your life
Publié: octobre 22, 2015, 3:39pm CEST par Ian Barker

Not so long ago collecting data required considerable effort. You had to measure and count things, then turn that raw information into useful data by inputting it into some sort of model. It was time consuming and took time to produce results.
Now there are millions of everyday devices collecting data, and lower storage costs mean that more of it can be retained and used to spot historical trends. This shift in how data is gathered, stored and analyzed is starting to have a significant effect.
BSA | The Software Alliance has released a paper highlighting how data is changing the way we live, in many cases without us even realizing it. Data is being used to solve complex problems around the world.
Examples highlighted by the report include farmers using data from seeds, satellites, sensors, and tractors to make better decisions about what to grow, when to plant, how to track food freshness from farm to table, and how to adapt to changing climates.
In the United Arab Emirates, new data tools are being used to design the world's first positive-energy building that actually produces more energy than it consumes. The city of Stockholm in Sweden has installed 1,600 GPS systems in taxi cabs to collect data on traffic flows, and then used software to analyze the data to inform the city's plans to reduce congestion. As a result traffic has been reduced by 20 percent, travel times have been cut in half, and emissions are down 10 percent.
In Kenya, mobile data is being used to identify malaria patterns and identify hotspots to guide government eradication efforts. Also on the medical front researchers have developed a machine learning algorithm that can predict cardiac arrest four hours in advance, and is accurate 66 percent of the time, by combing real-time data with a patient's medical history.
There are economic implications too. Economists estimate that if better use of data made industry only one percent more efficient it could add $15 trillion to global GDP by 2030.
The full report, What's the Big Deal With Data? is available to download from the BSA website. There’s also a video overview of the findings below.
Photo Credit: Sergey Nivens / Shutterstock
-

Machine learning solution helps to fight fraud
Publié: octobre 22, 2015, 2:04pm CEST par Ian Barker

Data is an essential part of combating and preventing fraud, but many organizations lack the data science and engineering teams needed to allow them to exploit the information they have effectively.
Big data company Feedzai is launching its new Data Science Studio software that uses artificially intelligent, machine-based learning to help prevent fraud.
Non-technical and business teams within organizations using Feedzai's Data Science Studio can build, deploy and manage predictive analytics models to unlock the power of big data. The Feedzai platform includes all the essential tools they need to manage fraud and risk.
"Data continues to provide both opportunities and hurdles for businesses of all sizes and across all industries because analyzing complex data requires a deep understanding of data science, software engineering and big data principles," says Nuno Sebastiao, CEO of Feedzai. "By putting a sophisticated, yet easy-to-use environment for data science modeling in the hands of all the teams and people who need it, we’re democratizing big data for our customers".
Accessible via the cloud or on-premise, Data Science Studio includes all the essential components to develop and manage predictive analytics to make commerce safe. Feedzai enables businesses to accurately analyze the large volumes of information they produce every day to keep their customers' data and transactions safe at any place or moment in time. The machine learning platform transforms the management of risk and fraud into a real-time decision science to help payment providers, banks and retailers prevent fraudulent activity.
You can find out more about Feedzai's fraud prevention technology on the company's website.
Image Credit: Gustavo Frazao / Shutterstock
-

Scholarship scheme aims to attract new female developers
Publié: octobre 21, 2015, 5:21pm CEST par Ian Barker

We reported last month that women only make up 10 percent of the IT security workforce and there's similar under representation across the tech sector.
To address this, freelance developer network Toptal is announcing a scholarship scheme to support and empower women aspiring to become professional software engineers.
Women from across the world of any education level can apply to win one of 12 scholarships over the next year. Winners will receive a $5,000 scholarship and weekly one-on-one technical training and mentorship from a Toptal senior software engineer to help them pursue their goals.
"Countless studies have shown that teams with a greater diversity of backgrounds and opinions consistently perform better and drive more innovation. This is something with which we're intimately familiar at Toptal. Our core team and engineering network members come from all over the world and all walks of life," says Toptal COO and Co-Founder Breanden Beneschott. "We're extremely intent on building the most innovative, talented network in the world, and building a more gender diverse community is critical towards being able to accomplish that".
Scholarship winners will be able to use the money in any way that helps them pursue their ambitions to become future software engineers. For example they could use it to help cover the cost of tuition fees, pay for courses, or pay themselves salary while they work on open source or start-up endeavors.
"In today's tech industry, quality education can come from so many different valuable places, and that’s something that this scholarship really embraces," says Anna Chiara Bellini, Director of Engineering at Toptal. "Giving winners access to top quality mentorship on topics of their choosing and $5,000 with very few strings attached will really allow them to learn and improve their skills as they prefer, instead of being locked into a rigid educational program".
To apply for a Toptal Scholarship, applicants must make an open source contribution on GitHub and write a blog post describing the experience, the problems they had to solve, and what they learned from it.
More information on how to apply and a how to guide to making a GitHub contribution are available on the Toptal site.
Image Credit: Stock Rocket / Shutterstock
-

Baby boomers spend more time online than millennials
Publié: octobre 21, 2015, 4:28pm CEST par Ian Barker

It's easy to assume that younger generations who have grown up with the internet spend more time online, but new research suggests that this isn't the case.
The 2015 State of the User Experience report from content delivery specialist Limelight Networks time spent online in the past year has dramatically increased, with 45 percent of respondents spending more than 15 hours a week on their laptop, tablet or phone.
But perhaps surprisingly the group spending the most time online is baby boomers, those aged 51-69. More than half (51 percent) are online 15 hours a week, as opposed to Millennials (18-33 year olds) at just 41 percent.
There's also a change in how long we're prepared to wait for sites to load on mobile devices. Last year, users were asked if they would be willing to wait longer for a website to load on a mobile device as opposed to a laptop or desktop, and 44 percent said they would. This year, the results are startlingly different, only 35 percent say they would be willing to wait longer on a mobile device, and nearly 40 percent expect equally fast-loading sites, regardless of how they're accessed.
Despite expecting better mobile performance thoughit seems we're becoming more tolerant of poor performance overall. This year, 33 percent said they would leave a website to buy a product from a competitor if the site loaded too slowly, down from 37 percent last year. Plus, in 2015, 72 percent would be willing to give the slow-loading site another try in the future, up from 69 percent last year.
Other findings include the importance of content. Respondents listed social media sites, reading news content and watching video content as their top three online activities, respectively, while reading news content was the most popular in 2014. Ecommerce finished in 5th place, behind researching products online. Whilst social media is the most popular online activity across the board, millennials are spending almost as much time viewing video.
We also want out online experiences to be more personal. In 2014 37 percent indicated they did not want a website to remember them from a previous visit. This year, the results are dramatically different as just 25 percent don’t want a personalized experience.
"Ultimately, consumers want more from their online experience, particularly as the mobile web and video continue their march toward ubiquity," says Jason Thibeault, senior director of marketing strategy at Limelight. "We have more options than ever -- more content, more video, and more shopping. And while patience has increased slightly, people -- whether they are Millennials, Gen X or Baby Boomers -- all expect a personalized, highly-functioning web experience. If not they will look elsewhere. With the explosion in content, branded entertainment, video and e-commerce, the stakes are higher than ever".
More detail is available in the full report which you can get from the Limelight website.
Image Credit: Kinga / Shutterstock
-

Smart reporting and auditing gives businesses improved visibility and control
Publié: octobre 21, 2015, 3:16pm CEST par Ian Barker

Business information comes from a variety of sources and it can be difficult to bring all of the separate streams together to extract meaningful data.
Enterprise file services company Egnyte is launching a new Smart Reporting and Auditing service. This allows organizations to build comprehensive dashboards of system-wide analytics around content (creation, editing, viewing and sharing), users, devices, applications, and more.
It uses the company's hybrid technology to provide comprehensive visibility and control across an organization's entire content lifecycle. This includes file infrastructure, which can be in the cloud, on premise, or a mixture of both, as well as user applications and devices.
"There is a tremendous opportunity for organizations to take advantage of all the detailed file analytics and insights we've collected within their infrastructure, applications, and devices", says Isabelle Guis, chief strategy officer at Egnyte. "Our focus on delivering this data in an actionable format will create an unparalleled level of efficiency and security that no other company in our space has the ability to do. It's critical for businesses to have tools like Smart Reporting and Auditing when collaborating internally and externally, not only to optimize file infrastructure and protect against potential threats, but also to gain a competitive advantage".
The service can help to save money by enabling informed, data-driven choices about infrastructure locally and globally -- reducing bandwidth consumption, minimizing support issues, and increasing productivity.
IT leaders can gain unique insights about user, file, and device activity that may be harmful to their organization. The Smart Reporting and Auditing service helps maintain security and compliance with preventative alerts that notify IT about suspicious activities.
It also empowers business users to make smart decisions at every level with relevant, viable information that is delivered straight to their Egnyte interface. IT will have more visibility into the security and efficiency of their entire corporate infrastructure and users will also gain insight into their usage patterns as well as internal and external collaborative efforts.
Egnyte Smart Reporting and Auditing is available now for all new and existing customers and you can find out more on the company's website.
Image Credit: Nata-Lia / Shutterstock
-

CFOs seek the truth through big data
Publié: octobre 21, 2015, 12:02pm CEST par Ian Barker

Chief financial officers (CFOs) want their company data to provide accurate insights and actionable business transformation.
This is one of the findings of a new survey by specialists in cloud corporate performance management Adaptive Insights. The global survey of 435 CFOs focuses on data analytics trends, business collaboration strategies, the top financial mistakes most companies make and 2016 plans and predictions.
According to the results CFOs want data to provide a -- rather Orwellian sounding -- 'single source of truth' from which to derive business insights. They predict that the amount of data they manage will greatly increase by 2020, and they face significant data challenges with respect to the accuracy and timeliness of data.
The survey also asked about the top financial mistakes most companies make, 69 percent of CFOs say that keeping data siloed is a major error while 40 percent name having inaccurate data for forecasting and planning.
"Faced with a challenging macroeconomic environment and the need to provide a more holistic view of the business, CFOs are increasingly becoming the 'knowledge executive' in the organization," says Tom Bogan, CEO of Adaptive Insights. "As both the volume and sources of data increase, CFOs are working across departments, driving toward a single source of 'truth' that gives them a more consistent, comprehensive view of the organization in real time. This view will ultimately provide more accurate business insights and inform more effective business strategy".
Data volumes are expected to grow, with a third of CFOs predicting the amount of data they manage will increase by over 50 percent within the next five years, 3 percent expect an increase of over 1,000 percent. The number of systems used is an issue too, with 41 percent of finance teams already managing data from three to five source systems and 22 percent pulling information from as many as five to 10 systems. Sales data is named as the top non-financial information they need to access by 58 percent of respondents.
Accuracy and integrity of data is cited as one of the most important characteristics needed for actionable reports and insights by 65 percent of respondents followed by timeliness or shelf-life of data by 42 percent.
When asked to look ahead to 2016 CFOs say that a potential rise in interest rates (48 percent), mergers and acquisitions activity (38 percent), cybersecurity (32 percent) and political volatility (29 percent) are the top factors likely to impact their business.
More information on how CFOs see the role of big data can be found on the Adaptive Insights site.
Image Credit: IMG_191 / Shutterstock
-

Microsoft steps up efforts to get Surface into businesses
Publié: octobre 20, 2015, 4:42pm CEST par Ian Barker

Microsoft is keen to get its Surface tablets in the hands of business users. This is one of the reasons why it increased the number of Surface sales partners back in July. And in September it launched the Surface Enterprise Initiative allowing Dell and HP to resell the product.
Now following the launch of Surface Pro 4 and Surface Book earlier this month, the company is making renewed efforts to crack the business market with new service offerings.
There are now around 5,000 business resellers for Surface across 30 countries. Writing on the Windows blog Cyril Belikoff senior director of Surface marketing says, "Achieving this breadth and reach is important because this allows us to make Surface and Windows 10 available to more customers than ever before. This means that we are better prepared now for the scale of demand we expect. The introduction of new Surface devices alongside the introduction of Windows 10 represents a big moment for us, our customers and our partners. We are ready!"
Today Microsoft is announcing two additions to the Surface Enterprise Initiative. From early next year it will launch a new service and warranty program for Surface customers via commercial resellers. Microsoft Complete for Enterprise will allow companies to pool warranty claims, allow claims for non-bootable devices where data policies mean the hard drive must be removed before return, and offer next-day shipping for fast replacement. It will also set up an on-boarding center where Microsoft will assist IT staff to get set up with warranty and support processes as well as provide online training for employees to get productive as fast as possible.
In addition the company is launching a Business Device Trade-in Program allowing customers to trade their used business laptops, tablets, and phones for credit towards the purchase of new Surface devices. This will be available in the US and Canada and will roll out across major European markets in the coming weeks. More information is available on Microsoft's trade-in page.
For more on Surface in business there's a dedicated micro site.
-

Commvault releases next generation open data platform
Publié: octobre 20, 2015, 4:17pm CEST par Ian Barker

Managing data in increasingly fast-paced business environments is a major challenge for companies. The latest release from data protection and information management specialist Commvault is seeking to address this with new levels of openness and flexibility.
The powerful combination of Commvault Software, the Commvault Data Platform and a range of professional services and support gives enterprises of all sizes the ability to open up new opportunities to reduce legacy spend, be released from vendor lock-in, find pathways to more modern environments, and drive new efficiencies and speed in their IT operations.
Major innovations include open API architecture that provides universal access to data under management in a standard captured format, ensuring no provider lock in. Customers and third party software partners cam allow their applications to write directly to the Commvault Data Platform. This allows information tasks to define data governance policies for all data right through its lifecycle. Customers can then benefit from common data management services of the platform across all data sources.
Incremental change capture for files and applications eliminates the need for backup windows. This opens opportunities to dramatically reduce workload impact during data protection operations while providing efficiencies in network and storage utilization. At the same time direct native access from the open platform to point-in-time data copies allows for instant recovery.
Enhanced total search now extends to live data sources, providing seamless and powerful search queries across multiple data solutions applications and storage locations, including the Commvault virtual repository, SaaS offerings, and cloud solutions without moving the data.
Disaster recovery technologies speed and simplify recovery planning and execution both on and off premise and in the cloud. These enhancements make DR operations easy to implement, test, validate, change and deploy regardless of the infrastructures and cloud technologies used.
"As a leading provider of integrated information technology solutions, CDW appreciates the ability to leverage Commvault's unified platform as a core data center solution that we can offer to our customers spanning all major segments and verticals," says Shea Hart, Director of Product and Partner Management, Data Center Solutions, at IT solutions provider CDW. "Given the partnered success we've experienced thus far in working with Commvault, we are extremely excited to explore the joint opportunities that the next generation of the Commvault solution platform will open for us".
Commvault says that there are more than 100 new innovations across its portfolio, a complete list is available on the company's website.
Image Credit: alphaspirit / Shutterstock
-

New workflow platform wants to empower workers
Publié: octobre 20, 2015, 3:08pm CEST par Ian Barker

Business collaboration tools like Clarizen have been around for some time, but a new entrant to the field is looking to change workflow management and give power back to employees.
Scalus is backed by Google Ventures and turns conversations into actionable, repeatable, automated tasks across apps, teams and organizations, adding accountability and oversight that's missing from other collaboration tools.
"Today's generation grew up on Facebook and demands immediacy and transparency as a default condition. We saw how scaling a business was nearly impossible based on the new way we work, so we created Scalus," says Kristen Koh Goldstein, founder and CEO of Scalus. "The proliferation of cloud apps and distributed teams has exposed how workflows and business processes are siloed. We developed Scalus to help organizations connect disparate systems, easily scale their distributed labor workforce and ensure that teams stay productive and effective".
Scalus isn't a linear platform where you insert a task and check off when it's complete. It includes a workflow tracking system which holds employees accountable for each aspect of a project. It also allows employees to make additions to tasks, and offer up ideas that they may be reluctant to share in a busy office.
The Scalus platform allows companies to automate distributed systems, automatically folding in daily activity and workflow. Compared to other collaboration and task management products on the market, Scalus is designed to uncover the real value of work. The platform strengthens accountability, connects the dots between business processes, automates and audits task management and lets workers avoid bottlenecks throughout the organization.
Features of the platform include the ability to track and manage recurring and repeating tasks; plus visibility into every task to identify bottlenecks, take action and eliminate dead-end work flows. It offers bi-directional task management across the internal systems and corporate email, and transparency across all levels of an organization.
Scalus is able to transform lists of tasks into a repeatable process to improve efficiency and scale, and it can integrate with communication platforms such as Slack and Chatter. It also allows collaboration with internal and external teams without everyone having to be a user. It helps companies with compliance too thanks to an immediate auto-generating audit trail.
You can find more information and sign up for a free trial on the Scalus website.
Image Credit: Tischenko Irina / Shutterstock
-

Apple pulls hundreds of iOS apps from its store for privacy violations
Publié: octobre 20, 2015, 10:56am CEST par Ian Barker

More than 250 apps have been pulled from the Apple App Store for secretly gathering users' information including email addresses, device serial numbers and details of other installed apps.
Apple's action comes as a result of a report from analytics service SourceDNA which uncovered the apps built using an SDK from a Chinese advertising company called Youmi. This allowed them to access the information via private APIs and send it back to Youmi's servers.
The Apps involved are mostly China-based and they include the official McDonalds app for Chinese speakers. SourceDNA's researchers estimate that around a million people may have downloaded them.
Since the SDK is delivered in binary form and the information gathered by the apps is uploaded to Youmi's server rather than that of the apps themselves, it’s likely that developers using the kit were unaware of the suspicious activity.
Apple has issued an official statement saying, "We've identified a group of apps that are using a third-party advertising SDK, developed by Youmi, a mobile advertising provider, that uses private APIs to gather private information, such as user email addresses and device identifiers, and route data to its company server. This is a violation of our security and privacy guidelines. The apps using Youmi's SDK have been removed from the App Store and any new apps submitted to the App Store using this SDK will be rejected. We are working closely with developers to help them get updated versions of their apps that are safe for customers and in compliance with our guidelines back in the App Store quickly".
The scale of the withdrawal does cast doubt on Apple's review process since it failed to identify the data gathering activity until told of it by a third party.
SourceDNA recommends that developers stop using the Youmi SDK until the data gathering code is removed. You can read more about the discovery of the suspect apps on the SourceDNA blog.
Photo credit: TK Kurikawa / Shutterstock
-

Teradata releases the power of IoT data
Publié: octobre 19, 2015, 4:56pm CEST par Ian Barker

The number of connected devices is increasing rapidly and producing large amounts of data. Extracting value from that data and gaining useful business insights from it though is a complex process.
Big data applications company Teradata is announcing two new software products that empower business users to uncover and operationalize the insights hidden within Internet of Things (IoT) data.
The first, Teradata Listener is an intelligent, self-service software for importing and distributing fast-moving data -- either individual or multiple streams -- at one time. It allows customers to push data to Hadoop, Teradata Aster Analytics, Teradata Database, and other platforms. It also enables data scientists, business analysts, and developers to quickly and easily analyze new data streams to deliver faster answers to business questions. Without needing to rely on IT for help, users can analyze data from numerous sources including sensors, telematics, mobile events, click streams, social media feeds, and IT server logs.
The second release is Teradata Aster Analytics on Hadoop, an integrated analytics solution featuring a set of more than 100 business-ready, distinctly different analytics techniques and seven vertical industry applications to run directly on Hadoop.
This allows organizations to seamlessly address business problems with an integrated analytics solution. The flexibility and simplicity of these capabilities enables everyday business analysts to perform as data scientists by tackling the organization's most challenging problems. Aster Analytics on Hadoop allows users to combine machine learning, text, path, pattern, graph, and statistics within a single workflow.
"Daily, we collect millions of sensor observations from our equipment, and from our engineers we receive thousands of written reports that are digitized. We subject the data to a variety of analytics to discover hidden patterns in order to ensure optimal equipment performance. Our partnership with Teradata has helped us predict the leading indicators for train equipment breakdown," says Gerhard Kress, director, Analytical Services, Siemens Mobility Division. "The collection and analysis of sensor and IoT data has been integral to driving the efficiency of the rail business".
Teradata Listener is now available in beta, and will be generally available globally in the first quarter of 2016. Teradata Aster Analytics on Hadoop will also be shipped globally in the second quarter of 2016. You can find more details on the Teradata website.
Image Credit: Ahmetov_Ruslan / Shutterstock
-

New feature helps drive sales team performance
Publié: octobre 19, 2015, 3:53pm CEST par Ian Barker
Sales platforms tend to be based on historical data which means that they don't always take account of the effect of transactions that are already in the pipeline.
Activity-based sales specialist LevelEleven is launching a new feature called Pacing, which improves the ability for salespeople and managers to use their sales pipeline data in real time.
"Today's salesperson wants to feel deeply engaged with their team, their manager and most importantly, their performance," says LevelEleven CEO Bob Marsh. "They want to know which key activities they should focus on to maximize their sales results. With Pacing, LevelEleven is a driving force behind a new movement in modern selling that helps companies identify the key activities and behaviors that lead to sales, and gives salespeople and sales managers a highly engaging, continuous feedback loop on how they are performing and where they need to focus their time".
LevelEleven aims to boost performance among sales teams by bringing together intelligent performance metrics, personalized sales scorecards, leaderboards, and goal management into a single platform, all within Salesforce. Performance metrics are visible within Salesforce, on mobile devices via Salesforce1, in a weekly email performance digest, and can even be broadcast on TV monitors around the office. By providing up-to-the-second, real-time reporting, LevelEleven drives more widespread adoption of the right sales process and in turn widespread adoption of Salesforce. Instead of sales leaders only being able to manage what's closing this month, they can empower their salespeople and front-line managers to manage the activities and behaviors that will lead to closing more business.
Marsh adds, "Before LevelEleven, sales performance management was limited to manually pulling reports that tell you about declining sales activity that happened in the past, leaving a sales leader thinking, 'I wish I would have known that a month ago when I could have done something about it.' The modern sales leader we call our customer can now stop creating complex and highly manual spreadsheets that salespeople barely look at, and leverage LevelEleven for real time performance management".
For more information about how Pacing can improve sales team performance and to arrange a free trial of LevelEleven you can visit the company's website.
Image Credit: EDHAR / Shutterstock
-

New cloud platform streamlines device management and patching
Publié: octobre 19, 2015, 3:05pm CEST par Ian Barker

Keeping devices secure means ensuring that they're up to date with the latest software patches. For IT managers this can present a major logistical problem, especially where different operating systems are in use.
IT management systems specialist Shavlik is launching a new version of its Shavlik Protect patch management solution, as well as Empower, a platform that aggregates data to give IT departments more insight into and control over their systems.
Protect 9.2 features improved patch assessments that cut the time needed to assess in half compared with the previous version. With agentless technology, Protect streamlines the patching process by giving IT departments increased opportunities to automate their patching. It also features intuitive scheduling based on Patch Tuesday releases. This allows admins to easily manage their patching based on this industry-standard release, rather than using arbitrary dates.
Admins can create templates that dynamically update, so systems that often leave the network are kept up to date no matter where they go or for how long. New Predictive Patch technology means Protect can anticipate what admins will need next and distribute it across the enterprise before it's detected as missing.
The new Empower platform aggregates data from Shavlik Protect, Active Directory and other systems -- both on and off the network. This gives IT departments instant access to much more information relating to different systems than was previously available. Using Empower's data, administrators can determine any problems an endpoint might have, from anywhere with an internet connection. Empower also allows users to see more about their environment and know more about the system before they make critical decisions, uniting operational efficiency and security.
Chris Goettl, senior product manager at Shavlik says, "Empower is designed to be everywhere you need it to be. It is purpose-built to manage your users, their devices and be with those users wherever they go. With this solution, Shavlik Empower will bring a new level of perspective to how you view operational and security data".
Empower includes Mac OS X asset inventory and patch management. It also features integration with Shavlik Protect. This integration allows a consolidated, web-based view of patch compliance across Windows and Mac systems. Improved inventory capabilities provide IT professionals with a visual timeline of events on a system, allowing them to see configuration drift, manage warranties and gain deeper insight into their software and hardware assets.
Empower is available at no extra cost to existing Shavlik Protect users. Mac Support can be added through a per seat workstation subscription license. You can find out more on the Shavlik website.
Photo Credit: Melpomene/Shutterstock
-

American households have a false sense of online security
Publié: octobre 16, 2015, 1:50pm CEST par Ian Barker

One in five American households was impacted by a data breach in the last year, yet 40 percent failed to properly secure their wireless routers.
This is one of the findings of a new survey from security company ESET and the National Cyber Security Alliance (NCSA). It reveals that despite the number of breaches 79 percent of Americans still feel safe in their connected homes, with almost half (49 percent) showing a remarkably strong sense of confidence.
"From the digital workplace to the connected living space and across age groups and demographics, today's households are more connected than ever and the number of connected devices is growing at considerable pace," says ESET Senior Security Researcher Stephen Cobb. "Sixty-seven percent of those surveyed had between one and five connected devices at home connected to the Internet, with 30 percent owning six or more. Even more telling, 30 percent of those surveyed today have two to three more devices at home compared to last year. With so many potentially vulnerable digital entry points, this survey underlines the importance of cybersecurity as a core commitment in our digital lives".
The study also looked at the effect of the connected world on parenting. Three-quarters of American parents say they have had a 'CyberEd' talk with their kids and 90 percent have made at least one rule about using the internet and connected devices. However, more than 61 percent of parents show a surprisingly high level of confidence in their kids' online activities and their abilities to use the internet and devices safely and securely.
Nearly 60 percent of parents don't require permission before downloading a new app, game or joining a social network, 60 percent allow password sharing with friends and only 34 percent require children provide all passwords to their online accounts. In addition 70 percent don't limit the kind of personal information their kids can share on social networks.
Only 33 percent have imposed a device free dinnertime rule and a mere 25 percent have rules about allowing the use of devices in bedrooms after a certain time. Just 30 percent of American parents have rules about not downloading pirated content from the internet such as illegal games, movies or songs.
There's more information on the survey's findings in the infographic below or on the NCSA's StaySafeOnline website.
Image Credit: Maksim Kabakou / Shutterstock
-

Trends and opportunities in enterprise storage [Q&A]
Publié: octobre 16, 2015, 12:54pm CEST par Ian Barker

The enterprise storage market has undergone significant change in recent years. In particular it's seen the rise of flash and the consequent decline of disk as a storage medium.
But what effect are these changes having on business? And what trends can we expect to see in the future? We spoke to Arun Agarwal, CEO of storage specialist Infinio, to find out his view of the market.
BN: How can companies extend their storage whilst making the best use of their existing infrastructure?
AA: The best way to extend the life of an array is with the addition of a server-side storage performance solution, like Infinio. Generally speaking, arrays need to be upgraded for one of two reasons: either they run out of storage performance (i.e. they can no longer keep up with applications), or they run out of storage capacity (i.e. they run out of space to store things).
What a solution like Infinio does is use low cost, commodity resources on the server (like its CPU and RAM) to create a caching and acceleration layer that prevents storage traffic from ever even going to the storage array. While this may seem like a solution only made for performance-triggered upgrades, that's not necessarily the case.
When an array no longer has to serve as much performance, you can configure it to be much more capacity efficient. In a nutshell, server-side solutions like Infinio can help avoid storage upgrades in a variety of scenarios.
BN: Flash storage is expensive. Is it possible to speed up performance without going to an all flash system?
AA: Yes. As discussed above, there are solutions that leverage server-side resources to prevent I/O from ever reaching the storage system. It is far preferable to entirely avoid serving an I/O from a storage system than it is to serve it from expensive all-flash media. Serving it from the server-side is both faster and lower cost.
BN: What are some of the common misconceptions surrounding storage performance?
AA: I think the industry has made storage performance about drive speed. This is reflected in the numerous comparisons and marketing around HDD performance vs. SSD performance. The reality is that many factors can affect storage performance, including things like CPU capacity on a storage controller or the capabilities of the storage network. What makes server-side technologies so powerful is that, by keeping data as close to the application as possible, you avoid most of these bottlenecks.
Another major misconception is that storage performance is only about IOPS (Input/Output Operations Per Second). Most storage vendors show a headline number of hundreds of thousands, or millions, of IOPS that their platform can provide, but vendors spend much less time talking about latency, another important dimension of storage performance. Administrators need to focus on both IOPS and latency when architecting a storage stack.
The thing we all tend to forget about the storage stack is that it's really just part of the memory hierarchy. People think of their processor, the L1 and L2 caches, and DRAM as the memory hierarchy, and have certain latency expectations there. However, what follows that is a huge dropoff in expectation for 'storage latency'. The reality is that it's all one system and we should aim for systems where all latency, including storage access, is in the microsecond range.
BN: Are hybrid arrays only a stop gap and will we inevitably see moves towards all flash storage?
AA: The logic of hybrid arrays -- a tuned ratio of SSDs and HDDs -- is sound, but the problem is that they miss a huge opportunity by putting the fast tier (the SSD cache) in the same box as the slow tier (the HDD). Solutions that locate the SSD caching layer server-side, closer to the applications, CPU and memory, provide much better performance.
So I do think that hybrid arrays are a stop gap, but not because the industry will move to an all-flash model. Instead, I think it's because the industry moves to a model of extremely fast I/O at the edge, and a very dense central core for capacity in the middle.
A logical question that follows this analysis is whether hyperconverged is the right architecture to provide the server-side performance we're talking about. While the storage resources are on the server improving performance, the reality is that data protection in a hyperconverged/distributed storage architecture has its own challenges. Most notably, both the performance and capacity implications of using distributed RAID render it impractical for most large-scale deployments.
BN: When is an all flash solution the best option?
AA: When evaluating an all-flash array as a potential solution, there are essentially two variables to keep in mind: the amount of storage capacity required and the working set size of the applications. Most customers spend a lot of time thinking about the former but they don't spend enough time understanding the latter.
The working set of an application is essentially the data that's regularly needed. That's the data you want on an SSD tier. If you have an application that has very high capacity needs but rarely accesses that data, an all flash array won't make sense because the working set would most likely fit on a flash tier in a hybrid array (or even better, on the server-side resources in an architecture like Infinio's).
If, on the other hand, you have an application where the overall capacity need and the working set size are similar, an all flash array could make sense. That said, such applications are rare as far as I have seen.
BN: What storage innovations are we seeing right now and what can we expect in the next few years?
AA: I think the really exciting thing going on, that people aren't talking about, is the new drive technologies. Remember, it was innovation in drive technologies that drove the whole flash revolution in the first place.
For example, recent press around Intel/Micron, 3D XPoint and other storage class memory (SCM) is absolutely worth following closely -- it's the next 10X when thinking about storage performance. Similarly, shingled magnetic drives (SMR) are the next 10X in capacity.
The drive technologies are what will lead the systems companies to build much faster, and much denser data center solutions for customers. The naïve view would be that applications won't even need another 10X of performance, or 10X of capacity, but if history has taught us one thing it's that the applications always find a way to catch up.
Photo Credit: Eugene Kouzmenok/Shutterstock
-

Addressing the IT security talent gap [Q&A]
Publié: octobre 16, 2015, 11:27am CEST par Ian Barker

October is National Cybersecurity Awareness Month in the US and the Department of Homeland security is calling for more attention to be paid to securing systems.
But whilst cybersecurity is a growing industry we risk a developing skills gap where workers aren't qualified or prepared for jobs in the field. We spoke to Andrew von Ramin Mapp, CEO of Data Analyzers, a cyber security and digital forensic firm, to get his view on how the industry can address this.
BN: We're seeing ever more sophisticated cyber-attacks in recent years. Is the security industry struggling to keep up?
AvRM: The industry is definitely struggling to keep up, it has always been a cat and mouse game, but over the past few years the momentum has accelerated drastically and the industry at large was not prepared for it. In the past, a lack of corporate awareness among executives and boards of directors meant the required funding to properly implement and adequately maintain a secure network and cyberinfrastructure was unavailable. Because of recent public scrutiny things have shifted a little and the security industry is trying to catch up.
BN: Are there misconceptions about what working in cybersecurity involves?
AvRM: There's often the assumption that all information security professionals spend their day hacking into their clients or their own systems to remove any vulnerabilities. Sure that can be part of the profession if your job includes penetration testing and vulnerability assessments. However, a large percentage of professionals spend more time writing reports, or security policies and analyzing gigantic quantities of repetitive system and network logs.
BN: Does the education sector need to up its game in providing the right skills?
AvRM: The education sector adapts relatively quickly to the needs of corporate America. The problem is cybersecurity involves a large spectrum of individual skills which require a strong understanding of the underlying technology and cannot be mastered in a short time frame. The education sector could potentially narrow the curriculum to develop specializations within cyber security in order to prepare a graduate for a specific entry level role within the industry.
BN: Would businesses benefit from hiring people without traditional security qualifications and training them in house?
AvRM: If they can find passionate individuals and have the resources to do so, then yes of course. With this recruiting method, companies can emphasize training on the specific needs, possible threats and risk factors specific to their business.
BN: Do we need to raise the profile of cybersecurity generally to make it a more attractive career option?
AvRM: No, cybersecurity has received a lot of attention in recent years from the media, business sector and academia. Great initiatives designed to encourage students to participate in cyber competitions like The Collegiate Cybersecurity Championship Cup have also increased awareness. Such events help elevate the interest and skills of university students who have an interest and passion for cybersecurity.
Image Credit: Africa Studio / Shutterstock
-

Platform enhancements seek to unlock the power of big data
Publié: octobre 15, 2015, 5:04pm CEST par Ian Barker

Businesses today have access to more data about their operations and their customers than ever before, but often that data is an underused resource.
Business intelligence company GoodData today announces new platform enhancements aimed at unlocking the value of data and widely distributing analytics to the people who are making business decisions on a daily basis.
"Company data is a dramatically underutilized asset. Organizations need to advance their use of analytics from merely driving efficiencies to empowering their networks of clients, partners, and internal stakeholders with relevant data," says GoodData Founder and CEO, Roman Stanek. "GoodData's engaging analytics distribution platform helps enterprises drive new revenue streams, improve partner relationships, and reduce customer churn".
The latest platform enhancements accelerate data distribution and monetization in several ways. Advanced distribution, automation and product lifecycle management allows businesses to manage deployments including automated provisioning and updating of large numbers of analytical workspaces.
An improved mobile experience can drive immediate action for consumers of the data thanks to a responsive, touch-friendly, personalized KPI dashboard and alerts. In addition self-service analysis enhances insights as end users are able to perform guided data discovery and can blend local data with governed, centrally distributed data.
More information and a free trial are available on the GoodData website. The company's executives will also be discussing how data can be used to generate revenue at a series of Data Monetization Summits starting in New York on 20 October.
Image Credit: Jojje / Shutterstock
-

The eight critical issues holding back IT
Publié: octobre 15, 2015, 2:51pm CEST par Ian Barker

The challenges of front line IT have become increasingly complex in recent years thanks to changes in technology, cyber threats and the sheer volume of work.
But what are the biggest challenges that IT teams face? A new survey by network monitoring company Ipswitch set out to find out and reveals the eight most critical issues that are holding IT teams back from achieving their innovation and operational goals.
The survey of 2,685 IT professionals across the globe reveals that their top challenges are seen as:
* Security (25 percent)
* IT infrastructure and application performance monitoring (19 percent)
* New technology, updates and deployment (14 percent)
* Time, budget and resource constraints (10 percent)
* Business issues (seven percent)
* Data management and storage (six percent)
* Device management and end user issues (five percent)
* Automation and reporting (four percent)It's hardy surprising that security comes out on top, and infrastructure and performance come second, but some support people may raise an eyebrow at end user issues only ranking seventh.
"Behind every business-critical application that serves as the lifeblood of modern commerce, companies rely on IT teams to keep them up and running 24/7," says Jeff Loeb, CMO at Ipswitch. "This survey identifies the key challenges facing IT organizations heading into 2016, and highlights how IT teams are coping with increasing complexity and security threats."
A full copy of the survey results is available from the Ipswitch website. Its major themes will be discussed at the Ipswitch Innovate 2015 Summit, a virtual two day conference to be held on 20 and 21 October.
Image Credit: Ronald Sumners/Shutterstock
-

SMS is key to business communication in a 'mobile first' world
Publié: octobre 15, 2015, 12:23pm CEST par Ian Barker

The switch to mobile devices has brought about a change in the way people communicate and consume media, moving away from the desktop PC and TV. This shift toward 'mobile first' or in some cases 'mobile only' needs to be reflected in how businesses expand their communication services.
This is one of the key findings of a new report by mobile engagement specialist OpenMarket and UK market research firm Portio Research. The report highlights that of the 7.3 billion people worldwide, 6.1 billion use an SMS-enabled phone, which amounts to 84 percent of the global population.
“With more people owning a mobile phone than a toothbrush, it's clear that 'mobile first' is much more than just a buzzword," says Karl Whitfield, managing director of Portio Research. "The way we interact has evolved in such a way that our mobile phones represent a conduit to the world around us, as we use them to communicate, shop for goods and consume content. This means that companies should not just incorporate mobile messaging into their communications strategy, but rather build their strategy around it".
The traditional 'broadcast' nature of enterprise communication doesn't work for the time-starved modern consumer and the use of social media highlights the need for personalized communication. The report suggests that because of its familiarity and ubiquity, SMS is the optimal channel for enterprise communication in the mobile first age.
"The shift towards a consumer-centric marketplace has meant that enterprise brands, regardless of the goods or services they are providing, have had to reassess their communications strategies," says Jay Emmet, general manager of OpenMarket. "SMS offers a unique blend of reach, flexibility and personalization to make it the most effective tool for businesses looking to engage more with their customers. What's important is that companies avoid the temptation to treat mobile messaging as just another tool for broadcasting information. They should implement it as a meaningful, two-way channel for individual customer interaction".
The full report is available to download from the OpenMarket website and there'll be a webinar to discuss the findings on 29 October.
Image Credit: Rido / Shutterstock
-

New AI product combines human and machine intelligence
Publié: octobre 14, 2015, 6:34pm CEST par Ian Barker

A number of major companies including IBM, Microsoft and Amazon have launched new machine learning platforms in the past year.
But data enrichment company CrowdFlower believes that to be effective and commercially viable machine learning needs more training and better data.
It's using the Rich Data Summit to launch its new AI product that combines machine learning and human-labeled training data sets to create predictive models which can be applied against new data. With this capability data scientists will be able to reduce the cost and increase the speed with which they enrich their data, without sacrificing quality.
"The industry has been having the wrong debate about human-versus-machine intelligence," says Lukas Biewald, chief executive officer and founder at CrowdFlower. "Human intelligence and machine intelligence aren't in competition; they're natural complements that reinforce each other. Humans' great strength is the cognitive ability of the brain, which brings into play context, meaning and judgment, and machines' great strengths are consistency and speed. By combining the best of human and machine intelligence into a single platform like CrowdFlower, the result is more data and higher quality data delivered faster and at lower cost. Data scientists who feed their machine learning platforms with high quality large scale human-labeled data sets can make the transition from interesting science experiment to a commercially viable business process generating millions of dollars of value for their company".
With AI, CrowdFlower customers will be able to apply a predictive model against new data sets. For rows of data that fall below a customer-defined confidence level, units can be routed to human contributors to complete enrichment tasks such as sentiment analysis or data categorization. By combining machine and human intelligence in a single platform, CrowdFlower can intelligently assign data enrichment tasks to either humans or a machine based on the customer requirements for scope, quality and cost.
The product is built to be interoperable with both open source and commercial machine learning solutions such as scikit-learn, Google Prediction, IBM Watson, and Metamind. The company plans to partner with other machine learning solutions so data science teams can make their own choice and avoid vendor lock-in.
AI will enter private beta this year with general availability expected in the first quarter of 2016. You can find out more on the CrowdFlower website.
Image Credit: art4all / Shutterstock
-

Time is crucial in dealing with cyber security threats
Publié: octobre 14, 2015, 4:41pm CEST par Ian Barker

Of 430 security and risk professionals surveyed, 55 percent were dissatisfied with the length of time it takes them to contain and recover from attacks.
This is according to information security training and analysis organization SANS, which has released the results of its latest report into data center and cloud security.
According to the survey, 59 percent of organizations are able to contain attacks within 24 hours, leaving many open to prolonged and increased damage as attacks spread laterally through data centers and clouds. 37 percent take up to 8 hours to contain attacks and 17 percent report taking more than a week.
"When it comes to limiting damage and preventing data breaches, time continues to be the biggest challenge for security and risk professionals," says SANS analyst Dave Shackleford. "Most respondents said they use traditional tools to monitor traffic between datacenters and internal or external clouds, and are unhappy with the level of visibility and containment speeds they get. If our security stance is going to improve, we need better visibility, the ability to make configuration changes faster and to contain attacks more quickly".
Other findings include that 44 percent of enterprises reporting breach information have had sensitive data accessed by attackers, these same respondents were among those using traditional security tools in their data centers and clouds. Multiple attacks are common too with 28 percent of organizations having experienced up to six data breaches in the past 24 months.
The results show that 37 percent of organizations use distributed cloud and data center computing systems. But security seems to be losing ground in the move to distributed computing, 44 percent of respondents said their biggest challenge was that cloud providers don't offer the visibility needed to protect users and data. In addition 19 percent say cloud providers don’t give them the security support they need and 49 percent have no formal cloud security strategy in place. Making matters worse is the lack of effective security controls available and in use. While 75-100 percent of respondents are using traditional tools in data centers, that number drops off to less than 35 percent in the cloud.
You can find the full report on the SANS website and there's an infographic summary of the findings below.
Image Credit: razihusin / Shutterstock
-

IT professionals express doubts over IoT security
Publié: octobre 14, 2015, 4:12pm CEST par Ian Barker

According to a new survey, 64 percent of consumers are confident they can control the information access of Internet of Things devices, but 78 percent of IT professionals say security standards are insufficient.
The findings come from the 2015 Risk/Reward Barometer of global cyber security association ISACA and suggest a major confidence gap about the security of connected devices between the average consumer and cyber security and information technology professionals.
More than three out of four US consumers (83 percent) consider themselves to be somewhat or very knowledgeable about the IoT, and have an average of five IoT devices in their home. Smart TVs top the list of most wanted IoT device to get in the next 12 months, with internet-connected cameras, connected cars and wireless fitness trackers also ranked highly.
However, the survey of IT and cyber security professionals reveals that there's an aspect to the IoT that exists below the radar of organizations. 50 percent believe their IT department is not aware of all of their organization's connected devices, things like connected thermostats, TVs, fire alarms and even cars. The likelihood of an organization being hacked through an IoT device is medium or high according to 74 percent of those asked. Also 62 percent think that the increasing use of IoT devices in the workplace has led to a decrease in employee privacy.
"In the hidden Internet of Things, it is not just connectivity that is invisible. What is also invisible are the countless entry points that cyber attackers can use to access personal information and corporate data," says Christos Dimitriadis, international president of ISACA and group director of Information Security for INTRALOT. "The rapid spread of connected devices is outpacing an organization’s ability to manage it and to safeguard company and employee data".
The survey suggests that some of the fault lies with device manufacturers. 77 percent of professionals say they don't believe that manufacturers are implementing sufficient security measures in IoT devices. A similar proportion (78 percent) don't think current security standards sufficiently address the IoT and believe that updates and/or new standards are needed. Privacy is also an issue with 88 percent believing that device makers don't make consumers sufficiently aware of the type of information the devices can collect.
Whilst consumers are generally less concerned than the professionals, 89 percent of US consumers say it's important that data security professionals hold a cyber security certification if they work at organizations with access to consumers' personal information.
You can read more on the results on the ISACA website and there's a summary of consumer attitudes in infographic form below.
Photo credit: Odua Images / Shutterstock
-

Instart Logic helps eCommerce sites gear up for the holiday season
Publié: octobre 14, 2015, 3:08pm CEST par Ian Barker

The holiday season is peak selling time for online businesses, so it's imperative that websites optimize their shopping experiences to acquire first-time visitors as customers.
Cloud application delivery specialist Instart Logic is launching new performance solutions designed to optimize website experiences for retail and e-commerce sites.
A new One Time Cache solution helps sites acquire first-time visitors with fast, personalized experiences, while User Prioritization allows companies to optimize revenue by predictively prioritizing users during peak traffic times. The new capabilities are the start of a family of features using predictive algorithms and big data to improve website performance and user experience.
"The holiday shopping season offers eCommerce websites a once-a-year opportunity to convert new visitors to customers and to optimize revenue from loyal customers," says Manav Mital, CEO of Instart Logic. "Instart Logic is helping eCommerce companies leverage software technologies like predictive algorithms and big data to improve business performance during the most important time of the year".
One Time Cache allows sites to predictively pre-load dynamically generated web pages and serve them from cache to first-time visitors. By avoiding the round trip back to the customer's origin it improves performance by between 30 and 50 percent for first-time visits to a retailer's website.
User Prioritization predicts which users are likely to be the most valuable and prioritizes those users at peak traffic times. By controlling the percentage of end users who are able to access the site and prioritizing certain higher-value buyers above others, companies can increase revenue under unexpected loads. Being able to control and manage the flow of web traffic during peak times allows for a dramatically improved user experience, improving customer retention and revenue.
More information on Instart Logic's solutions is available on the company's website.
Photo Credit: Nonnakrit/Shutterstock
-

Behavioral analysis adds protection to the cloud
Publié: octobre 13, 2015, 2:01pm CEST par Ian Barker

Protecting data in the cloud requires companies to secure the data itself but also to guard against cyber attacks, stolen credentials and more.
Security specialist StratoKey is announcing what it calls the 'second generation' of cloud protection using behavioral analytics tied to defensive countermeasures, as part of an update to its core StratoKey Cloud Access and Security Broker (CASB) platform.
It allows organizations to build behavioral analysis profiles that track specific user level metrics. These profiles are then tied into the StratoKey Countermeasure engine. When metrics within behavioral profiles are exceeded, StratoKey automatically enacts countermeasures to prevent the threat from progressing.
"Cloud encryption gateways started life as dumb gateways that waved users through, providing they entered appropriate authentication credentials," says Anthony Scotney, founder and CEO of StratoKey. "The second generation of cloud encryption gateways (now known as Cloud Access Security Brokers) are defined by not only encryption, but by Behavioral Analysis, Monitoring and Countermeasures in a single solution that is flexible enough to support all of an organization’s cloud applications".
Key features of the CASB platform include selective in-app encryption, identity aware authentication and cloud visibility though real-time monitoring and analytics. It also offers behavioral analysis and anomaly detection that are cloud and SaaS application agnostic. It meets the encryption requirements within HIPAA as well as guidelines regarding access control, including implementation specific details.
More information on the latest CASB platform is available on the StratoKey website.
Photo Credit: Slavoljub Pantelic / Shutterstock
-

Millennials lose faith in organizations' cyber security
Publié: octobre 13, 2015, 10:38am CEST par Ian Barker

New research suggests that millennials in the US and UK have lost trust in the ability of enterprises and governments to protect their personal data online.
The survey comes from digital identity and credentials specialist Intercede and questioned around 2,000 16 to 35 year-olds. It indicates a widespread state of mistrust that has the potential to change the nature of online interactions with public agencies and corporations and points to a need for action to avoid a future backlash.
The number of respondents describing their level of trust as 'none' or 'a little' are at significantly high levels -- 61 percent for social media platforms, 38 percent for retailers, 22 percent for federal/national government, and 19 percent for financial institutions.
Few respondents described their level of trust as 'complete' -- just 17 percent in state/local government, 13 percent for employers, and as low as 4 percent for fixed and mobile telecom operators.
The research also suggests that Millennials want the organizations they interact with to apply rigorous security to all of the personal information they provide. When asked how important it is that a range of personal data is only shared with those individuals or companies they have specifically authorized, 80 percent replied that it was 'very important' or 'vital' for financial and medical information. However, 74 percent of respondents also gave these ratings for location data, 58 percent for social media content and 57 percent for purchasing preferences.
"Unfortunately we now live in an age where data breaches have become a common occurrence and the more digitally connected we become, the greater the risk," says Richard Parris, CEO of Intercede. "Government and business need to step up to more effectively safeguard the private information of their constituents and customers online or risk eroding trust and further damage to their reputations. Millennials are a prime and extensive demographic driving votes and dollars worldwide. Restoring digital trust by taking active measures to ensure privacy and secure personal data should be a top priority".
More details on the research are available on the Intercede website.
Photo Credit: Catalin Petolea/Shutterstock
-

Who's looking at your screen and how can you stop them? [Q&A]
Publié: octobre 9, 2015, 5:12pm CEST par Ian Barker

We can all remember seeing kids at school hunched over their desks to prevent anyone seeing what they were writing on their test papers. But when it comes to hiding sensitive information on your screen things aren’t that easy.
How big a problem is eavesdropping in this way and what can be done to guard against it? To find out, we spoke to Dr Bill Anderson, Chief Product Officer of technology company OptioLabs which has just announced a collaboration with AMD to help solve the issue.
BN: How big a problem is visual eavesdropping?
BA: The reality of today's world is that data is constantly being exposed on mobile devices. Using laptops, tablets and phones in places like coffee shops, airports, hospitals, or even inside company offices, puts information at risk to visual eavesdroppers, often without a user’s knowledge. A surprising 42 percent of all data breaches are caused by the simple observation of a computer screen -- according to studies by the Secret Service, Verizon Business and CERT at Carnegie Mellon -- but when you consider the fact that 89 percent of people admit to reading over someone else's shoulder (OptioLabs Mobile Worker Privacy Survey, 2013), it is evident just how frequently this type of data loss can occur.
BN: What types of data are most at risk from this issue?
BA: The same OptioLabs survey also shows that 83 percent of mobile workers admit to using computers in public with confidential data displayed. All data is at risk from this issue, but sensitive data, such as corporate IP, personal and corporate financial information, health records, credit card information, and social security numbers are especially at risk because they are regularly exposed inside and outside of the work place. In fact, the 2014 US State of Cybercrime survey shows insiders made up the highest percentage of cases where data was compromised or stolen in 2014; 76 percent of the data lost were confidential records, 71 percent were customer records, and 63 percent were employee records.
BN: How effective are aftermarket solutions like filters and hoods?
BA: Screen filters and hoods can certainly prevent someone beside you from viewing your screen, but consider this: if someone is standing directly behind you, not only will they be able to see your screen just as clearly as you, but you will you not know that they are looking over your shoulder. Filters and hoods are ineffective because they do not protect information from visual eavesdroppers and they do not warn a user when their information may have been compromised.
Filters also introduce distortion, reduce screen brightness, and make it difficult for a colleague collaborating next to you to read your screen. This affects both consumers and enterprises, but enterprises face the additional issue of needing to comply with privacy regulations. When enterprise users remove their filters due to inconvenience, it takes enterprises out of compliance and puts them at risk of failing an audit.
BN: How is OptioLabs working to solve the problem?
BA: The security industry has focused on driving protection efforts toward the network and device layer, without much consideration for the most outward facing risk -- the last 2 feet from the computer to the user. OptioLabs PrivateEye Enterprise provides a layer of protection to address this vulnerability by protecting against data loss due to direct observation of the computer screen. The product provides organizations with a data security and compliance tool to prevent, monitor and respond to incidents they would otherwise miss. PrivateEye Enterprise protects against data leakage in real-time and provides actionable intelligence to monitor threat patterns.
BN: How does the technology work?
BA: OptioLabs' PrivateEye Enterprise uses facial recognition to unlock an authorized user's screen automatically, and continuously validates the user to ensure ongoing protection. Attention sensing technology in PrivateEye automatically protects the screen by blurring it whenever the user looks away or leaves their computer, and instantly clears it when they look back or return. The software continuously scans the scene around and behind a user to identify additional faces looking at the user's display, and if an eavesdropper is detected, PrivateEye alerts the user. The solution can also be set to automatically protect the screen when this occurs. Further, if an intruder attempts to log in while the user is away, a picture will be captured. Security alerts are also logged and can be sent to a 3rd party SIEM tool to incorporate into broader incident analysis.
Image Credit: racorn / Shutterstock
-

The benefits of moving from VMware to the cloud
Publié: octobre 9, 2015, 3:40pm CEST par Ian Barker

VMware has long been a favorite with businesses. But there's evidence that with the advent of second generation cloud many companies are considering a move away from VMware to a more flexible option that gives them better control over configuration and costs.
IaaS specialist ProfitBricks is helping businesses migrate their systems from VMware to the cloud and has a lot of experience in the field.
Enterprises may be nervous about some aspects of moving to the cloud, in particular how their data is going to be secured. ProfitBricks uses double redundant storage with data stored on two synchronised sub units in separate geographical locations. Customers have the option to ensure that machines aren't hosted on the same physical server if required and are free to make their own additional backup arrangements.
Achim Weiss CEO and co-founder of ProfitBricks says, "You can have the same level of security set up on our cloud systems as you can on your own servers. We're also able to attract a team of good security staff thanks to the size of the business and a varied workload".
ProfitBricks has a Data Center Designer tool which makes it easy to set up complex scenarios via a graphical interface. Customers can run any type of OS that works on an x86 architecture, this makes it very easy to migrate existing systems. Hyper-V and VMware configurations can be automatically converted too. "Once they're on the cloud then they can start optimizing their setups," says Weiss. "It's very easy to scale, for example the core size of a server can be increased while it’s running."
Web hosting company ComSite runs 200 virtual servers on behalf of clients and has switched from using VMware systems in data centers to using the cloud with ProfitBricks, it has seen a 20 percent reduction in its costs as a result.
Sean Burchell ComSite's CEO says, "ProfitBricks eliminates the need to worry about infrastructure. We can spin up a new server in five minutes and we only pay for the time we're using". The switch has helped the company to grow because it can concentrate on sales and spend less time on maintaining systems.
When customers buy a core and RAM on ProfitBricks it's dedicated to them and not shared with anyone else, and customers are free to adopt their own standards for encryption of data in transit. The company is also in the process of gaining ISO 27K certification for security management standards.
"Customers have 100 percent control of their data and applications on the cloud," adds Weiss. "The same thing you can do with your hardware at home you can do with us. There are no restrictions on what kind of network protocols you use or how you set up your networks. It's painless cloud".
You can find more information on the benefits of running IT infrastructure in the cloud on the ProfitBricks site.
Photo Credit: Roland IJdema/Shutterstock
-

New mobile CRM solution for smaller businesses
Publié: octobre 8, 2015, 5:04pm CEST par Ian Barker

Small businesses are no different from larger ones when seeking to get the most productivity out of each working day. However, they don't always have access to the kind of productivity software used by larger businesses.
To help smaller companies compete, client engagement specialist vCita is launching a new solution built from the ground up to support on-the-go lifestyles of service-based SMBs.
vCita Mobile is an integrated, customizable client engagement and CRM app that enables small business to access information, perform critical client facing tasks, and quickly serve customers round the clock. At the same time it helps them save resources on routine tasks such as scheduling, invoicing, and document sharing. The CRM app is integrated with a business website and email to let clients to schedule appointments, book services, and pay fees online, reducing the load on the company.
"Today's small business service professionals are trying to squeeze as much productivity out of their workday as possible, while facing ever increasing competition where client response times could make the difference between losing and keeping a client," says Itzik Levy, founder and chief executive officer of vCita. "When we developed vCita Mobile, this is the type of business we had in mind. The app’s business management capabilities maximize productivity, and our website, email and social network integrations ensure fast response to client requests, and unparalleled level of customer service".
Features of vCita Mobile include a customizable online portal where customers can schedule appointments, pay invoices, share documents, and communicate online or by phone. Staff are able to accept, reject or reschedule appointments from their phone, reducing scheduling conflicts. Businesses can get instant notification for any client request from the web, email or social media and immediately respond via the mobile app.
It's also possible to access all client information from anywhere, manage work schedules, assign client appointments to staff members and share information across a team. Invoices can be generated and sent outside the office and the system can generate reminders for upcoming appointments, or send alerts to clients who require a follow-up at a specific time or who warrant special attention.
The vCita Mobile platform can be downloaded from the Apple App Store and Google Play or you can find more information on the company's website.
Photo Credit: EDHAR/Shutterstock
-

How to confuse a self-driving car using everyday hardware
Publié: octobre 8, 2015, 4:31pm CEST par Ian Barker

We've already seen that conventional cars can be vulnerable to attacks by hackers. But it seems that self-driving vehicles may be equally vulnerable.
It's possible to trick a self-driving Google car into stopping or taking evasive action using around $60 worth of hardware according to a leading security researcher.
Jonathan Petit, Principal Scientist for Security Innovation, Inc has demonstrated that it's possible to trick the car’s sensors using a laser pen and a pulse generator -- which could be replaced by something simpler like a Raspberry Pi or an Arduino.
The vulnerability lies with the car's roof-mounted 'eye' which uses a Light Detection and Ranging (LIDAR) system to supplement its radar and cameras to create a 3D map of its surroundings using a laser and allow it to detect potential hazards.
Using the laser pointer system the car can be fooled into thinking there are objects alongside or ahead of it, forcing it to slow down or stop. Petit described a proof of concept attack in a paper written while he was a research fellow in the University of Cork's Computer Security Group.
During tests, he was able to trick the sensors into seeing 'ghost' vehicles or pedestrians from a distance of 330ft (100m). Although LIDAR works on private frequencies, Petit was able to record and imitate the pulses it generates to create fake objects.
Google isn't the only company to use LIDAR, with Mercedes, Audi and Lexus all having experimented with similar systems. In an interview with IEEE Spectrum Petit argues that it is never too early to start thinking about security. "There are ways to solve it," he says. "A strong system that does misbehavior detection could cross-check with other data and filter out those that aren't plausible. But I don’t think car makers have done it yet. This might be a good wake-up call for them".
Petit's paper is available to download and he'll be presenting his findings at Black Hat Europe in Amsterdam next month.
-

Corvil makes network data available across IT teams
Publié: octobre 8, 2015, 3:55pm CEST par Ian Barker

Network data is an increasingly important resource for IT teams, particularly when it comes to analyzing and resolving security threats. But unlocking the potential of that data can be difficult.
Dublin-based analytics specialist Corvil is launching a new platform that unlocks the power of network data, with an intuitive and customizable user interface and a new data automation engine that dramatically reduces the time, expense, and complexity of working with network data.
The Corvil Tera Release adds a new portfolio of real-time security analytics, giving network operations, application operations and security operations teams an accurate and collaborative, real-time picture of critical service chains across their business.
"We believe that the most effective way for IT to assure and safeguard the delivery of critical applications, services, and data to the business is for all IT teams involved to have a common, trusted, granular source of shared data," says Donal Byrne, CEO of Corvil. "Network data is widely regarded as the most granular and powerful source of real-time data that can be used for this purpose. The challenge is to make network data analytics super-easy, cost-effective and widely available to all. We believe that our new Tera Release achieves this objective with our customers reporting up to 90 percent reduction in time for IT Ops to see, analyze and act on critical business application flows at a cost that is less than what the network team traditionally spends on legacy network probes".
Key features of the product include a new HTML5-based user interface with polished, intuitive, and customizable dashboards that have been optimized to perform workflows for multiple teams. The Tera data engine automatically discovers application and business data flows within raw network data with zero configuration. The data in these flows is decoded, transformed, and self-populated into tables and graphical widgets, giving the full picture for what is happening across a business in real-time.
The new Tera release also seamlessly integrates live threat intelligence and real-time network forensics with leading SIEM (security, information and event management) platforms. It’s fully user programmable so that customers can decide for themselves how much data to keep, and for how long. In addition, the Tera Release now supports a broader array of connectors for streaming Corvil data to big data platforms such as Cloudera Enterprise Data Hub.
For more information on the Corvil platform and how it can be used for network and security analytics visit the company's website.
Image Credit: watcharakun/Shutterstock
-

New solution allows secure networking via public Wi-Fi
Publié: octobre 8, 2015, 3:00pm CEST par Ian Barker

We've come to expect public Wi-Fi pretty much everywhere we go these days. But using these networks can leave you open to a whole range of security risks.
There's now a way to use public networks safely as network specialist Xirrus is launching Xirrus EasyPass Personal Wi-Fi. This is a key feature now available in all Xirrus cloud managed networks that safeguards users and their data when accessing public Wi-Fi, guest networks and hotspot environments.
In a recent Xirrus survey on Wi-Fi usage, 76 percent of people said they know that public Wi-Fi is not secure, but 62 percent use it regardless of the security implications. EasyPass Personal Wi-Fi allows users to create a secure personal network via a simple, one-time process that authenticates all devices, ensuring the data across their platforms is safe inside the public network at all times.
Unlike a VPN, which encrypts end-to-end connections back to a corporate network and requires additional software, EasyPass Personal enables users to easily create their own secure personal network that automatically encrypts the data on the Wi-Fi network.
"Awareness of public Wi-Fi vulnerabilities is at an all time high. Whether we want to acknowledge it or not, every time we connect to public Wi-Fi we are putting our data at peril and are at risk of identify theft. Until now there hasn’t been a wireless solution to address this threat," says Shane Buckley, CEO of Xirrus. "EasyPass Personal Wi-Fi is groundbreaking for our industry. With this introduction, Xirrus offers the first and only solution in the market that allows a secure private connection to be created within a public Wi-Fi network. Now establishments that have deployed Xirrus Wi-Fi can deliver the safest connection available and protect their users from cyber crime".
EasyPass Personal Wi-Fi allows devices to communicate within the secure personal network, traffic encryption protects valuable data and users can connect all personal devices effortlessly with no client configuration needed. It allows businesses offering public Wi-Fi environments to reap the benefits of short term secure Wi-Fi communications. They can create a higher level of Wi-Fi security to offer new services, attract new business and create customer loyalty.
You can find out more about EasyPass Personal on the Xirrus website.
Image Credit: Sidarta / Shutterstock
-

Qualys launches customizable security assessment questionnaires
Publié: octobre 7, 2015, 4:57pm CEST par Ian Barker

With ever increasing regulatory requirements, guidelines and standards it's hard for businesses to ensure that they're following everything correctly. Add in the need to ensure compliance from third-party vendors too and it can become a major headache.
Cloud based security specialist Qualys is about to help streamline things by announcing the general availability of customizable questionnaires as a new addition to its suite of integrated services.
Qualys Security Assessment Questionnaire (SAQ) enables organizations to assess business processes and vendor risk by centrally capturing all relevant information, therefore reducing time and cost. In addition, this new service allows companies to demonstrate compliance against internal policies, standards and mandates such as PCI-DSS, HIPAA, COBIT and ISO 27001/2.
"Organizations must adhere to hundreds of constantly evolving regulatory requirements, standards and guidelines, and ensure that third-party vendors follow them as well," says Philippe Courtot, chairman and CEO of Qualys, Inc. "Until now the task was largely a manual process managed via email and spreadsheets. Qualys SAQ has turned a previously tedious and decentralized process into a streamlined, simple and repeatable one managed entirely online".
SAQ is a cloud-based solution that systematically gathers risk data, compliance information and evidence files. It addresses both the procedural and technical requirements of security and compliance. The package includes the ability to create custom templates by importing questions or can use out-of-the-box campaigns to assess risk and compliance requirements.
A questionnaire template can be assigned to specific users or groups. Questionnaire results can also be grouped together to simplify the management of multiple ongoing surveys. Results can be monitored via campaign progress tracking and customizable dashboards, reflecting vendor risk and compliance posture.
You can find more information and request a free trial on the Qualys website.
The company today also announced a beta app for the ServiceNow configuration management system that will automatically update the ServiceNow Configuration Management Database (CMDB) with any asset discovered by Qualys, and with up-to-date information on existing assets. This will give ServiceNow users full visibility of their global IT assets on a continuous basis.
"Every unidentified or misclassified asset and every delay in securing it invites security breaches," says Courtot. "Our highly distributed cloud-oriented architecture enables us to provide a real-time view of an organization’s global assets across on premise infrastructures, elastic cloud environments and endpoints. This seamless integration with the ServiceNow CMDB provides users full visibility of their global assets within the ServiceNow environment".
More details on this can be found on the Qualys blog.
Image Credit: pichetw / Shutterstock
-

90 percent of companies have suffered at least one cyber attack
Publié: octobre 7, 2015, 3:38pm CEST par Ian Barker

According to the latest survey by Kaspersky Lab, 90 percent of companies have suffered a cyber attack and for larger businesses the cost could be as much as half a million dollars.
Of the 5,500 companies surveyed nearly half, 46 percent of businesses, lost sensitive data due to an internal or external security threat.
The average cyber attack for enterprise incurs costs of up to $73,000 for professional services, up to $58,000 in lost business opportunities and up to $420,000 in downtime. Smaller companies suffer too and average cyber attack costs of up to $38,000 can prove crippling.
As well as the direct costs of an attack organizations both large and small need to address staffing, training and IT infrastructure upgrades to prevent future incidents from occurring. Those costs could be up to $69,000 for an enterprise and up to $8,000 for a small business. It's also important to factor in the reputational damage that an organization can suffer as a result of a cyber attack, which could total up to $204,750 for an enterprise and up to $8,653 for a small business.
"Businesses have known for a long time that any cyberattack has its consequences, but the high costs associated with addressing a cyberattack after an incident occurs is quite alarming," says Chris Doggett, managing director of Kaspersky Lab North America. "These numbers should serve as a wakeup call for both large and small businesses. IT security needs to become a more common priority for organizations and it is our hope that these numbers will motivate businesses to take the necessary steps to implement effective cybersecurity technology and strategies to prevent having to pay an enormous cybersecurity bill".
Despite the scale of threats many businesses are still not doing enough to protect themselves from what could be a financially crippling attack. Only 50 percent of IT professionals surveyed listed prevention of security breaches as one of their three major IT concerns and 44 percent of businesses have not implemented anti-malware solutions to prevent them.
More detail, including the types of threat most likely to lead to a security breach, can be found in the full IT Security Risks report available from the Kaspersky site.

Photo credit: Tashatuvango/Shutterstock
-

Large organizations struggle with end-user mobile computing
Publié: octobre 7, 2015, 1:32pm CEST par Ian Barker

Large organizations are unsure of how to approach the concept of end-user computing as a cohesive strategy, and manage the proliferation of devices and their associated security risks.
This is among the findings of the 2015 Mobile Workforce Report published today by global ICT services company Dimension Data.
The study looked at 730 organizations employing 1000 or more staff in five regions, 11 countries and across 14 industries. The research was undertaken to understand the challenges that CIOs are facing when it comes to adopting a user-centric approach to doing business, and provide insights into strategies and habits influencing end-user computing.
Of those polled, 44 percent say they have incorporated enterprise mobility into a broader end-user computing strategy and have budget for end-user computing on multiple devices, while 13 percent have no end-user computing strategy in place.
On average, end-user computing accounts for 28 percent of the IT budget. The research indicates that almost two thirds (61 percent) of participants indicated that they are seeing return on investment from end-user computing initiatives, with a further 65 percent of organizations are seeing competitive advantage from their approach.
"The global workspace is changing along with where and how people work and perform their business functions," says Jaco Hattingh, Senior Vice President for Enterprise Mobility at Dimension Data. "We're seeing a growing number of organizations starting to embrace future forward working styles such as flexible time and ability to work remotely, which includes accessing the corporate network".
Among other findings are that mobile IT management and mobile applications are top initiatives for 2016. But many respondents do not have a comprehensive management solution for both phones and tablets (32 percent) or utilize a siloed approach to manage both PCs and smart devices (31 percent).
Security is the single top priority component of EUC among almost half (43 percent) of respondents, followed by IT Service Management. CIOs are the most prominent driver of strategic mobility initiatives within the business. However, they remain in a reactive state when it comes to end user computing, and are struggling to act strategically.
Meanwhile the modern worker expects access to anyone, anytime and anywhere, but 82 percent of organizations stated that a key obstacle facing end-user computing initiatives is protecting company data and providing a good user experience.
"It appears that the proliferation of employee-owned mobile devices has placed the IT department in a reactive state when it comes to management and enablement, leaving CIOs unable to respond strategically. Nevertheless, it's a vibrant and exciting time for end-user computing as organizations press ahead aggressively," Hattingh adds.
The full results of the study will be discussed at a virtual event on October 20th. You can find out more and register to attend on the Dimension website.
Image Credit: Syda Productions / Shutterstock
-

Why buying a used mobile could get you more than you bargained for
Publié: octobre 7, 2015, 12:46pm CEST par Ian Barker

If you buy a mobile device or a hard drive second hand are you buying the previous user’s data along with it?
A new study from data erasure company Blancco Technology Group and recovery specialist Kroll Ontrack suggests that in a high percentage of cases the answer is yes.
Based on an examination of 122 pieces of second-hand equipment, the study revealed that 48 percent of the hard disk drives and solid state drives looked at contained residual data. In addition over 2,000 leftover emails and more than 10,000 call logs, texts/SMS/IMs, photos and videos were retrieved from 35 percent of the mobile devices tested.
When the devices were examined in more detail researchers discovered that a deletion attempt had been made on 57 percent of the mobile devices and 75 percent of the drives that contained residual data. More worrying was the discovery that those deletion attempts had been unsuccessful due to common, but unreliable, methods being used, leaving sensitive information exposed and potentially accessible to cyber criminals. Residual data left on two of the second-hand mobile devices was significant enough to discern the original users' identities.
"Whether you're an individual, a business or a government/state agency, failing to wipe information properly can have serious consequences. One of the more glaring discoveries from our study is that most people attempt in some way or another to delete their data from electronic equipment," says Paul Henry, IT Security Consultant for Blancco Technology Group. "But while those deletion methods are common and seem reliable, they aren't always effective at removing data permanently and they don’t comply with regulatory standards. There’s no better example of this danger than the findings of a recent state audit, which found that 12 US state agencies responsible for handling taxes, programs for people with mental illness and driver's licenses used inadequate methods to attempt to wipe information. The big lesson for both businesses and consumers is to understand which deletion methods are effective and comply with regulatory standards and, most importantly, to be cautious of blindly trusting that simply ‘deleting’ data will truly get rid of it for good".
More information is available in the full Privacy for Sale report which is can be downloaded from the Blancco Technology site.
Image Credit: LovePHY / Shutterstock
-

Transforming how enterprises handle unstructured IoT data
Publié: octobre 6, 2015, 4:54pm CEST par Ian Barker

The Internet of Things is growing fast and as more and more enterprise applications collect IoT data, specifically time series data from sensors, they need fast, reliable and scalable read and write performance.
To best accomplish this, the data must be stored, queried and analyzed together. To enable this Basho Technologies is launching Riak TS, a distributed NoSQL database designed to aggregate and analyze massive amounts of sequenced, unstructured data generated from the IoT and other time series data sources.
"The rise of unstructured data presents a significant opportunity for innovation. As a result, companies are demanding database solutions that are operationally easy and specifically optimized to handle this type of data," says Adam Wray, CEO of Basho. "Built on the same core Riak foundation, we now provide a solution specifically optimized for storing and retrieving unstructured data, making us the only NoSQL player that has specialized offerings for key value, large object and time series data. With Riak TS, customers can more easily scale and execute on Internet-of-Thing uses cases and more".
Riak TS provides high availability combined with massive scalability. It can be made operational at lower costs than traditional relational databases and is easy to manage at scale. Unlike other NoSQL databases, Riak TS enables customers to take advantage of time series applications and ensure they're always available for both read and write operations, with the ability to easily scale as devices or users increase.
If nodes are added Riak TS automatically and uniformly distributes data across the cluster to prevent sharding. Data co-location ensures that time series data is located on the same node based on time, geohash or both to prevent hot spots in clusters.
Data can be validated on input to ensure accuracy and it can be interrogated with SQL-like queries. It can seamlessly integrate with Apache Spark to ensure easier and faster operational analysis of time series data, and of course it integrates with the Basho Data Platform to support multiple database models taking the complexity out of building and deploying active workloads in Big Data, IoT and hybrid cloud applications.
You can find out more about Riak TS on the Basho website and it will be demonstrated at AWS re:Invent this week.
Image Credit: Profit_Image / Shutterstock
-

LookingGlass helps to close the DNS security gap
Publié: octobre 6, 2015, 3:52pm CEST par Ian Barker

One of the biggest areas of vulnerability for corporate networks is DNS, with companies having to contend with DDoS attacks and attempts to steal data.
In an effort to help customers close the gap in DNS security, threat intelligence specialist LookingGlass Cyber Solutions has developed an intelligence-driven network security solution that identifies and stops DNS-based cyber threats.
LookingGlass Dynamic Threat Defense focuses on using threat intelligence to identify threats, then addresses and mitigates them during DNS resolution, which is one of the biggest vulnerability areas of corporate networks today. Organizations are increasingly suffering attacks against their DNS infrastructure and many companies are simply not looking for covert communications where attackers use DNS as an avenue to communicate and exfiltrate data. This trend, along with years of research and monitoring networks, suggests protecting DNS infrastructure is essential to achieving improvements in overall cyber security for the enterprise.
It stops the communication between malware on the organization’s network and its command and control server or known bad destination. By stopping the beaconing out or the reception of control information, Dynamic Threat Defense prevents threats and prevents data breaches from occurring. This buys organizations valuable time to address the malware infection without fear of further infiltration or damage.
Chris Coleman, CEO of LookingGlass, says, "Dynamic Threat Defense 1.0 delivers on the LookingGlass strategy of integrating threat intelligence and network mitigation to help customers solve security challenges more efficiently and effectively by giving them the operational capability to actively defeat malware command and control while providing critical protection of DNS resources."
Dynamic Threat Defense integrates LookingGlass DNS Defender, a protocol-specific firewall for DNS, with LookingGlass ScoutVision, a threat intelligence and management system, and LookingGlass Virus Tracker, the world's largest botnet and malicious domain monitoring system.
By combining threat intelligence and network security at the DNS infrastructure level, LookingGlass Dynamic Threat Defense is able to fend off cyber attacks efficiently and effectively. You can find out more on the LookingGlass website.
Image Credit: Tashatuvango / Shutterstock
-

Threat Stack launches security monitoring for Docker containers
Publié: octobre 6, 2015, 3:20pm CEST par Ian Barker

The popularity of Docker to run software in containers has increased enormously, but it does raise issues surrounding keeping those applications secure.
To help Docker users stay on top of security issues Threat Stack, a specialist in security monitoring for AWS systems, has extended its product range to provide monitoring of Docker containers for security threats.
Threat Stack Pro Edition provides companies with flexibility in workload security. The product includes access to the fully-featured Threat Stack API, plus new reporting features and new integrations with Docker and AWS CloudTrail.
"It's important to companies that their security products allow them to scale with confidence, achieve compliance and operate efficiently," says Threat Stack Chairman and CEO Brian Ahern. "Our Pro Edition moves customers closer to a single pane of glass with the ability to share Threat Stack's powerful insights with the other tools and processes that keep them moving fast".
Support for Docker events in Threat Stack means that users gain complete visibility into key events within their environment. The integration includes out-of-the-box default rules -- the Docker Base Rule Set -- as well as the ability for users to easily apply custom rule sets to their environment. Container activity flows through and integrates seamlessly into the security, operations and compliance feature sets of Threat Stack, allowing companies to operate quickly and with confidence.
Threat Stack also provides the real-time visibility and historical records companies need to prevent data loss and meet compliance regulations. Threat Stack Pro Edition features key file tracking and reporting to ensure their important files stay protected, user and alert reporting to understand how a user escalated or changed their privileges to root, and compliance reporting for regulations including HIPAA.
"Docker use is exploding and the correlation of a host-based intrusion detection system (HIDS) with Docker and AWS CloudTrail is what gives Docker users the vital context they need to act swiftly on a security incident," says Venkat Pothamsetty, Threat Stack's vice president of products. "This integration is what makes the Threat Stack Pro Edition solution unique and gives customers operating on AWS with Docker additional information to evaluate their security strategy, to ensure all activity within their application environment is secure and compliant".
The product will be showcased at this week's AWS re:Invent 2015 or you can find out more on the Threat Stack website.
Image Credit: megainarmy/Shutterstock
-

IT pros love hybrid cloud but struggle to track consumption
Publié: octobre 5, 2015, 5:36pm CEST par Ian Barker

According to a new survey 79 percent of IT pros are pursuing a hybrid cloud strategy and one third will grow their cloud services by more than 50 percent in the coming year.
The figures come from cloud consumption management specilalist Cloud Cruiser which surveyed IT professionals who attended the Amazon Web Services (AWS) Global Summit held in San Francisco and New York City in April and July.
The study also highlights frustrations with respondent's ability to control cloud consumption and allocate costs to the proper business users within their organization. Its findings include that 66 percent find it challenging to track cloud consumption for cost allocations, 30 percent or more will complement their AWS cloud with another cloud, and only 25 percent are able to align IT costs with consumption.
When it comes to adding additional clouds the most popular options are an internal, private cloud on 31 percent and Microsoft Azure on 30 percent. Only 19 percent cited Google Cloud.
"Survey results like this are always useful to highlight trends and adoption rates of cloud services," says Deirdre Mahon, Chief Marketing Officer at Cloud Cruiser. "These findings tell us what we hear from our customers every day; budget tracking and forecasting is extremely difficult when you simply don't know who is using what service, at what capacity level much less the financial impact. Making investments in the right solutions is critical even during the early stages of cloud adoption. Measure from the beginning and it will pay dividends when your bill comes in month after month".
You can find more on the survey results on the Cloud Cruiser website. The company will be showing its CloudSmart-Now offering that makes it easy track hybrid cloud usage by user and costs at AWS re:Invent in Las Vegas this week.
Image Credit: Brian A Jackson / Shutterstock
-

HP announces new open source network OS
Publié: octobre 5, 2015, 5:16pm CEST par Ian Barker

With the volume of network traffic growing exponentially, large web-scale organizations need to scale their data centers to new levels. These organizations need scale and flexibility for their data centers to meet increasingly complex business and technology requirements.
To provide developers with the ability to accelerate innovation, avoid vendor lock in and protect their investment, HP together with a community of like-minded companies, today announced the launch of the OpenSwitch Community along with a new open source network operating system (NOS).
"To address the business and web-scale networking needs of the industry, HP along with partners, Accton Technology, Broadcom, Intel and VMWare, have created the OpenSwitch Community to develop an open source NOS," says Mark Carroll, chief technology officer for HP Networking. "Open source software with its collaborative community of specialized developers accelerates innovation and improves the stability of the software platform, providing organizations with a more powerful infrastructure to support their unique business requirements".
The closed model of traditional networking doesn't allow customers, or their software and integrator partners, to innovate and tailor their networks to meet their business needs. An open source NOS, based on open standards, allows developers to engineer networks to prioritize business critical workloads and functions, delivering the users a dramatically improved experience. Networks based on an open NOS will also remove the burdens of interoperability issues and complex licensing structures that are inherent in the proprietary model.
The newly released NOS offers L2/L3 protocol support, it's based on a state driven database for persistent and ephemeral states and all inter-module communication is through a system state database. It also has a universal API approach.
The OpenSwitch NOS will be supported on HP's Altoline open network switches. HP Technology Services will offer customers professional and support services for networks based on the OpenSwitch NOS to allow for secure and low risk deployments in production infrastructure. You can find more information and join the community on the OpenSwitch website.
Photo credit: asharkyu / Shutterstock
-

FireLayers and Check Point bring security to enterprise cloud apps
Publié: octobre 5, 2015, 3:44pm CEST par Ian Barker

As more employees use their personal devices for business, corporate data is increasingly put at risk from sophisticated malware.
To foil these attacks, real-time protection company FireLayers and security specialist Check Point Software Technologies today announced their joint Extend Perimeter Security solution, which spreads security to cloud applications and provides enterprises with protection from zero-day threats and malware distribution.
By pairing the FireLayers Secure Cloud Application Platform with Check Point’s SandBlast Threat Emulation service for advanced sandboxing, documents downloaded through file-sharing apps are scanned for and cleaned of any potential malicious behavior, ensuring the recipient of a document is safe from foul play.
"Today's organizations are increasingly dependent upon SaaS and the cloud and need the tools that will allow them to continue to be efficient and facilitate collaboration," says Alon Kantor, vice president, Business Development at Check Point. "Our Extend Perimeter Security solution will help organizations extend their security infrastructure to protect against many of the threats associated with SaaS application use today so that they can protect critical business information from any device".
As part of Extend Perimeter Security, the FireLayers Secure Cloud Application Platform scans all file repositories in the cloud, using Check Point SandBlast to identify and detect any malware infected files. Depending upon the results of the scan, FireLayers enforces security policies to eliminate risk. The joint platform continuously evaluates all files at rest and as they are used. This includes detecting malicious file uploads, shared file downloads, the opening of infected files and more, protecting the enterprise from active threats.
Check Point SandBlast inspects the file in a sandbox environment at the CPU level, evaluating whether the content is malicious or not. It then informs FireLayers of its analysis, triggering actions like blocking, quarantine, admin alerts or user notifications as required.
For enterprises this is extending the protection perimeter to include SaaS, IaaS and PaaS apps. It also allows safe collaboration with cloud-based platforms such as Office 365, Box, Dropbox, Jive, etc. Real-time user mitigations and a transparent user experience reduce false positives and ensure cloud application usage remains uninterrupted. Because there's no configuration required on the client side, deployment is fast and seamless.
"We are excited to provide enterprises with a totally new level of much-needed protection against malware being distributed by cloud apps," says Boris Gorin, vice president, Security at FireLayers. "Today, enterprises need security solutions that can manage BYOD and anywhere/anytime access across the extended corporate network. FireLayers extends security protections to cloud app data, access and usage and delivers highly granular policy-based rule enforcement and auditing down to the single command level. The combined technologies from Check Point and FireLayers detect malware and prevent it from infiltrating organizations via cloud apps".
FireLayers will be at the New York City Tech Security Conference on October 15 or you can find out more on the company's website.
Image credit: bannosuke / Shutterstock
-

Iconmedia WebAnimator Plus is a powerful animation creator [Review]
Publié: octobre 5, 2015, 2:42pm CEST par Ian Barker
Flash used to be a core part of the internet, because for a time it was the only practical way to produce animations on websites.
It was also easy to use which made it attractive to designers and advertisers and at one time it seemed almost every site was decorated by Flash banners and adverts. But the arrival of HTML5 and CSS3, plus worries about security vulnerabilities, means that Flash has been on the decline for some time.
WebAnimator Plus could be the alternative for businesses looking for a solution that’s as easy to use as Flash but capable of producing animations that will work in all modern browsers. Using HTML5, CSS and JavaScript its animations will work on PCs as well as smartphones and tablets without the need for and hassle of additional plug-ins.
Features
If you’ve used any sort of graphics or video editing package in the past then WebAnimator’s interface will feel immediately familiar. If you’ve created Flash animations you will feel even more at home as elements like the Stage, Scenes and Timeline even have the same names.
You can add objects to the Stage -- the central grid area of the screen -- using a simple drag and drop interface, then using keyframes on the timeline you can make them disappear, move, change color, zoom them in and out, and so on. You can use simple geometrical shapes but you can also add existing bitmap or jpeg images and work with those.
Of course you can add text too and WebAnimator gives you access to the Google Fonts Directory so you can access a wide range of web fonts safe in the knowledge that they’ll work on other systems. The Plus version also lets you add audio and video files.
In Use
Each element you place on the Stage has its own properties depending on its type. You can change opacity and rotation for example, add drop shadows, reflections and more. There are a number of default templates allowing you to easily set up things like slide shows and product presentations with minimum effort.
You can add a selection of pre-defined live animations like fade outs and zooms, plus you can create your own customised effects using key frames if you prefer. Once an animation is in place it’s possible to fine tune its timing from the timeline. It’s also possible to add user interactions so that an element will react to a mouse click or hover. This is handy for making website buttons so that they change colour when the mouse passes over them or after they’re clicked.
You can add audio and video files but the lack of a standard format across all browsers means that, currently, you need to make different formats available to ensure the user is served with the right version. This isn’t the program’s fault but it nonetheless feels a bit clunky.
You can preview your work in a browser at any time to see how it’s coming along. Once you’re happy the finished animation can be exported as HTML5 code ready to drop into a web page, or as an animated GIF. If you’re familiar with JavaScript there’s a built-in editor that lets you tweak the source code of your design.
Conclusion
WebAnimator Plus is easy to get started with if you’re new to creating animations, but there’s plenty of powerful functionality available if you dig deeper. You may find you’re sent scurrying for help on some of the more advanced options though as they’re not always intuitive. Fortunately there’s a comprehensive PDF manual included in the package which also has details on integrating WebAnimator’s code with your website.
WebAnimator Plus costs £64.99 or there’s a cheaper basic version for £44.99 that lacks some functions like the ability to create animated buttons or embed audio and video.
Although it may seem expensive it’s a very capable package and if you’re serious about adding animated content to your website it’s well worth a look. There’s a 14-day trial available from WebAnimator's site to allow you to give it a go.
Pros
Easy to get started
Uses open web standards
Plenty for advanced usersCons
Some less intuitive options
Clunky video functionsITProPortal Review 7/10 Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Big data + behavioral science = better decisions
Publié: octobre 5, 2015, 1:12pm CEST par Ian Barker

Companies sometimes struggle to get value from their data. Information is often static and can’t provide insights into individual business decisions.
To help deliver better value from data, decision analytics company OnCorps is unveiling its Adaptive Decision Analytics platform that intelligently engages users and prompts them to make better decisions.
It combines behavioral science and machine learning to identify, create and apply the data an organization needs to dramatically improve its desired results. OnCorps mobile and online applications are tailored to each client's unique requirements and provide real-time individual diagnostic visualizations, benchmarking, data correlation and personalized smart nudging capabilities.
"Though data and analytics tools are powerful, the challenge is making data relevant and actionable," says Bob Suh, founder and CEO of OnCorps. "Organizations spend too much time and capital collecting and charting data. Not enough time is spent turning data into better decisions. We created OnCorps to usher in the next generation of analytics, applying technology that enables users to track and measure their decisions and nudges them to make choices that improve their odds of success".
OnCorps applications enable individual users to compare their decisions and performance with the real-time benchmark data of various peer performance groups, gaining insight on key differences. Users then track their decisions over time to see how different decisions impact their performance and build a personalized 'decision diary' to capture and improve their decision rules. Finally, applications deliver smart 'nudge' messages, personalized and adapted over time for each user, these prompt changes in behaviors that lead to better outcomes.
OnCorps applications can result in 2-3 times higher user engagement rates and higher quality data. The platform allows configuration of custom applications along with rapid and repeated reporting.
You can find out more and try out the apps on the OnCorps website.
Photo Credit: Adchariyaphoto/Shutterstock
-

Rock Jaw Alfa Genus V2 -- quality earphones at an affordable price [Review]
Publié: octobre 2, 2015, 3:53pm CEST par Ian Barker

When you buy earphones you usually have to choose between audio quality and how much you want to spend. British company Rock Jaw Audio, however, is on a mission to provide a strong listening experience at an affordable price.
There's a definite grey theme here, supplied in an attractive grey box, the earpieces themselves are aluminium with a smart grey finish, they come with a selection of rubber ear tips so you can get a good fit. There's also a clip for the cable and a soft carrying pouch. They have an in-line microphone for making phone calls and the earpieces have 8mm dynamic drivers. The jack plug is gold-plated, it's a 90 degree design though so may be awkward connecting to some devices. They have a 1.2 metre long cord, which is fine for listening to a smartphone in your pocket but a bit limiting for other situations.
It also comes with three pairs of interchangeable tuning filters that screw into the earphones so you can set bass, neutral or treble response according to preference. This is a clever idea and does have an appreciable effect on the sound quality, it effectively gives you three sets of headphones in one. However, it's a bit fiddly and means you have to decide on your preferred setting in advance of a listening session.
The Alfas are supplied with a choice of small, medium and large silicone ear tips, plus large and medium memory foam and small double flange versions, so you should be able to find a good fit.

The important bit of course is the listening experience and that's where those interchangeable filters come into their own. The silver-coloured bass filters deliver a solid sound that's impressive given the small size of the earpieces. In the quest for bass though they do lose something in the mid range. The black treble filters on the other hand deliver a good top end response but leave you with a rather weedy bass. For day to day use then, and to avoid the hassle of swapping filters, the gold-coloured natural filters are the best option. They deliver clear vocals and the bass is good without being overpowering. It's handy to have the choice though for when you want to listen to particular types of music.
The Alfa Genius V2s are light, unobtrusively stylish and deliver a decent listening experience. The ability to fine tune their output using filters may seem gimmicky but it is effective. You could easily pay $100+ for earphones offering similar sound quality so at $66.45 (£44.95 in the UK) these look like a smart choice.
You can find more information and order direct from the Rock Jaw Audio site.
-

The most effective malware removal tools
Publié: octobre 2, 2015, 12:47pm CEST par Ian Barker

The security industry tends to focus on prevention, but even on the best protected system there's always a chance of zero day infections slipping through the net. It's therefore important that products have an effective removal capability too.
The latest report from independent testing organization AV-Comparatives focuses on 16 of the leading security tools and how good they are at removing malware from infected systems.
The programs were tested against 35 malware samples on a 64-bit version of Windows 8.1. Products were rated on their effectiveness in removing the malware and its remnants, and on their convenience in operation to produce a points score. Removal was ranked on what traces were left over. Convenience was assessed on whether removal could be carried out in normal mode, or whether a rescue disc was required or boot into safe mode.
The top performer in the tests was Kaspersky, earning 93 points, followed by Avast and BitDefender both on 89, AVG on 87 and Avira on 86. ThreatTrack Vipre achieved the lowest score of 65, with Sophos on 72 and Fortinet on 74.
The report suggests that some providers could improve their results by offering a rescue disc option, providing up to date offline installers and not requiring users to login to online accounts to activate cleaning features. It also recommends that products should check for infection before installing and that there should be the option to download installers with random names to fool malware that attempts to disrupt installation of cleanup tools.
The full report is available to download from the AV-Comparatives site.
Image Credit: Sergey Nivens/Shutterstock
-

IBM and Box collaboration delivers new data management tools
Publié: octobre 1, 2015, 3:38pm CEST par Ian Barker

Cloud applications, mobile use and the changes they bring to working methods make managing data in the enterprise a more complicated process.
We reported a few months ago on IBM and Box beginning a collaboration on cloud projects and the two companies have now announced new solutions that can help enable advanced collaboration, data classification, enterprise search and enhanced analytics.
"Organizations in every industry have an unprecedented opportunity to transform the way they connect with customers, collaborate with partners and engage with their colleagues and employees by gaining control over their data," says Rich Howarth, Vice President, Enterprise Content Management Products and Strategy at IBM. "Together IBM and Box are bringing the best cloud collaboration and content management solutions to bear to help our clients turn their data into a resource that they can call on to drive growth".
There are four new offerings, IBM Content Navigator with Box helps customers search, access and share content across both on-premise and Box environments, with a single integrated view. IBM Content Navigator provides an interface and development platform that clients can use to shape the user experience of content within desktop and mobile ECM solutions.
IBM StoredIQ with Box helps companies make more informed business decisions by providing them with an in-depth assessment of unstructured data across Box and on-premise environments, including where it resides. Using IBM StoredIQ with Box, customers will be able to search on-premise and Box-based data, classify it and migrate it to the Box Platform.
IBM Case Manager with Box helps seamlessly enable sharing content on the Box platform with external participants as part of the business process. It’s designed to optimize results by applying context to content and enabling flexibility across business processes.
Finally, IBM Datacap with Box helps businesses capture documents across multiple sources, extract key information from them, and store them to Box. This can help businesses reduce costs and increase accuracy and speed in powering workflows, regardless of device.
"The Box and IBM partnership reimagines enterprise content management and collaboration for the digital enterprise, meeting the deepest of security and control requirements while unlocking content experiences and digital business processes that were not previously possible," says Whitney Bouck, Senior Vice President and General Manager of Enterprise at Box. "As you can see with today's news, Box and IBM are committed to a rapid pace of joint innovation, and there’s much more to come".
You can find out more about the partnership on the IBM website.
-

Free software suite helps users get started with big data
Publié: octobre 1, 2015, 3:02pm CEST par Ian Barker

Many businesses are put off making use of big data by the costs and complexity of the software and infrastructure involved.
Enterprise data management specialist Solix Technologies is aiming to break down this barrier by making the Standard Edition of its Solix Big Data Suite available free of charge.
Built on a single node cluster and packaged in a virtual environment, Solix Big Data Suite Standard Edition is based on the company’s full suite. It features reports archiving, file achiving and Solix Secure Search Analytics to allow users to prove their enterprise archiving on Hadoop use cases.
"Eighty percent of the data generated by enterprises is unstructured, be it files, reports, videos, images, logs, or clicks," says Sai Gundavelli, CEO of Solix. "Archiving all of that in a secure central repository, built on commodity storage, compute and open source Hadoop, should equate to huge infrastructure cost savings for enterprises".
The Standard Edition software includes file share archiving which gives users the ability to archive files from network file shares into Apache Hadoop, supporting NAS devices, Windows shares and Unix shares.
It has a Solix Virtual Printer to capture print streams directly into Apache Hadoop in a compliant and searchable PDF/A format. Applications can print data directly to the Solix Virtual Printer to preserve documents and reports, and access them through a user-friendly search interface.
There's also a unified archive for storage optimization, built-in full text search and reporting capabilities, and integrated information lifecycle management to deal with retention management and legal hold requirements.
You can find more information and download the Solix Big Data Suite Standard Edition on the company's website.
Image Credit: Maksim Kabakou/Shutterstock
-

Social intranet allows anytime, anywhere workplace collaboration
Publié: septembre 30, 2015, 5:30pm CEST par Ian Barker

Teams need to communicate in order to work effectively, but in the modern work-anywhere world with a scattered workforce this isn't as easy as just popping over to someone's desk for a chat.
Social intranet provider Incentive is helping organizations and enterprise teams stay in touch, with the announcement of its new mobile apps for iOS and Android and desktop apps for Windows, Mac and Chrome.
The new native collaboration apps are designed to help teams, regardless of location, connectivity or device, experience the business benefits of a seamless, intuitive and consistent social intranet. This should result in increased productivity for teams through improved collaboration and communication, all from one secure platform.
Using Incentive's online platform, the new mobile and desktop apps will help enterprise teams work together to share files across the entire enterprise, directly from a mobile device or desktop.
It will also allow staff to connect with anyone in the organization through private conversations or team chat rooms, as well as get notified when items are uploaded, edited, shared or commented on, or when a team member tags an individual or a group. There's instant access to collaboration features like wikis, blogs, tasks and photo albums, with a smart search engine that saves and indexes data, making it easily retrievable from any device.
It can help managers discover team members with particular skills or expertise to improve cross-team collaboration. It preserves an enterprise's collective 'braintrust' by housing corporate knowledge and assets within a single, secure, all-in-one platform.
"Today's employees are used to not only being constantly connected, but also enjoying a social user experience that mimics popular consumer applications on any device -- phone, tablet or desktop," says Rickard Hansson, CEO and founder of Incentive. "The availability of Incentive's native apps makes the social intranet experience seamless, consistent and fast, regardless of location, device or connectivity, so teams can get more work done, together".
For more information, a free trial and to download the apps you can visit the Incentive website.
Photo Credit: nmedia/Shutterstock
-

How the mobile security landscape is changing [Q&A]
Publié: septembre 30, 2015, 4:28pm CEST par Ian Barker

As our mobile phones become increasingly central to both our personal and working lives, securing them and the data they hold has become paramount. The nature of the mobile space means that threats are more dispersed and change fast, so traditional security solutions are struggling to cope.
How does this change in the security landscape affect businesses who may be faced with supporting a range of different devices and operating systems thanks to BYOD policies? We spoke to Gert-Jan Schenk, VP for EMEA at mobile security specialist Lookout, to get his view.
BN: There are lots of really affordable Android devices available now, many of which don't use Google Experience. What challenges do these pose for business?
GJS: Because of BYOD, enterprises' mobile footprints are no longer homogeneous -- it's not a Blackberry-only world anymore. Now, the devices that an IT department must take into consideration include Android, iOS, and Windows. But things have gotten a bit more complicated recently with the development and growing popularity of non-Google Experience devices and OSs like Cyanogen and Xiaomi.
These devices and OSs offer flexibility and customization along with a low-cost rate -- with this appealing proposition, you can only expect user numbers to increase. Already, an estimated 50 million users are using the open source Cyanogen OS on their smartphones.
If you're an enterprise, this changing landscape means one important thing: these new devices, which you're not used to seeing, are soon going to start popping up on your network as employees bring them through the front door, and they present new security challenges.
For example, on a Google Experience device, because there is such brand recognition, there is more expectation that the devices and the apps running on them are vetted by Google, the manufacturers, the carriers, or some combination of the three. The majority of apps downloaded on these devices are also by default funneled through Google Play. Non-Google Experience devices introduce much more fragmentation. When using these devices, apps can be downloaded from a variety of sources including unvetted third-party app stores. These stores are generally much less-regulated environments where "shadier" apps can exist unchecked.
BN: Shouldn't the onus on security of business data be with the network rather than the device?
GJS: Look no further than the recent example with XcodeGhost for proof that security needs to be implemented at the device level as well as the network.
Knowledge is key and having visibility into whether a potentially risky app or vulnerable device has entered your corporate network gives you the power to make fast remediation decisions. Within 24 hours of XcodeGhost being discovered, Lookout enterprise users were protected.
Visibility will become even more instrumental as new devices begin to enter the workplace, as we are seeing with Cyanogen. Traditional network security, device security, application security, and app vetting, all need to work toward one common goal: a safer corporate network and protected personal data.
BN: What do enterprises need to do to assess the risk of embracing BYOD?
GJS: One of the biggest risks that enterprises actually create is not embracing BYOD. We call this 'Shadow BYOD,' when a company doesn't think they have a BYOD program but in fact, employees are doing corporate work on their smartphones anyway. This becomes an issue of unmanaged personal devices connecting to the network and accessing corporate data.
I know I sound like a broken record, but visibility and protocol are really key here. Organizations must have sight of the devices connecting to their network. That means having a simple but clear BYOD policy, and ideally tools like MDM so that patches can be rolled out quickly and easily. Secondly, and this is the area that still needs work today, organizations must understand that it's impossible to track and have visibility of all threats yourself, which is why it's important to have a security partner.
BN: How can admins spot potentially risky apps or vulnerable devices, such as jail-broken phones, especially as the OS space becomes more fragmented?
GJS: Let's dig into jailbreaking as an example of how IT admins can deal with security in the fragmented mobile market.
Did you know that an estimated 7.5 percent of all iPhones -- amounting to more than 30 million devices worldwide -- are jailbroken? Jailbreaking a device is very tempting to many; who wouldn't want access to a whole new world of apps, easier international travel, and more control over their phone?
Jailbroken devices create a major enterprise risk given their ability to run apps developed outside of Apple's review, which may be malicious or contain vulnerabilities. Jailbreaking removes the normal signing certificate checks that prevent these apps from executing and gives them unrestricted access to the device, including the ability to use undocumented APIs that Apple otherwise prohibits. These private APIs can empower apps with a wide range of dangerous capabilities on jailbroken devices, such as the ability to install or launch additional code or collect location data without notification.
One of the other security implications with jailbreaking is that it often requires a person to downgrade some of the security settings in the stock version of iOS in order to make the jailbreak work. People who don't know what they're doing may not know how to reinstate some of those security settings to ensure their jailbroken device is protected post-jailbreak.
If a device has been jailbroken or rooted then your existing security investments can be rendered ineffective. While most MDM/EMM solutions claim to provide jailbreak/root detection, they are not always effective due to the nature of the attack targeting the kernel of the OS.11. Lookout's Mobile Threat Protection identifies devices that have been rooted or jailbroken, even if they bypass MDM detection.
BN: Doesn't part of the solution rely in educating users rather than relying on technology?
GJS: You need both, but you can't rely completely on employee education. You need to supplement it with technology.
Employees are obviously in control of what they click on, download, or install. If you educate them to be highly security-conscious and suspicious of everything, there would be a significant reduction in the number of security breaches.
But the bad guys will keep innovating and finding new and more clever ways to target users. A sound security or BYOD strategy should never take a leap of faith that the end-user will operate with caution 100 percent of the time, or be able to keep up with attacker innovation as quickly as the security technology providers.
BN: Will there always be a trade-off between security and the convenience of mobile access?
GJS: Forward-thinking organizations have today recognized the need to embrace mobile devices in the workplace, due to enhanced worker productivity, increased revenues, and reduced device and data expenses.
At the same time, if employees are not provided access to the mobile tools they want, they are likely to adopt their own productivity tools, which can put sensitive data at risk. We have all come to expect a great user experience on our mobile devices. If IT-provided solutions are too hard to use or too obtrusive on user privacy, you can bet that employees will not be utilizing them.
As businesses look to securely enable their organization's mobile productivity, it is especially important that they also select mobile security solutions that meet the high standards of today’s mobile consumer. Overall, one of the biggest hurdles we see when it comes to having employees actually adopt these technologies is usability. If you make the protection or enforcement too complex or if it requires heavy lifting at all for the end user, you greatly increase the risk that the employee won't use the protection or that they'll figure out a workaround.
Image Credit: Moon Light PhotoStudio / Shutterstock
-

New cloud platform offers up to 20x performance improvement
Publié: septembre 30, 2015, 3:23pm CEST par Ian Barker

Modern applications and services need to deliver content to users at unprecedented speeds, without sacrificing quality or reliability. But as more systems move to the cloud that highlights the shortcomings of traditional delivery systems and WANs.
Cloud based networking company Teridion is announcing general availability of its advanced Global Cloud Network which it claims can provide up to 20x performance improvement for end-user generated, bi-directional internet content.
"The Internet is an incredibly powerful tool, but until now, we have struggled to take full advantage of its capabilities. It's still common for us to fall victim to slow response times and volatile connections," says Elad Rave, founder and CEO of Teridion. "We are breaking down these boundaries and providing users with a seamless Internet experience -- no matter their location, device or application. It's our goal for our SaaS customers to be able to generate additional customer loyalty, and the funding and general availability of our product are major steps in this direction".
Teridion has achieved its speed and reliability using SoftLayer infrastructure from IBM Cloud. Through the IBM Global Entrepreneur Program, IBM Cloud's startup ecosystem, Teridion has received free mentoring, support and SoftLayer infrastructure via the program’s Catalyst option.
The resulting Global Cloud Network features intelligent routing using proprietary algorithms and the Teridion Management System, in conjunction with Teridion Measurement Agents, to provide a real-time congestion map of the Internet to find the best possible path, taking into account bandwidth, latency and geography.
Teridion Cloud Routers are created on demand, providing scalability and enabling users to only pay for the resources they consume. The solution works with the largest cloud providers in the world to ensure the speed and reliability of traffic, without customers needing to leave their cloud provider.
The system doesn't cache users' data, and uses end-to-end SSL encryption with no termination to secure data across the network. Since there's no hardware or software to install, and quick and easy provisioning, a typical cloud customer can be connected to the network in under an hour.
The Teridion solution is currently being used by more than 15 companies spanning some of the most bandwidth-demanding applications and services, such as hosting and file sharing, rich media and advertising. You can find out more on the company's website.
Image credit: Alexander Kirch/Shutterstock
-

38 percent of online retailers are not yet prepared for the holiday season
Publié: septembre 29, 2015, 5:52pm CEST par Ian Barker

Online retailers rely on the holiday season for a high proportion of their revenue, yet a new survey suggests that with Black Friday only two months away, 38 percent aren't yet prepared for this year's sales.
The survey from email marketing company Campaigner shows this lack of preparedness is despite 70 percent anticipating a rise in mobile sales and nearly 50 percent planning to prioritize social sharing for marketing success.
Other findings are that 50 percent are enhancing their mobile responsive design to prepare for increased mobile sales this year. Social integration is seen as crucial too, with 71 percent agreeing that the number one add-on for email marketing success is integration with sites like Facebook and Twitter.
Content strategy is also changing with 69 percent saying they're approaching their content strategy differently this season compared to last year. There doesn't seem to be much consensus on how to do this, however, with almost 28 percent saying they're using more informational content over promotional content but just over 26 percent saying the opposite. Meanwhile 22 percent say they plan to incorporate more video content in their efforts but over 15 percent are planning a simpler approach to content.
"It's shocking to learn that such a high number of Internet retailers have not yet begun executing holiday strategies for this year," says Seamas Egan, manager of revenue operations for Campaigner. "Black Friday is just a couple of months away, and for most retailers, the holiday season is ripe with revenue if they prepare adequately".
You can see a summary of the survey results in infographic form below.

Photo Credit: Robert Kyllo/Shutterstock
-

New IBM partnership delivers improved communications compliance
Publié: septembre 29, 2015, 5:03pm CEST par Ian Barker

Additional reliance on social network platforms and social communication channels creates regulatory issues for enterprises.
This means that social media and communications content are becoming an increasingly popular target of opposing counsel in legal issues involving eDiscovery.
The problem for many companies is that they simply don't know what, if any, of these social communications are being used within their organization. As a result they're not actively capturing, managing or archiving all communications and social content -- potentially placing them at a higher risk of non-compliance and legal jeopardy.
In response to these issues IBM is announcing a partnership with real-time monitoring specialist Actiance. This will allow IBM to offer the Actiance Platform as part of its Information Lifecycle Governance (ILG) product portfolio to enable their customers to more effectively address the issues related to migrating their current technology solutions to the cloud.
"Unified communications, social media and cloud archiving are changing enterprise communications and how companies must control and manage those conversations so they are in compliance," says James Schellhase, worldwide business leader, IBM Information Lifecycle Governance Group. "With the Actiance Platform, IBM customers are now able to actively enforce and centrally manage policies to safely and securely govern all their communications data in the cloud at a lower cost".
Actiance's active compliance and archiving platform provides deeper insight into archived communications through the use of powerful cloud-based analytics. It will allow IBM customers to govern all of their enterprise communications across 70 plus different channels, including email, messaging, collaboration and social content, under one cloud platform.
This combined with IBM's deep expertise in the ILG space will enable companies across all industries, including financial services, manufacturing and insurance, to reduce the cost and risk of information governance and create and enforce policies for all business-critical communications.
You can find out more about the Actiance Platform on the company's website.
Image Credit: Jirsak / Shutterstock
-

Machine learning helps build better applications
Publié: septembre 29, 2015, 3:58pm CEST par Ian Barker

New toolkits and training for developers allowing them to create intelligent applications have been launched by machine learning company Dato.
Developers can use Dato Toolkits to build software that uses machine learning technology, combining historical data and real time user interaction to make predictions and decisions to deliver rich and adaptive experiences to their users.
The machine learning tookits include recommendation engines that can be added to applications to personalize user experiences by mining patterns in purchase and activity history, matching common users' tastes, and predicting future purchases or interests.
Image search and feature extraction using deep learning can be used to create more intuitive search experiences, automatically tag photos, and improve other application performance by using features extracted from images. Churn prediction detects which customers are likely to cancel a subscription or service by using advanced analytics to detect specific patterns. It can be added to applications to identify which customers are at risk of leaving.
There's also sentiment analysis which uses natural language processing, text analysis and computational linguistics to identify and extract subjective information in source materials. The technology can be used to discover the tone of a post in support forums or a customer’s opinion of a brand or product in reviews for better targeting.
"Over the next five years, every disruptive business will be differentiated by the intelligence of their applications. Machine learning is the core technology to make such intelligence happen," says Carlos Guestrin, Dato co-founder and CEO, and Amazon Professor of Machine Learning at the University of Washington. "We see a huge number of developers adding machine learning to their applications using the Dato platform, which is really exciting for us. Recommendation engines, sentiment analysis, churn prediction and deep learning are some of the most sought after machine learning technologies that help companies like Pandora, Zillow and StumbleUpon create new personalized customer experiences in real time".
In addition Dato has announced a partnership with Coursera and the University of Washington to deliver a six-course Machine Learning curriculum. Participants will be able to master machine learning fundamentals in six hands-on courses using the Dato platform. The course explains how to apply machine learning techniques to large and complex datasets, build applications that can make predictions from data, and create systems that adapt and improve over time.
You can find out more about Dato toolkits and download a free 30-day trial on the company's website.
Image Credit: art4all / Shutterstock
-

'Remediation gap' leaves businesses exposed to cyber attack
Publié: septembre 29, 2015, 3:02pm CEST par Ian Barker

Companies are leaving vulnerabilities unpatched for up to 120 days leaving them open to untargeted attacks, according to the findings of a new report.
Risk and vulnerability intelligence platform Kenna analyzed 50,000 organizations, 250 million vulnerabilities, and over one billion breach events from January 2014 to September 2015, and found that companies are regularly leaving vulnerabilities open for longer than it takes attackers to exploit them.
Unlike more widely publicized advanced persistent threats, non-targeted attacks pose a different challenge for security organizations. Rather than targeting a specific company, attackers attempt to steal valuable data from as many companies as possible, relying on automated tools and techniques to scale their attacks and exploit commonly found vulnerabilities. The recent discovery of the Heartbleed vulnerability in OpenSSL brought this to the forefront as a threat that exploited multiple targets at once.
"The public has grown plenty familiar with hacker seeking out a specialized target, such as Ashley Madison. But automated, non-targeted attacks still remain the most significant threat to businesses of all sizes," says Karim Toubba, CEO of Kenna. "Every company has data that hackers want to get their hands on, but security teams remain one step behind their adversaries. Security teams need to move quickly to remediate critical vulnerabilities, but they don’t have the tools needed to keep pace with hackers".
Among the report's findings are that automated attacks are on the rise with over 1.2 billion successful exploits witnessed in 2015 to date, compared to 220 million successful exploits in 2013 and 2014 combined -- an increase of 445 percent.
Despite their best intentions, most companies take an average of 100-120 days to fix found vulnerabilities. However, many companies have critical vulnerabilities that go unpatched altogether. The probability of a vulnerability being exploited hits 90 percent between 40-60 days after discovery, indicating that the length of time a company takes to react to vulnerabilities before attackers strike is critical. This creates a 'remediation gap', or time that any vulnerability is most likely to be exploited before it is close, of nearly 60 days.
"Companies will continue to face the cold reality that throwing people at the problem is no longer sufficient for remediating vulnerabilities and combatting the sheer volume of automated attacks," adds Toubba. "They need solutions that are as automated as the attacks that continue to hammer them -- fixing vulnerabilities manually is no longer possible in the 'new normal'".
You can read more in the full report which is available to download from the Kenna website.
Image Credit: alexskopje / Shutterstock
-

CloudHive provides protection for virtual machines
Publié: septembre 29, 2015, 2:02pm CEST par Ian Barker

One of the main concerns companies have about moving to the cloud is security. Traditional security measures can have gaps that leave systems vulnerable.
To address this network security specialist Hillstone Networks is launching CloudHive, a cloud security solution that uses micro-segmentation to protect networks beyond the perimeter down to every virtual machine in cloud deployments.
"Security in the cloud remains a key concern for organizations and is a major reason some applications and workloads have not yet moved to the cloud," says Tim Liu, CTO and founder, Hillstone Networks. "With Hillstone's CloudHive technology, organizations can now fully realize secure cloud services at scale through full visibility, control, and security across networks, down to the virtual machines".
CloudHive allows all virtual machine access points to be monitored to provide visibility and control of traffic, applications and attacks. VM topology, traffic insight, application identification, and comprehensive log features allow Cloud Service Providers (CSPs) to meet compliance and security audit requirements.
Each CloudHive Virtual Security Service Module (vSSM) is deployed on a physical server, enabling micro-segmentation for inter-VM communication. East-West traffic is secured with L2-L7 security services, including firewall features such as policy control and session limits. It also offers advanced security features such as Intrusion Prevention System (IPS) and Attack Defense (AD), as well as fine-grained application control.
On-demand security services can be applied to any and all new workloads and VMs through the scalability of vSSM. The deployment of vSphere with Operation Management (vSOM) enables unified security policy configuration for each virtual machine. CloudHive also supports vMotion to ensure security services persist in the event the VM moves.
Hillstone claims that CloudHive deployment doesn't impact existing network topology. It minimizes deployment and configuration overhead, so there's no business impact or network interruption. In addition, because it's a single appliance it reduces operational errors and improves overall efficiency. Total cost of ownership is reduced too as CloudHive security services do not need to update to Vmware's NSX.
You can find out more about CloudHive on the Hillstone Networks site.
Image Credit: Maksim Kabakou/Shutterstock
-

New solution automates integration of SaaS workflows
Publié: septembre 28, 2015, 3:25pm CEST par Ian Barker

Companies are increasingly turning to software as a service solutions. But these often lead to problems when needing to integrate workflows with in-house or other SaaS solutions.
To address this, cloud software specialist Azuqua has announced the availability of a new integration solution for connecting cloud applications and automating business-critical workflow.
Users and administrators of SaaS applications for marketing, sales, support, and customer success have a growing need to automate business-critical workflow between cloud applications. For example, triggering a hand-off from a closed sales opportunity in Salesforce to the support team in Intercom and professional services team in Workfront. However, existing integration options often don't meet these users' requirements. Predefined integrations available in SaaS marketplaces can't be extended to solve custom process requirements, and traditional integration platforms such as Enterprise Service Buses (ESBs) are expensive to purchase, and complicated to implement and modify.
Azuqua offers a simple and cost-effective approach to these business-critical integration needs. New and enhanced capabilities allow users to easily create, view, monitor and report on workflows. An easy-to-use visual designer expands the automation scenarios that can be defined with the addition of conditional branching. Data at each step in a workflow can be examined simplifying design, error-handling, and retries.
A log of all executions and reports summarizes usage and ensures workflows are always operating. Workflows can be arranged by process, team, or any custom classification. In addition, permissions ensure safe and secure collaboration on workflows by defining the individuals who can edit, view, or run them.
"The ability to use SaaS application APIs in workflows has become a fundamental business requirement, but the lack of easily customizable and affordable solutions only adds to the integration headache for many customers," says Jeffrey M Kaplan, managing director of THINKstrategies. "Azuqua is improving the way automations are developed and deployed, while significantly reducing the cost and improving the customer experience".
Azuqua will be on display at Integrate 2015 or you can find out more about the latest release and request a free trial on the company's website.
Photo credit: Alexander Supertramp / Shutterstock
-

Women make up only 10 percent of the IT security workforce
Publié: septembre 28, 2015, 12:51pm CEST par Ian Barker

New research carried out by non-profit certification organization (ISC)² and technology consulting firm Booz Allen Hamilton highlights a lack of gender equality in IT security roles.
Based on a survey of almost 14,000 global professionals, the report looks at the differences between men and women in the industry, the current and future outlook for women in the information security field and the unique skills women possess to fill information security positions today and in the future.
While women have represented only 10 percent of the information security workforce for the past few years, analysis from the last two (ISC)2 information security workforce surveys shows that women are quickly converging on men in terms of academic focus, computer science and engineering, and, as a gender, have a higher concentration of advanced degrees. Women in information security are making their largest impact in governance, risk and compliance (GRC) as one out of five women identified GRC as their primary functional responsibility compared to one out of eight men holding similar positions. The study identified GRC as a growing role in information assurance and cybersecurity.
"The information security field is expected to see a deficit of 1.5 million professionals by 2020 if we don't take proactive measures to close the gap," says (ISC)² CEO David Shearer. "Knowing this, it is rather frustrating to realize that we do not have more women working in the industry. Only 10 percent of information security professionals are women, and that needs to change. Through collaboration, research and partnerships, (ISC)² is committed to empowering under-represented minority groups in the industry, such as women, who bring skill sets that are critical to this industry’s future growth".
Among other key findings are that 58 percent of women have masters or doctorate degrees versus only 47 percent of men. In the GRC subgroup of respondents, women's average annual salary was 4.7 percent less than men. However, the study shows that men value monetary compensation slightly more than women who look for other incentives from their employers, such as flexible working.
Women are also more progressive in their views on training methods. Offering increased accessibility and wider diversity of information security training opportunities may prove to be increasingly valuable in retention and in elevating professionals' readiness to succeed in new roles.
The study is being released in conjunction with the (ISC)² Security Congress 2015 in California from September 28 to October 1, where there will be specific sessions discussing the issue of women in security.
Image Credit: Candy Box Images / Shutterstock
-

Companies grow using the power of the cloud
Publié: septembre 25, 2015, 3:07pm CEST par Ian Barker

Cloud technology specialist NewVoiceMedia has released the results of a survey showing that customers using its cloud services are growing at 13 times the international average.
The study carried out in July 2015, based on the publicly available revenue data of a sample of 300 UK and US businesses from the last two years, showed that NewVoiceMedia cloud users increased revenues by an average of 44 percent in the last financial year, compared with global economic growth of 3.5 percent.
In the UK its customers are growing at an average of 41 percent. Broken down by sector, media, telco and utilities customers are growing at 85 percent versus eight percent market growth. Financial services are growing at 76 percent versus -0.10 percent market growth, and business services customers are growing at 39 percent versus four percent market growth.
In the US the average customer growth rate is 46 percent. Retail customers are experiencing 109 percent growth versus seven percent market growth, business services are growing at 69 percent versus four percent market growth, and CPG and healthcare customers are growing at 57 percent compared with 12 percent market growth.
"We are honored to be working with some of the most successful businesses in their respective industries," says Jonathan Gale, CEO of NewVoiceMedia. "Our cloud customer contact solutions are attracting some of the world’s highest-growth businesses because we are relentlessly committed to driving innovation that is revolutionizing the way they connect with their customers worldwide and growing their business with improved efficiency, reduced churn and greater customer advocacy."
You can see a summary of the results in infographic form below or read more on the NewVoiceMedia blog.
Photo Credit: inxti /Shutterstock
-

MemSQL announces integrated Spark solution
Publié: septembre 24, 2015, 6:06pm CEST par Ian Barker

The in-memory performance and functionality of Spark is a valuable building block for enterprises looking to implement real-time data pipelines and streaming analytics.
This becomes more important as companies are faced with an increasing number of data points across different sources, and the need to deal with varied data types. Leader in real-time databases for transactions and analytics MemSQL, today released Spark Streamliner, an integrated Spark solution to give enterprises immediate access to real-time analytics.
It offers a one-click deployment of integrated Apache Spark to eliminate the pain of batch ETL (Extract, Transform and Load), and provides ease-of-use for broad adoption. With a web-based UI for pipeline setup, users can create multiple real-time data pipelines in minutes, perform custom transformations in real-time, and develop innovative applications inspired by fresh analytics.
"Spark Streamliner increases the opportunity for enterprises to work with real-time data, and now they can easily persist multiple data streams for ongoing analytics," says Eric Frenkiel, CEO and co-founder of MemSQL. "Streamliner is the first of many integrated Spark solutions to operationalize Spark, delivering intuitive access to sophisticated capabilities with the relational and in-memory architecture of MemSQL".
MemSQL Spark Streamliner, available as open source on GitHub, enabling development of innovative applications inspired by real-time data and easy access with full transactional SQL. Deployed along with a real-time data source like Apache Kafka, it can support thousands of concurrent users running real-time analytical queries, reduce data latency and stream data directly into MemSQL.
MemSQL will be at Strata+Hadoop World in New York next week or you can find out more on the company's website.
Image Credit: wavebreakmedia / Shutterstock
-

Fast data platform combines analytics and transactions
Publié: septembre 24, 2015, 3:59pm CEST par Ian Barker

The rapid growth of mobility and the Internet of Things is driving a need for real-time data analysis, and intensifying demand for faster insight and action in the enterprise.
In response to this demand, database specialist VoltDB is announcing version 5.6 of its SQL in-memory operational database, a fast data platform that combines streaming analytics with transactions to support mission-critical, real-time applications.
"Global organizations are using revolutionary approaches to leverage fast data to automate better operational decisions, enable micro-personalized customer experiences in real-time and enhance the performance of mission-critical applications," says Bruce Reading, president and CEO of VoltDB. "VoltDB is the industry's only database platform to take the complexity out of building fast data applications, enabling enterprises to more quickly monetize the value of their real-time data streams. By unifying continuous streaming analytics with transactions and adding the power of Active/Active replication, VoltDB is accelerating the business impact of fast data applications for every organization".
Enhancements in the new version include support for import and export of multiple data streams without the need to write code. There's also support for Elasticsearch so that VoltDB data can be sent to Elasticsearch servers or clusters to perform full-text searches using the popular text search engine.
Active/Active database replication enables disparate clusters to serve write transactions with changes replicated to another cluster. Data compression makes WAN transfers faster and more efficient, and customers can partition database replicas with rack-awareness to prevent having replicas on the same physical rack, improving availability in the event of a rack, chassis or power failure.
The latest version of VoltDB is available to download now from the company's website.
Image Credit: alphaspirit / Shutterstock
-

RightScale aims to simplify cloud management
Publié: septembre 24, 2015, 3:19pm CEST par Ian Barker

Whilst moving systems to the cloud can deliver savings in costs and efficiency, it presents new challenges in terms of managing systems and data.
With the launch of its Universal Cloud Appliance, California-based RightScale is aiming to deliver the self-service access that cloud users demand and give IT teams visibility and control over any cloud, any virtual machine, or any server through a single pane of glass.
Universal Cloud Appliance (UCA) supports Bare-metal server farms, virtualized environments such as KVM and Hyper-V, as well as clouds previously not supported by RightScale such as vCloud Air and Digital Ocean.
"RightScale enterprise customers use a wide range of infrastructure options, from existing virtualized and bare-metal datacenter environments to a variety of public and private clouds," says Kim Weins, VP of Marketing at RightScale. "Now our enterprise customers can use RightScale across any infrastructure that they run -- any cloud, any VM, any server -- by leveraging the Universal Cloud Appliance. RightScale customers will get a single point for visibility, control, monitoring, cost tracking, reporting, automation, and more".
UCA is delivered as a software appliance that can be downloaded and run on any server that has connectivity to the target resource pool. It provides a variety of out-of-the-box capabilities that can be used to manage individual servers and a plug-in model allows for RightScale, partners or customers to extend the functionality to include provisioning new resources on any platform. Combined with the RightLink agent, UCA enables a broad set of management, monitoring and governance capabilities.
The company says it can reduce development cycles and increase agility with faster provisioning, eliminate manual work with automation and orchestration, drive down spending with built-in cost controls, and help reduce risks with policy-based governance.
More information can be found on the RightScale website.
Image Credit: ND Johnston/Shutterstock
-

Zoomdata unifies analytics for cloud and on-premise data
Publié: septembre 24, 2015, 2:09pm CEST par Ian Barker

Businesses are increasingly dealing with a mix of data, both real time and historical, and stored locally and in the cloud. This can mean that they end up having to use a mix of analytic tools.
Visual analytics specialist Zoomdata is announcing its AnyCloud initiative, which enables enterprises to visually interact with all data in the enterprise, whether on-premise or in the cloud.
This includes the release of Zoomdata 2.0, featuring Zoomdata Fusion, which is now available via one-click deployments on leading cloud providers and allows hybrid deployment between cloud and on-premise data. The AnyCloud initiative also includes the launch of a new partner cloud enablement program that accelerates the creation of end-to-end big data solutions. Together, these innovations enable 'analytics anywhere' -- the ability to access modern and traditional data, plus real-time and historical information, across data in the cloud and on-premise.
Zoomdata has also announced that it's become a certified partner on the Microsoft Azure Marketplace. Through Azure HDInsight, Zoomdata provides enterprise business units the ability to run Hadoop distributions from Cloudera or Hortonworks. Customers seeking to capitalize on the performance of big data can now use Azure's One-Click deployment to activate the Zoomdata Server, along with its Cloudera, Hortonworks and Spark smart connectors. Those looking to deliver visual analytic solutions for big data can now take advantage of Zoomdata’s multi-tenant, distributed architecture to make business users more productive in gaining actionable insights about their organization's big data.
"Microsoft is an ideal associate for Zoomdata because of its global reputation for meeting the cloud computing demands of the world’s largest companies," says Justin Langseth, CEO of Zoomdata. "For enterprises looking for an on-demand solution that delivers fast visual analytics on Hadoop and big data, Azure and HDInsight paired with Zoomdata are a powerful combination of performance and ease of use. We look forward to working with Microsoft to accelerate the adoption of solutions on Hadoop among the Global 2000".
You can find out more about Zoomdata and set up a free trial on the company's website. You can also try Zoomdata on Azure free for 30-days.
Photo Credit: wavebreakmedia/Shutterstock
-

Consumers want ISPs to offer simpler online protection
Publié: septembre 23, 2015, 5:13pm CEST par Ian Barker

As the digital world expands with more and more connected 'things' from computers, tablets and smartphones to gaming systems, thermostats, cameras and smart TVs, many people feel less secure.
As a result consumers are looking for uncomplicated security solutions from their Internet Service Provider (ISP).
This is among the findings of new research from DNS platform provider Nominum which shows that 63 percent of consumers surveyed would like it if their current ISP provided one simple solution to increase security across all their connected devices. A majority (51 percent) agreed they would switch to another provider if they offered a higher level of online protection, without additional monthly charges.
Other findings include that 58 percent of consumers have either never changed their home gateway or router password, didn't know how to, or haven't changed it in more than a year. Up to 22 percent have never changed their home gateway password at all. This is despite publicity surrounding growth in internet vulnerabilities, and many expert security recommendations to change default passwords on gateways and routers.
Almost half (49 percent) of all respondents say they are adequately protected from online threats on their computers, tablets and smartphones. In addition 52 percent feel they understand Internet security well enough to choose, install and maintain the right security tools for their own home.
Consumer confidence drops, however, when other connected home devices -- gaming consoles, smart TVs, thermostats, etc -- are taken into consideration, with just 37 percent feeling they are adequately protected from online threats. Only 36 percent say they have installed security tools to protect connected devices beyond computers, tablets and cellphones.
Above all it seems people want simplicity, 80 percent of those who responded say that they didn't feel adequately protected online and would prefer to have a simpler solution.
"Old threats like phishing continue and the growing number of connected devices in the home creates even more exposure for consumers and their families. ISPs have a great opportunity to deliver a better, safer online experience for everybody and every connected device in the home," says John Arledge, general manager of applications at Nominum. "Consumers are looking for a straightforward, uncomplicated solution that keeps up with fast moving online threats without burdening performance or their user experience".
You can find out more about the findings on the Nominum blog.
Image Credit: Rawpixel / Shutterstock
-

DDoS attacks target online gambling sites
Publié: septembre 23, 2015, 4:15pm CEST par Ian Barker

The online gambling industry is big business, estimated to be worth over $40 billion this year. But its success makes it a target for extortion and for DDoS attacks.
DDoS can prove particularly harmful for this type of site as around 60 percent of transactions are carried out in real time and are therefore sensitive to latency.
IT security specialist Gold Security has produced an infographic looking at how these attacks affect the industry. It points out that service outages during major sporting events can lead to people going to other sites to place bets. Some attacks may therefore be down to unscrupulous competitors seeking to steal business.
Anthony Khamsei CEO of Gold Security says, "E-commerce events are busy times. With online gambling sites in particular, it’s like experiencing Black Friday -- several times a year. A half-second delay renders a site unusable, unlike shopping where the tolerance for imperceptible delays may not make or break a sale". Online gaming sites also have predictable rush hours during the weekend or major sporting events, they become easy targets for these DDoS attacks.
You can see the full infographic below or read more on the Gold Security blog.

Image Credit: EDHAR / Shutterstock
-

New archiving solution helps businesses stay compliant
Publié: septembre 23, 2015, 3:17pm CEST par Ian Barker

Companies are increasingly required to retain, quickly search and produce, as well as supervise electronic communications to meet regulatory compliance and e-discovery obligations.
To help businesses deliver on these requirements, hosted archiving specialist Smarsh -- not a villainous organization from a Bond film, honest -- is launching an enhanced version of its cloud-based Web Archiving solution.
The latest version introduces an enhanced supervision workflow that enables organizations to easily monitor and track changes in content, as well as document reviews of archived web pages. This is combined with a new user interface designed for efficiency.
"With the latest version of Web Archiving, we've simplified and strengthened the review of website content for customers who need to regularly monitor and produce it for regulatory examinations, audits or litigation", says Stephen Marsh, CEO and founder of Smarsh. "Web Archiving is an important offering of ours that is growing at 90 percent year-over-year. More companies recognize that archiving web content -- alongside email, social media, instant messaging, text messaging and video -- is a critical component of a comprehensive information governance strategy".
The enhanced supervision workflow allows users to easily document content status, flag content for further review or as a violation, and add notes. Statuses and flags can be updated one at a time, or in bulk, and used as search criteria -- for example, a reviewer can search for pages annotated with a specific tag. In addition, an audit trail documents all review activities and actions taken, so customers have evidence of supervision.
The latest version of Web Archiving is available now and you can find more information on the Smarsh website.
Image Credit: Eugene Kouzmenok/Shutterstock
-

BlueData simplifies big data infrastructure deployments
Publié: septembre 23, 2015, 2:00pm CEST par Ian Barker

The complexity of the systems needed to handle it is often a major barrier to companies setting up big data projects.
A new release from big data platform BlueData aims to simplify things by offering a turnkey, purpose-built big data infrastructure solution for enterprises to accelerate their deployment times.
BlueData EPIC 2.0 uses Docker containers to simplify big data clusters, supports Apache Zeppelin notebooks and other new functionality for Apache Spark, and includes an enhanced App Store that provides one-click access to big data distributions and analytics tools.
It provides greater integration and support for new Spark innovations, including Apache Zeppelin for data exploration and visualization. By enabling self-service Spark clusters pre-integrated with web-based Zeppelin notebooks, EPIC can accelerate Spark data analysis and can be used by business analysts who may have less technical expertise than traditional data scientists. In addition, EPIC 2.0 introduces support for SparkR, Spark Streaming, MLlib and Spark Streaming-SQL. Enterprises can simplify and accelerate their deployment of Spark on-premises -- either with Hadoop or in standalone mode, independent of Hadoop.
"BlueData's mission has always been to provide customers with an 'easy button' for Big Data. EPIC 2.0 builds upon this mission and further extends our ability to offer Big-Data-as-a-Service in a multi-tenant, on-premises deployment model," says Kumar Sreekanti, CEO of BlueData. "Our software innovations continue to break new ground and shatter pre-conceived assumptions about deploying Big Data infrastructure and applications. With just a few mouse clicks, our customers can now deploy instant clusters for Hadoop, Spark, and other Big Data tools running on Docker containers".
BlueData will be featuring the new EPIC 2.0 release at the Strata + Hadoop Summit in New York next week. Alternatively you can find out more on the BlueData website.
Image Credit: Tashatuvango / Shutterstock
-

UK businesses warned of growing cyber risk
Publié: septembre 22, 2015, 5:54pm CEST par Ian Barker

We reported back in July on the UK government's plans to help small businesses boost their cyber security. Today enterprises across the country are being urged to protect themselves by taking up the government's Cyber Essentials scheme.
Whilst £1 in every £5 earned by UK businesses now comes from the Internet, cyber attacks are considered a serious threat. The latest figures reveal that 74 percent of small businesses and 90 percent of major businesses have had a cyber breach of some sort in the last year.
"Good cyber security underpins the entire digital economy -- we need it to keep our businesses, citizens and public services safe. The UK is a world leader in the use of digital technologies but we also need to be a world leader in cyber security," Minister for the Digital Economy, Ed Vaizey says. "Trust and confidence in UK online security is crucial for consumers, businesses and investors. We want to make the UK the safest place in the world to do business online and Cyber Essentials is a great and simple way firms can protect themselves".
Speaking at today's Financial Times Cyber Security Europe Summit, the minister revealed that more than 1,000 businesses have now adopted Cyber Essentials -- the government's leading scheme which protects businesses against the most common threats on the Internet. Intel Security is among the firms who have recently achieved Cyber Essentials certification.
The Minister also announced a new £500,000 fund to help universities and colleges develop innovative teaching and learning to provide the cyber security skills needed to protect the UK now and in the future.
Commenting on the speech, Wolfgang Kandek, CTO at security management specialist Qualys says, "It's up to us all to make it easier to keep IT systems secure, from end-users knowing not to fall for phishing attacks or malware, through to IT teams keeping systems up to date and therefore protected. When one pound out of every five is driven by Internet activities, all sites and applications should be made secure by design, rather than having security bolted on as an after-thought".
Further details of Cyber Essentials, including the scheme documents and an online tool to help businesses assess themselves, can be found on the scheme's website.
Image Credit: Niyazz / Shutterstock
-

Gamers lack confidence in developers' security safeguards
Publié: septembre 22, 2015, 5:03pm CEST par Ian Barker

Despite the number of high-profile data breaches over the last year, many businesses and consumers are still not taking appropriate measures to ensure proper security online. The games industry is no exception, with several major game companies having been hit by significant breaches.
A survey by gaming industry backend service PlayFab of more than 500 users who play video games for more than four hours per week, reveals that 83 percent of respondents believe game developers should be responsible for securing players' personal data. However fewer than 40 percent say they feel confident in current safeguards.
In addition, while 86 percent of participants expressed concern with protecting personal data on the internet, for nearly half of all respondents data security ranked as one of their lowest priorities when making game purchases.
"Data breaches continue to plague businesses across the globe, and the games industry is not immune to these attacks," says James Gwertzman, co-founder and CEO of PlayFab. "These survey results underscore both the opportunity for game developers to improve trust by focusing on security measures, and the importance that they do so to safeguard an audience that relies on them. PlayFab plays a role in this by giving developers a battle-tested, secure backend that makes it easier to protect players' private data".
Other findings include that 46 percent of respondents say they provide the bare minimum of personal data required, and 20 percent indicate they will sometimes give false information, when making game purchases.
Nearly 60 percent cite cost and game play experience as the first or second most important factors when selecting a game, with almost half ranking security as one of the least important factors.
When asked about the security of their game accounts and experiences, more than 80 percent ranked either personally identifiable or financial related information as the most important thing to protect. Most respondents had minimal experience with compromised data -- only 30 percent were aware of data breaches that had affected the games industry, and 85 percent hadn't experienced a game-related security breach. 71 percent say they hadn't ever discontinued use of a game due to security vulnerability concerns, further highlighting a lack of awareness of potential risks.
The majority of participants, 55 percent, either view desktop and laptop systems as safer than other platforms, or believe all platforms to be roughly equal in terms of security, indicating a disconnect from the real world security landscape.
You can see more details of the survey results in infographic format below.
Image Credit: BonD80/ Shutterstock
-

Simplifying analytics with a building block approach
Publié: septembre 22, 2015, 4:36pm CEST par Ian Barker

Data is the lifeblood of business, but getting the answers to key questions from it can be time consuming and costly as it needs specialist tools and expert analysis.
Analytics specialist Looker is trying to simplify the process of gaining insights from data with the release of a new product called Looker Blocks.
These are apps that form components of business logic, such as churn prediction or lifetime value metrics, which can be put together and customized to address data needs company-wide as well as any industry-specific requirements. By combining a few Looker Blocks businesses can start to access and analyze data faster and have the tools to address all of their data needs across the entire organization. Looker Blocks can be used to analyze the sales funnel, monitor customer health, conduct sophisticated web analytics, or optimize an online storefront -- essentially any analysis that a company might need.
"In today's competitive market, every business in every industry should be leveraging data to make informed decisions, but available tools offer either limited views of the data or require data experts to answer even simple questions," says Frank Bien, Looker CEO. "Now with Looker Blocks, Looker’s Data Platform is clearly the solution to company-wide analytics -- offering a way for analysts to centralize their business logic while also offering access and exploration to everyone".
Looker began four years ago and became successful with data analysts because of its ability to describe, transform, and interrelate data directly within analytic databases. It's since added visualization and analysis tools and begun offering self-service exploration for business teams. With Looker Blocks it has made public the best of these centralized metrics and has turned its data modeling layer into a full platform that can easily consolidate all analytics functions across an entire organization.
You can find out more about Looker Blocks and set up a free trial on the company's website.
Image Credit: Nenov Brothers Images / Shutterstock
-

Surveying the survey makers -- Capterra reveals the top 20 packages
Publié: septembre 22, 2015, 3:43pm CEST par Ian Barker

Many companies rely on the use of survey software to stay in touch with and get feedback from their customers.
But there are lots of options available for conducting surveys, so which are the most popular? Software finding service Capterra has produced an infographic revealing the top 20 survey tools.
SurveyMonkey tops the list with more than 2.3 million customers and 2.5 million users, followed by QuestionPro with fewer customers but a similar number of users. Third comes Qualtrics, all three of these solutions having well over a million users.
Not surprisingly SurveyMonkey has gathered more social media followers than any of the rest. However, some solutions from lower down the list have a stronger social media presence than some of the big players.
You can see the full breakdown of the top 20 in the infographic below.
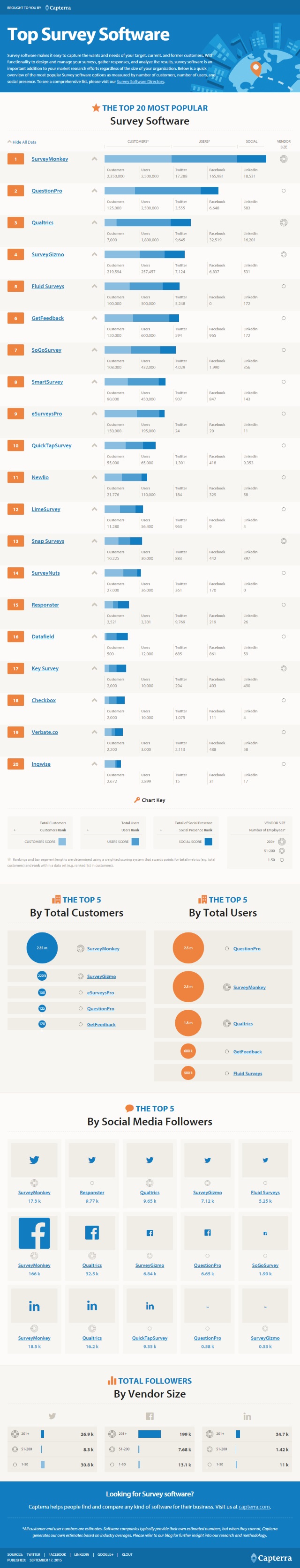
Photo Credit: tanewpix/Shutterstock
-

Your mother should know (how you use your computer at college)
Publié: septembre 22, 2015, 3:24pm CEST par Ian Barker

A new report by internet security specialist Webroot on the eve of National Cyber Security Awareness Month (NCSAM) asked over 500 mothers with kids leaving for college this year about the security of their offspring's computers.
Among the findings are that a worrying 24.45 percent of moms report that their child does not have a security solution installed on their laptop or computer. The reasons for this are interesting, with 37.4 percent not having thought about it, 34.15 percent because they said the machine came with security already, and 17.07 percent who don't believe security is necessary.
"Almost 40 percent of survey respondents said they just didn't think to install cybersecurity, and almost 20 percent don't think it's necessary. That's why NCSAM, as well as other initiatives to educate the general public about the dangers they face in cyberspace, are crucial," says Grayson Milbourne, security intelligence director at Webroot. "From sophisticated malware to spear phishing and ransomware, cybercrime continues to get more advanced. People who are not concerned or aware of internet risks make easy targets. As we're faced with an increasing number of high-profile hacks, individuals need to be more cautious than ever about the websites they visit, the URLs they follow from emails and social networks, and the apps they use".
Despite lack of awareness of security products, mothers are concerned about the internet safety of kids at college, with 11.93 percent being 'very worried' and 55.67 percent 'somewhat worried'. Their views on what is likely to have the biggest repercussions on their child’s identity are interesting too. 69.18 percent believe downloading free music and movies is the biggest risk, but only 30.82 percent say it’s visiting porn sites.
When it comes to the biggest risk students face stolen identity comes out on top, just ahead of stolen financial information. Hacked social networks and private photos being released rank third and fourth. But although ID theft is the biggest worry, 62 percent of mothers are 'somewhat' to 'not at all' confident that if their child's identity was stolen, they would know what actions to take.
You can find more information about NCSAM at staysafeonline.org.
Image Credit: Monkey Business Images / Shutterstock
-

BYOD adoption slowed by policy issues
Publié: septembre 22, 2015, 1:59pm CEST par Ian Barker

Most employees are interested in participating in BYOD, but many are put off by their employer's device and application management policies which are seen as too restrictive or invasive to privacy.
This is among the findings of a survey by data protection specialist Bitglass which also reveals that 67 percent of employees would participate in BYOD programs if their employers had the ability to protect corporate data but couldn’t view, alter or delete their personal information and applications.
The results show end users are challenging, and even rejecting, traditional mobile device management (MDM) and mobile application management (MAM) solutions, fearing their employer’s ability to access, alter or delete personal data stored on their mobile devices. Underscoring this, 57 percent of employees, and 38 percent of IT professionals are choosing not to participate in their company's BYOD program because they don't want their employer's IT department to have visibility into their personal data and applications.
"BYOD holds great promise for employee productivity and cost savings, but architectural challenges introduced by the first wave of solutions have inhibited adoption," says Nat Kausik, CEO, Bitglass. "Going forward, BYOD programs must comprehensively address privacy concerns while allowing users to maintain control over their personal data. Agentless, data-centric mobile security solutions solve these challenges and represent the next-generation of mobile security".
Despite lower-than-expected adoption, there remains a high interest in BYOD participation if the right conditions are met. Of IT professionals surveyed, 64 percent believe that their BYOD programs would be more successful without MDM hassles, such as installed agents and employee privacy challenges.
Other interesting findings are that 28 percent of organizations are doing nothing to protect corporate data on mobile devices. Also, 44 percent of millennials said they would participate in BYOD programs in which employers have the ability to wipe their personal mobile device to protect proprietary information. Perhaps most worrying is that 40 percent of security administrators have chosen not to participate in the same mobile policies that they're enforcing for their organization.
You can read more in the full report which is available on the Bitglass website.
Photo credit: Alessandro Colle/Shutterstock
-

Systems security in energy and utilities companies gives cause for concern
Publié: septembre 22, 2015, 12:14pm CEST par Ian Barker

Security ratings specialist BitSight Technologies has released a new report highlighting the differences in security performance across industries from August 2014 to August 2015.
Having analyzed security ratings of nearly 10,000 organizations across six sectors -- finance, federal government, retail, energy and utilities, healthcare and education. It reveals worrying performance trends in the critical energy and utilities sector, however, the federal government (despite recent headlines) is revealed as high performing and second only to finance.
BitSight Security Ratings range from 250 to 900, with higher ratings equating to better security performance. Industry ratings are calculated using a simple average of the BitSight Security Ratings of companies in that sector.
Over the past year, BitSight researchers noted a dip in the performance of energy and utility companies, with the average rating in this sector being 652. This is higher than the healthcare sector, which averages a 634 rating, but below the retail sector which averages 684 and has been grabbing the data breach headlines.
Analysis of federal government organizations shows that many are performing well when it comes to overall security performance. The average rating for the federal government sector was 688, while the average rating for finance, the top performing industry, was 716.
"There is no question that energy and utility systems are vulnerable and will be attacked. Organizations will never be able to protect against everything, but they need to continuously monitor their security posture in order to identify and mitigate issues before too much damage is done," says Stephen Boyer, co-founder and CTO of BitSight. "Benchmarking can also serve as a key indicator of security performance, allowing an organization to better understand their own posture, as well as that of the third parties with which they share their data. Given recent headlines that illustrate this security gap, we must look beyond our own companies and focus attention on those that access our information".
Other findings are that whilst most organizations have updated their servers to guard against Heartbleed, many haven't acted when it comes to POODLE and FREAK. The vulnerability rates for FREAK range from 30 percent in finance to 75 percent in education, meaning that at best, one in three finance organizations is vulnerable to FREAK. 79 percent of federal government entities analyzed were vulnerable to POODLE as were 90 percent of higher education institutions.
Finance has consistently been the top performing industry in BitSight's industry benchmark reports. In this report, the average rating was 716, in line with the 712 rating a year earlier. At the other end of the scale, education has consistently been the lowest performing industry, with an average rating of 554.
You can find out more in the full report which is available to download from BitSight's webpage.
Image Credit: Meryll / Shutterstock
-

Imation IronKey Workspace W500: Secure Windows To Go drive for enterprise users [Review]
Publié: septembre 21, 2015, 8:43pm CEST par Ian Barker

In the modern workplace there’s increasing demand for people to be able to work remotely or bring their own devices into the office. That presents a problem for IT departments who need to deliver secure access to corporate data and ensure that everyone is using approved applications.
One way of allowing employees and contractors to use their own PCs but still ensure they’re running the approved corporate software is the IronKey Workspace. It’s a bootable USB stick that can be loaded with a corporate Windows image including applications, security controls and access policies. It will work on any reasonably modern PC and on some Macs too.
It’s the same size as a normal USB memory stick but a lot heavier -- not for nothing does it have iron in its name -- obviously designed to survive the rough and tumble of a life on the road. Provided your system is set up to boot from a USB drive it simply starts up from the IronKey rather than its internal drive.
In Use
Effectively the IronKey bypasses the host PC’s native operating system, in fact it’s purposely isolated from it in order to provide additional security. It uses a Windows To Go licence so businesses can use an IronKey for every existing Windows licence with no need for additional licensing. Since it’s using a solid state drive and it’s not encumbered by software that’s installed on the PC it runs quickly even on older machines. Our test sample came with Windows 10 installed, though 8.1 versions are available too.
The first time you boot from the IronKey there’s a short ‘preparation’ session then you need to re-boot again and it runs a normal Windows set up. This lets you select the language and set up Wi-Fi, then one more boot and you have the choice of using Azure AD or a domain to connect to a company network and you’re ready to go.

We tested the IronKey on a Lenovo laptop and there was little difference between the performance whether running from it or from the internal drive. It does feel a little odd to be using the machine without the noise of the hard drive whirring away though.
Once up and running you can still access most of the laptop’s features like the DVD drive and Bluetooth. The IronKey did a pretty good job of detecting our machine’s hardware, though we did have to tweak the display settings to get the right resolution and it couldn’t cope with the scroll part at the side of the trackpad, but neither of these are major issues.
The PC’s own hard drive is hidden from Windows when you’re running from the IronKey and on our 32GB version there’s around 20GB of space available on the device itself to allow you to store files and install programs. Higher capacity versions are available. It comes with the standard range of Windows software, Windows Mail, Media Player, Windows Defender, etc installed. In use it’s like any other desktop environment so you can access cloud based apps and services via a web browser.
Security
The main reason for using something like this is to secure corporate information and provide a barrier between personal and work use of the same machine. When it’s running the IronKey’s LED is green and, as we’ve already pointed out, you can’t access the PC’s hard drive. Plug the device in while the PC is running its own OS and the LED turns red to show that the device is encrypted, it’s the IronKey that’s now hidden from Windows Explorer.
It has it’s own control panel that lets you set the device password and there’s the option to reset or self-destruct the device if it falls into the wrong hands. You can also set a custom 'if found...' message to display on the lock screen.
It’s hardware encrypted to keep its contents safe. Different versions of the IronKey are available with varying levels of encryption, the W500 tested here uses hardware encryption but there’s also a W700 which provides stronger encryption and access to a Federal Information Processing Standard (FIPS 140-1) validated workspace, plus there are W200 and W300 versions with BitLocker protection. The company says that the cryptographic chip keys never leave the device and that it’s physically and logically impenetrable.
For IT managers the IronKey offers control over the ability to run business apps and the ability to remotely disable the device if need be.
Conclusion
The IronKey is aimed at IT departments who need to allow employees to telecommute, implement a BYOD policy, or give contractors access to systems. Because it will work on pretty much any PC that has the ability to boot from USB it’s also a good way of extending the life of older hardware, though performance is better if you have USB 3.0 capability.
It’s easy to use, and it offers impressive security features and the ability to keep itself separate from the host PC’s storage. It isn’t cheap at £166 for the 32GB version but then again it’s a lot less than buying a laptop.
More information is available on the IronKey website.
Pros
- Solidly made
- High level of security
- Easy to use
Cons
- Hardware detection
- Not cheap
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Prelert improves insight into problems and threats
Publié: septembre 21, 2015, 3:29pm CEST par Ian Barker

Finding anomalies in data sets is an effective way of identifying performance issues or indicators of compromise before they impact a business.
Being able to link those anomalies together by identifying common traits among them would be even more effective and that's what a new Anomaly Detective tool from behavioral analytics specialist Prelert does.
"IT security and operations teams are drowning in log data that, if analyzed, could tell the story of most performance issues or security threats their organization faces. However, there’s no way a person can piece that story together on their own, which is why intruders go undetected for months and performance issues can persist indefinitely," says Mark Jaffe, CEO of Prelert. "With our machine learning capabilities, Prelert enables organizations to pinpoint issues that really matter. And with significant enhancements in this new version, teams can now see how those issues relate to one another, making it even easier to detect advanced threat activity or discover the root cause of operational issues".
Anomaly Detective V4 introduces a new feature called Insights that helps tell the story behind an organization's data. It identifies time-sequenced groups of anomalies linked by one or more common entities. By using machine learning to automate data analysis, Prelert can identify unusual or suspicious behaviors and the entities -- such as users, IP addresses and domains -- that influence them. Users can then access a list of other Insights that share a common influence, helping to make certain patterns of attack stand out as being more critical than others.
Key features include pre-configured Insight definitions to enable the system to automate Insight creation for activities including cyber kill chain progressions. It also delivers the ability for analysts to create Insights based on their own environmental factors and then save, label, comment and re-use them for future detection and investigation. An Anomaly Timeline shows the temporal relationship of anomalies included in any given Insight.
For more information about Anomaly Detective or to start a free trial you can visit the Prelert website.
Photo Credit: ollyy/Shutterstock
-

Inateck USB hub and Ethernet adapter improves ultrabooks' usability [Review]
Publié: septembre 21, 2015, 2:01pm CEST par Ian Barker

More and more devices now either connect through, or are powered by, USB connections which means you can easily find yourself running out of ports. This is especially true of the latest slimline ultrabook type systems.
Adding a USB hub is an easy way of expanding your number of ports and these latest offerings from Inateck give you a choice of solutions as well as a handy way of accessing wired networks.
Both versions -- the HB4102 and the HB4103 -- share the same size aluminium body which gives them a smart look with a nice solid feel whilst remaining light. Both support the latest USB 3.0 standard for 5 Gbps transfers -- that’s around ten times faster than USB 2.0 for those who are interested in these things. It is of course backwards compatible with earlier kit.
The HB4102 has four USB ports, three on top and one on the end panel, and connects via a standard USB socket. The HB4103 offers three USB ports on top as before, but the end panel now carries an Ethernet connection. Both are also available in ‘C’ versions to connect via a USB Type-C port, as found on the new MacBook for example, rather than standard USB.

They’re powered solely by USB so there’s no additional mains adapter required. The hardwired connection cables are quite short though -- about 30cm -- which means they’re better suited to use with laptop than desktop systems. There’s a white LED on top to indicate that the hub is active though this is a bit hard to see against the aluminium body.
The Inateck HB4102 is a nicely made USB hub, but it’s the HB4103 that’s likely to have more appeal to business users because of that Ethernet port. It’s not there to allow you to connect a NAS box or network printer, it acts as a gigabit Ethernet adaptor so you can use it to connect a PC to a router or to an office network.
Extra LEDs on this model show network activity. For devices like Chromebooks and MacBooks that don’t have a wired Ethernet port it’s a good option. The C version is compatible with Mac OS 10.6 without needing any drivers, settings can simply be handled from the Mac’s Network menu.
Combine HB4103 with a mini-USB adaptor and you can use the Ethernet port to connect to a wired network with a phone or tablet too. The advantage being that it will give you a faster connection than Wi-Fi for streaming or uploading large files, and allow you to connect if no Wi-Fi is available. It supports the 802.3az energy efficient Ethernet standard to reduce power consumption.
The HB4102 costs $11.99 on Amazon. The HB4103 costs $24.99 (or $28.99 for the HB4103C version). More information and technical specs can be found on the Inateck site.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Who you gonna call? Ghost Push Android virus infects 600,000 people a day
Publié: septembre 21, 2015, 12:15pm CEST par Ian Barker

If you frequent Android forums you'll probably have seen references to 'Monkey Test' and 'Time Service' as users report that it's hard to get rid of these apps.
Researchers at Cheetah Mobile's CM Security Research Lab have discovered that the source of these apps is a virus called 'Ghost Push'. This installs unwanted and annoying apps on the device and can't be removed easily even by doing a factory reset or using normal antivirus software.
Disguised as legitimate apps, the malware can spread itself widely via commercial SDKs or browser ads. Once a Ghost Push infection is active, it will automatically be able to root the device and download apps without the user's permission. This will slow down the system as well as consuming large amounts of data. CM Security says it's the most widespread and infectious virus it's seen to date. So far it's been affecting 600,000+ users per day.
The virus is mainly spread through Europe, Russia, the Middle East region, and southern China. So far 39 apps have been discovered that contain Ghost Push and it has affected 14,847 phone types and 3,658 brands.
The virus has so far not affected apps from the Google Play store so if your device is set to not download apps from third-party locations you should be safe.
For more information on the infection and how to remove it you can visit the Cheetah Mobile blog.
Photo Credit: Dmitrijs Bindemanis/Shutterstock
-

New solution helps avoid account lockouts
Publié: septembre 21, 2015, 11:13am CEST par Ian Barker

Being locked out of your account because you mistyped your password is not only frustrating, it takes up valuable IT staff time as it has to be treated as a genuine security threat and investigated before resetting.
Behavior analytics specialist Exabeam has produced a solution to the account lockout problem that uses machine learning to model lockout behavior and apply that logic and related rules to its latest release.
This also records how many times a user has been locked out in the past so companies can add that information to the user's behavior history.
"Exabeam Version 2.0 empowers companies to maintain strict security policies without relegating their security teams to futile, endless lockout investigations triggered by everyday user errors," says Nir Polak, Exabeam's CEO. "Separating true security risk from accidental lockouts is no longer a full-time job".
Other features of the latest Exabeam include user watchlists, allowing admins to create arbitrary lists of employees and contractors that will require special monitoring. For example, a customer might create a watchlist of all users whose systems had malware within the past month, to detect potential re-infection.
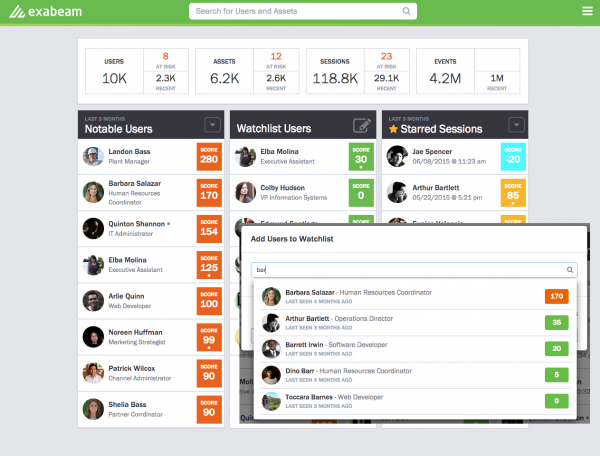
Security alert searches allows the entry of an alert from another security product and the ability to view a timeline of all users and activities connected to that alert. It can also use organizational information to automatically identify all machines -- laptops, smartphones, etc -- used by company executives, to enable special data monitoring rules as required.
Exabeam 2.0 will be on display at Splunk.conf15 in Las Vegas this week or you can find out more on the company's website.
Image Credit: Gunnar Pippel/Shutterstock
-

DDoS attacks are more dangerous than you think
Publié: septembre 18, 2015, 11:49am CEST par Ian Barker

We all know that DDoS attacks are capable of causing massive inconvenience, but according to a new survey they can have major financial and data loss implications too.
The study of over 5,000 companies by Kaspersky Lab finds that almost one in three DDoS attacks coincides with a network intrusion.
According to the research, 20 percent of businesses with 50 or more employees have suffered at least one DDoS attack. Furthermore, over a quarter of attacks lead to the loss of sensitive data, an unexpected and damaging consequence of a DDoS attack. Small businesses are most likely to lose data as a result of a DDoS attack -- 31 percent of SMBs reported data loss compared with 22 percent of larger enterprises.
There's a financial cost too. On average, a DDoS attack costs SMBs more than $50K in recovery bills, which is significantly more than the typical costs they face recovering from other types of attack. Larger enterprises spend a lot to recover from a third-party failure or cyber espionage attack, but a typical financial loss for enterprises from a DDoS attack is $417,000, below average compared to recovery from other types of attacks.
Most DDoS attacks only last for a few hours but in that time can cause complete disruption to a service. However, some attacks are even more damaging, nine percent causing a service to go dark for between two days and a week, and seven percent lasting for several weeks or more.
"Businesses have to re-evaluate their perception of a DDoS attack. The report clearly shows that the damage scope from such attacks goes far beyond the temporary downtime of a corporate website", says Evgeny Vigovsky, head of Kaspersky DDoS Protection at Kaspersky Lab. "Companies report total disruption to their operations, and in some cases -- loss of sensitive data. Still, many businesses feel that a mitigation strategy is too complex and expensive to implement. The solution to this is straightforward: vendors have to take technical challenges upon themselves, offering an easy to implement and use solution to clients. This is the approach that we have chosen for the Kaspersky DDoS Protection solution".
The full Corporate IT Security Risks Survey is available to download from the Kaspersky website.
Image Credit: sibgat / Shutterstock
-

Wanted: DDoS skills to fend off attacks
Publié: septembre 17, 2015, 4:48pm CEST par Ian Barker

DDoS attacks regularly make the news, but what are companies doing to help them fend off and guard against the threat?
Security company Incapsula has conducted some research to find out if companies are actively seeking candidates with DDoS mitigation skills.
By analyzing listings from the Indeed.com and Dice.com recruitment websites, it reveals a sustained increase in demand for professionals with DDoS mitigation experience across IT security, network engineering and operations, systems administration and DevOps, worldwide.
It finds that 85 percent of the listings seeking DDoS skills come from just eight counties with the US, China and the UK topping the list. The biggest demand is -- unsurprisingly -- for security professionals but demand for network engineers also showed a significant increase.
"Clearly, companies are looking to hire for DDoS mitigation skills. The growth in DDoS attacks makes it essential for every company to have a DDoS planning, prevention and mitigation strategy, and the staff to execute on that strategy," says Tim Matthews, vice president of marketing at Incapsula. "It can take months to hire a person with the right technical skills. We think finding people with good DDoS mitigation skills is especially hard, given that it crosses the domains of network and application layers, web infrastructure and applications, system administration, data center operations and DevOps. Also, DDoS attackers are skilled and nimble, and IT professionals need to be equally nimble and agile to stop new types of attacks".
You can read more about the research on the Incapsula blog.
Image Credit: Arcady / Shutterstock
-

Securing the Internet of Things [Q&A]
Publié: septembre 17, 2015, 3:58pm CEST par Ian Barker
The Internet of things is set to worm its way into many areas of our lives, but as our cars and domestic appliances become connected how can we be certain that they're secure? We've already seen issues with cars being hacked and do you really want to be installing security software on your fridge?
We spoke to Lev Lesokhin, Executive Vice President, Strategy and analytics, of software analysis and measurement specialist CAST to find out how developers of IoT products can keep them secure and retain consumer confidence.
BN: Many IoT devices are made by companies not traditionally involved in computing. Are they being caught out by lack of experience?
LL: Absolutely. It's a double whammy. Not only are these companies suddenly having to put together a software capability, where the market for software engineers is more and more demand-constrained, but they have to figure out how to manage software delivery. That's a long journey. Also, the traditional embedded software developers still haven’t caught up to the practices needed to develop internet-connected applications -- from a security, reliability and performance efficiency standpoint.
BN: Where in the product lifecycle does security need to be addressed?
LL: About 50 percent of security flaws are in the design and the architecture of an information system. Security needs to be addressed at the start of the design phase, making requirement tradeoffs as necessary. During code construction (i.e. development), security needs to be baked in that process all the way through. Security is then tested at the end of the development process. Security must be foundational -- it cannot be regarded as a mere 'bolt on'.
BN: Security is an ongoing process, how can companies deal with this and does it risk early obsolescence of devices?
LL: It may be counterintuitive, but it's actually the opposite. CAST Research Labs, in their latest research report (CRASH), found that security is highly correlated to software robustness. In fact, it may take a little bit more time upfront to build robust software, and it takes more management oversight, paying attention to their analytics about structural quality. But, as a result you have more secure and robust software -- which is actually more reliable and easier to maintain. So it will actually have a longer shelf life.
BN: Isn’t the answer to keep critical infrastructure devices isolated from the internet?
LL: You can have a solution to operate on secure subnets, but these will by definition be restricted to the other users of the same subnet. That may work for some business models, but for anyone that wants to access the worldwide market that’s on the internet, this won’t be a solution. As a result, embedded software components have to interact with internet-facing components in a safe way. This makes it much more difficult, because now the developers have to understand how these components will interact to ensure security, reliability and efficiency. This is a common problem in IT, but new in device software development.
BN: Won't IoT devices in the home be protected by being behind a firewalled router?
LL: The short answer is no. Some of the router security mechanisms can prevent novice hackers from entering home devices, but this is not failsafe. If we don't want an army of refrigerators creating DDoS attacks on critical infrastructure, we need to make sure the software onboard these devices is built with security in mind.
BN: Do device manufacturers need to be more open about why their devices are going online, what data they’re collecting and where it's being stored?
LL: Yes. The 'bad guys' will figure that out anyway. It's important for manufacturers to share this information with each other. It's also important for the consumer to know what information is being retained and/or broadcast by their devices. Manufacturers will also have to build in privacy options that can be invoked at the expense of additional functionality. This comes back to the first question about designing security in during the requirements phase of software development.
BN: What standards are in place which help businesses and developers meet specific goals for software quality?
LL: Software quality standards have existed for a long time. The traditional standard has been ISO 9126. Now that has been reworked into ISO 25010. The trouble with the ISO standards is they are vague and general. They specify the categories of 'what' should be measured, but they don’t specify 'how' to actually measure these criteria. There is also a standard being published by the Consortium for IT Software Quality (CISQ), the Object Management Group (OMG), and the Software Engineering Institute (SEI). It's aligned with ISO 25010, but gets into a great deal of detail as to 'how' these characteristics should be measured. Once this standard is rolled out, CISQ has made statements that they will provide a certification process in order to officially show that software follows the standard.
BN: In addition to measurement and analytics, what else needs to be a priority for manufacturers and developers?
LL: Keeping up with latest technologies, frameworks and coding practices. On the one hand, there are not enough experienced developers to go round, the flip side is that technical knowledge is among the quickest of all forms of learning to go stale. Managing this paradox is among the essentials of managing a development team. The best solution is to keep training all developers in the latest technology trends and practices. The best way of learning is on the job, and the best developers are the ones who feel they are being invested in.
Image credit: Gustavo Frazao / Shutterstock
-

AvailabilityGuard delivers predictive analytics for enterprise IT teams
Publié: septembre 17, 2015, 3:48pm CEST par Ian Barker

For IT teams to deliver reliable systems with high availability they need to be able to spot problems and potential problems early. These challenges are greater as systems move to the cloud and software-defined data centers.
Operations analytics specialist Continuity Software is launching the latest version of its AvailabilityGuard software, providing enterprise IT teams with advanced predictive analytics, risk detection, and outage prevention capabilities.
The software allows teams to identify and resolve hidden design and deployment flaws that may introduce downtime risks, single-points-of-failure and deviations from best practices across the entire infrastructure.
"The transition towards the software-defined datacenter delivers higher levels of agility and control to IT organizations, but at the same time presents new challenges," says Doron Pinhas, CTO of Continuity Software. "The risk of misconfiguration does not go away with automation. If a certain configuration deviates from best practices, automation only helps it spread faster and makes it more difficult to pinpoint. AvailabilityGuard is a safeguard against the diffusion of bad practices and risky configurations throughout the infrastructure".
AvailabilityGuard helps ensure systems are properly configured according to vendor best practices and internally-defined standards. It does this by performing daily verification of the entire IT landscape to identify single-points-of-failure and other configuration risks while reducing the time and effort associated with pre-rollout testing.
It can verify configuration changes before they affect the business, provide actionable recommendations for applying best practices and removing availability risks, as well as measuring performance indicators to establish safer and more agile best practices over time.
In addition it helps enterprises realize the benefits of the software-defined data center. It offers a blueprint for safer transition towards automation by verifying the existing environment to ensure a clean start, validating that automation scripts are programmed correctly and ensuring ongoing automated validation following the transition.
"Automating standard validation means you get things done right from day one, as opposed to learning how to get there after years of trial-and-error," adds Pinhas. "Best practices not only protect against risks to your environment, but also help you get the best utilization and performance from your technology and make systems easier to maintain and update".
The latest AvailabilityGuard is out today and you can find out more and get a free demo on the Continuity Software site.
Photo Credit: dotshock/Shutterstock
-

Why IT staff are unhappy at work
Publié: septembre 17, 2015, 12:17pm CEST par Ian Barker

If you work in IT it's generally the case that you're quite well paid and enjoy good career prospects. Yet according to a new survey you're probably also unhappy.
Workforce engagement specialist TinyPulse surveyed over 5,000 tech and IT workers and found that they are very, very unhappy. The top drivers of unhappiness were poor coworker relationships, little room for growth with their employer, and not enough praise for their work.
When asked to rate their happiness at work on a one to 10 scale, only 19 percent of IT workers gave a score of nine or 10, compared to 22 percent of other workers. Around half of non-IT workers say that their promotion and career path is clear compared to only 36 percent of IT staff.
They're similarly pessimistic when it comes to assessing their opportunities for professional growth and how well they believe their employer supports them in their interests and goals. When asked how valued they felt at work only 17 percent of IT workers gave a nine or 10 score compared to 22 percent of non-IT staff.
When asked whether their supervisor had given them any recognition for their work in the past two weeks, 69 percent of IT workers answered yes compared to 75 percent of non-IT staff. There's also a bigger mismatch between personal values and the organization’s values with only 34 percent of IT staff rating the match in values between nine and 10 compared to 45 percent of non-IT workers.
Relationships with co-workers are poorer in the tech sector too, with only 47 percent of IT staff rating these a nine 0r 10 compared with 56 percent of non-IT.
The report concludes, "These employees directly impact others with their work, so disengagement and unhappiness here has ripple effects throughout other industries. To drive the creativity and productivity we need, leaders must make it a priority to combat IT employees’ workplace dissatisfaction".
You can find the more in the full report available on the TinyPulse website.
Image Credit: Sergey Nivens / Shutterstock
-

Mobile messaging helps businesses connect with customers
Publié: septembre 16, 2015, 3:53pm CEST par Ian Barker

A new infographic from enterprise mobile specialist OpenMarket looks at how companies are using mobile messaging to improve marketing and awareness, and make a positive impact on customer experience.
Findings include that mobile messaging is the most frequently used communication channel on the planet and that 90 percent of texts are read within the first three minutes of opening. The millennial age group is 40 times more likely to react and respond to a business via text.
When used for marketing, click-through rates for SMS are at nearly 20 percent as against email at a mere two percent. Read rates are higher too with 98 percent for SMS, versus email at 20 percent. Even for surveys, mobile response rates are 20 percent, which is twice as high as phone polls and five times higher than for online questionnaires.
A company's willingness to use mobile messaging also drives people's perceptions of it. 77 percent of millennials have a positive view of a company they can text. When using SMS, businesses have experienced a 20 percent decrease in customer call volume and a 25 percent increase in customer satisfaction. It also shows that 64 percent of consumers prefer texting over voice communication for customer service.
You can see more detail in the full infographic below.

Image Credit: Bloomua / Shutterstock
-

Permission based publishing lets users keep control of content
Publié: septembre 16, 2015, 3:14pm CEST par Ian Barker

Once content has been published online it's almost impossible to retain control and know who sees it or where it's distributed.
A new solution from StoryCloud seeks to offer online content publishers control over how their material is consumed. Called Share By it provides user-controlled file transferring for media, videos, music and various file formats with easy to interpret analytics, integrated social networking and ecommerce.
By using permission-based technology that is tightly integrated with social networking, analytics and ecommerce, Share By allows content providers to easily determine who sees their content, when, and from what location. Other permissions include duration, view or download limits and scheduling time periods for sharing and the devices that are permitted. Once content providers upload content to StoryCloud and determine permissions, they receive a unique URL which can be shared with any online audience, including Facebook and Twitter.
Analytics graphically present how content is accessed and consumed, allowing owners to build an audience, engage users and monetize their offerings.
"StoryCloud is founded on the principle that content belongs to the content creator and publisher. We're providing users and publishers the ability to determine who sees their content, when, where, for how long and on any given device," says Ken Kalb, CEO of StoryCloud. "We then help them fully monetize with pay per view, subscription and advertising models".
Share By is now available in beta and you can find out more by visiting the StoryCloud website.
Image Credit: Toria / Shutterstock
-

IT decision makers worry about the security of containerized applications
Publié: septembre 16, 2015, 1:10pm CEST par Ian Barker

Containerization makes deploying applications faster and more cost-effective than using traditional means. As a result container technologies have become more popular with Docker rising rapidly in popularity and market share.
But a new survey from enterprise security specialist Twistlock shows that 91 percent of respondents said they are concerned about container security.
According to the study 86 percent of IT decision makers say their companies already deploy containers, or they plan to do so within a year. Of these, 35 percent say containers are already broadly deployed across their networks.
Security is a major concern though with half of respondents saying they are very or extremely concerned. Of those who don't use containers in their data center, 81 percent say the addition of in-container security would prompt them to adopt a container strategy.
The three container security features that respondents say they would most-benefit from are, the ability to ensure that all containers have a consistent security model from development through to production (83 percent), preventing development mistakes from reaching production (82 percent) and detecting vulnerabilities in containers (80 percent).
"This survey shows what Twistlock has known all along -- that even though containers are accessible and easy to deploy, many companies do not have a good grasp of how to manage container security. This remains a major adoption hurdle that is keeping data centers from migrating to containers completely," says Ben Bernstein, CEO of Twistlock.
You can see more of the survey results in the infographic below.
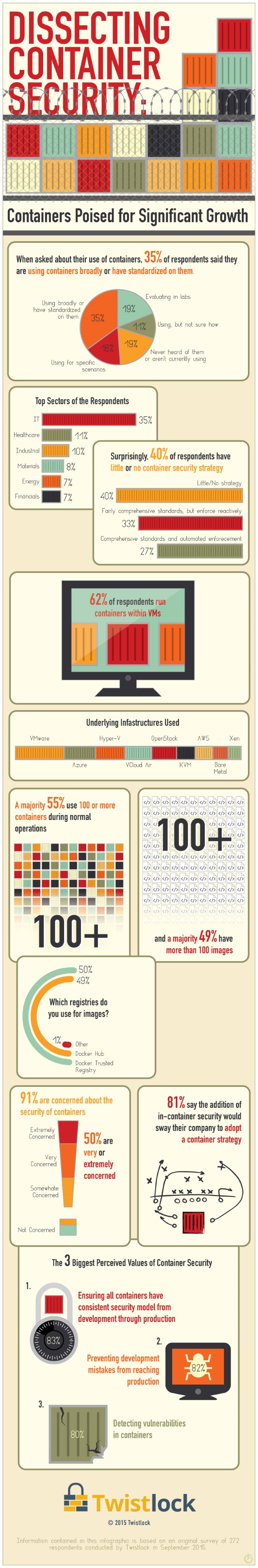
Image Credit: Sergey Nivens / Shutterstock
-

Why companies need to embrace mobile marketing
Publié: septembre 16, 2015, 11:53am CEST par Ian Barker

With mobile overtaking desktop as the main way of accessing the internet, brands have new opportunities to reach their customers on their preferred platform.
Mobile technology company Zumobi has produced an infographic looking at the opportunities for brands to harness the power of mobile content marketing strategies.
The headline figure is that mobile use has increased by 76 percent year-on-year since 2013. It also reveals that 71 percent of consumers are open to receiving personalized promotions and offers from their preferred brands and retailers. This gives companies the opportunity to unite mobile with content marketing and open up a new phase in the way they engage with their customers.
Other findings include that Americans spend almost three hours per day on their mobile devices and that 61 percent of millennials prefer to use mobile over desktop. The biggest growth in mobile use has come in lifestyle and shopping -- 174 percent up between 2013 and 2014, followed by utilities and productivity up by 121 percent and messaging and social up 103 percent.
"With the mobile landscape so influential and content marketing proven to be the most effective way to reach consumers, we’re right at the ideal intersection between the two -- offering an untapped opportunity for marketers that's personalized and data driven," says Marla Schimke, VP of Marketing at Zumobi. "As the infographic presents, seven out of every eight minutes of mobile use is spent in app. If a brand is not leveraging its mobile potential through content marketing initiatives, they’re missing a massive engagement opportunity".
You can see more, including how brands are investing in mobile content, in the the full infographic below.
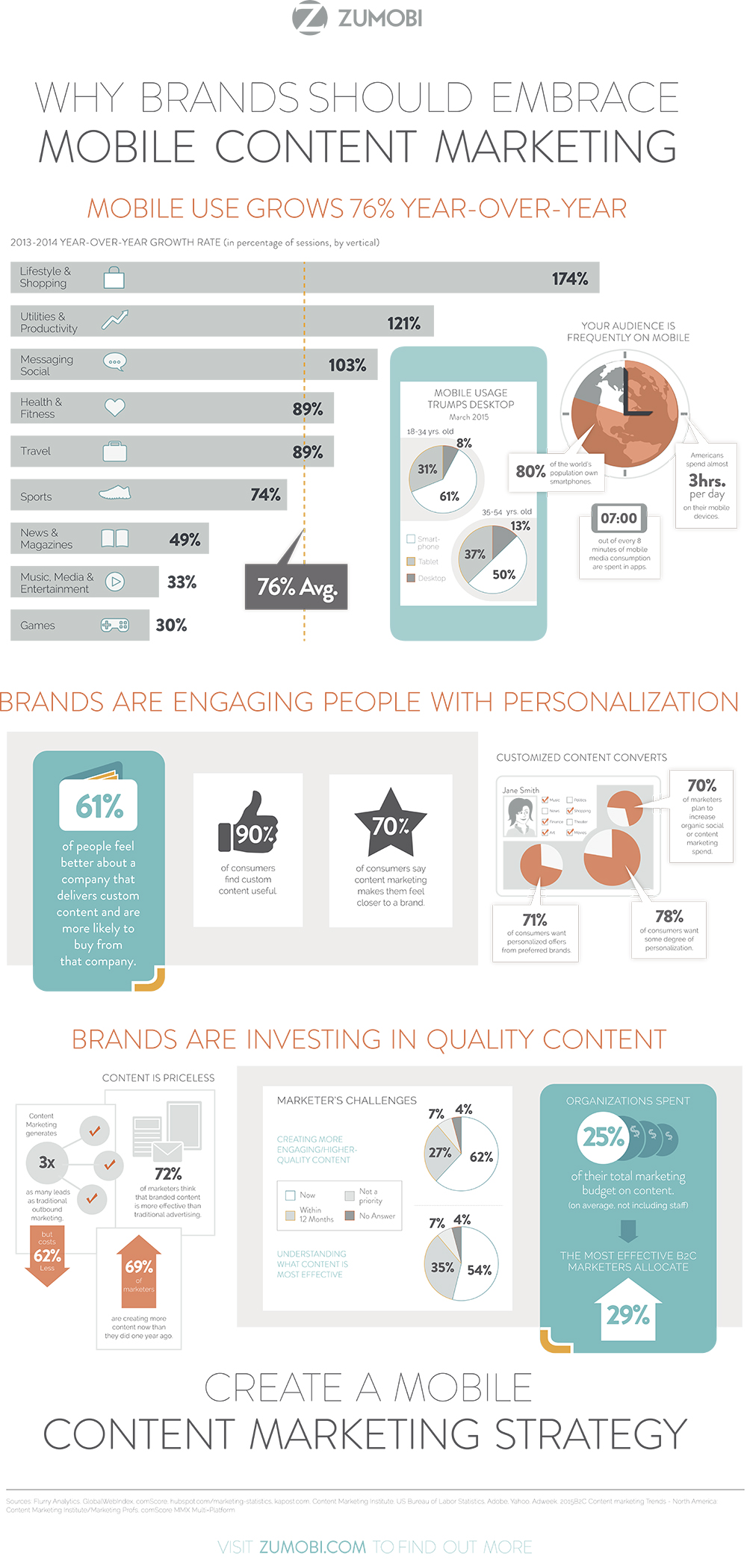
Image Credit: Slavoljub Pantelic / Shutterstock
-

More than 21 million new threats detected in second quarter of 2015
Publié: septembre 15, 2015, 4:43pm CEST par Ian Barker

PandaLabs, the malware research arm of Panda Security, has published its latest quarterly report showing that malware creation levels have broken new records.
It reveals that in the second quarter of 2015 there were an average of 230,000 new malware samples detected each day, which means a total of 21 million new types in these three months. Compared to the same period last year, where there were 160,000 registered samples, this is an increase of 43 percent.
The majority of these samples are variants of known malware, mutated by cybercriminals to try and stop the antivirus laboratories from detecting the infections. Trojans continue to be the most common source of infection, with 76.25 percent of users infected by this type of malware. This quarter also saw the proliferation of PUPs (Potentially Unwanted Programs) which accounted for 14.39 percent of infections, placed just behind Trojans.
Cryptolocker remains a major threat as cybercriminals have begun to reuse an old technique to infect users. This involves using macros in Office documents, especially Word. To complete the attack, the criminals included a blurred image which could only been seen if the user activated the macros. Once the user does this, they are infected with Cryptolocker.
"Cyber hackers are looking at businesses more and more as it is relatively easy for them to steal information," says Luis Corrons, Technical Director of PandaLabs. "Sometimes it's as simple as introducing a variant of Cryptolocker in a file that is sent to an employee and, once it’s opened, the security of the entire company is at risk".
Looked at geographically, the areas with the highest rate of infection were Asia and Latin America, which placed above the average of rate of infection (33.21 percent). China was the country with the highest rate of infection on 47.53 percent, followed by Turkey or 43.11 percent and Peru on 41.97 percent.
At the other end of the scale, Europe and Japan were the areas with the lowest rates of infection. Sweden on 21.57 percent, Norway on 22.22 percent, and Japan on 23.57 percent are the countries with the lowest infection rates worldwide, followed by Switzerland on 24.41 percent and the UK coming fifth on 25.17 percent.
Despite Europe's overall strong record, some European countries recorded infection rates above the global average. These include Spain on 36.37 percent, Poland on 38.48 percent, and Slovenia on 38.05 percent. In Latin America there were rates of 38.21 percent in Brazil and 37.86 percent in Colombia.
More detail is available in the full report which is available on the Panda website.
Image Credit: Sergey Nivens/Shutterstock
-

IntellaSphere offers SMBs free online marketing tools
Publié: septembre 15, 2015, 3:17pm CEST par Ian Barker

When it comes to marketing, smaller businesses often lose out to their larger competition because they can't afford sophisticated software tools.
Now digital marketing specialist IntellaSphere is looking to give small companies the edge with the launch of its new Freemium service, providing SMBs with access to a free suite of tools they can use to instantly start selling online, as well as find and expand online customers through targeted marketing.
Tools on offer include social media publishing to create and post content across popular social networks such as Twitter, Facebook, YouTube, LinkedIn and Google+, as well as blogs like WordPress, Blogger and Tumblr.
Users can create and distribute promotional coupons including percentage discounts, cash savings, buy 1 get 1 free, or buy 1 get 1 half price offers. IntellaSphere provides the ability to limit the number of coupon activations and can display the number of coupons still available. Offers can be shareable or limited to just one per customer.
There's a content planner and scheduler for easy planning, plus streamlined and automatic publishing of weekly or monthly marketing content. Campaigns and customer engagement can be tracked with notifications of engagements, coupon activations and company mentions associated with the business. Posts and offers are tracked and measured too and their effectiveness is reported, so businesses can identify the most effective and engaging content, the key social influencers engaging with company, and other analytics.
"IntellaSphere disrupts the market by leveling the playing field with our powerful, yet extremely low priced, all-in-one digital marketing platform for SMBs. With IntellaSphere you don't need to have dedicated marketing staff to effectively market your business and increase sales. Most large companies have sizable marketing teams and sophisticated marketing tools to increase prospects and customers. Now SMBs have access to an equally powerful, but much easier to use and affordable marketing solution," says IntellaSphere's CEO Bruce Worrall.
As well as its Freemium Service IntellaSphere offers three monthly business subscription plans ranging from $29 to $149 per month, and a $299 subscription plan for marketing agencies. For more information and to start a free trial you can visit the company's website.
Image Credit: arka38 / Shutterstock
-

SecureKey brings convenient, secure access to US online services
Publié: septembre 15, 2015, 1:31pm CEST par Ian Barker

As we rely more on using online services to control various aspects of our lives we end up with a host of login credentials that can be difficult to manage.
Toronto based identity specialist SecureKey is today launching its SecureKey Concierge service in the US. This allows consumers to choose a trusted credential they already have and use frequently to login to other sites, thereby eliminating the need for additional usernames and passwords.
The solution is being offered to online service providers in state and local government, healthcare, financial services, and other markets where consumer privacy, high assurance authentication and ID verification are required.
"As online fraud and security breaches increase, SecureKey Concierge is driving a new era of convenience, security and privacy, translating into peace of mind for consumers using the web for critical applications and services," says Charles Walton, CEO of SecureKey. "The US launch is part of SecureKey's commitment to expanding our ecosystem of trusted partnerships and online service provider communities to dramatically simplify the account opening process for increased customer acquisition, while facilitating greater efficiency in credential management".
SecureKey Concierge enables consumers to use their choice of credential from an Identity Partner in the SecureKey Concierge network to log into online service provider sites. For enhanced privacy, the service includes a privacy guard that ensures consumer online activity is not visible to the Identity Partners, and personal attributes, such as name, address and date of birth, are never shared without explicit consent. There are tiered levels of assurance to support a range of credentials from social IDs to high assurance, smart card-based digital IDs.
It also offers an Identity Verification Service, this allows online service providers to verify user identity data, such as social security number, date of birth, age, zip code and so on bound to a user's credential. A 'tokenization' process maintains the privacy of the consumer’s data, and consumer consent is always required at the start of the identity verification process.
You can find out more about the SecureKey Concierge service in the US on the company's website.
Image Credit: Gunnar Pippel/Shutterstock
-

Popular travel apps have inadequate security
Publié: septembre 15, 2015, 12:51pm CEST par Ian Barker

Travel apps have evolved to make life easier for users, with regular updates and enhancements to features and usability. But new research highlights inadequate security in the 10 most popular mobile apps for travel on both Android and iOS devices.
The study by self-defending app specialist Bluebox looked at more than a dozen security parameters in the 10 most popular travel apps on the App Annie iOS Top App Charts and Google Play Top App Charts and revealed that critical flaws were present in all of the apps examined.
Flaws found include a lack of data security with only one in ten Android apps and none of the ten iOS apps examined encrypting the data stored, leaving sensitive information easily obtainable by attackers. Additionally, only two of the ten Android apps and one of the ten iOS apps used certificate pinning -- a technology for securing app data in transit and preventing 'man in the middle' attacks.
The study also uncovered the potential for app manipulation. Four out of ten Android apps and six out of ten iOS apps contained code that could enable admin functionality not intended for a normal user to access, and which would grant special privileges for the end-user if enabled. None of the apps incorporated anti-tampering measures either, so attackers could activate restricted functionality and take full control of apps to alter them for their own gain or to launch attacks on other apps.
On average, the app vendor is responsible for creating only 30 percent of the code, while the remaining 70 percent was made up of third-party components. As OpenSSL bugs like Heartbleed have demonstrated, third party libraries present a huge potential attack surface and expose security blind spots for developers.
"All of the apps we reviewed could be modified and changed to act in ways other than what the developers intended, putting sensitive information at risk regardless of device," says Andrew Blaich, lead security analyst at Bluebox Security. "Data must be protected at the application level and security should be integrated into the development process. Without it, users -- enterprise employees and consumers alike -- could suffer damaging loss of important and personal information".
More information on the results is available on the Bluebox website.
Photo Credit: William Perugini / Shutterstock
-

The spooks' guide to choosing a strong password
Publié: septembre 11, 2015, 5:32pm CEST par Ian Barker

Britain's electronic intelligence agency GCHQ has released new guidelines to help individuals and businesses choose strong passwords.
In a report issued in conjunction with the Centre for the Protection of National Infrastructure it suggests that the use of complex passwords is no longer required.
It advises using password managers but warns that, "...like any piece of security software, they are not impregnable and are an attractive target for attackers". It also recommends that businesses make life easier for their users by only applying passwords when they're really necessary and only insisting they're changed when there's evidence of compromise. It suggests using alternatives like hardware tokens or RFID badges too.
The report warns of the limitations of common user techniques such as substituting letters for numbers, and of machine generated passwords -- principally that they're hard to remember. Instead it recommends using schemes that are more memorable such as combining four random dictionary words or adopting consonant-vowel-consonant constructions.
It also advises some common sense measures such as always changing default passwords on any new devices and never letting users share passwords. It suggests that administrator and remote user accounts be prioritized for stronger passwords.
Whilst much of the advice given is sensible, users may be forgiven for taking a negative view of security advice offered by GCHQ. The organization has in the past pushed for the introduction of back doors in software and a weakening of encryption. Cynical commenters on the Guardian website suggest that the advice is to ensure passwords are compatible with the agency's latest cracking algorithm.
At the risk of adding your IP address to a secret government database, the full guide is available to download from the gov.uk site.
Image Credit: Richard Peterson / Shutterstock
-

Development of as-a-service presents opportunities and threats for business
Publié: septembre 11, 2015, 1:04pm CEST par Ian Barker

The introduction of as-a-service delivery models is affecting the way companies operate as they increasingly buy services to supplement their existing systems.
A new report by consultancy firm Accenture looks at how technologies such as cloud, automation, analytics, artificial intelligence and mobility have forever changed the way companies receive and deliver significant business value.
Among the findings are that 53 percent of senior vice presidents and above see as-a-service (AaS) being critical to their businesses. Yet despite this seven out of 10 enterprises don’t expect their core systems to be delivered on an as-a-service basis for five years. Interestingly small and medium businesses and Asia Pacific buyers are more likely to see AaS as critical.
"Every day our clients tell us they are under pressure to find new ways to create business value quickly," says Michael Corcoran Senior Managing Director of Accenture Operations, Growth & Strategy. "The marketplace has moved towards a new era of service delivery where applications, infrastructure and business processes are brought together and delivered 'As-a-Service'".
In order to achieve a successful transition to AaS the report says that businesses must be prepared to encounter resistance and manage change. They also need to learn to buy in new ways and focus on the leadership and talent needed to establish expertise across the business.
They need to blend analytics and automation strategies to deliver intelligent automation too. Currently 70 percent of companies have definitive plans for, or are considering, investments in analytics tools and skills. By contrast, only 40 percent are similarly advanced with their plans for robotic process automation.
Other recommendations include starting with a small AaS projetc before scaling it up to the rest of the business, and building a relationship with service providers and consultants to drive innovation.
You can find more information and the full report on the Accenture website and there's a summary of the findings in infographic form below.
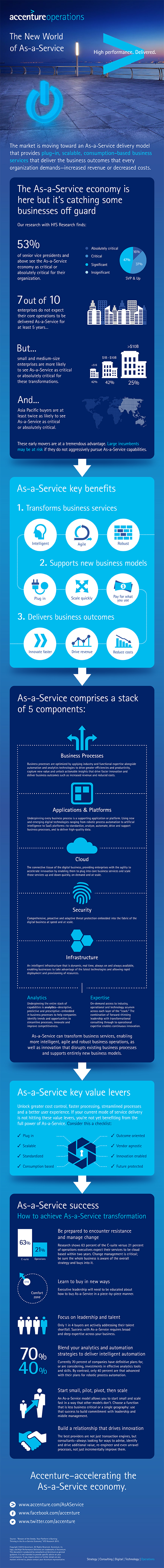
Image Credit: wavebreakmedia / Shutterstock
-

Microsoft confirms rollout of Office 2016 starts on September 22
Publié: septembre 10, 2015, 5:53pm CEST par Ian Barker

Preview versions of Office 2016 have been available since March but Microsoft confirmed today the news leaked a couple of weeks ago that the official rollout of the product will begin later this month.
Writing on the Office blog Julia White, general manager of Office 365 Technical Product Management says, "You may have heard the rumors, but today I'm happy to confirm that Office 2016 will be broadly available starting on September 22nd. If you have a volume licensing agreement in place, you can download Office 2016 from the Volume Licensing Service Center starting October 1st".
The update model is improved with a Current Branch for Business option, allowing enterprises who don't want to take updates every month to have just three cumulative updates per year. This is consistent with the approach followed for Windows 10.
Microsoft has also addressed a number of business requests in Office 365 ProPlus. These include deployment support for Background Intelligent Transfer Service (BITS) to help control network traffic when deploying updates, and new reports on Office activation and usage available in the Office 365 admin portal.
The company has reiterated the pledge it made in March to ensure compatibility with existing Office customizations by not making changes to the extensibility model for macros or add-ins.
Guidance for admins on updating from Office 365 ProPlus to the 2016 version is available on TechNet. In addition Microsoft will be running a Cloud Roadshow in November with free two-day training sessions in 12 cities around the world covering topics spanning Office, Azure and Windows.
-

IBM acquisition strengthens its place in the API economy
Publié: septembre 10, 2015, 5:00pm CEST par Ian Barker

The growth of mobile, web applications and the Internet of things has meant more use of APIs which is changing the way businesses operate and communicate. IBM forecasts that APIs will represent a $2.2 trillion opportunity by 2018.
One of the fastest growing development frameworks to support this new 'API economy' is Node.js and to help unite this developer community with enterprise clients, IBM has announced today the acquisition of StrongLoop, a leading provider of enterprise Node.js capabilities.
"Enterprises are focused on digital transformation to reach new channels, tap new business models, and personalize their engagement with clients," says Marie Wieck, general manager, Middleware, at IBM Systems. "APIs are a critical ingredient. By bringing together StrongLoop’s Node.js capabilities to rapidly create APIs with IBM's leadership in Java and API Management on our cloud platform, we are unlocking the innovation potential of two vibrant development communities".
This acquisition means Node.js developers now have a richer, operating environment on IBM Bluemix, big blue's platform-as-a-service offering. JavaScript ranked as the number one language for discussion and usage followed closely by Java in the RedMonk Programming Language Rankings. Java remains the leading language for web applications and transaction systems. Combining StrongLoop's tools and services with IBM's WebSphere and Java capabilities, IBM will help clients bridge Java and Node.js development platforms, which will enable them to extract greater value from their application investments.
"With this acquisition, the industry benefits from Node.js' formal entry into the mainstream enterprise," says Juan Carlos Soto, Chief Executive Officer of StrongLoop. "As leaders in the Node.js open community, we plan to further advance open, community-driven innovation coupled with global, enterprise class software and services offerings to grow client value in the API economy".
More information on IBM's acquistion of StrongLoop is available on the company's website.
Image Credit: Tomasz Bidermann/Shutterstock
-

How sales teams are being let down by their data
Publié: septembre 10, 2015, 3:28pm CEST par Ian Barker

Modern sales teams are more than ever reliant on data to help them identify opportunities and analyze performance. But can they really be confident in the accuracy of their data and are they using it effectively?
Business management platform Domo has conducted a survey of more than 400 sales leaders to find out how data impacts them in the real world.
Among the findings are that more than half of sales leaders aren't able to access their data in real-time, despite nine out of 10 saying that real-time access is important. 60 percent say they have to wait for someone else to access their data for them and 38 percent say they can't get hold of the data they need.
Analysis is a problem too, 71 percent report struggling with slow data analysis and nearly 40 percent don't know what to do with their data once they finally receive it. A further 53 percent say they feel overwhelmed by the volume of data they receive. They also struggle with the systems they have to use, 38 percent have to use more than four systems in order to track their goals and priorities.
"Sales organizations have so much data, but have no way to get real value from it all," says Domo President Chris Harrington. "Data sits in too many places -- CRM applications, compensation systems, marketing automation systems -- and in too many formats for it to be effectively leveraged. The data is there, they just need to be equipped to leverage it".
In addition half of sales leaders worry that their data isn't accurate and spend many hours -- and sometimes whole work days -- trying to determine how best to use it and developing reports. 65 percent say that it takes too long to gain insights from their data.
When asked to rate their relationship with their sales data only two percent of respondents gave it an A- or better, 83 percent a B- or lower and 38 percent a C- score.
The full report is available to download from the Domo website.
Image Credit: Andrey Popov / Shutterstock
-

Spanning expands its Salesforce backup capability
Publié: septembre 9, 2015, 4:39pm CEST par Ian Barker

Backup specialist Spanning will be using next week's Dreamforce '15 event to showcase the latest developments in its Saleforce backup solution.
Spanning Backup for Salesforce will now offer a European data center giving companies a choice of backup destination and aiding compliance with policies that specify data must be stored within the EU.
There are also enhanced restore options which allow the recovery of permanently deleted objects, bulk restores which preserve 'parent/child' relationships, and easier restores of single items. Enterprises will soon be able to self-manage encryption keys, enabling them to better meet their organization's security and compliance requirements -- this feature is expected to be generally available early next year.
"Our latest annual survey of Salesforce admins shows an appreciable increase in the awareness of the importance of data protection for Salesforce," says Jeff Erramouspe, vice president and general manager of Spanning by EMC. "At the same time, the survey showed more than 73 percent of organizations do not use third-party backup, leaving their Salesforce data at risk to user-driven data loss. Our continued focus on customer needs -- including those who require that their Salesforce data stay in Europe -- and our backing by EMC, make Spanning a trusted enterprise-class backup and recovery solution for Salesforce data".
Spanning will be using Dreamforce '15 to share the results from its Second Annual State of the Salesforce Admin Survey.
Photo Credit: Andy Harbin/Shutterstock
-

Corporate virtual drives targeted by ransomware attacks
Publié: septembre 9, 2015, 3:49pm CEST par Ian Barker

Recent discoveries like Adult Player have brought ransomware back into the news, but it's not just individuals that are being targeted.
Data recovery specialist Kroll Ontrack says it's seeing a rise in ransomware attacks aimed at corporate virtual drives. Recently Bitcoin payment was demanded in exchange for stolen data with the threat of the user's information being auctioned off.
The new attacks on corporate systems involve hackers deleting virtual drives completely and replicating the files on their own servers. The first thing companies know about the attack is when they find a note from the hacker where the virtual drives used to be. This criticizes their security arrangements and requests payment for return of the data or threatens to sell it on the open market. In a recent case dealt with by Kroll Ontrack, payment was demanded in the virtual currency Bitcoins in exchange for stolen data within two weeks or the user's information would be auctioned off. Kroll Ontrack was successfully able to recover the customer's data saving them from having to surrender to the demands of the criminals.
"The methods used in ransomware attacks are constantly evolving, but our engineering team have developed their own methods to retrieve and restore data which mean that companies avoid having to make payments to criminal gangs just to get their information back," says Shane Denyer, Data Recovery Engineer at Kroll Ontrack. "We are seeing a definite move away from attacks that target large numbers of small business or home users towards more of a spearfishing approach where individual, larger corporations come under fire".
To keep their data safe enterprises are advised to keep anti-virus software up-to-date, create regular back-ups of corporate data on devices outside the network, and store additional back-ups of virtual drives on devices at a different location.
"Earlier versions of ransomware have been broken down and antidotes are readily available," adds Denyer. "However, we are seeing more and more attacks on corporate systems and predict that there will be even more incidents as ransomware technologies continue to develop. The key is to ensure that data is always backed up on a regular basis and that reputable partners are involved in restoring data that is hacked".
Image Credit: Carlos Amarillo / Shutterstock
-

Avant browser tops the vulnerability charts in the May-July quarter
Publié: septembre 9, 2015, 12:27pm CEST par Ian Barker

According to the latest quarterly update from vulnerability management company Secunia, the product with the most vulnerabilities over the three months from May to July was the Avant browser and, once again, IBM is the vendor with the largest number of vulnerable products.
Avant clocked 206 vulnerabilities over the period, and this is partly because it uses both the Chrome and Firefox engines making it open to the vulnerabilities in both. Also Avant's July 2015 update was the first major version since March and will therefore include many of the Firefox and Chrome vulnerabilities uncovered in the meantime.
IBM tops the vendor list due to the large number of products it produces. Those making Secunia's top 20 lists over the quarter include Intelligent Operations Center, Security Access Manager for Mobile, and Cloud Manger with OpenStack.
The Stagefright vulnerability shone a spotlight on Android security in July with the ability to remotely control a device by sending code in a multimedia message. Secunia notes that some good has come of this as Google and some handset makers -- notably LG and Samsung -- have made a commitment to send out monthly security patches to users that will fix any upcoming issues in the operating system.
"For as long as Secunia has been in business, we have tried to get exactly that message across to IT security professionals across industries: you cannot predict what products will be making your infrastructure vulnerable next month, based on what made it vulnerable this month. And you certainly shouldn't assume that, by patching the 10 high-profile software names that spring to mind when you think about what is in your infrastructure, you are all set and secure," says Kasper Lindgaard, Secunia's Director of Research and Security. "Keeping track of what makes your environment vulnerable is an ongoing and complex task, that requires a combination of vulnerability intelligence and visibility of applications, devices and business critical data in your systems".
The full report is available to download from the Secunia website.
Image Credit: Pavel Ignatov / Shutterstock
-

More than a third of companies are looking for new file syncing solutions
Publié: septembre 9, 2015, 11:32am CEST par Ian Barker

Over a third of companies are planning to adopt a new file, sync and share (FSS) solution in the next year according to the findings of a new survey.
The study released by enterprise sharing specialist Connected Data shows that 21 percent of companies surveyed plan to make a change in their current FSS solution within the next year. It also finds that 13 percent of companies plan to adopt their first-ever FSS system within the next 12 months.
The survey conducted by Wilson Research Group asked IT managers, directors and other IT executives and consultants what their objectives for implementing FSS systems were. Enhancing teamwork and collaboration was cited by 51.3 percent, providing FSS for remote employees by 46.2 percent, and backing up company data on notebook and portable computers by 41 percent. In addition 33 percent listed acquiring a capability to share or distribute files too large to send via email, and 28.2 percent wanted to provide mobile access for all employees.
A large majority (87.3 percent) want to own and manage their FSS function rather than rely on a third-party provider. Also 12.8 percent wanted a corporate option to eliminate the use of unauthorized service providers.
"The Wilson Research Group study confirms the rapidly growing need for secure and compliant FSS solutions-particularly for larger companies," says Geoff Barrall, CEO of Connected Data. "From the data it is clear that these companies are looking for solutions that are able to deliver all the convenience of public cloud, combined with the security, performance, protection and control that only a private cloud onsite solution can provide. Unfortunately, as many have learned the hard way, there are very few options that can meet all, if any, of these requirements".
There's a summary of the results in infographic form below or there's more information on the Connected Data website.
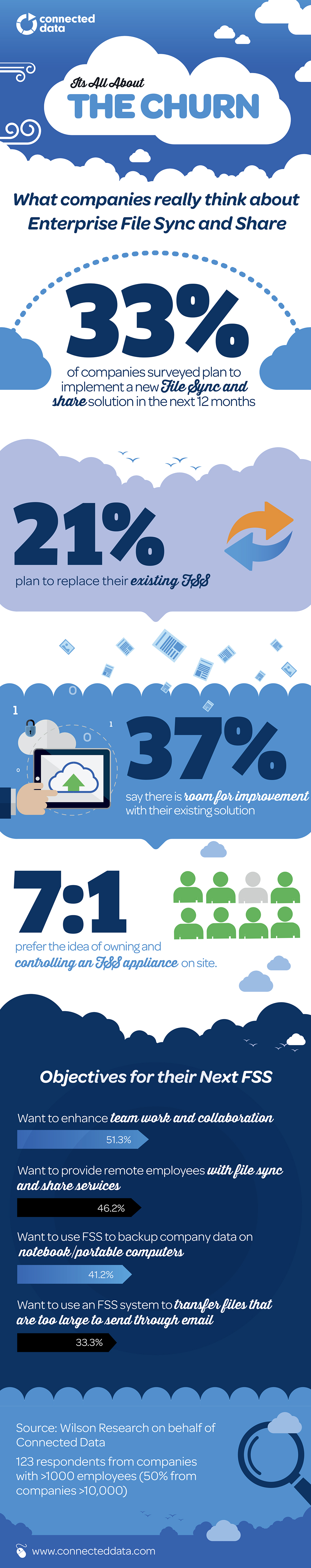
Image Credit: Chiran Vlad / Shutterstock
-

Dell to sell Surface Pro as part of a bid to get Windows 10 into enterprises
Publié: septembre 8, 2015, 5:53pm CEST par Ian Barker

Microsoft and Dell are teaming up to deliver Windows 10 devices, services and support to enterprise customers, starting next month with a new Surface Enterprise Initiative.
Beginning in early October in the US and Canada, Dell will sell Microsoft Surface Pro tablets and Surface accessories through its North America commercial sales organization. This will be rolled out to the remaining 28 markets of Microsoft's Surface commercial channel starting early next year.
"Windows 10 is off to a great start, and we're ready to help make the transition to Windows 10 as easy as possible for all of our customers," says Michael Dell, chairman and chief executive officer of Dell. "Together with Microsoft, we are giving our customers great products, including Surface, with the best sales, service and support in the world".
Surface Pro devices sold through Dell will offer the option of Dell Services, including up to four years hardware warranty, ProSupport with Accidental Damage Service, and Configuration and Deployment Services. The Surface Pro will be sold alongside Dell's existing Windows tablet portfolio.
"We want to move people from needing, to choosing, to loving Windows and so do our partners," says Satya Nadella, CEO of Microsoft. "Our global enterprise customers have asked us to match the Surface Pro 3 and Windows 10 experience with enterprise-grade support and services -- and our partnerships like this one with Dell will do just that".
New Windows 10 enterprise features will also roll out to Windows Insiders this month, with wider availability later in the year. These will include Enterprise Data Protection (EDP), which provides personal and corporate data protection wherever data flows, and Microsoft Passport for enterprise, which helps workers securely login to applications, websites and networks without the need for a password. There will also be a Windows Store For Business, delivering business customers a unified Windows app store experience with a choice of Windows store apps alongside company-owned apps, and allowing IT administers to acquire apps in bulk.
You can read more about the announcement on the official Windows blog.
-

New platform aims to redefine work with personal, smart apps
Publié: septembre 8, 2015, 5:14pm CEST par Ian Barker

Users of enterprise systems are often deterred from completing tasks via mobile apps due to complexity or poor user experience.
Enterprise mobility specialist Capriza is aiming to change that with the launch of a platform that will for the first time make legacy enterprise applications fully contextual and end-user relevant.
"Enterprise applications have been broken for decades, and for some reason we've come to accept this complexity and irrelevance in our work lives in a way we never would as consumers," says Yuval Scarlat, CEO and co-founder of Capriza. "Consumer apps work for us -- information is contextual and presented in a way that takes seconds to consume and act on. It’s time for the enterprise to catch up".
The Capriza platform provides a fully customizable and personalizable user experience, reducing the time it takes to complete complex work functions. Unlike current enterprise software, it uses smart sensors to remember behavior and data preferences and allows users to create proactive business alerts based on behavioural or performance indicator triggers. For example, a user could establish an alert to tell them once sales figures for a particular region are met, or if their teams have exceeded their maximum number of hours for the month on a particular project.
"Despite advances in intelligent mobile operating systems such as Google Now, Microsoft and iOS 9 Proactive, enterprise applications still suffer from a severe case of amnesia," adds Scarlat. "Every time the user logs in, they have to start from the beginning. They navigate dozens of screens to get to the same information they access every single day. With this release, that changes".
Capriza strips away complexity and enables new application users to be up and running within minutes, with no training required. The new platform learns from user behavior and allows the user to choose which data streams to follow in order to personalize their experience and deliver information that is most relevant to them. Apps can be deployed with zero disruption, coding or new infrastructure.
Smart sensors deployed by Capriza within the enterprise applications send users business alerts when certain pre-defined criteria and thresholds are met. This can be used to trigger actions like automatically reordering stock or prompting a phone call to a sales contact.
The platform is application agnostic, and consolidates workflows from multiple applications regardless of vendor and application age. These workflows can be pulled into the Capriza App, designed specifically for the role of the end-user, allowing businesses to get more from their enterprise systems.
More information is available on the Capriza website.
Image Credit: talitha_it/Shutterstock
-

Healthcare offers major opportunity for wearable technology
Publié: septembre 8, 2015, 3:13pm CEST par Ian Barker

According to a new report from research company IDTechEx the wearable market will be worth over $24 million this year. But much of this is for existing technology like smartwatches and fitness trackers.
Where are wearables headed in future though? According to the report the biggest opportunity is in medical and healthcare applications. Including blood glucose monitoring, healthcare is already the largest single sector by revenue in wearable technology and is likely to stay that way.
"More than any other sector, healthcare applications require data reliability and accuracy," says Raghu Das, CEO of IDTechEx. "Whilst many of the tests that are currently carried out under hospital conditions can be made wearable, the challenge is to achieve equivalent or superior reliability and accuracy at sensible price points. That said, wearable technology solutions offer more practical, comfortable and convenient solutions in many healthcare situations".
Expanding wearables into healthcare involves long lead times due to the need for clinical trials. However, there is potential for very lucrative sales for companies that get things right.
Other expanding sectors include infotainment, although devices like Google Glass and Oculus VR headsets have driven the hype in this area they haven't translated to large scale sales. IDTechEx points out that devices in this field such as smartwatches are subject to commoditization by Chinese manufacturers which drives up volumes and reduces prices.
Commercial use is the other area to watch. It has lower barriers to entry than healthcare and is less subject to commoditization than infotainment. Uses range from tracking technologies in wearable devices to replace scanners for warehouse processes, to tracking systems in smart glasses for providing assistance to workers in a hands free way, or wearable cameras used for quality control.
"Many of the opportunities using existing sensors are still to be explored, but in many cases components such as sensors would need specific adaptation for these applications. This acts as a barrier that has restricted the number of easy wins so far, but those that have invested heavily will begin to see the rewards in the next 2-5 years," Das says.
For more information and to buy the full report you can visit the IDTechEx website.
Photo Credit: mindscanner/Shutterstock
-

Acer Aspire V15: Attractive laptop for not a lot of money [Review]
Publié: septembre 7, 2015, 5:03pm CEST par Ian Barker

At the very top of the Acer range are the Aspire V Nitro gaming laptops. Slotting in below those, the workaday Aspire V models deliver decent performance and smart design at a price that’s more attractive to business and home users who want a fast machine without needing, or wanting to spend a lot of money on, a premium gaming rig.
The latest release is part of the V15 range, meaning it has a 15-inch screen, though rather confusingly it’s called a V3 -- V3-574G-51ZI to give it its full official title -- so what does it have to offer?
On paper the machine’s specification is pretty impressive; the 574G has a Core i5 5200u dual-core processor and 8GB of DDR3 memory. It comes with Nvidia GeForce 940M graphics with 2GB of dedicated RAM, and a hybrid storage system with 8GB of SSD and 1TB of conventional hard disk.
There’s a DVD burner and two USB 3.0 and one USB 2.0 ports, plus VGA and HDMI outputs too drive external displays. The screen is a 15.6-inch with 1080p HD resolution and uses Acer’s BluelightShield technology that reduces blue light emissions from the screen to make it easier on your eyes. For connectivity there’s a wired Ethernet port and dual-band 802.11ac Wi-Fi plus built-in Bluetooth.
First Impressions
Open the box and lift the PC out and you’re presented with a system that’s slim and looks smart with a subtly patterned machined aluminium finish to the top. The keyboard surround and the hinge mechanism is silver colored plastic, though it’s grained to look like aluminum.
The underside and the top edge above the screen where the wireless antennas live are grey plastic. Turn it on and you’ll find that the keys are backlit should you want to type in the dark. You can turn this off if you prefer and it gets switched off automatically when you’re running on battery.
The screen surface has a semi-matt finish that does a good job of warding off reflections in bright light. You don’t really notice the BluelightShield technology in operation but there’s no doubt that the screen is nice to look at. Excessive exposure to blue light is supposed to make it more difficult to sleep so it’s good to know Acer is looking after your well being. If you find yourself dozing off while using the laptop you’ll know it’s working.

The track pad is a larger size than many and supports gestures for scroll and zoom, there are no separate left and right buttons but the bottom edge of the pad itself rocks which feels a little odd at first and you can trigger it by accident if you’re not careful, but you quickly get used to it. The keyboard is okay although the keys are flat and have only a short travel and no positive click which may not suit touch typists. Acer has made use of the machine’s width to provide good spacing though, and there is a separate numeric pad on the right which will please spreadsheet junkies.
There’s a fair amount of pre-installed software on the machine including some CyberLink DVD and video programs, McAfee Live Safe Security, Spotify, Dropbox plus a trial of MS Office and Acer’s own BYOC (Bring Your Own Cloud) suite. Perhaps most useful is a Power Button app that steps in to prevent accidental shutdown should you hit the power switch without meaning to.
Performance
Switch on and the 574G boots up fast -- Windows 8.1 64-bit is pre-installed and of course it qualifies for a free Windows 10 upgrade -- it takes around 17 seconds from hitting the power button to seeing the lock screen, that hybrid drive helps here. It’s quiet in operation even when working hard with only a gentle whirr from the fan and it doesn’t get too hot either on the areas where you rest your hands or the underside.
The screen is the star feature here, it offers crisp clear colours and impressive viewing angles, helped by that matt finish which means you’re not troubled by reflections. This isn’t really intended to be a gaming machine but it turns in a respectable 2533 on 3DMark 11 and 2135 on PCMark 8. What this means in practice is it’s more than fast enough for day-to-day use and it provides smooth video playback too.
Sound comes from speakers on the bottom of the machine, they produce a response that’s easily good enough for day-to-day listening whether you’re streaming music or watching a movie. Being underneath they sound better if the PC is on a hard surface. If you were being really picky they’re a little lacking in bass but as laptop speakers go though they’re well above average.
Battery life will obviously vary depending on how you use the machine. Using it for general web surfing via Wi-Fi you should get around three hours out of a full charge which is okay but not brilliant.
Conclusion
The latest Aspire V15 model is slim, reasonably light and looks and feels well finished, the aluminium top panel in particular providing a classy touch. Its performance is easily good enough for everyday use like surfing the web and routine business tasks and the screen is particularly impressive making it a good choice for watching videos.
The only real downsides are average battery life and a not particularly nice keyboard feel. If you can live with those then at £579 it’s a good choice.
Pros
- Screen quality
- Good performance
- Nicely finished
Cons
- Average battery life
- Keyboard feel
- Too many pre-installed apps
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Android malware snaps secret pics of porn seekers
Publié: septembre 7, 2015, 3:24pm CEST par Ian Barker

A new piece of Android malware appears to offer pornographic images but instead takes pictures of the user via the phone’s front facing camera, then locks up the device and demands a $500 ransom.
Called Adult Player it was discovered by researchers at Zscaler. Having checked that a camera is available and taken a picture, it sends details of the victim's device and operating system to the remote servers before displaying the user’s picture on a personalized ransom screen.
Once infected the device will display the ransom screen even after a reboot. Researcher Shivang Desai writing on Zscaler's blog says, "The ransomware is designed to stay stagnant on screen and does not allow the the victim to uninstall it. Rebooting the device does not work in such cases as ransomware app becomes active immediately after reboot, which leaves no scope for the victim to get into device 'settings' and uninstall the ransomware".
The best way to avoid this type of infection is to only download apps from trusted sources and enforce this by unchecking Unknown Sources in the device's security settings. If you have been infected the malware can be removed by booting the device into safe mode.
Depending on the device and version of Android you can access safe mode by a long press of the Power Off option after pressing the physical power button -- you should be asked if you want to boot into safe mode. Or on older hardware or Jelly Bean systems by holding down both up and down volume buttons as the phone boots.
Adult Player is the second instance of porn themed ransomware uncovered by Zscaler following on from Porn Droid in May of this year.
Image Credit: LoloStock / Shutterstock
-

Attackers bundle an old version of TeamViewer to exploit vulnerability
Publié: septembre 4, 2015, 5:22pm CEST par Ian Barker

We're used to seeing malware that exploits unpatched vulnerabilities in software. But in a new twist attackers are bundling an old version of remote access package TeamViewer with their malware in order to take advantage of a flaw.
The malware known as TVSPY has been uncovered by researchers at security company Damballa. While the current version of TeamViewer has fixed this vulnerability, the bundled version works independently of any existing TeamViewer installation on the target PC.
Although TVSPY first appeared in 2012 researchers have seen more than four times the number of unique variants surface in 2015. It's been distributed by a targeted email campaign which included a malicious Excel file with a macro to download the malware. The email purported to come from the All-Russian Research and Design Institute of Nuclear and Energy Engineering. Analysis of the command and control server for this latest variant suggests it's owned by professional criminals.
The researchers point out that, "This particular threat is very dangerous as the attacker will have total control over the affected machine. It can be used during a regular infection campaign or by some advanced persistent threat actors for specific attacks against particular targets".
More information about the threat including how to tell if your system is compromised is available on the Damballa blog.
Photo Credit: Sergey Nivens / Shutterstock
-

Using freelance talent to plug the developer skills gap
Publié: septembre 3, 2015, 6:02pm CEST par Ian Barker

There is a growing skills gap in the apps economy. As businesses become increasingly software-driven, this gap becomes more obvious than ever, and hiring managers are faced with a constant struggle to find the skilled developers they need.
Yet a new survey by freelance work marketplace Upwork suggests that there are developers around the world who have time available and are actively seeking work to fill it.
The company surveyed more than 1,000 of the most successful coders on its platform. The results suggest that developers choose to offer their services on a freelance basis in order to have a more flexible work pattern, earn better pay and get to work on more interesting projects. Freelance developers work an avearge of 32 hours per week and 55 percent expect to be working longer hours in the next year.
What does this mean for managers looking to hire developers? They need to properly set out the details of their projects and over time build up trust with their developers by collecting feedback on how projects have gone. They also need to be realistic about rates of pay and about the timescale of the project.
You can see a summary of the survey results in infographic form below.

Image Credit: Stokkete / Shutterstock
-

The importance of education in combating phishing attacks [Q&A]
Publié: septembre 3, 2015, 6:00pm CEST par Ian Barker

It's usually the case that the weakest link in any security system is the human element. That's particularly true when it comes to phishing attacks. Hackers have become more creative in the social engineering methods they use to gain access to sensitive information.
A new service called LUCY, aims to educate people and identify vulnerable endpoints by allowing businesses or individuals to simulate phishing attacks. We spoke to LUCY founder Oliver Muenchow to find out more about this approach.
BN: How big a problem is phishing?
OM: There have always been phishing attacks, but the amount of attacks we see right now is at an all-time high. Hackers know that people make the easiest and most valuable targets. Criminals have learned the most efficient way to get information is sometimes simply just to ask. Many companies who felt their data was 'safe' are now feeling the financial impact of a security breach.
BN: What kind of attacks can LUCY simulate?
OM: Other than a typical phishing attack which would generate a mail that redirects the user to a webpage, we can simulate more sophisticated customized attacks including also malware simulations. Some recent examples like the Sony hack or a group of modern day bank robbers called the Carbanak gang used essentially the same type of combination attack.
BN: Can the product also check for vulnerabilities that may already be on a network?
OM: Yes, LUCY can check for vulnerabilities on the network, system & application layer. This feature allows users to perform security checks without involving employees outside their own IT department. The portable security scanner we also include in LUCY basically acts as an advanced persistent threat (APT), replicating typical malware attack patterns -- reverse tunneling techniques, privilege escalation techniques etc -- but without harming your infrastructure. You will get the inside view of your security defence layers -- but from the point of a piece of potential malware.
BN: Is education a better approach than prevention where phishing is concerned?
OM: I think both are important. A company should aim to prevent malicious mails from getting delivered to the end-users inbox, but as this is not always possible, we turn to our people as they are the last line of defence. The awareness is only one part. Keeping your employees up to date about phishing threats while presenting the information in an educational manner is the key.
BN: Why did you choose to make LUCY free for smaller businesses?
OM: The idea behind a community version is that larger companies are able to perform some sample testing with LUCY. But that 100 user test model can of course fit the needs of smaller businesses as it stands.
Image Credit: Maksim Kabakou / Shutterstock
-

HP adopts Browsium browser management as part of its Internet Explorer 11 migration service
Publié: septembre 2, 2015, 7:13pm CEST par Ian Barker

We recently reported on HP's new services to help enterprises migrate to Windows 10. Part of this being the WebApp Accelerator Service for Internet Explorer 11.
Web technology specialist Browsium has revealed that HP has selected its browser management solution as a core component of this service.
Because many business applications today run in a browser, web application incompatibilities can have a significant negative impact on business productivity, and become a barrier to a successful operating system or browser upgrades. With the Windows 10 upgrade cycle beginning this year, and added pressure to migrate to Internet Explorer 11 on Windows 7 systems by January 2016, enterprise IT departments are in need of complete browser management solutions.
"Each new operating system and browser release can result in complex and costly web application compatibility challenges for our enterprise customers", says Simon Hughes, vice president, Network and Mobility at HP Technology Services Consulting. "The combination of Browsium's browser management software and the HP WebApp Accelerator Service for Internet Explorer 11 give customers a cost-effective, comprehensive solution designed specifically to address their web application compatibility needs".
Browsium's browser management solution addresses these challenges by enabling legacy web applications to work in IE11 on Windows 7 or Windows 10, without modifying server-side code or virtualizing operating systems. It also ensures Java updates can be deployed quickly to keep IT infrastructure secure while retaining the legacy versions of Java needed for application compatibility. This approach is easy to deploy and manage, cost-effective, and provides an improved user experience. Browser management can also deliver a quick and cost-effective response to future changes in web technology.
More information about the Browsium solution is available on the company's website.
-

TeleSign simplifies end user verification
Publié: septembre 2, 2015, 3:15pm CEST par Ian Barker

Being able to accurately and safely verify identity is increasingly important as online fraud remains a major threat.
Mobile identity solutions specialist TeleSign is announcing the launch of TeleSign Smart Verify, a new unified API that simplifies end-user verification and two-factor authentication (2FA) for online and mobile app-based accounts to help prevent fraud and stop account compromise.
TeleSign Smart Verify uses a proprietary 'Smart Decision Engine' that provides a configurable workflow to determine the optimal use of verification and authentication methods -- choosing between SMS, voice or push notifications.
It allows developers to make use of a single API to access a configurable verification workflow based on industry best practices. It can help detect potential fraud with patented real-time analytics of a phone number's attributes, usage and fraud history to automatically determine if a verification process should proceed.
By using the optimal verification methods in each scenario, such as push notifications to mobile app users instead of SMS messages, and eliminating SMS messages being sent to non-SMS enabled numbers Smart Verify can help cut costs. It can also lead to better visibility by tracking user verification and authentication activity as well as costs incurred with a single reporting tool.
"As online fraud continues to surge, it is more critical than ever to verify the identity of those registering and accessing online accounts," says Steve Jillings, CEO of TeleSign. "Smart Verify brings to bear the full power of TeleSign’s product portfolio with a single API. The end result is that our customers can verify end users and stop account compromise in real-time and in the most reliable, cost-effective manner available."
Smart Verify is available from today and full product details are available from the TeleSign website.
Image Credit: Kirill Wright / Shutterstock
-

How mobile can improve capture and analysis of retail sales data [Q&A]
Publié: septembre 2, 2015, 11:17am CEST par Ian Barker

Modern organizations collect large amounts of data across multiple platforms, but they can find it hard to extract useful, actionable insights from the raw information.
San Francisco-based Zenput provides real-time data capture and analysis to retail, restaurant and consumer goods companies to help them centralize operations and support more informed decision-making. How much difference can this technology make to businesses? We talked to Zenput CEO Vladik Rikhter to find out.
BN: Don't existing PoS systems provide all of the data that retail businesses need?
VR: Quite the contrary, they're just the tip of the iceberg. One of the common frustrations of our retail customers occurs during big promotions. For example, a retailer plans for a July 4th promotion at all of their stores and sends out the materials to all 400 of their locations and then sits back to wait for the sales data from the PoS. One week later, they see that 80 of the stores have $0 in sales because they never set up the display or it got lost in the shuffle. What Zenput does is focus on helping retailers track the execution of these programs in real time via our mobile solution, so they know about those 80 stores before the sale even goes live and can address exceptions, which means no more missed sales numbers.
BN: Can using mobile data collection help store employees become more involved in decision making?
VR: We see a tremendous amount of collaboration between store managers. This could be anything from a clever way to set up a new display to get more visibility or a different way to showcase certain products -- anything that will boost sales. Before, it was difficult for the central support center to get this type of feedback from store employees, but with Zenput they can see these photos and share them with other team members. In a lot of ways, store employees can become innovators.
BN: In 'crisis management' situations isn't there a risk that technology will simply get in the way?
VR: We believe that mobile can only help in this situation. Most of these stores have desktop computers locked in a back office somewhere, making it difficult to get a timely message out to everyone. With mobile, retailers can deliver a message directly to employees' phones with key tasks that need to be actioned during the crisis. A vice president is able to track progress and can respond in real time to stores that need more help.
BN: How can Zenput help multi-site businesses achieve consistency across different locations?
VR: It's all about execution. One of the tough parts of being a multi-unit operator is not being able to be everywhere at all times. Zenput effectively achieves that on the behalf of the operator. With its ability to assign hundreds of tasks at once and bring back hundreds of photos, an operator can sit in her chair and view all of this from her phone or tablet. If something doesn't adhere to consistency standards, she can make comments on the task at hand and the individual concerned will receive them so they can immediately make the fix.
BN: Is there potential for similar mobile technology to be applied to other business models, field service operatives for example?
VR: Absolutely, there are opportunities for real estate, construction, oil and natural gas, manufacturing, etc. We've seen a lot of great verticalized solutions that have popped up in some of these industries and we believe that because 80 percent of the world doesn't work behind a desk, we should expect to see a large stream of mobile-enabled industries in future.
Image Credit: Tashatuvango / Shutterstock
-

Birst wants to Transform analytics with networked BI
Publié: septembre 1, 2015, 6:03pm CEST par Ian Barker
Business intelligence has traditionally relied on centralized data, an approach which is not only time consuming but also represents a barrier to end-user self-service.
Now cloud analytics specialist Birst is launching a new Networked BI technology which aims to redefine the way BI is delivered and consumed by enabling global control with local execution.
Built on top of Birst's modern, multi-tenant cloud architecture, Networked BI creates a grid of interwoven BI instances that share a common analytical fabric. This enables organizations to expand the use of BI across multiple regions, departments and customers in a more agile way, and empowers these decentralized groups to add to the global analytical fabric with their own local data.
This makes BI scalable across the enterprise, at the same time delivering speed and end-user freedom with self-service data preparation capabilities, along with transparent governance. By bringing analytics to the virtual world with Networked BI, Birst does away with data silos and accelerates the delivery of BI across the organization.
"Antiquated BI and analytics architectures force companies to trade off between agility and governance", says Brad Peters, Chief Product Officer at Birst. "Now, with Birst Networked BI, companies no longer have to make that trade off. Our modern, multi-tenant cloud architecture makes it possible to create a network of virtual BI instances so companies can achieve both rapid deployment and easy access to robust BI capabilities".
The company points out that this approach is also of value to software vendors, allowing them to embed analytics in their applications. By rolling out new virtual instances of analytics, without having to physically recreate metadata, data and BI content, application vendors can extend analytics to new customers, fast and at scale.
More information is available on the Birst website.
Image Credit: Andrea Danti / Shutterstock
-

New malware detection engine stops cyber threats sooner
Publié: septembre 1, 2015, 5:04pm CEST par Ian Barker

Attackers are increasingly capable of modifying their existing malware to slip into a victim’s infrastructure undetected. Because traditional security solutions are reactive and can only protect against already known threat vectors this leaves a gap in defenses.
Security company Check Point is launching its new SandBlast product that uses CPU-level threat detection to uncover threats at the pre-infection level. It elevates threat defense with evasion-resistant malware detection and comprehensive protection, significantly reducing the risk of expensive breaches.
"Enterprises are at risk of falling victim to targeted attacks, but implementing proactive, preventative technologies to block malware from entering the network will protect your business without compromising efficiency. Check Point SandBlast provides an additional layer of security from even the most sophisticated attacks by catching more malware, with minimal impact on delivery times", says Gil Shwed, CEO and chairman of Check Point Software Technologies. "The growth of our Threat Prevention portfolio continues to extend our depth of technology to enable us to continue to arming our customers with innovative defensive strategies against cybercrime. Together with Check Point Mobile Threat Prevention announced at Black Hat last month, Check Point is moving quickly and aggressively to secure the future".
Among SandBlast's features are the ability to identify malware at the exploit phase, even before evasion techniques can be applied. It can't be bypassed by delay loops, attempts to determine if a virtualized OS is in use, or other methods aimed at circumventing the sandbox.
By combining the power of CPU-level detection with OS-level emulation it works with a broad range of file types, including MS Office, PDF, flash, executables, and archives. An integrated Threat Extraction capability allows it to deliver safe versions of files. This means Check Point SandBlast can be deployed in prevent mode, while traditional sandbox products are typically run only in detect mode to avoid delivery delays.
SandBlast is available as a cloud service or an on-premise appliance and is part of a new generation of threat prevention products. Find out more on the CheckPoint site.
Photo Credit: Balefire / Shutterstock
-

Egnyte announces Office 365 integration
Publié: septembre 1, 2015, 4:29pm CEST par Ian Barker

Secure file sharing specialist Egnyte is releasing new integration between its product and Microsoft’s Office 365. These will allow business users to seamlesly access, manage and share their files.
Features include the ability to open Egnyte files directly from Microsoft Office Online for viewing and editing and changes are automatically saved back to Egnyte.
Native integrations within all of the Office tools will provide users with a variety of choices to easily open, edit, and share any of their Egnyte files. In addition users on the move can remotely access and edit Egnyte files from any of the native Office Mobile Apps.
"Egnyte's security-enhanced and hybrid architecture enables Microsoft users to seamlessly share and manage documents stored across heterogeneous storage locations -- in the cloud and on-premises -- while enhancing the user experience by connecting workflows across their favorite business applications, including Microsoft Office", says Steve Guggenheimer, corporate vice president and chief evangelist at Microsoft. "We are pleased to count Egnyte in our partner community as a hybrid file services platform for our customers to easily collaborate with their Microsoft content across desktop, mobile and online -- wherever business may take them".
Egnyte is also launching a new Technology Partner Program, providing enhanced value-added services on top of their open, hybrid technology -- which uses existing infrastructure on-premises, in the cloud, or a mixture of both.
"By partnering with key enterprise players and integrating their applications with the Egnyte solution, we’re creating seamless workflows around content that is mission critical for the enterprise", says Isabelle Guis, Chief Strategy Officer at Egnyte. "We're significantly scaling our ecosystem of infrastructure and application partners, on-premises and in the cloud. Supporting a broad variety of IT environments facilitates adoption and makes business users and IT professionals more efficient, allowing our customers’ businesses and ours to thrive".
More information on the Technology Partner Program is available on the Egnyte website.
Photo Credit: EDHAR/Shutterstock
-

New platform aims to speed up the sales process
Publié: septembre 1, 2015, 3:31pm CEST par Ian Barker

Sales are the lifeblood of a company, yet they can also be a frustratingly slow part of the whole business cycle. Finding a way of accelerating the sales process is therefore a bit of a holy grail for many organizations.
Salesforce solution specialist Velocify is launching a new enterprise-class sales acceleration platform. Velocify Pulse takes a universal approach that accelerates every step in the sales cycle, and aligns everyone in the sales organization on the same platform.
"Companies aiming to achieve exceptional growth all want to accelerate their sales process, but the problem is they can't operate at speed if they don't have control", says Nick Hedges, president and CEO of Velocify. "Focusing on speed alone is like giving a Ferrari to someone who has never driven a car before -- it will probably end badly. That’s why Velocify focuses on allowing teams to operate with velocity and discipline simultaneously".
The platform takes an insight-driven approach to developing the optimal sales processes, motivating people to follow the plan through 'Rewardification' -- delivering valuable incentives to salespeople that follow best practices and generate results -- and keeping the entire organization on a single platform that covers everything from prospecting to lead response to closing the final deal.
By using rules, logic, behavior, and historical data it can help determine the most effective sales strategies. There is complete visibility into how each part of the sales process works, so that leaders can adjust specific aspects to continually improve team performance.
"Predictive analytics is certainly a part of the equation, but sales leaders should not hand control over to predictive analytics entirely", adds Hedges. "A prescriptive, insight-based approach is really critical to optimizing sales processes and accelerating sales performance."
It includes a tool called SalesCaddy which has two components, SocialCaddy, to enable sales reps to build prospect lists using LinkedIn, and MailCaddy, to connect to Gmail and Office365 for seamless communication with prospects.
For more information on Velocify Pulse and to request a demo you can visit the company's website.
Image Credit: iQoncept / Shutterstock
-

IT workers suffer the summertime blues
Publié: septembre 1, 2015, 1:59pm CEST par Ian Barker

During the summer months, many organizations see a significant expansion in the number of remote workers, which can make the job of network managers or system admins more difficult.
Software company Ipswitch recently polled 239 IT professionals in the United States to identify the issues that most affect them over the summer.
A third of all survey respondents saw nearly half of their colleagues working remotely during the summer. Malfunctioning laptops were named as the top problem by 42 percent, followed by network connectivity issues (32 percent) and poor application performance (16 percent).
Wireless devices were named as a problem too. When asked what type of device they'd like to see eliminated from use on the corporate network, 49 percent of all IT pros surveyed chose tablets, followed by smartphones at 31 percent. Only 10 percent named wearable technology which may be due to relatively small size of the market at the moment.
When asked what employees could do to reduce the load on IT staff, 42 percent said eliminating the shadow IT effect, when employees download apps without telling or seeking permission. Nearly one third (29 percent) said they'd most appreciate if an employee rebooted their computer before seeking assistance. In order to feel more empowered at work, 32 percent of IT professionals would like the ability to choose and buy technology, while 25 percent wanted to have X-ray vision to figure out the source of problems.
"The summer months are a busy time for IT pros as employees expect continuous unfettered access to company networks while working from home or on vacation. A single organization can find itself with a significant bump in remote workers, all of whom may need support and assistance", says Jeff Loeb, Chief Marketing Officer at Ipswitch. "A unified network and server performance monitoring solution will help IT pros to solve network issues before they affect employees, wherever they are working".
The full report is available from the Ipswitch website and there's a summary of the findings as an infographic below.

Image Credit: Creative Images / Shutterstock
-

Millennials just want to have human contact
Publié: septembre 1, 2015, 12:37pm CEST par Ian Barker

Despite being thought of as the generation that organizes pretty much everything in their lives through social media, new research from call center specialist Mattersight reveals that when it comes to service issues millennials prefer to speak to a human being.
Only one percent of millennials want to use social media to contact a brand when they have a product question or problem. Of those surveyed, 76 percent say they prefer to call (56 percent) or email (25 percent) brands for customer service issues.
In addition more than 85 percent have been disappointed with a brand's service and support in the past year. All of this is in stark contrast to the views of brands, 67 percent of which believe social media-based service is growing in importance.
"Despite growing up in the digital age, millennials haven’t abandoned person-to-person contact", says Mattersight CEO Kelly Conway. "Contrary to popular belief, we found that most millennials prefer to communicate in-person and over the phone because it allows them to have the most meaningful conversations".
These communication preferences go beyond customer service too. At work, 85 percent of millennials surveyed said that they prefer to meet and communicate in-person with their co-workers. The second most preferred method of communication at work is a tie between email and talking on the phone, which indicates millennials' equal desires for efficiency and social interaction. Over half of those surveyed said that outside of work they prefer to communicate in person, and that an important characteristic of a quality conversation is having chemistry -- which is hard to cultivate through digital and online means only.
"Just like in the workplace, millennials want to be able to communicate with a company person-to-person in order to quickly solve problems", says Conway. "Unfortunately, companies generally aren’t providing the call center experience that millennials are seeking, forcing them to abandon phone options for less preferential ways to connect with brands, or even disengage completely."
You can find out more in the full report which is available to download from the Mattersight website.
Image credit: Prazis/Shutterstock
-

CloudPhysics helps manage virtual environments
Publié: août 31, 2015, 3:16pm CEST par Ian Barker

In the modern world of virtual servers, infrastructure can be complex and changes come fast. This also means that the potential for change-related risk to applications is greater than ever before.
IT administrators don't always have the ability or time to study all the known or unknown configuration issues in their vSphere infrastructure. They can therefore struggle to understand whether changes -- intended or accidental -- result in performance disruptions and availability issues in waiting.
Smart IT solutions provider CloudPhysics is launching a new release of its SaaS offering, expanding its analytics solution so that VMware users can spot and eliminate operational hazards that threaten to disrupt IT operations and applications.
CloudPhysics reduces disruption and incidents with always-on diagnostics that show up hot spots and emerging problems via configurable dashboards, enabling admins to get ahead of developing performance problems. It also improves mean-time-to-resolution with directed exploration, enabling admins to home in on the root cause and resolve application disruptions more quickly.
By generating insights that allow admins to spot misconfigured infrastructure CloudPhysics can help make corrections to prevent future performance and availability issues and improve efficiency. It uses a library of 'cards' to assist with managing health and pre-empting hazards.
"Dealing with unforeseen system disruptions kills IT productivity, and the most common 'cure' -- to add more hardware -- simply adds costs and masks the underlying problem", says John Blumenthal, CloudPhysics' vice president of product management. "Our unique insights and exploration capabilities are the fastest, easiest way for IT to get ahead of potential risk in their infrastructure, using an intuitive solution that uses predictive analytics to spot trouble early, guide to the root cause, and ultimately tune your infrastructure to prevent recurring hazards".
CloudPhysics is sold on a subscription model, it will be on display at VMworld and users can try it out with a Free Edition available to download from the company’s website.
Photo Credit: leedsn/Shutterstock
-

New analytics offering helps track hybrid cloud use
Publié: août 31, 2015, 12:18pm CEST par Ian Barker

Increasingly businesses are turning to the cloud or to hybrid solutions for their IT. But this can make it harder to track usage and keep control of costs.
Californian company Cloud Cruiser is launching a new CloudSmart-Now solution that allows customers to easily track hybrid cloud usage by user and keep an eye on costs with built-in analytics.
It's designed so that businesses of all sizes can quickly understand the financial and operational impact of the cloud with a single pane view of their total consumption of cloud services. It has pre-configured templates with built-in workflow to collect detailed usage and cost data from Amazon Web Services (AWS), Azure, Windows Azure Pack (WAP), VMware and Openstack.
"Hybrid cloud is simply a reality for most businesses. The single biggest area of improvement continues to be around efficiencies and reducing costs", says Fraser McKay, VP Products at Cloud Cruiser. "We love the promise of low-cost cloud but it's not unlimited and unless you track and measure, sprawl and anarchy quickly creep in. Our customers stay ahead and better forecast to meet business demands. We directly address this problem with a single solution to manage all hybrid cloud environments. You can't manage what you can't measure and we've done the heavy lifting with this new packaged offering".
CloudSmart-Now provides pre-configured collectors, built-in data mapping to existing business structure, report templates and an automated workflow so businesses can distribute reports to business users.
Users need to select which of the 'Big 5' clouds they want to measure and select Cloud Cruiser workbook templates. Then using built-in API for public cloud and automated private cloud collectors they can import usage and rate data at a detailed level.
With organizational structure in place, business mapping allows them to map usage to department and owner. Finally a standard set of rich reports including top spenders across the business, cloud spend by provider, and potential savings.
CloudSmart-Now will be on display at VMworld this week or you can find out more on the Cloud Cruiser website.
Photo Credit: everything possible / Shutterstock
-

Why mobile matters for online shoppers
Publié: août 31, 2015, 11:37am CEST par Ian Barker

There are currently an estimated 1.91 billion smartphone users worldwide, and 82 percent of them use their mobile devices to shop. As consumers are five times more likely to abandon shopping if the site isn’t optimized this means embracing mobile is crucial for businesses.
Online shopping portal DirectBuy has produced an infographic looking at how the world is moving towards a mobile shopping environment.
Interesting findings are that for younger users in particular the smartphone may be their main point of internet access. Shoppers already use their smartphone to compare in-store pricing, and the mobile device is becoming the consumer’s go-to tool for all shopping needs, 81 percent of people research online before buying locally and mobiles have a higher conversion rate (78 percent) than desktops and tablets.
As numbers increase the mobile experience becomes crucial. It’s estimated that by 2020 user experience will surpass pricing and product as the main differentiator between brands. If marketers aren’t optimizing their websites, they’re leaving a rapidly growing demographic without access to products.
You can see more detail in the full infographic below.
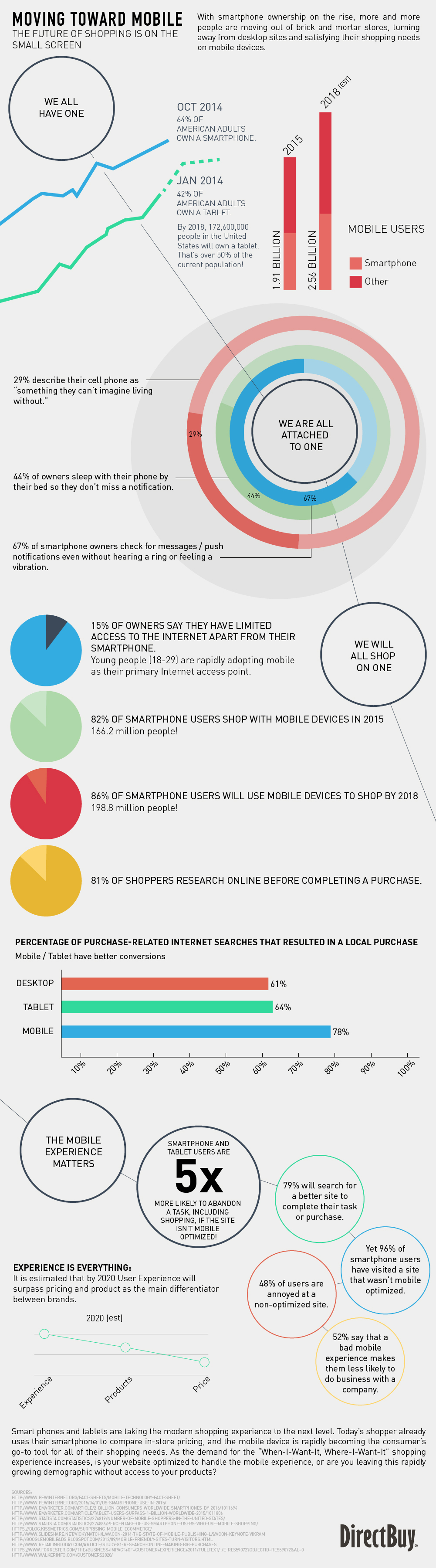
Image Credit: 3Dmask / Shutterstock
-

Kaspersky launches improved business security for Macs
Publié: août 28, 2015, 4:03pm CEST par Ian Barker

Macs have around six percent of the business endpoint market and Mac specific malware is on the increase. In the rapidly evolving world of malware and security, Mac users can no longer afford to be complacent when it comes to protecting their systems.
To tackle these threats Kaspersky Lab is updating its Kaspersky Endpoint Security for Business suite with Endpoint Security 10 for Mac. This offers a combination of deep protection, efficiency and manageability, designed to serve the needs of protecting diverse IT environments.
It delivers a broad array of tools and technologies which are easy to deploy and use, offering Mac owners a host of new security benefits. Features include integration with the Kaspersky Security Network which allows businesses to take advantage of cloud-enabled security intelligence for the quick identification of malware and other suspicious activity.
A Network Attack Blocker monitors suspicious activity on company networks and lets IT specialists pre-define how their systems will respond if any suspicious behavior is detected. This component can block network attacks including port scanning, denial-of-service attacks, buffer-overrun attacks and other remote malicious actions taken against programs and services working on the network.
To combat web threats it offers web protection and anti-phishing technology. This scans all incoming and outgoing traffic, blocks harmful scripts without impacting system resources and helps ensure users don't fall prey to phishing sites.
"At Kaspersky Lab we believe that every business, regardless of its size and market, has unique and complex infrastructure, which requires deep multi-layered cybersecurity protection," says Konstantin Voronkov, Head of Endpoint Product Management at Kaspersky Lab. "We believe that each component of corporate infrastructure should be protected because cybercriminals will use every chance they can to infiltrate a corporate network. Enhancing our Kaspersky Endpoint Security for Business line -- providing flexible multi-layered protection for different infrastructures and platforms against modern cyberthreats -- will make it easy for businesses to protect themselves, including those businesses using Mac platforms. We believe that this approach allows our partners to concentrate on business development without having to worry about cybersecurity".
You can find more about Kaspersky Endpoint Security for Mac on the company's website.
Image Credit: Kotka fotoaloja / Shutterstock
-

Charge as you drive -- Inateck USB car chargers [Review]
Publié: août 28, 2015, 1:11pm CEST par Ian Barker

It's not unusual for modern cars to have a built-in USB facility, but generally you only get one port and it has to do duty as both a charging point and an input for the audio system. That means family journeys with multiple devices demanding power can lead to squabbles.
For those who need extra USB charge points in the car Inateck has produced two new solutions in the form of adaptors that plug into a standard 12V power socket -- lighter socket for older readers and classic car owners.
The AL 4001 is a 4-port device with a smart white and silver finish and comes supplied with two micro USB cables. The AL2001 has two ports and a choice of white or shiny black finish, it comes with one cable but it also has a hard-wired Lightning cable to charge Apple devices.
Both have a blue LED indicator to let you know when they're working. The 4-port delivers a maximum of 5V/2.4A, the 2-port gives 5V/2.1A on the USB sockets and 2.4A on the Lightning cable. Talking of cables the Lightning cable is three feet long, the supplied USB cables with both units are a more generous four feet allowing you to power a device like a satnav or camera that's sitting on top of the dash.
Inateck uses intelligent charging technology to detect the connected device and deliver the appropriate current. The chargers also have short circuit, over current, over watt and overheating protection for safety.
The units feel well made and are easy to use straight out of the box. The 4-port charger is a bit bulky so may be awkward to use depending on where your power socket is located but other than that there's not much to criticise here.
The two port costs $19.99 on Amazon (£20.99 in the UK) the 4-port is $14.99 and £13.99 in the UK. More information is available on the Inateck website.
-

How managed DNS has evolved
Publié: août 28, 2015, 12:42pm CEST par Ian Barker

DNS is essential to the smooth running of the internet but the rise of the cloud and the spread of distributed applications has placed it under increasing strain.
This has led to the rise of managed DNS services that streamline reporting, traffic management and more. But how has managed DNS evolved? Specialist in the field NSONE has produced an infographic showing its history and looking at its future.
Managed DNS first took off in the 2000s initially to improve redundancy and reliability and ultimately allowing domain owners to achive faster response times and improve reliability. By the 2010s with applications becoming increasingly distributed, managed DNS services have to offer advanced traffic management to reliably route users to the correct service.
In future managed DNS will need to become application aware to ensure users always arrive at the most appropriate service endpoint. They'll also need to be easy to use without coding and be able to adjust based on real-time conditions to deal with varying loads and network congestion.
You can see more including a list of what to expect from a modern DNS platform in the infographic below.
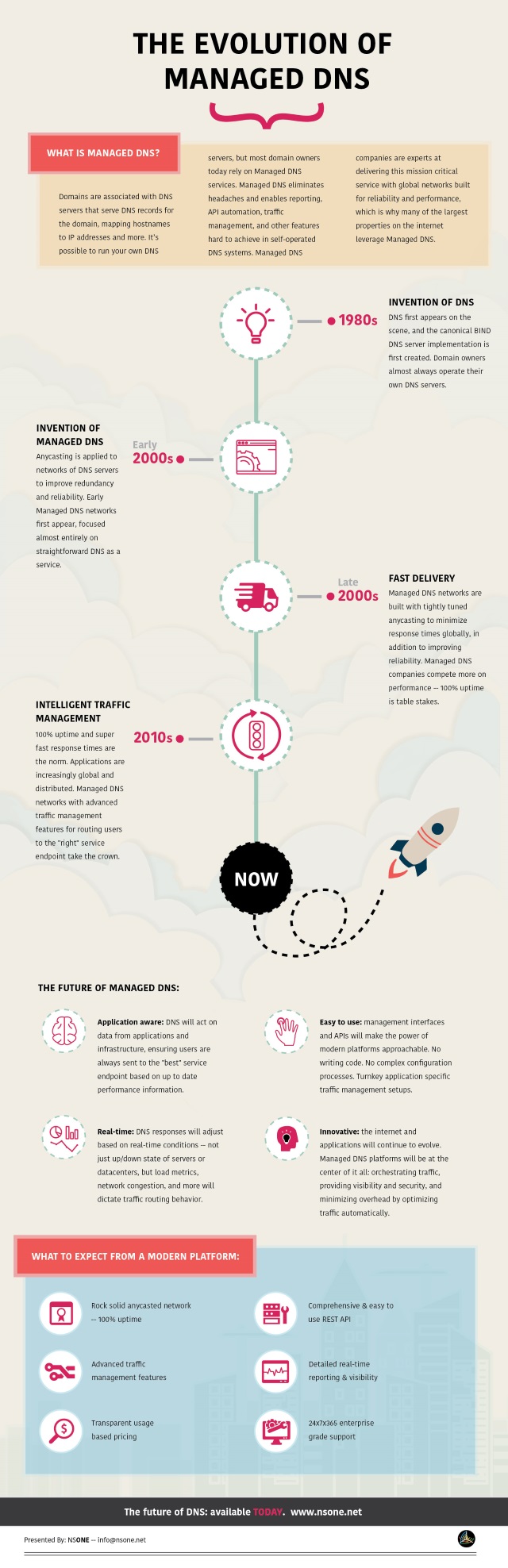
Image Credit: Tashatuvango / Shutterstock
-

TeleSign and Telefόnica team up to cut mobile fraud
Publié: août 27, 2015, 4:47pm CEST par Ian Barker

Mobile identity specialist TeleSign has announced an agreement with Spanish telecoms giant Telefόnica -- the company behind O2 in the UK and Germany -- to deliver a suite of services to address account security and fraud prevention for enterprises and service providers.
The partnership will use TeleSign's products and infrastructure, along with Telefόnica's consent-based insights, to increase account security, reduce fraud, and improve customer experience for consumers. At the same time it will help to manage costs for service providers across financial services, e-commerce, cloud and social media.
"With its market leadership and unique technology to secure mobile identity, TeleSign is a natural partner to improve our customers' experiences, while protecting them from fraud at the same time," says Phil Douty, Managing Director of Telefόnica Dynamic Insights. "The services we are launching together will have meaningful impact for consumers, banks and service providers, and are built on unique data insights only available from mobile network operators. The service will be optional for our customers, requiring consent for data to be used. This means that they remain in control of their data and how it is used".
The first products of the partnership will focus on using phone verification and real-time country location information to help combat fraud and poor customer experience in payment card transactions. Legitimate cardholders should enjoy a swift and secure experience, while fraudsters will be frustrated, thanks to a secure link between TeleSign, Telefόnica and participating financial institutions. The solution does away with the need for special smartphone apps and works on any mobile device when traveling -- once the customer requests the service, it automatically protects them from the minute they switch their phone on.
"Telefόnica has a strong history of innovation amongst mobile operators for delivering new services which benefit their subscribers," says Steve Jillings, CEO of TeleSign. "TeleSign is excited to join with Telefόnica to bring offerings to market that respect user privacy and make it easier for individuals to assert their identity in a simple and reliable manner".
More information on TeleSign's mobile identity offerings is available on the company's website.
Image Credit: photomaimai / Shutterstock
-

84 percent of people support eliminating passwords
Publié: août 27, 2015, 1:23pm CEST par Ian Barker

Spare a moment to consider the plight of the humble password. It has become an essential component of modern life, but it would be wrong to say we've grown to know and love it.
In fact a survey by mobile authentication specialist LaunchKey shows that 84 percent of respondents would like to do away with passwords altogether and 76 percent believe their information would be more secure with an alternative form of authentication.
Almost half of the survey respondents (46 percent) say they currently have more than 10 passwords to manage, and 68 percent acknowledge that they reuse passwords for multiple accounts. In addition, 77 percent say they often forget passwords or have to write them down. Among respondents' top password peeves are those systems that require users to change their password frequently, and systems that require users to create passwords that do not fit the model of one they regularly use. 27 percent admit that they've shared passwords with someone else.
"Today, the pace of security breaches directly related to stolen passwords and bypassed authentication is increasing along with the severity of their consequences," says Geoff Sanders, CEO, LaunchKey. "Passwords are inherently insecure as a method of authentication, and their efficacy relies on end users, developers, system administrators, and the applications themselves, all of which are vulnerable to a wide variety of attack vectors currently being exploited by cyberattacks around the world".
Whilst two-factor authentication is often touted as a solution, 64 percent of those surveyed say they don't know what 2FA is, while only 20 percent say it's easy to use.
The survey also looked at how much people trust enterprises with their data. Given recent breaches at stores such as Target and Home Depot, it's not surprising that 52 percent of survey respondents expressed little to no confidence in retail stores being able to properly secure their data and 43 percent lacked confidence in online retailers. On the other hand, 48 percent of respondents expressed high confidence in banks being able to protect personal information.
"The future of authentication is free from traditional passwords," Sanders concludes. "We must remove the vulnerability and liability that passwords have created while implementing more secure authentication methods that account for an evolving and diversified landscape of use cases, end users and threats".
You can find more about the survey results on the LaunchKey website.
Image Credit: Zsolt Biczo / Shutterstock
-

How do you know if the cloud is right for your business? [Q&A]
Publié: août 27, 2015, 11:58am CEST par Ian Barker

The rapid growth in cloud adoption might suggest that every workload businesses currently have on-premise is destined for some sort of cloud-based service. The reality is that, other than for small companies, that's probably not the case.
Entrusting key applications to a third party requires intelligent planning in many areas such as management, portability, security and support requirements. What can IT organizations do to reduce risks, tame the complexity and increase their potential for success? We spoke to Jerry McLeod, vice president of business development at hybrid cloud management provider HotLink to find out.
BN: The cloud is rapidly becoming the norm for many businesses. How important is it to choose the right provider?
JM: It's critically important to choose the right cloud provider; it's one of the most important IT decisions most businesses will make. However, no one provider is right for every business. There are some cloud options that have a wider portfolio of robust features, but are essentially self-service. At the other end of the spectrum are providers that offer more of a managed service. The 'right' provider for any individual business could actually be a mix-and-match of cloud services, but that will depend on your workloads and support needs, which can change over time.
BN: As more enterprises choose a mix-and-match approach for cloud providers, what struggles do they face in terms of managing those resources?
JM: There is certainly operational complexity related to managing multiple cloud providers. If you're administering several platforms -- say, Microsoft Azure, Amazon EC2 and OpenStack -- monitoring, managing and automating those resources individually becomes a real challenge for IT teams.
However, the reality for most enterprises is even more difficult, because they're building hybrid IT infrastructures that span internal and external resources. So, at the same time teams have to figure out how to manage a spectrum of cloud alternatives, they're also grappling with managing existing on-premise virtual infrastructure and platforms like vCenter, Hyper-V, XenServer or KVM. The difficulty inherent in doing that can threaten the benefits that draw companies to the cloud in the first place: reduced cost, increased agility and faster time to market.
BN: Most organizations will be worried about security when moving to the cloud. What can they do to minimize vulnerability during migration?
JM: Many cloud providers are more secure than some on-premise data centers. Why? Because they have spent years making them that way. Businesses should be worried about their security all the time, not just when the cloud is involved. Unfortunately, many companies believe they're secure simply because they're on premise, even if they don't have a security expert on staff to assess their risk. When those businesses move to the cloud, they gain a team of security professionals who are constantly updating security to stay ahead of evolving threats. During the migration itself, companies can minimize their vulnerability with a tool that creates a VPN tunnel between their on-premise systems and the cloud with secure agent proxies.
BN: Isn't having your applications and data in the cloud always going to be riskier than keeping them in house?
JM: Physically, the cloud is more secure than most companies' data centers. I equate it to the difference between the deadbolts you might have on your house and the purpose-built buildings your bank uses -- there's just no question which one is more secure. Cloud providers build their businesses on security, and they have the infrastructure and personnel power to keep their sites safe.
BN: What are the challenges of the cloud when it comes to ensuring business continuity?
JM: The cloud's economics make it feasible for companies to have a comprehensive data protection solution for all their workloads, not just their critical workloads. That encompasses backup, data replication, disaster recovery (DR) and business continuity (BC) at a fraction of the cost and complexity of traditional, physical DR/BC sites. Comprehensive cloud data protection is now an option for everyone. However, cloud providers don't deliver business continuity. Each individual company has to be responsible for that by adopting adequate tools, processes and plans. If you don't have a business continuity plan for managing your infrastructure, then it's on you when there's a failure.
BN: What are the keys to ensuring an early return on cloud investments?
JM: An apples-to-apples comparison is the key to ensuring ROI. What are your on-premise costs and what will the same usage cost in the cloud? People tend to assume the cloud is almost free, so they end up running three times as many applications in the cloud as they did on premise; that won't be cheaper. Let's say you're paying 10 cents per instance per hour, for example. That's around $1,000 per year. Multiply that by 20 or 30 instances, and it adds up quickly. To make sure you're not chewing through your potential savings, first make sure you understand what your on-premise costs are, and then closely monitor and manage your cloud usage.
BN: Are there times when the cloud simply isn’t the right approach?
JM: If you're running, say, a large logistics company using internal mainframes in secure data centers around the world, it probably doesn't make a lot of sense to move everything to the cloud right now. There are critical enterprise workloads that may never be well suited to the cloud. For those companies, it makes sense to have some workloads in the cloud and some on premise.
HotLink has been working with companies since 2011 to streamline the management of those types of hybrid environments, and we recently released HotLink Cloud Management Express to take that to the next level. For enterprises with multiple cloud providers and several on-premise resources, the ability to unify management and administration into a single, familiar interface such as VMware vCenter means that 'the right approach' can be a multi-faceted one that is also intuitive and flexible.
Image Credit: everything possible/Shutterstock
-

Security education saves companies millions of dollars a year
Publié: août 26, 2015, 5:04pm CEST par Ian Barker

Successful phishing attacks can lead to costs from loss of employee productivity and credential compromise, among other factors, which together may cost an average sized company $3.77 million per year.
New research released by Wombat Security Technologies and the Ponemon Institute finds that the phishing email click rate improved an average of 64 percent following security training.
"In talking with security officers, we know that many do not expect much benefit from employee training as part of their defense against phishing attacks. This research proves that security officers should expect more from employee education and seek providers like Wombat Security who can provide results like these", says Dr. Larry Ponemon, chairman and founder of the Ponemon Institute. "As the threat landscape continues to intensify and phishing tactics become more sophisticated, this research shows that employees who have undergone security training are far less likely to fall victim to a phishing attack".
As a result of training provided by Wombat, Ponemon estimates a cost saving of $1.8 million or $188.4 per user. If companies paid Wombat's standard fee of $3.69 per user for a program for up to 10,000 users, Ponemon determined a substantial net benefit of $184.7 per user -- an annual rate of return on investment of 50X.
Other findings include the average total cost for a company to contain malware is $1.9 million per year. Uncontained malware can cost an average-sized company as much as $105.9 million. The cost of business disruption due to phishing is $66.9 million and employees waste an average of 4.16 hours annually due to phishing scams.
The average annual cost to contain a credential compromise that resulted from a successful phishing attack is $381,920. An uncontained credential compromise could cost a company as much as $105.9 million.
"This is yet another proof point that an overall security posture is multifaceted and needs to include employee education to prevent against increasingly more sophisticated phishing attacks, which leave companies vulnerable to significant losses and business disruption", says Joe Ferrara, President and CEO of Wombat Security Technologies. "This research reveals the compelling value and ROI from putting in place a comprehensive security training program. Our methods have shown that a continuous training methodology does change employee behavior and reduce risk within an organization".
The full report, The Cost of Phishing and the Value of Employee Training is available on the Wombat Security website.
Photo Credit: Ivelin Radkov/Shutterstock
-

One percent of employees account for 75 percent of cloud risk
Publié: août 26, 2015, 4:06pm CEST par Ian Barker

Cloud security specialist CloudLock has released a new report looking at the risks of user behavior to businesses using cloud systems.
It reaches the startling conclusion that just one percent of users account for 75 percent of the security risk. The top one percent of users are responsible for 57 percent of file ownership, 81 percent of files shared, 73 percent of excessively exposed files and 62 percent of app installations.
Understanding the composition of this one percent of users is crucial for security teams. Often it includes super-privileged users and software architects, as well as machine-based identities (such as applications with programmatic access) that grant access privileges and archive data.
A similar imbalance also shows in cloud-based collaboration. While organizations on average collaborate with 865 external parties, just 25 of these account for 75 percent of cloud-based sharing. Also, 70 percent of external file sharing occurs with non-corporate email addresses which security teams have little control over.
Risky installs are a problem too. Many cloud applications support integration with third-party applications, outside the network and undetectable via traditional security tools, such as proxy- or gateway-based solutions. These apps may be targeted by cybercriminals as entry points to organizations. CloudLock research reveals that 52,000 instances of applications are installed by highly privileged users -- this represents a high risk given that privileged accounts are highly coveted by malicious cybercriminals.
"Cyber attacks today target your users -- not your infrastructure. As technology leaders wake up to this new reality, security programs are being reengineered to focus where true risk lies: with the user," says CloudLock CEO and co-founder Gil Zimmermann. "The best defense is to know what typical user behavior looks like - and, more importantly, what it doesn't".
You can read more in the full report which is available to download from the CloudLock website.
Image Credit: Creativa Images / Shutterstock
-

The impact of big data on IT operations analytics
Publié: août 26, 2015, 3:29pm CEST par Ian Barker

Decision makers at Fortune 1000 companies are increasingly seeking to make use of big data to help their IT strategy.
Analytics specialist ExtraHop has released the results of a survey conducted by research firm TechValidate which shows how organizations are evolving their IT Operations Analytics (ITOA) practices.
The popularity of ITOA is on the rise particularly for network performance monitoring, application performance monitoring, root-cause analysis and IT security, 65 percent of respondents are planning to integrate data sources for ITOA in the next year. In terms of big data types, wire data and machine data are ranked as the most valuable sources for IT visibility. In addition, organizations that combine multiple data sources for ITOA gain greater insights from the data, resulting in quicker, more accurate data analysis. Of IT professionals who are combining wire data with other sources machine data is used by 54 percent, agent data by 31 percent and probe data by 26 percent.
60 percent of IT professionals understand the value and benefits of wire data for obtaining deeper ITOA insights. 93 percent of IT decision makers rely on wire data sources for IT management and monitoring, more so than any other traditional big data sources like machine, agent and probe information.
"As awareness of Big Data matures, we are seeing faster and more widespread adoption of ITOA, and the importance of wire data as a source of insight has become a key topic in conversations with customers," says Erik Giesa SVP Marketing and Business Development at ExtraHop. "Businesses rely on IT as the lifeblood of their organizations, so the stakes are high for keeping that machine running as efficiently as possible. That's where ITOA has really proven itself as a high-value, must-have initiative".
The full report is available to download from the ExtraHop website and there's a summary of the findings in infographic form below.
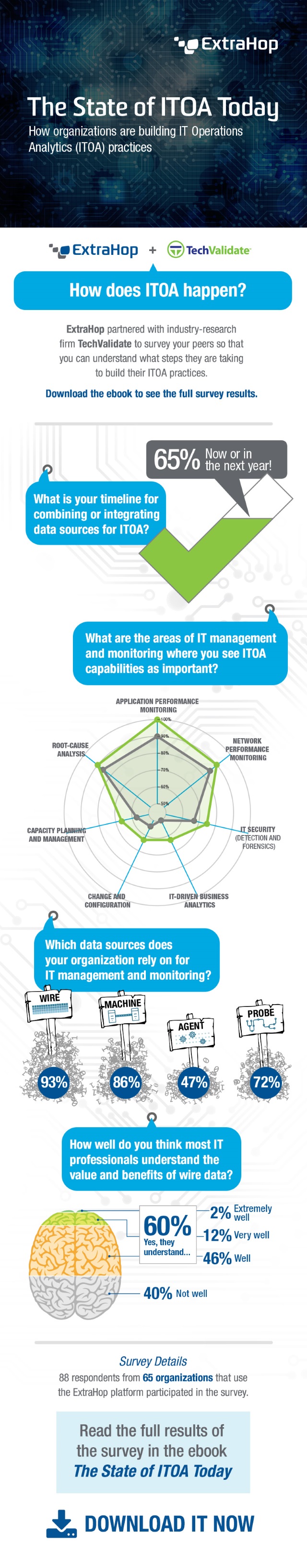
Image Credit: bleakstar / Shutterstock
-

Millennials lose trust in the digital economy
Publié: août 26, 2015, 11:11am CEST par Ian Barker

Although millennials are the first fully connected generation, having lived their whole lives in the Internet era, new research suggests that they're beginning to recognize that their identity and personal data may not be properly protected.
Digital identity specialist Intercede surveyed around 2,000 16-35 year-olds in the US and UK to get their views on current security measures. The results suggest what the company calls a 'millennial malaise' towards existing safeguards, in particular the use of easily-hackable but widely used password-based authentication methods.
A quarter of the millennials questioned access more than 20 password protected websites, applications or devices over the course of a year, with 45 percent claiming they only ever change passwords when they have to. Only six percent believe their data is completely secure based on the password policy they apply.
When asked about the impact of an increasingly digitally-connected world, such as the increased use of mobile devices and tablets on their digital privacy, nearly 70 percent of millennials believe the risk to their online safety will increase -- with 31 percent believing this increase will be dramatic. More worrying is that 54 percent feel the failure of companies and governments to adequately protect identities and data will result in public distrust of their goods and services. A further 44 percent believe there will be an eventual decline in data sharing and 36 percent predicted demands for action. Smaller but still significant percentages of the research group say there is even potential for a decline in economic or political stability.
"It's time for organizations to stop playing fast and loose with what, in a digital economy, are our most important assets -- our identity and our data," says Intercede CEO Richard Parris. "There seems to have been a collective consensus that millennials will accept sub-standard security in exchange for online services. This clearly isn't the case. The humble password should be consigned to the dusty digital archives where it belongs. To restore trust, smart companies need to look to stronger authentication techniques to ensure the future of digital commerce and information exchange and their own competitive edge".
Growing levels of distrust may partly be down to adverse publicity as news of high-profile breaches means people are more aware of the risks. But Parris points out, "Trust is hard to win and easy to lose. There is a tipping point coming soon where the consequences of doing nothing could be severe, yet the technology to resolve trust issues already exists, service providers just need the vision to use it".
Image Credit: Lane V Erickson / Shutterstock
-

Free versions of enterprise streaming analytics platform launches
Publié: août 25, 2015, 5:55pm CEST par Ian Barker

Businesses are under pressure to get applications out quickly and that means they benefit from having real-time streaming analytics as a way of cutting preventable losses, gaining operational insight and uncovering new business opportunities.
Big data specialist Impetus Technologies is helping developers do this by launching free versions of StreamAnalytix, its enterprise-class, streaming analytics platform, based on open source technology components.
It uses a GUI-based platform to allow developers to gain experience, conduct pilots and take a wide range of applications into production. The free versions of StreamAnalytix are intended to address the heightened interest among Fortune 1000 enterprises which want to quickly and easily capitalize on real-time streaming analytics.
The product comes in three flavors, StreamAnalytix Lite is a free, perpetual license to a production ready, unlimited scale, limited functionality version of the StreamAnalytix platform. It's aimed at developers looking to pull streaming data into Hadoop and use a powerful visual toolkit for developing real-time applications based on Apache Storm.
StreamAnalytix Developer is a free, one-year trial of StreamAnalytix Enterprise with all features included and scale limited to a maximum of eight processing cores of Apache Storm. It’s designed to provide maximum power and flexibility for developers to build real-life and complex enterprise applications and perform functional testing before expanding to a full scale deployment.
Finally StreamAnalytix Sandbox offers a free, one-year pre-licensed copy of StreamAnalytix Enterprise limited to eight processing cores, integrated with underlying open source components and pre-packaged in a binary virtual machine format that can be downloaded and used within minutes with no software installation process required other than the sandbox player tool.
"The power to ingest and analyze real-time streaming data at scale is one of the core value propositions of the big data eco-system. We are delighted to unleash that power in an easily consumable manner at no cost to a wide audience with the free versions of StreamAnalytix," says Anand Venugopal, head of product for StreamAnalytix at Impetus Technologies. "StreamAnalytix is being recognized as a leading solution among enterprises and analysts specifically because it offers the power and flexibility of the underlying open source systems along with the usability and manageability features, as well as support and professional services that are critical for enterprises to achieve business ROI through these technologies".
All three versions are available to download from the StreamAnalytix site as is a 60-day trial of the Enterprise version.
Image Credit: Rawpixel / Shutterstock
-

Using social collaboration to deliver better IT visibility
Publié: août 25, 2015, 5:16pm CEST par Ian Barker

For enterprises to stay on top of their IT and in particular to deal with incidents they need to be able to navigate through high volumes of information and work out what’s important.
In order that operations teams can minimize time lost from searching mixed information sources and spend more time on resolving incidents, ops performance specialist PagerDuty is announcing integration with VMware's Socialcast enterprise social collaboration tool.
"During an incident, enterprises must currently navigate through a glut of information sources to resolve issues and maintain uptime," says PagerDuty Vice President of Product Management, Jonathan Wilkinson. "With this integration, we're deepening our commitment to supporting the enterprise and enabling faster and more efficient resolutions".
By linking with VMware, PagerDuty creates an integrated workflow across the tools that IT operations teams are already using. Incidents can be understood and resolved more efficiently with a means to share the data needed to fix the problem and the ability to seamlessly access that information from any device or platform.
"Two-way integration between Socialcast and the PagerDuty operations performance platform sets a new bar in helping our common customers identify and resolve IT issues rapidly," says Bob Schultz, vice president and general manager, Workspace Services, End-User Computing at VMware. "The ability to swiftly communicate about time-sensitive incidents is critical, and our collaboration with PagerDuty will provide our customers an even better solution to resolve issues quickly".
The feature is available now via the Socialcast Integration Store. It will also be demonstrated at next month's VMworld conference in San Francisco.
Photo Credit: dotshock/Shutterstock
-

Clarizen improves visibility into work management
Publié: août 25, 2015, 4:03pm CEST par Ian Barker

Work collaboration specialist Clarizen is launching the latest version of its software aimed at delivering 360-degree visibility at any level of the enterprise, so teams can improve transparency within projects and among users and increase efficiency, accuracy and overall project quality.
Features include pre-built dashboards and reports that provide immediate visibility into projects and company wide effectiveness. New in-context data formatting automatically highlights key problems across all work items, as well as reports based on configurable rules.
An enhanced interactive resource load allows managers to make smarter resource deployment and project approval decisions. New mobile improvements enable team members to stay on top of changes as well as provide updates back to the rest of the team wherever they are.
It allows users to perform 'what if' analysis by filtering work items in or out to understand the impact of demand changes to a resource's workload. They can review the full work plan details on the same page as resource load, and view resource load data with more display and filtering options. Together the package offers a fully centralized resource planning process.
"Better work management starts with better visibility, and the fastest way to visibility is collaboration," says Avinoam Nowogrodski, CEO of Clarizen. "Executives, project managers and team members all need easy access to relevant information, not only to review off-track efforts, but also to properly allocate resources against ever-changing demand. Collaborative work management can only be achieved with visibility within projects and among team members. By simplifying work, businesses can move faster".
Clarizen's summer release is available now at no extra charge to existing customers. For more information visit the company's website.
Image Credit: Tischenko Irina / Shutterstock
-

Xirrus makes Wave 2 easier for businesses
Publié: août 25, 2015, 3:18pm CEST par Ian Barker

Wave 2 Wi-Fi -- otherwise known as 802.11ac -- brings a number of advances to help wireless networks keep up with the increased demand from mobile devices.
Wireless network specialist Xirrus is aiming to make Wave 2 more accessible for business by introducing the industry’s fastest and only customizable Wave 2 Wi-Fi solution.
Xirrus' new Wave 2 access points (XD2) deliver triple the speed of competitive solutions, also allowing vendors to scale based on their specific connectivity needs. It includes two Wave 2 radios each capable of up to 3.47 Gbps, which enables customers to deploy a Wi-Fi network that keeps up with the demand from their environments, and ensures a longer network lifespan.
Other advantages include double the speed of competitive Wave 2 solutions with 7 Gbps per AP, four-stream multi-user MIMO (MU-MIMO) compared to three-stream MU-MIMO supported by other solutions. XD2 is fully customisable with the ability to enable both radios to Wave 2 with the click of a mouse and is also Bluetooth low energy (BLE) enabled for location based services.
"Until the XD2, all Wave 2 Wi-Fi solutions introduced to the market to date have been effectively 'Wave 1.5' because they do not fully support the MU-MIMO standard," says Bruce Miller, vice president of product marketing at Xirrus. "Customers should steer clear of Wave 1.5 solutions and verify they are getting Wave 2 technology in order to deploy the fastest solution available and achieve the best return on their investment".
The company is also launching a low-cost range of X2 access points. The X2 delivers affordable, fast, reliable cloud managed Wi-Fi for the small to medium enterprise, hospitality and education markets.
The X2 delivers 1.2 Gbps of bandwidth per access point, a graphical interface for seamless, simple management, easy one-step, device-agnostic connection, and cloud-based activation to cut down on the need for on-site IT support.
You can find out more about Wave 2 solutions on the Xirrus website.
Photo credit: Shutter_M / Shutterstock
-

Virtual infrastructure means higher recovery costs
Publié: août 24, 2015, 5:59pm CEST par Ian Barker

Businesses may be paying a lot more to recover from security breaches if they're using virtual rather than conventional in-house infrastructures.
According to a study by Kaspersky Lab enterprises pay more than $800,000 on average to recover from a security breach involving virtual systems, which is twice as much compared to incidents involving only physical infrastructure.
The problem affects smaller businesses too. SMBs reported damage of more than $26,000 for an attack on their physical infrastructure. The involvement of virtual infrastructure in a security breach, however, drives the cost up to nearly $60,000.
The main reason behind the additional cost is that many businesses use virtual infrastructure for their most important operations. The survey finds 62 percent of companies use virtualization in some form. As a result, many organizations are likely to entrust virtual environments with critical business processes. While an attack on physical nodes leads to the temporary loss of access to business critical information in 36 percent of incidents reported, this rises to 66 percent when a breach affects virtual servers and desktops. Attacks affecting virtual environments also typically require additional third-party expertise to fix. Businesses have to request help not only from IT consultants, but may also involve also lawyers, risk management experts and others.
The survey found that 42 percent of businesses believe that security risks in virtual environments are significantly lower than in 'physical' ones. In addition, 45 percent of companies report that security management in virtual infrastructures is seen as a problem and yet only 27 percent of businesses have deployed a security solution specifically designed for virtual environments.
"Businesses expect that going virtual will drive down their IT spend and streamline their infrastructure," says Matvey Voytov, Corporate Products Group Manager at Kaspersky Lab. "However, the survey results show us that if there is not enough attention paid to security matters in the virtual environment, expenses may exceed the benefit. Our view is that businesses should use customized, virtual-aware security solutions with centralized management and reporting. The solution should have a low impact on resources, a high detection rate and the ability to spot suspicious activity right away".
The full report is available on the Kaspersky Lab site.
Photo Credit: Andy Dean Photography/Shutterstock
-

Spotify says sorry for confusion over its privacy policy
Publié: août 21, 2015, 4:42pm CEST par Ian Barker
We reported earlier today that streaming music service Spotify had upset a lot of users with changes to its privacy policy. In particular sections concerning what information the company is allowed to collect have sent some users into a spin.
Evidently stung by the reaction, Spotify has been quick to respond. In a blog post by CEO Daniel Ek it says sorry and explains more about what the changes actually mean.
"We are in the middle of rolling out new terms and conditions and privacy policy and they've caused a lot of confusion about what kind of information we access and what we do with it," writes Ek. "We apologize for that. We should have done a better job in communicating what these policies mean and how any information you choose to share will -- and will not -- be used".
He points out that although the policy asks for permission to use information including photos, mobile device location, voice controls, and contacts, Spotify will seek express permission before accessing any data and will only use it to improve the Spotify experience.
Ek gives specific examples of how data might be used, for example on location information, "We will never gather or use the location of your mobile device without your explicit permission. We would use it to help personalize recommendations or to keep you up to date about music trending in your area. And if you choose to share location information but later change your mind, you will always have the ability to stop sharing."
There are similar clarifications for other areas which you can read in full on the blog. Ek says that the privacy policy will be updated in the next few weeks to better reflect how data will actually be used. In the meantime users with concerns or questions can email privacy@spotify.com.
Does this reassure you about what Spotify is up to? Do let us know.
-

How today's work gets done in the cloud
Publié: août 21, 2015, 4:04pm CEST par Ian Barker

In recent years cloud technology has allowed organizations of all sizes and across all industries to become more flexible and more productive.
Identity and mobile management specialist Okta has produced a report based on usage data across more than 2,500 customers and 4,000 apps that sheds light on how organizations and people get work done today, and on what security measures companies use to keep data safe.
"We're seeing companies of all sizes, industries and regions depend on cloud and mobile to propel their businesses forward," says Todd McKinnon, CEO of Okta. "Business leaders are making big investments in cloud and mobile, and Okta's dataset offers some insightful trends into the apps, services and security measures businesses are choosing to leverage".
Among its findings are that company size is no longer a strong indicator of how many cloud or mobile apps a company licenses with a median of between 11 and 16 off-the-shelf cloud apps. There has also been a 40 percent increase year-on-year in companies protecting their sensitive data with multi-factor authentication for at least one app.
Some enterprise apps have maintained their early leadership positions, for example Salesforce.com in CRM, AWS in infrastructure and Box in content storage -- but others have lost ground to the competition, these include Google Apps which is now trailing Microsoft Office 365 in almost every category. Media darling Slack has also done well, increasing its user base by 50 percent in the second quarter of 2015.
The report also finds that businesses are making aggressive efforts to enable their partners, customers and contractors through new cloud-based applications, websites or portals. The number of the external identities in Okta grew by 284 percent from July 2014 to July 2015, while internal identities grew 192 percent in the same timescale.
Companies are also looking at more sophisticated authentication methods. Usage of traditional security questions has dropped 14 percent since April 2014. Businesses increasingly prefer SMS authentication, with usage increasing by eight percent in the same period.
With companies putting a premium on security, developers are increasingly creating apps using the Security Assertion Markup Language (SAML) authentication system from the start. 19 percent of applications that are in the Okta Application Network (OAN) today are SAML-enabled, a six-fold increase over the past two years.
You can get the full Businesses @ Work report from the Okta website.
Photo Credit: RPeshkova/Shutterstock
-

How secure are professional services companies?
Publié: août 20, 2015, 3:56pm CEST par Ian Barker

The number of high profile security breaches in recent years highlights the risk for individual organizations. But what about the risks that stem from other businesses in the supply chain?
Security ratings specialist BitSight has released new data that looks at the overall security ratings of four common business services industries -- law, PR, accounting and benefits administration -- each of which have access to sensitive data.
BitSight scores the performance of companies across different sectors to produce a security rating between 250 and 900, it also looked at the average number of days taken to fix a problem. The benefits administartion sector comes out on top with an industry average score of 740 and a fix time of 1.8 days. Next is accounting with 725 and 1.9. The legal sector only manages a score of 670 but has an impressive remediation time of 1.3 days. PR brings up the rear on 615 and 2.3 days.
The study underlines that businesses need to be aware of which third parties have access to their data, what security measures they have in place and communicate any potential issues.
You can see more information including how the ratings are calculated in the infographic below or on the BitSight blog.

Photo Credit: Alexander Kirch/Shutterstock
-

Lightning strikes four times and Google loses cloud data
Publié: août 19, 2015, 5:01pm CEST par Ian Barker

They say lightning never strikes twice, but they're wrong as Google reports that it's lost some data after the power grid serving one of its European data centers suffered four consecutive lightning strikes last Thursday.
Google Compute Engine (GCE) disks in the europe-west1-b zone data center, located in Belgium, suffered I/O errors in the strikes and 0.000001 percent of disks suffered permanent data loss. GCE allows customers to run virtual machines and store data in the cloud.
It's not known what data was lost or which customers have been affected, but writing on its Cloud Platform status page yesterday Google points out that, "The issue only affected Standard Persistent Disks that existed when the incident began at 09:19 PDT. There was no effect on Standard Persistent Disks created after 09:19. SSD Persistent Disks, disk snapshots, and Local SSDs were not affected by the incident". We understand that customers have been able to successfully recover from Persistent Disk Snapshots and from their own backups.
Google has apologized to affected customers and says that it's working to improve the reliability of its GCE storage layer. However it does say that, "GCE instances and Persistent Disks within a zone exist in a single Google datacenter and are therefore unavoidably vulnerable to datacenter-scale disasters. Customers who need maximum availability should be prepared to switch their operations to another GCE zone. For maximum durability we recommend GCE snapshots and Google Cloud Storage as resilient, geographically replicated repositories for your data".
Fans of Douglas Adams' Hitchhiker's Guide series will know that 'Belgium' is the most unspeakably rude word in the galaxy, customers of GCE now understand why.
Photo Credit: Igor Zh /Shutterstock
-

Syntonic launches BYOD billing management for smaller businesses
Publié: août 19, 2015, 4:39pm CEST par Ian Barker

The rise of BYOD offers businesses improved flexibility and employee productivity, but those things come at a price. BYOD can lead to extra costs such as needing to reimburse staff for air time.
Mobile platform provider Syntonic is launching DataFlex, an operator-independent split billing solution designed to cost-effectively deploy, operate, and manage BYOD usage for businesses of any size.
The solution offers separation of personal from business use on any mobile operator network, including AT&T, Verizon, T-Mobile and Sprint. Syntonic DataFlex can also be easily integrated into any existing expense management platform to streamline employee reimbursement. It can be accessed via a self-service portal for easy provisioning of employee devices with business applications and website access.
"BYOD has transcended the large enterprise and is now regarded as an essential business function for businesses of all sizes," says Gary Greenbaum, Syntonic CoFounder and CEO. "With Gartner anticipating nearly half of all businesses to require employees use of personal devices for work by 2017, it will be imperative for business owners to adopt solutions that help control BYOD costs now. Syntonic DataFlex allows businesses to cost efficiently initiate and scale BYOD programs".
Key features of DataFlex are that it will work with both Android and iOS devices across all mobile operators. It doesn't require any app modifications like SDK integration and it protects businesses with threat detection and encryption even if the employee is using an unsecured network. For managers and accounts teams it offers detailed app-level analytics segmented by employee, department, company, time period, data used and other details to help guide mobile forecasting, budgeting and investments.
You can find out more and sign up for a free trial on the Syntonic website.
Image Credit: Peter Bernik / Shutterstock
-

Executives lack confidence in enterprise security
Publié: août 19, 2015, 12:19pm CEST par Ian Barker

A new survey of security executives at large companies in the US reveals that many don't have confidence in their enterprise security posture. Less than a third of these executives are confident in their organization's security position, and only slightly more than a quarter feel that their communications on security to senior management are effective.
The survey commissioned by Raytheon|Websense shows that many still rely on technology aimed at preventing breaches but do little after one has occurred. Yet 9 out of 10 of the organizations represented in the survey have had at least one breach involving a loss or compromise of data in the past year.
Despite this only a third of the executives surveyed employ qualitative techniques, such as dwell time, that help them understand the state of their network post-breach. 57 percent measure their security position simply by counting the number of breaches.
"With security spending continuing to skyrocket, it is more important than ever to be able to report on metrics that matter, not just quantitative metrics like counting breaches. When breaches are constant, and inevitable, we need a better way," says Ed Hammersla, president of Raytheon|Websense. "We know threats are going to get in. If we want to be more confident, we need to shift our thinking to metrics such as dwell time, or reducing the time a threat is in our network, which reduces damage and helps strengthen our overall security posture".
When asked about metrics used to communicate their security posture, only 28 percent of executives surveyed felt the ones they used were 'Completely Effective'. 65 percent felt the metrics were only 'Somewhat Effective'. Only 33 percent of those surveyed use dwell time (the elapsed time from initial breach to containment) alongside the other more established measurements such as Cost of Incidents (39 percent) and Reduction in Vulnerabilities (39 percent).
Intruders can do more damage to a business the longer they have to poke around and move within the network. The lesson from this research is that if an organization can limit the length of time a threat exists, the damage will be minimized. Enterprises therefore need to employ different detection, analysis, and ejection techniques to stay secure.
More information on the report is available on the Raytheon|Websense site.
Image Credit: Manczurov / Shutterstock
-

The most dangerous places to use your mobile on vacation
Publié: août 18, 2015, 5:39pm CEST par Ian Barker

We all know that using public wireless hotspots can be risky, but is seems that some places are more of a threat than others.
Mobile threat defense company Skycure has put together a study into the most dangerous tourist destinations to use your mobile device, the type of threats you might encounter, and offers some tips on how to avoid falling victim to an attack.
Large city locations dominate the list but Disney theme parks, places where you might expect to feel pretty safe, also feature -- insert your own Mickey Mouse security joke here.
The safest attraction is India's Taj Mahal, though the good karma there is largely down to limited connectivity and a ban on using mobile phones within the monument. The safest destination in the US is the Great Smoky Mountains national park in Tennessee, again largely because it's hard to get a signal.
The research also finds that Android devices encounter network related threats almost twice as often as iOS devices. Even though iOS devices connect on average to more Wi-Fi networks, Android devices manage to connect to more threatening ones.
"Unfortunately for mobile tourists, the most magical places on earth can sometimes be the most dangerous," says Adi Sharabani, CEO of Skycure. "When you’re in a high-traffic area like these famous destinations, you're a target for hackers. Unlike your computer, your phone is always on, even when you're taking in the sights. Mobile tourists are a lucrative target for cyber criminals".
The most frequent threat comes from SSL decryption attacks, which allow cyber criminals to capture personal and work information like logins, passwords and corporate credentials even when the user thinks they're secure. The research also revealed cases of SSL stripping, which downgrades secure URLs (https) to non-secure URLs (http). Like SSL decryption attacks, this allows hackers to gain access to private information and communication while the user thinks they're safe.
To protect yourself, Skycure suggests avoiding networks with 'Free' in their name, eight percent of the total reported threats originated from these. You should also read the warnings on your device and don’t continue if you’re not comfortable with the exposure. You should also ensure you have the latest updates on your device and use a mobile security app. If your phone begins to behave oddly you should disconnect immediately.
You can see the list of the riskiest and safest destinations in the infographic below. You can also check for threats in your area using Skycure's interactive map.
Photo Credit: William Perugini / Shutterstock
-

Wombat Security helps employees report phishing attacks
Publié: août 18, 2015, 4:03pm CEST par Ian Barker

Phishing is a popular route for cyber criminals to gain a foothold in organizations as the weakest link in security is usually the person sitting at the keyboard.
To help combat this Wombat Security is adding a new PhishAlarm to its security awareness and training platform. PhishAlarm is a plug-in for Microsoft Outlook that enables end users to report suspected phishing emails to security and incident response teams with a single mouse click.
The software reinforces the right actions that are key to achieving long term behavior change and protecting organizations from attack. It simplifies the reporting process and therefore shortens the time it takes information security analysts to recognize and respond to phishing attacks. PhishAlarm also provides positive behavior reinforcement by immediately thanking end users (via a pop-up message or email) for reporting suspected phishing emails and encouraging them to continue those actions in the future.
"Future versions of PhishAlarm will give security officers enhanced intelligence to quickly act on phishing attacks as they are reported," says Joe Ferrara President and CEO, Wombat Security. "We continue to keep the needs of security officers as a driving force behind our solutions. Wombat's best-of-breed security education solutions, including our anti-phishing products, are appreciated by our customers because of their effectiveness and ability to deliver results for the organization".
You can find more information on Wombat's security and phishing awareness products on the company's website.
Image Credit: Maksim Kabakou / Shutterstock
-

Private clouds for VMware customers made easy
Publié: août 18, 2015, 1:42pm CEST par Ian Barker

VMware vSphere is the world’s leading virtualization platform, estimated to run on more than six million physical servers in businesses. But enterprises looking to implement private clouds often turn to OpenStack and up till now this has had limited support for vSphere.
Cloud specialist Platform9 has an answer with the general availability of Platform9 Managed OpenStack for VMware vSphere environments. This is a SaaS solution that transforms an organization's existing servers into an AWS-like agile, self-service private cloud.
"Platform9's mission is to make private clouds easy to deploy and manage for the enterprise. By fully supporting VMware vSphere, we are enabling every VMware customer to instantly derive greater value and infrastructure agility from existing virtualized infrastructure," says Sirish Raghuram, Co-founder and CEO of Platform9. "Customers no longer need to choose between the world's leading private cloud platform (OpenStack) and the world's leading virtualization platform (VMware vSphere): Platform9 Managed OpenStack is 100 percent interoperable with VMware vSphere, allowing customers to integrate OpenStack and vSphere seamlessly. Developers can have self-service provisioning using OpenStack while at the same time, IT Operations manages the underlying infrastructure using vSphere".
Using a SaaS delivery model Platform9 Managed OpenStack not only makes it easy for IT to quickly deploy an OpenStack private cloud but also provides ongoing operational support by including monitoring, troubleshooting and updates for OpenStack. It fully supports VMware vSphere environments and a new VMware specific Virtual Appliance is now available to integrate the OpenStack controller services with vSphere resources.
It offers self-service automation making life easier for developers, support for OpenStack APIs, a single pain view with KVM and VMware vSphere virtualization. Docker support is in development with a beta expected later this year. Platform9 takes care of monitoring, troubleshooting and upgrading the OpenStack framework, ensuring customers have a reliable production environment.
Platform9 Managed OpenStack is available now and there's a free trial available on the Platform9 website.
Photo credit: Maksim Kabakou / Shutterstock
-

FixMeStick: Eliminating malware with a USB drive [Review]
Publié: août 17, 2015, 8:06pm CEST par Ian Barker

We all know that virus infections are a pain, not only do they disrupt your work they can also be hard to remove as they often prevent you from downloading or running cleanup tools or even from accessing Windows.
If you don’t have access to a friendly geek with the right tools you can be faced with hours of work or even having to wipe out and reload your machine.
Now there’s a solution in the form of FixMeStick. It’s a USB stick that removes viruses and infections from both Windows PCs and Macs. It follows the same process that professionals do by running multiple scanning tools to increase detection rates and operating outside the machine’s normal operating system to prevent interference.
How It Works
The FixMeStick is a bootable drive so if your BIOS is set to start from USB you can just plug it and switch on the machine. Alternatively you can plug it in while the operating system is running and it will read your Wi-Fi details so it can get online and then force a reboot. After booting it will update itself over the Internet -- you’ll need to enter your wireless details if you didn’t run it in Windows first -- and begin a scan.
Depending on the size and condition of your machine scanning may take several hours to complete. It uses three anti-virus engines, Sophos, Kaspersky and GFI Vipre to ensure that it has the best chance of finding all infections. There’s a custom scan option for advanced users that allows you to restrict the scan to specific disks or files if you want to.
When the scan is complete you get the opportunity to review the detected items before removing them to quarantine. After booting back to Windows you’re presented with a browser page giving contact details should you want to follow anything up, though the phone number supplied is in Canada. The important thing to note here is that it only quarantines files, it won’t repair infected system files so if a key Windows file gets canned you might find your system won’t boot and you need that support. It doesn’t remove virus traces from the registry either, you’ll need to scan with another product to do a complete clean up once FixMeStick has got you up and running again.
FixMeStick copies itself to the hard drive and leaves a quarantine folder there too so you can get back any files that have been wrongly removed. It sends you an email too with a link to view your scan results via an online portal.
FixMeStick costs £45 which allows you to use it on three machines for a year -- you need to specify whether it’s for PC or Mac when you order. After that you can reset it for £37 to give you a further year’s use. There’s a pro version available which gives use on unlimited numbers of machines for a year costing £200.
Is It for Me?
So, should you buy one? There are of course plenty of free bootable rescue discs available to download but they’re generally not easy to use. FixMeStick is. If you’re not confident with using conventional anti-virus tools or creating rescue disks then FixMeStick provides a fully automated scan and it’s cheaper than paying a specialist to clean up your machine. You get access to email and telephone support should you need it too.
It isn’t intended to be a complete solution and there’s no long-term protection. However, it will get a heavily infected machine working again so that you can complete the clean up with a conventional installed antivirus product.
Not for experienced PC wranglers then, but as a get-out-of-jail card for non-techies it’s hard to beat. You can find out more at the FixMeStick website or click the button below to get one for yourself.
Pros
Easy to use
Multiple scan engines
Access to supportCons
Quarantines infected system files
Doesn’t remove registry traces
No ongoing protectionCompany Release
PriceITProPortal
ReviewLatest Prices FixMeStick £45 7/10 $58.99 Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Silver underpants protect your family jewels from Wi-Fi radiation
Publié: août 17, 2015, 4:05pm CEST par Ian Barker

More and more of the devices we use these days rely on wireless signals for their connectivity. If you're male you quite likely carry your smartphone in your trouser pocket or use your laptop or tablet on your knee, which means these signals are being transmitted in close proximity to your gentleman's area.
Should you worry about this? A 2014 study by the University of Exeter suggests that just one hour's exposure to radiation from a mobile phone can reduce in vitro (outside the body) sperm motility to 49 percent and viability to 52 percent. In addition the World Health Organization has classified electromagnetic radiation in the same category of harmfulness to humans as petrol exhaust fumes.
So, short of going back to wired connections or lining your trousers with tin foil what can you do? A British scientist has come up with a solution in the form of underpants made with silver. By using a mesh of pure silver woven into fabric the pants claim to shield against 99.9 percent of harmful electromagnetic radiation (EMR) emitted by Wi-Fi devices.
For people of a certain age the mention of silver underpants will probably bring to mind the scene in Dune where Sting emerges from the shower in a rather disturbing pair of budgie smugglers and an even scarier ginger hair do. But fear not, Wireless Armour uses silver threads woven into the cotton so you won't look like you're wearing a cast off from NASA.
"Like so many people, my smartphone and laptop use has increased dramatically in recent years which made me realise that I was exposing myself to large amounts of electromagnetic radiation, mostly centred on my groin," says London scientist and Wireless Armour inventor, Joseph Perkins. "With my physics background I knew there must be a way to shield from electromagnetic radiation using a simple solution. Wireless Armour has been tested by an industry leader in wireless shielding and the results show that our fabric shields against 99.9% of the radiation emitted between 100MHz to 2.6GHz. Put simply, this covers the entire range of radiation emitted by wireless devices, from voice and text through to 4G and Wi-Fi, almost everything is blocked."
Silver has the added advantage of being anti-microbial so you'll end the day fresher and more hygienic as well as being protected against wireless emissions.
At between £24 and £35 ($37 to $55) a pair from the company's website Wireless Armour undies aren't cheap, but what value do you place on your fertility?
-

IBM launches Linux-only mainframes for enterprises
Publié: août 17, 2015, 3:41pm CEST par Ian Barker

IBM is making a serious bid for a slice of the enterprise Linux market with the launch of a new range of mainframe servers called LinuxONE.
At the top end of the market is LinuxONE Emperor, a machine based on the IBM z13 and which can scale up to support 8,000 virtual machines or thousands of containers. It also delivers the security and advanced encryption features needed by large enterprises.
For the entry level market there's also LinuxONE Rockhopper. This is aimed at customers who need the speed, security and availability benefits of a mainframe but in a smaller package.
Big blue says that the LinuxOne system will work with open source software including Apache Spark, MariaDB, PostgreSQL and Chef. It's also announced a partnership with UK-based Canonical to distribute its Ubuntu open source OS software on LinuxONE and z systems.
All of this is backed up by a LinuxONE Developer Cloud which provides a virtual research and development engine for creating and testing new applications, and generating links to mobile apps, hybrid cloud apps and more.
More information about LinuxONE is available on the IBM website.
-

Solving the enterprise storage management problem [Q&A]
Publié: août 14, 2015, 3:37pm CEST par Ian Barker

Many companies would like to use the cloud as a new approach to storage management, but it isn't without problems. High latency, unpredictable performance of internet transport and fear of data breaches may make the public cloud services unsuitable for many production applications.
We spoke to Ellen Rubin, CEO and founder of enterprise storage startup ClearSky Data to find out how enterprises can address these issues and get their cloud storage projects moving.
BN: What proportion of enterprises are using cloud storage solutions, and how will changes in enterprise needs drive storage-as-a-service?
ER: There is a chronic, incredibly expensive problem in the enterprise data center. It stems in part from the longevity of data. Enterprises have data buried in files, databases, emails and other places where it sits -- basically -- forever. That data is used in varying degrees depending on its timeliness and value to the enterprise, but no one ever wants to throw anything away, so the data center footprint keeps growing.
As enterprises struggle with that scenario, we hear a variety of numbers suggesting IT's approach to managing growing data stores. At the end of 2014, 451 Research said 32 percent of enterprises were using the public cloud and 39 percent had hybrid infrastructure in place. Enterprises like the idea of extending their data centers out to the cloud. Even more attractive is the potential for managed cloud -- being able to tap into an enterprise-class storage-as-a-service offering that takes the weight off their data centers and infrastructure teams. They want all the things that are great about the cloud, but they need the hybrid storage management aspect to protect them from security concerns as well as performance and latency issues. There is the potential in the market now to challenge the long-standing enterprise storage status quo, and the service aspect will be key to that disruption.
BN: What is the biggest concern for enterprises wary of straying from the traditional approach to storage?
ER: We see the answer to that question in every industry survey. The main hesitations about cloud storage adoption are control and security. Companies want the scalability, agility and economics of the cloud, but they worry about losing the control they feel with local enterprise storage. Because of that, enterprises are making their way to the cloud with Web apps or test and development workloads. If they could mitigate concerns around control and security issues, enterprises could shrink the expense and complexity in their data centers while improving performance.
BN: Data security is a major concern for enterprises that use cloud storage, how can that issue be addressed?
ER: The major cloud providers have made significant strides in meeting enterprise security concerns over the past few years, but there are still several issues to address. The most critical ones are around data encryption and key management – these are table stakes for putting data in the cloud. A managed service provider (MSP) can address these issues upfront for enterprises, as well as provide many other requirements, such as third-party audits, operational controls, background checks and more.
BN: Is there a cost benefit to having storage in the cloud? How does that vary based on the amount of data a company creates?
ER: There is a huge cost benefit to putting archival, backup and cold data in the cloud and leaving it there. That kind of storage is dirt cheap. But -- and this is a big but -- it's not cheap to pull that data out of the cloud and use it in a production-ready way. Plus, there is unpredictable performance and a level of latency that is unacceptable for most production applications. The amount of data enterprises create isn't the point. The cloud is endlessly scalable -- if they want to put a ton of petabytes in the cloud, they can go ahead. However, the speed and performance required for enterprise apps needs to be addressed.
BN: What are the biggest misconceptions surrounding enterprise storage?
ER: Enterprise IT teams believe they have no choice but to invest and reinvest in data center infrastructure every few years as their data stores grow and technology changes. They are stuck on a commodity storage treadmill.
Secondly IT teams often view new platforms as cure-alls for storage headaches, but if enterprises are going to become more agile, they'll have to focus on something different: managing their data more effectively as it cycles through the hot, warm and cold lifecycle stages.
Also some label the public cloud as a panacea for storage management, but enterprises have security and control questions about the cloud, and performance and latency are also barriers. There are unavoidable latency issues around moving data between clouds and across complex networks that span hundreds or thousands of miles. Fixing this will require the help of service providers with regional resources and the ability to help enterprises maintain the performance levels their users demand.
MSPs and enterprises need to partner with companies that are focused on helping them overcome these market challenges.
Photo Credit: fbmadeira/Shutterstock
-

The best value breach detection systems
Publié: août 13, 2015, 1:07pm CEST par Ian Barker

Given the current threat landscape and the fact that attackers are finding new ways to bypass traditional security, it's no surprise that many companies are turning to the use of breach detection to protect their systems.
Independent testing organization NSS Labs has evaluated eight of the leading BDS vendors -- BlueCoat, CheckPoint, Cisco, Fidelis, FireEye, Fortinet, Lastline, and Trend Micro -- for security effectiveness, performance, and total cost of ownership.
The security effectiveness test looked at detection rate, anti-evasion capabilities, device stability and reliability and time to detect. Cisco came out on top with a 99.2 percent overall effectiveness score with Trend Micro second on 96.2 percent, Checkpoint and Lastline tie for third on 95.9 percent. Worst performer is FireEye on 51.8 percent.
Assessed on performance, BlueCoat and Fidelis both offer higher throughput rates. The front runners for detection all have similar throughput rates with FireEye again bringing up the rear. Lastline lags behind the others for devices with 4.5 and 1.7Kb responses, but on 'real world' traffic patterns it's on a par with Cisco, Trend Micro and the others.
Looking at total cost of ownership (TCO) BlueCoat comes out on top at $50 per protected Mbps followed by Fortinet on $76 and Lastline on $106. Cisco does less well here with a TCO of $228 per Mbps. FireEye again brings up the rear on $541 thanks to its lower throughput rates.
NSS also calculated a Security Effectiveness value indicating whether a product is underpriced, overpriced, or priced accurately depending on the performance and overall security effectiveness. A product with a Security Effectiveness value that is higher than its purchase price can be considered good value for money. Looked at in these terms the top four are BlueCoat, Fortinet, Lastline and Fidelis.
The full reports are available for NSS Labs subscribers. You can download a security value map with an overview of the findings free from the NSS website.
Image Credit: Balefire / Shutterstock
-

Understanding Windows 10 update options for business
Publié: août 13, 2015, 11:53am CEST par Ian Barker

One of the big under-the-skin changes Windows 10 has made is the way it updates, thanks to Microsoft's new system of continuous updates.
For businesses this presents a problem as there may be some parts of the update process they'd rather opt out of.
There are options to allow IT managers to control the update process and Deepak Kumar, CTO and Founder of systems management company Adaptiva has put together an infographic explaining the differences.
Aside from the Current Branch which home users get, there are essentially two options for enterprises. Current Branch for Business (CBB) which allows IT managers to install security updates immediately but delay new features and bug fixes. The alternative is the Long Term Servicing Branch (LTSB) option which gives them the flexibility to put off the installation of new Windows 10 features for up to 10 years.
You can see the different branches explained in the infographic below.

-

How can businesses get the best from remote working? [Q&A]
Publié: août 12, 2015, 6:01pm CEST par Ian Barker

The days of spending all of your working hours in a single office location are increasingly behind us. Both employers and staff are demanding more flexible solutions. Add to this a new generation of millennial workers demanding a better work/life balance and it’s clear that enterprises need to deliver on new ways of working,
But how can they do this and what effect does the change have on corporate culture? We spoke to Rickard Hansson, founder and CEO of enterprise collaboration specialist Incentive, to find out.
BN: What's driving the demand for more remote working?
RH: Several things, actually. First, I would say the way people in general get stuff done nowadays. Everything is a finger tap away -- your "computer" is in your pocket. What everyone realizes and experiences is that they can get stuff done -- everywhere and any time -- so why not when it comes to work? And this has finally reached the C-level as well, meaning they have also discovered this in their own lives and are therefore more open to implementing it in the workplace.
Second, it's the need for work/life balance -- picking up kids, waiting for the service technician, etc. Getting control of your time gives you more time. And if you can get the same amount of (or often more) work done from home, why not do it? This is very tied into trust from management, of course, and dependent on the culture in the workplace.
Third, I would say is the need for "focus time". An office space can often be the most disruptive place you can be when you really need to focus on that report or preparing that presentation. I make it a habit to work from places other than the office -- a coffee shop, a startup incubator, etc. I always have my co-workers there, but I can still keep in touch and interact through our social intranet.
BN: What benefits can remote working bring for the enterprise?
RH: Some -- if not most -- enterprises have no choice working remotely with a distributed workforce in multiple offices around the country or world. Remote working is often translated into working from home, but remote working is really everything you do when you're out of the office or not in the same office as others.
If you succeed with remote working across the board, your enterprise will be better on every level. Cross-communication between departments will be improved, you will be more responsive when you have access to all knowledge and information all the time -- you can even get stuff done when you're stuck in your two-hour commute.
BN: Doesn't having people working remotely mean missing out on opportunities for in-house collaboration?
RH: You can NEVER replace the human meeting, especially when you need to work as a team. We do it all the time. We have offices on the West and East Coasts and one office in Sweden.
I fly to Sweden and the East Coast every five weeks or so, then I fly over people from the other offices to LA on a regular basis. The meetups are for what I call "focus sessions" -- issues we need to discuss in-depth and sort out so we can create a roadmap for the next 5-6 weeks. In between the meetups, remote working is a wonderful way of continuing the work. It maximizes the value and outcome of your focus sessions continuing your work through your social intranet using video chats, instant messaging, document collaboration, file sharing and more -- you just pick up where you left off, seamlessly.
BN: How can the corporate environment adapt to be viable regardless of employee location?
RH: This is always tricky, but it's something many businesses have been dealing with successfully for ages. Enterprises should create a strong foundation and policy for remote working, and not just about security and codes -- there has to be more focus on the people and the social layer where people can connect on mutual (business) interests instead of just finding people based on their title on the business card or hierarchy charts.
If remote workers are already implementing the social part, meaning employees are connecting and collaborating regardless of their location, you can easily weave it into the business' core values and culture.
BN: Doesn't reliance on the cloud for collaboration lead to additional risks for the business?
RH: The reality is you need the cloud to be truly remote. Even if you have everything on premise, you need VPN and therefore you are dependent on a carrier -- the Internet. So the cloud is always going to be there, whether you like it or not.
Instead of worrying about the cloud itself, focus on the services you are using and what control you have over them. Most breaches you read about aren't the cloud per se -- it's the service, and most services are in a multi-tenant environment. That means all data is stored in the same location for all customers and the only thing that differentiates one customer from another is a key in the database. The risk here is hackers can get in and find the "master key" to dump all the data.
Enterprises should look for single-tenant solutions with multi-tenant capabilities. The advantage of multi-tenant solutions is the never-ending stream of new features and upgrades that happen automatically. There are single-tenant solutions that have that same capability. In fact, many people will probably be reading this on a device that is single-tenant but still updated: the OS.
With single-tenant, you're in control of your data -- where it's stored and geographically located. You can have it on premise or in the cloud -- it's all up to you.
Image Credit: Dragon Images / Shutterstock
-

Script injection vulnerability leaves Salesforce users open to phishing attacks
Publié: août 12, 2015, 5:58pm CEST par Ian Barker

A script injection vulnerability in the popular Salesforce cloud CRM system could have left users open to attack from phishing emails that appear to come from within a trusted domain.
Cloud application security specialist Elastica has released details of the vulnerability -- disclosed to Salesforce in early July -- which opened the door for attackers to use a trusted Salesforce application as a platform to conduct phishing attacks to steal end-users' login credentials and hijack accounts.
Though it was considered to be a low-impact threat because it existed in a sub-domain rather than the main Salesforce domain, Salesforce patched the vulnerability on August 10, a finding validated by Elastica researchers.
The flaw enabled attackers to execute JavaScript to steal cookies and session identifiers, which could have led to a potential Salesforce account takeover depending on Same Origin Policy (SOP). They could also force Salesforce users to visit phishing sites to potentially extract credentials via social engineering tricks. Attackers could also have injected pop-up windows to facilitate phishing attacks or forced users to download malicious code on their machines by executing unauthorized scripts in the context of the browser running a vulnerable application.
"Exploitation of XSS vulnerabilities is among the most prolific methods of Web application hacking today," says Dr. Aditya K Sood, lead architect of Elastica Cloud Threat Labs. "Although this particular flaw was only present in a Salesforce subdomain, exploiting the trust of the company's primary domain could have allowed attackers to easily implement phishing attacks to gain access to user credentials. With stolen credentials, attackers can then access users' accounts and exfiltrate sensitive data undetected for long periods of time".
You can find a detailed analysis of the flaw and how it could be exploited on the Elastica blog.
Photo Credit: Ivelin Radkov/Shutterstock
-

Malvertising becomes a billion dollar problem
Publié: août 12, 2015, 3:45pm CEST par Ian Barker
According to a new report by endpoint security specialist Invincea malvertising is causing more than $1 billion worth of damage each year.
Based on data gathered in the first six months of this year the company detected and blocked approximately 2,100 malvertising attacks against its customers, representing 2.1 million malicious advertisements. Invincea estimates this caused $525 million of damage in repair and recovery expense, excluding the impact of any data breaches.
Other trends identified include the emergence of just-in-time (JIT) malware assembly. This technique builds malware executables on targeted machines, using native Windows utilities from those machines to assemble their malicious payloads. JIT malware is able to bypas filters and sandboxes that look for complete malicious executables in network traffic.
Microsoft Office files are also being used by multiple criminal gangs via weaponized documents sent in spear-phishing emails. Adding a new twist to malware delivery via e-mail attachments, adversaries are using Visual Basic scripts available on Pastebin and elsewhere to flexibly adapt weaponized documents to distribute malware payloads.
It also highlights that recent spear-phishing initiated attacks against the White House and health insurer Anthem shared key common attributes. In each case, employees were lured into clicking on malicious content that enabled the threat actors to gain a crucial foothold on the targeted networks. The malware employed in each attack was also similar, although customized to avoid detection by traditional security tools.
"Our latest research shows the relentless innovation of threat actors' techniques that in turn highlights the inadequacy of most organizations' network defenses. This is consistently leading to intellectual property loss, costly remediation, loss of employee productivity, and reputational harm," says Invincea Founder and CEO Anup Ghosh. "The endpoint is today the pivotal battleground in security, as both traditional anti-virus and newer network security controls are blind to now common attack techniques used in pervasive cyber-crime, industrial espionage, and nation-state campaigns".
More details are available in the full report which can be downloaded from the Invincea website.
Image Credit: Sam72 / Shutterstock
-

LastPass switches to freemium model to encourage take up
Publié: août 11, 2015, 4:55pm CEST par Ian Barker

With increasing numbers of credentials being stolen in data breaches it makes sense to use a password manager to protect your online accounts.
Popular password manager LastPass is encouraging users to make the leap by making its service available free on mobile devices, including smartphones and tablets from today.
The new version also enables first-time users to sync data across the same device type they get started on, without needing to upgrade to LastPass Premium. Users can still choose to get started with LastPass on a desktop or laptop computer if they prefer.
"People often hear about useful apps on the go and want to get started right away from their smartphone," says Joe Siegrist, CEO of LastPass. "This new freemium model allows LastPass users to get started with our password manager on the device of their choice".
Whatever device users choose to get started on, they can use LastPass on that device and any others of the same device type -- desktops, smartphones or tablets -- for free. With this latest change, LastPass is making it easier and more affordable for people to organize their digital lives and improve overall online security.
To sync across an unlimited number of devices, including desktops, laptops, smartphones and tablets, users can upgrade to the LastPass Premium service, which comes with a free 14-day trial and costs $12 per year. You can get started by downloading the free version from the LastPass website.
Photo credit: shutteratakan / Shutterstock
-

New platform helps bring APIs and apps to market faster
Publié: août 11, 2015, 4:33pm CEST par Ian Barker

IT departments and developers are under increasing pressure to support innovation at a much faster pace. This requires agility but also the needs to meet governance requirements and allow people both inside and outside IT to build cross-platform apps that conform to best practices and standards.
Digital transformation specialist AnyPresence is launching a new platform that offers a comprehensive solution for API-driven enterprise app development and enabling the Internet of Things.
"We see increasing demand for enterprise IT to support digital transformation and innovation initiatives at a much faster pace, creating challenges balancing agility and governance," says Anirban Chakrabarti, CEO of AnyPresence. "This requires proliferation of microservices and empowering anyone within or outside IT to build cross-platform apps that conform to IT governance standards and best practices. The latest release of AnyPresence goes beyond typical MBaaS capabilities to meet these needs by enabling rapid API development, direct connectivity to APIs from client SDKs, and generation of IT-sanctioned app starter kits from any web portal".
Key features include Smart SDKs that can connect directly to REST web services without going through a backend server. This allows developers to have the benefits of client-side SDK acceleration by connecting directly to any API gateway, which can then pass the call on the AnyPresence backend server as required.
Integration Kits are pre-configured components that can be used to enable specific functionality such as connecting to an IoT hub, or implementing business logic such as an approval workflow. Customers can use integration kits as either a starting point to build an app, distribute as best practices via an app template, or as a working example of how to meet specific enterprise requirements.
A JustAPIs feature supports endpoint connectivity to Microsoft SQL Server databases, and adds an API Workflow Test Console to improve developer productivity. In addition AnyPresence now provides faster integration to virtually any enterprise data source via powerful connectors and authentication adaptors. Legacy or custom web services can be easily transformed into RESTful APIs within the AnyPresence Designer, minimizing the amount of code that needs to be created and maintained.
Support IT governance and policies is provided via a detailed history of all user actions on app definitions made within the AnyPresence Designer.
You can find more information about the latest version on the AnyPresence website.
Image Credit: Stokkete / Shutterstock
-

How the cloud is changing the role of IT admins
Publié: août 11, 2015, 3:18pm CEST par Ian Barker

The shifting of systems to the cloud has an effect on many areas of the enterprise, not least IT. The role of IT professionals is beginning to enter new territory.
In the latest of its Trends in Cloud IT series automated management specialist BetterCloud looks at how the emergence of the cloud is altering perceptions. It's freeing up valuable time that cloud IT admins are using to become proactive decision makers in their organizations, rather than simply reacting to problems.
Based on data collected from more than 1,500 IT professionals the report finds that the average cloud IT admin has 15 years experience and two certifications. Of Google Apps admins 13 percent have Certified Administrator status and seven percent are Google Apps Deployment Specialists. In Office 365 shops 19 percent of admins have a Certified Solutions Expert (MSCE) qualification and 15 percent Certified Solutions Asociate.
Other findings are that cloud IT admins are substituting routine work with a wide variety of strategic and proactive tasks such as improving security, end-user training and application integrations. Regardless of organization size or admin experience, around 25 percent less time is being spent on routine maintenance tasks and 20 percent less on storage management.
Office 365 and Google Apps admins are similarly involved in their companies' migrations to cloud office platforms, with the majority of migrations happening in house (67 percent vs 68 percent). Office 365 admins are managing multiple cloud office systems more often than Google Apps admins (47 percent vs 24 percent).
"With cloud adoption set to rise in the coming years, cloud IT admins need to prepare themselves for the changes to come -- especially as they become significant decision makers within their organizations. For some, these new roles are already taking effect, for others, change will come more gradually," says founder and CEO of BetterCloud David Politis. "But for every IT admin, the cloud has the potential to expand their roles and reverse the 'cost center' perception that IT departments often wear like a scarlet letter".
As cloud adoption increases admins will need to gain the skills, and tools, necessary to manage a wide variety of cloud applications, regardless of where their organization sits on the adoption curve. They're also likely to become more influential within their organizations meaning that businesses with strong cloud skills will gain a competitive edge.
You can read more about the findings on the BetterCloud blog.
strong>Image Credit: ND Johnston/Shutterstock
-

84 percent of enterprises have considered encrypting all sensitive data
Publié: août 11, 2015, 1:59pm CEST par Ian Barker

Security professionals are naturally concerned with protecting sensitive data within their organization and elsewhere, particularly given the increasing numbers of threats.
A new survey of more than 100 information security professionals by data security specialist Vormetric and risk management research organization IANS reveals that 84 percent of respondents had considered a security strategy of encrypting all their sensitive data.
The top reasons given for encrypting information include preventing data breaches, cited by 66 percent, fulfilling compliance or audit mandates (54 percent) and protection of financial and other assets (53 percent).
Respondents to the survey are keen to implement encryption to solve problems with securing information held in databases, laptops, emails, private clouds and big data environments. 54 percent say that their top challenge when implementing encryption is legacy technology and support for encryption. Other roadblocks include the cost of encryption technology (52 percent) and worries about performance impact (44 percent). But interestingly, and in spite of these pain points, a massive 84 percent of respondents have considered a security strategy of 'encrypt everything'.
"Not only are perceptions of difficult and expensive implementations outdated, but encryption now also enables business velocity and advantage," says Vormetric's VP of Global Marketing, Tina Stewart. "Modern encryption solutions enable organizations to not only safeguard traditional applications, but also to take advantage of cloud, SaaS services, IoT and big data without incurring new risks to data. As a result, encryption in now a critical driver of lower operational costs as well as the rapid development new services and offerings for competitive advantage and market expansion".
The full report is available to download from the Vormetric website.
Image Credit: Maksim Kabakou / Shutterstock
-

European retailers rush to go digital for a competitive edge
Publié: août 10, 2015, 2:58pm CEST par Ian Barker

Perhaps more than any other type of business, retailers are always keen to gain an advantage over their competitors. A new study by IDC suggests that they're increasingly turning to technology in order to stay ahead.
It reveals that 64 percent of retailers in Western Europe are currently undertaking some form of digital transformation effort while 21 percent are planning to do so by the end of the year.
Among other findings are that it's essential for retail companies to have a single view of core data elements such as orders, customer details, and inventory. They are expected to strongly focus on these areas, a view backed by the high percentage of new investments in them.
Retailers are increasingly seeking to add digital elements to their physical stores, though there's no single way to achieve this objective. Western European companies are prioritizing two areas of investments -- empowering sales associates with mobile capabilities and replicating personalized online engagements in-store.
IDC expects to see considerable investments made in the eCommerce space. The technology and business situation is rapidly evolving and pushing retailers to add more advanced capabilities to their traditional eCommerce platforms. However, they're also expected to embrace mobile commerce to optimize customer experience.
There's a challenge for retailers to fulfil complex customer order requirements across multiple platforms and customer interfaces. This is expected to trigger a wave of new investments to provide the capabilities needed.
"As retailers in Europe seek new ways to differentiate themselves from the increasing competition in the region, digital transformation is a train they cannot afford to miss. Today, all the top Western European retailers are in the process of determining how digital impacts them and what their digital transformation approach and strategy should be," says Luca Bonacina, senior research analyst, IDC Retail Insights.
The full report Digitally Transforming Retail Businesses: The Western European Perspective is available from the IDC website.
Image Credit: Hasloo Group Production Studio / Shutterstock
-

Stay in control of your privacy in Windows 10
Publié: août 7, 2015, 5:05pm CEST par Ian Barker

Over the past week and a half many thousands of people worldwide will have taken the plunge into Windows 10. But, as we've previously pointed out the free upgrade comes at a price in terms of privacy.
So what can you do to enjoy the advantages of Windows 10 without giving away too much of your information? Here are some tips to help you protect your details.
Installation Options
If you’re yet to install Windows 10 you’re probably keen to get started, but don't just accept the Express Settings option in a bid to be up and running as soon as possible. The Express option allows the OS to share speech, typing, contacts, calendar, and location data and advertising ID information to Microsoft and its partners. If you choose the Custom install option you can turn most of these off to guard your privacy. These can also be turned off later from Settings, Privacy, General.
Stop Sharing Updates
As we pointed out last week Windows 10 will try to use your network connection to share updates with other systems. This uses a P2P-type system called Windows Update Delivery Optimization (WUDO). To stop this open up Settings and click Update & Security. In the Windows Update section on the left select Advanced options and click Choose how updates are delivered. You can switch off WUDO by flicking the toggle switch to the Off position. Or if you have other PCs on your network you can continue to share updates with these but not with the outside world by leaving this toggle in the On position and selecting PCs on my local network.
Cutting Feedback
If your system or a piece of software you're running crashes, the OS will send diagnostic data back to the software vendor. There's a risk that these could include memory dumps which contain personally identifiable data. You can't stop Windows sending these reports but you can reduce the amount sent by going to Feedback & diagnostics from Privacy settings and changing the Diagnostic and usage data drop-down to Basic.
Taming Cortana
Windows 10's digital assistant might look nice and friendly, but in order to be responsive to your needs it uses machine learning. This means Cortana can snoop into your emails and contacts, if you’d rather it didn’t do this turn the assistant off. To do this go to Settings and select Privacy, Speech, Inking & typing and then click the Stop getting to know me button.
Keep It Local
Microsoft is very keen to get you to sign in using a Microsoft ID so that you can synchronize information with other machines, but doing this means some of your details will be stored in Microsoft's cloud. It is still possible to use a local ID to access Windows 10 but in order to do so you need to have your internet disconnected during installation up to the point where you're prompted to create a Microsoft account.
Limiting Account Information Sharing
By default Windows 10 will happily share some of your account details, including your picture and your name, with third-party apps. You can stop this from happening in the Account Info section of Privacy settings.
Photo credit: Anton Watman / Shutterstock
-

Over half of UK smaller businesses spend less than 2 percent of their IT budget on security
Publié: août 7, 2015, 12:20pm CEST par Ian Barker

Smaller businesses often have a limited budget for securing their IT systems which can leave them uniquely vulnerable. Antivirus company Avast launched its free Avast for Business cloud offering aimed at SMBs earlier this year and has been surveying users to find how they handle their security.
Among the findings are that almost three-quarters of respondents say that all of their employees use the internet. Yet despite the high number of data breaches 57 percent of SMBs in the UK invest only between zero and two percent of their IT budget on security.
There's little consistency in who handles security either. One out of 10 said respondents say that an employee who isn't a dedicated IT admin handles the company's IT support services. Almost half have an in-house technician, 10 percent have an external supplier or technician to handle the company's IT support services and 28 percent of SMB owners handle their company's IT.
Before switching to Avast for Business 55 percent of SMBs were relying on free consumer security solutions. Only 23 percent used premium business solutions and a worrying three percent used no solution at all.
The biggest threats are seen as losing valuable data (31 percent) along with loss of productivity (23 percent) and losing customers (16 percent). Where BYOD is concerned 52 percent allow employees to access company data on their own devices, but more than half of these (54 percent) don’t have a BYOD policy in place.
There's a summary of the survey findings in infographic form below or you can read more on the Avast blog.
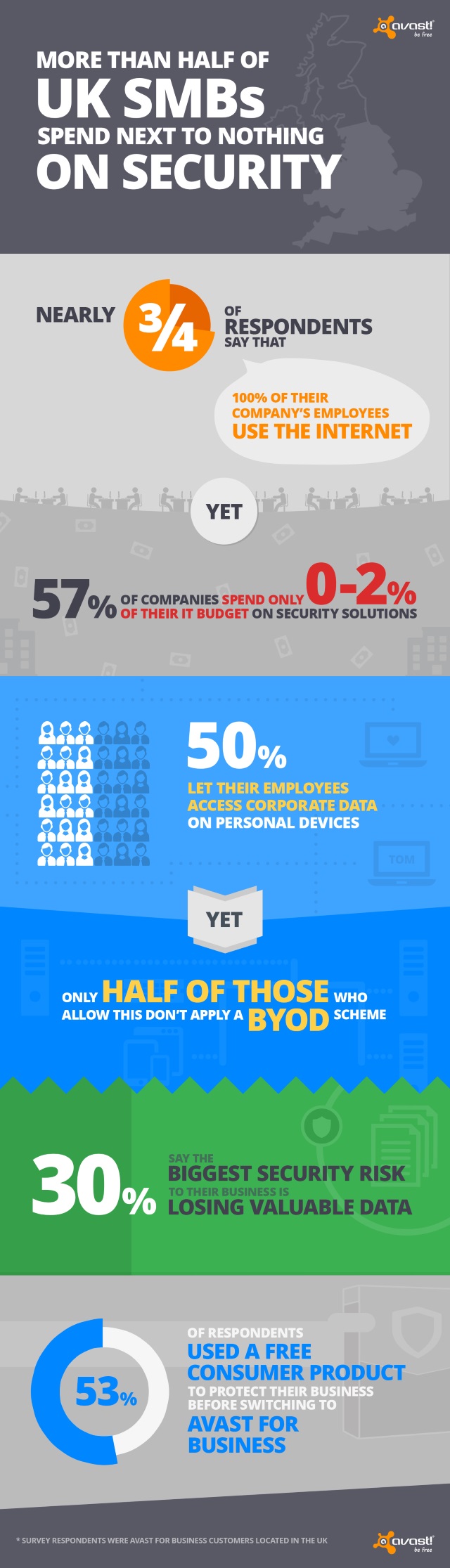
Image Credit: Manczurov / Shutterstock
-

Lookout launches Stagefright detector
Publié: août 7, 2015, 11:39am CEST par Ian Barker

Stagefright detectors seem to be flavor of the month at the moment, not surprising when the vulnerability could affect around 95 percent of Android devices. We reported yesterday on Zimperium's version and now mobile security specialist Lookout has launched its own detector.
The app will tell users whether or not their Android device is vulnerable to Stagefright. If it is affected, it provide a run-down on how to reduce the risk of being attacked. Uses will also be able to check back in after receiving a security patch to confirm it contained the fix for Stagefright.
Once downloaded, the app checks to see if the device has a vulnerable version of the media player. It will then inform you if you’re not vulnerable or your device has already been patched, or that you are vulnerable and it hasn't.
If you are vulnerable Lookout provides detailed instructions on disabling the auto-fetching of MMS messages in your default messaging app. Depending on your phone, this app may be 'Hangouts,' 'Messages,' 'Messaging,' or 'Messenger.' By disabling auto-fetching attackers are prevented from getting the device to automatically download a malicious video containing Stagefright exploits.
You can download the detector free from the Play store and there more is information on the Lookout blog.
-

Zero-day vulnerabilities increase over 2014
Publié: août 6, 2015, 5:01pm CEST par Ian Barker

Danish security company Secunia is using the Black Hat conference to reveal an early look at the vulnerability trends to date for 2015.
One of the main findings is that 15 zero-day vulnerabilites have been discovered so far in 2015, making it likely that the total for the year will exceed the 25 discovered in 2014. The 2015 zero-days were all discovered in popular Adobe and Microsoft products widely in use across both personal and professional IT systems.
"The increasing number of zero-days is not a surprise," says Kasper Lindgaard, Director of Research and Security at Secunia. "It would be more of a concern if the number dropped, because that would mean that the zero-days we can be sure are out there were going undetected -- after all, Hacking Team, the Italian company reported to be selling a product utilizing bought zero-days to governments and corporations, is not the only company of its kind out there".
The total number of vulnerabilities discovered from January 1 to July 31st at 9,225 is on a par with the 9,560 discovered over the same period last year. However, Secunia's preliminary findings do indicate a shift in how critical they are. A slightly higher share of the vulnerabilities discovered are rated as 'extremely critical' (from 0.3 percent to 0.5 percent) and 'highly critical' (from 11.1 percent to 12.7 percent) while there is a drop in the 'moderately critical' category (from 28.2 percent to 23.7 percent).
The company has also looked at vulnerabilities for mobile operating systems and discovered around 80 vulnerabilities in iOS, and approximately 10 in Android. Lindgaard says, "The fact that fewer vulnerabilities are discovered in Android should under no circumstances be misinterpreted to imply that Android OS is more secure than iOS. The trouble with a vulnerability in Android OS is that Google, the vendor behind the operating system, has no control of its patch status on majority of the devices that run it, because those devices are produced and maintained by third-party vendors. The 'Stagefright' vulnerabilities discovered by Zimperium, which was disclosed last week, is a perfect example of the problem: Google has acted quickly and issued a patch, but from there on it’s up to phone vendors -- Samsung, HTC, Sony, etc. -- to push the patch live to the users. In comparison, Apple can issue patches and push updates directly to all devices running iOS -- a much more controlled process".
Secunia also points out that since Heartbleed brought OpenSSL vulnerabilities to public notice there have been five distinct waves of OpenSSL vulnerabilites. Lindgaard points out that, "Because OpenSSL comes bundled in many third-party products, customers are not necessarily aware that they have it in their inventory, and so cannot take appropriate action".
You can find more information about the company's findings on the Secunia website.
Image credit: fotogestoeber / Shutterstock
-

API security becomes a senior management concern
Publié: août 5, 2015, 3:04pm CEST par Ian Barker

As APIs fast become the dominant channel for exchanging data between both external and internal audiences and services, there's increasing concern over the threats and vulnerabilities they present.
A new survey by API management company Akana reveals that API security is as much an issue for the business as it is for IT, with 75 percent of respondents saying that API security was a CIO-level concern whilst 65 percent say it's an issue for business managers. As APIs are increasingly being adopted to drive digital initiatives, both business and IT increasingly see value in securing them.
The survey is aimed at understanding the maturity of API security practices amongst the leading digital enterprises, its results reveal that while the majority of respondents are taking steps to secure API access, only few had taken steps to ensure that sensitive data was being securely handled in the Apps that access the APIs.
Just as the emergence of Web brought web-based threats and resulting countermeasures to the forefront, the survey indicates recognition from security practitioners of threats that are unique to the API channel.
"APIs are new enough in the enterprise that people want the latest on how industry peers are dealing with security threats," says Roberto Medrano, EVP at Akana. "We felt there was an opportunity to ask others to share their insights and worries. The survey report should be a helpful starting point for determining best practices in API security going forward".
Other findings are that more than 65 percent of respondents report that they don’t have processes in place to ensure that the data being accessed by applications using APIs is managed securely. With mobile apps and IoT devices increasingly being API consumers, enterprises face exposure to threats of unauthorized access to data once it's been accessed through an API.
Almost 60 percent of survey respondents indicated that they weren't securing API consumers. A large proportion of survey respondents -- more than 45 percent -- also didn't rate limit access to their APIs, a control that can reduce the risk of hacking.
Respondents identified JSON (JavaScript Object Notification) Scheme, DDoS, message-level security and encryption amongst the top API security threats. The overall results suggest that a digital divide is developing as high-performing companies embrace core digital capabilities and APIs to move ahead. But enterprises needs to recognize and take steps to address the additional threats that API use might be exposing their data and organization to.
You can download the full report from the Akana website and there's a summary of API security risks in the graphic below.
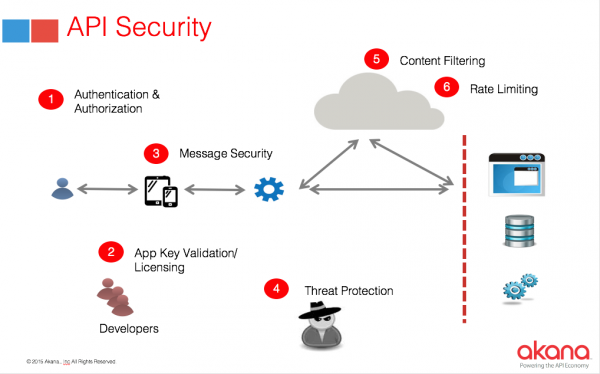
Image Credit: Profit_Image / Shutterstock
-

Bringing the power of analytics to performance management
Publié: août 4, 2015, 5:11pm CEST par Ian Barker

Smooth management of IT systems relies on being able to spot issues early and resolve them before they have a major impact on performance.
Infrastructure analytics specialist Virtual Instruments is launching a new version of its VirtualWisdom solution, a vendor-agnostic platform that ensures performance for enterprise applications spanning physical, virtual and cloud computing environments.
VirtualWisdom4.3 offers new software probes that support Microsoft Hyper-V and IBM PowerVM. It's also introduced a flexible cloud delivery model, moving a customer's platform appliance and data analytics to the cloud, as well as new hardware probes for NAS and fibre over Ethernet (FCoE).
By correlating and analyzing millions of data points across the entire infrastructure, VirtualWisdom 4.3 provides business leaders, IT operations and application teams with definitive answers to optimize their systems. As a result, IT teams can spend less time troubleshooting and more time focusing on the business, enabling greater cross-department collaboration and increasing the value that IT delivers.
"Successful performance management centers on being proactive, and the new components of VirtualWisdom4.3 enable our customers to get ahead of looming performance issues," says Barry Cooks, senior vice president of products, engineering and support at Virtual Instruments. "Heterogeneous, multi-vendor IT infrastructures are the norm in enterprise IT, and our engineering team is committed to bringing our customers a solution that solves performance problems throughout the entire infrastructure ecosystem. Multi-hypervisor support, expanded analytics and our cloud delivery option combine to make VirtualWisdom4.3 a critical platform for a greater range of enterprises that are recognizing the role IPM can play in driving a business toward its higher level goals".
VirtualWisdom 4.3 is available now, to find out more visit the Virtual Instruments website.
Image Credit: alexmillos / Shutterstock
-

Microsoft selects Interana to improve Bing performance
Publié: août 4, 2015, 4:10pm CEST par Ian Barker
Bing is the second largest search engine in the US and in order to maintain its position the team behind it needs to make constant improvements and for that they need insights into how it gets used.
Microsoft has chosen behavioral analytics solution Interana to analyze the massive volumes of clickstream event data generated daily on Bing.
"Interana and Microsoft share a common vision of innovation. During the proof of concept, Interana met the challenge of delivering the insights we needed from our massive volumes of event data," says Craig Miller, group engineering manager for Bing Experiences. "Interana's scale is impressive. It took only minutes to get answers to questions, opening new possibilities as to what we can do with analytics at interactive speeds. We look forward to continuing to work with the team".
The Bing team will use Interana to analyze experiments at interactive speeds for tasks like A/B testing, trend analysis, automated reporting, ad hoc exploration and discovery, and knowledge sharing. Interana's behavior-based tools will allow Bing to quickly work through a variety of testing, optimize its search engine, and measure how new and current features perform with users. Bing will also enable new data producers and consumers by allowing non-technical team members to access their data via Interana’s end-to-end self-service experience.
"Bing and Interana illustrate how a business can draw actionable insights quickly from massive amounts of data," says Ann Johnson, co-founder and CEO of Interana. "Interana helps organizations like Bing better understand their customers and business. We do this with a solution that’s sophisticated enough to provide insights for seasoned data scientists and simple enough to produce value for business users".
Interana's scalability and performance will enable Bing to interactively analyze the growing amounts of event data generated by searches to better understand users' preferences and accelerate its speed of innovation.
-

Web isolation platform adds threat intelligence to improve accuracy
Publié: août 4, 2015, 2:49pm CEST par Ian Barker

We reported on the Menlo Security Web Isolation Platform, which aims to eliminate threats before they reach the desktop, earlier this year.
Now Menlo Security is beefing up its offering, announcing a partnership with threat intelligence specialist Webroot. The link up will deliver granular threat intelligence for the Web Isolation Platform through integration with Webroot's BrightCloud Web Classification Service.
"Webroot has the most comprehensive and effective Web classification service in the market," says Poornima DeBolle, chief product officer at Menlo Security. "Integrating Webroot's BrightCloud Web Classification Service with our Web Isolation Platform enables us to give our customers comprehensive control, security and visibility for their organization's Web activity".
For most enterprises, restricting access to unproductive and known-malicious websites is a best practice for preventing productivity loss and reducing risk. However, according to Menlo's recent Vulnerability Report, more than 20 percent of the top million websites are running vulnerable software and are therefore open to compromise by attackers. As a result, even those sites considered to be 'safe' may be compromised and used to serve malware at any time.
The Menlo Security Isolation Platform provides an extra level of security that prevents any malware from reaching user devices via compromised or malicious sites. By isolating and executing all web content in the public or private cloud and delivering only safe, malware-free information to the user's device, the Menlo platform eliminates the risk of malware.
Adding classification data and threat intelligence from Webroot lets administrators of the Menlo Security Web Isolation Platform establish policies that selectively allow, block or isolate websites based on category. The classification data from Webroot also augments the logs and reports provided by the Web Isolation Service, enabling administrators to track and analyze all web usage.
Webroot Web Classification is available now as part of the Web Isolation Service, visit the Menlo Security website for more information.
Image Credit: Maxx-Studio / Shutterstock
-

Monetizing mobile apps without harming the user experience [Q&A]
Publié: août 4, 2015, 12:55pm CEST par Ian Barker

In the past making money from a mobile app has usually involved signing up to an advertisement network and allowing the app to display banner ads.
The problem with this is that it doesn't make for a particularly good user experience and may actually turn people off using the app. For some time now the buzz around the industry has been about 'native' ads within apps. But exactly what is a native ad and what are the benefits? We spoke to Yannis Dosios, VP of Yahoo Publisher Services to find out.
BN: What is a native ad and how do they differ from more traditional options?
YD: At Yahoo, we believe advertising doesn't have to compromise how users enjoy an app, and that advertisements should, and can, complement the user experience. This is why Yahoo introduced native advertisements inside its own mobile applications. What makes these advertisements native is how seamlessly they are integrated into the user experience. For example, users scrolling through the Yahoo Finance application articles see a native advertisement after every few pieces of content. This ad has the same look and feel, and layout as the other content sections, while clearly denoting that this content is sponsored.
What we have found is that these native ads deliver significantly higher revenue and eCPMs (revenue per thousand impressions) than the traditional banner or full-screen interstitial advertisements. We also have found that these ads perform well for advertisers, delivering superior click-through rates and post-click conversion rates. Users notice and engage with these advertisements.BN: Yahoo announced back in February that it was launching native ads following its acquisition of Flurry. What success has this brought?
YD: The Yahoo Mobile Developer Suite is helping mobile developers measure, advertise, monetize and enhance their apps. We've seen a lot of early success with Gemini, Yahoo's native advertising solution. According to a recent Flurry from Yahoo survey, nearly half of mobile app publishers already have or are planning to introduce native ads, and that number is growing rapidly. We’ve seen publishers express that revenue and control of the user experience are most important to them right now. It's a rapidly evolving space, and we're excited to be a leading player in it.
BN: Is Yahoo competing directly with other mobile ad networks?
YD: With its Yahoo Mobile Developer Suite, Yahoo offers mobile developers a comprehensive solution for acquiring, engaging and monetizing users, and for deeply measuring and optimizing their mobile applications. In particular, with Yahoo App Marketing, developers can use just one platform to gain exposure to an enormous audience of highly engaged and active users across desktop, mobile and social. With Yahoo App Publishing, developers can maximize their advertising revenues through a combination of well-integrated Gemini native, video and search ad units, extensive and unique data from both Yahoo, Tumblr and Flurry, and a powerful ad selection algorithm that leverages this unique data. And with Flurry Analytics and Explorer, developers can instantly measure their application performance and identify problem and opportunity areas to maximize performance.
BN: Are search ads as important for mobile apps as they are for the desktop?
YD: Search ads are certainly also important in mobile. But the search context and experience are also very different in mobile. Flurry data shows that about 88 percent of time spent on mobile devices is spent inside mobile applications, so it makes sense that mobile searches also get initiated directly from those applications. This is why Yahoo offers a Search-in-Apps service, which enables app developers to introduce search capability from within their apps. For example a user of the Pinger messaging application can easily search for movie times for the movie that they have just chatted about with their friends, all without leaving the Pinger application. This is an exciting space with lots of room for innovation.
BN: What trends are you seeing in the mobile advertising market?
YD: This is a fast changing market, but the main trends I would call out are:
1. Growing interest of brands in spending more on mobile -- in recognition of the very rapid increase in mobile usage.
2. Increased advertiser focus on measurement and impact assessment from mobile campaigns.
3. Growing importance of data and programmatic for more precise and better optimized advertising campaigns.
4. Rapid growth of native and video ad formats.BN: Native ads are obviously good for the end user but what benefits do they offer advertisers?
YD: What's special about native ads is that they appear to be meeting the needs of all three key parties: they monetize well for developers, they perform for advertisers, and they are accepted and even liked by users. In particular, a recent Yahoo/Ipsos Consumer Perceptions study showed that 60 percent of consumers have said they feel positive about native ads. And 80 percent of advertisers say they will invest in Native in 2015. This, combined with the superior monetization performance of native advertisements over other ad formats makes native advertising a very compelling ad format.
Photo Credit: 3Dstock / Shutterstock
-

New intelligence tool aims to make enterprises smarter
Publié: août 4, 2015, 12:02pm CEST par Ian Barker

Businesses are constantly on the look out for information to support their decision making processes. But they need to understand industry and market trends as well as what’s happening internally.
Today enterprise services platform and marketplace provider blur Group is launching an online business intelligence tool that provides a comprehensive industry overview on specific trends in business services -- including insights into geographical focus, technology and more.
Called blur Data it’s designed for anyone in the business services industry searching for insights to support forecasting and budgeting. It combines insights from blur Group's established global marketplace with analytics gleaned from external data across search engines and social media to offer a one-stop source of information.
"Imagine having immediate access to trending technologies and global, up-to-date statistics to inform your upcoming budget projections. We believe blur Data will become a key strategic tool for buyers of business services when it comes to making informed pricing, forecasting and procurement decisions." says Philip Letts, blur Group's CEO. "This product launch comes at an exciting time for the Group, which is attracting more enterprise level buyers and service providers than before. We remain committed to our goal of attracting large enterprise customers to the platform and this launch will position us even better to service their needs".
Offered as a standalone product from blur's Enterprise Services Platform, blur Data will be available to customers for $39 per user per month. More details can be found on the blur Group website.
Image Credit: Mopic / Shutterstock
-

New version of RIG exploit kit sees 34 percent attack success rate
Publié: août 3, 2015, 5:59pm CEST par Ian Barker

At the beginning of this year the RIG exploit kit had its source code leaked online by an unhappy reseller. This led to a hit in its success rate as security company Trustwave published details of its workings.
Trustwave has revealed today at BlackHat that RIG's authors have been working on a new RIG 3.0 version. The company's researchers say there are now up to 1.25 million victims worldwide and more than 3.6 million attack attempts. A remarkable success rate of 34 percent.
RIG 3.0 has multiple layers making it more robust. It targets via outdated versions of Internet Explorer and browser plugins, particularly Flash. RIG attacks via three routes, infected adverts which account for over 90 percent of victims, already infected computers being re-infected (the malware enables hidden browsing on an already infected computer so it browses other exploit kits to then re-infect the machine) and by simply visiting a compromised website.
The developers have also learned from the leaking of RIG 2.0's code. "This time around they're not using resellers but hosting the kit directly in Russia and protecting the server using CloudFlare," says Arseny Levin, Lead Security Researcher at Trustwave SpiderLabs. "They've also fixed the vulnerabilities that allowed the leak back in February".
The country most hit by RIG 3.0 is Brazil with 450,529 infected victims followed by Vietnam with 302,705 infections. The US has 45,889 victims, Canada 3,913 and the UK 9,662. The software is able to deliver various payloads, each depending on the specific customer, but the top one delivered so far is the Tofsee spam bot, representing 70 percent of all infections.
To avoid falling victim to this attack, users should make sure all software -- including browser plugins -- is up to date, and uninstall any software that is actually not in use to reduce the attack surface. "It's also worth enabling click-to-play in your browser so that plug-in content from Java, Flash, Silverlight, etc isn't automatically opened when you visit a website," says Levin. Businesses should be using managed anti-malware controls, such as gateway technologies that can detect and strip out malware in real-time.
More information about RIG 3.0 is available on Trustwave SpiderLabs' blog.
Photo Credit: ra2studio/Shutterstock
-

MODECOM FreePC is so small it can fit in your pocket [Review]
Publié: août 3, 2015, 12:42pm CEST par Ian Barker

A portable PC used to mean something the size of a suitcase, then it became a laptop or notebook. Now with the FreePC you get one that you can slip into your pocket with no need for specialist tailoring.
You’ll need to have an HDMI screen, keyboard and mouse available to be able to use it, but if you know they’re going to be available at your destination why take anything bigger?
The FreePC is about four times the size of a USB memory stick, but it manages to pack in a lot of technology. There’s a 1.83GHz quad-core Intel Atom CPU, 2GB of RAM and 16GB of storage, it comes with Windows 8.1 pre-installed. You can extend the storage with a microSDHC card. It also has Wi-Fi, Bluetooth 4.0, a USB 2.0 port and a micro USB port with OTG, and it’s capable of driving a full HD, 1080p screen.
In the box you get a short HDMI extension cable, a power adaptor and a microUSB to USB adaptor. There’s a multi-language quick start guide which only devotes four pages to each, so doesn’t tell you a lot. You’ll search in vain for more documentation on the maker’s website, so if you need to access the BIOS or perform a system refresh you’re left to figure it out for yourself or contact support.
Performance
Being Windows 8.1 and having solid state storage the FreePC boots fast and is ready to use within 30 seconds or so of you pressing the power button. Performance for surfing the web is perfectly fine, but try to do other things and you do notice the lack of storage.
It comes with a trial of Office 365 pre-installed, so out of the box you’re left with just 3.7GB of free space. This means that file operations like copying documents and unpacking zip files can seem painfully slow so you will want to budget for an SD card. You can of course use OneDrive -- which comes installed -- or your choice of cloud storage to store your files and documents.
You aren’t really going to be using this in the same way you would a desktop or laptop so file performance isn’t the whole picture. For the sort of things it will be used for it works well. The FreePC is quite at home playing videos from YouTube, iPlayer or the like so you can use it to turn your television into a smart TV.
For business use the FreePC is ideal for presentations as you can simply hook it up to a big screen or even a projector with minimal hassle.
Should You Buy One?
This isn’t a machine you’d choose to play the latest games or crunch massive spreadsheets, but for making presentations, or to turn a TV into a smart media centre, it’s a lot better than you might expect from something so tiny.
Of course for multimedia use there are cheaper, Android powered, options. Worth noting too that you can buy a full size desktop PC -- less portable but more powerful -- for around the same money. That leaves the FreePC appealing to a particular type of business user who needs to access cloud apps or make presentations on the go with the comfort of a familiar Windows environment.
The FreePC costs £159.99 on Amazon and you can find more information on the MODECOM website.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Why millennials want self-service solutions [Q&A]
Publié: août 3, 2015, 11:05am CEST par Ian Barker

The millennial generation has grown up with the internet, so naturally they demand more from their business systems and online service providers. Product managers need to recognize this dynamic and ensure that their SaaS products deliver.
We spoke to William Colleran, CEO of online contextual help provider AnswerDash to explore this wake-up call for businesses.
BN: What impact is the millennial generation having on service delivery?
WC: Millennials are influencing service delivery more than any generation, especially by expecting and demanding efficient, reliable and intuitive technologies. At over 75 million strong according to Pew Research, millennials are now the largest demographic cohort, and with immigration expanding this group more than any other, that population is projected to peak in 2036 at over 80 million. Because of these huge numbers, the preferences of millennials strongly influence the user experience that technology companies are designing into their products and services, impacting everything from tablets to smartphones and from SaaS apps to mobile apps. This emphasis on enhanced user experiences requires not just intuitive, easy-to-use interfaces but also systems that respond rapidly to create interactive, real-time experiences. Millennials want information at their fingertips, they want it easy to consume, and they want it now.
BN: Are businesses going to lose out if they don't embrace this trend?
WC: To put it simply, yes. Being steeped in technology, millennials are self-reliant with no patience for poor customer service, and businesses must cater to this generation to stay relevant and trusted. Industry research indicates that by 2017, the millennial generation will comprise the largest online audience and will have more buying power than any prior generation, including baby boomers. Given millennials' massive market impact, businesses must appeal to their values, lifestyle and preferences.
BN: How can virtual service agents and alternatives enhance the customer experience?
WC: We see self-service options, such as that offered by AnswerDash, as improvements over the experience that virtual agents provide. A "virtual service agent" is a software program that imitates live chat but without the "live" part -- meaning, there’s no human in the communication loop. Instead, the software program provides responses to textual inquiries by mining information in a knowledgebase. We advocate a more direct interaction, where users point and click on questions and answers that are selected from the knowledgebase because they are highly relevant based on the history of prior users in similar contexts. We have found this approach to be more effective and less burdensome on users than the mock-dialogue (typing large amounts of text back and forth) required by a virtual agent. AnswerDash's approach is more familiar to users, since people are accustomed to tapping on content via their smartphones and tablets. Tapping an image or text takes less effort than typing and is more intuitive, making it easy for users to find answers they are looking for.
BN: Can we expect to see enterprise systems adopting a similar self-service approach in future?
WC: Absolutely. In fact, we all see rapid adoption of self-service kiosks in airport terminals, grocery stores, banks, movie theaters and many other venues. Online businesses are starting to see the same value in adopting self-service on their websites. Self-service kiosks in the physical world reduce the time for customers to achieve their goals while simultaneously reducing the labor costs for business owners to service those customers. Similarly, online self-service enables users to help themselves, obviating the need for customers to engage with customer service agents. This approach saves businesses time and money while enhancing customer satisfaction.
BN: Isn't there a risk that adopting a 'millennial approach' will alienate older users?
WC: Adopting a millennial approach with self-service solutions doesn't mean abandoning other options, such as email, FAQ, phone or live-chat, that appeal to older generations. Rather, adopting millennial-friendly, self-service technologies represents an evolved approach to customer care, providing a faster, more efficient option for customers who grew up with technology. Businesses that provide a variety of customer care options, allow customers to make their own decisions on what level of attention is best.
Image Credit: Zurijeta / Shutterstock
-

HP rolls out a range of Enterprise Services for Windows 10
Publié: juillet 31, 2015, 5:08pm CEST par Ian Barker

Businesses usually like to wait a while before rolling out a new operating system to allow any initial snags to be ironed out.
Of course systems providers have to be ready to support them when they do make the move and HP has announced the availability of a full suite of Windows 10 services designed to help enterprises control costs and smooth out the move to the new operating system.
The new Windows 10 services include HP Test Drive Services for Windows 10 which lets enterprises test the new operating system with a control group of users to evaluate the new user experience, capabilities and potential incompatibilities in advance of any wholesale migration.
HP Transformation Services for Windows 10 offers a suite of services to assess, design, implement, deploy and support Windows 10 as part of a digital workplace transformation. The service helps build and integrate supporting infrastructure, transform client and web applications for the new environment, build operating system images, and then manage the rollout.
HP Roadmap Service for Windows 10 is a workshop-based advisory service which will deliver a roadmap for an organization's Windows 10 implementation. This will focus on productivity, security and manageability improvements, as well as how Windows 10 can fit into a broader workplace transformation opportunity.
Finally the HP WebApp Accelerator Service for Internet Explorer 11 is an implementation and migration service to ensure that critical web applications built for legacy versions of Internet Explorer will continue to work effectively in the latest browsers and operating systems.
"HP's unique relationship with Microsoft allows us to offer Windows 10 in a controlled manner integrated into the client's world -- giving both IT and the user the chance to experience the new operating system," says Eric Harmon, Senior Vice President, Global Practices and Transformation at HP Enterprise Services. "IT and developers get to validate the application portfolio in advance -- lowering the cost and risk of a large scale migration, and the user sees innovation and a more personal computing experience".
Most of these services are available now, HP Transformation Services for Windows 10 will be out on October 1st. More detail is available on the HP website. HP also has additional products to help small- and medium-sized businesses, deploy Windows 10 across their organization.
-

Turning Splunk data into pre-emptive breach detection
Publié: juillet 31, 2015, 4:27pm CEST par Ian Barker

In case you haven't heard of it Splunk is one of the most popular machine data analytics tools, used to provide early warning of network and system issues.
IT teams often rely on access to this data for security information and event management (SIEM), but as malware becomes more sophisticated it can be difficult to spot what's important in time to prevent major breaches.
Breach detection specialist TaaSera is launching NetTrust for Splunk which allows users to integrate NetTrust's preemptive breach detection solution into Splunk-based security management applications.
"Splunk is one of the most widely used analytics platforms on the market today and is becoming increasingly popular for cybersecurity purposes as a SIEM. But when malware is increasingly able to avoid leaving traces in logs, critical IOCs and similar pre-breach behaviors can go unrecognized by SIEMs allowing dangerous and malicious activity to go undetected within a network’s perimeter," says Ivan Shefrin, Vice President of Security Solutions at TaaSera. "With many of TaaSera’s customers invested in Splunk, we are ensuring that they have access to the best possible data and analytics necessary to act in time before sensitive information, business continuity and reputations suffer due to data breaches".
NetTrust uses patented 'Threat DNA' mapping technology to identify otherwise hidden network behaviors at run time and continuously analyze behavioral and contextual evidence. At the same time it integrates tightly within Splunk Enterprise 6.1 and 6.2. It gives users access to real-time visualizations of network systems at the greatest risk, along with the ability to identify the precise indicators of compromise (IOCs), in the right context and at the right time. This allows it to provide a more actionable early warning system for breach containment and response.
NetTrust for Splunk is available now, more information and downloads can be found on the TaaSera website.
Image Credit: Balefire / Shutterstock
-

Small but (almost) perfectly formed -- Inateck MercuryBox BP2101 [Review]
Publié: juillet 31, 2015, 3:37pm CEST par Ian Barker

A technology writer's world can often seem full of Bluetooth speakers, they have successfully colonized a corner of my office, so it takes something special to stand out from the crowd. In terms of build quality the latest from Inateck makes an immediate impression but does it live up in other areas?
The whole package has a premium feel to it, even the cardboard box is nice. The speaker itself is a neat design with an aluminum chassis that feels solid and weighty. There are rubber end caps, one of which has a fold-down flap covering the USB and Aux ports, and a rubber panel on top with buttons for power, pause, +/- and Bluetooth calls. It comes with braided USB and 3.5 mm jack cables both of which have Velcro ties to keep them tidy when not on use, another quality touch, a wrist strap and a soft pouch to carry the speaker around in. There's a well-produced instruction leaflet too.
Inside are two 5w speakers and a polymer lithium-ion battery. The design is compliant with the IPX5 standard for waterproofing, this means it's protected against dust and 'low pressure' water jetting. So while you won't want to drop it in the bath it should be fine to take to the beach or use in the rain.
When you switch it on the speaker goes into pairing mode automatically, making it easy to link it to your phone. The +/- buttons have a dual function, a short press will skip tracks while a longer press adjusts the volume. The need for a long press does make it tricky to set the volume accurately though. It has a built-in microphone so you can make calls or use it with the likes of Cortana and Siri.
For such a compact unit (165 x 58 x 27mm, small enough to slip into a pocket) the MercuryBox produces a surprisingly good sound. There's decent bass and although it won't fill a big room it's perfectly adequate for everyday listening. There's decent battery life too, you should be able to get about 15 hours of playback on a full charge.
At $54.99 on Amazon or £49.99 in the UK the MercuryBox isn't the cheapest Bluetooth speaker around. It does, however, feel like a quality item -- an impression reinforced by the accessories -- is easy to use, though the volume control lets it down a little, and produces acceptable sound quality.
You can find out more about the MercuryBox on the Inateck site.
-

Hackers target PDF readers, yet a high percentage go unpatched
Publié: juillet 30, 2015, 1:15pm CEST par Ian Barker

Vulnerability intelligence firm Secunia has released its second quarter 2015 country report for US and 14 other countries around the world. This looks at what programs users have installed and which are most at risk.
The big news is that a high percentage of users have unpatched versions of Adobe Reader. Adobe has the highest market share in this segment and PDF readers are a common target for hackers.
Kasper Lindgaard, Director of Research and Security at Secunia says, "PDF readers remain one of the world’s most popular targets for hackers so it is concerning that we are still seeing 75 percent of PCs that have Adobe Reader 10 or 11 installed are unpatched. There are steps that PC users can take to defend themselves, and any system they are connected to, against known exploits. By upgrading to the latest version of the program and by applying priority patches in a timely manner, PC users can make great strides towards minimising their exposure to security risks".
Among other findings are that the average US PC user has 76 programs installed from 27 different vendors, 43 percent of those installed are Microsoft programs. Unpatched operating systems are in use by 13.2 percent of users and 11.9 percent have other Microsoft programs unpatched. End of life programs -- those that are no longer patched by the vendor -- are in use by 5.5 percent.
Oracle's Java Runtime Environment is least likely to be up to date, with 80 percent of version 1.7 and 38 percent of 1.8 users running an unpatched version. Among VLC Media Player 2 users 54 percent have an unpatched version and Apple QuickTime 7 is 31 percent unpatched.
The reports are based on data from users of Secunia's Personal Software Inspector (PSI). The data includes the average numbers of installed programs -- patched and unpatched -- on private PCs in each of the different countries.
You can see Secunia's reports on the US and other countries on the company's website.
Image Credit: viviamo / Shutterstock
-

How to cope with Stagefright
Publié: juillet 30, 2015, 12:26pm CEST par Ian Barker

Earlier this week we reported on the Stagefright vulnerability that could affect 95 percent of Android devices. It has arisen as a result of code vulnerabilities which could have been detected and resolved earlier.
Application security company Checkmarx has been looking more deeply into Stagefright and what it means for users and developers.
Stagefright can infect a device by simply downloading an MMS message -- which happens automatically in most cases. Once infected, the hacker has full control over the phone's data. The scary thing is that the Android device just needs to receive an MMS message. The user doesn't have to open it in order to get infected.
First of all there's a temporary workaround to avoid infection. Open the Hangouts app, go to Settings from the hamburger menu, select SMS, choose Hangouts as your default SMS app and uncheck Auto-retrieve MMS. There's usually an option to turn off auto retrieval of MMS in other messaging apps too, so check your settings.
Google was notified about the vulnerability and the numerous bugs quite a while ago and after a couple of days introduced a fix to the software. That, however, doesn’t mean everyone is safe. It means that all the different mobile-phone makers need to implement the fix in their versions of the Android OS and distribute a patch to their users. This may take some time, however most mobile phone companies have already stated that they are working on it while others have announced availability of a patch or have already addressed the issue when it was reported to Google.
Amit Ashbel of Checkmarx writing on the company's blog says, "It is clear by now that the Stagefright vulnerability was a result of one or more code vulnerabilities. It is also clear that these could have been detected at an earlier stage of the development and resolved at that stage. What is not yet clear is what the exact vulnerability is however that should become clear within the coming days after the full information about the CVEs reported are disclosed".
Checkmarx's CxSAST for Mobile delivers code security analysis for Android, iOS and Windows applications. This helps eliminate code vulnerabilities during the coding process rather than waiting for them to appear at a later stage.
Image Credit: Christos Georghiou / Shutterstock
-

Most malvertising attacks come from news and entertainment sites
Publié: juillet 29, 2015, 6:01pm CEST par Ian Barker

Since news and entertainment websites are amongst the most popular on the net, it's not surprising that they're more likely to play host malicious adverts.
A new report by Bromium Labs reveals that more than half of malvertising is unknowingly hosted on news and entertainment websites. 58 percent of online adverts with hidden malware were delivered through news websites (32 percent) and entertainment websites (26 percent). Major websites unknowingly hosting malvertising included cbsnews.com, nbcsports.com, weather.com, boston.com and viralnova.com.
Other findings from the report include that Flash exploits have increased 60 percent in the past six months. This is due to the rapid growth in availability of active exploit kits many of which now target Flash.
The growth of ransomware families has doubled each year since 2013, with nine new ransomware families emerging in the first six months of this year. Ransomware continues to grow, as cybercriminals realize it is a lucrative form of attack.
Malware is also getting better at evading detection. Bromium Labs analyzed malware evasion technology and found it is rapidly evolving to bypass even the latest detection techniques deployed by organizations, including antivirus, host intrusion prevention systems (HIPS), honeypots, behavioral analysis, network filters and network intrusion detection systems (NIDS).
"For the last couple years, Internet Explorer was the source of the most exploits, but before that it was Java, and now it is Flash; what we are witnessing is that security risk is a constant, but it is only the name that changes," says Rahul Kashyap, SVP and chief security architect, Bromium. "Hackers continue to innovate new exploits, new evasion techniques and even new forms of malware -- recently ransomware -- preying on the most popular websites and commonly used software".
The full report, Endpoint Exploitation Trends 1H 2015, is available from the Bromium Labs site.
Image Credit: Sam72 / Shutterstock
-

TeleSign SDK streamlines verification on mobiles
Publié: juillet 29, 2015, 4:21pm CEST par Ian Barker

Many of the latest cyber attacks focus on mobile platforms as they're often seen as inherently less secure, particularly when handling account logins and important transactions.
Mobile identity solutions company TeleSign is today launching its TeleSign Auto Verify, a new lightweight software development kit (SDK) for mobile app developers that streamlines the account verification process while providing a more reliable and cost-effective method than SMS-based verification alone.
Auto Verify seamlessly integrates with new or existing mobile apps and verification processes and employs a proprietary network signaling method to ensure greater completion rates without the need for one-time passcodes (OTPs) to be sent to the consumer's mobile phone and manually entered, the way verification is most commonly experienced today.
"With the mobile platform serving as fertile ground for today’s cyber attacks, app developers know it’s essential to take a security-first approach to development," says Steve Jillings, CEO of TeleSign. "TeleSign Auto Verify delivers a frictionless registration experience by authenticating users 'behind the scenes' -- no passcodes required. Now customers can protect account registrations and important transactions easier than ever".
TeleSign Auto Verify integrates user registration into a mobile app to streamline the verification of a user’s mobile phone number during account creation. It can therefore increase assurance for high value transactions, such as money transfers, payment transactions, and password changes, by requesting and then verifying, in real time, a user's phone number within their mobile app. It can also ensure an existing end user has a legitimate phone number attached to each account by seamlessly verifying the number in the background, while users interact with the mobile app as usual.
TeleSign Auto Verify is available from today as a 34Kb SDK for Android versions 4.1.x and higher, and is easily embedded into new or existing mobile apps and verification processes, while giving developers complete control over the branding and user experience. You can find more details on the TeleSign website.
Image Credit: Oleksiy Mark / Shutterstock
-

Bitcoin payments move towards the mainstream with new payment partnership
Publié: juillet 29, 2015, 3:41pm CEST par Ian Barker

We reported recently on a new system that reduces the risk for merchants in accepting bitcoin payments.
Now there's more evidence that the digital currency is going mainstream with the announcement of a partnership between enterprise bitcoin payments processor, Bitnet and payments platform provider Zooz that will enable merchants to accept bitcoin as a payment method on the Zooz payment platform.
"We have seen the growing interest in digital currencies among our customer base and are excited to partner with Bitnet to add bitcoin to our service offering," says Nathan Jackson, VP Europe at Zooz. "We selected Bitnet as a partner due to their advanced platform, integrity of its team, in addition to demand from some of our key customers for bitcoin payments".
Zooz customers will be able to add bitcoin as an option to their checkout pages quickly and easily. Bitnet will enable Zooz's customers to accept payments in bitcoin without being exposed to the risk of fraudulent transactions or any volatility in the price of bitcoin.
"Our partnership with Zooz enables us to work with one of the most innovative payments platforms in the market," says Akif Khan, Chief Commercial Officer, Bitnet. "We are excited to partner with this rapidly growing company and help its merchants drive profitability across all channels".
You can find out more on the Bitnet website.
Photo credit: Lightboxx / Shutterstock
-

New digital consent initiative to give users control of personal data
Publié: juillet 29, 2015, 2:48pm CEST par Ian Barker

As more and more of our data gets stored in digital format, keeping it secure becomes a bigger challenge. One possible solution is User Managed Access (UMA) which gives a web user a unified control point for authorizing who and what can get access to their online personal data.
The UMA standard has already received support from major organizations such as Philips and the New Zealand government. Access management company ForgeRock along with a number of open-source technology companies and experts, is announcing a new digital consent and privacy initiative to help accelerate developer adoption of UMA.
Using UMA, individuals are able to grant access to digital records on a need-to-know basis and for only an appropriate length of time. For example, instead of making copies of a child's healthcare records at the beginning of the school year and walking it into the school office, a parent could give temporary access to the online record then revoke it later. This would eliminate the need to duplicate personal records while maintaining privacy. In a similar fashion, financial records can be shared with authorized tax accountants and loan officers, and healthcare records can be shared with medical specialists.
Eve Maler, ForgeRock's vice president of innovation and emerging technology, says, "As organizations collect more and more user information in order to deliver more personalized experiences to consumers, failing to offer those consumers a way to actually manage that personal information themselves is a privacy time-bomb. As a leader in the adoption of open identity standards, ForgeRock believes UMA is the right solution to apply before the problem explodes".
You can find out more about UMA and the OpenUMA community dedicated to improving it on the ForgeRock website.
Photo credit: Ivelin Radkov / Shutterstock
-

Malware writers turn back the clock as MS Office macro attacks resurface
Publié: juillet 28, 2015, 11:32am CEST par Ian Barker

When Microsoft turned off default execution of macros in Office their popularity as a means of delivering malware declined. But thanks to the use of social engineering techniques to get people to turn them on, macro attacks are making a comeback.
This is one of the findings of the latest mid-year security report from networking specialist Cisco. In two recent campaigns Dridex Trojans were delivered as attachments to emails -- each sent to specific recipients -- purporting to deliver invoices or other important documents.
Other findings in the report are the continued popularity of the Angler exploit kit thanks to its authors' recent concentration on, and quick work to take advantage of, vulnerabilities in Adobe Flash. Cisco reports that, on average, 40 percent of users who encounter an Angler exploit kit landing page on the web are compromised.
Ransomware continues to be a problem too. Cryptocurrencies like bitcoin and anonymization networks such as Tor are making it even easier for miscreants to enter the malware market and quickly begin generating revenue. To become even more profitable while continuing to avoid detection, operators of crimeware, like ransomware, are even hiring and funding their own professional development teams to create new variants and tactics.
"Ransomware exists on its reputation," says Craig Williams, Security Outreach Manager at Cisco. "Users pay up to get their data back, so they finance new generations of the malware".
Typically a ransom of between $300 and $500 is demanded, not so high that a user won't pay it or, worse, that it will motivate the user to contact law enforcement. Instead, the ransom is more of a nuisance fee. And users are paying up. Cisco reports that nearly all ransomware-related transactions are carried out through the anonymous web network Tor. This allows adversaries to keep the risk of detection low and profitability high.
The report notes that so far 2015 has seen unprecedented speed in the innovation, resiliency, and evasiveness of attacks. "Attackers have no barriers to rolling out new technology," says Williams. "While users are not as agile in moving to new versions to stop attacks".
The full Cisco 2015 Midyear Security Report is available to download from the Cisco website.
Photo Credit: Balefire / Shutterstock
-

Vulnerability in Stagefright could expose 95 percent of Android devices to risk
Publié: juillet 27, 2015, 2:59pm CEST par Ian Barker

Although you may not have heard of it, Stagefright is at the heart of the Android operating system. It's a media library that processes several popular media formats. Since media processing is often time-sensitive, the library is implemented using native code (C++) that is more prone to memory corruption than memory-safe languages like Java.
Researchers at mobile security company Zimperium have uncovered an issue in the Stagefright code that they believe to be one of the worst Android vulnerabilities to date.
Zimperium zLabs VP of Platform Research and Exploitation, Joshua J Drake, carried out the research which will be presented at Black Hat USA on August 5. The study found multiple remote code execution vulnerabilities in Stagefright that can be exploited using various methods, the worst of which requires no user-interaction. These issues could critically expose 95 percent of Android devices, an estimated 950 million units worldwide.
"Attackers only need your mobile number, using which they can remotely execute code via a specially crafted media file delivered via MMS." says Drake. "A fully weaponized successful attack could even delete the message before you see it. You will only see the notification. These vulnerabilities are extremely dangerous because they do not require that the victim take any action to be exploited. Unlike spear-phishing, where the victim needs to open a PDF file or a link sent by the attacker, this vulnerability can be triggered while you sleep. Before you wake up, the attacker will remove any signs of the device being compromised and you will continue your day as usual -- with a trojaned phone".
Android versions after and including version 2.2 Froyo are vulnerable. Devices running Android versions prior to Jelly Bean (roughly 11 percent of the total) are at the worst risk due to inadequate exploit fixes.
Zimperium reported its discovery to Google and also submitted patches. Google has acted promptly and applied these patches to internal code branches within 48 hours, but that's only the start of what will be a very lengthy process of update deployment.
Fixes for these issues require an OTA firmware update for all affected devices. Such updates for Android devices have historically taken a long time to reach users. Devices more than 18 months old are unlikely to receive an update at all.
Drake says, "We hope that members of the Android ecosystem will recognize the severity of these issues and take immediate action. In addition to fixing these individual issues, we hope they will also fix any business processes that prevent or slow the uptake of such fixes".
Two groups are already protected against the reported issues. Users of SilentCircle's Blackphone have been protected as of the release of PrivatOS version 1.1.7. Mozilla's Firefox, which is also affected, has included fixes for these issues since version 38.
Zimperium advises users and enterprises to contact their device manufacturer and/or carrier to find out whether or not their device has been updated with the necessary patches.
Image Credit: Vepar5 / Shutterstock
-

Preventing IoT cars from being hacked
Publié: juillet 27, 2015, 12:16pm CEST par Ian Barker

We reported last week that a number of Fiat Chrysler vehicles were being recalled due to the potential for them to be hacked.
Experts at IoT security specialist INSIDE Secure have been looking at the risks and how vehicles can be made more secure in future.
Previously access to a car's systems was only via a diagnostic port either under the hood or on the dash. But in any modern car there is a series of increasingly powerful computers on several networks. The problem is that there are now connections between information systems (SatNav, Radio head unit, etc) and control systems (ECU, Transmission) and safety systems (ABS brakes, 4WD, tyre pressure sensors, lights) which are increasingly interwoven with each other. Add in Cellular, Wi-Fi, BlueTooth NFC and other inputs and you have a car that can potentially be hacked from anywhere.
The car has pretty much become a data center on wheels but lacks the perimeter defenses that protect traditional data centers. This means that security is often down to individual components, sometimes relying on basic hardware authentication. However, rarely has anyone thought about the interaction of thousands of lines of software code in these components.
INSIDE Secure suggests that the way to address this is via a more holistic approach. Manufacturers need to ensure that the executables for each individual component are secure. They can do this by adding cryptography to ensure that communications and authentication between software inside a device and between devices are authenticated and that the software is only allowed to run in the manner designed by the coder.
Manufacturers should also add in remote security monitoring to alert if there is a software or network breach. This means they don’t have to rely on spotting known attacks. INSIDE Secure's VP of Business Development, Douglas Kinloch concludes, "In other words, the car network has to be treated in the way that the mobile payment folks are treating mobile phones, a potentially hostile environment, and act accordingly".
More information on INSIDE Secure’s solutions to secure chips and other system elements is available on the company's website.
Image Credit: cybrain / Shutterstock
-

New password manager aims to reach people who don't use password managers
Publié: juillet 24, 2015, 4:41pm CEST par Ian Barker
We're always being told that we need to use stronger passwords, but most of us tend to trade off security for real world convenience.
Minneapolis-based Password Boss is hoping to convert people with the launch of its free password manager and digital wallet aimed at consumers.
According to a Harris Interactive survey of 2,030 US adults conducted for Password Boss, 92 percent of consumers don’t use a password manager to store their passwords for online accounts. Instead 63 percent say they memorize them, while 43 percent say they write them down on paper. The survey also found that more than half of consumers (54 percent) agree that they need to change their online password habits.
"Most people aren't motivated to change their poor password habits," says Password Boss founder and CEO Steve Wise. "Despite the fact that four of ten companies were hacked in 2014, most of us continue to use and reuse crackable passwords that are easy to remember, store passwords in unsafe places and rely too much on clicking 'forget password' links. As consumers, we want things to be easy. That’s why we created Password Boss. By securely storing personal information and synchronizing it across all devices, Password Boss is the easiest way for people to safely login to websites, access their accounts and shop online".
Password Boss is the only free password manager that allows people to store an unlimited number of passwords, choose where their data is securely stored and share any item in their account with anyone they choose.
It uses 256-bit AES encryption to protect data and synchronizes consumers’ accounts across all of their devices instantaneously for easy access to their passwords and personal data at any time and from anywhere. It also provides a personal security score with recommendations on how consumers can increase their level of online security.
Password Boss is available free for download on Windows PCs and tablets, as well as iOS and Android mobile devices. There’s also a premium, paid version with extra features including features like online backups, 2-step verification and unlimited, secure password sharing. For more details visit the Password Boss website.
-

Enterprise cloud economy is booming
Publié: juillet 23, 2015, 6:24pm CEST par Ian Barker

The market for enterprise technology products is booming with 72 percent of high-technology providers reporting growth in sales quote volumes according to a new report.
According to the SAAS Purchases Report from sales quoting software specialist SteelBrick this market is growing much faster than the overall US economy.
The report looks at how enterprise companies are selling to customers and also examines B2B selling trends compared to the same time last year. SteelBrick ran the survey online during May 2015, based on a poll of over 130 SteelBrick customers, 80 percent of which work in the high-tech economy, including SaaS, storage, cloud infrastructure, telecommunications, networking, and big data leaders.
The report also shows that sales are up, closing times are down and overall quote volumes are up, indicating a growth in demand as enterprise technology shifts to the cloud and seeks to make sense of the big data being generated by accelerating mobile and cloud adoption.
Other findings are that in the first quarter of this year sales teams have seen a 12 percent year-over-year increase in the number of quotes being processed. Sales cycles are shorter too, high-tech companies report sales cycles of 100 days compared to up to a year across the board. On average tech companies are successfully closing 38 percent of the quotes they issue, again indicating robust demand.
SteelBrick says that its Configure, Price, Quote (CPQ) software helps companies improve turn around times and eliminate errors in quotes.
"Our new barometer for the high-tech economy shows that sales of enterprise technology are growing at a robust clip as cloud and mobile adoption accelerate. Furthermore, many tech companies are becoming more sophisticated around the process of selling software services and are now implementing CPQ tools in conjunction with their CRM platforms, helping them sell even faster and more efficiently than their high-tech peers," says Godard Abel, CEO of SteelBrick. "By polling our customers, we are able to provide benchmarks for sales process efficiency and growth, as well as validate how our solution is helping them grow their business to become Silicon Valley’s next big unicorns".
You can see more findings from the report on the SteelBrick website.
Photo Credit: Andy Dean Photography/Shutterstock
-

Mozilla Developer Network turns 10
Publié: juillet 23, 2015, 4:18pm CEST par Ian Barker

In February 2005 a small team of developers set out to create an open, free, community-built online resource for all Web developers.
A few months later, on 23 July, 2005 the original Mozilla Developer Network wiki site launched. Since then it has evolved steadily for the convenience and the benefit of its users.
Ten years on and MDN hosts more than 34,500 documents and its global volunteer community is bigger than ever.
Currently, MDN has more than 4 million users with over 1,000 volunteer editors per month creating and translating documentation, sample code, tutorials and other learning resources for all open Web technologies. These include CSS, HTML, JavaScript and everything else that makes the open Web as rich and versatile as it is.
Milestones along the way include the development of its own Kuma wiki platform in 2012, and a complete redesign of the front end in 2013.
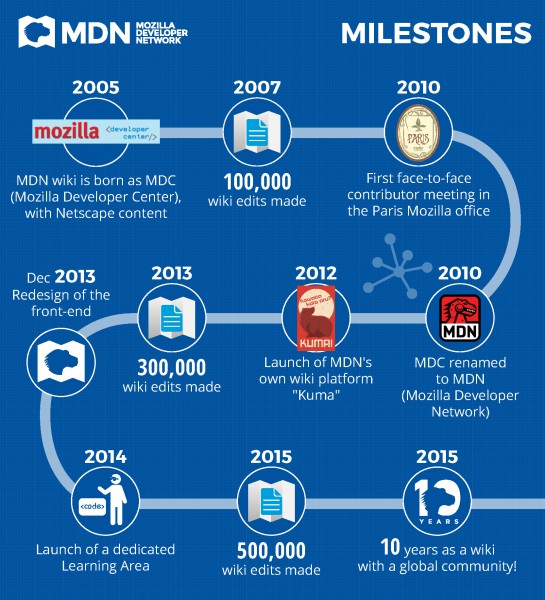
To celebrate the birthday it's produced an infographic showing some facts and figures on how the network is used. Visitors to the network are spread across the world with 26 percent coming from the USA.
The most viewed documents relate to JavaScript, CSS and Firefox. MDN isn't just for experienced developers though, there are 90 articles for complete beginners and people learning the Web. There's more information on the Mozilla blog or in the facts and figures infographic below.
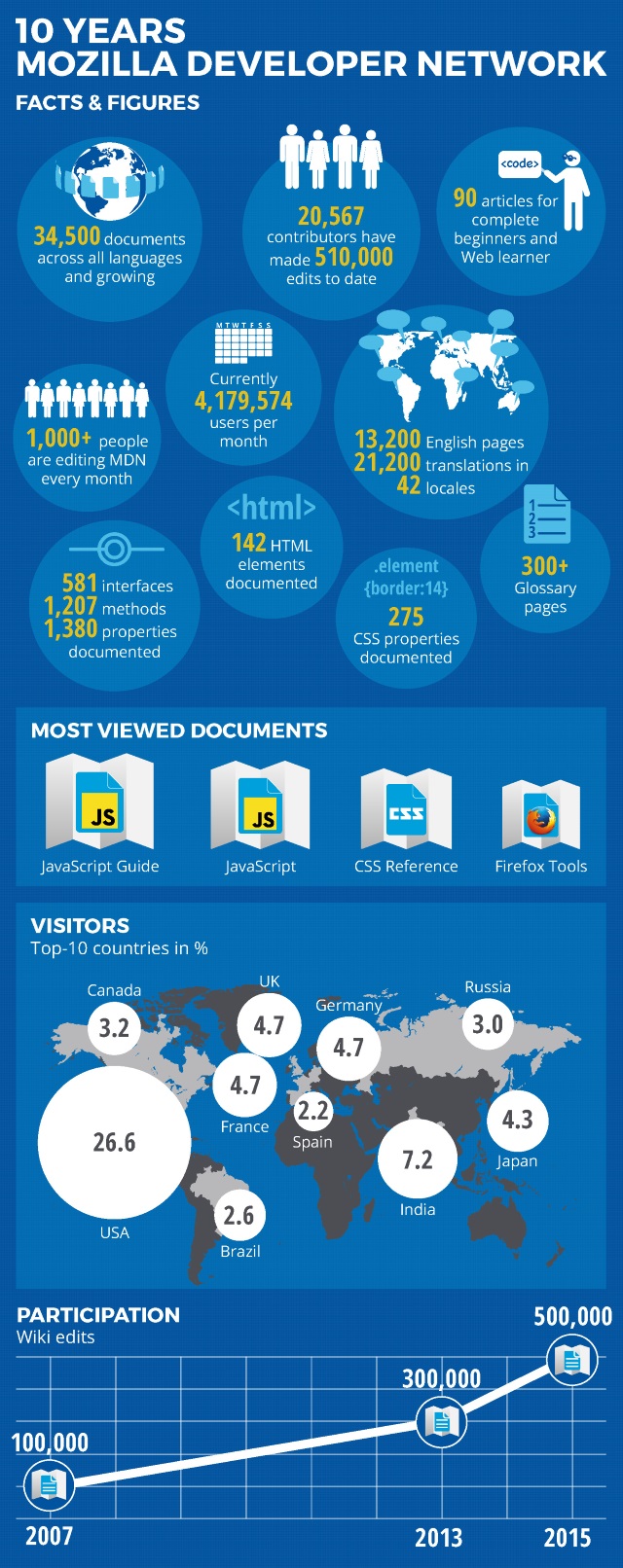
Photo Credit: Elena Schweitzer/Shutterstock
-

New collaboration helps deliver self-serve analytics solutions
Publié: juillet 23, 2015, 3:48pm CEST par Ian Barker

Business intelligence is only of use if it can be delivered quickly to decision makers. That's why there's increasing demand for self-service solutions that make it easy for managers to extract information.
Enterprise BI specialist Pyramid Analytics is announcing a strategic collaboration with Microsoft to deliver development collaboration and technology integration.
The partnership will bring new features to the Microsoft Power BI Desktop. Among these will be an option to publish a Power BI Desktop file to Pyramid Analytics Server making integration between the two easier.
"Organizations are getting hooked to self-served data discovery, but want to expand the benefits beyond departmental or individual usage," says Omri Kohl, co-founder and CEO of Pyramid Analytics. "Our clients come to us to scale BI adoption and share analytics content across the enterprise. Our work with Microsoft will give Power BI Desktop users the ability to publish files to an on-premises or private cloud server for broad collaboration on BI content".
Pyramid Analytics offers a turnkey enterprise analytics solution that makes it easy to self-serve and share trusted BI content. Its approach not only ensures data integrity and privacy, but also drives meaningful, contextual, and collaborative analytics that can work for both IT and business goals. This allows organizations to expand and scale their BI adoption via governed sharing of analytics content, reports, data models, business logic, and more across the whole enterprise.
"Pyramid Analytics brings technology that complements Microsoft SQL Server Analysis Services and uses all of the features of the Microsoft BI stack," says Amir Netz, Technical Fellow at Microsoft. "Pyramid Analytics has a proven record of partnering with Microsoft to deliver analytics solutions to meet the needs of our joint customers".
More information on the collaboration can be found on the Pyramid Analytics website.
Image Credit: leedsn/Shutterstock
-

New tool helps businesses understand and optimize APIs
Publié: juillet 23, 2015, 3:11pm CEST par Ian Barker

APIs provide a convenient way of giving developers the building blocks needed to extract data from and gain insights into digital systems.
But it's important for organizations to know how APIs are performing, how they are being used and whether they're providing business value. To help with this API and cloud integration specialist Akana is launching Envision, an enhanced API analytics platform that helps enterprises to find critical insights across their systems.
"In today's digital economy, data-driven insights are proving to be a key differentiator for businesses. Understanding the data that is being tunneled through their APIs and how it can be used to optimize their business and operations is of paramount importance," says Alistair Farquharson, CTO of Akana. "We have delivered Akana Envision to extend the Akana API Management platform with powerful analytics capabilities so that digital businesses can increase agility and adapt based on intelligent insights gleaned from their API programs".
The Envision platform can be used to perform complex custom analytics or integrate with an existing analytics platform to reduce infrastructure redundancy. It targets enterprises that require advanced analytics and insights around their APIs and the data that is exchanged through them.
The platform can also help identify new opportunities and provide insights to improve business models. Envision API Analytics can identify top APIs by usage, monetization, app type, platform or channel. API owners can analyze licenses and usage as a means to fine-tune developer and partner integration. Operationally, IT professionals can use Envision to analyze how their infrastructure responds to requests from different devices, locations and request types. Enterprises gain the ability to manage the quality-of-service of their APIs, oversee quota usage and troubleshoot and react to problems before they impact on the business.
Features include policy-based data collection for regulatory and security compliance, pre-configured reports and dashboards, data import from external sources, and the ability to export to external analytics tools for further analysis.
Envision is available from today and you can find more details on the Akana website.
Image Credit: Profit_Image / Shutterstock
-

Mac security software on test
Publié: juillet 23, 2015, 11:07am CEST par Ian Barker

Not so long ago most Mac users would have told you that their systems didn't need any form of protection as they were inherently safe. But the world has become a more dangerous place and last year the iWorm malware is thought to have recruited some 18,000 Macs into a botnet.
Whilst experienced users who are careful about what they install and where they go online may still be justified in feeling safe using a Mac without additional protection, there's no doubt that non-experts need extra security. Particularly as cyber criminals have started to target Macs because they know more of them are unprotected.
Independent testing company AV-Comparatives has been testing 10 Mac security products to assess their usability and malware protection abilities.
The products tested are a mixture of free and paid programs: Avast Free Mac Security, AVG AntiVirus for Mac, AVIRA Free Antivirus for Mac, Bitdefender Antivirus for Mac, ESET Cyber Security Pro, F-Secure SAFE for Mac, Intego Mac Premium Bundle X8, Kaspersky Internet Security for Mac, Kromtech MacKeeper, and Sophos Anti-Virus for Mac.
All were tested on OS X 10.10.3 Yosemite, against 105 samples of recent Mac malware. Compared to its Windows equivalent a Mac security product only has to identify a relatively small number of samples, but it needs to to protect the system against all threats that have not yet been blocked by OS X itself. Of those tested seven achieved 100 percent detection, two (Avira and BitDefender) 99 percent and one (Kromtech) 98 percent.
All were assessed as having good interface usability though Kromtech comes in for criticism that its initial analysis can prove misleading and delivers different results depending on whether it's run from an administrator or standard account.
For a more detailed analysis of each product you can download the full report from the AV-Comparatives website.
Photo Credit: Jirsak/Shutterstock
-

Financial services companies turn to mobile messaging
Publié: juillet 22, 2015, 3:32pm CEST par Ian Barker

With financial services companies more at risk from the consequences of a data breach than other businesses, they're on the look out for the safest, most secure communication channels to interact with customers and employees.
New research from IDC and mobile engagement specialist OpenMarket reveals that mobile messaging is the top tool many are utilizing to accomplish this task with 80 percent of global financial services organizations using Global SMS/mobile messaging to communicate and share sensitive info.
This is seen as having a big effect on customer experience with 80 percent of these businesses believing SMS has a considerable or major impact on customer service and 73 percent considering it to be very effective for employee-focused emergency alerts.
Other findings from the study are that more than half of organizations use mobile messaging to differentiate or improve the customer experience, while 35 percent use the technology to attract and retain new customers.
More than 25 percent use it to improve their risk mitigation and more than 20 percent use it to ensure business continuity and to enhance multichannel delivery capacity. However, only 15 percent use mobile messaging to improve their organization’s security.
Because it's secure and scalable, and with critical capabilities such as two-factor authentication for fraud detection, secure SMS technology is being rapidly adopted industry-wide. According to the research, the top customer-facing uses for SMS include timely offers and notifications regarding high-risk, high-dollar transactions. Secure SMS messaging is used to gain deeper customer insights and to meet industry compliance requirements by 30 percent of companies.
Internally, financial services organizations use mobile messaging as a key component for employee communication and contingency planning to improve their internal security and enable secure employee notifications. Business leaders are also driving new investments in mobile messaging and are closely involved in solution, specification, selection, and deployment to ensure that technologies are meeting the standards the industry.
"These findings show that financial services organizations are incorporating secure, effective mobile messaging into many aspects of their customer service and employee communications, as well as their internal business operations," says Jay Emmet, General Manager of OpenMarket. "A well-designed, company-wide mobile messaging strategy that meets the industry’s high-compliance and regulated standards will allow businesses to enhance the customer experience, gain additional customer insights, improve employee relations, and drive operational efficiencies".
More detail is available in the full report which can be downloaded from the OpenMarket website.
Image Credit: 3Dstock / Shutterstock
-

New techniques to deal with data breaches [Q&A]
Publié: juillet 22, 2015, 11:43am CEST par Ian Barker

It's easy to think of data breaches as being someone else's problem, until you're affected by one yourself. Because breaches can involve large volumes of data, dealing with one can be a lot of work.
Can new techniques in capturing and storing data help to ease the burden on IT teams and even help prevent breaches in the first place? We spoke to Perry Dickau, director of product management from data-aware storage provider DataGravity to find out.
BN: How can better data storage techniques help with visibility into security issues?
PD: Most companies don't even know what’s in their data, so they can't ensure adequate protection is in place -- it's that simple. Files containing sensitive information -- such as intellectual property, customer identification numbers, tax audit or financial data, or Social Security or credit card numbers -- are often mistakenly saved to public servers, rendering them vulnerable to an external threat or internal management issue. For example, if you left diamond jewelry sitting in plain view of a window and then left home for the weekend, you'd be making a thief's job easy. Just having your internal storage 'house' in order can go a long way toward mitigating potential breaches and the subsequent fallout. And, while the threat of a data breach is always looming, regulatory compliance violations can spark fines and industry-specific security issues.
BN: What is 'data-aware' technology?
PD: Traditionally, storage is seen and treated as a stagnant box in your data center where information would rest and usually fade into long periods of inactivity. It didn't matter if stored data contained information that could improve your business or compliance violations that could wreak havoc during a tax audit.
Storage of that type doesn’t have a place in today’s data-driven IT landscape. You need to ask critical questions of your data to adequately manage sensitive information. For example, "Where is our sensitive data?" "What happened to our misplaced files?" "Can we detect a breach based on suspicious user activity?" "Are we wasting our storage budget by saving and protecting the wrong files?" Data-aware technology can answer, even raise, those questions for you. If your storage is data-aware, it's collecting insights and giving you unprecedented risk awareness, allowing your team to collaborate and become more productive. It also illuminates how your IT budget should shift.
BN: Is data-awareness limited to storage?
PD: Not at all. Data awareness manifests differently throughout the IT stack. Storage has come a long way, but new breakthroughs are also taking place in networking, applications, data migration and endpoint security. Palo Alto Networks, Informatica and similar companies are pioneering the data-aware charge, as well. It will take time and collaboration between vendors, analysts, investors, partners and end users before the entire enterprise ecosystem can become fully data-aware, but given today's headlines about high-profile hacks and data leaks, the need couldn't be more dire.
BN: Isn't there an increased cost and complexity involved in keeping all the data needed to understand and fix security issues?
PD: Not when those data insights are being gathered, identified and recovered on a near-instant basis. If you can streamline your processes for storing, managing and securing sensitive data, and you can enhance employee productivity and collaboration in a holistic process, you're actually cutting costs. When you're data-aware, fixing security issues is more a matter of letting go of complexity than introducing new layers.
BN: Many businesses now have a mix of on-site, cloud and hybrid systems. How can they ensure data is protected at all levels?
PD: A popular myth is that security breaches usually result from third-party attacks, but your internal users actually pose the biggest security risk in any part of your system. The Ponemon Institute reports that 78 percent of breaches begin within an organization. The actions causing these issues aren’t always malicious – an employee might save a spreadsheet to a consumer-facing file share, or use a public Wi-Fi network without realizing the document contains customers' personally identifiable information (PII). You can combat these risks by employing security guidelines among your team members, conducting frequent audits to check the security status of your core on-premise data and setting up security alerts. Then, extend this protection to your hybrid and cloud networks by working with a channel partner who's an expert on the platform in question and understands the nuances of your industry.
BN: Is it possible to stay ahead of the hackers and stop a breach before it occurs?
PD: The best strategy to combat attacks by hackers is two-fold: first, confirm that sensitive data is in the appropriate location and is not exposed. Second, monitor your infrastructure for suspicious user activity and limit access rights to your sensitive data. In other words, ensure information is available to the people who should have it and protected from the people who should not. There's a reason Cisco Systems reported last year, "all organizations should assume they've been hacked." Cyber criminals' strategies are rapidly evolving, and sooner or later, your network will be compromised -- if it hasn't been already. You just need to take steps to ensure they won't reach your company's crown jewels once they've broken in.
BN: Does this help to guard against internal threats too?
PD: Yes. For example, if an employee is planning to leave the organization, she might begin transferring client information and intellectual property to personal data stores to take with her. Or, an employee might become frustrated at the company and attempt to delete critical files in an act of malice. Data-aware technology helps storage and security administrators pick up on these issues by quickly identifying anomalous activities, so teams can react and mitigate the risks and damage.
Image Credit: Sergey Nivens / Shutterstock
-

New security service helps protect the Internet of Things
Publié: juillet 20, 2015, 3:52pm CEST par Ian Barker
The Internet of Things is growing fast, according to Gartner around 4.9 billion devices will be in use this year, up 30 percent on 2014, and there could be 25 billion IoT devices by 2020.
But with all of these devices being rushed to market security can be left behind. According to managed security specialist Trustwave's 2015 Security Pressures Report, 77 percent of respondents said they had been pressured to unveil IT projects that were not security ready.
To combat this issue, Trustwave is announcing a new set of managed security services -- Trustwave Managed IoT Security. These services are designed to help manufacturers and developers of Internet of Things technologies identify and fix security vulnerabilities within their products before they hit the market, as well as helping business end users using IoT technologies prevent IoT-related cyber-attacks.
"As everyday objects connect to the network, IT teams struggle to manage assets and attack vectors previously outside their purview," says Steve Kelley, Senior Vice President of Product and Corporate Marketing at Trustwave. "Manufacturers of those products also struggle with getting them out to market on time while ensuring security. Trustwave’s Managed IoT Security helps both parties overcome those challenges by identifying and remediating security weaknesses within the products and ecosystem surrounding them in addition to round the clock monitoring to detect and deflect a breach".
Trustwave Managed IoT Security works on two levels. Developers and providers of IoT products and services can use it to find weaknesses in embedded devices, back-end services and the connections in between. Trustwave's elite team of ‘SpiderLabs’ ethical hackers attempt to compromise devices by exploiting vulnerabilities in the hardware, software and the manufacturers’ servers that provide the link between IoT devices and applications.
In addition it monitors the security of the IoT ecosystem. This helps protect organisations from the security challenge brought about by a raft of new and unusual, devices. Businesses can access Trustwave's Managed IoT Security services through the company’s cloud-based portal, Trustwave TrustKeeper.
Managed IoT Security will launch on Wednesday (22 July) and more information will be available on the Trustwave website.
Image Credit: PlusONE / Shutterstock
-

TV and porn dominate piracy statistics
Publié: juillet 20, 2015, 11:07am CEST par Ian Barker

With the launch of Apple Music and a number of high-profile artists withdrawing their music from streaming services, piracy has been in the headlines of late.
But a new infographic from application security company Arxan reveals that piracy of music is only a small part of the overall problem.
Between 2012 and 2014 the average number of pirated assets 1.6 million per year, that’s expected to increase to 1.96 million this year. However, only 12 percent of pirated material is music. Television on 24 percent and adult material on 23 percent make up the bulk of pirated assets, movies account for 14 percent and even ebooks and magazines (also on 14 percent) account for more than music.
In monetary terms, out of $109 billion worth of pirated assets in 2014 the vast majority ($73 billion) was accounted for by movies, $18 billion by TV and $12 billion by music. Adult content, despite its high percentage of total content, was worth only $6 billion dollars -- sex, it seems, is cheap.
More detail including the distribution model for pirated material and the amount of bandwidth it takes up is in the infographic below.
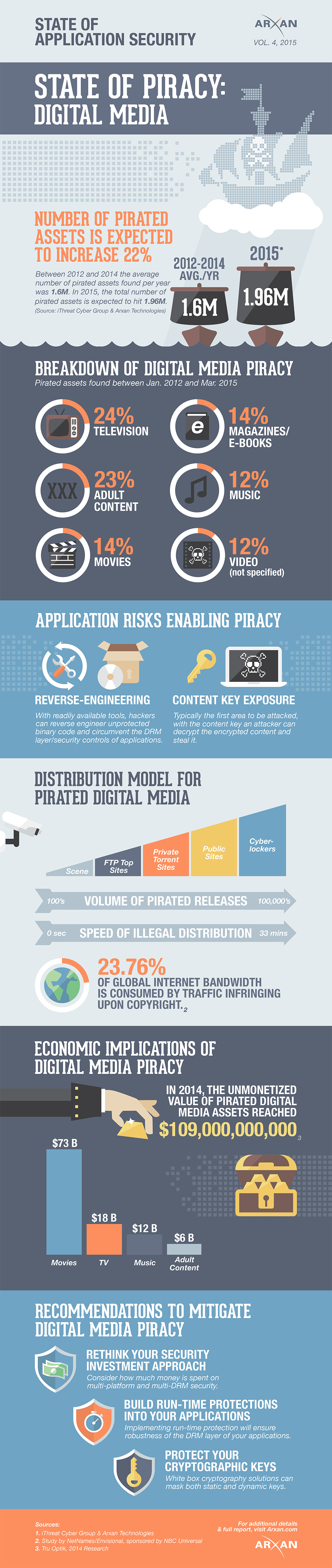
Image Credit: Marcos Mesa Sam Wordley / Shutterstock
-

Application monitoring tools are often underused
Publié: juillet 17, 2015, 5:27pm CEST par Ian Barker

Enterprises may have eleven or more commercial tools in place for application performance management (APM), yet they're not using them effectively according to a new survey.
Application intelligence company AppDynamics has released the results of a survey, conducted by Enterprise Management Associates (EMA), of IT professionals from companies of all sizes across both North America and Europe, looking at the APM solutions they have in place, monitoring gaps, and the time and resources required to resolve application-based issues.
Findings include that 65 percent of the companies surveyed own more than 10 different commercial monitoring products. But nearly half also indicated that 50 percent or fewer of their purchased tools are actively being used.
Calls from users are the second most frequent way that IT organizations find out about application-related problems (27 percent cited detection by monitoring centers; 25 percent cited user calls). For problems escalated beyond level one support, mean time to repair (MTTR) is most often between five and seven hours. It can also take between three and four people to solve a given problem.
"Based on our findings, the majority of companies are still trying to manage complex applications with a combination of siloed tools, 'all hands on deck' interactive marathons, and tribal knowledge," says Julie Craig, research director, application management at EMA. "The ability to automatically discover and manage the business transaction topology as the application itself changes is a significant challenge encountered by virtually every IT organization".
When asked what they wanted from APM tools, 75 percent identified flexible deployment options as a critical factor, while 70 percent want the ability to monitor infrastructure as a service (IaaS) public cloud systems.
In terms of feature preference the top three 'must-haves' are: an integrated monitoring platform, cloud readiness, and support for trending and reporting.
More details about the survey and its findings are available on the AppDynamics blog.
Photo Credit: Sergii Korolko/Shutterstock
-

Tracking cloud use and costs is an essential part of the IT function
Publié: juillet 17, 2015, 3:11pm CEST par Ian Barker

Businesses turn to the cloud in search of efficiency and cost savings, so being able to measure how successful a strategy is at these aims is important.
A survey by hybrid financial management provider Cloud Cruiser shows that 72 percent of respondents indicated that tracking cloud usage and costs is extremely or very important to their IT function.
The study by Dimensional Research surveyed 279 IT professionals who attended the recent Microsoft Ignite 2015 event and reveals that 92 percent of those surveyed say they are pursuing a cloud adoption strategy with the primary goals of improving IT efficiencies and reducing costs.
"This latest survey is representative of what we are seeing in the market with our partners and enterprise customers," says Deirdre Mahon, Chief Marketing Officer, Cloud Cruiser. "Once an organization gets serious about cloud, they quickly hit a wall in terms of tracking usage and gaining full control on forecasts -- essentially delivering services with efficiency and agility. Cloud Cruiser addresses that pain across the broadest range of cloud services today".
Other findings show what respondents would like to do if they had access to consumption or cloud usage information across their entire enterprise. Of those surveyed 57 percent would improve IT forecasting, 39 percent compare costs across different cloud service platforms, 37 percent implement showback and/or chargeback policies, 34 percent would expand their on-demand and self-service options access to the cloud and 30 percent would better match allocation to utilization.
The full survey results are available to download from the Cloud Cruiser website.
Photo credit: Tom Wang/Shutterstock
-

Spam drops below 50 percent of email for the first time since 2003
Publié: juillet 17, 2015, 1:48pm CEST par Ian Barker

For the first time in more than a decade the amount of spam has fallen to less than 50 percent of the total volume of email.
According to the latest Symantec Intelligence Report, the overall spam rate has dropped to 49.7 percent, the first time a figure this low has been recorded since September 2003.
Phishing rates and email-based malware were also down this month. It's not all good news though as there were 57.6 million new malware variants created in June, up from 44.5 million pieces of malware created in May and 29.2 million in April. This increase in activity suggests that, with the continued drops in email-based malicious activity, attackers are simply moving to other areas of the threat landscape.
Ransomware attacks were up in June too, with over 477,000 detected during the month. While still below the levels seen at the end of 2014, this is the second month in a row that ransomware attacks have increased since they reached a 12-month low in April.
Targeted attacks on the manufacturing sector fell from 41 percent in May to 22 percent. Manufacturing still comes out on top in terms of sectors being subjected to targeted attacks, but the activity is now in line with what is being seen in the Finance, Insurance, and Real Estate sector and the Services -- Professional sector, which come in at second and third place. It's interesting too that 38.1 percent of attacks were directed against companies with fewer than 250 employees.
On social media 83 percent of threats relied on users to spread them by sharing videos, offers and other messages. 11 percent tried to get users to join fake groups in order to expose their details to hackers, five percent used 'likejacking' to get users to click fake website buttons that install malware and may post updates on a user's newsfeed.
More detail is available in the full report which is available to download from the Symantec website.
Photo Credit: Balefire/Shutterstock
-

A short history of text messaging
Publié: juillet 16, 2015, 4:35pm CEST par Ian Barker

The text message has become such a key part of our modern lives that it's hard to believe that the concept behind it dates back 31 years. Email to SMS gateway service Neon SMS has produced an infographic tracking how SMS has evolved.
The first text message was sent in 1992, although it had to be from a PC because it was the following year before Nokia introduced the first SMS-enabled phone. In 1997 the Finnish company produced the 9000i Communicator, the first mobile phone to feature a full keyboard.
However, it wasn’t until 1999 that it became possible to exchange SMS messages across networks. In the same year short codes were introduced, allowing businesses to provide an easier way of contacting them.
The 2000s saw SMS put to new uses with American Idol pioneering 'text to vote' in 2003, and the first 'text to donate' campaign launching in 2008. Bulk texting was used by Barack Obama in 2008 to announce his presidential running mate. In 2010 the verb 'texting' made it into the dictionary for the first time.
For a look at these and other milestones, plus why SMS is still popular as a business tool, take a look at the infographic below.
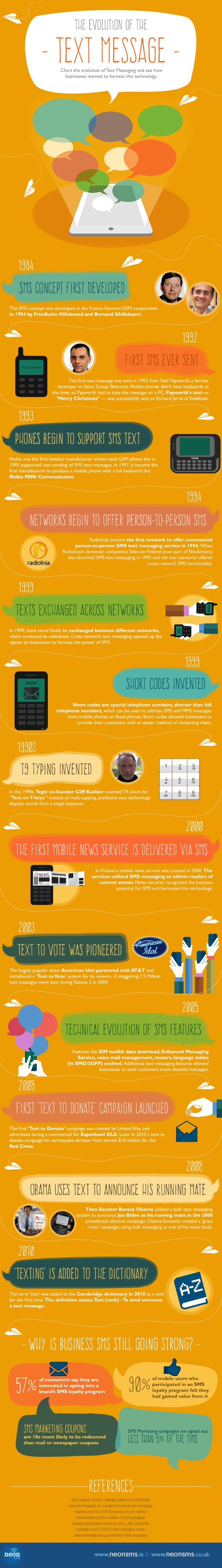
Photo Credit: Potstock / Shutterstock
-

New process removes the risk from accepting bitcoin payments
Publié: juillet 16, 2015, 3:52pm CEST par Ian Barker

One of the things that inhibits merchants from accepting bitcoin payments is that there’s a time lag in receiving cleared funds. A bitcoin payment can take around 10 minutes to be verified and confirmed on the blockchain.
Even then most payment processors will wait for 2-6 confirmations (taking 20-60 mins) before guaranteeing to the merchant that the transaction in complete and the merchant will receive the funds. For merchants used to accepting card payments which are verified in seconds this is a problem.
But now payments processor Bitnet is introducing a new 'Instant Approval' system that looks at a bitcoin transaction and, in less than 10 seconds, assesses the probability that the transaction will be confirmed on the blockchain and sends the merchant a notification. Bitnet guarantees the payments this service approves, simplifying the acceptance of bitcoin for merchants.
Bitnet has partnered with BlockCypher, a blockchain web services company, as a key data provider for the new service. The Instant Approval process relies on a number of data points, crucial to which are BlockCypher's double-spend detection and transaction propagation metrics.
"One of the biggest challenges for merchants wanting to accept bitcoin is how to accommodate the delayed confirmation times into their 'real-time' checkout flows and still be assured of being funded," says Seamus Cushley, VP Product at Bitnet. "We partnered with BlockCypher to provide key data for our 'Instant Approval' service due to their best-in-class metrics and enterprise service".
You can find out more about how merchants can reduce the risk in handling bitcoin payments on the Bitnet website.
Photo credit: ppart/Shutterstock
-

DataSift brings machine learning to analyzing social data
Publié: juillet 16, 2015, 3:23pm CEST par Ian Barker

Information from social media is becoming more and more important to many companies. But extracting data and getting something useful from it can prove difficult.
Business intelligence specialist DataSift is launching a new technology called VEDO Intent, which aims to take social analysis further, gaining more nuanced insights into markets and customers using machine learning.
Previously this sort of analysis would have always relied on human input, but by using an approach known as Active Learning, VEDO Intent learns as posts are manually classified into categories such as rant, rave, purchase intent or churn. VEDO Intent then dynamically builds a machine learning-based model to at first suggest, and then fully automate, the real-time classification of millions of posts to uncover insights that previously would have been hidden. By having a system carry out the data analysis it also helps protect individuals' privacy.
"Organizations have long recognized the huge potential of social data -- it's the voice of the market and the voice of your customer. Companies are now hungry to go beyond sentiment analysis into more advanced insights," says Tim Barker, Chief Product Officer at DataSift. "Social data has evolved. Everyone from financial institutions through to the United Nations refers to it and we recognized that people need actionable, nuanced insights from social data to better understand their audience’s mood and intent".
The company is also launching a forum to help developers and data scientists share statistical models that form the building blocks of advanced analysis. Helping guide researches to the keywords and hashtags they should be using in their analysis for example.
More information about VEDO Intent and the forum can be found on the DataSift website.
Image Credit: Oleksiy Mark / Shutterstock
-

UK government launches voucher scheme to boost small business security
Publié: juillet 16, 2015, 1:01pm CEST par Ian Barker

For smaller businesses cyber security isn't always their highest priority which means they can be left vulnerable to attacks.
In an effort to beef up protection for small and medium businesses, the UK government is launching a voucher scheme as part of a package of measures designed to increase the resilience of UK businesses to cyber-attacks.
The package also includes a new online learning and careers hub to help ensure the UK has the cyber skills talent pool to protect both the public and private sectors as it faces the reality of increasing cyber threats.
"We want to help protect UK businesses against cyber attack and make the UK safest place in world to do business online," says Digital Economy Minister Ed Vaizey. "The new voucher scheme will offer increased protection for small businesses, and the new online hub will help ensure we have the skilled workforce in place to manage the increased pressures of the digital age".
The voucher scheme, which launches later this month, will offer micro, small and medium sized businesses up to £5,000 for specialist advice to boost their cyber security and protect new business ideas and intellectual property. The scheme will be overseen by the Government’s innovation experts at Innovate UK.
The new Inspired Careers online skills and career hub is being launched today and has been developed by industry body CREST along with the Government to tackle the skills shortage in cyber security.
The hub features careers information and advice, internship and apprenticeship opportunities, academic and professional training courses, work experience and senior level vacancies, and will be a powerful tool to promote the cyber security profession and encourage the next generation of cyber specialists to help protect the UK.
As part of a National Cyber Security Programme the Government is investing £860m between 2011 and 2016 to protect the UK in cyber space. More details of information security policy are available on the Government's site.
Image Credit: fredex / Shutterstock
-

Huddle launches desktop app for easier collaboration
Publié: juillet 16, 2015, 12:05pm CEST par Ian Barker

Business collaboration specialist Huddle is launching a new desktop app for Windows and Mac aimed at improved productivity and greater integration with other products.
Huddle Desktop comes with plug-ins for Microsoft Word, Excel, PowerPoint and Outlook to deliver deeper integration into the user's existing desktop applications. Documents stored within Huddle can be opened, edited, and saved natively from within Office programs. Users can also view team members' comments and sync their own comments back to Huddle.
"Our goal is to make document collaboration as simple and intuitive as possible," says Stuart Cochran, CTO of Huddle. "Huddle Desktop is all about personal productivity: the app provides instant access to recent work, allows users to manage offline availability, controls and prevents version conflicts, and enables you to search all of your Huddle content. Huddle's cross-platform recent files mean you can pick up on a document you were just reading on your iPhone or iPad, and start editing on your Windows PC or Mac immediately".
Features of the new product include Full integration with Microsoft Office with the ability to read and make Huddle comments directly from Office applications and archive any Outlook email and its attachments to a Huddle project workspace or attach Huddle files to email.
Huddle Desktop provides quick, direct access to relevant files, along with instant search from the desktop to give users access to the files they need most, across all their projects and teams.
Users have the ability to lock a document, preventing any overlapping edits and providing full transparency into the status of any document at any time. Up to 50 files can be made available offline for when users don’t have a connection.
"Huddle Desktop is the perfect bridge to connect the desktop experience to the industry’s most powerful cloud-collaboration platform," adds Cochran. "For example, if I know I'm going to be without Internet connectivity, I can quickly make a file available offline through the Desktop App, then edit it, review team comments and save from within Microsoft Word. When I reconnect, Huddle Desktop will automatically manage the synchronization of the file -- and my comments -- back into the cloud for the rest of my team".
Huddle Desktop is available now for all new and existing Huddle users and you can find out more on the company's website.
Photo Credit: Pressmaster/Shutterstock
-

Jitterbit makes cloud applications more accessible with APIs
Publié: juillet 15, 2015, 4:20pm CEST par Ian Barker

As businesses move towards cloud and hybrid environments, providing real-time access to digital assets from anywhere and on any device becomes more of a challenge.
Integration solutions company Jitterbit is launching a new Harmony Live! cloud platform that lets companies quickly design, orchestrate and manage real-time APIs. This allows the connection of thousands of B2B, consumer and mobile apps, as well as smart devices and the Internet of Things.
Harmony Live! goes a stage beyond management and offers API 'orchestration'. This means that APIs are connected to the business, tied to real-time digital processes, and shared securely for plug-and-play connectivity with any system.
Harmony Live! lets non-technical users connect any on-premise system, cloud app or device and expose it instantly as an orchestrated API in minutes. Using the Jitterbit Studio, users can connect, orchestrate and manage their APIs without having to write a single line of code. In addition they can use the Workflow Designer to visually map out business processes.
Live! 'Anywhere' APIs can run in any environment while connected to the Harmony API Gateway, which exposes APIs securely, reliably and with fast response times.
These Live! Anywhere APIs can also be linked to popular apps through pre-built connectors, available for systems including SAP, Oracle, Microsoft, Salesforce, Autodesk, and NetSuite. These systems can then be securely exposed as a service connected to a specific business process that tie together employees, partners and customers. If a data source, app or device doesn't have an API, Live! can provide it with an Anywhere API, and even combine multiple sources into a composite API to offer services that tie together users, systems and processes.
Live! security controls can limit and block access to APIs and comply with industry standards. These combine with View Live! analytics to reveal how APIs are being used and allow admins to manage them proactively.
You can find out more and sign up for a 30-day trial of Harmony on the Jitterbit website.
Image Credit: rzoze19 / Shutterstock
-

The things we do for Wi-Fi
Publié: juillet 15, 2015, 3:36pm CEST par Ian Barker

We use Wi-Fi almost without thinking about it, but a new survey of users in the US and Europe reveals just how big an impact it has on our daily lives and what we're willing to do to stay connected.
Network company Xirrus polled hundreds of people about their Wi-Fi habits and expectations. The results reveal the far-reaching impact Wi-Fi has on users' lives, as well as its importance to the future.
Rapid expansion of the IoT and BYOD means that businesses need to re-evaluate how they design their Wi-Fi networks to meet users' expectations to connect anywhere, on any device, at any time. The survey finds a majority of consumers (76 percent) connect to Wi-Fi outside of their home on a regular basis. It also reveals a growing expectation of being able to get connected everywhere.
Although 79 percent of respondents don't feel that public Wi-Fi is secure, 62 percent are still willing to connect to it. More than half (66 percent) of travelers would change hotels for a better Wi-Fi experience, and 49 percent would change their preferred airline provider.
84 percent of respondents say that bad Wi-Fi has kept them from doing their job. Almost all consumers (90 percent) now own at least one connected device -- such as a laptop, smartphone or tablet -- and a surprisingly high one in three of those polled own a wearable device of some kind, such as a smartwatch or fitness band.
"We are now more than ever a mobile, wireless-reliant society," says Shane Buckley, Xirrus CEO. "The proliferation of Wi-Fi connected devices combined with the expectation of steadfast connectivity has put increased demand on Wi-Fi networks everywhere. Nowhere is this more apparent than in the enterprise. Our study highlights the need for organizations to reinforce their networks to ensure a seamless connected experience for users at all times, no matter the location".
The Xirrus Where the Wires End Survey is available to download from the company's website and there’s a summary in infographic form below.
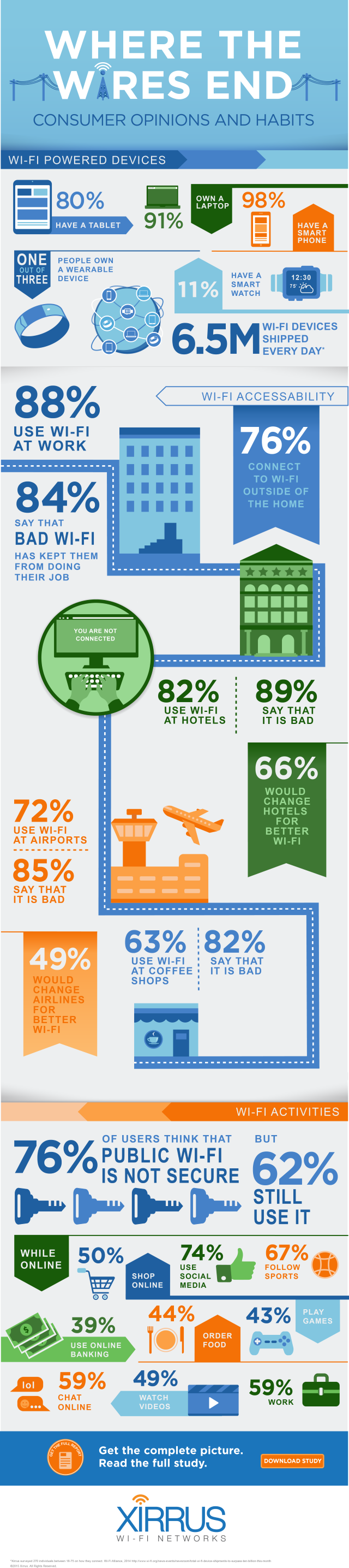
Photo credit: Shutter_M / Shutterstock
-

Edifier Exclaim Connect e10BT speakers [Review]
Publié: juillet 15, 2015, 1:39pm CEST par Ian Barker

On the whole speakers tend to be quite dull-looking pieces of kit. There's no way you can level that criticism at the Exclaim Connect though, a pair of speakers which have rather unique style.
They feel nicely weighty, the upright parts are metal and the bottom ball-like segments have a smooth rubbery finish. They look like a piece of modern sculpture or something out of a 1950s science fiction comic.
Leaving aside the looks, these PC speakers also offer Bluetooth connectivity, making them a versatile choice for home or small office use. There are three-inch subwoofers in the base of each unit and two 1.5-inch mid-range speakers in the upright parts. The power output is 2 x 8W and 2 x 10W.
They come supplied with a mains power adaptor, a cable to link the two speakers together and a 3.5mm audio cable. The right-hand speaker is the master unit and has controls for power and volume on its side. There's a red LED behind the grille to indicate that the power is on which turns blue to show that a Bluetooth connection is active.
The speakers incorporate some clever technologies. Digital Signal Processing (DSP) claims to deliver active crossover frequencies and good tonal balance, even at high volumes. While Dynamic Range Compensation (DRC) technology is aimed at keeping distortion to a minimum.
A good thing about the design is that if you're using them on a desk they sit neatly either side of a monitor and the height of the units means that the mid-range speakers are in line with your ears. However, you do need to be a little further back than normal desktop distance to get the best effect. That said, the listening experience is good with a rich tone and decent bass, though there are no bass and treble controls so you’ll need to fine tune the listening experience at source. You do get a bit of distortion if you crank up the volume too high but it's fine at normal everyday levels.
It would be nice to have a built-in microphone to allow for making hands-free calls via Bluetooth, and some bass and treble controls would have been good too, but otherwise there’s not much to fault here. You can pay a lot more for speakers without getting significantly better sound quality and you’re getting that added touch of sci-fi style with the Edifier Connect.
The Exclaim Connect e10BT currently costs £78 on Amazon in the UK ($131.77 in the US) more detail is available on the Edifier website.
-

How CRM software benefits business
Publié: juillet 15, 2015, 12:04pm CEST par Ian Barker

Customer relationship management is on target to be a $36 billion market by 2017, overtaking enterprise resource planning as the most significant enterprise tool.
Business software selection specialist Capterra has surveyed over 500 users of CRM in the US to determine the ways they find, buy and use their software.
Key findings are that more than half of users adopted CRM within their company’s first five years in business, and two-thirds of companies had at least 100 customers when they first purchased a CRM system.
A third of CRM users surveyed use Salesforce, while other software industry giants Microsoft, Oracle, and SAP combine with Salesforce to dominate 75 percent of the CRM market. On average, businesses spend $150 per user per month on their CRM, with 61 percent spending over $50.
Despite recent growth of social CRM capabilities, people still want more. The most desired CRM features were social media monitoring capabilities (25 percent) and the ability to pull in prospect information from social media (24 percent).
"This report shows that, despite four CRM industry main-stays continuing to dominate the market, businesses continue to invest heavily in CRM technology early in their life cycle," says Katie Hollar, Director of Marketing at Capterra. "This trend indicates that there's tremendous opportunity for newer, small-business CRM solutions to cater to the unique needs of startups -- especially as we see the economy rebound and more startups investing in software. And as those startups mature into larger companies, there's opportunity -- both for CRM users and for sellers of CRM software -- to continue to expand into related software categories and product offerings, such as marketing automation, help desk software, social media marketing, and other areas of the sales and marketing stack. Already, the report showed that 44 percent of CRM users had integrated their system with a marketing automation solution, and we expect that number to continue to grow in the coming years".
The research shows that businesses are using their CRM software to better measure their company's performance, boost their sales and marketing efforts, and maintain loyalty among customers. They're also using CRM data to branch into new types of business software, such as marketing automation and social media monitoring.
For the future as more businesses continue to adopt CRM, vendors will introduce add-ons and plug-ins to make better use of CRM databases, such as help desk software for customer service teams or marketing automation systems.
More information is available on the Capterra website.
Photo Credit: Mikko Lemola / Shutterstock
-

TP-Link Archer D9 AC1900 modem router review
Publié: juillet 15, 2015, 10:30am CEST par Ian Barker

Most home or small business users never even think about upgrading the router that was supplied by their internet service provider. But by simply sticking with the default box you may well be missing out on the extra features and performance of a more sophisticated router.
The Archer D9 from TP-Link offers a smart design and decent performance but at a price that undercuts much of the competition. So, is this a good choice or a budget manufacturer trying to punch above its weight?
Design
The first thing to note is that it’s quite large and it’s designed to stand upright. The stand is fixed so there’s no option to lay it down flat or mount it on a wall. The router itself stands around six-inches tall and you can almost double that when you’ve attached the three antennas to the top.
A row of LEDs along the top of the shiny, white front panel allow you to monitor its status, though there’s only one Ethernet light so you can’t check on individual ports. On the back you have three LAN ports and a LAN/WAN port, a power switch and buttons for WPS and for turning Wi-Fi on and off -- a handy touch that many routers don’t offer.
There are also two USB ports, a 3.0 on the back and a 2.0 on the side, for attaching storage or other devices.
Setting Up
Plug it in and you can access a Quick Setup mode via the browser interface that will auto detect your ISP settings so all you have to provide is a username and password. There’s also a mini CD with an Easy Setup Assistant which is good for less experienced users who aren’t confident with the web interface.
That interface is not hard to navigate but it has a vast array of options and feels like it’s very much for techies. If you know what you’re doing you’ll have no problem forwarding ports or configuring VPNs and the like.

This is a dual-band router so it provides 2.4GHz and 5GHz connections and there’s support for a guest network on both. You get limited parental control via a MAC defined whitelist. It has a bandwidth control feature too that lets you limit the amount a particular port or IP address can use. The USB ports provide access to storage, media streaming and printer support -- though you’ll need to download and install TP-Link’s own printer controller software.
In Use
Signal strength is more than adequate to cope with most domestic or small office situations. The 5GHz band offers good performance with fast data transfers (up to 1,300Mbps) and smooth streaming.
The lower speed 2.4GHz band comes into its own at longer ranges though allowing you to connect where the faster one struggles. Beamforming technology concentrates the signal towards connected devices to give more reliable operation.
Conclusion
At just over £120 currently on Amazon, the Archer D9 has a lot to offer. It performs well, has plenty of features and it feels solidly built.
There are some minor niggles, like the lack of individual status LEDs for the Ethernet ports, but if you’re looking for a good value router with lots of configuration options it’s well worth considering.
Pros
- Solidly built
- Easy setup
- Very configurable
Cons
- Only one Ethernet LED
- Web interface is very much for techies
- No wall mount option
Company Release
PriceITProPortal
ReviewCompany Site TP-LINK £120.00 7/10 Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

Consumers are ready to accept Identity 3.0
Publié: juillet 14, 2015, 5:35pm CEST par Ian Barker

There's always a trade off between access and security. Identity management specialist Gigya has released its latest State of Consumer Privacy & Personalization report looking at consumer attitudes surrounding data privacy.
A key finding is a growing willingness to accept next-generation authentication methods known as 'Identity 3.0'. Biometric technologies are emerging as a popular option for signing in. The study shows 41 percent of consumers have a high level of comfort logging in to a site or mobile app using a thumbprint or face/eye scan.
The study also shows heightened demand for data privacy and more relevant marketing communications, which consumers believe can be achieved through business transparency and personalization. More than 90 percent of consumers are at least somewhat concerned about data privacy and how companies are using customer data.
This contributes to a willingness to use existing logins, 59 percent of consumers say they are willing to register or log in to a website or mobile application with an existing identity from a payment provider such as PayPal or Amazon. 57 percent say they would be prepared to use their Apple ID.
Also 88 percent of US consumers have logged in to a website or mobile application using an existing social network identity, an 11 percent increase over last year’s findings. This is happening across demographic groups, 75 percent of consumers aged 55 and over have used a social identity to authenticate on a site or mobile app.
An aversion to filling out online registration forms (56 percent) and not wanting to remember yet another user name and password (43 percent) top the list of reasons why consumers choose to use social authentication. Being able to use the same identity on all devices and websites to get a more personalized experience is the third most cited reason at 25 percent.
"Although data privacy concerns are seemingly at an all-time high, it's evident that consumers are prepared to share their personal information with businesses if presented with a clear value exchange and a high level of transparency," says Patrick Salyer, CEO of Gigya. "In addition, as consumers continue to embrace advanced authentication methods, brands must equip themselves to handle an increasing volume and variety of rich identity data in order provide truly relevant 1:1 experiences".
The full report is available to download from the Gigya website or there's a summary of the findings in infographic form below.
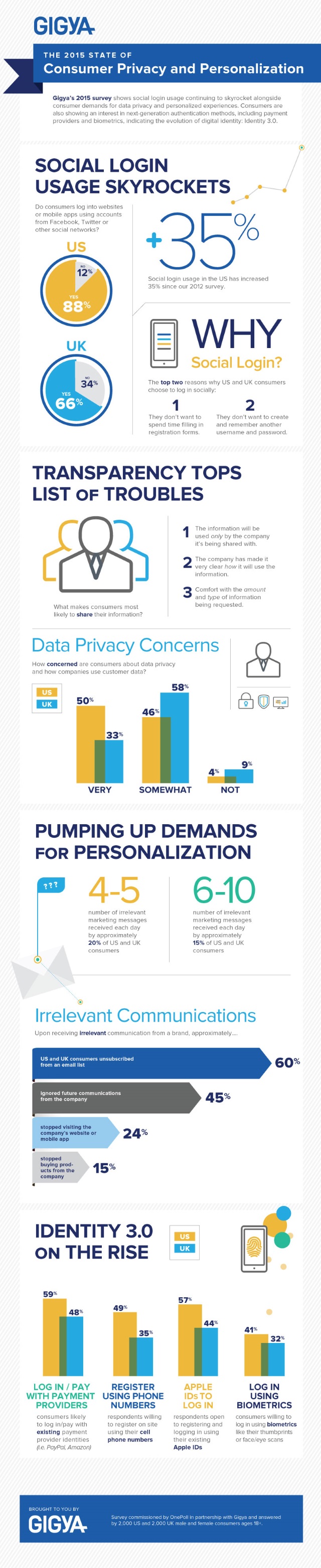
Image Credit: Gunnar Pippel/Shutterstock
-

Pssstt! Wanna host some malware?
Publié: juillet 14, 2015, 4:31pm CEST par Ian Barker

Whilst it's the hacks and the data breaches and the information thefts that grab the headlines, no one ever mentions the technology that lies behind them.
Where do the bad guys host their malware and where do they keep their stolen information? Like any legitimate online businesses, cybercriminals need a reliable, high availability hosting infrastructure.
A new report from TrendLabs -- the research arm of security company Trend Micro -- uncovers the existence of what it calls 'Bulletproof Hosting Services' (BPHSs) which provide the discreet infrastructure needed for cybercriminals to operate their business, store stolen data and hide out from anyone trying to shut them down. This often overlooked, component of cybercrime is more significant than it might seem. Without BPHSs, many cybercriminal groups would cease to operate.
Unlike regular hosts, bulletproof servers primarily host malicious content like phishing sites, pornography, fake shopping and carding sites, and command-and-control (C&C) infrastructure. They need to offer the service reliability of any ordinary host, but also need to appear as legitimate as possible so that authorities don't shut them down. Bulletproof host owners rent hardware colocation facilities in various countries to ensure the continuity of their operations. They normally rely on nations with lax information security laws to minimize the risk of them being blacklisted or shut down.
Like legitimate hosts, BPHSs offer different specialisms including torrent download sites, blackhat SEO to drive traffic to malicious sites, C&C components and spam tools. TrendLabs identifies three main delivery methods, dedicated BPH servers, compromised legitimate servers and abused cloud hosting services.
BPHSs also parallel the legitimate world in their pricing models. Low risk content can be hosted from as little as $2 a month with dedicated high-risk content servers -- based in China, Bolivia, Iran, or the Ukraine -- costing $300 or more.
The best BPHSs have support teams who communicate with clients via ICQ, Jabber, or their own JavaScript-based messaging services. Like legitimate providers they use a ticketing system to prioritize and process queries.
Robert McArdle, Trend Micro's FTR Senior Manager says, "The very nature of BPHSs is that they protect malicious activity against law enforcement, giving cybercriminals the much-needed loophole to wriggle out of and escape from the clutches of both law enforcement and the security industry. That loophole unfortunately largely remains open today".
Photo Credit: Bartlomiej K. Kwieciszewski/Shutterstock
-

Two-thirds of time spent responding to malware alerts is wasted
Publié: juillet 14, 2015, 3:44pm CEST par Ian Barker

Organizations are increasingly bombarded with malware reports and that can lead to wasted time dealing with false alarms or minor issues.
A new report from The Ponemon Institute, commissioned by breach defense specialist Damballa, reveals that two-thirds of the time spent by security staff responding to malware alerts is wasted because of faulty intelligence.
The survey of 551 IT and IT security practitioners across EMEA (Europe, Middle east and Africa) finds that teams spend, on average, 272 hours each week responding to 'false positive' cyber alerts -- due to erroneous or inaccurate malware information. This equates to an average cost of £515,964 (around $800,000) annually, for each organization, in lost time.
The findings show that organizations are dealing with nearly 10,000 malware alerts per week, however, only 22 percent of these are considered reliable. More worryingly, only a small fraction -- 3.5 percent -- of all alerts are deemed to be worthy of further investigation. IT teams could therefore be struggling with the resources, or expertise, to block or detect serious malware.
"These findings are significant as they highlight the real impact of false malware intelligence. Not only are teams devoting valuable time and resources to hunting down the false positives but they’re also in danger of missing the real infections, which could have a devastating impact," says Stephen Newman, CTO of Damballa. "The severity and frequency of attacks is increasing, so the focus really needs to be on building better intelligence, which means that organizations will have the confidence of knowing exactly where the real threats are. This means that teams can direct their efforts where it is most needed; on finding and quickly remediating the active infections".
Among other findings of the report are that fifty-seven percent of respondents say the severity of malware infections have significantly increased or increased in the past year. Yet whilst the severity of infections is rising, nearly a quarter of respondents (23 percent) say that they have an 'ad hoc' approach to containment, with 38 percent having no one person accountable for the containment of malware.
Only 37 percent of respondents reported that their organization has automated tools to capture intelligence and evaluate the true threat of malware. Organizations that do have automated tools report that an average of 44 percent of malware containment does not require human input or intervention and can be handled automatically.
The full report is available to download from the Damballa website.
Photo Credit: Sergey Nivens/Shutterstock
-

New software provides simplified view of IT assets
Publié: juillet 14, 2015, 1:22pm CEST par Ian Barker

For large companies keeping on top of IT assets and software licenses can be a complex and time consuming process.
IT management company LANDESK is releasing a new version of its IT Asset Management (ITAM) Suite which provides a simplified view of assets in one central place via a LANDESK Workspace, putting decision-making data at the fingertips of managers.
Features of the software include improved asset visibility. IT managers get a comprehensive look at managed assets, making it easy to identify owned assets, optimize software, reclaim unused licenses and regain negotiating power with vendors.
ITAM delivers detailed, reliable licensing information, helping monitor the current state of compliance and respond faster to software audits. For hardware it can automate tracking of warranty data and lease information.
LANDESK Workspaces is compatible with Mac, Windows, iOS and Android operating systems, and it provides the same experience regardless of device, so it can be used centrally or during on site audits.
"Many asset management tools, whether they are discovery, license optimization or asset repositories, tout the total number of reports available in the product," says Patricia Adams, ITAM evangelist at LANDESK. "While this is useful information, knowing how to act on the data is more meaningful. Having the data displayed in a format that allows for rapid business decision-making enables the asset manager to be more efficient. LANDESK Workspaces provides a customizable dashboard and the visibility needed to understand the health of the IT assets and make actionable decisions".
More information on the IT Asset Management Suite is available on the LANDESK website.
Photo Credit: .shock/Shutterstock
-

Machine learning simplifies managing VMware environments
Publié: juillet 14, 2015, 11:33am CEST par Ian Barker

With a mix of on-site, virtual and hybrid environments, today's IT systems are increasingly complex and time consuming to manage. Yet traditional monitoring tools can result in information overload.
For businesses using VMware environments, SIOS Technology Corp is launching a new solution that applies machine learning techniques to IT analytics.
SIOS iQ applies advanced machine learning analytics to broad data sets, including application and infrastructure data from third party tools and frameworks. This allows it to understand and explain complex behaviors and predict the impact of changes in dynamic virtual environments.
"This extensible analytics platform delivers simple, intelligent solutions to the most pressing problems in today's complex VMware environments," says Jerry Melnick, COO of SIOS Technology Corp. "SIOS iQ brings extraordinary ease of use and time savings to tasks that have typically required multiple experts from various IT disciplines. The solution improves IT and infrastructure efficiencies, reducing costs while helping IT meet critical quality of service goals for applications operating in VMware environments".
Traditional approaches focus on recording and reporting discrete events, such as a CPU utilization exceeding a threshold, to identify problems in a VMware environment. This means that complex or subtle issues can go unnoticed while IT staff are inundated with alerts without any guidance for prioritizing, interpreting or correcting them. SIOS iQ learns the relationships of objects and their normal patterns of behavior in a VMware infrastructure. It's then able to recognize abnormal patterns and identify the root causes of issues.
It can also analyze interactions between SQL and infrastructure resources in the VMware environment to identify the root cause of performance issues. SIOS iQ recommends the best solutions via its SIOS PERC Dashboard, filtering out the noise and large numbers of alerts that go with traditional approaches. This reduces staff time spent manually compiling and analyzing data from various sources to identify causes of issues and assign ownership of solutions.
You can find out more about SIOS iQ on the company's website and there's currently a limited feature, free edition available to allow you to try it out.
Image Credit: art4all / Shutterstock
-

77 percent of people are open to using password alternatives
Publié: juillet 13, 2015, 5:32pm CEST par Ian Barker

The username and password combination has been with us for a long time, but we're increasingly seeing its shortcomings for protecting sensitive data.
A new survey of 24,000 consumers across six continents by technology services and consulting company Accenture reveals that 60 percent of consumers find passwords cumbersome and more than three-quarters worldwide would be open to using alternatives.
"The widespread practice of typing usernames and passwords to log on to the Internet might soon become obsolete," says Robin Murdoch, managing director of Accenture's Internet and Social business segment. "Consumers are increasingly frustrated with these traditional methods because they are becoming less reliable for protecting their personal data such as email addresses, mobile phone numbers and purchasing history".
Users in China and India are most likely to be open to alternatives, at 92 percent and 84 percent, respectively. More than three-quarters (78 percent) of consumers in each of Brazil, Mexico and Sweden, and 74 percent in the United States, are also willing to consider security methods other than usernames and passwords.
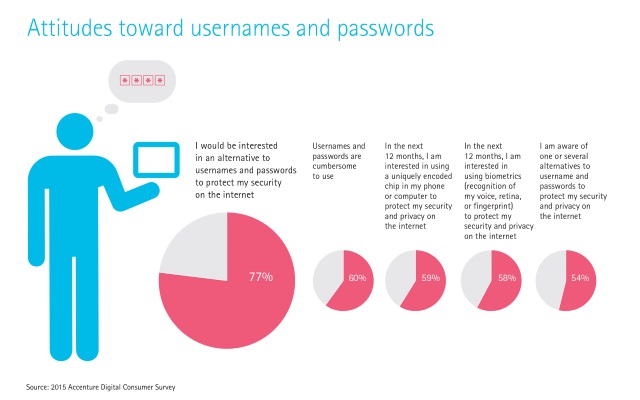
The survey also shows a general lack of faith in the security of personal data. Fewer than half (46 percent) of consumers globally are confident in the security of their information. Those in emerging countries are slightly more confident in the security of their personal data than were those in developed nations, at 50 percent and 42 percent, respectively.
"As hackers use more-sophisticated and less-obvious methods, passwords are no longer seen as the definitive answers to the security question," Murdoch adds. "Traditional one-step passwords are now being matched with alternative methods using biometric technologies such as fingerprint recognition and two-step device verification. Within the next few years we are likely to see many more consumers embracing these and other alternative methods".
You can read more in the full report Digital Trust in the IoT Era which is available to download from the Accenture website.
Photo Credit: Dr. Cloud/Shutterstock
-

Android users know about vulnerabilities but aren't taking precautions
Publié: juillet 13, 2015, 3:22pm CEST par Ian Barker

Although the majority of consumers are well aware of potential malware attacks on the Android platform, and they overwhelmingly understand the importance of mobile security, they're still not taking the steps needed to safeguard their devices and they’re reluctant to pay for protection.
This is among the findings of a new survey of more than 100 Android users from Chinese company 360 Security. It shows that Android mobile users worry most about untrustworthy apps (27 percent), online payments (20 percent), and hackers (13 percent).
Additional concerns are single sign-ons, Wi-Fi connections and personal data leakage. More than 90 percent of respondents say they think mobile security is important and two thirds are aware of weaknesses on the Android platform.
Yet despite these concerns almost half of the respondents currently aren't -- or are unsure if they are -- using a security app on their personal smartphone. Plus around one-out-of two people didn't know they needed a security app. They're also reluctant to pay much for protection, more than 80 percent of respondents want to spend less than $4.99 on a security app and 44 percent don't want to pay anything at all.
"The survey results are a good reminder that while today’s consumers are aware of threats to the Android platform, most are not leveraging the tools and apps needed to protect themselves," Yan Huang, COO of 360 Security says. "The 360 Security app is free for download in the Google Play store and will keep consumers -- around the globe -- safe from any suspicious activity, while boosting overall device performance".
Photo credit: Kirill__M / Shutterstock
-

How malware and gaming have grown up in parallel
Publié: juillet 13, 2015, 12:21pm CEST par Ian Barker

Since the advent of personal computing, games and malware have developed more or less side by side. Today the world of gaming has become intertwined with malware as cyber criminals have turned game theft into something much more lucrative.
The digital world, as we know it today, can be a dangerous place, to bring these issues to light anti-malware company Webroot has teamed up with the new movie PIXELS, released on July 24, to issue an infographic on the history of malware and gaming.
The global cost of cybercrime is estimated at $445 billion, but in the 1980s viruses merely had nuisance value, they might stop you playing Donkey Kong but they wouldn’t be after your bank details.
It wasn't until the turn of the century that malware stared to get really serious, the estimated cost of cleaning up the ILOVEYOU virus was put at around $6 billion. Meanwhile in the gaming world hundreds of thousands are turning to online worlds like Everquest.
In 2015 ransomware is encrypting gamers' save files and extracting money from virtual wallets, and even console gamers are no longer safe from attack.
You can see the infographic below. Webroot is also giving US-based gamers a chance to win a trip to one of the cities featured in PIXELS, PIXELS swag, and free gamer cybersecurity for PC, Mac, smartphone or tablet devices. Visit www.gamersvspixelsmovie.com and complete the quiz to enter.
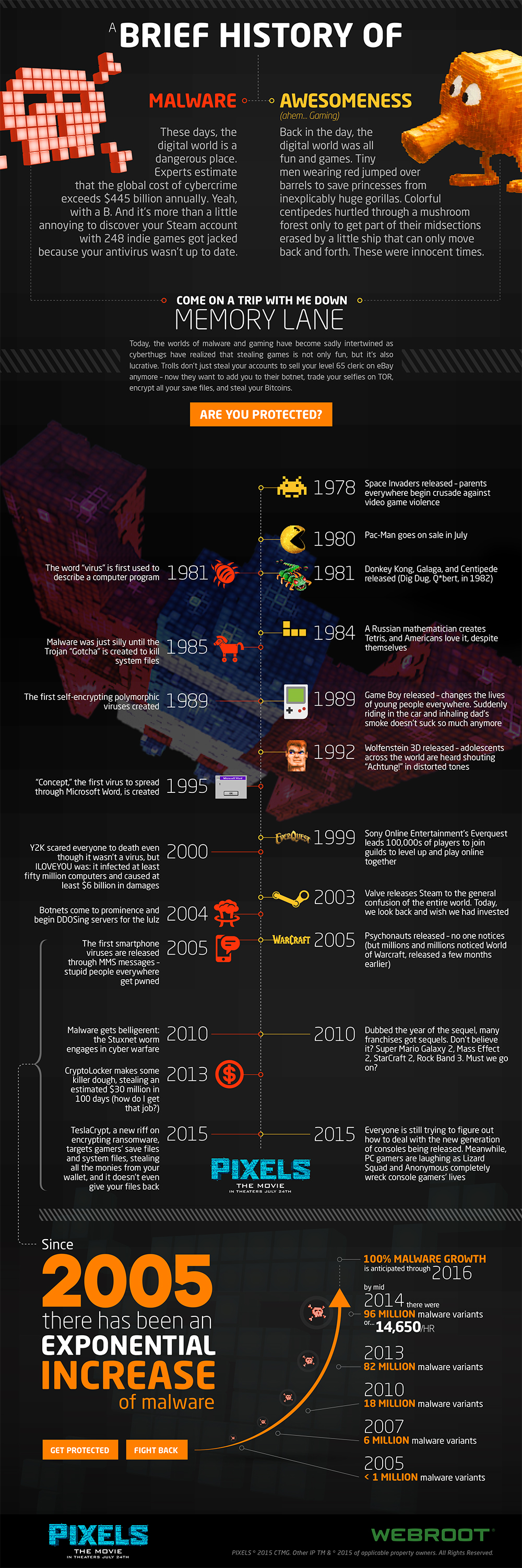
Image Credit: Ernesto Orchoa / Shutterstock
-

App performance shapes consumer perception of retailers
Publié: juillet 10, 2015, 4:15pm CEST par Ian Barker

A new survey reveals that shoppers are not forgiving of their favorite retailers or brands when their mobile apps aren't working as they should. According to the results 70 percent of consumers say the performance of a mobile app impacts their perception of the retailer.
The survey by application intelligence specialist AppDynamics spoke to 4,000 smartphone and tablet owners in the UK, US, France and Germany. It shows that 20 percent admit to making purchases on their phone while at work in front of their computer.
Also 67 percent would be put off shopping with a retailer if they had a negative experience with its app -- putting the onus on brands to deliver flawless application performance. However, 75 percent felt that a prompt and personal apology would persuade them to revisit the retailer.
When asked what they want from retail apps, 43 percent of consumers want mobile apps that allow them to purchase products while in the store, instead of queuing for a sales assistant. 57 percent would like retail apps to provide store assistants with details of past purchases to give a tailored in-store experience. Also 56 percent would be encouraged to visit bricks-and-mortar stores if apps provided them with personalised offers when they were nearby.
"As the lines between work and personal, digital and physical, continue to blur, retailers must ensure their apps function at all times across multiple platforms in order to retain and nurture always-on consumers", says Jyoti Bansal, founder and CEO of AppDynamics. "Technology has transformed the retail landscape significantly over the past decade, and now more than ever, software defines business success -- with revenue and reputation often hinging on customer interactions with apps".
The full report is available to download from the AppDynamics website.
Image Credit: 3Dmask / Shutterstock
-

IBM research promises 50 percent improvement in processor performance
Publié: juillet 10, 2015, 2:57pm CEST par Ian Barker
Moore's Law, the rule describing the steady growth of computing power, seems to have been under threat of late. But work by an alliance led by IBM research could see it safe for a few years yet.
Researchers have produced the first 7nm (nanometre -- one billionth of a meter) test chips. What does this mean? Current chips have components with a width of 14 or 20nm so a 7nm chip will allow many more components to be included.
The breakthrough could result in the ability to place more than 20 billion transistors -- effectively tiny switches -- on a fingernail-sized chip. Industry experts believe that 7nm technology will be crucial to meeting the anticipated demands of future cloud computing and big data systems, cognitive computing, mobile products and other emerging technologies.
"For business and society to get the most out of tomorrow's computers and devices, scaling to 7nm and beyond is essential," says Arvind Krishna, senior vice president and director of IBM Research. "That's why IBM has remained committed to an aggressive basic research agenda that continually pushes the limits of semiconductor technology. Working with our partners, this milestone builds on decades of research that has set the pace for the microelectronics industry, and positions us to advance our leadership for years to come".
To achieve the higher performance, lower power and scaling benefits promised by 7nm technology, researchers have had to bypass conventional semiconductor manufacturing approaches. Among the novel processes and techniques pioneered by the IBM Research alliance are a number of industry-first innovations. These include Silicon Germanium (SiGe) channel transistors and Extreme Ultraviolet (EUV) lithography integration at multiple levels.
If translated to production these techniques and scaling could result in at least a 50 percent power/performance improvement for the next generation of mainframe and POWER systems that will power the big data, cloud and mobile era.
Image Credit: Darryl Bautista/Feature Photo Service for IBM
-

How personal devices are changing the American workplace
Publié: juillet 9, 2015, 5:25pm CEST par Ian Barker

We're all familiar with the idea of BYOD and allowing employees to use their own devices for work. But how much impact is it having out in the real world workplace?
Workspace as a service provider Workspot has produced an infographic based on a survey of 500 US workers sheds some interesting light on things. High numbers of Americans are using their own devices for work, with 64 percent admitting that they sometimes do so. Those that do use their own devices do so for between 10 and 30 percent of the work day.
The breakdown of devices is interesting since it doesn't reflect system popularity in the wider world. 40.4 percent are using iPhones for work compared with only 17.2 percent using Android phones, 28.3 percent use their own laptops.
When asked where they use their devices for work, most (74 percent) do so in the car, 52 percent in the kitchen and 41 percent in bed -- which seems to confirm all of those working from home stereotypes. As to what they do, 56 percent access their work email and 33 percent make work related phone calls. However, only 4.2 percent access work applications and 5.6 percent access calendar appointments which suggests that the BYOD revolution still has some way to go.
You can see the full infographic below.
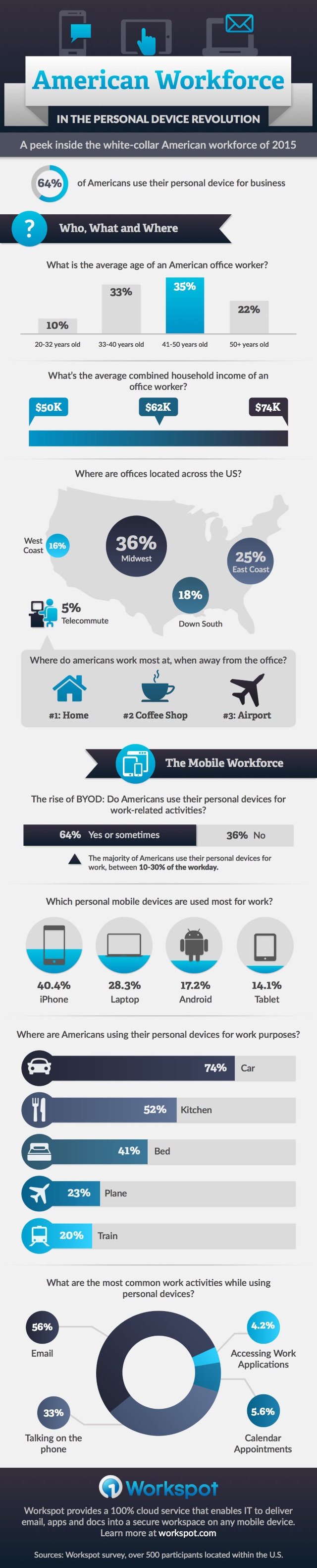
Photo credit: Alessandro Colle/Shutterstock
-

Choosing the best software for your business [Q&A]
Publié: juillet 9, 2015, 11:37am CEST par Ian Barker

Selecting software is one of the most crucial decisions that many enterprises have to make. The right choice can make all of the difference between success and failure.
However, finding impartial advice on the pros and cons of various business packages can be difficult. Could crowd sourcing of opinions provide an answer? The people behind software review platform G2 Crowd definitely think so. We spoke to company president Tim Handorf to find out more.
BN: What types of software does G2 Crowd cover?
TH: We have more than 33,000 reviews across more than 475 categories, from marketing technology such as CRM and marketing automation, to to IT infrastructure tools and development tools. We've also recently added a number of industry-specific software categories.
BN: Tell us about how the Grid rating methodology works.
TH: Every product within a given category that has 10 or more reviews is plotted on two axes. The Satisfaction (horizontal) axis is based on G2 Crowd review data and includes, overall satisfaction, feature satisfaction, customer service and more. The Market Presence (vertical) axis is based on social indicators, age of the company, the number of employees it has, earnings -- if the vendor's stock is publicly traded -- and more.
Grids update and normalize in real time, based on new review and social data that come in each day. You can see an example in our backup software category. Also, you can read more details on our methodology here.

BN: Where do you source your reviews from?
TH: Reviews are primarily sourced in three ways, and the distribution is fairly evenly split between the methods. Firstly users find our site (via a search engine or other referral) and write a review after visiting.
Second, our team finds users of specific products through social networks and asks them to write a review of the product. Third, software providers encourage their users to write reviews for several reasons: product feedback, public-facing testimonials and more. We provide all software developers with a landing page to which they can direct customers to write a review. However, if software providers are going to ask customers to write reviews, we do ask they follow the guidelines we provide.
BN: How can you prevent developers 'gaming' the system with positive reviews?
TH: We take pride in having a rigorous vetting process for reviews. We also require all reviewers to authenticate with LinkedIn before they post so we know they are a real person and who their employer is. Our QA team vets every review that comes in to ensure the authors aren't affiliated with the software provider or one of their competitors.
In addition, we ask users to upload a screenshot of the software that displays user credentials which match their LinkedIn credentials. This serves as an additional method for readers to know that this review came from a real user.
BN: Do you have any plans to expand into other areas, consumer software for example?
TH: Although we are currently focused on business software, we also have categories on G2 Crowd for related support areas, such as IT consulting. Beyond software-related services, we haven't determined if or when we will expand into other areas.
Photo Credit: nopporn/Shutterstock
-

Google Apps vs Office 365 in the workplace
Publié: juillet 8, 2015, 5:08pm CEST par Ian Barker

Google and Microsoft are the two big players in the cloud office suite market. But what do the customers of each look like and how are they implementing and using the software?
Cloud management specialist BetterCloud has released the results of a survey of 1,500 IT professionals looking at customers of both systems, the age and size of their companies, cost-savings for each, and when companies will achieve 100 percent cloud use.
Among the findings are that Google Apps organizations are experiencing savings of 41 percent while organizations using Office 365 see savings of 27 percent. However, Office 365 organizations are more than four times larger than their Google Apps counterparts. Because of their size, Office 365 IT teams are also more than six times larger than those that use Google Apps, yet, surprisingly, they service the same average number of employees per IT admin.
Office 365 organizations tend to have been in business longer, having been founded seven years earlier on average than Google Apps organizations. This may account for differences in deployment strategy. Sixty eight percent of Google Apps organizations surveyed roll out Google Apps all at once while 62 percent of Office 365 organizations choose to implement a hybrid deployment strategy.
Both systems are good for promoting collaboration with 84 percent of enterprises using Google Apps experiencing increased collaboration compared to 72 percent of Office 365 enterprise organizations.
Google Apps usage rates far surpass the online equivalents for Office 365, suggesting many Office 365 organizations’ employees are still using local versions of the Office suite. No Google Apps or Office 365 enterprise organizations currently run 100 percent of their IT in the cloud, projected to 2026 that number jumps to 74 percent and 57 percent respectively.
"Google and Microsoft have taken different approaches to the market. Google has built a cloud-only suite that’s focused on business transformation. They've been revolutionary in their approach since the beginning", the report concludes. "Microsoft has owned the enterprise software and messaging market for 20 years, and now, under new leadership, they are taking their customer base and an established product set on an evolutionary path to the cloud. Microsoft has finally put the weight of their name behind the cloud by offering their customers a safe and comfortable upgrade path".
You can read more about the survey's results on the BetterCloud blog.
-

Microsoft to shed over 7,000 jobs in revamp of phone business
Publié: juillet 8, 2015, 4:33pm CEST par Ian Barker

Just over a week on from Microsoft's announcement that it was getting out of the display advertising business with the loss of 1,200 jobs, the company's CEO is wielding his ax again.
This time up to 7,800 jobs are set to go in the company's phone hardware business as it says that the future prospects for the segment are, "...below original expectations".
The company will record an impairment charge of approximately $7.6 billion related to assets associated with the acquisition of the Nokia Devices and Services (NDS) business, in addition to a restructuring charge of approximately $750 million to $850 million as a result of the change.
"We are moving from a strategy to grow a standalone phone business to a strategy to grow and create a vibrant Windows ecosystem including our first-party device family," says Microsoft CEO Satya Nadella in an email to staff. "In the near-term, we'll run a more effective and focused phone portfolio while retaining capability for long-term reinvention in mobility".
This marks the latest step in Nadella's strategy to refocus the company on personal computing, cloud platforms, productivity and business processes. Since taking over as CEO last year he has been busily acquiring cloud and mobile software businesses and shedding parts of the company that don't fit with this overall plan.
The latest changes are expected to be complete by the end of the calendar year.
Photo Credit: turtix/Shutterstock
-

Securing networks is harder than it was two years ago
Publié: juillet 8, 2015, 12:51pm CEST par Ian Barker

Enterprises face evolving security challenges and solutions due to the introduction of cloud infrastructures. Growing cloud adoption has been identified as one of the key reasons why a majority of IT and security professionals find securing their networks more difficult today than two years ago.
Network security company Tufin has produced an infographic, based on a recent research report with ESG, looking at why 56 percent of professionals believe network security is getting harder.
This is partly down to increasing complexity as well as cloud adoption. The top five drivers of network security strategies are listed as: supporting cloud initiatives (38 percent), increasing network security efficiency (33 percent), implementing better monitoring and reporting of network topology and controls (30 percent), improving troubleshooting and problem solving (29 percent), and improving workflow between the security team and other IT groups (26 percent).
The full report is available to download from the Tufin website and you can see the infographic below.
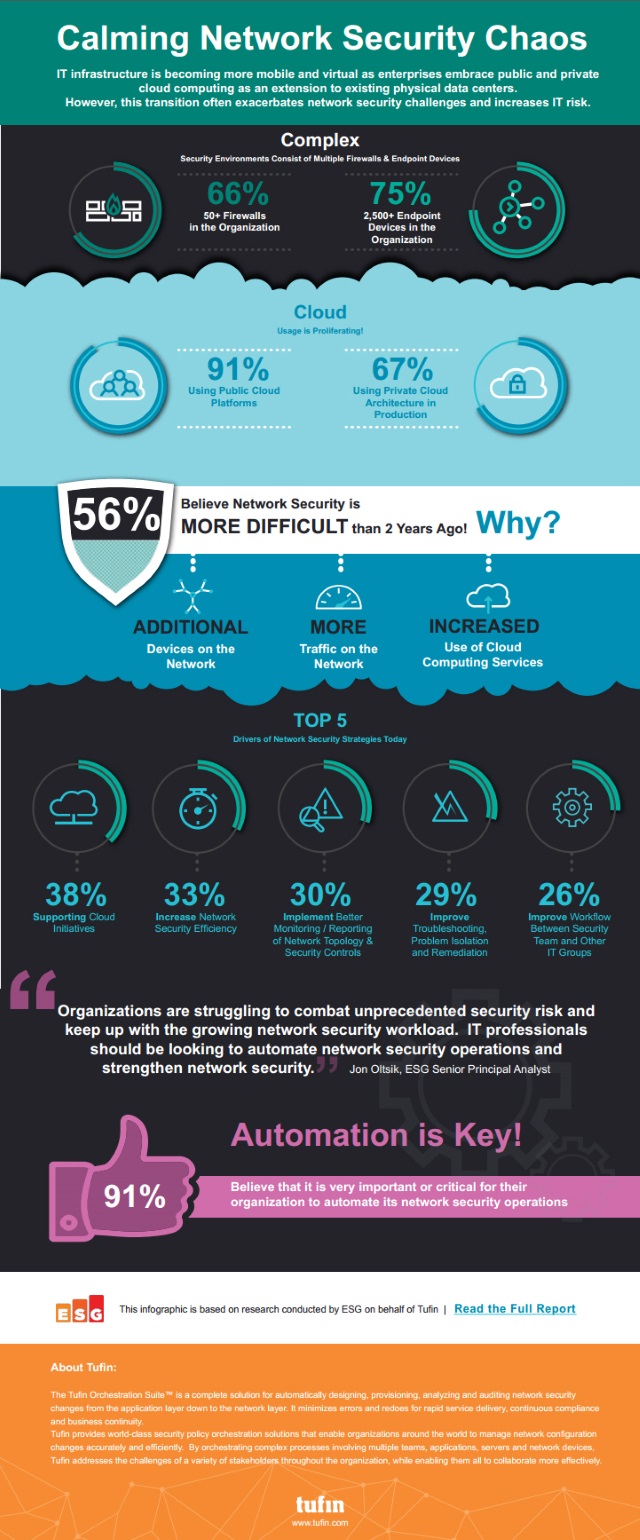
Image Credit: watcharakun/Shutterstock
-

Acronis brings business data protection solutions to the cloud
Publié: juillet 8, 2015, 11:54am CEST par Ian Barker

With the increased threat of data loss from security breaches or system failures, many enterprises are turning to cloud solutions to look after their information.
Backup specialist Acronis is keen to take a slice of this market with the launch of its Acronis Data Protection Platform. This is a cloud platform that seeks to transform the way data protection is delivered to end-user customers by service providers, resellers and distributors.
"For companies everywhere, suffering from data loss and disasters is not a matter of if, but when -- it will happen", says Serguei Beloussov, co-founder and CEO at Acronis. "With the introduction of the Acronis Data Protection Platform, we make complete data protection easy, complete and affordable for businesses of all sizes and empower service providers and resellers to capitalize on this massive market opportunity".
The company is also is releasing a new version of Acronis Backup Cloud, its leading cloud backup solution, and introducing Acronis Files Cloud, a new file sync and share product. Acronis is also announcing the global availability of Acronis Disaster Recovery Service, its all-in-one solution for backup and disaster recovery.
Based on an advanced cloud architecture, the Acronis Data Protection Platform delivers software-as-a-service solutions, including backup, disaster recovery and file sync and share. The platform is powered by the Acronis AnyData Engine -- a set of powerful data protection technologies that can capture, store, recover, control, and access any data from any location.
Improvements to Backup Cloud include expanded support for Microsoft SQL, Microsoft Exchange, and Mac OS X environments, plus initial seeding capabilities to easily move large volumes of data to the cloud.
File Cloud offers workers a secure alternative to consumer file sharing services, with safe file access, sync, and share in an easy-to-use cloud service. The solution helps service providers and partners quickly address the growing need for businesses to securely support BYOD and mobile workforces.
More information about Acronis business products is available on the company's website.
Image Credit: Maksim Kabakou/Shutterstock
-

Translation Connector for AEM helps companies manage localized content
Publié: juillet 7, 2015, 4:59pm CEST par Ian Barker

Adobe Experience Manager (AEM) is used by many businesses to control content and ensure that it's consistent across channels. But what it doesn't help with is localizing sites into different languages.
Into this gap is stepping translation specialist Smartling with Translation Connector, which brings its cloud-based translation management platform to users of AEM 6.1.
It allows AEM users to seamlessly connect to the Smartling platform from within the AEM 6.1 system where they can then submit content for translation and localization to be fulfilled by their preferred language service providers.
"When we released our first Connector for Adobe CQ 5.4 in early 2014, it gave CQ users translation functionality never before possible," says Andrew Saxe, senior director of product at Smartling. "We are thrilled to be among the first partners to support AEM 6.1, and we look forward to bringing the most advanced translation functionality to Adobe's fast-growing base of AEM 6.1 customers, many of whom already use the Smartling platform".
Smartling can translate and manage content from almost any data source, including business documents, resource file types, AEM third-party plug-in content, and dynamic content built into AEM sites even though they not have data stored in AEM. Changes to content are detected automatically, and translations are automatically returned to AEM when they are complete.
Smartling's centralized translation memory integration makes use of previous translations to boost quality, consistency and speed, while reducing translation costs by up to 40 percent. The company's "in-context" translation interface provides translation resources with full visibility into site design and layout during the entire process, resulting in greater accuracy from the outset. Translation progress updates are available directly within the AEM interface, eliminating the need to switch between multiple systems to monitor project activity.
More information on Smartling's Translation Connector for AEM is available on the company's website.
Photo Credit: marekuliasz/Shutterstock
-

How mobile access is changing the Internet
Publié: juillet 7, 2015, 3:48pm CEST par Ian Barker

Mobile Internet doesn't just liberate us from the constraints of a wired connection, it offers hundreds of millions around the world their only, or primary, means of getting online.
The latest Global Internet report from the Internet Society focuses on mobile usage and how it has changed, and is changing, the way we use the Web.
In addition the mobile Internet doesn't only extend the reach of the Internet as used on fixed connections, but it offers a range of new functionality in combination with the latest portable smart devices.
Already 94 percent of the global population is covered by a mobile network, 48 percent are covered by mobile broadband, and 28 percent have subscribed to mobile Internet services. Mobile Internet penetration is forecast to reach 71 percent by 2019 and usage per device is forecast to more than triple over the same timescale. 192 countries now have active 3G mobile networks, which cover almost half of the global population. Smartphone sales now account for the majority of mobile handsets sold worldwide and tablet sales will soon exceed total PC sales.
The report points out that mobile Internet will play a key role in bringing the next billion Internet users online. Mobile has already leap-frogged fixed-line access in many countries because of limitations in the coverage of the network, and the availability of mobile Internet access significantly outpaces adoption today.
This combined with new services, often accessed via apps, are key to enabling social inclusion, interaction with government and commerce, and other applications. According to the report’s authors, these innovations are already driving a further evolution of the Internet and helping to
realize the Internet Society’s vision that 'The Internet is for everyone'.Mobile Internet access has the potential to improve many areas of people's lives from education and healthcare to productivity and leisure. It does, however, raise concerns particularly surrounding privacy and tracking. The report also notes that the 'app economy' may also limit our choice of device as new players find it hard to break into the market.
"Today we associate the mobile Internet with a smart device that runs on a specific platform and provides access to the apps that we use," says Michael Kende, Internet Society Chief Economist and author of the report. "While this has created amazing benefits for users and an entire app economy for developers, it locks users into a chosen platform and ultimately limits choices in a way that is new to the Internet".
The full report is available on the Internet Society website.
Image Credit: Ilin Sergey / Shutterstock
-

New backup service protects data stored in cloud apps
Publié: juillet 7, 2015, 1:28pm CEST par Ian Barker

You might think that by moving applications to the cloud your data is automatically protected and worrying about backups is a thing of the past.
But just storing and processing data in Office 365 or Salesforce doesn't guard against user errors like accidentally deleting files. To offer extra peace of mind, backup specialist KeepItSafe is launching a new Cloud2Cloud service to protect data in SaaS applications.
With Cloud2Cloud, users can back up data held in cloud-based SaaS applications such as Microsoft Office 365, Salesforce.com and Google Apps, as well as platforms like Windows Azure and Amazon Web Services.
"More and more mission-critical data is being stored online, but many businesses are unaware that the responsibility for backing up this data rests entirely with them; not the service providers", says Eoin Blacklock, Managing Director of KeepItSafe. "Yes, well known cloud service providers do back up customer data, but research evidence suggests that's only because it's of benefit to them, rather than a requirement of the agreement they have with their clients. Often, backup and disaster recovery from the service providers themselves is charged out at an excessively high rate, and the data isn’t very easily accessible".
Businesses can select the frequency and granularity of their backups, and have the ability to opt for different parameters for each data source, based on their business continuity and compliance needs. Minimal configuration is required, users can also deploy en-mass backup rules to hundreds of Office 365 and Google Apps users, ensuring consistent protection across all parts of an organization.
"Problems around user error don’t necessarily go away when an organization moves its infrastructure into the cloud", Blacklock adds. "Nor does it eliminate the chances of data getting hacked by an outsider, or deleted by a disgruntled employee. Cloud-to-cloud backup has become a business imperative, and KeepItSafe Cloud2Cloud addresses the growing demand we have experienced for this kind of solution from our customers".
You can find out about Cloud2Cloud and sign up for a webinar on July 23 to learn more on the KeepItSafe website.
Image credit: Alexander Kirch/Shutterstock
-

Small businesses under-prepared for cyber security
Publié: juillet 7, 2015, 11:58am CEST par Ian Barker

Although there has been heavy media coverage of information security issues in the past year, more than half of Britain's small businesses say that they aren't taking any preventative measures to protect themselves against cybercrime.
According to a survey by identity protection specialist CSID 52 percent of UK small businesses aren't guarding against cybercrime and a large majority (85.3 percent) don't have any plans to increase their budgets for security implementation, and less than 13 percent are working with a third party vendor to protect themselves. When asked about their concerns in the event of a data breach, 53 percent of respondents were worried their reputation would be damaged. Yet despite these fears only 47 percent of respondents are monitoring what is written about their brands online, and less than 15 percent have a social media policy in place. Only nine percent were worried about the negative impact on employees.
"While monitoring what is written about your business online is a good practice, we’re surprised by the lack of employee education and social media policies in place," says Andy Thomas, managing director of CSID in Europe. "It seems that time and again businesses misjudge the element of staff related security breaches which appear to be increasing every year. Yes, there will always be threats from malware, phishing and DOS, but never underestimate the human factor".
When asked about their concerns, most respondents cited the threat of undetected malware, 33 percent stated phishing attacks, and the least concerning threat was BYOD with only 2 percent of answers.
In the event of a breach, the CSID survey finds that 63 percent of small businesses would most likely turn to their insurer, bank, lawyer or IT supplier for assistance; the police being the least likely first point of call. Yet despite this 68 percent of respondents say that their IT service provider hasn't provided them with any information regarding data breaches and 68.6 percent confess to not having a disaster recovery or business continuity plan in place.
More information about how small businesses can protect themselves is available on the CSID website.
Image Credit: Manczurov / Shutterstock
-

New cloud solution makes video management easier for developers
Publié: juillet 6, 2015, 4:42pm CEST par Ian Barker
Thanks to the wide availability of fast connections, online video is no longer confined to the likes of YouTube but crops up on all kinds of websites.
This presents a challenge for the developers who need to maintain those sites but a new solution from online image management specialist Cloudinary is set to make life easier.
"Our customers frequently asked us for a video solution that offered the same capabilities as our image solution, a 'Cloudinary for Videos' if you may," says Itai Lahan, CEO and Founder of Cloudinary. "We are excited to unveil our brand new video support, a complete video service that complements our image-management solution perfectly. We hope that with this, we'll manage to save our customers additional valuable R&D, IT and DevOps time that could be re-focused on their core product instead, save IT costs, and greatly improve their users’ online experience".
Cloudinary's new video support provides a technical solution to all aspects of handling videos online, allowing developers to focus on their core product instead of spending time building and supporting in-house video solutions.
Videos can be uploaded at any scale using rich APIs, from a back-end application or directly from a browser or mobile application. They can be managed via an interactive online interface, and automatic transcoding makes it possible to generate HTML5 and mobile friendly videos for optimized viewing on all web browsers and mobile devices.
Videos can be manipulated on-the-fly, in real-time, to fit with graphic design and product requirements. Cloudinary also makes it easy to brand videos, embed ads and captions inside, generate thumbnails and convert to animated GIFs if required. End-user experience is improved too by optimizing videos and streaming them from a global content delivery network.
You can find out more about how Cloudinary can streamline image and video management for developers on the company's website.
-

Vodafone Smart ultra 6 review
Publié: juillet 6, 2015, 9:57am CEST par Ian Barker

Not so very long ago each new mobile phone that launched would be smaller than its predecessor whilst packing in more features. In recent years though we’ve come full circle and phones have started to get bigger again, offering more screen real estate for apps and improved image quality for multimedia use.
Bigger doesn’t necessarily mean more expensive though and the Smart ultra 6 from Vodafone appears to offer a lot of phone -- both physically and technically -- for just £125 on pay-as-you-go. Let’s see how well it delivers.
What You Get
What you receive is a nicely non-flashy package, the box is eco-friendly recycled cardboard and the phone comes with a USB charger cable and mains adaptor and a set of iPod-white earphones. This stripped back approach applies to software too and the phone isn’t overloaded with pre-installed bloatware apps.
Although it carries the Vodafone brand name the Smart ultra is made by Chinese manufacturer ZTE. The first thing that strikes you when you open the box is the size: it’s 154mm long and 77mm wide (about six inches by three), but slim though at under 9mm thick. Even so if you like things snug in the trouser department your friends will notice you’ve upgraded your handset before you take it out of your pocket. In the interest of gender equality, if you favor a smaller handbag you may have to leave some other essentials behind to accommodate the Smart Ultra.

The back cover is plastic but it has a nice semi-matt grey finish and doesn’t really feel cheap, though at the same time doesn’t really have a wow factor. Under the skin it has an eight-core Qualcomm Snapdragon processor (four running at 1.5GHz and four at 1GHz), 2GB of RAM, plus a generous 16GB of storage that can be expanded with a microSD card. It runs the latest Android 5.0 Lollipop and it’s 4G capable. There’s a 13-megapixel rear camera and 5-megapixel front, with 4x digital zoom and an LED flash.
It’s the screen that’s the star of the show here though: it’s a 5.5 inch with a 1,920 x 1,080 pixel resolution, and it is impressive. It’s bright with strong colors and there’s no hint of fuzziness in icons and text; video playback is smooth too. The built-in speaker sounds a bit tinny though so you’ll want to use headphones.
In Use
In fact performance is smooth generally with no noticeable lag when loading apps or making entries via the keyboard. The camera is pretty good too, it defaults to Auto mode but there’s a high dynamic range (HDR) option available along with some artistic filters. Exposures aren’t always perfect, tending to look a little washed out in bright conditions but it’s fine for everyday use.
Although there aren’t many apps pre-installed, apart from the standard Android stuff like Gmail and YouTube, you do get Vodafone’s own Smart Tips software. This leads you though some of the phone’s features, useful if you’re an Android virgin. There are a few other Vodafone apps too but not enough to get annoyed about.
The phone charges up from flat in a couple of hours -- it does get quite warm when it’s charging though -- and a full battery will give you around 240 hours of standby and 15 hours of talk on 3G. There’s no user access to the battery so if it ever needs replacing you’ll be sending the phone back.
Conclusion
Priced at £125, or from around £17 a month on contract, you do get a lot of phone for your money here. Yes there are some minor niggles, but if you want a big screen, 4G connectivity and decent performance there’s not currently much else in UK to match the Smart ultra 6 in this price range.
Pros
- Screen quality
- Minimal bloatware
- Good value
Cons
- Tinny speaker
- Variable camera performance
Company Release
PriceITProPortal
ReviewCompany Site Vodafone £125 7/10 Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
-

How much does security software slow down your PC?
Publié: juillet 3, 2015, 12:52pm CEST par Ian Barker

One of the main complaints that people express about security software is that it harms the performance of their PC. But how much of an effect does it really have?
Independent testing organization AV-Comparatives has conducted a test of 20 leading security products for Windows to assess their impact. Tests were performed on a 64-bit Intel Core i5 machine with Windows 8.1.
Performance was assessed on a number of tasks; file copying, archiving and unarchiving, installing and uninstalling applications, launching applications, and downloading files. These results were used to provide an AV-C score for each product. Researchers also ran the industry standard PC Mark 8 benchmark test and combined this with the AV-C results to come up with an overall impact score.
Based on these scores, the top five with least effect on system performance were; Avast with an impact score of 4.1, Emsisoft on 4.2, Avira on 7.6, Kaspersky Lab on 9.3 and AVG on 12.5. The poorest performers were Quick Heal and ThreatTrack both on a score of 25.7.
The researchers point out that other factors such as the age of the hardware, how up to date the software is, and the content and fragmentation state of the hard disk can have an impact on real-world performance.
The test doesn't cover how effective the protection provided is either so you'd have to compare the results with AV-Comparatives Real World Protection and File Detection tests to find the best balance of performance and protection. Some of the best performers here don't do as well in the other tests.
You can download the full report with details of the results for all 20 products along with the methodology used from the AV-Comparatives site.
Photo Credit: m00osfoto/Shutterstock
-

Business intelligence analysts spend too much time cleaning up data
Publié: juillet 2, 2015, 4:47pm CEST par Ian Barker

We hear a lot about the potential benefits of big data, but a new study reveals that those benefits are won at a cost of considerable time spent in cleaning up and preparing raw information.
The study by data integration company Xplenty surveyed over 200 business intelligence professionals and finds that a third of them spend 50-90 percent of their time just cleaning raw data.
Looking at the 'extract, transform and load' (ETL) process, including preferences for on-premise or cloud-based solutions, perceived challenges, and the amount of time spent on ETL, the results show that 97 percent of those surveyed say that ETL is critical for their business intelligence efforts.
More than half (51 percent) of those polled say that they currently use on-premise ETL solutions. However, 51 percent of these say that they are 'strongly considering' moving all ETL processes to the cloud.
"While many organizations still rely heavily on existing on-premise IT for ETL, the desire to shift to a more cloud-based model has never been stronger," says Yaniv Mor, CEO & Co-Founder of Xplenty. "Cloud ETL offers a host of benefits over on-premise, from increased agility in resource deployment to reduced costs. As such, the cloud is an increasingly attractive option from both a performance and operational perspective".
When asked what the biggest challenges were in making data ready for analysis, 55 percent say integrating data from different platforms, followed by transforming, cleansing and formatting incoming data (39 percent), integrating relational and non-relational data (32 percent), and the sheer volume of data that needs to be managed (21 percent) at any given time.
"BI professionals should be spending the majority of their time evaluating data and deciphering patterns gleaned through the analytics process -- not readying data for analytics," adds Mor. "The more time they spend making raw data analytics usable, the less time they have to generate real value from it. We have to accelerate Big Data's 'time-to-insight,' boosting efficiency and bringing more immediate answers to an organization so that they can more quickly take advantage of them".
More about how analysts are spending time as 'data janitors' is available on Xplenty's blog.
Photo Credit: Amy Walters /Shutterstock
-

Security pros lack faith in endpoint protection
Publié: juillet 2, 2015, 3:52pm CEST par Ian Barker

Organizations face increasing numbers of threats today and a high percentage of security professionals now no longer trust traditional protection solutions.
A survey by enterprise security specialist Bromium reveals that 92 percent of respondents have lost confidence in the ability of traditional endpoint protection solutions, such as antivirus and white listing, to detect unknown threats like zero-day attacks. In addition 78 percent believe antivirus software is not effective even against general cyber attacks.
End users are seen as the greatest security risk by 62 percent of respondents. In addition more than one-quarter cited emerging cloud and mobile technologies that reduce IT control, 29 percent cited cloud services and 29 percent said mobile devices are among the top sources of risk.
When asked what they thought was most effective at preventing cyber threats 58 percent of information security professionals named endpoint threat isolation. Nearly one-third said network-based solutions are effective; 28 percent have faith in intrusion detection/intrusion prevention (IDS/IPS), and 27 percent think network sandboxes are effective.
"The frequency and magnitude of high-profile data breaches is causing organizations to lose faith in detection-based solutions, such as antivirus," says Clinton Karr, senior security strategist at Bromium. "Information security professionals are turning instead to technologies that provide proactive protection, such as threat isolation, as the foundation of their security architecture".
The loss of confidence in traditional solutions means security professional are turning to other measures. Prevention, such as hardening and isolating systems, is at the root of security architecture according to 58 percent of respondents, compared to 23 percent who believe it's detection, 16 percent response, and 34 percent predictive analytics.
You can find out more about the study on Bromium's blog.
Image Credit: Sergey Nivens / Shutterstock
-

Can't remember your brother's phone number? You could be suffering from digital amnesia
Publié: juillet 2, 2015, 1:16pm CEST par Ian Barker

When you can find a phone number with the swipe of a finger or resolve an argument with a quick trip to Google, why would you need to remember anything?
A new report from Kaspersky Lab calls this phenomenon 'digital amnesia'. It surveyed over 1,000 consumers across the US and finds that 91 percent of them say they use the Internet as an online extension of their brain.
Almost half (44 percent) say that their smartphone holds almost everything they need to know or recall. There's a downside to this though as the study also shows that losing personal data -- such as pictures of your children, vacation videos or someone's phone number -- causes immense distress, particularly among women and people under 35.
Odd then that many Americans are failing to adequately protect the devices they’re so reliant on. Just one in three installs extra IT security, such as anti-virus software on their smartphone, and only one in five adds any security to their tablet.
"Connected devices enrich our lives every day, but they have also caused the prevalence of Digital Amnesia in our country. As consumers, it is important for all of us to understand the long term implications of this effect, and why it reinforces the need for us to diligently protect our valuable information and precious memories," says Chris Doggett, managing director of Kaspersky Lab North America. "By conducting this study, Kaspersky Lab is able to shed further light on how consumers are using and depending on their devices, and armed with this information, we will continue our mission to raise public awareness about the importance of using technology to protect our digital lives".
Despite the fact that we depend heavily on our devices it seems we can remember some things. When asked, most participants could phone the house they lived in aged 15 (67.4 percent) as well as their partners (69.7 percent), children (34.5 percent), and place of work (45.4 percent). However, they'd be unable to call their siblings (44.2 percent), friends (51.4 percent), or neighbors (70.0 percent) without first looking up the number.
It seems that digital amnesia is a growing trend among people of all ages, not just younger 'digital natives'. The long term implication of storing less in our heads is that we need to take steps to protect the stuff we no longer bother to remember.
The full report is available on the Kaspersky Lab site and there's a summary of the findings in infographic form below.
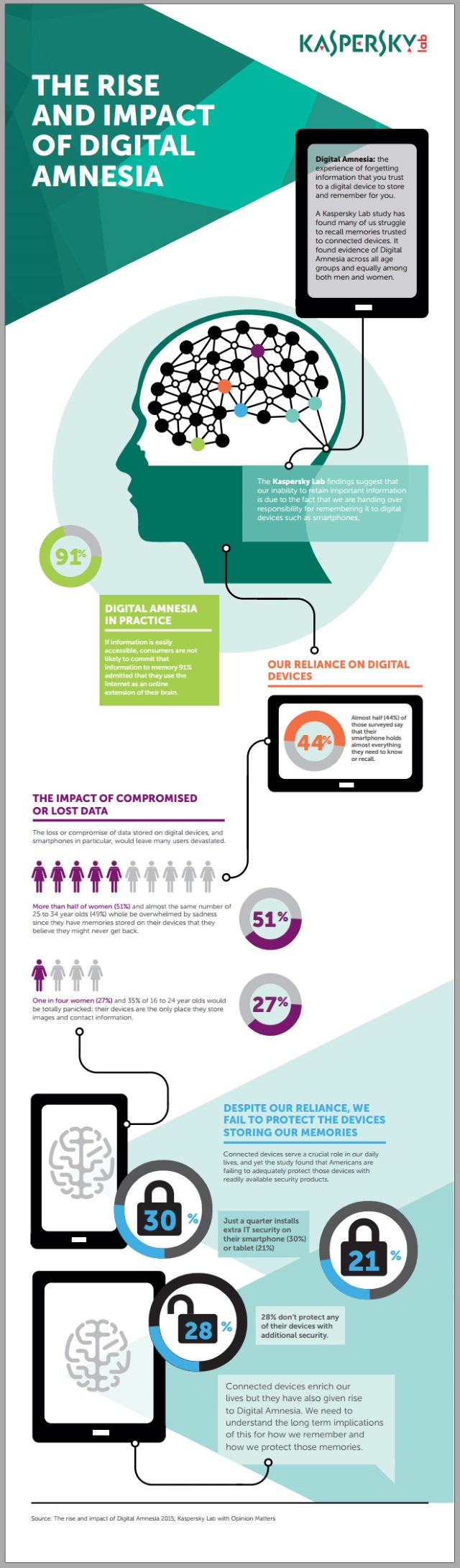
Image Credit: PathDoc / Shutterstock
-

Digital piracy up by 22 percent over the last three years
Publié: juillet 1, 2015, 4:58pm CEST par Ian Barker

Despite attempts to combat it, illegal distribution of copyright material via the internet is a continuing problem.
Protection solutions specialist Arxan Technologies has released the results of a new report produced in collaboration with the iThreat Cyber Group which shows that illegal reproduction and distribution of copyrighted material on the Web is booming as a result of security breaches in both mobile and desktop software applications.
The report is based on analysis of data collected over the past three years that examined the distribution of unauthorised digital assets on the Dark Web, and indexed sites that are focused on distributing pirated material. Thousands of sites were analysed, including over 50 that are in the sole business of distributing pirate releases.
Among the findings are that 1.6 million releases were pirated in 2014 and that the extent of digital media piracy is far more extensive than commonly realised. In 2015, videos (TV, Movies, etc., excluding Adult Content) accounted for about 50 percent of pirated content, and adult content accounted for roughly 25 percent of releases found.
The cost of all this copyright infringing releases in 2014 is estimated to be more than $800 billion and continuing to grow. 1.96 million pirated assets are expected by the end of 2015 -- an increase of 22 percent over the last three years. If distribution of pirated games continues at the current rate, over 31,000 unauthorised releases will be active in 2015 -- double the number of pirated releases three years ago.
There's a further cost arising from Malware linked to pirated software. Enterprises will spend $491 billion, due to malware associated with pirated software.
"The findings in Arxan's State of Application Security prove that piracy is one of the greatest threats to intellectual property and creative content, highlighting the enabling role pirated releases play in spreading extremely harmful malware across a range of industries -- where the challenges of defending against it -- are complex, but not insurmountable," says Patrick Kehoe, Chief Marketing Officer of Arxan.
The full report is available from the Arxan website and there's an overview of the findings in infographic format below.
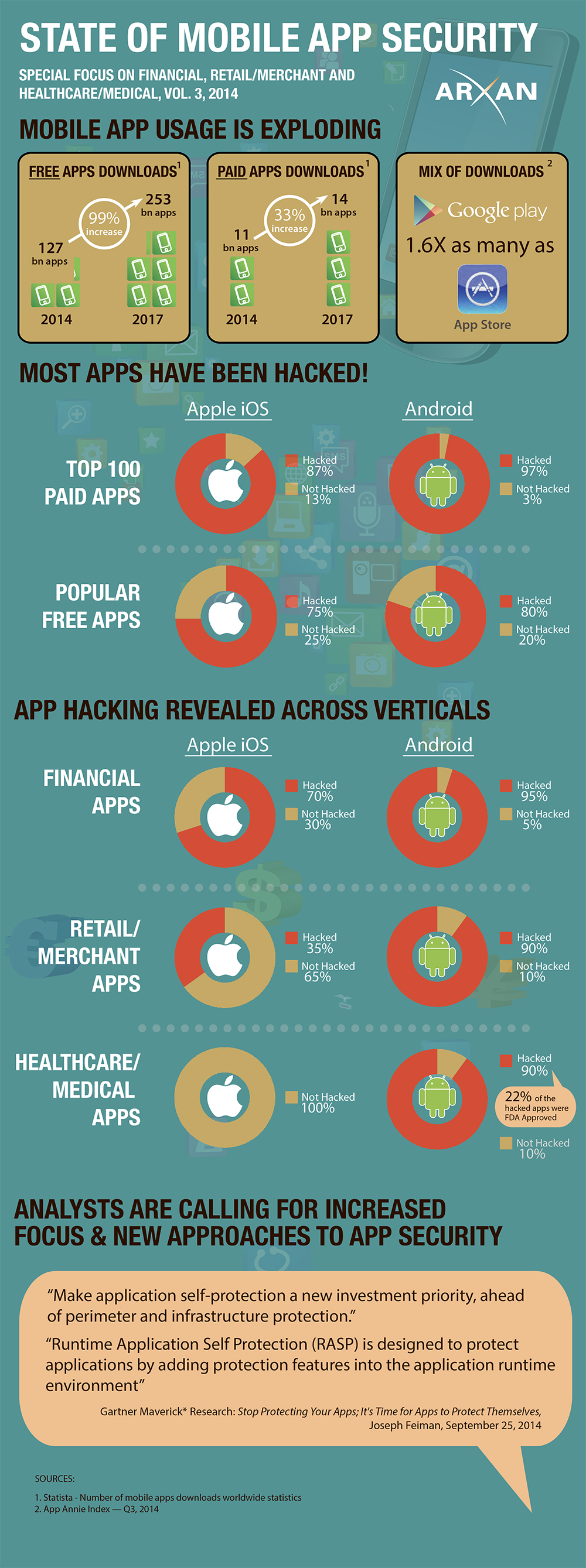
Image Credit: Feng Yu / Shutterstock
-

New survey reveals a preference for local web hosting
Publié: juillet 1, 2015, 3:44pm CEST par Ian Barker

Choosing the right host to use for a website can be a critical decision for businesses, but information on how various hosts measure up can be hard to come by.
Online comparison service Host Advice has released the results of a survey that looks at which Web hosting services are faring best so far this year by looking at each company’s total number of hosted sites and dividing it by the total host sites of the industry over the same period of time.
The results show that GoDaddy ranks the highest in the industry with 5.82 percent of market share amongst worldwide web hosting sites, beating industry giants such as Amazon Web Services and Rackspace. Out of Host Advice's top ten hosting sites, seven are American companies, one is French, and two are German. Host Advice's data also indicates that just over 50 percent of the world's websites are hosted by a US-based provider.
Among other interesting findings are that the top ten hosting companies account for only 20.7 percent of the market. Despite the fact that many non-US companies actually choose American hosting services, the web hosting market is largely local in nature. For example, in France, eight out of the top ten hosting websites are French, and similarly with Germany and German companies. In Italy, nine out of the top ten hosting sites are Italian and in smaller markets like the Czech Republic, ten out of the top ten hosting companies are local.
Generally the hosting market is quite fragmented. In most countries the top global companies occupy less than 20 percent of the market. France is the only exception with OVH dominating 64 percent locally.
"Web hosting comparison is a competitive market," says Eliran Ouzan, the Founder of Host Advice. "Many web hosting comparison sites are not really showing the top companies, but rather the ones that pay a fee. We are honest in how we rank the most popular web hosting sites as well as how we survey their customers for quality. Our goal is to give our customers all of the relevant information so they can choose the site that meets all of their web hosting needs".
You can see an overview of the findings in infographic format below.
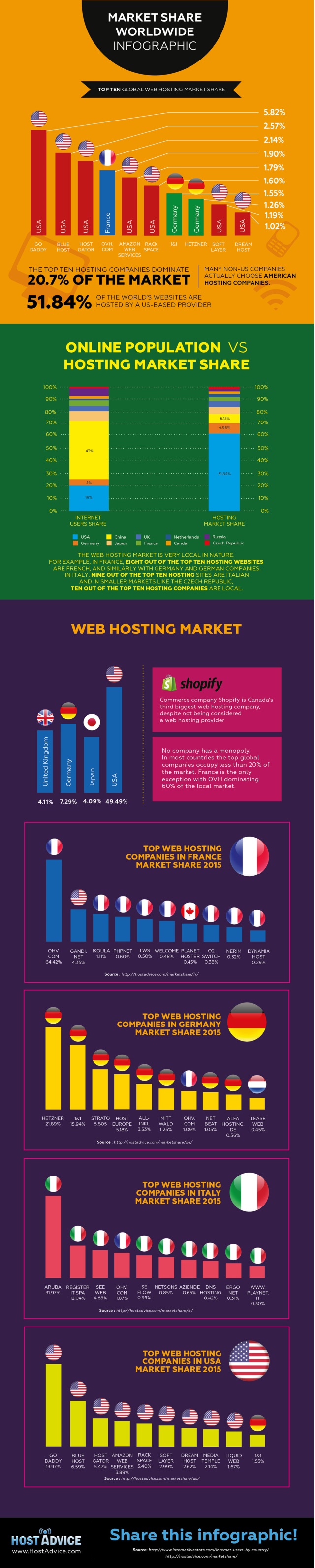
Photo Credit: Yuriy Boyko/Shutterstock
-

How personalization is changing the face of marketing [Q&A]
Publié: juillet 1, 2015, 3:01pm CEST par Ian Barker

[BetaNews Recommended Reading] Companies today have access to more information about their customers than ever before. This gives them the opportunity to effectively personalize their marketing messages, but are they failing to take advantage of the opportunities this offers? And with large volumes of often unstructured data available how difficult is it to find and use the right information?
We spoke to Sara Vera, data scientist at CRM specialist Insightly to find out more about the challenges enterprises face in adapting to a personalized world.
BN: Is personalized communication really a more effective way of reaching customers?
SV: Consumers today are savvy shoppers and expect companies to understand them and their needs. If you can predict customers' needs or wants based on previous purchases, they are more likely to make a purchase in the future, while also increasing their overall spend. Personalization evokes a more emotional response, driving customers to take action. For example, an email that comes from a real person rather than a mass email blast, complete with a personal tone, will see much higher open rates. A personal touch can make all the difference.
BN: Does personalization only work for existing customers or can it help recruit new ones too?
SV: Both. Even if you don't know a potential customer's purchase history, you can leverage other details, such as location, age or gender to create individualized messages. Your communication with customers might be based on broad information, but it's a better starting point than not adding personalized information at all. If something in your communications resonates with your potential customer, he or she is more likely to engage with your brand.
BN: Is there a danger that companies can simply be overwhelmed by the amount of data they’re now able to collect?
SV: This is a tricky question because there are a couple of things to consider. There is no danger of being overwhelmed by the amount of data a company collects if the leaders of the company hire the right data architects, scientists and analysts to figure out what information is most important to their customers, how to use the data and how to act on those insights. However, if a company hasn't hired the right staff, it can be easy to think it is collecting and analyzing the right data when that is not the case. This is why it takes solid statistical education to get good insights when you have a lot of data with which to work. The main takeaway is to hire competent employees that you can trust.
BN: How can businesses make use of unstructured information, such as that collected from social media?
SV: Considering that 80 percent of a company's data is unstructured in the form of emails, social media posts and phone calls, it's easy to overlook valuable insights, which can lead to a lot of missed opportunities. It can seem like a daunting task, but capturing and analyzing this data is valuable for identifying patterns and trends that can give you an idea of your customers' thoughts and feelings. Once you've decided on a toolset, you can do several types of analyses with unstructured data, such as:
* Signal detection and trend analysis to identify recurring themes and patterns.
* Information extraction, categorization and mapping to pull information out of text and map it to something. For example, pulling a location name in text and putting it on a map.
* Content-based clustering to segment information, or even customers, based on similarities in preferences, feelings and thoughts.
BN: How long, and how much data, does it take before a consumer profile is accurate enough to be useful?
SV: The more you know about your customers, the easier it is to figure out why they buy from you and where there are opportunities to sell more. It doesn't take much more than age and gender to assume quite a bit about your customers. Add location, income and/or spending habits and you have a lot of information with which to work. Once your customers build a purchase history, you should have a pretty good idea of who they are as consumers. If you want to dive deeper into the 'why' and 'how' of customer behavior, consider surveys and interviews with various customer segments to gain a comprehensive view of who your customers are and where opportunities lie.
However, proceed with caution when using third-party data to fill out customer profiles; it is sometimes treated as static information when it's really not. For example, if you email a customer offering him a romantic getaway promotion, but he is recently divorced, he is much more likely to be annoyed and unsubscribe from your email list than if he had received a generic email.
BN: Is it likely that consumers will become resistant to increasing levels of personalized communication? How can they remain in control?
SV: Customers could become resistant to increasing levels of personalized communication after a point, however, they do appreciate some level of targeted marketing. Privacy versus targeted, personalized marketing will be a difficult thing to balance over the next few years. There is so much data out there and companies are continuously experimenting to determine where the line should be drawn. Customers don't want to be reminded of the NSA or Big Brother, but they do like to see ads that are interesting to them. Businesses need to be smart about data collection and only aggregate information relevant for basic targeted marketing and remember to keep that data updated and accurate.
Image Credit: iQoncept / Shutterstock
-

The organizations we least trust with our data
Publié: juillet 1, 2015, 12:30pm CEST par Ian Barker

US consumers are most concerned about the ability of retailers and government departments to protect their data according to a new survey.
The Security Insights survey from Unisys shows that 44 percent of American respondents are worried that their personal data held by retailers is likely to be breached in the next year, as many consumers seem to be losing trust in retail data security owing to recent high profile breaches.
Concerns about unauthorized access to personal data held by US government agencies is also quite high at 39 percent, again possibly due to recent high profile breaches. Healthcare and banking organizations fare better in terms of retaining consumers' confidence that their personal data won't be breached in the next year, with only 28 percent worried about healthcare breaches and 24 percent about banking.
"Organizations that hold consumers' personal data have a major challenge maintaining public confidence that they safely protect private information," says Dave Frymier, vice president and chief information security officer at Unisys. "While hackers will always find their way into an organization's network, enterprises can protect high-value data through basic precautions like patching and sharing threat intelligence as well as using advanced security technologies like micro-segmentation".
Americans are less worried about data breaches than those in other countries, however. US respondents had the lowest overall level of concern about likely security breaches among the 12 countries surveyed. For example, nearly twice the percentage of respondents in the Netherlands and Germany thought a breach of their personal data was likely than their counterparts in the US.
Results from the survey also show mixed feelings about the use of biometrics to protect smartphone data, with only 38 believing that it strengthens security. It also shows that men are more likely to use biometrics to protect their devices than women.
The full US report can be downloaded from the Unisys website. Details for other countries will be available soon.
Image Credit: Lightspring / Shutterstock
-

PagerDuty backs its product with Downtime Insurance
Publié: juin 30, 2015, 3:56pm CEST par Ian Barker

The IT services industry revolves around service level agreements (SLAs) but they don't often provide adequate compensation for damage caused to business by an outage of providers' systems.
Operations and performance management specialist PagerDuty is so confident of its product that it's putting its money where its reliability is and introducing Downtime Insurance, the IT operations industry's first reliability service-level agreement to be backed by a multi-million dollar insurance policy.
Under the insurance agreement terms, PagerDuty will reimburse customers for profit losses should there come a time when PagerDuty is not available to them during a downtime incident.
"We've spent over six years bulletproofing the PagerDuty platform to ensure high availability for our customers," says PagerDuty CTO and Co-Founder, Andrew Miklas. "Today, 37 of Fortune 100 companies trust PagerDuty to help them deliver highly reliable services. We want our customers to know that we're truly committed to PagerDuty's availability with a Downtime Insurance guarantee that reimburses customers for profit losses if they occur".
PagerDuty helps customers manage incidents, minimize downtime and resolve issues more quickly. High availability is maintained via multiple data centers across multiple hosting providers geographically, redundant telephony providers across each notification channel, proprietary technology for tracking alert delivery through all providers and for automatically re-routing if delivery is slow and rapid scaling capabilities to support any size business. PagerDuty also has weekly 'Failure Friday' testing during which it proactively looks for weaknesses in its infrastructure and fixes them.
Downtime Insurance is available to customers on PagerDuty's Enterprise Plan, more information is available on the company's website.
Image Credit: donskarpo / Shutterstock
-

Kyvos aims to change the big data analytics landscape
Publié: juin 30, 2015, 3:03pm CEST par Ian Barker

Big data can provide many benefits for businesses, but the complexities of dealing with systems like Hadoop can make it expensive and time consuming to roll out projects.
California-based Kyvos Insights is launching a new product specifically designed for big data that enables business users to easily and quickly derive powerful insights from their data for more informed decision-making, with no programming required.
Kyvos helps enterprises remove the complexities of Hadoop and deal with data at any scale with fast response times and an interactive experience. Its 'cubes on Hadoop' technology allows business users to visualize, explore and analyze big data interactively, working directly on Hadoop.
"Companies are collecting unprecedented amounts of data, but it's very difficult for a business user to directly access and interact with this data in a meaningful way," says Ajay Anand, vice president of products at Kyvos Insights. "Kyvos addresses this need by enabling interactive analytics on big data using Hadoop at any scale, with instant response times. Business users can now visually analyze their data and get insights instantly, without having to wait, so they can make smarter, more informed decisions".
The product has been developed with the help of industry leaders most affected by the benefits and challenges presented by big data analytics. It's being used in industries including telecommunications, media and entertainment, financial services, technology and travel.
Kyvos allows business users to develop insights from all data, both structured and unstructured, regardless of size and granularity with a simple, drag and drop interface. Users can do self-service analytics and work visually, with no programming required. They can drill down and examine all aspects of data and interact with it without waiting for reports and get query results in seconds.
For developers it brings the ability to build cubes directly on Hadoop at any scale for multi-dimensional analytics. They can also deal with rapid data ingestion with incremental cube builds, avoid having to move data for analysis, and transform data visually with no programming required.
For more information and to schedule a demo pay a visit to the Kyvos Insights website.
Image Credit: Maksim Kabakou/Shutterstock
-

Network visibility solution harnesses the power of big data
Publié: juin 30, 2015, 1:10pm CEST par Ian Barker

Thanks to the Internet of Things and the growth in the use of mobile devices, network traffic is growing faster than ever. But the tools used to manage and monitor that traffic haven’t kept pace.
Network visibility specialist Kentik (previously known as CloudHelix) is launching a SaaS platform to enable full visibility into networks of any size giving real-time, actionable insights into network traffic activity, DDoS attacks and peering efficiency.
Based on a big data engine Kentik Detect is quick and easy to deploy and equips service providers, web enterprises and network operations teams with the insights they need to keep their networks up and running smoothly. Kentik Detect has the capacity to store raw data for 90 days or longer and so can provide better detection, clearer understanding, and real-time response to all network conditions.
With high levels of raw data retention and fast query responses combined with proactive real-time alerting, Kentik Detect allows operators to understand how their networks are behaving, reveal the root causes of issues, and plan for growth based on reality rather than guesswork.
"My peers and I have been struggling with poor tools for network visibility and analytics for decades. As the volume and complexity of networks has grown, the data handling and analytics required have become so complex that traditional network management tools have been unable to scale and innovate," says Avi Freedman, Co-founder and CEO of Kentik. "We intend to make Kentik the single, unified source of intelligence for all infrastructure data. By bringing the SaaS model and unparalleled analytics to network and infrastructure management, we are redefining what it means to have true operations visibility, and providing the insights needed to drive real-time, data-driven operations".
Available now as either public SaaS or on-site SaaS, you can find out more about Kentik Detect on the company's website.
Photo credit: asharkyu / Shutterstock
-

Huddle launches updated iOS collaboration app
Publié: juin 30, 2015, 11:31am CEST par Ian Barker

Businesses need their employees to be able to collaborate on projects but the increasingly mobile nature of the workforce and the pressures of BYOD use can make that hard to achieve.
Collaboration software specialist Huddle is updating its iOS apps to provide iPhone and iPad users with a simple and secure way to collaborate on content and manage projects while on the move, as well as delivering a more social experience by focusing on team activity around content.
"Surfacing relevant content is vital for mobile users, and our iOS apps are designed to help them get to the work that matters most by placing particular focus on discoverability of content and tasks," says Stuart Cochran, CTO of Huddle. "No one wants to have to drill down into folders to find files while they're rushing between meetings, so notifications and a live activity stream keep them up to date with team progress, upcoming tasks and approvals. It's a far more effective way to get to the content that matters, as well as being a more enjoyable experience".
The latest updates improve the cross-platform functionality of Huddle, allowing users to pick up where they left off as they switch between their PC, smartphone and tablet. Features of the latest iOS version include, version control which lets users rdit files using compatible iOS apps, lock files to protect them from further editing and maintain version control through cross-platform synchronization.
Documents can be approved, or approval can be requested and approval status tracked. Users can quickly find assigned tasks, comment on files and respond to team questions as the app makes items needing attention more discoverable. The search function will now immediately present users with a list of recent files, before a search term is even entered. Documents can be made available offline across all devices, then automatically synchronize when reconnected.
"If I'm working on a document at my desk on my laptop, my recent files will automatically be waiting for me on my iOS devices," adds Cochran. "Huddle will even suggest files that it thinks will be of interest to me and sync them down to my mobile devices ready for my commute home. It makes hopping between devices seamless, it reduces the time spent searching for documents and it keeps users on top of their workload, wherever they are".
The iOS apps are available now for anyone with a Huddle account and you can find out more on the company's website.
Image Credit: Tischenko Irina / Shutterstock
-

NETGEAR launches cloud management platform
Publié: juin 29, 2015, 3:03pm CEST par Ian Barker
It's not uncommon for businesses to have multiple access points, whether on a single site or in multiple locations. This can lead to challenges when it comes to managing access and ensuring software and security are up to date.
To make life simpler NETGEAR is launching a software as a service platform called Business Central designed to provide small to mid-sized organizations with an affordable way to establish and manage key IT networking services and network devices.
The first service to be introduced under Business Central is a Wireless Manager which makes it easy for businesses with multiple sites like retail chains, coffee shops and those with several branch offices to roll out the same settings to every location and manage it all centrally.
"Having multiple standalone access points is no longer feasible as configuration changes become routine rather than occasional. However, for some organizations, the jump to a managed wireless LAN network can become demanding and overly complex for both IT budgets and IT resources," says Peter Newton, senior director of product management for the NETGEAR Commercial Business Unit.
"What's needed is a bridge solution between standalone APs and a controller, where flexibility, scalability and ease-of-use are standard and -- more importantly -- affordable," adds Newton. "For small to large enterprises and organizations with single to multiple branch locations, our Business Central Wireless Manager maximizes ROI and is the optimum tool for easy and cost-effective centralized WiFi management. It's an effective solution for both customer-deployed scenarios as well as a VAR-managed service. VARs and their customers can benefit from a free 90-day introductory trial".
With Business Central Wireless Manager, all management is performed remotely through a standard web browser. Admins can manage wireless SSIDs, configure wireless security settings, control free or fee-paying guest and private Wi-Fi access on the network, and run bandwidth usage reports. It allows clear, comprehensive and real-time visibility into the network for total control of evolving service needs.
Pricing is per access point per year on 12 or 36 month contracts but is arranged so that even if new devices are added mid-contract everything expires together to make licensing easier. You can find out more about Business Central Wireless Manager on the NETGEAR website.
-

Almost half of leading websites fail security and privacy tests
Publié: juin 26, 2015, 12:57pm CEST par Ian Barker

In an audit of 1,000 websites, including those of leading retailers, banks, social media, news and government bodies, 46 percent were found vulnerable to known online security threats.
According to the non-profit Online Trust Alliance, which conducted the study, sites belonging to Internet of Things companies are most at risk. The audit included the websites of 50 leading Internet of Things device makers, focused on wearable technologies and connected home products. 76 percent of these sites failed the assessment, while only 20 percent scored highly enough to qualify for the OTA's Online Trust Honor Roll.
Craig Spiezle, Executive Director and President of OTA says, "The results of this audit serve as a wake-up call to Internet of Things companies who are handling highly sensitive, dynamic and personal data. In rushing their products to market without first addressing critical data management and privacy practices, they are putting consumers at risk and inviting regulatory oversight".
The OTA evaluates websites based on dozens of criteria in three categories: consumer protection, privacy and security. While 46 percent of audited websites failed outright, another 10 percent didn't perform strongly enough to earn the OTA's Honor Roll status. This is an improvement, however, with 44 percent qualifying for Honor Roll status compared to only 30 percent in 2014.
Among sites that scored well, Twitter topped the overall ratings for the third year running. Top banking site was the USAA Federal Savings Bank and top government site the Federal Deposit Insurance Corporation (FDIC). The retail sector saw the largest increase in Honor Roll qualification, up from just 24 percent of evaluated websites in 2014 to 42 percent in 2015.
"Our audit and Honor Roll program rewards companies for a commitment to data stewardship, security and privacy policies that protect against cybercrime’s escalating threats," says Spiezle. "OTA commends the companies whose dedication to responsible data practices earned them a place on our list. At the same time, it is concerning to see others remain complacent, failing to embrace responsible practices year after year".
The full report listing all Honor Roll sites is available as a PDF on the OTA's website.
Image credit: Jimmi/Shutterstock
-

Click fraud provides the gateway to ransomware
Publié: juin 26, 2015, 12:09pm CEST par Ian Barker
Just as drug dealers try to get people hooked on progressively more addictive substances, it seems that the hijacking of a device to perform simple click fraud can quickly lead to the distribution of nastier malware.
According to the latest State of Infections report from threat protection specialists Damballa, a compromised device, originally exploited for the relatively low-level purpose of committing of click fraud -- a scam to defraud pay-per-click advertisers -- became part of a chain of infections, which led within two hours to the introduction of the toxic ransomware CryptoWall.
The findings are based on analysis of the RuthlessTreeMafia click fraud malware introduced by the botnet Asprox. Once the device was under the command of the botnet, the RuthlessTreeMafia operators were able to sell access to the compromised device to others who used downloaders to deliver the Rerdom and Rovnix Trojans, generating additional revenue for the criminals.
As the click-fraud infection chain continued, the device became infected with the CryptoWall ransomware. The click fraud activity was able to continue though as the device remained under criminal control and the attacker continued to make money. Within two hours, the initial click fraud infection had escalated to subject the compromised device to three further click fraud infections as well as CryptoWall itself.
"As this report highlights, advanced malware can quickly mutate and it's not just the initial infection vector that matters, it's about understanding the chain of activity over time. The intricacies of advanced infections mean that a seemingly low risk threat -- in this case click fraud -- can serve as the entry point for far more serious threats," says Stephen Newman, CTO of Damballa. "The changing nature of these attacks, underscores the importance of being armed with advanced detection, to combat these more stealthy threats. As infections can spread quickly through the network, security teams should take proactive measures to avoid becoming a cautionary click-fraud tale".
More information can be be found in the full report which is available to download from the Damballa website.
Image Credit: djmilic / Shutterstock
-

Analytics app helps make sense of marketing data
Publié: juin 25, 2015, 4:11pm CEST par Ian Barker

Marketing departments today operate across multiple channels from traditional routes to digital campaigns and social media. That means they're dealing with more data than ever before.
But being data rich isn't an answer in itself as the information can be fragmented and difficult to analyze. Big data insights specialist Datameer is launching its Multi-Channel Marketing Analytics App which offers an end-to-end view of the marketing process from lead-to-customer.
It combines and analyzes data from websites, digital ads, social media, Salesforce and Marketo into one unified view of the customer journey, giving marketers a comprehensive understanding of the behavior of leads.
The software provides four key insights, letting marketers see where high quality leads come from, what combination of campaigns converts leads to customers, what assets are the most effective in influencing those conversions, and what the conversion speed and effectiveness is of both campaigns and assets.
"Marketing executives have to become data-driven in order to be key drivers of customer acquisition for their companies", says Azita Martin, CMO of Datameer. "We want to remove the barriers that are commonly encountered when using traditional marketing platforms and make it incredibly easy to understand the lead to customer journey. Now, businesses can decipher and drill down into customer decisions to deliver higher levels of conversion and greater marketing and sales success".
Datameer's application also delivers an on-demand dashboard that allows users to view the performance of channels, campaigns and assets in a single view by deals, opportunities and leads. This gives executives a critical view of how they can fine tune customer campaigns while they’re under way. It simplifies a process that's usually manual, can take several hours a week and is usually prepared using spreadsheets.
You can find more information on how Datameer can speed up the analysis of marketing data on the company's website.
Photo Credit: Sergey Nivens / Shutterstock
-

Mobile app developer platform adds new capabilities
Publié: juin 25, 2015, 3:36pm CEST par Ian Barker

With mobile devices becoming increasingly popular there's ever increasing demand for apps, but that can prove a bottleneck for businesses.With the launch of a new version of its RhoMobile developer platform, Illinois-based Zebra Technologies Corporation is aiming to make multi-platform development easier.
RhoMobile 5.1 focuses on supporting more industrial and consumer-facing mobile devices, along with an expanded set of common APIs. New live update and app simulator capabilities enable developers to immediately push code changes out to devices to enable more efficient testing. New common API updates are added for inputting and controlling cameras, barcodes, event timers, and USB printing functionalities.
"With RhoMobile 5.1, we're excited to deliver an improved developer experience that simply makes feature-rich enterprise, consumer mobile apps easier to develop," says Mark Kirstein, senior director, Enterprise Software at Zebra Technologies. "With this launch, we've added support for new devices critical to use in industrial and retail scenarios. The addition of new common APIs means that developers looking to leverage functionality on a specific mobile platform no longer need to consider which API is used for which, because we've added a single, all-capable option. With live updates, developers who previously may have waited 15 minutes each time code was updated to a device for testing can now push those changes automatically and see the impact of those code changes immediately. We're glad to provide these new capabilities, and eager to see developers put them to work to create game-changing apps".
You can find out more and sign up for a free trial of the suite on the RhoMobile website.
Image Credit: Alex Mit / Shutterstock
-

New tool helps companies publish and manage APIs
Publié: juin 23, 2015, 4:31pm CEST par Ian Barker

More and more businesses are publishing their own apps, and that involves the use of APIs. Yet many existing API tools focus only on publishing and ignore the user and partner side of things.
Platform as a Service (PaaS) company WaveMaker is releasing its new WaveMaker Gateway, to make it easier for enterprises to open up their APIs to partners and external developers.
WaveMaker Gateway brings together API publishers and API consumers to form an ecosystem that benefits all of them. It helps in the simplification, management and securing of APIs, as well as making them operationally ready and analyzing external rollouts.
"Custom apps are key to innovating and fostering ecosystems, and this cannot be done without APIs", says Samir Ghosh, CEO of WaveMaker. "WaveMaker Gateway completes our suite of API tools for the enterprise, and is the next step for enterprises looking to selectively and securely share apps outside of their organization with partners as well as third-party developers. We believe we are unique in that we provide enterprise developers with tools to create, manage, and consume APIs and applications -- within and outside the enterprise -- on a single unified platform".
For publishers WaveMaker offers API owners the ability to upload, document and make APIs visible. Product managers can easily publish APIs and apply business relevant policies to manage their external consumption. Operational administrators can monitor the consumption of APIs in real time, providing useful business insights.
For consumers it means that partners as well as third-party developers can choose various API subscription plans based on their needs. They can easily bring onboard applications and generate the required keys to use APIs within their apps. App developers can browse, list, test and understand published API behavior. Developers can also use the visual drag-and-drop Rapid Application Development methodology of WaveMaker Studio to simplify the consumption of APIs and reduce the effort of developing custom apps.
More information on WaveMaker Gateway is available on the company's website.
Image Credit: Profit_Image / Shutterstock
-

BUFFERZONE joins the Intel Security Innovation Alliance
Publié: juin 23, 2015, 3:31pm CEST par Ian Barker

Security of the endpoint is often the weakest link in enterprise security as users may not be aware of the risks from malicious content that can slip past traditional protection.
Endpoint security company BUFFERZONE is announcing today that it's joining the Intel Security Innovation Alliance (SIA) program as a Sales Teaming Partner and that it's been certified as McAfee Compatible with the McAfee ePolicy Orchestrator (ePO) platform.
BUFFERZONE is a containment solution that defends endpoints against advanced malware and zero-day attacks without harming end user and IT productivity. By isolating potentially malicious content from web browsers, email and removable media, it complements McAfee Endpoint Security products and helps defend the organization from advanced threats that can evade detection.
"Organizations are looking for smarter ways to reduce their attack surface and combat advanced threats without investing scarce resources on false alarms and restrictive policy enforcement", says Israel Levy, BUFFERZONE's CEO. "By integrating BUFFERZONE with McAfee ePolicy Orchestrator, IT can leverage existing investments in McAfee ePO and employees can browse the web, open email attachments and access their mobile phones more safely".
It includes a configurable bridge for transferring content and data safely between the container and secure network zones, and provides critical intelligence for enterprise-wide security analytics. BUFFERZONE is a lightweight solution that provides cost-effective containment for thousands of endpoints and is easy to deploy and configure with McAfee ePO.
"We are happy to welcome BUFFERZONE to the Intel Security Innovation Alliance," says Tom Fountain, senior vice president of Strategy and Corporate Development at Intel Security. "Our joint customers can now easily help protect their endpoints using BUFFERZONE solutions and manage those devices through a common, scalable platform".
You can learn more about BUFFERZONE's endpoint protection by visiting the company's website.
Image Credit: Sergey Nivens / Shutterstock
-

Application intelligence platform adds Unified Monitoring
Publié: juin 23, 2015, 2:46pm CEST par Ian Barker

Monitoring applications and their infrastructure can involve the use of multiple different products. According to recent research by Enterprise Management Associates, some 65 percent of enterprises report owning 11 or more commercial monitoring/management tools.
Application intelligence specialist AppDynamics is launching an update to its Application Intelligence Platform that introduces Unified Monitoring to trace and monitor transactions from the end user through the entire application and infrastructure environment to help solve performance issues and improve user experience.
AppDynamics Unified Monitoring is built on a single platform, and monitors and manages end-user experience in the context of business transactions. It traces the entire business transaction path from the end-user device, through the application code, databases, third-party API calls, servers, and other infrastructure, and unifies the monitoring of the application through the business transaction. Using a common data platform makes it easy to install and manage, and provides consistent and shareable interfaces for all users. It can therefore replace a mix of non-integrated, and infrastructure-specific tools that make up the monitoring solution for many enterprises.
"What really sets Unified Monitoring apart is its focus on business transactions and the end user," says Jyoti Bansal, AppDynamics founder and CEO. "You can’t understand what the experience is like for the end user by looking at this silo or that silo. You need to have the big picture to see how a transaction is performing from start to finish. If the shopping cart checkout process is slow, what’s making it slow? With Unified Monitoring, we can pinpoint the issues and quickly get to root causes and resolve them. It's a radically different approach from the old way of looking at infrastructure and trying to piece together the picture. In this new world -- where businesses are defined by software -- it's clear that unified, fully integrated, application-centric monitoring is an absolute must-have".
AppDynamics Unified Monitoring offers a single unified platform, with one consistent user interface, one data platform for everything, one easy install, and easy ongoing management. There are flexible deployment options including on-premise, SaaS, or hybrid.
Role-relevant views support DevOps collaboration and give teams awareness of their areas of responsibility. It offers comprehensive application and infrastructure support for end-user client applications/browsers, application code and more, plus the platform can be extended to support a broad range of components and infrastructure through a library of community-contributed extensions.
"We've been working toward this for a long time," Bansal adds. "Everything in Unified Monitoring works together because it’s been designed to work together and is architected on a single platform. It's not stitched together as an afterthought. And now with the addition of Browser Synthetic Monitoring and Server Monitoring, we have a true end-to-end solution, all unified into a single view, a single fully integrated platform".
Fore more information and to sign up for a free trial you can visit the AppDynamics website.
Photo Credit: Sergii Korolko/Shutterstock
-

Intronis launches simplified backup platform
Publié: juin 23, 2015, 11:51am CEST par Ian Barker

For smaller businesses organizing backups can be a chore which is why they often choose to buy a service solution from their systems provider rather than do it in house.
Backup and data protection specialist Intronis is one of the leaders in backup platforms for IT providers and is launching a new release of its ECHOplatform designed to deliver simplified operations and improved value.
Enhancements in the latest version include a new and intuitive dashboard that's easy to read and manage. It enables channel partners to streamline administrative tasks and accelerate problem resolution by capturing the health of the entire Intronis ECHOplatform portfolio in a single interface.
New filtering options deliver critical data at a glance and save those options for future reference each time the portal is used. There's also an automated executive summary report generator. The reporting tool complements the ECHOplatform dashboard and makes it easier for channel partners to demonstrate the value of their services and discuss opportunities to improve the overall effectiveness of their client's data protection strategy.
"Making it easier and more profitable for our channel partners to deliver a comprehensive data protection strategy to small and midsize businesses is what Intronis does best," says Chris Crellin, vice president, product management, Intronis. "We're specialists, and by keeping our focus on technology and partner enablement we are able to optimize, refine, and refresh our cloud-based data protection solution to meet and anticipate the needs of our partners and their customers".
The Intronis ECHOplatform Summer Release '15 is now available to channel partners and is being rolled out in phases to existing Intronis partners over the next 45 days. The data protection service portfolio is sold exclusively through IT channel partners to small and mid-size businesses as a managed service.
More information on the latest ECHOplatform is available on the Intronis website.
Image Credit: Oleksiy Mark / Shutterstock
-

LuguLake-24 Bluetooth speaker -- style over substance? [Review]
Publié: juin 23, 2015, 10:29am CEST par Ian Barker

Bluetooth speakers usually need some sort of distinctive feature to help them to stand out from the crowd. In the case of the LuguLake that distinctiveness is in the way it looks.
The first thing that strikes you is the funky design, it's about the size of a tennis ball, or an apple if you prefer, with a shiny black finish and a sort of suspended saucer over the speaker cone itself. On the top of this is a touch pad that acts as a volume control as well as allowing you to pause and skip tracks, and answer calls so you can use it as a speakerphone.
There's a USB socket on the back -- this is the only connection, it lacks an aux-in for an alternative audio source -- and a power switch on the base. An LED next to the USB port lets you know it's charging, though this is in a recess so it's hard to see if you're looking from above.
The unit feels nicely weighty and it comes with a short USB cable and small instruction pamphlet. The glossy piano black finish looks good but quickly picks up more fingerprints than a police database. Once it's charged and you switch it on you'll find that there are voice prompts to help you with the Bluetooth pairing process. You can use NFC if your phone supports it just by touching it against the front of the speaker.
After you've paired it and begin to play some music you’ll find that the speaker has a neat party trick. The underside of the flying saucer bit lights up and pulses a dull red though this isn't in time with the music. This is called a "Breathing Light" in the instructions. It's amusing the first few times you use it though ultimately a bit pointless.
The listening experience is acceptable without being in any way outstanding. Probably what you’d expect from a 2-inch speaker with a power output of only 2W and a frequency range of 60Hz to 20KHz. It has the sort of the sound quality you might get from a portable radio, there isn't quite enough bass and even at maximum volume you never really get a room filling sound. Don’t worry about distortion, you can't turn it up high enough to get any.
As a piece of quirky design that will look good on a shelf and amuse your visitors with its pulsing red light the LuguLake-24 is hard to fault. As an audio experience though you can do a lot better at this price.
The speaker costs $39.99 from Amazon in the US or £32.99 on Amazon UK. BetaNews readers can get a 20 percent discount. For US orders enter code 53B3RTFT at the checkout, customers in the UK should use code IORQIC5G -- codes expire on June 30.
-

More than just a USB hub -- Inateck HB4009 [Review]
Publié: juin 22, 2015, 12:17pm CEST par Ian Barker

USB hubs are commonplace and, let's be honest, not especially exciting pieces of kit. Inateck’s HB4009 is a three-port USB 3.0 hub, but it also has an extra trick up its sleeve. It has a Magic Port, allowing you to link two systems together for file transfers or establish a client/host link using the USB On-The-Go (OTG) standard.
This makes it a versatile little device as you can link Windows, Mac OS and Android devices to their own kind or to each other. You can also attach another USB device like a flash drive or camera to a system, such as a tablet, that might not otherwise have a suitable port.
Some Android devices support a mouse and keyboard swap via OTG so you can control the device from your PC. Links for the software needed to connect your systems are stored on the HB4009 and you're prompted to install it when a connection is made, so getting hooked up is a simple plug and go process. For Android devices you need to scan a QR code to install the Windroid Linker app.
It feels well made and is nicely weighty, the contacts of the USB ports and the OTG cable are gold-plated. A mini USB adaptor is included for OTG connection to smartphones and other devices without a full-sized USB socket.
If you've bought a new PC and want to transfer data from your old one, or regularly need to transfer files between computers, smartphones and other devices, then the HB4009 is well worth having.
The device costs $24.99 on Amazon (£22.99 in the UK) and you can find more details on the Inateck website.
-

Samsung announces fix for Galaxy keyboard vulnerability
Publié: juin 19, 2015, 1:12pm CEST par Ian Barker

We reported on Wednesday that a flaw in the pre-installed SwiftKey keyboard software could put millions of Galaxy devices at risk.
Samsung has moved fast to reassure users and has announced that it's preparing a fix which will be pushed out to devices in the next few days. In addition to the update the company says it will continue to work with third-parties like SwiftKey to address risks in future.
In its official statement the company is at pains to point out that the likelihood of an attack successfully exploiting the vulnerability is low. It says, "This vulnerability, as noted by the researchers, requires a very specific set of conditions for a hacker to be able to exploit a device this way. This includes the user and the hacker physically being on the same unprotected network while downloading a language update. Also, on a KNOX-protected device there are additional capabilities in place such as real-time kernel protection to prevent a malicious attack from being effective".
The update will be rolled out via the KNOX security platform which is installed on all models since the Galaxy S4. To make sure you can receive the update you need to go to Settings > Lock Screen and Security > Other Security Settings > Security policy updates, and make sure that the Automatic Updates option is activated. On the same screen, you can also click Check for updates to manually retrieve any new security policy updates.
For devices that don't have KNOX by default Samsung says it's working on expediting a firmware update that will be available once testing and approval is complete.
If you have a Samsung smartphone make sure that it's properly configured to receive the update.
-

Forensics for everyone as a new approach to network security [Q&A]
Publié: juin 19, 2015, 12:13pm CEST par Ian Barker

Organizations are increasingly under pressure to respond to security incidents quickly in order to minimise damage and losses. Yet conventional security approaches don't always provide enough information, or make it accessible enough, for this to happen.
Is it time for businesses to take a more forensic approach to securing their networks? And won’t this involve time-consuming trawls through masses of raw packet data? We spoke to Uriel Cohen, head of marketing at network forensics specialist WireX Systems to find out.
BN: Network visibility is nothing new, so why has it become more relevant recently?
UC: The ability to truly understand what is going on in the network was and always remains critical to every organization with an IT team. And yet, 2014 has proved that no one is immune to cyber-attacks, from large finance firms who spend millions of dollars on security, to small retailers who mistakenly believe they are not a target. The paradigm of enterprise security today is shifting from prevention towards detection and forensics and security budgets are changing accordingly. It all comes down to better visibility as a first and crucial step to mitigate business loses from the inevitable security beaches.
BN: Why isn't the normal approach of collecting logs and other metadata sufficient any more?
UC: Network solutions record high-level event details to logs and discard the actual content. This is barely enough and sometimes even irrelevant when trying to understand network activities across the many applications running your business. It wasn't surprising when Verizon found that less than one percent of successful attacks were spotted by SIEM. For over a decade we were trying to achieve contextual awareness around incidents by aggregating and correlating endless logs and failed. Today we have the technology to keep it all -- the actual content of our entire network history.
BN: So how come most organizations today are still left behind with limited visibility into their network activity?
UC: To date, there have been no tools available to the enterprise that could bring true value. Adopters of forensics technologies report challenges in investigating network and security incidents without a team of dedicated experts working around the clock. Every week we are meeting more frustrated analysts, telling us that instead of devoting their time to conducting investigations, they are sorting through massive amounts of unrecognized sessions, gluing together the bits and bytes. Another important factor is the required storage. Existing solutions are based on full packet recording, meaning that you need 11TB to store a single day of 1Gbps network traffic. Obviously, this cannot scale considering today's growing infrastructures.
BN: How does WireX approach the problem?
UC: Think of it as a Google-like interface that enables even entry-level personnel to understand every action and piece of data that traversed the network. Instead of choosing between limited visibility with metadata only or an army of experts digging in mountains of packets, WireX approaches this with deeper, more powerful analysis capabilities. The WireX Platform automatically analyses all parts of the enterprise network to reduce to zero the time wasted on collecting relevant intelligence.
BN: What makes WireX special? Tell us a bit more about your analysis capabilities.
UC: Our core technology is WireX Layer-8 Contextual Analysis which provides real-time network analysis. WireX picks up where traditional DPI has failed, creating intelligence that is human-readable. The analysis engines understand the activities within each application and therefore reveal the precise actions performed and extract its content. This includes the data center, perimeter, organization's LAN and the cloud, with the ability to easily add new decoders also for homegrown applications. Moreover, by performing real-time extraction and compression of textual content, the WireX platform provides significantly longer history than traditional solutions that rely on full-packet capture.
BN: Does this do away with the need for specialist analysts?
UC: Once the network traffic is fully analyzed, stored and indexed, security and IT teams can finally perform their tasks effectively. Whenever an alert is triggered by any existing solution (such as next-generation firewall, IPS or SIEM), the solution will provide the complete network story related to the incident in question, including the actual content. The important part to understand here is that the intelligence delivered can be understood immediately, without any additional post-processing needed.
BN: What's the next step for the company?
US: WireX was founded in 2010 to empower defence forces and intelligence agencies with tools to combat cyber-terrorism. Today, we are expanding our reach to the enterprise market, tailoring WireX's field-proven technology to revolutionize security operations. We are currently preparing for launch in the US by the end of the year.
Image credit: d3images/Shutterstock
-

Komprise aims to manage data growth while cutting costs
Publié: juin 18, 2015, 6:31pm CEST par Ian Barker

It's reckoned that 90 percent of the world's data has been created in the last two years and that every two years the amount of data will continue to double.
Existing data management solutions aren’t designed to cope with this rapid explosion of data. However, San Franciso-based startup company Komprise is building a platform uses analytics-driven adaptive automation to manage massive data growth transparently across all storage.
Businesses are currently spending around 25 percent of their IT budgets on storage, and 80 percent of this cost is in the management of the data -- storing, migrating, protecting, and finding information. Komprise aims to eliminate 70 percent of these costs by breaking the cycle of buying and managing more storage. It intelligently automates the data management processes transparently across data silos.
"The reality is most businesses today are struggling simply to keep up with the growth of their data," says Krishna Subramanian COO and co-founder at Komprise. "Not only are storage needs growing rapidly, but most of the data ends up collecting dust in a storage bin since it can be costly and complex for a company to find and interpret. Our solution helps businesses to organize, discover and unlock the value of unstructured data while streamlining costs".
The founding team has successfully built two prior start ups aimed at simplifying complex IT infrastructure and Komprise has raised $6 million in venture capital funding to expand and develop its new platform.
You can find out more and sign up for the early access program on the company's website.
Photo Credit: wavebreakmedia/Shutterstock
-

SAP HANA vulnerable to weaknesses in encryption keys
Publié: juin 18, 2015, 3:01pm CEST par Ian Barker

SAP HANA is the ERP specialist's recent key product. Based on in-memory technology, it provides a considerable increase in the speed of data processing, helping large enterprises process their data in real time. It's implemented in more than 500 companies.
But at a "Black Hat Sessions" conference today in the Netherlands, Dmitry Chastuhin, Director of professional services at SAP security company ERPScan, has presented a report on the latest trends in SAP Security. It uncovers multiple problems related to encryption algorithms and static keys used by SAP in their products.
The SAP HANA database holds the bulk of its data in memory for maximum performance, but it still uses persistent disk storage to provide a fallback in case of failure. Data is automatically saved from memory to disk at regular savepoints. The data belonging to a savepoint represents a consistent state of the data on disk and remains in place until the next savepoint operation has completed -- according to the SAP Security Guide. This means that some data is stored on the file system, and an attacker can get access to it.
"People think that SAP HANA is in-memory database and doesn’t store any sensitive data on hard drive. The reality is not that nice as you might think. Some data is actually stored on the disc," says Chastuhin. "For example, some technical user accounts and passwords along with keys for decrypting savepoints are stored in storage named hdbuserstore. This storage is a simple file on the disc. It is encrypted using 3DES algorithm with a static master key. Once you have access to this file and decrypt it with static master key, which is the same on every installation, you get system user passwords and keys for disk encryption. After that, you can get access to all data. According to our consulting services, 100 percent of customers we analyzed still use default master key to encrypt hdbuserstore".
SAP's mobile platform has a similar issue with passwords stored in encrypted form but with a static key. The report also reveals that the XS JavaScript language for working with the HANA database can be vulnerable to SQL injection attacks. It points out that if these issues are present in SAP's code they're also likely to be found on custom applications developed by third-party or in-house developers.
More information on the vulnerabilities uncovered in SAP can be found on the ERPScan website.
Image Credit: Pavel Ignatov / Shutterstock
-

Vulnerability could put up to 600 million Samsung smartphones at risk
Publié: juin 17, 2015, 3:52pm CEST par Ian Barker

According to a report published by security specialist NowSecure, a vulnerability in the Swift keyboard software, pre-installed on Samsung devices, can allow a remote attacker to execute code on the user's phone as well as access functions like the microphone and camera.
Worse still there's no way to uninstall Swift and the flaw can be exploited even if you don't use the app. It affects leading Samsung smartphone models from the Galaxy S4 to the S6.
Samsung and the Google security team were notified in December 2014. Samsung began providing a patch to mobile network operators in early 2015, but it's not known if the carriers have rolled out the patch to devices on their networks. It's also difficult to determine how many mobile device users remain vulnerable, given the device models affected and the number of network operators globally.
It isn't easy for users to tell if their device has been patched either. NowSecure recommends avoiding connection to insecure Wi-Fi networks, contacting their service provider for patch details or even temporarily switching to a different mobile device.
Standalone SwiftKey apps on the Google Play and Apple App Stores are not affected by this flaw. A SwiftKey statement says, "We supply Samsung with the core technology that powers the word predictions in their keyboard. It appears that the way this technology was integrated on Samsung devices introduced the security vulnerability. We are doing everything we can to support our long-time partner Samsung in their efforts to resolve this important security issue".
It goes on to say that the vulnerability is not easy to exploit and that users would need to be connected to a compromised network where hackers had the right tools available to attack their device.
More information including a list of affected Samsung models is available on the NowSecure website.
-

PagerDuty speeds up incident resolution using real-time data
Publié: juin 17, 2015, 3:03pm CEST par Ian Barker
 Solving problems successfully is all about having the correct information for accurate diagnosis and then assembling the appropriate people to put things right. The problem is that the necessary knowledge is often spread across several areas of IT.
Solving problems successfully is all about having the correct information for accurate diagnosis and then assembling the appropriate people to put things right. The problem is that the necessary knowledge is often spread across several areas of IT.Operations performance management company PagerDuty is launching an extension to its platform called Rich Incidents aimed at reducing incident resolution times using real-time data.
Rich Incidents brings rich information from multiple sources together inside the notification, empowering operations teams to make the most of critical time. It has direct access to collaboration tools -- such as Slack, HipChat and Google Hangouts -- so teams are also able to connect with the right people faster.
"Rich Incidents delivers an important extension to PagerDuty’s incident lifecycle capabilities by providing our customers the right information they need to solve problems quickly," says PagerDuty CTO and Co-Founder, Andrew Miklas. "We are committed to delivering operations, IT and engineering professionals with the resources they need to protect uptime, and we’re hearing from customers that Rich Incidents help reduce resolution time to do just that".
The software provides more contextually relevant information about each incident along with relevant historical detail and graphs that increase incident understanding. It also offers links to help IT staff find relevant information that connects all the important resolution elements, has direct connection to conference bridges, chat rooms or runbooks, along with the ability to display custom graphs based on specific needs.
Rich Incidents is available now for all existing PagerDuty customers. More details are available on the company's blog.
Image Credit: lucadp / Shutterstock
-

New analytics platform unlocks the value of unstructured information
Publié: juin 17, 2015, 2:14pm CEST par Ian Barker

Modern businesses invariably have access to lots of data, but deriving simple straightforward insights from that can be difficult, especially if it's stored across multiple applications or extracted from the web.
SaaS analytics provider FirstRain is unveiling a new analytics platform that lets enterprise customers deliver business-critical and actionable insights to departments, teams and individuals.
FirstRain Orion adds new families of business analytics and the ability to integrate and analyze internal company data with information from the web and social media. It integrates into any enterprise or commercial platform and gives FirstRain's customers access to disruptive analytics that drive smart business decisions.
"We are delighted to bring the new FirstRain Orion architecture to our Fortune 1000 enterprise customers," says Penny Herscher, FirstRain president and CEO. "The seamless integration of critical and personalized customer and market insights into their enterprise-wide solutions and mobile-first initiatives will help them grow revenue by dramatically improving the speed and quality of the employee’s daily business decisions".
Among Orion's features are the ability to add new families of business analytics, such as marketing campaign enrichment, diverse fact extraction, opportunity and business risk triggers and financial risk analyses to create concise real-time business insights, and enable executives, sales, marketing and finance professionals to make higher quality decisions. Information is presented in a clear, graphical style.
It can build high precision business data analytics from a broad range of content and deliver it together into one user experience. Insights can be automatically personalized and configured for each user, team or for enterprise-wide initiatives.
Integrating into the client's business workflows and existing platforms is straightforward and Orion can incorporate both external unstructured data -- from the web for example -- and internally created unstructured business data. It's designed to work on smartphones and tablets and can be rapidly deployed through web service APIs.
For more information and to request a demo you can pay a visit to the FirstRain website.
Photo Credit: Sergey Nivens / Shutterstock
-

US consumers receive over 86 million scam phone calls per month
Publié: juin 17, 2015, 12:25pm CEST par Ian Barker

You might think that today's scammers spend most of their effort on the Internet, but a new report by call center authentication specialist Pindrop Security reveals that phone fraud is still big business.
More than 86.2 million calls per month to US consumers are down to scammers, and 36 million of those calls can be traced to one of the 25 most common phone scams. It also finds a 30 percent rise in enterprise attacks.
Financial and retail institutions have seen an increase in phone fraud of more than 30 percent since 2013, with one in every 2,200 calls being fraudulent. This rate increases for retailers that sell popular, expensive products with a high resell rate. The report also indicates that credit card issuers are getting the highest rate of fraud attempts, with one in every 900 calls being fraudulent. The report attributes this to cards being one of the most common ways for the public to complete transactions, and thus card numbers being at greater risk of theft.
Attackers have also been quick to embrace technology, using VoIP lines for 53 percent of their calls, compared to 7.8 percent of the general public using VoIP as a means for phone communication. Robot dialers are common too with 1 in 6 numbers calling consumers using auto-dialers. Fraudsters are also using spoofing to manipulate their caller IDs to mimic legitimate organizations.
"These attackers are sophisticated, using a variety of tactics, including automation, working in criminal rings and using both the phone and cyber channel to make tracking their actions more difficult," says Matt Garland, vice president of research and head of Pindrop Security’s newly formed Pindrop Labs team, which analyzed the data behind the report. "As major data breaches such as Anthem and Target have occurred, attackers have found the phone channel to be the vulnerable underbelly for corporations and consumers, allowing them to monetize the breaches through social engineering and account takeovers".
This isn't just a US problem, however, rates of phone fraud are similar across all economically developed countries, regardless of security regulations and legislation in place. Fraudsters rely on casting a wide net and catching people who aren't informed about the latest scams. Phone fraud rates are lower in developing countries and when it does occur it tends to be local in origin.
Pindrop expects the shift to chip and pin cards in the US to make attackers shift more attention to the phone as it's traditionally the least protected of the card-not-present channels. It advises call centers to begin preparing now for an increase in attacks.
The full report is available to download from the Pindrop Security website.
Photo Credit: Ana de Sousa/Shutterstock
-

Most employees are satisfied with the service they get from IT departments
Publié: juin 16, 2015, 4:26pm CEST par Ian Barker

Enterprise IT specialist LANDESK has released the results of a poll into end users' experiences with their IT departments.
The study polled more than 2,500 employees at organizations of various sizes worldwide, when asked to rate satisfaction with their IT department on a letter scale, 80 percent gave an A or B rating.
It also finds that 81 percent of respondents attempt to solve their own IT issues before asking for help. This follows the trend of increased self-sufficiency and autonomy in end users and indicates that users are becoming more resourceful.
"The results of this survey validate exactly what we already believed at LANDESK -- IT departments are doing increasingly better work and end users are more empowered to solve issues on their own," says Steve Daly, CEO of LANDESK. "This shift gives IT teams more time to focus on solving the more vexing IT issues they’re faced with each day".
Other findings are that IT departments are generally quick to respond to requests for help, with 88 percent of respondents reporting that IT generally resolved their issues in less than 24 hours and 28 percent seeing results within the first hour.
However, users now expect answers in real-time and are increasingly taking matters into their own hands. With proactive super users and responsive IT departments, it's perhaps no surprise that most IT issues don't significantly cut into productivity. In fact, 46 percent of respondents reported losing less than an hour of work per month and 80 percent reported losing less than three hours work per month.
When asked about subjects related to personally-owned devices in the workplace, the survey showed that most end users (75 percent) use at least one personally-owned device for work purposes, but only 23 percent of respondents reported their businesses have a bring-your-own-device (BYOD) policy.
"We are pleased with the results of this survey and what it means for IT departments around the world," says Daly. "For example, the findings from this study support our belief that with all the mobile devices employees are using to get their work done, organizations may need to implement or improve BYOD policies and mobile security practices within their companies".
The full report is available to download from the LANDESK website.
Image Credit: wavebreakmedia / Shutterstock
-

Datto launches new solutions to protect data wherever it's stored
Publié: juin 16, 2015, 4:18pm CEST par Ian Barker

With distributed networks, virtual servers and the cloud, corporate data is increasingly stored in lots of different places, making backup and business continuity more of a challenge.
Following its acquisition of Backupify in December last year, backup and recovery specialist Datto is launching a range of new products and enhancements designed to protect data no matter where it resides -- across on-premise physical or virtual servers or in the cloud via SaaS applications.
Announced at Datto's partner conference in New Orleans, the new products and features are part of Datto's Total Data Protection platform, which includes physical and virtual appliances, software and Datto's more than 140-petabyte private cloud.
The new announcements include a Datto DNA Router, offering remote configuration and 4G failover designed to meet the specific needs of MSPs and to protect data in transit. While traditional routers are susceptible to downtime and can be challenging to manage remotely, the Datto DNA router can be easily configured from the cloud -- reducing the need for onsite visits, decreasing downtime and providing a better experience for end users.
Datto Backupify for Office 365 brings automated, secure backup for data stored in Office 365. Datto partners supporting Microsoft Office 365 will be able to offer superior cloud-to-cloud backup protection for their users, ensuring that customers experience zero data loss from human errors, malicious deletions, hackers or viruses. It joins existing Backupify products for Google Apps, Salesforce and other SaaS applications.
Datto has recently partnered with ownCloud to offer secure file sync and share capabilities on all new and existing Datto SIRIS 1 and Datto SIRIS 2 devices. There's also a new Datto Linux Agent to deliver business continuity to Linux-based environments. MSPs working with Datto can use their existing Datto devices to extend protection to Linux.
An updated Datto Partner Portal will give MSPs a single place to manage their entire collection of Datto devices and services, it's expected to be available this fall.
"We're making the technology investments today to help our partners deliver end-to-end data protection that makes them even more successful tomorrow," says Austin McChord, Datto founder and CEO. "The DNA Router, Datto Backupify for Office 365 and other new product features and functionality provide more value than ever before for our partners, so they can guarantee protection for their customers’ data whether it is on-premise, in a SaaS application or in the cloud".
More information on all of these products is available via the Datto website.
Photo Credit: Andy Harbin/Shutterstock
-

Xirrus simplifies Wi-Fi access for BYOD
Publié: juin 16, 2015, 2:53pm CEST par Ian Barker

According to Gartner 85 percent of enterprises expect to have policies for allowing employee-owned devices in the workplace by 2020. This gives administrators a growing challenge in securing, supporting and managing them.
High-performance wireless specialist Xirrus is launching a new service suite called EasyPass, designed to manage mobile device connections to Wi-Fi networks in the simplest way and with minimal IT involvement.
"Users expect to connect anywhere, anytime without waiting. It's no longer enough to simply provide Wi-Fi -- today, connecting must be fast, easy and secure," says Bruce Miller, vice president of product marketing at Xirrus. "EasyPass addresses the pain points IT departments face due to the growing number of disparate devices on their Wi-Fi networks. Xirrus is the only Wi-Fi vendor to provide secure, device-independent Wi-Fi access with the simplest way to connect".
The EasyPass suite is made up of three modules. EasyPass Onboarding provides device-independent secure access for known users such as employees or students and ensures each user's connection is individually secured, eliminating the shared keys used on many Wi-Fi networks that expose them to compromise.
EasyPass Guest allows users to self-register without any IT assistance, and delivers fast and easy Wi-Fi access for anyone that wants to connect from anywhere, on any device. Finally EasyPass Voucher allows guest access using pre-created voucher codes to give greater control over who receives Wi-Fi access and for what duration.
"In higher education, students are accessing the Internet on more and more devices," says Tim Carlyle, director of network computing of Northwest Missouri State University. "Not only does this create a strain on our networks, it is also incredibly difficult and time consuming to manage. Xirrus; XMS-Cloud paired with EasyPass provides us with the easiest solution for controlling devices on our Wi-Fi network while simultaneously allowing our administrators and students to connect their devices easily and securely".
EasyPass is available from today and you can find out more and sign up for a free trial on the Xirrus website.
Photo credit: baranq/Shutterstock
-

Database vendor brings accessible cloud analytics to the US
Publié: juin 16, 2015, 12:34pm CEST par Ian Barker

As data volumes grow managing them and being able to extract meaningful insights in a timely manner becomes more and more difficult, especially for small and medium businesses.
Latvian database-as-a-service (DBaaS) company Clusterpoint is looking to expand its innovative technology to developers and small to medium sized businesses in North America by opening a new server cluster in Dallas.
"Our mission is to accelerate computing and the database plays a very central role in computing infrastructure today," says Zigmars Raascevskis, CEO of Clusterpoint. "Developers who are maintaining their own databases today face two major obstacles because of hardware: fixed capacity and speed limitations. This is why we have built a cloud-based database service. In the cloud, the developer's database request can be distributed among hundreds of servers in parallel, significantly reducing clock time to get a result".
Clusterpoint 3.0 is a cloud-based NoSQL database that allows developers to scale instantly regardless of data volume. They also have access to massive distributed computing power in the form of a cloud-based database, and benefit from a unique pricing model that is appealing to individual developers and those at SMBs. Clusterpoint 3.0 offers a true pay-per-use model rather than the tiered pricing model of today’s traditional DBAAS offerings.
Clusterpoint's cloud-based DBaaS model allocates resources based on need and these are accounted per request on the millisecond level. This results in cost benefits that can be three or even 10 times better than traditional pricing models, and with no hardware provisioning required.
With a server cluster already operating in Europe, Clusterpoint's first major investment in the US demonstrates its commitment to the marketplace. More information is available on the company's website.
Photo credit: LilKar/Shutterstock
-

Benchmarking engine helps unlock commercial insights
Publié: juin 16, 2015, 11:33am CEST par Ian Barker

Traditionally benchmarking organizations or parts of an enterprise against each other has been a complex process involving a team of specialist analysts. But the amount of data available to modern businesses means that they're increasingly looking for ways to automate gaining insights information.
Pittsburgh-based OnlyBoth is launching a new commercial benchmarking engine based on artificial intelligence principles. It enables business-services providers to offer comprehensive, automated benchmarking services to their end customers.
It's designed to answer fundamental business questions like, how are we doing? Where could we improve? And which similar peers do best? The clever bit is that it delivers results in English rather than just as numbers.
"Benchmarking is laudable, worthwhile, and widespread, but it has been handicapped by a lack of software automation and easily-available data," says Raul Valdes-Perez, CEO of OnlyBoth. "We envision a new world of universal business betterment made possible by automated benchmarking engines. Combining novel and unique technologies, OnlyBoth takes benchmarking to new playing fields where it delivers actionable paragraphs that drive real business value".
The artificial intelligence technology used was first developed in the late 1990s at Carnegie Mellon University through a National Science Foundation research grant to Valdes-Perez, but then set aside for 12 years while the founders grew a previous startup, eventually acquired by IBM and incorporated into the Watson platform. OnlyBoth combines machine discovery -- algorithms that discover humanly-digestible knowledge -- with natural language generation, which makes the resulting knowledge easy to read and share.
More information and the opportunity to try out the benchmarking for yourself using public hospital data is available on the OnlyBoth website.
Photo Credit: amasterphotographer/Shutterstock
-

The problems facing chief information officers
Publié: juin 15, 2015, 1:16pm CEST par Ian Barker

With technologies like cloud systems and big data increasingly in demand the role of the chief information officer (CIO) is evolving and throwing up new problems all the time.
Enterprise search company Lucidworks has produced an infographic looking at the changes most affecting CIOs and what can be done to embrace them.
Big data is the major challenge with 67 percent of Fortune 1,000 companies already having initiatives in production and only four percent with no big data projects planned at all. 91 percent of CIOs feel that the move to big data has made their role more important whilst 85 percent say they've become more important to the business as a result.
Investment in big data is up too with 74 percent of companies expecting to spend more than $10 million by 2017. The growth of big data has also led to many more companies appointing chief data officers. Only 19 percent of Fortune 1,000 companies had a CDO in 2012, this is up to 43 percent in 2014.
The top challenges for CIOs are identified as security, downtime and staffing. Skills shortages are affecting many of the key areas including big data, business intelligence and security.
More information including recommendations to help CIOs adapt to the challenges they face is in the full graphic below.
Image Credit: leedsn/Shutterstock
-

Five into one will go -- ARCTIC Smart Charger 8000 [Review]
Publié: juin 15, 2015, 11:29am CEST par Ian Barker

Most of today's gadgets seem to use USB for charging their batteries so you inevitably end up with a whole stack of cables and the mains power adapters to go with them.
If you're looking to simplify things the Smart Charger 8000 from Swiss company ARCTIC may be the solution. It's a little box with five USB ports that allows you to charge a number of devices at the same time. It intelligently detects the devices connected to it in order to provide the best charging speed for each one.
The unit is compact with edges in a gray soft-touch rubber material, the top is hard black plastic with a subtle gray pattern, and rubber feet on the bottom stop it from sliding around. It comes with a one metre long mains lead so you can comfortably stand it on a desk or a bedside table.
Switch it on and a yellow LED on the top tells you it's active. This same LED will flash to tell you if you've reached the 10 amp current protection limit. The makers say it's up to 86 percent efficient so minimal energy is wasted generating heat.
On test it coped with an Android smartphone, a Kindle and an MP3 player all taking different times to charge. It does make a very slight whining noise when it's working but unless you put your ear next to it you won't notice it other than in a very quiet environment.
The Smart Charger 8000 is a handy gadget for organising all of your charging in one place. It's a neat, unobtrusive design and coped well with all of the USB devices we tried on it. It costs $23.99 on Amazon or £18.99 on Amazon.co.uk. More information is available on the ARCTIC website.
-

New marketing tool allows email to be personalized right up to it being opened
Publié: juin 12, 2015, 1:08pm CEST par Ian Barker

Most marketers are focused on providing a personalized experience for the customer. However, many still rely on email communication. Whilst this is still an effective delivery method there’s an inevitable time lag in the message arriving by which time it could be out of date.
That delay may be a thing of the past as eCommerce specialist Reflektion is launching Right Time Messaging. This has the ability to hyper personalize emails to individual recipients right up to the moment the message is opened.
Reflektion's 1 to 1 search and product merchandising products have already enabled retailers and brands to convert large numbers of website visitors into customers. The Right Time Messaging solution is focused on reactivating customers by injecting real-time, 1 to 1 content into triggered and promotional emails, selecting the most relevant products and promotions for each individual.
"Email can be the most powerful and efficient reactivation tool for marketers. But the batch and blast technique still in use is often not effective with today’s digital consumer," says Sean Moran, CEO of Reflektion. "With the ability to deliver relevant products and promotional messages to individuals based on their shopping behavior up to the time they open the email, marketers can breathe new life into their brand’s email strategy by dramatically improving results".
It can offer products targeted to each individual recipient's preferences. Reflektion clients generate emails that feature a direct link to products, which cuts the number of clicks needed to get to the sales page across all devices and reduces shopper frustration and abandonment.
More information on Right Time Messaging is available on the Reflektion website.
Photo credit: Pavel Ignatov/ Shutterstock
-

100 percent cloud is closer than you think
Publié: juin 11, 2015, 5:30pm CEST par Ian Barker

Cloud management specialist BetterCloud has released the results of its latest survey into the pace of cloud adoption in businesses.
The survey of 1,500 IT professionals from 53 countries also looks at the differences in cloud office systems and their customers, the current and expected usage rates for cloud applications, and the effects of cloud office systems on productivity, collaboration, cost savings and more.
The key finding is that by 2020, 62 percent of all organizations surveyed expect to be running 100 percent of their IT in the cloud. Currently, 12 percent of organizations surveyed run all of their IT in the cloud. By 2017, more than a quarter expect to be doing so. However, 27 percent of respondents believe that their organizations will never go 100 percent cloud.
As businesses look to replace legacy applications they increasingly turn to the cloud. In 2015, enterprise organizations are running an average of 18 cloud applications, by 2017, that number is expected to nearly triple to 52.
Google shops are going all-in on the cloud at a much faster pace than Microsoft-based companies. 66 percent of Google Apps customers who took the survey expect to run all their IT in the cloud by 2020, against only 49 percent of Office 365 customers.
One of the strongest indicators of cloud adoption is the age of the organization itself. The majority (66 percent) of organizations five years old or younger expect to run 100 percent of IT operations through the cloud by 2017. Only nine percent of organizations 21 years or older expect to be running fully in the cloud by then. It's clear that the cloud offers an advantage to businesses that aren't tied to legacy systems. The age of the workforce is an important factor too. Younger workforces tend to consist entirely of digital natives who have grown up working in the cloud.
"We are at the beginning of the biggest shift in IT in more than 20 years. The growing use of cloud office systems and the increasing reliance on cloud applications is driving us to a tipping point -- an entirely new way of working," says BetterCloud CEO David Politis. "Cloud office systems are the foundation of the transition to the cloud, serving as the gateway to overall cloud adoption. Running 100 percent of IT in the cloud was unthinkable only a few years ago, but as our data shows, in less than 10 years it will be the norm".
You can find out more about the results on the BetterCloud blog.
Photo Credit: RPeshkova/Shutterstock
-

Windows 10 in the enterprise? Not for six months, thanks
Publié: juin 11, 2015, 3:16pm CEST par Ian Barker

According to a new survey from Microsoft System Center specialist Adaptiva, 71 percent of IT leaders plan on waiting six months or more before deploying Windows 10.
In the survey, conducted at Microsoft Ignite 2015, 49 percent said they planned to wait a year or more before updating. Of larger companies 80 percent of those with over 100,000 nodes said they are planning to adopt in a year or more.
Only 11 percent of all respondents' organizations are still running Windows XP. This is down from 53 percent last year in a similar survey Adaptiva conducted at TechEd 2014, indicating that XP is well on the way out in the corporate world.
The biggest barriers to upgrading to Windows 10 were given as application compatibility and time investment (98 percent), followed by user training (35 percent), and product maturity (23 percent). A majority (54 percent) say the cloud has no impact on their ability to upgrade and patch applications or migrate operating systems. However, 40 percent claim the cloud is actually making it harder for them to perform these basic systems management tasks, up from just seven percent who felt that way in 2014.
Other findings are that the vast majority of respondents were running Windows 7 (89 percent) and/or Windows 8 (57 percent). Of those at organizations with more than 10,000 nodes, 99 percent are running Configuration Manager in their enterprise and 62 percent plan to use it to deploy Windows 10.
To move to the new OS, nearly three-quarters (73 percent) of large organizations plan to use side-by-side replacements -- deploying new computers with Windows 10. This compares to 36 percent who plan to perform in-place upgrades to existing hardware.
More information on the survey and on how Adaptiva's OneSite 5.0 can make migration to Windows 10 easier is available on the company's blog.
Image Credit: iQconcept / Shutterstock
-

Ecommerce traffic being hijacked by client side malware
Publié: juin 11, 2015, 11:30am CEST par Ian Barker

According to new research 15 to 30 percent of eCommerce site visitors are infected with Client Side Injected Malware (CSIM) that causes them to view injected ads, malicious links and fraudulent spyware on otherwise legitimate sites.
These findings are from a study by online security company Namogoo which shows that CSIM has grown rapidly in the past two years and is able to operate completely undetected by site publishers because it lives locally on consumers' systems.
Consumers may unknowingly download CSIM via bundled apps or extensions and most commonly experience injected ads -- fake advertisements that look native to an authentic site, but actually lead consumers away from the website to make their final purchases elsewhere.
Namogoo has already identified over 25,000 ad injector signatures, with an average of 200 new signatures appearing daily. It says that injected ads made up an estimated $7 billion market in 2014, and the culprits behind the industry can range from lone developers in emerging markets to large public companies operating in the gray area of the law while siphoning off millions in eCommerce traffic and revenue from unsuspecting brands.
"We even see anti-virus companies using their software to secretly infect consumers with CSIM. It's a startling but unfortunate truth," says Namogoo co-founder and CEO Chemi Katz. "Because it's an easy way to make a buck, struggling anti-virus companies have given in to the dubious practice in order to stay alive, although we think it's quickly becoming evident in the eyes of the public".
In the past six months Namogoo has seen client-side attacks increase by 20 percent, a sign that the CSIM industry is becoming more aggressive. In some markets, including travel and luxury goods, it has found an especially concerted effort by malware developers as consumers are not only more likely to click on an injected ad, but ultimately make larger purchases.
The company has developed a new technology that allows eCommerce sites to combat CSIM by suppressing all active CSIM on a consumer's computer or browser when that consumer visits a Namogoo-protected site. Its servers scan millions of pages creating malware injection blocking rule sets in real-time and delivering them to the website via a single line of code, so site publishers can control the user experience, down to the individual computer.
A white paper looking in more detail at CSIM and at how Namogoo can combat it is available as a PDF from the company's website.
Photo Credit Konstantinos Kokkinis/Shutterstock
-

Microsoft Surface Hub coming to a business near you soon
Publié: juin 10, 2015, 4:19pm CEST par Ian Barker

The promise of surface computing for businesses seems to have been around for ages, remember all those cool videos of interactive coffee tables and screens from around three years ago? Yet so far there hasn't been a great deal of practical application.
That could be about to change as Microsoft makes its Surface Hub available for businesses to order in 24 markets -- including Australia, North America, Japan, the Netherlands, Singapore, and the UK -- from July 1.
Surface hub will be available in two sizes, a 55-inch model for $6,999 and an 84-inch model for an eye-watering $19,999. The larger model has a 4k touch-screen display that refreshes faster than the human eye can detect -- every 8.33 milliseconds. On both sizes, Surface Hub supports 100 points of multitouch and up to three simultaneous pen inputs, has dual 1080p front-facing video cameras and a four-microphone array help ensure that those remotely joining Skype for Business meetings can see and hear the entire room.
Microsoft says it will offer the power and versatility of a complete, cloud-connected Windows 10 device along with the simplicity and consistency of a custom interface that's built for shared spaces. Surface Hub has built-in Wi-Fi, Bluetooth 4.0, NFC and a variety of ports for easy wired and wireless connectivity options
"While there are a number of devices designed to improve our productivity as individuals, there has yet to be a device that is truly optimized for a group of people to use together -- designed not just for what we need to do, but how we want to work. Until now," says Mike Angiulo, corporate vice president, Microsoft Devices. "Just as the PC revolutionized productivity for individuals, Surface Hub will transform the way groups of people work together".
Microsoft is working closely with a number of strategic partners to make it easy for businesses to deploy Surface Hub into their organizations in a way that naturally integrates into their existing rooms and IT environments.
The price means this is going to be the preserve of big corporations, but hopefully if it takes off it will become more accessible. To find out more you can pay a visit to the Surface Hub website or the Microsoft Surface Blog.
-

PandaDoc integrates with Zendesk to simplify customer service paperwork
Publié: juin 10, 2015, 3:02pm CEST par Ian Barker

One of the problems with business software is that it tends to exist in compartments when it would make life much easier for users if it all worked together.
Sales document creation specialist PandaDoc is launching a new add-on to integrate its software with the Zendesk customer service platform.
"PandaDoc's heritage in enabling stronger, more results-driven document collaboration between sales and marketing teams makes us a natural partner for Zendesk. Through this integration, we’re now empowering customer service agents to do their jobs better by making traditionally mundane paperwork processes, like securing e-signatures, much simpler and faster," says Mikita Mikado, Co-Founder and CEO of PandaDoc.
Administering customer support documentation -- particularly securing electronic signatures -- from within Zendesk can be a challenge. Service agents may find themselves spending too much time switching between applications to send various document types, plus document-related details aren't connected back to Zendesk.
Using PandaDoc enables form fields to be automatically filled using previously supplied information, saving time and effort when Zendesk users are creating things like NDAs or contract renewals.
In addition, the PandaDoc integration means that documents and document-related information will now be part of the comprehensive information available to service agents. End-customers will also have the option to access these documents themselves, an important capability for outsourcing organizations offering branded self-service communities through Zendesk.
"PandaDoc greatly simplifies the paperwork tasks involved in customer service. This not only increases the efficiency of service agents, but also helps organizations maximize their Zendesk benefits including delivering greater customer convenience, building stronger relationships and generating more revenues," adds Mikado.
You can find out more about PandaDoc and sign up for a 14-day trial on the company's website.
Image Credit: HABRDA / Shutterstock
-

Four things businesses need to know about payment card compliance
Publié: juin 10, 2015, 11:28am CEST par Ian Barker

We reported last month that new security standards for the payment card industry, known as PCI DSS, were coming into force by the end of June.
Security company Rapid7 has produced an infographic looking at PCI compliance, cybersecurity and new related requirements for penetration testing. Based on data from the Verizon 2015 PCI Compliance Report it sets out four things enterprises should know about going into PCI compliance.
It shows that enterprises are getting better at PCI compliance, however, only one in five organizations were fully compliant at interim assessment. Vulnerability scanning remains a major challenge, PCI DSS Requirement 11 (regularly test security systems and processes) was the only area where compliance levels have fallen year-on-year.
It also points out that tracking and monitoring is critical, with every company that suffered a data breach being found non-compliant with PCI DSS Requirement 10 (track and monitor all access to networks and cardholder data). Finally starting on July 1, companies must comply with new, more stringent pen-testing requirements.
You can see the full infographic below.
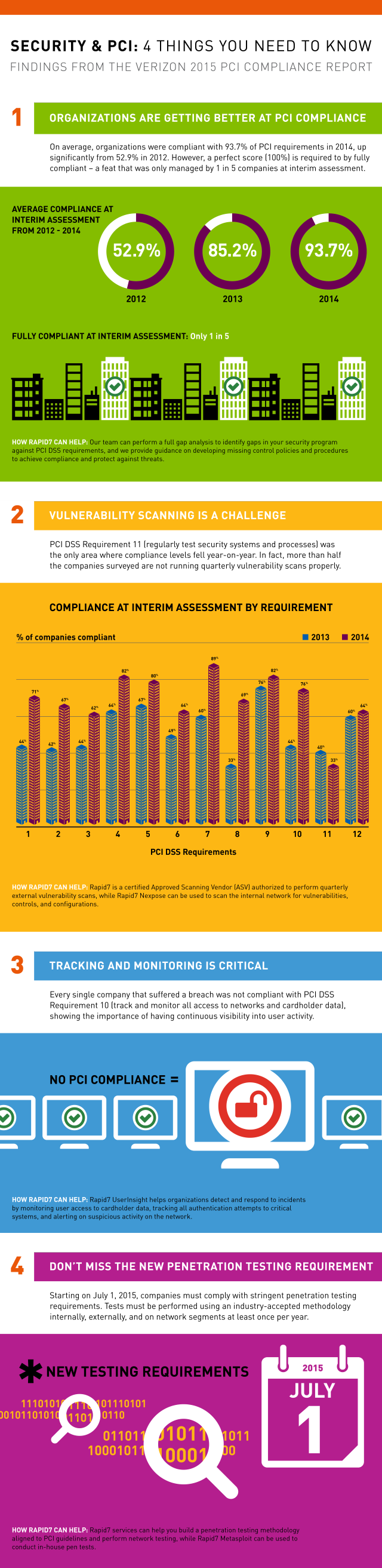
Image Credit: Sedlacek / Shutterstock
-

Ransomware sees 165 percent increase in 2015
Publié: juin 9, 2015, 4:51pm CEST par Ian Barker

The first quarter of this year saw a 165 percent increase in new ransomware driven largely by the new, hard-to-detect CTB-Locker ransomware family, a new ransomware family called Teslacrypt, and the emergence of new versions of CryptoWall, TorrentLocker and BandarChor.
This is the main finding of the latest McAfee Labs Threats Report released today by Intel Security. Among other highlights are a 317 percent increase in Adobe Flash malware samples and the emergence of new efforts to exploit hard drive and SSD firmware.
Part of the CTB-Locker ransomware's success is down to clever techniques for evading security software, higher-quality phishing emails, and an 'affiliate' program that offers accomplices a percentage of any ransom payments in return for flooding cyberspace with CTB-Locker phishing messages.
McAfee Labs suggests that organizations and individuals need to learn how to recognize phishing emails and has launched an online quiz to help develop your skills.
The rise of Flash malware is put down to the popularity of Adobe Flash as a technology, user delay in applying available patches, new methods to exploit product vulnerabilities, a steep increase in the number of mobile devices that can play Adobe Flash files (.swf) and the difficulty of detecting some Flash exploits. In the first quarter 42 new Adobe Flash vulnerabilities were submitted to the National Vulnerability Database though initial fixes were made available for all 42 on the same day they were posted.
"With the popularity of a product like Flash, there comes a tremendous responsibility to proactively identify and mitigate security issues potentially threatening millions of users," says Vincent Weafer, senior vice president, McAfee Labs. "This research nicely illustrates how the tech industry works together constructively to gain an advantage in the realm of cybersecurity -- industry partners sharing threat intelligence, and technology providers acting on information quickly to help prevent potential issues".
The HDD and SSD firmware issues were uncovered in February 2015 when the cybersecurity community became aware of efforts by a secretive outfit called Equation Group. McAfee Labs has analyzed modules that could be used to reprogram the firmware in SSDs in addition to previously-reported HDD reprogramming capability. Once reprogrammed, the firmware can reload associated malware each time infected systems boot and the malware persists even if the drives are reformatted or the operating system is reinstalled. Once infected, security software can't detect the associated malware which is stored in a hidden area of the drive.
Other findings are a slight decline in PC malware growth but a jump in mobile malware samples of 49 percent. SSL attacks have continued too although they're down on the levels reported in the last quarter of 2014.
There's more detailed information in the full report which is available as a PDF on the McAfee Labs website.
Image Credit: Robynrg/Shutterstock
-

Cisco announces new embedded security solutions
Publié: juin 9, 2015, 3:55pm CEST par Ian Barker

Networking specialist Cisco is announcing new products to provide embedded enterprise security from the data center out to endpoints, branch offices and the cloud.
The company used this week's Cisco Live conference to announce that it's adding more sensors to increase visibility; more control points to strengthen enforcement; and pervasive, advanced threat protection to reduce time-to-detection and time-to-response, limiting the impact of attacks.
Cisco expects the Internet of Everything (IoE) to be worth $19 trillion over the next decade while the cybercrime sector could be worth up to $1 trillion.
Cisco's solutions include endpoint protection using its AnyConnect 4.1 VPN client which allows customers to easily deploy and significantly expand their threat protection to VPN-enabled endpoints to continuously and retrospectively guard against advanced malware.
Branch office protection is provided by FirePOWER Services solutions for Cisco Integrated Services Routers (ISR), offering centrally managed Next-Generation Intrusion Prevention System (NGIPS) and Advanced Malware Protection (AMP) where a dedicated security appliance may not be feasible.
Cisco will also add embedded multiple security technologies into the network infrastructure to provide broad threat visibility, to identify users and devices associated with anomalies, threats and misuse of networks and applications.
It's integrated StealthWatch with its Identity Services Engine to spot and block suspicious network devices and added NetFlow monitoring to offer greater insights into network traffic.
"To protect against today's threats and increase agility for organizations to seize new growth opportunities and implement new technologies, security must be pervasively embedded across the entire network infrastructure," says David Goeckeler, Senior Vice President and General Manager of Cisco's Security Business Group. "By integrating 'Security Everywhere' throughout the extended network and through cloud-delivered services, Cisco is protecting a wider array of attack vectors. This also provides enterprises and service providers with the confidence that they have the continuous and retrospective visibility and control to support new technologies and business opportunities in the Internet of Everything and the Digital Economy".
You can find out more about Cisco's ability to secure extended networks on the company's blog.
Image Credit: Katherine Welles / Shutterstock
-

Mid-sized businesses are underusing their IT management
Publié: juin 9, 2015, 1:36pm CEST par Ian Barker

In 89 percent of mid-sized companies IT management focuses on day-to-day tasks that are often time-consuming and manual which means that business isn't getting the most from its IT investment.
This is one of the main findings of a survey by cloud-based IT management provider Kaseya which looked at 500 mid-sized enterprises globally and compares the practices of IT departments in faster growth companies with those in slower growth companies, and the practices of more mature IT organizations with those of less mature ones.
The 11 percent of companies that have achieved higher levels of maturity are reaping benefits in important ways for their businesses. The survey findings suggest IT groups can do more to drive the effectiveness of both IT and the business by better utilizing the limited resources they have. Results indicate that by using automation more for both routine tasks and problem avoidance, and by fully embracing cloud technologies, IT groups can spend more of their time on strategic projects that contribute to end-user productivity and drive the success of the business overall.
"Most IT groups in mid-sized companies find that they don't have enough time to invest in strategic projects," says Loren Jarrett, chief marketing officer for Kaseya. "Our survey results suggest that by adopting the practices of mature IT organizations, including automating IT management activities, standardizing and streamlining processes, and leveraging cloud services, IT groups at companies of all sizes can free up more time and resources to focus on projects that will drive results for the business".
Other findings include that there's no correlation between the size of a company and its IT management maturity level, indicating that companies of all sizes can benefit from investments in maturing their IT operations. For companies who grew their revenue at greater than 10 percent between 2013 and 2014, 36 percent were considered to have reached the highest maturity levels, against 11 percent for all companies in the study.
Two-thirds of companies at the highest IT management maturity levels have formal service level agreements (SLAs). For more than half of these meeting their SLAs is mandatory. IT organizations at the highest levels of maturity are also almost twice as likely to report that they drive IT decisions, instead of their CEO or CFO.
The full report is available to download from the Kaseya website.
Image Credit: alphaspirit / Shutterstock
-

New isolation technology seeks to eliminate malware threats
Publié: juin 8, 2015, 1:17pm CEST par Ian Barker

According to Gartner, businesses spent more than $70 billion on cyber security tools in 2014, and collectively lost nearly $400 billion as a result of cyber crime. This suggests that existing security technologies are struggling to cope with the growing number of cyber threats.
Californian company Menlo Security is launching an new approach which it calls Isolation Platform, a technology that claims to eliminates the threat of malware from key attack vectors, including web and email.
Built by a team of industry experts in security, cloud and virtualization, alongside academics from the University of California, Berkeley, the Menlo Security Isolation Platform requires no endpoint software and can be deployed to eliminate the threat of malware from web traffic, web-based documents and email.
"Organizations and individuals should be able to interact online without the fear of being compromised," says Amir Ben-Efraim, co-founder and CEO of Menlo Security. "By focusing on ease of deployment and a seamless user experience, the team at Menlo Security has reinvented isolation as a highly usable and scalable front line of defense against malware".
Instead of trying to distinguish legitimate content from malware, what the Menlo Security Isolation Platform does is to isolate and execute all web content in the cloud and away from the endpoint. The solution uses patent-pending, clientless rendering technology called Adaptive Clientless Rendering (ACR), to deliver a non-executable, malware-free copy of the user's session to their native browser, creating a transparent user experience that is 100 percent safe.
Menlo Security Isolation Platform is available now as a public cloud-based service or as a virtual appliance for on-premise deployment. The Platform needs no software on the endpoint and is compatible with any hardware, any OS and any browser. More information can be found on the company's website.
Image Credit: Aleks vF / Shutterstock
-

LYCOS wants to change your life with wearables
Publié: juin 5, 2015, 1:51pm CEST par Ian Barker

Remember LYCOS? Before Google came along it was one of the leaders in the search engine market. It's since tried to reinvent itself as a digital portal in the style of Yahoo or MSN but, be honest, when was the last time you visited its site?
The company is now making a renewed bid for attention with its entry into the wearables market. On June 8 the company is launching a range of devices that will, it says, "serve as a single point of entry into users' digital lives".
There will be two products initially, a wristband called Life Band that includes a fitness monitor and personal security manager, and more intriguing a Life Ring that puts a security manager and Tap to Transfer feature on your finger.
"The most valuable commodity in life is time and this technology helps LYCOS Life users maximize their time by making smarter and more informed decisions using the data they receive from LYCOS Life," says Brad Cohen, president and chief strategy officer of LYCOS.
LYCOS Life will intelligently sense individuals' everyday patterns and transfer this information securely and wirelessly to a smartphone via Bluetooth and its Tap to Transfer (T2T) communication protocol. The wearable devices will allow users to automatically monitor their activity, sleep, heart rate, incoming calls, and important notifications from their phone completely hands-free.
The company says that LYCOS Life will soon be able to uniquely identify its wearer by using onboard sensors to recognize its user simply by the way they move. It has developed software that can learn who you are, what you prefer, and what you do based on your own patterns and behaviors.
Features of the Life range include a Personal Security Manager that securely and seamlessly logs in to favorite apps and websites on a phone, unlocking them without the use of passwords. T2T capability lets users securely give a new friend their number, clients a business card, or instantly share an address to launch directions to a restaurant. The LYCOS Life activity tracker allows users to monitor steps, calories burned, speed and heart rate.
There doesn't seem to be anything especially innovative in any of these functions, though the ring idea looks attractive from a convenience point of view.
The wristband will cost $124.99 and the ring $59.99 more information will be available on the LYCOS Life website from Monday.
-

Millions of US government workers’ records exposed by data breach
Publié: juin 5, 2015, 11:51am CEST par Ian Barker

The US government has been hit by a massive data breach at the department which handles government employee records, the Office of Personnel Management (OPM). According to officials this has the potential to affect every federal agency.
The Reuters news agency says that it's been told by a US law enforcement source that a "foreign entity or government" was believed to be behind the attack. Suspicion has fallen on China although Chinese foreign ministry spokesman Hong Lei said the accusations were, "irresponsible and unscientific".
The OPM acts as the human resource department for the federal government. The agency is responsible for issuing security clearances, conducting 90 percent of background checks, and for holding records of federal employees. Information held on OPM databases covers employee job assignments, performance reviews and training.
"The FBI is conducting an investigation to identify how and why this occurred," the department of homeland security said in a statement on Thursday. "DHS is continuing to monitor federal networks for any suspicious activity and is working aggressively with the affected agencies to conduct investigative analysis to assess the extent of this alleged intrusion".
According to the OPM's official announcement it first became aware of the incident in April of this year.
The OPM says that as a result of the incident it will begin sending out notifications to around four million individuals starting on Monday. In order to guard against the risk of fraud and ID theft it says it will be, "...offering affected individuals credit monitoring services and identity theft insurance with CSID, a company that specializes in identity theft protection and fraud resolution". This protection will be free for 18 months.
Photo credit: solomonjee / Shutterstock
-

70 percent of consumers lack confidence in passwords
Publié: juin 4, 2015, 4:50pm CEST par Ian Barker

When we regularly hear stories of personal details being stolen through data breaches and hacks, it's not surprising that people are losing faith in the ability of passwords to protect them.
A new report from mobile ID provider TeleSign reveals that 70 percent of consumers lack confidence that their passwords can adequately protect their online accounts. In addition, about the same amount (72 percent) are in search of additional means to secure accounts.
Commissioned by TeleSign and conducted by Lawless Research, the survey polled 2,000 consumers in the US and the UK and reveals that while concerns around online security and password strength persist, 'password fatigue' among consumers is widespread.
Not changing passwords is common, 21 percent of consumers use passwords that are over 10 years old, pre-dating the launch of Twitter, YouTube and many online banking services. Almost half (47 percent) rely on a password that hasn't been changed for five years. Password reuse is widespread too with 73 percent of online accounts using duplicated passwords and an average of just six unique passwords being used to protect 24 online accounts. This trend leaves people vulnerable to the 'domino effect' where a hacker compromises a user's password for one service and can then access all of their accounts.
On a positive note the findings show that consumers are eager to learn about online security. In fact, 72 percent would welcome advice on how they can better protect their online accounts. The majority (68 percent) would like companies to provide an extra layer of security to keep their online accounts safe. Yet in spite of this desire to learn and improve their online security, six out of 10 are still not making use of the stronger security that two-factor authentication can offer. The top reasons consumers give for not enabling 2FA are that they don't know how to set it up, don't know what it is or that companies simply don't offer it.
"The number one tip most experts give for increasing account security and stopping the fallout from data breaches is to turn on two-factor authentication," says Steve Jillings, CEO of TeleSign. "Yet our research shows that the majority of consumers (61 percent) do not know what two-factor authentication is, even though it's available on almost every account, free to the consumer and just waiting to be turned on".
In order to help with this confusion TeleSign is launching a Turn It On campaign offering guide to 2FA and providing step-by-step instructions for turning it on for popular social networking and other sites.
The full report is available to download on the TeleSign website and there's a summary of the findings in infographic format below.
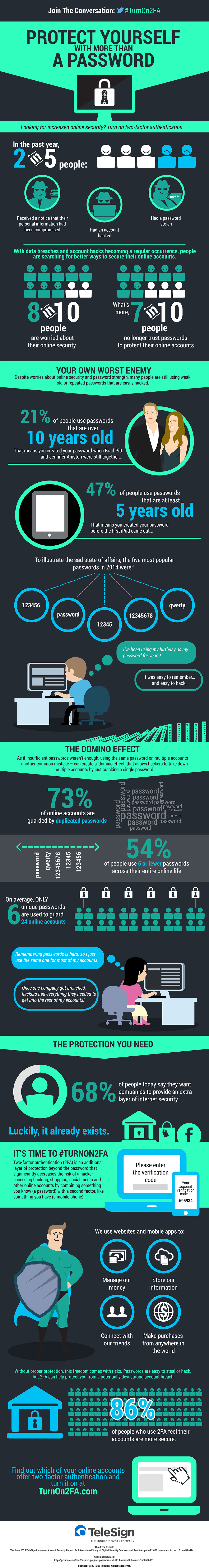
Photo Credit: JMiks/Shutterstock
-

BlueData adds support for Docker containers
Publié: juin 4, 2015, 4:09pm CEST par Ian Barker

Big data infrastructure specialist BlueData has announced that it's introducing support for Docker containers in its BlueData EPIC platform.
It will allow organizations to quickly and easily deploy Apache Hadoop or Apache Spark in a lightweight container environment making it simpler to deploy big data infrastructure.
"Container technology is disrupting the IT market, and Docker is seeing rapid enterprise adoption," says Kumar Sreekanti, co-founder and CEO of BlueData. "There are now thousands of applications running on Docker, but until today there were only a few applications supporting containers for Big Data analytics. Together with Docker, we're disrupting the Big Data market and leveraging the power of containers for enterprises deploying Hadoop and Spark on-premises".
Docker containers create new possibilities to streamline infrastructure deployment for big data analytics. By integrating the EPIC software platform with Docker, BlueData is providing the benefits of virtualization for big data applications, while delivering the simplicity of containers and the performance of bare-metal servers.
The BlueData EPIC software platform works with all major Hadoop distributions as well as Spark. It integrates with the leading analytical applications, so data scientists can use the tools they prefer. It runs with any shared storage environment too, eliminating the need to move data. It also delivers the agility of Hadoop-as-a-Service in an on-premises deployment model, whilst providing the enterprise-grade security and governance that IT teams require.
BlueData EPIC Lite is available today as a free edition With EPIC Lite, data scientists and developers can easily create multi-node Hadoop clusters or standalone Spark clusters running in Docker containers. The enterprise edition of BlueData EPIC will be available in the fall of this year.
Image Credit: Marynchenko Oleksandr / Shutterstock
-

MicroStrategy makes powerful business analytics more accessible
Publié: juin 4, 2015, 3:09pm CEST par Ian Barker

IT departments face increasing demands for self-service applications to enable users to manipulate data themselves, but this often conflicts with the needs of the enterprise.
Enterprise software provider MicroStrategy is addressing this with the launch of its latest software which combines self-service analytics and data visualization with enterprise-grade infrastructure.
MicroStrategy 10 contains a number of new and improved features including data discovery offering enhanced exploration and visualization capabilities on both Mac OS and Windows. Users can quickly prepare data for analysis without using other tools.
New governed data discovery makes it simple to make dashboards from the desktop available to the enterprise, providing a path from self-service analytics to enterprise BI. Native Hadoop access makes analyzing large volumes of multi-structured data easy. Better in-memory performance lets users put more data on parallel-partitioned in-memory cubes, so organizations can run faster queries across larger volumes of data.
A redesigned HTML5 interface makes self-service analytics faster, more intuitive, and easier to use, so users can quickly connect to any data and drag-and-drop their way to business insights. Admins can save time too with a new Operations Manager that enables them to manage and monitor all of their environments from a single interface.
MicroStrategy's security uses biometric and multi-factor authentication to lock down every method of analytics delivery, conveniently and seamlessly. It uses Usher Mobile to instantly deploy security badges that replace passwords and ID’s with a mobile app distributed to all employees, partners and customers.
"We currently rely on the MicroStrategy Analytics Platform to track programming investments, analyze ad and affiliate sales trends, and review sales team performance," says Madhur Sawhney, Sr. Director Data & Analytics Technology at Discovery Communications. "After testing MicroStrategy 10 as an early adopter, our team really likes the new functionality, in particular, the ability to easily wrangle and parse data as well as save/import wrangling scripts functionality. The enhanced data blending features and on-the-fly data manipulations made possible with version 10 and Visual Insight provide incredible speed-of-interactivity and ease of use".
You can find more about MicroStrategy 10 on the company's website and it will be presented in a symposium series over the coming months.
Image Credit: alphaspirit / Shutterstock
-

Bromium launches smoother endpoint protection for enterprises
Publié: juin 3, 2015, 6:27pm CEST par Ian Barker

Enterprise security teams are under increasing pressure to respond to threats from breaches as well as more traditional security threats.
To ease their workload threat isolation specialist Bromium is launching a new platform designed to speed deployment time and give security teams better management capabilities.
Bromium Enterprise Controller (BEC) is a scalable security management platform that delivers one-click deployment, policy control, monitoring and threat management for enterprise endpoint infrastructure.
"Endpoint threat isolation should be a core component of security prevention programs because of the challenge companies face due to increased threat volume," says Roland Cloutier, Chief Security Officer of Automatic Data Processing. "With hardware-enforced isolation and micro-virtualization technology in Bromium's solution, we have an ability to gain increased visibility into threats and act on those attempts in real-time to mitigate their disruption to our business and clients".
BEC automates the deployment and configuration of Bromium's existing vSentry and LAVA products allowing even large enterprises to efficiently control their enterprise security. Key features include fully autonomous installation and updates, simplified policy management, centralized monitoring and analysis, and integration with threat intelligence systems to streamline collaboration in the fight against cyber attacks.
Bromium's isolation and micro-virtualization technologies don't allow malware and malicious threats to access the network in the first place. Unknown tasks and malware are shifted into hardware-isolated micro-virtual machines before they can attack the endpoint.
Bromium Endpoint Controller is available from today and more information can be found on the company's website.
Photo Credit: Alexander Kirch/Shutterstock
-

Datameer launches regulatory tools for Hadoop
Publié: juin 3, 2015, 3:43pm CEST par Ian Barker

The popularity of big data has boosted demand for Hadoop systems. Yet data handling and analytic capabilities are often seen as the key features while governance and security get relegated to a support role.
In corporate environments though the governance side of things is important which is why big data specialist Datameer is launching new tools for maintaining data validity and manageability in the Hadoop ecosystem.
The enhanced offerings allow businesses to have complete transparency into their data by making it easier to navigate data pipelines while keeping information secure and encrypted. Features include access control and auditing to determine and track who has access to which data, who granted access to it and what changes have been made. Datameer access control also integrates with Apache Sentry 1.4.
In addition an impact analysis feature shows users who or what will be affected if a change is made at a particular stage in the data pipeline. Data lineage allows users to understand where analytics results originated and how they were used, modified or published to a downstream system, via either the UI or a REST (Representational State Transfer) API.
Datameer's open governance APIs and pluggable architecture enable other capabilities too including, metadata synchronization with external data management tools, as well as standards that are filtering into the broader Hadoop ecosystem like Cloudera Navigator and Hortonworks' Data Governance Initiative (DGI).
Version control and change management for data and metadata is available via API-based synchronization with both commercial and open source versioning systems. This allows for automated deployment of new changes and/or rolling back the Datameer environment to its previous state if required.
"Hadoop has been seen as the Wild West in which vendors have been developing different products for the ecosystem without really thinking about data governance and sophisticated security protocols," says Stefan Groschupf, CEO of Datameer. "Data security is imperative to providing an enterprise-grade product for our customers and to driving Hadoop adoption and success overall. With these new features we're driving home the point that we're serious about helping enterprises transform their business into data-driven organizations".
More information is available on the Datameer website where you can also register for a Data Governance Webinar to be held on June 23.
Image Credit: Tashatuvango / Shutterstock
-

Boosting website visibility for small businesses
Publié: juin 3, 2015, 12:39pm CEST par Ian Barker
Having a website is one thing, but getting it seen is another matter. Ensuring visibility of a site involves lots of factors which in the past may have been beyond the expertise and budget of smaller organizations.
Leading European web host 1&1 Internet is launching its latest MyWebsite 8 tool which includes an Online Success Centre making it easier for businesses to be found online.
Accessed via a central, easy to use dashboard the 1&1 Online Success Centre platform analyzes and displays the elements needed for online visibility while guiding business owners via a step-by-step process to improve their Internet presence.
By centrally managing basic information like name, address and phone number as well as opening hours and directions, businesses can enhance their local search ranking. With this information and the semantic appeal of the website, a Google preview is automatically generated allowing users to check how their data is displayed to their customers in the most popular search engine.
In addition it provides an instant appraisal of how a website appears on the most relevant online directories like Google Maps or Yelp, which are becoming more and more important for local searches. Users can also automate the management of their listings by applying 1&1 ListLocal to their online strategy.
A Content Optimisation interface guides users by an easy to use, speed-dial graphic that illustrates their level of search engine optimization. Content can be optimized to a high degree by applying an SEO tool which is integrated in selected packages.
"Since 2008, 1&1 has been committed to being a strong partner for small businesses by continually enhancing our website builder year after year," says Robert Hoffmann, CEO of 1&1 Internet Ltd. "With 1&1 MyWebsite 8 we introduce an industry first approach for small businesses to increase their online visibility. The new 1&1 Online Success Centre allows small businesses to get found easily on search engines and to be listed on the most influential online directories in a matter of just a view clicks".
Prices for MyWebsite 8 start from £6.99 per month in the UK, a 30-day free trial is available via the company's website.
-

New motion predictive technology aims to improve user experience
Publié: juin 2, 2015, 7:44pm CEST par Ian Barker

Most current user interfaces rely on some form of two-step interaction, point and click, or tap and lift, or press and hold for example.
The latest development from Quantum Interface promises to deliver a more seamless experience by using predictive navigation to infer user choices before they're made.
When a user moves towards a menu selection with a finger on a touchpad or screen, moves their hands in the air or moves their eyes in a car's head up display or under a VR hood, the app infers the choice, and moves the selection towards the user. This not only offers a more immersive experience it presents more information to the user faster than conventional interfaces.
This approach is now being made available to users with the beta unveiling of an Android smartwatch launcher, QiLaunch Wear. As a user puts a finger on the watch face and starts moving it towards a selection, the app launches with no lift and tap or point and click required. This streamlines the interface, speeds up engagement with apps, and allows the user to see more content and choices on a smaller screen.
It works by analyzing motion to predict the user's intent. The Qi interface reacts to changes of speed and direction as a user moves so it has the potential to work with any kind of interface from touchscreens and track pads to gesture or retina tracking and even old-fashioned mice. The only requirement to control any device is continuous motion, there's no special sign language or gestures to learn nor any special remotes or other hardware necessary. Designed to be universal it can be added to any application or operating system. The interface also consumes less power than current touchscreens, gestures or other ways of communicating with devices.
"User interfaces today are really frustrating and surprisingly old-fashioned. The Qi predictive navigation approach delivers the most advanced and intuitive interface, and with it, an entirely different user experience," says founder and CTO Jonathan Josephson. "With any device, notice how you drill down through multiple options, or long rows of choices, rather than moving smoothly exactly where you want to go. Qi has created a 'human' interface that seamlessly and intuitively connects people to their technology".
If this sounds like something you'd like to try for yourself you can apply to become a beta tester on the Qi website. There's a short video of the interface in action below.
Image Credit: alphaspirit / Shutterstock
-

Cloud storage survey highlights governance and security concerns
Publié: juin 2, 2015, 4:16pm CEST par Ian Barker

New research by cloud storage specialist CTERA Networks highlights the challenges that enterprises face in providing cloud storage and file sharing services, while reducing IT costs and maintaining security and data control.
It shows that security of data remains a major issue with 35 percent of organizations experiencing corporate data leakage in 2014 as a result of employees sharing files via often-unsanctioned file sync and share (FSS) services, a four percent increase over 2013.
Companies are taking this threat seriously and 83 percent of organizations have established corporate policies that either sanction the use of specific SaaS-based file sharing solutions or forbid their use in the organization entirely.
Nearly three-quarters of companies (73 percent) have implemented or are considering an alternative to public FSS, and two thirds of those favor private or "virtual private" cloud storage solutions. In addition, 59 percent of those organizations indicated that they favor a private cloud FSS solution run either on hosted (virtual private) infrastructure or in their own data center.
Cloud storage gateways are replacing and augmenting traditional file servers and tape storage, particularly in remote or branch offices (ROBO). One third of all organizations with more than 50 ROBOs have implemented on-premise cloud storage gateways that support both the private cloud and public cloud, and 27 percent of all companies have implemented them.
Enterprises are coming under pressure to establish contemporary cloud storage solutions that provide the visibility and control required to meet enterprise needs and industry regulations. In the more heavily regulated financial services, government and life sciences industries 42 percent prefer a completely private cloud that does not rely on external hosted infrastructure, as do 40 percent of organizations with 10,000 employees or more.
"Cloud storage is simplifying and accelerating data services across the enterprise. However, an increasing number of data leakage events, and a desire to exercise more control over file sharing and data protection are forcing organizations to investigate and deploy alternatives to public cloud storage services," says Rani Osnat, VP of Strategic Marketing at CTERA. "In our second year of research, the trend continues, demonstrating that organizations are leveraging cloud storage for efficiency gains and cost savings, while combating security, control and governance requirements with virtual-private or fully-private topologies".
The full report is available from the CTERA website and there's a summary of the findings in a Star Trek themed -- it's about enterprises, get it? -- infographic below.

Image Credit: Maksim Kabakou/Shutterstock
-

Consumers want personalized offers but don't want to share data
Publié: juin 2, 2015, 3:30pm CEST par Ian Barker

Consumers love getting personal, timely and relevant offers from retailers but they don't like having to share the data that makes them possible.
This is one of the main findings of new research by predictive marketing and consumer intelligence specialist Boxever. Of 507 consumers surveyed more than 60 percent indicated they prefer offers that are targeted to where they are and what they are doing, but 62 percent said that they don't want retailers tracking their location.
"Retailers are losing consumer trust for failing to effectively leverage personal data; it's negatively affecting the customer experience and retailers' ability to market and sell effectively," says Dave O'Flanagan, co-founder and CEO of Boxever. "While today's consumers crave a personalized, value-added shopping experience, they're unlikely to continue sharing personal data because they aren't seeing enough value from the data that retailers already collect".
The survey also finds that for more than half of consumers, three out of four sales offers received are irrelevant to their needs and preferences. This means that millions of consumers are being spammed daily, an ineffective communication strategy that can have a negative impact on future sales and customer loyalty.
When consumers experience this type of marketing 40 percent say they're less likely to buy from that company in future, 50 percent are less likely to open the next offer that comes from that company, 59 percent said they would unsubscribe from the company's content, and 31 percent would delete the company's app.
The three most-preferred channels for receiving offers and communications are email, in-store, and direct mail, with email being far-and-away the most popular platform. A mere two percent of survey respondents identified mobile as their preferred channel for receiving offers and communications, and only four percent prefer social media. Those preferences change slightly for millennials, who prefer mobile twice as much as the general population, and who are nearly three times as likely to prefer offers on social media.
When asked what factors influence them to buy or act on an offer, 70 percent say when the offer adds value to something they are already doing or plan to do, 42 percent when the offer revisits a product or event that they've expressed interest in before, and 21 percent when the offer is targeted to what they are doing at that moment.
"The days of personalizing offers based on high-level demographics are long gone, and continuing along this path will actually hurt, not help brands," says O'Flanagan. "Brands need complete visibility into the preferences of every customer, and the ability to integrate contextual customer intelligence and value into each marketing offer sent".
The full report The Data-Sharing Disconnect: The Impact of Consumer Trust and Relevance in Retail Marketing is available to download from Boxever's website and there’s a summary of the findings in infographic form below.

Image Credit: Tashatuvango / Shutterstock
-

Organizations take too long to fix security vulnerabilities
Publié: juin 2, 2015, 2:03pm CEST par Ian Barker

A new study from threat prediction and remediation specialist NopSec reveals key security vulnerability issues and highlights the length of time it takes for enterprises to fix problems.
NopSec analyzed more than 65,000 vulnerabilities contained in the National Vulnerability Database over a 20-year period, as well as a subset of more than 21,000 of those vulnerabilities identified across customers in all industries.
Key findings include that Microsoft and Apple dominate the vulnerability chart, based on the two-decade analysis, with Linux operating systems trailing behind. In addition, Adobe, Apple, Microsoft, Mozilla and Oracle face the most severe vulnerabilities.
While rapid vulnerability detection is at an all-time high, it still takes the typical organization too long to address known security issues. The average time it takes to fix a security vulnerability is 103 days. However, this varies by industry, while cloud providers respond fastest (50 days), followed closely by healthcare organizations (97 days), financial services companies and education organizations take a worrying 176 days to take corrective action. That means they're potentially exposing themselves to data breaches for almost six months. Even worse, nearly a third (32 percent) of security vulnerabilities take more than a year to fix in the financial industry.
Cloud providers are more exposed to attack with an average 18 vulnerabilities per asset. This contrasts with the six vulnerabilities per asset in financial services, three in healthcare and two in education. The type of vulnerability matters too, whilst application vulnerabilities are fixed within three weeks on average (20 days), network vulnerabilities are left unaddressed for a scary 182 days.
Interestingly although threats may be going unfixed within organizations, they're often well known on social media. The typical security vulnerability averages 115 social media mentions when there is a known malware exploit. However, that number increases when an exploit earns a "critical" risk severity rating based on the NopSec technical risk score. Critical vulnerabilities average 748 social media mentions, whereas high risk vulnerabilities rate only 89 mentions.
"Organizations are still very vulnerable to exploitation. Although businesses have been alerted of the potential risks, system vulnerabilities and misconfigurations continue to be the root causes for costly security breaches," says Michelangelo Sidagni, NopSec Chief Technology Officer and Head of NopSec Labs. "Detection is simply not enough in today’s threat landscape of sophisticated attacks; organizations need to focus on improving threat prioritization. Vulnerability remediation efforts need to move much faster than they are right now in order to close the window of opportunity for exploitation and win the race against hackers".
More information on the study is available on the NopSec website.
Image Credit: razihusin / Shutterstock
-

New big data platform helps with security analytics and forensics
Publié: juin 2, 2015, 1:48pm CEST par Ian Barker

Cyber attacks are becoming more covert which helps them to consistently evade detection and means they can take weeks to uncover.
Cyber security startup Niara is unveiling its Security Intelligence Solution, combining advanced security analytics and forensics to help security teams quickly find sophisticated cyber threats within their organization.
Based on big data architecture, the Niara Security Intelligence Solution analyzes security data from disparate sources to ensure that security teams can identify and respond to sophisticated, multistage attacks that can be missed by existing monitoring and response solutions.
"The threat landscape is continuously evolving and enterprises need a way to discover and investigate advanced threats inside their network faster and more efficiently," says Sriram Ramachandran, CEO of Niara. "Niara's Security Intelligence Solution is designed from the ground up to leverage analytics and forensics from disparate data sources, providing unprecedented views into an organization’s network. This fundamentally elevates their threat discovery, incident investigation and breach response capabilities, reducing risk and helping them stay out of the headlines".
It can operate on a mix of data sources including logs, flows, packets, alerts and threat feeds to flag up threats and risky behaviors that remain undetected by log-based analytics alone. It builds an overview of an organization's threats by monitoring not only users, but also devices and applications to collect and discover threat information. Combined with Niara's ability to profile entity behaviors by linking together disparate events to uncover them as a multistage attack, it means teams have a complete view of an organization's risk posture.
Security Intelligence Solution provides one-click access to a comprehensive forensic trail and analytics in the same solution to simplify and accelerate threat discovery and incident investigation. It can make use of existing data stores too without the need to recreate or duplicate data.
The Niara Intelligence Security Solution is available now and can be delivered for cloud, on-premise and hybrid deployment. More information is available on the Niara website.
Photo Credit: ra2studio / Shutterstock
-

IT heads want scalable, secure mobile app platforms
Publié: juin 1, 2015, 5:31pm CEST par Ian Barker

Developing mobile and web-based continues to present a major challenge for enterprises, especially with regard to the costs associated with infrastructure and DevOps.
A new survey of 200 technology decision makers by mobile backend-as-a-service (MBaaS) company moBack shows that 80 percent of respondents, including both large and small businesses, consider mobile app development very important and essential for their business.
Of the respondents 65 percent say they're currently using cloud-based platforms such as BaaS or MBaaS to develop mobile apps. However, some of the challenges they face include sourcing the right technical skills, speed of delivery and flexibility for rapid app development.
Scalability is cited as important by 80 percent, cost reduction capabilities by 80 percent and customization for business specific functions by 81 percent. 75 percent of the respondents indicated ease of use as being very important and essential in a MBaaS platform. Two-thirds want or highly value the ability of a MBaaS platform to customize, include their organization’s business specific functions and reduce cost. Cost and security are cited as the deciding characteristic of 70 percent of all technology decision-makers.
"From our experience in building apps for enterprises across various industry segments, we find that the need for adopting mobile technologies is becoming a top priority in order to stay ahead of competition," says Dev Gandhi, CEO of moBack. "The challenge most IT executives face is to achieve this in a cost-effective manner, while also maintaining control over business-critical information. moBack's MBaaS platform aims to provide enterprise IT the control and flexibility it needs to deploy mobile services, while saving considerable costs".
More information on the results is available on the moBack website and there's a summary of the findings in infographic form below.
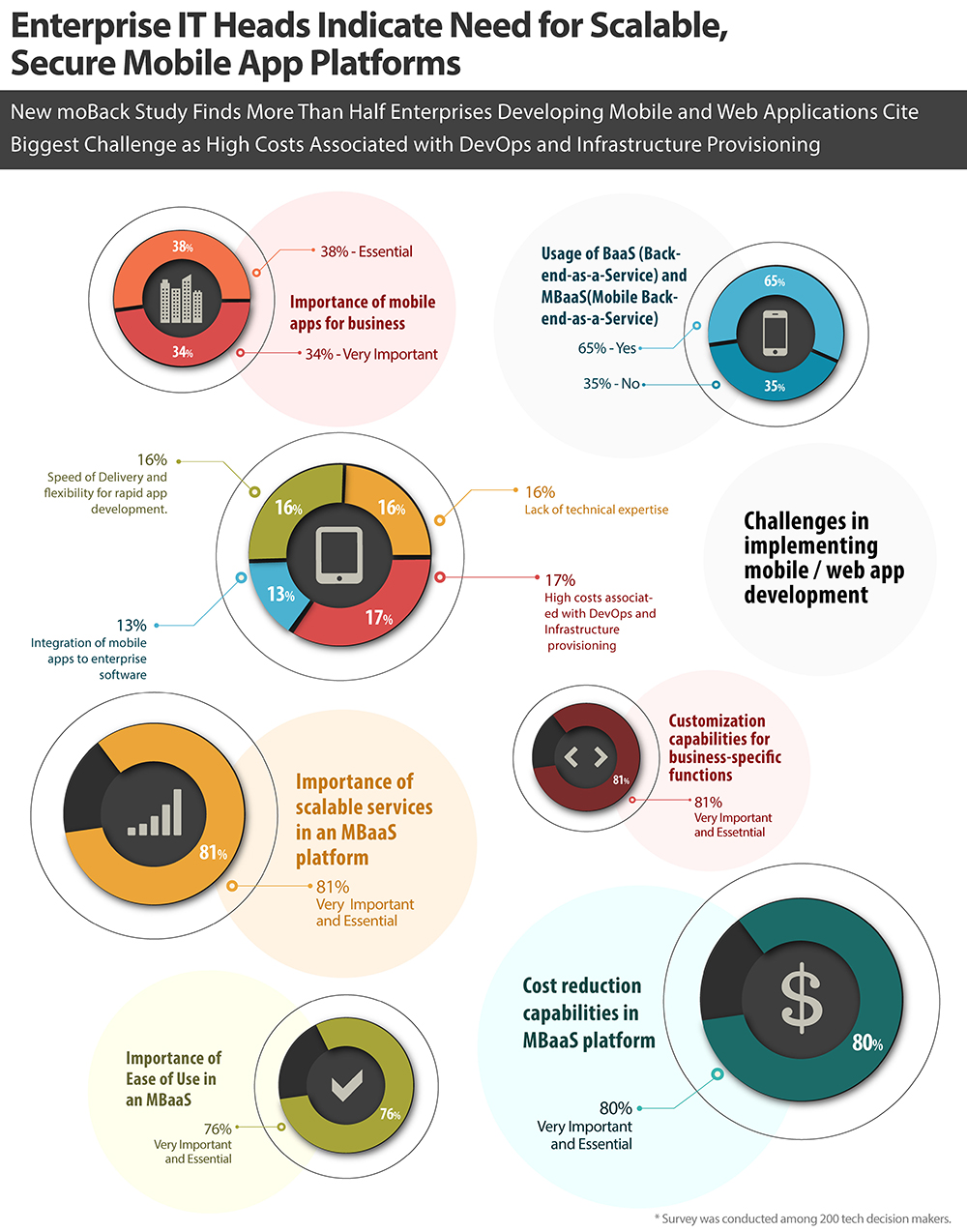
Image Credit: Alex Mit / Shutterstock
-

Adding business intelligence to the hiring process
Publié: juin 1, 2015, 3:30pm CEST par Ian Barker

Business intelligence tools are usually thought of in terms of marketing and strategic decision making. Using them for other tasks like recruitment has usually meant links to other products and significant manual input.
Now though recruitment software specialist Gild is launching a BI solution specifically for hiring, applying predictive analytics and insight to every stage of the process, delivering 360-degree information and customized reports to help every make better decisions.
"There's a sea change coming to talent acquisition that's similar to the transformation marketing automation tools created in how companies go to market", says Sheeroy Desai, CEO of Gild. "By arming each person involved in the hiring process with the real-time information to become more effective, Business Intelligence for Hiring eliminates the need for a dedicated business analyst or costly, separate BI application. As an integral part of The Gild Platform, our new BI solution lets everyone see the data that matters most as well as data they never had access to before -- whether it's understanding which sources produce the best candidates, where recruiting campaigns are most successful, how employees are performing or where resources are being spent. And because we offer data in a form that's both meaningful and easy to understand, companies can now get a truly accurate overview of their entire business ecosystem".
Delivered as part of the Gild smart recruitment platform, BI for Hiring is made up of persona-specific dashboards that can be customized for each hiring role from CEOs to recruiters.
For example CEOs can assess the return on investment of each hiring expense, benchmark performance against that of similar businesses and make educated decisions about where to focus resources and what strategies to pursue over time. Finance officers can understand the fiscal impact of hiring on budgets and the bottom line, identify expensive errors and optimize the hiring process for the most cost-effective return.
Departmental managers are able to access data about how hiring and firing rates impact each team, which factors affect productivity the most and which areas need improvement and optimization. Over time recruiters can boost their personal productivity and make better hiring decisions by understanding the impact of their role on the business.
Gild Business Intelligence for Hiring is available from today to existing users of the Gild platform. You can find out more on the company's website.
Photo Credit: Adam Gregor/Shutterstock
-

Little and large -- Inateck FE3001 and FE2007 USB 3.0 HDD enclosures [Review]
Publié: juin 1, 2015, 1:42pm CEST par Ian Barker

What do you do with the SATA hard drive you took out of that old machine you threw away a couple of years ago? One answer is that you get hold of an external enclosure and use it as an archive or for making backups.
Inateck's latest external enclosures allow you to do just that for both 3.5- and 2.5-inch drives. Let's take the larger one first, the FE3001 is USB 3.0 for fast transfers and the case is made of sturdy aluminum with a smart, grained finish. There's an external power supply, USB cable and everything else you need -- screws, rubber pads and even a small screwdriver -- is included in the box.
It's easy to fit your drive into the case -- pull out the back panel, which carries the connections and an on/off switch, and out slides a half-length metal tray. Plug the drive into the SATA connector, attach it to the tray with a couple of screws, slide it back in and fasten the cover with a couple of longer screws and you're done. There are good printed instructions if you get stuck, these also give advice on formatting disks and safely disconnecting.
The FE2007 is for 2.5-inch drives, it's a bit larger than you'd normally expect to accommodate this size disk but that's because it incorporates a USB 3.0 hub. The case is made of plastic but it's a neat tool-free design with a sliding cover. There’s an on-off switch, which is something you don’t often get on small disk enclosures, and there’s a separate power input for systems that don't provide enough juice on the USB port. Cables for both this and the normal USB connection are supplied.
As a drive enclosure it's similar to the FE2004 that we reviewed a few months ago but the addition of a USB hub means you can leave it connected all the time without sacrificing a USB 3.0 port.
You can buy hard drive enclosures cheaper, however, the Inateck products have an air of quality and are thoughtfully designed with some nice touches you don’t get in budget-priced alternatives. If you have an old hard drive that you want to rehouse they’re well worth considering.
The FE2007 costs $29.99 on Amazon (£25.99 in the UK). The FE3001 is on Amazon for $22.99 (£23.99 in the UK).
-

DDoS attacks spread to more countries
Publié: mai 29, 2015, 5:15pm CEST par Ian Barker

A total of 23,095 DDoS attacks were carried out on web resources located in 76 countries in the first quarter of 2015, up 15 percent from the 66 countries affected in the final quarter of last year.
This is one of the findings of a new study by cyber security firm Kaspersky Lab into the botnet-assisted DDoS attack landscape. But although the geography is expanding the overall number of botnet-assisted attacks is down by 11 percent and the number of unique victims down by eight percent.
Servers in the US, Canada and China are targeted most frequently. The study also finds that the greatest number of attacks on a single web resource in Q1 2015 was 21, compared to 16 in Q4 2014, and the most prolonged botnet attack occurred for almost six days.
"A DDoS attack is often a cross-border effort; the customer is located in one country, the executor in another, the C&C servers are hosted in a third country, and the bots involved in the DDoS attack are scattered across the world," says Evgeny Vigovsky, Head of DDoS Protection at Kaspersky Lab. "This often makes it more complicated to investigate attacks, take down botnets and catch those responsible. Although cybercriminals do not limit their DDoS toolkits to botnets alone, this is still a widespread and dangerous tool, and it demands preventive protection measures from potential targets, i.e. web resources".
The fact that China and the US for most frequently attacked countries and highest numbers of victims is, says Kaspersky Lab, down to low hosting prices that encourage many companies to have their sites located in those countries.
The most attacks on a single resource were against a Russian language website belonging to an investment group. A Vietnamese wedding services site was second most attacked, and a US hosting provider third.
Only three sites suffered attacks of more than 100 hours, down significantly from 13 in the final quarter of 2014. However, as the report points out even a short, one-off attack can make a site inoperable and cost the victim both financially and in damage to reputation.
The full report with much more detail is available from the Kaspersky Lab site. There's also an infographic showing the geographical breakdown of attacks below.
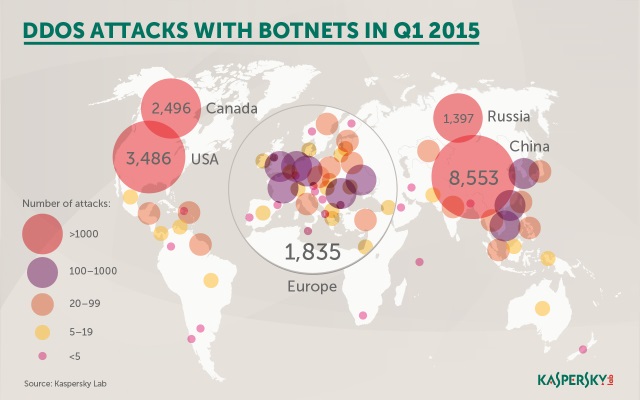
Image Credit: Jozsef Bagota/Shutterstock
-

Adware makers turn their sights on OS X
Publié: mai 29, 2015, 5:05pm CEST par Ian Barker

Hot on the heels of news that OS X topped the vulnerabilities charts in April comes Dr. Web's virus activity review for May which shows increasing quantities of adware and unwanted applications targeting the Apple operating system.
The company reports several programs aimed at OS X that either install adware, install other applications or inject JavaScript code into webpages.
Adware.Mac.InstallCore.1 cannot only install unwanted programs on the user's computer but also change the browser home page and the search engine used by default. The program incorporates debugging functions too -- once launched, it scans the system for the presence of virtual machines, anti-virus tools, and some other applications. If the scan returns positive results, the malware will not prompt the user to install additional programs.
Adware.Mac.WebHelper can be launched automatically with the help of PLIST (Property List) files. The application can modify the home page in Chrome, Firefox, and Safari. It can also change the default search engine to my-search-start.com. It contains a binary file that executes two AppleScripts (for Chrome and Safari) in an infinite loop. These scripts inject JavaScript code into webpages browsed by the user. Running of this code, in turn, results in downloading other JavaScripts that display adverts in the browser window.
There's similar functionality in Mac.Trojan.Crossrider which is distributed in the guise of an installation package (Safari Helper). Crossrider trojans may be familiar to Windows users but this variant specifically targets Apple systems. Running it triggers a stealthy installation of the FlashMall extension for Safari, Chrome, and Firefox. It also adds two applications to the system startup list: "WebSocketServerApp" and "Safari Security". The first is responsible for communication with the command and control server and the second one installs browser extensions. In addition the malware modifies the startup scripts for the browser extensions to be updated in the future.
Apple users may like to know they're not the only ones that are coming under attack. Linux.Kluh.1, developed by a Chinese hacker group, infects routers with the purpose of launching DDoS attacks. Linux.Iframe.4 is a malicious plug-in for the Apache web server that injects code into web pages browsed by users redirecting the victim to the web page run by cybercriminals.
Trojans continue to be the big threat to Windows systems with an overall increase of 14.9 percent in the amount of malware and riskware detected in May. Android users aren't safe either with an increase in numbers of banking and SMS trojans as well as the emergence of new ransomware.
There's been a big increase in malicious websites too with 221,346 URLs being added to Dr. Web's database in May. Many of these use social engineering techniques like sending bulk SMS messages informing the recipient that they have won a car. The message contains a link to a wesbite which tries to get visitors to part with their financial details.
More information on these and other threats is available on the Dr. Web site.
Photo Credit: Stephen Finn/Shutterstock
-

How a growing cyber attack industry is good news for investors
Publié: mai 29, 2015, 3:21pm CEST par Ian Barker

Whilst cyber attacks continue to make the news, a new report published by Capital News Desk suggests that around 70 percent of organizations choose to keep their security incidents quiet.
It also reveals that around 73 percent of large organizations have been infiltrated by attacks. It's newer technologies like BYOD and the cloud that are seen as the biggest threats along with cyber crime.
In an effort to combat these attacks worldwide information security spending is expected to reach $94.8 billion by the end of this year. By 2019 the cyber security sector is forecast to be worth $155 billion.
The US government has budgeted $14 billion for cyber security in 2016 with the Pentagon alone requesting $5.5 billion for cyber defense. This boom in security is good for investors though and has led to venture capitalists seeking out companies in the sector.
More detail is available in an infographic reproduced below.
Photo Credit: Sergey Nivens/Shutterstock
-

Making it easier for small businesses to create a professional online presence
Publié: mai 29, 2015, 1:01pm CEST par Ian Barker
It's becoming almost essential for businesses to have an online presence today, but for smaller companies or one-man operations employing a professional designer may be prohibitively expensive and basic template-based design tools don't always produce quality results.
Russian website specialist uCoz is about to make life easier for small businesses with the launch of the open beta of its new website creation platform, uKit.
uKit is designed with even the least tech-savvy user in mind. It's a browser-based drag-and-drop website builder that lets micro and small sized businesses create personalized websites in an easy yet effective way.
"Micro, small businesses and freelancers account for over 95 percent of the world's enterprises, and with increasing competition, an online presence has become even more vital. In the United States alone, around 50 percent of the businesses don't have a website. We want to help business owners save on initial start-up costs with a do-it-yourself solution that is highly flexible and professional, yet affordable," says Evgeny Kurt, uKit's CEO and Co-Founder of uCoz.
uKit offers a number of templates to get you started which you can then customise to meet your needs. It's easy to add various kinds of content, social links, online stores, blogs, etc. A toolbar to the left of the screen adapts to offer options for whichever page element you click on.
A clever feature of uKit is that the software limits user customizations based on recommendations by skilled design professionals. This helps users avoid scenarios like mismatched fonts, awkward color combinations, unprofessional headers and other design mishaps. The sites it creates are designed to adapt seamlessly to display across all devices including tablets and smartphones.
Further additions to the service to be rolled out later this year include a landing page generator. There will also be an automatic AI-assisted conversion from FB pages and outdated websites to a new, redesigned and adapted to current marketing standards, business website.
The beta is available now and you can try it out for yourself by visiting the uKit site.
-

Meeting the challenge of unstructured data
Publié: mai 29, 2015, 11:33am CEST par Ian Barker

Businesses around the world are relying more on big data than ever before. But it’s crucial that they know the right way to store and protect their data as well as knowing how to use it effectively.
Communications and managed infrastructure specialist XO Communications has produced an infographic looking at how intelligent networking can be used to manage the rise in unstructured data use.
It shows that the average enterprise will need to manage 50 times more information by 2020, but with only a 1.5 percent increase in IT staffing. Also that more than 90 percent of the data in today’s enterprises is unstructured.
Of 1,800 IT professionals surveyed 48 percent expect network loads to double over the next two years and 23 percent expect them to triple. 81 percent say that cloud computing will be needed to handle their big data projects.
You can see more in the full infographic reproduced below.
Image Credit: alphaspirit / Shutterstock
-

Server market revenue up 17 percent in the first quarter of 2015
Publié: mai 28, 2015, 4:54pm CEST par Ian Barker

Figures released today from two major research organizations show that the worldwide server market has made a strong start to 2015.
According to Gartner shipments grew 13 percent year on year, while revenue increased 17.9 percent from the first quarter of 2014. IDC's Quarterly Server Tracker shows server revenue up 17.2 percent to $12.8 billion in the first quarter of 2015.
"The first quarter of 2015 was a particularly strong start to the year, with the strongest shipment growth since the third quarter of 2010, when the market was recovering from the downturn. It was also the second-largest-volume quarter ever," says Adrian O'Connell, research director at Gartner. "The market was driven by particularly strong demand from the hyperscale area, which benefited North America, in particular. This comes at a time when other regions are struggling, due to price pressure driven by the appreciation of the U.S. dollar. The strength in North America was strong enough to offset declines in Latin America and Japan. EMEA was barely positive, with 1 percent volume growth".
Both sets of figures show that HP still holds the top slot in the server market with around 24 percent market share, followed by Dell and IBM on around 18 and 14 percent respectively. Lenovo and Cisco are neck and neck for fourth, each on around seven percent. Lenovo showed the strongest growth in shipments according to Gartner though, up almost 240 percent in the first quarter.
iChartsMost of the market growth is down to demand for x86 systems, whilst RISC/Itanium Unix server shipments declined. Demand for high-end systems showed revenue growth though driven partly by IBM's refresh of its z13 mainframe range.
"Even as high-end systems are increasingly being deployed on x86 platforms, opportunities for long-term non-x86 growth still exist with OpenPower and ARM, as customers are looking for non-x86 alternatives to hyperscale problems," says Kuba Stolarski, Research Manager, Enterprise Servers at IDC. "Some of that transformation is likely to occur in the greenfield opportunities related to Internet of Things (IoT) solutions, while optimizing hardware and software for hyperscale datacenter workloads continues to be a driver of design innovation and supply chain diversification."
More information on server market performance is available from Gartner and from IDC.
Photo Credit: dotshock/Shutterstock
-

New analytics language makes log data more accessible
Publié: mai 28, 2015, 3:50pm CEST par Ian Barker
Modern computing environments generate vast quantities of log entries. Analyzing this data in the event of a problem can be a mammoth task often involving different tools for different systems.
Boston-based Logentries is announcing a new Analytics Language that offers an easy-to-use alternative to traditional search languages with no need for technical skills.
Logentries Query Language (LEQL) bridges the gap between management and analysis by enabling users to not only collect and search log data in real-time, but now use logs to visualize high-level trends, perform sophisticated correlation across log data streams, and drill down as needed into the data.
"Our new LEQL language has been designed to be powerful, yet easy to use," said Trevor Parsons, Chief Scientist, Logentries. "It enables our users to easily ask questions of their log data and get immediate visibility across their software stack, without requiring them to learn a new, complex query language".
LEQL helps users to slice-and-dice their data using search functions such as Count, Sum, Average, Min, Max, Group By, Sort and more. It delivers the ability to see both high level trend reports and a fine-grained view of system and application performance using one single tool.
Logentries cloud-based service collects and pre-processes log events in real-time for on-demand analysis, alerting and visualization. With custom tagging and filtering, users can draw data from across their infrastructure to better understand application usage and performance, as well as security and performance issues, and user behavior.
You can find out more about Logentries and sign up for a 30-day trial on the company's website.
-

Security software market grows more than 5 percent in 2014
Publié: mai 28, 2015, 12:04pm CEST par Ian Barker

Security is always in the news so it hardly comes as a surprise that the market for security products is growing. According to research specialist Gartner the worldwide security software market was up 5.3 percent in 2014.
In terms of value the market is worth $21.4 billion, however, the make up of that market is shifting. Low growth in endpoint protection platforms and a decline in consumer security software -- possibly because of improved built-in security in the latest versions of Windows -- are balanced by high-growth areas, such as security information and event management (SIEM), secure Web gateway (SWG), identity governance and administration (IGA) and enterprise content-aware data loss prevention (DLP).
"Overall market growth was up slightly in 2014 to 5.3 percent from 4.9 percent in 2013," says Sid Deshpande, principal research analyst at Gartner. "Even though the SWG segment experienced single-digit growth in 2014, cloud-based and hybrid SWG deployments are becoming increasingly popular. As organizations' corporate data traffic becomes more exposed to the Internet and moves out of the control of traditional network security boundaries, SWG technologies continue to be an important piece of the overall security technology strategy of most enterprises".
Symantec remains the biggest player in the security market with $3.69 billion of revenue, but it suffered its second consecutive year of revenue decline in 2014. This is in part due to its heavy reliance on consumer security software which accounts for 53 percent of its business.
Intel -- which owns McAfee -- is in second place with $1.8 billion, up 4.6 percent, followed by IBM which saw its security software revenue up 17 percent in 2014 to reach $1.48 billion.
The DLP market grew 15.8 percent year on year to reach $643 million in revenue in 2014. This was mainly due to a strong showing from Symantec in this sector, accounting for nearly half of the total market. SIEM was up 11 percent to $1.6 billion thanks to a strong focus on threat detection and response from security buyers.
The full report is available to Gartner subscribers via the Gartner - security software report.
Image Credit: Norebbo/Shutterstock
-

Mac OS X tops vulnerabilities chart for April
Publié: mai 27, 2015, 4:20pm CEST par Ian Barker

Security company Secunia has released its latest quarterly Vulnerability Update covering the period from February to April 2015.
It looks at the top 20 products with the most vulnerabilities each month and finds that there have been a total of 1,691 new vulnerabilities appearing in the top 20 over the three month period.
The vendor with most vulnerable products in the quarter was IBM, but the top spot for highest number of vulnerabilities in a single product goes to Avant Browser in February and Apple Mac OS X in April, each with 84. March's chart is topped by Google Chrome with 51 vulnerabilities.
Cisco IOS put in an appearance in March with 23 vulnerabilities. Whilst that's not a huge number it does emphasize the need to be aware of problems coming from unexpected directions. Cisco IOS is the operating system used on the many of the routers that operate the Internet, and also on the Cisco network switches found in many company networks.
Windows 8 has made the list every month, with 25 vulnerabilities in February, 31 in March and 24 in April. As did Windows Server 2012 with 25, 32 and 24. Windows 7 just sneaked into the bottom of March's top 20 with 20 vulnerabilities.
There have been seven publicly disclosed zero-day vulnerabilities in the first four months of 2015, all of them in Adobe Flash Player and Microsoft Windows. Cause for concern as these are two of the most widespread programs globally, on both private PCs and corporate networks.
What's interesting is how varied the monthly lists are. Although there are some products that appear regularly there are also a variety of others making 'guest appearances' underlining the need to stay vigilant and ensure that all of your software -- not just the operating system -- has the latest patches installed.
The full report is available to download from the Secunia website.
Image Credit: Sergey Nivens / Shutterstock
-

New Instart Logic platform set to deliver faster, more reliable websites
Publié: mai 27, 2015, 3:20pm CEST par Ian Barker

Web developers are under pressure to deliver sites and applications faster and at the same time offer greater flexibility and a more personalized end-user experience.
Cloud application delivery provider Instart Logic is using the O'Reilly Velocity Conference to launch its latest Software-Defined Application Delivery (SDAD) platform.
The new release offers performance features including JavaScript interception that accelerates third-party code, the development of Browser Cache Purge to extend cache control to the browser, and opening up SDAD to developers with new APIs.
There's also a new management portal for improved agility and end-to-end control, a big data platform that enables consolidated real-time reporting and analytics, and embedded machine learning to automatically improve performance.
Enhanced performance and security are on offer with Nanovisor 2.0, an upgrade to Instart Logic's patented client technology. This includes an industry first client-side redirection system which enables runtime redirection of client-side asset requests. This allows it to redirect third party JavaScript requests through Instart Logic's service, improving performance, availability and reliability. It also removes the overhead involved in domain name lookup and connection establishment.
With Browser Cache Purge, publishers will be able to push changes to the browser via an API and clear browser cache instantaneously whenever necessary. This new capability seeks to boost performance by eliminating unnecessary network requests to check for current content and is set to fundamentally change how applications are designed. There's an Early Experience Program to recruit application publishers and get their input into how this capability impacts application design.
Third-party JavaScript interception is available from today and the APIs will come on stream over the summer. Developers can sign up for the Browser Cache Early Experience Program by visiting the Instart Logic Developer Central site.
Photo Credit: nmedia/Shutterstock
-

Antivirus products for Linux compared
Publié: mai 27, 2015, 12:50pm CEST par Ian Barker

Though Linux is often seen as being immune to malware it's still important to have protection, partly because Linux malware does exist, even if it’s rare, and partly to prevent the passing on of viruses to more vulnerable operating systems like Windows and Android.
Independent testing organization AV-Comparatives has been looking at the leading Linux anti-malware offerings to gauge their ease of installation, features and more.
Linux has only around a 1.5 percent share of the desktop market so there are relatively few antivirus programs aimed at home users. Also Linux software is usually installed via community-maintained repositories that make it harder to distribute malware.
The report doesn't rank the tested programs but does deliver an individual verdict on each. Singled out for praise are BitDefender Antivirus Scanner for Unices, which offers an easy to use graphical interface and good help facilities, ESET has a clear status display and good malware alerts, and eScan too is praised for ease of use though it provides only on-demand scanning and not real-time protection.
Kaspersky too is easy to manage and configure as is McAfee, both of which use a web console approach as does TrendMicro's Server Protect for Linux.
Others including Comodo Antivirus for Linux, and Dr. Web Anti-virus for Linux come in for criticism for needing use of the terminal for configuration, making them unsuitable for Linux novices. AVG Free Edition for Linux is criticized for being unable to run real-time protection without making the system inoperative.
As well as installing antivirus software, AV-Comparatives recommends that Linux users implement some basic security procedures including keeping installed software up to date, only installing from trusted sources, disabling services you don’t use and not logging in as root.
The full report with verdicts on all 18 programs tested is available to download from the AV-Comparatives site.
Image Credit: maimu / Shutterstock
-

New platform offers simpler big data operation
Publié: mai 27, 2015, 11:23am CEST par Ian Barker

The adoption of big data often sees developers struggling to balance multiple data models, hybrid architectures, distributed workloads and more.
Seattle-based Basho Technologies is looking to simplify the operation and integration challenges of deploying and managing big data, IoT and hybrid cloud applications with the launch of its Basho Data Platform.
It integrates Riak KV (formerly Riak), a distributed NoSQL database and Riak S2 (formerly Riak CS), with Apache Spark for in-memory analytics, Redis caching for increased performance and Apache Solr for enhanced query capabilities, offering improved productivity for development and operations teams.
"This is a true turning point for the database industry, consolidating a variety of critical but previously disparate services to greatly simplify the operational requirements for IT teams working to scale applications with active workloads," says Adam Wray, CEO and president of Basho. "The impact it will have on our users, and on the use of integrated data services more broadly, will be significant. We look forward to working closely with our community and the broader industry to further develop the Data Platform".
The Basho Data Platform is purpose-built to simplify operations for organizations needing database scalability, multi-model support and seamless integration with complementary technologies. Features include real-time, in-memory analytics with Apache Spark, enhanced read performance with integrated Redis caching, and Riak Search with Apache Solr allowing for transparent indexing and querying of Riak data values.
In addition it makes for simplified operations with download and deployment of instances of Riak KV, Apache Spark and Redis. It can auto-detect and auto-restart failed instances to ensure optimized operations and high availability, plus it eliminates the need to use Zookeeper with Spark to maintain configuration information.
Replicating and synchronizing data and indexes ensures seamless data access and data accuracy with no data loss should an instance of Redis or Spark become unavailable due to network, system or other connectivity failures.
Basho Data Platform is available from today and you can find out more on the company's website.
Photo Credit: T.L. Furrer / Shutterstock
-

1&1 Cloud Server offers scalable computing for smaller companies
Publié: mai 26, 2015, 5:20pm CEST par Ian Barker
One of the problems for smaller businesses when specifying servers is that it's easy to be caught out by a sudden surge in traffic or need for extra capacity.
It can take time to ramp up capacity to cope during which you could be losing business. Hosting company 1&1 Internet has launched its new Cloud Server solution aimed at smaller businesses which offers flexibility and control along with a transparent pricing model.
It uses SSD storage through a Storage Area Network (SAN), to provide greater reliability and better performance than the company's old Dynamic Cloud Server product. The whole thing is controlled from a browser-based interface to a VMware virtual machine, from which you can monitor what's happening, install software and add extra hardware resources as required. There's a virtual DVD drive which makes it easy to install one of a selection of operating systems without the need to upload anything, options include RedHat and Ubuntu Linux as well as Windows Server.
If ever an action will result in an extra charge -- for example if you want to add extra storage or memory -- you get a pop up window making this clear and showing you how much it will cost, so it's easy to keep track of what you're paying for. Adding resources uses simple slider controls so you don't need to be a technical wizard, this also means you can play around with the options and compare the costs before committing yourself.
You can specify applications like SQL Server too and it's possible to have a server up and running in just a few minutes. Firewall settings can be tweaked and you can assign IP addresses and passwords giving you a lot of flexibility. Once you have a server active a graphical control panel lets you keep an eye on the resources it's using. You can add extras like load balancing and private networks as well as being able to mount shared disk volumes of up to 2TB capacity.
"Many small and medium businesses are considering moving to the Cloud but until now there has not been a Cloud service available that met their expectations in terms of security and flexibility while still being easy to manage," says Robert Hoffmann, CEO of 1&1 Internet Ltd. "Now, whether they need one server or several servers, professionals can trust in 1&1 as the leading web host in Europe to support them on their migration to the Cloud, where they will discover a new category of Cloud solution that has been specifically designed to address their needs with the best quality-price ratio on the market".
What makes 1&1 Cloud Server particularly attractive is that it's effectively a pay-as-you-go service. There's no hardware to buy and you don't have to sign up to a long-term contract. It's also easy to manage making it a good option for businesses with limited in-house support.
Basic configurations start from $19.99 (£15.84) per month, you can find out more on the 1&1 website.
-

Inateck KT9001 PCIe USB 3.0 and wireless card [Review]
Publié: mai 26, 2015, 10:44am CEST par Ian Barker
In a world increasingly dominated by mobile devices it's easy to forget that many people, particularly in business environments, are still using desktop PCs.
Desktops of course tend not to come with built-in Wi-Fi which means adding a PCIe card or a USB wireless adaptor. With the KT9001, what Inateck has produced is a PCIe card that's a clever mash up of wireless adaptor and three port USB 3.0 hub.
The three USB ports offer transfer rates of up to 5 Gbps and have three-layer power management so you shouldn't need an extra port to provide power for devices like external hard drives. This part of the card uses a Fresco Logic chip.
The other side of its capability is an 802.11 AC protocol, dual-band wireless network card, using a Realtek chip supporting both 2.4GHz and 5GHz networks. It comes with two antennas allowing it to select the most suitable wireless network automatically should you have a dual-band router or access point. Speeds of up to 300Mbps and 867Mbps are available provided your network supports it.
Everything you need is in the box, Inateck even provides a screw to fix the card into its slot. The supplied driver CD supports versions of Windows from XP up to 8.1 -- but more on that in a second. You need to run two separate driver installs, one for the Wi-Fi and one for the USB ports. A Realtek Wireless LAN Utility program is provided too although this wouldn't install on my Windows 8.1 64-bit system. That's not a huge issue as the card works with the in-built Windows network management tools. The drivers were more of a problem and I had to download a newer Realtek driver than the one provided in order to get reliable operation.
The one slight drawback is that you end up with the USB 3.0 ports on the back of the PC where they're not exactly convenient for plugging in things like external drives that will benefit most from the extra speed. It's worth investing in an extension cable or two to make them easier to use.
That and software issues aside the card works well, if you want to update a desktop machine to give it wireless and USB 3.0 capability then there's nothing else on the market that will do both jobs with just one card.
The KT9001 costs $39.99 on Amazon, or £41.99 in the UK. You can find the full technical spec on the Inateck website.
-

ProtectWise streamlines data breach analysis
Publié: mai 25, 2015, 4:09pm CEST par Ian Barker

It often takes time for data breaches to be uncovered and that can present problems when it comes to analysing them and tracing their cause.
Denver-based startup ProtectWise has an answer in the form of its new technology that can record all network activity and store it in the cloud for analysis and playback at a later date.
Called Cloud Network DVR, it provides unlimited retention of full-fidelity network data with the ability to automatically go back into weeks, months and even years of historical data to uncover threats that were previously unknown using the latest intelligence. It also uses threat detection from proprietary research, machine learning and flow-based traffic algorithms as well as multiple commercial intelligence feeds across ProtectWise's customer base.
Cloud Network DVR is delivered as a service allowing for rapid deployment, evaluation and time to value, and eliminates the costs associated with appliance-based solutions.
In addition it allows users to visualize its data via an interface designed by special effects professional Jake Sergeant. It includes a head-up display which provides an at-a-glance view of an organization's network security posture. It includes a Kill Box feature that prioritizes threats, a SitRep tool to provide threat context and reporting as well as easy, intuitive threat search functionality.
"Enterprises today are grappling with Defense in Doubt," says Scott Chasin co-founder and CEO of ProtectWise. "The traditional defense in depth approach has left security professionals with a costly daisy chain of endpoint solutions that provide only a point-in-time view of threats and emit a tidal wave of security alarms with no context or correlation across solutions. By shifting network security to the cloud, we make it possible to leave this outdated, ineffective model of enterprise network security behind".
ProtectWise is built on a scalable, secure and efficient cloud-based infrastructure that collects and analyzes data from a number of small, lightweight software sensors which can be deployed anywhere on the corporate network. The sensors use-patent pending technology to optimize and compress network traffic and replay it to the company's cloud platform to provide a single, source of threat intelligence. More information is available on the ProtectWise website.
Image Credit: sommthink/Shutterstock
-

Making it easier for developers to monetize their apps [Q&A]
Publié: mai 25, 2015, 11:45am CEST par Ian Barker

Anybody can develop a mobile app, but making money out of it is another matter. Accepting adversing is a popular route but it involves linking the app to a specific network and that means making code changes if you decide to switch at a later date.
Estonian company MoneyTap is aiming to change that and put the developer in control. We spoke to the company's business development manager Pavel Goryakin to find out how.
BN: Why do traditional ad networks fail to deliver?
PG: Ad networks have limited coverage. More often than not, their demand is tied to a certain territory and a fixed group of local advertisers. Networks are committed to deliver the best traffic out there to these specific advertisers, albeit there may be a higher bidder on the market. That's how game developers potentially miss out on better demand and lose money.
Besides, a single ad network cannot guarantee optimal fill rate. Any malfunction or failure to render an ad at a given point results in revenue losses all the same. Whereas other, albeit lower paying, networks could pick up the request and fill the channel. One soldier does not make a battle in this business.
Now, let's take a look at it from the user prospective. One network means the same advertisers and, not surprisingly, same ads all along. However loyal, any gamer grows weary of seeing identical content, which results in a diminishing click-through rate and jeopardized user experience. A slippery slope, isn't it?
BN: What makes MoneyTap different?
PG: MoneyTap is not an ad network, it's a developer-made tool for optimizing developer revenues. Its goal as a supply side platform is to get the utmost out of 250+ ad networks, and we employ quite a few smart techniques to achieve that.
We don't deal with direct advertisers and have no commitments to the brands whatsoever, so we just sell the developer’s inventory at the best CPM rate in every given region, no matter what. Unlike the competing mediating solutions or separate ad networks, we always backfill with the next highest bidder if the top pick network fails to deliver an ad.
MoneyTap is a turnkey monetization solution that lifts the burden off the publishers so they can focus on R&D. The only thing developers have to do is integrate a single comprehensive SDK, and they are all set.
Here's what we do for the app publisher:
- Come up with UX and ad placement recommendations to ensure seamless impressions and user satisfaction
- Analyze the app’s traffic against the entire pool of ad networks, evaluate the results, define priorities and build custom waterfalls
- Create IDs for all ad formats in all ad networks
- Communicate with ad networks on technical and accounting issues
- Track third party SDK updates and roll them out in subsequent iterations of MoneyTap SDK.
BN: So there's no recoding required in order to switch ad networks?
PG: Once MoneyTap SDK is integrated, we take charge of all network management issues. All third-party network integrations are performed on the MoneyTap sever side, so the developer doesn’t have to waste time and bloat the app code to add yet another network. It's already there. A single SDK delivers multiple networks.
BN: Which platforms does it support?
PG: MoneyTap supports iOS, Android and Unity platforms.
BN: How are payments handled?
PG: MoneyTap goes the extra mile to facilitate developers' accounting. We collect payouts from 250+ networks and deliver the net payment to the developer.
BN: Is it easy for developers to see how well they're performing?
PG: The system displays transparent revenue reports easily filtered by app and region, so developers have a clear insight into their finances.
Image Credit: nopporn / Shutterstock
-

UK elderly and disabled are missing out on Internet use
Publié: mai 22, 2015, 1:31pm CEST par Ian Barker

According to new figures released by the UK's Office for National Statistics (ONS), in the first quarter of this year 86 percent of adults had used the Internet in the last three months, up one percent from the same period in 2014.
That means that 11 percent (5.9 million people) have never used the Internet. But this percentage is much higher for the disabled, a group where 27 percent of adults (3.3 million) had never been online. There were also 0.5 million disabled adults who had last used the internet more than three months ago, making up 48 percent of the total 1.1 million lapsed internet users.
Looked at geographically, the South East has the highest proportion of recent Internet users (90 percent) and Northern Ireland is the area with the lowest proportion (80 percent). The South East also has the fewest lapsed users.
Age plays a big part in whether or not Brits use the Net according to the figures, almost all adults aged 16 to 24 years are recent Internet users, in contrast with just 33 percent of adults aged 75 years and over. Although the proportion of adults aged 75 years and over who have never used the Internet, has decreased from 76 percent in quarter two (Apr to June) of 2011 to 61 percent in quarter one 2015.
Adults aged 75 years and over also have the highest rate of lapsed internet users at six percent, compared with 0.3 percent of those aged 16 to 24. The ONS report says, "This suggests that, although more adults aged 75 years and over are becoming internet users, they are not necessarily continuing to use the internet". Just over half of the 5.9 million adults who had never used the Internet were aged 75 years and over.
The full report is available to download from the ONS website.
Image Credit: PathDoc/Shutterstock
-

Top lessons from data breach investigations
Publié: mai 22, 2015, 12:43pm CEST par Ian Barker

Data breaches are an all too common part of our landscape today, but are we learning the lessons from them to make our systems more secure?
The 2015 Verizon Data Breach Investigations Report found that there were nearly 80,000 security incidents -- including more than 2,100 confirmed breaches spanning 61 countries in the past year. Security solutions company Rapid7 has produced an infographic of expert takeaways from the report.
It reveals that credentials are still the number one attack method and that it still takes too long to detect a breach with an average of 205 days. Also vulnerabilities are not being patched soon enough, with over 99 percent exploited more than a year after publication.
Phishing is an effective means of attack too, 23 percent of users admit to opening phishing emails and 11 percent click on attachments. Almost 50 percent open emails and click on phishing links within the first hour.
Trey Ford, Global Security Strategist at Rapid7 says, "The maturation of cybersecurity has halted – and right now, that’s largely the result of a self-fulfilling prophecy. When breaches occur, there’s a general lack of root-cause analysis being performed. But even when we do have root-cause findings, the common points of failure are generally not shared, essentially sealing the fate of other organizations to repeat the same mistakes. This year's DBIR shines a very bright light on the lack of information sharing across the industry. In the coming year, I hope to see a focus on the effectiveness on controls – what failed, what was missing, what was defeated".
There's more information in the full infographic which you can see below.

Image Credit: Sergey Nivens / Shutterstock
-

Are our industrial and infrastructure systems safe from cyber threats? [Q&A]
Publié: mai 21, 2015, 4:48pm CEST par Ian Barker

Industrial control systems like those used to run the electricity distribution grid are vital to the economic well being of any country. But protecting those systems needs a different approach from normal enterprise security.
In the US the North American Electric Reliability Corporation (NERC) is the body charged with ensuring grid reliability. But the NERC's critical infrastructure protection (CIP) standards call for only standard firewall use. Is this putting the grid at risk from hackers or terrorists? We spoke to Andrew Ginter, vice president of industrial security at Waterfall Security Solutions to find out more.
BN: How worried should we be about attacks on industrial control systems (ICS) and national infrastructure?
AG: I'm very much worried. Modern attacks have demonstrated repeatedly that they can punch through corporate-style cyber defenses, more or less, at will, and it is corporate-style defenses that are deployed at the majority of critical industrial infrastructure sites. This is a mistake. IT can restore damaged systems from backup. There is no way to restore a damaged turbine or a boiler from backup. There are industrial sites that understand all this and have taken appropriate steps to defend themselves, but the vast majority of sites are not protected thoroughly enough.
BN: Should enterprise IT and ICS be kept completely separate? Why connect ICS to the Internet at all?
AG: There are too many ways to profit from ICS data to keep it locked up and inaccessible. For example, if business systems can determine how often and how long each piece of costly equipment has been used, we can delay maintenance until it is really needed rather than maintain the equipment every few months whether it needs it or not. This predictive maintenance application of ICS data alone, integrated with HR personnel scheduling, spare parts ordering and other business applications, is estimated to save the average industrial facility between three and seven percent of total operating costs. In some industries, this is the plant's entire operating profit. There are many other uses for industrial data.
BN: What's wrong with using a conventional firewall?
AG: Firewalls are IT technology and porous by design. Firewalls let both good and bad communications through. Firewalls are designed to let Web requests, responses, email and remote control sessions through. Remote control is the number one modern attack method. When a firewall is hacked, misconfigured or its credentials stolen, the "protected" network is finished. I could go on. Firewalls simply aren't strong enough to protect industrial sites.
BN: What is unidirectional security?
AG: Unidirectional security gateways give business systems access to industrial data while protecting industrial networks in ways that firewalls simply can't. The gateways let nothing at all back into protected networks -- it doesn't matter how smart the attackers are. If some attacker across the Internet, or some corporate insider, gains access to each and every password on both corporate and industrial networks, there is physically no way to send any sort of attack back through the gateways. No mistake in gateway software protections can put the operation of the industrial network at risk. Remote control attacks simply can't work.
IT-style security is fine for IT networks, but, for computers controlling costly, powerful industrial processes, we need at least unidirectional protections.
BN: Surely technology is only part of the picture, isn't part of the solution always going to lie with training and awareness?
AG: Yes, of course. Unidirectional security gateways eliminate one very dangerous threat vector, namely network attacks from corporate networks and through corporate networks from the Internet, but there are no silver bullets when it comes to security.
That said, what good is training people not to pick up USB sticks in the parking lot if any hacker who wants to sabotage the plant can simply weave a connection straight through porous firewalls? Unidirectional gateways make investments in training and awareness more effective. With the industrial firewall "barn door" well and truly wiped out, investments in "barring the windows" with training and awareness programs suddenly pay much bigger dividends.
BN: Does government need to act to enforce stricter controls on ICS?
AG: That's a tough one. Security is doing whatever we need to do to address safety and reliability risks to complex, powerful industrial processes. Compliance is doing whatever somebody else tells us to, whether it's useful or not. When governments specify detailed regulations, such as the NERC CIP rules for the electric grid, many businesses respond by hiring lawyers to run their security programs. These programs quickly transform into minimal compliance programs -- do as little as possible to meet the letter of the law.
I would rather see government agencies publish clear guidance identifying threats and explaining how best to address those threats with strong security programs and technologies, such as unidirectional security gateways. Governments should use their influence and expertise to encourage strong security programs, not mandate minimal compliance programs.
Image Credit: Meryll / Shutterstock
-

How we’re bringing our texting habits into the workplace
Publié: mai 21, 2015, 3:36pm CEST par Ian Barker

SMS messages have been a part of our personal lives pretty much since mobile phones first became available. But what impact does texting have on our working lives?
Cloud communications provider RingCentral has released the results of a survey looking at how SMS is being used in the workplace.
Of the 500+ people surveyed 78 percent have between one and four messaging apps on their phone. Over half use two or three apps on a daily basis so it’s perhaps not surprising that 43 percent have sometimes felt a communication overload with too many apps to check for messages.
SMS is widely favored over other apps like Facebook Messenger with 72 percent preferring to text rather than message. 74 percent find texting easier while 56 percent find it faster.
47 percent of all respondents receive between one and 20 texts per day while 31 percent receive 21-40 texts, however, for business users this figure rises to 37 percent. Ten percent of all users and 12 percent of business users receive 60 or more text messages per day.
Business users seem to send fewer texts though, over half of all users (52 percent) send 1-20 texts a day (only 47 percent for business users). 47 percent of all users send 21-60+ texts a day but only 42 percent of business users send this number.
Texts are mostly used for quick responses (71 percent), though 29 percent use them to conduct full conversations. 38 percent are willing to put themselves at risk by texting while driving. Emojis are creeping into business communications too, with 57 percent admitting to sometimes using them.
The overall picture then is that texting has made it into the workplace and workers feel they need to stick to the same protocol and norms they would in personal conversations -- making quick responses, using emoji and so on. This is leading to communication overload and a general lack of protocol surrounding texting at work.
You can see a summary of the findings in infographic form below.
Image Credit: Bloomua / Shutterstock
-

Fastest in-memory database now available to all with Community Edition
Publié: mai 20, 2015, 5:06pm CEST par Ian Barker

The growth in use of big data is putting increased pressure on databases to aggregate and report on information in real time.
In response real-time database specialist MemSQL is launching a new release -- MemSQL 4 -- which further extends the company's mission of providing enterprises with a real-time database solution that reacts fast, improving business performance in areas such as the Internet of Things, financial services and mobile applications.
In addition a new Community Edition makes the world's most sophisticated in-memory database freely available to global users. MemSQL Community Edition provides unlimited capacity and scale and full transactional and analytical features. This means that anyone can access MemSQL to achieve the speed and scalability needed to process and analyze real-time data.
"In our interactive and connected business environment, companies must capture and analyze both real-time and historical data faster and more efficiently than ever," says Eric Frenkiel, co-founder and CEO of MemSQL. "Two years ago, we introduced the general availability of MemSQL. Today, we have not only made our software more powerful for enterprises to derive new insights in big data, we have extended it freely to companies seeking in-memory database analytics".
MemSQL 4 features updates in core engine innovation, management and monitoring functionality as well as ecosystem integrations. Highlights include geospatial capabilities, wider support for advanced analytics with an enhanced optimizer and expanded SQL functionality, and easier integration with Apache Spark, Hadoop file system and Amazon S3.
Application and solution sets are available for digital advertising, financial services, retail, public sector, high technology, media, communications and data-driven industries. In addition MemSQL applications including real-time analytics, risk management, personalization, position tracking and monitoring help companies make fast, intelligent decisions based on their data.
The latest release is available from today, for more information visit the MemSQL website.
Image Credit: Jirsak / Shutterstock
-

Event management platform adds website builder
Publié: mai 20, 2015, 3:03pm CEST par Ian Barker

Earlier this year we reported on the launch of the Bizzabo platform designed to make life easier for people who manage events.
Now Bizzabo is extending its offering to include a website builder aimed specifically at event planners, giving them the ability to build a custom event website within minutes, with no prior coding or design experience required.
Bizzabo's Event Website Builder provides organizers with the ability to build a professional website that is fully integrated with the wider event management software in order to streamline planning and help support event organizers' need to keep event information across platforms up to date.
The event websites allow event managers full control over their web presence while at the same time providing attendees with a seamless registration experience. The overall result is an improved event experience with event planners free to focus more on success than maintenance.
"Developing a website builder was a crucial component of our event success platform," says Bizzabo CMO and Co-founder, Alon Alroy. "Event organizers deserve a toolkit that allows for the ultimate event planning experience from beginning to end, smoothly and without interruptions. Until now, many organizers are tasked with comparing seven to ten different tools throughout the lifetime of their event. By utilizing Bizzabo's Event Success Platform, including our new Website Builder, every stage of the planning process can be easily tracked and implemented, right down to each event’s social footprint. The integration of the platform is smooth, and any agenda or schedule change is synced across the event website and event app immediately, along with all attendee touch points with a simple click".
Features of the website builder include the ability to host the site at any URL, ticket sales directly from the website without redirecting to a third party, and control over look and feel by selecting from a wide range of templates, fonts, colors, and elements. Features such as a sponsors section and countdown clock can be added quickly using drag-and-drop. Sites can be live within minutes without the need for developers or web designers and are fully responsive for smartphones and tablets. Changes can be made in real time and custom HTML sections added if required.
For customers already using Bizzabo's event platform the website builder is available free of charge. More information is available on the company's website.
-

Security is the major challenge to enterprise mobility goals
Publié: mai 19, 2015, 4:28pm CEST par Ian Barker

More and more companies are turning to apps to improve business mobility, but 67 percent cite security as the top challenge to achieving their goals.
This is among the findings of the 2015 Enterprise Mobility Report from app management specialist Apperian. Although security is the major challenge others include determining return on investment, lack of budget and reaching BYOD or unmanaged devices.
The most common reason for moving to mobile is improved business processes, given by 64 percent of respondents. Increased user satisfaction and competitive advantage were both selected by 60 percent of respondents.
Productivity apps are believed to have the greatest impact on return on investment, followed by field service apps, selling tools and HR apps. Custom-built apps specific to a particular industry may have a greater impact, but not all companies have such apps yet.
The survey also shows that many respondents don't believe they have enough visibility into how their apps are being used. Just over half of respondents can tell which apps are being used, while 48 percent can see who is using them and 42 percent can see how frequently apps are used.
Developing their own apps seems to be the key to successful mobile deployment. 65 percent of those who were most satisfied with their mobility strategy had developed internally. Overall, 60 percent of organizations have internally developed apps in place, compared with 42 percent in the 2014 survey.
The report concludes that to take advantage of enterprise mobility companies need to: focus on their core business when developing apps, support business processes with internal development, invest in technology to manage their apps, develop an internal marketing program to drive app adoption, think of their users as customers and invest in analytics.
The full report is available to download from the Apperian website.
Photo Credit: lucadp/Shutterstock
-

New enterprise file management suite takes mobile first approach
Publié: mai 19, 2015, 3:49pm CEST par Ian Barker
According to research by IDC the number of enterprise applications optimized for mobile is set to quadruple by next year as businesses seek to improve workflow across the organization.
Adaptive enterprise file services specialist Egnyte is unveiling its new enterprise mobile suite that's optimized for business users. It allows them to seamlessly access, manage and share online and offline data from both cloud and on-premises storage.
Available for Android, iOS and windows as well as being optimized for the Apple watch, Egnyte enables users to seamlessly manage online and offline content, rename files, view high-res thumbnails and previews, and receive notifications when large files or folders are being uploaded and downloaded.
For administrators it’s easy to add new users and manage permissions for users and groups, all from mobile devices. Apple Watch users can manage offline files, monitor the status of uploads and downloads, and will soon be able to get notifications when files are edited or commented on by other team members.
"As we reinforce our mobile-first enterprise file services approach, it will be vital for organizations to provide employees with a full suite of enterprise-grade applications for secure access to any content in the cloud and on premises," says Rajesh Ram, chief customer officer and co-founder of Egnyte. "Our enhanced mobile applications, with the addition of functionality for wearables including the Apple Watch, are able to combine a user-friendly experience for employees and contractors with enhanced security features IT can trust in today's always-on business environment".
Egnyte is available now from the Google Play store, from iTunes and from the Windows Phone app store.
-

DataStax launches database platform designed for mixed workloads
Publié: mai 19, 2015, 3:03pm CEST par Ian Barker

Enterprises currently have a greater volume and variety of data available to them than ever before, but this leads to increased pressure to exploit that data effectively to make timely business decisions.
Apache Cassandra database specialist DataStax is today launching DataStax Enterprise 4.7 which offers integrated enterprise search, analytics, security, in-memory computing, and database management and monitoring, making it ideal for mixed workload environments.
"As the amount of data collected by enterprise web and mobile applications continues to grow at an immense rate, it's critical to have database systems in place that are capable of providing instant insight into that data," says Robin Schumacher, Vice President of Products at DataStax. "With DataStax Enterprise 4.7 and OpsCenter 5.2, users can search, analyze, secure and manage all their online data in one platform and ensure it's immediately available for real-time decision making".
DSE 4.7 includes a new certified version of Apache Solr and DSE's 'Live Indexing' capability that makes new data immediately available for search. It also uses Cassandra's native ability to run across multiple data centers and cloud availability zones, which provides constant uptime for search operations and allows results to be sent back to users in the fastest possible time.
Search and analytics tasks can run simultaneously on the same machine, thus delivering the potential for lower hardware expenditure and improved cost of ownership. Intelligent query routing allows search queries to be transparently routed to the best performing machines in a cluster. It also has the ability to customize how failed queries are handled, delivering either partial results or a full retry automatically.
DSE 4.7 delivers upgraded data at rest protection by providing an option to store encryption keys, needed to unlock the data for use, on servers outside the DSE cluster. Plus OpsCenter now supports the use of LDAP and Active Directory to manage administration security, making it easy to control what administrators and operations personnel can do on database clusters.
New visual features in OpsCenter 5.2 make it easier for admins to provision, administer, and monitor multi-site databases, while new visual performance dashboards deliver expert recommendations help simplify performance tuning.
DSE 4.7 can be downloaded now from the DataStax website and OpsCenter 5.2 will be available in late June.
Image Credit: Ermek/Shutterstock
-

GV18 Aplus smartwatch -- what can you expect for $35? [Review]
Publié: mai 18, 2015, 5:32pm CEST par Ian Barker

It's always the way with technology that it starts out expensive then tumbles in price as more manufacturers enter the field. With smartwatches that fall in price has come pretty quickly as Chinese manufacturers have jumped on the bandwagon.
The last budget smartwatch we looked at proved pretty impressive for the price. The GV18 Aplus is cheaper still and yet packs in even more features. So, is it cheap and cheerful or cheap and nasty? Let's find out.
The watch comes in a sturdy cardboard box along with a USB cable, a battery and a Chinese/English instruction leaflet. It's compatible with Android phones and comes with a whole host of features including NFC, a camera, sleep monitoring, anti-theft feature and more.
You need to insert the battery before you do anything else. You're on your own with this as it's not mentioned in the instructions at all. There's a screw on the back presumably to hold on the cover but on our review sample it just went round and round without biting on anything. Even with the screw loose -- stop making up your own jokes! -- you need to lever the back off and there's a nagging worry that you might damage something.

Battery installed you need to plug it into a USB port for a couple of hours to charge it up. The socket is covered by the obligatory rubber flap. Once plugged in it's recognized by a PC as a storage device making it easy to download any pictures you've taken. While it's charging you can download the sync software to your phone by scanning the QR code in the instructions. This is a bit disconcerting as the initial setup screens are in Chinese, it’s also not on the Play Store so you'll need to compromise your security settings to install it.
The watch is a chunky design and quite weighty, but whilst the front is stainless steel the back is plastic, the strap is a soft rubbery material that's comfortable to wear. However, that screw is a bit annoying as it stands slightly proud of the surface.
Okay time to switch on, you're greeted with an animation and a slightly too loud jingle. The screen is nicely responsive though and bright enough for most use, although it can be hard to see in bright sunlight and there are only a limited range of color options. As with most smartwatches you need accurate fingers as it's easy to press the wrong button especially on things like the settings screens and calculator.
The watch has some useful standard features including a pedometer -- "your private health butler" as the website rather charmingly describes it -- and a sedentary warning which tells you if you've been sat still for too long. All of these are easy to set up and work reasonably well. It's also possible to install a SIM card in the watch itself and use it independently of your phone.
The built in camera is only 0.3 megapixels and the resulting images aren't brilliant quality with washed out colors and limited depth of field as you'll see from the full-size example below. There's also a long delay after taking a picture before the watch will let you do anything else. If you don't want to use the built-in camera there's also the option to control your phone's camera remotely.

At just under $35 the GV18 is undoubtedly cheap, and with that plastic back, dodgy battery cover and low-res camera it feels it. On the other hand all of the day-to-day functions like reading messages or accepting calls from your phone work well enough. If you have an Android phone and want to try out a smartwatch without straining your budget it might be worth a look but don't expect premium quality.
The GV18 Aplus is currently on sale for $34.79 and our review sample was provided by GearBest.com.
-

Traditional security approaches produce too many false positives
Publié: mai 18, 2015, 3:32pm CEST par Ian Barker

According to 62 percent of IT professionals traditional security approaches produce too many alerts and false positives for them to handle.
This is among the findings of a new study from research firm Enterprise Management Associates (EMA), sponsored by machine learning and automation specialist Prelert, which shows that 25 percent of organizations know they experienced a breach or significant cyber attack that incurred loss last year.
When asked how they felt about security analytics, 70 percent of respondents indicated that they either have an investment in the technology or would have an investment if it weren't for insufficient resources. Of those IT professionals already using security analytics, 95 percent were confident of their ability to detect a security issue before it had a significant impact.
"Security analytics, though a relatively new field of technology, are the next step in detection and response technology. Machine-learning algorithms and analysis techniques have advanced far beyond the capabilities of what was available in the commercial markets only 2-3 years ago," says David Monahan, Research Director at EMA.
More than half of respondents (57 percent) say that security analytics provides unique or specialized data for context -- data that's needed to identify today's stealthier security threats. Better data flexibility and the adaptability to address a wide range of requirements was cited by 36 percent the top reason for using analytics. Other reasons named were better data correlation and fidelity for creating responses (36 percent), and lowering false positives (29 percent). A further 29 percent see security analytics as a way to reduce incident response time.
'Alert blindness' on traditional systems continues to be a major issue, with 62 percent seeing too many false positives or having too many alerts to handle, with the result that they don't feel confident in the security protections they have in place. Another 38 percent say they aren't confident because there's too much uncorroborated data and a lack of context about that data.
"Lack of knowledge about what is really a security threat and what needs your immediate attention is hurting the ability of IT security teams to understand and respond quickly and effectively," says Mike Paquette, VP of Security Products for Prelert. "Organizations need machine learning-based tools to cut through the clutter and detect threat activity before it becomes a problem for customers".
The full report Data Driven Security Reloaded is available to download from the Prelert website.
Photo Credit: Sergey Nivens/Shutterstock
-

Shoppers use mobile mainly for research rather than purchasing
Publié: mai 18, 2015, 12:30pm CEST par Ian Barker

Businesses are using analytic tools to gather information online, through digital and social channels, as well as call center data, to get to know and build a closer relationship with their customers. However, a survey by customer experience specialist TimeTrade reveals that mobile channels in particular are mostly used for research rather than buying.
The survey looks at consumer buying habits and how retailers need to adapt and provide a better customer experience in order to succeed. It shows that retailers are realizing that a highly personalized in-store experience leads to a lasting impression and creates brand loyalty.
This has led to traditionally online only retailers like Amazon seeking to open up brick-and-mortar stores in the hope of providing a more personalized experience. At the same time consumers are admitting that in terms of their shopping habits, they prefer the in-store experience so they can feel and touch items and most importantly, make final purchase decisions.
Key findings are that many people still prefer the in-store experience with 65 percent saying that if an item they want is available online or in a nearby store they prefer to shop in the store. The main reason cited for this is that they like to 'touch and feel' products.
The survey also finds that despite all its hype purchasing on mobile is slow to take off. When looking to buy something only 13 percent will buy from their mobile device and 42 percent have never purchased from a mobile device at all. However, mobile is an important part of the shopping process with 50 percent using it to research products, 50 percent to compare prices and 46 percent to find the nearest store.
Among 18-34 year-olds, 92 percent will walk into a store either knowing exactly what they want or having narrowed it down to 2-3 products via online research. Important for retailers though is that 87 percent of this age group will buy more than they intended to when shopping in a store. In-store expertise is still important though with 90 percent of all respondents saying they're more likely to buy when helped by a knowledgeable associate.
The report concludes, "In order for retailers to survive and retain market share, they must be progressive in how they create the in-store experience, using modern-day technology while providing prompt service, all the while knowing a customer’s needs before they even enter the store".
The full survey is available to download from the TimeTrade website.
Image Credit: Slavoljub Pantelic / Shutterstock
-

Payment card industry must meet new security standards by end of June
Publié: mai 15, 2015, 4:13pm CEST par Ian Barker

Companies that accept credit card payments and process cardholder data are facing some significant changes that they will need to comply with by June 30th.
This is a result of new Data Security Standard requirements from the Payment Card Industry Security Standards Council, known as PCI DSS 3.0. This will see many of the things that were previously only seen as best practice become mandatory.
Key changes include a requirement for businesses to verify that broken authentication and session management are addressed. This will help prevent unauthorized individuals from compromising legitimate account credentials, keys or session tokens that would otherwise enable the intruder to assume the identity of an authorized user.
In addition any third-party service providers with remote access to customer premises must use a unique authentication credential for each customer. Providers must also go through additional testing to examine authentication policies and procedures and interview personnel to verify that different authentication is used for access to each customer. Third-party service providers must acknowledge in writing to customers that they are responsible for the security of any cardholder data they process or store.
Businesses must add protection for in-store point-of-sale devices too. This includes the need to train employees on how to be aware of suspicious behavior and to report tampering or substitution of the devices.
Finally, businesses need to implement a new penetration testing methodology based on industry-accepted approaches. Penetration testing must cover the entire card data environment and critical systems as well as validate any segmentation and scope-reduction controls.
There will be further tightening for online transactions thanks to the National Institute of Standards and Technology (NIST) guidance that SSL is no longer considered adequate for transport layer security and recommending migration to TLS 1.2 instead.
PCI DSS 3.1 will require organizations accepting payments online to use TLS. This should have minimal impact on consumers provided they're using a recent browser version.
Michael Aminzade, VP Global Compliance & Risk Services at Trustwave says, "Organizations had 18 months to comply with PCI 3.0 because of the need to replace kit and update software on retail sites. We expect a tighter timeline for TLS implementation as it's easier for merchants to turn off earlier software versions and update security certificates".
More information about PCI DSS standards and what they mean for businesses is available on the Trustwave website.
Image Credit: Sedlacek / Shutterstock
-

Consumers are being outsmarted by their washing machines
Publié: mai 15, 2015, 1:17pm CEST par Ian Barker

Given all of the hype surrounding the Internet of Things and intelligent devices you might think that consumers would be keen to make use of all the latest options.
However, a new study by UK online retailer Appliances Direct suggests that for many people even mastering their washing machine is too much.
The survey of 1,000 British homeowners shows that only 1 in 10 users surveyed made 'regular' use of all of the settings available to them, while only 21 percent understood when to use every setting.
Despite the average British family running on average 250 wash cycles each year and over 2.6 million washing machines being sold annually, 20 percent of homeowners surveyed claimed to use only one of the settings available to them most of the time. 70 percent regularly use between just two and four settings. 1 in 3 respondents confessed to 'rarely' using the 30 degree setting meaning they could be unwittingly wasting money and energy by using a higher temperature setting than is required.
A startling 60 percent admitted to making use of professional laundry services for some prized, delicate items, when they could utilize one of the features of their machine to do it themselves.
"With household bills on the rise, it’s important that families are making the most of their washing machines and other household appliances to keep costs to a minimum. The numerous settings are there to make life easier for users, and to ensure items are being washed in the best way possible, such as the often featured 'Heavy Duty' setting -- a welcome option for those looking to deep clean towels, bed sheets and perhaps gym-wear," says Mark Kelly, marketing manager at Appliances Direct. "Although the settings available on the latest models are there to suit the needs of the modern day family, they must be fully understood in order for the product to reach its full potential -- and those who take the brief time required to acquaint themselves with these options will find they reap numerous benefits, whether it’s longer lasting garments, lower bills or more effective washes".
When you inhabit a high tech world it's easy to assume that offering more features is always better, but it seems that approach may currently be lost on consumers. Does the answer lie in better education and clearer instructions? Or perhaps an even smarter machine that can read garment care labels? The answer might be to make a much simper machine with just the settings people actually use -- the first manufacturer to do that could clean up.
Image Credit: Ljupco Smokovski / Shutterstock
-

How the cloud marketplace is shifting to target specific niches [Q&A]
Publié: mai 15, 2015, 12:16pm CEST par Ian Barker

Spending on Platform-as-a-Service (Paas), Software-as-a-Service (SaaS) and Infrastructure-as-a-Service (IaaS) is forecast to reach $118 billion this year, and it's clear the cloud is now big business. Companies are fighting to enter the space with new industry- and marketing-specific offerings. But what effect will this have and will it worry the big players like Amazon Web Services?
We spoke to Scott Swartz, CTO of BUSS at Ericsson and founder of MetraTech, an enterprise billing specialist recently acquired by Ericsson, to find out more about the state of the IaaS space.
BN: Can we expect to see current big players, such as AWS, losing share to more specific offerings?
SS: The cloud market is still evolving, and there is plenty of opportunity for nimble players to take market share from leaders. For example, the new battleground for enterprise customers will be value-added IaaS and not simple vanilla offerings. Winners will be determined based on their abilities to provide a platform for partners to build, run and integrate their products and services into the ecosystem. It is a race to develop a network of partners that deliver the desired third-party apps integrated with an IaaS service. The enterprise cloud also creates opportunities for new companies and new alliances targeted at specific verticals. The original players will see competition from marketplaces that deliver industry-specific services. To date, even with the hype, the cloud has been about tackling low-hanging fruit in the test and development areas, but we are now actively seeing the movement of production workloads to the cloud. Also, the ongoing convergence of the cloud and Internet of Things will create opportunities for platforms to support smart cities, energy and utilities, transportation, security, financial services, retail services and many more fields.
BN: Is there a danger that an increasing number of companies targeting specific sectors will lead to a fragmentation of the cloud market?
SS: The market will still be dominated by big players, since they will have the reach and pull to deliver an easily consumable and serviceable application marketplace on top of IaaS cloud. There will be opportunity for targeting offerings to specific industry sectors as specialist clouds (financial services and healthcare are obvious ones given their unique requirements). However, I believe the fragmentation will likely be how partner offerings are managed as part of IaaS. How integrated the partner services will be and how easily accessible and serviceable these are will have a big impact on traction with enterprises. In addition, partnerships need to include services targeted at developers building applications on a provider’s cloud. We are still at the infancy stage when it comes to cloud maturity; the doors will open based on the richness of the partner marketplace.
BN: If solutions become very specific, isn't there a danger of losing some of the advantages of moving to the cloud in the first place?
SS: Once you move past commodity cloud services and start consuming provider-specific services or content you run the risk of not being able to run the load on another cloud. That lock-in may or may not be worth it and that equation will likely change over time. If a cloud provider has added so much value that it’s worth being locked in for certain loads, then they’ve done their job. The beautiful thing about competition is that it drives innovation and, within the cloud, you have the ability to try valued-added offerings quickly and inexpensively.
However, locking yourself to a specific cloud can be a slippery slope. It's critical that you have strong architectural governance to identify and manage lock in proactively. Specifically, you need to abstract and isolate areas of lock in. There are a multitude of frameworks that facilitate this, but, if the one you pick doesn’t provide the correct level of abstraction, you need to look at what other clouds are offering to ensure that your implementation is as generic as possible. It’s also very important to partition the automated tests for the locked in functionality so that you can test on other clouds to ensure the lock in hasn't crept into areas that you didn't except -- that happens with slippery slopes.
If properly managed, specific solutions can provide you with a strategic advantage and a manageable downside.
BN: Will new targeted clouds kill off traditional data centers?
SS: Commodity clouds have already started putting a dent in traditional data centers. The benefit of just paying for utilization with minimal or no infrastructure or software licenses while also gaining elasticity is easily understood. With industry-specific cloud providers, the ability to meter out independent software vendor (ISV) application workloads and the requisite licensing of applications and content makes the cost/benefit equation even more compelling.
It is unlikely to be all or nothing. Hybrid cloud scenarios will continue to be dominant. Depending on the enterprise, there may be regulatory or data sovereignty issues that prevent you from moving databases to the cloud, but you may use a point-to-point VPN from your data center to the cloud provider to connect to your on-premise database cluster.
BN: What are the pitfalls enterprises should be aware of when planning a shift to a cloud-based solution?
SS: Security, regulatory and data sovereignty issues, and cloud sprawl are well documented pitfalls. As more production workloads are moved to the cloud, uptime and service-level agreements (SLAs) will become increasingly important. In addition, the proliferation of value-added and industry-specific clouds creates opportunities, as well as the potential for inappropriate lock in. Picking the right cloud will become more complex because there will be business in addition to the existing technology and operational implications.
BN: What effect will new technologies like the Internet of Things have on the provision of business services?
SS: The convergence of cloud, IoT and big data will have a massive impact on the technology and business services landscape as we know it. Things are moving from simple monitoring to providing critical and time sensitive information that can be utilized for analytics and corrective, proactive automated action. The vast amounts of data generated means that the cloud is playing the critical role of enabler for smart things to operate more effectively, and for data to be used by machines themselves to self-diagnose and self-repair. Analytics platforms for managing data produced by intelligent machines and sensors will convert data from machines and turn it into new offerings for consumer and enterprise customers.
An industry-specific cloud provides an opportunity for competitors to pool appropriately cleansed data to gain better insights. This data and the associated analytics can be sold to third parties.
We will see entire industries including aviation, health care, energy production and distribution, transportation and manufacturing have the ability to manage and operate machines in the cloud. We're already seeing a movement from buying to leasing applications on the cloud, as well as the bundling of pooled industry-specific data and analytics, in these industries.
Photo Credit: everything possible / Shutterstock
-

Bots generate more internet traffic than humans
Publié: mai 14, 2015, 4:03pm CEST par Ian Barker

According to a new survey from cloud security provider Distil Networks humans accounted for only 40.9 percent of web traffic in 2014 with the remainder accounted for by bots.
This compares with 50.8 percent human traffic in 2013, however the good news is that 'bad bot' traffic is down from 24.22 percent to 22.78. The rise in good bot traffic that makes up the difference is thought to be from more aggressive indexing by Bing and new search engines in 2014.
But although the percentage of bad bot traffic is down, Distil still saw 23 billion threats in 2014. The bad bots are also increasingly mimicking human behavior to evade detection, only 59 percent now behave like bots. Small sites suffer most from bad bots as they account for 32.04 percent of their traffic. Large sites see more good bots (43.65 percent), though as Distil points out this can still be undesirable due to the amount of traffic involved. Digital publishing and travel websites suffer the most bad bot traffic whilst the good bots account for more traffic on directory and real estate sites.
The rise of mobile has had an influence on the bot landscape too. There are more bots masking themselves as mobile users. The same characteristics that make mobile sites easier for humans to navigate also benefit the bots.
In 2013 Verizon Business accounted for almost 11 percent of all bad bot traffic, but the company has cleaned up its act with only 2.83 percent last year. Amazon Technologies is now top of the list originating 15.07 percent of all bad bot traffic thanks to its presence in the cheap hosting market.
The US with thousands of cheap hosts, dominates the rankings in bad bot origination. However, taken in isolation bad bot volume data can be somewhat misleading. Distil measures bad bots per online user to calculate a country's 'Bad Bot GDP'. On that measure Singapore tops the chart with 152.87 bad bots per user while the US slips to sixth with only 6.34.
The report concludes, "The bad bot landscape continues to evolve rapidly, particularly with the dramatic increase in mobile bot traffic, and an ever wider range of geographic and ISP points of origin. With the advent of cheap or free cloud computing resources, anyone with basic computer skills can download open source software and get into the game". But it notes that most companies still don't have visibility into or control over malicious traffic.
The full study is available to download from the Distil Networks site.
Image credit: Gunnar Assmy/Shutterstock
-

More than 1,000 companies join IBM in the battle against cybercrime
Publié: mai 14, 2015, 11:59am CEST par Ian Barker

Last month IBM launched its X-Force Exchange opening up access to threat intelligence data to help in the fight against cybercrime.
With 80 percent of cyber attacks now coming from organized gangs it's important that the good guys get organized too. IBM has announced today that more than 1,000 organizations across 16 industries are participating in the new threat intelligence community.
"Cybercrime has become the equivalent of a pandemic -- no company or country can battle it alone," says Brendan Hannigan, general manager at IBM Security. "We have to take a collective and collaborative approach across the public and private sectors to defend against cybercrime. Sharing and innovating around threat data is central to battling highly organized cyber criminals; the industry can no longer afford to keep this critical resource locked up in proprietary databases. With X-Force Exchange, IBM has opened access to our extensive threat data to advance collaboration and help public and private enterprises safeguard themselves".
X-Force Exchange has a 700 terabyte threat database -- a volume equivalent to all data that flows across the internet in two days. It includes two decades worth of malicious cyberattack data from IBM as well as anonymous threat data from more than 4,000 other organizations for which IBM manages security operations. Participants have created over 300 new collections of threat data in the last month alone.
In the month since X-Force Exchange’s launch there have been more than 1,000 data queries per day from organizations around the world. These include six of the world's top ten retailers and five of the top 10 banks, as well as top 10 companies across the automotive, education and high-tech sectors. By freely consuming, sharing and acting on real-time threat intelligence from their networks and IBM’s own repository of threat intelligence, users can help identify and help stop threats.
There's a look at the profitability of organized cybercrime in infographic form below and you can find out more about X-Force Exchange on IBM's website.

-

Commvault launches new solutions to speed up cloud adoption
Publié: mai 13, 2015, 4:24pm CEST par Ian Barker

As the pace of cloud adoption accelerates, businesses often come across unforeseen issues that add to costs and may derail projects completely.
Enterprise data protection and information management specialist Commvault is aiming to streamline moving to the cloud with additions to its product suite to enable organizations to get the most from existing investments and accelerate enterprise wide cloud adoption.
Commvault's Cloud Disaster Recovery makes large scale recovery a reality in the cloud, Cloud Development and Test reduces development time and management overhead to improve R&D efficiency, and Commvault Cloud Gateway and Cloud Replication ease cloud data migration and give customers improved choice, flexibility and speed.
"Our customers are moving to operationalize the cloud usage for applications and accelerate the time to value," says Sabrinath Rao, Head of Virtualization, Cloud Business Unit at Commvault. "Our Cloud Backup and Recovery solutions make it much easier for customers to derive value off their cloud investments by deeply integrating the on-premises and in-cloud workflows, starting with the data and then extending out to controlling access and optimizing utilization in the same manner as they do on premise".
Cloud Disaster Recovery enables recovery in the cloud, regardless of platform -- supporting VMware, HyperV, AWS and Azure -- or location whether public, private or hybrid. It also Extends virtual machine provisioning and workflows from on premise into the public/hybrid cloud for consistent, policy-based management. And it enables full data restores to virtual machines in IaaS, making full disaster recovery possible across all workload types.
Cloud Development and Test ties VM provisioning and workflows together and applies them to the management and utilization of development environments in the cloud. In addition to reducing administrative time spent on managing the cloud resources, it provides managers with insurance against runaway bills.
The Cloud Gateway improves overall backup agility, flexibility and performance, extending the protection tier from on premise to cloud. Cloud Replication allows copying directly to cloud storage targets natively making for easier migrations.
More information on Commvault's portfolio of cloud products is available on the company's website.
Photo Credit: Roland IJdema/Shutterstock
-

Millennials are a bigger risk to mobile security than other age groups
Publié: mai 13, 2015, 3:25pm CEST par Ian Barker

Around half of the workforce will be millennials by 2020, but according to a new survey by endpoint security specialists Absolute Software they're likely to present a bigger risk to data security.
The survey questioned more than 750 Americans over the age of 18 who work for a company with 50 or more employees and use an employer-owned mobile device.
Whilst 79 percent of those surveyed prefer separate devices for work and personal use, 52 percent do use their work devices for personal purposes and 14 percent believe their behavior puts their organization's security at risk.
Security isn't their responsibility according to 50 percent of respondents and 30 percent believe there should be no penalty for losing company data. It's when you start breaking down the responses into groups that they become really interesting though.
Whilst only five percent of baby boomers compromise IT security the figure jumps to 25 percent for millennials. 64 percent use their work machine for personal use compared to only 37 percent of boomers, and 27 percent have not safe for work content on their device compared to only five percent.
Position in the organization makes a difference too, with those higher up the command chain more likely to be putting data at risk. Of those at a senior level 76 percent admit to personal use, 33 percent to NSFW content and 26 percent have lost a device in the last five years. At the bottom of the executive food chain whilst 51 percent admit to personal use just nine percent have NSFW content and only five percent have lost a device.
"We conducted this survey with the intention of helping enterprises better understand the current attitudes that employees have towards data security and privacy," says Stephen Midgley, vice president, Global Marketing at Absolute Software. "Armed with this information, our customers can consider user behavior as an additional data point in their endpoint security and data risk management strategies".
The report recommends that to stay safe businesses need to implement a security solution on their devices, train employees on best practices and build policies to address risky behaviors. Midgley adds, "Ultimately, everyone is responsible for protecting sensitive business information. Knowing there is ambiguity between how different users may approach this requirement, IT leaders need to provide meaningful guidance and training that reinforces this collective accountability".
The full report is available from the Absolute Software website.
Image Credit: Syda Productions / Shutterstock
-

IBM helps brands to understand customers
Publié: mai 13, 2015, 12:31pm CEST par Ian Barker

New channels, new markets and changes in device usage make today's marketing environment more complex than ever, and that means delivering the right message to the consumer is increasingly vital.
But according to an IBM/eConsultancy study in April, only 35 percent of consumers say the communications they receive from their favorite brands are relevant and four out of five consumers believe that brands fail to understand them as individuals.
Last week IBM announced it was partnering with Facebook to offer more tailored marketing, now it's adding further design and analytics capabilities as part of its Marketing Cloud to offer businesses an integrated solution.
The new features include IBM Journey Designer, a virtual whiteboard where staff on multiple teams within an organization can collaborate with a single overview of a customer's interactions to make more informed decisions.
IBM Journey Analytics allows marketers to sift through valuable insights about the customer, making it easier for marketers to visualize the journey of the customer then map and design a campaign to help deliver more relevant experiences with greater precision.
IBM Customer Experience Analytics offers a single platform that unifies IBM's Journey Analytics, Digital Analytics, and customer behavior analytics capabilities to give brands a complete overview. Finally, IBM Commerce Insights provides business executives a view into the performance, operation and growth of their digital business.
"Marketers are the gatekeepers to the customer and have the opportunity to understand each individual and guide them on the path through a mix of campaigns designed to nurture brand loyalists. To succeed, however, marketers must embrace technologies that offer them the opportunity to build two way engagements with each customer and deliver a meaningful and relevant experience," says Deepak Advani, General Manager, IBM Commerce. "IBM is providing innovations such as journey analytics to allow marketers to gain insights into customers at depths they could never have imagined just a few years ago. Teams can then turn these insights into campaigns to deliver powerful experiences that engage customers in-context and ultimately build advocacy".
More information on IBM eCommerce solutions is available on the company's website.
-

The challenges of protecting the hybrid cloud [Q&A]
Publié: mai 13, 2015, 11:14am CEST par Ian Barker

With more and more companies storing apps in the cloud and others remaining in-house, security can become something of a headache. On-site security tools are ineffective against web attacks leaving organizations with multiple protection solutions in place.
The launch of hybrid cloud solutions such as Radware's WAF (Web Application Firewall) means it’s possible to protect all systems with just one application but what implications does this have for the enterprise? We spoke to Carl Herberger, VP of Security Solutions at application delivery and security specialist Radware to find out more about the benefits of hybrid WAF solutions and how they can be implemented.
BN: With the rapid rise of cloud use is it fair to say that many companies have taken the leap to the cloud first and only thought about security later?
CH: It sometimes seems that security has become almost an afterthought. IT managers have left a secure, premise-based operating environment in search of agile and cheaper alternatives, but leave with hopes that security would somehow also improve. The overall responsibility of network security for today’s cloud delivered services is still left to those who write the checks for the services and hold those delivering the services accountable. Unfortunately, those security practitioners often fall behind the evolving threat landscape.
BN: Why don't the security practices applied to in-house solutions work for the cloud?
CH: There are three basic principles which help illustrate why an enterprise-security solution will not work easily or at all in the cloud. First, enterprises don’t often concern themselves with tenants. Cloud and managed service environments must isolate an operating environment from other customers, and in-house environments drive feature sets, which are not available in most security tools, such as tenanted reporting, self-service provisioning and various configurations per tenant. Second, Enterprises benefit by having predictable routing and an ability to see 'state' and 'symmetry' on traffic patterns. This provides enterprises with knowledge of their networks, and thus, security. Many Cloud companies don't always have these luxuries, and in as such are at a disadvantage with their ability to learn baselines and take actions. Lastly, enterprises know how to distinguish their legitimate traffic and block the rest. Cloud companies need to be much more tolerant on the types of traffic they allow into their environments, as they have to take into account network traffic patterns of their entire customer base.
BN: Do public and private clouds need a different approach?
CH: It is generally accepted that private and public clouds are different and the intimacy of a private cloud affords the opportunity for better security. It is also generally agreed that as time marches on, the lines between these two environments will blur as new technologies are adopted and the rise of automation and orchestration between various cloud providers becomes paramount.
BN: What are the main challenges of introducing a WAF in hybrid environments?
CH: Generally speaking, there have been two main problems with WAF introductions to environments: introducing network and application disruption (e.g. breaking something which wasn't broken) and the introduction of latency (e.g. slowing the application down). This has been a perennial problem which is now being solved by many powerful out-of-path solutions, however the basic WAFs are still wrought with these 'security' problems. Managing and maintaining the solution has also been a problem. Typically the best WAFs required heavy 'hand-holding' and expert knowledge and don't integrate with solutions in the cloud.
BN: How can companies ensure their systems remain protected during the transition to the cloud?
CH: When transitioning to the cloud, a hybrid approach is the way to go to remain protected. Most businesses simply aren’t positioned to move all legacy applications to the cloud, and starting a hybrid cloud approach does not require a complete migration of traditional IT infrastructure to a public or private cloud. Most companies will retain some internal application delivery infrastructure. Dedicated infrastructures are a luxury and will make most companies uncompetitive vis-à-vis hybrid competitors. The verdict is in about the merits of virtualization and cloud. It unleashes hidden efficiencies that have been elusive to the traditional datacenters of the past. At its core, cloud was designed to take the complexity of virtualization away from the end user and fully enable self-provisioning and speed to service delivery.
BN: What additional challenges do the rise of mobile devices and BYOD present?
CH: Mobile devices, BYOD and the Internet-of-Things will forever extend the attack landscape and operating environments. Soon enough, these devices will soon become centers of processing themselves and they will be conscripted (often without knowledge) to be part of future 'botted' armies. This movement to 'things' which process IT and are connected/interconnected will increase the threat level of the attack landscape and require an immeasurable amount of new security controls.
Photo credit: allepu / Shutterstock
-

EasyAcc DP100 Bluetooth 4.0 speaker [Review]
Publié: mai 8, 2015, 4:51pm CEST par Ian Barker

There are lots of Bluetooth speakers on the market, so which one you choose really comes down to the features you value most. Is sound quality your top priority or is portability and long battery life a bigger attraction?
The EasyAcc DP100 certainly qualifies on the portability front. It's a compact design, about the size of a Coke can, feels nicely weighty and has a rubber base so it won't slip around. The design is quite stylish in matt black with a shiny highlight around the top. There's an on/off switch and sockets for charging and aux-in at the back. Playback controls are operated by a grey, rubbery button on the top, this works well enough but doesn’t have a particularly nice feel.
As well as playing music the DP100 has a built-in microphone so you can use it to make hands-free phone calls. It comes with a little cloth drawstring pouch to protect it when you're carrying it around, cables for USB and audio and a decent printed instruction leaflet.
Charging from USB takes just over three hours which gives between 15 and 20 hours of playback or 8 to 10 hours of talk time. It will therefore get you through a full day at work, say, without needing a recharge. Switch on and it sounds a tone to let you know it's ready to pair, from then on it will automatically connect to the last paired device each time it gets switched on.
Maximum power output of the speaker is 4W, which doesn't sound like a lot but the noise it produces is enough to fill a modest sized room and has a tone that's rich and full with decent bass for a compact unit.
Overall then the DP100 is a good compromise between portability and performance. It's small enough to pop into a bag or pocket and whilst it doesn't offer concert hall sound quality it's perfectly acceptable for day-to-day use.
It's reasonably priced too at $35.99 on Amazon or £18.99 on the UK site. More information and the full technical spec can be found on the EasyAcc website.
-

Is it time for apps to protect themselves against threats? [Q&A]
Publié: mai 8, 2015, 1:48pm CEST par Ian Barker

Most security researchers now acknowledge that it is only a matter of time before a business suffers some form of compromise as the bad guys follow the money and conventional security tools struggle to keep pace. A recent report from Gartner stresses the need for apps to become self protecting rather than rely on security tools.
But how easy is it to produce a self-protecting app and how effective are they against malware? We spoke to Gordon Young, UK Sales Director of security specialist Promon to find out more.
BN: How vulnerable are apps in general to the threat of being compromised?
GY: When talking about mobile bank apps, payment apps, authentication apps etc. we can say that all are vulnerable to compromise by malware or hackers. For an attacker, being inside the app allows them trusted access to all the app's internal interfaces - screen, keyboard and file system.
BN: Does this mean that the traditional security approach of protecting the device is broken?
GY: Indeed they are, traditional security solutions are based on first identifying, and then neutralizing threats. With this approach the attackers are almost always in the front seat. Alternatively, Promon's technology works from inside the app by closely monitoring the app's runtime process and taking action against any unknown code that tries to enter the app.
BN: Tell us a bit about how Promon Shield can supplement existing security measures?
GY: An application protected by Promon Shield runs securely even if the device itself is infected, jail-broken or rooted with no noticeable overhead and is totally transparent for end users. Being able to proactively block known and unknown threats, Promon's in-app security technology is unique in being able to co-exist with any existing security approaches.
BN: Will this work across all platforms and all kinds of app?
GY: Yes it will. We have deployments on WinPC, MacOS, iOS and Android protecting banking apps, authentication apps etc. Promon has desktop deployments, mobile deployments and deployments where Promon protects employee remote access in a virtual desktop environment using Citrix, for example.
BN: Does it require any action on the part if the end user?
GY: The end user has no visibility or knowledge of Promon security, and the user process is not changed or impacted in any way.
BN: Will an app secured with Promon Shield be effective even if the device is already infected with, say, a keylogger or if it's been jailbroken?
GY: That is correct, Promon Shield protects the App even if the device is already compromised, thus a bank can allow the user transaction to safely execute even when Promon has flagged that the device is compromised.
BN: Are we about to see a major shift in the way banks and other companies address security concerns?
GY: We are seeing a gradual recognition that existing security mechanisms based upon simple detection of malware is not an effective security mechanism whereas the Promon approach of creating the "Self-Defending" app is a fundamentally superior approach that is better suited to the current and future threat environment.
Image Credit: Anan Chincho / Shutterstock
-

Twistlock adds security to container-based applications
Publié: mai 7, 2015, 6:06pm CEST par Ian Barker

The move towards containerized technologies such as Docker for creating and scaling applications is great for development times but presents challenges for enterprises when it comes too keeping apps secure.
Unveiling a security suite designed to give enterprises the visibility and control they need over their container-based applications and data, Twistlock aims to maintain security and maximize efficiency and portability.
"Enterprises are in the midst of a data center revolution," says Ben Bernstein, CEO and co-founder of Twistlock. "Twistlock’s container security suite provides the fuel enterprises need to accelerate their ability to use containers to develop, share and scale the applications that drive their business forward. With our solution, security operation teams finally have the visibility and granular controls they need over their 'Dockerized' workloads".
Containers represent a problem for enterprises, as security operations teams only see a virtual machine (or group of machines) running unknown processes being accessed by large numbers of remote systems. Twistlock understands what's really going on within a container or cluster of containers. It knows who is accessing what and which processes relate to which workloads. By plugging into the control channel that manages containers it enables intelligent inspection of containers at rest, as well as at run-time.
The Twistlock suite addresses risks on the host and within the application of the container, enabling enterprises to consistently enforce security policies, monitor and audit activity and identify and isolate threats in a single container or cluster of containers.
Key features include the ability to monitor both static container images and runtime container applications to identify risks, and to specify security baselines to ensure the host has been hardened and the application meets quality and security standards. It can protect containers deployed both in the cloud and on-premises in a virtual data center, and keep up with dynamic security concerns.
To find out more and sign up for the beta program you can visit the Twistlock website.
Image Credit: Spartak/Shutterstock
-

Working in IT is getting more stressful
Publié: mai 6, 2015, 3:08pm CEST par Ian Barker

Do you feel more stressed at work? If your job is in IT then the answer is probably yes, according to a new survey from security and email specialist GFI Software.
The study of over 200 IT administrators in the US finds that 78 percent of those surveyed experience workplace stress, while almost 82 percent of respondents are actively considering leaving their current IT job due to workplace stress and dissatisfaction with working conditions, up from 78.5 percent in 2014.
Key findings include that 45 percent of respondents have missed social functions due to overrunning issues and tight deadlines at work, up from 38 percent in 2014. A further 40 percent also report missing time with their children due to work demands eating into their personal time.
Losing sleep due to work pressure is reported by 38 percent of IT staff and the number of respondents experiencing stress related illnesses increased slightly, to 27 percent from 25 percent in 2014. A further 19 percent continue to report feeling in poor physical condition due to work demands, up two percent from last year.
More than 25 percent report that a relationship or friendship has failed or been severely damaged due to work commitments intruding on personal life.
"Even in an industry like IT that's well-known for being extremely stressful and highly demanding of its workforce, the findings of this year's IT Stress Survey makes for worrying reading. The 2015 survey results clearly show a substantial deterioration of the work/life balance and job satisfaction among the US IT workforce -- quite concerning at a time when the IT sector is playing such a pivotal role in the growth of our economy," says Sergio Galindo, general manager of GFI Software.
The biggest driver of stress is cited by 28 percent as unreasonable demands and pressure from management, though this is down from 36 percent last year. Stress caused by end users is increasing, however, rising from 16 percent last year to 23 percent.
Galindo adds, "Smart employers understand that an over-stressed and unhappy workforce means less productivity, and the higher levels of illness, mistakes and staff turnover directly related to stress can have a very significant and direct cost to the bottom line. Investing in worker happiness and in systems to simplify the job of the IT department is often far cheaper than replacing over-stressed or unhappy staff".
More information along with the full report is available from the GFI website and there's a summary of the results in infographic form below.

Photo Credit: sunabesyou/Shutterstock
-

IBM and Facebook team up to offer tailored marketing
Publié: mai 6, 2015, 1:37pm CEST par Ian Barker

All advertisers are keen to use the power of the Internet to deliver the right message at the right time. From today IBM and Facebook will be collaborating on the delivery of tailored marketing to help with that process.
IBM's marketing cloud clients will be able to utilize Facebook's powerful ad capabilities such as Custom Audiences, along with IBM's deep analytics and design features, to target their customers across applications, devices and time.
Using IBM's new Journey Designer, brands will be able to create personalized customer experiences and then use Journey Analytics to gain an understanding of how customers responded.
By combining Facebook's ad technologies with IBM's Journey Analytics, brands can more accurately determine which groups of customers are among the 1.44 billion people active on Facebook and establish links between their interests and interactions across multiple channels. IBM's Journey Designer solution will then help brands to deliver more compelling messages on Facebook and other mediums.
IBM has also announced that Facebook will be the first company to join its new IBM Commerce THINKLab, a research and collaboration environment in which companies will work directly with brands to accelerate development of new technologies designed to personalize customer experiences.
"Our partnership with IBM will help top brands achieve personalization at scale by using IBM’s marketing cloud to find and engage their target audiences on Facebook, as well as solve their vexing challenges by consulting with IBM Commerce THINKLab," says Blake Chandlee, VP of Partnerships for Facebook. "We will also be working closely with IBM Commerce THINKLab to help deliver people-based marketing that’s optimized to achieve each brand’s business goals".
IBM will use deep analytics, on top of Facebook's anonymized and aggregate audience insights along with additional information from IBM’s marketing cloud to give marketers a clearer picture of their target audiences. They'll also be able to replicate proven campaigns beyond Facebook to other brand channels including their own stores, websites and mobile apps. All of which means better targeted ads.
"Brands understand the increasing need to provide customers with powerful and personalized experiences to nurture loyalty", says Deepak Advani, General Manager, IBM Commerce. "Through this collaboration, consumer product companies and retailers will be able to quickly and easily gain deeper insight into what their customers expect and provide them with compelling experiences that bridge the physical and virtual divide".
You can get more information about IBM cloud marketing solutions on the company's website.
Image Credit: IBM UK
-

ImmuniWeb takes a fresh approach to detecting website vulnerability
Publié: mai 5, 2015, 4:42pm CEST par Ian Barker

As apps and commerce increasingly move online they provide a tempting target for hackers. It's important that websites are properly tested for vulnerabilities but this can be a time consuming process and many smaller organizations lack the resources and expertise to do it themselves.
High-Tech Bridge's ImmuniWeb offers a fresh approach to website vulnerability assessment. It uses a hybrid approach combining automated testing with the skills of security professionals.
ImmuniWeb is an on-demand web penetration testing assessment service, that enables any organization, regardless of its size, location, or in-house technical skills, to order online an automated website security assessment combined with manual penetration testing by experienced security professionals.
The test is run over a four day period and looks for known vulnerabilities and weaknesses like outdated server software, exposed email addresses, untrustworthy third-party content, whether HTTPS access is available and more. The testing is non-invasive and requires nothing more than standard browser access to the site to be examined.
At the end of the process the results are delivered in an easy-to-understand multi-page PDF report which highlights any vulnerabilities found and offers tips for fixing them.
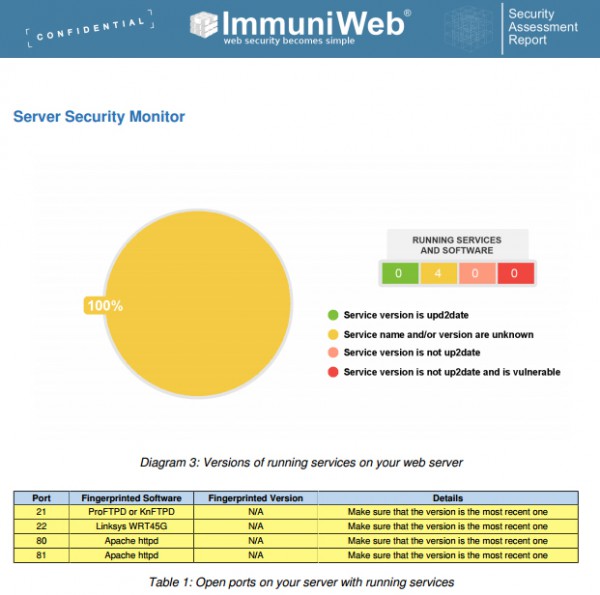
The fact that it combines automated testing combined with human expertise means ImmuniWeb can accurately detect complex security flaws missed by scanners and other automated solutions. ImmuniWeb auditors can also step in and provide assistance when firewalls and other defenses block the scanning tools employed.
ImmuniWeb won bronze awards in the Best Security Service, and Vulnerability Assessment, Remediation and Management categories at the 2015 Global Excellence Awards. More information about the service is available on the High-Tech bridge website.
Image Credit: ksenvitaln / Shutterstock
-

Birst shapes data analytics around the user
Publié: mai 5, 2015, 1:38pm CEST par Ian Barker

Data is in many ways the lifeblood of business, yet there are many different ways to present and use the results of analysis.
Business intelligence specialist Birst is launching its Birst 5X Adaptive User Experience which allows users to work with data in the way they want without suppressing their curiosity and creativity.
The new release includes updates to Birst Dashboards and Visual Discovery Capabilities, and an enhanced Birst Mobile experience. In addition it introduces an Open Client Interface that enables users to continue with their preferred front-end tool, such as Tableau, Microsoft Excel or R, to analyze a trusted source of data in the form of Birst's User Data Tier.
Allowing people to use their tool of choice on top of a complete and trusted source of data delivers a two-tier analytics model that combines agility with governance. The BI solution adapts to a person's mobile work style too so that key business insights are available anywhere and anytime.
"Birst is continuing to pioneer a two-tier approach to BI and analytics. With Birst 5X we are rethinking the user experience by focusing on how people interact with data instead of putting them in a rigid user role", says Junaid Saiyed, VP Product Management and Engineering, Birst. "Birst 5X gives people an agile experience that adapts to their work style, whether they need operational dashboards or visual discovery, in the office or on the road, and all against a trusted source of truth".
Birst 5X allows users to seamlessly switch between modes so they can use both dashboards and visual discovery. It supports disconnected analysis on mobile devices so that users can access critical information wherever they are. A responsive design also adjusts how the data is displayed based on the form factor of the device.
You can find out more about Birst's two-tier analytics technology on the company's website.
Image Credit: Rawpixel / Shutterstock
-

HP brings performance testing solutions to Microsoft Azure
Publié: mai 5, 2015, 11:20am CEST par Ian Barker

Developers are under ever increasing pressure to roll out applications quickly, and that means performance testing is more important than ever to ensure they work as they should.
To address this HP is using Microsoft Ignite to announce updates to its performance testing tools and that it’s making them available on the Azure marketplace.
Both HP StormRunner Load and HP LoadRunner are now pre-configured for Microsoft Azure environments, providing organizations with access to cloud-based tools on demand for faster and easier application performance and load testing.
"The mobile application development market is evolving rapidly, and developers today require fast, flexible, and easy-to-use tools to help them accelerate mobile app delivery," says Robert Youngjohns, EVP and GM at HP Software. "By delivering HP StormRunner Load and HP LoadRunner in the Microsoft Azure environment, we are providing developers with a fast-path to a proven, cloud-based platform that they can use to build and test scalable, high-performing applications".
HP StormRunner Load is a SaaS solution for agile development teams. It allows them to test, analyze, and tune applications and gain confidence in application scalability up to millions of geographically distributed web and mobile users. Features include an integrated WebPageTest to show client side single user response time when a back-end application is under load. It also links in with HP Network Visualization and HP SiteScope so that impact on network behavior and application health is included in testing.
HP LoadRunner is designed to provide developers with an accurate picture of end-to-end system performance and help identify and resolve issues before application changes go-live. It allows organizations to reduce the cost of application downtime related to performance issues in production and supports continuous testing of web, mobile, and legacy technologies.
HP LoadRunner Community Edition is available now on the Microsoft Azure Marketplace and HP StormRunner Load Community Edition will be available next month.
Image Credit: alphaspirit / Shutterstock
-

Companies team up to create powerful Internet of Things solution
Publié: mai 4, 2015, 3:43pm CEST par Ian Barker

The Internet of Things is set to change many aspects of the way we live, but for companies and developers it represents a whole range of challenges when it comes to integration with existing systems and analyzing the extra data it generates.
Now analytics specialist Glassbeam and development platform supplier ThingWorx have announced a collaboration to allow their solutions to work together.
The ThingWorx rapid application development IoT platform is designed to build and run applications for the connected world, allowing customers to reduce the time, cost, and risk required to build innovative applications for smart, connected products. Glassbeam's proven IoT analytics as a service offering provides advanced machine learning and real-time analytics, taking in and analyzing data collected and stored inside the ThingWorx platform.
"Customers need the ability to derive new intelligence from data, and we're building out our certified partner marketplace to meet that need," says Chris Kuntz, Vice President of Ecosystem Programs at ThingWorx. "The addition of Glassbeam allows customers to analyze their data directly in the Glassbeam platform. It's a powerful and complementary offering to the ThingWorx platform".
Combining the two solutions allows customers to reduce costs, increase revenues, and accelerate the time to bring products to market as well as improving customer satisfaction and retention. The solution has already been selected by medical device company VytronUS to collect and analyze machine data from its systems.
"We believe that Glassbeam and the ThingWorx platform working in tandem as an end-to-end solution for customers to view rich analytics, based on data in their machines and from adjacent applications, is highly valuable," says Puneet Pandit, CEO and co-founder of Glassbeam. "We knew that our collaboration with ThingWorx was going to be successful. Now, with the addition of VytronUS as a customer and active prospect discussions, we're excited about the possibilities created by this collaboration".
More information and a trial of the ThingWorx platform is available on the company's website.
Image Credit: PlusONE / Shutterstock
-

Spanning launches automated protection for Office 365
Publié: mai 4, 2015, 2:35pm CEST par Ian Barker

The rise of SaaS applications like Microsoft Office 365 has brought benefits in terms of collaboration and efficiency. However, switching to a cloud-based service doesn't remove the need for backups.
For example, Office 365 doesn't protect against accidental deletion of files and a deleted mailbox is only available for 30 days after which it's not recoverable. These problems are addressed by a new product from backup specialist Spanning Cloud Apps.
Launched at Ignite, Spanning Backup for Office 365 provides IT administrators and end users with a simple way to locate lost mail, calendars and contact data from any point in time, from any device and accurately restore them to their original state.
"We have witnessed the groundswell of interest in Office 365 as more and more companies want to take advantage of the improved collaboration, higher productivity and increased mobility that comes with cloud computing," says Jeff Erramouspe, VP and General Manager of Spanning. "The tremendous interest in our beta program has exceeded our goals, and shows that IT organizations understand they need a solid data protection plan in place before moving to the cloud. As the first fully responsive cloud-to-cloud backup application for Office 365, Spanning Backup allows Microsoft customers to harness cloud-based productivity without having to worry about user-driven data loss that can significantly hinder their work".
Launched in beta at the end of last year the product minimizes risk of data loss and assures availability of Mail, Calendars and People. It also helps enterprises meet audit and compliance requirements for backup and recovery. It reduces the IT department's workload too by allowing users to easily restore lost data themselves.
Spanning Backup for Office 365 will be available form the end of June at a $48 per user, per year subscription price with unlimited back-up storage. Discounts are available for volume purchases, long tern agreements, and non-profit and education use. More information is available on the Spanning website.
Image Credit: Modella / Shutterstock
-

Why backups are shifting to the cloud
Publié: avril 30, 2015, 4:11pm CEST par Ian Barker

A backup and recovery solution is essential for enterprises if they're to safeguard their critical data. Yet whilst they may take care of their servers, according to a new infographic from private cloud company SingleHop they're less concerned about endpoint data.
Only 50 percent of companies have endpoint backups in place and this leads 16 percent of end users to do their own backups using a non-approved solution.
This seems short sighted given that system downtime is a major cost, loss of mission critical data costs in excess of $70,000 per hour on average and even losing non-critical data can cost $42,000 per hour.
Organizations encounter unplanned downtime 13 times a year on average and targeted attacks are a major threat with 50 percent aimed at larger enterprises and 31 percent at those with fewer than 250 employees.
No surprise then that data loss is a major concern for management and that they're increasingly turning to the cloud as a solution. 64 percent already store data in the cloud and 78 percent plan on changing their protection product in the next two years.
There are more interesting statistics on the effects of downtime in the full infographic below.
Photo credit: LilKar/Shutterstock
-

Unpatched PDF readers leave US private PCs open to attack
Publié: avril 30, 2015, 12:18pm CEST par Ian Barker

Adobe Reader 10 has 39 vulnerabilities and is unpatched on 65 percent of private PCs in the US, whilst Adobe Reader 11 with a 55 percent market share has 40 vulnerabilities and remains unpatched on 18 percent of machines.
This is one of the findings of the latest Secunia country report. Additional findings show that 14 percent of PC users in the US (up from 12.9 percent last quarter) have an unpatched operating system, and that Oracle Java once again tops the list of applications exposing PCs to security risks.
Other applications in the vulnerability top 10 include Apple QuickTime, Microsoft Internet Explorer and uTorrent for Windows. Also one in 20 programs on the average US PC have reached end-of-life, meaning they are no longer supported by the vendor and don't receive security updates. Adobe Flash Player, one of the end-of-life applications, is still installed on no less than 78 percent of the PCs surveyed.
"It is worrying that, with such a high market share, one in five US users fail to patch their Adobe PDF reader," says Kasper Lindgaard, Director of Research and Security at Secunia. "Considering the fact that PDF documents is a prominent attack vector used by hackers to gain entry into IT systems, users put themselves and any system they are connected to at risk, by neglecting the security risk the popular reader represents when not maintained. It is paramount that users remember to patch their PDF readers, and that corporate IT teams have procedures in place to update all PDF readers on devices that are in any way connected to the company infrastructure".
More interesting findings are that the average PC user in the US has 76 programs installed from 27 different vendors. 42 percent of these programs are from Microsoft while the rest come from other companies. Whilst there's a single update mechanism for the Microsoft programs this means that users may have to master up to 26 other, different update processes to keep their machine secure. Little wonder that a popular social engineering trick for malware is to pose as an update for a video player or similar.
Secunia's country reports for the US and elsewhere are available to download from the company's website.
Image Credit: alexskopje / Shutterstock
-

Incentive launches Dropbox integration for secure file collaboration
Publié: avril 29, 2015, 4:08pm CEST par Ian Barker

Businesses often use different applications to create, store and share content. Whilst most enterprise collaboration tools allow for some sort of file sharing it can involve additional time and effort importing data.
The Incentive platform is now making sharing information easier by adding one-click integration with Dropbox cloud storage.
The integration provides secure access to Dropbox folders from within Incentive, enabling users of the file sharing application to search for, discuss, comment, share and collaborate on files across both internal and external groups.
"Companies around the globe use Dropbox and other platforms to store and share files, but none of them are inherently collaborative," says Rickard Hansson, CEO and founder of Incentive. "Incentive's integration with Dropbox gives users the ability to add any Dropbox folder into Incentive so teams can do more than just view and share files. This is just one of many integrations to come that will make it easier for organizations to be more collaborative, efficient and productive".
Incentive's integration with Dropbox lets users add any folder within a Dropbox account to Incentive for easy and quick access from one central location. Users can discuss, share, comment, like and collaborate on Dropbox files natively within Incentive and make Dropbox content instantly discoverable with Incentive’s search. Updates can be added to the app's news feed whenever Dropbox content is edited or changed, for improved team collaboration and productivity.
You can get more information and try out Incentive for free on the company's website.
Image Credit: Chiran Vlad / Shutterstock
-

'You don't post pictures of us on Facebook -- I want a divorce!'
Publié: avril 29, 2015, 3:13pm CEST par Ian Barker

According to a new survey of 2,000 people in the UK, one in seven say they've contemplated divorce because of their partner's activity on social media.
Nearly a quarter also say they have at least one row a week with their partner because of social media use and 17 percent say they argue every day because of it.
Just under half of all Brits surveyed admit they have secretly checked their other half's Facebook account and one in five go on to row about what they discover. The most common reason cited for checking a partner's social media account was to find out who they were talking to, to keep tabs on them, to check who they were out with, and to find out if they were telling the truth about their social life. 14 percent say they specifically look for evidence of infidelity.
The research was commissioned by family law specialists Slater and Gordon who have seen an increase in the number of people citing social media use as a cause of divorce year on year.
"Social media can be a wonderful way of keeping in touch with family and friends, but it can also put added strain on a relationship," says Andrew Newbury, head of family law at Slater and Gordon. "Five years ago Facebook was rarely mentioned in the context of a marriage ending, but now it has become common place for clients to cite social media use, or something they discovered on social media, as a reason for divorce".
One in 20 say they were upset that their partner didn't post any pictures of them together. But it isn't just what partners are doing on social media that causes problems, couples argue over how much use they make of sites too.
Social media is considered dangerous to their marriage by 15 percent of respondents, with Facebook seen as being most hazardous, followed by WhatsApp, Twitter and Instagram. Yet one in ten admit they hide images and posts from their partner, while eight percent admit to having secret social media accounts.
Whilst a third said they keep their social media log-in details a secret from their partners, 58 percent admit to knowing their partner’s log-in details, even if their spouse wasn't aware they knew them.
Newbury concludes, "We are now actively advising our clients to be cautious when it comes to using Facebook and all forms of social media because of its potential to damage relationships".
In the interests of marital harmony therefore, if you're planning on sharing this story on social media please keep your partner informed.
Image Credit: Feel Photo Art / Shutterstock
-

Smart meeting service helps bring business people together
Publié: avril 29, 2015, 1:09pm CEST par Ian Barker

As the workforce becomes increasingly mobile, setting up meetings and making sure time spent in them is used effectively becomes more and more difficult.
Israeli company Meeter is launching a 'smart meeting' solution that doesn't only automate the scheduling of meetings, but also provides a standardized framework for managing what happens during them and collects documentation on what happened.
Meeter is powered by an algorithm that searches for optimal meeting availability, learns behaviors, and adapts to the meeting preferences of participants. As an alternative to passive calendar systems, Meeter adds value to its users through the full 'meeting lifecycle' -- before, during and after.
It's SaaS-based and allows for meetings to be scheduled instantly for up to 100 participants at a time. The Meeter app can be downloaded through the app stores for iOS and Android systems, as well as from the web and can work with participants who may not have the app via email. It creates a unique landing page for each scheduled meeting to allow participants to easily share agendas, presentation materials and so on.
Meeter tracks and analyzes the user's time, providing insights about past meeting history and reporting on who a user met with, for how long and when. Over time this allows it to suggest useful future meetings and help significantly increase productivity.
"Meetings today are a major drain on the workforce productivity. Our mission is to optimize meetings and automatically organize data so a significant portion of your day that is currently spent on setting them up, can be made productive. With Meeter people will be able to easily collaborate about meetings; creating one place that immediately serves as an archive for meetings," says Niv Kagan, CEO and founder of Meeter. "Setting up meetings instantly is a crucial first step and we’re delivering that with an intelligent app that is easy to use, has universal application, and is non-intrusive".
For more information and to download the app you can visit the Meeter website.
Photo Credit: nmedia/Shutterstock
-

Microsoft and Adobe team up to offer integrated marketing solution
Publié: avril 29, 2015, 11:41am CEST par Ian Barker

Enterprises are always looking for ways to better understand and connect with their customers. The Adobe Summit in London this week is being used to launch a partnership with Microsoft that will integrate Adobe's Marketing Cloud Solutions with Microsoft's Dynamics CRM.
The partnership will offer businesses an integrated CRM-marketing solution across a range of industry segments including financial services, travel and leisure. It's aimed at helping eliminate the frustrating customer experiences that result when efforts are fragmented.
Key features include the ability to align sales and marketing activities by tightly integrating audiences and their behaviors to help guide sales or service calls, identify sales opportunities or inform lead scoring.
It will also allow users to find high-value audience segments and provide them with real-time offers on a website or enable targeted display ads. It offers the ability to combine Web behavior data with order history, return history, loyalty status and call center history to not only identify where in the sales lifecycle stage a customer is, but then also deliver the right content at the right time.
"Helping our customers reinvent productivity and business processes is one of our top priorities. Partnering with Adobe enables us to deliver a comprehensive set of customer engagement processes to enterprise customers to help them be more productive and better engage with their customers," says Kirill Tatarinov, executive vice president, Microsoft Business Solutions, Microsoft. "The integration of our industry-leading Microsoft Dynamics CRM solution with the Adobe Marketing Cloud will enable business professionals to maximize their investment in technology and deliver breakthroughs in marketing, sales and customer care".
Both companies are committed to expanding other areas of collaboration and product integration too, these include Adobe Marketing Cloud Solutions running on the Microsoft Azure cloud platform. Adobe Campaign and Adobe Experience Manager are also now certified on Microsoft Azure. Adobe is already partnering with Microsoft Azure to deliver streaming of major sporting events including the Olympics and Super Bowl through Adobe Primetime. The two companies are also working on a connector that will enable data and insights from Adobe Analytics to appear in Power BI, Microsoft's business analytics service that enables users to see all of their data in one place, providing a consolidated view across a business.
More information on Marketing Cloud is available on the Adobe website, and on Dynamics CRM from the Microsoft site.
Image Credit: Zurijeta/Shutterstock
-

Kaspersky launches new security solution for small businesses
Publié: avril 28, 2015, 3:23pm CEST par Ian Barker

Security issues affect smaller businesses just as much as big ones, but they're often less equipped to deal with them due to limited resources.
Today Kaspersky Lab is releasing the latest version of its Kaspersky Small Office Security, built specifically for businesses with fewer than 25 employees. It's aimed at providing world-class protection and easy use without the need for specialized IT skills.
Even small businesses hold valuable data relating to customers, payments and intellectual property, but they often rely on basic protection measures like free anti-malware programs. Kaspersky Small Office Security uses enterprise-grade technologies, but is designed specifically to serve the needs of smaller businesses. It brings the power of the company's award-winning anti-malware and online transaction protection, cloud management, backup and password management, but in an easy-to-use package.
"Running a small business can be very exciting and fun, but being small doesn't mean being less noticeable by cybercriminals," says Konstantin Voronkov, Head of Endpoint Product Management at Kaspersky Lab. "It's very important for businesses to pay more attention to ensuring their cybersecurity, and Kaspersky Small Office Security has made it easy. It's straightforward to install, simple to configure, and easy to maintain, so that business owners can get on with doing what they do best: making the company a success".
Features in the new version include enhanced protection from all known, unknown and advanced threats -- with multi-layered protection for Windows and Mac computers, servers and Android-based mobile devices. A new cloud-based management console lets business owners or their IT advisers easily manage security and devices from anywhere using a web browser.
Cloud-based password management stores critical company login details and enables users to have a different, unique password for every secure site, across all devices, while only needing to remember a single master-password. The package also protects online business and personal transactions from financial fraud with improvements to the award-winning Safe Money module.
Kaspersky Small Office Security protects Windows-based desktop systems from XP through to 8.1, Mac-based systems, Windows file servers, and Android smartphones and tablets. Each user gets protection for one Windows or Mac computer and one mobile device plus access to Kaspersky Password Manager.
You can find out more and get a full feature list on the Kaspersky website.
Imaged Credit: soliman design / Shutterstock
-

Mobile messaging study reveals the need for tailored solutions
Publié: avril 28, 2015, 1:25pm CEST par Ian Barker

Mobile engagement specialist OpenMarket has released the results of a study, commissioned from IDC, into the business impact of mobile messaging.
The study looks at how mobile messaging is being used across a number of key industries including automotive, education, financial services, healthcare and utilities. It shows that many companies have failed to adopt holistic mobile messaging with 62 percent having at least two messaging platforms deployed, and 78.5 percent with more than one active initiative.
According to the research, the greatest benefits of mobile messaging are its ability to improve customer experience and employee relations. Because there's no 'one size' solution, organizations tailor their implementations to meet requirements within their industry segments. Results reveal that business leaders are driving new investments in mobile messaging and are closely involved in specification, selection, and deployment. Businesses are also finding that maximizing investments requires integrating mobile messaging into their business work flows, and that it's easier to do this if the IT team can use a work flow engine from a trusted vendor to quickly create services and address needs.
"Although use cases can differ in terms of how global enterprises are utilizing mobile messaging, these findings revealed that no matter what sector, businesses need to take a long-term, purpose-led approach to their mobile messaging investment," says Robert Parker, Group Vice President of IDC Insights. "Businesses must look towards vendors with a track record of support excellence that can provision company-wide use cases in order to meet the specific mobile messaging needs of the internal and external stakeholders within their sector".
There is confidence in the effectiveness of mobile messaging solutions with 72 percent of organizations surveyed believing they have a significant impact on the customer experience. Of high-tech companies 82 percent consider SMS to be effective for customer alerts. Businesses in all industries are adopting a ‘mobile first’ strategy to engage customers through promotions and offers, alerts, and surveys and increase the relevance and immediacy of their marketing message. Currently, 87 percent of travel and hospitality company respondents are piloting or in production with mobile messaging programs that include customer promotions.
"These findings show that no matter what vertical or industry a business is in, organizations are incorporating mobile messaging into many aspects of their internal operations, as well as customer and employee communications and engagement," says Jay Emmet, General Manager of OpenMarket. "A well-designed, company-wide mobile messaging strategy will give organizations a path to enhance the customer experience, gain additional customer insights, improve employee relations, and drive operational efficiencies".
You can find out more in the full report which is available to download from the OpenMarket website.
Photo Credit: bloomua/Shutterstock
-

Free service combines cloud data integration and backup
Publié: avril 28, 2015, 11:21am CEST par Ian Barker

With the wide choice of cloud services available it can be all too easy for business data to become fragmented with different parts of the organization using different services.
Database connectivity solutions provider Devart has announced the release of Skyvia 3.0, a free online service that can integrate cloud data from different sources and in this latest version provide cloud backup too.
The Skyvia service enables users to perform data export, import, replication and synchronization all via a simple user interface. With the addition of Skyvia Backup in this version users get automatic daily and anytime manual backup together with one-click restore functionality. New predefined templates for data mapping speed up configuring import and synchronization operations and simplify migration of information between cloud data sources.
"The goal of our team is to offer the best cloud service for wide array of data operations with no need of coding," says Alex Hyrniy, Skyvia Product Manager. "For now, as long as Skyvia is a growing service, it's free of charge, because we're aimed to hear the needs and opinions from the customers to make Skyvia a strong player on a cloud market soon".
Skyvia supports a wide range of database systems including SQL Server, MySQL and PostgreSQL; popular CRM systems, Salesforce, Dynamics CRM, Zoho CRM and SugarCRM; plus data storage services including Dropbox, FTP, Box and Google Drive.
Skyvia backup currently supports Salesforce, Dynamics CRM, SugarCRM and Zoho CRM. It offers the ability to search backed up data making it easy to restore specific records if required.
You can find out more and sign up to use Skyvia for free on the company's website.
Photo Credit: Melpomene/Shutterstock
-

Mobility is the top focus for developers
Publié: avril 27, 2015, 3:20pm CEST par Ian Barker

According to a new survey by application delivery company OutSystems, 43 percent of respondents rate apps or sites that are mobile friendly as critical to their plans in 2015. The way in which Google has changed how it weights mobile-friendly sites is presumably a driving factor.
The survey conducted with content specialist TechValidate talked to 200 IT decision makers worldwide and focused on the business and technical priorities and challenges that IT organizations face in building applications in today's complex development landscape.
Other findings are that 25 percent of respondents say that between 76 and 100 percent of new apps they plan to build in 2015 will have a mobile component. An additional 26 percent say that 51-75 percent of new apps will have a mobile element.
The dominant mobile architectures for 2015 will be mobile Web (60 percent) and hybrid (65 percent), with only 26 percent of enterprises planning to use native mobile architectures. Despite the number of packaged and SaaS solutions available many enterprises are still finding it easier to develop their own apps rather than spend time customizing packaged solutions.
It's also the case that there's significant integration with existing systems. 79 percent of organizations say they need to integrate with at least 1-5 cloud-based applications and 66 percent need to integrate with at least 1-5 on-premises applications. Integration with custom developed applications is needed by 61 percent. Any given app may need to integrate with multiple different systems.
Paulo Rosado, CEO of OutSystems says, "These survey results echo the challenges we hear from customers -- that they are increasingly focused on delivery of mobile applications, that they aren't getting what they need from off-the-shelf from packaged applications, and that they desperately need the ability to integrate quickly and seamlessly with a wide variety of technologies. This confluence of challenges within enterprise application development is leading organizations to seek alternatives that dramatically simplify the delivery of applications, regardless of the underlying technology requirements".
The survey coincides with OutSystems releasing new features for its Rapid Application Delivery platform. These include simpler integration, improved change management and continued commitment to open standards.
Image Credit: violetkaipa / Shutterstock
-

Broadband policy could affect how 1 in 5 UK residents vote
Publié: avril 27, 2015, 11:39am CEST par Ian Barker

If you live in the UK it probably won't have escaped your notice that there's an election campaign underway. But could your broadband connection affect the way you vote?
According to a survey from broadband, TV and mobile comparison site Cable.co.uk almost one in five (18 percent) of 2,500 people polled say that broadband policy could affect the way they vote.
Those surveyed also said they want a minimum broadband speed, on average, of 32Mbps -- 600 times faster than the speed broadband providers are currently legally obligated to supply.
Dan Howdle editor-in-chief of Cable.co.uk says of the results:
It's likely no coincidence that the one in five households in the UK that are yet to have superfast broadband deals made available to them matches proportionately to those who say broadband will affect the way they intend to vote.
No doubt this is, in part at least, due to the fact that no party manifesto has promised to roll out superfast broadband to 100 percent of households, and to a deadline acceptable to those whose homes, businesses and childrens' educations are respectively isolated, diminished or stunted by poor connectivity.
So if the electorate really cares enough to vote based on broadband policy what are each of the main parties offering?
The Conservative Party says it will make ultrafast broadband -- speeds of 100Mbps or more -- available to, "nearly all UK premises as soon as practicable." The party's manifesto sets out a £100bn investment in infrastructure, including broadband and mobile.
The Labour Party says it will deliver, "affordable, high speed broadband" to the whole of the UK by the end of the parliament. The party has also pledged to deliver the infrastructure needed to extend mobile coverage and reduce "not-spots."
The Liberal Democrats pledge to, "complete the rollout of high-speed broadband, to reach almost every household (99.9 percent) in the UK".
Ukip doesn't mention broadband or mobile in its manifesto at all.
The Green Party says it will give internet service providers an, "obligation to provide affordable high-speed broadband-capable infrastructure to every household and small business".
The Scottish National Party pledges to invest in superfast broadband, so that, "at least 95 percent of premises across Scotland will be able to access fibre broadband by the end of 2017".
The Welsh nationalist party, Plaid Cymru, says it will deliver 30Mbps broadband to the whole of Wales. The party also wants to ensure, "that mobile phone operators provide a better service in all parts of Wales".
So there you have it, six parties offering some form of better broadband and one not mentioning it at all -- possibly because the Internet connects us to abroad. Current Ofcom regulations set out a universal service obligation (USO) which states that communications providers need to provide, "data rates that are sufficient to permit internet access," meaning 'dial up' internet (56Kbps or less) is an acceptable minimum. However, the current government has pledged to raise the USO to 5mbps and ensure everyone has at least 2mbps by the end of 2016.
Howdle concludes, "Comparing broadband to the headline issues, it is ironic that while parties seek to connect with us on immigration, welfare and the deficit, those getting a raw deal on connection itself wield the power to swing this election".
Is broadband policy important enough to influence your vote? Do let us know.
Image Credit: Blablo101 / Shutterstock
-

How CEOs are failing to exploit social media
Publié: avril 24, 2015, 5:10pm CEST par Ian Barker

Social media is a large part of many people's lives these days but it seems that people at the top of enterprises and large organizations are more reluctant to engage.
Management education advice site MBA Central has produced an infographic looking at how CEOs are lagging behind in their use of social media despite the benefits it can bring to their personal and professional reputation.
It shows that 68 percent of CEOs have no social media presence at all and of those that do only one in three uses more than one site. The platform of choice for single site users is LinkedIn which is used by 73 percent. Only 8.3 percent of Fortune 500 CEOs have Twitter accounts but between them they have 3.7 million followers, showing the size of the potential audience the others are missing out on.
Interestingly three out of four consumers say they feel a company is more trustworthy if its high level management participate in social media. Also 76 percent of executives say they'd rather work for a socially engaged CEO.
You can see the full infographic, which includes tips on how CEOs can use social media effectively, below.

Source: MBACentral.org -

The Apple Watch becomes an enterprise security tool
Publié: avril 24, 2015, 3:20pm CEST par Ian Barker

Everyone, it seems, is jumping on the Apple watch bandwagon today with new apps, but one of the more interesting developments comes from enterprise security specialist MicroStrategy.
It's launched a version of its Usher platform allowing the Apple Watch to be used as a secure digital key, enabling wearers to log into business systems, unlock devices, validate personal identity, and open physical doors with a simple gesture or tap.
"Apple Watch is the ideal platform to replace the password, plastic card, and metal key," says Michael Saylor, CEO of MicroStrategy. "By integrating Apple Watch, iPhone, and Touch ID with enterprise applications, resources, and business processes, Usher for Apple Watch brings a new level of convenience, capability, safety, and security to the marketplace".
The Usher platform allowing smartphones to be used as a security key was released earlier this year. By using a number of Apple Watch features, including Glances, Notifications, and Force Touch, this latest version of Usher seamlessly enables the new device to be used for a broad range of business security applications. The app is designed to detect a wide range of systems, hardware and physical entryways as users approach. Users also receive push notifications on their watch prompting them to unlock their workstation, log into a system, or open a doorway with a simple tap or gesture on the device.
More information about Usher for Apple Watch is available on the MicroStrategy website.
-

Microsoft makes improvements to IE11 for enterprises
Publié: avril 24, 2015, 12:34pm CEST par Ian Barker

Microsoft is continuing its crusade to wean customers off earlier versions of Internet Explorer before the Support Lifecycle changes kick in in January 2016.
The company has announced changes in its April update to Enterprise Mode and Enterprise Site Discovery in IE11 to provide enhanced backwards compatibility for sites designed to run in earlier versions of the browser.
It adds a new IE7 Enterprise Mode option which enables Enterprise Mode together with Compatibility View. This is based on customer feedback that some sites work best with both Enterprise Mode and Compatibility View enabled.
Put a site in IE7 Enterprise Mode and it will automatically use Enterprise Mode with IE7 document mode if there's a DOCTYPE in the markup, or fall back to IE5 document mode if there isn't a DOCTYPE. The previous Enterprise Mode is still there but renamed IE8 Enterprise Mode. There's also a new IE11 Document Mode replacing the earlier Edge Mode to call IE11 on Windows 10 systems. All of these options are available via the Enterprise Mode Site List Manager.
Enterprise Site Discovery adds XML as an output option either on its own or in conjunction with WMI output. The option of management by group policy is added too with four policies to give control over the output of the feature in addition to the parameters for privacy.
More information on these changes is available on the MSDN IE blog.
-

How mobile is changing the way we communicate at work
Publié: avril 23, 2015, 5:38pm CEST par Ian Barker

The rise of mobile device use and of BYOD policies in the workplace is bringing about a major shift in the way people communicate at work.
Email solutions provider Newsweaver has produced an infographic looking at the rise of mobile devices for business use. It also looks at how bring your own app (BYOA) and enterprise app use have different effects.
Findings include that 41 percent of employees do not believe that the tools their company provides actually meets their needs. They therefore choose to 'go rogue' and use their own apps instead. This is acknowledged by IT teams where three out of four workers say they are delivering outdated enterprise tools which don’t meet employee needs.
The adoption of enterprise apps is a more effective approach as it boosts work productivity by over 34 percent. Over half of employees say that enterprise apps help them to do their job more effectively.
There are concerns though, 46 percent of IT departments are not confident in their own mobile security systems effectiveness to protect company data. Cost is also a major issue with the average enterprise app costing $100,000 plus to design, develop and launch.
You can see the full infographic with additional findings below.
Image Credit: Syda Productions / Shutterstock
-

DevOps salaries rise as the skill set becomes more recognized
Publié: avril 23, 2015, 4:02pm CEST par Ian Barker

A new study by website security specialist Incapsula and community site DevOps.com shows that DevOps is rapidly becoming one of the hottest technology career paths.
DevOps -- a hybrid of development and operations -- is a recent field, recognizing that software development, quality assurance, and IT operations all depend on each other. It aims to help organizations rapidly produce software products and services and to improve operational performance.
The survey aims to find out more about this rapidly expanding field and polled hundreds of DevOps professionals across the world on their salary, title, daily duties, and level of education required for the job.
Writing on the Incapsula blog Dori Harpaz, director of marketing says, "As this is a relatively new field, we thought it would be enlightening to see how DevOps professionals define their own roles within their organization. Taking this one step further, we decided to not only explore what DevOps professionals do, but also how much they earn and the various factors that affect salaries in this field".
Findings include that 52 percent of respondents have a bachelor's degree, while 25 percent have a master's. However, the level of education completed doesn't affect salary, the results showed professionals with high school diplomas could earn salaries comparable to those with master’s degrees.
Those salaries are also increasing. More than 76 percent of respondents reported that their salaries increased in 2014 and 85 percent expect a further increase this year. Almost half of respondents also received a bonus last year.
There's also a direct correlation between the size of the DevOps team and median salary. Perhaps not surprisingly larger teams pay higher salaries. Companies of all sizes place strong value on DevOps though. The median salary for professionals working at companies with revenues less than $1m was $87,058, and at companies with more than $1b in revenue $118,867.
Other findings include that 65 percent of respondents work for North American companies, and that the field is overwhelmingly male dominated with 96 percent of respondents being men.
The full survey report is available to download from the Incapsula website.
Image Credit: Nata-Lia / Shutterstock
-

New platform gives one-person developers the tools for faster app creation
Publié: avril 23, 2015, 3:10pm CEST par Ian Barker

Businesses and development teams are under ever more pressure to produce new apps to meet tight deadlines, this can lead to the creation of apps that fail to meet user requirements.
Platform as a service company WaveMaker is looking to streamline the development process for enterprise developers and non-programming users with the announcement of WaveMaker Desktop, a free, open source, browser-based, single-developer version of its recent WaveMaker Studio 7 release.
WaveMaker Desktop is based on open standard technologies including Java, Spring, Hibernate, AngularJS, and Bootstrap. It allows users to quickly evaluate the rapid API application development (RAAD) capabilities of WaveMaker Enterprise using live data behind the firewall and without having to involve the IT department.
WaveMaker Desktop improves on other SaaS-only solutions for app development, which prevent developers from accessing data behind the firewall. It also provides enterprises with the permanent assurances of open source software and doesn't lock them into proprietary technology.
"Speeding app creation speeds innovation. Many enterprises need their apps to access private data and work with an increasing myriad of devices. WaveMaker's Enterprise platform solves these and other related challenges for the enterprise. Before that can be done, developers first want to quickly evaluate WaveMaker's RAD capabilities on live data and WaveMaker Desktop makes that very easy," says Samir Ghosh, CEO of WaveMaker. "We also know that enterprises want a thriving ecosystem of service providers around WaveMaker. WaveMaker Desktop enables an extensive range of large and small SIs, VARs, and ISVs to thrive. Plus, we’re also seeing more SaaS ISVs, or ISVs wanting to move to SaaS looking for an open-standards-based RAD solution to not only build their apps, but to OEM as a UI customization option for their users".
WaveMaker Desktop is available to download now from the company's website. You can also sample the product's enterprise capabilities at WaveMakerOnline.
Image Credit: alphaspirit / Shutterstock
-

New app set to streamline small business accounting
Publié: avril 23, 2015, 1:40pm CEST par Ian Barker

Many small business owners see accounting as a necessary evil. They know they need to stay on top of their sales, cash flow and so on but the actual process of doing so is a chore.
Now a new mobile app called ONE UP is claiming to reduce the amount of time taken to handle accounts to just a few minutes per month. It automatically synchronizes with banks and provides suggested entries that can be validated with a single click. In addition the ONE UP suite includes automatic inventory, CRM and invoicing.
"It's as if you had a CPA on your shoulder. ONE UP is the killer app for small businesses, and with the accounting solution we literally provide hands-free bookkeeping," says Francois Nadal, CEO of ONE UP. "ONE UP gives you your free time back because you get what matters to run your business -- cash flow, profit, loss -- quickly and without the hard work. After just three months, most of your data entry is eliminated as the app learns about your business".
The app is designed to make routine tasks automatic for small businesses ranging from solo business owners up to those with 20 employees. With ONE UP Inventory, the app synchronizes with the point of sale, for example, so all that is left is to validate the suggested orders to vendors and stock can be replenished with one click.
Developed from the successful myERP product which has more than 300,000 users in 50 countries, ONE UP is in three parts. Inventory generates packing lists or delivery notes from sales orders so users can deliver to customers faster and update the status of orders. All inventory movements are posted into ONE UP Accounting, the second module, which allows an accountant to log in remotely to audit books or export financial records to their location. Finally ONE UP CRM tracks chats, calls and tasks, helps organize time with leads, creates personalized quotes with a custom template, and can turn quotes instantly into an invoice or sales order.
Pricing for ONE UP starts at $9 per month for a single user, more information and a 30-day free trial is available via the company's website.
Image Credit: EM Karuna / Shutterstock
-

Conficker remains top of the threats as existing malware for Windows dominates
Publié: avril 23, 2015, 12:38pm CEST par Ian Barker

Though we're constantly being warned about the threat offered by new malware it seems that, for Windows systems at least, the old favorites continue to catch us out.
The latest threat report from security company F-Secure shows that Conficker continues to be the number one Windows threat, kept alive by the number of unpatched legacy systems still around.
Android is still the main target for mobile malware, with 61 new families discovered compared to only three for iOS. The fastest growth has been in malware that sends premium SMS messages. Ransomware is still growing too, the Koler and Slocker trojans being the largest ransomware families on Android.
Mikko Hypponen, F-Secure's Chief Research Officer says, "Criminals use ransomware to extort people by locking them out of their own devices unless they pay a ransom. Because of virtual currencies, it's becoming a lot easier for criminals to use ransomware, making it more profitable and more useful for them. For end users, ransomware is now the most prominent type of digital threat".
When it comes to spreading malware social networking sites are popular, using routes such as Kilim, a family of browser extensions that post unwanted content (messages, links, 'Likes,' etc) to the user’s Facebook account and alter browser settings. Kilim is ranked second in the top 10 threats.
Looked at geographically, most threats reported by F-Secure users in the second half of 2014 originated from Europe and Asia, but in the last six months the company saw more activity reported in South America.
The top 10 threats identified by F-Secure in the second half of 2014 are:
1 Conficker/Downadup -- a worm exploiting a vulnerability in Windows to spread via the web, network shares and removable media.
2 Kilim -- Browser extension that posts unwanted content to Facebook.
3 Sality -- A virus family that infects exe files and hides its presence to kill processes, steal data and perform other actions.
4 Ramnit -- Infects EXE, DLL and HTML files. Variants may also drop a file that tries to download more malware from a remote server.
5 Autorun -- A family of worms that spread mostly via infected removables and hard drives, and can perform harmful actions like stealing data and installing backdoors.
6 Majava -- A collection of exploits against Java vulnerabilities, a successful attack can, among other things, give the attacker total system control.
7 Rimecud -- A family of worms that spreads mostly via removable drives and instant messaging. Can install a backdoor that allows a remote attacker to access and control the system.
8 Anglerek -- A collection of exploits for multiple vulnerabilities. At worst can give the attacker total system control.
9 Wormlink -- Specifically-crafted shortcut icons used to exploit the critical CVE-2010-2568 vulnerability in Windows to gain system control.
10 Browlock -- A police-themed ransomware family that steals control of the users’ system, allegedly for possession of illegal materials then demands payment of a 'fine' to restore normal access.
Much more detail is available in the full report which can be downloaded from the F-Secure website.
Image Credit: underverse /Shutterstock
-

Corporate privacy policies are out of step with protecting sensitive data
Publié: avril 22, 2015, 5:50pm CEST par Ian Barker

Technology makes it easier than ever for businesses to collect data but that also means they have greater responsibility for looking after it.
Data protection specialist Druva has released the results of a new study conducted by Dimensional Research which examines companies' efforts to protect sensitive data, the challenges they face ensuring data privacy and gathers respondent views on protecting data privacy in the cloud.
Among the findings are that 99 percent of respondents reported having some for of sensitive data, including personal financial, healthcare and authentication-related data, they needed to manage. 84 percent reported plans to boost their efforts to protect the privacy of sensitive data. There are problems with enforcement, however, with almost 84 percent of respondents reporting that employees don’t follow data privacy policies.
The shift towards the cloud is also having an impact, nearly 90 percent of respondents indicated that their volume of data stored in the cloud will increase through 2015 and 87 percent of companies reported being 'concerned' or 'very concerned' about data privacy in the cloud.
"Organizations are facing a real data protection crisis. Data privacy is top-of-mind for companies worldwide, and for good reason," says Jaspreet Singh, CEO, Druva. "Today's enterprise is a borderless one. The globalization of data creates a challenge that exposes each region to their specific and local privacy regulations. Protecting and managing corporate data -- especially in the cloud -- calls for a multi-faceted approach for which Druva is setting the standard".
Other statistics are that 81 percent said their business has data privacy requirements they must meet for compliance and governance regulations. Insufficient employee awareness and understanding of data privacy policies was cited by 56 percent as a major challenge to ensure privacy of sensitive data, and 67 percent reported that meeting regional requirements for data privacy is challenging.
The full report is available on the Druva website and there's a summary of the findings as an infographic below.
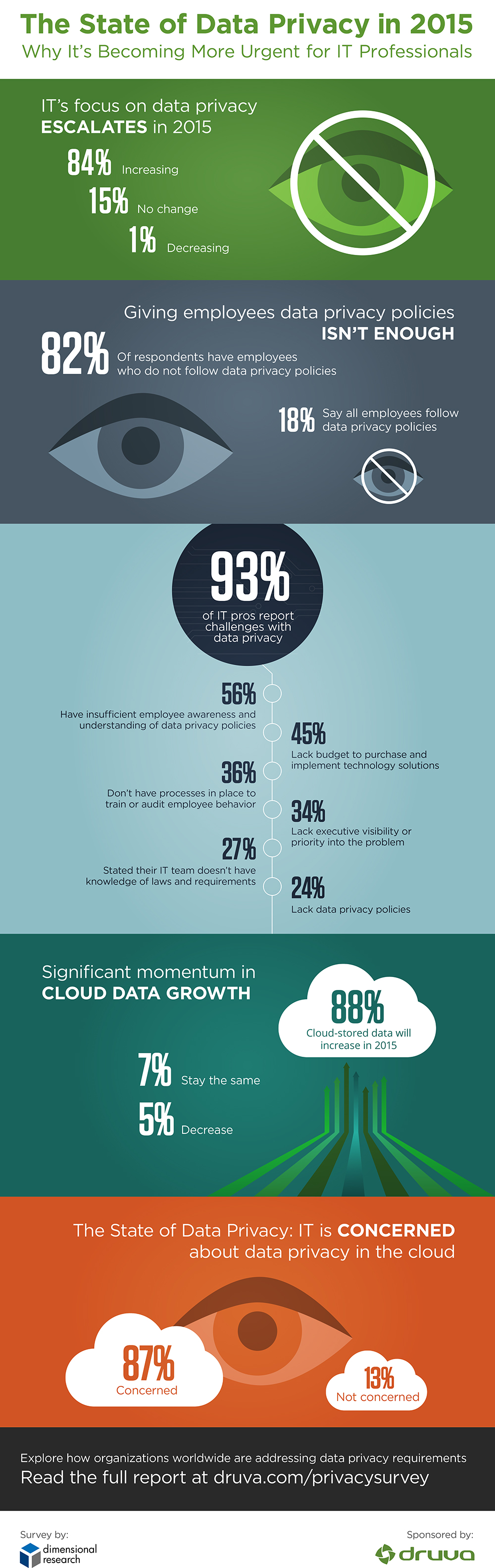
Photo credit: Ivelin Radkov / Shutterstock
-

You're more likely to be struck by lightning than hit by mobile malware
Publié: avril 22, 2015, 5:06pm CEST par Ian Barker

We constantly see stories about the latest threat from malware, particularly relating to mobile devices. But is it really as bad as it's made out to be?
No, says threat detection and containment specialist Damballa which is unveiling new research based on its big data analysis of almost half of US mobile traffic.
Damballa originally did a study in the spring of 2012 to determine the extent of mobile devices contacting malicious domains. At the time it monitored approximately 33 percent of US mobile data traffic. Repeating the study in 2014 Damballa now monitors about 49 percent of traffic. During the new test period researchers saw 130 to 160 million devices per day and observed 2,762,453 unique hosts contacted by mobile devices.
In 2012 researchers identified 3,492 out of a total of 23 million mobile devices -- 0.015 percent -- contacting a domain on the mobile blacklist. In Q4 2014 only 11,699 out of a total of 151 million mobile devices contacted mobile black list domains, a mere 0.0077 percent. For contrast the US National Weather Services says the odds of being struck by lightning in a lifetime are 0.01 percent.
Also only 1.3 percent of mobile hosts were not in the set of hosts contained by historical non-cellular data. There's a big overlap between wired hosts and mobile hosts therefore and mobile applications are reusing the same hosting infrastructure as desktop applications.
"This research shows that mobile malware in the Unites States is very much like Ebola -- harmful, but greatly over exaggerated, and contained to a limited percentage of the population that are engaging in behavior that puts them at risk for infection," says Charles Lever, senior scientific researcher at Damballa. "Ask yourself, 'How many of you have been infected by mobile malware? How many of you know someone infected by mobile malware?'"
For more information on the study and a look at Damballa's threat detection and defense systems you can visit the company's website.
Image Credit: Khakimullin Aleksandr / Shutterstock
-

New tools help speed up the unlocking of business intelligence
Publié: avril 22, 2015, 3:54pm CEST par Ian Barker

Where business intelligence is concerned it's often the case that companies don't lack data. However, they struggle to use the information they have in a way that offers meaningful insights.
San Francisco-based cloud analytics provider GoodData is releasing some new additions to its platform to break down the barriers of traditional business intelligence and improve self-service options without compromising the IT department's need for data governance and integrity.
"My goal when founding GoodData was to give everyone access to insights, creating a truly data-driven enterprise at which decisions occur quickly across every level of the business," says CEO Roman Stanek. "These new features accelerate time to insights by helping users work smarter through guided recommendations".
The additions are Data Explorer, a user-facing data exploration interface that allows business analysts to gain insights from new data sources in less time; Analytical Designer, a self-service data discovery tool that guides analysts to better insights using GoodData’s Collective Learning and recommendations; finally, Email and Group Sharing makes it easy to deliver insights to the right people across the organization.
"The new capabilities GoodData is bringing to the table make producing insights far more straightforward for our organization," says Chris Marin, senior principal, digital marketing platform and analytics at CSC. "The simple drag-and-drop Analytical Designer will support our data analysis on a daily basis".
More information about GoodData and how it can unlock the accumulation of a company’s experience, best practices, and millions of user interactions can be found on the company's website.
Image Credit: Peshkova / Shutterstock
-

Cybercrime gets smarter and more complex
Publié: avril 22, 2015, 2:00pm CEST par Ian Barker

There are 85,000 new malicious IPs launched every day and the top phishing targets are technology companies and financial institutions.
These are among the findings of a new report from threat intelligence and security company Webroot. The Webroot 2015 Threat Brief provides the latest cyber threat trends collected from tens of millions of users and over 30 security technology partners.
The report finds that the United States accounts for 31 percent of malicious IP addresses, followed by China with 23 percent and Russia with 10 percent. Overall, half of malicious IP addresses are based in Asia.
It shows a 30 percent chance of Internet users falling for a zero-day phishing attack in the course of a year, and indicate a more than 50 percent increase in phishing activity in December 2014, most likely due to the holiday season.
On average, there are nearly 900 phishing attempts detected per financial institution, but over 9,000 attempts detected per technology company. The top five technology companies impersonated by phishing sites are: Google, Apple, Yahoo, Facebook and Dropbox. Looked at by country, the US is by far the largest host of phishing sites, with over 75percent being within its borders.
Looking at mobile systems the report finds that, on average, only 28 percent of apps on the Android platform were trustworthy or benign, a drop from 52 percent in 2013. Almost half were rated were moderate or suspicious, and over 22 percent were unwanted or malicious. Trojans make up the vast majority of malicious threats, averaging 77 percent for 2014.
"Webroot has seen a continued rise in the number of malicious URLs, IP addresses, malware, and mobile applications used to enable cybercriminals to steal data, disrupt services, or cause other harm," says Hal Lonas, chief technology officer at Webroot. "With more breaches at major retailers, financial institutions and technology companies in the headlines and scores of other, smaller breaches in 2014, the trend shows no signs of slowing down. The Webroot 2015 Threat Brief highlights the need for highly accurate and timely threat intelligence to help organizations assess the risk of incoming data, reduce the volume of security incidents, and accelerate response to successful attacks".
2014 has also seen more sophisticated techniques being used to attack PCs. These include the Poweliks registry exploit which doesn't require extra components to deliver infections like ransomware. Webroot also discovered five new families of potentially unwanted application, each demonstrating new social engineering techniques and complexity.
The full report is available as a PDF from the Webroot site and there's a summary of the findings in infographic form below.
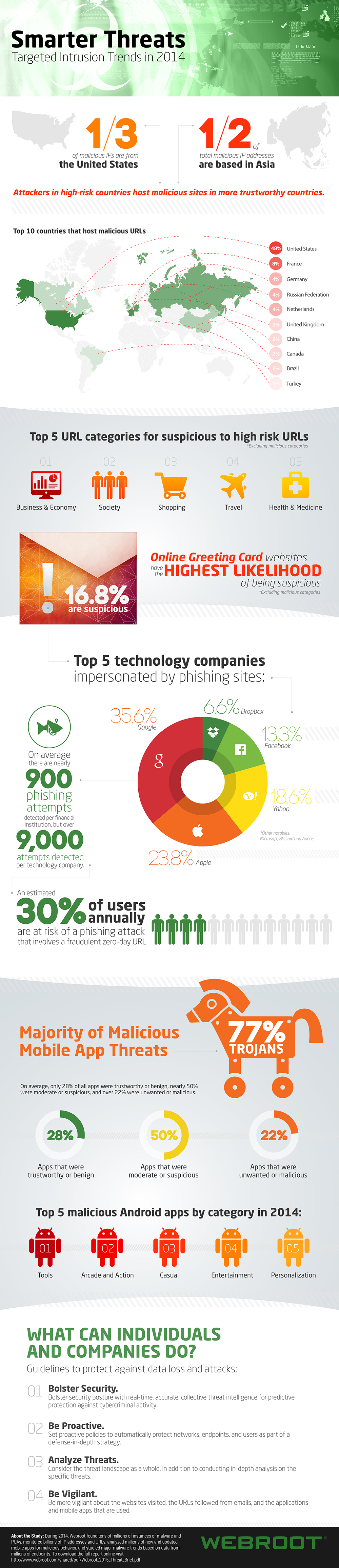
Photo Credit: ra2studio / Shutterstock
-

Funding for SaaS businesses grows by 70 percent
Publié: avril 22, 2015, 1:29pm CEST par Ian Barker

Software as a Service (SaaS) is one of the biggest technology growth areas at the moment. That's reflected in the amounts of capital being pumped into the sector by investors.
A new SaaS Trends Report by Tibco Analytics and venture capital tracker CB Insights shows that funding for SaaS companies was $11.7 billion in 2014, up 70 percent over the past year. SaaS funding has tripled since 2011.
The biggest deal of the last year was Dropbox which received $350 million in extra funding. SurveyMonkey raised $250 million, with online publishing and development specialist Automattic third on $160 million. Cloud storage company Box and security provider Lookout each received $150 million.
Broken down by industry most funding between 2011 and 2014 went to SaaS businesses in the area of business intelligence and analytics (838 deals totaling $6.6 million), followed by CRM and marketing each with around 400 deals totaling over $2 million for each area. Monitoring and security comes next with fewer deals (226) but over $2 million of investment.
Also interesting are the figures for the number of companies exiting venture capital funding, either via mergers and acquisitions or IPOs. Total exits in 2014 were up 66 percent year-on-year. The last quarter of 2014 also saw the highest number of SaaS IPOs in the last four years, companies floating including New Relic and Hubspot. But whilst it's the really big deals that make the news it's important to note that 49 percent of SaaS companies exiting VC funding raised less than $10 million.
Of the companies snapping up SaaS businesses the most acquisitive is Oracle, which went on a $700 million shopping spree to snap up BlueKai and Virtue among others. Next come IBM, Google and Saleforce each of which have made five or more SaaS acquisitions between 2011 and 2014.
The full report with much more information is available to download from the CB Insights website.
Photo Credit: Rrraum/Shutterstock
-

IBM brings threat analytics to the cloud
Publié: avril 21, 2015, 4:57pm CEST par Ian Barker

Last week we reported on IBM's decision to open up its threat intelligence data in X-Force Exchange to help fend off cyber attacks.
Today the company is making its threat intelligence system QRadar available as a cloud service, giving companies the ability to quickly prioritize real threats and free up critical resources to fight cyber attacks.
It will be on offer to customers on a Software as a Service (SaaS) model, with optional IBM Security Managed Services plus integration with the cloud-based X-Force Exchange to provide deeper expertise and flexibility for security professionals.
The product comes in two parts, IBM Security Intelligence on Cloud helps organizations determine if security-related events are simple anomalies or potential threats. Built as a cloud service using IBM QRadar, enterprises can quickly match security event data with threat information from over 500 supported data sources for devices, systems, and applications. This is complemented by pre-defined reports for use cases like compliance, vulnerability management and security incident response.
It also offers Intelligent Log Management using analytics and a hosted, multi-tenant technology to deliver compliance with powerful real-time correlation and anomaly detection capabilities. It supports over 400 platforms allowing security teams to gather data from any device in their organization.
"Organizations are facing a security data tsunami that can overwhelm even the most sophisticated enterprise’s security program," says Jason Corbin, Vice President, Product Management and Strategy at IBM Security. "Security leaders are telling us they want increased visibility through the cloud and control throughout their hybrid IT environments. The option of doing predictive analytics via the cloud gives security teams the flexibility to bring in skills, innovation and information on demand across all of their security environments".
By bringing QRadar to the cloud IBM is aiming to offer its customers improved threat response times, while potentially reducing overall security costs by an average of 55 percent. Significantly improved threat detection is promised too, helping clients automatically handle up to 95 percent of their security events.
More information is available on the IBM Security website.
-

New solution improves protection for business email and documents
Publié: avril 21, 2015, 4:05pm CEST par Ian Barker

Recent security breaches like that at Sony Pictures highlight the difficulty of protecting unstructured information that's held in things like emails and documents.
Security company TITUS is offering a solution with a new version of its TITUS Classification Suite that uses a blend of content and context to automatically classify and protect information as it's handled by users.
Already in use by the French Ministry of Defense and others, TITUS Classification Suite 4 offers organizations a new flexible policy engine that can apply complex rules to protect information without getting in the way of business process or requiring users to remember specific security policies.
Administrators can set up policies to classify email based on recipients; protect messages based on the content or classification of attachments; classify and protect documents based on content, filename or location; or prevent printing of sensitive documents to non-secure devices. Customizable alerts warn users of special information handling conditions or possible impending security violations.
It's capable of integrating with data loss prevention (DLP) solutions, allowing enterprises to optimize security policy, focus on high-risk areas, and capture retention-related metadata for use in archiving or deletion. New integration capabilities, such as with Intel Security Data Exchange Layer (DXL), will allow organizations to enhance their behavioral analytics and reporting capabilities and help them uncover malicious insider threats.
"TITUS is proud to deliver a solution that we have worked toward with the input of hundreds of customers over the last ten years," says Tim Upton, Founder and CEO of TITUS. "From simplifying the administration for our largest enterprise customers, to helping address malicious insider threats, to supporting advanced business rules for challenging problems such as IP protection and export control -- we are delivering a unique ability for enterprises worldwide to protect their most sensitive information".
Classification Suite 4 is comprised of TITUS Message Classification for Microsoft Outlook, TITUS Classification for Microsoft Office, and TITUS Classification for Desktop. Solutions for mobile and Outlook Web App (OWA) are also available. You can find out more and request a free trial on the TITUS website.
Image Credit: ktsdesign / Shutterstock
-

New cloud agent brings enterprises greater security and asset control
Publié: avril 21, 2015, 11:30am CEST par Ian Barker

Increased use of the cloud and hybrid systems is bringing new challenges for businesses needing to ensure their systems are secure and compliant.
A new Cloud Agent Platform (CAP) from cloud security specialist Qualys provides organizations with a flexible solution to assess the security and compliance of their IT assets in real time, whether they're on-site, cloud-based or mobile endpoints.
Qualys CAP provides a lightweight agent that can be installed on any host such as a laptop, desktop, server or virtual machine. Qualys Cloud Agents then extract and consolidate vulnerability and compliance data and update it continuously within the Qualys Cloud Platform for further analysis and correlation. This allows it to offer a continuous view of the security compliance status of a network.
The agent installer can be embedded in system images, deployed via group policy or run from the command line. It can also be embedded into images on cloud servers allowing it to work with environments like Azure. The agent is light on CPU resources, using around five percent at peak and less than two percent in normal operation. Once installed it takes a full assessment of its host while running in the background, and sends that assessment snapshot back to the Qualys Cloud Platform for evaluation. From then on a configurable profile controls how often the agent sends host changes back to the platform to incorporate with the snapshot. Initial, full snapshots are only a few megabytes, and subsequent updates just a few kilobytes. This reduces the network bandwidth consumption to far below that of traditional scanning as well as other agent-based solutions.
CAP also makes for easy inventory management as admins can interrogate all of their systems from a central location. Assets can be monitored for the latest operating system, application and certificate vulnerabilities as well as tracking missing critical patches on each device. The system can also check for compliance with standards like HIPAA.
"Traditional vulnerability scanning methods present a number of challenges for IT security teams who either don’t have the proper credentials, or are scanning assets that aren't always connected to the local network," says Philippe Courtot, Chairman and CEO of Qualys. "Qualys Cloud Agent Platform is a game changer and a new paradigm of continuously assessing IT systems. This platform provides our customers with the flexibility and choice they need to conduct real-time vulnerability and compliance management for IT assets whether it's on-premise, cloud-based or mobile endpoints".
Qualys Cloud Agent Platform is currently available on a trial basis for Windows systems and will go live on May 15. Unix and OSX versions will be available later in the year. For more information and to sign up for a trial visit the Qualys website.
Photo Credit: wavebreakmedia/Shutterstock
-

Microsoft enters the PaaS market with Azure Service Fabric
Publié: avril 20, 2015, 5:16pm CEST par Ian Barker

Cloud computing has stepped up the pace of app development, with many businesses coming under pressure to deliver new services fast.
Following on from last month's launch of the Azure IoT Suite, tech giant Microsoft is stepping into the platform as a service (PaaS) space with Azure Service Fabric.
Mark Russinovich CEO of Microsoft Azure writing on the company's Azure blog says, "Service Fabric was born from our years of experience delivering mission-critical cloud services and has been in production for more than five years. It provides the foundational technology upon which we run our Azure core infrastructure and also powers services like Skype for Business, InTune, Event Hubs, DocumentDB, Azure SQL Database (across more than 1.4 million customer databases) and Bing Cortana -- which can scale to process more than 500 million evaluations per second".
The platform is designed to understand the available infrastructure resources and needs of applications, enabling automatic updating and self-healing so that highly available and durable services can be delivered at hyper-scale. Russinovich adds, "We're now making this battle-hardened technology available for everyone use -- not a version of what we use, but the exact technology we use ourselves".
Key features of Service Fabric include support for creating both stateless and stateful microservices -- meaning that complex applications are made up of small, independent processes talking to each other using APIs -- allowing it to power complex, low-latency, data-intensive scenarios and scale them into the cloud.
This approach makes it easy to roll out changes to parts of an application and to reverse them if things go wrong without needing to rebuild the whole thing. It also allows for efficient load management as Service Fabric can, for example, launch more instances of a service that's under heavy demand.
It includes Visual Studio tooling as well as command line support, which enables developers to quickly and easily build, test, debug, deploy and update their Service Fabric applications whether in test or production environments.
Whilst it will be aimed at Windows development initially, Russinovich says Linux support will be offered in future. More information will be available at next week's Microsoft Build developer conference.
-

New firewall provides stronger protection for hybrid cloud systems
Publié: avril 20, 2015, 11:50am CEST par Ian Barker

As more apps move to the cloud business infrastructures are increasingly fragmented. This can make traditional on-site security tools ineffective in fighting off cyber attacks.
The threat of attacks remains, however, and a new release from security software company Radware is aimed at protecting both on-premise and cloud-based applications, using just one solution.
Radware’s Hybrid Cloud Web Application Firewall (WAF) protects against web attacks and can also defend and mitigate a wide range of DDoS attacks through its always-on DDoS attack protection. It can provide comprehensive detection and mitigation of attacks with minimal false positives and no impact on legitimate traffic.
Radware's WAF protects both in-house and web applications using a single technology. Unlike existing WAF solutions that integrate dual technologies which results in a gap between protection coverage and quality, Radware's single technology approach makes migrating applications to the cloud safer and more secure.
"It's not uncommon for enterprises to distribute their applications both on-premise and in-the-cloud. In addition, we see enterprises employ multiple cloud vendors to host various aspects of their infrastructure. However, having a disparate network infrastructure adds a level of complexity when trying to protect your web applications," says Carl Herberger, vice president of security solutions for Radware. "We have taken actionable steps to provide enterprise with a unified hybrid solution against web-based attacks regardless if protection is needed on-premise or in the cloud and provide better security when moving applications to the cloud as well as ease of security policy orchestration and automation".
You can find more information on the Radware website and the technology will be on display at the RSA Conference this week.
Photo Credit: Andrea Danti/Shutterstock
-

Security professionals worry about technology sprawl as threats evolve
Publié: avril 17, 2015, 2:59pm CEST par Ian Barker

A new study of nearly 14,000 information security professionals worldwide shows that two-thirds of respondents are concerned about the addition of multiple security technologies, often referred to as sprawl.
The Global Information Security Workforce Study (GISWS) produced by (ISC)² a not-for-profit membership body of certified information and software security professionals worldwide, is largest study of the information security profession ever conducted.
"Many of the facets discovered in this year’s workforce study demonstrate that aspects of the information security program are being carried out in IT departments and other business units -- positioning IT as a force multiplier," says David Shearer, executive director of (ISC)². "Cloud adoption rates and projected increases in spending on security tools and technologies are further increasing the need for IT and security departments to function collaboratively. Year after year, the study has shown a workforce shortage; but now, we're finding that the shortage is being compounded with issues that are becoming more prevalent, such as configuration mistakes and oversights that can be detrimental to the security posture of global businesses".
Among the findings of the study are that phishing is the top threat technique employed by hackers, cited by 54 percent of respondents, and that the estimated time to fix an attack following a system or data compromise is getting longer. An average attack takes between two and seven days to fix according to 44 percent.
It also shows that respondents think additional training and education are needed most in the areas of cloud computing (57 percent), BYOD and incidence response (both 47 percent). Respondents felt that when it comes to retaining information security professionals, support for training and professional security certifications is essential. Lack of in-house skills is cited by 49 percent as the reason for turning to outsourcing.
There's much more detail in the full report which can be downloaded from the (ISC)² website and there will be a session discussing the findings at the RSA Conference on Monday April 20.
Image credit: fotogestoeber / Shutterstock
-

Red Canary seeks to bring simpler endpoint security to businesses
Publié: avril 17, 2015, 12:30pm CEST par Ian Barker

The endpoint is the most vulnerable link in enterprise security, constantly under attack and prone to human error. Yet the security products designed to protect it are subject to high levels of false positives.
The result is that providing effective protection can be complex and stretch the resources and budget of even quite large organizations.
Denver-based Red Canary, founded by a team with a strong background in security and defense intelligence is offering a four-pronged approach to detecting threats in real time and eliminating false positives.
It uses a combination of behavioral analysis to detect malicious software or activity; anomaly detection to pick up activity such as logons from other locations; binary analysis to look at the reputation of binaries but also their potential for harm; and threat intelligence to protect across the customer base.
Crucially every suspicious event flagged by the company's Threat Detection Engine is then subject to human review. "Businesses have become over reliant on technology to protect their endpoints. This is why Red Canary uses a human analyst team to eliminate false positives," Red Canary's CEO Brian Beyer says. "Smaller companies can't afford the expertise to do this in house".
Combining best of breed technologies and adding human review Red Canary enhances response by detecting threats in hours rather than weeks, by delivering actionable detections, and by providing extensive endpoint visibility.
"Enterprises have to identify assets, know what they're defending and have the right systems in place if their perimeter is breached," adds Beyer. "This means investing in people and giving them the right tools to do the job."
You can find out more about Red Canary's approach to endpoint protection on the company's website.
Image credit: bannosuke / Shutterstock
-

WildPackets becomes Savvius and switches focus to security
Publié: avril 16, 2015, 4:54pm CEST par Ian Barker

Internet performance specialist WildPackets is changing its name to Savvius and at the same time is also launching its first security appliance.
"This name change comes at a defining moment in our history," says Tim McCreery, CEO of Savvius. "We are deepening our commitment to network performance management solutions and expanding our focus to include support for security forensics. Our team is united in providing great solutions and world-class support to our customers and partners".
The company's first security appliance the Savvius Vigil is able to intelligently store months of packet-level information in order to assist security investigations. It means packets related to a breach can be examined weeks or even months after the incident occurs, providing information that is often vital to a full understanding of the threat.
There's typically a lag between a threat entering a network and it being detected which leads to a gap in the data analysts have available to study the issue. Once a threat is spotted, Vigil responds by intelligently storing the network packets associated with that event, including packets that led up to it, those that were created immediately after, and those in related conversations. It will allow security professionals investigating a weeks- or months-old security breach to add specific network packet data to their investigation -- something that was previously unachievable.
"Security threats begin at the packet level. Unfortunately, months of long-term packet-level forensics have been a missing piece of the security puzzle for far too long," says Mandana Javaheri, Chief Technology Officer of Savvius. "Until today's announcement, organizations have not had a practical way to store long-term network packet data. With Savvius Vigil, security analysts can have greater insight into security incidents that occurred in the past".
More information about Savvius Vigil is available on the company's website.
Photo Credit: Sergey Nivens/Shutterstock
-

IBM opens up threat intelligence data to help combat cyber attacks
Publié: avril 16, 2015, 4:02pm CEST par Ian Barker

With cyber attacks often being driven by organized crime rings and the tools and expertise behind them widely shared, threat intelligence is more important than ever to fend them off.
Announcing today that it's opening up more than two decades' worth of cyber threat intelligence IBM is seeking to unite, mobilize and rally the private sector to defend itself against increasingly sophisticated and organized cyber threats.
It's set up a new cloud platform called X-Force Exchange which builds on IBM's scale in security intelligence, integrating its portfolio of deep threat research data and technologies like QRadar, thousands of global clients, along with the acumen of a worldwide network of security analysts and experts from IBM Managed Security Services.
"The IBM X-Force Exchange platform will foster collaboration on a scale necessary to counter the rapidly rising and sophisticated threats that companies are facing from cybercriminals," says Brendan Hannigan, General Manager of IBM Security. "We're taking the lead by opening up our own deep and global network of cyberthreat research, customers, technologies and experts. By inviting the industry to join our efforts and share their own intelligence, we're aiming to accelerate the formation of the networks and relationships we need to fight hackers".
The X-Force Exchange features over 700 terabytes of raw aggregated data supplied by IBM. This makes it one of the largest and most complete catalogs of vulnerabilities in the world. Data includes threat information based on monitoring of more than 15 billion security events per day, malware threat intelligence from a network of 270 million endpoints, threat information based on over 25 billion web pages and images, intelligence on more than 8 million spam and phishing attacks, and reputation data on nearly a million malicious IP addresses.
The data will continue to grow, be updated and shared. The platform is able to add up to a thousand malicious indicators every hour including real-time information which is critical to the battle against cybercrime.
Within the platform, IBM intends to provide future support for STIX and TAXII, the emerging standard for automated threat intelligence sharing. This will make for easy extraction and sharing of information to and from the exchange, as well as enabling seamless integration into existing security systems.
You can find more information about IBM X-Force Exchange on the company's website.
Image Credit: Tomasz Bidermann/Shutterstock
-

2014: The year data breaches came of age
Publié: avril 15, 2015, 5:24pm CEST par Ian Barker

There were 783 reported data breaches in 2014, up 27.5 percent over the previous year and the most in any year of the past decade. The average cost of each of those breaches was $3.5 million, up 15 percent over 2013.
These are among the statistics highlighted in a new infographic from user behavior intelligence specialist Exabeam. Ten breaches each led to more than a million records being reported stolen, the biggest being Home Depot with 56 million records.
But whilst retail -- partly distorted by that massive Home Care figure -- accounts for the highest percentage of records stolen, it's the health care sector that accounts for the majority of breaches. Health care reported 333 breaches in 2014, accounting for 42.5 percent of the total. Retail comes second on 33 percent with government and military third on 11.7.
How breaches happen is interesting too. Whilst 29 percent were down to hacking, 15.1 percent were laid at the door of sub-contractors or third-parties, and 12.5 percent physical theft. Accidental exposure (ooops!) accounted for 11.5 percent, employee negligence 10.9 percent and insider theft 10.2 percent.
You can see the full infographic below.
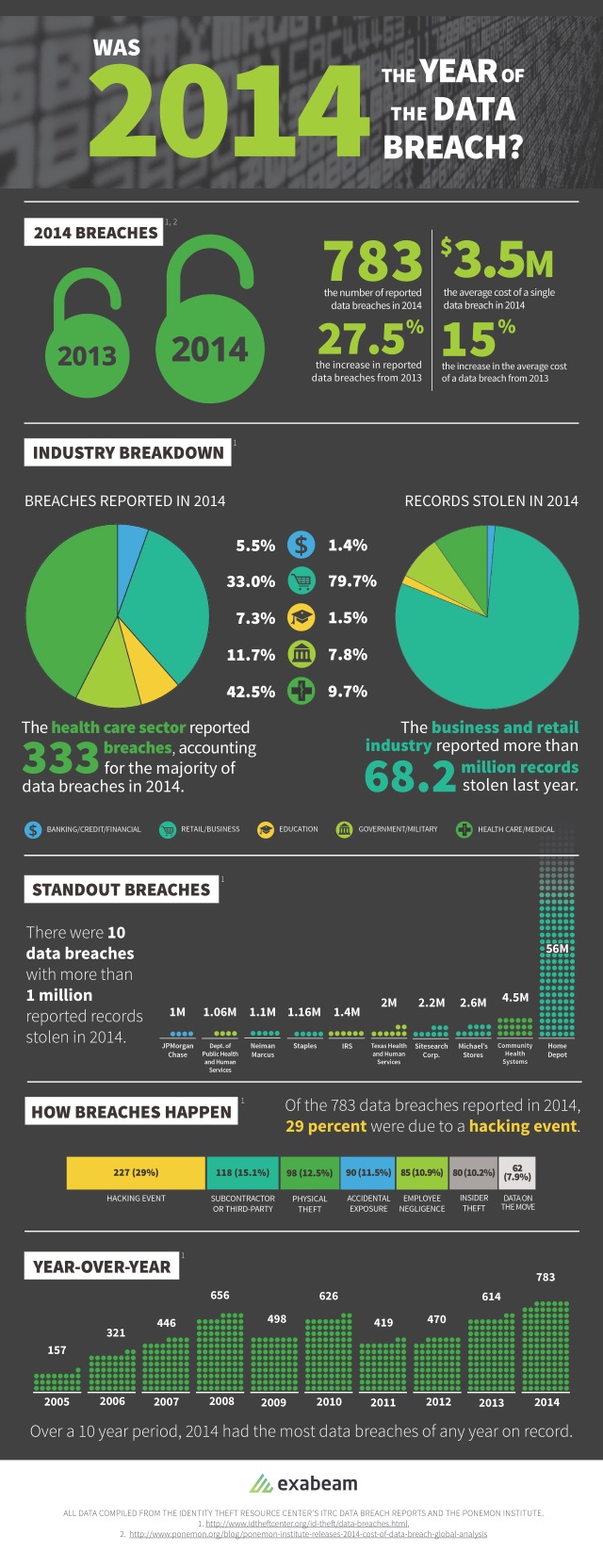
Image Credit: Pavel Ignatov / Shutterstock
-

HighQ brings confidential collaboration to the cloud
Publié: avril 15, 2015, 3:54pm CEST par Ian Barker

There are lots of options for business collaboration but security of data is always a concern, especially when implementing cloud solutions.
The answer to these worries may lie with cloud collaboration specialist HighQ which is launching Collaborate 3.4, the first hybrid version of its platform providing both cloud and on-premise secure storage of data.
In addition to hybrid storage, the new Collaborate platform offers the ability to store encryption keys onsite, giving companies a safeguard with which to secure their data against threats, whether hackers, data-center workers or NSA snoopers.
"Collaborate 3.4 opens up important new use cases for customers around the world," says HighQ's Chief Strategy Officer Stuart Barr. "Organizations can collaborate on any device with the utmost levels of data sovereignty and security -- and pass those benefits on to their own clients. Our customers require all their data to stay protected and confidential, and we listened, evolving Collaborate to meet the most stringent requirements".
Key features include hybrid storage which gives customers the option of storing files within a particular jurisdiction or their own network. A custom-build appliance can be used to select where to store files for each individual workspace -- on-premise, in another location of the user's choice, or in one of HighQ's own data centers.
In addition encryption key management lets customers store their encryption keys on-premise rather than in the cloud where they're potentially vulnerable. This adds another layer of protection and lets companies retain full oversight of their data.
Microsoft Office integration enables users to seamlessly open and edit files from Collaborate in Word, Excel and PowerPoint. Once a file is closed, Collaborate automatically uploads and publishes the latest version. A new Outlook plugin also lets users securely transfer files from within Outlook. Plus there's a personal file syncing feature which provides a secure alternative to public cloud services services by letting users sync personal files to their PC or Mac.
"Collaborate 3.4 completes the vision that we first laid out in 2012," says Barr. "It combines the best aspects of enterprise file sharing and sync with social collaboration and secure team workspaces. We’re proud to be the only provider to be built from the ground up for the world’s most sensitive industries, and to continually keep pace with the most advanced privacy, security and data-sovereignty requirements".
You can find out more about Collaborate on the HighQ website.
Image Credit: Lightspring / Shutterstock
-

New malware family attacks retail systems
Publié: avril 15, 2015, 3:09pm CEST par Ian Barker

Only two weeks ago we reported on the underlying vulnerabilities that put point-of-sale systems at risk. Now acting as part of an investigation by the US Secret Service, researchers at security services company Trustwave have identified a new family of PoS malware.
Cyber criminals are already using the malware -- which researchers have named "Punkey" in an obscure '80s sitcom reference -- to infect businesses. Payment card information and more than 75 active victim IPs were found as part of the investigation.
Trustwave doesn't know the number of businesses that have been infected but its researchers have seen multiple command and control servers and multiple campaigns related to Punkey and it appears that a number of malware authors have been at work on the source code used in the campaigns.
The software hides inside Windows Explorer and scans other processes for card holder data, sending any details found to a server. It periodically checks in with the server to see if there are any updates such as new programs to run or if an update to the malware is needed. The Punkey malware also performs keylogging, capturing 200 keystrokes at a time and sending them back to the server. Thus the attacker can capture usernames, passwords and other important information. All of these functions run continuously and will start up again if the computer is rebooted.
Trustwave notes that, "The injection and hiding process with Punkey is more advanced than most of the point-of-sale malware that we currently see. In particular, command and control server interaction with the malware is something we don't see very often. The ability to execute arbitrary programs and update the malware is not something typically seen in point-of-sale malware".
You can read more about the discovery on the Trustwave blog.
Image Credit: Sedlacek / Shutterstock
-

New partnership helps businesses analyze and present Birst data
Publié: avril 15, 2015, 1:28pm CEST par Ian Barker

Business intelligence systems have in the past delivered large amounts of data but in a format that wasn't necessarily easy to use as it was extracted from legacy systems.
In an effort to make BI data more accessible, cloud intelligence and analytics specialist Birst has announced a partnership with Tableau Software to combine the latter’s powerful visual analytics with Birst’s agile and scalable Cloud BI data platform through an ODBC connector.
"Tableau's mission is to help people see and understand their data. Insightful visual analytics require access to every source of data across an organization," says Dan Jewett, Vice President of Product Management at Tableau Software. "By helping Birst create a connector to Tableau, our companies are continuing this vision by elevating the analytics experience for customers".
The combination enables Birst customers to create dynamic, interactive visualizations that are based on a single source. It offers the speed and ease-of-use that people want in analytics combined with the modern, enterprise-grade data architecture needed to run today’s businesses.
"In an era where legacy BI vendors are losing ground, you have two forward-thinking technology companies like Birst and Tableau, typically seen as competitors, now working together to help more people make better decisions with data," says Jay Larson, CEO of Birst. "The reality is that Birst's and Tableau's technologies are much more complementary than competitive, and we’re thrilled about this unique opportunity to work with Tableau to deliver analytics to everyone, from developers to data analysts to business users, without forcing companies to make trade-offs between speed, ease-of-use and data governance".
More information is available on the Birst website and you can sign up for a webinar on the link up taking place on May 21.
Image Credit: leedsn/Shutterstock
-

Salesforce integration helps PandaDoc deliver better sales content
Publié: avril 14, 2015, 4:42pm CEST par Ian Barker

Producing documents has in the past been the slowest part of the sales process. Collecting information and putting it into quotes and proposals can take up a lot of sales staff time that could be better used in other tasks.
California-based PandaDoc is announcing its software's integration with Salesforce to make sales proposal and quote generation faster and more personalized.
PandaDoc combines everything sales reps need in one place to build and deliver attractive content making the whole process fast and efficient. It allows users to connect their document templates with Salesforce CRM data to close deals faster. The integration gives full document creation functionality within Salesforce, allowing the document creation process to start at the earliest opportunity. PandaDoc's software pulls relevant data from the sales lead, including general information, contacts, product, and pricing details, putting these into preset PandaDoc templates.
"With business processes all finding their way to the cloud, it seems that sales documents are the last to make the leap. Dealing with Word and Excel results in long turnaround times that slow down our sales teams," says Mikita Mikado, Co-Founder and CEO of PandaDoc. "Your salespeople are spending more than half of their day doing mundane back-office work. We want to provide your team with all the building blocks that they need to speed up creation of sales collateral, and to ensure a consistent, seamless experience for the end clients".
Other solutions on the market often require sales teams to use separate software for document generation, pricing configuration, document analytics, and electronic signing. Since PandaDoc includes everything it cuts the time taken to create and send documents to just minutes.
For more information on PandaDoc and to sign up for a 14-day free trial you can visit the company's website.
Image Credit: EDHAR / Shutterstock
-

Attackers switch tactics to gain access to corporate networks
Publié: avril 14, 2015, 1:42pm CEST par Ian Barker

In the current information security climate it seems that falling victim to some form of cyber attack is just a matter of time. If you haven't been hit yet chances are you will be soon.
The latest Internet Security Threat Report from Symantec shows that five out of six large companies were targeted in 2014, a 40 percent increase over the previous year, and that attackers are shifting their tactics when targeting corporations.
Networks continue to be breached using highly-targeted spear-phishing attacks, which increased a total of eight percent in 2014, confirming the findings of another report today. Over the last year the precision of these attacks has increased, they've used 20 percent fewer emails to successfully reach their targets and incorporated more drive-by malware downloads and other web-based exploits.
Symantec has also observed attackers using stolen email accounts from one corporate victim to spear-phish other victims higher up the company chain. Attacks have been taking advantage of companies' management tools and procedures to move stolen intellectual property around the corporate network before exporting it. The report reveals the building of custom attack software inside the networks of their victims to disguise attacker's activities too.
"Attackers don't need to break down the door to a company's network when the keys are readily available," says Kevin Haley, director of Symantec Security Response. "We're seeing attackers trick companies into infecting themselves by Trojanizing software updates to common programs and patiently waiting for their targets to download them -- giving attackers unfettered access to the corporate network".
Although email remains a popular source of attack criminals are increasingly experimenting with other methods using mobile devices and social media. "Cybercriminals are inherently lazy; they prefer automated tools and the help of unwitting consumers to do their dirty work," adds Haley. "Last year, 70 percent of social media scams were shared manually, as attackers took advantage of people's willingness to trust content shared by their friends".
Ransomware remains lucrative too, rising 113 percent last year. More worrying still, rather than the traditional ransomware approach of pretending to be a law enforcement agency levying a fine for stolen content, Symantec has noted a rise of crypto-ransomware which holds a victim's files, photos and other digital content hostage without masking the attacker's intention. There were 45 times more victims of crypto-ransomware attacks than in 2013.
The full report is available as a PDF from the Symantec website, or you can sign up to hear Haley discuss the findings in a webcast taking place at 10am Pacific Time tomorrow (April 15).
Photo Credit: ra2studio/Shutterstock
-

Wowza makes live video streaming easier for enterprises
Publié: avril 13, 2015, 4:38pm CEST par Ian Barker

Streaming isn't just for broadcasters any more, it's become a useful commercial tool too, allowing meetings, conferences and events to be shared with a worldwide audience. However, it can be tricky to implement.
Wowza Media Systems is launching its latest Wowza Streaming Cloud and Wowza Streaming Engine Pro, increasing the power and ease of streaming online video and extending flexible options to organizations looking to stream live content.
Wowza's pre-configured settings help inexperienced users get started in minutes, while advanced options allow power users to create tailor-made solutions with more control and flexibility. Customers can stream directly from cameras or encoders without the need for additional streaming infrastructure.
"Businesses that stream live content demand solutions that can adapt to meet their ever-changing streaming needs, while consistently delivering high-quality video," says David Stubenvoll, CEO and co-founder of Wowza Media Systems. "Now with Wowza Streaming Cloud and Wowza Streaming Engine Pro, customers can stream professional-quality content to global audiences with a personalized solution that is the perfect mix of economics, control and flexibility".
Customers benefit from adaptive bitrate technology which delivers high-quality experiences regardless of users' bandwidth and devices. Wowza Streaming Cloud includes a content delivery network (CDN), so users know their video will work no matter the size or location of their audience.
Users have complete control over their content and brand as it works without imposing ads or Wowza branding. They can also mix and match Wowza and third-party components to meet their individual needs for economics, flexibility and control. Flexible APIs for both Wowza Streaming Cloud and Wowza Streaming Engine Pro allow users to use existing systems and business processes or add customized streaming services as needed. Advanced features include access to transcoding in the cloud and customization for CDNs.
You can learn more about Streaming Cloud and Streaming Engine Pro on the Wowza website.
Image Credit: Thampapon / Shutterstock
-

Four into one will go with new TV streaming device
Publié: avril 13, 2015, 3:24pm CEST par Ian Barker

We're all familiar with the dilemma of what to watch, what to record and what to seek out on a catch up service later. There's so much TV content available these days that tough decisions are needed.
It's especially hard for sports fans who may find themselves with several events going on at the same time. Trying to catch up with one or more of them later runs the risk of accidentally finding out the result in advance, so what's the solution?
It might be a new TV streaming device from 4SeTV which allows you to watch up to four live television shows at once on a tablet, smartphone, or TV. Alternatively, up to four people can view an individual live show of their choice on four different devices at the same time.
4SeTV uses over-the-air broadcasting and then streams the HD content you want to see to your connected devices in your home network. 4SeTV hooks up to your TV antenna and then connects to your router with an Ethernet cable allowing content to be streamed out to your devices via Wi-Fi. You can see how it works in the video below.
"Like many of us, I love relaxing and watching TV, but my busy life leaves me very little spare time to do so," says Hyung Lim, president and founder of 4SeTV. "One day I was staring at my big screen TV, and it hit me -- what if I could stream more than one feed at once and make the most of my TV time? Not only have we created the technology to make this a reality and become the only company to offer a four screen TV experience, we've done it in the form of a simple streaming device that anyone can use -- it's ready to go right out of the box".
4SeTV is available to pre-order on Kickstarter which allows early adopters to secure a unit for $99.
-

MariaDB improves security and performance for cloud databases
Publié: avril 10, 2015, 3:03pm CEST par Ian Barker

Open source database solutions specialist MariaDB is launching the latest version of its MariaDB Enterprise product offering high availability, scalability and security capabilities for enterprises.
It's aimed at meeting the requirements of web scale businesses for performance, scalability, disaster recovery and business continuity, along with database solutions that support flexibility including interoperability across SQL and NoSQL.
"Enterprises are facing massive volumes of data they need to process and manage effectively and securely. In the SaaS scenario in particular, databases have to be capable of responding to huge spikes in demand while ensuring high availability. E-commerce providers for example need their database to be equipped with the latest in performance, agility and security," says Patrik Sallner, CEO of MariaDB. "We recognize the tremendous value the open-source community and cutting-edge companies like Google bring in delivering that innovation. At MariaDB we see our role as curating, further evolving and hardening what the community has contributed to deliver a truly enterprise-grade product and service".
MariaDB Enterprise is offered as a subscription service and is made up of server binaries based on the leading open-source MariaDB community server. It also has a selection of tools, connectors and subscription services to address the needs of mission-critical applications. Users have the option to deploy MariaDB MaxScale, a database-aware proxy platform that provides capabilities such as load balancing and firewall protection without the need to modify existing applications.
New MaxScale features in this release include advanced security protection against SQL injection attacks, enhanced scalability, support for industry-standard monitoring with a Nagios Plugin architecture, and improved security and systems maintenance with timely alerts from MariaDB Enterprise Notification Services.
You can find out more about MariaDB Enterprise on the company's website and there's also a YouTube video explaining how it works with IBM's POWER8 processor technology.
Image Credit: wavebreakmedia / Shutterstock
-

SysCloud launches security and backup solution for Google Apps
Publié: avril 9, 2015, 4:51pm CEST par Ian Barker
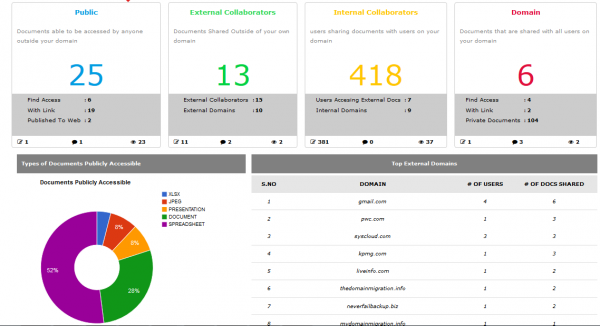
Placing your data in the cloud doesn't mean that you remove the need to properly protect it. For Google Apps users, New York-based SysCloud is launching a comprehensive security and backup solution in the form of SysCloud 360.
In addition to offering Google Apps security and protection in a single interface, the system features real-time backup and compliance capabilities.
Continuous real-time backup, protects against accidental loss or malicious deletion. It's also designed to help organizations meet compliance objectives. The application masks sensitive data by regulating access control and strengthening admin oversight, as well as assisting in user education for Google App solutions.
"SysCloud 360 marks a new era in protection against data theft and loss on Google Apps," says Vijay Krishna, CEO of SysCloud. "Too often, user errors on Google Apps cause unintentional -- but preventable -- security breaches. SysCloud's new SysCloud 360 solution gives businesses the tools they need to protect sensitive information and data across their Google Apps ecosystem and comply with regulatory standards. SysCloud 360 takes care of meeting compliance objectives, from PCI to FERPA, so businesses don’t have to worry".
SysCloud 360's features include built-in SOX, PCI, FERPA, CIPA AND SOC2 policy templates to easily deploy automated enforcement. Protection for the entire Google Apps suite against loss of email, contacts, calendar, documents and sites at any time. Recovery options cover everything from a single data item to an entire account. Policies can be created to safeguard personal information and ensure data is not accidentally exposed to third parties. It also offers insight into how data is being shared within an organization or to the public, along with automatic enforcement of Google Drive security policies to protect against exposure of sensitive data.
You can visit the SysCloud website for more information and to sign up for a free trial.
-

Botnets and how they're linked to corporate data breaches
Publié: avril 9, 2015, 3:22pm CEST par Ian Barker

Data breaches that result in the loss of large volumes of information continue to make the headlines. One of the ways companies can guard against attack is by understanding what makes them vulnerable.
Security ratings firm BitSight has performed an analysis of the risk factors that make up its BitSight Security Ratings against publicly disclosed data breaches. What emerges from its study is the important role which botnets play in attacks.
The report notes that, "Although a botnet compromise may not always equate to data loss, it invariably means that one or many protective controls have failed and that at least some data or system confidentiality, integrity, or availability is at risk".
For each area of risk BitSight assigns an overall letter grade (A-F), indicating the company's performance relative to others. The grade takes into account factors such as frequency, severity, and duration (for events) as well as record quality, evaluated based on industry-standard criteria.
The study shows that BitSight botnet grades -- which are a component of the top-level security rating -- can serve as a key metric in predicting the likelihood of a breach. Among companies with botnet grades of A, the percentage having breaches was only 1.7 percent; for those with a B or lower grade, the incidence of breaches was more than twice as high at 3.7 percent.
Looked at by industry, financial companies are most likely to have an A botnet grade (74 percent) and those in the education sector the least (23 percent, with 33 percent getting the lowest F rating). Retail, healthcare and utilities all fall somewhere in between with around 50 percent getting A scores.
The report concludes that, "The implications for organizations across industries are that botnet infections cannot be ignored. Companies with poor botnet grades have been breached far more often than those with good grades, and actions should be taken to mitigate these risks".
The full report is available to download from the BitSight website.
Image credit: Gunnar Assmy/Shutterstock
-

IBM sets new record for tape storage -- and why you should care
Publié: avril 9, 2015, 3:15pm CEST par Ian Barker

If you began your IT career in the 1980s or before you probably have fond memories of spooling up half-inch, nine-track magnetic tapes. You'd be forgiven for thinking that in the age of affordable large capacity hard disks and SSDs tape storage was now firmly confined to the past, but not so.
IBM scientists working with FUJIFILM of Japan, have demonstrated a recording density of 123 billion bits per square inch on tape, the equivalent of a palm-sized 220 TB tape cartridge.
To make that a bit more meaningful 220 TB is equivalent to 1.37 billion text messages or the text of 220 million books. It also represents a 22 fold improvement over IBM's current enterprise tape product.
Tape has of course traditionally been used as an archive or backup medium as it has a longer shelf life than disk. Even today 500 exabytes of archive data are still held on tape storage systems according to analyst company Coughlin Associates. But thanks to its low cost per gigabyte it's becoming an attractive option for big data and cloud applications.
IBM Research scientists in Zurich are exploring the integration of tape technology with current cloud object storage systems like OpenStack Swift. This would enable object storage on tape and allow users to seamlessly migrate cold data to a low-cost, highly durable cloud based storage tier perfectly suited for back-up or archive use. So far from being stuck in the past tape could be the storage medium of the future.
"With this demonstration, we prove again that tape will continue to play an important role in the storage hierarchy for years to come," added Evangelos Eleftheriou, IBM Fellow. "This milestone reaffirms IBM's continued commitment and leadership in magnetic tape technology".
The 123 million bits per square inch storage density has been achieved using a number of new technologies. These include a set of advanced servo controls that enable head positioning with an accuracy better than 6 nanometers. This allows a track density of 181,300 tracks per inch, a more than 39 fold increase over an industry standard LTO6 tape cartridge. There's also an enhanced write field head technology enabling the use of much finer barium ferrite (BaFe) particles, and innovative signal-processing algorithms for the data channel, based on noise-predictive detection principles.
IBM will be demonstrating the technology at the National Association Broadcasters Show in Las Vegas next week. There's an overview in infographic form below and you can find out more about the company's history with tape storage on IBM's website.

Image Credit: Claudio Divizia / Shutterstock
-

Imperva brings network layer DDoS protection to smaller enterprises
Publié: avril 9, 2015, 3:12pm CEST par Ian Barker

Enterprise data can be put at risk from DDoS attacks, but whilst larger businesses have the resources to guard against these attacks smaller ones sometimes struggle.
Security company Imperva is committed to protecting data for all sizes of business with the release of its latest Imperva Incapsula cloud-based application delivery service.
Additions to the product include a turnkey integration with leading security information and event management (SIEM) tools, external monitoring of network infrastructures, and multi-protocol DDoS protection for dedicated customer IP addresses. Combined, these new enhancements bring advanced security capabilities to organizations of all sizes, without the need for larger security and networking teams.
Incapsula DDoS Protection and Website Security now integrates directly with leading SIEM platforms including HP ArcSight and McAfee Enterprise Security Manager. Integration includes a connector that delivers event logs produced by Incapsula directly to the existing SIEM, as well as advanced reporting and viewing options that allow users to spot and analyze attack patterns.
It offers external monitoring of network infrastructure based on sampling of data from routers and for smaller organizations it allows individual IP addresses to be secured. This means that businesses with proprietary protocols and a small number of IP addresses -- typical of SaaS, gaming and mobile application companies -- now have access to the same advanced DDoS protection as bigger enterprises.
"Unfortunately, we believe DDoS attacks are not only becoming more prevalent, but they continue to grow in sophistication. Many smaller organizations need protection that can keep up with evolving threats yet doesn’t require hiring an entirely new security team," says Jim Davis, senior analyst at IT research specialist the 451 Group. "External monitoring and protection for smaller networks is needed for a host of businesses with proprietary protocols and demanding users, notably gaming servers and mobile applications".
More details on the new release and its features are available on the Incapsula blog.
Image Credit: rosedesigns / Shutterstock
-

New endpoint protection offers instant detection and response to unknown threats
Publié: avril 7, 2015, 5:14pm CEST par Ian Barker

Traditional endpoint protection is usually reliant on the use of signature-based detection systems. But of course these don't spot zero day attacks that can slip in before the antivirus software catches up.
Security solutions provider Endgame is using its extensive experience providing security intelligence and analytics solutions to the US government to offer an enterprise solution focusing on protecting critical infrastructure, enabling customers to detect and respond faster to unknown threats, and preventing damage and loss.
It uses detailed attack-chain analysis to allow enterprise security teams to accelerate detection, investigation, containment and remediation. Endgame Enterprise captures and analyzes the details of an attack, giving incident responders attack-path intelligence and insight into the consequences of cyber threats. Endgame Enterprise features military-grade adversary intelligence and state-of-the-art threat detection algorithms. These are designed to detect zero-day and advanced threats without the use of signatures -- using an inherent ability to detect suspicious behavior.
"Attacks are becoming increasingly sophisticated, but you don't need to have a PhD in computer science to stay one step ahead of them. Companies need to quickly assess the extent and potential impact of relevant incidents, which is where many traditional solutions fail," says Endgame CEO Nate Fick. "Our research on advanced threats, vulnerabilities and attack patterns, and our history protecting some of the nation’s most sensitive national security assets, allows us to understand defenses from the adversary’s perspective. Endgame Enterprise empowers existing security teams to accelerate the investigation and remediation of threats that would otherwise go undetected".
By building a profile of malicious behavior, the software provides advisories to an administrative console, without impacting performance or user experience. Security teams are presented with a comprehensive picture of the attack to support rapid containment and allow remedial action. These advanced visualizations complement forensic tools and help forensic analysts understand, in detail, how a breach occurred and help prevent future occurrences.
You can learn more on the Endgame website and the company will be at the RSA Conference.
Photo Credit: watcharakun / Shutterstock
-

AlienVault delivers extra layer of security for Amazon Web Services
Publié: avril 7, 2015, 3:06pm CEST par Ian Barker

Amazon's AWS cloud offering is hugely popular, with over a million users. But it presents a security challenge for IT teams as it uses a 'shared security model' protecting the underlying infrastructure but relying on users to secure anything they place on there.
Security startup AlienVault is aiming to make protecting AWS systems easier with the launch of its Unified Security Management for AWS, offering asset discovery, vulnerability assessment, behavior monitoring, alerting and integrated threat intelligence.
USM for AWS takes the burden off IT teams -- particularly those with limited resources -- by providing the essential security capabilities needed to quickly identify and respond to malicious behavior and secure AWS environments. It's a cloud-native product and offers full visibility into AWS environments using the AWS API, providing analysis of the use of built-in security features like CloudTrail and Security Groups to improve the environment's security from day one.
"USM for AWS is a great way to meet your shared security responsibilities on top of the reliability and protection already offered by AWS," says Russ Spitler, VP of Product Strategy at AlienVault. "USM for AWS significantly reduces complexity and deployment time so that you can go from installation to first insight in about 15 minutes".
Key features of the product include maximum visibility of potential threats or misconfigurations in the AWS environment, making it easier to use Amazon's standard features like CloudTrail and Security Groups. Built-in security capabilities offer asset discovery, vulnerability assessment, behavior monitoring, log management, alerting and event correlation. This enables IT or security practitioners to quickly update and respond to malicious behavior and insecure AWS configurations. It also includes threat intelligence to identify the most significant issues targeting an organization's network, with context-specific remediation and threat mitigation guidance, powered by AlienVault Labs and AlienVault Open Threat Exchange (OTX).
USM for AWS will be on display at the RSA Conference later this month or you can find out more on the AlienVault website.
Photo Credit: jörg röse-oberreich/Shutterstock
-

Nexmo helps brands engage with consumers via chat
Publié: avril 7, 2015, 2:21pm CEST par Ian Barker

Companies are constantly on the lookout for new methods of interacting with their customer base but it can be hard to integrate these with existing systems.
Cloud communications firm Nexmo is launching a new API that allows a chat application to interact with a customer service platform.
The Nexmo Chat App API helps brands consolidate all chat messages into their existing communication platforms, eliminating the need to manually manage communications over individual chat applications. The Chat App API does this by automatically detecting and connecting brand messages with the appropriate chat application in real time.
It lets marketing, sales or customer support staff send one message and have it appear on all relevant chat applications at once. Nexmo also works directly with each chat application to ensure messages appear correctly on all platforms. In addition it informs brands which features are available on each chat application. Through Nexmo's carrier relations it knows the cultural restrictions in play on each network and can make them clear to brands.
"We live in an always-on world, where customers expect to be engaged anytime, anywhere and on their preferred channels," says Nexmo CEO and co-founder, Tony Jamous. "This means the bar for customer engagement has risen dramatically. At the same time, solutions that are put in place need to be scalable, near real time and cost efficient, and that’s where we see the tremendous opportunity for the Chat App API. Adding the Chat App API to our portfolio of industry-leading messaging and voice APIs transforms Nexmo from a company helping brands navigate the current landscape of mobile communications to a resource that brands can come to as customer communications dynamically changes shape".
The Nexmo Chat App API currently supports messaging on WeChat and Line. The company will be adding support for additional chat apps, service platforms and new features in the coming months. You can find out more and sign up for beta access on the Nexmo website.
Image Credit: Rawpixel / Shutterstock
-

Cisco launches new Advanced Malware Protection for enterprises
Publié: avril 7, 2015, 11:09am CEST par Ian Barker

Enterprise security is a constant battle between good and evil which means that businesses can't afford to be complacent when it comes to guarding against threats.
Networking specialist Cisco is unveiling a number of new capabilities and services designed to give security professionals the edge in protecting against and dealing with attacks.
These changes come from the addition of AMP Threat Grid to the Cisco Advanced Malware Protection (AMP) portfolio. This integrates innovation gained through the company's acquisition of ThreatGRID last year. It provides the latest malware threat intelligence and dynamic malware analysis capabilities, both on‐premise and in the cloud, to strengthen Cisco AMP's continuous analysis and zero‐day detection capabilities.
Plus to help bridge the gap between the availability of security practitioners and industry needs, Cisco is introducing Incident Response Services. This aims to equip organizations with teams of information security experts who can leverage threat intelligence and best practices for readiness and response.
"Every day, organizations are faced with advanced threats that infiltrate and persist in company environments for months before they are discovered," says Marty Roesch, Vice President and Chief Architect of Cisco Security Business Group. "We believe that the most effective way to address these real‐world challenges is continuous threat protection against these attacks. Further enhancements like advanced correlation of indicators of compromise, vulnerability mapping and expanded retrospective security further differentiate Cisco AMP and strengthen security teams’ responses before, during and after an attack".
As well as providing intelligence at a high level with AMP Threat Grid the company aims to protect at all levels. AMP for Endpoints provides a list of hosts that contain vulnerable software, a list of the vulnerable software on each host, and the hosts most likely to be compromised. AMP identifies vulnerable software being targeted by malware and the potential exploit, and provides customers with a prioritized list of hosts to patch. It also continuously monitors file activity allowing it to pick up suspicious behavior and track back to the origin of potential threats.
AMP Threat Grid will be demonstrated at the RSA Conference in San Francisco on April 20-24 or you can find out more on the Cisco website.
Image Credit: alphaspirit/Shutterstock
-

Inateck BP2001 Bluetooth stereo speaker [Review]
Publié: avril 6, 2015, 2:19pm CEST par Ian Barker

With smartphones and tablets increasingly becoming the focus of our entertainment a decent portable speaker is becoming an essential accessory if you don’t want to be tied to headphones or want to share your music with others.
Inatek's latest offering has a pair of 5W speakers mounted in a stylish, compact (around 9.5 inches long by 2.5 inches high) black and silver enclosure. It has a nice weighty feel and there's a slot in the top into which you can sit a smartphone or tablet -- a pop-out strut at the back prevents the unit from becoming top heavy and tipping over as well as keeping a comfortable viewing angle -- so you can use it to watch videos. A built-in microphone means you can make hands-free calls too. However, it isn't an actual dock so it won't charge your phone or tablet.
Of course you don't have to sit your device on the speaker, the BP2001 can also connect via Bluetooth from across the room and there's a standard 3.5mm input jack so you can attach it to just about anything with an audio out. It comes with a USB charging cable and an audio cable, though both of these are quite short.

There's a large button on the front that allows you to pause playback and accept calls. On the black ring around this are LED icons showing the state of charge and the current input source. There's no volume control on the speaker itself so you need to handle that from the playback device. The BP2001 will switch itself off after five minutes without a connection in order to preserve battery life. The battery itself is 800mAh and should give you around six to seven hours of playback.
So, what does it sound like? The answer is surprisingly good for such a small unit, it has a rich tone and decent bass and there's little distortion even if you crank the volume up.
There are a few minor niggles, the shiny black finish shows off every fingerprint and the cables are silly short, but at $29.99 on Amazon (£28.99 in the UK) the BP2001 represents good value for a speaker that is capable of producing a sound that's enough to fill a decent sized room.
More information on the BP2001 is available on the Inateck website.
-

MicroStrategy platform Ushers in password-free security
Publié: avril 2, 2015, 3:29pm CEST par Ian Barker

Keeping systems secure is still heavily reliant on the use of passwords. But in order to be secure these need to be complex which makes them hard to remember.
An answer to the problem may lie with a product from enterprise software platform suppler MicroStrategy. Called Usher it replaces traditional passwords with biometric mobile identity and multi-factor authentication, and offers streamlined security administration.
Already available in the cloud, Usher is now available for on-premises installation to protect systems that need to live behind a corporate firewall. It uses an Usher badge which is downloaded onto a mobile device, this then allows users to log in by scanning a QR code. Because the system knows your phone it can verify your identity without the need for a password.
Usher can take advantage of the phone's other features too, GPS data for example can be used to geo-fence logins so they can only take place in a particular area. It can also be tied to a biometric identifier such as a fingerprint scan. Logins can be restricted to specific time periods too.

As well as being used to login to workstations or to enterprise cloud deployments Usher can be used for access to buildings or even vehicles. Admins have an insight into user activity allowing them to detect anomalies and abnormal usage patterns and enhance enterprise risk management.
MicroStrategy is also releasing an Usher SDK, enabling developers to build Usher security capabilities -- including any of its logical or physical access functionalities -- into their existing mobile applications, web applications, and enterprise software packages.
"We wanted a more secure and efficient method for our students and administrators to log into university websites and web apps than the traditional user name and password," says Marty Johnson, Senior Director of Identity, Collaboration, Mobile, and GOCard at Georgetown University. "We have deployed Usher, which integrates with our Shibboleth single sign-on system and allows our university population to securely sign in to any Georgetown website by simply scanning a QR code with their mobile phone, eliminating the need for passwords. This Spring semester, we are also working closely with MicroStrategy and the Usher product team to design a solution to address our costly password reset problem. Once that work is completed, we expect to see a significantly reduced number of help desk requests for locked user accounts and, as a result, to reap substantial cost savings".
To find out more and to try Usher out for yourself you can visit the product's website.
Image Credit: Nata-Lia/ Shutterstock
-

Apache -- 20 years of the world's favorite web server
Publié: avril 2, 2015, 12:33pm CEST par Ian Barker

In 1995 a group of just 21 web masters got together to develop some server software. They became the Apache Group and today the project they started powers over 500 million websites, around half the internet.
Open source software specialist Lucidworks has produced an infographic that looks at the history of Apache and how it has succeeded by becoming a collaborative, consensus-based development process with an open and pragmatic software license.
The Apache community as we know it was formed in 1999 to provide organizational, financial and legal support for Apache server. It now has almost 600 members and in addition to Apache has been behind a number of other products including the Hadoop big data tool and OpenOffice.org.
It has succeeded by sticking to its open source approach and using a modular API which allows members to experiment in a risk-free environment and perfect functionality before incorporating it into a project.
You can see the full infographic below.
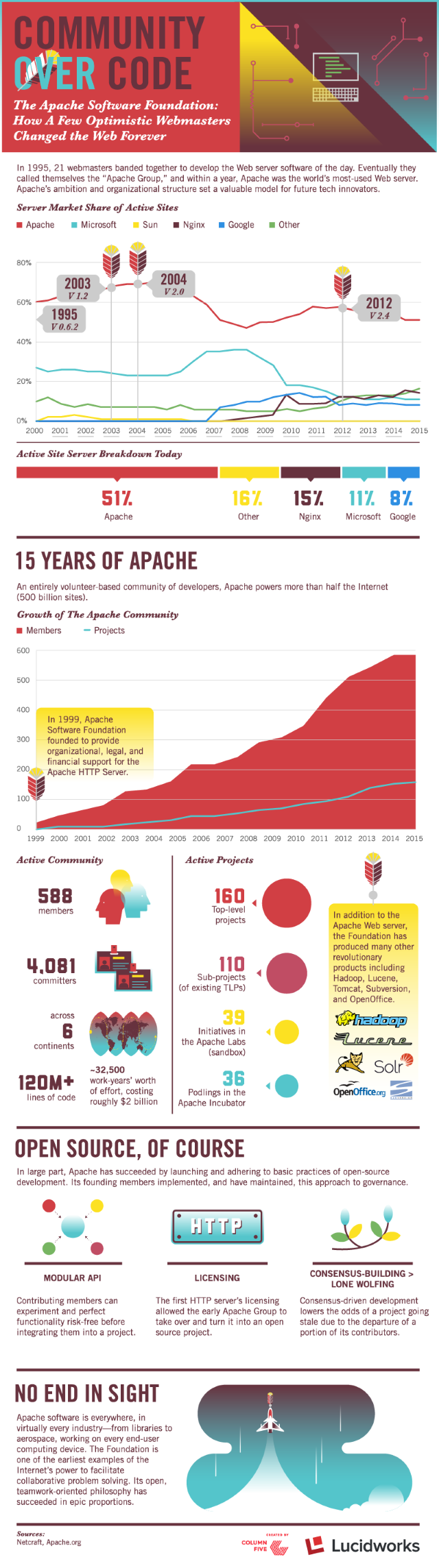
Photo Credit: sheelamohanachandran2010/Shutterstock
-

Point of sale systems at risk from underlying vulnerabilities
Publié: avril 1, 2015, 5:02pm CEST par Ian Barker

Last week we reported on the PoSeidon malware threatening credit card security by stealing transaction details.
Charles Henderson vice president of managed security testing at information security specialist Trustwave believes that there's a bigger underlying problem with the way retailers implement PoS systems putting them at risk.
Card transactions have always been the subject of attacks going right back to skimming details by stealing the carbons from old-style card machines. As technology has advanced they've progressed through physical mods made to electronic card readers to malware on back office systems, allowing attacks to become more virtual. While new technologies like chip and pin make it harder to create cloned cards but don't protect details at the point of sale.
Henderson warns that retailers are failing to take some basic precautions that would help protect them from attacks, for example, "One of the most popular makes of PoS terminal has a six-digit default password which has been the same since 1990 and was published on news groups back in 1994. Yet of the terminals we test 90 percent are still using that default password".
By failing to fully test their deployment retailers are leaving themselves open to attack. Yet as Henderson points out, "Averaged out of the number of PoS terminals deployed testing isn't a big investment as you only need to test one of each type". Modifications to systems can introduce vulnerabilities too and any changes need to be properly tested before deployment.
Rather than react to new pieces of malware like PoSeidon, businesses should look towards closing the loopholes that allow them to get onto their systems. "The industry hasn't learned from parallel technologies -- routers for example -- which are now mostly supplied already secured," says Henderson. Back office systems need to be kept secure too as employees can inadvertently introduce malware by actions such as playing games or opening infected email attachments.
In order to combat attacks he recommends a three pronged approach: network segmentation and security testing, user security awareness training, and anti-malware technology as a backstop.
More information on threat and vulnerability management is available on the Trustwave website.
Image Credit: scyther5 / Shutterstock
-

Backup? What's a backup? One in five Brits don't save their PC data
Publié: mars 31, 2015, 4:26pm CEST par Ian Barker

Today is World Backup Day, I'm not sure if it's significant that it comes just before April Fool's Day, but it does seem that the backup message isn't getting through to everyone.
A new survey of 1,000 UK adults by digital storage manufacturer Verbatim reveals that one in five have never backed up their home computers and more than a third never back up their mobiles.
"Having the hard drive on your PC crash can be a traumatic experience. It's not difficult to do regular backups. There’s a plethora of hardware and software solutions available for backing up, and innumerable tutorials and advice on the internet. Back up and restore is even built into the latest version of Microsoft Windows and requires just three clicks of the mouse. Apple offers similar functionality with Time Machine," says Rüdiger Theobald marketing director of Verbatim. "Computer data recovery is a tricky business. Where physical failure has occurred, and the hard drive needs to be worked on in a cleanroom, typical costs can be in excess of £500 and there’s no guarantee all the data will be recovered".
Of those who had reported losing data from their computers in the last year, 25 percent experienced data loss because of hardware failure, 17 percent due to accidental damage, 13 percent because of a virus, and a further 13 percent lost out to software corruption.
It seems that men are more likely than women to back up their home computers and phones every month, according to the research.
"One potential issue, when it comes to our apparent reticence about backing up, is that people don’t trust online storage providers in spite of the fact that they routinely commit our content to the likes of Facebook and YouTube," says Theobald, making the point that online backups should be seen as a supplement to and not a replacement for local copies.
He also warns of the need to consider media life. "What also is apparent is that people do not pay as much attention as they should to considering the likely longevity of the media they use. The average hard drive -- internal or external -- will last for five years and USB/flash memory sticks around eight years".
Verbatim has also produced an infographic highlighting some global statistics on the main causes of data loss, the types of file people are most worried about losing, and the excuses they use for not backing up. You can view it below.
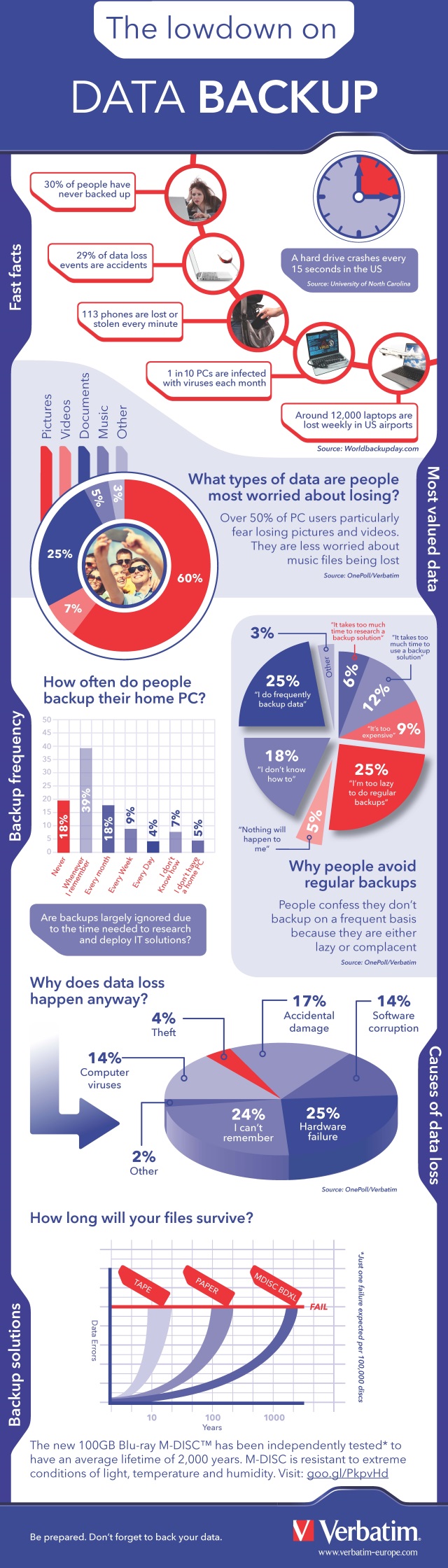
Photo Credit: Brian A Jackson/shutterstock
-

Anonymous proxies used to carry out shotgun DDoS attacks
Publié: mars 31, 2015, 3:38pm CEST par Ian Barker

We're all increasingly concerned about our privacy and the footprint that we leave on the internet. It's not surprising then that more of us are turning to anonymous proxies to hide our origin IP and HTTP details.
But new research from website security company Incapsula has uncovered a darker side to the use of anonymizers as a source of DDoS attacks.
According to the findingd DDoS attacks from anonymous proxies accounted for 20 percent of all application layer attacks. On average, perpetrators were directing traffic from 1,800 different IPs. This is what Incapsula calls a "Shotgun" attack.
The idea behind this type of attack is to use a large number of open proxies, turning a single-source denial of service (DoS) attack into a distributed one (DDoS), thereby making it much harder to mitigate. It's also attractive to attackers as it makes them harder to trace.
The attackers harvest a list of publicly available proxy servers, using a script or online list tools available online. They then use a modified version of a DoS toolkit or a homemade DoS script to send out a batch of malicious requests through each of the harvested proxies.
This produces a scattering effect, similar to the small pellets from a shotgun shell -- hence the name. Yet, where the real shotgun pellets would disperse, the DoS requests always zero-in on the same target; hitting it from multiple directions creating a DDoS attack.
The graphic below shows the distribution of a Shotgun DDoS compared to that of a similarly sized conventional attack. With anonymous proxies, the attack cannot only spread across multiple IPs, but also across multiple geographic locations, making geo-blacklisting techniques ineffective.
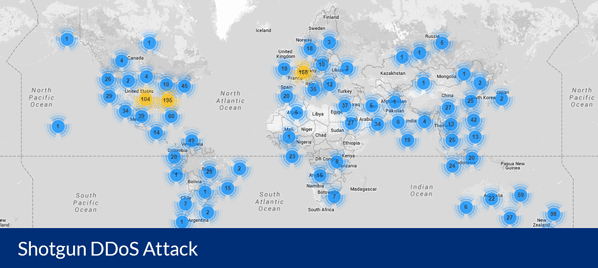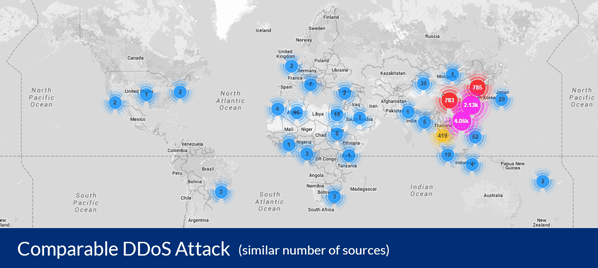
The report shows that nearly 45 percent of all shotgun DDoS attacks originated from IPs on the Tor network. Of those, 60 percent were performed using Tor's Hammer DoS tool. Anonymous proxies averaged 540,000 requests per attack.
For more about Incapsula's research into DDoS attacks and how to guard against them you can visit the company's website.
Photo Credit: Duc Dao / Shutterstock
-

Enterprise security places increased reliance on threat intelligence
Publié: mars 31, 2015, 1:59pm CEST par Ian Barker

It's easier to combat security threats if you're prepared for them so it isn't perhaps surprising that security teams are increasingly turning to threat intelligence to stay ahead of the game.
A new report commissioned by endpoint protection specialist Webroot and prepared by the Ponemon Institute shows that most companies believe threat intelligence is essential for a well-rounded cybersecurity defense and has proven effective in stopping security incidents.
It does, however, also point out that threat intelligence needs to undergo changes in order to make it more timely, accurate and actionable. The report's findings show that 40 percent of companies surveyed had suffered a material security breach in the past 24 months, and 80 percent believed if they'd had threat intelligence at the time of the breach, they could have prevented or minimized the consequences of the attack.
The report is based on a survey of 693 IT and IT security professionals in the US, with 61 percent of them working in large companies. Only 36 percent of respondents rate their own company's defenses as strong. Almost half are increasing the amount of intelligence data they receive in order to prevent or mitigate the consequences of an attack.
There's concern about speed of response though with 56 percent saying intelligence becomes stale within seconds or minutes. The more valuable features of a threat intelligence solution are the ability to implement intelligence and gauge the trustworthiness of the source in real time.
Almost half of respondents (49 percent) use paid for sources of intelligence, saying that free sources aren't adequate for comprehensive threat analysis and make it more difficult to prioritize threats. A third of respondents expect to increase their threat intelligence budget significantly in the next two years.
"Businesses are struggling to identify and stop new web threats because they must assess the risk of more unknown objects than before and the rate of change across the threat landscape is faster than their traditional security technologies can keep up with," says Patrick Kennedy, vice president of enterprise marketing at Webroot. "The study highlights the need for highly accurate and timely threat intelligence to help organizations assess the risk of incoming data, reduce the volume of security incidents, and accelerate response to successful attacks".
The full report Importance of Threat Intelligence to a Strong Security Posture is available as PDF on the Webroot site.
Image Credit: underverse / Shutterstock
-

Why traditional email marketing techniques aren't dead [Q&A]
Publié: mars 31, 2015, 10:53am CEST par Ian Barker

Most of the hype around online marketing these days seems to revolve around using social media, big data and other tools to predict what the customer wants.
It would be easy to assume that outbound marketing techniques like email campaigns have become a bit last century, but Victoria Godfrey, chief marketing officer at B2B data provider Avention thinks otherwise. We spoke to her to find out why.
BN: Does email still have a place in a social media world?
VG: Social media marketing is effective at keeping prospects and customers engaged and informed on a daily (or even much more frequent) basis. However, email campaigns are still king when it comes to conversion, especially for B2B companies. In today's marketing landscape, social media and email are both relevant and required -- they're just doing different jobs. Through email campaigns, marketers can use lead scoring and event-based triggers to target prospects that are already in their database, further along in the funnel and more likely to make a purchase. These targeting techniques increase the chances that a prospect will respond by up to 600 percent. While social can contribute to lead conversion as well, email allows marketers to track the prospect-to-customer journey more efficiently so that they continue to optimize campaigns.
BN: Isn't it true that email marketing in the past has simply been about throwing out large volumes of material and hoping some of it sticks?
VG: By now, the availability of big data should have done away with any remnants of the see-what-sticks mentality. Modern marketers know that reaching decision-makers requires far more specificity, and they also know that the information to reach that level of precision is readily available. The email campaigns delivering returns on investment today are those driven by big data analytics. Rather than mass emails, these brand messages are targeted down to the prospect’s position level, the region of his or her business activity, the market sector, the stage of the prospect’s business and any number of other factors.
BN: How can companies increase the effectiveness of their marketing emails?
VG: One of the most useful strategies for increasing effectiveness is tracking milestone events. These are the changes that indicate prospects are likely ready to buy, and marketing campaigns tied to these moments have higher success rates. For example, if a prospect company announces it has hired a chief information officer (CIO), is expanding into a new city or is laying off workers at headquarters, those events might be essential information to brands selling technology, recruitment tools or outsourcing services, respectively. Marketers can set trigger alerts inside their data to look for these moments like these when significant change is occurring inside a prospect company.
BN: How can they monitor that effectiveness?
VG: The great thing about email is that it's relatively easy to track the effectiveness of campaigns and adapt accordingly. Any campaign should include at least one clear call to action, whether it’s signing up for a webinar, visiting a landing page, following the company on social or downloading a case study. Marketers should monitor campaigns closely to see how these calls to actions are performing and how those metrics compare to previous campaigns. If you're seeing a decrease, pivot and try a new message. On a macro level, marketers should always keep an eye on whether email lead sources have helped to contribute to an overall increase in closed or won opportunities. It’s important to keep in close touch with sales to assess what’s working and what’s not.
BN: What are the most common emailing mistakes?
VG: The most common mistake in email today is a hesitation to apply big data analytics to campaigns. This data is obtainable, but because marketers don't always understand what to do with it or why they should shift their methods to embrace it, some fail to do so. This is a mistake. To get ROI from email campaigns, brands have to invest in technology that automates the process of collecting dynamic data and identifying targets based on defined ideal profiles. Once this segmentation is obtained, the messaging must be tailored to specific audience segments. You can’t send the same campaign to five different email lists and expect to see the same results.
BN: How much difference does the shift toward mobile devices make?
VG: Increasingly, prospects are reading -- and screening -- their email on mobile devices. That makes it easier than ever for recipients to swipe a screen and delete a marketer’s message before reading it. Therefore, those messages have to be as finely targeted as possible in order to reach the right prospects at the right times. On mobile, compelling subject lines and responsive design also influence how effective email campaigns will prove to be, so marketers need to be tuned into best practices in these areas, as well.
Victoria Godfrey is the chief marketing officer of Avention. Prior to joining Avention, she spent five years running her own marketing and research company, Godfrey Research. Previously, Victoria was the chief marketing officer of Zipcar. She has an international MBA from Thunderbird (The American Graduate School of International Management) and a bachelor's degree from The University of Vermont. Since 2001, Victoria has taught marketing at the Gordon Institute at Tufts University.
credit: Gina Sanders/Shutterstock
-

Big data: All hype and no investment?
Publié: mars 30, 2015, 3:15pm CEST par Ian Barker

Although there's lots of talk surrounding the use of big data it seems that in many cases that's all it is and that companies aren't actually following through on deployments.
This is among the findings of a new report from Dimensional Research commissioned by data warehousing specialist Snowflake Computing which shows that whilst 91 percent of respondents have considered investments in big data, only 5 percent have actually put any investment into a deployment, and only 11 percent had a pilot in place.
Although Hadoop is cited as being the answer to big data worries it seems it may also be a roadblock. More than 70 percent of respondents say a lack of expertise is a major concern about using the open source framework. Only 12 percent of respondents say they have easy access to Hadoop expertise. These numbers are far lower at companies with 1000 or less employees, where only 5 percent say they have easy access to Hadoop expertise.
Other highlights are that 96 percent say Hadoop won't replace their existing data warehouse, 99 percent of respondents say their data warehouse is important to business operations, and 70 percent are increasing their investment in data warehousing.
Cloud-based data warehousing is seen as desirable with 93 percent seeing value in its potential benefits, particularly scalability and reduced overhead. 32 percent already have a cloud-based data warehouse and 16 percent exclusively use data warehousing in the cloud. Of those with data in the cloud 79 percent bring it into their data warehouse, although only 9 percent bring all their data in.
The report is based on a survey of 319 individuals with responsibility for data initiatives, you can find out more and download a copy on the Snowflake website.
Image Credit: bleakstar / Shutterstock
-

Inateck FE2004: Turn your old hard disk into a USB 3.0 external drive [Review]
Publié: mars 30, 2015, 1:34pm CEST par Ian Barker

You can of course buy ready to use external hard drives, but should you have a spare 2.5 inch disk from an old machine lying around it's easy enough to pop it in a case so you can use it for backups or transferring files.
There's lots of choice when it comes to buying an external enclosure and most of them aren't very expensive, so what makes this offering from German company Inateck attractive?
Firstly it looks smart with a smooth matt black finish. It's slightly larger -- to the tune of about 1.5 centimetres in length -- than a ready-made WD Elements external drive, but it's still small enough to slip into a pocket. It's USB 3.0 so you can take advantage of the faster interface though it is of course backwards compatible with USB 2.0. You get a connecting cable and a printed instruction leaflet in the package.
A nice feature of the FE2004 is that it's tool-free so there's no fiddling around with tiny screws to install your drive. The cover simply slides off with a clip to hold it in place when it's closed. You can use any 2.5 inch SATA hard drive, including SSDs, providing it's between 7.5 and 9mm thick. Just push the disk into the connector and there are foam pads to hold it in place and prevent it from rattling. With the disk installed you simply plug in to a USB port and away you go, it's fully plug and play compatible so no need to install drivers.
The FE2004 currently costs $12.99 on Amazon (£11.49 in the UK). You can buy drive enclosures for less but the tool-free design of this one is a neat touch, especially if you work in support and you need to swap drives around on a regular basis. The smart looks are an added bonus.
You can find more information and a full spec on the Inateck website.
-

How the cloud can benefit smaller enterprises
Publié: mars 27, 2015, 1:21pm CET par Ian Barker

Moving systems to the cloud is increasingly popular, but it can seem daunting for smaller and medium businesses with the added worry that it may not prove cost effective.
In an effort to make the move easier, Irish telephony and VoIP provider Speechpath has produced an infographic setting out the benefits that smaller companies can gain from a switch to the cloud.
It seems that smaller businesses are turning to the cloud, 43 percent in 2013 compared to only five percent in 2010. But still it's estimated that four out of five could cut costs with a move to cloud technology.
The key benefits of moving to the cloud are streamlining work processes, reducing technology infrastructure spend, allowing employees to work from anywhere, reducing capital costs and gaining flexibility.
The graphic also looks at the merits of public, private and hybrid cloud models as well as identifying the cloud apps that businesses may already be using without realising it. For those that decide to take the plunge there's a five step guide to ensuring migration runs smoothly.
You can view the full infographic below.
Photo Credit: Roland IJdema/Shutterstock
-

Is your computer bugging you? [Q&A]
Publié: mars 26, 2015, 5:30pm CET par Ian Barker

Data leaks due to security flaws and hacker activity constantly make the news, but they're not the only ones that businesses have to worry about. Leaks can stem from employee or industrial espionage activity too and of course there's always government snooping.
Whilst larger businesses with sensitive data or intellectual property to protect often check for old-style surveillance they may not be as aware of the potential for PCs and other gadgets to gather intelligence as well as leak data. We spoke to Andre Ross, Director of Australian digital forensics and information security company Elvidence to find out how businesses may be at risk and what they can do to combat it.
BN: Why isn't a conventional TSCM (Technical Surveillance Counter Measures) bug sweep enough any more?
AR: Whilst an experienced TSCM specialist is capable of detecting a phone tap, radio frequency (RF) bug or candid video recording devices, he/she is helpless with Bluetooth or Wi-Fi devices or transmissions. The latest and greatest spectrum analysers can detect the source of Bluetooth or Wi-Fi transmissions, but the operator is unable to tell the difference between the legitimate or rogue transmission devices or communications.
Most commercial TSCM operators are helpless when dealing with computer devices and networks. Planting a bug requires physical access to secure premises. Infecting a computer with malware that turns any computer into a listening or video recording device can safely be done from a remote location.
BN: How easy is it to turn a PC into a bugging device?
AR: Not only PCs, but telephones, other computers, smartphones, and other network-connected devices with built in microphones. All of these can surreptitiously be turned into listening devices by compromising their operating software.
On a PC there are a number of ways to achieving this, starting from luring the unsuspecting user to a trivial clickable link, leading to installation of malicious software. Or it could be done by sending a payload hidden in Microsoft Office or Adobe Acrobat documents as an email attachment from an address appearing to be within the same company. It can also be done by infecting USB peripherals with BadUSB and dropping a few during an office visit.
Another example is when a Chrome user visits a website that uses speech recognition to offer voice control or other cool functionality, the site asks the user for permission to use his microphone. The site remembers this decision (standard behavior for HTTPS sites) so it can now turn the mic on and start listening without asking for permission again. While Chrome displays a clear notice in the browser that speech recognition is on, a malicious or compromised site may have opened another hidden pop-under browser window. The user can stop the speech recognition on the front window, but the hidden windows would keep speech recognition on and continue to listen in.
Office telephones can be bugged too. Before Cisco released a software update to its Unified IP Phones 7900 Series -- found in many corporate offices -- these phones could be exploited by gaining physical access to the device or remotely via SSH. After executing malicious code the phones could be turned into a listening devices. Many phones are still run on a vulnerable version of software even though an update fixing the issue was released on in November 2014.
Smartphone apps Shazam, Color, Shopkick and many others are capable of automatically activating the microphone in Android or iPhone devices. These apps gather contextual information such as music, ambient noise or even sounds inaudible to humans generated by other devices. Android smartphones that have lesser app quality control and jailbroken iPhones can have such modified or "dual-purpose" apps installed without the user having knowledge of its true nature. BYO devices are commonplace and having one such smartphone in a meeting room is enough for business security to be compromised.
BN: How hard is it, and is specialist knowledge required, to detect that a computer is being used in this way?
AR: It is very hard for an ordinary user or even TSCM operator to detect such devices. A typical computer forensic specialist may also struggle to identify these zombies. It requires a good knowledge of network forensics, memory forensics and malware detection as well as skills in the area of information systems security. An experienced and knowledgeable forensic professional knows where to look for tell-tale signs and can effectively detect sources of information leaks.
BN: Is there an overlap between this type of surveillance and malware that attempts to steal data from individual machines or corporate networks?
AR: These are close relatives and use the same attack vectors to achieve the same goals, that is to steal valuable information.
BN: What's the best way for businesses to protect themselves from computer eavesdropping?
AR: To follow best Information Security practices, keep the devices up-to-date and of course perform regular (TSCM) bug sweeps in conjunction with IT security audits, ideally performed by an experienced computer forensic specialist. Some TSCM operators are starting to offer joint IT security audits and bug sweeps performed simultaneously to deliver better results.
BN: Should we just accept that surveillance is now a fact of life and if something is really confidential we should maybe keep it on paper?
AR: Surveillance is a fact of life. But that doesn't mean that we should limit ourselves from using modern technology. That would be shooting ourselves in the foot. Technology is an enabler for businesses and organizations. When thinking about information security, confidentiality and privacy, we should always remember The Frog in the Milk Pail.
Image Credit: Maxx-Studio / Shutterstock
-

New solution makes cloud-based storage and recovery accessible to SMBs
Publié: mars 26, 2015, 12:32pm CET par Ian Barker

Enterprise standard data storage and recovery can be beyond the reach of smaller businesses with the result that they end up using compromise solutions often based on consumer products.
UK-based managed services provider ITS is launching two new services -- BlackCloud and BlackVault -- to offer affordable off-site data backup and disaster-recovery-as-a-service on its private cloud platform in the company's dedicated, secure data center.
BlackCloud makes enterprise-level storage and recovery affordable for small- and medium-sized businesses. The cloud solution provides secure and compliant data vaulting and recovery at a cost equivalent to an in-house backup operation.
Features include, fully automated cloud backup, rapid recovery, de-duplicated and encrypted data stored off-site, a customer access portal, and hardware and application support with guaranteed response times.
For customers that need extra protection, BlackVault is available as an on-site addition to BlackCloud. This solution is a complete disaster-recovery-as-a-service (DRaaS) package, offering on-site and off-site recovery services. It's a pre-configured, fully integrated data storage unit, provided by ITS, that offers backup and recovery within a customer's office, removing the need to purchase expensive equipment for replication and recovery. The unit can be installed at a location of the customer's choice, creating a virtual environment while providing quick and easy access to the services when needed.
Head of managed services at ITS, Matt Kingswood, says, "Small- to medium-sized businesses struggle with data replication and disaster recovery (DR) because of the price tag. The ITS BlackVault appliance makes DR feasible for SMEs, enabling efficient and reliable data recovery to help meet recovery time objectives (RTOs)".
You can find more information on both BlackCloud and Black Vault on the ITS website.
Photo Credit: Andreas Weitzmann/Shutterstock
-

DDoS attacks are up -- and getting more sophisticated
Publié: mars 25, 2015, 8:20pm CET par Ian Barker

Yes, I know, on Tuesday we reported on a study showing that DDoS attacks were down in frequency, though increasing in severity. But another report from Corero Network Security now suggests that they've actually increased in numbers.
Measuring the number of DDoS attacks is beginning to look like asking how long a piece of string is. Anyway, Corero says that attacks are up with its customers experiencing attack 3.9 attempts per day.
It also finds that they're getting more sophisticated in an effort to evade security measures. Corero’s data points to two new trends in DDoS attacks, short bursts of attack traffic instead of prolonged events, and partial link saturation attacks rather than completely flooding the network. Around 96 percent of attacks targeting Corero’s SmartWall Threat Defense System lasted for 30 minutes or less.
Also 79 percent of the DDoS attack attempts targeting the company’s customers between October 1 and December 31, 2014 were less than 5Gbps in peak bandwidth utilization. These attacks were intended to partially saturate the Internet link and distract corporate security teams, but leave enough bandwidth available for a subsequent attack to infiltrate the victim’s network.
Corero's full report is available to download from the company's website.
As to why these findings differ from those of Black Lotus we asked Corero Network Security's CTO, Dave Larson. "Corero’s findings are different from other vendor-driven analyses of the DDoS landscape, primarily due to the deployment and positioning of DDoS mitigation appliances in customers' networks," Larson says. "Corero’s SmartWall Threat Defense System (TDS) is deployed at the very edge of the customer network or at the Internet peering points as a first line of defense – inspecting and mitigating all the traffic from the Internet in real time before attacks can impact the customer environment. Cloud-based anti-DDoS solutions only have insight into the attack traffic that is re-routed to them for scrubbing, well after an attack has permeated the network, so their data only represents that traffic. While those reports offer very interesting data points about large-scale DDoS attacks, that is only a fraction of the DDoS traffic an organization faces on a daily basis. With its position on the front lines of an organization’s network, Corero has a complete view of the DDoS attacks targeting corporate networks -- whether they’re high volume attacks or sub-saturating events".
So there you have it, how bad the DDoS problem is all depends on where you're measuring from. How long was that piece of string again?
Photo Credit: Duc Dao / Shutterstock
-

Software vulnerabilities up 18 percent in 2014 and Microsoft isn't to blame
Publié: mars 25, 2015, 11:47am CET par Ian Barker

Errors in software, whether operating systems or applications, are usually the root cause of security issues, allowing hackers and cyber criminals a way in to systems.
In 2014, 15,435 vulnerabilities across 3,870 applications were discovered according to a new report from vulnerability intelligence specialist Secunia. That represents an 18 percent increase in vulnerabilities compared to the year before, and a 22 percent increase in the number of vulnerable products.
"Every year, we see an increase in the number of vulnerabilities discovered, emphasizing the need for organizations to stay on top of their environment. IT teams need to have complete visibility of the applications that are in use, and they need firm policies and procedures in place, in order to deal with the vulnerabilities as they are disclosed," says Kasper Lindgaard, Director of Research and Security at Secunia.
The list of core products with the most vulnerabilities in 2014 makes for surprising reading. Google Chrome comes top with 504, it's followed by Oracle Solaris on 483, Gentoo Linux on 350, with Microsoft Internet Explorer fourth on 289. Apple's OS X is 13th with 147 and Windows 8 20th with 105.
The report points out that open source vulnerabilities often arise from bundling. The risk lies in the fact that the applications and libraries can be bundled in a variety of products and installed in a host of different contexts.
Looking at a portfolio of the top 50 most popular applications on private PCs, 1,348 vulnerabilities were discovered in 18 products. However, what's interesting is that 77 percent of vulnerabilities in the 50 most popular applications on private PCs in 2014 affected non-Microsoft applications, by far outnumbering the two percent of vulnerabilities found in the Windows 7 operating system or the 21 percent discovered in Microsoft applications.
There is some good news, of all the 15,435 vulnerabilities, 83 percent had a security patch available on the day the vulnerability was disclosed to the public. This represents a continued improvement in time-to-patch from a low of 49.9 percent in 2009.
Lindgaard adds a note of caution though, "But numbers also show that while an impressive 83 percent of vulnerabilities have a patch available on the day of disclosure, the number is virtually unchanged when we look 30 days ahead. 30 days on, just 84.3 percent have a patch available which essentially means that if it isn't patched on the day of disclosure, chances are the vendor isn't prioritizing the issue. That means you need to move to plan B, and apply alternative fixes to mitigate the risk".
You can read more about the findings in the full report available to download from the Secunia website.
Image Credit: alphaspirit / Shutterstock
-

Multi-purpose backdoor Trojan threatens Windows systems
Publié: mars 24, 2015, 5:13pm CET par Ian Barker

New variants of malware come and go with depressing regularity, but some have capabilities that offer more cause for concern than others.
The latest piece of scary software comes from researchers at security company Doctor Web who have uncovered a new Trojan dubbed BackDoor.Yebot that's capable of carrying out a wide range of destructive actions on an infected machine.
It's spread via another piece of malware, Trojan.Siggen6.31836. When launched on the target machine, this injects its code into the svchost.exe, csrss.exe, lsass.exe and explorer.exe processes. After sending a request to the remote server it then downloads and decrypts BackDoor.Yebot and transfers control to it. Some features of Trojan.Siggen6.31836 are encrypted (and can be decrypted only while it's being executed). It also incorporates mechanisms to verify the virtual machine in a target system and bypass User Account Control.
Once active on an infected system BackDoor.Yebot has a range of capabilities. It can run an FTP server or a SOCKS 5 proxy server on an infected computer, it can also modify the RDP protocol to provide remote access to the machine.
It has the ability to log keystrokes and can intercept surfing activity by capturing PCRE (Perl Compatible Regular Expressions) patterns. It's able to inject arbitrary content into web pages loaded in browser windows too.
As well as monitoring and interfering with your surfing it can intercept various system functions, modify the code of the running process, interact with plug-ins, take screenshots, and search in the infected system for private keys.
BackDoor.Yebot communicates with its C&C servers using standard HTTP protocol as well as native binary protocol and it has the ability to blacklist IP addresses if they're unavailable or getting too much traffic.
Doctor Web's analysts suggest that BackDoor.Yebot is being used as a banking Trojan, but its range of abilities suggests it's been designed as a piece of multi-purpose malware. It has already been added to the Dr.Web virus database and more technical detail on the infection can be found on the company's website.
Image Credit: Spectral-Design / Shutterstock
-

Workspot offers secure access to workplace data on personal devices
Publié: mars 24, 2015, 4:13pm CET par Ian Barker
Mobile workforces present a number of challenges in terms of accessing data and keeping it secure. Mobile solutions company Workspot believes it has a new approach to enterprise mobility with its Workspace as a Service solution.
Workspot Enterprise supports Windows, Android and iOS access and allows users to get to their work desktop applications and work files from any PC or mobile device via the Workspot app.
It's a cloud-based service, users install a Workspot client on their PC and after entering their PIN, all their desktop applications and workspace files are made available through the service. Workspot's solution integrates the VPN, app, data and browsing for the end-user allowing them secure access to their work from anywhere in the world.
Companies benefit too as they can instantly beam new files and applications to users' devices through the app, allowing employees to be effective and up to date whether working in the office, on the road or from home and on any device. IT administrators can manage their entire workforce, regardless of device, and grant remote access to applications from a single pane interface.
"Workspot's goal is to make the enterprise completely mobile, and the launch of our PC application marks a major accomplishment toward this objective," says Amitabh Sinha, CEO and co-founder of Workspot. "Cloud-based Workspace as a Service solutions are essential for the modern enterprise, and over 95 percent of devices that users work from are Windows-based. The Workspot client for Windows provides a way for the vast majority of employees around the world to securely access their documents and data wherever they are, no matter whether it’s a company-managed or personal PC".
Workspot client is available for Windows 7 and Windows 8 in addition to Android and iOS. You can find out more on the Workspot website.
-

DDoS attacks reduce in frequency but grow in volume
Publié: mars 24, 2015, 2:51pm CET par Ian Barker

According to the latest quarterly threat report from network security specialist Black Lotus the frequency of DDoS attacks fell by 44 percent in the last quarter of 2014.
However, the average packet volume of attacks increased 340 percent to 4.36 million packets per second (Mpps), and the average bit volume swelled 245 percent to 12.1 gigabits per second (Gbps) over the same period.
The report is based on analysis of Black Lotus' customer network logs. The largest bit volume DDoS attack observed during the report period was 41.1 Gbps on Oct 1, a rise in volume since the beginning of 2014, due to attackers' usage of blended, complex attacks to achieve outages.
Of the 143,410 attacks observed during Q4 2014 49 percent were regarded as severe and more than half (53 percent) of all those mitigated resulted from UDP flood attacks. These cause poor host performance or extreme network congestion by producing large amounts of packets and IP spoofing.
The average attack during the report period was 12.1 Gbps and 4.36 Mpps, tripling average packet volume since the previous quarter. This indicated a continued reliance on using multi-vector attacks, signaling the need for security practitioners to use intelligent DDoS mitigation rather than padding networks with extra bandwidth.
"We found DDoS attacks continued trending down in frequency quarter over quarter, but, on average, attack volumes multiplied," says Shawn Marck, co-founder and chief security officer of Black Lotus. "With networks and IT teams becoming defter at spotting and stopping volumetric attacks, cybercriminals are turning to blended approaches to confuse organizations, often using DDoS attacks as smokescreens for other underhanded activity".
Looking ahead, Black Lotus has revised its estimate of the security measures enterprises will need to protect against the majority of attacks throughout 2015. It now says they'll need to be capable of handling 15 Gbps minimum in bit volume, up from its Q3 prediction of five Gbps minimum. The research team anticipates that attackers will continue to try new DDoS recipes in an effort to confuse security teams and allow agitators to steal user credentials, customer billing information or confidential files.
The full quarterly threat report is available to download from the Black Lotus website.
Photo Credit: Fabio Berti/Shutterstock
-

Jitterbit streamlines enterprise cloud integration
Publié: mars 24, 2015, 1:23pm CET par Ian Barker

Although the cloud is increasingly popular, few businesses run all of their systems in a cloud environment so there’s generally a need for some integration with on-premises IT.
California-based Jitterbit specializes in this type of integration and is releasing the latest version of its Harmony product offering increased speed, scale and reliability.
Harmony Spring '15 includes powerful upgrades and additions to Jitterbit's multi-tenant cloud integration platform. New and improved features include reliable messaging to ensure that data reaches its destination even if systems experience downtime or other issues. Real-time connectivity between the Salesforce1 platform and any external source, new SAP Destinations enabling real-time process integration from SAP, and a new Microsoft CRM Connector with support for MSCRM 2015.
There's also an enhanced NetSuite connector with broader search and performance improvements, and new LDAP support to connect, search and modify Internet directories.
"This new release to our leading cloud integration platform delivers a new level of speed, scale and reliability to support the most complex enterprise integration requirements we are seeing from our customers," says Jitterbit CEO George Gallegos. "While Jitterbit Harmony has evolved to support even more complicated and demanding use cases, we stay true to our mission to enable everyday business users to design and manage integration without the need to call on an army of developers".
Jitterbit Harmony is built on a single platform to allow non-developers to design, deploy, and manage app integrations without needing to write code or purchase additional products and components. Harmony Spring '15 enables business users to manage the entire integration life cycle on a single multi-tenant cloud platform. It provides ease-of-use, fast setup time and enterprise performance with what the company claims is the lowest total cost of ownership for any integration solution.
Existing Harmony customers will benefit from the new release with a seamless upgrade. New users can sign up for a 30-day free trial on the Jitterbit website.
Photo Credit: RAJ CREATIONZS/Shutterstock
-

New malware makes credit card transactions a scary PoSeidon adventure
Publié: mars 23, 2015, 3:16pm CET par Ian Barker

As more and more transactions are carried out electronically, point of sale systems become an ever more tempting target for cyber criminals. Security researchers at networking company Cisco have identified a new strain of PoS malware that seeks to extract credit card data from memory and send it to remote servers.
Named PoSeidon it has a more sophisticated design than other PoS malware and has some resemblance to ZeuS. It's written to evade detection, can communicate directly with C&C servers, self-update to execute new code and has self-protection mechanisms to guard against reverse engineering.
The infection starts with a loader binary that, when executed, will try to gain persistence on the target machine in order to survive a system reboot. It does this by hiding itself in a process named WinHost32 and adding an entry to the registry.
The loader then contacts a command and control server, retrieving a URL containing another binary to download and execute. Once downloaded the binary, FindStr, installs a keylogger and scans the memory of the PoS device for any number sequences that could be credit card numbers. Once it's verified that the digits it's found are in fact credit card numbers, both keystrokes and card numbers are encoded and sent to a server.
Cisco's blog says that PoSeidon is evidence of the growing sophistication of PoS malware attacks. It also notes that this is likely to be part of a long-term campaign against such systems. "As long as PoS attacks continue to provide returns, attackers will continue to invest in innovation and development of new malware families. Network administrators will need to remain vigilant and adhere to industry best practices to ensure coverage and protection against advancing malware threats".
Image Credit: Sedlacek / Shutterstock
-

Updated System Center add-on improves server-less software deployment
Publié: mars 19, 2015, 5:01pm CET par Ian Barker

Microsoft's System Center Configuration Manager (SCCM) has become one of the leading products form managing large groups of computers, whether or not they're running Windows.
In order to improve its usefulness still further, add-on provider Adaptiva is launching the latest version of its flagship SCCM solution. OneSite 4.5 is focused on enhancing visibility and security while optimizing the speed at which enterprises can perform server-less software deployments.
Adaptiva's award-winning solution lets large enterprises manage clients worldwide at lower cost and with less IT staff effort, by removing the need for a global server infrastructure. Since 2011, Adaptiva has been the solution provider of choice for many Fortune 500 companies who rely on OneSite for seamless SCCM operations from a single site with zero impact to their business WAN traffic.
"It is a testament to the OneSite platform that many of the world's largest financial institutions, manufacturing leaders and healthcare providers rely on our technology to perform massive system updates and their input is deeply reflected in our new software," says Deepak Kumar, CTO and founder of Adaptiva. "The emphasis on visibility, security and global scalability in version 4.5 gives Adaptiva customers a distinct advantage, and we will continue to deliver innovations of this caliber".
New features in OneSite 4.5 include an update manager that makes it simple for customers to seamlessly update directly from the OneSite software they're currently running to a newer one through the automated generation of a single customized smart patch. There's also integrated security which gives customers the ability to use network access accounts for an extra layer of protection.
For multinational companies where computers travel around the globe, OneSite automatically senses where they are and intelligently retrieves SCCM content accordingly. For example if a user travels between London to New York, their system always gets content locally.
For admins there's a WAN Performance Visualizer to generate customizable network load in a test/proof-of-concept environment to verify that an application won't impact WAN traffic or decrease responsiveness. The latest OneSite also has enhanced predictive bandwidth harvesting to forecast usage and maintain responsiveness.
More information on OneSite 4.5 is available on the Adaptiva website.
Photo Credit: nmedia/Shutterstock
-

13 instances of adware detected in Google Play store
Publié: mars 19, 2015, 3:49pm CET par Ian Barker

Despite the recent announcement by Google that it has introduced a vetting process on the Play store it seems that there are still rogue apps to be found.
Mobile security company Lookout has uncovered 13 apps with adware. Worse still these display malware-like characteristics that make them hard to remove. The company has alerted Google to the apps and they've already been removed from the store.
Two families of adware called HideIcon and NotFunny were hidden within the apps which between them have been downloaded thousands of times.
HideIcon, as its name suggests, hides its icon to make it harder to remove and then targets the user with aggressive ads. It came in an app pretending to be a card game, complete with playing instructions.
NotFunny was hidden in a number of downloads including wallpaper apps and a free Christmas ringtone app. It has two parts, a dropper and payload, once the dropper is installed with the app it prompts the user to download the payload. This drops an icon pretending to be Facebook on the device then hides itself once installation is complete. Like HideIcon it then pushes aggressive advertising and disrupts the user experience.
You can read more on the Lookout blog. Meanwhile the company is reminding users that apps with hidden icons can be uninstalled from Android's application manager under the Settings menu or from the Play Store app.
Photo Credit: Stephen Finn/Shutterstock
-

Document Cloud moves Adobe further down the SaaS track
Publié: mars 17, 2015, 5:34pm CET par Ian Barker
Adobe's latest offering Adobe Document Cloud will, says the company, address the waste and inefficiency associated with document processes.
It's made up of a set of integrated services that use a consistent online profile and personal document hub. Users will be able to create, review, approve, sign and track documents whether on a desktop or mobile device.
"People and businesses are stuck in document-based processes that are slow, wasteful, and fragmented. While most forms of content have successfully made the move to digital (books, movies, music), documents and the process of working with them have not, and that needs to change," says Bryan Lamkin, senior vice president of Technology and Corporate Development at Adobe. "Adobe Document Cloud will revolutionize and simplify how people get work done with critical documents".
Document Cloud uses Acrobat DC, with a touch-enabled user interface, which will be available both via a subscription model subscription and as a one-time purchase. Its Tool Center offers simplified and quick access to the tools you use most. Also, Acrobat DC uses Photoshop imaging magic to convert any paper document into a digital, editable file that can be sent for signature.
The subscription includes eSign Services that allows users to electronically send and sign any document from any device. There's also a Mobile Link feature to allow access to documents on the move and a Send & Track feature that allows documents to be shared whilst still protecting sensitive information.
None of these features is particularly innovative in itself, but Document Cloud is significant since it joins Adobe's Creative Cloud and Marketing Cloud in a move towards shifting the business to an SaaS model.
The Adobe website has a video preview of Document Cloud in action or you can read more about it on the company's blog.
Image Credit: Adobe
-

Condusiv optimizes performance for network storage
Publié: mars 17, 2015, 4:53pm CET par Ian Barker

If you've been around the PC world for a while you’ll no doubt have encountered Diskeeper, the unattended defrag tool. With modern server storage using RAID controllers and SSDs you may think that the need for this kind of software is over, but Condusiv, the company behind Diskeeper, believes otherwise.
It's launching Diskeeper 15 Server, a fragmentation prevention solution for storage area network (SAN) systems connected to physical servers to keep both servers and storage running like new.
While modern RAID controllers do a good job of managing data at the physical disk layer, which helps in the fight against file fragmentation, it does nothing about fragmentation at the logical software layer that Windows sees. This is the primary reason why SAN storage performance degrades over time.
"Even with over 45 million Diskeeper licenses sold, Condusiv is not sitting still in regard to addressing performance-robbing fragmentation wherever it appears in the data center. Performance-robbing file fragmentation affects SAN storage equally as much as it affects server local storage or Direct-Attached Storage. As much as Condusiv offers a robust software solution to accelerate virtual environments, the fact remains that some of the most mission-critical applications still run on physical servers. That’s not a small number considering there are over five million physical servers in production across North America and EMEA," says Brian Morin, SVP, Global Marketing at Condusiv Technologies.
Diskeeper 15 Server's real-time fragmentation prevention software operates at the physical server layer where input/output operations originate. By preventing files from being fractured and broken apart into pieces before being written to disk or SSD in a non-sequential manner, fragmentation is eliminated before it becomes an issue. That means a SAN storage system never needs to be taken offline for defragmentation maintenance. Significantly it also reduces the amount of I/O needed to access the file as it doesn't have to be fetched in sections and reassembled.
Morin likens the effect to managing rush hour traffic, "It's like ensuring that every car has the maximum number of occupants so you use fewer vehicles to move the same number of people. With Diskeeper 15 Server you need fewer I/O cycles to access a file".
You can find more information about Diskeeper Server on the Condusiv website.
Photo Credit: klRr / Shutterstock
-

LiquidPlanner uses visualization to make project data more accessible
Publié: mars 17, 2015, 2:41pm CET par Ian Barker

Project plans can house a huge amount of data, but turning that into useful information which can help with business decision making can be difficult and time consuming.
Online project management specialist LiquidPlanner is introducing a new Dashboards feature designed to help teams easily curate and share project data with internal and external stakeholders.
"People are overwhelmed by too much information and bogged down by too many meetings. We created Dashboards to make sharing key project data with your stakeholders more efficient than ever before," says Liz Pearce, CEO of LiquidPlanner. "Dashboards are both easy to use and powerful, so all of your communication needs -- from team coordination to executive sponsor updates -- can be managed in one place and updated dynamically".
Members of LiquidPlanner workspaces can create customized Dashboards to communicate and share ideas, project data, status, or anything else related to a project, ensuring that the right information can always be made available to the right people.
Dashboards are made up of customizable widgets which are dynamically linked to the project data that already exists in a workspace. Widgets can include many dimensions of a project workspace such as data tables, charts, notes, documents and images, they can be easily organized simply by dragging and dropping a particular widget into a new space.
They can be used in a number of ways such as tracking key performance indicators, as a visual way for a creative team to share design concepts, or as a means for a professional services firm to update project status of with a client.
You can find more information about Dashboards and sign up for a free trial on the LiquidPlanner website.
Photo Credit: suphakit73/Shutterstock
-

Half of users believe using the internet means giving up privacy
Publié: mars 17, 2015, 11:30am CET par Ian Barker

More than half of internet users in the US, UK and Germany believe it's impossible to keep their personal information private if they're to enjoy the Internet.
This is one of the findings of research by Open-Xchange, the German open source software company. The Consumer Openness Index surveyed 1,000 internet users in each of the three countries to gauge their opinions about online privacy.
Although they doubt their ability to remain private, 50 percent of respondents say that if they had a tool which could alert them when a website was sharing their personal data they would stop using the site immediately. Another 36 percent said they would revisit how or where their data is stored and make changes to it. Only 6 percent would simply continue using the website or service as normal.
The survey's respondents are also open to the idea of encryption for emails and online chats with 72 percent saying they could be convinced to use it. The top factors that would persuade users to adopt encryption are ease of use (54 percent saying they would use it if it involved just clicking a button). 47 percent would use it if it came standard with their applications, and 47 percent would use it if they had a better understanding of the technology.
"In today's age of famous whistle-blowers and nearly constant data leaks, most users know that their online privacy is severely compromised," says Rafael Laguna, CEO of Open-Xchange. "However, we are seeing an acceleration of individuals who are open to new technologies and are demanding help to monitor their privacy and online communications. In order for such encryption technologies to become mainstream, however, they must be easy to use and straight forward to understand -- as these are currently the largest obstacles to adoption".
The results also show differences in attitude between regions. Germans are warier about making financial transactions online, with nearly a quarter (23 percent) saying they make no financial transactions online at all, compared with 16 percent in the US and just 6 percent in the UK. Similarly, the recent controversies surrounding Facebook's privacy policies and terms and conditions have resonated more with German users, 23 percent of whom have deactivated their Facebook accounts, compared to 18 percent in the UK and 14 percent in the US.
Regardless of where they live all respondents are frustrated by complex terms and conditions. More than 72 percent say that T&Cs are too long and complicated to read before agreeing to them. However, 80 percent would read terms of service in full if they were shorter, 64 percent if they highlighted the main points and 49 percent if they used language that was easier to understand.
"There are no quick and easy solutions to today’s Internet quandaries, where giant Data States hold our information captive with undecipherable terms and conditions," Laguna concludes. "But by listening to users, and keeping a finger on the pulse of 'openness' that's out there currently, makes it ten times easier for those of us in the Internet industry to continue to drive the changes that matter now, and that repairs the trust-gap being more and more experienced across the Internet's broken state".
Image Credit: iQoncept/Shutterstock
-

Predictive communication helps optimize online sales
Publié: mars 16, 2015, 4:21pm CET par Ian Barker

Modern businesses spend a lot of money on customer service and on e-Commerce solutions, but often it seems that there's a disconnect between the two.
California-based company Altocloud has come up with a solution that combines machine-learning technology with real-time communications to predict the right time to interact with customers.
The software can determine the best answer to real-time decisions such as "will connecting this prospect to this sales representative now help them purchase today, or should we simply make a recommendation?" Since it's cloud based, the Altocloud software needs no extra infrastructure and is also integrated with existing marketing automation and e-commerce platforms.
"There is a better route to digital customer engagement than yesterday's 1-800 numbers, random chat popups and disjointed telephone conversations," says Altocloud CEO Barry O'Sullivan. "Our platform enhances existing marketing and sales software so that companies doing business online can reach out to prospects at a time when they're most interested, to drive increased sales".
The software can be used to enhance customer experience by embedding voice, video, chat and screen sharing into websites and mobile apps. Plus it can be deployed fast with lightweight JavaScript snippets and mobile APIs powered by a SaaS platform. Live communications can be integrated with marketing automation and CRM systems to enhance existing enterprise contact center solutions.
Altocloud has announced the commercial availability of its product from today along with $2 million of seed funding to allow it to carry its business forward.
It's exhibiting its software at the Enterprise Connect Conference and Exhibition from March 16-19, 2015 at the Gaylord Palms in Orlando. You can also sign up for a free trial via the company's website.
Image Credit: Dusit / Shutterstock
-

SoftWatch offers SMBs smoother transition to cloud office tools
Publié: mars 16, 2015, 1:08pm CET par Ian Barker

For businesses moving to a cloud-based office solution the biggest problem can be understanding and controlling the licensing costs involved.
Cloud transition specialist SoftWatch has a solution for this in the form of its analytics tool which provides in-depth information on how businesses are actually using desktop-based and web based applications as well as cloud storage and web conferencing.
It offers solutions for businesses moving to Google Apps and to Office 365. For SMBs that are moving to the Google Apps for Work suite of services, SoftWatch has an OptimizeIT Google solution to enable informed decisions based on actual usage information, manage the transition from MS Office to Google Apps and optimize their license spending.
For those that are moving to the Office 365 suite, SoftWatch offers SaaS solutions which include CloudIT 365 to enable the transition to Office 365 and help in selecting the best Microsoft price plan.
"We are very pleased to introduce our analytics solution to the SMB market segment and make it easy for them to purchase and start using our software right from our website," says Uri Arad, co-CEO of SoftWatch. "Our SoftWatch Benchmark now has 400,000 users and it is consistently showing that companies are overspending on MS licenses and can save substantially by transitioning to cloud-based alternatives. We believe that our solutions can help smaller companies to better manage their software assets and optimize their IT spending".
SoftWatch has previously been available to enterprise customers though Office 365 and Google Apps resellers, but it's now being opened up to businesses with fewer than 500 end users via the company's website. The site also offers the chance to sign up for a free trial before purchasing.
Image Credit: ND Johnston/Shutterstock
-

The keys to a successful BYOD policy
Publié: mars 13, 2015, 12:32pm CET par Ian Barker

The BYOD trend is something that often creeps up on companies as employees take the initiative in using their own kit. That can leave businesses with a BYOD environment but no proper policy.
There are many potential benefits to BYOD in terms of employee efficiency and morale, but that's of limited use if it puts the safety of commercial data at risk.
Webmasters' blog StudyWeb has created an infographic guide to creating an effective BYOD policy. Whilst it acknowledges its popularity, with 74 percent of IT leaders saying that using personal devices can improve employee productivity, it also points out concerns about underground use, lack of oversight and security issues.
It then goes on to examine the keys to a successful BYOD policy including listing approved and unapproved devices, requiring complex passwords, being clear on service policy, being clear on which apps can be used, and having an effective employee exit strategy.
You can see the full infographic below.
-

Google Apps leaks Whois data for over 280,000 protected domains
Publié: mars 13, 2015, 11:44am CET par Ian Barker

Private information relating to more than 280,000 domains registered via Google Apps has leaked, leaving the registrants open to risk of identity theft or spear phishing.
The ability to buy domain names from one of Google's partners is a feature offered by Google Apps to allow easier access to and management of services.
A problem has existed since 2013 that has been slowly revealing the hidden registration information for domains that had opted into Whois privacy protection as they were renewed. Full names, addresses, phone numbers, and email addresses for each domain have been leaked in the form of Whois records.
There around 305,925 domains registered via Google's partnership with eNom. Of these 282,867 domains, around 94 percent seem to have been affected. Google says that new domains that haven’t yet faced a request for renewal are not affected and of course some registrants choose not to hide their details anyway.
The leak was uncovered by security research group Cisco Talos which immediately notified the Google security team. Within days the privacy settings were restored to the affected domains. Google issued a notice to affected customers yesterday once it was sure the problem had been resolved. However, the information has been available for a long time, so anyone with a cached copy of Whois information will still be able to access it.
There's an interesting side effect to all of this as some of the leaked data relates to domains associated with malicious activity. For example, the domain "federalbureauinvestigations.com" which has an extremely poor web reputation score and might lead to some embarrassing questions for the people who registered it.
Cisco Talos concludes its blog post on the issue, "Organizations that handle any sensitive information must ensure that the appropriate systems are safeguarded and that the processes handle failure gracefully. In this instance, a simple check on domains changing state from being privacy protected to not being privacy protected could have identified the problem as it started to occur".
Image Credit: Angela Waye / Shutterstock
-

Cyber attacks rise as confidence in avoiding them falls
Publié: mars 12, 2015, 5:36pm CET par Ian Barker

According to a new survey by the CyberEdge Group although IT security spending is increasing, confidence is falling, with the majority of respondents expecting to be breached in the next 12 months.
The survey of more than 800 security decision makers and practitioners finds that more than 70 percent of respondents' networks had been breached in 2014, which is a 62 percent increase from the previous year.
In 2014, 71 percent of respondents' networks were breached with 22 percent of them having been attacked six or more times. A majority of respondents (52 percent) now believe a successful cyber attack is likely in the coming year -- up from 39 percent in last year's report.
These fears are driving a shift away from traditional security solutions. 67 percent of respondents indicated their intent to evaluate alternative endpoint anti-malware solutions to either augment (34 percent) or replace (33 percent) their existing products.
Half of those surveyed are also now relying on continuous monitoring technologies for discovering network assets, achieving policy compliance, and mitigating vulnerabilities and security misconfigurations.
"Cyberthreats hit an all time high in 2014, in terms of not only the number of breaches but their impact on all aspects of business. Who would have thought that we would see a time when a simple movie would spur attacks that forced an entire industry to publicly address the way it thinks about privacy, piracy, and geopolitical implications of the product it produces," says Steve Piper, CEO of CyberEdge Group. "For the first time in our research, a majority of participants predict their networks will become compromised in 2015. These are indeed dangerous times, but there is still cause for optimism as organizations take active steps to prepare for the unexpected. Welcome to the new reality".
The full report is available to download from the CyberEdge website.
Photo credit: Tashatuvango/Shutterstock
-

BetterCloud provides added security for Google Apps
Publié: mars 12, 2015, 1:28pm CET par Ian Barker

There's no doubt that cloud office platforms offer gains in productivity and easier collaboration, but they also present challenges for information security teams who need to limit content sharing.
For organizations that must comply with industry regulations like HIPAA this can lead to significant legal risk which, until now, was extremely difficult to mitigate.
With the launch of BetterCloud Enterprise for Google Apps they now have a real-time auditing, compliance, and data loss prevention (DLP) solution for the popular cloud service. It offers Drive Compliance to allow administrators to continuously audit the contents of their organization's entire Google Drive in real-time. Using custom regular expressions, they can scan for social security numbers, payment information, or any other type of number or phrase, in an effort to certify compliance with industry regulations.
"At many organizations, millions of documents are created, edited, deleted, and shared daily, with little oversight," says David Politis, BetterCloud’s CEO. "An enterprise IT or information security team’s responsibility to meet privacy and compliance regulations requires a tool like Drive Compliance. BetterCloud Enterprise for Google Apps is the only product that makes real-time DLP available to all Google Apps customers, and the only solution that combines DLP functionality with the rest of the toolset that enterprises need when deploying Google Apps across their organization".
BetterCloud uses new APIs made available by Google to allow it to connect securely with data at its source, providing maximum control with minimal setup and no impact on network performance. This allows it to alert admins to security risks and policy violations through a dashboard, prompting administrators to take action. They can notify the document owner, correct the violation, or automate future occurrences by building context aware compliance policies.
BetterCloud Enterprise for Google Apps is available to try for free for 30 days and costs $2 per user per month following the trial period.
Image Credit: Nata-Lia/ Shutterstock
-

New online tool simplifies project management for smaller enterprises
Publié: mars 12, 2015, 12:42pm CET par Ian Barker

Project management can be daunting, especially for smaller organizations with limited resources or lack of expertise to use complex tools.
Dallas-based project and professional services automation specialist Vorex is launching an updated version of its cloud-based platform which offers new and enhanced features that aim to help SMBs better manage and grow their businesses, while increasing profitability.
It's aimed particularly at businesses such as IT service providers and professional services firms. By streamlining day-to-day tasks, Vorex frees up business owners' and managers' time so they can focus on strategy and growing their businesses, rather than on logistics and operations. Key features of the new release include the ability to transfer billable time into Quickbooks, creating invoices that map to tracked time.
It also offers enhanced native CRM features to track accounts, service desk tickets, contacts and new revenue opportunities. This can happen within Vorex's native CRM system, or integrate directly with leading CRM systems. There's Outlook Calendar integration too so users can directly and easily schedule projects, tasks, to-dos and appointments, as well as allocate resources according to existing schedules.
Vorex can keep track of the team's individual skills, skill categories and education levels to better match the talents of employees to upcoming and existing projects. An online dashboard offers improved project insight through graphics, statistics and charts in a single location.
"Vorex is taking our business management solution to the next level by adding features that our customers and channel partners need to run business more efficiently, effectively and profitably," says Vorex CEO and Founder Mike Salem. "We are on a mission to create the perfect software that allows companies and IT service providers to run their businesses smarter".
For more information on how Vorex can help streamline project management you can visit the company's website.
Photo credit: Tashatuvango/Shutterstock
-

Clarizen strengthens integration with Box
Publié: mars 9, 2015, 4:17pm CET par Ian Barker

Enterprise collaboration software specialist Clarizen is introducing enhanced integration between its product and cloud storage service Box, making it easier for businesses to manage and share materials.
Thanks to strengthened integration between the two cloud services, companies can now connect files and folders seamlessly between platforms, leading to increased productivity that drives business results.
"More than ever, people are constantly collaborating across organizations, teams and geographies -- this makes it crucial that the services they use work well together and provide a seamless user experience within a secure environment," says Roger Murff, VP of Business Development at Box. "We value our great partners like Clarizen that are committed to evolving their integrations with Box in an effort to address the new way that people work".
Key features of the integration include access to one-time authentication via oAuth, the ability to link existing Box files and folders to single or multiple Clarizen items, assigning of folders to collaborators, uploading of files to Box directly from Clarizen, and viewing of files and folders in context.
The announcement coincides with enhancements reports and dashboards in the Clarizen package to offer stronger business insights. Specific views and visualizations can be shared as 'widgets' or snapshots for a high-level executive view. These can be accessed by internal as well as external users, including customers, without requiring a login.
"Transparency and context are prerequisites for continuous improvement in today’s modern workplace," says Avinoam Nowogrodski, CEO, Clarizen. "Leaders need a 360-degree view of the health of their initiatives, so that they can quickly understand patterns, predict potential business trends and make organizational improvements. The world-class reporting capabilities in Clarizen’s latest release deliver deep insights to accelerate the speed of doing business".
Both of these enhancements will be on display at the Clarizen@Work conference in San Francisco from March 8-10 or you can find out more on the company's website.
Image Credit: Lightspring / Shutterstock
-

Google versus human -- how good is Google Translate?
Publié: mars 9, 2015, 1:50pm CET par Ian Barker

Earlier this year Google introduced a number of enhancements to its Translate service. As well as written text this now makes it able to transcribe and translate audio.
But how does it compare to a human? Translation service Verbal Ink has done a head-to-head comparison and released the results as an infographic.
The tests show that Google Translate has come a long way since its 2001 launch. It does a pretty good job of getting the gist of a text or recording, certainly enough for basic understanding. However, it still struggles with capturing nuance and its translated texts suffer from poor word choices that harm readability.
So whilst it's a good choice for day-to-day tasks where you need a translation fast, it seems Google has some way to go before it can be relied on for commercial documents.
The infographic is reproduced below. You can find out more and access the text files and recordings used in the test on the Verbal Ink website.
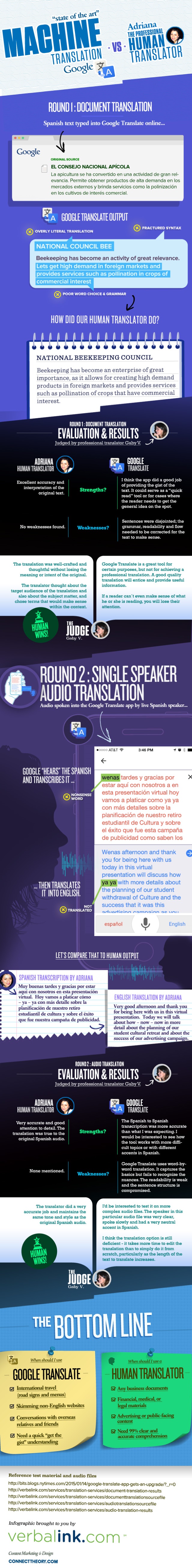
Image Credit: Cienpies Design / Shutterstock
-

Around half of mobile app demand comes from hobbyists and startups
Publié: mars 9, 2015, 11:23am CET par Ian Barker

Companies increasingly want to take their business to new consumers by using mobile sites and apps. But it seems that it's startups and hobbyists that are driving a big chunk of app demand.
ContractIQ, which offers a service that matches developers to software projects, has produced its latest report on app development trends and pricing, offering some interesting insights into the market.
Key findings include the difference between the cheapest app development market (Indonesia) and the costliest (USA) being about 30x. In addition only 10 percent of app publishers know what SDKs to use for their apps. The lack of knowledge among customers about SDKs and APIs leaves developers to evangelize the technology.
The report shows that 75 percent of app developers surveyed from over 500 app development agencies believe that demand for app development services will be robust in 2015. But a high proportion of their demand comes from hobbyists and idea stage entrepreneurs, the segments that are most susceptible to macroeconomic shocks. Even in a buoyant market, developers say that only 1 in 4 customers publishing an app have gone on to become a viable business.
Most developers are also confident that the rates they charge will rise by five to 10 percent in 2015, though this confidence is higher among iOS and Android developers than those working in Windows and HTML 5.
The full report, with more information about worldwide app pricing trends and the most popular development tools, is available to download from the ContractIQ website.
Photo credit: bloomua/Shutterstock
-

Financial companies seek cloud strategy for secure relationship
Publié: mars 6, 2015, 12:36pm CET par Ian Barker

Cloud technology is being adopted across a wide range of industry sectors and financial companies are no exception. But a new report from the Cloud Security Alliance suggests that many of them are still looking for the right strategy.
The survey targeted executives from banking, insurance and investment firms around the world. Whilst it found that cloud computing is becoming more and more prevalent throughout the financial sector, many respondents still don't have a firm strategy.
Among the findings are that 61 percent of respondents admitted that a cloud strategy was in the formative stages within their organization, with 39 to 47 percent planning to use a mix of in-house IT, private, and public clouds, and 18 percent planning to use private clouds.
None of the respondents had plans to be hosted mostly in a public cloud. Worryingly though the results of the survey also showed that the higher the electronic channel transaction base among a firm's customers, the less tough the policy with only three percent of these types of organizations indicating having a strict cloud policy in place.
"The results of this report are insightful into understanding how the financial services industry is progressing in terms of cloud adoption and how cloud providers can best serve their interests and needs," says Jim Reavis, CEO of the CSA. "We hope that cloud providers and financial institutions can use this as guidance to help accelerate the adoption of secure cloud services in the financial industry".
Increased transparency and better auditing controls are something 80 percent of financial firms want from their cloud providers, even more than better data encryption (57 percent). On motives for moving to the cloud, respondents indicated that flexible infrastructure capacity was at the top of their list (68 percent), followed closely by the need for reduced time for provisioning (63 percent).
The most popular services and features being adopted when moving to the cloud include CRM (46 percent), application development (45 percent), and email (41 percent). Backend services (20 percent) or virtual desks (14 percent) are low priorities.
The report also looks at compliance regulation requirements when moving to the cloud. Top of the list here is data protection (75 percent), followed by corporate governance (68 percent), Payment Card Industry Data Security Standard (PCI-DSS) at 54 percent, and national regulations on 47 percent.
The full report How Cloud is Being Used in the Financial Sector is available to download from the CSA website.
Photo Credit: Rrraum/Shutterstock
-

Intronis simplifies cloud backup and recovery for service providers
Publié: mars 5, 2015, 1:17pm CET par Ian Barker

Moving systems to the cloud presents new challenges when making sure that data is safely backed up. This is a particular issue for service providers who offer backup as an added value product for their customers.
Backup specialist Intronis is simplifying and accelerating real-time data backup and recovery for its channel partners with the launch of a new release of its Intronis ECHOplatform.
The latest version has enhancements designed to help channel partners better support more complex cloud, virtualized and physical IT environments, and attract new business by offering a real-time, cloud-based data recovery solution that’s built to protect the business.
Key features include Hyper-V Rapid Recovery for better support of hybrid IT environments by offering Hyper-V environment recovery from local image-based storage in as fast as 30 seconds. There's also Imaging Rapid Recovery which simplifies recovery for physical server environments from local image-based storage, using a combination of advanced algorithms, native data formats and reverse incremental backup techniques.
It enables object-level restore to retrieve specific files, folders, and databases from physical and virtual local image-based backups with greater ease, accuracy and efficiency. Plus it's VMware 6.0 ready to ensure channel partners will be able to provide native backup for the upcoming release of the industry’s leading hypervisor platform.
"Intronis is continually looking for ways to simplify the backup and recovery processes our partners use, and the 2015 Winter Release is another dramatic step forward," says Chuck DeLouis, vice president, product management at Intronis. "The Intronis ECHOplatform offers one of the fastest recover time objectives in the industry, while at the same time offering channel partners greater flexibility in how and what they recover. This combination of speed, flexibility, and reliability enables our partners to rapidly and efficiently get their clients back up and running in just minutes -- when they need it most".
More information on the latest release is available on the Intronis website.
Photo Credit: everything possible / Shutterstock
-

WorksPad aims to streamline enterprise mobility
Publié: mars 5, 2015, 12:00pm CET par Ian Barker
Businesses are increasingly keen to turn to mobile solutions, but this often presents problems in terms of integrating functions and keeping corporate data secure.
Launched at this week's Mobile World Congress, MobilityLab's WorksPad combines enterprise file sync and sharing, a fully-featured office package (Polaris Office Enterprise core) and a corporate email client in one app.
All of these capabilities are integrated into a single secure environment which allows control via centralized application level policies. The embedded office package allows document editing and users can attach documents to emails, save attachments on corporate resources, and manage file structures on iPad, iPhone and Android devices.
"Apple's and Google's mail, calendar, and contacts are good for consumers, but they are about a one function, per app approach. Acompli's 'Triaged Email' rebranded to Microsoft Outlook is about integration of mail, calendar and contacts in one app. But it has the same consumer user experience of working with one item at a time without ability to open multiple items to switch across them. This is the key mobility issue when supporting multitasking scenarios," says CEO of MobilityLab Sergey Orlik. "From another perspective, how do we work with business documents? Enterprise file sync and sharing solutions are about accessing file resources, viewing documents, and editing. However, these three key information worker tools -- file management, office and email client -- have traditionally been disconnected. WorksPad solves this entire problem in a secure and centralized way".
WorksPad's multiscreen user interface allows the opening of multiple documents, email messages and appointments on separate swipeable screens, with ribbons to keep track of all of the opened items. It also has a presentation mode on iPad, Android and Windows PCs that provides business users with cross-device screen sharing.
WorksPad is available on the Apple App Store and Google Play Store or you can find out more and sign up for a free trial on the company's website.
-

New platform helps fend off high volume cyber attacks
Publié: mars 4, 2015, 4:07pm CET par Ian Barker

Cyber attacks are getting bigger and more complex and are targeting many different types of organization and industry. This means defending against them is more than ever a major concern for businesses.
Attack mitigation specialist Radware has launched a new version of its DefensePro platform to provide enterprises with stronger protection.
As the industry's first dedicated attack mitigation platform to offer 100Gb interfaces with the ability to handle 230 million packets per second of attack traffic, Radware's DefensePro x4420 platform is designed for multi-tenant environments with the ability to support up-to 1,000 active policies, separate processing capabilities and customized management and reporting.
The new design offers up to 300Gbps of mitigation capacity while allowing customers to enjoy the widest range of simultaneous cyber-attack protection. It can address today’s most tenacious volumetric DDoS attacks -- where the amount of traffic becomes too much for a site to handle -- such as UDP reflection attacks, fragmented and out-of-state floods. At the same time it can pick out and mitigate the sophisticated non-volume threats which can lurk below the surface in multi-vectored attacks.
"Cyber-attacks have evolved and reached a tipping point in terms of quantity, length, complexity and targets," says Carl Herberger, vice president of security solutions for Radware. "In 2014, one in seven cyber-attacks were larger than 10Gbps and we've seen attacks 100+Gbps in size. The attack landscape is changing and cyber-attackers are getting more and more aggressive with their tactics. It's not uncommon for mobile carriers and cloud providers to experience extra-large attacks".
Radware's attack mitigation platform can provide service and cloud hosting providers with better value for their investment as it eliminates the need to deploy multiple devices and provides a high performance platform that can protect networks from sophisticated and volumetric attacks.
The platform is currently being showcased at Mobile World Congress in Barcelona or you can find out more on the Radware website.
Photo Credit: Andrea Danti/Shutterstock
-

Don't let your gadgets ruin a good night's sleep
Publié: mars 4, 2015, 12:09pm CET par Ian Barker

Blue wavelength light emitted by the screens of computers and gadgets is known to suppress the body’s production of melatonin, the hormone which regulates sleep.
Use of gadgets therefore can prevent you from getting a good night's sleep. Mobile accessory company Fabre Technik has come up with some tips to help you make use of your gadgets but still get some decent shut-eye.
The body produces melatonin in the two hours before bedtime so limiting gadget use during that two hour window is key to getting off to sleep. If you must check your email or catch up with the latest BetaNews story in bed use a device with a smaller screen as it emits less light, also hold it away from you as the closer it is the more light your eyes will take in.
You should also turn down the brightness or engage reading mode to reduce the amount of light produced. It's possible to get apps that change the wavelength of light produced depending on the time of day. These can help your ability to get to sleep and improve your sleep quality.
Finally, you need to get out more. Humans need blue light to alert their bodies and let them know it’s time to work. The more blue light taken in during the daytime, the better the body is able to desensitize itself to blue light's effects when it's time to go to bed.
Photo Credit: Shumilina Maria/Shutterstock
-

Employee file transfer and email habits put corporate data at risk
Publié: mars 4, 2015, 11:31am CET par Ian Barker

Employees are putting business data at risk with their email and file sharing habits. This is among the findings of the latest survey by email encryption specialist DataMotion.
Although companies are increasingly putting security and compliance policies in place nearly 44 percent of respondents admitted that these are only moderately enforced at best.
In addition more than three-quarters of respondents said they believe employees at least occasionally violate their company’s compliance and security policies. More than one in five said those who do so are aware of what they are doing, but violate the policy anyway to simply get their job done.
"Though the survey shows us there is year-over-year growth in the number of companies putting security and compliance measures in place, the widespread security risks occurring are of great concern," says Bob Janacek, chief technology officer at DataMotion. "Particularly at a time when a number of organizations -- both large and small -- have experienced serious data breaches, it is essential that companies have strong security and compliance policies in place and that they ensure their employees fully understand and diligently follow them".
Other findings from the survey show that 30 percent of respondents don't have the ability to encrypt email. Nearly 86 percent of respondents said their organization permits the use of mobile devices for email. However, of those who have the ability to encrypt email and allow email use on a mobile, almost 36 percent can't send and receive encrypted email directly from their mobile email client.
Smaller organizations are more at risk when it comes to mobile with 47.4 percent stating email encryption was not enabled on their mobile clients, versus 30.9 percent for large organizations.
The results show a lack of confidence too with more than half believing it was likely their company would be selected for a compliance audit within the next year. Yet, nearly 60 percent admitted they are, at most, only somewhat confident they would pass this type of audit.
The full report is available to download from the DataMotion website.
Image Credit: Balefire/Shutterstock
-

Monitoring third-party security is a major concern for enterprises
Publié: mars 3, 2015, 5:03pm CET par Ian Barker

A new study carried out by Forrester Research for security rating company BitSight Technologies reveals that third-party security has become a major concern for enterprises.
The results show that when it comes to tracking third-party risk, critical data loss or exposure (63 percent) and the threat of cyber attacks (62 percent) rank as the top concerns. These come above standard business issues, including whether the supplier could deliver the quality of service they were contracted for.
It also shows that the majority of IT decision makers believe that continuous third-party monitoring would have a major improvement on their security effectiveness in key areas. These include event identification time (76 percent), event remediation time (72 percent) and response times to high-profile events (71 percent).
However, whilst it's a major concern the findings also suggest that many businesses suffer a lack of resources to actively monitor and manage third parties. Only 37 percent of survey respondents reported tracking third-party security metrics on a monthly basis. This is despite the fact that 63 percent of respondents believe continuous third-party monitoring would improve their ability to screen vendors based on risk.
The landscape is changing though with 79 percent of respondents reporting that ensuring business partners and third parties comply with their security requirements is a top IT security priority over the next 12 months.
"The supply chain has become a cyber security minefield for companies, as we've seen with breaches caused by third-party vendors at Target, Neiman Marcus, Goodwill, Home Depot and many more," says Stephen Boyer, CTO and co-founder of BitSight Technologies. "Continuous, data-driven monitoring of third-party security vulnerabilities and threats has become essential for effective vendor risk management".
The full report is available to download from the BitSight website.
Image Credit: iofoto / Shutterstock
-

DDoS attacks have major impact on service providers
Publié: mars 3, 2015, 4:29pm CET par Ian Barker

A majority of service providers have experienced some form of DDoS attack and have experienced loss of revenue or customers as a result.
This is among the findings of a new report by security and DDoS protection specialist Black Lotus. Only 16 percent of service providers said they'd rarely or never experienced a DDoS attack whilst 35 percent are being hit by one or more attacks each week.
There's no doubt that DDoS attacks have a major impact, 61 percent of all service providers see them as a threat to their business. Attacks are carried out across industry sectors too, 64 percent of platform as a service providers have been impacted by DDoS, as have 66 percent of managed hosting solutions providers and 66 percent of VoIP service providers.
"DDoS attacks lasting hours or even minutes can lead to loss of revenue and customers, making DDoS protection no longer a luxury, but a necessity," says Shawn Marck, co-founder and chief security officer of Black Lotus. "DDoS attacks will continue to grow in scale and severity thanks to increasingly powerful (and readily available) attack tools, the multiple points of Internet vulnerability and increased dependence on the Internet. Enterprises have to move from thinking of DDoS as a possibility, to treating it as an eventuality".
How providers respond to attacks varies too. In the event of a DDoS attack, 34 percent of the surveyed providers remove the targeted customer, and 52 percent temporarily null the route used or block the problem customer. Despite their efforts though 85 percent of respondents say they've experienced customer churn due to DDoS attacks.
The full report is available to download from the Black Lotus website and there's a summary of the findings in infographic form below.
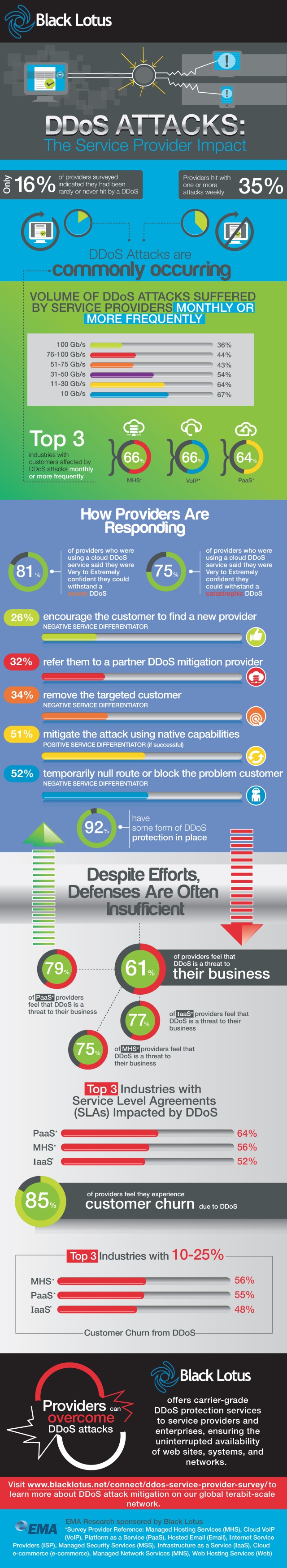
Photo Credit: Duc Dao / Shutterstock
-

Samsung devices overtake Apple in mobile ad impressions
Publié: mars 2, 2015, 3:50pm CET par Ian Barker

One of the advantages of advertising on digital platforms is that it reveals information about the devices and apps being used to view ads. This is useful for marketers but also echoes some general industry trends.
Digital advertising specialist Millennial Media has released its latest Mobile Mix report charting the use of its platform over the past year. The results throw up some interesting patterns. Among them are that Samsung saw the greatest number of impressions on the platform in the past year, unseating Apple who had previously been the leader.
This jump in Samsung impressions contributed to an overall increase in Android impressions, with hits from all Android devices growing six percentage points year-on-year. 54 percent of all tablet impressions came from Android devices. However, the Apple iPhone remains the most popular single device when measured by ad impressions.
More sophisticated devices and bigger screens has also led to an increase in video advertising. Some 29 percent of apps allowed video ads in 2014, up six percentage points from the previous year. Millennial's figures show that video and rich media ads see nearly twice the engagement rate of standard banners proving that they pay off for advertisers.
Looking at ad impressions by app type, games, music and entertainment, and productivity apps lead the way. However, health and fitness apps entered the top ten for the first time in 2014.
The Mobile Mix Report is available to download from the Millennial Media site along with breakdowns of data for specific regions.
Image Credit: Denphumi / Shutterstock
-

Mobile users face risks on multiple fronts
Publié: mars 2, 2015, 12:20pm CET par Ian Barker

A new report from security company FireEye, based on analysis of over seven million mobile apps during 2014, reveals that mobile users are being targeted from a number of directions.
Risks on the Android platform include malicious apps that steal information once installed, legitimate apps written insecurely by developers, legitimate apps using insecure but aggressive ad libraries, malware and aggressive adware that passes Google Play checks and is assumed to be safe, identity theft, and premium rate phone and SMS fraud.
Whilst malware on the iOS platform is still comparatively rare due to stricter app store review processes, there are other risks. The report identifies a new delivery channel for iOS malware that is able to bypass the Apple App Store review process. Attackers can take advantage of enterprise/ad-hoc provisioning to deliver malicious apps to end users, either through USB connections or over the air. FireEye researchers have uncovered more than 1,400 iOS apps publicly available on the internet -- signed and distributed using enterprise provisioning profiles -- that introduce security issues.
FireEye's director of technology Jason Steer writing on the company's blog says, "Apps are the future for online experiences to complete our jobs, shop, bank, use social media and many other purposes in modern daily life. Our mobile devices are also the most important piece of equipment we have today; they contain our diaries, contacts, emails, photos, videos, employer information and many other pieces of important and sensitive information. Yet our mobile devices still do not have sufficient security to ensure they, and the information they contain, are secure".
Apps are the main source of threat which means consumers and enterprises need to understand their behavior and the risks they may present. Legitimate app stores work hard to identify harmful content but Steer warns, "Third-party app stores, while providing app content not available elsewhere, provide a safe harbor for many more malicious apps to be available".
The full report is available to download from the FireEye website.
Photo Credit: style-photography.de/Shutterstock
-

The earphone's connected to the head bone - DIGICare bone conduction headphone [Review]
Publié: mars 2, 2015, 10:49am CET par Ian Barker

Bluetooth headphones are pretty common place but these from DIGICare are a bit different because they use bone conduction technology -- as does Google Glass and some hearing aids.
That means instead of sitting in or over your ears they rest on the sides of head and feed the sound into your inner ear via your skull.
First impressions are that the headset is light and nicely made using a combination of shiny white and matte black plastic. It comes with a hard case and a soft bag so you have a choice of how to protect it when you’re carrying it around. You also get a USB charger cable, some ear plugs and a carabiner-style clip so you can attach it to a belt or backpack when not in use.
There's a built-in microphone for making phone calls, a play/pause button on one side and a call answer/drop button on the other. The on/off switch, volume controls and charging point, with obligatory flimsy cover, are on the headband. Charging up from USB takes a couple of hours then you're ready to go.
It's a simple process to pair with your phone via Bluetooth as there are audible alerts that walk you through the process. You also get a tone when Bluetooth disconnects or goes out of range or when the battery is running low. The light weight means they're comfortable, there’s an adjustable band to adapt to different sized heads, although they’re a bit awkward if you wear glasses.
If you’re not used to bone conduction the listening experience feels slightly weird at first. You can still hear ambient noises -- unless you opt for the ear plugs -- but otherwise it's not unlike using conventional headphones. The bass isn't particularly strong which means these won't please the serious music listener but then I suspect that's not really the intended market here.
Getting the fit right is very important, if you don’t they'll shift slightly as you move around and you'll hear changes in tone as they do so. A little trial and error is necessary to find the right position for optimum listening.
There are a number of advantages to bone conduction technology. Because it bypasses the eardrum it still works even if your hearing isn't perfect and there's less potential to damage your ears with loud music. Plus, because it doesn't block other sounds, there's less potential to damage the rest of you -- by not hearing an approaching truck when you're out cycling or running for example.
If any of these things matter to you then these are well worth considering but if you're a hard core audio fan you'll probably want to look elsewhere.
Our review sample was provided by Geekbuying.com and the headphones cost $69.99. BetaNews readers can get a $15 discount by using coupon code ULNIVVZC at the checkout. Code expires on 28 March 2015.
-

The top four places your data is at risk
Publié: février 27, 2015, 4:49pm CET par Ian Barker

We all worry about protecting our information, but how do we know which activities or locations are most likely to put it in jeopardy?
Digital rights management company Seclore has produced an infographic showing the four places where your data is most at risk. Unsurprisingly perhaps some of these are areas where you have the least control.
Third parties are a particular worry. The Home Depot breach in 2014 saw details of 5.6 million credit cards stolen. Yet it seems businesses still haven’t learned the lesson, with only 32 percent of vendors having security certifications.
Mobile is a risk too with 113 phones lost or stolen every minute in the US alone and 86 percent of mobile apps lacking adequate security. The cloud is also a worry with 71 percent of IT professionals believing their cloud service providers wouldn’t alert them to a breach involving customer data.
Email is a bigger threat than you might think too with 88 percent of companies having experienced some sort of data loss via email. Each email is copied an average of six times thanks to team collaboration increasing the risk of exposure.
You can view the full infographic below.
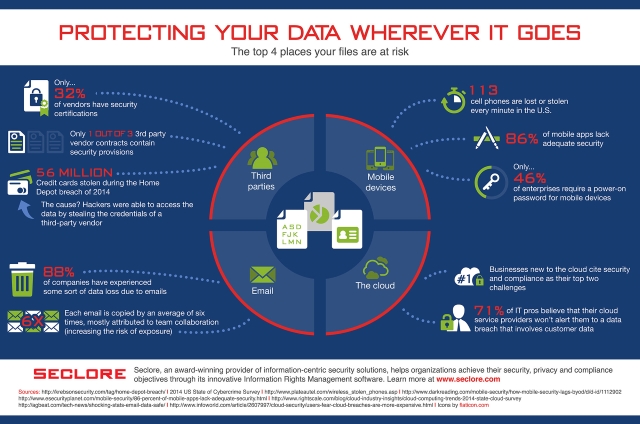
Photo Credit: D.R.3D/Shutterstock
-

Creating advocates for SaaS and B2B products
Publié: février 27, 2015, 10:58am CET par Ian Barker

One of the best ways of getting people to buy your product is to get your existing customers to recommend it. That’s equally true in the business world as it is for consumer products.
A new infographic from SaaS customer management specialist Bluenose looks at how companies can create more powerful advocates for their B2B and SaaS products.
Among the key points are that acquiring new customers can cost seven times more than retaining existing ones, so it’s important to focus on the customers you have. Satisfied users are more likely to become advocates for your business and can be worth as much as $500,000 each.
It's also useful to offer a rewards program for those who recommend your services to others. Some 84 percent of B2B decision makers start off the process with a referral and these leads are 36 times more useful than a lead from a cold call.
Employees are also an important part of the process. They are the face of the company and if they’re positive about the product it reflects well on the business. It's important that they know their product too, 67 percent of customers trust content provided by a company’s technical expert.
You can see the full infographic with other tips including promoting word of mouth and social media advocacy below.

Photo Credit: bikeriderlondon/Shutterstock
-

Emailage fights fraud with email address scoring
Publié: février 26, 2015, 6:42pm CET par Ian Barker

Email is the most common form of digital ID, used to login to websites, complete transactions and more besides. This means that over time each email address develops its own unique reputation and digital life based on its past behavior and actions online.
Phoenix-based startup company Emailage has used this to develop a risk scoring system for email addresses which will help companies to reduce the risk of fraudulent transactions. Emailage has successfully flagged over 2 million transactions as risky in the past year alone, amounting to $150 million it's saved customers. The company has now received $3.8 million in venture capital funding to further develop its product.
"Email is the most unique and common ID in the online world," says Rei Carvalho, CEO of Emailage. "By using our proprietary machine learning algorithms across a vast consortium of data, we are able to stop fraudsters in real time. As our customer base grows, our solution becomes more powerful and our industry-leading fraud detection rates will continue to improve. We are excited to use this financing to grow quickly and expand our offerings".
Emailage customers have already benefited from faster approval rates for 60 percent of transactions and improved pinpointing of the the most risky transactions with an average hit rate of 25 percent. Some customers are detecting 50 percent or more of their total fraud just by analyzing risk based on the email. Having this information available in real time not only prevents fraudulent transactions from occurring but also helps recognize reputable new customers that may have been declined based on other criteria.
More information on how email scoring is able to help prevent fraud is available from the Emailage website.
Photo Credit: Balefire/Shutterstock
-

Cloud-hosted script library simplifies web development
Publié: février 26, 2015, 5:59pm CET par Ian Barker

Developers often find themselves repeatedly going over the same ground when it comes to adding functionality like forms or product pages.
California-based Cloudward is aiming to make life easier for web app developers with the launch of Cloud Snippets. These are cloud-hosted scripts, powered by Google Cloud Services, that allow anyone to instantly add forms, surveys, landing pages, ecommerce product listings, and more using the simplicity of Google Docs, Sheets, and Drive.
Developers can add a Cloud Snippet to any website, including platforms like WordPress, Weebly, Squarespace and Wix, or any HTML page. All they have to do is copy and paste the JavaScript code and publish it. Cloud Snippets also gives developers the code allowing them to make customizations as required.
"Cloud Snippets are important because they allow anybody to easily build an independent, embeddable web app," says Cloudward co-founder and CTO Danny Kolke. "For the first time, a web designer or developer has the power to build sophisticated web functions without having to know PHP, Python, Java, etc. Small agencies and web designers can use Cloud Snippets to gain big-agency capabilities. Small businesses can easily add complex functionality to their websites. And enterprises gain development flexibility".
Cloudward has set up a Snippet Store which has lots of free snippets for developers to get started. It intends to open this up as a marketplace for other web designers and developers to build and sell their own custom snippets.
Current snippets include one to create a content slideshow by taking images and tagline descriptions from a Google Sheet and displaying them in a slider, and one to take addresses from a Google Sheet and display each on a map with a marker and an information window.
You can find out more about Cloud Snippets on the Cloudward website.
Photo Credit: dencg/Shutterstock
-

New tool simplifies translating apps into different languages
Publié: février 26, 2015, 3:03pm CET par Ian Barker
Developers put a lot of time and resources into the technical aspects of their apps. But when it comes to selling them in other markets there's often little left for localization.
Now OHT-Mobile, part of One Hour Translation, has a solution with the launch of Lingui, a low-cost way to localize apps quickly without the need for extra manpower, complicated processes or even the requirement to send updates to the App Store or Google Play.
"Having spent a lot of time and effort developing their application, one of the biggest challenges facing developers is how to make their applications accessible and engaging for users around the world," says Ofer Shoshan, CEO of One Hour Translation. "Lingui by OHT-Mobile allows developers to cut out the time consuming and expensive process of localizing applications for multiple audiences".
Lingui simplifies the development process by inserting a few lines of code into the app that detect text in the UI and allow the option to translate in a number of ways. There's the choice of automatic translation, professional human translation or crowd sourced translation. Once the process is complete, the update goes live instantly and everywhere allowing app users to choose from all active languages.
"Until now any newly translated apps would have to be uploaded to the relevant app stores, delaying the time to get the app to market. What's more, users often had to update the app in order to get support for new languages or updated translation," says Shoshan. "With Lingui, your app translations and supported languages are managed on OHT-Mobile's cloud. Updated translations or additional languages are simple and easy to add. There is no need to republish the app in the market or to update the app on the user's device".
Lingui will be on display at Mobile World Congress in Barcelona from the 2nd-5th March or you can find out more on the One Hour Translation website.
-

Using the power of big data to understand customers
Publié: février 26, 2015, 12:18pm CET par Ian Barker

Companies are increasingly tuning into the importance of understanding their customers in order to make their marketing more effective and big data has a key role to play in providing them with the information to do so.
A new infographic produced by Hadoop solutions specialist Datameer looks at how companies are using big data to build their brands and boost revenue.
Big data analysis can help to increase customer acquisition, reduce churn and enable businesses to develop more innovative products with features that customers actually want. The graphic uses two examples, the first being a credit card company that was able to achieve a 25 percent better conversion rate and reduce its annual advertising spend by $3.5 million thanks to big data.
The second example is an online game company that was able to understand the features that make players stay for longer and introduce new elements to boost revenue.
You can see the full infographic below and read more on the Datameer blog.
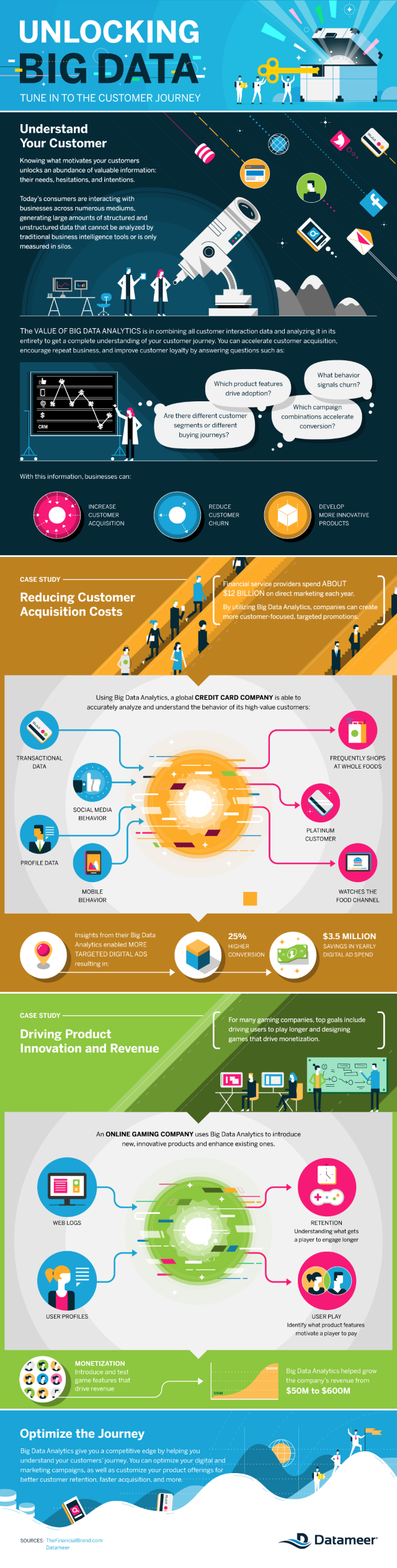
Image Credit: Maksim Kabakou/Shutterstock
-

Enterprises fail to get the best from mobile messaging initiatives
Publié: février 25, 2015, 5:46pm CET par Ian Barker

A new report from IDC and enterprise mobile specialist Amdoc's OpenMarket reveals that taking an ad hoc approach to mobile messaging is harming return on investment.
The findings reveal that 62 percent of businesses have more than one messaging platform deployed and 78.5 percent have more than one instance of the same platform active across different departments.
This disjointed strategy is problematic for today's enterprises, as 75 percent of companies demand payback on these initiatives in less than a year. The results indicate the need to adopt a flexible mobile messaging platform that supports multiple use cases across business functions.
According to IDC, it will be critical for enterprises to implement a streamlined platform with global reach that can be used company-wide. To do this, 29.7 percent of enterprises are looking to partner with a mobile messaging specialist, and a majority are seeking a global provider.
"With mobile devices in the hands of employees and customers who show a preference for messaging-based communications, businesses should focus on proven mobile communication formats such as SMS and MMS," says Robert Parker, Group Vice President, IDC Insights. "Enterprises must avoid deploying single use case products, and should seek comprehensive solutions that improve customer and employee communications across the business. To do so, they should select providers that have domain expertise, service flexibility, optimal professional services, and a knowledgeable customer service staff to ensure they are getting the proper support for all their mobile messaging initiatives".
70 percent of enterprises use mobile messaging for internal communications. However, IDC sees the largest area for future growth in the adoption of SMS and MMS as in service-focused initiatives such as customer surveys, opening up SMS channels for customer support and providing valuable, time-sensitive alerts and reminders.
The summary report is available to download from the OpenMarket website.
Image Credit: Bloomua / Shutterstock
-

New solution makes online payments simpler for small businesses
Publié: février 25, 2015, 4:29pm CET par Ian Barker

Being able to do business online is almost essential these days, but for smaller companies the mechanisms needed to accept payments can prove complex and expensive.
Specialist in web client engagement software for small businesses vCita is making things simpler with the launch of its new, seamless online payment solution for service-based small businesses.
According to MasterCard's 2014 Merchant Scope study, 90 percent of small businesses have an online presence, yet only 20 percent are leveraging their websites for product or service focused transactions.
The vCita LiveSite Online Payment system eliminates these barriers by allowing small businesses to use web technology for a cost-effective and convenient online payment system that works on any internet-connected device. LiveSite Online Payments gives businesses a website-integrated, online payments solution where clients can easily pay with any credit card, at any hour, even from their mobile phone. This caters to the growing population of consumers in the US who prefer using their mobile device to pay bills.
"We've created a solution that is easy to use and intuitive for small businesses to efficiently offer online credit card payment options to their clients," says itzik Levy, founder and chief executive officer of vCita. "For small businesses today, the ability to easily accept online payments in a secure and hassle-free manner is a huge advantage that can make or break a consumer's decision to continue the business relationship, and vCita is pleased to bridge this gap with these new capabilities".
Features of LiveSite Online Payment include a Pay Now button that accepts credit card payments to be deposited straight to a bank or PayPal account. It has a customized payment form, where the business can request additional information about the customer as part of the payment process, plus a seamless user interface ensuring the client doesn’t have to leave the business' website to pay.
There are also online payment options directly from Facebook, emails, and any other online presence. A self-service portal allows returning clients to be automatically recognized and view their account, inquire or pay their balance.
For more information on the vCita online payment and other engagement options you can visit the company's website.
Photo Credit: Slavoljub Pantelic/Shutterstock
-

Smart glasses, coming soon to an enterprise near you
Publié: février 25, 2015, 3:14pm CET par Ian Barker

Up to now smart glasses have been a bit of a gimmick, but they could soon be making a major impact in the enterprise market, allowing workers to communicate as they carry out tasks.
Eyewear technology company Vuzix has announced a partnership to use its Vuzix M100 Smart Glasses for the EyeSight platform from wearable software specialist Pristine. Customers taking advantage of the combined Pristine and Vuzix platform will benefit from impressive video quality, strong integrations into safety goggles and a vertically adjustable camera, useful for surgery and hands-on repair tasks.
"Pristine's EyeSight platform is a killer app for the exploding smart glasses market and enables users to collaborate in industries and locations never before imagined," says Dan Cui, Vice President of Business Development at Vuzix. "Having Pristine's solution optimized for our award-winning smart glasses will open new opportunities and deliver real value and ROI to customers around the world".
EyeSight is a powerful video communication platform for wearables that allows colleagues to securely collaborate and solve problems hands-free. It uses cross-platform architecture built on open source technologies and hosted in the cloud. This means no on-site hardware is needed and users can get up and running quickly with zero capital investment. For healthcare organizations, EyeSight also fulfills strict requirements for HIPAA-compliance.
This makes the software a good fit with Vuzix M100 Smart Glasses which are are the world's first commercially available hands-free display and wearable computer designed for enterprise users. The M100 contains a virtual display with an integrated camera and a powerful processing engine running Android. It can connect wirelessly using Bluetooth or Wi-Fi directly to most standard networks or to a smartphone.
"Our customers are generating incredible ROI. What used to cost them $2,500 per day now costs next to nothing. Using Vuzix technologies, we are delivering an incredible telepresence solution for clients in life sciences, industrial equipment, field service and healthcare." says Kyle Samani, co-founder and CEO of Pristine.
You can find more information about the M100 and enterprise smart glasses solutions on the Vuzix website.
Image Credit: Vuzix
-

Data classification is the key to protecting information
Publié: février 25, 2015, 12:27pm CET par Ian Barker

Although organizations are increasingly concerned about data protection many of them don’t have the appropriate tools in place to secure their information.
According to a new report from data loss prevention specialists Boldon James compiled by Bloor Research, although over half of organizations see data security as a major concern 47 percent say they don't have a data classification tool.
The report is based on a survey of 200 organizations in the UK and US. It finds that even where classification policies are in place 64 percent of respondents that have a critical or serious concern over data security admit that their policy is not being adequately enforced. This is partly because of a lack of knowledge.
Martin Sugden, MD of Boldon James says, "Enterprises need to understand what information they have and where it is held in order to know what level of security to apply". Security strategy also needs to take account of new technologies like mobile. Over a third of respondents stated mobile security to be of serious concern, particularly as mobile devices are easy to lose or have stolen.
Unsurprisingly financial services companies report the most concerns over data security, with almost all respondents from this sector saying that it is serious or critical. However, they're also most likely to have policies and classification tools in place. Manufacturing firms lag behind, most seeing data security as a low concern with only 27.5 percent rating it as serious or critical. They also lag in implementing data classification policies, with a quarter stating that they do not have one in place and just 41 percent using a technology tool for enforcing data classification.
But securing data based on classification needs a combination of technology and understanding and Sugden believes understanding is more important, "If users add labels themselves they have more trust in what they mean. They're therefore less likely to leave confidential documents lying around or read them on the train".
Boldon James' solution allows labels to be used to filter documents so that they can be kept within an organization or prevented from being sent to mobile devices or specific domains like Gmail. You can read more on the company's website.
Image Credit: megainarmy/Shutterstock
-

Ekko integrates communications across popular online services
Publié: février 24, 2015, 4:38pm CET par Ian Barker
It's rare these days to rely on just one service -- you find yourself using Facebook, Twitter, Gmail and more which means information and messages are coming at you from many different angles.
This can lead to information overload as well as security worries. With its new secure platform San Francisco-based Ekko is launching a way to streamline all of your communications and protect your privacy.
"Messaging has become fragmented across multiple apps and services. We created Ekko to simplify the way we communicate, and provide everyone with a way to keep messages private and secure," says Rick Peters, President and CEO of Ekko. "Ekko also offers new and unique messaging features, including comprehensive search, multi-modal messaging, and context-sensitive functions that we feel should be part of any messaging app. We’re confident that Ekko is the next generation of messaging -- private, secure, powerful, and right at your fingertips".
Available for iOS or as a web app, Ekko supports Facebook, Twitter, Gmail, iCloud, Exchange, Outlook, Yahoo, AOL, POP3, and IMAP accounts, with others in the pipeline. It uses a subscription-based model that allows you to link unlimited accounts and use channels to tune, filter, and search your messages in any way you want. Built-in, user-friendly features protect your data and support private and secure messaging. Crucially, Ekko doesn't track you or your data, nor does it scan your messages, or profile you in any way.
It allows users to apply easy-to-use security controls to any type of message, using any linked account. They can also password protect any message, redact it, or set it to delete on read -- after a predefined time or after a defined number of unique views. It lets you search simultaneously across all of your accounts ensuring you never lose track of anything important.
"A recent Pew Research Center poll revealed that 91 percent of adults surveyed felt consumers have lost control over how personal information is collected and used by companies. Clearly we, and many of you, are tired of trading away our privacy and being profiled in exchange for 'free' services and apps," says Peters. "That's why messages sent through Ekko will always be kept private, and personal data will always be protected".
Ekko charges a subscription of $5 per month (or $50 per year) but new users can try it out for $1 for the first month. You can download it from the Apple App Store or sign up via the company's site.
-

New cloud framework addresses data privacy concerns
Publié: février 24, 2015, 3:59pm CET par Ian Barker

Data privacy is a growing concern and a number of countries including Germany, France and Russia have recently adopted new data protection regulations to protect their citizens' information.
Add in regulations like HIPAA and FINRA in the US and it's clear that businesses need to have an infrastructure to meet the various requirements or face possible legal consequences.
Data protection and governance specialist Druva is launching a set of new capabilities that offer a comprehensive data privacy framework to enable businesses to meet growing global privacy demands.
Built on the company's existing cloud security offerings it addresses concerns about corporate and employee data misuse and emerging legal data requirements. Druva centralizes and controls business data residing on employees' desktops, laptops, tablets and smartphones via integrated endpoint backup, data loss prevention, IT-managed file sharing, and data governance controls. It then continually mirrors end-user data, which enables rapid data recovery for lost or stolen devices, allows remote user access to any file or folder from any device, and supports eDiscovery, compliance and forensics needs when required.
Using a single cloud solution it has support for 11 different global admin regions. So for example companies with operations in Germany can comply with the country's tough employee data legislation. But whilst meeting local requirements enterprises can maintain a single global record of activity.
"Securing data is important, but addressing security without enacting appropriate privacy measures leaves data -- and companies -- vulnerable. Today, more than ever, global organizations must comply with regional data regulations. Privacy concerns are being forced into IT’s top priorities. Focusing exclusively on security can compromise privacy, exposing organizations to negative publicity as well as possible legal and regulatory action," says Jaspreet Singh, CEO of Druva. "With 70 percent of new inSync customers now choosing our cloud deployment option, we have developed a rigorous privacy framework to reduce those risks and support their global needs".
You can find more information about the framework on the Druva website.
Photo Credit: Slavoljub Pantelic / Shutterstock
-

Machine learning speeds up web application load times
Publié: février 24, 2015, 3:16pm CET par Ian Barker

The increase in web application use means that we're loading more code than ever into our browsers. According to httparchive, the amount of JavaScript used by the top 100 websites has almost tripled in the last three years whilst HTML has almost doubled. This has performance implications because larger page-sizes mean end users have to wait significantly longer for web pages to load.
California-based cloud delivery service Instart Logic is hoping to improve things with the launch of SmartSequence, a new technology that employs machine learning to optimize how HTML and JavaScript code is loaded in browsers.
SmartSequence uses a cloud-client architecture and machine learning technology to accelerate JavaScript and HTML, enabling browsers to load only the code that's needed, thus reducing download size and speeding up performance.
It learns which code is most frequently used by watching user behavior. For JavaScript Streaming, it then downloads only what a web page or web application needs, while ignoring unused code. For HTML Streaming, it determines which portions of dynamic HTML are used across all users, and sends that in advance. SmartSequence can also learn which sections of the page <HEAD> are dynamic as opposed to static and patch dynamic data in as needed.
"With SmartSequence, we are taking a revolutionary approach to a critical web performance challenge that is created by dynamic HTML and heavy use of JavaScript," says Peter Blum, vice president of product management at Instart Logic. "Our team of computer scientists and algorithmic experts have developed new machine learning techniques that enable us to intelligently stream JavaScript and HTML code, greatly improving page load times and customer experience".
SmartSequence is available now as part of Instart Logic's software-defined application delivery platform and you can read more about it on the company's blog.
Image Credit: isak55 / Shutterstock
-

UK businesses don't all have their heads in the cloud
Publié: février 24, 2015, 11:44am CET par Ian Barker

Although as we reported last week more businesses are turning to the cloud it seems that some UK companies are lagging behind the trend.
According to a new Service Provider and Performance Satisfaction survey by audit and accounting specialist KPMG 71 percent of UK organizations are spending 10 percent, or less, of their IT budget on cloud services.
As part of a global study of almost 2,100 contracts covering deals worth £7.8 billion (around $12 billion) it looked at 330 UK-based contracts. Asked why they are reticent about employing cloud services, the top 3 reasons cited by UK respondents centered around data location, security and privacy risks (26 percent), concerns over regulation and compliance (16 percent) and cynicism around the ease with which cloud services can integrate with legacy systems (15 percent).
The results show that many organizations continue to rely on 'tried and tested' outsourcing models. The favored destinations for outsourced IT support services remain India (51 percent), Poland (8 percent) and South Africa (8 percent).
"Despite widespread acceptance that cloud services offer access to the latest technologies, and make IT more accessible, adoption remains relatively sluggish. While concern about the security risks surrounding new technology is understandable it may also be disproportionate, as cloud options are just as safe as other outsourcing solutions. Of course, investors and stakeholders will welcome caution on the part of the buyers, but they also want to see innovation, meaning that UK plc will need to find the right balance to remain competitive," says Jason Sahota, director in KPMG's Shared Services and Outsourcing Advisory team.
The survey also shows a nervousness about IT spending in the UK despite improvements in the economy. Only 43 percent said they plan to increase spending on outsourcing in the next two to three years. This figure contrasts with 77 percent this time last year.
More information of the study is available on the KPMG website.
Image Credit: Brian A Jackson / Shutterstock
-

Securing enterprise mobile systems [Q&A]
Publié: février 24, 2015, 11:12am CET par Ian Barker

The use of mobile devices for business presents a new set of challenges both for IT departments and the broader enterprise. This is leading many companies to turn to enterprise mobility management (EMM) solutions to secure their data and devices.
But how effective are enterprises at looking after mobile data and how will they need to adapt to the needs of new legislation? We spoke to Ryan Spence, Director of Enterprise Mobility Management for managed service company MOBI to find out.
BN: How important is it for businesses to have procedures and protection in place to protect their use of mobile?
RS: The need for active security design for the mobile workforce is nothing short of paramount. Properly designed security procedures and platforms are so critical to a valuable mobility program that I would recommend appointing security experts to help develop your security needs. Mobility platforms and the devices they manage are very good at constant change. This means organizations are required to create adaptive security structures.
BN: Does the advent of BYOD and the proliferation of different operating systems and devices make EMM more difficult to implement?
RS: Device and OS diversity do make strong EMM programs very complex and with that complexity comes increasing difficulty to build and maintain. The complexity of properly implemented EMM solutions requires integrators with expertise across diverse disciplines. It is common for current EMM solutions to be underutilized because so few organizations are clear about all of the moving pieces of EMM. The field of mobility arrived without respect to business processes or platforms, requiring business and IT to change. Change, especially in competitive markets, is a difficult process for everyone.
BN: How complete an answer are technical solutions? Isn't educating employees in safe data practices equally important?
RS: That's correct. Technical "solutions" are not, in themselves, the totality of security design. Technical solutions are vital, but they must be designed hand-in-hand with an organization’s education and communication strategy, business goals, and projections for the changes yet to come. Technical solutions only go so far, and if poorly implemented, they can create more problems and slow an organizations ability to win in their market. More often than not, this is what I see happening to organizations who are attempting to implement security measures. It is not enough to appoint a person, or buy a technology, or implement policies. Organizations must now revisit how they think about nearly every process and reshape it around the assumptions of mobility.
BN: How will President Obama's proposed data breach notification law affect the way businesses handle data security?
RS: Well, honestly, I don't think the proposed law will inform how businesses think about their data security. It was already common for states to require organizations to report data breaches. The proposed law simply unifies all current requirements across the US, making the requirement clear no matter the location of your organization. The proposed timeline on breach awareness will require businesses to be aggressive about their internal reporting in order to inform legal and messaging departments.
BN: Is this likely to have an impact beyond the boundaries of the IT department?
RS: Absolutely. As mentioned above, the proposal creates requirements that will effect PR and Legal more than technical. The impact of a required timeline on public awareness will predominantly be felt by departments outside of IT. There isn't anything technologically new in the proposal, it is really geared toward information and what an organization’s legal requirements are around public disclosure.
BN: Do you think legislation will lead to greater overall visibility in terms of the way enterprises handle data security?
RS: That's a great question. For good reason, much of the dialogue around security is not part of the public discourse. Discussing security designs publicly can have the unfortunate result of increasing risk. I do not anticipate legislation increasing visibility into enterprise security, but I do expect the frequency of data breach to compel open, public conversation around the difficulties of providing security, the complexity of security design, how this generation defines privacy, the nature and lifecycle of data, and so much more. The questions around security in the mobile age force us to dig deeply into how we have built technology, what we must do to move forward safely, and what kind of society and organizations we are working to build.
Image Credit: Anan Chincho / Shutterstock
-

Old threats still dominate the security landscape
Publié: février 23, 2015, 4:28pm CET par Ian Barker

Most of the biggest IT security risks aren't new but are threats that have been around for years or even decades.
This is one of the findings of the latest HP Cyber Risk Report published today which looks at pressing security issues facing enterprises during the previous year and indicating likely trends for 2015.
"Many of the biggest security risks are issues we've known about for decades, leaving organizations unnecessarily exposed," says Art Gilliland, senior vice president and general manager, Enterprise Security Products at HP. "We can't lose sight of defending against these known vulnerabilities by entrusting security to the next silver bullet technology; rather, organizations must employ fundamental security tactics to address known vulnerabilities and in turn, eliminate significant amounts of risk".
Among the key findings of the report are that 44 percent of known breaches came from vulnerabilities that are 2-4 years old. Attackers continue to use well-known techniques to successfully compromise systems and networks. Every one of the top ten vulnerabilities exploited in 2014 took advantage of code written years or in some cases decades ago.
The main causes of commonly exploited software vulnerabilities are defects, bugs, and logic flaws. Yet most vulnerabilities stem from a relatively small number of common software programming errors. This means that old and new vulnerabilities in software are swiftly exploited by attackers.
Server misconfigurations represent the number one vulnerability. Over and above things like privacy and cookie security issues, server configuration issues dominated the list of security concerns for enterprises in 2014, providing adversaries with access to files that leave an organization susceptible to an attack.
Additional avenues of attack were introduced via connected devices. As well as security issues presented via Internet of Things devices, 2014 also saw an increase in the level of mobile malware. As the computing ecosystem continues to expand enterprises must take security into consideration or attackers will continue to find more points of entry.
In order to stay safe HP recommends that businesses carry out a number of measures including keep their software patches up to date, carry out regular penetration testing, and take advantage of intelligence sharing to reduce risk.
The full Cyber Risk Report 2015 is available to download from the HP website.
Image Credit: Myibean/Shutterstock
-

Dear EE, it really shouldn't be this way
Publié: février 20, 2015, 5:40pm CET par Ian Barker

Dear EE,
We've known each other for a long time, you were called Orange when I first got to know you. A work colleague said we'd be good together and he was right. We've been through more than 12 years and five pay as you go mobile phones together. Then you decided to change your name to EE. What's in a name? I thought, a change to what was shown on the screen of course, but the service seemed the same as before so we carried on and I was still happy. Until I decided I needed a new phone.
I went to your website which had a shiny new look, alarm bells really should have started to ring at this point -- I'll come to that in a bit -- but it was Black Friday, you were offering good deals and I placed an order.
You emailed me to say there'd be a delay due to strong demand but that was okay. Then a few days later you send me a message, displaying high levels of apostrophe misuse, telling me that you didn't have the phone I ordered in stock but that you’d be in touch within 21 days to tell me what was happening or suggest an alternative.
I waited, Christmas came and went, so did New Year, you didn't email me any more. Had I done something wrong? Then in February a chance visit to your website revealed that the phone I'd ordered was back in stock. I called customer services -- a process that involves one of the most labyrinthine menu systems known to man -- and spoke to someone who said the phone was indeed in stock and I could have one next day, still at the Black Friday price. Good, although I really shouldn’t have had to chase you over this you should have kept in touch. But a new phone is on the way so everything will be all right. I thought...
The phone arrives, and this is where I knew your website should have rung alarm bells. On your old Orange site I could log into my account before ordering, the new phone came with a SIM programmed to my old number, I just activated it and all was good. On your new site there seems to be no link between my account and your shop. The new phone arrives with a SIM that has a new number and I have to get my old one swapped across.
Still, that shouldn't be a problem, there's even a page on your website to do it. Except the page doesn't work, it asks for a 19 digit SIM code, the new card you sent me only has 12. So I call your customer services line again, another trip down Menu Lane, and talk to a pleasant chap who doesn't really know what he's doing and has to keep putting me on hold to talk to colleagues. Eventually he tells me the transfer is set up and will take up to 72 hours, after which my old SIM will stop working and I can switch to the new one.
The following day I receive a text from you saying my credit is low. I knew there was about £20 on there when I started so I assume this is evidence of the transfer happening. Switch on the phone with the new SIM and I have credit, but I have the wrong phone number. Another call to customer services, "press three if you're losing the will to live," and I speak to someone else. She tells me this is normal, that the credit will move first and the number will catch up.
The problem is I now need two phones. One with credit to make calls, one with my old number to receive calls and texts -- which I can’t reply to because it has no credit. Another day later and the old SIM stops working but if people ring my old number it comes up unrecognized so no one can contact me. My online account login no longer works either. None of this would be so bad if you properly explained the process or sent updates so I knew what to expect.
At last! After two days you’ve finally managed to put my number and credit back together but, EE, I’m afraid that you and I are drifting apart. I still can't login to my online account and it really shouldn't be this hard to switch to a new phone with your existing provider.
Maybe things will be better when you merge with BT but I’m not holding my breath.
Yours truly,
IanPhoto Credit: NinaMalyna/Shutterstock
-

IT departments take the lead in bringing cloud services to the enterprise
Publié: février 20, 2015, 2:39pm CET par Ian Barker

It’s no surprise that more and more organizations are using the cloud, but the latest State of the Cloud report from RightScale throws up some interesting trends.
The company surveyed 930 technical professionals across a broad cross-section of organizations about their adoption of cloud computing.
Among the findings are that a vast majority, 93 percent, of organizations surveyed are running applications in the cloud or experimenting with infrastructure-as-a-service. In addition 82 percent of enterprises now have a hybrid cloud strategy, up from 74 percent in 2014.
It seems to be IT departments that are driving the move with 62 percent of enterprises reporting that central IT makes the majority of their cloud spending decisions. 43 percent of IT teams are offering some form of self-service portal to allow access to cloud services, with an additional 41 percent planning or already developing a portal.
Public cloud is the most popular with 88 percent of enterprises using it compared to 63 percent with private clouds. However, the private cloud leads in workloads with only 13 percent of enterprises running more than 1000 virtual machines in public cloud, while 22 percent of organizations run more than 1000 VMs in private cloud.
Amazon Web Services is the most popular public service, AWS adoption is 57 percent in this years' survey, while Azure IaaS is second on 12 percent, up from 6 percent in 2014. Among enterprise respondents, Azure IaaS has narrowed the gap with 19 percent adoption compared to AWS with 50 percent. The rebranded vCloud Air from Vmware comes in with seven percent adoption among enterprises, behind AWS, Azure, Rackspace, and Google.
Despite this widespread adoption there's still room for more with 68 percent of enterprises saying they run less than a fifth of their application portfolio in the cloud. 55 percent report that a significant portion of their existing application portfolio, although not in cloud, is built with cloud-friendly architectures.
A full copy of the report is available from the RightScale website.
Image Credit: everything possible/Shutterstock
-

Large enterprises targeted by mobile Trojans
Publié: février 19, 2015, 4:31pm CET par Ian Barker

Mobile cyber threats are more common and more sophisticated than ever before, with a number of high profile threats in the past year.
According to a new report from security companies Check Point and Lacoon Mobile Security, this means mobile devices are growing into a serious threat to the enterprise.
The survey monitored more than 500,000 Android and 400,000 iOS devices from over 100 countries, uncovering over 20 variants and 18 different mobile remote access Trojan (mRAT) families. Of the 1,000 devices found to be infected 60 percent were Android and 40 percent iOS.
It finds that enterprise employees are increasingly targeted by mRATs, risking sensitive data found from emails, messages, keystrokes, calls, employee locations and more. Large organizations in the US have only a 0.21 percent chance of an infection, but employees of infected corporations are twice as likely to be infected by mRATs. If there are 2,000 devices or more in an organization, there is a 50 percent chance that it will have infections within the enterprise network.
It also points out that attacks on organizations are clustered. Attackers choose certain large organizations and attack multiple targets inside them, as opposed to just attacking corporate employees of random organizations.
There's a summary of the findings in infographic form below or the full report is available to download from the Lacoon website.
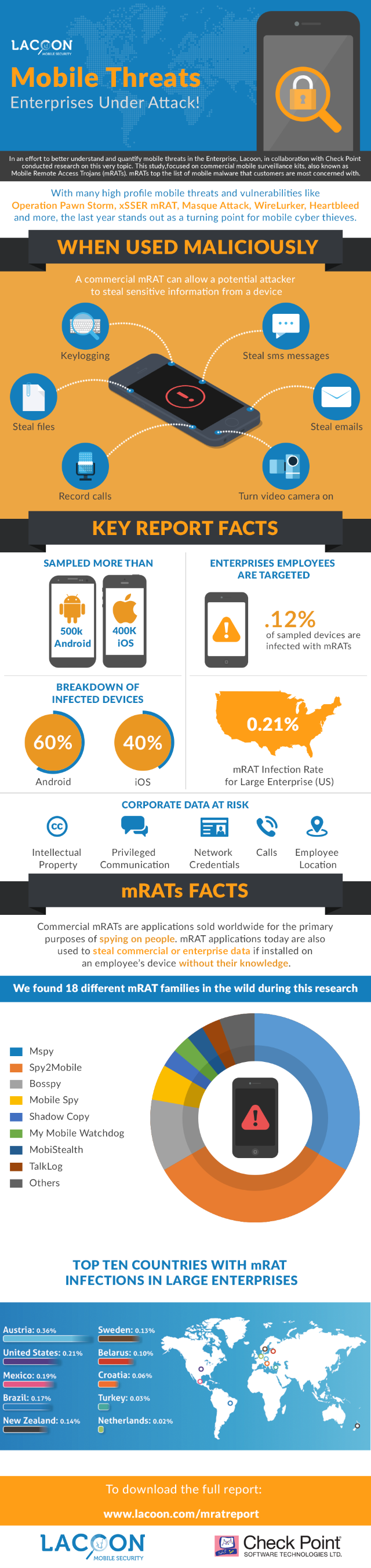
Image Credit: watcharakun/Shutterstock
-

Fighting cyber threats hampered by disconnect between IT and business
Publié: février 19, 2015, 3:26pm CET par Ian Barker

A disconnect between systems leaders and business leaders coupled with a lack of resources is keeping enterprises from properly addressing cyber threats.
This is according to a new study commissioned by defense and security company Raytheon and conducted in conjunction with the Ponemon Institute.
Among the findings are that less than half of respondents (47 percent) believe their organizations take appropriate steps to comply with the leading cybersecurity standards. Also only one-third of those surveyed believe their organizations are prepared to deal with the cyber security risks associated with the Internet of things (IoT) and the proliferation of IoT devices.
Only 47 percent of respondents believe their organizations have sufficient resources to meet cybersecurity requirements. Plus 66 percent of those surveyed indicate that their organizations need more knowledgeable and experienced cyber security practitioners.
When asked about trends over the next three years almost half of respondents believe zero-day threats will become one of the most prevalent cyber threats. More than one-third (35 percent) believe attacks on critical infrastructure will become one of the world’s five most prevalent threats.
Senior IT leaders see the use of virtual currencies as being a low risk to their organizations today but likely to become a very high risk in the future. Surveyed CISOs believe that when it comes to strengthening cyber security, the three most important technologies in the future will involve big data analytics, forensics and next-gen firewalls.
"You don’t have to wait until you’re attacked to take cybersecurity seriously," says Jack Harrington, vice president of cybersecurity and special missions at Raytheon Intelligence, Information and Services. "From the board room to the President’s desk, rallying around the cybersecurity issue is critical to address the real threats we face as a global society".
You can see an overview of the report's findings in infographic form below, or read more on the Raytheon website.
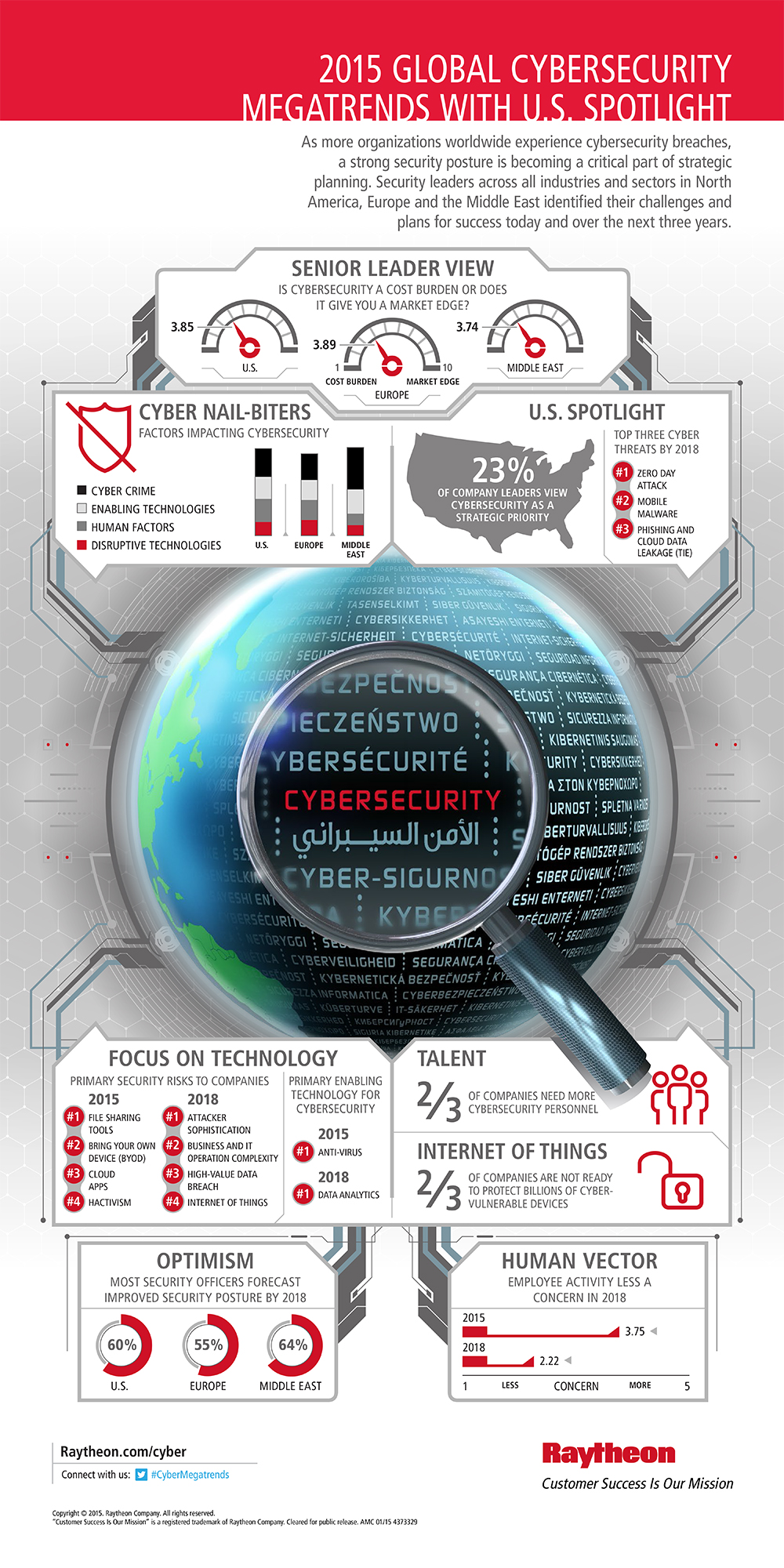
Photo Credit: Sergey Nivens/Shutterstock
-

DataRPM brings machine learning to big data
Publié: février 18, 2015, 5:26pm CET par Ian Barker

We constantly hear about the benefits big data can bring to organizations, but a shortage of expertise means that many are missing out. A recent McKinsey report reckoned that the US alone faces a shortage of up to 190,000 people with big data skills.
In order to overcome this DataRPM is introducing Smart Machine Insights which uses machine learning to automatically model data, perform advanced statistical analyses, and present key insights to users in an easy to use visual format.
"This is not a human scale issue, it' a machine scale issue," says CEO of DataRPM Sundeep Sanghavi. "As Smart Machines dominate the disruption in the next decade, the only way to provide any insights in any reasonable time frame is through machines. Current data discovery tools presume that the enterprise knows where to look and what to specifically ask and have enough resources and skills to address it. As we learned with one of our smart enterprise customer, Cisco, this assumption is simply flawed, hence we are advancing beyond data discovery to insights discovery using smart machines, which will completely reshape how analytics is performed on Hadoop infrastructure".
DataRPM runs natively within Hadoop and its algorithms automatically discover entities and relationships in the data and conduct statistical analyses and hypothesis tests. This includes machine learning algorithms such as time-series analysis, forecasting, prediction, root cause analysis, anomaly detection, recommendations and more.
You can visit DataRPM's website for a demonstration of how it works or the solution will be on display at Strata + Hadoop World in San Jose from February 17-20th.
Image credit: David Gaylor / Shutterstock
-

New software boosts productivity for event managers
Publié: février 18, 2015, 4:00pm CET par Ian Barker

Organizers of events and conferences often find themselves using multiple software tools in the process, from ticketing services and project management to emails and spreadsheets.
To streamline things Bizzabo is launching what it calls an Event Success Platform, equipping small to medium event organizers with a complete system to promote, manage and monetize their events.
"The Bizzabo Event Success Platform is the next step in the natural development of our product -- a comprehensive system where event organizers can actually take more ownership of their event branding and overall event experience," says CEO Eran Ben-Shushan of Bizzabo. "After working closely with thousands of organizers we understood the need for a holistic event software that works. We wanted to free the industry from a reliance on multiple siloed tech solutions that increase an event organizer’s workload, minimize their ability to measure success and limit productivity. By evolving our current product offering we are able to provide a one stop shop for all event technology needs, delivering the same quality we’re known for through a much more enhanced and complete experience from start to success".
Bizzabo's Event Success Platform has been trialled by a number of conferences around the world prior to its official launch. It can create an event website, sell tickets, launch an event app, initiate email marketing campaigns, build engaged networking communities. It can also help organizers get to know their audience using a smart contact management system.
The platform helps organizers measure success too by generating real-time analytics on each feature giving a snapshot of all aspects of an event's progress as it happens. The success dashboard allows organizers to deliver on measurable ROI to stakeholders, and track how they're doing compared to their goals.
Bizzabo is available online and on mobile platforms, for more more information go to the company's website.
Image Credit: Maxim Blinkov / Shutterstock
-

New cloud platform helps promote employee engagement
Publié: février 18, 2015, 1:31pm CET par Ian Barker

If a workforce is engaged people will be happy and more productive in their jobs, so it's something that businesses are keen to promote. But a Gallup survey last year found that 87 percent of workers worldwide and 70 percent of employees in the US are either not engaged or are actively disengaged in their jobs.
In order to try to put this right Californian company Glint is launching a real-time cloud solution to help people succeed at work. It's based on attractive and user-friendly pulse surveys that take only two or three minutes to complete.
Automatic analysis of survey data gathered then delivers immediate insights into key employee engagement drivers like leadership, culture, manager, and recognition. Managers can analyze the data by business unit, tenure, location or performance rating, while protecting individual employee confidentiality. In addition, Glint's cloud solution delivers smart alerts that can highlight groups with engagement scores that fall below industry benchmarks or company averages, as well as flagging up significant increases or decreases in scores.
"We created a platform to deliver real-time feedback that allows you to drill down into specific engagement data while ensuring a level of confidentiality that employees need in order to give direct and honest feedback," says Glint CEO and Co-Founder Jim Barnett. "In addition, we spent a lot of time and effort designing our pulse surveys so that they are a quick and positive experience that employees look forward to, as opposed to the dreaded annual survey".
Unlike traditional employee engagement solutions that produce reports with a long time lag, Glint delivers real-time insights that can keep pace with the business. It's also quick to implement and easy to configure allowing companies to get started quickly.
Glint is available on a SaaS subscription model, you can find out more or sign up for an introductory webinar on the company's website.
Image Credit: wavebreakmedia / Shutterstock
-

New vulnerabilities kick off 2015
Publié: février 17, 2015, 3:46pm CET par Ian Barker

There's always that tiny glimmer of hope that in some way a new year is going to be somehow different from and better than the one that went before.
Usually it's extinguished quite quickly and it seems that, in software terms at least, 2015 is no exception according to the latest vulnerability report from Secunia released today.
It finds that in the last quarter of 2014 there were 1,357 new vulnerabilities in the 20 most used software products and that the vendor with the most vulnerable products in the period was IBM. The single product with most vulnerabilities was X.Org Xserver, the open source X Window implementation.
2015 meanwhile has got off to a bang with two zero day vulnerabilities for Adobe Flash in January and one at the beginning of February. As Secunia points out a zero day in a popular product like Flash, "...means there are more entry points into any organization. The only thing to do about it is to either remove the affected product from everywhere in your infrastructure -- which can effectively paralyze your business -- especially when the affected application is bundled and widespread -- or have complete visibility to your systems and complete data control."
The report also highlights a new set of patches for Java in Oracle's January update which see 19 vulnerabilities fixed. Java is high on Secunia's 'Most Exposed' product list thanks to its large market share, but many users simply don't bother to patch it.
The Ghost vulnerability in GNU Library C was patched in version 2.18 as long ago as 2013. However, older versions are often bundled in other applications which may remain unpatched. Secunia has issued advisories on 24 products made vulnerable by Ghost, including McAfee, Cisco, IBM, Red Hat and Xerox. Exploitation of Ghost may allow for remote code execution so users are advised to make sure their product patches are up to date.
There's some praise for Google in the report for relaxing its strict 90-day rule on disclosing vulnerabilities. On 13 February it amended its policy to allow a two week grace period to allow vendors to release patches.
You can read more about Secunia's vulnerability reviews on the company's website.
Image Credit: Pavel Ignatov / Shutterstock
-

Malware on the increase as Android and Windows battle for 'most infected' top spot
Publié: février 16, 2015, 4:57pm CET par Ian Barker

According to a new report from telecommunication company Alcatel-Lucent's Motive Security Labs security threats to mobile and residential devices and attacks on communications networks all rose in 2014.
It estimates that 16 million mobile devices worldwide have been infected by malware. It also points out many retail cyber-security breaches in 2014 were the result of malware infections on cash registers or point-of-sale terminals, not online stores, so shopping offline isn't guaranteed to keep your details safe.
The report finds that malware infections in mobile devices increased 25 percent in 2014, compared to a 20 percent increase the previous year. Android devices have now caught up with Windows laptops, which used to be the primary workhorse of cybercrime. Infection rates detected by researchers are now split roughly 50/50 between Android and Windows devices.
Less than one percent of infections come from iOS and Blackberry devices, indicating the benefit of their more strictly controlled app stores. However, new vulnerabilities indicate that these platforms aren't entirely immune from threats. Alcatel-Lucent says that mobile malware generally is gaining in sophistication with more advanced command and control features.
The overall monthly infection rate in residential fixed broadband networks is up too at currently just under 14 percent, a fairly substantial rise from the nine percent recorded in 2013.
The big increase in mobile infection rates is aided by the fact that many users still don't take proper precautions. Few people would now think of attaching a Windows PC to the web without protection but the same isn't true of Android. The spotlight therefore tends to fall on service providers to address the issue.
"With malware attacks on devices steadily rising with consumer ultra-broadband usage, the impact on customer experience becomes a primary concern for service providers," says Patrick Tan, General Manager of Network Intelligence at Alcatel-Lucent. "As a result, we're seeing more operators take a proactive approach to this problem by providing services that alert subscribers to malware on their devices along with self-help instructions for removing it".
The full report is available to download as a PDF from the Alcatel-Lucent site.
Photo Credit: style-photography.de/Shutterstock
-

CIOs are being held back by their focus on details
Publié: février 16, 2015, 11:25am CET par Ian Barker

Chief Information Officer (CIO) is usually seen as a plum role in technology organizations. But new information from search specialist Lucidworks reveals that day-to-day responsibilities are holding back CIOs from driving innovation.
Some 25 percent of CIOs are solely responsible for leading tech-driven innovation at their organizations, but most of their time is being taken up with problem solving and troubleshooting.
Ideally CIOs would like to be spending 57 percent of their time driving innovation but currently are only spending 12 percent. In order to free up time for innovation they're increasingly turning to unconventional activities like hack days, study tours and tech showcases.
There also seems to be a trend towards recruiting more staff to take pressure off the department head, with 87 percent of CIOs surveyed saying they plan to increase headcount in the coming year. The findings show that appointing a deputy can free up the equivalent of one day a month.
CIO time needs to be spent in promoting a digital rather than corporate culture. They can do this by maintaining regular contact between IT and business leaders and by increasing the level of business knowledge within IT. They're also increasing their spend on tools to empower individuals, with the biggest investment being in business intelligence and analytics.
You can view the complete findings in infographic form below.
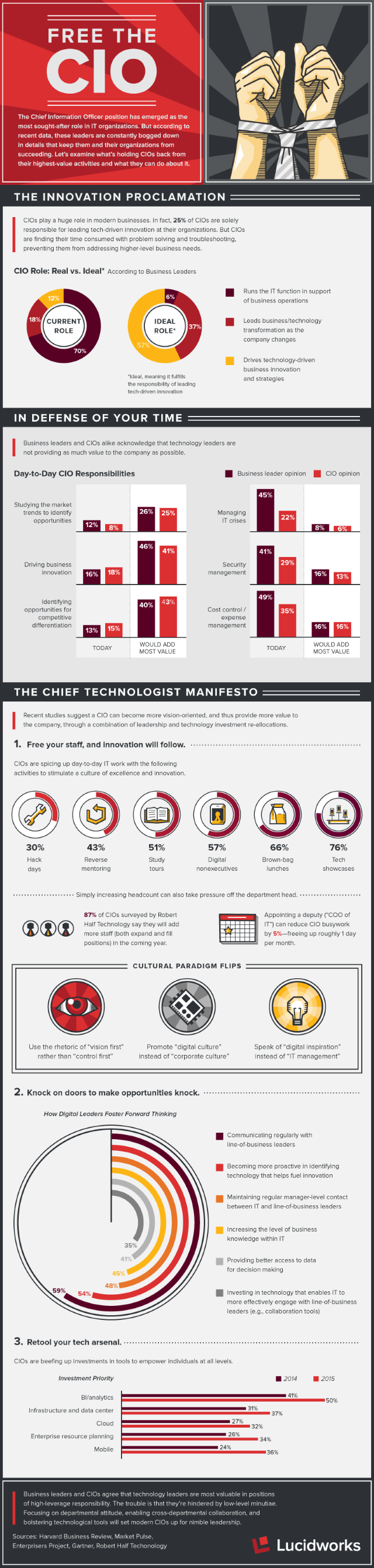
Image credit: olly/Shutterstock
-

Antivirus tools miss almost 70 percent of malware within the first hour
Publié: février 12, 2015, 4:36pm CET par Ian Barker

Threat protection company Damballa has released its latest State of Infections report for the fourth quarter of 2014 which highlights the limitations of a prevention-focused approach to security.
The report finds that within the first hour of submission, AV products missed nearly 70 percent of malware. Further, when rescanned to identify malware signatures, only 66 percent were identified after 24 hours, and after seven days the total was 72 percent. It took more than six months for AV products to create signatures for 100 percent of new malicious files.
This has an impact on containment and raises the risk that at any time there may be live infections on a network. The report also highlights the importance of automating manual processes and decreasing the noise from false positives to make the most of skilled security manpower, rather than trawling through uncorroborated alerts to find the true infections.
In order to reduce manual efforts, Damballa advises that security teams must have automatic detection of actual infections able to reach a statistical threshold of confidence in a true positive infection. They also need integration between detection and response systems, and policies that enable automated response based on a degree of confidence.
"What's clear from these figures is that we have to turn the table on infection 'dwell' time. In much that same way that a flu vaccine hinges on making 'best-guess' decisions about the most prevalent virus strains -- AV is only effective for some of the people some of the time. Viruses morph and mutate and new ones can appear in the time it takes to address the most commonly found malware", says Brian Foster CTO of Damballa. "Dependence on prevention tools simply isn't enough in this new age of advanced malware infections; attackers can morph malware code on a whim, yet organizations have a finite number of staff to deal with the barrage of noise generated from security alerts. We urge taking a fresh 'breach-readiness' approach, which reduces dependence on people and legacy prevention tools".
The full report is available to download from the Damballa website.
Image Credit: Sergey Nivens / Shutterstock
-

Web app self-service reduces support queries and cuts costs
Publié: février 12, 2015, 3:47pm CET par Ian Barker

Last year we looked at how supplier of point-and-click answer technology AnswerDash was integrating its software with the Zendesk help centre system.
Now the company has released performance stats from its customers which show that self-service technology can cut support costs by an average of $20k a year.
The technology can also boost conversion rates by up to 85 percent and reduce support ticket volume by 60 percent.
By providing a first line of defense for handling customer questions Answerdash can reduce the volume of incoming support inquiries requiring human assistance and allow customers to get answers at their point-of-action where they are most likely to complete a purchase.
"We calculated AnswerDash's impact on support ticket reduction across our early customer base and examined the average support cost savings, revealing a substantial $20K average cost reduction across all verticals. AnswerDash provides the biggest impact for SaaS customers, with a $32K average cost reduction", says Jake Wobbrock, founder and CEO of AnswerDash. "By answering common and frequently asked questions, AnswerDash reduces support ticket volume by up to 60 percent, allowing businesses to grow without a huge support investment".
A separate analysis across eight customers revealed that companies which had implemented AnswerDash witnessed double-digit increases in sales conversion rates, averaging around 30 percent increases.
For example PetHub experienced a 24.9 percent increase in sales conversion rate and also a 67 percent reduction in customer support tickets. Similarly after implementing AnswerDash, TireBuyer saw an 13 percent increase in revenue per visitor by deploying AnswerDash in the checkout process.
You can find out more about how AnswerDash works and see interactive demos on the company's website.
Photo Credit: sheelamohanachandran2010/Shutterstock
-

Datameer brings big data analytics to the cloud
Publié: février 11, 2015, 3:08pm CET par Ian Barker

As more businesses want to take advantage of the insights that analysis of big data can offer there's greater demand for the cloud to allow direct access to stored data.
San Francisco-based big data platform specialist Datameer was the first big data analytics platform purpose built for Hadoop. Now the company is first to market with a big data analytics platform designed specifically for the cloud.
Datameer Professional offers an affordable and agile option for business executives who want to start integrating, preparing, analyzing and visualizing all of their data right away. Using Hadoop-as-a-Service (HaaS) it allows businesses to start taking advantage of big data without the need to invest time or effort in setting up and maintaining a Hadoop infrastructure.
"Datameer Professional is the accelerant the market has needed for individual departments within an organization to stop talking about the benefits of big data and Hadoop and start realizing them immediately", says Stefan Groschupf, CEO of Datameer. "Now companies that want to gain a competitive advantage with big data analytics right away can simply purchase Datameer Professional running on a HaaS offering and discover actionable insights in hours or days, not months. We believe that this will catapult Hadoop adoption as a whole as businesses discover shared success between departments and discover new use cases, encouraging the entire company to become data-driven".
The company has established partnerships with cloud providers Altiscale and Bigstsep. This will allow it to make its latest offering available to companies with limited IT or Hadoop expert resources but who want direct and immediate access to their data, regardless of its size.
For more information and to request a demo you can visit the Datameer website.
Photo Credit: T.L. Furrer / Shutterstock
-

DH2i launches first container management solution for Windows Server
Publié: février 11, 2015, 1:23pm CET par Ian Barker

Containerization of applications has done much to enhance the flexibility and portability of software as it makes it easy to move between in-house, private cloud and public cloud.
Until now, however, it's been restricted to Linux systems, using solutions like Docker, or Oracle servers running Multitenant. Now though containerization is coming to Windows servers as DH2i launches its DxEnterprise container management solution for Windows Server.
By decoupling the apps and all associated data from the host OS and the underlying physical infrastructure, DxEnterprise delivers fast and transparent application portability. This offers enterprises cloud-like agility and ensures high availability. It also makes it easier to provision, test, deploy, and manage new applications.
Each container -- called a Vhost -- consists of a logical computer name, an associated IP address (or addresses), Vhost management metadata, and portable native NTFS volumes. The metadata within the Vhost coordinates container workload management and directs the managed application to launch and run locally. Multiple DxEnterprise containers can share a single Windows Server OS instance and are then stacked on virtual or physical servers.
Management features include protection from hardware, OS or application faults with "self healing" and quality of service automation. Resource management allows workloads to be adjusted to meet the needs of the highest priority tasks.
"With DxEnterprise, customers can containerize and make any new or existing Windows Server app service, file share, or Microsoft SQL Server instance portable and highly available, with the native dynamic NTFS volumes following the workload -- all with just a few clicks", says OJ Ngo, CTO and Co-Founder of DH2i. "The results include a reduction in software and infrastructure costs of 30 percent - 60 percent and the elimination of significant lifecycle management expense -- and headache. It also eliminates OS sprawl and reduces OS cost by eight-15 times, and provides near zero application downtime as well as protection from OS, application and infrastructure faults".
DxEnterprise is available now and there's a technical white paper with more details of how it works on the DH2i website.
Image Credit: Oleksiy Mark / Shutterstock
-

Intelligent and connected devices are driving a 'third industrial revolution'
Publié: février 10, 2015, 3:30pm CET par Ian Barker

Software-driven intelligent devices and the Internet of Things are changing the way companies deliver their products and services.
This is among the findings of a new report from Flexera Software and IDC which points towards a 'third industrial revolution' transforming the global economy.
The report based on responses from software vendors, intelligent device manufacturers and end-user enterprises, finds that the number of manufacturers making Internet of Things devices is set to more than double in the next two years.
There's also strong growth in intelligent devices, with 50 percent of respondents saying they currently develop intelligent devices and another 21 percent planning on making their devices intelligent over the next two years.
79 percent of respondents say they are, or plan on, delivering remote monitoring and maintenance as part of their product/service mix. 66 percent will add business intelligence capabilities and 37 percent will improve their supply chains with new services, such as automatic replenishment -- for example empty water coolers being able to order their own refills.
Software licensing and entitlement management is seen as key to monetizing the Internet of Things, allowing companies to develop new offerings that bundle device, services and consulting. This will see the proportion of revenues gained from hardware decline over the next two years and revenue from services grow to take its place.
"The report supports a long-proven truism in the high-tech arena -- that innovation, alone, isn't sufficient to transform an industry. There must also be a practical means to monetize new technology in order to profit from it," says Vikram Koka, Vice President of Intelligent Devices and Internet of Things at Flexera Software. "Software- and Internet-enabled products are spawning a vast new category of products and services previously unimaginable. The data from today's report shows that in conjunction with their new products and services, device makers are also beginning to transform their business models via flexible licensing and entitlement management -- enabling them to turn their innovations into revenue".
Image Credit: alexmillos / Shutterstock
-

New and nastier Android ransomware uses unique keys to lock data
Publié: février 10, 2015, 1:34pm CET par Ian Barker

The Simplocker ransomware targeting Android systems first appeared in mid 2014. Prior to Simplocker most ransomware only claimed to encrypt files but didn't actually do so.
Fortunately files locked by the malware were fairly easy to decrypt, but now researchers at antivirus company Avast have uncovered a new version of Simplocker with an even nastier trick.
The latest version uses unique keys for each device it infects making it much harder to decrypt and is already believed to have infected around 5,000 devices.
Avast mobile malware analyst, Nikolaos Chrysaidos writing on the company's blog says, "To use an analogy, the original variant of Simplocker used a 'master key' to lock devices, which made it possible for us to provide a 'copy of the master key' to unlock already infected devices. The new variant however, locks each device with a 'different key' which makes it impossible to provide a solution that can unlock each infected device, because that would require us to'‘make copies' of all the 'different keys'".
The new Simplocker masquerades as a Flash Player update to trick users into installing it. Android blocks installs from unofficial markets by default, so users should be safe unless they've changed their settings.
If it is installed the app is granted administrator rights and uses social engineering to deceive the user into paying a ransom to unlock the device and decrypt the files. The app claims to be the FBI, warning the user that they have found suspicious files, violating copyright laws and demanding the user pay a $200 fine to decrypt their files.
There's more information including a look at how the Simplocker malware operates on the Avast blog.
Image Credit: Carlos Amarillo / Shutterstock
-

Safer Internet Day tips for parents
Publié: février 10, 2015, 11:28am CET par Ian Barker

It probably hasn't escaped your notice that today (10 February) is Safer Internet Day. This is intended to promote safer and more responsible use of online technology and mobile phones, especially amongst children and young people.
Online advice site Knowthenet.org.uk -- operated by the Nominet domain registry -- has published some new research looking at the attitudes of parents to their children's use of social media and finds that whilst it has a generally good effect there's still a need for caution.
Parents are mostly positive about social media's effects, with 27 percent saying it has helped their children make new friends, 23 percent that it helped them feel more included and 18 percent that it helped them feel more confident.
There are some worries though with 24 percent saying that their child was unhappier since using social media and 31 percent that their child had been upset by something they'd seen on a site. 42 percent of parents say they don't set any time limit on their child's internet use.
In response to the findings Knowthenet has put together some handy tips for parents. These include:
- Being open with your child about social media sites and listening to any problems they may be having.
- Setting time limits on internet usage and if possible keeping smartphones and laptops in communal spaces rather than allowing them in bedrooms.
- Checking the privacy settings of social networking sites to ensure children don’t over share information or get exposed to anything they shouldn't be.
- Educating yourself about how sites work in case of a problem and remembering to check the policies of social networking sites: both Facebook and Twitter have age limits of 13 for example.
- Finally, set a good example yourself. If parents are constantly checking and updating social media sites it sends a message to children that they should be doing the same.
For more information on keeping children safe online and understanding internet safety in general you can visit the Knowthenet website.
Image Credit: Pressmaster / Shutterstock
-

How secure is Android? And should we be worried? [Q&A]
Publié: février 9, 2015, 11:10am CET par Ian Barker

In the past malware developers and hackers have tended to concentrate on Windows. But as mobile has taken off and there's been a shift in the type of systems people use they've diversified their efforts into other systems.
In particular Android, as the most popular mobile OS, has become a prime target. We spoke to Ren Huan, chief architect at Android security and performance specialist 360 Security to get his view of the mobile security landscape.
BN: How does the Android threat landscape differ from other operating systems? Are premium SMS threats still a major problem for example?
RH: There's no absolutely safe operating system on the market. Android in particular has from day one been the go-to platform for a couple of reasons. Android makes up nearly a third of the global smartphone market. At the same time, Android's open platform supports many different variants of the Android ROM running on different types of devices, and hundreds of different app stores around the world. It's no surprise under these conditions that hackers target Android -- the low hanging fruit. With a far higher volume of threats to account for, compared to other operating systems, Android also tends to be home to the more creative types of hacks, whether it’s an SMS Trojan, or even an adware scheme.
BN: Does the fact that Android is often customized by hardware OEMs make it more difficult to keep it secure?
RH: There are pros and cons to Android's open platform. The open platform has encouraged Android to flourish, it provides developers and OEMs the convenience of adopting a single operating system, and users with choices between phones. However it's far more difficult to provide robust security services in an incredibly fragmented market when it's not only Google's responsibility to provide support to users. For instance, Google will push a vulnerability patch through a new OS version but historically the OEMs are slow to react and deliver the patch to the end user. In a real world analogy, this explains why Jelly Bean has been delivered to under 0.1 percent of Android users.
BN: People tend to point to the operating system when breaches occur, but how much of the security risk comes from poorly designed apps?
RH: You're definitely onto something. The Google team is known to be on top of Android security vulnerabilities. For example, Google rolled out Security Enhanced Linux (SELinux) with Jelly Bean. Google also updated SMS broadcast requirements, which secures SMS messages that are delivered to mobile apps. Of course this is just the tip of the iceberg. Google offers encryption protocols including MD5, AES, and HTTPS, along with regular security patches. The consequence of providing an open platform is a loss of control over its own platform and security standards. If security isn't a prerogative for an app developer they may decide to store users' information in plain text format for the sake of developing a fast, minimum, viable product. Of course this opens the app up to vulnerabilities and hackers wouldn't need to sweat to steal any stored information about the app's users.
BN: Are we at the stage where it's essential for Android users to have some sort of anti-malware app installed on their device?
RH: Many Android users end up installing malware because they're downloading untrustworthy apps or apps from third-party Android markets with questionable policies. Or users may unwittingly download malicious apps from forums and even other devices. Surprisingly, not many Android users are cognizant of the threats that lurk on Android, so we'd argue that it's essential for Android users to have one additional anti-malware app installed on their device. Fortunately, these days, security apps are simple to use and free-to-download. Think of an Android security app like the antivirus software you’ve installed onto your PC. Because Android security apps have varying degrees of quality, you might have more than one antivirus product installed in the case that one product failed to catch a virus. You can check AV-TEST's monthly list of top security apps, which includes 360 Security's antivirus engine by Qihoo 360.
BN: In response to Google's recent pulling of support for WebView you recommended users switch to using Chrome. Is the Chrome browser significantly more secure and why?
RH: Ideally you'd want to be using Chrome or Firefox if you want to avoid these WebView vulnerabilities. The reason isn't because of how secure Chrome is. Google explained that it's dealing with five million lines of outdated code, not to mention thousands of commits developers are submitting regularly, making it more difficult to deliver patches to WebView, particularly when WebView until recently came packaged in firmware. That means to get the latest WebView version delivered to end-users Google had to first send it to OEMs and carriers to distribute the patch. Once that happens it's out of Google's hands and it's a waiting game before the OEM and carrier gets around to delivering the patch. So to cut to the chase Google decided to deliver WebView patches directly and instantly to users by way of the Google Play store. Because Chrome and Firefox can be downloaded from the Play store, to receive the latest WebView patch all you need to do is update your browser version when a new one is available.
BN: Is the user always the weakest link in keeping any system secure?
RH: I'm sure, based on my previous response, that you'll get the inkling that Android users aren't taking enough precautionary measures to safeguard their mobile security. Oftentimes it's what apps you download, sites you browse, or links you click that causes you to have that nasty bug hiding away in your phone. Of course, not everything is in the users' control. For instance, there are plenty of situations where a trusted developer's app is hacked and user data is stolen. But more often it's the users’ actions that cause their device to contract malware. Luckily, there are measures that users can take to safeguard themselves to minimize the chance that this happens.
BN: Finally, what everyday steps should people take to protect their Android devices?
RH: We'd recommend that you update your apps and operating system regularly to ensure that you're receiving the latest patches. This will minimize the chances that a hacker could take advantage of your device. At the same time, security apps are a great aid in not only detecting any new threats, but also removing them. And of course, users should pay more attentions to how they're engaging with the content on their device. That means avoiding suspicious links, apps, mobile sites, and unfamiliar Wi-Fi networks.
Image Credit: Palto / Shutterstock
-

The top five mobile marketing mistakes
Publié: février 5, 2015, 4:15pm CET par Ian Barker

Consumers are increasingly using mobile devices to access various aspects of their digital lives including online shopping.
Yet in many cases businesses are failing to take advantage of the extra marketing opportunities that mobile offers them.
Smart online forms company Formstack has put together an infographic that uncovers the top five mistakes businesses make in their mobile marketing.
The first mistake is simply not bothering to build an app or a mobile optimized site. Yet 46 percent of consumers say if they're using a company's mobile app they're unlikely to shop around for other options. The second error is not optimizing for devices with different screen sizes like tablets.
Not having a strong call to action, such as a one-click button to download a coupon, is another error, as is not offering the ability to auto-fill forms using links to social media accounts. Companies also suffer from overloading their mobile sites with content, 57 percent of users say they won’t recommend a badly-designed mobile site to their friends.
You can view the five main mistakes in infographic form below.

Image Credit: Bevan Goldswain / Shutterstock
-

Unplanned app downtime costs companies billions
Publié: février 5, 2015, 3:33pm CET par Ian Barker

System downtime is always frustrating, but according to a new survey from IDC, sponsored by performance management specialist AppDynamics, it has major cost implications too.
According to the survey respondents an infrastructure failure can cost $100,000 per hour. A critical application failure costs between $500,000 and $1 million per hour.
A little more than a third of those outages last from one to 12 hours; 17 percent of infrastructure failures and 13 percent of application failures last more than a full day. This means that downtime could be costing the Fortune 1000 companies between $1.25 billion and $2.5 billion every year.
The quest for more reliability is why many companies are turning to DevOps practices. 40 percent of Fortune 1000 companies already use DevOps and the survey shows that a further 40 percent are actively investigating its adoption.
They expect it to deliver improvements in customer experience, productivity, costs and profitability, as well as speed of application delivery. These benefits will be delivered through increased capabilities in automation, continuous delivery, continuous integration, automated testing, and application monitoring.
You can read more about the report's findings and download a full copy from the AppDynamics blog and there's an infographic summary of the findings below.
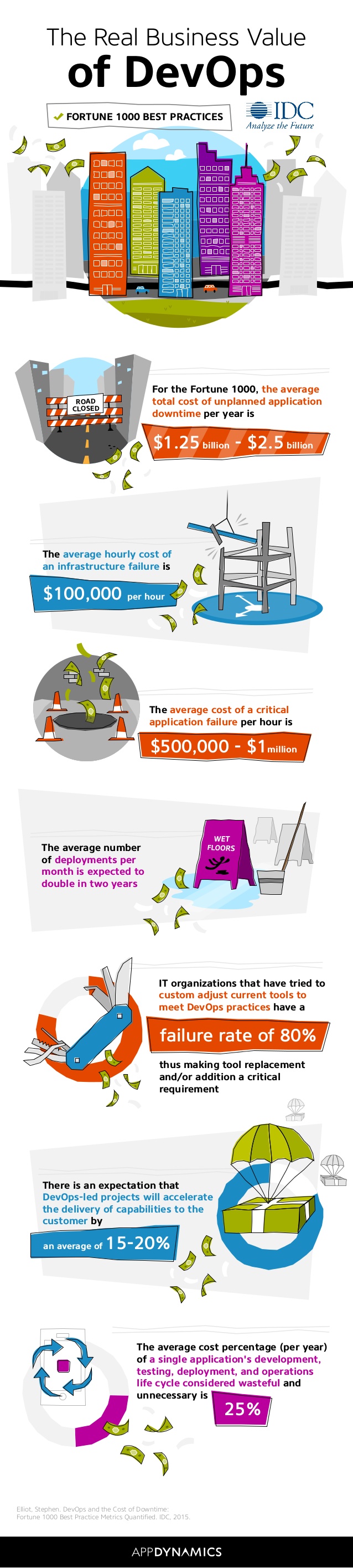
Image Credit: amadorgs / Shutterstock
-

Lack of trust holds back app downloads
Publié: février 4, 2015, 4:15pm CET par Ian Barker

Consumers are increasingly wary of downloading apps according to a new report by mobile commerce community MEF and antivirus company AVG.
The study is based on data from 15,000 mobile media users in 15 countries across five continents. It explores the key areas of trust, privacy, transparency and security to identify their impact on mobile consumers, from purchasing a new device to downloading apps or paying for goods and services.
Among the findings are that almost half of all consumers surveyed (49 percent) say a lack of trust limits the amount of apps they download, compared to 37 percent last year. 72 percent of mobile consumers are not happy sharing personal data such as their location or contact details when using an app and 34 percent say a lack of trust prevents them from buying more goods and services using their mobile device.
Of the markets studied the US experienced the largest increase in a lack of trust, at 35 percent (up nine percent year-on-year). Many consumers feel that app stores and device manufacturers should be taking greater responsibility for protecting their personal information. 30 percent of respondents said this would give them greater trust in the platforms and 63 percent said that they considered transparency important or extremely important (compared to 49 percent last year).
Interestingly although the results show a high awareness of malware, caution surrounding it has decreased. Only 48 percent of respondents said the threat of malware would make them think twice when downloading apps compared with 74 percent last year.
"Building consumer trust is an integrated process," says Judith Bitterli, Chief Marketing Officer at AVG Technologies. "While the mobile industry across the board must step up and take responsibility for increasing transparency across user privacy policies, it is equally important that consumers take their own steps to educate and protect themselves in order to better protect their rights and understand their choices online. This research shows that while consumers are taking certain proactive steps towards greater protection there is still some way to go in order to ensure their privacy and security are not at risk".
More information about the report is available from the MEF website.
Photo Credit: phloxii/Shutterstock
-

New tool to identify website vulnerabilities
Publié: février 4, 2015, 2:20pm CET par Ian Barker

Many of the security breaches that have made the headlines over the past year have been due to some form of web vulnerability. It's no surprise that the web has become the main route for cyber attacks as highlighted by things like Shellshock.
But identifying these flaws manually can be a mammoth task. Which is why cloud security provider Qualys is announcing the latest version of its Web Application Scanning (WAS) tool.
Qualys Web Application Scanning is a cloud service that provides automated crawling and testing of custom web applications to identify vulnerabilities including cross-site scripting (XSS) and SQL injection.
It's an automated service which makes it possible to carry out regular testing that produces consistent results, reduces false positives, and easily scales to secure large numbers of web sites. Qualys WAS also proactively scans websites for malware infections, sending alerts to website owners to help prevent search engine black listing and consequent damage to brand reputation.
"In today's increasingly digital world, web applications are the new battleground for attackers looking to gain access to corporate or personal data," says Philippe Courtot, Chairman and CEO for Qualys, Inc. "Since its inception, we designed our web application scanning solution with scale and accuracy in mind as we anticipated this explosive growth of web apps. Now with the new progressive scanning capabilities, we have reached a new milestone, which coupled with our recently introduced Web Application Firewall, allows companies of all sizes to ensure the security of their web apps".
Key features of the new release include progressive crawling where each scan builds on the information obtained in previous scans, prioritizing newly identified pages over previously tested ones. Similarly, progressive testing enhances the flexibility of scanning by automatically starting, stopping and resuming scans across networks without manual intervention. There are also new customized reporting templates to simplify the time and effort needed.
For more information and to sign up for a free trial you can visit the Qualys website.
Photo Credit: Yuriy Boyko/Shutterstock
-

Samsung launches advanced enterprise mobility solution
Publié: février 4, 2015, 12:07pm CET par Ian Barker

The increasing use of mobile devices for business has highlighted the need for solutions to manage devices and keep them secure.
Samsung has recognized the growing importance of this and has announced the release of the Good app container and management system on the Samsung KNOX enterprise security platform for Android.
Good's container platform and app ecosystem are integrated directly into the KNOX security stack. This joint solution creates a secure solution for enterprises and government agencies looking to accelerate their Android deployment to drive secure mobile productivity.
"Together, Samsung and Good are addressing the growing importance of mobility management for enterprises by delivering an unmatched secure mobile productivity solution for Android that will relieve organizations of past concerns with Android adoption," says Injong Rhee, executive vice president of enterprise business, IT and mobile business at Samsung Electronics. "The combination of Samsung and Good represents the best solution for secure enterprise Android productivity -- no matter whether corporate-liable, COPE (Corporate Owned, Personally Enabled) or BYOD(Bring Your Own Device) device ownership models are being used".
The product creates a Good-secured domain within the KNOX Android system where any secured apps sit. It prevents the rooting of corporate Android devices and stops rooted BYOD devices from accessing corporate resources. It also protects devices against Android malware that attempts to modify the kernel or system and secures corporate apps and data whether they’re at rest, in motion, in memory, or between apps.
"The large companies in the world trust Good Technology as the secure mobility leader, including all of the Fortune 100 commercial banks and other industry leading companies in over 190 countries," says Christy Wyatt, chairman and CEO of Good Technology. "By partnering with Samsung to integrate our container and secure app ecosystem with the KNOX platform, we are delivering a comprehensive, layered solution to secure Samsung Android devices in the enterprise".
You can find more information about Good for Samsung KNOX and see a video of how it works on the Good website.
Image Credit: Moon Light PhotoStudio / Shutterstock
-

Clustrix launches updated eCommerce database
Publié: février 3, 2015, 3:38pm CET par Ian Barker

Availability and performance are key factors to success in the eCommerce field but as sites grow, the software used to support them needs to be able to keep pace.
San Francisco-based database company Clustrix is rolling out the latest version of its ClustrixDB product to help businesses cope with expansion and reduce the risk of slowdowns and outages.
ClustrixDB 6.0 is compatible with MySQL and includes performance enhancements for Magento Community and Enterprise Editions. It can support hundreds of thousands of customers per hour and an unprecedented 2,000+ active sessions. In addition, its built-in fault tolerance and high availability capabilities ensure zero downtime and continuous processing of eCommerce transactions even during hardware failures, both on premise and in the cloud.
It allows eCommerce sites to adjust their capacity easily to keep pace with variable volumes of customers, products and orders. Product highlights in this release include up to five times more read and write performance than standard Magento with MySQL, automatic recovery from hardware failures, prioritizing eCommerce transactions over other tasks, and data made available directly at each server to reduce load times.
"Our largest customers manage upwards of 170 million products that require constant real-time inventory and pricing updates, and eCommerce retailers of all sizes are already benefiting from the performance and availability that ClustrixDB's scale-out architecture provides," says Mike Azevedo, Clustrix CEO. "Version 6.0 builds on these features, offering a scalable solution that ensures zero downtime and provides live reporting of business performance metrics to increase sales opportunities and capture more revenue".
For more details of Clustrix's eCommerce products you can visit the company's website.
Photo Credit: Nonnakrit/Shutterstock
-

UK companies pay more attention to cyber security
Publié: février 3, 2015, 12:47pm CET par Ian Barker

We reported a few weeks ago on research showing that cloud security was becoming a concern outside the IT department and having an impact on the boardroom.
Now a new study in the UK by Tom Neaves, Managing Consultant at security specialist Trustwave backs this up, showing that cyber security is increasingly becoming a corporate issue.
Looking at the annual reports of UK companies over recent years, the findings show that in 2012, just 49 percent of FTSE 100 companies made a reference to cyber security. In 2013, the number increased to 60 percent. And in 2014, more than three-quarters of companies (76 percent) referenced it.
There are also changes across industry sectors. Neaves says, "In 2012 and 2013, the utilities industry remained stagnant at 60 percent of companies recognizing cyber security. In 2014, that number rose to 80 percent. On the other side of the spectrum, the oil-and-gas industry saw no change in 2014 at 85 percent. But that’s still a vast majority. I also saw a significant jump in the financial and health care industries, both showing an increase of 25 percent".
As to why companies are taking security more seriously, it could be due to a number of things, the number of data breaches that made news headlines in 2013, increases in the number of internet-connected control systems, as well as involvement at a Government level to help improve cyber security across all businesses such as the UK government's Cyber Essentials Scheme.
Neaves concludes that increased recognition of security at board level is a step in the right direction, but notes, "...a security program is only as good as the people who manage it. If businesses lack the manpower and skillsets to ensure their controls are installed, updated and working properly, they should augment their in-house staff and partner with a third-party team of experts whose sole responsibility is to protect their information".
You can read more about the findings on Trustwave's blog.
Image Credit: Manczurov / Shutterstock
-

IBM announces new cloud-based identity protection
Publié: février 2, 2015, 4:01pm CET par Ian Barker

Many of the things we do online require an ID and password, but typically whilst this makes things easier for the site it doesn't always do a lot to protect the user, who may be revealing more information than they need.
For example you may have to reveal your full date of birth and address to a video streaming service in order to verify your age and region, running a risk that the information may fall into the wrong hands.
Now researchers at IBM have announced plans for a new cloud-based technology to help consumers guard their personal data.
The technology, called Identity Mixer, uses a cryptographic algorithm to encrypt the identity attributes of a user, such as their age, nationality, address and credit card number in a way that allows the user to reveal only selected pieces to third parties.
Identity Mixer can be used within a digital wallet, which contains credentials certified by a trusted third party, such as a government-issued electronic identity card. It's important to note that the issuer of the credentials has no knowledge of how and when they are being used.
"Identity Mixer enables users to choose precisely which data to share, and with whom," says Christina Peters, IBM's Chief Privacy Officer. "Now web service providers can improve their risk profile and enhance trust with customers, and it's all in the cloud, making it easy for developers to program".
Taking the example of the video site above, Identity Mixer would be able to confirm a user's age and region without revealing any more. This ensures that even if the website is hacked personal data remains safe.
Similarly, if you wanted to make a payment Identity Mixer would be able to confirm that a credit card is valid and that it can accept payment, without actually revealing the full card number or expiration date.
Identity Mixer is now being made available to developers as an easy-to-use web service in IBM Bluemix, IBM's new platform-as-a-service (PaaS) cloud. Beginning this spring, Bluemix subscribers will be able to experiment with Identity Mixer within their own applications and web services. Using simple pull-down menus, developers can choose the types of data that they wish to secure and Bluemix will provide the code, which can then be embedded.
"Identity Mixer incorporates more than a decade of research to bring the concept of minimal disclosure of identity-related data to reality, and now it is ready to use for both computers and mobile device transactions," says Dr. Jan Camenisch, cryptographer and co-inventor of Identity Mixer at IBM Research.
You can find out more about Identity Mixer and how it works on the IBM website.
Image Credit: Nata-Lia/ Shutterstock
-

New business collaboration platform secures data with personalized cryptography
Publié: janvier 29, 2015, 5:13pm CET par Ian Barker

Data security is a big concern for both individuals and businesses. This doesn't only apply to the public face of a business, but to exchange of information and collaboration between employees too.
Canadian company Witkit is launching a new platform that allows the creation of teams and groups within industries, companies, and departments to tackle projects and solve problems collectively, with the safety and security of knowing their data cannot be breached.
"Our intention with Witkit is to make the first fully encrypted global collaboration platform so that companies and individuals can more easily reap the benefits that socialized teamwork brings to their business challenges," says Sean Merat, president and CEO of Witkit.
Witkit is a modular platform that works by allowing users to create tailored workspaces. These center on 'Kits' -- virtual groups based on specific topics or projects. Within each Kit, members can upload and access shared files, initiate and contribute to group discussions, post and respond to team tasks, and use a single synchronized calendar.
Additional features include secure storage using proprietary encryption, along with messenger and video conferencing services.
Kits can be made private or public and users are able to participate in multiple Kits at the same time. A single dashboard and news feed collates all of a user's memberships in one place.
"The vast majority of breaches today happen on a centralized system which contains sensitive user data," says Merat. "WitCrypt technology ensures that the encryption and decryption of user data is only done on user devices locally. All data that is sent to the Witkit servers is fully encrypted and can only be decrypted by the user's WitCrypt passphrase. We can confidently say that we've minimized most, if not all the risk, to user data being hacked. That is to say that in the unlikely event that the Witkit servers are compromised, there will be no decrypted data to be found".
For more information visit the Witkit website, the first 50,000 people who sign up for the platform will get 50GB of encrypted storage and all available applications for free.
Image Credit: Tischenko Irina / Shutterstock
-

A single DDoS attack could cost over $400,000
Publié: janvier 29, 2015, 3:00pm CET par Ian Barker

One of the major worries for online businesses is being subject to a DDoS attack. As well as damaging reputations these can have a serious effect on finances too.
According to a new study by Kaspersky Lab the average cost of a DDoS attack ranges between $52,000 and $444,000 dollars depending on the size of the business.
The cost reflects a number of different issues. According to the study, 61 percent of DDoS victims temporarily lost access to critical business information, 38 percent of companies were unable to carry out their core business, and 33 percent reported the loss of business opportunities and contracts. In addition, in 29 percent of DDoS incidents, a successful attack had a negative impact on the company’s credit rating while in 26 percent of cases it prompted an increase in insurance premiums.
The figures also factor in the costs of dealing with an attack. These include 65 percent of companies having consulted with IT security specialists and 49 percent paying to modify their IT infrastructure. Also 46 percent of victims had to turn to their lawyers and 41 percent turned to risk managers.
Attacks can have an ongoing effect too depending on how an organization deals with them. 72 percent of victims disclosed information about a DDoS attack on their resources. Specifically, 43 percent of respondents told their customers about an incident, 36 percent reported to representatives of a regulatory authority and 26 percent spoke to the media. 38 percent of companies say they suffered reputational loss as a result of an attack.
"A successful DDoS attack can damage business-critical services, leading to serious consequences for the company," says Eugene Vigovsky, Head of Kaspersky DDoS Protection at Kaspersky Lab. "For example, the recent attacks on Scandinavian banks (in particular, on the Finnish OP Pohjola Group) caused a few days of disruption to online services and also interrupted the processing of bank card transactions, a frequent problem in cases like this. That's why companies today must consider DDoS protection as an integral part of their overall IT security policy. It's just as important as protecting against malware, targeted attacks, data leak and the like".
You can see a summary of the study's findings in infographic form below or the full report is available from the Kaspersky website.

Photo Credit: Fabio Berti/Shutterstock
-

It's Data Privacy Day and Facebook knows you're reading this
Publié: janvier 28, 2015, 5:32pm CET par Ian Barker

A new global study conducted by Microsoft across 12,000 people shows that most internet users still don't believe they're aware of all the data that's being collected about them.
For example, Facebook, Twitter and Google+ know you've read this page, as they track your visits to any website with a 'Like', 'Tweet' or '+1' button, whether you click that button or not. Information gathered can include anything from your IP address and general geography, to insights into your age, gender, income, hobbies, health status and financial situation, by way of your browsing and purchase history.
All of these bits of data may not be much use on their own, but according to the Internet Society's Privacy and Identity Director, Robin Wilton, companies are increasingly putting them together to create a bigger picture. They can then use this to predict your behavior, including your habits, preferences, values, aspirations and intentions.
This can have significant implications for your finances. Wilton says, "According to one study, you may pay more than others when shopping online based on your web browsing history or the kind of smartphone you own. Some consumers have seen their credit limits reduced by their credit card companies because they shopped at stores frequented by cardholders who don’t have good repayment histories. From there, it’s possible insurance companies might eventually string your data together to determine if you’re insurable (and what kind of premium you should be charged based on your perceived risk) and credit card companies could use it to determine your creditworthiness (and charge you higher interest)".
What can you do about all this? Wilton suggests fragmenting your online identity. "Strategically use different email addresses, browsers, credit cards, and maybe even devices, for different web activities (like personal, work and online shopping) to make it more difficult to collect one cohesive data set about you".
You can also adjust your browsing habits by using Do Not Track or Incognito settings to prevent cookies from being left on your system. That doesn't prevent your searches from being tracked by the provider of course. To stop that you could switch to a non-tracking search engine like DuckDuckGo, or Boston-based privacy company Abine is about to launch a private search service for Google -- with Yahoo and Bing to follow soon -- integrated into its Blur product that protects passwords and payments.
"By the end of 2015, anybody who wants to use the Internet safely should be using Private Search, alongside a password manager and a secure payments service," says Rob Shavell, CEO of Abine. "Blur users can use the best search engine the way it used to be -- simple and not nosy".
Using the internet is a balance between convenience and privacy. It may be inconvenient to use additional privacy tools, but do remember that someone somewhere knows you're reading this.
Image Credit: Stuart Miles / Shutterstock
-

Securing business applications in real-time
Publié: janvier 28, 2015, 4:09pm CET par Ian Barker

As demand to access company information on the move and from mobile devices increases it places extra strain on security resources.
Existing web applications firewalls (WAFs) monitor traffic but don't have an understanding of the logic of data flows and the behavior of applications. This can make it hard for them to distinguish between legitimate traffic and attacks on apps such as SQL injection and cross-site scripting.
Israel-based security company Checkmarx is launching a run-time application self-protection (RASP) tool called CxRASP which will monitor an app’s bidirectional data flow, enabling the detection of and defense against real-time attacks.
Checkmarx's technology 'listens' at each interaction junction of the app, covering access points between the application and the user, the database, the network, and the file system. With complete visibility into the app's input and output, CxRASP tailors the protection mechanism to the specific flow within the application to achieve high detection accuracy in real-time. Suspicious activity is flagged when it enters the app, and then verified to see if it is actually malicious at the output to minimize false positives and false negatives. If an attack is identified, the organization is alerted and instructions are sent on how to fix the vulnerability.
"The fast increasing number of applications and the resulting vast amounts of insecure code written and released into production means that we need a more intelligent way to ensure software security," says Emmanuel Benzaquen, CEO of Checkmarx. "CxRASP is the ultimate way to protect applications as it lets applications do the work of protecting themselves so that security vulnerabilities are revealed and blocked in real-time".
The product can be integrated with static application security testing tools from Checkmarx and elsewhere to ensure application protection throughout the development process.
For more information on Checkmarx products you can visit the company's website.
Imaged Credit: soliman design / Shutterstock
-

VoltDB looks to simplify database app development
Publié: janvier 28, 2015, 3:33pm CET par Ian Barker

As the need for real-time data increases thanks to the Internet of Things and growing demand for mobile services, organizations are looking for new ways to capture and process information.
In response to this demand database company VoltDB is launching version 5.0 of its in-memory database application offering increased support for the Hadoop ecosystem, expanded SQL support and a new Management Center.
"Developers are in need of better tools with which to develop fast data streaming applications with real-time analytics and decision making across industries," says Bruce Reading, President and CEO of VoltDB. "As the popularity and adoption for Hadoop continues to surge, there is an increased need for integration between fast and big data so developers can focus on the applications and not the infrastructure. Version 5.0 meets that demand".
Along with improved Hadoop support key features of the latest release include new export connectors for HDFS, HTTP, Kafka and RabbitMQ as well as Avro format. There’s also a new Kafka data Import option as well as bulk data import from, JDBC Loader, Hadoop OutputFormat and Vertica Udx. The new VoltDB Management Center (VMC) provides browser-based, one-stop database monitoring and configuration management.
As an example of how effective the product is, VoltDB Developer John Hugg has used version 5.0 to develop a real-time analytics app that counts the number of unique mobile devices/types of devices accessing an application. He was able to do that using only 30 lines of code, while the traditional Lambda architecture would have needed thousands of lines.
The latest version of VoltDB is available to download now. For more information visit the company's website.
Image Credit: wavebreakmedia / Shutterstock
-

Simplifying enterprise mobility management
Publié: janvier 28, 2015, 2:31pm CET par Ian Barker

Mobile device strategy, especially if it involves BYOD, can mean having to manage a wide range of devices and operating systems. That makes it difficult for IT departments to find a single solution to do the job.
Now though secure mobility specialist Good Technology is launching its Good Management Suite, a comprehensive cross-platform solution for organizations getting started with mobile business initiatives.
"As mobility continues to assume a larger role in the enterprise, organizations need to plan for both their current and future mobile needs," says John Herrema, senior vice president of product management at Good Technology. "By delivering a comprehensive cloud-based Enterprise Mobility Management solution, we are ensuring that organizations have access to a simple solution that expands as their mobile initiatives evolve".
Good Management Suite is a cloud based solution that can be installed and configured quickly. It provides a unified solution to simplify the deployment of mobile devices across an enterprise.
Unlike traditional MDM products, Good Management Suite is designed to adapt to an organization's growing and changing mobile needs. It can be used in conjunction with other Good Enterprise Mobility Management products for maximum flexibility, while simplifying management of these environments through a single management console called Good Control.
"The rising complexity of the mobile landscape is forcing many organizations to examine how MDM products can integrate with broader mobile management capabilities," says Stacy Crook, research director, mobile enterprise at research company IDC. "While standalone MDM products used to be the entry point, organizations are now looking for more comprehensive EMM solutions with flexible deployment options. We believe this shift is indicative of the growing sophistication of mobility strategies within these organizations".
For more information on Good Technology's mobile management solutions you can visit the company's website.
Image Credit: jannoon028 / Shutterstock
-

Delivering enterprise solutions faster via the cloud
Publié: janvier 27, 2015, 4:26pm CET par Ian Barker

Shifting to mobile and cloud solutions has led to expectations that software projects should be delivered faster and more efficiently.
However, according to a recent Mendix survey 71 percent of development teams are unable to keep up with demand.
To help ensure software projects are delivered faster and within budget, enterprise and collaboration software company iRise is launching its iRise 10 Enterprise Visualization Platform in the cloud.
It allows dispersed teams, both business and technical, to work together in real time on software requirements, designs and prototypes. By allowing issues to be spotted early it can reduce the need for reworking and cut delivery times. iRise's Professional Services team works with each client to develop an adoption strategy that is scalable across the organization.
"Delivering software with speed and agility is more critical than ever before," says iRise CEO and CoFounder, Emmet B. Keeffe III. "In today's hyper-competitive business landscape, it's very difficult to compete without a world class software development capability. Collaborative visualization is the single best investment organizations can make to ensure they deliver the right software ahead of their competition".
Because it's web-based iRise is easy and intuitive to operate even for non-technical users. All team members can provide instant feedback on projects, thus allowing greater clarity and understanding across the enterprise.
Additional features include shared libraries to allow modules to be assembled using pre-built templates and UI elements that meet corporate design standards. An iRise Studio desktop companion permits the adding of complex behaviors, business logic and data operations.
Available from today, iRise 10 can be deployed on-premise or in the cloud and can be purchased on subscription or a perpetual license basis. For more information and to sign up for a free trial visit the iRise website.
Photo Credit: Vallepu / Shutterstock
-

Enterprise app store streamlines BYOD adoption
Publié: janvier 27, 2015, 3:07pm CET par Ian Barker

Businesses are turning increasingly to mobile devices as means of boosting productivity, but if employees are allowed to use their own devices for work it can be difficult to ensure they use approved apps.
Licensing and compliance specialist Flexera Software has a solution in the form of its App Portal. This is a universal enterprise app store which allows self-service delivery across platforms.
The latest release of App Portal, launched today, allows the IT department associate mobile and desktop versions of an application, allowing employees to request an application once and have it deployed to all of their devices at the same time -- eliminating the need to individually request software from each device.
It also goes further by proactively suggesting apps that are available for other registered devices. It includes support for the iOS and Android public stores as well as for internally developed apps. The checkout process works with a number of management solutions including AirWatch and Microsoft System Center Configuration Manager.
"Employees want the ability to request an app once and use it wherever they work -- on their desktops, tablets or mobile phones -- without having to go to each of their devices and request the same app over and over again. They want immediate access, and don’t appreciate that behind the scenes, a very complicated request has been triggered for IT to fulfill," says Maureen Polte, Vice President of Product Management at Flexera Software. "App Portal is the first universal enterprise app store able to centralize and manage those back office processes, making ‘request once, fulfill anywhere’ a reality".
App Portal 2015 is optimized for use on mobile devices, giving employees simplified access to approved mobile apps directly from their phone or tablet. Employees can browse, select and check out corporate approved mobile apps from their Apple or Android device.
The portal enables enterprises to provide a transparent, friendly, personalized user experience while maintaining proper control and governance over valuable enterprise software assets. You can find out more by visiting the Flexera website.
Photo Credit: Digital Storm/Shutterstock
-

Facebook is the world’s favorite identity
Publié: janvier 27, 2015, 11:29am CET par Ian Barker

With more and more websites requiring passwords to access them, people are looking for ways to manage their surfing that don't require multiple IDs.
Increasingly the answer they're turning to is social media and in particular Facebook. A new infographic from identity management specialist Gigya shows that the social network accounted for over 60 percent of logins in the fourth quarter of last year.
Google takes care of 22 percent of logins, with Twitter and Yahoo trailing on six percent each. Facebook’s most dramatic gain cane from mobile devices which showed a 15 percent increase over the third quarter as consumers increasingly use smartphones as their main internet device.
The graphic also breaks down logins by type of site and by region. Interestingly Facebook is least popular as a login in North America with only 59 percent of the market. In Europe it accounts for 71 percent but Facebook is most popular in Africa and the Middle East with 79 percent.
When looked at by site, Facebook is most popular for education and non-profit sites on 76 percent, and least popular for media and publishing sites on 55 percent.
You can view the full infographic below.
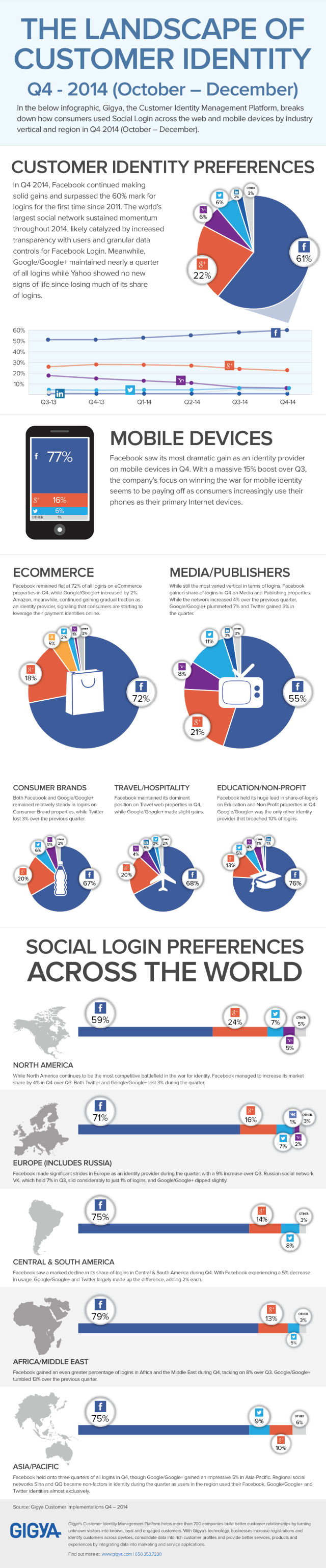
Photo credit: JuliusKielaitis / Shutterstock
-

How hackers can infiltrate a network and remain undiscovered
Publié: janvier 26, 2015, 3:34pm CET par Ian Barker

In 2014 we saw many data breaches which were often due to a direct attack on a company’s network in which human error played a part.
Big data security specialist Exabeam has produced an infographic showing how hackers can penetrate a network and remain difficult to spot.
It points out that 76 percent of breaches involved stolen user credentials. Using stolen identities hackers can penetrate a system and will then look to elevate their access privileges to allow them access to sensitive information.
Because they're using valid credentials these attacks often remain below the radar. This allows hackers to remain on the system for a long time, 200 days according to some sources.
Exabeam uses SIEM (Security Information and Event Management) technology to digitally monitor user behavior, and take human error out of the equation.
You can view the full infographic below.
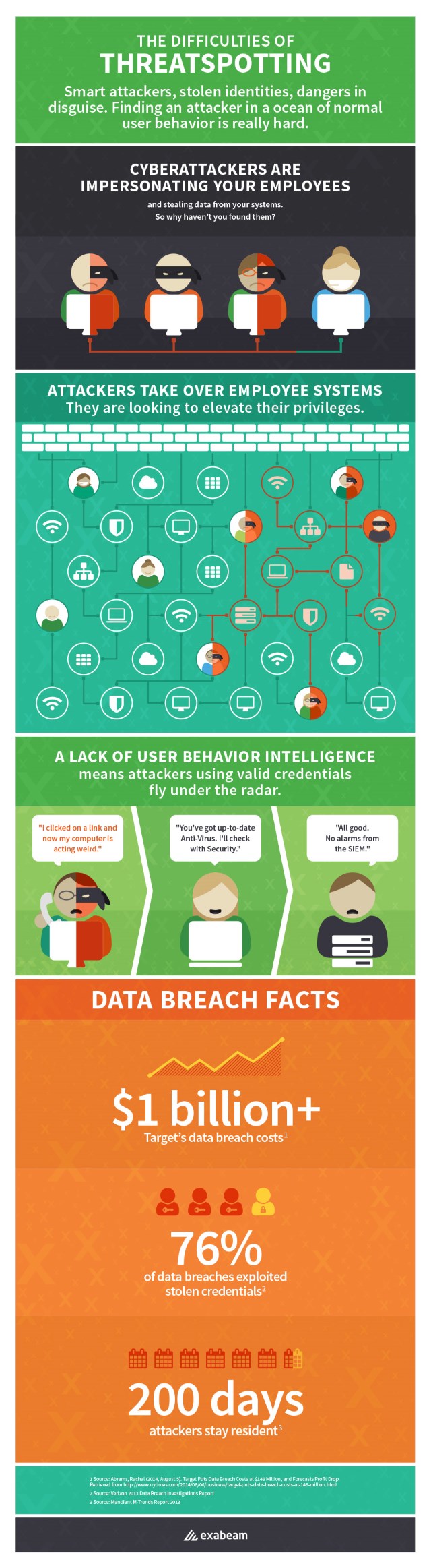
Photo credit: Adchariyaphoto/Shutterstock
-

The social media threats to watch for in 2015
Publié: janvier 23, 2015, 12:10pm CET par Ian Barker

The increased popularity of social media, for business as well as personal use, has opened up a new avenue of attack for cyber criminals.
Risk management company ZeroFOX has produced a list of the top social media attacks to look out for this year.
These include impersonations of businesses and executives using fake accounts. These can be used to send phishing messages, launch social engineering attacks or to damage the reputation of those targeted.
Hijacking accounts is another approach. Once in control an attacker can do serious damage either by malware attacks or cyber vandalism. Organizations need to treat their accounts like any other high value asset when it comes to protecting them.
As social media has become a popular source of news, so attackers have realized that they can launch a successful attack by planting malicious links where people are discussing events. This is known as 'watering hole phishing' and is made worse by the fact that 75 percent of people use the same password for their social media and email so once one account is compromised the other is too. Clickbait attacks using sensationalist headlines are another concern as is the hijacking of hashtags to distribute malicious links to a specific audience or divert traffic.
ZeroFOX points out that cyber criminals are using social media to plan their attacks too. With the right tools in place, organizations can leverage social media as an early warning system, unlocking a wealth of attack data that could give security teams the edge.
You can see the full list of threats on the ZeroFOX blog.
Image Credit: Fabio Freitas e Silva / Shutterstock
-

Face-to-face status meetings are bad for productivity
Publié: janvier 22, 2015, 1:22pm CET par Ian Barker

American workers spend an average of 4.6 hours a week preparing for meetings and 4.5 hours actually in them, but most would rather be doing something else.
This is among the findings of a new survey by enterprise collaboration software specialist Clarizen. It also shows that almost half of respondents would rather "do any unpleasant activity" than sit in a status meeting, including going to the Department of Motor Vehicles or watching paint dry.
35 percent say that status meetings -- a meeting with updates for team members on completed and active work tasks -- are a waste of their time. Three in five also report that they multitask during meetings.
"Survey results continue to show that status meetings do not boost employee productivity," says Avinoam Nowogrodski, founder and CEO of Clarizen. "In today's modern workplace, where demands are constantly changing, employees need easy, real-time access to their discussions, work content and processes. This is what fuels employee productivity and quality work, not sitting in status meetings or preparing lengthy status reports. Clarizen enables company-wide collaboration, accountability and transparency, meaning workers spend less time in meetings and more time completing actual, meaningful work".
Clarizen's latest release includes a new mobile platform which mirrors the features of its web-based application. This creates a seamless user environment which allows users to have a consistent experience wherever they are and whatever device they’re using.
By offering immediacy and flexibility it allows employees to get their work done and stay up to date without having to spend time sitting in meetings.
The latest release is available now at no charge to existing Clarizen customers. For more information on what it offers you can visit the company's website.
Image Credit: wavebreakmedia / Shutterstock
-

Is it time to say goodbye to the password?
Publié: janvier 22, 2015, 12:01pm CET par Ian Barker

Microsoft's Bill Gates predicted the death of the password as long ago as 2004, yet we're still heavily reliant on them for our day-to-day security.
Part of the reason the password has lingered so long is the lack of solutions that provide security combined with ease of use.
Now though thanks to the widespread adoption of smartphones we may be getting closer to seeing the death of the one-time password. SSL certificate supplier SSLs.com has produced an infographic looking at the alternative authentication methods that are set to take over.
Biometric security methods range from the fingerprint readers we're increasingly familiar with to technologies that can detect your cardiac rhythm, scan the shape of your ear -- perhaps not so useful for boxers -- or even read your brainwaves.
Other authentication technologies involve syncing your phone to other devices, proximity devices or wearables that authenticate devices within range. There's even the possibility that you could swallow a pill or have a tattoo that lets your body act as an authentication token.
For a look at these and other methods of eliminating the need for a password you can see the full infographic below.

Photo Credit: Dr. Cloud/Shutterstock
-

Resilience becomes key as businesses rely more on data
Publié: janvier 21, 2015, 4:11pm CET par Ian Barker

Increased reliance on systems and data means that downtime and loss of information is a greater problem than ever before.
Disaster recovery specialist Vision Solutions has launched the latest version of its annual State of Resilience report which highlights the trends and challenges for business and IT leaders.
The report combines information from five industry-wide surveys of more than 3,000 IT professionals. Among the findings are that nearly 75 percent of respondents have not calculated the hourly cost of downtime for their business. For those who did experience a storage failure, nearly 50 percent lost data in the process due to insufficient disaster recovery methods or practices.
Almost two-thirds of those surveyed said they had delayed an important data migration for fear of downtime or lack of resources. Hosted private cloud is still the most prevalent cloud environment at 57 percent usage, with hybrid cloud adoption at only 32 percent with room to grow.
Despite the growing popularity of the cloud, nearly two thirds stated they didn't have high availability or disaster recovery protection in place for their data once it's stored in the cloud.
"In order to address the many challenges presented by exploding data growth, businesses must invest in better data protection," says Vision Solutions' Vice President of Sales Engineering Henry Martinez. "Importantly, these solutions must be agile enough to minimize system disruptions, support emerging technologies and provide the flexibility to operate in any combination of physical, virtual and cloud platforms and storage environments. This is a critical foundation for IT resilience and business success in the future".
The company is hosting a webinar to discuss the report's findings on January 22nd and you can register to take part on its website.
Image Credit: Oleksiy Mark / Shutterstock
-

Predictive marketing cloud helps companies unlock customer data
Publié: janvier 21, 2015, 3:14pm CET par Ian Barker

In order to gain a competitive edge marketers are keen to gain insight from customer data. But the information may be spread across various systems and the cloud, making it hard to access.
In response to this problem marketing software company AgilOne is launching a product built from the ground up to unify online and offline data integration, cleansing, insights and campaigns, seamlessly bridging the worlds of digital and offline marketing.
We reported last month on the company's predictive intelligence solution but the new AgilOne 5 Predictive Marketing Cloud provides marketers with a comprehensive turnkey solution that works out of the box. It allows users to predict the needs of the customer and to design and execute relevant email, social media, web and direct mail campaigns from a single hub.
"Companies of all sizes need to deliver relevant customer experiences that not only delight their customers and build loyalty, but also improve business results," says AgilOne CEO Omer Artun. "Today, AgilOne delivers the industry’s first an easy-to-use, truly predictive and out-of-the-box marketing cloud, so that all brands, large and small, can take advantage of the wealth of customer data available to them and deliver an omni-channel experience that improves customer engagement and the company’s bottom line".
Key features include a drag and drop builder that enables any marketer to create and design targeted audience campaigns based on sophisticated predictive analytics. They're able to generate smart content based on an individual's recommended products, abandoned cart items, or personalized discounts.
It allows users to tailor the look and feel of the web recommendations to match their brand image. They can also add rules that automatically adjust recommendations to achieve the best results, by excluding items that are in short supply, for example.
For more information and to sign up for a webinar you can visit the AgilOne website.
Image Credit: Kidsana Maimeetook / Shutterstock
-

93 percent of US organizations are vulnerable to insider threats
Publié: janvier 21, 2015, 12:11pm CET par Ian Barker

In the past few years the adoption of new methods to access corporate data has led to traditional endpoint security being less effective. At the same time there are concerns about the number of employees who have access to data and how much of a threat they present.
Data security specialist Vormetric has released its latest Insider Threat Report which reveals that 93 percent of US organizations polled believe that they’re vulnerable to insider threats.
Among other findings are that 59 percent of respondents in the US believe privileged users pose the biggest threat to their organization, and preventing a data breach is the highest or second highest priority for IT security spending for 54 percent.
The cloud comes under scrutiny too with 46 percent of US respondents believing they present the greatest risk for loss of sensitive data in their organization. However, 47 percent believe databases have the greatest amount of sensitive data at risk.
Businesses are subject to pressure from attacks and security breaches too. 44 percent say their organization has experienced a data breach or failed a compliance audit in the last year and 34 percent of respondents say their organizations are protecting sensitive data because of a breach at a partner or a competitor.
"As the past year demonstrates, these threats are real and need to be addressed," says Alan Kessler, CEO for Vormetric. "Organizations wishing to protect themselves must do more than take a data-centric approach; they must take a data-first approach. Although we are heartened that 92 percent of organizations plan to maintain or increase their security spending in the coming year, our larger concern is about how they plan to spend that money. The results indicate there is still disagreement about where corporate data, which is most at risk, actually resides. Our experience, observations and conversations with customers have taught us that even if the situation isn't entirely black and white, organizations’ use of encryption, access controls and data access monitoring greatly reduce their risk and exposure".
The problem isn't limited to the US either, 55 percent of global respondents believe privileged users are the biggest threat. Also 54 percent say they will be increasing spending to offset the threat in the coming year.
The full report is available from the Vormetric website.
Image Credit: Andrea Danti/Shutterstock
-

Platform9 makes private clouds easier to implement
Publié: janvier 20, 2015, 5:11pm CET par Ian Barker

Public cloud services put a lot of resources into managing their systems in order to provide an efficient service with automated infrastructure and self-service features.
For businesses wanting to implement their own private clouds, however, achieving a similar level of service can be difficult. They often turn to solutions like OpenStack but fail to reach its full potential thanks to a lack of the resources and skills required.
Private cloud specialist Platform9 aims to make things easier with the announcement of the general availability of Platform9 Managed OpenStack. This is a SaaS solution that transforms an organization's existing servers into an AWS-like agile, self-service private cloud.
"Today, Platform9 is disrupting the complexity barrier to private clouds with Platform9 Managed OpenStack -- its SaaS simplicity, production readiness, and seamless integration with existing environments enable every organization to manage their in-house infrastructure with greater agility and efficiency", says Sirish Raghuram, Co-founder and CEO of Platform9.
Platform9 Managed OpenStack offers ease of use without the need for any OpenStack expertise. It supports existing environments so that businesses can import their own servers, storage and network configurations. It can also work seamlessly across multiple sites, integrating all of an enterprise's distributed infrastructure into a single private cloud.
The service is continuously monitored by Platform9's internal telemetry for availability and operational health. Also updates are seamless and non-disruptive and in most cases will be transparent to the customer. It incorporates an update to a new, stable OpenStack release each year to take advantage of the latest enhancements.
The product is available as a free, Lite, version to allow users to test or learn about it on a limited scale. There are then pricing models for business from $49 per month. You can find out more and sign up for the Lite tier on the Platform9 website.
Photo Credit: Marynchenko Oleksandr / Shutterstock
-

Users and IT teams are part of the security problem says Cisco
Publié: janvier 20, 2015, 3:15pm CET par Ian Barker

Careless user behavior and targeted malware campaigns are putting many industry sectors in danger from security breaches with the pharmaceutical and chemical industries at highest risk.
This is among the findings of the latest Annual Security report from networking specialist Cisco. It also finds that attackers are adapting their methods to make their campaigns harder to detect.
Among the changes are the rise of 'snowshoe spam' which involves sending low volumes of spam from a large set of IP addresses to avoid detection, and the use of less common exploit kits so as not to attract attention. There's also an increase in malicious combinations, sharing attacks between two files, for example Flash and JavaScript to make them harder to detect.
Users are the main target though and may also be unknowingly aiding cyber attacks. Throughout 2014, Cisco threat intelligence research has revealed that attackers have increasingly shifted their focus from servers and operating systems as more users are downloading from compromised sites leading to a 280 percent increase in Silverlight attacks along with a 250 percent increase in spam and malvertising exploits.
Users are increasingly targeted using web browser add-ons as a medium for distributing malware and unwanted applications. This approach too is proving successful because many users inherently trust add-ons or simply view them as benign.
"Attackers have become more proficient at taking advantage of security gaps. At any given time, we should expect for one percent of high-urgency vulnerabilities to be actively exploited while 56 percent of all OpenSSL versions are still vulnerable to Heartbleed," says Jason Brvenik, Principal Engineer, Security Business Group at Cisco. "Despite this, we see less than half of the security teams surveyed using standard tools like patching and configuration management to help prevent security breaches. Even with leading security technology, excellence in process is required to protect organizations and users from increasingly sophisticated attacks and campaigns".
The report also reveals that while many defenders believe their security processes are optimized, and their security tools are effective, in truth, their security readiness likely needs improvement. It concludes that corporate boards need to take a role in setting security priorities and expectations.
It sets out some basic principles for achieving security which include that security must be transparent and informative, that it must enable visibility and appropriate action and that it must be viewed as a 'people problem'.
A complete copy of the report is available from the Cisco website.
Image Credit: watcharakun/Shutterstock
-

A smartwatch for under $50 -- Rwatch R5 [Review]
Publié: janvier 20, 2015, 11:36am CET par Ian Barker

Like any new technology, smartwatches when they first appeared were fiendishly expensive. Now that budget manufacturers are getting in on the act however prices are starting to tumble.
The R5 from Chinese company Rwatch costs less than $50 and will work with most Android phones, but can it compete with the pricier offerings from big name manufacturers?
First impressions are pretty good. The R5 comes in a nice sturdy, white cardboard box which you wouldn't be ashamed to hand over as a gift. What you get in the box is the watch, a USB cable and some basic instructions. The watch itself is quite stylish (it's available in silver, gold or the black of the review unit) and it looks very similar to the Samsung Gear 2. It has a rubbery plastic strap and a shiny surround to the screen.
You only get one button on the front of the device which is used to turn it on and off and wake it from standby. There's a cover over the USB port on the left side which feels a little bit flimsy. The R5 has a 1.5-inch touch screen with a 240 x 240 resolution and the makers claim 120 hours of standby or three hours of talk time from a full battery charge.
Plug it into a USB port and leave it to charge for a while then you can get started. To sync it with your Android phone you need to download an app -- there's a QR code in the instructions to allow you to do this -- once connected with Bluetooth it allows you to sync various phone functions. There's all of the usual stuff related to calls and messages, plus you can control your phone's media player and camera remotely.
There's also an 'anti lost' function which will vibrate the watch to alert you if the phone goes out of range and some basic health monitoring in the form of a sleep monitor and a pedometer. Being a watch of course it also tells the time and you can choose between a digital or analogue-style display and there are stopwatch and alarm functions.
The R5 may look like a Gear 2 but it's a lot cheaper than it or any of the big name smart watches. It has a capacitive screen which proved to be quite responsive and with decent viewing angles. You need pretty accurate fingers to access some of the settings or to dial numbers though. If you look closely the display is a little pixellated but it's good enough for day-to-day use. It's not as if you're going to be watching movies on it.
There are only a limited number of rather weedy ring tones, but for most people the vibrate function is probably more useful as an alert anyway. As with a lot of Chinese devices the instructions are written in somewhat mangled English but most of the functions are easy to use anyway.
The device feels a bit chunky compared to a normal wristwatch, but given its price the R5 has a surprisingly good range of features and is nicely usable. You're also not tied to a particular make of phone, it should work with anything running Android 4.3 or above. If you want to give smartwatches a try without spending a lot of money it's worth a look.
Our review sample was supplied by GearBest.com and currently sells for $43.19. BetaNews readers can use coupon code: RWR5CN at the checkout to get it for $38.99. The coupon expires on March 3rd.
-

The FUZE gets an update and new features
Publié: janvier 19, 2015, 3:47pm CET par Ian Barker

It was over a year ago that the FUZE, a machine aimed at getting a new generation interested in programming, hit the market.
Now there's a revised T2 version of the Raspberry Pi- based machine that brings a number of useful updates and new features.
There's now a built-in USB hub so that spare ports are available after a mouse and keyboard are connected, an uprated PSU and, something that we mourned the lack of in our original review, an on/off switch.
It now comes with an 8GB SD card rather than the 4GB of the old version, plus the IO board has been updated with the main pins duplicated and clearer labeling. GPIO pass through has been added allowing popular add-on boards to be directly connected and the case has gained mounting holes for popular kits and building blocks.
In addition to the hardware changes there's a special edition FUZE-T2-SE available, styled to look like a 1980s home computer. You can also now buy a FUZE complete with a robot arm kit.
The standard version complete with a Raspberry Pi B+ costs £179.99 (around $273) or if you already have a Pi you can buy the unit for £129.99 (around $197). If you want the robot arm the complete package costs £229.99 (around $350). For more information visit the FUZE website.
-

IObit launches safe payment environment for mobile users
Publié: janvier 16, 2015, 4:28pm CET par Ian Barker

Perhaps best known for its SystemCare products for Windows, software company IObit is launching a new version of its Android app, AMC Security.
AMC Security is a combined security and device optimization app. Among the new premium features included in this release is Payment Guard, which is designed to protect mobile users' financial data and the mobile payment and banking process.
It has built strategic partnerships with more than 1,000 of the world's leading mobile banking apps and online retailing apps in order to offer payment protection. The software helps users ensure safe access to a payment environment thanks to a number of features.
These include a fake Wi-Fi hotspot detector, a copycat payment app remover, the ability to block fake and phishing sites and a tool to prevent the theft of account details and passwords.
"With the increasing awareness of mobile wallet, 2015 will see the global m-commerce market's boosting to reach a new record high level. Therefore, our Payment Guard is just the beginning. AMC Security will keep on working out solutions for NFC and fingertip payment methods," says Fiona Choo, PM of IObit Mobile.
AMC Security has a base of more than 12 million consumer users for Android. It has established itself as a global leader in the mobile security space by building long-term partnerships with scores of major mobile manufacturers, operators and carriers to provide payment protection to their users and subscribers.
AMC Security is available to download now from the Google Play store.
Photo Credit: Slavoljub Pantelic/Shutterstock
-

The cost of dealing with false positive malware alerts
Publié: janvier 16, 2015, 12:46pm CET par Ian Barker

False positives are often accepted as a fact of life with anti-virus programs but a new survey commissioned by breach detection specialist Damballa reveals that they have a significant cost for businesses.
The study produced by the Ponemon Institute reveals that enterprises spend $1.3 million a year dealing with false positive cyber security alerts, which equals nearly 21,000 hours in wasted time.
In a typical week, organizations receive an average of nearly 17,000 malware alerts, yet only 19 percent are deemed reliable -- or worthy of action. This means security teams can waste time on alerts that pose no threat to their data security and which can distract them from dealing with threats that can lead to compromise.
Compounding the problem, respondents believe their prevention tools miss 40 percent of malware infections in a typical week. The longer malware goes undetected of course, the greater the risk of a breach.
In addition 60 percent of respondents report that the severity of infections has increased over the last year. But despite this 33 percent of organizations revealed that they have an unstructured or ad hoc approach to handling alerts. In terms of responsibility, 40 percent of respondents say there is no one person or function in their enterprise accountable for the containment of malware.
Only 41 percent of respondents say their organization has automated tools to allow them to capture intelligence and evaluate the true threat caused by malware.
"These findings confirm not only the sheer scale of the challenge for IT security teams in sifting out the real threats from tens of thousands of false alarms, but also the huge financial impact in terms of time. The severity and frequency of attacks is growing, which means that teams need a way to focus on responding to true positive infections if they are to get a firmer grip on their security posture," says Brian Foster, CTO of Damballa. "It's more important than ever for teams to be armed with the right intelligence to detect active infections to reduce their organization's risk exposure and make the best use of their highly-skilled, limited security resources".
The full report is available on the Damballa website or there’s a webinar to discuss the findings on January 20th.
Photo Credit: Alexander Kirch/Shutterstock
-

Fast forward to the 1980s as the cassette player makes a comeback
Publié: janvier 16, 2015, 11:50am CET par Ian Barker

For anyone under 30 it may be hard to remember a time when you shared your musical tastes via mixtapes rather than playlists, when the top of every bus shelter was adorned by a broken cassette trailing yards of tape, and when loading a home computer program involved a tense few minutes hoping that you wouldn't suffer a read error before the end of the tape.
Well, prepare for a wave of hissing and clicking nostalgia as the cassette player seems to be making a comeback. According to UK catalog retailer Argos sales of cassette players over the past three months are 45 percent higher than the same period last year.
It's hard to see the cassette staging a comeback in the same way as vinyl records though and the trend is believed to be down to older users rediscovering their favorite music.
"We know that many of our customers have been buying cassette players for older friends and family to enjoy their favorite music from the 60s, 70s and 80s," says Argos audio buyer Rachel Bartram. "The devices also provide a great way of finding out about the lives of our loved ones when they were younger, from mixtapes created for friends to recordings of favorite radio shows, and even family events captured on tape".
It could be too that people are digging their old cassettes out of the attic before converting their musical memories to MP3. However, in the last couple of years indie bands including British Sea Power and MGMT have embraced the cassette and released material in the format.
Are you nostalgic for the hiss of a C60? Tempted to revisit your old mixtapes? Got a pencil handy to take up the slack? Let us know in the comments.
Image Credit: Luis Louro / Shutterstock
-

SAASPASS makes two-factor authentication available to the masses
Publié: janvier 15, 2015, 5:16pm CET par Ian Barker
Passwords are increasingly being seen as inadequate for protecting information and businesses and end users alike are looking for more secure alternatives.
San Francisco-based SASSPASS is making it easier to implement two-factor authentication with the launch of its Computer Connector. In conjunction with a SAASPASS mobile app it enables quick and easy 2FA for Macs and PCs.
The need to possess a physical device helps prevent 99 percent of hacks, which are typically launched remotely. With SAASPASS new passcodes are generated every 30 seconds, thereby enabling a level of security that in the past would only have been available to the largest companies and governments using expensive and complex corporate 2FA systems.
The SAASPASS Computer Connector enables this level of security in an intuitive, seamless way by allowing users to use their mobile devices to login to their PCs and Macs. Users can simply use their mobile phone to unlock access to paired accounts with just their device proximity or a simple scan, rather than have to rely on individual passwords.
As well as logging into devices it can be used to allow access to websites or cloud services like Office 365 or Dropbox for Business. The API means it can be integrated into things like access control systems too allowing a phone to substitute as a pass card.
"We believe strong security is a right, and it shouldn't be a pain in the ass. If a solution isn't simple enough for my mom to use, then it's not a solution. The average person doesn’t care for complexity, they want security to just work in the background simplifying their lives." says SAASPASS Chairman Oliver Ring. "SAASPASS does just that. Never before has strong security been so simple and easy to use. It's the iPhone of Strong Security".
You can get more information on the SAASPASS website and there’s a video demonstrating how it works below.
-

Changing employee behavior can cut security risk by up to 70 percent
Publié: janvier 15, 2015, 3:52pm CET par Ian Barker

Whilst companies employ an array of sophisticated technology to combat security risks, often the weakest link remains the person sitting in front of the screen.
New research from Wombat Security Technologies and the Aberdeen Group suggests that changing employee behavior when responding to cyber threats via social media, phishing and other popular attack vectors can reduce an organization's risk by as much as 70 percent.
The report finds that despite controls and protection being in place many -- if not most -- reported security incidents result from the actions of company employees. The new research clearly demonstrates that investments in security awareness training can help businesses close the security gap.
"It's important for security teams to communicate clearly about the risks that organizations are accepting when their employees' response to cyber threats is not addressed," says Derek Brink, VP and Research Fellow for Aberdeen Group, at Harte Hanks Company. "While the public disclosures of the past several months have provided some startling examples about what can happen when security awareness and training is ignored, Aberdeen and Wombat have developed this model to address the most basic and logical question that security teams so often struggle to address: How does an investment in changing end user behavior through innovative security education solutions actually reduce the organization's risk?"
The findings show that an investment in user awareness and training is effective in changing behavior and measurably reduces security-related risks by between 45 and 70 percent. The report also estimates that for an organization with $200 million in annual revenue there is an 80 percent likelihood that infections from employee behavior will result in total costs of $2.5 million, with a 20 percent chance of exceeding $8 million.
The full report, The Last Mile in IT Security: Changing User Behavior, is available to download from the Wombat Security site.
Photo Credit: tommaso79/Shutterstock
-

CommVault launches endpoint protection for mobile enterprises
Publié: janvier 15, 2015, 12:32pm CET par Ian Barker

The growth of mobile workforces means that employees are often reliant on data that's stored outside the protection of the normal IT infrastructure.
With global data breaches having an average cost of $3.5 million, according to a study by the Ponemon Institute, due to lost or unrecoverable data on employee devices, organizations are beginning to embrace centrally managed platforms that can be used to address data protection, collaboration, regulatory, and eDiscovery requirements in a secure manner.
Information management specialist CommVault is launching a new solution called Simpana for Endpoint Data protection, designed to help protect and enable the mobile workforce by efficiently backing-up laptops, desktops and mobile devices and providing secure access and self-service capabilities.
"We are excited to bring Endpoint Data Protection to market with an expanded new feature set and pricing structure that will give customers flexible options in how they want to tackle the growing challenges and complexities around data management beyond IT’s traditional reach," says Rama Kolappan, senior director and head of CommVault's Mobile Business Unit. "With data breaches continuing to make headlines and wreaking havoc on corporate reputations, our new solution set is able to give organizations the 'peace of mind' knowing their data is protected while freeing employees access to information residing within IT".
The product offers a number of capabilities that can be purchased as separate modules. Rapid backup and recovery protects devices and lowers business risk, secure file sharing makes sure data is available when and where it's needed. Integrated compliance and eDiscovery delivers security with role-based access and allows faster response to legal requests for data. Security and data loss protection encrypts data in transit and at rest as well as allowing remote wiping of lost devices. Finally, analytics make it easy to review data and ensure compliance requirements are being met.
More information is available on the CommVault website.
Photo Credits: Slavoljub Pantelic/Shutterstock
-

Bushel makes Apple mobile device management available to smaller businesses
Publié: janvier 14, 2015, 4:57pm CET par Ian Barker
Mobile device management is becoming essential for more and more businesses, but solutions are often complex and difficult for enterprises without specialist IT staff to adopt.
Software company JAMF which produces MDM solutions for iOS devices has launched a low cost, easy-to-use solution called Bushel aimed at small and medium businesses.
Bushel is a cloud-based solution that’s designed to be easy to set up, even by non-experts, and can protect Apple devices at any time and from anywhere. It makes complex tasks including Apple device setup, security and management, simple and quick -- enabling users to focus on their business, rather than get caught up with managing technology.
"Bushel marks a remarkable step in Apple device management. For the first time, workgroups and smaller businesses have a solution that is specifically designed for them," says Charles Edge, Product Manger of Bushel. "Bushel enables anyone, including non-technical staff, to manage Mac, iPad and iPhone without the headache. Users can take advantage of all the best in Apple technology, including enterprise-grade security features simply and at low cost. We look forward to this new era in Mobile Device Management as we continue to fulfil our mission of making people's lives easier".
Bushel features easy, hands-free device configuration through the Apple Device Enrollment Program (DEP), as well as comprehensive device inventory features. With automated device enrollment, users can get up and running quickly, while businesses can ensure ongoing management and inventory insight into their devices.
Businesses can automatically install applications to all devices at once, saving time and manpower. Enrollment in Apple’s Volume Purchasing Program (VPP) means that management can also keep their application investments in-house with the option of revoking applications from any devices that are no longer in use.
If a device with Bushel is lost or stolen, it can be locked remotely or wiped completely. Users can also require devices to have passcodes and specify a time before a device automatically locks. Additionally, Bushel allows for easy disk encryption and control options to ensure that all valuable business data is kept safe and separate from personal information in BYOD environments.
Bushel can be installed on up to three devices for free so that companies can try it out and thereafter costs $2 per machine per month. You can find out more and sign up for a free trial on the Bushel website.
-

Optimove offers real-time customer marketing tools
Publié: janvier 13, 2015, 6:00pm CET par Ian Barker

Turning customer data into sales is something of a holy grail for businesses and there are an increasing number of software solutions aimed at helping find it.
One player in this field, customer retention platform Optimove, is using the National Retail Federation's Annual Convention and Expo to launch a version of its platform with real-time capabilities.
Optimove CEO, Pini Yakuel says, "By building into our customer retention software a complete, end-to-end system for real-time personalized messaging, we have not only taken another great stride towards achieving the ultimate retention marketing solution, but we've also become the first platform to offer real-time retention marketing in such a sophisticated and easy-to-deploy manner".
The product allows users to deliver messages to customers at the time when they'll be most effective. It employs trigger-based campaigns to enable marketers to respond to customer behaviors as they happen in real-time, increasing customer engagement and loyalty while reducing churn rates.
A variety of events or activities can be used to trigger a marketing message. For example if a customer is about to spend, say, $75 they can be sent a message offering free shipping if they increase their order to $100. If products are viewed but not added to the shopping cart a discount can be offered, or social gamers can be invited to extend their play time by inviting friends.
Other features include end-to-end campaign management tools, automatic selection of control groups, event tracking, automatic message delivery, results analysis, and optimization recommendations.
You can find out more about how it works and request a free web demo on the Optimove website.
Image Credit: donskarpo / Shutterstock
-

Google patch policy leaves over 900 million Android users out in the cold
Publié: janvier 13, 2015, 4:48pm CET par Ian Barker

When a version of Windows reaches the end of its normal support, as Windows 7 has today, Microsoft continues to provide security patches for an extended time.
Google it seems prefers to take a tougher line and is not issuing patches for versions of Android prior to 4.4 KitKat, leaving millions of users of older versions out in the cold.
The policy came to light when researchers at security company Rapid 7 reported a vulnerability in WebView -- a core component used to render web pages -- on pre 4.4 versions of the OS and received the following reply:
"If the affected version [of WebView] is before 4.4, we generally do not develop the patches ourselves, but welcome patches with the report for consideration. Other than notifying OEMs, we will not be able to take action on any report that is affecting versions before 4.4 that are not accompanied with a patch".
In other words security companies are now expected to report a bug along with a patch to fix it. Otherwise Google will simply inform manufacturers like Samsung and Motorola and expect them to provide fixes for their handsets. Imagine for a moment if you reported a Windows bug and Microsoft told you you had to call Lenovo or Dell to get a fix for your PC.
This potentially puts over 900 million Android devices out of the loop when it comes to getting security patches. Given that many of these will be budget phones and tablets that won't have the option to upgrade to a later version they're likely to remain vulnerable.
Of course Android is open source so handset makers -- or anyone else -- can come up with a patch. However, leaving this to chance seems like a short-sighted policy on Google's behalf and could dent long-term confidence in the operating system, particularly when it comes to safeguarding personal details.
On its blog Rapid 7 urges Google to reconsider. Whether or not it will have a change of heart we'll have to wait and see.
Image Credit: Gary Ham
-

What security threats will enterprises face in 2015? [Q&A]
Publié: janvier 13, 2015, 11:41am CET par Ian Barker

Last year saw a number of high profile security incidents hit businesses. From attacks on individual companies to bugs like Heartbleed that had the potential to affect large numbers of organizations.
Can we expect more of the same in 2015 or will the threat landscape continue to evolve? We spoke to Mark Bermingham, director of global B2B marketing at Kaspersky Lab, to find out.
BN: We've seen cybercriminals become much more businesslike with the dark web being used to sell tools and services. Can the security industry combat this or does it risk driving the perpetrators further underground?
MB: Cybercriminals have recently become more focused on stealth attacks. While this is their focus, Kaspersky Lab has evolved its discovery techniques to keep pace with the renewed emphasis on malware authors attempting to hide or erase their tracks. It's become a complicated game of cat and mouse. However, it's important to acknowledge that as malware increasingly becomes more sophisticated, one specific goal of cybercriminals is to attempt to be completely anonymous.
BN: Windows has historically been the main target for malware but we're starting to see that spread to Android and other systems. Can we expect to see more systems including iOS and Linux becoming vulnerable?
MB: One of the largest growth areas for malware is mobile. We've seen mobile malware spike significantly over the last couple of years. As consumers and businesses shift to using mobile devices for a greater percentage of their daily activities, cybercriminals will place a larger emphasis on targeting these platforms -- specifically Android and jail-broken IOS devices. Remote find, lock and wipe aren’t enough. Containerization is an excellent vehicle for ensuring isolation and separation of corporate and personal data on mobile devices, but these measures offer reactive security. It is critical for businesses to place mobile security agents on these devices, with capabilities like anti-malware, anti-spam and anti-phishing, to ensure proactive security.
BN: Is there a trend towards attacks becoming more targeted with a view to stealing financial information or intellectual property?
MB: There isn't a clear cut answer. It is important to note that stolen data assets are often monetized and that both attack types have increased and will likely remain high. In fact, we recently conducted a survey that found 94 percent of organizations encountered at least one cybersecurity incident in the past 12 months. Of these incidents, the number of organizations that reported having at least one targeted attack rose substantially, with 12 percent of respondents indicating that they experienced at least one targeted attack in the past year. However, I expect we'll see more financial impacts being publicized as businesses, and particularly consumers, become more comfortable and increase financial transactions via the Internet. This will likely become an attractive target for malware authors.
BN: Mobile payment systems are expected to take off in a big way this year. How can consumers and retailers ensure they stay protected when using mobile in new ways?
MB: Ensure due diligence with these devices. Deploy security agents when and where possible. Implement the security measures that are available with some devices like encryption and basic credential checks. Don't store passwords on these devices or have settings in place that don't require passwords. And make sure that you have a plan in place should a device become lost or stolen.
BN: As more and more devices get connected to the Internet of Things will they become subject to mass attacks and how can the data they hold be protected?
MB: IoT presents a new challenge for vendors like Kaspersky Lab since these devices will operate differently from traditional devices where security is understood to be required. Over time, the IoT will likely become a target -- especially as it becomes more connected to personal and corporate devices. These devices will require security in place, but special challenges exist in this space because of the functional goals of IoT. This is an emerging space and security requirements continue to evolve, but this environment will likely be a target of attack and security must be a key consideration.
BN: Recent events like the Sony hack have led to fears of state-sponsored hacking and malware. How real a threat is this and will we see governments becoming more involved in combating cyber threats?
MB: This is a trend that may continue, but these are generally extremely well-funded, highly sophisticated attacks designed with a specific purpose and are laser-focused. There is generally a tremendous effort with these types of attacks for cybercriminals to hide their tracks, so these are some of the most difficult types of attacks to identify. The threat resulting from these attacks is that malware authors often learn from these sophisticated attacks and deploy similar techniques on businesses and consumers.
BN: Finally, what simple steps can business take today to help protect themselves?
MB: Perform due diligence when selecting and deploying security in your environment. The game has become more complex so your security infrastructure must keep pace. Deploying a best-in-breed AV solution is a tremendous first step, but not all AV is created alike. Small differences in AV efficacy have a significant impact. Additionally, security tools such as controls, patch management, encryption and others are critical to evaluate.
Photo Credit: watcharakun / Shutterstock
-

Cloud security becomes a boardroom concern
Publié: janvier 12, 2015, 12:34pm CET par Ian Barker

Moving systems and data to the cloud is increasingly common, but it inevitably leads to concerns about security and those worries are now reaching the boardroom.
This is according to new research by the non-profit Cloud Security Alliance which looks at how companies are currently approaching the cloud, including their views on shadow IT, obstacles preventing cloud adoption, and security priorities.
The report includes responses from more than 200 IT and security professionals from varying sized companies around the world. Almost 72 percent admitted that they didn't know the number of shadow IT apps within their organization. The survey also highlights that decisions concerning the security of data in the cloud have moved from the IT department to the boardroom, with 61 percent of companies indicating that senior executives are now involved in such decisions.
Security remains the major barrier to cloud adoption but that isn't stopping companies from moving ahead. 74 percent of respondents indicated that they're moving forward with cloud adoption. However, lack of knowledge on the part of IT and business managers was cited by 34 percent as a reason for slow adoption.
The size of the business makes a difference, those with more than 5,000 employees being more likely to have things like policies and training in place to cope with the cloud. Yet large enterprises, seem to be more hesitant when it comes to investing in cloud services, with only 36 percent spending more than a fifth percent of the IT budget on cloud services, compared with 49 percent of companies with fewer than 5,000 employees.
"As companies move data to the cloud, they are looking to put in place policies and processes so that employees can take advantage of cloud services that drive business growth without compromising the security, compliance, and governance of corporate data," says Jim Reavis, CEO of the CSA. "We hope that this report provides companies with some good peer insight so that they can make better decisions to help confidently and responsibly accelerate the use of cloud services in their environment".
The full report is available to download from the CSA website.
Image Credit: Ferbies / Shutterstock
-

The Windows exploit landscape in 2014
Publié: janvier 9, 2015, 12:47pm CET par Ian Barker

Over the years we've grown used to Windows being the target of viruses, hacks and other forms of attack. Although other systems like Android are now coming under attack too it’s still Windows that gets the most attention.
Researchers from security company ESET have released a report showing the major trends in Windows exploits over the past year.
Among the findings are that Windows saw twice as many vulnerabilities in 2014 as in the previous year. Internet Explorer was the most attacked Windows component, and many users are still running potentially unsafe versions of the OS like XP.
Drive by downloads are the main means of exploiting vulnerabilities and delivering malicious code and ESET predicts that this is likely to continue to be the case in 2015. Other Microsoft products can be targeted too and researchers uncovered a number of cases where vulnerabilities in MS Office have been used to deliver a malicious payload.
Microsoft hasn’t been idle in protecting it's newer systems, however. The latest version of its Enhanced Migration Experience Toolkit (EMET) introduced some new security features. These features are ASR (Attack Surface Reduction) and EAF+ (Export Address Table Filtering Plus). ASR is similar to IE’s option to block outdated Active-X controls but can cover a wider range of exploits and protect the address spaces of Word, Excel and Powerpoint.
EAF+ improves on the existing EAF system and can work independently of the older option. It blocks attempts to access addresses exported from various system modules. In addition to blocking access to the Export Address Table from unknown code, it also blocks attempts by code from legitimate libraries that could be used by attackers for scanning the EAT.
These technologies make it harder for attackers to succeed in remote code execution exploits for newer versions of Windows. Older versions such as XP, however, don’t contain this anti-exploit technology leaving them more vulnerable.
You can access the full report in PDF format with details of the most common exploits on the ESET website.
Image Credit: Sergey Nivens/Shutterstock
-

Mini TV MK808B -- the low cost way to a smart TV [review]
Publié: janvier 9, 2015, 11:18am CET par Ian Barker

If you want the features of a smart TV but don't want to have to buy a new set or spend $99 on Fire TV then the MK808B, which offers Google TV for less than $35, might be the answer.
It's basically a tiny Android PC that you hook up to your TV set and your Wi-Fi to allow you to stream media from the web or from another device on the same network or via Bluetooth.
The back of the box spec looks impressive with a quad-core 1.5GHz processor, 1GB of RAM and the latest-but-one Android KitKat. It comes with an HDMI Cable, a power adapter, and a USB cable, plus there’s a slot for a microSD card if you want to expand the storage.
On the unit itself are a USB 2.0 port, an OTG port, a mini USB power port and an HDMI connector. You can use the USB to attach a variety of devices like webcams or external storage or you can plug in a mouse or keyboard to control the device. The Wi-Fi is dual-band to ensure a good signal and there’s built-in Bluetooth too which lets you stream media from other devices.
So much for the theory then, how does it work in practice? When you power up the device there's a few seconds delay while it boots and you're then presented with a chunky, tiled interface that looks a bit like Windows 8 but is no worse for that. Dig into the settings and you'll find there’s standard Android lurking underneath.
Setting it up and getting connected to your network is easy. The instructions leave a bit to be desired but the steps you need to take are mostly intuitive if you've used Android before.
You can share media with other devices via Miracast, DNLA or AirPlayer. There are also a number of pre-installed apps including NetFlix, YouTube, Skype and XMBC media player. Playback of streamed media from the web is smooth with good video and sound quality. I did find that it refused to play some YouTube videos though.
You can control the device by plugging in a USB mouse or keyboard, but it's better to install a remote control app -- a link is provided in the instructions -- on your Android smartphone. This makes navigation easier and leaves the USB port free to connect external storage or a a headset to use Google Voice commands.
Often what lets budget media devices down is the interface, but because it runs Android the MK808B has no such worries. If you don't like the standard apps you're free to install others you prefer. Add in ease of use and a smooth playback experience and you have to keep reminding yourself that this is a device that only costs $35.
Our review sample was supplied by GearBest.com and currently sells for $34.64. BetaNews readers can use coupon code MK808BCN at the checkout to get it for $29.98. The coupon expires on 31 March 2015.
-

Mini TV MK808B Plus -- the low cost way to a smart TV [review]
Publié: janvier 9, 2015, 11:18am CET par Ian Barker

If you want the features of a smart TV but don't want to have to buy a new set or spend $99 on Fire TV then the MK808B, which offers Google TV for less than $35, might be the answer.
It's basically a tiny Android PC that you hook up to your TV set and your Wi-Fi to allow you to stream media from the web or from another device on the same network or via Bluetooth.
The back of the box spec looks impressive with a quad-core 1.5GHz processor, 1GB of RAM and the latest-but-one Android KitKat. It comes with an HDMI Cable, a power adapter, and a USB cable, plus there’s a slot for a microSD card if you want to expand the storage.
On the unit itself are a USB 2.0 port, an OTG port, a mini USB power port and an HDMI connector. You can use the USB to attach a variety of devices like webcams or external storage or you can plug in a mouse or keyboard to control the device. The Wi-Fi is dual-band to ensure a good signal and there’s built-in Bluetooth too which lets you stream media from other devices.
So much for the theory then, how does it work in practice? When you power up the device there's a few seconds delay while it boots and you're then presented with a chunky, tiled interface that looks a bit like Windows 8 but is no worse for that. Dig into the settings and you'll find there’s standard Android lurking underneath.
Setting it up and getting connected to your network is easy. The instructions leave a bit to be desired but the steps you need to take are mostly intuitive if you've used Android before.
You can share media with other devices via Miracast, DNLA or AirPlayer. There are also a number of pre-installed apps including NetFlix, YouTube, Skype and XMBC media player. Playback of streamed media from the web is smooth with good video and sound quality. I did find that it refused to play some YouTube videos though.
You can control the device by plugging in a USB mouse or keyboard, but it's better to install a remote control app -- a link is provided in the instructions -- on your Android smartphone. This makes navigation easier and leaves the USB port free to connect external storage or a headset to use Google Voice commands.
Often what lets budget media devices down is the interface, but because it runs Android the MK808B has no such worries. If you don't like the standard apps you're free to install others you prefer. Add in ease of use and a smooth playback experience and you have to keep reminding yourself that this is a device that only costs $35.
Our review sample was supplied by GearBest.com and currently sells for $34.64. BetaNews readers can use coupon code MK808BCN at the checkout to get it for $29.98. The coupon expires on 31 March 2015.
-

XSS vulnerability uncovered in Microsoft Dynamics CRM
Publié: janvier 8, 2015, 4:40pm CET par Ian Barker

Information security company High-Tech Bridge has uncovered a flaw in the Microsoft Dynamics CRM package that could allow the insertion of malicious code.
The self-XSS issue isn't currently recognised by Microsoft itself as a flaw but could trick a logged in user into putting malicious HTML and script code into the 'newUsers_ledit' input field on vulnerable websites that are thought to be secure.
"Taking into consideration that same vulnerabilities were actively and successfully exploited by hackers in 2014, this XSS vulnerability is pretty serious, despite the 'low' category we assigned due to this being a relatively complex exploitation. I think that Microsoft's decision not to patch the vulnerability is wrong as, regardless of their general policy, they should think about their customers' security first and foremost," says Ilia Kolocheno, CEO of High-Tech Bridge and Chief Architect of ImmuniWeb. "Such vulnerabilities could potentially be ignored in the past, but not in 2015, especially in such popular and sensitive products as Dynamics CRM".
Dynamics CRM is used by the US government among others. High-Tech Bridge's security advisory says that it could be exploited using a social engineering technique to get a user to copy some seemingly legitimate text from a specially prepared malicious document to their clipboard and then paste it into the vulnerable web page.
It recommends that companies protect themselves by blocking access to the vulnerable script using a firewall or web server configuration as a temporary solution.
You can read the full advisory on the High-Tech Bridge website or there's a video explaining how it could be exploited below.
Photo Credit: Sergey Nivens/Shutterstock
-

Clarizen awarded patent for its email-based workflow system
Publié: janvier 8, 2015, 3:34pm CET par Ian Barker

There are a number of companies offering enterprise collaboration products, but Clarizen is among the first to be awarded a patent for its technology.
The patent relates to the company's InterAct email engine which lets users trigger specific project-related actions like approval processes, generating reports, creating new projects and other workflows through their email.
"This patent is an important technical milestone for Clarizen, one that has been in the making for several years," says Avinoam Nowogrodski, founder and CEO of Clarizen. "It underscores the significant investment we have made in continuous innovation to stay one step ahead of customer and market needs. The value the technology delivers is a strategic win for Clarizen's customers, and we look forward to sharing more patented innovations with them in the future".
Clarizen InterAct allows users to use their email as a routing system so they can generate an unlimited number of email addresses and associated actions, business and routing rules. Emails can be sent via Clarizen requesting an updated report and receive an automated reply with the report attached.
Issues can also be submitted to InterAct via email or a form, prompting the issue to be automatically added to the appropriate project with a notification sent to the project manager.
"Email is still by far the most used collaboration tool, but email was not really built to support collaboration (many-to-many). What Clarizen has done with this patent is part of a trend we are seeing where team members are moving from email to more context-based in-app communications," says David Coleman, senior research analyst at Gigaom Research and managing director of Collaborative Strategies, Inc.
You can find more information about InterAct on the Clarizen website.
Photo Credit: Arcady/Shutterstock
-

New mobile digital rights app launches but not for iPhone users
Publié: janvier 8, 2015, 1:11pm CET par Ian Barker

Digital rights campaigner Electronic Frontier Foundation has launched its own EFF mobile app with the aim of alerting users to issues and campaigns.
Users will get a notification and be able to one-click connect to the EFF action center to help fight for freedom online. Unless they happen to be iPhone users.
Writing on the EFF blog Corrynne McSherry the foundation's intellectual property director says, "Sadly, though, we had to leave out Apple devices and the folks who use them. Why? Because we could not agree to the outrageous terms in Apple's Developer Agreement and Apple's DRM requirements".
The blog post highlights a number of terms in Apple's Developer Agreement including the ban on reverse engineering and exclusive distribution restrictions as being bad for both developers and users.
The EFF also objects to Apple's imposition of DRM, McSherry says, "Contract restrictions aside, the final barrier was knowing that we’d be required to include a form of Digital Rights Management (DRM). DRM means that Apple is putting technical restrictions on what you can and can’t do with your app. When we create tools for EFF, we want them to be broadly available to others to use, adapt, and customize".
It has started an online petition to Apple asking the company to revisit its developer agreement.
Meantime if you're an Android user you can download the EFF app from the Play Store and start receiving alerts. Presumably these will include updates on how the Apple petition is progressing so you can keep your iPhone owning friends in the loop.
Image Credit: iQoncept/Shutterstock
-

Poor mobile customer service harms engagement
Publié: janvier 7, 2015, 3:29pm CET par Ian Barker

No matter how effective a business is at selling products or services it's the quality of customer service that often determines how consumers feel about it.
A new report from research company Gartner looks at the importance of mobile customer service and how it will need to adapt in the future.
Although automation of support tasks may reduce the number of interactions, Gartner reckons that by 2017 a third of all customer service queries will still need human input. This is down from the 60 percent that needed human input in 2014 but it will still require companies to retain a core of trained customer service representatives.
"Businesses need to focus on what key customer experiences would benefit from customer engagement with a human," says Michael Maoz, vice president at Gartner. "It is important to poll customers and internal stakeholders such as those in marketing, sales, customer support and inventory/shipping/billing, where the availability of a human customer support representative can mean the difference between a sale or no sale, the acceptance of an offer or its rejection, and/or a quality customer experience".
The Internet of Things is set to play a part too. By 2018 it's estimated that five percent of support calls will be initiated by internet connected devices. "The explosive growth of the IoT and associated use cases will bring a transformational change in the customer service space". says Olive Huang, research director at Gartner. Industries including healthcare, banking, insurance and retail are expected to lead the way in this trend.
Growth in the use of mobile devices will also lead to more video chats being used for resolving customer service issues. Gartner estimates that more than 50 of the 500 largest global businesses will introduce video-based chat for customer-facing interactions by 2018 and this is set to double in three years.
"Video chat provides customers with a richer sense of presence, personalized experience by helped coordination of communication and the support of emotional expression, and the real-time sharing of content," says Brian Manusama, research director at Gartner.
More detailed analysis is available via the Gartner website and analysts will further discuss mobile CRM trends at the Gartner Customer 360 Summit to be held in Tokyo next month.
Image Credit: Rawpixel / Shutterstock
-

Time to get Intel outside as the company targets wearables
Publié: janvier 7, 2015, 12:32pm CET par Ian Barker

Chip maker Intel is using the 2015 CES to announce its plans for moving into the wearable technology sector.
These include the Curie, a button-sized hardware module, and a collaboration with sports sunglasses brand Oakley.
"The rise of new personal computing experiences, intelligent and connected devices, and the wearable revolution are redefining the relationship between consumers and technology," says Brian Krzanich, Intel CEO in his keynote address. "Our goal with Intel technology is to help solve real problems and enable experiences that are truly desired by people and businesses. In order to do this, we must also do more to lead the growth of diversity and inclusion within the technology industry. Women and under-represented minorities will continue to play a greater role as consumers, influencers, creators and leaders".
The Intel Curie is a tiny hardware device based on the company's first purpose-built system-on-chip (SoC) for wearable devices. The module is scheduled to ship in the second half of this year -- subject to getting FCC approval -- and includes the Intel Quark SE SoC, plus Bluetooth low-energy radio, sensors and battery charging.
Intel has been pursuing collaborations with a number of different fashion and lifestyle brands and Krzanich announced a new tie up with Oakley. The two companies are said to be working on an intelligent product, available later this year, designed to enhance athletic performance.
Also highlighted was Nixie, winner of Intel's 2014 Make It Wearable challenge. Nixie is a camera that's worn as a bracelet but can fly off to take photographs. You can see it in action on YouTube below.
Aside from wearables, Krzanich reaffirmed Intel’s commitment to diversity with the announcement of a $300 million fund to help recruit and retain more women and under represented minorities. "We're calling on our industry to again make the seemingly impossible possible by making a commitment to real change and clarity in our goals," says Krzanich. "Without a workforce that more closely mirrors the population, we are missing opportunities, including not understanding and designing for our own customers".
You can find out more about the Make It Wearable project on Intel's site.
Image Credit: Intel
-

When the going gets tough the hard drives get rugged
Publié: janvier 6, 2015, 3:31pm CET par Ian Barker

More than ever before we expect our technology to come with us wherever we go and more importantly be able to survive the journey.
The weakest link in the past has usually been storage because even SSDs don't take too kindly to rough treatment. Storage company G-Technology is using CES to launch a solution in the form of its range of rugged drives.
There are two models, the G-DRIVE ev ATC which has an all-terrain case that will survive a drop of up to 2 meters, is dust and water proof and will float if dropped in water. The 1TB drive has a transfer rate of 136MB/s and comes with a three-year warranty. It's available as USB 3.0 or Thunderbolt versions at $179.95 (£139.95) or $229.95 (£179.95) respectively. For people who already own a G-DRIVE the case is available separately.
The second device is the G-DRIVE ev RaW fitted with a removable rugged bumper making to drop-proof up to 1.5 meters. Available in 500GB or 1TB versions it too has a three-year warranty. Prices are $99.95 (£79.95) for 500MB or $129.95 (£99.95) for 1TB.
"Whether you’re capturing a professional skier flying down the slopes or your family's beach vacation, keeping your data safe is essential," says Mike Williams, vice president and general manager at G-Technology. "We know how precious data is for professionals and consumers alike, and we've developed our rugged series to keep up with even the most active lifestyles and professions, so you can focus on capturing once-in-a-lifetime moments without worrying about your data".
The G-DRIVE ev RaW will be available this month with the ev ATC following in February. For more information visit the G-Technology website.
-

Let's work together for the Internet of Things says Samsung CEO
Publié: janvier 6, 2015, 11:55am CET par Ian Barker

It's been a common joke in the technology industry for many years that the wonderful thing about standards is that there are so many to choose from.
But whilst it may be a joke, in the past conflicting standards have led to very real issues when it comes to getting systems to work together. In the modern era when we increasingly expect things to 'just work' compatibility issues are becoming less acceptable.
Samsung's president and CEO BK Yoon used his keynote speech at 2015's CES to call for greater openness and collaboration across industries to unlock the possibilities of the Internet of Things.
He also said that the Internet of Things must fit into people’s lifestyles, "The Internet of Things is not about 'things'. Instead, it is about people. Each person is at the center of their own technology universe, and the IoT universe will constantly adapt and change shape as people move through their world".
As part of Samsung’s commitment to making the IoT work, Yoon announced a timetable that will see all the company's TVs become IoT enabled by 2017 and all Samsung devices IoT ready within five years. He also stressed the importance of developers in making all of this work and announced a $100 million investment in Samsung’s developer community this year.
Sensors are key to making the IoT work and Samsung is working on chips, such as the embedded package on package (ePOP) and the Bio-Processor, which are energy-efficient and compact enough to go into a wide range of devices, especially wearables.
"Expanding the devices in the IoT ecosystem and the components that power them is the first step in fulfilling the promise of the Internet of Things," says Yoon. "Samsung already has a broad range of IoT devices. Last year, Samsung delivered more than 665 million products, and this number is set to increase. We have already begun to unlock the value hidden in connected devices and all the everyday objects around us".
The importance of openness was emphasized too. Alex Hawkinson CEO of SmartThings joined Mr Yoon on stage and stressed that, "Any device, from any platform, must be able to connect and communicate with one another. We’ve worked hard to accomplish this, and are committed to putting users first, giving them the most choice and freedom possible. The SmartThings ecosystem is now compatible with more devices than any other platform".
Samsung believes that the IoT will have an impact far beyond the electronics industry, Yoon says, "I know in my heart that neither one single company nor one industry alone can deliver the benefits of the Internet of Things. To create this IoT universe, we have to see the potential of the Internet of Things across all kinds of industries. Only if we work together can we improve people’s lives".
You can see highlights from the speech on the Samsung website.
Image Credit: Samsung
-

Tablet sales set to stay slow in 2015
Publié: janvier 5, 2015, 3:20pm CET par Ian Barker

The tablet market experienced something of a slump in 2014 and things don't look like being much better this year according to a new report by research specialists Gartner.
It estimates that tablet sales will reach 233 million units in 2015, an increase of only eight percent over last year's figure. Worldwide combined shipments of devices (PCs, tablets, ultramobiles and mobile phones) for 2015 are estimated to reach 2.5 billion units, an increase of 3.9 percent over 2014.
"The collapse of the tablet market in 2014 was alarming", says Ranjit Atwal, research director at Gartner. "In the last two years global sales of tablets were growing in double-digits. The steep drop can be explained by several factors. One is that the lifetime of tablets is being extended -- they are shared out amongst family members and software upgrades, especially for iOS devices, keep the tablets current. Another factor includes the lack of innovation in hardware which refrains consumers from upgrading".
The strongest percentage growth is set to come from the premium ultramobile sector though sales numbers here are still relatively small, 39,000 in 2014, expected to reach 62,000 this year and 85,000 in 2016.
The mobile phone market is set to grow by only 3.7 percent in 2015 and reach two billion units in 2016. "The smartphone market is becoming polarized between the high- and low-end market price points", says Annette Zimmermann, research director at Gartner. "On one hand, the premium phone with an average selling price at $447 in 2014 saw growth dominated by iOS, and on the other end of the spectrum you have Android and other open OS phones' growth area in the basic phone segment, where the average phone costs $100. For the midrange smartphones, the market opportunity is becoming increasingly limited".
Android is expected to continue its rapid growth -- it reached a billion shipments in 2014 -- with a further 26 percent increase this year. Windows is expected to stage something of a comeback too. "From 2015, we expect Windows to grow faster than iOS, as the PC market stabilizes and the challenge for the next iPhone to find significant growth becomes greater, narrowing the gap between the two operating systems", says Atwal.
All of this should prove good for consumers as manufacturers fight to attract buyers for their devices, so keep a look out for bargains.
Image Credit: vinzstudio / Shutterstock
-

Is Facebook more useful for professionals than LinkedIn?
Publié: décembre 30, 2014, 1:44pm CET par Ian Barker

When the LinkedIn network for professionals launched it was sometimes referred to as social networking for grown ups. But is it really any better than Facebook for business users?
The UK's Brighton School of Business and Management has produced an infographic comparing the relative merits of the two sites and it shows that Facebook may be getting overlooked as a business tool.
With over 300 million members LinkedIn is by no means small, but Facebook's 1.35 billion puts it in the shade. The breakdown of those members is interesting, whilst Facebook as a 50/50 gender split, a majority of LinkedIn users (57 percent) are female. There are also, a little surprisingly perhaps, more people aged over 35 on Facebook than on LinkedIn.
When it comes to business pages, again Facebook wins the numbers game with 25 million to LinkedIn's four million. For advertising too Facebook looks to offer better value with a higher click through rate for your spend.
Where LinkedIn has the edge is in B2B networking and recruitment, though the graphic shows that Facebook has useful benefits in these areas too.
You can see the full infographic with more interesting statistics on the two sites below.

Image Credit: Oleksiy Mark / Shutterstock
-

My favorite tech products of 2014 [Ian]
Publié: décembre 29, 2014, 8:31pm CET par Ian Barker

When your working life involves being bombarded with information about new technology it's easy to become a bit blasé about it all. For something to really impress therefore it has to be pretty good or fill a niche that others have missed.
You've already read Alan and Wayne's picks for the year, so here are some of the things that ticked the right boxes for me in 2014.
Fire HDX 8.9
 The second generation of the Fire HDX 8.9 did more than just drop the Kindle bit from the product's name. It built on the already impressive capabilities of the original with a faster processor and graphics and the latest 802.11ac wireless.
The second generation of the Fire HDX 8.9 did more than just drop the Kindle bit from the product's name. It built on the already impressive capabilities of the original with a faster processor and graphics and the latest 802.11ac wireless.The screen is unchanged from the first version but it still offers one of the best viewing experiences of any tablet even though others are starting to catch up with its 339ppi pixel density. If there's a downside it’s that you’re tied to Amazon's ecosystem rather than having access to the Google Play store but if you can live with that it’s an impressive piece of kit.
Motorola Moto E
 The Moto E is never going to compete with the latest iPhone or Galaxy, but that's not what it's about. The idea is to take smartphone ownership into a whole new marketplace, aiming at people who may be switching from older basic handsets.
The Moto E is never going to compete with the latest iPhone or Galaxy, but that's not what it's about. The idea is to take smartphone ownership into a whole new marketplace, aiming at people who may be switching from older basic handsets.Okay, so there's no 4G and no front-facing camera -- so no selfies or video calls. The Wi-Fi is only 802.11n rather than the newer, faster 802.11ac and the rear camera is 5MP, which is okay but not exceptional. It's nicely designed though with swappable rear panels and a family resemblance to the Moto G so it's a budget phone you won’t be ashamed to be seen with.
ChargeKey
 The ChargeKey is a simple idea, a USB charger cable that you can fit on a keyring, but its very simplicity is what makes it so clever. Being caught with an uncharged device is one of the great 21st century problems. The ChargeKey means that as long as you have a USB socket -- on a PC or in your car -- you always have the means to replenish the batteries in your smartphone, MP3 player, Kindle or whatever.
The ChargeKey is a simple idea, a USB charger cable that you can fit on a keyring, but its very simplicity is what makes it so clever. Being caught with an uncharged device is one of the great 21st century problems. The ChargeKey means that as long as you have a USB socket -- on a PC or in your car -- you always have the means to replenish the batteries in your smartphone, MP3 player, Kindle or whatever.Sony Action Cam Mini
 Whilst smartphones have been growing in 2014 thanks to demand for bigger screens, Sony has been busy making its video camera smaller. At around three inches long, an inch and a half high and an inch wide it’s small enough to slip into a pocket. Yet it still packs an 18.6 megapixel image sensor that can handle resolutions up to 1080p at 60fps.
Whilst smartphones have been growing in 2014 thanks to demand for bigger screens, Sony has been busy making its video camera smaller. At around three inches long, an inch and a half high and an inch wide it’s small enough to slip into a pocket. Yet it still packs an 18.6 megapixel image sensor that can handle resolutions up to 1080p at 60fps.The trick to making it smaller is that the LCD display is taken off the camera and put on a separate remote that you can wear on your wrist. You also have the option to connect to your smartphone and control the camera from that.
Software
On the software front Windows 10 previews came along and surprised with a number-skipping name but otherwise looked and felt like Windows 8.1 with a few tweaks, though it works well enough. Android Lollipop brought in a sleeker interface and improved notifications but more importantly under the hood changes for faster app performance and improved battery life.
Do you have any particular technology favorites from the last year? Let us know via the comments.
Image Credit: StockThings / Shutterstock
-

It's beginning to look a lot like Christmas 2024
Publié: décembre 23, 2014, 1:45pm CET par Ian Barker

You send a command from your smartphone and your house automatically decorates itself with a holographic Christmas tree complete with decorations and a suitably conifer-like smell.
Sound like science fiction? Maybe, but this is among the predictions by the authors of a new book that looks at how technology is changing our lives and how we do business.
Here are some more of their views on what Christmas might look like in ten years time. As customization capabilities become more sophisticated we'll see more and more things like clothes and shoes being tailor made for the individual. And it could be the end of sending your Christmas gifts through the post. Affordable 3D printing means simply emailing a code to someone so they can create their own present at home.
3D printing will also lead to a new cottage industry of designers simply selling the code needed to print out their products rather than doing their own manufacturing. The authors also predict the growth of a 'sharing economy' which will reduce the number of products we own as we share more details online via Facebook and Twitter. For example, cars or power tools will become shared items, used when and where needed.
For elderly members of the family it might be possible to get a robot companion able to emotionally connect with its owner and play a comprehensive role as a friend and helper.
Because we'll know much more about our friends and family thanks to social media it will be possible to create gift giving algorithms to ensure everyone gets the right present with no risk of someone else buying them the same thing.
As physical products become less valuable their attractiveness as gifts will decline. It will therefore become more common to give services as gifts, things like meals in restaurants or activity days.
If you want to read more about this sort of stuff including predictions for many areas of life, not just Christmas, the book is called iDisrupted by John Straw and Michael Baxter and is available now via Amazon.
Image Credit: Kirill_M / Shutterstock
-

North Korea's internet disrupted -- is this the start of a cyber war?
Publié: décembre 23, 2014, 11:03am CET par Ian Barker

North Korea experienced a complete internet outage for several hours last night before links were restored early this morning.
With the North Koreans at the center of the political storm over the Sony hack could this be some form of revenge attack?
Whether or not you believe that the Koreans were behind the Sony episode -- and some security experts like Graham Cluley are sceptical -- the timing of this attack is interesting. It also comes just a day after the leaking of information from South Korea’s nuclear power operator.
There are therefore potentially two sources that would like to make some form of response. Plus North Korea's internet is delivered via China. The Beijing regime has become increasingly frustrated by the rogue state's behavior, so could the Chinese be sending a message?
On the other hand, is this nothing more than hackers carrying out a DDoS attack? "According to public reports, North Korea’s total bandwidth is 2.5 gigabits per second, with a single Internet Service Provider STAR-KP, and a single IP range consisting of 1024 addresses. We routinely see attacks of 10 to 20 gigabits against our commercial clients, with those of 100 gigabits per second no longer uncommon," says Ofer Gayer, security researcher at Incapsula. "Even if North Korea had ten times their publicly reported bandwidth, bringing down their connection to the Internet would not be difficult from a resource or technical standpoint".
By relying on a single service provider and a limited range of IP address North Korea has left itself particularly vulnerable to attack.
At the moment we just don't have enough information to know who is behind this outage -- DDoS attacks are notoriously hard to trace anyway.
In the meantime feel free to discuss your conspiracy theories below.
Photo credit: Thomas Reichhart/Shutterstock
-

Only half of companies take DDoS seriously
Publié: décembre 22, 2014, 3:12pm CET par Ian Barker

DDoS attacks can have a serious effect on businesses, yet according to a new survey by Kaspersky Lab and B2B International only 50 percent of companies regard countering DDoS attacks as an essential part of their IT security.
This is despite the fact that the average cost of a DDoS attack to small and medium businesses is put at $52,000. For larger companies the average is $444,000.
The damage isn't only financial, 38 percent of businesses believe that a DDoS attack has damaged their company's reputation. 29 percent reported that a DDoS attack damaged their credit rating, and 26 percent reported an increase in their insurance premiums as a result.
How seriously the threat of attacks are taken does vary by industry too. 60 percent of financial institutions, energy companies and utility services are conscious of the need of protection against DDoS attacks.
However, countermeasures against DDoS were named as important by 53 percent of telecom companies, 50 percent of IT businesses, 41 percent of e-commerce and only 38 percent of media companies. This is despite the media being one of the four most frequently attacked sectors.
Size matters too, only 38 percent of small businesses consider protection against DDoS attacks an important component of IT security, compared to 60 percent of big companies.
Eugene Vigovsky, head of Kaspersky DDoS Protection says, "Even if a company does not have a public-facing website, its finances and reputation can be seriously affected by DDoS attacks. It is known that DDoS can be organized not only to incapacitate online services or for ransom, but also to mask other cybercriminal activities such as targeted attacks on the company to gain access to its confidential data. Therefore, protection against DDoS attacks is not reinsurance, but a logical precaution important for any company that has business processes dependent on Internet services. To provide this protection, companies should use specialized solutions from vendors who have a wealth of experience and expertise in combating cyberthreats".
You can find out more in the full report which is available on the Kaspersky Lab website.
Photo Credit: Duc Dao / Shutterstock
-

How your data will be at risk in 2015
Publié: décembre 19, 2014, 3:36pm CET par Ian Barker

The world of information security is, as we know, a constant arms race between the hackers and cyber criminals and the protection industry.
Since the focus has turned to making money rather than simply causing disruption it's become big business too. 2014's string of retail and other security breaches is testament to this.
The money angle also means that trends in security tend to follow trends in the wider industry. So what do the experts think are going to be the key targets for next year’s attacks and how do they see the industry adapting?
Kaspersky Lab expects payment systems to come under increasing threat as cybercriminals seek to monetize their efforts. It predicts increased levels of attacks against NFC payment systems as technologies like Apple Pay become more popular.
Kaspersky also sees the internet of things as being ripe for exploitation. It expects to see networked printers and other connected devices come under attack as a way of gaining access to corporate systems. ATM and point of sale systems could come under increased threat from advanced persistent threats (APTs) seeking to gain access to their processors. Many of these systems still run variants of XP leaving them vulnerable.
More malware targeted at Mac systems is on the cards too. Although the closed ecosystem makes it harder for malware to take hold, Kaspersky's blog notes that, "[...] there remains a subsection of users who'll gladly disable Mac OS X security measures -- especially people who use pirated software. This means that those looking to hijack OS X systems for a variety of reasons know that they simply need to bundle their malware with desirable software (probably in the form of a key generator) to enjoy widespread success". Since Macs are less likely than PCs to have antivirus solutions installed a successful infection can go undetected for longer.
The success of the recent Sony attack will lead to more of the same according to Jason Lewis, Chief Scientist, at threat intelligence company Lookingglass. "As with all high profile attacks, security spending will increase as a result of the Sony compromise. The cyber impact on PII and Sony employees will force companies to re-evaluate their security. While insider threat solutions have grown in popularity, the trend of external threats moving inside the enterprise is growing".
There will be a greater need for businesses to focus on incorporating security into all aspects of their operations says Shawn Marck, CSO and co-founder of DDoS protection company Black Lotus. "Since cybercriminals don’t limit themselves to targeting just one component of a company, a company can't limit itself to only protecting its offerings and departments in isolated manners. IT and security teams need to investigate every aspect of their enterprise to identify each area that needs to be taken into account for an effective cybersecurity strategy."
Where mobile security is concerned, document sharing service WatchDox sees technology taking a role in keeping company data safe. "In 2015, we'll progress into what Gartner calls the new era of mobile security: making work safe on untrusted devices. Thanks to developments in iOS and Android Lollipop, developers can now create apps that self-destruct in the event that they're opened on a rooted or jailbroken device in order to keep company data safe. This means enterprises can worry less about what devices employees are using, and focus instead on apps and software that can keep data safe wherever it travels", says Ryan Kalember, chief product officer.
Open source software is likely to play a big part in helping companies remain secure too. Oliver Thierry, chief marketing officer of social collaboration specialist Zimbra says, "We can expect to see an uptick in the interest in and implementation of open source software solutions due to the increased continuity and control open source software provides over proprietary solutions. In fact, a November 2014 Ponemon Institute study of U.S. IT professionals found that 74 percent of respondents believe that commercial open source software offers better continuity and control than proprietary software."
Whatever the coming year has to bring one thing is fairly certain, at some point there will be a Heartbleed moment that nobody has foreseen at all.
Image Credit: northallertonman / Shutterstock
-

Who's afraid of the big bad bot?
Publié: décembre 18, 2014, 4:45pm CET par Ian Barker

Web security specialist Incapsula has released its 2014 annual Bot Study which reveals that 56 percent of website traffic is accounted for by bots.
That's down from 61.5 percent on last year's study, however the number of 'bad' bots posing as humans has increased significantly.
The number of impersonator bots has risen by 15 percent in the two years since Incapsula began its annual study and by 10 percent in 2014. These include DDoS bots, bots masked by proxies and bots that are trying to avoid security measures by using false identities.
The overall decline in bot traffic is, says Incapsula, mainly down to the drop in bots associated with RSS. Google stopped crawling RSS feeds some time ago as its place has increasinngly been taken by social media.
Interestingly it's smaller websites that receive the most bot traffic, reaching 80 percent this year for those with fewer than 1,000 daily visitors. Large sites by contrast -- those receiving more than 100,000 daily visitors -- receive only 56.2 percent bot visits.
The proportion of bad bots stays pretty much the same, however, product evangelist Igal Zeifman writing on the Incapsula blog says, "...the average percentage of bad bots consistently hovers around the 30 percent mark, regardless of website size or popularity. In absolute terms, Incapsula can state that malicious bot traffic grows in an almost exact proportion to a site’s human traffic".
You can see a summary of the report in infographic form below and find out more in Incapsula's blog.
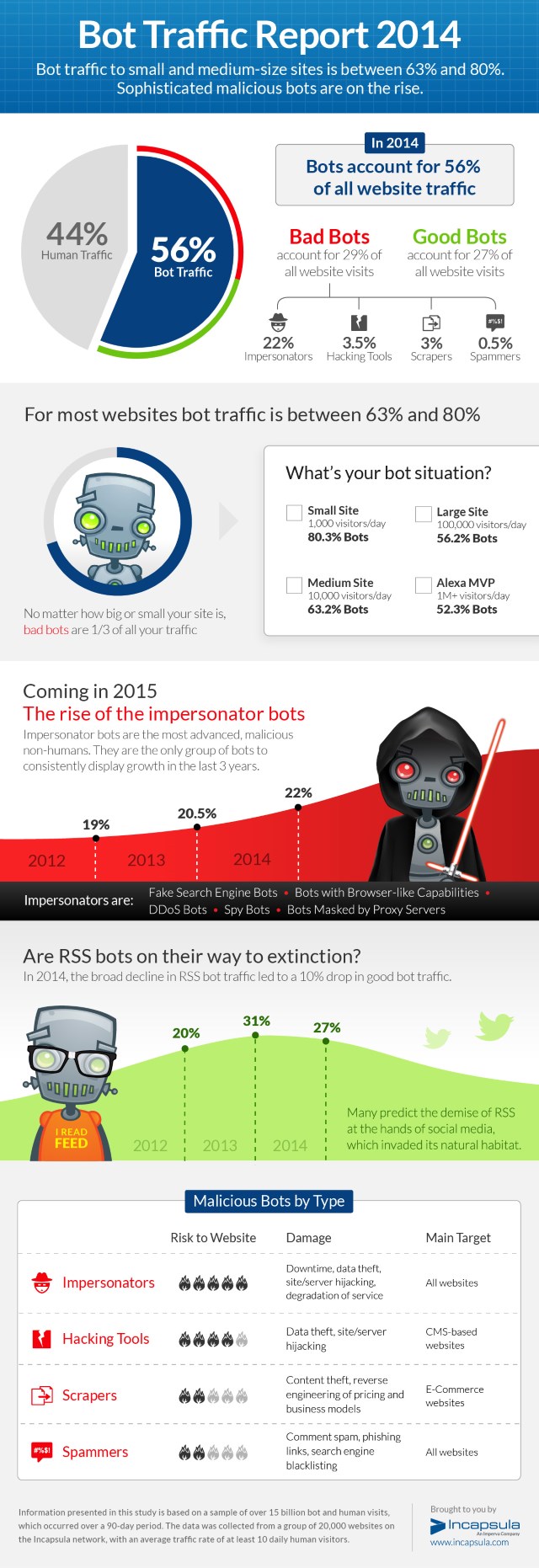
Image credit: Gunnar Assmy/Shutterstock
-

Self service platform helps cut online help desk requests
Publié: décembre 18, 2014, 3:20pm CET par Ian Barker

Ask anyone who has worked on a help desk and they'll tell you that a lot of their time is spent on solving the same problems.
In order to reduce the help desk workload for online businesses and allow users to solve straightforward issues themselves, contextual answer specialist AnswerDash has announced the integration of its technology with Zendesk.
The integration makes it easy for websites to display help content from Zendesk Help Center as contextual Q&A that appear on relevant objects on a web page. The effect is that website users have access to Help Center content wherever they have questions, with just a click of the mouse and without having to type search queries. Links from revealed content connect users back to Help Center, making it easy to directly access full Help Center articles.
"For most online businesses, 80 percent of support ticket volume is due to just 20 percent of the most frequently-asked questions, leading to customer service agent fatigue and inability for support teams to cost-effectively scale," says Jake Wobbrock, CEO and co-founder of AnswerDash. "Our integration with Zendesk helps transform traditional assisted customer service into highly-efficient customer self-service, reducing the number of help tickets and enabling support teams to scale".
AnswerDash's self-service technologies allow users to get answers to their commonly asked questions in the context of existing webpages, without having to visit separate knowledge bases. Customer service staff can sync their Zendesk articles to AnswerDash and syncing take place every 10 minutes to ensure the most recent content is available.
Any new questions raised via AnswerDash are automatically raised as Zendesk tickets and the answers linked back as they're solved.
You can find out more and try out how it works for yourself on the AnswerDash website.
Image Credit: lucadp / Shutterstock
-

How the way you work is going to change in 2015 [Q&A]
Publié: décembre 18, 2014, 10:35am CET par Ian Barker

Enterprise computing is more and more centered around the user, but how will this trend affect the workplace and what changes will it make to productivity and the way systems are managed and delivered?
We spoke to Torsten Volk, VP of product management, cloud at business software specialist ASG Software Solutions to find out.
BN: What do you think will be the main trends for IT in the workplace during 2015?
TV: In 2015, the workplace will become more and more end user centric. Business staff, developers and IT operators will receive an individualized user experience that enables them to be more productive. All three of these user groups will be able to receive a more consistent interface from any PC or mobile device, with all the applications, content, services and business data they require. This means, 2015 will be the year where enterprise IT becomes much more independent of the OS and truly focused on delivering a role based and unified user experience.
BN: Are we going to see a continuing shift towards the cloud and SaaS product delivery?
TV: The short answer is 'yes'. In many cases, the economics of delivering software via public cloud cannot be beat. However, we can expect a paradigm shift toward a truly policy driven approach to software delivery. Each placement decision -- physical, virtual, private cloud or public cloud -- comes with different parameters in terms of cost, compliance, security and performance attached to it. The only way to ensure consistent delivery is to introduce a policy engine that 'intelligently' decides where to place an application. The end user should be entirely removed from this decision process.
BN: How can dynamic workspaces make things easier for the user?
TV: Dynamic Hybrid Workspaces go significantly beyond the application centric approach to enterprise computing by offering a truly unified dashboard, where end users no longer have to worry about where their apps, services, data or content are coming from. These placement decisions are made by a policy engine that works its magic in the background. To optimally complete their daily tasks, end users will no longer have to log into multiple applications with different user interfaces. Instead they will receive one unified dashboard with services and apps that exchange content to enable truly business driven computing.
BN: Can this work with a range of different devices in a BYOD environment?
TV: The idea is to provide the same user experience independent of device and operating system. Whether or not content can be accessed will ultimately depend on compliance and security policy. The CFO should not be able to review payroll data on the train, where his iPad might be stolen. Context sensitive computing will become a standard, freeing users from the limitations of individual Operating Systems and providing the ultimate level of control and governance to the IT department.
BN: Will offering users a 'self service' approach to installing apps help reduce support workloads or just add more complication?
TV: The workspace aggregation principle enables end users to request and receive apps without a complex installation procedure. Of course, depending on cost and other considerations, there will be workflows that enable IT or LOB management to approve the delivery of certain costly applications or services. However, the actual delivery will be automated and shift more and more toward virtualized apps and services that can easily scale.
BN: Can using hybrid workspaces help businesses control their software licensing costs?
TV: Yes, the idea is to have one central place -- the workspace -- to monitor user behavior. If certain apps and services are not used, a workflow can be triggered to ask the user whether the license could be returned to the pool. The key is the tight integration with a software asset management solution, to prevent licensing violations before they occur and to enable IT to govern the newly introduce self-service paradigm. Simply letting end users order apps and services in a self-service manner does not work without the right checks and balances in place. Workspaces represent the central hub, where the optimal degree of license control can be applied and enforced.
Photo Credit: wavebreakmedia/Shutterstock
-

Sinch enables low-cost SMS integration for apps and websites
Publié: décembre 17, 2014, 6:01pm CET par Ian Barker

Businesses are increasingly turning to mobile to communicate with both customers and employees. But whilst attention tends to be focused on apps, SMS messaging still has its place.
Communications platform Sinch is announcing the launch of its SMS API, making it easier for developers to integrate SMS capability into their apps and websites.
Previously integrating SMS capability has been a difficult challenge for developers, involving deals with SMS termination providers, then managing the back-end operation, which can require a major commitment of resources.
Sinch offers a simple, affordable route to in-app SMS communication. Features on offer include the ability to notify customers or users instantly without relying on push notifications. It's useful for marketing campaigns and to drive downloads by sending links to apps. It can also be used to enable two-factor authentication to verify user login details. Analytics allow an at-a-glance view of how many messages have been sent successfully delivered.
"We're in a great position to help developers take advantage of huge time and cost savings while implementing a much needed communication layer into their offerings," says Daniel Forsman, COO of Sinch. "Sinch takes all the hassle out of the integration process, so new features can be added quickly and securely. By implementing new communication features, not only can developers create richer apps, they can help drive up active users and time spent within their products".
One of the first customers for the SMS API is Swedbank, one of Sweden's largest banks which is now using Sinch to send fleet management notifications to the 15,000 drivers of its company cars. "The Sinch SMS API was really easy to implement and did just what I needed," says Robert Bergman, head of fleet management at Swedbank.
You can find more information on the SMS API on the Sinch website.
Image Credit: Bloomua / Shutterstock
-

35 percent of all security breaches take place in higher education
Publié: décembre 17, 2014, 3:09pm CET par Ian Barker

Higher education institutions with their rapid turnover of students' devices each year present particular problems when it comes to protecting data.
A new infographic from enterprise security and backup specialist SysCloud looks at the risks higher education bodies face and how they can improve their levels of protection.
Amongst the findings are that there have been over 500 security breaches at more than 320 higher education institutions since 2005 -- that's around one a week. Also 35 percent of all breaches take place in higher education.
The most common cause is hacking or malware on 36 percent, followed by unintended disclosure on 30 percent. Portable devices are more likely to be the source of a breach than fixed workstations.
Interestingly the higher you go up the education ladder the more likely a breach is to occur with 63 percent happening at doctoral level. Maybe their minds are on higher things?
The key challenges for IT professionals in higher education are seen as protecting data and intellectual property, balancing productivity and protection, and meeting compliance standards. The graphic also recommends five ways in which higher education institutions can strengthen their protection.
You can see the full infographic below.
Image Credit: hxdbzxy / Shutterstock
-

Avast wants beta testers for its business security software
Publié: décembre 16, 2014, 2:59pm CET par Ian Barker

Avast has long been a favorite with home PC users thanks to its free antivirus offering, and protects 175 million computers worldwide. It also launched a free mobile product in 2011 and now protects around 50 million smartphones too.
In 2015 it's looking to move into the business market and is seeking beta testers to help perfect its product before launch.
Avast For Business will offer free business-grade security from the cloud for any number of devices. It's designed to protect devices in the background without being intrusive and will protect both Windows and Mac devices. There's a Secureline option as well to protect business users when they're on public Wi-Fi connections. Cloud-based controls allow system admins to upgrade and add new features to protected systems.
Testers get early access to pre-release versions of the Avast for Business product and will be able to make suggestions for improvements and additional features. They'll also be rewarded for their efforts with three months of the product's Premium service for free when it’s launched in 2015.
For more information and to sign up to take part in the beta program you can visit the Avast website.
Image Credit: soliman design / Shutterstock
-

New performance testing tool brings added speed and flexibility
Publié: décembre 15, 2014, 5:02pm CET par Ian Barker

With increasing pressure to produce new apps to meet customer demand, testing is vital as problems can lead to the loss of customers and revenue.
Yet the test process can often prove a bottleneck as the tools involved are cumbersome and can struggle to cope with modern complex apps and sites.
Website and app performance testing pioneer Appvance aims to streamline the process with the launch of Appvance PerformanceCloud 2 (APC2), the next generation of its flagship testing platform.
Its advanced feature set allows for test teams to develop complex and comprehensive testing scenarios. It also allows the re-purposing of functional tests to data-driven performance tests all with detailed simulated user controls. Test scripting with APC2 has been found in independent benchmarks to be up to 20x faster than other tools.
"The performance testing market has seen far too many over-hyped tools touting incomplete solutions that only address protocol-level issues and offer limited results that don't provide the beginning-to-end insight that professional testers need," says Srikar Achanta, Applications Engineering Manager at Appvance. "APC2 is the first platform to offer serious testers the comprehensive breadth of features required to drive website and app performance on a day-in, day-out basis. APC2's beginning-to-end testing platform in the first technology to properly address the user experience level (UX), giving testers the most realistic test scenarios possible to mimic real-world user behaviors at scale and identifying client side code issues before launch".
APC2 offers a wide range of features including advanced analytics to identify performance issues, improved cloud support giving testers a wider array of Amazon Web Services instances for load generation, and offering new capabilities for IBM SoftLayer cloud.
Testers can gauge response times over simulated 3G, 4G, LTE or Wi-Fi network bandwidths. There's also support for deeper testing of Java-based applications. For testers of large-scale, enterprise-grade apps and websites, APC2 allows test scenarios to be created in hours, instead of days or weeks, enabling performance issues to be located quickly with little or no coding necessary.
You can find more information and request a free trial on the Appvance website.
Image Credit: alphaspirit / Shutterstock
-

Enhanced Aerospike speeds up big data deployment
Publié: décembre 15, 2014, 3:44pm CET par Ian Barker

Businesses are keen to harness the benefits of big data, but traditional database solutions are often confined by their design, making them hard to scale.
Aerospike which claims to be the world's fastest database has unveiled new features and enhancements to its product to improve performance, streamline deployment and breed a new generation of real-time, context-driven applications.
The latest release of the open-source, flash-optimized, in-memory, NoSQL database brings new clients, easier installation and deployment, storage and performance improvements, enterprise security enhancements and Hadoop integration. Aerospike's speed, scale and simplicity make it possible for organizations of all sizes to innovate with new applications that drive improvements, and enable bottom-line savings.
"Big data is big context, and organizations looking to harness the power of real-time context to personalize the user experience for millions of consumers across billions of devices have a small window of opportunity for success," says Monica Pal, CMO of Aerospike. "Aerospike's next-generation, NoSQL database is poised to lead the way as startups and enterprises alike choose its technology as the context store and system of engagement for consumer-facing applications. With Aerospike, companies can turn insights into action, reach consumers with the right message right now and scale with the best price to performance ratio, making it a no-brainer for today’s disruptors".
Unlike first-generation NoSQL databases and traditional in-memory technologies, Aerospike is self-managing and scales on a handful of servers instead of hundreds. Enhancements include more flexible development with upgrades for popular clients and a beta Ruby client. Deployment is simplifies with Docker containers and Click-to-Deploy on the Google Cloud Platform.
Storage and performance are improved with features like a new disk write cache and hot-swap SSD capability. Role-based authentication and authorization improve security and control. Enhanced Hadoop integration includes a patented Indexed MapReduce capability so Hadoop jobs can operate on a targeted subset of data within Aerospike.
The latest version is available now and you can find out more on the Aerospike website.
Image credit: David Gaylor /Shutterstock
-

CIO jobs at risk as mobile computing weakens data governance
Publié: décembre 15, 2014, 12:42pm CET par Ian Barker

The shift to mobile computing has led to some major changes for enterprises, not least in how the security and confidentiality of data is governed.
A new report, commissioned by data protection specialist Druva from Forrester Consulting, surveyed 205 IT and legal professionals in enterprises in the US and UK. It suggests that 20 percent of CIOs could lose their jobs in 2016 for failing to implement information governance.
Forrester’s analysis revealed rising recognition of the role that mobile computing is playing in weakening existing governance infrastructures. 44 percent of survey participants believe that endpoint data remains at risk despite security and governance controls already in place. The top three challenges are seen as proliferation of file shares (45 percent), lack of coordinated governance (42 percent) and mobile devices (41 percent).
"With the rise of the mobile workforce, organizations must establish strategies to govern not only corporate and employee-owned mobile devices, but also the multiple channels that are now required to make data available anywhere on any device. The increase in complexity is staggering," says Chandar Venkataraman, Chief Product Officer at Druva. "As these findings indicate, technology solutions are going to become increasingly important in identifying, preserving and collecting content from end user devices for all aspects of governance, including compliance and eDiscovery".
The results show that 89 percent of respondents plan to invest more in information governance programs, with 44 percent expecting increases of between 10 and 20 percent. Some 53 percent expect to centralize information governance to ensure that content on end user devices is protected and managed.
Using eDiscovery is expected to increase with 84-85 percent expecting to use technology to facilitate governance and eDiscovery on end user devices.
You can see a summary of the findings in infographic form below and the full report is available to download from the Druva website.
Image Credit: Sergey Nivens / Shutterstock
-

Knowledge-based marketing system delivers streamlined social interaction
Publié: décembre 12, 2014, 11:43am CET par Ian Barker

Social marketing has become an increasingly popular option for companies, but delivering it often involves using a number of different tools to handle publishing, monitoring of campaigns and more.
To streamline the process brand and audience specialist Parllay has announced some new integrated, knowledge-based tools. Parllay Studio is a complete content marketing and trend Intelligence platform powered by a semantic knowledge engine.
It has also released Parllay Channels, a content aggregation, product discovery and loyalty marketing platform that helps brands create sales from social engagement.
"The Parllay ecosystem of products helps brands cut through the social clutter and establish meaningful relationships with their customers and build branded communities at scale", says Tarek Najm, CEO and founder of Parllay. "As a team of former data mining, advertising and knowledge engineering executives, we saw an opportunity to usher in a new wave of products to close-the-loop from content discovery and marketing to merchandising".
Parllay Studio has a number of key features including a visual dashboard of trending stories, social listening and intelligence to gauge what’s being said about brands, and an interactive calendar to manage campaigns and messages across channels. Analytics allow campaign performance to be reviewed and summarized.
Parllay Channels helps businesses build branded communities, creating dynamic social hubs using their aggregated social content, user-generated content, campaigns and loyalty rewards programs. Features include the ability to create personalized messages and promotions in real time, point-based loyalty programs, and a Semantic Explorer that blends user-generated and branded content.
Cloud-based subscriptions to Parllay start from $500 per month. For more information you can visit the Parllay website.
Image Credit: Oleksiy Mark / Shutterstock
-

New partnership boosts Office 365 security
Publié: décembre 11, 2014, 4:13pm CET par Ian Barker

As businesses move their systems to the cloud security becomes a major concern but often applications don't offer the flexibility and ease of access that administrators need.
To address this need for users of Office, cloud security automation company Palerra has announced a partnership with Microsoft to add an extra layer of security to the Office 365 suite.
Palerra's LORIC will allow enterprises to automate security configuration management, threat detection, predictive analytics and incident response for their entire cloud footprint. It unobtrusively monitors activity and detects threats at the source of the data. There's no hardware, software, or agents required making deployment and operation straightforward.
"As proven by recent high-profile security breaches, the market is facing a gap in security as enterprises increasingly adopt cloud services while the threat landscape intensifies," says Rohit Gupta, founder and CEO of Palerra. "The recent launch of our unique cloud security automation platform, LORIC, aims to tackle this market gap so enterprises don't have to make security compromises when embracing productivity. As such, we’re thrilled to be partnering with Microsoft, the market leader in enterprise productivity tools, to provide their global customer base with greater assurance as they embrace the cloud".
LORIC for Office 365 offers a number of useful features including automated monitoring and enforcement of security configurations across all Office 365 services. It also evaluates deviations from normal user behavior, suspicious locations, and non-compliant security configurations. Admin accounts are monitored for suspicious behavior too in order to cut the risk of backdoor access.
Threats are identified across the enterprise's cloud footprint and predictive analysis is used to produce real-time analysis of potential risks. Incident tickets are automatically generated for threat events and can be integrated with existing change management systems.
Also integration with Single Sign-On and Active Directory means user-level policies, reports, and remediation can be used for visibility and control.
You can find out more via the Microsoft Office Showcase or the Palerra site.
Photo Credit: Slavoljub Pantelic / Shutterstock
-

Email is 2014's best digital marketing tool
Publié: décembre 11, 2014, 3:04pm CET par Ian Barker

Technology has had a major impact on the world of marketing, making it possible to target customers more accurately than ever before.
However, when it comes to selecting the best tool to deliver a message there's still confusion, especially since the rise in importance of social networks. A new survey by email marketing brand Campaigner looks at the technologies businesses see as most effective as part of their marketing effort.
The results show that email remains a favorite channel with 60 percent of respondents rating it as the best return on investment generator. Looking ahead to next year 76 percent plan to invest in email will with 33 percent investing in social media.
Newer methods like mobile are developing slowly with 36 percent reporting that it won't impact their marketing strategy and 39 percent saying they’re still researching the technology. Mobile payments are seen to have limited impact too, with 87 percent saying that Apple Pay won't have an impact on their 2015 marketing strategies.
"2014 has been a year of evolution in the marketing industry. Given the introduction of tech advances like Google's Inbox, the new Promotions tab, Twitter's Buy Button and Apple Pay, the modern day marketer has a lot to consider when developing 2015 strategies," says EJ McGowan, general manager at Campaigner. "In order for marketers to effectively stay up-to-speed, they should regularly monitor consumer reactions to new innovations and adjust strategies accordingly. Moving into 2015, I predict email will remain a significant investment in overall planning, with added emphasis on the mobile commerce movement".
An overview of the survey results along with hints for marketers for the coming year is in infographic form below.

Photo Credit: Balefire/Shutterstock
-

LiveSite helps small businesses improve customer interaction on the web
Publié: décembre 10, 2014, 5:00pm CET par Ian Barker

According to a BIA Kelsey report for the Manta small business community, 61 percent of small businesses get the majority of their revenue from repeat clients.
This means that timely interaction and following up with customers is important. Yet many smaller businesses still manage these tasks manually and may be losing sales as a result.
To help businesses use their websites more effectively to retain clients, customer engagement specialist vCita has launched a new version of its LiveSite software giving small businesses greater control and providing a simplified, seamless user experience, increasing customer engagement while improving business efficiencies.
With LiveSite added to their websites, businesses can create an interactive menu of calls-to-action that improve online client engagement. It transforms any website into an interactive app that also works on mobile devices and enables clients to schedule appointments, pay online, upload files and complete forms.
"For small service businesses, the ability to streamline payments, scheduling and client communications is key to creating customer retention and loyalty," says Itzik Levy, founder and chief executive officer of vCita. "The new LiveSite will help over 100,000 businesses working with vCita to deliver an exceptional service to their clients, increase customer satisfaction and make their website look more professional than ever".
Enhanced features in the latest version include an online payment form that can be added to a website or embedded in an email, a MyTime scheduling feature that lets customers set appointments in line with staff availability, and new email templates with greater flexibility and branding options.
The basic system is free and additional modules are available starting at $9.95 per month. For more details and to try out the free version visit the cVita website.
Image Credit: Sebastian Duda / Shutterstock
-

The top threats to your business data in 2015
Publié: décembre 10, 2014, 3:55pm CET par Ian Barker

With OpenSSL problems, ransomware, retail security breaches and the rise of the internet of things, 2014 has been a difficult year for businesses from the security point of view.
Each year brings its own set of challenges of course and Mike Foreman SMB general manager at security company AVG has been looking ahead to the threats companies need to watch for in 2015.
Cyber criminals are increasingly aiming their attacks at smaller businesses and a new class of malware aimed at stealing logins and customer data is the Advanced Persistent Threat (APT). "They are purposely designed to gain a foothold in the business and remain there undetected for a prolonged period of time," says Foreman. "To counter this businesses require an equally sophisticated approach to defense that includes protection from risks in mobile communications and Cloud services as well as traditional networks".
Ransomware is expected to remain a major threat too. Foreman advises businesses to use reputable antivirus software, avoid risky downloads, and to educate their staff about the dangers.
Password breaches will continue to be a problem as internet of things devices become more common. Foreman cites the example of the Russian website streaming images from insecure IP cameras left open by the use of default passwords.
The other area to watch is mobile threats as the use of cloud systems and mobile working increases. Even devices previously thought to be secure could be at risk says Foreman, "Not so long ago it was probably quite natural for your Apple-loving colleagues to congratulate themselves for using the relatively threat-free Macintosh platform. But the tide is turning. The prevalence of iPad and iPhone mobile devices in the office has turned the Apple operating system into a prime target".
You can read more about Foreman's predictions and how small businesses can protect themselves on AVG's blog.
Image Credit: Lightspring / Shutterstock
-

Bitrix24 rolls out new business communication and collaboration tools
Publié: décembre 10, 2014, 1:24pm CET par Ian Barker

One of the biggest trends in enterprise systems this year has been the rise of social collaboration tools within the workplace.
Business intranet tools specialist Bitrix24 has been a major player in this field and is releasing a new and enhanced suite of unified communication and collaboration solutions targeted to businesses of all sizes.
Among 35 new features and upgrades included in this release are an enhanced mobile app for both Android and iOS users, an improved Activity Stream that offers fast rendering speeds yet and is provided in real time and a new CRM social collaboration platform that features a new product catalog, support for the new Bitrix24.Drive and faster processing capabilities.
"We always want to ensure that Bitrix24 is on the cutting edge of the unified communications and collaboration industry, and we believe this advanced suite of tools exemplify our pledge to product superiority," says Dmitry Valyanov, CEO of Bitrix24. "Unlike other recently released products, Bitrix24 also offers an in-depth set of sales tools and CRM functionality. Providing the additional value-add of client management and CRM are key cornerstones for Bitrix24 and crucial elements of our comprehensive solution".
Key features include free two factor authorization to protect users from spyware, and powerful new Bitrix24.Drive and document options which lets users work with documents stored inside Bitrix24 using an office suite that's already installed on their computer. There’s also a new instant messenger feature with the ability to edit and delete messages and share files.
Businesses pay a competitive $199 a month for unlimited users and unlimited online storage. Bitrix24 is now available in Russian, English, German and Spanish. For more information and to sign up for a free trial you can visit the Bitrix24 website.
Image Credit: Diego Cervo / Shutterstock
-

Android business users get a virtual desktop in the cloud
Publié: décembre 10, 2014, 12:18pm CET par Ian Barker
One of the key reasons why businesses migrate their systems to the cloud is to make them easier to access from anywhere.
But that can create complications where office systems are Windows based and mobile devices are running a different OS. Cloud services provider dinCloud has an answer in the form of webHVD, its HTML5-based virtual desktop.
The company has now released an Android version of the app which supports Adobe Flash, Microsoft Silverlight, YouTube, Netflix and more, and is ideal for businesses with 50 or more Windows desktops. It's compatible with a wide selection of Android devices including Google's Nexus 7 and the Samsung Galaxy range.
Companies can use webHVD as a replacement for remote access VPNs and other technologies that allow access from home or remote locations. No backend or virtualized infrastructure setup is required, allowing customers to provision, access, or upgrade a turnkey desktop within minutes.
"As tablet growth approached almost 10 percent in the 3rd quarter, it has created an exciting opportunity for companies to utilize a hosted virtual desktop offering like webHVD," says Mike Chase, CTO at dinCloud. "Users want to connect to legacy applications from any device, and now that Android has an extension for Chrome, we provide an application for this without traditional and costly VDI set up when using a Windows virtual desktop in the cloud".
The webHVD Android app offers a number of features including anytime accessibility, security that requires the user to enter their password and PIN code, similar to the Google Chrome app and an easy-to-use virtual mouse and keyboard for data input. There's also a Send Key facility allowing the use of commands like Ctrl+Alt+Del and the ability to zoom in and out.
Existing webHVD customers can download the free Android app now from the Google Play store.
-

Secunia reveals some of 2014's top software vulnerabilities
Publié: décembre 9, 2014, 5:13pm CET par Ian Barker

Whilst high profile vulnerabilities in popular products tend to make the headlines, they’re often not the ones that most of us face on a regular basis.
IT security specialist Secunia has released a new quarterly Vulnerability Update revealing the day-to-day threat landscape. It lists the number of vulnerabilities disclosed for software products over a three month period.
Secunia looked at 50,000 products and ranked the top 20 with the most disclosed vulnerabilities for each month. Google Chrome topped the tree in August with 64 vulnerabilities and in October with 162, however, Apple OS X took over the top slot in September with 59.
Other interesting entries include Oracle Solaris, taking the number two slot in August with 58 vulnerabilities, and Apple iOS which took the eighth slot in September with 20. Several IBM products make the top 20 list for each month, this is largely due to the fact that IBM likes to bundle products with third-party software, often things like Java and OpenSSL.
That these programs are bundled within the individual IBM product means that every time a vulnerability is discovered and a patch released the corresponding IBM products need patching too.
Also interesting is that August saw nine OpenSSL vulnerabilities. Not terribly exciting you might think, but what Secunia calls 'OpenSSL Take 3' shows that in the wake of earlier OpenSSL vulnerabilities like Heartbleed and Shellshock if a problem doesn't have a catchy name and a dose of publicity it’s less likely to be disclosed and patched.
More information on Secunia's vulnerability reviews is available on the company's website.
Photo Credit: Sergey Nivens/Shutterstock
-

Tamper resistant licensing protects applications from theft
Publié: décembre 9, 2014, 4:17pm CET par Ian Barker

Theft by hackers is a constant problem for software companies, so solutions that can prevent license abuse can help protect revenue.
In the past these have often been quite clunky, involving hardware dongles and such. The cloud era means that more sophistication is needed and Flexera Software has created a secure licensing technology with leading tamper resistance and detection.
"The amount of revenue illegally being siphoned away from producers due to unauthorized software use is staggering," says Mathieu Baissac, Vice President of Product Management at Flexera Software. "Today's hackers are extremely sophisticated and relentless, leaving vulnerable the application producers that fail to implement the latest security measures. FlexNet Licensing offers best-in-class, multifaceted, patent-pending tamper resistance to ward off hackers, allowing producers to better guard their intellectual property, protect revenues, and focus on their core competencies".
FlexNet establishes a virtual 'moat' around software making illegal access by hackers significantly more difficult. It prevents the debugging and application signature spoofing techniques hackers use to reverse engineer applications and gain illegal entry.
Code obfuscation makes it harder to find an entry point, FlexNet Licensing hides strings, variables and functions that control the flow of software and application data which may contain sensitive information. Built-in alarms can also alert the developer to tampering attempts.
There's better support for the cloud too, a new Microsoft Virtual Machine Generation ID helps producers detect cloning and ensure that their customers stay compliant in virtual environments. Developers can choose to prevent cloning or to monetize it should it occur.
FlexNet Licensing works in Microsoft Azure too, so developers can keep track of customers shifting their priorities to cloud-based solutions. It also gives them the ability to adjust their revenue model based on usage.
More information on FlexNet Licensing is available on the Flexera website.
Photo Credit: mkabakov/Shutterstock
-

Jitterbit updates its cloud platform for greater integration
Publié: décembre 9, 2014, 3:22pm CET par Ian Barker

One of the problems that larger businesses face is pulling together information from different sources in order to get an overview of the whole.
Integration specialist Jitterbit has upgraded its Harmony cloud platform to allow it to bring together digital processes spanning multiple applications, departments and partners in real time.
The new release includes Salesforce connectors that allow any application or endpoint system to connect to Salesforece in a matter of minutes. To design the new integration solutions Jitterbit partnered with Salesforce to get direct access to the platform and engineering teams behind the latest products. The resulting connectors deliver fast, reliable integration capabilities that business users can quickly and easily configure to meet their needs.
Jitterbit Analytics Connect can unlock the power of the new Salesforce Analytics Cloud and external data, helping business users to instantly analyze on-premise, cloud, internet of things, mobile and social enterprise data from any device. Salesforce1 Lightning Connect integrates the CRM system's data with back office applications including SAP.
"We're excited to offer true real-time cloud integration with our Winter release to give businesses connectivity between their enterprise applications at the speed of the cloud," says Jitterbit's Vice President of Alliances and Marketing Andrew Leigh. "With the addition of our real-time and analytics connectors, companies can not only amplify the value of their on-premise, cloud, and mobile solutions but also harness this explosion of data for better intelligence within their analytics tools".
The new release also includes an updated messaging system that delivers improved performance and increased throughput whilst using fewer resources. The new messaging bus provides guaranteed delivery, ensuring that companies never miss a transaction even if an outage occurs during the integration process.
Current Jitterbit Harmony users will receive a seamless upgrade to the latest release. For new customers prices start at $1,000 a month and there's a free trial available via the company's website.
Photo Credit: EDHAR/Shutterstock
-

Predictive intelligence boosts social and mobile marketing campaigns
Publié: décembre 9, 2014, 3:03pm CET par Ian Barker

Bombarding customers with irrelevant communications is not an effective way of getting across a marketing message and generating new sales.
The key is to understand the consumer and deliver the right message at the right time. Cloud marketing specialist AgilOne is making this easier for retailers with a new 'predictive intelligence' product.
It can be used to personalize Facebook advertising campaigns and understand user behavior on Apple iOS-native apps. This allows marketers to create personalized, relevant campaigns. The AgilOne cloud integrates easily with Facebook to create custom audiences. AgilOne's Facebook API integration allows marketers to translate their insights to Facebook advertising campaigns almost effortlessly. Retailers can use AgilOne to find specific segments or "clusters" in their existing customer base, such as those who tend to favor specific types of products or brands, or those who have unsubscribed from their mailing list, they can then use Facebook custom audiences advertising to reach those customers.
AgilOne has also released new capabilities for native Apple iOS ecommerce apps. This feature allows marketers to integrate user behavior data from Apple iOS apps with customer data, which includes days since the first and last visit to the app and visit frequency. This makes it possible to identify mobile users as a specific audience and contact them directly. It can also spot things like when items have been placed in a cart but not purchased, allowing the seller to send reminders about those products later.
"Consumers are inundated constantly with less-than-relevant communications from brands, and Facebook has become a new, very busy and cluttered touch-point," says AgilOne CEO Omer Artun. "People react to content that is relevant and courteous. With our predictive marketing cloud, marketers can create relevant conversations with their consumers".
More information on AgilOne's predictive marketing is available on the company's website.
Image Credit: Sarawut Aiemsinsuk / Shutterstock
-

Accenture and Microsoft team up to create hybrid cloud platform
Publié: décembre 8, 2014, 5:05pm CET par Ian Barker

Moving applications to the could is a major step for businesses and finding the right partner to make the transition a success is vital.
The latest latest fruit of the long-standing alliance between technology consulting specialist Accenture and Microsoft is aimed at providing a powerful hybrid cloud platform to bring new capabilities, economics and innovation to the enterprise.
Accenture Hybrid Cloud Solution for Microsoft Azure -- suggestions for snappier names welcome in the comments -- uses new hybrid cloud technologies and services to help enterprises build and manage enterprise-wide cloud infrastructure and applications. It's jointly funded and developed along with Avenade -- a company launched by the two technology giants in 2000.
"Enterprises around the globe are looking for the right platforms and partners to help them transform and thrive in a mobile-first, cloud-first world," says Satya Nadella, CEO of Microsoft. "The Microsoft cloud, combined with Accenture's industry knowledge and implementation expertise, accelerates our customers’ cloud adoption and unlocks new benefits, including powerful new applications, data-driven insights and increased productivity".
The new solution integrates and builds on key existing capabilities from the three companies to help enterprises deliver a one-stop service solution. The Microsoft Azure platform provides enterprise performance, hyper-scale and hybrid capabilities connected to Windows Server with Hyper-V, System Center and Azure Pack running in customer data centers.
The Accenture Cloud Platform supports multi-platform environments with self-service provisioning for any application. There's a central dashboard to control cloud brokerage and management capabilities, along with enterprise-grade governance, reliability, security and operations.
The product also includes professional services to help clients define and execute their cloud goals, based on Accenture's specialized industry knowledge.
"Our expanded relationship with Microsoft represents a game-changing proposition that addresses the biggest concerns and complexities our clients face as they look to leverage the cloud," says Pierre Nanterme, chairman and CEO of Accenture. "With new demands being placed on IT departments every day, enterprises need to smartly connect their infrastructure, software applications, data and operations capabilities in order to become agile, intelligent, digital businesses. This unique collaboration with Microsoft and Avanade is one of Accenture's most strategic and important initiatives for driving enterprise-wide cloud adoption".
The solution is already being piloted and more information is available on the Accenture website.
Photo Credit: everything possible / Shutterstock
-

What to look out for in 2014's last Patch Tuesday
Publié: décembre 8, 2014, 1:03pm CET par Ian Barker

After last month's blizzard of patches tomorrow's last round of Windows updates for the year looks set to be rather quieter.
Only seven bulletins have been announced, of which three are rated Critical and four Important. Of the Critical patches one is for Internet Explorer, one for Office and one for Windows itself -- likely to be for a remote code execution vulnerability.
There's an Important MS Exchange patch to resolve an elevation of privilege problem. Chris Goettl Product Manager of IT management specialist Shavlik says, "As you may recall, this patch was held out of last month's Patch Tuesday updates along with another out-of-band patch that was released later in November. With all of the changes at Microsoft recently, this practice of holding a patch could become a pattern. It is likely that with less important patches, these will be released on a subsequent Patch Tuesday".
The Internet Explorer patch looks set to be a cumulative security update, something that will probably become a regular fixture in future Patch Tuesdays as hackers increasingly target browsers. There are three Office updates in total all of which address remote code vulnerabilities.
Karl Sigler, Threat Intelligence Manager at Trustwave says, "This security update will be light compared to the previous patch Tuesday. None of the CVEs included in this release are exploited in the wild at the moment. Also, it's not likely there will be a vulnerability as nasty as the Schannel Remote Code Execution vulnerability (MS14-066) from last month".
Third-party patches are expected from Adobe too according to Wolfgang Kandek, CTO of cloud security specialist Qualys. "Adobe has notified of a new version of Adobe Reader and Acrobat in APSB14-28. Both versions 10 and 11 on Windows and Mac OS X are affected by this critical vulnerability. In addition we also expect a new version of Flash as Adobe has had monthly release for Flash in every month in 2014 so far".
All versions of Windows, Office and IE are thought to be affected by at least one of the vulnerabilities. Users with automatic updates enabled should receive these updates automatically though a reboot will be required to apply them.
Photo Credit: fotoscool/Shutterstock
-

Macs and Linux come under attack as the threat landscape shifts
Publié: décembre 5, 2014, 4:30pm CET par Ian Barker

The latest monthly report from internet security specialist Doctor Web shows that whilst Windows and Android users have no cause for complacency, November saw substantial numbers of malicious programs aimed at Mac OS X and Linux platforms.
Trojans remain the most popular form of attack making up 8.7 percent of all malware detected. Trojan.InstallCore.12, which installs different adware, toolbars and browser extensions, ranks first. BackDoor.Andromeda.404, which downloads other malicious programs into an infected system when commanded to do so by intruders, ranks second.
In November BackDoor.Andromeda.404 was distributed in large quantities by email thanks to a mass spam campaign. It accounted for 2.4 percent of the malware detected by Doctor Web. The malware top 10 includes a number of other programs that seek to steal confidential information.
Several new examples of OS X malware have been added to Doctor Web's database. These include Mac.BackDoor.Ventir.2 a backdoor that can execute commands from a remote server, log key strokes and relay information to criminals. Particularly sneaky is Mac.BackDoor.WireLurker.1 which waits for the moment when an iOS device is connected to an infected Mac and then uploads its files onto the device. It even comes in two versions, one intended for jailbroken devices, while the other is for unaltered iOS devices. It takes advantage of the "enterprise provisioning" feature that enables companies to bypass the AppStore and install applications onto its employees’ devices.
Linux systems have been targeted by Linux.BackDoor.Fgt.1 which scans random IP addresses on the internet and launches a brute force attack in an attempt to establish a Telnet connection with their nodes. If successful, it commands the attacked host to download a special script. The malware’s command and control server stores versions for various Linux distros and versions allowing it to infect not only internet-connected servers and PCs running Linux, but also other devices, such as routers.
Android doesn't escape the onslaught, with a large number of malicious programs being detected. Many of these are banking trojans aimed at stealing money from accounts accessed on compromised devices. For example Android.BankBot.33.origin is aimed at Russian internet banking users. It employs SMS commands to covertly transfer money to the intruders' account and hide SMS replies from the bank, so that the user won't notice unauthorised transactions. In addition it can load a bogus web page in the browser to lure users into submitting their online credentials.
For more information about the latest virus activity and a free online scanner for malicious files and links you can visit the Doctor Web site.
Photo Credit: Jirsak/Shutterstock
-

Cortana says bonjour, ciao, hola and tag to Europe
Publié: décembre 5, 2014, 3:34pm CET par Ian Barker
Since its beta introduction to the US in the spring of this year Windows Phone 8.1's personal assistant tool Cortana has generated lots of interest.
It became available in the UK and China over the summer but now it's moving into the rest of Europe with native language versions for France, Germany, Italy and Spain.
From today Cortana will be availabe in these countries as an alpha via the Windows Phone Developer Preview Program. This will have most of the features of the beta but some are still missing.
Flight tracking isn't available for alpha for example and transit data is currently limited to larger cities. Also reference data isn’t available, though Microsoft says it's working hard to enable this soon. Cortana's 'personality' will be tailored to each market with local chat and jokes to make it culturally relevant. It will also show European football league data.
Marcus Ash, program manager for Cortana, writing on the Microsoft blog encourages the developer community to use Cortana, "By working with her, you will help to improve her conversational understanding and also help us improve her intelligence -- the breadth of answers she can provide and the categories she's aware of -- so she can truly help you throughout your day. There's no need to file explicit feedback: simply using Cortana will help make her better over time. It's so exciting to see the passion the community has had for Cortana and your passion has been one of the driving forces for us to bring Cortana alpha to more countries".
In order to try the new alpha you'll need to sign up to the Developer Preview Program.
Image Credit: Microsoft
-

OpenDNS opens its platform to allow intelligence sharing
Publié: décembre 4, 2014, 4:54pm CET par Ian Barker

As the IT landscape changes and employees are more likely to be accessing cloud services on a range of devices, it's important that they remain properly protected from threats.
Cloud-delivered security service OpenDNS has announced that it's opened up its platform to other security vendors to fight attacks through intelligence sharing.
The company has launched a new security platform and APIs that enable leading enterprise security vendors to integrate with OpenDNS's worldwide network. The combining of OpenDNS with threat intelligence can protect users wherever they are and whatever system they're using.
This will improve protection by using OpenDNS's capability to provide global threat enforcement. It will also reduce the need for security professionals to develop their own custom integrations between security solutions, leading to lower operational costs.
Two new partners Check Point Software Technologies and ZeroFOX have also been announced and will be integrating OpenDNS with their security offerings.
"Combining OpenDNS’s global, cloud-delivered security platform with intelligence from our partners’ advanced detection capabilities results in unmatched protection for our mutual customers," says David Ulevitch, CEO of OpenDNS. "Hackers and cybercriminals are already
experienced at sharing intelligence, infrastructure and operational expertise. We see vendor partnerships -- such as the ones we are announcing today -- as the best strategy for the security community to leverage our collective strength against advanced, targeted attacks".The OpenDNS Global Network currently handles more than 50 billion of the world's internet requests daily. With this announcement joint customers can now offer the same level of security to employees both inside and outside of the network perimeter while adapting to new threats as they are detected.
For more information on OpenDNS services you can visit the company's website.
Image Credit: Yellowj / Shutterstock
-

Spanning offers new backup solution for Office 365
Publié: décembre 4, 2014, 3:37pm CET par Ian Barker
As more and more data gets moved to the cloud it's easy to forget that it still needs to be protected against corruption and loss.
Cloud backup specialist Spanning has a new solution for Office 365 users with the launch of an enterprise grade cloud-to-cloud backup solution. It's aimed at bringing the same application-centric focus and backup and restore expertise to Office 365 that it already has for Google Apps and Salesforce solutions.
"We are seeing a rapid adoption of and migration to Office 365, and we are also seeing data protection for cloud application data becoming more important than ever," says Jeff Erramouspe, CEO of Spanning. "A mobile and collaborative work environment opens the door for increased user error and other data issues. As Microsoft customers move to the cloud in droves, they now can do so without worry, knowing they can implement the industry’s most trusted cloud-to-cloud backup to ensure they are fully protected from data loss and are compliant with industry regulations and requirements".
Spanning Backup for Office 365 enables IT administrators and end users to quickly and easily find and restore lost data from any point in time, from any device. Features include Automated daily and on-demand backups of Mail, Calendar, and Contacts. Point-in-time backups let administrators and end users search, view and directly restore any previous version of the data. Cross-user data restore makes it easy to restore data from one Office 365 account into another, useful when employees leave or change roles.
There are multiple layers of operational and physical security to ensure the integrity and safety of data, including 256-bit encryption, SSAE 16 compliance, intrusion detection and compartmentalized access. Pricing is on a simple single rate, per user, per year, no matter how much data is stored.
The product will be generally available in the first half of 2015 but in the meantime Office 365 users can sign up for early access via a beta program.
-

New Clarizen release delivers extra enterprise productivity
Publié: décembre 4, 2014, 2:49pm CET par Ian Barker

Whilst access to data is often the key to things running smoothly in business, providing access to that data for the right people at the right time can be a challenge.
Enterprise collaboration specialist Clarizen combines social engagement with powerful project management to redefine enterprise collaboration and has announced a new release of its product bringing a number of tools together in a single solution.
Clarizen v6 was announced last year and the latest release is aimed at providing greater productivity with a number of new key features.
Using a single cloud platform it offers Clarizen Panels, giving users a new way to visualize any data -- via panel or page -- whether internal or external to Clarizen. Clarizen Home is a single page that contains all daily work items, cases and relevant conversations in one easy-to-read, easy-to-access view. Clarizen Home also includes quick access to common actions, recent items and new items. Users can customize the page to show specific fields and data.
A new partnership with ProofHQ allows users to proof any digital file, from a simple text document to commercial videos and Flash applications, in full context with Clarizen workflows, projects and tasks. It's possible to create new proofs and manage them for any uploaded file.
There's also expanded integration between Clarizen and Box. Box users can now seamlessly connect and view their Box work files and folders from within Clarizen. Workers can also easily create new folders and upload new files to Box directly from Clarizen by connecting them to tasks, work items and projects.
"In today’s workplace, priorities, projects and action items can change at a moment’s notice. The modern worker needs easy, all-in-one access to their mission-critical information and a single place to get work done," says Rachel Haim Hadas, Clarizen's VP of Product. "We are enabling workers to customize and configure how they visualize and access their day-to-day work information and project-related data. This increased customization translates to more productive employees, better project visibility and, in the end, quality work".
For more information on Clarizen's latest features you can visit the company's blog.
Photo Credit: Pressmaster/Shutterstock
-

Real world experiences of bare metal recovery
Publié: décembre 2, 2014, 3:52pm CET par Ian Barker

Bare metal recovery (BMR), restoring a machine with no requirement for operating systems or software to be present beforehand, isn't always seen as a reliable technique.
To look at how successful it really is, cloud backup and disaster recovery specialist Zetta.net has released the results of a survey looking at companies’ real world experience of BMR.
"Anecdotally, bare metal recovery has a reputation for being unreliable," says Gary Sevounts, CMO of Zetta.net. "But it was difficult to find any numbers related to success. We conducted this survey to learn more about how our customers use this technology, and how successful it's been for them".
The company asked 200 IT professionals about their BMR experiences including usage, success rates and causes of failure. Among the findings are that 34 percent of respondents had used BMR at some point in their career. 23 percent of respondents were currently using BMR, though the findings revealed several respondents citing increased virtualization as eliminating their need for this approach.
Of those using BMR 48 percent reported that they had experienced problems trying to perform a restore. Among these the primary cause was most commonly dissimilar hardware (36 percent), corrupt backups (35 percent), 24 percent driver failure, and three percent other issues such as tape problems.
More information about the findings is available on Zetta.net's blog and there's an infographic summary of the results below.
-

New call center technology adapts to visually impaired employees
Publié: décembre 2, 2014, 11:54am CET par Ian Barker

Meeting the needs of employees to access systems is an important consideration for any modern business. Now, cloud-based call enter systems provider TCN is making its technology accessible for the visually impaired.
Its Platform 3 Vocal Vision product is optimized to work with Job Access with Speech (JAWS) technology and allows visually impaired call center agents to effectively navigate TCN's cloud-based contact center suite, helping to improve agent productivity while also creating new employment opportunities for the visually impaired.
"We’ve been impressed with TCN's VocalVision cloud-based phone service. They have been very willing to customize the solution to meet our employee's accessibility needs. So, our employees like the system and its ease of use. It has enhanced the level of service we can offer our customers through its call recording and time reporting capabilities," says Jim Kerlin, president and CEO of Beyond Vision. "In the future, we plan to use the system to measure and report productivity and utilization metrics, just as we do in our manufacturing environment".
JAWS assists computer users whose vision impairment prevents them from seeing screen content or being able to operate a mouse. VocalVision helps the agent navigate Platform 3.0's workflows via hot keys that use JAWS functionality during both incoming and outgoing calls, while audible tones signal the connection of an incoming call.
Standard features of VocalVision include handling incoming and outgoing calls, agent dashboard along with reporting and call analytics. It works without any need for complex, specialist hardware.
"TCN has always been committed to providing customers with the most advanced call center technology," says Terrel Bird, CEO and co-founder of TCN. "We are excited to bring Platform 3 VocalVision to the market to meet the needs of the visually impaired community and open new doors for employment".
More information on Platform 3 VocalVision is available on the TCN website.
Image Credit: HABRDA / Shutterstock
-

Consumers warned to be on the alert for Cyber Monday scams
Publié: décembre 1, 2014, 5:46pm CET par Ian Barker

Cyber Monday is once again set to break records for online sales and web traffic, but there’s a darker side to the day too.
Social risk management company ZeroFOX has released the results of some research into the risks associated with the Cyber Monday spending spree.
Among the findings are that 64 percent of companies report an increase in cybercrime on Cyber Monday, phishing links go up as much as 336 percent at Thanksgiving, and on Twitter, there are 30 Million fraudulent or malicious tweets sent out daily.
Attacks are carried out in several ways, for example by spear phishing -- fake emails and landing pages designed to trick consumers into thinking they're dealing with a real company. But hackers increasingly use social media either by posting clickbait offers for tempting deals or by hijacking trending hashtags.
You can see a summary of the findings, along with tips on how to keep yourself safe, in infographic form below.

Image Credit: Gustavo Frazao / Shutterstock
-

Enterprise mobility set to remain a hot topic for 2015
Publié: décembre 1, 2014, 5:14pm CET par Ian Barker

It's that time of year when industry analysts like to start rolling out their predictions for the year ahead. One of the first out of the blocks is technology research specialist Ovum with a new report on enterprise mobility.
Up to now mobility has been driven by the consumer market with employees demanding to use their own devices in the workplace. Among Ovum's predictions are that this will continue to lead to a 'mobility mismatch' where employee demand isn't matched by IT department's ability to deliver.
It also predicts that businesses will start to look beyond BYOD, adopting a more managed approach to device usage, particularly where sensitive data is involved. This is likely to mean framing mobile management as part of a wider workspace strategy. By governing management of all endpoints and applications the strategic aim is giving employees access to the tools and data they need wherever they happen to be and with whichever device they happen to have in front of them.
Ovum also sees more pressure from senior executives, particularly in HR and operations, to allow mobile deployments. SME's should expect 2015 to become even more mobile centric, vendors and service providers will need to adapt to this additional demand.
Richard Absalom, senior analyst, enterprise mobility at Ovum, says, "While pressure from end users continues to have an impact on the shape of the EMM market, it is time for enterprises to become more proactive with their mobility strategies and look for ways that mobile devices -- whether corporate or employee-owned -- and apps can work in tandem with other endpoints to transform the way that people work. Vendors and service providers in the space need to keep expanding the range of features and services that they offer to meet the growing range of demands, and they will also need to continue to build effective partnerships, especially in support of large, global organizations which expect and demand consistent global service delivery".
More information on Ovum's research into enterprise mobility can be found on the company's website.
Image Credit: Sergey Nivens / Shutterstock
-

SAP launches new manufacturing solution to improve enterprise integration
Publié: décembre 1, 2014, 4:20pm CET par Ian Barker

Enterprise software specialist SAP has announced the availability of a new manufacturing application to help deliver data integration across businesses using the SAP HANA platform.
SAP Manufacturing Execution includes the SAP Manufacturing Integration and Intelligence (SAP MII) application and SAP Plant Connectivity software. This allows it to provide machine-to-machine integration and orchestrate intelligent manufacturing.
Using the existing SAP HANA platform it offers global visibility into operations by making manufacturing big data more accessible and enabling predictive analytics capabilities to be used in house or in the cloud. This gives businesses advanced problem solving ability and ease of access to manufacturing data so they can make improvements in cost, quality, asset utilization and performance.
"The launch of SAP Manufacturing Execution is helping SAP to close in on the vision of running manufacturing operations in memory," says Hans Thalbauer, senior vice president Extended Supply Chain at SAP. "By integrating manufacturing results with real-time feeds into SAP HANA, companies can take advantage of the cloud for orchestrating global performance management".
The product gives manufacturers an enhanced user experience, extended mobility and end-to-end enterprise integration with deeper operations transparency. This release gives enterprises the deployment option of SAP MII on SAP HANA, extending the internet of things capabilities of SAP into manufacturing operations. SAP Plant Connectivity simplifies integration at the equipment level and allows direct data feeds to SAP HANA, giving access to big data sources and enabling analytics.
Manufacturing Execution is available now for existing SAP HANA users and more information is available on the company's website.
Image Credit: SAP
-

India falls in love with smartphones and tablets
Publié: novembre 28, 2014, 1:15pm CET par Ian Barker

We're frequently being told that the real potential for growth in mobile devices sales is coming from emerging markets, particularly in Asia and the Far East.
The latest research findings from IDC into the Indian market bears this out with strong growth in sales of both smartphones and tablets.
A new high in smartphone shipments in the third quarter of 2014 saw them take over 30 percent of the Indian market for the first time with 23.3 million units shipped. That represents a growth of 27 percent over the previous quarter and 82 percent year on year.
Most of these are standard smartphones rather than oversized devices, however. "With 6 percent of the overall smartphone market, Phablets (which IDC defines as smartphones with a screen size of 5.5 inches to 6.99 inches) are observed to be hitting a plateau," says Kiran Kumar, Research Manager, Client Devices at IDC India. "Smartphones with screen sizes between 4.5 inches and 5.5 inches are seen as the sweet spot for consumer preference. However, consumers need larger screen sizes to enjoy media content and with the 4G rollout expected in calendar year 2015, we expect the Phablets segment to pick up again".
Looked at by manufacturer, Samsung is the market leader with 24 percent, followed by local brand Micromax on 20 percent, up two percent on the previous quarter, whilst Samsung’s share contracted slightly. Next come Lava and Karbonn, with Motorola rounding off the top five.
The tablet market has also shown its best year to date growth, with quarter on quarter growth of 10 percent in the third quarter taking it to 0.94 million units. Android devices dominate with 90 percent of the market and this trend is expected to continue. The adoption of Windows tablets is forecast to increase as units become available at lower prices but they’re starting from a low base.
Samsung again has the largest share of the market with 22.2 percent with Micromax second on 10.9 percent. Coming up fast in third is relative newcomer iBall on 10.6 percent, its growth mainly coming from consumer sales.
Next year IDC expects the commercial tablet market to show the most growth whilst consumer sales remain relatively stable. "We are likely to see increased activity by PC OEMs in the tablets space with a focus on the 7 inch and 8 inch form factor," says Tanvi Mann, Market Analyst at IDC India.
More information on IDC's market trackers is available on the company's website.
Image Credit: SnowWhiteimages / Shutterstock
-

You better watch out -- online retailers' security practices under the spotlight
Publié: novembre 26, 2014, 5:20pm CET par Ian Barker

This time of year sees a spike in online shopping activity, but that also means added worries about how well our information is being looked after when we buy online.
Password management company LastPass has put together an infographic 'naughty and nice' list looking at how online retailers store information when we shop.
On the naughty step are some big names including Amazon and Walmart. Problems include weak password requirements, collecting too much information before you make a purchase and the storing of credit card details -- convenient for future buys but a risk if someone gains access to your account.
On the nice side of the list are eBay and the Apple Store, along with one of last year's bad guys Target. The graphic also offers some tips for staying safe as you shop including looking out for HTTPS connections, using a different password for each account and lying in your answers to security questions to reduce the chances of your account being hacked.
You can see the full infographic below and if you have any extra tips for surviving the online shopping experience do let us know in the comments.
Photo Credit: RTImages / Shutterstock
-

Cloud-based tracking creates an internet of lost things
Publié: novembre 26, 2014, 10:52am CET par Ian Barker
Electronic tags to help stop you losing stuff are nothing new. But usually they rely on Bluetooth or similar to sound an alarm when an object goes out of range.
A new solution from Canadian company Linquet mixes the cloud and the sharing economy to track tagged devices in a kind of internet of lost things.
"We've all been there. We always lose or misplace our phones, keys, wallets, laptops, pretty much everything," says Pooya Kazerouni, Linquet's president. "Now, we have a product that is much more than a great anti-loss solution. Not only does Linquet prevent your valuables from getting lost in the first place, but it also allows for smart sharing and connecting of important items with guests, acquaintances and customers".
More than one person can connect to a Linquet tagged item making it easy to share things like bikes or keys. You can loan gadgets to colleagues, or even track your pets, and see where they are via an iOS or Android app. The cloud element allows you to have Smart Profiles so you can, for example, customize times and locations when alarms don’t sound.
You can build up a network of trusted friends who can help you locate missing items at locations you visit regularly. If something strays further afield the whole Linquet network can be brought into play. You can be anonymously notified of an object’s location if it comes within 100 feet of another Linquet user.
The device tags also have a Magic Button that can be used to find your phone, take a picture with its camera or alert your friends in an emergency.
The introductory pricing model (until January 5) is $1.99 a month for a single device and user, $6.99 for four devices, two users and three smart profiles, and $14.99 for ten devices, five users and seven profiles.
The company is also set to release an API which will allow developers to build apps or integrate Linquet with their own products.
You can find out more and sign up on the Linquet website.
-

Philips launches full HD display with easy one-plug access
Publié: novembre 25, 2014, 1:08pm CET par Ian Barker

Anyone who's tried to connect a notebook to a big screen for use in meetings or presentations knows it can be a process that's fraught with difficulty, particularly when it comes to finding the right connection and cable.
The latest release from electronics giant Philips solves this problem by offering simple, one-plug access to desktop equipment, networks, intranet and internet via a single, super-speed USB cable.
The 231P4QUPES may lack a catchy name but it does have a 23-inch full HD display. This offers extra wide 178 degree viewing angles making it ideal for meeting rooms, plus a 90 degree pivot so it can be used portrait or landscape.
It also has Philips' PowerSensor technology that can detect if nobody is in front of the screen and automatically reduce the brightness.
Its big draw though is connectivity. It has an integrated Ethernet port and two USB 3.0 ports as well as one USB 2.0. This means users can plug in their notebooks to the monitor for immediate access to all the IT resources connected to the display, which can include printers, external drives, camera, keyboard or mouse. All the peripherals remain connected to the monitor ready for immediate use -- so there's no need for separate docking stations. Via USB 3.0 connection it's possible to stream video and connect to networks and the internet.
The display is available now with a recommended price in the UK of £239 (around $375).
-

E-cigarettes can damage your PC's health
Publié: novembre 24, 2014, 12:01pm CET par Ian Barker

Using e-cigarettes, or vaping, is widely touted as being healthier for you than smoking tobacco, however, it may not be so healthy for your PC.
Many e-cigarettes offer a USB charging option but a story on social news site Reddit suggests that this is a potential source of malware attack. An executive's PC became infected after he'd recently given up smoking and the infection was traced to his e-cigarette charger.
It seems likely that this is a variant of the BadUSB malware uncovered in August this year by German company SRLabs. This allows the firmware on USB controller chips to be reprogrammed to deliver a malicious payload or masquerade as another device, such as a network card, to capture transmitted information.
Dave Goss of London's Vape Emporium told the Guardian that e-cigarette users can stay safe by purchasing respected brands but added that, "Any electrical device that uses a USB charger could be targeted in this way, and just about every one of these electrical devices will come from China".
How much you read into the fact that these devices originate in China is also open to question. Carelessness on the production line or more sinister, state-sponsored malware? Either way it's a good idea to treat unknown USB devices with suspicion.
Users can protect themselves by using a 'charge only' cable with the data pins disconnected to connect devices that don't need to exchange information. This news is likely to encourage more businesses to restrict the use of unauthorized USB devices on corporate networks too.
Have you suffered any kind of malware problem with a USB device? Let us know in the comments.
Image Credit: scyther5 / Shutterstock
-

The rising importance of big data to big business
Publié: novembre 21, 2014, 4:05pm CET par Ian Barker

Analysis of large volumes of information is increasingly used by businesses to gain an advantage. A new infographic produced by big data specialist Datameer looks at how it’s being used to gain a competitive edge.
Among the highlights are that the global Hadoop Market is projected to be worth $50.2 billion by the year 2020, a huge increase from the $1.5 billion it was worth in 2012.
North America is currently the biggest investor in big data at 37.8 percent, though Asia/Pacific businesses plan to increase their investing by 106.6 percent, bringing them to a close second. Looking at usage by industry, financial services lead the way, followed by technology and communications companies.
The most popular use of big data is to analyze customer behavior, with 48 percent of users. It allows businesses to look at the customer journey, reduce churn rates, increase revenue and improve existing products.
Operational analytics is carried out by 21 percent of companies to improve supply chain efficiency and help with IT analytics and network planning.
You can see the full infographic below (click to view a larger version) and read more on Datameer's blog.
Photo Credit: Maksim Kabakou/Shutterstock
-

Cloud-based software is a major revenue source for service providers
Publié: novembre 21, 2014, 12:35pm CET par Ian Barker

Communication service providers (CSPs) have spent the last few years investing heavily in cloud software provision to expand their business.
A new report by Israel-based Allot Communications shows that this is paying off as software as a service is now a major revenue source for CSPs.
The most innovative CSPs surveyed have addressed enterprise CIO concerns around security and performance by responding with specific cloud-based visibility, control, quality of service (QoS) and security managed service offerings.
Of those surveyed 47 percent offer hosting services, and 42 percent have specifically developed cloud applications aimed at SMBs. 45 percent offer public cloud applications and services for enterprises, ranging from basic email and storage to sophisticated CRM and ERP solutions. . Microsoft’s Office 365 is the most popular cloud office suite, well ahead of Google, and is offered by 33 percent of surveyed CSPs.
Quality of service management for the cloud is lagging behind according to the results. Just 23 percent of CSPs are currently offering QoS and/or visibility solutions for mission-critical applications. 32 percent of CSPs offer some form of cloud-based security service such as anti-DDoS or URL filtering. However, QoS management is more popular when unified communications or Office are involved. With unified communications, 32 percent of CSPs offer QoS management, 48 percent offer it with Office applications and 50 percent with Microsoft Lync .
"Workforce productivity and mobility needs are causing CIOs to re-evaluate their network infrastructure and operations. At the same time, CSPs are responding by evolving their SMB and enterprise cloud services to reach beyond classic connectivity and IT solutions traditionally provided," says Yaniv Sulkes, AVP Marketing at Allot Communications. "The market trends surfaced in our report reflect what we are seeing with our CSP and enterprise customers. CSPs around the globe are increasingly delivering value added digital services that can help enterprises overcome their toughest adoption challenges and achieve the cost and efficiency benefits promised by the cloud".
For more details of the report visit the Allot website.
Photo Credit: Rrraum/Shutterstock
-

Personalized marketing is the key to consumer's wallets
Publié: novembre 20, 2014, 5:32pm CET par Ian Barker

Sending out generic marketing emails and scatter-gun coupon offers is no longer enough to attract the attention of consumers and can in fact have the opposite effect.
Predictive marketing company AgilOne has released the results of a survey which shows that online shoppers appreciate personalized communication -- as long as it's done right.
The survey asked more than 3,000 adult online shoppers about what information they expected companies to know about them and what personalized experiences they appreciate. The results indicate that while consumers appreciate and even expect brands' efforts to personalize the buying experience, the preferred methods for that personalization vary greatly across demographic groups.
Key findings are that 79 percent of US consumers and 70 percent of UK consumers expect some sort of personalization from their brands. Also more than half of consumers in both the US and UK expect e-commerce sites to remember their past purchases.
Among the most popular personalized experiences are emails offering discounts on products shoppers have previously viewed, alerts when products they like are on sale and VIP customer appreciation rewards.
The millennial generation is more likely to appreciate almost all forms personalization. For example 52 percent of those aged 18 to 24 expect brands to remember their birthday as compared to 21 percent of shoppers aged 65 and over.
Interestingly whilst email targeting is popular, with 66 percent of US and 57 percent of UK consumers welcoming it, web targeting is much less so. Only 24 percent of US and 17 percent of UK consumers liked web-based targeting such as on-site pop-ups for particular products.
You can see more of the report's findings in infographic form below.
Image Credit: iQoncept / Shutterstock
-

The security challenge of business mobile devices
Publié: novembre 20, 2014, 4:09pm CET par Ian Barker

The trend towards mobile devices and BYOD is great for productivity but it creates new challenges in terms of keeping information secure.
Identity and access management specialist Ping Identity has produced an infographic looking at the vulnerabilities introduced by letting employees use mobile devices.
Some 460 million smartphones will be shipped worldwide in 2016 and 65 percent of these will be used for both personal and business purposes. Combine this with two-thirds of companies expected to adopt BYOD by 2017 and the potential for problems is huge.
It's not surprising then that 49 percent of companies see security as their biggest concern for the cloud. However, the weakest link is often the employee, 40 percent don't password protect their devices and 57 percent don’t realize security systems exist for their device.
This means that as BYOD becomes more widespread there'll be added focus on corporate solutions including mobile device management, extending single sign-on protocols to mobile devices and using multi-factor authentication.
You can see the full infographic with more hints on how to keep mobile systems secure below.

Photo Credits: Slavoljub Pantelic/Shutterstock
-

XSS vulnerabilities open the door to drive-by downloads
Publié: novembre 20, 2014, 3:25pm CET par Ian Barker

Cross-site scripting (XSS) vulnerabilities allow attackers to inject script into web pages in order to infect client computers.
Security company High-Tech Bridge has released a report revealing that 95 percent of XSS vulnerabilities can be used to perform sophisticated drive-by-download attacks, which infect users who open harmless-looking URLs that they trust. More worrying is that 90 percent of vulnerabilities can be exploited in such a way that even advanced users and IT professionals won't suspect anything. The structure and architecture of more than 70 percent of web applications allows the creation of a sophisticated XSS exploit that can perform several fully-automated actions, ultimately giving full administrative access to the attacker. This access can then be used by hackers to compromise the entire website and even the web server.
To protect against this type of attack companies are advised to explain to their web developers that one XSS vulnerability may lead to total compromise of the entire company. Developers and server admins need to respect security best practices as this will resolve majority of potential problems.
It's also important to make sure that the IT team has a clear inventory of web resources and that there are no abandoned or test web projects that are accessible from the outside. Regular web penetration testing by an independent company is recommended too.
Ilia Kolochenko, High-Tech Bridge's CEO, says, "SQL injection vulnerabilities are becoming more and more rare, as well as other high and critical risk vulnerabilities. They are complex to detect and quite often requires a lot of time to exploit. At the same time almost nobody cares about 'medium-risk' XSS vulnerabilities leaving their websites vulnerable. Obviously, hackers benefit from such negligence and use XSS vulnerabilities to achieve their goals. If you close your door, don't forget to close your windows -- otherwise the entire security is at risk".
There’s much more information on how XSS can leave users open to hacking on the High-Tech Bridge blog.
Image Credit: spaxiax / Shutterstock
-

New venture aims to completely rethink enterprise security
Publié: novembre 19, 2014, 3:53pm CET par Ian Barker

Up to now cyber security has generally taken a defensive approach to protecting data and intellectual property.
That’s set to change as a team of industry experts has got together to create a system that's aimed at dramatically improving the reliability and security of enterprise data and applications running in both cloud and conventional environments.
Called Virtual Software Systems (VS²) the company is set to offer an entirely new approach to security based on the founders’ deep expertise in systems architecture, design and development.
VS²’s technology is intended to fill the gap between current perimeter solutions (firewall, intrusion detection/prevention, anti-virus, etc.) and interior defenses such as encryption, which is currently the only method for protecting data following a perimeter breach.
Existing security doesn’t go far enough says VS² President and CEO John Conway, "They've applied technologies and methodologies from the physical world to the virtual world -- but the headlines tell us every day that this approach is incomplete. The mechanisms used by intruders to evade detection and trick perimeter defenses are infinite, so the key is to simplify and manage the attack surface from the inside of the computer. VS² achieves this by rethinking security at the system design level, combining principles of fault tolerance with a new spatio-temporal architecture that virtually manipulates time and neutralizes attacks before they can become harmful exploits".
The engineering team behind VS² holds more than a dozen computer design patents and is responsible for many of the foundational technologies that support today’s complex computer and network infrastructure.
The company is intending to demonstrate its new technology in 2015, in the meantime you can keep up with developments on its website.
Imaged Credit: soliman design / Shutterstock
-

Splice Machine reduces the cost and complexity of building database applications
Publié: novembre 19, 2014, 3:35pm CET par Ian Barker

Databases are important to enterprises of all sizes, but building applications to exploit data effectively can be time consuming and expensive.
Now Splice Machine, maker of the only Hadoop RDBMS (relational database management system), is making its product publicly available for the first time. It will allow database architects and app developers to build real-time, scalable applications without the burden or cost of a traditional RDBMS.
The product has been in beta for the past year and the company has been working with customers to gather feedback on what matters most to enterprises in a scale-out relational database. As a result the version 1.0 release has some key new features.
These include analytic window functions providing advanced SQL analytic capabilities based on the SQL-2003 standard. Native backup and recovery to protect against data loss, and a cost-based optimizer to ensure efficient query performance. There's also a console that provides a view into how well queries are working.
Splice Machine integrates with the Hadoop big data ecosystem and has a native ODBC driver offering custom-built database connections.
"With these new features and the validation from our charter customers, we are now fully prepared to support enterprises that are growing quickly and looking to scale affordably," says Monte Zweben, co-founder and CEO of Splice Machine. "Shipping the 1.0 version of our Hadoop RDBMS is just one milestone for us in a year of many, but it's perhaps the most important one. It says 'we’re here, and we’re ready,' which is an exciting place to be".
A standalone version of Splice Machine Hadoop RDBMS is available to download allowing users to try it out. For enterprise customers Splice Machine offers comprehensive services and support, including training courses, a Kickstart Package to speed implementation, and on-demand consultants to optimize operations.
Image Credit: alphaspirit / Shutterstock
-

Celebrating 60 years of software
Publié: novembre 19, 2014, 12:23pm CET par Ian Barker

There's an old computing joke that says the difference between software and hardware is that hardware is the bit you can kick.
To celebrate software's 60th birthday business package selection specialist Capterra has produced an infographic charting the history of the bit you can't kick. It'll provide a trip down memory lane for anyone involved in computing.
The software industry as we know it, selling software separately from hardware, began in 1955 with the formation of the Computer Usage Company. Two years later an IBM mainframe (IBM dates back to 1911 by the way) was used by ADP to process payroll for the first time.
Other milestones include the foundation of SAP in 1972 and Microsoft in 1975. The first business accounting software for PCs, Peachtree, was released in 1978 followed a year later by Visicalc, the first spreadsheet.
In 1989 the first version of Microsoft Office was released and in 1993 Mosaic, the first web browser, entered the world. The graphic brings things right up to date with the rise of big data, tablets and wearables. It also looks at the future of software and charts the history of programming languages.
You can see the full infographic with lots more fascinating milestones below. Do let us know about your early software experiences in the comments.
Photo Credit: Elena Schweitzer/Shutterstock
-

Build your own 3D printer in 90 weekly parts
Publié: novembre 18, 2014, 4:50pm CET par Ian Barker

We've all seen those adverts for partworks allowing you to build a scale model of the Titanic at a cost not far off that of raising the real thing.
Now though UK publisher Eaglemoss Collections is producing a partwork that allows you to produce something a bit more useful. In 90 weekly parts it lets you make your own working 3D printer.
Up to now 3D printing has required expensive, complex equipment that’s meant it's been largely the preserve of industry and academic institutions. 3D Create & Print will give consumers the ability to build their own machine and safely print jewelery, games, figurines, mobile phone cases and many other objects.
The collection will be supported by its own website allowing users to download designs and software. There'll also be an online shop to purchase consumables and tools.
Maggie Calmels, Eaglemoss' senior VP, global creative and innovation says, "This collection also allows us to utilize our unique 'partwork' retail model; offering people the opportunity to purchase and build their own printer at small weekly costs, while the accompanying magazine is aimed at engaging readers and giving them the chance to learn more about the science behind the product".
The printer has been designed by Sebastian Conran, founding director of Sebastian Conran Associates, and is the first non-industrial model to come with a safety hood. "As 3D printing technology and applications become more mainstream, 3D printers are moving from the hi-tech workshop into the home, office and shed. Recognizing this trend and opportunity, we worked with Eaglemoss to develop a 3D printer that was more suitable for home use," Conran says.
3D Create and Print will be available in the UK from December 26th with the first issue costing £1.99 and subsequent issues £6.99 -- plus two premium issues at £14.99. For more information or to pre-order a subscription visit the www.3dprinter-collection.com site.
-

DGA malware evolves to get past security solutions
Publié: novembre 18, 2014, 4:12pm CET par Ian Barker

Malware developers are constantly shifting the goal posts in order to evade detection mechanisms. Part of this involves changing the domain names used to communicate with command and control servers and spread infections.
The latest trick identified by security company Seculert is the increasing use of Domain Generating Algorithms (DGAs).
The latest DGAs like that used by the Matsnu Trojan can create domains that are comprised of a noun, verb, noun, verb combination until the domain is 24 characters long. This attempts to bypass machine learning phonetic algorithms that are looking for domain names with no meaning.
The latest variant of Matsnu with the new DGA was first seen in June 2014 and has been targeting mainly German speakers, with 89 percent of infected users being located in the DE domain region. It's thought to spread mainly via spam emails relating to shopping sites.
Seculert's research has also uncovered that Matsnu can have additional capabilities added to it through an extension, enabling it to think on its feet, and adjust according to the obstacles in its way.
In addition it lets the user set the number of domains they want to generate daily as well as how many days in the past to reuse previously generated domains. It monitors the registry to ensure its run key is still present and renews it if it's been removed. Matsnu contains its own built in Uninstall function too allowing it to remove itself from systems.
There's more information about Matsnu and DGA malware on the Seculert blog.
Photo Credit: Balefire / Shutterstock
-

DDoS attacks fall as defenses improve
Publié: novembre 18, 2014, 3:15pm CET par Ian Barker

New research from DDoS protection specialist Black Lotus shows that cyber attack incidents have continued to decline throughout this year.
There were 201,721 incidents in the third quarter of this year (down from 462,621 in Q1 2014 and 276,447 in Q2). This can be attributed to the security industry's increased knowledge and filtering against NTP DrDoS types of attacks, as well as more proactive activity to stop malicious attacks before or as soon as they're detected.
The character of DDoS attacks is changing too. The average attack bit volume is increasing while the average packet volume is going down. A change of attack methods used, from large volumetric network-based attacks to more complex multiple vector attacks with application layer attacks and SYN flood attacks blended together accounts for this change.
DDoS attacks have declined in peak size and total incident count as NTP DrDoS attacks have largely subsided. This is thanks to better awareness in the security community about the threat of vulnerable NTP daemons, prompting administrators to upgrade from vulnerable versions and, in some cases, prompting network operators to filter potentially malicious NTP traffic.
When more effective zero day attacks aren't possible, attackers will often fall back to tried and tested methods of attacking systems. These include SYN floods and application layer attacks, which are often launched in tandem. The largest bit volume attack observed by Black Lotus in the last quarter was the result of a SYN flood against a Web server, largely sourced from Chinese networks.
Whilst most still come from China, the US and Russia, DDoS attacks are increasingly originating from Vietnam, India and Indonesia. These countries have a large number of compromised mobile end point devices which makes them prime sources of newly created botnets.
SYN flood attacks aren’t as dangerous to providers of internet infrastructure, since the bit and packet volumes are much lower and within the capacity of many tier 1 networks. However, they continue to pose a serious threat to service providers and enterprises that don’t have significant excess capacity and DDoS mitigation solutions in place.
You can find more information about the report's findings on the Black Lotus blog.
Photo Credit: Duc Dao / Shutterstock
-

One third of retail security breaches come from third-party vulnerabilities
Publié: novembre 18, 2014, 2:00pm CET par Ian Barker

The last year has seen a number of high profile security breaches involving retail businesses and there’s no sign of the trend slowing down.
Security ratings company BitSight Technologies has released some new research looking at the performance of 300 major US retailers over the past 12 months. It shows that 75 percent of retailers that suffered a data breach have improved their security effectiveness.
"While it's encouraging that a majority of the breached retailers have improved their security effectiveness, there is more work to be done, especially in the area of vendor risk management," says Stephen Boyer, co-founder and CTO of BitSight. "This trend in retail highlights the importance of proactive measures such as industry and peer benchmarking, as well as continuous monitoring of one's supply chain. We are seeing retail take steps in the right direction, with the formation of the Retail Information Sharing and Analysis Center to increase intelligence sharing among retailers in the US, but more improvements are needed".
BitSight uses publicly available data to rate the security performance of organizations. Ratings range from 250 to 900 with higher numbers indicating better performance. Key findings include that the of the 300 retailers analyzed 58 percent experienced a decline in overall security performance with an average 90-point decrease. The 34 percent of retailers that improved saw an average 70-point increase, while eight percent of retailers saw no net change in their Security Ratings over the past year.
Of the 20 large retailers that had a high-profile breach within the last year, nearly 75 percent saw an average increase of 50 points to their Security Rating score since their breach.
It's securing the supply chain that remains a challenge though. Nearly a third of all breaches in the retail sector began with a compromise at a third-party vendor. Organizations can take steps in securing their own networks, but ignoring risks posed by third-party partners can leave them exposed and vulnerable to breaches.
The findings also show that infections are increasing across a range of different threats with malware showing the largest increase. It finds that incident response times are up too, averaging 1.33 days in November this year compared to 1.26 in November 2013.
You can see an infographic summary of the report's findings below.
Photo Credit: nokhoog_buchachon/Shutterstock
-

When to find the best cyber shopping deals
Publié: novembre 17, 2014, 4:31pm CET par Ian Barker

'Tis the season to go and spend lots of money, as we approach Thanksgiving (in the US), Christmas, Black Friday, Cyber Monday and other shopping opportunities.
With November and December sales expected to top $616 billion dollars, payment processing specialist Merchant Warehouse has produced an infographic looking at what to expect from the holiday shopping season.
There are some interesting statistics, for example Thanksgiving has 229 percent more gaming deals than Cyber Monday and is the best time to shop if you’re looking for a TV or Blu-ray player. Black Friday is best for laptops, data storage and kitchenware, and Cyber Monday, interestingly, is the best time to buy clothes and shoes.
Shipping options are seen as increasingly important since in 2013 15 percent of Christmas eCommerce purchases arrived after 25th December. 70 percent of shoppers now say that shipping options are a key part of their buying experience.
The graphic rounds off with some tips on how to work the system to get the best deals. You can see the full thing below.
Image Credit: Slavoljub Pantelic / Shutterstock
-

87 percent of the top 100 paid iOS apps available as hacked versions
Publié: novembre 17, 2014, 2:37pm CET par Ian Barker

According to the third annual State of Mobile App Security report from application protection company Arxan Technologies, 87 percent of the top 100 paid iOS apps have been hacked.
Don’t feel smug if you're an Android user though as the report reveals 97 percent of the top 100 paid Android apps have been too. But whilst the Android figure is in line with previous years, the iOS percentage represents a jump from 2013 when 56 percent were found to have been hacked.
Before you start to panic, what Arxan means by a 'hacked' app, is one that's actually a modified version available from an unauthorized store or torrent site. In the case of iOS apps this also means the device needs to have been jailbroken.
The situation isn't much better with free apps. The report shows that 80 percent of popular free Android apps and 75 percent for iOS also have hacked versions available.
Not surprisingly high profile targets like banking are most at risk. 95 percent of the Android financial apps reviewed were 'cracked' while 70 percent of the iOS financial apps were hacked. This is an increase in both cases, with Android hacks growing about 80 percent.
Shopping apps are being targeted too with 90 percent of retail/merchant Android apps and 35 percent of iOS apps in the same field having been compromised. Hackers are targeting growth in B2C retail apps, as stores launch mobile payment and wallet services, but also B2B merchant point-of-sale apps. In both cases sensitive data, intellectual property, and financial transactions are at risk.
Also worrying is that 90 percent of Android healthcare/medical apps have been hacked, 22 percent of which are FDA approved.
With app downloads still increasing and forecast to reach 253 billion free and 15 billion paid in 2017 there are potentially huge numbers of people at risk if they venture into unofficial stores. Among the report's recommendations are that apps with high-risk profiles running on any mobile platform should be made tamper-resistant and capable of defending themselves and detecting threats at run time. Also that apps be developed to maintain the confidentiality of the code and that software used to enable mobile wallets and payment apps should be protected with secure crypto and app hardening.
"The pursuit of greater mobile application security remains at the forefront our research and development initiatives," says Jonathan Carter, technical director at Arxan. "We continue to evolve our security innovations based on emerging threats to ensure the strongest application protection for our customers in the dynamic battlefield against hackers".
The full report is available to download from the Arxan website and there's an infographic summary of the findings below.
Photo Credit: lucadp/Shutterstock
-

Uncovering the real value of online reviews
Publié: novembre 17, 2014, 11:11am CET par Ian Barker

We've become used to the fact that for pretty much any product or service we want to buy there will be reviews available online to help us with our purchase decision.
These reviews matter to businesses as they can have an impact on sales. Open review community Trustpilot has carried out a survey looking at how online reviews can influence the bottom line.
Findings include that 54 percent of companies fear the impact of negative reviews, however, 79 percent report that a mix of negative and positive reviews posted together have a positive financial effect on the business.
Collecting online reviews helps attract new customers according to 75 percent of companies and 25 percent say reviews improve loyalty. Plus 58 percent say that reviews help them identify opportunities for business improvement.
From the consumer side of the fence 62 percent say that they are more likely to do business with a company after reading a positive review. How a company deals with negative reviews is important too, 90 percent of unhappy customers will return if an issue is resolved quickly and effectively. Also 15 percent are more likely to do business with a company after reading a response resolving a negative review.
You can see an overview of the findings in infographic form below.

Image Credit: Rawpixel / Shutterstock
-

WatchDox finds and protects sensitive documents anywhere
Publié: novembre 14, 2014, 2:49pm CET par Ian Barker

With more and more data stored in the cloud or accessed from corporate systems on mobile devices, security and regulation becomes a major concern.
Enterprise file sharing specialist WatchDox has announced a new solution to both detect and protect sensitive files everywhere, on every device.
By integrating with Symantec Data Loss Prevention, WatchDox can now automatically and proactively protect sensitive files detected in motion on networks or emails, at rest in file shares and other repositories, and created on both mobile and PC endpoints.
This allows IT and security teams to apply controls to sensitive files on the fly. This can be encryption, digital rights management, tracking or revocation, and these continue to apply wherever the files travel. Traditional DLP solutions identify potentially sensitive data on the move, and flag it for action. Administrators then choose to ignore it or block it. However, blocking the data impedes workflows and letting it go involves risk.
WatchDox DLP solves this problem, protecting workflows but also enabling external collaboration. For example, a sensitive email attachment can still be delivered to the recipient, but be controlled, tracked and can even be revoked if it’s found that it should not have been shared.
"DLP is great at finding sensitive data, but historically it’s been hard to take action to protect that data without blocking someone’s workflow," says Ryan Kalember, chief product officer at WatchDox. "Through this integration, organizations can keep their workflows intact, while still securing the data, even when the sensitive data is involved in an external collaboration or on an unmanaged mobile device".
The new feature is available to all users of WatchDox Enterprise. There's a data sheet on how it works available to download and you can sign up for a free trial.
Photo Credit: Maksim Kabakou/Shutterstock
-

Beware the rise of the digital doppleganger
Publié: novembre 14, 2014, 12:48pm CET par Ian Barker

Data breaches in large organizations have made the headlines in recent years and that’s led to a huge increase in the amount of personally identifiable information being traded online.
According to UK credit report company CreditExpert there's been a 300 percent jump in the amount of personal information being traded online since 2012.
The company has produced an infographic analyzing this information. Interesting facts include that passwords are now more valuable than credit card details. The value of a username and password has continued to rise since 2010 whilst those of debit and credit card information are declining.
Despite this, 5 percent of Britons still use the same password everywhere and 10 percent never bother to change their passwords. The graphic shows how one stolen password can be used to expose other sites and ultimately steal an identity. Hackers can then go on to attack others in the victim’s social media networks.
The full infographic including tips on how to keep yourself safe is below.

Image Credit: Minerva Studio / Shutterstock
-

Microsoft acquisition boosts network defenses for enterprise customers
Publié: novembre 13, 2014, 4:51pm CET par Ian Barker

With more businesses adopting cloud and hybrid environments, protecting data is more important than ever but it’s also more complex.
Microsoft is looking to improve protection for its enterprise customers with today's announcement that it has acquired Aorato, an innovator in enterprise security.
Writing on Microsoft's official blog, Takeshi Numoto, Corporate Vice President of Cloud and Enterprise Marketing says, "We all know corporate security is more important than ever. Nearly every day there are more headlines about breaches, fraud and data loss. Unfortunately, compromised passwords, stolen identities and network intrusion are a fact of life. Companies need new, intelligent solutions to help them adapt and defend themselves inside the network, not just at its edge".
Aorato's technology uses machine learning techniques to detect suspicious activity on a corporate network. It understands what normal behavior is and then identifies anomalies, so a company can quickly see suspicious activity and take appropriate protection measures.
It uses an Organizational Security Graph, which is a continuously-updated view of all of the people and machines accessing an organization's Windows Server Active Directory (AD). AD is used by most enterprises to store user identities and administer access to critical business applications and systems. Since it leverages this existing technology existing Microsoft enterprise customers should be able to easily take advantage of the Aorato system.
Numoto adds, "This will complement similar capabilities that we have developed for Azure Active Directory, our cloud-based identity and access management solution".
An announcement on Aorato's website says, "At our core, Aorato has always been focused on strengthening enterprise security, by giving customers deeper visibility into their Active Directory and identity infrastructure with an emphasis on user behavior intelligence and analytics. Joining Microsoft gives us a unique opportunity to pursue this vision, and help customers at the broadest possible scale".
Image Credit: rosedesigns / Shutterstock
-

New solution secures and masks sensitive data for Amazon RDS databases
Publié: novembre 13, 2014, 3:18pm CET par Ian Barker

Securing data and making sure that it's stored in compliance with regulatory standards is a key task for all businesses, but it relies on knowing where the information is stored in the first place.
That isn't always as easy as it sounds but a new solution from database security specialist GreenSQL allows enterprises to easily identify all sensitive and regulated data fields across their Amazon Relational Database Service databases.
The software scans RDS databases to automatically identify sensitive fields, providing rapid implementation of regulation compliance, reporting and auditing, enabling data masking policies and enforcing role-based access to data.
"Without touching the database or applications, organizations are now able to instantly discover and protect their most sensitive data and achieve regulatory compliance," says Amir Sadeh, CEO of GreenSQL. "Users of Amazon RDS are now able to use one-click activation of polices for database monitoring, enforcement of duties and data-masking for every sensitive data field in their organization’s databases".
The company has also launched Dynamic Data Masking to allow users and applications to fulfill their job functions without ever gaining access to sensitive data fields. This makes for easier, faster and cheaper regulatory compliance as it hides data from unauthorized persons without making changes to databases or applications. As the data is never exposed to unauthorized employees or applications this reduces the risk of theft or abuse of information.
The solution is policy-driven, meaning that data masking policies can be defined by data table column, user or user role, client IP address and/or client application. Based on these policies, protected data fields are masked or randomized in real-time using a context-relevant template, allowing users and applications to function normally.
"GreenSQL’s out-of-the-box solution enables enterprises to easily identify and mask all sensitive and regulated data fields in their RDS databases," says Sadeh. "Without touching the database or applications, organizations are now able to instantly protect their most sensitive data and achieve regulatory compliance, among other benefits".
Both solutions are being launched at the AWS re:Invent conference this week, for more information visit the GreenSQL website.
Image Credit: wavebreakmedia / Shutterstock
-

Axway brings cloud B2B to Amazon Web Services
Publié: novembre 13, 2014, 10:52am CET par Ian Barker

Enterprises can be reluctant to move some functions into the cloud because of security and other concerns. So services that can allay these fears have big potential in the market.
Data flow specialist Axway already hosts secure private cloud portfolio solutions with AWS and has now announced that it’s making a Cloud B2B service available.
The Axway Cloud B2B Service enables companies to securely manage and integrate with their B2B communities in the cloud without the additional investment in hardware or labor resources common with legacy solutions.
Antoine Rizk, VP, Global Go-To-Market Programs at Axway says, "The solution has low initial cost and is scalable to allow for seasonal peaks. This also means a cloud solution becomes affordable for smaller companies."
Rizk belives there is large potential for the product as B2B cloud services currently only account for around six percent of the enterprise software market and will grow to 18-20 percent over the next five years.
Axway offers subscription-based product configurations that enable organizations to seamlessly connect their on-premises systems to their partner communities. The Cloud B2B Service includes extensive reporting, alerting and monitoring capabilities that enable companies to onboard, manage and interact with their communities through a cloud-based infrastructure, enterprise application integration, and advanced community management.
As Axway hosts its secure private Cloud portfolio solutions with AWS, it has access to infrastructure regions located around the world, including Western Europe, which helps protect the data integrity of its customers at all times.
"We designed AWS to enable our customers and partners to manage their computing needs through a highly flexible model, paying only for resources used and allowing organizations to avoid costly and time consuming traditional infrastructure," says Brian Matsubara, Head of Global Technology Alliances at Amazon Web Services, Inc. "By moving to the cloud Axway is able to take advantage of the scalable, reliable, secure and flexible technologies offered by AWS to power their Axway Cloud B2B Service technology, allowing them to focus on serving customers around the world."
Axway Cloud B2B Service is available now on the AWS Marketplace as a SaaS offering, or for more information visit the Axway website.
Image Credit: Lightspring / Shutterstock
-

The true cost of DDoS attacks on business
Publié: novembre 12, 2014, 5:03pm CET par Ian Barker

DDoS attacks can be extremely disruptive to business but it can be hard to quantify that disruption in financial and business terms.
A new report by security company Incapsula collates responses from 270 North American organizations of varying sizes to gauge the true impact of attacks. The findings indicate that DDoS attacks are relatively common with 45 percent of the respondents indicating their organization has been hit at some point. Of these, almost all (91 percent) reported an attack during the last 12 months, and 70 percent were targeted two or more times.
Larger organizations are more at risk with those having over 5,000 employees most likely to suffer an attack. The attacks tend to be short-lived though with 86 percent reporting a duration of 24 hours or less.
Motives for attacks vary too with respondents pretty evenly split between those who had and hadn't received a ransom note as part of an attack. 40 percent believe perpetrators were attempting to flood their organization’s network, 25 percent surmised they were trying to cause an outage by targeting specific applications, and 33 percent believe that both were the motivating factors.
In terms of business impact, 49 percent of DDoS attacks last between 6-24 hours so with an estimated cost of $40,000 per hour, the average DDoS cost can be assessed at about $500,000, though some are significantly higher. Costs aren't limited to the IT department either, they can have a large impact on security and risk management, customer service, and sales.
Among companies that had been targeted, 87 percent experienced non-financial consequences, such as loss of customer trust, loss of intellectual property, and virus/malware infection. 52 percent had to replace hardware or software, 50 percent had a virus or malware installed/activated on their network, and 43 percent experienced loss of consumer trust. Also 33 percent admitted to customer data theft, and 19 percent suffered intellectual property loss.
You can find out more and download a copy of the report on the Incapsula website.
Photo Credit: Duc Dao / Shutterstock
-

Software producers gear up for 'appification' of the enterprise
Publié: novembre 12, 2014, 4:05pm CET par Ian Barker

As consumers we're used to being able to download apps for just about any purpose. As we come to expect this sort of flexibility in enterprise applications too, a shift is needed in the way software is delivered in order to keep us appy -- sorry!
A new report by Flexera Software in conjunction with IDC suggests that a transformation is under way, paving the way for software vendors and intelligent device makers, including IoT manufacturers, to profit from the 'appification' of the enterprise.
What makes an appified enterprise is a shift to software that is task-oriented allowing employees to focus on things like sequencing a DNA molecule, executing email campaigns, or utilizing specific drone aircraft features.
To profit from task-oriented apps, producers need to alter their focus to target usage-based activities. According to the Report, this is exactly what's happening. 17 percent of producers indicate that they now offer utility software licensing models -- up from 9 percent in last year's survey. That number is forecast to grow to 23 percent over the next two years.
"As consumerization of IT gains hold within the enterprise, increasingly we’re seeing business users want more flexible buying models allowing them to align cost to value," says Amy Konary, Research Vice President - Software Licensing and Provisioning at IDC. "Usage-based licensing models give producers a new way to capture revenue from customers that want to pay based on how they’re actually using an application. Offering utility licensing can supplement more traditional monetization models such as device, nodelocked, processor, core and others".
In an appified enterprise, employees want app-store-like, one-click software access and activation rather than more traditional, complex license activation models like email or website activation. In the survey 44 percent of respondents report that they now distribute license keys/files via in-product activation.
This also marks the demise of technologies like the hardware dongle for securing licenses. Only 19 percent of producers report using hardware dongles as their licensing technology.
"The key to capturing a growing market of users who view enterprise software in a more app-centric way is to offer tailored licensing, activation and delivery models that appeal to this audience," says Mathieu Baissac, Vice President of Product Management at Flexera Software. "The challenge for producers is that it requires tremendous time, resources and money to build, manage and maintain in-house these myriad new and traditional licensing models, and track back-office customer entitlements. This is why adopting automated software monetization solutions is becoming increasingly essential for producers".
You can download the full report from the Flexera website.

Image Credit: logolord / Shutterstock
-

Cloud application security suite protects against DDoS and other attacks
Publié: novembre 12, 2014, 2:04pm CET par Ian Barker

Moving business applications to the cloud doesn't remove the need for securing them, in fact it potentially makes them more vulnerable.
Cloud application delivery service Instart Logic has announced a new Security Suite offering customers multi-layered protection against DDoS attacks and other cybersecurity threats.
It builds on the company's software defined application delivery (SDAD) platform, a software-based architectural approach that provides control, extensibility and performance.
Features of the suite include a secure ProxyWall that combines web application firewall capabilities with origin protection. It inspects plain text and SSL traffic and can issue alerts, set rate limits or block malicious traffic, designated user agents or IP addresses. ProxyWall also protects the origin server from non-HTTP(s) traffic and transmits 'clean' traffic from a dedicated connection to the Instart Logic cloud.
In addition the suite offers DDoS protection that absorbs denial of service (DoS) and distributed denial of service (DDoS) attacks. It has PCI DSS Level-1 compliance too so it can provides a dedicated environment for carrying out financial transactions.
"Instart Logic uses the same open source web application firewall engine and rule set for its Security Suite that are standard in the application delivery market," says Peter Blum, vice president of product management at Instart Logic. "What sets us apart is our patented SDAD platform, which delivers unmatched application performance -- especially over wireless networks. Now, customers don't have to choose between speed and security".
The Instart Logic security suite is available now, for more information visit the company's website.
Photo Credit: Slavoljub Pantelic / Shutterstock
-

Companies add more physical security to combat BYOD risks
Publié: novembre 12, 2014, 1:35pm CET par Ian Barker

According to a new survey carried out for security device specialist Kensington, 73 percent of executives recognize that BYOD presents greater risks for the organization.
However, 59 percent still approve the use of personal devices for business use and to address concerns 55 percent are planning to invest more in physical security.
"With the rapid rise in the use of BYOD mobile devices and laptops, organizations need to consider protecting their employees devices with physical security locks to protect them from the risk of theft and putting critical business and personal data into the wrong hands," says Judy Barker, Global Product Marketing Manager at Kensington. "By employing simple and secure device locking products, organizations can safeguard their data and mobile assets with an added layer of protection".
Security measures in use by respondents include 64 percent opting for employee training and guidelines, 61 percent using anti-malware and encryption, 55 percent having compliance and governance policies, and 48 percent using data loss prevention and authentication solutions.
There’s a summary of the findings in infographic form below.
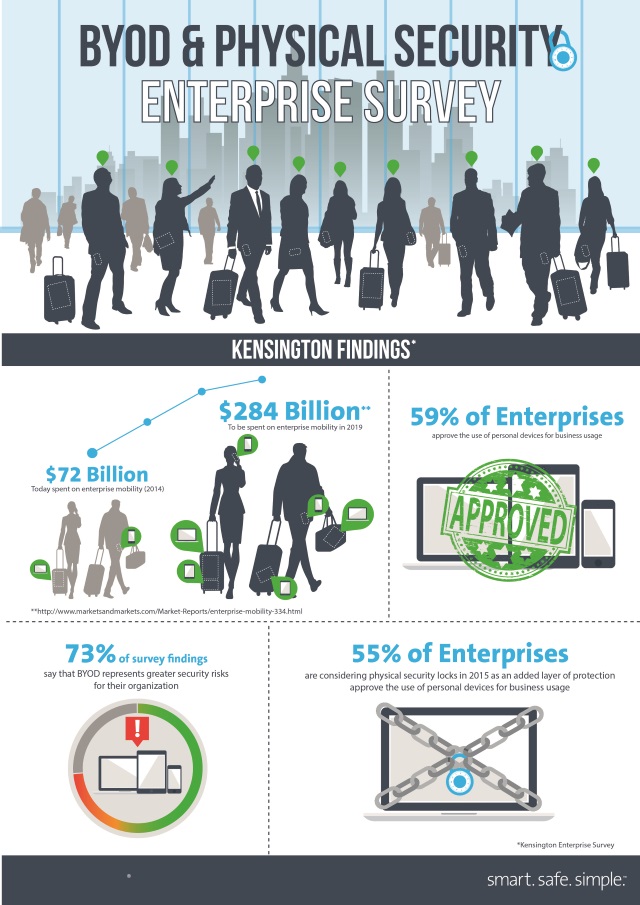
Photo Credits: Slavoljub Pantelic/Shutterstock
-

IT service problems are a weekly occurrence for over half of businesses
Publié: novembre 11, 2014, 3:47pm CET par Ian Barker

We all experience the frustration caused by IT issues from time to time, but a new survey by Forrester on behalf of operations performance specialist PagerDuty reveals that 55 percent of IT and business decision makers in the US experience IT service problems at least once a week.
What's more worrying is that 53 percent found out about the problems via users or external customers rather than through internal monitoring tools. Also 54 percent of respondents said their companies lacked adequate incident and problem management processes or didn't provide enough information to identify where the problem comes from.
The study points out that these problems often occur due to the approach taken to incident management. Companies may use multiple non-integrated monitoring tools, resulting in overlapping notifications and multiple sources of information and causing information overload for support teams.
Disorganized corporate culture may lead to teams focusing on passing the blame rather than collaborating to resolve problems quickly.
"Today's businesses desperately need a better way to manage their expanding collection of enterprise technologies to guarantee greater reliability in an always-on world," says PagerDuty CEO Alex Solomon. "I believe that this latest study from Forrester Consulting confirms the effectiveness of the holistic approach to incident lifecycle management that we have pioneered at PagerDuty".
The study suggests that by adopting a more strategic approach to solving problems and creating a unified operations center to manage incidents the impact on the business can be reduced and user satisfaction will be higher.
There needs to be a command center that is responsible for a broad overview of incidents. The second element is an automation center that owns the entire life cycle of incident resolution tools. Finally a service center or service desk to act as a center of excellence within the IT organization.
Whilst this takes care of the day-to-day handling of problems, businesses also need to understand the strategic importance of IT services and identify those which are most crucial. Incidents which affect customer service should always be given precedence.
The full report us available to download from the PagerDuty website.
Image Credit: alphaspirit / Shutterstock
-

Secure mobile platform helps smaller businesses adopt BYOD
Publié: novembre 11, 2014, 12:56pm CET par Ian Barker

Allowing employees to use their own devices for work is increasingly popular, but it can present problems for smaller businesses when it comes to implementing the technology and keeping it secure.
California-based hopTo has an answer for small and medium businesses in the form of its mobile productivity platform hopTo Work. The platform provides instant BYOD functions with a flexible and secure mobile workspace.
Using hopTo Work employees can access files, corporate email, SharePoint sites, and the organization’s intranet web services and storage locations, along with full editing capabilities for Microsoft Office documents in a rich, touch-friendly user interface.
"We have taken an entirely different approach to BYOD that will provide the ultimate user experience while still meeting the needs of IT departments for corporate security and governance," says Eldad Eilam, President and CEO of hopTo. "We designed the hopTo Work platform to allow mobile business users access to their workplaces by leveraging the devices they are carrying in everyday life. This will deliver an instant BYOD solution that both IT departments and end-users can agree to implement and begin using immediately".
The platform doesn't need any network configuration effort, which eliminates the complex planning and deployment stages required with other BYOD solutions. It also offers best-of-breed protection against data loss by ensuring that documents remain on the server while being edited and viewed, rather than on the end-user’s devices. This means the organization retains full control over the flow of content, so documents are never at risk of leaking outside the organization.
Key hopTo Work features include a seamless user experience with the ability to multitask using multiple tabs, enabling users to easily switch back and forth between projects. Touch-friendly access to all permitted documents on the corporate network from a variety of sources such as SharePoint, local files, network shares, etc. Access to all Windows applications and rich, touch-friendly editing capabilities for Office documents (Excel, Word, and PowerPoint) on the mobile device.
Early next year hopTo Work will receive additional enhancements including support for secure web browsing through the corporate network as well as support for secure access to corporate email in a native iOS user interface.
Introductory pricing is available until January 1st 2015 and you can find out more on the hopTo website.
Image Credit: Peter Bernik / Shutterstock
-

SAP helps business embrace the internet of things
Publié: novembre 11, 2014, 11:10am CET par Ian Barker

A recent report by Gartner predicts that there will be 4.9 billion connected 'things' in use in 2015 and as many as 20 billion by 2020.
There’s little doubt that the internet of things is set to have a big impact which will be felt across enterprises and homes. Business systems specialist SAP is keen to be at the forefront and is using its TechEd conference in Berlin to announce three new IoT solutions.
"The Internet of Things will be the key enabler of industry scenarios and of innovations in the digital economy," says Bernd Leukert, member of the Executive Board of SAP SE, Products & Innovation. "It is converging our digital and physical worlds, which will spur new products and services, and even change business models. The Internet of Things has the potential to dramatically improve responsiveness of businesses, re-imagine customer experience and open up new opportunities and brand new business models such as move from sell-to-service based models. SAP customers that have already implemented Internet of Things solutions have seen considerable improvement in asset utilization and higher business process efficiency and helped address operational costs".
The IoT solutions are powered by the existing SAP HANA Cloud Platform which offers features including in-memory computing, predictive analytics and complex event processing. In addition, it has open APIs that allow third-party providers to develop IoT applications.
The three new applications announced today are; Predictive Maintenance and Service, Connected Logistics and Connected Manufacturing.
Predictive Maintenance and Service will help assess historic and sensor data to assist users in predicting a malfunction before it occurs and prevent a negative impact on profits. It will be able to automatically generate work requests for field service technicians when a device is failing.
Connected Logistics is planned to allow logistics hub operators and others to monitor traffic toward and within a hub and facilitate communication between involved parties including those that don't have a direct business relationship. It will also use a recently announced AR warehouse picker mobile app that uses wearable technology, such as smart glass devices, for a complete hands free operation, helping to eliminate the need for handheld scanners.
Finally Connected Manufacturing is aimed at optimizing global operations. It will allow businesses to use predictive analytics to drive cost efficiencies and achieve higher asset utilization.
You can find out more about SAP and the internet of things on the company's website.
Image Credit: PlusONE / Shutterstock
-

Darkhotel steals data from traveling executives
Publié: novembre 10, 2014, 3:36pm CET par Ian Barker

Darkhotel sounds like it ought to be one of those budget hotel chains you find on the outskirts of towns -- possibly one built without windows to keep costs down.
In fact researchers at Kaspersky Lab have revealed that it's an espionage campaign, which has been operating for almost a decade, that steals sensitive data from corporate executives traveling abroad.
It works by hitting its targets while they're staying in luxury hotels. Never going after the same target twice it operates with surgical precision, obtaining all the valuable data it can from the first contact, then deleting traces and fading into the background to await the next high profile victim. 90 percent of the infections seen by Kaspersky have been in Japan, Taiwan, China, Russia and Hong Kong, but it has also detected infections in Germany, the USA, Indonesia, India and Ireland.
The Darkhotel perpetrator places software on hotel networks and the unsuspecting victim downloads it with the welcome package when connecting to the hotel's Wi-Fi. Once on a system, the backdoor may be used to further download more advanced tools such as keyloggers and Trojans. These tools collect data about the system and the anti-malware software installed on it, steal all keystrokes, and hunt for cached passwords and other private information. Victims lose sensitive information likely to be the intellectual property of the businesses they represent. After the operation, the attackers carefully delete their tools from the hotel network and go back into hiding.
Kurt Baumgartner, principal security researcher at Kaspersky Lab, says, "For the past few years, a strong actor named Darkhotel has performed a number of successful attacks against high-profile individuals, employing methods and techniques that go well beyond typical cybercriminal behavior. This threat actor has operational competence, mathematical and crypto-analytical offensive capabilities, and other resources that are sufficient to abuse trusted commercial networks and target specific victim categories with strategic precision".
Kaspersky Lab recommends that when traveling, all networks should be treated as suspicious. Executives are advised to use VPN to get a secure network channel to their company systems and to treat any software updates they may be offered when on unfamiliar networks as potentially harmful.
You can find more information about Darkhotel on the Kaspersky Lab blog.
Image Credit: Dragon Images / Shutterstock
-

Fileless malware runs entirely from memory to make detection harder
Publié: novembre 10, 2014, 11:49am CET par Ian Barker

Traditional malware infections usually require a file object to be placed on the system which makes it relatively easy for them to be detected and removed.
Now though there’s a stealthier threat uncovered by security company Malwarebytes. Poweliks is an infection that runs without a filesystem object, completely from the registry and memory using rundll32.exe, javascript and a create on-the-fly dll.
Code can be injected into the machine via a fake landing page which makes traditional security solutions like white listing ineffective in combating it.
It doesn't place a physical file on the system, instead Poweliks injects code into processes which are currently running, like Internet Explorer. This allows it to run on the back of the legitimate process and thus avoid detection.
Security researcher Jerome Segura says, "There are many advantages of doing that. For starters, by never dropping anything onto the hard-drive, you reduce your payload's footprint on a system and chances for it to get detected. It is typically much easier to detect a piece of malware on disk than one hiding in memory".
To ensure that it can survive after a system restart it places code in hidden registry keys allowing it to execute and infect the legitimate process again after a reboot.
A newly released version of Malwarbytes Anti-Rootkit is able to remove Poweliks. There's also more information on fileless infections and how they work on the Malwarebytes blog.
Image Credit: alphaspirit/Shutterstock
-

Usability survey reveals the most frustrating websites
Publié: novembre 7, 2014, 1:59pm CET par Ian Barker

We've all encountered websites that are badly designed or seem to be willfully hard to use and now a new survey reveals the sites which cause the most frustration and are likely to be rapidly abandoned.
Website FAQ technology provider AnswerDash has released the results of its first website survey revealing Comcast.com, IRS.gov and CenturyLink.com as this year's most frustrating websites for US consumers.
Those that get it right are Amazon.com, Facebook.com and Apple.com which yielded the highest scores in terms of website usability among survey respondents.
The survey also shows that we're quick to give up and move on when a site doesn't deliver what we want. Among 18-24-year-olds, 75 percent will abandon a website within two minutes if they can’t find what they need. 57 percent of those 55-years or older abandon a website in two minutes or less, with 28 percent indicating that they would spend only 4 minutes trying to accomplish their task on a website before leaving. Across all demographics the average abandonment time is 90 seconds.
"As e-commerce grows, and particularly in the light of the upcoming holiday season, delivering an excellent online user experience is imperative to helping propel consumers along the path to purchase," says AnswerDash CEO Jake Wobbrock. "We conducted this survey to provide companies with actionable insights around website usability, and the results are telling. Companies face a huge opportunity to provide an intuitive online experience by including website support tools, such as Contextual FAQs, that reduce abandonment through improved user experience".
Key findings include that more than half of consumers (59 percent) selected Comcast.com as this year's most frustrating website. While consumers said the IRS and CenturyLink websites were also difficult to use, they both out performed Comcast, at 37 percent and 35 percent disapproval, respectively.
Microsoft's website is more difficult to use than Apple's according to consumers, with 20 percent stating that the Microsoft site is confusing, compared with only 6 percent who get flummoxed by Apple’s website.
Of US government sites, the IRS is rated most frustrating, with Healthcare.gov ranked as the easiest, just edging out the Department of Motor Vehicles. In e-commerce Amazon leads the way with over 70 percent of consumers approving its ease of use, Target comes bottom with 16 percent selecting it as the most frustrating site.
Are there any sites you find particularly frustrating? Do let us know.
Image Credit: Syda Productions/Shutterstock
-

Brace yourself for a bumper Patch Tuesday say experts
Publié: novembre 7, 2014, 12:02pm CET par Ian Barker

Next week's round of Patch Tuesday updates from Microsoft is set to be the biggest so far this year with 16 bulletins in total, five of which are rated Critical and nine as Important.
Most of the Critical bulletins are for Windows components and affect a range of supported systems. Karl Sigler, Threat Intelligence Manager at Trustwave says, "If you are currently running a supported version of Windows, you will want to update as soon as these updates become available. These are some of the nastier vulnerabilities we've seen in Windows in a while".
It's likely that one of these bulletins will address the OLE remote code execution for which a security advisory was published last month. Exploits have continued in the wild and it’s likely that two or three of the critical patches will address this according to Chris Goettl, product manager with enterprise systems specialist Shavlik.
There will be an update to .NET Framework too which Goettl says, "...usually means a little longer time on the maintenance window as those patches tend to take a little longer than the average OS patch to install".
Patches for the Windows 10 and Windows Server Technical Previews will be available in this round too which is a good opportunity to try out the update process on the new OS.
Wolfgang Kandek CTO of Qualsys points out that despite the large number of updates this month, "Overall the additional 16 bulletins will bring Microsoft's count up to 79, meaning that we will finish the year under 100 vulnerabilities, which is a bit lower than in 2013 and 2011 and probably on par with 2012".
Kandek believes that bulletin 2, which covers all versions of Internet Explorer from IE6 on Windows 2003 to IE11 on Windows 8.1, should be the highest priority for admins since there's a whole underground industry developing browser exploit kits.
The Important bulletins address Windows, the .NET runtime framework and Word along with the SharePoint and Exchange servers. If you have automatic updates turned on all of the required updates will be downloaded as they become available. A reboot will be needed to complete the installation.
Adobe has put out Flash updates on all but one of this year's patch Tuesdays, so you can add that to your list of things to do too.
Image Credit: alexskopje / Shutterstock
-

Dell Cloud Marketplace simplifies selection and purchasing
Publié: novembre 6, 2014, 3:58pm CET par Ian Barker

Cloud adoption is booming amongst business users, but there's a big variation in what developers and IT managers want from their cloud deployments.
Developers want instant access to cloud services and true self-service capabilities, while IT managers require greater control, visibility and integration across the whole cloud spectrum.
The beta launch of Dell Cloud Marketplace gives both developers and IT managers the ability to compare, purchase, use and manage public cloud services from Amazon Web Services (AWS), Google Cloud Platform and Joyent via a single, unified console on the dell.com site.
Cloud Marketplace gives users the tools they need to select the best cloud services and solutions to meet their unique requirements. With management, governance and security built in. It streamlines the buying and deployment of cloud services, allowing customers to use single, multiple and hybrid cloud environments across several users and various accounts.
"The Dell Cloud Marketplace epitomizes the Dell Cloud strategy of offering customers choice and flexibility while simplifying the cloud experience," says Nnamdi Orakwue, Vice President, Software Strategy, Operations and Cloud at Dell. "Developers benefit from the ease of multi-cloud purchases and the immediate use of cloud services. IT managers benefit from the governance, secure management and single billing of multiple cloud services. By combining those benefits with the strengths of Delphix, Docker and Pertino, together we will knock down the hurdles to using multiple cloud services effectively so customers can unlock the full potential of the public cloud ecosystem".
In addition to the marketplace Dell has announced alliances with Delphix, Docker and Pertino. Solutions from these companies will be made available via the Dell Cloud Marketplace next year, allowing users to subscribe to these offerings along with the public cloud infrastructure resources of their choice.
Dell Cloud Marketplace beta is now available in the US and you can sign up at www.dell.com/cloudmarketplace there’s also more information on the company's blog.
Image Credit: Dell Inc.
-

Consumers are looking for long-term relationships with online sellers
Publié: novembre 6, 2014, 12:24pm CET par Ian Barker

It's easy to assume that the range of choice available when buying online leads to a lack of consumer loyalty with people shopping around for the best deal.
However, a new survey from e-commerce specialist Avangate suggests that customers are looking for a long-term relationship with providers of online services.
Findings of the survey include that 60 percent of consumers have set up at least one or two recurring payments online. 46 percent refuse to purchase online subscriptions without a 'freemium' option and almost 40 percent prefer to pay bills online.
The ability to compare is still important though with 45 percent comparing three to four online channels before making a purchase decision. Payment methods remain resolutely conservative with 99 percent of consumers not using Bitcoin and the one percent who do not using it as their primary payment method.
Mobile payments are catching on but mainly among younger age groups. In total 52 percent of consumers have used their mobile to make a purchase. But while 30-44 year olds are most active with 30 percent making monthly mobile payments, 72 percent of over 60s have not used a mobile to make a payment.
The main concern with mobile payments is security with 22 percent of consumers saying that they don’t feel secure when making mobile payments, but they do it anyway.
"Today, we are seeing the digitization of products into services -- what we are calling the 'New Services Economy' -- and it's spawning the next generation of software and online services companies that are redefining commerce. For these new service providers and vendors, the ability to truly monetize their offerings is no longer about point payment transactions with the customer, but rather being able to interact, service and expand the relationship with the customer from the discovery, trial, and add-on and retention phases -- all of which are potential opportunities to make purchasing decisions," says Carl Theobald, CEO at Avangate.
Avangate has added more than 200 new features to its Commerce Solution for Service Providers to help businesses exploit online revenue streams. You can find out more on the Avangate website and see more details of the survey findings in the infographic below.
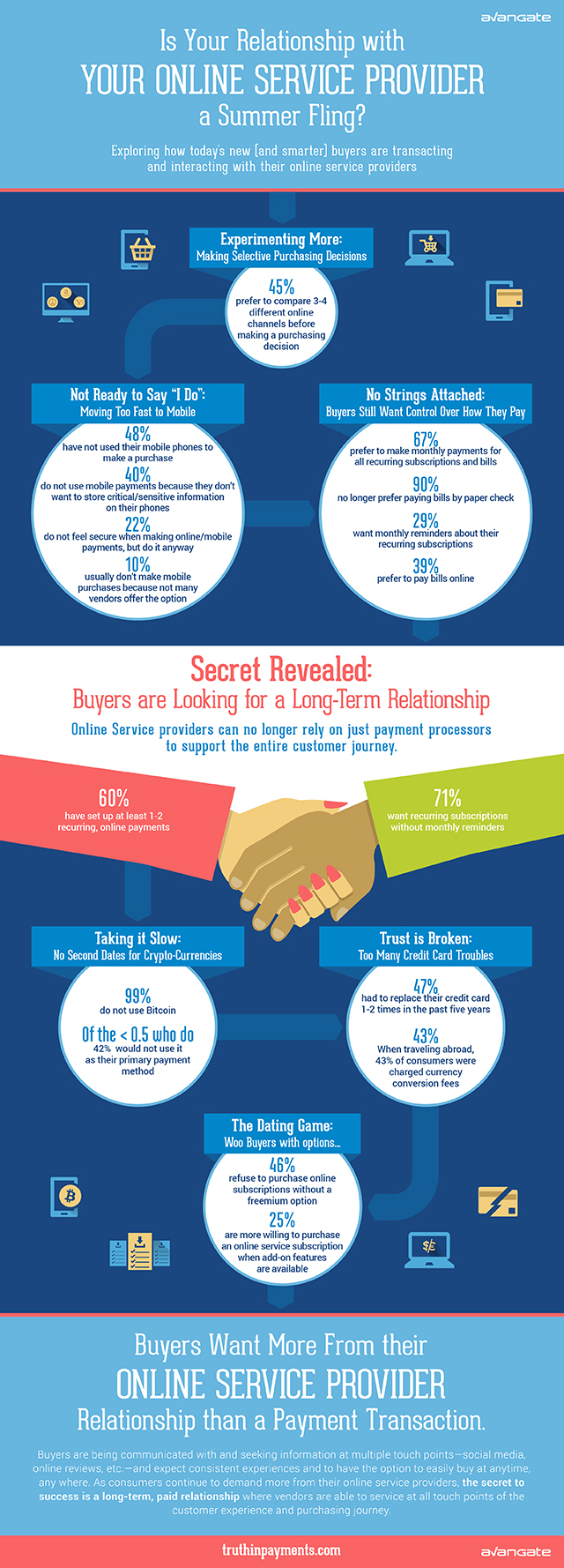
Photo Credit: Nonnakrit/Shutterstock
-

Backupify adds HIPAA compliance to enterprise security features
Publié: novembre 5, 2014, 5:26pm CET par Ian Barker

Cloud backups are all the rage at the moment, but they do raise security concerns, particularly for businesses that deal with sensitive information.
Cloud to cloud backup specialist Backupify has added some new features to its service to make it more secure. These include HIPAA (Health Insurance Portability and Accountability Act) compliance as well as new features for admins.
"Given all the changes in the regulatory landscape, Backupify wanted to get independent verification that we meet the required standards for HIPAA compliance," says Ben Thomas, VP of Security at Backupify. "We now have third party validation through an independent audit which should help customers feel even more comfortable entrusting their data to Backupify. As we build innovative backup solutions, data security remains a core focus. It always has been and always will be".
All companies dealing with protected health information (PHI) must ensure the right security measures are in place and followed. While Backupify doesn’t interact with PHI directly, the company does have many healthcare organizations as customers and therefore felt it necessary to meet HIPAA compliance requirements.
In addition to HIPAA, Backupify is self-certified in compliance with the US Department of Commerce Safe Harbor program. It also allows customers to store data in Amazon's VPC (Virtual Private Cloud), and goes beyond using Amazon's built-in bucket-level encryption, with every Backupify account receiving a unique AES 256-bit encryption key. Backupify has also renewed its SOC 2 Type II compliance which reviews Backupify's backup and recovery system to ensure that controls are suitably designed to protect financial information.
You can read more about Backupify's security on the company's blog.
Photo Credit: jörg röse-oberreich/Shutterstock
-

Badly secured routers leave 79 percent of US home networks at risk of attack
Publié: novembre 5, 2014, 4:40pm CET par Ian Barker

As many as four out of five internet-connected households in the US could be at risk of attack through their wireless router.
This is among the findings of a study by security specialist Avast which found that more than half of all home routers are poorly protected using default or easily hacked password combinations such as admin/admin or admin/password.
It also found that 25 percent of consumers use their address, name, phone number or other easy to guess items as their router passwords. "Unsecured routers create an easy entry point for hackers to attack millions of American home networks," says Vince Steckler, chief executive officer of Avast. "Our research revealed that the vast majority of home routers in the US aren't secure. If a router is not properly secured, cybercriminals can easily gain access to an individual’s personal information, including financial information, user names and passwords, photos, and browsing history".
Among the biggest threats to any Wi-Fi network is DNS hijacking. This involves malware being used to exploit vulnerabilities in an unprotected router to redirect the user from a known site, such as a bank website, to a fake site designed to look like the real thing. When the user logs in, hackers capture the user’s login credentials and can then use them to access the real site.
Less than half of Americans strongly believe their home network is secure, according to the survey and 16 percent of respondents said they had fallen victim to hackers. This is despite being aware that a breach can lead to their bank or financial information being stolen (42 percent were concerned about this), losing personal information (33 percent), having their browsing history stolen (11 percent), and getting their photos hacked (9 percent).
"Today's router security situation is very reminiscent of PCs in the 1990s, with lax attitudes towards security combined with new vulnerabilities being discovered every day creating an easily exploitable environment. The main difference is people have much more personal information stored on their devices today than they did back then. Consumers need strong yet simple-to-use tools that can prevent attacks before they happen," says Steckler.
You won't be surprised to learn that the recently launched Avast 2015 is able to identify and protect against network threats including DNS hijacking and weak passwords.
Image Credit: Piotr Adamowicz / Shutterstock
-

Faster cloud deployments with Metalogix
Publié: novembre 5, 2014, 3:34pm CET par Ian Barker

Many businesses are put off moving their systems to the cloud by the complexity and time involved to complete the transfer process.
To help overcome this problem management tools specialist Metalogix is launching a Cloud Acceleration Suite along with a Partner Program to help businesses deploy collaboration abilities on their chosen cloud platform.
It works with Office 365, Microsoft Azure and Amazon Web Services, as well as hybrid and private cloud systems. By bringing together migration and management tools from Metalogix with Microsoft qualified cloud deployment partners it offers organizations a start-to-finish solution to rapidly migrate email, files and SharePoint content to the cloud.
The Cloud Acceleration Suite uses expert tools to provide IT professionals with a single, unified solution for the migration of email, files and SharePoint content into OneDrive for Business, Office 365 and other cloud-based platforms. Employees are also given simple and secure tools to move business content from their personal cloud storage into their corporate cloud accounts. Once migrated to the cloud, the suite then provides tools for the on-going management of sites, security, users, content and metadata.
"Successful cloud deployments combine the right set of tools and the right expertise to accelerate migration to and adoption of cloud-based collaboration platforms," says Steve Murphy, CEO of Metalogix. "So today, we are launching the Cloud Acceleration Suite and Partner Program to provide clients the tools, training and expertise they need to overcome the unique deployment and user adoption challenges of rolling out a cloud-based collaboration platform".
The Partner Program gives clients access to experts in cloud deployment who can help at each step of their cloud transition including developing a migration road map, establishing governance and management processes and ensuring sensitive content stays secure.
You can find out more about both the Cloud Acceleration Suite and the Partner Program on the Metalogix Website.
Photo Credit: IdeaStepConceptStock/Shutterstock
-

Insightpool updates its audience analysis tools for marketers
Publié: novembre 4, 2014, 5:40pm CET par Ian Barker

Understanding the audience is key to success in marketing and thanks to our ability to gather data from transactions and social networks there's more opportunity to analyze customer actions than ever before.
Atlanta-based Insightpool is launching a new version of its audience cultivation and conversion platform aimed at giving brands greater insight into and control over their marketing.
Insightpool 2.0 uses predictive analytics and machine learning to drive conversion and return on investment for brands. Instead of needing to piece together multiple tools or services to execute large scale digital campaigns, users can target the audiences most likely to engage with a brand. They can also drill down into the most relevant set of messages to produce the desired results.
The platform delivers real time, goal-specific analytics so that brands can easily understand what resonates with individuals and tailor their efforts accordingly.
"Marketing software is mature enough that ROI should be expected as it is in any other technology category. Because Insightpool is focused on conversion, we can deliver results that drive the bottom line and not just vanity social metrics," says Devon Wijesinghe, Insightpool's CEO. "Insightpool's level of sophistication for social marketing is unrivaled, and completes the full engagement cycle to achieve measurable business results that scale".
Using proprietary algorithms that can be custom tuned for specific organizations, Insightpool can predict social engagement using over 60 variables. It can integrate with existing social media management software so that businesses can take advantage of its insights without upsetting their existing operations.
Key features of version 2.0 include 'social drip' campaign management and optimization designed to generate leads. Social predictor rankings that use proprietary algorithms and machine learning to analyze and identify people with the highest potential for conversion. It also allows easy identification of the most effective messages along with social customer relationship management integration and a real-time dashboard for easy management.
You can find more information on the Insightpool website.
Image Credit: Kidsana Maimeetook / Shutterstock
-

Dropbox partners with Microsoft for improved Office integration
Publié: novembre 4, 2014, 5:28pm CET par Ian Barker
In an unexpected announcement today Microsoft and Dropbox have revealed that they're joining forces to integrate Dropbox more closely into Office.
The link up will allow Office files to be edited directly from the Dropbox mobile app and the changes synced across devices. It works the other way too with access to Dropbox from within Office.
Dropbox links can also be shared directly from within the Office app. The changes will roll out to all users of Dropbox for Android and iOS over the next few weeks. They'll be available for Dropbox for Business customers with Office 365 licenses too.
Microsoft's Office blog also confirms that next year connections will be added to both Dropbox and Office Online web services.
Writing on the Dropbox for Business blog Ilya Fushman, head of product for Dropbox and Dropbox for Business says, "With this partnership, we're bringing the magic of the Dropbox and Office desktop experiences to mobile and the web. What does that mean for you? In short: boundless productivity. You'll be able to edit Office documents right from your Dropbox mobile app, and access your Dropbox from within your Office apps".
You might wonder where this leaves Microsoft's own OneDrive cloud storage service which will continue to appear alongside Dropbox in Office apps. It seems that Microsoft is simply recognizing that with Dropbox for Business in use in over 80,000 organizations worldwide, and the service being home to more than 35 billion Office documents, it simply can't afford to ignore a potentially valuable source of users.
"In our mobile-first and cloud-first world, people need easier ways to create, share and collaborate regardless of their device or platform," says Satya Nadella, CEO of Microsoft. "Together, Microsoft and Dropbox will provide our shared customers with flexible tools that put them at the center for the way they live and work today".
Is this a surprising announcement or is it an inevitable consequence of the state of the cloud storage market? Let us know what you think in the comments.
-

All the web's a stage as Shakespeare goes on-demand
Publié: novembre 4, 2014, 3:09pm CET par Ian Barker
Shakespeare's Globe in London is known for its productions of the bard's plays in an atmosphere close to their original environment.
Now the Globe is going global with the launch of a new online video platform offering full-length HD films of its productions to rent or buy on demand in a world first for a theater.
Every foreign-language production from the 2012 'Globe to Globe' festival of international Shakespeare has been made available on film, along with the main productions from the 2012, 2011, 2010 and 2009 summer seasons.
Last year's touring production of the three Henry VI plays are also available now and 2013's main titles, The Tempest, A Midsummer Night's Dream and Macbeth will be available online in the coming months.
Dominic Dromgoole, Artistic Director of Shakespeare's Globe, says, "Whether we're touring the world, inviting the world to the Globe, or being the first to experiment with low ticket prices with our £5 groundling tickets, the Globe is always looking for bold new ways to take Shakespeare out into the world and share his astonishing plays with as many people as possible. Globe Player will allow us to reach brand new audiences and to make access to our productions simple and seamless for anyone with the internet. We are delighted to be the first theatre with its own dedicated video-on-demand platform".
Globe Player also hosts a range of other material including footage gathered in the making of the film Muse of Fire, available free to allow people to try out the site. Other content either available now or coming soon includes dozens of short films from the New York Shakespeare Exchange’s Sonnet Project and the feature-length documentary A Summer Hamlet.
The player has been created by Qip Creative, a digital agency founded by two recent Cambridge graduates and specializing in innovative online shopping and other projects.
You can try out Globe Player now. Rentals cost £2.99-£4.99 (around $4.80-$9.60) and purchases £4.99-£9.99 (around $9.60-$15.99).
-

Microsoft breaks down business barriers with new cloud solutions
Publié: novembre 4, 2014, 12:33pm CET par Ian Barker

With Azure and Office 365, Microsoft already has a strong position in the business cloud market. But the company isn't resting on its laurels, it used this week's Convergence 2014 conference in Barcelona to announce a number of innovations to help enterprises gain greater benefit from the cloud.
The main announcement is that the latest Microsoft Dynamics CRM 2015 release will be generally available in December this year. The new release is designed to address the growing need for businesses to deliver seamless experiences to their customers by helping them break down the barriers between divisions.
New capabilities in this release include advancements in natural user interface and integration with Cortana -- the intelligent personal assistant on Windows Phone 8.1. With Cortana, users will be able to set up meetings and reminders; search for contacts, accounts and activities; view customer lists; and create new customer records -- all using voice commands.
There will also be platform updates allowing companies to create pre-defined, configurable processes, along with API enhancements to ensure consistency across devices. Templates will be made available to help customers with industry-specific requirements.
Other announcements include a Sales Productivity solution for Office 365 and a partnership with Thunderhead.com. The Thunderhead.com link will offer a complete customer engagement solution bringing together the Microsoft Dynamics CRM platform and Thunderhead.com's ONE Engagement Hub. This will enable marketers to build customer engagement by tying together customer insight, context and behavior.
There's a new version of Microsoft Dynamics AX, the company's flagship ERP solution, too. The update allows businesses to combine all the benefits of Dynamics AX and Azure in an end-to-end cloud solution. It lets companies run hybrid environments with an optimal mix of development, test and production. Plus it adds a new Point-of-Sales client for Windows tablets and phones, giving in-store staff the ability to access product and customer information at their fingertips to deliver improved shopping experiences.
Microsoft also showed off a new Dynamics NAV 2015 release that adds a tablet and touch-optimized user experience. This will allow small and mid-sized business customers to access their company data and processes regardless of location or device.
"To better engage with their customers, businesses are looking to the cloud for greater collaboration and the right insights to help them be more productive," says Microsoft Business Solutions executive vice president Kirill Tatarinov. "Microsoft is re-imagining and reinventing productivity by harnessing the power of the cloud through a flexible platform in Azure, a cloud productivity suite in Office 365, and customer-centric business applications delivered through Microsoft Dynamics solutions that are helping organizations transform the way they engage with customers and run their business".
Tatarinov's full keynote speech is available on demand if you want to learn more.
Photo Credit: Sakonboon Sansri/Shutterstock
-

The smarter the phone the harder the fall
Publié: novembre 3, 2014, 1:08pm CET par Ian Barker

Using your smartphone can be dangerous according to findings from a new study by gadget insurance specialists SquareTrade and it's people as well as devices that are getting damaged.
A poll of UK smartphone owners found that a stunning -- or possibly stunned -- 86 percent had tripped, stumbled or hit a lamppost or wall when distracted by using a mobile device. Stumbling incidents accounted for 37.2 percent of people damaging their phones in the last two years with over half of all accidents happening in the home. Also 18 percent of accidents were caused by someone other than the phone owner.
Brits aren't the clumsiest in Europe though -- 40 percent of Greek smartphone users managed to damage their phones in stumbling incidents the last two years. Whilst over the same period, 39.8 percent of Italian and 38.9 percent of Spanish smartphone users had slipped up when using a phone. Maybe the Mediterranean climate has something to do with it?
Least likely to have accidents whilst using their phones are the Poles (24.3 percent), Belgians (24.9) and Swiss (26.3). Kevin Gillan, SquareTrade's European managing director says, "While the percentage of smartphone tumbles varies from country to country, it’s clear that there are a lot of people out there who have damaged their phone and themselves in some way. Talking and walking are perfectly safe, but perhaps our smarter phones are now putting us at risk by diverting our eyes off the path ahead".
Doctors too are reporting an increase in the number of people admitting to having mobile-related mishaps. Dr Louise Newson, a British GP, says "I've seen a lot of mobile-related injuries in my surgery in the last 12 months, mostly from people tripping or bumping into something because they've been distracted by their smartphone. Some of the injuries are quite nasty. As more young children and elderly people are using mobile phones, I expect that we’ll see more mobile-related injuries in these groups of people in future".
You can see a breakdown of Europe's clumsiest countries when it comes to damaging smartphones in infographic form below. And if you've had a mobile related accident do let us know in the comments. We promise not to laugh.
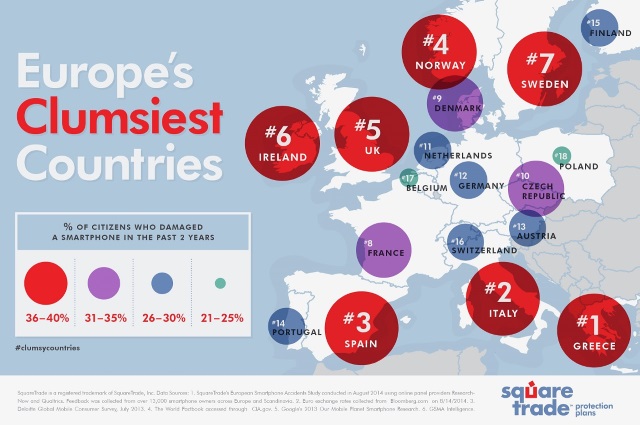
Image credit: Stokkete / Shutterstock
-

Mobile devices make sales work more complicated
Publié: octobre 31, 2014, 1:29pm CET par Ian Barker

We're frequently being told that the use of mobile devices makes our work lives easier, but it seems that a sizable percentage of people don't share that view.
Mobile sales solution company Seismic has released the results of its Salesforce Spotlight survey showing the complex relationship between business users and mobile technology.
The survey carried out amongst Dreamforce attendees reveals that Salesforce is still the main platform for handling sales data and that 57 percent of respondents use the package for more than two hours a day. When it comes to mobile access though, 21 percent said they had no plans to implement the Salesforce1 platform.
Of those who have already implemented Salesforce1, 66 percent say they access it via both smartphone and tablet. Those that use it on just one platform favor their smartphones, but more than 60 percent of respondents using both reached for their tablet more frequently than their smartphone for CRM, content management and presentation tasks.
Perhaps most interesting though is mobile's perceived impact on working lives. Whilst the previous survey in 2013 showed that seven percent of Dreamforce users thought mobile technology would complicate their work life, this year's findings show nearly 20 percent feel that mobile technology has made their work lives more complicated in the past year.
"While our survey findings validate the growing importance of mobile devices in the enterprise, it was surprising to find that users view mobile technology as a complication to their work lives," says Seismic CEO Doug Winter. "Cutting-edge mobile technologies should be simplifying marketing and sales processes, not complicating them. Organizations need to become more strategic and agile when implementing new software if they want to gain a competitive advantage".
The full report is available to download from the Seismic website.
Image Credit: Sergey Nivens / Shutterstock
-

Getting the basics of network security right
Publié: octobre 31, 2014, 12:22pm CET par Ian Barker

With every new breach, network security hits the news, yet many people and companies still don’t get the basics right.
UK-based wireless network specialist Exigent Networks has produced an infographic that looks at the importance of network security and offers tips and expert advice.
It covers the essentials of what network security does as well as looking at some of the most common attack vectors like eavesdropping, trojans and denial of service attacks. It also looks at the technology of network security and sets out some best practice guidelines for businesses.
It concludes with quotes from some of the industry's leading security experts on why network security is vital. You can see the full infographic below.

Image Credit: rosedesigns / Shutterstock
-

IBM and Twitter join forces to improve enterprise decision making
Publié: octobre 30, 2014, 4:20pm CET par Ian Barker

Twitter provides a unique window into public thinking and that can be useful for businesses, not only to see what people are saying about them but also to get an insight into market trends.
In order to help enterprises understand their customers and markets, IBM and Twitter have announced a partnership that will allow Twitter data to be used in IBM's cloud-based analytics platforms.
The two companies will deliver a set of enterprise applications to help improve business decisions across a range of different industries and professions. The first joint offering from big blue and the blue bird will integrate Twitter data with IBM ExperienceOne customer engagement solutions. This will allow sales, marketing, and customer service professionals to map sentiment and behavior, and help them to better engage with and support their customers.
There will also be collaboration to develop unique solutions for specific industries such as banking, consumer products, retail, and travel and transportation. The partnership will use the skills of tens of thousands of IBM Global Business Services consultants and application professionals including consultants from the industry's only integrated Strategy and Analytics practice, and IBM Interactive Experience, the world's largest digital agency.
"Twitter provides a powerful new lens through which to look at the world -- as both a platform for hundreds of millions of consumers and business professionals, and as a synthesizer of trends," says Ginni Rometty, IBM Chairman, President and CEO. "This partnership, drawing on IBM's leading cloud-based analytics platform, will help clients enrich business decisions with an entirely new class of data. This is the latest example of how IBM is reimagining work."
IBM plans to offer Twitter data as part of other select cloud-based services. These include IBM Watson Analytics, a service that brings intuitive visualization and predictive capabilities to business users. Businesses and developers will also be able to integrate Twitter data into cloud services they build using IBM Watson Developer Cloud and IBM Bluemix platform as a service.
"When it comes to enterprise transformation, IBM is an undisputed global leader in enabling companies to take advantage of emerging technologies and platforms," says Dick Costolo, Twitter CEO. "This important partnership with IBM will change the way business decisions are made -- from identifying emerging market opportunities to better engaging clients, partners and employees."
For more information on the partnership and what it will offer you can visit the IBM website, or the official Twitter blog.
-

Breach detection market expected to exceed $1.3 billion by 2018
Publié: octobre 29, 2014, 5:28pm CET par Ian Barker

Security breaches have become a major worry for businesses in the last two years and that's reflected in strong growth of the market for breach detection products.
A new market intelligence brief by NSS Labs looks at the rapid rise of breach detection systems (BDS). In 2013 the BDS market was worth over $289 million dollars, up 99 percent over the previous year.
The market is expected to continue growing at an annual rate of 36.9 percent to reach $1.39 billion by 2018. Given that BDS is an emerging market with few products that have been around for more than three years this is an impressive jump.
The study finds that lack of mature solutions along with inconsistent marketing is, however, causing considerable confusion around the necessity, effectiveness and best practices for deployment of these products. The high price of many on-premises solutions is also inhibiting adoption.
Another barrier is that BDS solutions are complex in their own right and require a level of security expertise that is currently hard to find. As a result many vendors are deploying cloud-based or managed offerings to offset the high costs and complexities of BDS. NSS Labs predicts that hybrid solutions could become the primary vehicle for BDS deployments in the future.
Current BDS offerings are deployed primarily as hardware appliances, but many vendors are also introducing virtual appliances, software as a service and the endpoint as part of the product suite.
The report notes that, "The immediate challenges for the BDS market are twofold: Vendors must demonstrate that these expensive solutions do in fact provide increased security (i.e, they will discover threats that all other devices in the security stack have missed), and end users must be trained in how to deploy these devices and manage their output".
To address the training issue some vendors are offering services built around these solutions or are integrating breach detection into their existing security products.
NSS Labs concludes that there's no best approach to BDS, it's more important to determine what works best for a particular business. More details on the report are available on the NSS labs site.
Image Credit: Sergey Nivens / Shutterstock
-

Bring your own security approach protects Azure cloud apps
Publié: octobre 29, 2014, 11:15am CET par Ian Barker

Securing applications in the cloud can prove a difficult challenge for businesses. Any solution needs to balance protection against accessibility and not harm performance.
Java security specialist Waratek has used the Microsoft TechEd Europe conference in Barcelona to announce an innovative bring your own security (BYOS) approach to the problem called Waratek Locker.
It's a secure container that provides Runtime Application Self-Protection (RASP) for Java applications deployed on the Azure cloud platform. Waratek Locker provides transparent protection against business logic and network layer threats regardless of where an application is hosted and without the need to make any code changes.
The product works within the Java virtual machine allowing it to provide security monitoring, policy enforcement and attack blocking. It can guard cloud applications from exploits that target vulnerabilities in third party libraries and malicious activity including SQL injection, abnormal file manipulation or unexpected network connections.
Applications deployed in Waratek Locker are protected by a rule-based engine. This can be remotely managed by administrators and it comes pre-configured with rules to restrict application access to only required files and network functions, and to block SQL injection attacks.
"Microsoft Azure is a powerful platform for deploying enterprise applications in the cloud that includes industry leading infrastructure level security," says Brian Maccaba, CEO of Waratek. "With Waratek Locker we enable organizations to bring their own application security controls to Azure in one easy to deploy and manage container. It is truly portable enterprise class security for the cloud".
You can find out more and get a free trial on the Waratek website. The company has also made a free tool available for writing custom security rules.
Photo Credit: Slavoljub Pantelic / Shutterstock
-

Skills gap still the biggest challenge in mobile app delivery
Publié: octobre 28, 2014, 4:05pm CET par Ian Barker

Finding skilled mobile developers is one of the top challenges when it comes to the timely delivery of new apps.
This is among the findings of the 2014 Mobile Trends report from enterprise mobile platform provider Appcelerator. The company along with IDC surveyed over 8,000 mobile developers and 121 IT decision makers to get their take on trends that affect the way businesses use mobile in the workplace.
The skills gap was rated by 33.3 percent of developers and 41.3 percent of decision makers as the number one difficulty. The skills problem isn't simply about coding languages but also the way processes must be adapted and apps designed to connect to back office data. Agreeing on features and design priorities is seen as a problem by 17.6 percent of developers and 9.9 percent of decision makers.
There's also division of opinion over who owns the mobile agenda. 66.9 percent of IT decision makers feel that IT is the primary driver in setting the organization’s mobile agenda, however, 49.7 percent of developers say the business side is in control.
This same split is evident on HTML5 too. Among decision makers 70.6 percent report a positive experience of implementing HTML5 but that figure falls to 37.2 percent amongst developers.
The report indicates that release velocity is increasing too along with the number of platforms that need to be supported. 83.9 percent of developers report that their businesses are supporting two or more mobile operating systems, and 55 percent say they release monthly or more often.
What both sides agree on is the importance of accessibility to mobile platforms, with 90 percent of developers and 87 percent of IT decision makers saying it was likely or very likely that connecting mobile apps to both public and enterprise data sources will become the norm.
The full report is available in a snazzy page-flipping format on the Appcelerator website.
Image Credit: logolord / Shutterstock
-

Incapsula launches how-to guide for dealing with DDoS attacks
Publié: octobre 28, 2014, 2:01pm CET par Ian Barker

We reported back in March that DDoS attacks had risen sharply to become a major threat for online businesses.
In order to help companies cope, cloud security provider Incapsula is today launching a DDoS Playbook analyzing the threat landscape and providing businesses with a how-to guide to fend off attacks.
Incapsula's DDoS Playbook provides companies with a practical guide for planning and executing a DDoS response plan. It outlines pragmatic steps and best practices to help in choosing the right mitigation solution for an organization. It will help enterprises authoritatively respond to an attack and conduct a thorough post-attack analysis for developing follow-up defense strategies.
The Playbook starts with the basics of how often DDoS attacks occur and how and why they're launched. It then covers building a response team, preparing a plan and carrying out a risk assessment.
It looks at the key technologies and capabilities needed to build a protection strategy, including detection and the importance of timing. Crucially it also looks at what's needed to respond to an attack, covering establishing a communications center, responding to ransom notes and more.
The book's authors say, "Organizations that engage in advance DDoS response planning are far more likely to limit potential damage and act in an effective manner than those that try to improvise their way through a DDoS-induced crisis".
Written for executives rather than technical staff, the Playbook includes a glossary of terms and is written in an accessible style offering practical advice. For more information and to download a copy visit the Incapsula website.
Image Credit: sibgat / Shutterstock
-

BigPanda automates IT incident management
Publié: octobre 28, 2014, 11:56am CET par Ian Barker

Over the past decade or so there's been a big change in the way data centers work and in many cases procedures for managing incidents haven't kept pace.
This is partly due to greater complexity brought about by the cloud and virtualization, and partly due to the fact that monitoring has become more fragmented with companies using, on average, five different monitoring tools.
In order to bring data center incident management up to date, data science specialist BigPanda is aiming to use its platform to automate IT incident management. It analyzes alerts then automates the processes involved with detecting, investigating and collaborating to resolve IT incidents. This enables companies to resolve IT issues faster and minimize their impact on customers and revenue.
Assaf Resnick, Co-Founder and CEO of BigPanda, says, "The new generation of IT infrastructure requires a fundamentally different approach to incident management. We believe that only through leveraging data science can IT teams tackle the scale of machines, events and dependencies that must be understood and managed".
BigPanda uses a SaaS platform that aggregates and normalizes alerts from leading monitoring systems, such as New Relic, Nagios and Splunk, as well as in-house monitoring solutions. It then uses powerful data algorithms to automate the incident management process.
It sorts high level incidents from the flood of alerts so that critical issues can be spotted quickly. BigPanda also cross checks IT incidents with the code deployments and infrastructure changes that may have caused them, so IT and DevOps teams have instant access to the data they need to make smart decisions quickly.
In addition the platform makes it easy to notify the right people and keep everyone updated on incident status, notes, activities, metrics, and more. BigPanda syncs with help desk systems like ServiceNow, JIRA and Remedy, which frees IT staff from having to manually manage tickets and keep them up-to-date.
The company has also announced $7 million of funding from venture capitalists to allow it to develop the product. A lite version of BigPanda is available for free and there's a 30-day free trial of the full version available on the company's website.
Image Credit: leungchopan / Shutterstock
-

HP launches free executive tools to reduce the impact of security incidents
Publié: octobre 27, 2014, 4:41pm CET par Ian Barker

More than 70 percent of executives think their organization only partly understands the risks it could be exposed to as a result of a data breach. This is among the results of a study from technology giant HP into the importance of executive involvement in breach responses.
In addition less than half of board-level executives are kept informed about the breach response process and only 45 percent believe they are accountable for the incident response process.
Some 79 percent of respondents say executive level involvement is necessary to achieving a successful data breach response, while 70 percent believe board level oversight is also crucial. However, only 45 percent of executives believe that their own enterprise's incident response process is either proactive or mature.
In terms of what constitutes a serious incident, 57 percent of respondents say the lost or theft of more than 10,000 records containing confidential or sensitive information constitutes a significant data breach. In cost terms, a data breach that averages approximately $2 million is considered significant.
"Without a well thought out plan in place, and without the proper guidance, training and process instituted throughout the organization, executives can stumble when dealing with the public outcry once sensitive data has been compromised", says Arthur Wong, senior vice president and general manager, Enterprise Security Services at HP. "No amount of spend can completely protect organizations from highly sophisticated cyber attacks, but how prepared an organization is in the event of a breach can mean the difference between a speed bump in the road or a catastrophic business event".
To help executives prepare for handling data breaches HP has made some free online resources available as part of an Executive Breach Response program. These include a study exploring how 300 global organizations plan and use best practices to prepare for cyber security incidents.
There's also a breach response assessment which contains a series of questions to compare an organization's answers to those of its industry peers. Using the tool, an individual can assess an organization’s ability to respond to a data breach and identify areas of strength and weakness when it comes to preparing for a breach.
A breach response playbook offers scenarios, best practices, and benefits in planning that will help organizations be prepared in the event of a data breach. Finally there are a series of webinars to help executives draft and implement breach preparedness plans.
The full report and details of the Executive Breach Response program are available on HP's website.
Image Credit: Pressmaster / Shutterstock
-

Targeted attacks against businesses are on the rise
Publié: octobre 27, 2014, 3:01pm CET par Ian Barker

In the last year 94 percent of organizations have encountered at least one cyber security incident, with 12 percent indicating that they’d been on the receiving end of a targeted attack.
These are among the findings of a survey of worldwide IT professionals by security company Kaspersky Lab and research specialist B2B International. Damages from one successful targeted attack could cost a company as much as $2.54 million for enterprises and $84,000 for small businesses.
Whilst the threat of targeted attacks affects businesses of all sizes, the survey finds that large companies in particular see them as a major threat. 38 percent of companies with 1,500 to 5,000 employees, and 39 percent of companies with more than 50,000 employees named targeted attacks as their number one concern.
Smaller businesses are slightly less concerned, with 34 percent naming targeted attacks as a key priority. A major worry for all businesses is losing sensitive data with more than a third saying that protection of confidential data against targeted attacks is a key problem for IT management teams.
Chris Doggett, Managing Director of Kaspersky Lab North America says, "The survey results clearly indicate that many businesses now recognize that the threat of a targeted attack is very real and could be very harmful for their organization. However, we are seeing that the number of companies that are actually taking that knowledge and turning it into an action to protect their organization from such attacks is still alarmingly low. With major breaches being reported regularly now, it is critical for businesses of all sizes to make protection of their IT infrastructure their top priority, especially given the damages that arise from each successful targeted attack".
Other findings from the report are that spam is now seen as the number one external threat, named by 64 percent of respondents. Viruses and other malware were named by 61 percent. Phishing attacks trail some way behind on 38 percent followed by network intrusions on 25 percent. Whilst DDoS attacks rate only 18 percent on the overall threat scale they're placed much higher by IT and telecom companies.
Where internal risks are concerned, flaws or vulnerabilities in software are rated highest at 36 percent, followed by accidental leaks by staff (29 percent) and loss or theft of mobile devices (26 percent). Again these figures vary by industry with 42 percent of telecom companies being worried about accidental leaks.
There's much more information in the full report which is available on the Kaspersky Lab website.
Photo Credit: Sergey Nivens/Shutterstock
-

Employees' bad habits could put businesses at risk
Publié: octobre 24, 2014, 4:58pm CEST par Ian Barker

Individuals are frequently the weakest link in the chain when it comes to protecting business data, often through simple day-to-day lapses that can have a serious consequence.
Atlanta-based IT Services company Leapfrog Services has identified five common bad habits of employees that businesses need to manage in order to guard their information.
Poor password practices are top of the list. If employees fail to log out when they leave their desks, or write passwords on sticky notes attached to the monitor, they're putting company data at risk. It's important to establish and enforce security procedures especially if workstations are shared.
Updating social media may seem like a harmless activity, but badly-judged comments about products, clients or even colleagues can have serious consequences. Enterprises need to have a clear social media policy which outlines what can be shared and what needs to be kept confidential.
Sending texts may be convenient, but if employees use personal devices for business it risks losing the security that's in place for company systems. As a result something like sending links, images and quick thoughts by text may fall outside of the IT department's control or access.
Social engineering is a problem across all businesses and phishing emails do make it through to inboxes occasionally, even with protection in place. Opening an email mindlessly may be all it takes for hackers to infect a system or company network. Whilst it's important to keep security systems up to date, education is vital to make sure staff are aware of the potential threat posed.
Finally, seemingly helpful working methods such as using public clouds to share files or working via insecure home networks or access points can put company data at risk. If employees are allowed to work away from the office or on their own devices this needs to be backed up by security systems that keep the company safe but don't compromise convenience.
"Lines are now blurred between using company computers vs. personal devices for work," Leapfrog’s CTO Trey Hawkins says, "And as we learned with recent celebrity hacking incidents, even cloud-based platforms can be compromised. It is critical to have rules in place that protect company information".
Image Credit: Jirsak / Shutterstock
-

Point of sale malware infections show sharp rise
Publié: octobre 24, 2014, 1:38pm CEST par Ian Barker

Threat protection specialist Damballa has released its threat protection report for the third quarter, highlighting that the malware threat is still growing.
Based on analysis of traffic from the company's ISP and enterprise companies, the report looks at one of the biggest challenges facing IT security teams, that of identifying genuine attacks amongst a plethora of security alerts. In the last quarter it says that the 'noisiest' enterprises experienced some 138,000 events in a day. This represents a 32 percent increase over Q2, with customers experiencing an average of 37 infected devices a day.
There is some good news thanks to a 40 percent reduction in daily infections over the previous quarter. This is thanks to customers using technologies like automatic incident detection to respond to threats and identify true positives.
The biggest worry though is an increase in point of sale malware. Damballa detected a 57 percent increase in infections of Backoff from August to September and a 27 percent increase from September to the end of the month. Backoff, is a new breed of highly targeted POS malware and is reported by the US government to have infected 1,000 businesses including Kmart and Dairy Queen.
Brian Foster Damballa's CTO says, "Fundamentally, these figures show that prevention controls cannot stop malware infections. POS malware and other advanced threats can, and will, get through so we can't simply build the walls around the network higher. And for security teams, faced with the trawling through a tsunami of events every day, manually correlating these to find the 'true positives' is simply not feasible".
The particular worry with Backoff malware is that it attacks via local area networks where traffic may not come under the same scrutiny as external traffic. Once an infection is present therefore it can remain active but hidden.
Foster concludes, "The encouraging news is that automatically correlating evidence, can have a significant impact in reducing the number of infected devices within the network. We'd advise enterprises to be prepared, to get ahead by assuming that they will be compromised, and take proactive measures to be ready to remediate".
The full State of Infections report can be downloaded from the Damballa website.
Photo Credit: Balefire / Shutterstock
-

Understanding how decisions affect the enterprise
Publié: octobre 23, 2014, 1:34pm CEST par Ian Barker
In large companies it can be difficult for decision makers to see the full impact their choices have. A new product from decision support specialists Mu Sigma aims to provide a holistic picture of how things are connected.
The product, called muUniverse, is designed to give decision makers at Fortune 500 companies a complete view of their business decisions, allowing them to navigate an increasingly complex set of interconnected problems they face in areas such as sales, marketing, finance, supply chain, risk, and others.
It's based on the patterns found in nature where problems occur in clusters rather than isolation and organisms increase in complexity over time. MuUniverse maps the decision foot print within the organization and is claimed to be the only solution available today that can provide an intelligent path to drastically improve decision making and impact the outcomes that are necessary for growth and survival.
"In the age of big data, companies often lack the tools they need to appreciate and understand the complexity of problems they face. A new art of problem solving is needed to address this. The big goal of our new platform is to automate dynamic thinking that is often baked into the DNA of innovators like Steve Jobs and Elon Musk, but now make this available to any major corporation," says Dhiraj Rajaram, CEO and founder of Mu Sigma.
It builds on the company's existing muPDNA business intelligence platform and is aimed at helping businesses improve problem solving and planning by allowing the creation of better insights. It can also assist in prioritizing and engaging with the correct stakeholders, as well as investigating the relationship between problems allowing the impact of decisions to be anticipated. Eliminating risk is another benefit as is the ability to spot new opportunities based on data analysis.
You can find out more on the Mu Sigma website.
-

IBM and Microsoft team up to offer greater hybrid cloud choice
Publié: octobre 22, 2014, 4:30pm CEST par Ian Barker

One of the problems that enterprises often see in implementing cloud computing is that they risk getting tied into a single supplier for software and platform.
This is leading to more interest in 'hybrid cloud' solutions which allow the mixing and matching of features from different suppliers. Today industry giants IBM and Microsoft announce that they're working together to provide their respective enterprise software on Microsoft Azure and IBM Cloud.
"Together we are creating new opportunities to drive innovation in hybrid cloud," says Robert LeBlanc, Senior Vice President of IBM's Software and Cloud Solutions Group. "This agreement reinforces IBM's strategy in providing open cloud technology for the enterprise. Clients will now gain unprecedented access to IBM's leading middleware and will have an even greater level of choice over the tools that they use to build and deploy their cloud environments".
The idea is to give clients, partners and developers a wider range of options. IBM middleware such as WebSphere Liberty, MQ, and DB2 will be available on Microsoft Azure, whilst Windows Server and SQL Server will be offered on IBM Cloud.
At the same time the two companies are working together to deliver a Microsoft .NET runtime for IBM’s Bluemix cloud development platform. Plus IBM will expand support of its software running on Windows Server Hyper-V. The companies plan to make IBM Pure Application Service available on both Microsoft Azure and IBM SoftLayer for automated deployment, configuration and license management in a hybrid cloud environment.
Customers will be able to bring their own software licenses to the IBM and Microsoft clouds, helping them to avoid extra cost. IBM middleware licenses for things like WebSphere will be made available to Azure users with per user pricing.
"Microsoft is committed to helping enterprise customers realize the tremendous benefits of cloud computing across their own systems, partner clouds and Microsoft Azure," says Scott Guthrie, executive vice president, Cloud and Enterprise at Microsoft. "With this agreement more customers will be able to take advantage of the hyper-scale, enterprise performance and hybrid capabilities of Azure".
For more information visit the IBM Cloud or MS Azure websites.
Photo Credit: Minerva Studio/Shutterstock
-

Using Google Analytics to gauge return on investment
Publié: octobre 22, 2014, 12:19pm CEST par Ian Barker

Google Analytics has become something of an industry standard for gathering web metrics. But a new report from form building company Formstack says that businesses may be concentrating on measuring the wrong things.
It suggests that users tend to focus on vanity metrics, like page views and bounce rate, but stop short of real data tracking. What they should be focusing on are the actionable GA metrics that will impact conversion rate and ultimately revenue.
The company has produced an infographic guide to calculating the return on investment of a landing page using Google Analytics. This sets out four key steps: defining the audience, discovering conversion rates, calculating page revenue and assigning value to customer actions. Given the relatively simple process it's surprising that only a third of marketers bother to calculate the ROI of their sites.
You can download the full report from the Formstack website and view the infographic below.
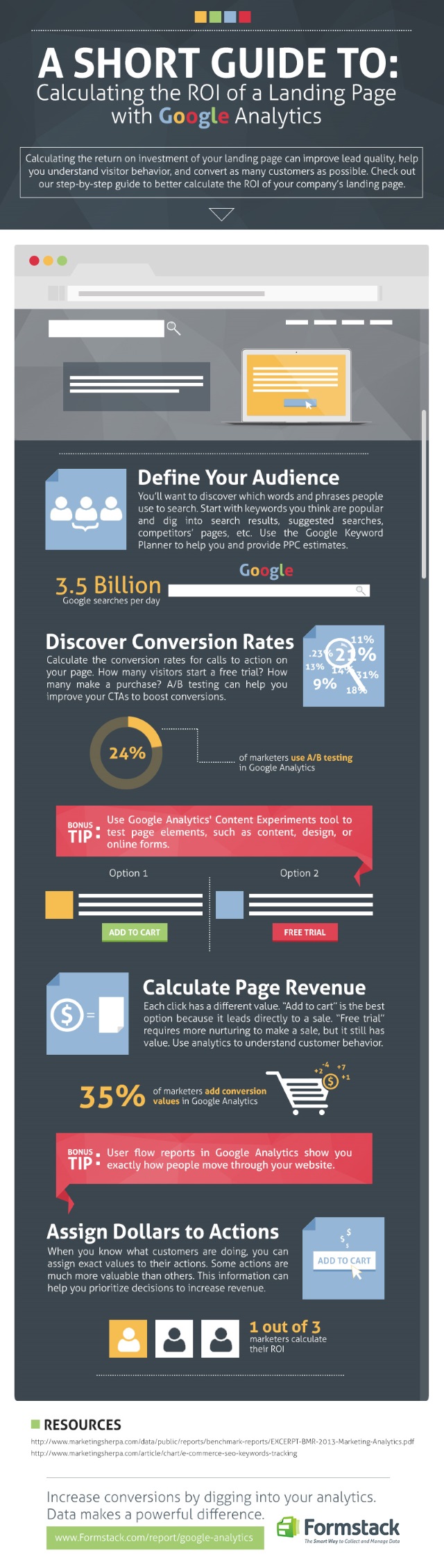
Photo Credit: Sergey Nivens / Shutterstock
-

Making direct interconnection of networks a Snap
Publié: octobre 22, 2014, 10:55am CEST par Ian Barker

As businesses increasingly turn to the cloud to store their data the weak link in the chain remains the use of the public internet to transfer information.
To overcome these concerns enterprises are looking for secure and scalable ways to directly connect data centers across the globe. Now IIX (International Internet Exchange) has acquired a platform that fully automates the buying and provisioning of network connections in under five minutes, replacing a manual process that can take as long as 30 days.
IIX has acquired UK-based Allegro Networks which has a pioneering automation platform called Snap. This provides organizations with a new and unique capability to purchase and provision virtual cross connects, point-to-point circuits, and peering interconnections in minutes.
Snap eliminates the manual and laborious process of creating direct network interconnections across multiple markets, something which can take weeks or even months. Using a laptop, tablet or mobile device, customers can log on to a secure portal. From there they can buy and provision connections to the content providers, cloud providers, and other trading partners that are key to their business, in under five minutes.
"Enterprises are rapidly adopting cloud computing solutions, driving the demand for scalable, secure, and flexible direct interconnections to content, cloud, and application providers and other enterprise networks. With the acquisition of Allegro, IIX gains top engineering talent, innovative technology, and 34 network Points of Presence (PoPs) in the UK to support growing customer demand," says Al Burgio, founder and CEO of IIX.
As part of the deal Andy Davidson, Allegro's Chief Technology Officer, has been appointed IIX's Vice President of Network Engineering, Europe. He says, "IIX is at the forefront of next-generation direct interconnection for enterprises worldwide. This acquisition enables our customers to have direct access to additional leading content and application providers globally. Our two organizations share the same philosophy, believing that the ability to provision scalable, reliable, and secure interconnects will power new innovation for the benefit of online users".
You can find out more about the Snap platform and how it works on the Allegro website.
Photo Credit: Palto/Shutterstock
-

1 in 4 organizations use Hadoop to manage their big data
Publié: octobre 17, 2014, 11:56am CEST par Ian Barker

You can't go too far in the big data world without encountering Apache Hadoop. The open source framework was created in 2005 to handle large scale processing.
A new infographic from data management company Solix looks at what Hadoop is, the four modules that make it up, and how it’s used in the enterprise, along with a glimpse at its future.
Key facts are that one in four organizations use Hadoop to manage big data, up from one in 10 in 2012. Reasons cited for using it include low cost, computing power and scalability. More than 60 percent of companies say that Hadoop is used to supplement or replace their existing data environments.
Looking into the future, 61 percent of organizations plan to deploy Hadoop in the future or have already started to deploy it. Worldwide sales of Hadoop-based technology are expected to exceed $50 billion by 2020.
You can see the full infographic below.
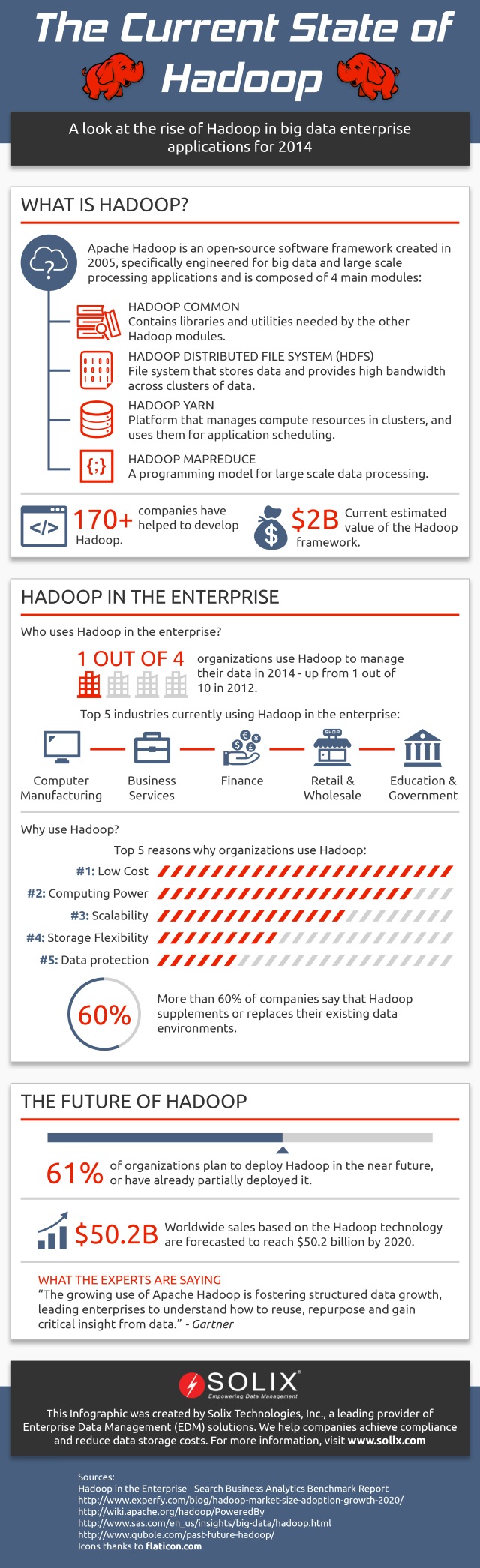
-

Protecting your PC is like defending a castle
Publié: octobre 16, 2014, 3:46pm CEST par Ian Barker

Most people are aware that they need to have some form of protection on their PC if it's attached to the internet. Yet it seems that a lot of users still don't know how to properly protect themselves.
Many believe that the security software that comes with their PC is enough to protect them. Security company Check Point ZoneAlarm has released an infographic which shows that 71 percent don’t have both a firewall and antivirus solution on their PCs.
It also shows that 32 percent of PCs in the world have a malware infection and that unprotected machines are 5.5 times more likely to get infected. The graphic compares protecting your PC to defending a medieval castle, but don’t go heating the boiling oil just yet.
ZoneAlarm has also released a blog post on the results of the recent AV-TEST research which shows that its premium product out performs free offerings from Avast and AVG. The message being that relying on free solutions may not protect you as much as you think it does.
The key thing though is that whatever you use you need to have both a firewall and antivirus to provide protection. Otherwise it's back to the drawbridge and the suit of armor. More details in the infographic scroll below.

-

How can consumers stay secure as payment systems evolve? [Q&A]
Publié: octobre 16, 2014, 2:49pm CEST par Ian Barker

Data breaches continue to make the news on a regular basis and payment details are high on the hacker’s shopping list when it comes to protecting information. We reported yesterday on Intel introducing a new secure solution for protecting payments and card providers are engaged in a continuing arms race to stay secure. The latest part of this is the introduction of more secure EMV (EuroPay, MasterCard and Visa) compliant payment terminals around the world. Banks are issuing the new chip cards as current cards expire or need replacement. Retailers are installing new chip-enabled terminals.
As the holiday shopping season approaches keeping your details safe as you hit the shops is at the top of many people's thoughts. We spoke to Carolyn Balfany, SVP, Product Delivery and EMV of payment card specialists MasterCard to find out about what consumers can do to help protect themselves as they shop.
BN: Have EMV technologies like chip and pin made a difference to the way criminals target payment card information?
CB: New chip cards have embedded computer chips which provide more layers of security. Chip cards generate a unique code with every purchase, which makes each purchase unique and prevents the creation of counterfeit cards.
BN: What does the upcoming EMV liability shift mean for consumers?
CB: The liability shift means a higher level of security for consumers. Liability for fraud will lie with the bank or retailer with the least secure technology. This is an incentive for banks to issue the new cards and retailers to update their terminals to accept the safest form of payments.
BN: Why has EMV taken so long to roll out in the US given that it's been the norm in Europe for some years?
CB: There are a few reasons. Historically the US has low levels of fraud due to sophisticated processes and technologies which identify potential issues, in many cases, before they happen. Therefore the move to chip cards was not as urgent in the US.
In addition the process for banks and retailers moving to chip cards takes time. It's as if the US decided to drive on the left-hand side of the road -- all cars, road signs, exit ramps and toll bridges would need to be modified. The US adoption of chip cards actually started back in 2012.
BN: How safe are contactless card payments and do they require additional safeguards?
CB: Contactless card payments are extremely safe due to the unique codes mentioned above. Your contactless card or device never leaves your hand, reducing the risk of it being lost or stolen. Safeguards are even in place to only charge once, even if you accidentally tap twice.
BN: What effect will non-card technologies like the new Apple Pay and other NFC systems have? Are these more or less secure than using a card?
CB: Digital payment platforms such as Apple Pay, Google Wallet and MasterPass will make mobile payments as easy and secure as using cards. Think of applying the security of chip cards in the online and mobile worlds.
BN: How worried should people be that if they're using a mobile phone for payments they risk losing their whole identity of they lose their device?
CB: When cardholders use their MasterCard cards they are protected by zero liability -- consumers are never held responsible for fraud. All MasterCard credit, debit, prepaid and small business cards issued in the US. MasterCard's zero liability policy in the US protects consumers and small businesses against card being fraudulently used in stores, online or at ATMs, including all signature and PIN tractions.
In addition there's identity theft resolution assistance. The program provides help in canceling missing cards and alerting credit reporting agencies, as well as targeting searches to detect if stolen personal and confidential data appears online.
As discussed above, chip or EMV cards provide an additional level of security. MasterCard cardholders can also download the InControl app. InControl allows cardholders, parents or employers to establish parameters for when, where and how their cards are used and even block transactions that they deem inappropriate. Additionally, it enables cardholders to receive real-time alerts about card activity via email or text message.
MasterCard has also worked with Apple Pay on security to protect our cards when they are used in connection with the iPhone 6. Apple Pay assigns a unique Device Account Number with a transaction-specific dynamic security code for every purchase. These codes or numbers are never stored on Apple servers and never shared with merchants. If iPhones are lost or stolen, features such as Find My iPhone can quickly put devices in Lost Mode. iPhones can also be wiped completely clean. Either way, both card numbers and identities are not accessible. For Android users, Google Wallet requires users to set up PINs that must be entered before making payments. Android phones also support a separate lock screen. Together, these two security features make it difficult for someone other than you to pay with your phone.
Image Credit: Sedlacek / Shutterstock
-

The best tools for removing malware 2014
Publié: octobre 16, 2014, 10:56am CEST par Ian Barker

Independent testing organization AV-Comparatives has released the results of its latest Real World Protection and File Detection tests showing which security products perform best at dealing with malware.
The Real World Protection test results are based on over 600 live threats including drive-by downloads, malicious URLs, and infected email attachments. 22 products were tested and rated against the 'out of the box' protection provided by Windows (80.4 percent).
The only product to achieve 100 percent protection in the tests was trend Micro Titanium Internet Security, though it did so at the expense of five false positives. Qihoo 360 Internet Security and Panda Cloud Free Antivirus both achieved 99.5 protection with Qihoo scoring no false positives and Panda six.
Kaspersky managed 99.3 percent with no false positives, Avira and BitDefender both scored 99.2 percent again with zero false positives. ESET came next with 98.7 percent and one false positive.
Other notable results were F-Secure which although it managed to block 97.2 percent of malware recorded a massive 66 false positives, and McAfee which blocked 94.7 percent with 36 false positives.
At the other end of the scale Lavasoft and AhnLab both managed 85.2 percent and no false positives. At the bottom of the pile ThreatTrack Vipre scored 84.4 percent with 14 false positives.
So much for protection. The File Detection test measures the product's ability to detect malicious files already present on a system. Products were tested against more than 126,000 malware samples, again the out-of-the box protection of Windows (9.8 percent of samples missed) is used as the benchmark.
No product achieved total detection, Kingsoft and Avira score best here, missing just 0.1 percent, followed by McAfee on 0.2 and Kaspersky Labs and Baidu both on 0.3 percent. Only two products missed more than two percent of samples, Fortinet on 2.1 percent and AhnLab on 6.3.
Looking at false positives ESET scored only one, Panda two, with Emsisoft, Escan and Fortinet on four and Panda five. At the other extreme Avast clocked 120 false alarms, yet still managed to miss 1.4 percent of the malware samples.
What we can conclude from all this is that choosing internet security tools is a balance. No one product offers perfect protection across the board and detection rates need to be set against the number of false alarms likely to be generated.
There's an interactive chart of the Real World Protection Test results and the latest plus previous reports are available on the AV-Comparatives site for both Real World Protection and Detection tests.
Photo Credit: Balefire / Shutterstock
-

New Intel technology helps safeguard the payment process
Publié: octobre 15, 2014, 6:45pm CEST par Ian Barker

Recent high profile data breaches involving retailers have led many people to have doubts about the security of transactions.
Chip maker Intel has today announced a new data protection technology that will both address these concerns and help speed up the roll out of internet of things devices in retail environments.
Intel Data Protection Technology for Transactions adds an extra layer of software to protect the payment process. This complements other security and authorization technologies. The software sits on an Intel chipset and creates a secure pathway between the retailer's point of sale system and the servers.
The solution supports all modern forms of credit and debit payment including EMV (Europay, Mastercard and Visa), magnetic stripe and near field communication (NFC) transaction readers, including Google Wallet, Softcard and Apple Pay.
"This solution introduces a significant improvement in today's retail transaction data protection without costly hardware upgrades, and provides retailers a path for adopting new Internet of Things technologies," says Michelle Tinsley, director of Mobility Retail and Payments at Intel. "It also sets the stage to expand to other industries such as financial services, healthcare or even government agencies".
The client software is available now and the full solution is expected to be available to retailers by the end of next year. More information is available on the Intel website and there’s an overview of how it works in infographic form below.
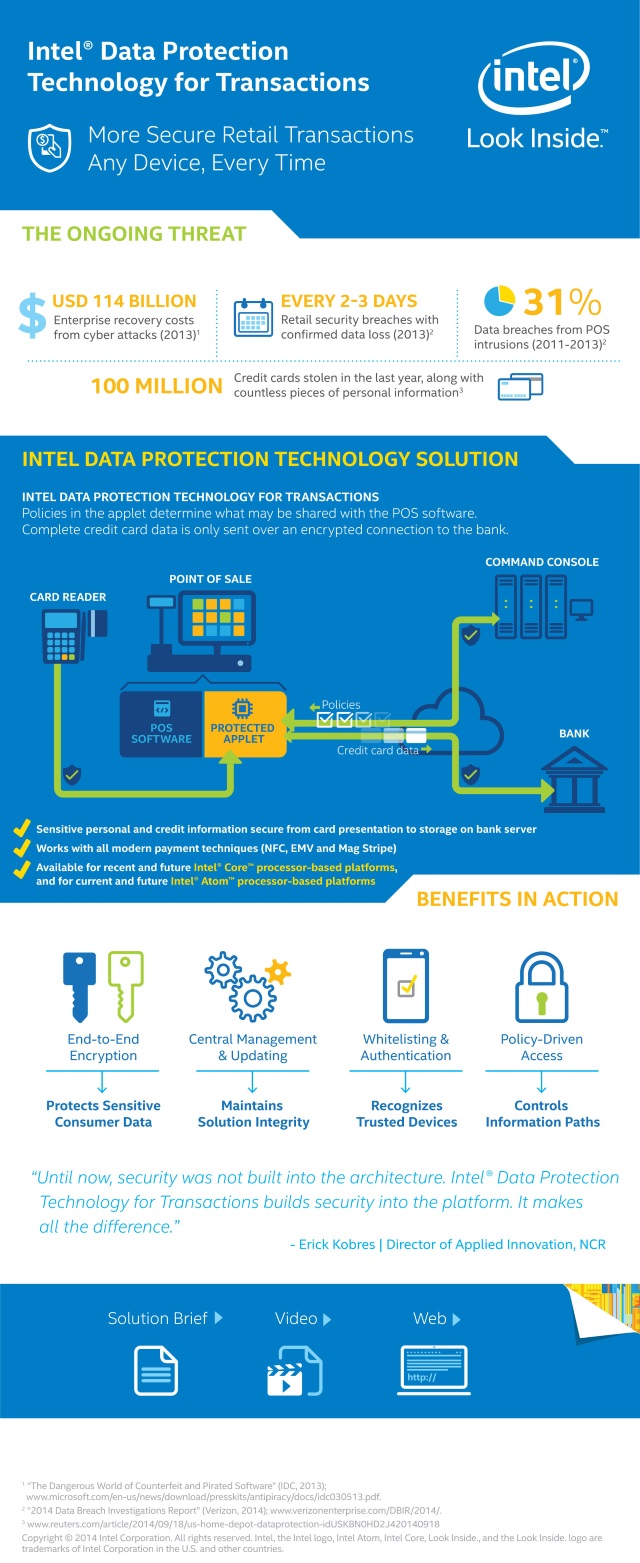
Image Credit: Sergey Nivens / Shutterstock
-

Cloud-based security and why it's here to stay
Publié: octobre 15, 2014, 4:38pm CEST par Ian Barker

As the popularity of cloud services has grown, so have concerns over the security of the data that's stored on them. This has led security vendors to adapt and develop solutions for the new environment.
A new report by security company NSS Labs looks at the rise of cloud security solutions and at the business demands driving their adoption, as well as the limitations and potential hidden costs in their use and recommendations for enterprises.
Findings include that many cloud security appliances and services are from new vendors rather than established providers, something which significantly complicates integration. Also a key feature of many data protection services -- manipulating data before it heads to the cloud -- can require organizations to deploy new critical assets, such as databases and servers and lead to new processes and potential expenses.
Ensuring compliance with organizations' unique regulatory and other requirements is a critical issue too, as is accounting for any gaps that exist between on-premises security and the cloud.
NSS recommends that enterprises deal with these issues by conducting thorough testing of all SaaS tools, either in-house or through a trusted third party, and that they include mobile platforms in their testing.
They also need to perform total cost of ownership (TCO) analysis on any SaaS solution, and take into account the cost required to change vendors including any updates to security. Legacy applications need to be mapped to existing security functions in order to understand their dependencies. The final recommendation is that businesses don’t outsource security related to mission-critical applications or business functions.
The report’s authors conclude, "The decision to rely on virtual security appliances or SaaS products for the protection of enterprise data presents a dilemma for organizations. While there is interest in leveraging cloud services, if security components cannot be seamlessly integrated to the cloud, organizations will experience gaps in their security architecture that could increase risk and expose sensitive data. Vendors must go beyond merely offering cloud-based services; they must prove that they can extend existing on-premises security controls to the cloud while maintaining regulatory compliance and controls".
The full analyst brief is available to download as a PDF from the NSS Labs website.
Photo Credit: Slavoljub Pantelic / Shutterstock
-

Bitcoin will do nicely -- the state of Russian cyber crime
Publié: octobre 15, 2014, 2:01pm CEST par Ian Barker

Banking fraud is down, mobile threats are up and cryptocurrency is the preferred payment method in the world of Russian cyber criminals.
Fraud prevention and cyber crime investigation specialist Group-IB has released a report on the Russian high-tech crime market in 2014. The report provides detailed assessments of the who, what, where and how of high-tech crime, who is behind what crimes, where they originate and who they target.
"With recent cybersecurity events such as the leaks at JPMorgan, Home Depot, Target and others, it pays to know which threats matter and where to best allocate security resources," says Ilya Sachkov, CEO at Group-IB. "Having solid information on the exact nature of cybercrime attacks, and knowing the vulnerabilities that criminal target and exploit, is invaluable to protecting personal and corporate data. Our report provides readers with the knowledge to make smart security decisions".
The report identifies a number of key trends, banking fraud overall is down. Of eight criminal groups active in Russian online banking theft last year, two have switched to foreign targets and one was broken up following the 2014 arrest of one of its leaders. However, mobile banking threats are up as five criminal groups have emerged that specialize in mobile banking theft using Trojans. These groups infect Android phones and steal information via SMS banking and the use of phishing sites.
Attacks on financial institutions continue and groups targeting them have stolen about $40 million during the report period, using techniques including Trojans, phishing sites, and even assistance from inside personnel. ATMs are a popular target too either via physical attack or access to networks.
A look at the online black market in stolen card details -- known as SWIPED -- reveals that one individual uploaded details of over five million cards in the past year. Group-IB estimates the market in stolen cards at $680,000,000. Investigation of a test sample found that all sampled cards on offer were originally stolen from the retail chain Target, which suffered a security breach in the past year.
When it comes to payment hackers prefer virtual currencies. The report finds that 80 percent of payments on SWIPED are made using Bitcoin. The use of malware-based botnets to mine bitcoins has also become more widespread and stealing from cryptocurrency wallets using Trojans is also more sophisticated and commonplace.
None of this means that the old favorite cyber crimes are going away though. Group-IB still detects 10,000 stores selling fake pharmaceuticals via spam every month.
You can read more about the report's findings and look at its prediction of trends for the coming year on the Group-IB website.
Image Credit: Augusto Cabral / Shutterstock
-

Intronis ECHOshare brings simple, secure file sharing to SMBs
Publié: octobre 15, 2014, 11:08am CEST par Ian Barker

Sharing files among employees can be difficult for any business, but particularly for smaller ones which often end up adopting solutions like emailing attachments or using public cloud services.
These approaches can put data at risk and also cause problems for support staff. Backup and disaster recovery specialist Intronis has a new solution to help businesses share files safely in the form of ECHOshare.
"Intronis ECHOshare is an affordable, enterprise-grade file sharing and collaboration technology, delivered through the cloud, purpose built for business and easy for employees to use," says Chuck DeLouis, vice president of product management at Intronis. "With ECHOshare, we are empowering our partners to address use cases that go beyond backup and data protection, and helping them provide their SMB clients with the ability to access and share their data anywhere, anytime".
ECHOshare can be integrated with existing Intronis backup solutions or supplied separately. It's designed to allow managed service providers (MSPs) to offer sharing to their clients with features including centralized management and billing. It offers security too with remote wipe capability for lost or stolen devices, compliance with industry and government regulations, and integration with the existing ECHOplatform backup solution.
End user clients benefit from team-based sharing with user control over permissions on all projects, folders and files, along with password policies and data wipe features. Data can be accessed remotely from portable devices or branch offices and version control allows tracking of who edited a document and when.
There's also the facility to send large files within teams and to create a public link that can be shared with people outside the organization.
For more information about ECHOshare and to request a free trial you can visit the Intronis website.
Image Credit: megainarmy / Shutterstock
-

Organizations struggle to balance security with systems integration
Publié: octobre 14, 2014, 3:04pm CEST par Ian Barker

Many organizations are failing to meet data security and governance requirements according to a new Ovum survey sponsored by data flow specialist Axway.
The results reveal that 23 percent have failed a security audit in the past three years and 17 percent lack confidence in their ability to pass one today. It also puts the average cost of a data breach at $350 per record.
The report also highlights the growing complexity of governance and integration challenges facing organizations. With the EU soon to impose data protection legislation reforms, businesses need to ensure they have a 360-degree view of their data or face risks to their economic position and reputation.
"Ovum's findings shine a light on the challenges most organizations have in meeting today's increasing data security and compliance requirements, as well as the risks of failing to instil effective data flow governance," says Dean Hidalgo, executive vice president, global marketing, Axway. "With proven MFT and API management technologies, either on-premise or in the cloud, and by designing a more unified and comprehensive integration strategy, organizations can govern the flow of data across internal and external sources".
The study identifies key priorities for chief information officers, chief information security officers and chief risk officers. Business continuity and disaster recovery is seen as the top priority (87 percent), followed by protecting against cyber threats (85 percent), managing insider threats (84 percent) and compliance monitoring (83 percent).
More worrying is that many organizations struggle to balance security requirements with other strategies. Also more enterprise assets are likely to be exposed to external sources, such as partners, customers and third-party developers, with 78 percent of organizations either having an API program in place or planning to implement one in the next few years. File transfer solutions are also a concern with reliability, monitoring and compliance among the top issues.
"As the volume and speed of business continues to grow, organizations face greater risk of exposing sensitive data. Moreover, stringent regulatory mandates call for transparent audit trails and a high level of visibility into and control over the flow of sensitive data. Therefore, enterprises can no longer afford to implement infrastructure and governance solutions in isolation," says Saurabh Sharma, Senior Analyst, Ovum. "Traditional approaches to managing business interactions are not suitable for meeting these complex requirements and significantly increase the chance of a data breach and compliance failure".
A whitepaper of the results is available to download from the Axway website there will also be a webinar on the topic tomorrow (15 October) with Axway and Ovum experts. Meantime you can see an overview of the results in infographic form below.

Axway Ovum Governance, Risk and Compliance Infographic by Axway.
Photo Credit: tlegend/Shutterstock
-

Why hackers love the holiday season [Q&A]
Publié: octobre 14, 2014, 12:41pm CEST par Ian Barker

Recent high profile security breaches involving retailers like Target and Neiman Marcus mean that people are increasingly aware they may be vulnerable when shopping online. Yet many don't fully understand the landscape that lies behind hacking and why it’s such a lucrative business.
With Christmas and its associated e-commerce peak fast approaching we spoke to Kelly Yee, Vice President of secure email provider Penango who has a wealth of security systems experience in both the public and private sectors. Here are her views on how hackers work and how we can guard against becoming victims over the holiday season.
BN: Most people realize that today’s hackers are motivated by financial gain, but how do they turn stolen data into money?
KY: In the case of stolen identities, an attacker may sell a bulk package of stolen identities to the highest bidder who will pay what they think the information is worth. Selling large amounts of data in the black market is a sophisticated enterprise and has become the new "it" product to sell on the black market.
BN: Hacking seems to be changing from a solitary activity into a serious business. Is there such a thing as a 'typical hacker' and if so what is he or she like?
KY: Today one rarely sees a waitress stealing someone's credit card information and going to Bloomingdale's to buy new clothes anymore. Instead what is more likely to happen is an attack involving tens of thousands of consumers' credit card information from a business being stolen and then sold to the highest bidder on the black market. There is rarely a typical attacker and that is why it is so hard to place a face to them or stereotype them.
BN: Are some companies less vulnerable to attack than others?
KY: Unfortunately, no. As consumers, we do not know what kind of internal security measures a company has and it's unlikely that a company would be willing to share this, as attackers would love to get their hands on this kind of information. For businesses keen to beef up their security, they should investigate what their potential partners are doing to secure their data. For instance, if a company is choosing an online portal to process orders that company should definitely inquire about the security measures that portal has in place for data at rest and in transit.
BN: Is there any way for consumers to know that a particular site is visible to attack?
KY: There are small precautions users can take to help reduce the use of sites that are prone to attacks. For example, consumers should utilize sites that have "https:" as they add a protocol encryption layer (TLS/SSL) for http:.
However, even a trusted website can be attacked. Take the Heartbleed bug infiltration of TLS/ SSL. What's more, the way companies store their customers' data is what is really prone to attack. This storage system, has nothing to do with a company's website.
The bottom line is, it is very hard to know which particular website, let alone which company's security and data retention measures are prone to attack.
BN: How can individuals and companies protect themselves?
KY: As a consumer, first check your credit card statements at least once a month. This only takes a few minutes and users can generally recognize a transaction that is not familiar. Also credit card companies are fairly easy to work with if there is any suspicious activity, and they remove the charge quickly.
Second credit card companies are federally required to have policies in place to help their users when an attack happens. For this reason, consumers should opt to use their credit card over their debit card where they can.
Third, some people prefer to use cash to protect themselves from attackers altogether. However, doing this may affect individuals in other ways: one can easily lose money and returns may be harder without a card receipt. Also some credit card companies have extended warranties or return policies, so consumers should take advantage of those benefits.
Companies should ensure their data is protected at rest and in transit. Using a secure gateway for data is the first step, but what about the data at rest or stored in the company's database? Penango offers a solution to this by providing true end-to-end (at rest and in transit) authenticated and encrypted email. Even if an email is compromised, Penango can prevent an attacker from reading your messages. This is just a first step, so companies should also make sure that the have a security policy from everything to credit card information down to daily emails.
Image Credit: billdayone / Shutterstock
-

Dropbox passwords held to ransom after third-party leak
Publié: octobre 14, 2014, 10:59am CEST par Ian Barker

Hackers claim to have stolen the login details of almost seven million Dropbox users. Having released a teaser file on Pastebin with details of around 400 accounts they’re offering to release more in exchange for a Bitcoin ransom.
Like the Snapchat photo leak it seems that this information has come from insecure third-party services rather than from Dropbox itself.
In a post on the Dropbox blog the company's Anton Mityagin says, "Recent news articles claiming that Dropbox was hacked aren't true. Your stuff is safe. The usernames and passwords referenced in these articles were stolen from unrelated services, not Dropbox. Attackers then used these stolen credentials to try to log in to sites across the internet, including Dropbox. We have measures in place to detect suspicious login activity and we automatically reset passwords when it happens".
A later list of passwords posted yesterday are, says Dropbox, not associated with its services. It appears that the breach doesn't stem from services using the service’s API -- as with Snapchat -- but from simple poor user practice in reusing passwords across multiple sites. Once again a third-party is the weak link here though there's a new twist in the form of the hackers trying to make a quick profit from the information via Bitcoin.
It's not currently clear which site or service is the source of the breach, which potentially means that other services are at risk too. Dropbox says the initially posted batch of 400 credentials have now been reset. It also recommends that users enable two-factor authentication on their accounts to add an extra layer of protection.
This is the second bad news for Dropbox this week after it confirmed the existence of a bug that was deleting user files.
Image Credit: alexmillos / Shutterstock
-

100,000 mostly dull photos leak online -- behind the 'Snappening' hype
Publié: octobre 13, 2014, 3:35pm CEST par Ian Barker

After all of the recent stories related to the Fappening you could be forgiven for thinking that stories about leaks of nude photos were becoming passé.
That didn't stop the media going into overdrive at the weekend when news emerged of 100,000 (or 200,000 depending on where you read the story) images from disposable message service Snapchat being leaked online.
What got the tabloids hot under the collar was the fact that Snapchat is popular with users under the age of consent. "Thousands of kids, some as young as 10, could have nude photos posted online" shrilled the Mirror. "Naked 'Snapchat images' put online by hackers" the Metro shrieked.
In the cold light of a Monday morning, however, things look a little bit different. So, here's what’s really happened.
First of all, yes there has been a leak of photos. These didn't originate from Snapchat itself but from the SnapSaved.com website, a service that allows Snapchat users to save images that have supposedly been destroyed.
Snapchat is keen to distance itself from the leak saying in a statement, "We can confirm that Snapchat's servers were never breached and were not the source of these leaks. Snapchatters were victimized by their use of third-party apps to send and receive Snaps, a practice that we expressly prohibit in our Terms of Use precisely because they compromise our users' security. We vigilantly monitor the App Store and Google Play for illegal third-party apps and have succeeded in getting many of these removed".
Which is fine except that SnapSaved isn't an app it's a website. There are though apps which offer the same sort of service, similarly named but also not implicated, SnapSave being one of them.
The SnapSaved site is currently offline but has posted a statement on its Facebook page confirming it was hacked and saying, "We had a misconfiguration in our Apache server. Snapchat has not been hacked, and these images do not originate from their database".
That accounts for the leak, but what has been leaked doesn't seem to be the 100,000 plus naked teen images of the tabloids' wet dreams either. According to comments from users on 4chan and Reddit where the photos were leaked most are of everyday activities like displaying a new hairdo or preparing a meal. There may be a small percentage of nudes but certainly not hundreds of thousands.
The other scary suggestion in early stories was that the images were indexed, allowing hackers to link them to user names. Thus leaving the way open for embarrassment at best and blackmail at worst. It seems that this isn't quite true either. Whilst there is a database it's missing its index making it a mass of un-sorted data from which it would be difficult to connect images and users.
So what have we learned? First Snapchat isn't at fault though it does have form for losing data. Second third-parties are often the weakest link when it comes to security, Snapchat makes its users feel secure by claiming images are deleted after 10 seconds but you've no way of knowing if the recipient is using a site or app to capture them. Third the majority of these leaked photos are pretty innocent stuff. Fourth the pictures aren't easily linked to users.
Finally, and you knew this anyway, it isn't a good idea to send naked photos of yourself winging around the internet.
-

Free tablets for UK pensioners as Argos promotes digital skills
Publié: octobre 13, 2014, 11:38am CEST par Ian Barker

We're increasingly becoming a digital society, yet almost one in five people in the UK lack digital skills and 52 percent of those are aged over 65.
In an effort to provide practical skills and access to technology, catalog retailer Argos has partnered with digital skills charity Go ON UK to offer workshops to 10,000 adults.
The workshops will take place at 120 of the company's stores and will cost £20 per head. In return attendees will receive a Proscan 7-inch 8GB tablet and a voucher to get free TalkTalk broadband for a year. Specially-trained store staff will help participants learn the basics of how to use a tablet, connect to and surf the internet, use a search engine, set up email, stay safe online and more.
John Walden, Chief Executive of Home Retail Group, which owns Argos, says, "The digital revolution continues apace, however, millions remain on the side-lines. Argos Internet Workshops have been developed to help people overcome the barriers of access and affordability and improve their knowledge, understanding and confidence in digital technology. The internet is becoming increasingly essential in day-to-day life, and offers a world of new possibilities that we believe everyone should be able to access".
Research earlier this year from communications regulator OFCOM shows that there's a big increase in over 65s going online and more people are using tablets to do so. This is partly down to technologies like Skype that enable communication between generations.
"Access, affordability and skills have all been cited as key barriers to bringing people online and this fantastic initiative from Argos is exactly the type of program we need to help people become more confident with technology," says Baroness Lane-Fox, Chair of Go ON UK.
The workshops will run from 25 October through to January next year. People interested in participating can call 0345 600 4408 or visit their nearest Argos store for more information.
Image Credit: Home Retail Group
-

SAP and Birst team up to deliver cloud analytics for the enterprise
Publié: octobre 10, 2014, 3:06pm CEST par Ian Barker

Enterprise software specialist SAP has announced a partnership with business intelligence company Birst to deliver faster analytics on the SAP HANA cloud platform.
The tie up will allow organizations to use a single cloud platform which can deliver instant analytics giving managers the ability to more quickly turn insight into action. It brings together SAP's next-generation cloud platform and Birst's comprehensive two-tier data architecture to provide instant access to business data.
"Driving better business execution and enabling each and every organization to become data-driven is only achievable when leaders come together to innovate and achieve something that solves real business problems, and that is exactly what Birst and SAP plan to do," says Brad Peters, chairman and chief product officer at Birst. "The real opportunity in BI lies in our ability to push data to the front lines, empowering every person to make every decision better. Together, SAP and Birst will give customers instant access to data and allow people to turn insight into action -- that's something today's businesses have been waiting for and we are thrilled to be delivering it".
The SAP HANA Cloud Platform is based on a breakthrough in-memory technology and offers an open platform for customers and developers to build, extend and run applications in the cloud.
Birst's patented analytics engine aims to build a user-ready data store in SAP HANA that can deliver visual discovery, dashboards and enterprise reports across a single business model, accelerated by SAP HANA. By combining the two this solution is designed to offer instant analytics across on-premise and cloud data sources from large-scale data source vendors.
More information about the collaboration and how it will help enterprises to make more effective use of their business data is available on the Birst website.
Image Credit: Dmitriy Shironosov/Shutterstock
-

Is it the end of the line for the password?
Publié: octobre 10, 2014, 1:15pm CEST par Ian Barker

In an era of increasing security threats the password is often the weakest link that allows attackers a way into a system posing as a legitimate user.
A new infographic from security company Ping Identity looks at the problem of poor passwords and how in the future they may give way to more sophisticated forms of authentication.
Whether they're obtained by keylogging or through social engineering, 40 percent of the entire internet population has been a victim of stolen passwords at some point. The graphic shows that despite the fact over 90 percent of passwords are vulnerable to hacking, 54 percent of Americans trust systems that rely on passwords alone.
It also reveals the top 10 silly places where people store their passwords, including writing them on the keyboard in permanent marker and attaching them to the screen on a sticky note.
More secure alternatives to simple passwords include password managers that can create long and complex logins. In addition biometrics such as fingerprint and facial recognition are likely to become more common. Behavioral patterns are a possible measure too, using gyroscopic identification of the device's movement, as well as device-based authentication linking the computer with a mobile device to verify identity.
You can see the full infographic below.
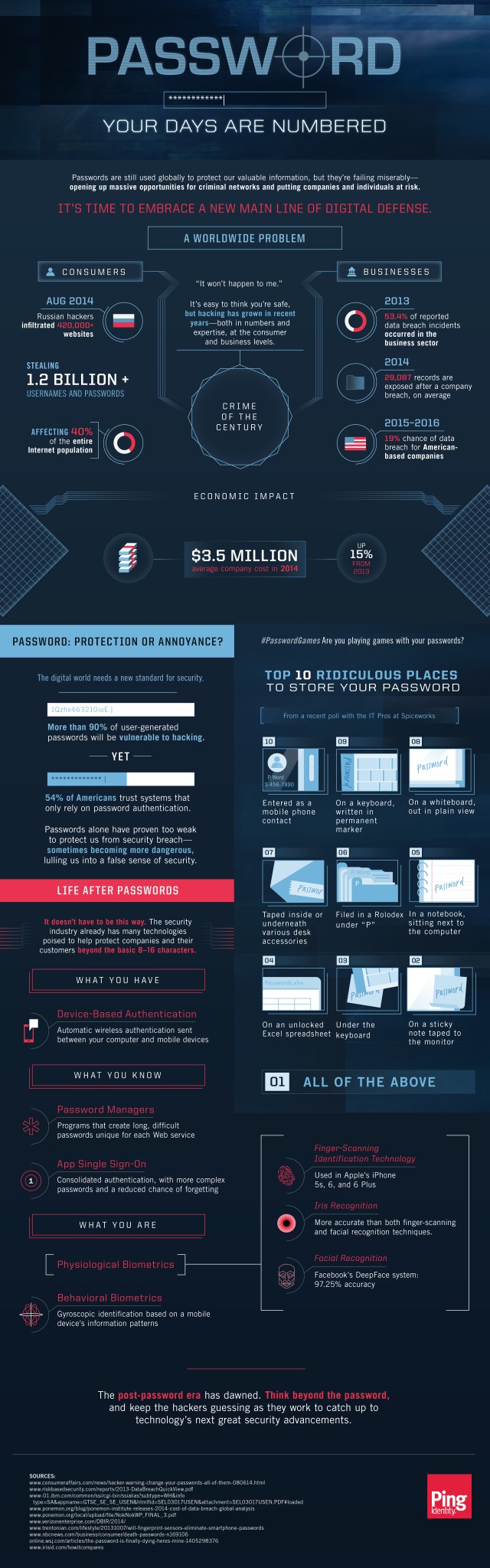
Photo Credit: JMiks/Shutterstock
-

New public cloud backup cuts the cost of protecting data
Publié: octobre 9, 2014, 5:00pm CEST par Ian Barker

Backups have traditionally involved removable media, whether tape or disk, to allow copies of essential information to be held off site for safety.
The cloud has changed all that but companies still have concerns about security and retention of data, as well as expense. A new product released today by Druva is aimed at delivering a long-term storage solution with less complexity and lower cost.
Druva Phoenix offers a practical alternative to the traditional server backup model requiring backup to secondary storage, tape and then long-term offsite archiving. Phoenix unifies hot, warm and cold backup and archiving processes and administration, offers unlimited retention, and can perform backups and restores up to 20 times faster than other solutions. The company also reckons it can achieve 70 percent cost savings over traditional backup solutions.
"The traditional backup-to-tape-to-archive process is expensive, resource-intensive and subject to error, with 75 percent of organizations experiencing tape failure in the last year. The cloud is clearly a better choice, but current cloud-based solutions have serious limitations ranging from slow speeds and limited data retention to failure to utilize the distributed nature of the cloud to perform large-scale backups," says Jaspreet Singh, CEO of Druva. "By leveraging the technology we developed for our inSync endpoint backup platform as well as our five years of experience with the AWS public cloud, Phoenix offers a truly disruptive alternative that eliminates tape and makes the cloud a viable choice for server backup for the first time".
Key features of the product include unified backup and archiving with ever-incremental backups that remove the need for companies to perform periodic full backups. All processes are centrally managed from a single console to reduce IT overhead.
Storage is optimized so that organizations can store limitless recovery points and archive and retain their data for as long as required -- decades if necessary -- to meet regulatory and compliance rules.
Phoenix delivers direct-to-cloud backup and restore speeds of 100Mbps -- 20 times faster than other solutions -- utilizing the latest in object storage coupled with parallel data transfers. Sites with large data sets, limited bandwidth or demanding recovery time objectives can utilize Phoenix CloudCache, an on-site soft appliance that provides hot LAN-speed backups and restores via local caching. Transfers to the cloud are then staggered to free up real-time bandwidth.
Phoenix uses Amazon Web Services to ensure customer data is maintained in a secure public cloud infrastructure and protected by a full range of system certifications.
For more information and to sign up for a free trial you can visit the Druva website.
Photo Credit: Andreas Weitzmann/Shutterstock
-

The Thing from the Internet -- and why we’re scared of it
Publié: octobre 9, 2014, 4:12pm CEST par Ian Barker
According to a new survey UK consumers increasingly fear the pace of change they face and are particularly cynical about the need for connected, "Internet of Things" devices.
According to the survey of over 1,600 consumers by UK-based audit and accounting specialist KPMG, more than half of people (58 percent) resent the idea that computers seem to run their lives. Also 70 percent suggest that with the marketplace flooded by inter-connected devices, it's too easy for things to go wrong. The survey reveals a hankering for a return to 'simple' technology. Many, for example, mainly want their phone to make calls (54 percent) and the majority think that more advanced internet-based products such as smart fridges which self-order food or cookers reminding owners about recipes aren't needed.
Asked about the reasons for their worries respondents cited difficulties in keeping personal information private, with 56 percent of those polled concerned about a 'Big Brother' effect occurring as a result of internet enabled products and the pace at which they are being produced and implemented. In a work environment, more than a third (36 percent) fear that employers are monitoring their every action.
Wil Rockall, a director in KPMG's Cyber Security practice, says, "It is clear that consumers are struggling with a desire to use connected devices as a route towards an easier life, but they remain wary of the rise of the machine. They still support innovation, recognizing that in the right environment having the latest technology is key -- nearly 60 percent acknowledge that technology makes us more effective at our job".
Indeed, respondents are quick to recognize that inter-connected devices can bring some benefits, with 48 percent welcoming the idea that smart meters can save energy and money, for example. Four in 10 also suggest that health monitors which issue warnings about impending illness are a good idea and 46 percent want to use security systems to monitor their property whilst away from home.
"Security and privacy are high on the list of worries for the consumer with 62 percent believing that there is insufficient concern about it," adds Mark Thompson, a senior manager in KPMG's Cyber Security practice. "The fact remains that where once an Englishman's home was considered to be his castle the advent of the Internet of Things means that fortress walls can be breached more easily. There are also so many opportunities for the latest technologies to provide value and enhance our lives but we are failing to take advantage of them and we will continue in that vein until consumers can be convinced that always-connected devices are safe and worthwhile".
Image Credit: Julien Tromeur / Shutterstock
-

Big data helps with detection of cyber attacks
Publié: octobre 8, 2014, 1:20pm CEST par Ian Barker

The main problem that organizations face when combating cyber attacks is that they don't know what to look for and find it difficult to interpret all the data they get from their networks.
Big data analytics company Exabeam has a new product that can cut through the forest of data to make it easier to detect attacks and insider threats in real time using existing security information and event management (SIEM) details.
What Exabeam does is to add a layer of user behavior intelligence on top of existing SIEM and log management data to give IT security teams a complete view of the attack chain. This helps to spotlight valid attack indicators which currently risk getting lost in a sea of security noise.
According to research from Verizon 76 percent of network intrusions in 2013 used authorized credentials to impersonate legitimate users. This is something existing SIEM technologies struggle to detect, Exabeam provides access to real-time data which makes it easier to spot suspicious behavior.
"For too long, security teams couldn’t get ahead of hackers because they didn't know what to look for, had too many security alerts to process and didn’t get the complete picture of what was happening in their network," says Nir Polak, Exabeam's CEO and co-founder. "Exabeam fundamentally changes the way that cyberattacks are managed by addressing these challenges in an automated way and giving security teams the intelligence they need in real time. The future of cyberattack management starts with Exabeam, and the future is now".
Capabilities of the Exabeam platform include extraction and enrichment of existing log feeds, such as Windows, Unix, VPN and security events. It also allows tracking of all user activities regardless of the IP, devices and accounts used.
It uses machine learning to carry out behavioral analysis to automatically and continuously learn user and peer group behavior. By applying risk scoring it can assess the importance of a threat taking into account user access, assets exposed and threat intelligence.
You can find out more and request a demo of the product on the Exabeam website.
Photo credit: Tashatuvango/Shutterstock
-

Professionals believe their Java apps are secure despite relying on third-party code
Publié: octobre 8, 2014, 11:50am CEST par Ian Barker

Almost two-thirds of senior IT professionals say that their enterprise Java applications contain 50 percent or more third-party code.
These are findings from application security company Waratek based on a survey of attendees at last week's JavaOne conference. However, despite recent high profile vulnerabilities in third-party code, like Shellshock and Heartbleed, nearly 80 percent of respondents still believe their java apps are secure.
"It's a well-known fact that custom developed Java applications are largely constructed with third party software libraries that provide no assurances of security or timely vulnerability mitigation," says Brian Maccaba, CEO of Waratek. "What we found surprising was the high degree of confidence that software developers have in the security of Java applications that use open source components, especially given the widespread threats posed by the recent 'Shellshock' and 'Heartbleed' software flaws".
Further results from the survey show that of those polled 33 percent believe their Java applications are very secure, 46 percent somewhat secure and 13 percent not very secure. When asked about the proportion of third-party or open source code used in their applications, 27 percent say it makes up more than two-thirds of applications, 30 percent say it's more than half and 16 percent more than a quarter with only 19 percent saying less than that.
When asked about the most important considerations when moving Java applications to the public cloud, 71 percent cited security, 54 percent stability and up time, and 28 percent portability and migration. Almost half (46 percent) of respondents said the ability to run Java applications in a secure container would accelerate their plans to move to the public cloud.
You can find out more about Waratek's Application Security for Java platform on the company’s website.
Image Credit: isak55 / Shutterstock
-

How US organizations are losing the cyber war
Publié: octobre 7, 2014, 5:32pm CEST par Ian Barker

Cyber crime, hacking and data breaches have seldom been out of the news in 2014, but just how well are organizations coping with it?
Not very well, according to a new infographic released by security solutions company CSO that's based on the results of a survey of over 500 private and public sector executives and security experts.
Among the findings are that 77 percent of organizations have reported a security breach in the past year, with an average of 135 incidents per organization. Yet only 38 percent have a system to prioritize security spending based on risk and business impact.
Of those that detected an incident, 69 percent said they weren’t able to estimate the cost. Those that did, put the average annual loss to cyber incidents at $415,000. However, 19 percent of US companies put losses at between $50,000 and $1 million.
Among the major concerns are that most organizations don't take a strategic approach to security, supply chain risks that aren’t adequately assessed or understood, and inadequate mobile device security.
The report finds that effectively fighting cyber crime requires collaboration in order to share experience and knowledge of threats. It also needs strategic spending, particularly on security training for employees.
You can view more detail in the complete infographic below.
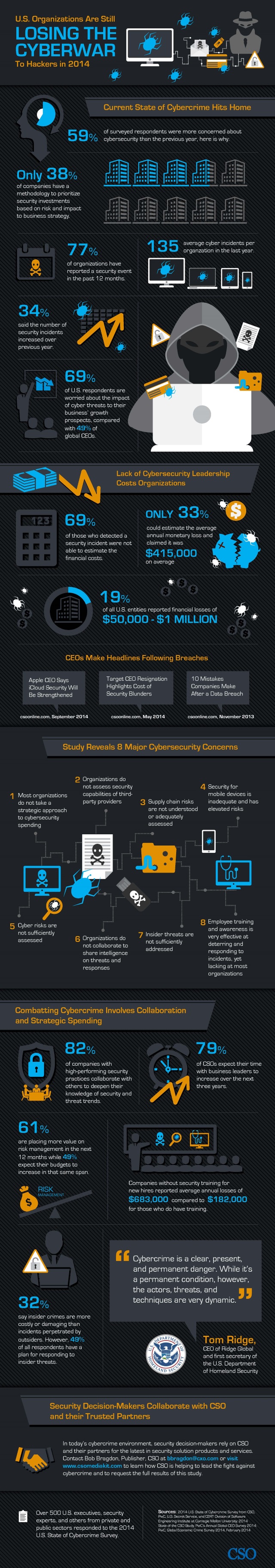
Image Credit: Oleksiy Mark / Shutterstock
-

New dedicated tool makes for easier Spark monitoring
Publié: octobre 7, 2014, 4:17pm CEST par Ian Barker

The Apache Spark framework is a popular add on to Hadoop for handling big data, particularly for building machine learning algorithms.
Until now though it's been hard to effectively monitor Spark performance. That's about to change as Brooklyn-based performance management company Sematext is launching its SPM for Spark.
The tool monitors key metrics for all Spark components -- master, workers, driver, and executor. It also includes alerting, anomaly detection, custom dashboards, log correlation and event graphing. SPM for Spark can be installed on premises or used from the cloud.
"Spark usage has been going through the roof," says Otis Gospodnetic, Sematext’s founder and CEO. "And engineers and DevOps folks handling Spark have not had a good monitoring tool at their disposal. By releasing the first Spark monitoring product to market with SPM, we have just filled a big hole in the Spark ecosystem".
SPM works seamlessly with centralized logging, log management and analytics solution Logsene, to provide a single pane of glass for performance monitoring, centralized log management, alerts, anomalies, custom events, and custom key performance indicators.
John Tripier, Alliance and Ecosystems lead at Databricks says, "One of the critical factors in the success of Spark has been the large developer community contributing to it, and the growing number of applications using Spark. We're very excited to have Sematext join this community and contribute their expertise with a comprehensive monitoring solution like SPM".
You can find out more about SPM for Spark's features with a downloadable datasheet or sign up for a free trial on the Sematext website.
Image Credit: alphaspirit / Shutterstock
-

New partnership makes it easier for merchants to accept bitcoin payments
Publié: octobre 7, 2014, 3:06pm CEST par Ian Barker

Whilst virtual currency bitcoin has soared in popularity in recent times it still isn't an option when it comes to buying goods and services from many mainstream merchants.
That could be about to change thanks to a new partnership between SaaS mobile marketing and customer service provider Acromobile and ecommerce platform Bitnet.
Acromobile Payments will integrate the Bitnet platform to make bitcoin acceptance available to any merchant in a fully integrated order-to-bitcoin-to-cash solution with easy integration into existing CRM and ERP systems.
"Bitcoin is tailor-made for the Internet," says Alain Gendre, VP of Alliances at Bitnet. "No fraud, no risk, no borders, and lower fees than the most common current payment methods. And bitcoin acceptance is only going to grow; we’re seeing merchants who are early adopters of bitcoin reporting that they’ve increased sales and added a new base of customers. We're excited to partner with Acromobile in providing merchants with the ability to accept bitcoin payments".
Black Friday in 2013 saw total bitcoin transaction volume exceed $487 million, making it the fifth largest payment network on the day behind only Visa, MasterCard, American Express, and China UnionPay, and ahead of Discover and PayPal. It's clear therefore that accepting bitcoin payments has benefits for retailers.
"With companies like Dell and eBay already accepting Bitcoin, the demand from B2B and B2C merchants is really accelerating," says Jason Masciarelli, founder of Acromobile. "With Bitnet we are able to deliver an integrated CRM and commerce platform to unlock the bitcoin opportunity for merchants with no risk and have them get paid in their local currency".
Acromobile Payments includes CRM features for easy management of customer profiles, orders, invoices, and transactions to monitor payment status and history. The request payment feature enables merchants to quickly send payment requests to customers. It's mobile-optimized too, allowing customers to pay with bitcoin from any iOS or Android device.
The bitcoin-enabled software is currently available to merchants by invitation and is scheduled to be generally available by the end of next year. To find out more and request an invitation visit the Acromobile website.
Photo Credit: igor.stevanovic/Shutterstock
-

Cloud-based management allows parental control of multiple devices
Publié: octobre 7, 2014, 11:03am CEST par Ian Barker

As we saw last week, parental control products are a bit of a mixed bag and are only part of a protection strategy that includes effective education.
If you have several different devices in the family you may also end up using multiple products to protect them. That is unless you use the latest version of Remo Software's MORE which offers cloud-based management across multiple platforms.
MORE lets users manage and control Windows, Mac, Android and iOS systems and promises to add several internet of things devices in the near future. It gives parents more control over children's device use and also provides home users the ability to manage health technologies and other IoT devices used by their family members.
Version 1.25 of MORE allows the software to be installed on every family member's device and a customized level of control to be set for each via an easy-to-use web console. It's possible to block apps like Facebook and Twitter, allow full access to apps or set time limits. With a single click, administrators can perform device maintenance tasks such as cleanups and can also update device settings at any time, either from the web console or via an app on a mobile device.
It can remotely track devices via GPS, take pictures using the built-in camera, sound a panic alarm or remotely wipe data from lost or stolen devices.
"The 1.25 version of Remo MORE provides families and small to midsized businesses with everything they need to control device usage, ensure security and perform cleanup and maintenance tasks," says Omer Faiyaz, Remo Software’s founder and CEO. "Now parents have the tools necessary to protect kids online and set limits on app usage, and this is just the beginning -- by early 2015, Remo MORE will even allow users to manage IoT devices like health technologies, lighting, switches, appliances and more".
You can get more information on the Remo Software website and try out the software on two devices for free.
Photo Credit: wavebreakmedia/Shutterstock
-

Prelert cuts big data down to size for real-time analysis
Publié: octobre 6, 2014, 3:53pm CEST par Ian Barker

Identifying complex anomalies that show up the presence of a persistent threat or pinpoint the cause of network and IT performance problems is the sort of thing big data analysis was made for.
The problem though is that big data is often just too big. This means it's usually necessary to transfer the information before doing any work on it which makes real-time analysis impossible and means valuable insights aren't available when they're most needed.
Prelert, a specialist in anomaly detection, has a solution in the form of its new Stats Reduce feature that can dramatically shrink data transfer sizes by up to 40 times. This cuts the time it takes to transfer data but retains its integrity to ensure accurate results.
It works by using the statistical aggregation functions already available in platforms like Splunk and Elasticsearch. The software has been rigorously tested against real world data sets and proven to deliver the same results whether working on the raw or aggregated data.
"Prelert is committed to providing the most accurate and robust insight into data in real-time, no matter how large or complex," says Stephen Dodson Ph.D, Prelert's CTO. "The scale of modern environments presents challenges that require careful selection of methods and techniques, and we built our technology to align with these environments from the start. With Stats Reduce, the aggregation techniques we developed allow massive volumes of data to be analyzed in a distributed manner, enabling real-time multidimensional anomaly detection on Big Data".
Stats Reduce is available from today in the latest version of Prelert's Anomaly Detective and will be rolled out to other big data platforms later this year. The company will be demonstrating it at the Splunk Worldwide Users' Conference this week in Las Vegas.
Photo Credit: Arkady/Shutterstock
-

Security risk is the main reason for banning BYOPC
Publié: octobre 6, 2014, 2:30pm CEST par Ian Barker

According to a survey of IT decision makers commissioned by efficiency software specialist 1E and carried out by Vanson Bourne 86 percent of companies that ban employees from using their own PCs do so because of security concerns.
To address these fears 1E is launching its new MyWorkNow solution, a client-hosted virtual desktop (CHVD) to offer a fast, low-cost way of mobilizing workforces using their own PCs.
The virtual desktop runs locally on the host PC and by using the enterprise's chosen desktop management framework, such as Microsoft's System Center Configuration Manager (SCCM), MyWorkNow eliminates the need for additional hardware and central infrastructure.
It allows enterprise security to be delivered to any PC or Mac with 4GB or more of RAM. Using a FastBoot technology it streams the MyWorkNow desktop in real time as the machine starts up, allowing fast access to the corporate desktop and offline capability if required.
MyWorkNow delivers secure authentication and a 256 AES encrypted local image on a user's own hardware. There’s a remote wipe functionality, which enables an IT department to immediately deactivate MyWorkNow on a user's PC if it's lost or the employee leaves. It also provides default client security, which controls employee opportunities to copy or paste in or out, file drag or drop, or copy intellectual property to a USB drive. Thus ensuring that corporate data is encrypted and secured at the user endpoint.
Other findings of the survey include that more than a quarter of respondents currently don't have a formal policy in place for personal desktop/laptop PC use. More than a third of IT decision-makers prohibit BYOPC because of the associated needs to support and track software usage on personal devices. Yet 11 percent reported that despite the business not allowing it, employees used their own PCs to access work anyway. 84 percent of IT decision-makers allow email access from personal devices, while only 52 percent allow access to hosted applications.
"Employees and organizations will both benefit from the BYOPC movement as evidenced by the Vanson Bourne survey," says Sumir Karayi, CEO of 1E. "MyWorkNow addresses the security concerns that have historically been the deterrent for adopting a BYOPC policy. Not only does it help IT departments sleep better at night knowing they have full control, but it also enables them to run IT for less".
To find out more you can register for a joint Forrester/1E webinar to be held on on Oct 16 or visit the 1E website.
Photo Credit: auremar/Shutterstock
-

Using mobile messaging to deliver better customer service
Publié: octobre 6, 2014, 12:09pm CEST par Ian Barker

As mobile devices become almost ubiquitous, their attractiveness as a channel for businesses to interact with their customers becomes greater.
According to last year's ICMI mobile customer service strategy survey, 68 percent of experts believe mobile can improve the customer experience. To help companies take advantage of the opportunities mobile offers, enterprise mobile specialist OpenMarket is launching its latest Mobile Engagement Platform. It's a SaaS-based solution, allowing enterprises to easily create and deploy smart, interactive mobile engagement services worldwide with connectivity to over 200 countries.
The platform can integrate with existing CRM systems, using current customer data to create automated, personal and real-time mobile interactions with customers. Key features include the ability to deliver customer alerts to send up-to-date information about orders, deliveries and appointments as well as targeting special offers. Two-way messaging allows businesses to gather feedback and conduct surveys. It can also be used for technical support to offer real-time issue and resolution tracking.
"Customer service is a key differentiator for major enterprises," says Jay Emmet, General Manager at OpenMarket. "Consumers want to communicate with customer service on their preferred channel, which is mobile, and get quick resolution of their issues. They do not want to wait on hold after navigating an IVR system. Enterprises decision-makers should be leveraging the mobile channel as much as possible to accomplish this goal. By implementing two-way SMS communication through OpenMarket’s Mobile Engagement Platform, enterprises can provide a better customer experience that closely aligns with the increasing consumer demand for mobile messaging interactions".
You can find out more on the OpenMarket website and there's a free whitepaper on how mobile can be used to transform the customer experience. The company's solutions will also be on display at the Gartner Symposium/ITExpo being held in Orlando this week.
Image Credit: Art Allianz / Shutterstock
-

Shellshock -- we ain't seen nothing yet
Publié: octobre 3, 2014, 12:35pm CEST par Ian Barker

It's now just over a week since news of the Shellshock bug broke and analysts are still trying to work out just how much of an impact it could have.
Security specialist Incapsula has been tracking the vulnerability to get an idea of its magnitude, looking at the number of sites attacked and the damage caused.
The company says it has so far stopped 310,928 exploit attempts, an average of over 1,800 per hour. A spike in attacks over 27/28 September it says was partly down to attackers moving quickly and partly to businesses testing their own vulnerability.
Of the total traffic around 94 percent was some form of attack in the form of scans, server hijack attempts and DDoS malware seeding. Writing on the Incapsula blog co-founder Marc Gaffan says, "The highjack attempts were the most immediately troubling, comprising about 20 percent of the total. Scans and DDoS malware seeding made up the remaining 70 percent or so. To answer the question of how dangerous the vulnerability is, my experience leads me to believe that this may well be the calm before the storm. This appears as if a lot of criminals are setting the stage for future attacks".
These figures are based on Incapsula's sample of 100,000 websites. If its hourly figure for attacks is extrapolated over the entire web that’s potentially 1.3 billion attacks carried out over the first weekend of the vulnerability.
Gaffan warns, "The sheer volume of attacks and the types of planning Incapsula is seeing -- scans, backdoor insertions, and DDoS groundwork -- on such a large scale means that companies need to work now to fix their vulnerabilities". He goes on to say that the real fallout may still be to come from the numbers of machines that have already been compromised.
The bottom line is that businesses need to stay alert, patch systems and not assume that the danger has passed. You can read more and download the latest threat landscape report on Incapsula's website.
Image Credit: Jirsak/Shutterstock
-

Increase in unpatched browsers and operating systems leads to security concerns
Publié: octobre 2, 2014, 4:03pm CEST par Ian Barker

October is National Cyber Security Awareness Month (NCSAM) in the US and security company Secunia has marked this by issuing its latest Country Report assessing the state of security among PC users.
Key findings include that Microsoft’s Internet Explorer, with a market share of 73 percent, had 218 vulnerabilities with 11 percent of installed programs being unpatched and vulnerable. The percentage of users running unpatched operating systems has increased to 12.6 percent, from 11.1 percent in the previous quarter.
The number of people running unpatched, end of life, programs is also up from 4.9 to 5.7 percent. The most exposed programs over the last quarter were: Oracle Java 7 with 145 vulnerabilities and 42 percent of installations unpatched, Apple QuickTime 7 with 11 vulnerabilities and 33 percent unpatched, and Adobe Reader 10 with 21 vulnerabilities and 23 percent of installed programs unpatched.
Interestingly though it seems that the power to stay safe is often in users' hands. Secunia's Vulnerability Review 2014 finds that 86 percent of vulnerabilities in the top 50 software applications on private PCs had patches available on the day when they were disclosed in 2013.
"It only takes one vulnerability for a hacker to exploit a user’s system. Just one. We are concerned to see such a high share of users with unpatched and End-of-Life browsers and operating systems," says Kasper Lindgaard, Director of Research at Secunia. "We hope that as part of National Cyber Security Awareness month, users will take a moment to make sure their systems are up to date with the most recent program versions and patches".
As part of NCSAM Secunia is encouraging users to download its free Personal Software Inspector to check that their installed versions are up to date and protected against vulnerabilities.
You can access the full US Country Report for Q3 2014 on the Secunia website.
Image Credit: alexskopje / Shutterstock
-

NoSpyProxy wants to put your data and identity out of reach of the NSA
Publié: octobre 2, 2014, 3:21pm CEST par Ian Barker

Since the Edward Snowden revelations that governments as well as hackers were likely to be snooping on your internet activity it's been widely assumed that there's no such thing as safe online access.
VPN specialist CyberGhost has other ideas and has been seeking funding via Indiegogo for what it calls a NoSpyProxy. The company's VPN already uses AES256 military-grade encryption to protect passwords, bank accounts and other details as well as obscuring locations and IP addresses. It now aims to make things even more secure by placing the data center hardware under the control of an additional layer of security. This will put CyberGhost in control of the whole process from login through encryption protocol, key management and finally also the server itself.
CyberGhost's NoSpyProxy will be setup and taken care of by its own Certified Security Specialists and will serve to protect people all around the world from mass surveillance, hackers, data and identity theft. It refers to this not as a data center but as a "no-data" center, a new generation of working technical unit that is built to protect people's privacy and security online.
It aims to make this the blueprint for more NoSpy nodes that can be easily rolled out in other countries and regions.
This is obviously a popular idea as the company has managed to reach its $70,000 funding target in just 14 days. "We are so excited that our #NoSpyProxy campaign has reached its initial goal and we managed to draw attention on this important subject of online privacy. We're sure that more victories of privacy will follow, but every citizen has to take responsibility for his own online privacy and personal data by using trustful encryption services," says Robert Knapp, the CEO of CyberGhost VPN.
If you're interested in finding out more and maybe contributing to the funding you can visit the project's Indegogo page.
Photo Credit: auremar/Shutterstock
-

Just how effective are parental control products?
Publié: octobre 1, 2014, 3:37pm CEST par Ian Barker

Parents are keen to ensure that their offspring don't access inappropriate material on the web and for that reason most security software providers now offer parental control products, whether as a standalone product or part of an internet security package.
In a study commissioned for a German magazine, AV-Comparatives has looked at the leading products for Windows and mobile platforms to assess which are the most effective.
There is of course no universal standard for what is acceptable content and as the report points out, "Parents need to talk to their children about the potentially dangerous and upsetting things in life, whether or not they use parental control software". It also stresses that the software is only effective if it’s properly configured.
The tests looked at 22 Windows products, five for Android and three for iOS. Using settings based on those suitable for a nine-year-old girl researchers tested them against almost 600 websites on subjects ranging from abortion to weaponry. They also checked whether it was possible to bypass blocks using Google’s cache or translate functions.
Of the Windows products only two, Microsoft Windows Live Family Safety and Telekom Kinderschutz, achieved a 100 percent block of restricted material but at the expense of a high level of false alerts. AVG Family Safety and Norton Family both achieved 99 percent block rates for porn with low levels of false alerts (zero for AVG) but did less well in blocking other material.
For iOS devices the best product was Deutsche Telekom Surfgarten with 100 percent success rates across the board but again a high level of false positives. The parental controls in iOS 7 managed 92 percent porn blocking but only 62 percent overall.
No Android product managed a 100 percent score, the best being BlueCoat K9 with 98 percent porn blocking and 72 percent overall, and Mobicip Safe Browser (97 and 77 percent) but both had low levels of false alerts.
It's clear from the results that no parental control solution is perfect and the report’s authors say, "We strongly advise parents using parental control software to test that it is working as they intend by performing a spot check of whether categories and individual sites are being appropriately blocked/allowed". They also recommend visiting the UK government backed Get Safe Online site which has lots of advice about online risks.
You can download the full report which offers much more detail on each of the products tested from the AV-Comparatives website.
Image Credit: Pressmaster / Shutterstock
-

'Grandroid' smartphone designed to meet the needs of the elderly
Publié: octobre 1, 2014, 12:13pm CEST par Ian Barker

As increasing numbers of government and other services go online, internet access becomes more important and mobile devices play a big part in that.
Yet according to charity Age UK there are 10.8 million people aged 65 or over in the UK but only three percent of them own a smartphone which could mean they're missing out on 'digital inclusion'. In order to make smartphones more accessible to older users, the new Amplicomms M9000 has all the benefits of an Android touch screen phone but with hardware and software specially adapted for the less technically adept.
Users of the phone can opt to use the standard Android 4.2 operating system or the Amplicomms operating system which features extra-large icons, intuitive menus and large, easy-to-read text along with built-in apps including a music player, calendar, email and internet browser. It's easy to switch between the two operating systems in the phone's menu.
The phone's hardware also has features geared to the needs of elderly users. It has a speaker volume of up to 40Db and a ringer volume of 90Db, it's also hearing aid compatible. On the back is an SOS button which can be programmed to call or text selected numbers in an emergency.
Standard phone features include 300K front and 5MP rear cameras, a 1.2GHz dual-core CPU, 256MB of RAM, 3G, Wi-Fi, GPS and Bluetooth. It also has dual SIM slots to make it easy to switch networks. The M9000 is available now in the UK from Hearing Direct.com. It's SIM free so you can use any network and costs £139.99.
If you're wondering what your elderly relatives might use a smartphone for there's a handy infographic guide to suitable apps from HomeCare Technologies reproduced below.
-

Most businesses waste money on 'shelfware' that’s never used
Publié: octobre 1, 2014, 11:06am CEST par Ian Barker

Almost two-thirds of companies plan on freezing or shrinking their software spend and 96 percent of organizations report that they're wasting money on software that is unused.
These are among the findings of a new report by Flexera Software in conjunction with IDC which looks at pricing and licensing. The biggest concern is that almost all businesses have "shelfware" that is never used.
The results show that 39 percent of companies report that 21 percent or more of their software spend is wasted on unused software. Yet at the same time software budgets are expected to remain the same or shrink over the next two years.
"It’s very easy for shelfware to accumulate when organizations don’t proactively implement best practices and technology to track, manage and optimize their software estates," says Amy Konary, Research Vice President -- Software Licensing and Provisioning at IDC. "Enterprises must have the ability to continually identify where software licenses are deployed, how those licenses are being used, and reconcile that data with the complex set of rules contained in the licensing agreements. By having this level of insight, CIO's can begin to identify shelfware, eliminate waste and reallocate their budgets more effectively".
Shrinking budgets are driving a shift in the way software is licensed though. The previously common perpetual software license is now only used for the majority of software by 45 percent of organizations. This is expected to decline to 36 percent over the next one to two years.
Instead businesses are switching to subscription (24 percent) or usage-based (17 percent) models. In response software producers are offering a wider variety of licensing options with only 35 percent saying that the majority of their revenue now comes from perpetual licenses.
"It doesn’t always make sense to pay up front for the full cost for software before the application has proven its value to the organization," says Steve Schmidt, Vice President of Corporate Development at Flexera Software. "In their drive to increase efficiency and cost effectiveness, some organizations prefer to pay for software in ways that allow them to better align their costs to value. That might mean paying over time via a subscription model, or by the features, functionality or capacity that they’re actually using, via a usage-based model".
The full report is available to download from the Flexera website.
Image Credit: Ilyarexi / Shutterstock
-

Another data breach... Yeah, yeah, whatever
Publié: septembre 30, 2014, 5:06pm CEST par Ian Barker

It seems like data breaches are seldom out of the news these days, but whilst that means we're more likely to be aware of their existence it also means there's a risk that individual threats begin to fade into the general day-to-day techy chatter and we don't give them the attention they deserve.
The growing number of breaches -- up 10 percent over last year according to a recent study by the Ponemon institute -- means they're less likely to catch our attention. Security training firm KnowBe4 refers to this phenomenon as "breach fatigue" and warns that it may be placing companies at risk.
"The increasing volume of customers affected by these data breaches may be causing a complacency that creates even more risk," says Stu Sjouwerman, CEO of KnowBe4. "For most companies, it is not a matter of if, but when, followed by a free year of credit monitoring. For users, the constant barrage of breach news can cloud their awareness of cyber-threats as it all becomes background noise".
The company warns that a careless attitude on the part of individuals can carry over to the business environment. This in turn leads to more risk of being hacked, phished or socially engineered into giving away company information.
Michael Bruemmer, vice president of the credit information company Experian's data breach resolution group which sponsored the Ponemon study, says that 80 percent of the breaches his group works with, "had a root cause in employee negligence." He goes on to say, "It could be from someone giving out their password, someone being spear-phished, it could be a lost USB, it could be somebody mishandling files, it could be leaving the door to the network operations center open so someone can walk in".
You can find out more about how KnowBe4's security awareness training can help employees stay alert to the risks on the company's website. It's also offering a free whitepaper charting the rise of ransomware.
Photo Credit: Suzanne Tucker/Shutterstock
-

Simpler, faster, more secure file transfers with Send Anywhere 2.0
Publié: septembre 30, 2014, 3:31pm CEST par Ian Barker

Sending files to someone else has always been a bit of a problem. Often they’re too big for email, sharing via public cloud services raises security concerns and of course flash drives and DVDs can fall into the wrong hands.
Korea-based startup Send Anywhere has an answer to making file transfers easily and safely in the form of an updated version of its iOS app and a new app for Windows Phone.
Send Anywhere uses peer-to-peer file transfer technology. The way it works means that users don't need to sign-up, log-in, or even know their recipients' contact information. They simply select the files they want to send and get a six-digit one-time key that is only available for 10 minutes before it self-destructs. The code is then sent to the recipient who uses it to download the files.
The updated iOS version offers more complex encryption codes for better security along with a fresher, cleaner design. In addition it has a feature to make sharing the key easier, holding the center of the Send screen automatically copies the key to the clipboard. Pressing a Share button then gives easy access to email and messaging in order to send it.
The Windows Phone app currently offers just basic sending and receiving functions but the company says it will be used as a platform to develop the Windows offering.
Send Anywhere is also available on Android and as a web service, allowing files to be sent and received on any type of PC or mobile device. There's a plugin for Chrome browsers as well. Version 2.0 is available on the app stores from today.
Image Credit: dny3d/Shutterstock
-

Weak passwords are still a major problem for business security
Publié: septembre 30, 2014, 12:26pm CEST par Ian Barker

According to data released by security company Trustwave which has analyzed evidence from almost 700 security breaches that took place in 2013, retail is the most compromised industry, accounting for 35 percent of attacks investigated.
The food and drink industry ranks second on 18 percent followed by hospitality on 11 percent. Perhaps not surprisingly e-commerce is most at risk, making up 54 percent of assets targeted whilst data centers account for only 10 percent. Point of sale breaches made up 33 percent of Trustwave’s investigations.
A little worrying is that the median time from an initial intrusion to its being detected was 87 days. Also over 70 percent of compromise victims didn’t detect the breach themselves.
The report looks at the top 10 vulnerabilities found in network penetration testing too. This reveals that weak passwords are still a major problem when it comes to security. During its penetration tests Trustwave collected 626,718 stored passwords and managed to recover more than half of them in minutes. 92 percent of the sample were able to be cracked in 31 days.
Weak or default passwords contributed to a third of the investigated breaches. The three most common passwords in order are "Password1", "Hello123", and "password". Password length is mostly around eight characters -- probably because many systems use that as a minimum.
The report suggests that administrators need to, "Educate users on the value of choosing longer pass-phrases instead of simple, predicable, easy-to-crack passwords". It also recommends deploying two-factor authentication.
More details of Trustwave's 2014 Global Security Report are available in interactive form on the company's website.
Image Credit: Africa Studio / Shutterstock
-

Educated, tall, rich, female coffee drinker? You must own an iPhone
Publié: septembre 29, 2014, 3:21pm CEST par Ian Barker

When the first iPhone went on sale in June 2007 expert opinion was very much of the view that it wouldn't have a significant impact. Steve Wildstrom of Business Week for example said, "The iPhone will never be a threat to the BlackBerry".
Proving that experts can be very wrong, the iPhone has of course gone from strength to strength and Carphone Warehouse in Ireland has produced a fascinating infographic charting its evolution up to the latest version.
There are more fun quotes from 2007, but there's also a detailed list of the technical specs of the various versions over the years. It looks at the apps that have been a big part of the phone's success too.
There's a fun look at the typical iPhone owner as well. Apparently they're more likely to be better educated, richer, older, taller and female compared to Android users. They also give more to charity, drink fancier coffee and watch the Simpsons. So, basically iPhone owners are a great bunch of people.
Finally the graphic looks at what we're likely to see when the iPhone 7 comes along. This includes things like better battery technology, flexible screens -- as opposed to bendy phones -- and 3D display technology.
You can view the full infographic below, and do let us know if you're a typical iPhone user, or if like the experts you thought it would never catch on.

Image Credit: KieferPix / Shutterstock
-

Shellshock bug is bad and could take years to eradicate say experts
Publié: septembre 26, 2014, 3:40pm CEST par Ian Barker

Ever since yesterday’s news of the Shellshock Bash bug broke cyber security experts have been lining up to make clear how bad it really is.
Unlike Heartbleed, which affected mainly servers, Shellshock leaves a whole host of systems vulnerable including Apple OSX systems and many internet of things devices with embedded code that’s based on Unix or Linux.
Professor Mike Jackson cyber security expert at the UK's Birmingham City University says, "Obviously everyone wants to know if they might be vulnerable to attack. If you are an Apple PC user then the immediate answer is 'Yes'. Apple's OS X operating system is Unix based and therefore vulnerable. Window’s users should not however be complacent. Your PC might be safe but what about the router you use for your broadband? Like as not it will use Unix-based software and therefore may be at risk of attack".
Because a great deal of the web relies on Apache which is also Unix based many internet sites are at risk too. This leads to general consensus that Shellshock is -- or at least has the potential to be -- worse than Heartbleed. Joe Siegrist, CEO and co-founder of LastPass sums up why, "The reason this could be potentially worse than Heartbleed is that with Shellshock you can make things run on a server, and get access to anything on that server, so in that way the exploits could be worse in terms of the actions that can be taken and the data at risk, and have worse consequences than Heartbleed."
The internet of things also represents a target rich environment for hackers thanks to this bug. Corero Network Security's Vice President of Product Management, Bipin Mistry says, "The Internet of Things or Machine to Machine could enable millions of network attached devices, both hardwired and mobile, to become bots for initiating amplification or high bandwidth attacks -- hackers and attackers know this quite well and are exploiting the vulnerabilities that are substantiated in IoT devices".
A huge number of IoT devices means the potential to create large botnets. To combat this Mistry suggests, "Above and beyond the threat protection, there is additional value in understanding the details of the attack from analytics and insight and then rapidly turn the visibility around and provide even greater threat protection for the business".
Daniel Ingevaldson, CTO of Easy Solutions warns that companies must remain vigilant, "Everyone should watch their logs carefully -- this exploit is noisily and easily logged -- and patch as soon as possible. In addition, given the risk that the patches may not be effective, organizations should consider monitoring to ensure their devices are not being used to host phishing or other attacks."
Ron Gula, CEO and CTO of Tenable is worried that some companies may struggle to deal with the problem. "Auditing systems for ShellShock will not be like scanning for Heartbleed. Heartbleed scans could be completed by anyone with network access with high accuracy. With ShellShock, the highest form of accuracy to test for this is to perform a patch audit. IT auditing shops that don't have mature relationships with their IT administrators may not be able to audit for this".
Quite how serious Shellshock is only time will tell but we’ll leave the last word to Birmingham City University's Mike Jackson, "Literally millions of websites could be open to the exploitation of the Shellshock bug. The damage it could cause is as yet unknown. The only safe prediction is that given the number of computers which are at risk that it will be years before this vulnerability is completely eradicated".
Photo Credit: Ollyy/Shutterstock
-

Private cloud deployments lead to better quality of enterprise IT
Publié: septembre 26, 2014, 11:47am CEST par Ian Barker

According to an IDG survey commissioned by information management specialist CommVault, private cloud adoption can lead to better IT services, greater agility and reduced risk for businesses.
In order to help companies make the most of these advantages CommVault is introducing a Private Cloud Services Design product that means customers can build a service-centric approach for data management supporting the private cloud in approximately six weeks.
"The benefits and barriers to private cloud adoption are causing organizations to seek strategic data management approaches that can maximize the value of their data and technology assets," says Robert Kaloustian, vice president, worldwide technical services at CommVault. "CommVault's new Private Cloud Services Design offering addresses cost, time and risk -- the Achilles’ heel of private cloud implementation -- to speed the transition to cloud infrastructure and help improve agility, business alignment and service level transparency".
The new design services combines best practices with the experience of CommVault's consultants to help enterprises ensure their cloud deployments are successful. It aims to work closely with IT and business management to make certain that cloud strategy chimes with business requirements.
You can find out more about Private Cloud Services Design on CommVault's website and see the results of the survey into the benefits of private cloud services in infographic form below.
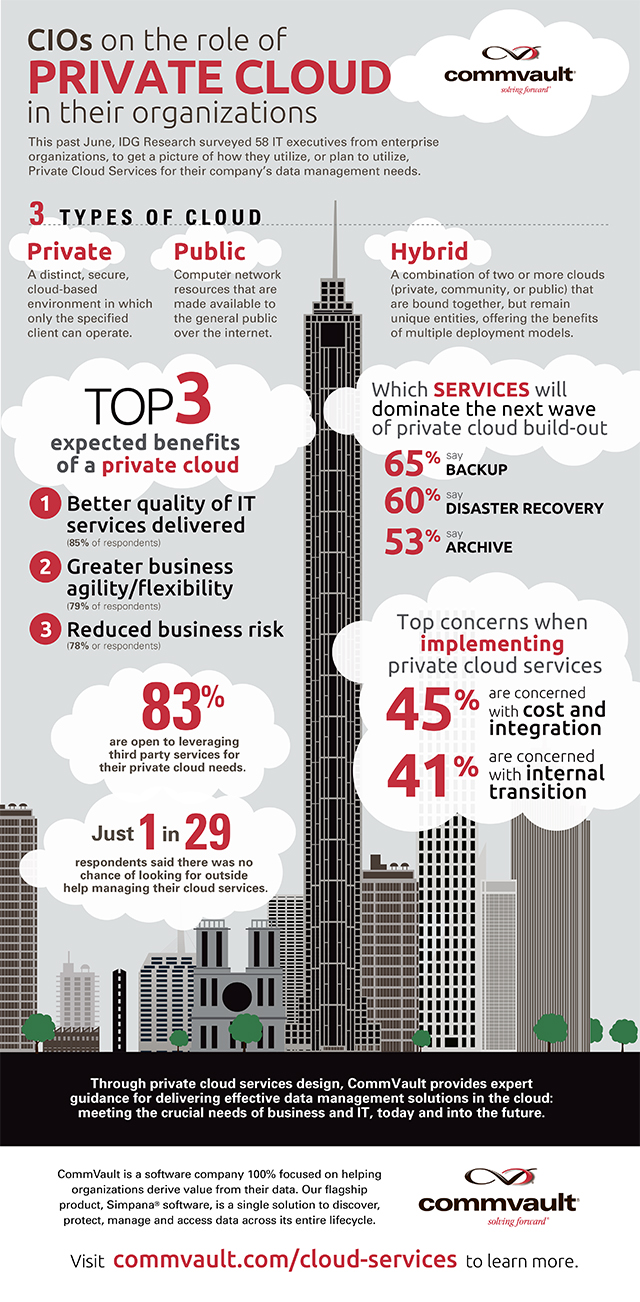
-

Shellshock Bash bug could be bigger than Heartbleed
Publié: septembre 25, 2014, 5:03pm CEST par Ian Barker

Although it seems that the Heartbleed bug wasn't exploited before its existence was disclosed, that doesn’t mean the security world can rest on its laurels.
The latest problem to be revealed is a bug in the commonly used Bash command interpreter that poses a critical risk to Linux and Unix systems. And since these form the backbone of the internet and are in many other systems as well it's a threat to the rest of us too.
The bug called Shellshock, discovered by Linux specialist Stephane Chazelas, is present in versions of Bash up to and including 4.3 and has potentially been there for many years. It poses a particular risk to Apache web servers. CGI scripts that use or invoke Bash are vulnerable to remote-code injection. This includes any child processes spawned by a script. OpenSSH and some DHCP clients are also affected on machines that use Bash.
Systems based on Debian -- including Ubuntu -- shouldn't be at risk since they use Dash. However, it's possible versions of Bash may be present so it's important that admins check which interpreters are installed and patch them if needed.
According to Darien Kindlund of security company FireEye, "It's worse than Heartbleed, in that it affects servers that help manage huge volumes of Internet traffic. Conservatively, the impact is anywhere from 20 to 50 percent of global servers supporting web pages".
A further problem is that Apple systems use Bash as the basis of their command line Terminal program. In addition Robert Graham of Errata Security warns that, "Internet-of-things devices like video cameras are especially vulnerable because a lot of their software is built from web-enabled bash scripts. Thus, not only are they less likely to be patched, they are more likely to expose the vulnerability to the outside world".
Graham also notes, "Unlike Heartbleed, which only affected a specific version of OpenSSL, this Bash bug has been around for a long, long time. That means there are lots of old devices on the network vulnerable to this bug. The number of systems needing to be patched, but which won't be, is much larger than Heartbleed".
Linux distros have responded quickly and patches are already available for most major flavors. Apple had yet to respond at the time of writing but advice on testing for and responding to Shellshock is available at StackExchange.
Security company Secunia has released an advisory saying that the patch issued by GNU -- the open source project behind Bash -- is ineffective but GNU is expected to "release another patch today due to the criticality of this vulnerability".
Security researchers Bromium Labs suggests that, "... this likely won't be the last vulnerability found in Bash. Application developers should try to avoid invoking shells unless absolutely necessary, or use minimalist shells where required".
Image Credit: Zhukov / Shutterstock
-

Adaptiva offers 5 Tips for a successful XP migration
Publié: septembre 25, 2014, 3:54pm CEST par Ian Barker
Windows XP is still in use in a surprisingly high number of businesses. A recent survey suggests that more than half of organizations are still running it somewhere.
The survey was conducted by systems management specialist Adaptiva among more than 100 TechEd North America attendees showed that 53 percent still had some XP systems.
Based on the company's experience in helping large enterprises migrate from XP using Microsoft’s System Center Configuration Manager (SCCM), Adaptiva has come up with five tips to ensure successful migration.
"It is very difficult for a large organization to move off of Windows XP completely, especially one with many operating locations around the globe," says Deepak Kumar, Founder and CTO of Adaptiva. "IT departments can begin taking steps now to ensure a smoother migration, whether moving from Windows XP or from Windows 7 to 8. Our 5 Tips come from successful enterprise migrations where they have reduced costs, slashed migration times, and improved success rates".
The tips for ensuring smooth migration are:
1 Optimize task sequences in order to plan for debugging and troubleshooting. Make use of logical phases -- called groups in task sequences -- so others can more easily monitor for success/failure, perform troubleshooting, and remediate. Plan ahead for debugging by saving log files to a network share, otherwise there will be no way to perform root cause analysis in the event of failure during the pre-OS phase.
2 Ensure the health of SCCM clients. The success of each migration depends on a healthy Windows system with a properly functioning SCCM client. Administrators need to be sure all the clients are problem-free in advance of migration to avoid delays.
3 Make friends with the network team and make them a part of the planning process. A good working relationship with the networking team will reduce political obstacles and accelerate troubleshooting.
4 Use hardlinking when possible to reduce reliance on network transfers during migration. Backing up a system’s user settings and data (state) on the system being migrated reduces the chance of the network becoming a bottleneck. This is much simpler with unencrypted hard drives, but can work on encrypted drives in some situations.
5 Set accurate user expectations. SCCM asset intelligence can ensure that users don’t lose capabilities. If the migration would cause a user to lose a personal or otherwise non-business-critical application, then it’s important to communicate that even though the change has no impact to the business. It is common to leave off some data, such as a user's "My Pictures" directory and it's important to let the user know early what won't be transferred.
To find out how add-ons like Adaptiva OneSite can further help to cut migration times and for more information on XP migration generally you can visit the company's website.
Photo credit: JNT Visual/Shutterstock
-

Flushed and crushed -- the most popular ways to damage your iPhone
Publié: septembre 24, 2014, 5:07pm CEST par Ian Barker

By virtue of the fact that we carry them around most of the time, mobile phones often get damaged and the iPhone is no exception. Insurance company Protect Your Bubble has analyzed its customer data to reveal the most common ways in which iPhones suffer problems.
Cracked screens are, as you might expect, the most common type of damage on 41 percent. Water damage accounts for 24.4 percent, though unfortunately no details are given on how this occurs or the exact nature of the liquids involved. We'd guess toilets are a factor in quite a few and Protect Your Bubble says it has had calls about phones damaged in Ice Bucket Challenge related incidents. It seems a high number of people manage to completely destroy their phone by smashing it into pieces too with nine percent admitting to running over their phone with a heavy object.
When asked how damage occurred 26 percent say they simply dropped the phone, 13 percent say their child damaged it and an intriguing nine percent are too embarrassed to say what caused the damage.
The company has also looked at the states that suffer the most damaged phones. Californians it seems are the clumsiest, accounting for 16.67 percent of damaged phones with New Yorkers, Floridans and Texans vying for second slot all on between 10 and 11 percent. New Jersey makes up the top five on 9.98 percent.
You can view the most common fates of Apple devices in infographic form below.
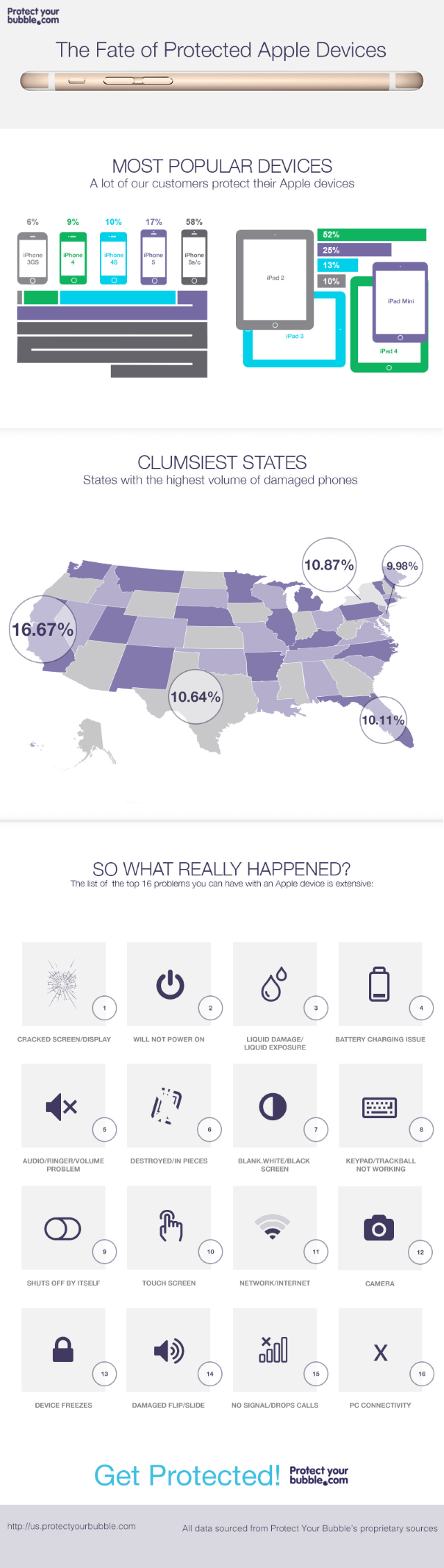
Photo Credit: Ammit Jack/Shutterstock
-

Selligy launches new mobile sales tools to boost productivity
Publié: septembre 24, 2014, 2:08pm CEST par Ian Barker

Key to the sales process is communicating with customers and often that means sales people being away from the office. Mobile technology means that there's no excuse for being out of touch though.
CRM specialist Selligy is launching a set of tools that allow sales professionals to manage their deals and update their sales forecasts quickly and accurately from their smartphones. IT uses information from the phone including location and calendar details to deliver relevant information when it's needed.
The latest update also includes the launch of Selligy Opportunity Manager. This is a tool that allows salespeople to quickly do their own 'what-if' analysis when setting and updating their sales goals. Using Opportunity Manager, salespeople can adjust all of their sales forecast numbers, preview the totals, make adjustments, see the new totals and then -- when ready -- record all the changes with a single save. Selligy estimates that with this feature, salespeople can perform forecasting tasks roughly 90 percent faster as performing the same task in traditional CRM systems may require navigating 30 to 40 pages of information.
"CRM was born in the 1990s, when the introduction of the laptop gave salespeople computing power on the road for the first time. In the past 20 years, CRM has not really changed," says Nilay Patel, Selligy's co-founder and chief executive. "Now, mobile is paving the way for a new breed of activity-based, mobile CRM applications that are upending traditional CRM. Just like the first wave of selling applications, these new applications are giving enterprises dramatically more visibility into their sales pipeline".
In addition to the new features this release sees Selligy become available for Android for the first time. You can find more information and request a free demo on the Selligy website.
Photo Credit: Kimberly Hall / Shutterstock
-

Small businesses lack the security knowledge to protect their mobiles
Publié: septembre 24, 2014, 12:14pm CEST par Ian Barker

Whilst smaller businesses are keeping pace with mobile adoption trends they don't always have the security knowledge needed to protect themselves.
This is among the findings of a survey by Kaspersky Lab which asked 3,900 IT professionals worldwide about the challenges encountered by their businesses over the last year.
The results show 34 percent of very small businesses (VSBs) adopting mobile technology in the past year, almost as many as enterprises at 35 percent. VSBs actually reported six percent more mobile integration than small businesses with 26 to 99 employees and two percent more than large businesses with between 1,500 and 5,000 employees.
Yet despite these adoption rates only 31 percent of VSBs listed securing mobile devices as one of their top three priorities for the next year. Plus only 28 percent thought that BYOD brought increased security risks to their business as compared to 52 percent of large businesses.
Evan Munno, Manager of North America Public Sector Sales at Kaspersky Lab says, "Is it possible that VSBs are overlooking employee-owned mobile devices as a security risk? This seems like a particularly troubling possibility, given that VSBs and their limited budgets are most likely to view employee-owned devices as a cost-savings measure and gladly welcome these devices onto their networks. Common threats from employee-owned mobile devices include malware or rogue applications connecting to the company’s network via the employee's device, or company data disappearing along with a lost or stolen employee device".
To achieve mobile security on a limited budget, Kaspersky recommends that employees need to be educated to develop a security mindset and that basic anti-theft technology be used so that data can be wiped from lost or stolen devices. It also suggests that small businesses should keep things simple to avoid implementing complex security systems.
The full report is available on Kaspersky's website as is more information about the company's Small Office Security product.
Photo Credits: Slavoljub Pantelic/Shutterstock
-

The global supply chain behind the iPhone 6
Publié: septembre 23, 2014, 4:26pm CEST par Ian Barker

We all know that the majority of our technology gadgets are produced in China, but the supply and manufacturing process isn't quite as simple as it might appear.
Apple more than most is a master at using the supply chain to its advantage, sourcing suppliers that can turn out parts in the most cost effective way whilst still adhering to the company's quality requirements.
The team at review website Comparecamp.com has been tracking Apple's supply chain to discover where it's made and how this affects the wider industry.
It estimates that an iPhone would cost $4 more if it was built in the US, but crucially for Apple it would also mean the company had to pay a lot more tax on its profits -- 35 percent as opposed to two percent. That's not to say the US isn't important to the business, however, with all of the design work still carried out there. Apple also supports over a quarter of a million US supply chain jobs.
In addition the findings reveal how Apple contracts have enabled its suppliers to invest in their own businesses. Foxconn, Apple's biggest supplier, for example has invested heavily in robotics to help it meet its production quotas.
Other emerging economies are getting in on the act too with iPhones now being assembled in Brazil. There are Apple suppliers in more than 30 countries around the world.
You can find out more with a full summary of Comparecamp's findings in infographic form below.

Brought to you by: [comparecamp.com] Author: Alex
Image Credit: Jozsef Bagota/Shutterstock
-

Clustrix releases specialist database for reliable ecommerce
Publié: septembre 23, 2014, 3:33pm CEST par Ian Barker

Performance is vitally important in ecommerce applications as customers won't wait around for a slow site to respond, they'll simply surf away and shop elsewhere.
This need for performance is as much about the back office systems handling inventory and orders as it is about the site itself. Cloud database specialist Clustrix is announcing the latest version of its ClustrixDB, purpose-built and optimized for fast growing ecommerce sites.
ClustrixDB aims to ensure zero downtime and latency along with continuous support for ecommerce transactions, with automated fault-tolerance even during hardware outages or upgrades to the database. It's flexible so it can cope with changes in capacity, customer numbers and the size of the product catalog.
The latest version is compatible with MySQL for easier reporting and offers performance enhancements for Magneto-based ecommerce setups. Distributed processing helps eliminate bottlenecks and ensures that the system can handle tens of thousands of users along with real-time catalog updates and live performance reporting.
Data is automatically rebalanced for maximum efficiency without harming the user experience. In addition it gets redistributed in the event that a single server goes offline in order to keep the system running.
"It's that time of year again -- the time when everyone starts speculating about how many sites will crash on Cyber Monday," says Mike Azevedo, CEO of Clustrix. "Many companies using MySQL are unprepared to handle website traffic spikes and don't realize they're at risk year round, not just during the holiday shopping season. Without a scale-out database to support peaks, your biggest sales day could become your last".
For more information on this latest release you can visit the Clustrix website.
Photo Credit: Nonnakrit/Shutterstock
-

Axway expands operational intelligence capabilities
Publié: septembre 23, 2014, 2:43pm CEST par Ian Barker

All sizes of organization increasingly expect their employees to deliver against measurable objectives and part of the key to achieving this lies in providing accurate data.
With the launch of its Decision Insight product, data flow specialist Axway aims to supply the numbers needed for productivity by offering insight and intelligence into real time and historical information.
Axway acquired Systar in June 2014 to combine its expertise in operational intelligence and real-time viewability into data flows with Axway's leading data governance solutions. The result is Axway Decision Insight, previously known as Systar Tornado.
"Without visibility into day-to-day operations, businesses cannot proactively manage operations and are exposed to greater risk," says Dean Hidalgo, executive vice president, global marketing at Axway. "With Axway Decision Insight, business users can take advantage of both real-time and historical data to proactively achieve operational objectives and support broader organisation-wide goals".
Key features include personalized information available via a single user interface which can be customised to the needs of each employee. A code-free platform means non-technical business users are able to configure and create applications to quickly respond to changes. In addition a rapid configuration process replaces typical lengthy redesign and redevelopment cycles, letting business users configure new versions of dashboards in hours. Time-based analytics allow businesses to uncover warning signs based on past data patterns.
The software can be accessed via a web browser making for fast installation with no need for specialist client applications and allowing businesses to be up and running quickly.
Axway decision Insight is available from today and you can find more information on the company's website.
Photo Credit: Adchariyaphoto/Shutterstock
-

Social media becomes a critical marketing channel for holiday sales
Publié: septembre 23, 2014, 11:50am CEST par Ian Barker

Driving sales and increasing the reach of their brand is seen as key to the marketing success of companies, and many are turning to social media to pursue their strategy.
New survey data from marketing software platform Offerpop shows that brands are increasing their investment in social media and focusing on using it to drive sales in the run up to the holiday season.
In contrast to the days when social media strategy was all about getting more fans, companies now see it as a serious part of their sales effort. Compared to last year, 67 percent of companies plan to spend more on social media in the 2014 holiday season. Facebook is the main beneficiary here, with 92 percent of respondents saying that they plan to spend the majority of their marketing budget on the platform.
As far as future trends go, 73 percent of marketers polled identified Instagram as the breakout social network of 2014 for brands, with Vine and Snapchat making up the remaining 27 percent. There's still wariness about untried networks though, with 48 percent having no plans to invest on emerging platforms like Snapchat.
"Offerpop's survey data shows that social marketing is maturing rapidly, with a new focus on driving commerce and increasing investment in proven revenue channels like Facebook", says Kevin Bobowski, vice president of marketing for Offerpop. "This holiday season, we'll see marketers testing Facebook and Twitter's new commerce capabilities and leveraging Instagram for holiday campaigns".
The full report is available for subscribers to Offerpop's free Holiday Marketing 365 content program. There's a summary of the findings in infographic form below.
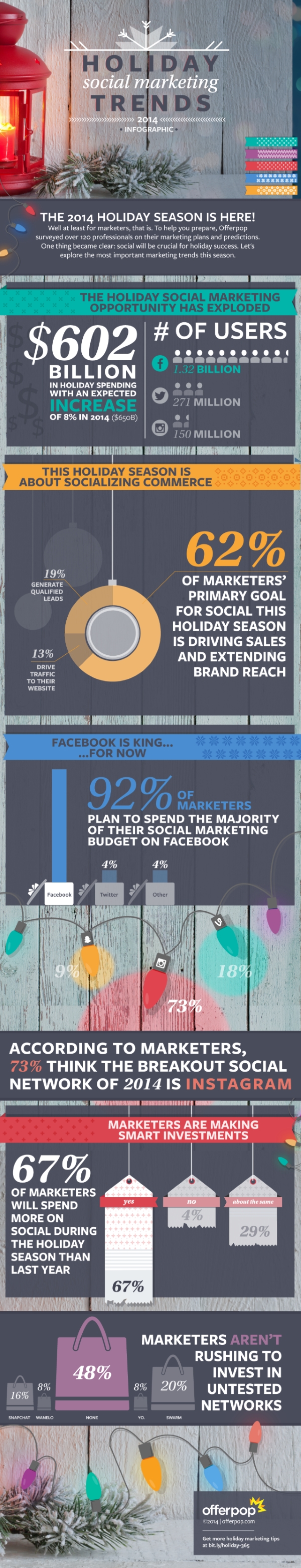
Image Credit: Sarawut Aiemsinsuk / Shutterstock
-

Intelligent sales productivity platform from Base adds new features
Publié: septembre 22, 2014, 4:37pm CEST par Ian Barker

Many businesses rely on CRM tools to store sales data, but the increased use of mobile devices has led to new demands for information to be available anywhere at any time.
Now Base which describes itself as an intelligent sales productivity platform, has added a range of new features to boost team productivity and make data available in real time.
"Base picks up where other CRMs have left off," says Uzi Shmilovici, CEO of Base. "Until now, legacy cloud Sales and CRM products like Salesforce have been accepted as 'the norm' by the enterprise market. However, recent advancements in big data, mobility and real-time computing reveal a need for a new generation of intelligent sales software that offers flexibility, visibility, and real-time functionality. If you're using outdated technology that cannot adapt to the advanced needs of modern day sales teams, your competition will crush you".
Base is designed for sales staff to use whether they're operating from their desktops, mobile devices or tablets. Its embedded communication tools automatically aggregate email, phone calls and appointments into a single contextual view that gives the user an immediate overview of all conversations, updates and history. Base therefore eliminates the tedious task of manually entering data into a CRM system as it captures relevant details automatically. This allows sales staff to concentrate on closing deals.
New features include real-time notifications allowing action to be taken at the appropriate time, scheduling of meetings and tracking of past meeting with clients. It also offers managers a rep performance dashboard that brings together staff performance indicators in one view.
In addition it uses stage duration analysis to measure how fast deals move through the pipeline and by employing sophisticated analysis can predict the likelihood of winning a deal based on its state of progress.
You can find out more about the product and sign up for a free trial on the Base website.
Photo Credit: Kimberly Hall / Shutterstock
-

Mobile security budgets aren't keeping pace with demand for devices
Publié: septembre 22, 2014, 3:39pm CEST par Ian Barker

Although mobile devices are becoming essential in many workplaces security budgets are failing to reflect the growing numbers of devices that need protection.
This is among the findings of a new report by electronics and systems specialist Raytheon. According to the research around one-third of employees use mobile devices exclusively to do their work and this is expected to increase to an average of 47 percent of employees in the next year.
Despite this anticipated growth, 64 percent of those surveyed claim they don't currently or expect to have sufficient budget to mitigate or curtail mobile device cyber security threats. A majority of respondents, 52 percent, say that security practices on mobile devices have been sacrificed in order to improve employee productivity. In addition 60 percent believe employees have become less diligent in practicing good mobile security.
Of the 618 IT and IT security professionals surveyed 75 percent say it's important to secure employees' mobile devices but only 50 percent are happy with their current solution. A virtualized approach is popular with 57 percent of respondents. The methods most often used are mobile device management and secure containers.
"This survey points to the fact that there is a struggle to find the right balance between the cyber security needs of an organization and the efficiencies demanded by employees to do their jobs," says Ashok Sankar, senior director of product management and strategy at Raytheon Cyber Products. "Mobile devices are becoming a dominant workplace tool, and organizations must adopt a mobile strategy with data security technologies that enable employees to work effectively without putting sensitive information at risk".
Despite the risks, allowing BYOD is seen as important for productivity. 48 percent of respondents say the biggest incentive for BYOD is ensuring employees are always connected. Interestingly 67 percent prefer to use a web-based approach to delivering services on mobile rather than develop native apps.
The full report is available via the Raytheon website and you can view a summary of the findings in infographic form below.
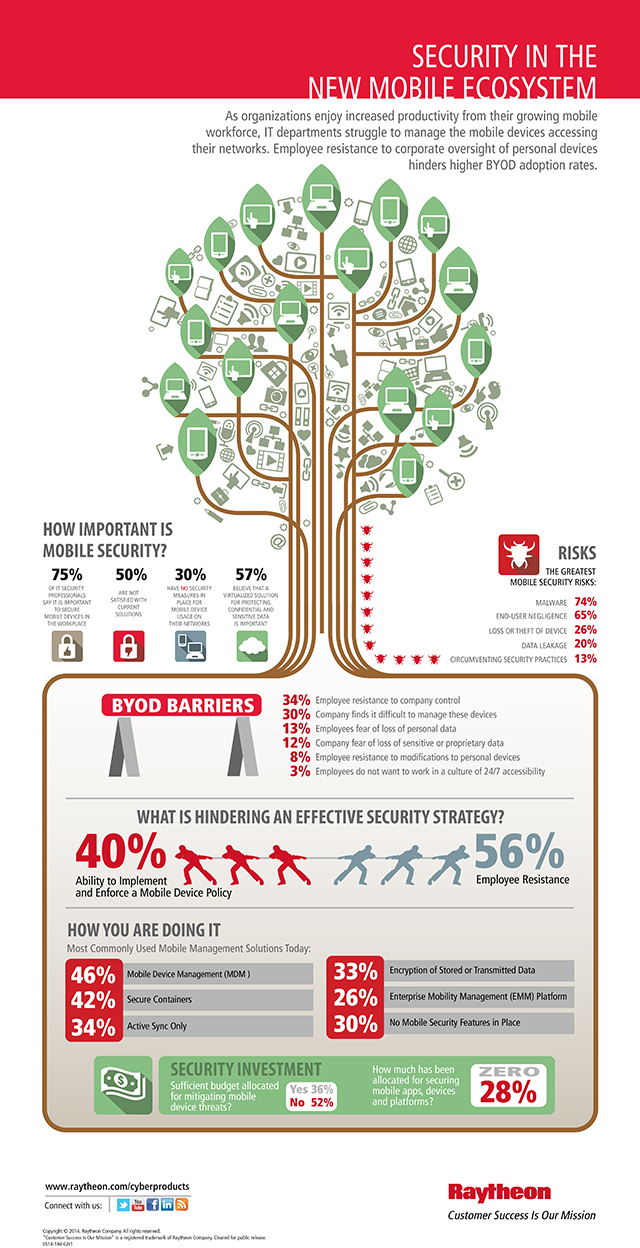
Image Credit: Anan Chincho / Shutterstock
-

How to keep yourself safe from hacking [Q&A]
Publié: septembre 22, 2014, 11:46am CEST par Ian Barker

As we all carry out more of our day-to-day transactions online and access the internet through a wider range of devices, we're opening ourselves up to greater potential risk.
Add in the constant battle of security providers to stay ahead of hackers and malware writers and it's easy to doubt if you can ever stay truly safe online. Joe Siegrist CEO of password management specialist LastPass thinks that although it's not 100 percent possible to hack-proof yourself, you can significantly reduce your risk, we spoke to him to find out how.
BN: What do you think is the greatest threat facing people online?
JS: The greatest online threat to consumers is identity theft and exposure of sensitive data caused by password reuse, as well as unnecessary data collection. You would never use the same key for all your locks, so why do consumers use the same password for all of their online logins?
BN: Do we rely too heavily on security products to protect ourselves and, perhaps, suspend our common sense as a result?
JS: At times, yes. The security of most companies relies heavily on knowing what your high school mascot is. That isn't security at all. Not practising client side encryption and giving companies the keys to encrypt your data places all trust in these companies to do the right thing -- which, unfortunately, they don't usually do. LastPass doesn't have your encryption key -- we have a zero-knowledge approach to our product.
BN: We all have to remember lots of passwords for our everyday lives. Isn’t it reasonable to reuse the same one for less important sites?
JS: No! Invariably you will use it on sites that expose large amounts of data about you. For example, sites like Amazon or Yahoo would expose your name, address, credit card, etc to the company. Using a tiered approach to password management and using easy passwords will always fail and expose your data. Studies have proven that our human-generated password "tricks" and "systems" are not nearly strong enough.
BN: What should you check before handing over your payment details to a website?
JS: Make sure this is a company you've heard of before and have dealt with in the real world. And make sure the URL is an 'https://' secured connection.
BN: Does using mobile devices like smartphones and tablets to access the web present greater levels of risk and what can you do to guard against it?
JS: It's actually quite the opposite. Phones are more likely to be locked down in sand-boxed environments.
BN: What would you say to a complete newcomer starting to use the internet for the first time?
JS: Make sure you start with well known, reputable sites. Don't download anything you're unsure of. Keep your browser and anti-spyware program up to date. Learn about the various scams and ways people can trick you into giving away your passwords like running security scans that install malware. Until you understand fully how people can take advantage of your online data, stay on the beaten path and use a password manager. Passwords you don't know can't be phished.
BN: Are we kidding ourselves if we think we can ever be truly secure online?
JS: Without client-side encryption, we can never be sure if we're secure online. If there are ways for companies to access your data, you can never be sure that they aren't revealing it to someone else.
Image Credit: Gunnar Pippel/Shutterstock
-

Virtual reality is coming to the workplace and it may be sooner than you think
Publié: septembre 22, 2014, 10:45am CEST par Ian Barker

Not so very long ago virtual reality was the stuff of science fiction but it's increasingly emerging into the real world.
A new infographic produced by collaboration specialist PGi explores the current state of virtual reality and the possibility that it will soon be appearing in the world of work.
Key findings include that the virtual reality market is expected to grow into a $407 million industry with around 25 million users by 2018. Many of the major tech companies including Facebook, Apple and Google are investing billions of dollars into developing and releasing virtual communications, virtual reality and augmented reality. For example Facebook recently acquired Oculus VR for $2 billion.
Virtual reality has the ability to improve the workplace by providing the possibility of upgraded training techniques with fewer distractions and enhanced efficiency through virtualization of data. Technologies like 3D displays will allow for more immersive business collaboration, letting companies create virtual 3D conference rooms.
You can see more detail in the infographic below or on PGi's blog.
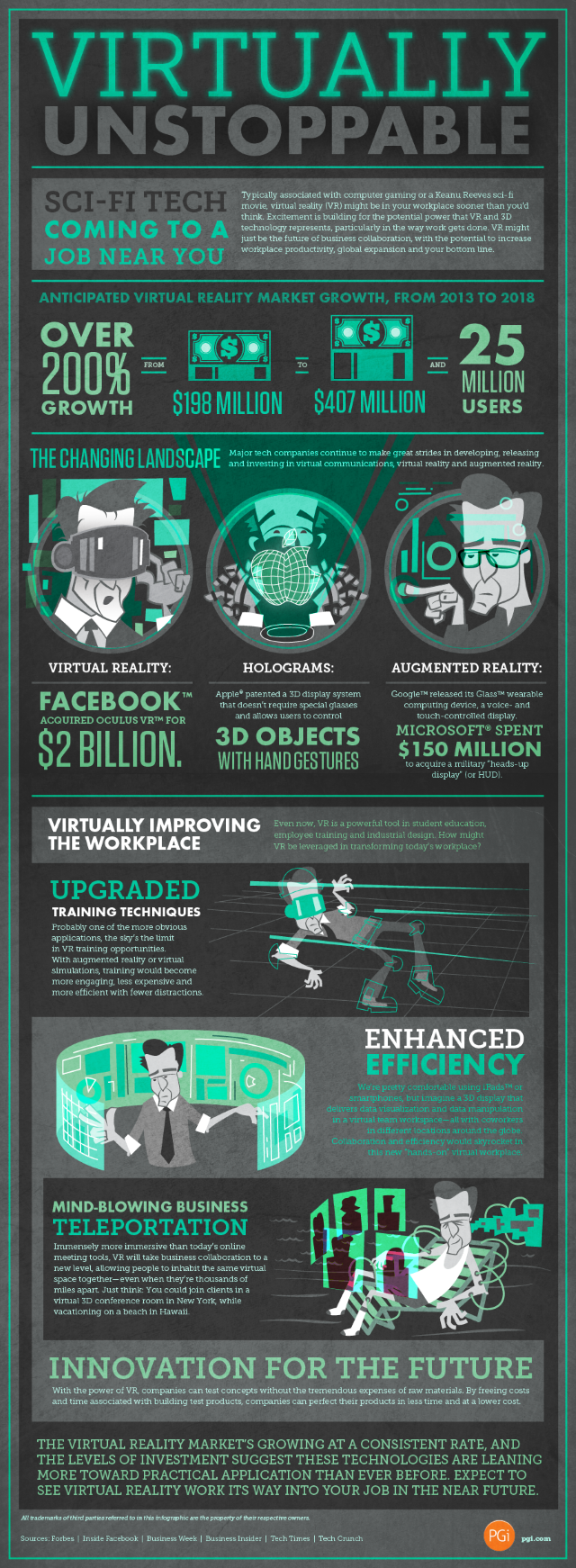
Image Credit: Nejron Photo / Shutterstock
-

The best CRM software as selected by business professionals
Publié: septembre 18, 2014, 3:08pm CEST par Ian Barker

By allowing companies to track and manage customer interactions, CRM (customer relationship management) systems are key to the success of sales and marketing teams. There are a lot of alternative systems to choose from though which can present a problem when it comes to picking the best option for the needs of a particular enterprise.
In order to help with this business software user review site G2 Crowd has produced its regular Grid report ranking 27 different CRM systems.
The report is based on more than 1,700 reviews and ratings from business professionals, including 500 new reviews since the last report in January. The Grid, G2 Crowd's software recommendation engine, factors in customer satisfaction as reported by users and vendor market presence determined from social and public data to rank products.
The top products are rated as Leaders or High Performers. To qualify as a Leader, a product must receive a high customer satisfaction score and have substantial market presence. Salesforce and Microsoft Dynamics CRM were named Leaders, with 13 additional vendors named High Performers.
Of the High Performers Nimble and Workbooks.com were tied with the highest customer satisfaction scores. Across all products reviewers reported the CRM software they use meets their requirements at an average rate of 82 percent, and on average reviewers said they were 81 percent likely to recommend their product.
The Grid is reproduced below and you can find out more, access the full report and read individual reviews of each product on the G2 Crowd site.
![CRM-Grid-Fall-2014[1][1][1]](http://betanews.com/wp-content/uploads/2014/09/CRM-Grid-Fall-2014111-600x549.png)
Photo Credit: Mikko Lemola / Shutterstock
-

What makes Apple such a success? -- Free ebook
Publié: septembre 18, 2014, 11:31am CEST par Ian Barker

Love it or hate it, you can't deny that Apple is a phenomenally successful company. But how has it managed to achieve this from a business that started in a garage?
Mostly it hasn’t been by innovation but by taking technology that already existed and turning it into the devices that people want to buy. Apple, more than any other company, has succeeded in making technology cool and desirable.
From the earliest Apple I to the latest iPhones and iPads, Apple has made gadgets accessible, even to people who don't really care about the underlying technology.
If you want to read more about how it did this and take a look at the milestone products that have made Apple the company it is today you can download my book, Game Changers: Apple's Breakthrough Moments free from the Kindle store today as part of a promotion for International Read an eBook Day.
If you’re shopping from the UK use this link.
-

Datastickies and the rebirth of the cassette -- the future of data storage
Publié: septembre 17, 2014, 3:44pm CEST par Ian Barker
Remember when floppy disks really were floppy? Or the joys of loading programs on a home computer from a C15 cassette? In just over 40 years storage technology has gone from these crude devices to cloud servers that put terrabytes of space in reach of anyone.
But where does the future lie? Hardware supplier Ebuyer has produced an infographic looking at the direction storage may take in the future.
Highlights include "Datastickies", a flash drive alternative that stores information on a thin sheet like a Post-it note that can be read by sticking it to a monitor equipped with a special surface. The sheets are made of Graphene, a revolutionary material that's made up of carbon atoms in a honeycomb lattice.
Other techniques to pack more data into smaller devices include sealing helium gas inside drives. This reduces friction and produces a drive that runs cooler and faster as well as using less power. Shingled Magnetic Recording (SMR) writes disk tracks closer together and overlaps them allowing more data in the same space. Seagate claims this could result in a 20TB drive by 2020.
Further down the track are technologies like liquid state storage where the metal inside a drive is kept in liquid form. There's also heat-assisted magnetic recording (HAMR) where a laser heats the disk to change its magnetic state, allowing more data to be stored per square inch.
Holographic storage is another technology with potential for the future, storing data in three dimensions using the full depth of the medium. Storing data in DNA is another possibility and has the potential to ensure information lasts forever.
And finally let's not forget our old friend the cassette. Sony has developed a new technology that can store 148GB per square inch of tape, potentially allowing a single cassette to store 185TB of data.
You can see more details of where storage has come from and where it's headed in the infographic below.
Image Credit: kavee29 / Shutterstock
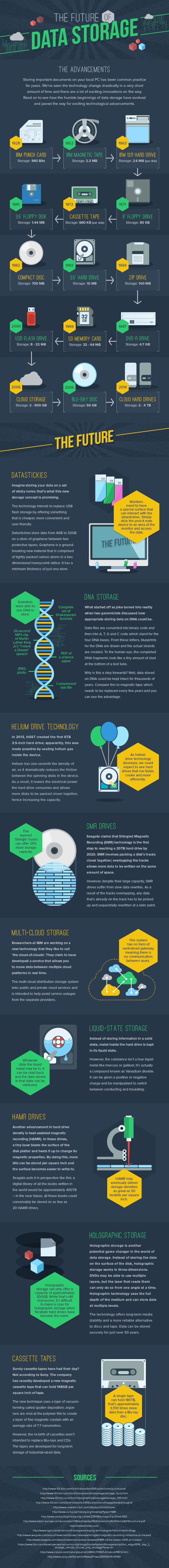
-

Selligy launches new mobile sales tools to boost productivity
Publié: septembre 17, 2014, 2:53pm CEST par Ian Barker

Key to the sales process is communicating with customers and often that means sales people being away from the office. Mobile technology means that today there's no excuse for being out of touch with the data they need though.
CRM specialist Selligy is launching a set of tools that allow sales professionals to manage their deals and update their sales forecasts quickly and accurately from their smartphones. IT uses information from the phone including location and calendar details to deliver relevant information when it’s needed.
The latest update also includes the launch of Selligy Opportunity Manager. This is a tool that allows salespeople to quickly do their own "what-if" analysis when setting and updating their sales goals. Using Opportunity Manager, salespeople can adjust all of their sales forecast numbers, preview the totals, make adjustments, see the new totals and then -- when they're ready -- record all the changes with a single save. Selligy estimates that with this feature, salespeople can perform forecasting tasks roughly 90 percent faster as performing the same task in traditional CRM systems may require navigating 30 to 40 pages of information.
"CRM was born in the 1990s, when the introduction of the laptop gave salespeople
computing power on the road for the first time. In the past 20 years, CRM has not really changed," says Nilay Patel, Selligy’s co-founder and chief executive. "Now, mobile is paving the way for a new breed of activity-based, mobile CRM applications that are upending traditional CRM. Just like the first wave of selling applications, these new applications are giving enterprises dramatically more visibility into their sales pipeline".In addition to the new features this release sees Selligy become available for Android for the first time. You can find more information and request a free demo on the Selligy website.
Image Credit: EDHAR / Shutterstock
-

Internet users say they want privacy but behave like they don't
Publié: septembre 17, 2014, 12:27pm CEST par Ian Barker

We all say that we want privacy and security online, yet we indulge in potentially risky behaviors that put this in jeopardy according to a recent study commissioned by Trend Micro and released to coincide with the launch of its Internet Security 2015 product.
Activity like browsing suspect websites and allowing apps to access public information from their social media profiles puts people’s privacy at risk. Also 67 percent of people let their browser save passwords for websites. Trend Micro says saving passwords leaves them susceptible to being hacked, especially in light of recent retail security breaches.
Further findings are that 40 percent of mobile users don’t use a password to protect their devices, 28 percent of respondents allow mobile apps to access their social media profiles and 10 percent of mobile users believe they have downloaded a malicious app to their device.
The survey also finds that people continue to indulge in online behaviors that increase the risk of damaged reputation or identity theft. Some 74 percent of Internet users indicate they are concerned about sharing personal data via social media. 60 percent of social network users have removed a post from social media for fear of consequences in their personal life. 40 percent say they share the results of their game playing on social networks and 11 percent are "friends" with their boss online.
"Trend Micro Security 2015 provides protection against threats and privacy concerns regardless of the device or operating system," says Akihiko Omikawa, general manager of global consumer business at Trend Micro. "The solution protects users' personal information from being compromised by cyber criminals while maintaining privacy and protection of online activity. A simple step to protecting our digital lives begins with being mindful of the hazards to privacy and personal data the Internet presents. Each of us is a potential target for cyber criminals, but Trend Micro Security 2015 protects individuals anytime, anywhere, on any device, acting as a great deterrent".
To help combat risky behaviors the new product includes a secure password manager to save online passwords in an encrypted form. It also has a social network Privacy Scanner to scan LinkedIn, as well as Facebook, Twitter and Google+. This gives users technology to help them maintain privacy, security and positive online reputations.
"Managing privacy and security in this connected world is something that is often overlooked as we walk through life with our smartphones and laptops. To ease the concerns of Internet users regarding privacy and oversharing, Trend Micro Security 2015 enables users to maintain online privacy from strangers and cyber criminals while protecting their data," says Omikawa.
You can find more about Trend Micro Internet Security 2015 and download a free trial from the company's website.
Image Credit: iQoncept/Shutterstock
-

PagerDuty delivers advanced reporting and visualization
Publié: septembre 16, 2014, 6:08pm CEST par Ian Barker

Monitoring of IT systems is only effective if you're able to interpret the data you collect and act on it in a timely manner. This is especially true when it comes to resolving incidents.
Operations performance management company PagerDuty is launching new advanced analytics tools to provide IT teams with insights into team and system performance. Using operational metrics like incident frequency and time taken to respond and resolve, companies can now drive even faster incident resolution. At the same time it gives managers the opportunity to understand and improve the key factors that drive uptime.
"Responders make real-time decisions throughout the lifecycle of an incident, but little of that institutional knowledge is saved to make systematic improvements. Advanced Analytics gives responders and managers the tools they need to identify, analyze and share trends about their resolution times and incident load," says PagerDuty Product Manager David Shackelford. "After gathering feedback from many top-performing Operations teams, we designed a set of highly flexible dashboards to expose these insights. Since technical reliability and scalability are incredibly important for us, we invested heavily in the infrastructure for Advanced Analytics, building a fully decoupled service that’s fast, highly reliable, and doesn't put our existing application at risk. We're excited to help our customers make smarter, data-backed decisions about their operations".
Advanced Analytics allows companies to see trends and peaks in response and resolution times, compare incident trends by team and monitoring service and drill down to individual incidents to see what drives spikes.
It achieves this with a service-oriented architecture that offers reliable reporting, separates analytics load from production load, and supports future reporting enhancements. Metrics can be stored to allow efficient queries and are continually recalculated to take account of production changes. All of which saves time spent on manual analysis.
You can find more information and sign up to try PagerDuty for free on the company's website.
Image Credit: Nata-Lia / Shutterstock
-

New Dell partnership strengthens enterprise risk management
Publié: septembre 16, 2014, 5:32pm CEST par Ian Barker

In the event of a major problem, whether it's a cyber attack, political unrest or a natural disaster, getting critical information to the right people in a timely manner is crucial.
To address this, Dell Software has formed a partnership with enterprise risk visualization software company, IDV Solutions to integrate Dell's AlertFind enterprise notification solution with IDV's Visual Command Center. The combined product will give companies the ability to monitor and respond to security threats by enabling communication with affected employees when a risk occurs (via email, text, voice, pager or fax) and track real-time status of message recipients to know who has responded and who may require assistance.
The IDV Visual Command Center offers businesses a single, integrated picture of their asset locations and risk events that may threaten them. This information is combined with things like floor plans, security systems and details of internal procedures to provide a single resource when disaster strikes.
Dell's AlertFind is a cloud-based service that provides communication with employees in the event of an emergency. It's scalable to meet the needs of large organizations and can deliver communication via a variety of routes with the ability to track responses. Features include automated escalation, text to speech conversion and conference call bridging.
Jonathan Wolf, director, product management at Dell Software says, "Dell is committed to helping organizations maintain business continuity during emergencies, even when communications infrastructure may be impacted. Integration with a risk monitoring platform is a natural extension of the value Dell AlertFind brings to the entire risk management process. We’re excited about the Dell AlertFind and IDV Solutions Visual Command Center integration. Not only do we use this integrated solution internally at Dell, but many of our customers -- particularly Global 500 organizations -- use or are evaluating Visual Command Center".
You can download a PDF with more details of the integrated solution from the Dell website.
-

PaaSLane 2.5 release adds new capabilities for cloud developers
Publié: septembre 16, 2014, 5:17pm CEST par Ian Barker

The PaaSLane tool for assessing the cloud-readiness of applications has been available for two years and has helped many organizations transition their software smoothly. It's able to detect outdated architecture, weak security, platform issues and more.
Now Cloud Technology Partners has brought out a new release to allow Java and .Net developers to assess and optimize their source code for the cloud more quickly and efficiently.
PaaSLane 2.5 adds security by profiling locally with no need to upload source code to the cloud. It adds support for the Google cloud platform including the App Engine and Compute Engine. There’s enhanced .Net profiling too with more than 50 new rules for modernizing applications.
Rule management is improved overall too with easier to manage custom rule sets and report templates. The new version also includes over 100 new rules for modernization and cloud readiness across multiple categories.
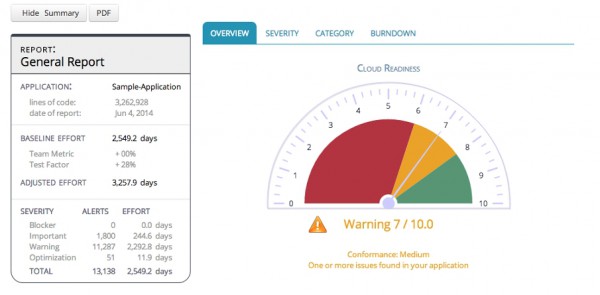
The software can target specific platforms such as Amazon Web Services (AWS) or Google, and produce enhanced recommendations specifically for that platform. This allows it to be used as a "what if" tool to help decide which platform is the best fit for enterprises planning a new cloud strategy.
"Developing modern cloud applications without PaaSLane is complex and error-prone," says Ben Grubin, Director of Product Management for PaaSLane. "With PaaSLane, application developers and engineering leaders get deep visibility into the architectural improvements that are necessary before ever starting a project, as well as guidance on exactly how and why to make specific code changes. Having PaaSLane in your software development process means avoiding the pain of outdated, expensive to maintain, and inflexible applications in the future".
Two versions are available, PaaSLane Assess, which offers a one-time application assessment, and PaaSLane Optimize, an annual subscription service designed to integrate with software development life cycles.
The latest PaaSLane is available now, with prices starting at $500 per application. You can also request a free trial account via the company's website.
Photo Credit: everything possible / Shutterstock
-

Cisco adds threat focus to its firewall platform
Publié: septembre 16, 2014, 2:50pm CEST par Ian Barker

The firewall is usually the first line of defense for any network, but most offerings are focused on access policy and application control which makes it hard for them to respond to zero-day and more advanced attacks.
Now networking company Cisco is launching what it calls the first threat-focused Next-Generation Firewall (NGFW). Cisco ASA with FirePOWER Services provides the contextual awareness and dynamic controls needed to automatically assess threats, correlate intelligence, and optimize defenses in order to protect networks.
The new product integrates the proven Cisco ASA 5500 series firewall with application control, and the industry-leading Next-Generation Intrusion Prevention Systems (NGIPS) along with Advanced Malware Protection (AMP) from Sourcefire.
It offers greater visibility thanks to enterprise-class management which provides users with dashboards and reports into which they can drill down for details of discovered hosts, applications, threats, and indicators of compromise.
Protection against known and unknown threats is offered thanks to big data analytics, continuous analysis and Cisco Collective Security Intelligence (CSI) working together to provide detection, blocking, tracking, analysis, and remediation.
Being platform based it can combine firewall and application control with intrusion prevention and breach detection on a single device. This means it simplifies an organization's security architecture and reduces its network footprint with fewer security devices to manage and deploy and needing no extra license subscriptions to extend functionality.
"In today's climate of industrialized hacking and sophisticated cybercrime gangs, we've entered an era in which legacy NGFW solutions are not enough to thwart attackers," says Christopher Young, senior vice president, security business group at Cisco. "Now more than ever, organizations need to be able to implement dynamic controls to manage the pace of change of their environments and address security incidents. Cisco ASA with FirePOWER Services is a major step forward for the NGFW market, empowering customers to deepen their protection from the data center, through the network, to the endpoint with the agility to identify, understand, and stop advanced threats in real-time and retrospectively."
New Cisco ASA units can be bought with a bundled FirePOWER license or existing customers can add FirePOWER to their current ASA 5500-X and 5585-X series firewalls. More information is available on the Cisco site.
-

Riak Enterprise 2.0 enhances NoSQL database usability
Publié: septembre 16, 2014, 11:01am CEST par Ian Barker

For organizations that deal with large quantities of data, the NoSQL database is a popular choice. However, it can present problems for traditional database programmers.
For this reason developers are always on the look out for ways to build applications more easily and unlock the potential of unstructured data. With the release of its latest Riak Enterprise 2.0, NoSQL specialist Basho is addressing these needs.
The new version improves performance with a complete redesign of Riak Search, integrated with Apache Solr. The release also includes support for new distributed data types, enhanced configuration management and user security to enable faster development and simplified configuration. This new NoSQL database functionality provides enterprise application developers with enhanced usability and scalability for faster development of highly available, globally scalable applications.
"Our goal is to provide the most advanced NoSQL database system available that is innovative and constantly evolving," says Dave McCrory, CTO of Basho. "Riak is the only data platform supporting key value store, object storage and search. Riak 2.0 solves the usability issues that have slowed NoSQL developers for years. We have tightly integrated Solr, the popular high performance full text search platform and developed new data types that automatically address conflicts".
Among the new features in Riak Enterprise 2.0 are support for additional data types, plus updated searching enabling better integration with other software through client query APIs. Security is improved too with authorization and authentication now available to manage users and groups.
Configuration management is also simplified with information stored in an easy to parse transparent format. Tiered storage is available too so files can be optimized for low latency of the most accessed data.
Riak Enterprise 2.0 is available now, the technical documentation can be accessed on the Basho website and you can also request a trial license.
Image Credit: wavebreakmedia / Shutterstock
-

IT professionals not confident they can prevent cyber attacks
Publié: septembre 15, 2014, 5:35pm CEST par Ian Barker

Despite the number of high profile attacks in recent months, many organizations are still lacking confidence in their ability to prevent a cyber attack or data breach.
These are the findings of a new survey from risk consultancy firm Protiviti which also shows that companies aren't properly preparing for crises and often don’t have adequate core data policies.
"Our survey results tell a story of gaps between where companies currently stand and where they should be in relation to fundamental elements of IT security. Some progress has been made since our last survey, yet many organizations still fall short of important standard protocols for IT security and privacy," says Ryan Rubin, managing director with Protiviti and UK leader of the firm's IT security and privacy practice. "Companies need to take more action in relation to the risks they recognize to better protect their crucial data".
The survey uncovers five main themes which indicate that companies need to improve their data policies. First is a lack of confidence in their ability to prevent attacks. Despite executive management having a higher awareness of the possibility of attack, the creativity of attackers leads to lower confidence among IT staff.
Secondly companies are not preparing for crises. The survey finds a year-on-year jump in the number of organizations without a formal and documented crisis response plan to execute in the event of a data breach or cyber attack.
Third, board-level engagement leads to better preparation. Organizations whose boards are concerned with how the organization is addressing its risks, have significantly stronger IT security profiles. However, the survey finds that one in five boards have low engagement.
Lack of policy is the fourth key theme. One in three companies doesn't have a written information security policy and over 40 percent lack a data encryption policy. One in four don't have acceptable use or record retention/destruction policies. These represent critical gaps in data governance and management, and they can carry major legal implications.
The final theme is inequality of data. The percentage of organizations that retain all data and records has more than doubled but this isn't necessarily a positive development. The report finds a relatively large number of organizations which don't prioritize data that is processed and governed in a specific way. Even fewer companies appear to prioritize data that is highly regulated such as payment and healthcare-related information.
There are some positive findings, principally that enterprises are becoming more aware of their data lifecycle -- how and where data is stored. Also CIOs are more likely to take primary responsibility for security than in recent years.
The full report is available on the Protiviti website and the results will be discussed in a webinar on September 30th. You'll also find a summary of the findings in infographic form below.
Photo Credit: Alexander Kirch/Shutterstock
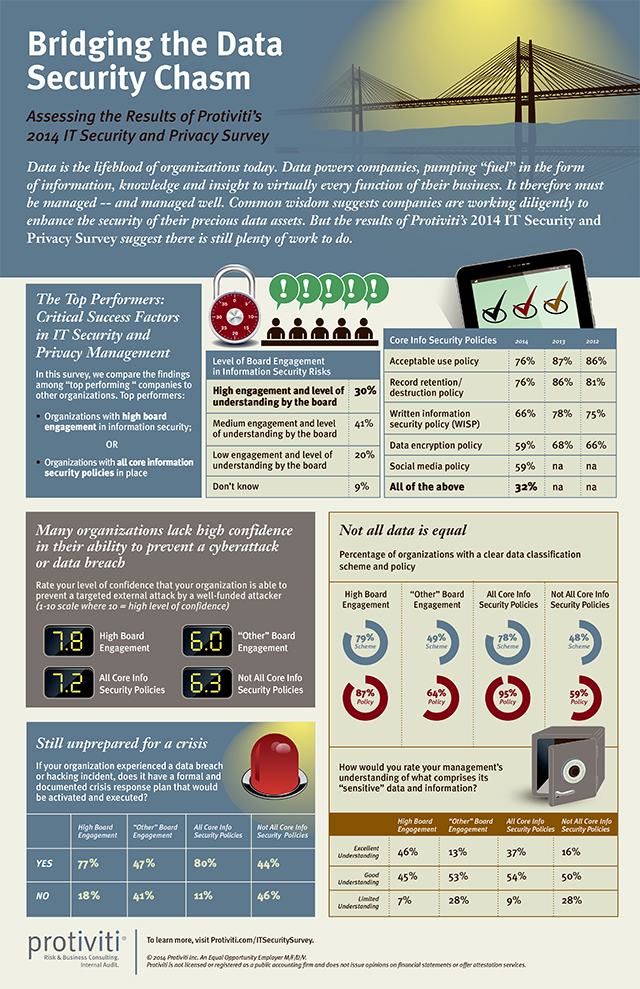
-

Over three-quarters of mobile apps will fail security tests by 2015
Publié: septembre 15, 2014, 1:56pm CEST par Ian Barker

New research by analysts at Gartner shows that more than 75 percent of mobile apps are set to fail basic security tests by 2015.
This is a particular worry for enterprises as employees may download software from app stores. These apps offer minimal or no security assurances but are able to access sensitive business data and violate company security policy.
"Enterprises that embrace mobile computing and bring your own device (BYOD) strategies are vulnerable to security breaches unless they adopt methods and technologies for mobile application security testing and risk assurance," says Dionisio Zumerle, principal research analyst at Gartner. "Most enterprises are inexperienced in mobile application security. Even when application security testing is undertaken, it is often done casually by developers who are mostly concerned with the functionality of applications, not their security".
Existing security vendors will need to modify their approach and their products in order to adapt to these new threats. As well as testing the client layer -- the app on the mobile itself -- there's also a need to look at the server layer. Code and user interfaces of server side applications need to be tested to ensure that data isn't leaked.
"Today, more than 90 percent of enterprises use third-party commercial applications for their mobile BYOD strategies, and this is where current major application security testing efforts should be applied," says Zumerle. "App stores are filled with applications that mostly prove their advertised usefulness. Nevertheless, enterprises and individuals should not use them without paying attention to their security. They should download and use only those applications that have successfully passed security tests conducted by specialized application security testing vendors".
Looking further ahead to 2017, Gartner predicts that the focus of security breaches will have shifted to tablets and smartphones. Already it says there are three attacks on mobile devices for every one on a desktop.
It also expects that by 2017 misconfiguration of apps rather than actual attacks will account for 75 percent of mobile breaches. Gartner recommends that enterprises focus on data protection on mobile devices by employing usable and efficient solutions like application containment.
The outlook for mobile security will be discussed at a Gartner Security & Risk Management Summit taking place September 15-16 in Dubai.
Photo Credit: lucadp/Shutterstock
-

Companies shouldn't 'over think' internet of things security
Publié: septembre 12, 2014, 3:36pm CEST par Ian Barker

The internet of things opens up a vast range of new opportunities for individuals and businesses. But as we saw yesterday with expert predictions on the impact of the Apple Watch it also brings additional risks.
Analysts at Gartner are predicting that by 2017 more than 20 percent of businesses will have security devices aimed at protecting services and devices in the internet of things.
"The power of an Internet of Things device to change the state of environments and of itself will cause chief information security officers (CISOs) to redefine the scope of their security efforts beyond present responsibilities," says Earl Perkins, research vice president at Gartner. "IoT security needs will be driven by specific business use cases that are resistant to categorization, compelling CISOs to prioritize initial implementations of IoT scenarios by tactical risk. The requirements for securing the IoT will be complex, forcing CISOs to use a blend of approaches from mobile and cloud architectures, combined with industrial control, automation and physical security".
On Gartner's predictions the number of "things" -- which doesn’t include PCs, tablets, smarthones, etc -- will be around 26 billion by 2020. This is forecast to create a $309 billion opportunity for suppliers delivering IoT products and services.
"In an IoT world, information is the 'fuel' that is used to change the physical state of environments through devices that are not general-purpose computers but, instead, devices and services that are designed for specific purposes", says Perkins.
Securing the IoT then brings new challenges in terms of the type and scale of technologies involved. As Perkins points out there is no, "guide to securing IoT" to provide CISOs with a framework. Even the definition of an IoT device is still open to interpretation.
Perkins concludes, "Gartner advises security leaders against over thinking IoT security by attempting to draft a grand strategy that encompasses all IoT security needs to this point in time. Instead, they should lower the residual risk of the IoT by assessing whether the particular business use case provides better control and performance. Lessons from these initial use cases will serve as building blocks for a broader strategy for addressing the security of the IoT".
Security solutions for the IoT will be discussed further at the Gartner Security & Risk Management Summit next week in Dubai.
Image Credit: PlusONE / Shutterstock
-

Data center market will show massive change over the next two years
Publié: septembre 11, 2014, 4:23pm CEST par Ian Barker

Four major factors will bring about dramatic change in the data center market by the end of 2016, according to a new report released by Gartner.
The factors are: highly disruptive competition, big cloud provider dominance, economic warfare, and nationalism. All of these will occur with different intensities over different time frames but will have a significant impact on the market.
"There are four market disruptions in play in the DC infrastructure market," says Joe Skorupa, vice president and distinguished analyst at Gartner. "Elements of them are already in play, and will become visible no later than early 2016; however, radical action by just one significant player could accelerate the market disruption of any of the factors".
Outlining the likely impact of each factor Gartner says that there are a number of potentially disruptive technologies that can spark changes to the business model. Things like software-defined networking (SDN) and software-defined storage, network function virtualization; extreme low-energy processors have the potential to release latent demand for improvements.
The dominance of big cloud providers like Amazon, Google, IBM and Microsoft is likely to see a shift away from traditional managed service providers as they find it harder to compete. This may well have a strong influence on the price of data center architecture.
Economic warfare may create an increasing east versus west divide. Gartner predicts that China, thanks to deep resources, increasingly respected brands and strong original design manufacturers, will improve its share of the data center market at the expense of western companies.
Finally nationalism, driven by the "Snowden effect" is likely to see a shift to locally developed and based providers as buyers lose trust in the ability of big players to protect their data.
Although the data center market looks set to grow it can't be assumed that existing predictions will hold true. Skorupa says, "Underneath this calm surface, increasing market pressures are driving a change in vendor behaviors, which, along with the four disruptive factors, make the market ripe for a period of major disruption. These behaviors will become more obvious as the pace of change increases".
Gartner will be hosting a webinar focusing on the data center market on October 14 as well as hosting summits in London in November and Las Vegas in December.
Photo Credit: dotshock/Shutterstock
-

Apple Watch will boost wearable adoption and add risk say experts
Publié: septembre 11, 2014, 11:35am CEST par Ian Barker

The adoption of wearable technology is on the verge of becoming mainstream and that process can only be accelerated by the release of the Apple Watch.
A recent study by Acquity, part of the Accenture consulting group, shows that wearable fitness devices are already taking off. By the end of 2015 they’re expected to reach 22 percent adoption and 43 percent within five years.
Smart watches are set to be the second most popular according to the same study, with five percent of consumers planning to purchase in the next year for a total of eight percent adoption by the end of 2015, and 25 percent planning to own one in the next five years.
Most experts believe the launch of the Apple Watch will generate new momentum in the wearables market but that brings with it some additional hazards. Antoine Rizk, VP of Global Go-To-Market Programs at API management specialists Axway says, "As developers rush to meet the demands of the Apple Watch, we will see a proliferation in new apps, creating a new wave of data flow to information back-offices, and an influx of security challenges for businesses to manage".
In an increasingly connected environment it’s important that new services are brought to the market quickly but also remain secure. Rizk says that APIs are key to this. "Apple Watch apps will be calling on APIs that must be delivered in real-time and able to communicate instantaneously; our smart watches will be linked up to our smart cars, and data on location and battery level has to be communicated in real-time. To achieve the agility and instant communication required, API gateways will be a fundamental cog in the infrastructure".
The adoption of NFC and the ability to use the watch to make payments makes an interesting target for hackers and we may see the rise of the "digital pickpocket". Ken Westin, security analyst at Tripwire expects the Apple Watch to become a prime target. "In the same way the original iPhone became an immediate target for hackers, so too will any new device Apple releases. There will be a race to hack the Apple Watch. The device connects to iPhones and other iDevices, so that connection may be a potential attack vector. Even though Apple's security team will have vetted the product, whenever a new product is available to security researchers and hackers alike, weaknesses are discovered".
Westin points out that recent issues surrounding iCloud mean that security will be in people’s minds where the Apple watch is concerned. "How this device collects and stores data and how access is secured are key questions Apple needs to address to help allay consumer fears".
New technology always brings new problems and it will be interesting to see how the Apple Phone survives contact with the real world. Watch this space...
-

Shippable wants to help developer teams innovate faster
Publié: septembre 9, 2014, 5:16pm CEST par Ian Barker

In a fast-changing world there's demand for new applications to be delivered quickly and traditional development processes often can't keep pace.
Seattle-based startup Shippable has announced a new version of its platform that helps developers to innovate and deliver more quickly using open source Docker containers. Docker -- in case you didn't know -- isolates resources of the Linux kernel to allow independent software containers to run on one Linux platform without the need to launch virtual machines. Docker containers can be run on any Linux machine whether on site or in the cloud.
"Container-based development is becoming essential for DevOps teams because it enables application development to move more quickly and efficiently," says Al Hilwa, program director, application development software at IDC. "Enterprises adopting agile practices and seeking options for continuous development and delivery will find that workflow containerization solutions like Shippable will ultimately lead to better software quality".
Shippable creates containerized, instant development and test labs which can help reduce an organization's cloud footprint by more than 50 percent. Each developer's code change is tested on a personal, dedicated environment that starts up in seconds and accurately replicates production topology.
This approach helps detect errors quickly and reduces reliance on weekly 'test passes' to find topology related issues. This improves developer efficiency by reducing the amount of time taken to rework code and fix bugs as a result. Developers will avoid the frustration and extra time spent fixing bugs that only occur on other systems.
"Docker is disrupting the virtualization space and enterprises are fast recognizing the value of containerizing their workflows. We believe that the first wave of adoption will be in dev and test workflows, and Shippable is focused on helping enterprises make that transformation," says Avi Cavale, co-founder and CEO of Shippable. "However, customers can use Shippable even if they have no plans to adopt containers into their workflow since Shippable is fully compatible with hypervisors and still delivers its continuous delivery platform to enable agile software development".
The Shippable platform is available as a hosted service or a dedicated host where the containers run on the customer's own machines but are managed in the cloud. A complete on-premise solution is currently in private beta.
You can find out more or sign up for a trial on the Shippable website.
Image Credit: Stokkete / Shutterstock
-

Dyreza trojan may pose a risk for Salesforce users
Publié: septembre 9, 2014, 3:23pm CEST par Ian Barker

A warning has gone out to customers of Salesforce.com that the Dyreza trojan, previously targeted at banking sites, may be a risk to users of the CRM solution.
The malware uses social engineering techniques to get the victim to infect the system via email. Once installed it uses "browser hooking" to allow Dyreza to intercept content entered by the user into the web browser before that content is transmitted over the network to a web site. Critically this allows the interception to occur before the data is encrypted.
By siphoning off traffic in this way the attacker can access the victim's credentials including username, password and any additional two-factor authentication token values. The attacker can then use this information to impersonate a user and fraudulently access their account for Salesforce or any other SaaS services targeted by Dyreza.
Zulfikar Ramzan, the CTO of cloud security specialist Elastica, says in a blog post, "So far, none of Elastica's customers appears to have been impacted by this threat, but we are monitoring the situation closely. Elastica’s Detect, Protect, and Investigate applications all can provide protection capabilities against Dyreza and similar malware".
Salesforce itself offers additional means of protection such as IP address restrictions to ensure that access comes from within the corporate network or VPN. It also offers SAML (Security Assertion Markup Language) authentication to further secure access.
Because the trojan siphons off information before it reaches the legitimate servers, it's able to intercept two-factor authentication token values so the attackers can exploit them in real time. Customers therefore need to be alert to potential compromises.
Razman concludes, "As organizations house increasing volumes of sensitive data on SaaS applications like Salesforce, it is a certainty that attackers will find increasingly clever ways of going after this information. It is therefore important for customers to put multiple protection mechanisms in place and to have deeper visibility into how their SaaS applications are being accessed and used".
Image Credit: Sadik Gulec / Shutterstock
-

iOS performance in the spotlight ahead of Apple's launch event
Publié: septembre 9, 2014, 2:17pm CEST par Ian Barker

In the run up to Apple's latest eagerly anticipated launch event, mobile benchmarking specialist Crittercism has released an Apple edition of its Mobile Experience Benchmark Report.
Focussing on statistics gathered from over a billion users across more than 120 countries it looks at key performance metrics including crash rates across iOS versions and devices along with latency by carrier and Wi-Fi.
Highlights include the finding that 46 percent of iOS apps have a crash rate of over one percent and 30 percent a rate of more than 2 percent. For comparison, on the web the norm for crash rates is 0.1 percent.
Looking at crashes by operating system, iOS 7 and 7.1 have the highest crash rate at 2.1 percent. Broken down by hardware the iPhone 5s crashes least (1.9 percent) whilst the iPad Mini crashes most (2.4 percent).
Apps on iPhones generally seem to be more stable than on iPads, but game apps are the most likely to crash. Photo and video apps are the next most crash prone with health and fitness and business apps being least likely.
If you want the most responsive carriers you need to be in Japan, the USA rates only 5th but there are regional differences which we'll come to shortly. China is slowest for carrier response. Those who prefer Wi-Fi should move to France which has the fastest iOS Wi-Fi responsiveness of any G20 country with India being the slowest.
In the US you’ll find the fastest iOS carrier responsiveness in Raleigh and the slowest in Kansas City. For Wi-Fi Virginia Beach is the best place to take your iOS device while Cleveland is the worst. Overall across the US it's T-Mobile that’s the fastest carrier for mobile users with AT&T and Verizon tied for second place.
The full report is available from the Crittercism website. Ahead of the general availability of iOS 8 Crittercism has also released a performance tracker which will monitor how the new OS performs through the launch and beyond.
Image Credit: logolord / Shutterstock
-

Major malvertising network targets Windows and Mac users
Publié: septembre 9, 2014, 10:20am CEST par Ian Barker

A new malicious advertising network is affecting sites including Amazon, Yahoo and YouTube. Dubbed "Kyle and Stan" by the Cisco Talos Security Research group that uncovered it, the malware is able to mutate to attack both Windows and Mac systems.
Online advertising has relatively few major distribution networks, by getting ads onto one of these an attacker has the potential to get malicious content in front of large numbers of users.
Talos Security Research has found a major network doing just this. Because of the naming scheme of hundreds of its sub-domains such as "stan.mxp2099.com" and "kyle.mxp2038.com", Talos has named the malvertising group "Kyle and Stan".
There's no drive-by download, the malware relies on social engineering to get the user to click on an ad. Once they do though the software redirects depending on the type of system you're using, allowing it to infect both Windows and Mac systems.
Clicking on the ad downloads a legitimate application like a media player but one which is bundled with adware and browser hijackers.
The network was first detected in early May and has shown spikes of activity in June and July. The research finds that the attack is using more than 700 domains, allowing the attackers to use a domain for a very short time, burn it and move on to use another one for future attacks. This helps them avoid reputation based and blacklist-type security solutions.
The malware dropper also employs unique checksums and encryption to try to avoid detection. The researchers conclude, "All in all we are facing a very robust and well-engineered malware delivery network that won’t be taken down until the minds behind this are identified".
You can read more and find a full list of the sites known to have been targeted on Cisco's blog.
Image Credit: Sam72 / Shutterstock
-

One in three financial services firms inadequately protected against cyberattack
Publié: septembre 8, 2014, 3:13pm CEST par Ian Barker

We trust financial services organizations with some of our most precious data, but are these companies doing enough to protect the information?
According to a new survey by Kaspersky Lab and market research company B2B International, 93 percent of financial services organizations have experienced some form of cyberthreat in the past 12 months.
Yet despite the increase in attacks nearly one in three still don't provide protection of users' endpoints or implement specialized protection inside their own infrastructure. This lack of protection is causing a loss of faith with only 53 percent of businesses feeling that financial organizations are doing enough to protect their information.
It also finds that 82 percent of businesses would consider leaving a financial institution that suffered a data breach and that 74 percent choose a financial organization according to its security reputation. This is echoed in a separate consumer survey which shows that 60 percent of people prefer to use companies offering extra security measures to protect their data.
Of the financial services organizations themselves, 27 percent are willing to suffer the losses incurred by cybercrime because they believe the cost of prevention will be higher. This seems to be a flawed view given that 52 percent have a policy of fully reimbursing losses caused by cybercrime without investigation, and that the true cost of loss may amount to hundreds of thousands of dollars depending on the size of the organization.
Kaspersky uncovered some cause for hope though as 47 percent of financial businesses think the loss of credibility and damage to reputation that would occur as a result of a data breach is the worst consequence to the company.
Ross Hogan, Global Head of Fraud Prevention Division at Kaspersky Lab says, "While it is encouraging that financial services organizations recognize the damage to their reputation that can result from a cyberattack, it is concerning that many firms have not taken the necessary steps to implement proper security. We are seeing more and more cyberattacks targeting financial organizations and while many will take action to reimburse the financial losses as a result of cybercrime, the damage done to a financial organization's reputation isn’t as easy to repair. Based on these survey results, we expect to see more financial services organizations take the necessary steps to not only protect customer data and financial information, but to take the steps needed to ensure their important reputation remains intact".
The full results of the survey are available as a PDF from the Kaspersky site.
Image Credit: Rob Hyrons / Shutterstock
-

New collaboration tool to make online discussions more productive
Publié: septembre 8, 2014, 11:11am CEST par Ian Barker

Business collaboration is most often organized by email, but it isn't always the most efficient way of ensuring things get done and it can be time consuming to deal with.
A recent survey by the McKinsey Institute shows that an average American spends 28 percent -- around 9 hours -- of their work week just dealing with emails. You can see how this time breaks down in infographic form below.
New team messaging platform Hooli aims to free workers from the tyranny of dealing with email by using simple, actionable commands that can be updated and received by all team members in real time.
Messages are sent instantly to all members of a group via a single live document and changes are color-coded so they're easy to spot. It offers a lean interface that's tailored to help online discussions run smoothly and make following up on actions easy.
Unlike chat collaboration tools like Slack and HipChat, Hooli can create actionable tasks from discussions and keep the whole team updated. It also allows progress updates to be made with a single click, so no need to write a long, detailed reply. Messages can be synced across desktop and mobile devices too.
You can try out Hooli free for up to three users and 100 meetings. Visit the company's website to find out more.

Photo credit: Alessandro Colle/Shutterstock
-

Lighter, thinner, tougher and more productive -- Dell's new commercial PCs
Publié: septembre 5, 2014, 4:03pm CEST par Ian Barker

As summer draws to a close and people start to go back to school or back to work technology manufacturers like to tempt them with new and shiny kit.
Today is the turn of Dell as it launches its latest commercial PC range aimed at offering productivity, manageability and security for business users in smaller, thinner and generally nicer packages.
"Dell understands the complexity of supporting the wide variety of devices present in today’s evolving workforce environment," says Kirk Schell, vice president and general manager, commercial client solutions at Dell. "Our new portfolio enables businesses of all sizes to embrace sleek and innovative form factors their workforce will be proud to use day after day to accomplish their productivity goals. While they look like thin and light consumer devices, these commercial PCs are backed by the industry's best security and manageability that only Dell provides".
First up are new additions to the Latitude range including the Latitude 13 7000 series which claims to be the world's most secure 2-in-1, combining a lightweight business ultrabook and a detachable tablet in one powerful device. It will be available from mid-October starting at $1,199.
The Latitude 12 5000 offers a secure business laptop featuring a new design that's 20 percent thinner than the previous model. It offers all day battery life from a 4-cell battery, enhanced materials for durability and enterprise-class support and services. The range starts at $769 and will be available from September 25th.
New Latitude 14 and 15 3000 models for the Asian market are a more affordable package for smaller businesses. Again these are thinner and lighter than previous models with spill-resistant keyboards, all day battery life and up to a terrabyte of storage with prices starting at $640.
There's a new addition to the company's rugged range too with the Latitude 14 which has an outdoor-readable display and uses QuadraCool technology for performance at high temperatures. It also features a backlit keyboard so it can be used in a wide range of environments.
Dell hasn’t forgotten desktops and it's been busy making them smaller too. New Optiplex 9020 and 3020 Micro PCs have a chassis that's 67 percent smaller than Dell's previous desktops and offer a choice of mounting options. The OptiPlex 9020 Micro is aimed at environments where space is limited and security is a priority, while the OptiPlex 3020 Micro provides essential business class performance in a compact unit. The OptiPlex Micro range starts at $499.
In addition there's a new Chromebox for meetings, designed to offer an easy-to-use platform for managing video conferences. Costing $999 it comes equipped with an HD webcam, speaker phone and RF remote control, it's only available in the US initially though. Dell is also launching a standard Chromebox to provide a small, quiet desktop for smaller businesses. This will be available from September 26th starting from $179.
Rounding off the announcements are some new monitors including an outsize 55-inch model intended for meeting rooms and a 27-inch Ultra HD 5K model. The Dell 55 Monitor is available now at $1,049, the UltraSharp 27 will be along in the fourth quarter priced at $2,500.
More information on all of these devices will be available on the Dell website as they're released.
-

Trustwave ethical hacking lab looks to counter hidden threats
Publié: septembre 5, 2014, 12:57pm CEST par Ian Barker

Security exploits aren't always aimed at computers or mobile devices. Often they target the infrastructure devices like ATMs and point of sale terminals that we take for granted in our everyday lives.
In order to protect against these threats, enterprise security specialist Trustwave has announced that it's enhancing its capabilities with the opening of an ethical hacking lab at the company’s Chicago HQ.
The lab's aim is to uncover weaknesses in devices like ATMs, point of sale keypads and security cameras that are regularly used by businesses but which may have hidden security flaws. By uncovering these problems ethical hacking can help companies take action before it's too late.
It can carry out assessments to determine if an existing device has been compromised as well as carrying out penetration testing for businesses to uncover potential problems in devices before they’re put to use.
The lab is also being used to carry out studies following security breaches to identify how the criminals broke in and which details have been compromised. It's currently working on a credit card skimmer planted at gas pumps to steal payment information.
If you've ever wondered what ethical hacking looks like, Trustwave has created a video to give you an insight. To be honest it looks pretty much like we expected it to, right down to the hairstyles.
Photo Credit: ra2studio / Shutterstock
-

Privacy and financial threats top mobile malware trends
Publié: septembre 5, 2014, 11:22am CEST par Ian Barker

With mobile malware showing a 68 percent increase over the first half of last year it seems that, as with the PC malware field, profit is the main driving force behind it.
New data released by security specialist NQ Mobile shows that infections were detected in 37.5 million Android devices in NQ Mobile's database of 136 million active user accounts worldwide, an increase of 78.6 percent over last year.
Some 62 percent of this malware falls into categories that aim to generate financial gain for the people behind it. Often this is through premium rate scams or data overcharges. NQ Mobile has also uncovered a new strain of encryption malware for Android.
Called 'Simpelocker,' the Trojan is packaged with genuine Android apps and infects the devices of unsuspecting users downloading the APK file from apps in third-party markets. Once installed, the app requests permissions to perform a variety of actions like writing to external storage devices. The Trojan can also scan the SD card for specific file types like photos and documents and attempt to encrypt them.
Privacy is another issue with 11 percent of mobile threats coming from a genuine or malicious app with the ability to gather and leak personal information without the device user’s knowledge or consent. This information can then be shared or sold on the dark web to cybercriminals who will attempt to use social engineering tactics to gain access to the consumer’s finances. Apps like 'Fake Play' which poses as the Google Play store can be used to intercept user data in the background.
Server side botnets remain a major concern too thanks to their ability to control infected devices and download more malicious material from a remote host.
You can read more on NQ Mobile's blog and there's a summary of the company's findings in infographic form below.
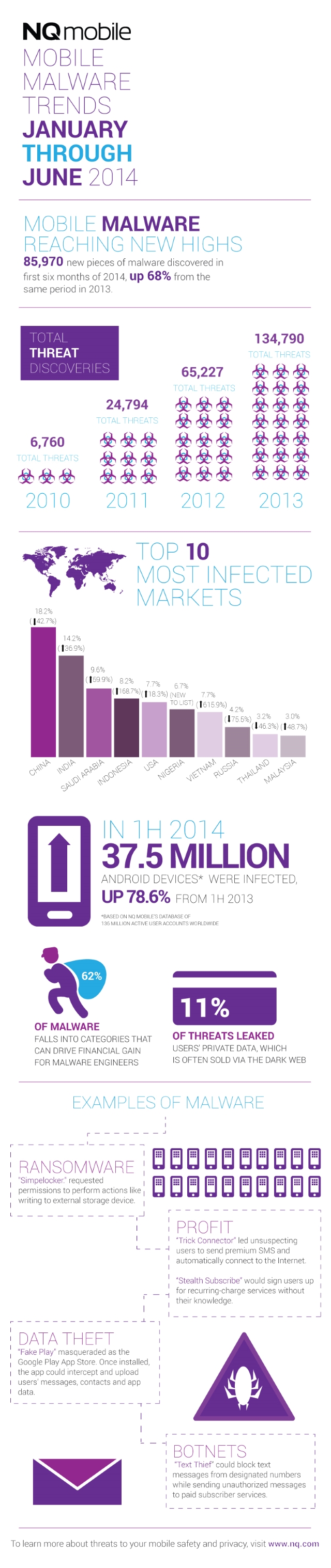
Image Credit: Paul Michael Hughes/Shutterstock
-

DecryptCryptoLocker helps almost 3,000 victims
Publié: septembre 4, 2014, 4:07pm CEST par Ian Barker

A few weeks back we reported on the launch of a free tool to help out CryptoLocker victims allowing them to retrieve locked files.
One of the companies behind the DecryptCryptoLocker tool, Fox-IT, has released some details of how well it's working. It has so far dealt with 2,900 requests for decryption keys and dozens more are being received on a daily basis.
Decryption requests have come in from around the world with most being from the US with 1,933 and the UK with 546. The most common file type being decrypted is PDF closely followed by .doc files.
Fox-IT's blog notes that new players are still trying to fill the vacuum left by the demise of P2P Zeus. "Parts of the inject code have reappeared in other botnets, we are tracking new malware variants being developed which appear to re-use or build upon parts of P2P Zeus and there is an upsurge activity from Gozi, Bugat and other existing malware variants. This means some of the high profile customers of P2P Zeus are looking for a new custom piece of malware while others customers simply joined other existing operations like Gozi".
It also points out that CryptoLocker made significant income for its operators which has led to a renewed interest in ransomware.
The DecryptCryptoLocker tool is still available for victims who need to unlock their files.
Photo Credit: BL/Shutterstock
-

Marketing Raven helps sales and marketing teams become more productive
Publié: septembre 4, 2014, 12:51pm CEST par Ian Barker

The business of marketing has always been about understanding the customer, and the modern information-driven world means there's more potential to know what customers are up to than ever.
The trouble is that many businesses fail to properly exploit this due to lack of visibility into how their marketing efforts work. Cloud-based file distribution specialist Content Raven aims to change this with its new Marketing Raven tool.
Marketing Raven adds tracking and analytics to all common file types so users can determine how recipients have engaged with a document, how many times they viewed it, on what device, and more. This allows it to provide valuable insight to further customize and improve campaigns. In addition, Marketing Raven sends real-time alerts to sales and business development staff when a prospect is interacting with piece of content, enabling them to time contacts when the lead is most engaged and follow up with appropriate information.
It can also track when a piece of content is shared or forwarded, giving new insight into the customer’s decision making and opening up potential new leads.
"We are excited to launch Marketing Raven as a way to help marketers and salespeople better analyze and enhance their marketing campaigns and sales cycles," says Ronald Matros, CEO of Content Raven. "Data-driven marketing is quickly becoming the norm in the marketing industry and this new product allows us to tackle the biggest issues faced by enterprises today as they look to improve their sales cycle and gain insight into how their customers and prospects are consuming their content".
You can find out more on the Content Raven website, where you can also download a Five Blind Spots in Your Digital Marketing Strategy ebook and view a video demonstration of what the product can do.
Image Credit: donskarpo / Shutterstock
-

One in five businesses loses data to mobile device theft
Publié: septembre 4, 2014, 12:00pm CEST par Ian Barker

The results of a new survey from Kaspersky Lab show that the rate of mobile device theft is increasing but over the same period the time taken for IT departments to respond has increased.
Part of this is down to employees taking longer to report mobile loss or theft. Only half report the theft of a mobile device within a day with 38 percent taking up to two days and nine percent waiting between three and five days.
In 2014 25 percent of companies have experienced the theft of a mobile device, compared to only 14 percent in 2011. Most concerning though is that 19 percent of those surveyed say that mobile device theft has resulted in the loss of business data.
The survey of over 3,900 IT security professionals also finds that 52 percent are more concerned about mobile risks than in previous years, 43 percent believe that mobile working patterns pose too much risk, and 42 percent belive that BYOD policies pose increased risk to the business.
"The survey results clearly indicate that IT managers are dealing with multiple security challenges associated with a mobile workforce, and as the use of mobile devices in the workplace continues to grow, employees appear to be less engaged in helping secure mobile platforms," says Mark Bermingham, Kaspersky Lab's Director of Global B2B Product Marketing.
All of this highlights the need for businesses to have a mobile device management policy. Kaspersky also suggests that having an MDM policy managed through the same console as the company’s other endpoint security software can enable IT managers to enforce policies customized to each individual employee, including 'containerization' to keep business information on mobile devices encrypted and separated from personal data on employee-owned devices.
These results are part of Kaspersky's 2014 IT Security Risks Survey which is available on the company’s website where you can also find details of Kaspersky Security for Mobile.
Photo credit: cunaplus / Shutterstock
-

Mystery fake cellphone towers discovered across America
Publié: septembre 3, 2014, 5:54pm CEST par Ian Barker

Fake mobile phone 'towers' dotted across the US could be listening in on unsuspecting smartphone users according to recent reports. And -- tin foil hats on, everyone -- nobody knows who's behind them.
Security company ESD America discovered 17 of the fakes called 'interceptors' whilst testing its secure Android phone. The towers can attack devices via the baseband chips that allow them to communicate with their networks and can, says ESD, eavesdrop or even install spyware.
These fakes use known technology and have existed in China for several years according to 360 Safe which has uncovered fakes masquerading as carriers, banks and other organizations to send SMS messages.
ESD America CEO Les Goldsmith told Popular Science magazine, "Interceptor use in the US is much higher than people had anticipated," Goldsmith says. "One of our customers took a road trip from Florida to North Carolina and he found 8 different interceptors on that trip".
The technology used targets the 'baseband' of the phone which sits in between the cellular network and the phone's OS. Baseband attacks are difficult to carry out as the technical details of the chips are closely guarded and the equipment needed is relatively expensive -- around $100,000.
"What we find suspicious is that a lot of these interceptors are right on top of US military bases." Says Goldsmith. "Whose interceptor is it? Who are they, that's listening to calls around military bases? Is it just the US military, or are they foreign governments doing it? The point is: we don't really know whose they are".
Documents leaked by Edward Snowden have revealed that the NSA has the ability to carry out baseband attacks to, for example, remotely activate a device's microphone. A similar type of attack is used by the 'stingray' devices employed by law enforcement agencies.
So, should you be worried that your weird neighbor is building a 50ft mast in his backyard? Maybe, although it's likely that these fake towers aren't permanent physical installations but something more mobile.
At the moment no one knows who's behind the fakes and the cost of something like a GSMK Cryptophone needed to detect them is thought to be around $3,500 dollars.
It's perhaps best just to assume, as many of us have been doing for years, that nothing you do on a mobile device is ever completely secure. In the meantime your conspiracy theories about who might be behind these fake towers are welcome below.
Image Credit: mikeledray / Shutterstock
-

Employees opt to stick with consumer file sharing tools at work
Publié: septembre 3, 2014, 4:45pm CEST par Ian Barker

Most of us prefer to stay with familiar consumer file syncing and sharing tools at work rather than use the alternatives provided by the IT department.
This is the finding of new research by global analyst company Ovum. The survey of 5,187 full-time employees shows that 89 percent are using consumer products and only nine percent are happy with the commercial tools on offer from their companies.
Of those that have adopted the technology 29 percent are using three or more different products in order to get their work done. However, 44 percent still aren't using file sharing products at all, relying on email or flash drives to move data around.
Richard Edwards, principal analyst at Ovum, says, "These figures paint an anarchic picture of file sharing and document-centric collaboration within the workplace, and support Ovum's thesis that while there may be an enterprise file sync and share solution to address almost every business need, there is no product that meets them all".
Ovum’s report, Selecting an Enterprise File Sync and Share Product, looks at 19 different offerings from vendors of all sizes, including Box, Citrix, Dropbox, Egnyte, EMC, Google, IBM, Microsoft, Salesforce.com, and WatchDox.
"No commercial product is dominating the workplace," says Edwards. "The wide-scale use of Dropbox among knowledge workers highlights the power and impact of IT consumerization, while the pervasiveness of Google Drive and Apple iCloud demonstrates the effects that mobile devices are having on the enterprise. And of course Microsoft is omnipresent in this market too".
The number of products competing for this market indicates the importance which vendors attach to it and the fact that each offers a slightly different approach. Edwards concludes, "As always, the challenge for CIOs and IT managers is to identify the solution that best meets the organization's current and future requirements, with regard to a broad set of employee roles and business use cases. Herein lies the problem, as no single product on the market today offers everything that a large enterprise is likely to need".
Image Credit: megainarmy / Shutterstock
-

Easy Solutions adopts DMARC to fight phishing attacks
Publié: septembre 3, 2014, 3:16pm CEST par Ian Barker

Phishing attacks attempting to steal user credentials have become a common occurrence in recent years and made people wary of trusting anything they receive in email.
Fraud protection specialist Easy Solutions is aiming to help restore that trust by adopting the DMARC (Domain-based Message Authentication, Reporting & Conformance) specification to allow its customers to improve productivity and speed detection of phishing sites.
A DMARC industry group was formed in 2012 by a number of technology, financial service, media and retail companies. Its aim is to fight email fraud, helping email senders and receivers work together to better secure emails and protect users and businesses from abuse.
Using the DMARC technical specification email senders can authenticate legitimate messages and exchange information with email receivers about how to handle unauthenticated traffic by monitoring, quarantine or deletion.
The technology has been implemented by major email providers including Google and Microsoft, as well as large financial institutions and retailers, such as Amazon, Apple, Bank of America, eBay, Facebook, FedEx and more.
"Fraudulent email and orchestrated attacks have eroded trust in email as a communications medium to such an extent that it is nearly impossible for major financial institutions, retailers and marketers to authentically communicate with their customers," says Daniel Ingevaldson, CTO of Easy Solutions. "DMARC shows great promise, not only for securing email channels and reducing the amount of fraudulent or spoofed email but also for improving threat intelligence around targeted attacks. DMARC gives banks, retailers and other institutions the power to effectively project their own policy to the world on how fraudulent email is handled. We are pleased to offer our customers the ability to leverage this emerging standard to improve the health of email communication, reducing the asymmetry they face in this battle against fraudsters".
You can find out more about Easy Solution's fraud protection platform and how it can help businesses stay safe across a variety of channels and platforms on the company's website.
Photo Credit: Ivelin Radkov/Shutterstock
-

Cloudfinder for Box free for business users until January 2015
Publié: septembre 2, 2014, 6:00pm CEST par Ian Barker

As the market for storing and sharing files in the cloud has grown, Box has become one of the most popular solutions. As a result lots of other add-on products have grown up around it offering added security, compliance and more.
The latest to join the Box ecosystem is backup specialist eFolder with its Cloudfinder product, a multi-platform cloud-to-cloud backup service.
Cloudfinder for Box provides an encrypted, tamper-proof SafeHaven and second-site location for Box and other critical SaaS data. It also reduces the administrative burden thanks to self-service point-in-time restores, cross-service instant full-text search and automated enforcement of corporate data governance policies.
"Businesses have adopted SaaS applications en masse," says Kevin Hoffman, CEO of eFolder. "Now, companies, small and large, are looking for ways to avoid data sprawl and ensure data retention across a host of SaaS business applications. Today, Cloudfinder spans across many of the most popular enterprise-grade applications to provide an additional layer of protection, archiving and discovery. Our integration with Box and other leading SaaS applications, position Cloudfinder as the central repository for the modern, cloud-based business."
Cloudfinder offers unified cloud-to-cloud backup and instant full-text search of Office 365, Google Apps and Salesforce, and now adds Box to its capabilities. From a single user interface, businesses can backup, search, restore and get a data overview across all of the SaaS services that are supported by Cloudfinder.
"The value of business data is priceless," says Marcus Nyman, founder of Cloudfinder and eFolder president. "It is a universally accepted best practice to have a second-location backup of all on-premises corporate data regardless of the robustness and reliability of the underlying storage. For data living in SaaS applications, it is no different."
Cloudfinder for Box is available from today and is free with unlimited storage for all businesses until January 1 2015. Go to www.cloudfinder.com/boxfree to find out more and register for the free trial.
Image Credit: alexmillos / Shutterstock
-

Zetta.net integrates cloud backup with ConnectWise to help MSPs add value
Publié: septembre 2, 2014, 3:33pm CEST par Ian Barker

The ConnectWise system management platform is popular with managed services providers, with more than half of MSPs worldwide using it to enhance efficiency and control for their clients.
Now cloud backup company Zetta.net has announced that it's integrated its enterprise-grade cloud backup and disaster recovery platform with ConnectWise to allow MSPs to offer an extra layer of service.
This integration will give IT service providers a complete view of their customers' data usage, alerts, billing and other activities from within the ConnectWise platform, streamlining their management and administrative tasks. This will allow service providers to concentrate on the efficient running of their business and focus on better servicing their customers.
"We're excited Zetta.net's MSP strategy includes integration to ConnectWise," says Jeannine Edwards, Director, ConnectWise Platform at ConnectWise. "Their SaaS-based approach to protecting mutual partners' backup and recovery needs will make for a great addition to the ConnectWise Platform community."
Zetta.net uses an appliance-free approach to database and server image backups for both physical and virtual environments. Along with built-in WAN acceleration means it can deliver faster backup and recovery speeds with data transfer rates of up to 5TB in 24 hours.
Because there's no need for additional hardware on customer sites, backup solutions can be up and running quickly and be remotely managed from anywhere.
"We continue to drive simplicity and efficiency into our solution to help MSPs build a more profitable backup service", says Art Ledbetter, Director of Channels at Zetta.net. "The integration with ConnectWise enables MSPs to eliminate manual business processes and enhance visibility into their clients' backup activities to effectively manage their business".
Although it's currently aimed at service providers the solution could also appeal to large enterprises looking to streamline their backup strategy. You can find out more about Zetta.net's cloud backup solutions on the company's website.
Photo Credit: Andreas Weitzmann/Shutterstock
-

Tired of privacy breaches? How to remove yourself from social networks
Publié: septembre 2, 2014, 1:17pm CEST par Ian Barker

The leaking of celebrity photos which may have come from iCloud is just the latest in a series of high profile security and privacy breaches that are leading many people to question how safe their data is online.
For those who have decided enough is enough, secure transaction specialist Imprima has produced an infographic guide to "unfriending the internet" which covers how to take your personal profiles off the main social networking sites.
It explains how to remove yourself from Facebook, Twitter, Google+ and LinkedIn, as well as explaining the right to be forgotten on Google. It also covers useful stuff like the difference between simply deactivating your Facebook account and deleting it altogether.
If you want to cut yourself off from the world of social networking you'll find the full infographic below.
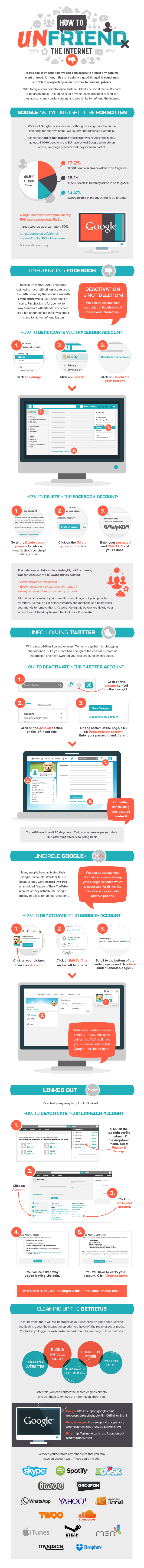
Image Credit: jurgenfr / Shutterstock
-

Intel reveals its first 8-core desktop CPU
Publié: septembre 1, 2014, 12:36pm CEST par Ian Barker

Despite continuing reports of its death, the desktop computer still has a place in the world, particularly amongst power users and gamers. It's these people that Intel has squarely in its sights with the new Core i7-5960X processor Extreme Edition.
Intel’s first 8-core desktop CPU features 16 computing threads which, along with support for the latest DDR4 memory, will enable some of the fastest desktop systems yet seen. Combine this with the new enhanced Intel X99 Chipset and you also have robust overclocking capabilities which will allow enthusiasts to tune their systems to extract maximum performance.
"We're thrilled to unveil the next phase in our 'reinvention of the desktop' we outlined earlier this year", says Lisa Graff, vice president and general manager of Intel's Desktop Client Platform Group. "This product family is aimed squarely at those enthusiasts who push their systems further than anyone, and we're offering the speed, cores, overclocking and platform capabilities they have asked us for".
Launched at the Penny Arcade Expo in Seattle, Intel used the event to demonstrate the new processor's ability with various gaming titles. It has been working with a number of OEMs, memory and motherboard makers and graphics partners to unlock maximum potential from the product.
Companies involved in the gaming industry are particularly excited by the new processor. Alienware's general manager, Frank Azor says, "It was an easy decision to work with Intel to bring its new eight-core extreme processor to our new flagship gaming desktop, the Alienware Area-51. Using new overclocking and monitoring features in Alienware Command Center 4.0, we've been able to really push the processors to the fullest extent and are seeing impressive overclocking headroom. This new Intel processor lineup is the perfect choice for gamers who demand the absolute best performance from their systems".
For those with slightly less need for speed, Intel has also announced a range of 6-core, unlocked enthusiast CPUs. All the new processors will be available from this week with prices ranging from $389 to $999. You can find out more about the line up on the Intel website.
-

Smartphone shipments show strong growth as Android dominates emerging markets
Publié: août 29, 2014, 1:04pm CEST par Ian Barker

More than 1.25 billion smartphones will be shipped worldwide in 2014, up 23.8 percent over last year, despite a slowing of growth in more mature markets, according to the latest data from IDC's Quarterly Mobile Phone Tracker.
Growth in mature markets has slowed to 4.9 percent but emerging markets are surging ahead with 32.4 percent growth. Since these emerging markets have accounted for more than half of smartphone shipments since 2011 this is perhaps not too surprising.
"The smartphone market, which has experienced runaway growth over the last several years, is starting to slow. Mature markets have slowed considerably but still deliver strong revenues with average selling prices (ASPs) over US$400. Meanwhile, many emerging markets are still barreling along, but with ASPs of less than US$250", says Ramon Llamas, Research Manager with IDC's Mobile Phone team. "The key for vendors now is to maintain a presence in the higher-margin mature markets, while establishing a sustainable presence within the fast-growing emerging markets. To enable this strategy, operating system companies are partnering with OEMs to provide low-cost handsets".
Looking ahead to the end of the year, IDC expects emerging markets to account for 73.5 percent of all smartphone volume shipped. This is being driven by Android devices which are expected to take up 88 percent of the volume. Further ahead, emerging market smartphone volume is expected to reach 1.4 million units by 2018, accounting for 79.5 percent of worldwide volume.
"The support that Google's Android platform has received from over 150 handset manufacturers has allowed it to gain the share it has in emerging markets", says Ryan Reith, Program Director with IDC's Worldwide Quarterly Mobile Phone Tracker. "The lack of constraints around hardware and software specifications has helped bring to market many low-cost products, a lot of which could be considered borderline junk. With Google's recent announcement of Android One, they hope to change this by laying out a set of standards for manufacturers to follow".
Aside from growth in volume shipments, IDC sees a move towards larger screen mobiles, or phablets, which it expects to grow from 14 percent of the market this year to 32.2 percent in 2018. Apple's expected entry into this field should give it the ability to drive replacement cycles in mature markets.
More information about the IDC Worldwide Quarterly Mobile Phone Tracker is available on the company's website.
Photo Credit: 3Dstock / Shutterstock
-

British parents set to spend millions on back to school gadgets
Publié: août 29, 2014, 11:52am CEST par Ian Barker

More than a quarter of British parents say they'll be buying new gadgets for their kids ahead of the autumn return to school, with an average spend of £329 per family making a massive nationwide total of £659 million.
This is among the findings of a new survey by comparison and switching site uSwitch.com which finds that the average school bag now contains around £130 worth of tech.
Ernest Doku, telecoms expert at uSwitch.com, says, "Kids today are learning to use gadgets even before they can walk, and parents are investing heavily in the latest tech for school too -- the new term has sparked a flurry of gadget purchases".
49 percent of children take at least one gadget to school. More worryingly, however, nine percent have had gadgets stolen at school and 14 percent have been bullied because of their gadgets -- usually because they're the "wrong" brand.
Technology is changing the pattern of study too. A third of homework is now typed rather than hand written and a quarter submit their work via email or via an online system set up by their schools. The majority (38 percent) use laptops to do school work, but tablets (24 percent) are now more common than desktops (20 percent).
The results show that parents are concerned about the move to technology. Whilst 82 percent recognize that it's an essential part of their children's lives, 43 percent are concerned that they lack the technical ability to help with homework.
Parents are also troubled about the effect of technology on their children's abilities. 66 percent worry about over reliance on spell check and 61 percent about the effect using computers has on their handwriting.
Kids are getting their gadgets at an earlier age too. The average age for getting a mobile phone is 9 years 10 months, whilst tablets come even earlier, British kids receiving their first one at 8 years 7 months.
Although 63 percent of parents say they restrict the time their children spend using gadgets, 70 percent admit to employing technology to keep children quiet. The average age at which parents start to distract their kids with smartphones or tablets is 5 years 8 months.
Doku concludes, "Although gadgets are great educational tools, it's important to monitor your child's usage to ensure they are safe online -- as well as actually doing their homework".
Image Credit: Pressmaster / Shutterstock
-

Prelert adds Elasticsearch connector to open up big data
Publié: août 26, 2014, 3:25pm CEST par Ian Barker

Big data analysis can open up valuable insights that are locked up in databases, but releasing that information without access to a team of data scientists isn't easy.
Analytics company Prelert is aiming to make big data accessible and valuable for all businesses with its anomaly detection engine, built using unsupervised machine learning technology. No human intervention is required to set parameters or tell it what to look for, once it's pointed in the right direction it will go to work on massive volumes of streaming data.
The latest stage of its development is today's release of a connector to allow deployment of the technology on Elasticsearch stacks. Offering an Elasticsearch connector, opens up the use of machine learning technology, providing tools that make it easier to identify threats and opportunities hidden within massive data sets.
"Prelert is dedicated to making it easier for users to analyze their data and drive real, actionable value from it", says Mark Jaffe, CEO of Prelert. "The amounts of data that companies and organizations have these days are simply massive -- too massive for humans to process and analyze. The release of our Elasticsearch Connector is the latest step toward making the analysis of large data sets possible, repeatable and valuable without a team of data scientists".
The Anomaly Detective can process large volumes of streaming data, automatically learn normal behavior patterns represented by that data and identify and cross-correlate any anomalies. Add in the ability to processes millions of data points in real-time and it can identify performance, security and operational anomalies so they can be acted on before they have an impact on the business.
The Elasticsearch Connector is written in Python and is available now via GitHub. Additional connectors for other big data technologies are set to be released in the coming months. Meantime you can find more about anomaly detection on Prelert's website.
Photo Credit: T.L. Furrer / Shutterstock
-

SSL vulnerabilities leave Android apps open to attack
Publié: août 22, 2014, 4:11pm CEST par Ian Barker

If you're an Android user you may already have been tempted to don your tin hat and descend to your bunker following today's earlier story about app hacking. Prepare to settle in for a long seige then as new research reveals that many of the most popular Android apps have SSL vulnerabilities that leave them open to man in the middle (MITM) attacks aimed at stealing personal information.
According to threat protection specialist FireEye a significant proportion of apps allow an attacker to intercept data exchanged between the Android device and a remote server.
A MITM attacker may simply "listen in" to data as it's transmitted, replace or modify it to inject malicious content into an app, or redirect traffic to a new application.
FireEye has looked at the 1,000 most downloaded apps in the Play store and found that around 68 percent have one of three major SSL vulnerabilities leaving them open to MITM attacks.
Of 614 apps that used SSL/TLS to communicate with a remote server, 73 percent didn't check certificates. Eight percent failed to verify the hostnames of servers making redirection possible, and of 285 apps using WebKit, 77 percent ignored SSL errors which could allow the exploit of Javascript vulnerabilities.
The company suggests that users can help protect themselves, "...by not accessing websites that require user login credentials when using public wi-fi networks. This in itself, with general vigilance in opening emails from unknown sources, will go a long way in protecting sensitive information from MITM attacks".
You can read more details of the research, which includes case studies of individual apps, on the FireEye blog. You might also want to sign up to beta test the latest Sophos security solution for Android.
Image Credit: Palto / Shutterstock
-

Information security spending to grow 8 percent in 2014
Publié: août 22, 2014, 1:44pm CEST par Ian Barker

Worldwide spending on information security is set to top $71.1 billion this year, up almost 8 percent over 2013, according to forecasts by Gartner. It's also forecast to grow by a similar percentage next year to reach $76.9 billion.
Gartner says increased use of mobile, cloud and social services will drive new security technology through 2016. There's been a democratization of security threats too, driven by the easy availability of malware and infrastructure, via the underground economy, that can be used to launch targeted attacks.
"This Nexus of Forces is impacting security in terms of new vulnerabilities," says Gartner research director Lawrence Pingree. "It is also creating new opportunities to improve effectiveness, particularly as a result of better understanding security threats by using contextual information and other security intelligence".
Among Gartner's forecasts are that by 2015 around 10 percent of IT security for enterprises will be delivered via the cloud. This is higher for small and medium businesses which are expected to have around 30 percent of their security controls cloud based by 2015.
Increased regulatory pressure is also expected to drive spending with new data privacy and compliance legislation being introduced in several countries. By 2018, more than half of organizations are predicted to be using security services firms that specialize in data protection, security risk and infrastructure management to enhance their security positions. In addition Gartner predicts a rise in the number of infrastructure protection products bought in package form to 30 percent by 2015.
Finally it sees mobile security becoming a higher priority for consumers who at the moment don’t recognize that antivirus is important on mobile devices. Protection is expected to become a higher priority from 2017 onward, when new market opportunities for security providers are likely to emerge.
Security trends will be discussed further at Gartner Security and Risk Management Summits in Australia, London and Dubai in coming weeks.
Photo Credit: Sergey Nivens/Shutterstock
-

Gmail app hacked with 92 percent success rate
Publié: août 22, 2014, 12:08pm CEST par Ian Barker

Researchers from the University of California Riverside's Bourns College of Engineering have identified a weakness in Android which allows personal data to be obtained from apps.
Tested against seven popular apps the method was between 82 and 92 percent successful on six of them, only Amazon with a 48 percent success rate proved more difficult to crack. Most vulnerable were Gmail and H&R Block at 92 percent, followed by Newegg (86 percent), WebMD (85 percent), CHASE Bank (83 percent) and Hotels.com (83 percent).
Although demonstrated on Android the researchers believe their method will work on iOS and Windows devices too because they share a key feature exploited in the Android system.
The attack works by getting a user to download a seemingly benign app, such as one to display background wallpaper on a phone. Once the malicious app is installed, the researchers can exploit a newly discovered public side channel, the shared memory statistics of a process, which can be accessed without any privileges.
Shared memory is an operating system feature commonly used to allow apps to share data. By monitoring changes that take place in it researchers are able to correlate them to what they call an "activity transition event," which includes such things as a user logging on to Gmail.
"The assumption has always been that these apps can't interfere with each other easily," Zhiyun Qian of the Computer Science and Engineering Department at UC Riverside says. "We show that assumption is not correct and one app can in fact significantly impact another and result in harmful consequences for the user".
The attack needs careful timing in order to work. "By design, Android allows apps to be preempted or hijacked," Qian says. "But the thing is you have to do it at the right time so the user doesn’t notice. We do that and that’s what makes our attack unique".
The Amazon app proved harder to attack because it allows one activity to transition to almost any other activity, making it more difficult to guess which activity the user is currently in.
Users can protect themselves by not installing untrusted apps, but in the longer term researchers say the operating system needs to be changed to better regulate side channels.
The full research paper is due to be presented at today's USENIX Security Symposium in San Diego. It's available to read online and there are some short videos demonstrating how the attack method works.
Photo Credit: Stuart Miles/Shutterstock
-

How security breaches have changed the cyber landscape
Publié: août 22, 2014, 10:59am CEST par Ian Barker

There's no doubt that security breaches are becoming more common. According to the US Government Accountability Office cyber incidents increased by 782 percent between 2006 and 2012.
But how does this impact the world at large? Security management company SRC Cyber has put together an infographic looking at some of the most infamous occurrences over the last decade and how they've affected the global cyber landscape.
It points out that security breaches can happen to anyone at any time. And whilst system problems and human error account for the majority of data breaches the most common single cause at 42 percent is malicious intent.
The infographic shows how three of the most high profile recent attacks have had an effect on security spending, attack awareness and in the case of the Target breach how it's hit the company's profits.
You can view the details below or on the SRC Cyber website.
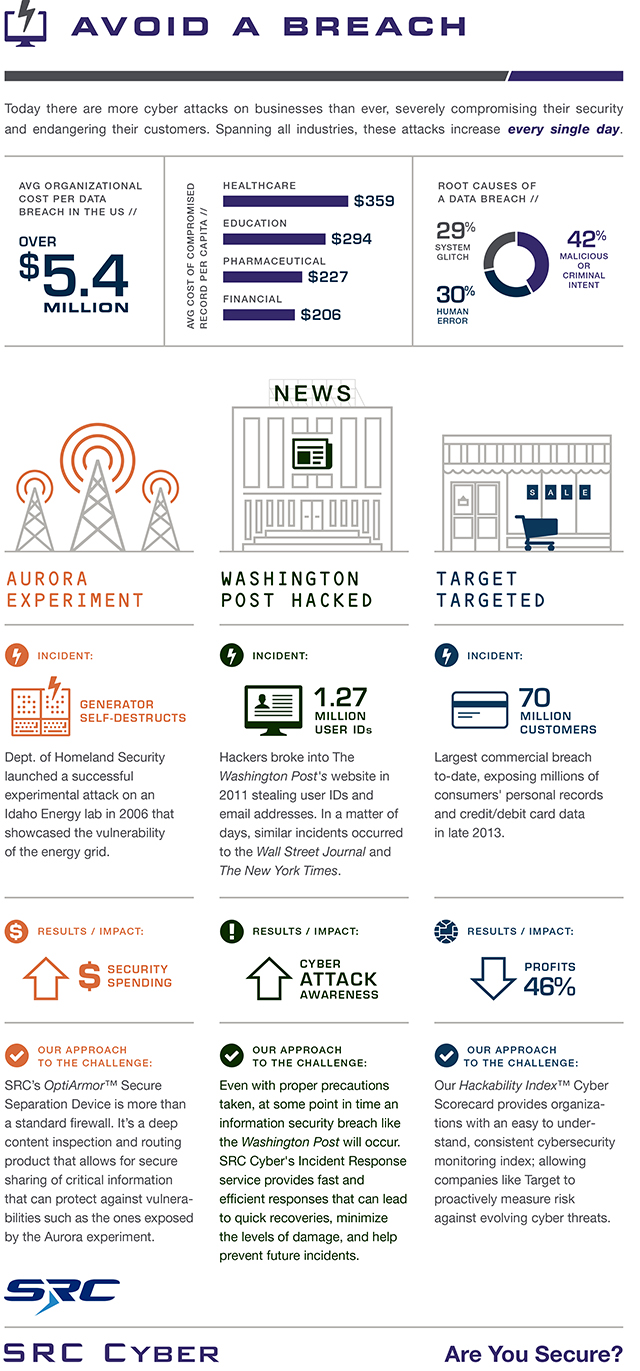
Image Credit: Sergey Nivens / Shutterstock
-

Symantec sets out plans to simplify its Norton range
Publié: août 19, 2014, 10:26am CEST par Ian Barker

We all know it's important to keep our PCs safe from online threats, but the range of options available to do that -- even from just one developer -- can be bewildering.
Symantec has recognized this problem and has announced that from this fall it will streamline its nine existing security offerings into just one flagship Norton Security product.
Norton Security combines the features of existing packages and will be available with or without cloud backup. This means that legacy products like Norton Internet Security, Norton AntiVirus and Norton360 will be retired.
Writing on Symatec's Information Unleashed blog, Fran Rosch, Executive Vice President of the Norton Business Unit says, "We are making it easier to select and buy the security products you need, and download and maintain them. As cybercriminals and the attacks they launch become more sophisticated, we're strengthening our advanced threat protection technologies and improving performance across your Android, Windows, Mac and iOS devices".
The product will also be made easier to use with improvements to the interface and cloud-based management features. Rosch says, "Norton Security will feel much more like a service and less like the software you used to 'set and forget'".
As it's cloud based it will be easy to add extra devices to your account. This also means it's backed by Symantec's threat intelligence network. The company is so confident in the level of protection offered by Norton Security that it will be offering a money-back 100 percent virus-free guarantee.
If you want to try out Norton Security ahead of its release a beta version is available to download now.
-

Traditional development practices don't work for mobile apps
Publié: août 15, 2014, 4:52pm CEST par Ian Barker

As IT teams face more demands from business units for new mobile applications they'll need to adopt practices that are different from traditional development techniques.
This is according to IT research company Gartner which says that users find it challenging to effectively describe what a mobile app needs to do and therefore the approach of sitting down with a business analyst to define requirements doesn't work.
Speaking at a presentation to IT leaders in China this month, Van Baker, research vice president at Gartner said, "There are several reasons these efforts don't succeed for mobile applications, even though they've worked historically. Firstly, mobile apps are a new category for most users and secondly, mobile apps are constrained by the nature of the platform and the size of the screen, so porting the workflow of a mature desktop app is not viable. Finally, the experience associated with mobile devices is significantly different from that of desktop devices, including shorter session lengths and limited presentation, due to screen size constraints that affect how mobile apps need to function".
Most complaints about mobile apps arise from bad user experience and this can be down to bad interface design, poor workflow or lack of responsiveness. To avoid this developers need to focus on the user experience and creating a flow that reflects the way users actually work.
"Letting the users experience what the application will look like and building the screens on the fly with the appropriate tools will ensure that the initial build of the app looks familiar to the users and is close to what they'll need once the application has been piloted or deployed", says Baker.
Testing is also a challenge for mobile developers as different devices and OS versions can behave in different ways. Testing on simulators is a start but the most popular devices need to be used too in order to reproduce real-world user experience.
The process doesn't end after an app is launched either. It needs to be monitored to see if user behaviors change and this puts added pressure on development teams. This is compounded by a more frequent release cycle.
According to Gartner a typical desktop app has an 18-month development time and may be maintained for five years, but Baker says, "Mobile apps are different. They need to be frequently revised to meet end-user expectations, and this agile development process especially requires operations to be on top of infrastructure and systems to support frequent mobile app deployments and pushed updates".
The pace of change in the mobile market seems unlikely to change in the near future so developers will need to learn to adapt. You can read more on the Gartner website.
Image Credit: Rafal Olechowski / Shutterstock
-

Silver surfing lessons can help fight dementia
Publié: août 15, 2014, 1:04pm CEST par Ian Barker

Encouraging the elderly to use the internet can not only help them keep in touch with friends and family and take advantage of the best deals, it can also reduce the likelihood of dementia.
The results of an eight-year study of 6,500 50-90 year-olds reveal that those who regularly go online experience less mental decline compared to those who don't use the internet. The study shows a significant improvement in delayed recall over time for those who were frequent online users, highlighting the role played by the internet in preventing the degeneration of mental abilities in the elderly.
Dr Tom Stevens, Consultant Psychiatrist at London Bridge Hospital says, "People over the age of 65 must remember the phrase 'use it or lose it', and the internet is a good way to ensure that older people are still able to use their mental faculties".
However, there is a need to educate older people about online dangers. Ben Williams, head of operations at open source ad control project AdBlock Plus warns, "...we mustn't forget that with more older people using the internet, they must be informed about the choices they have online. With no experience of online advertising, constant blinking banners and pop-up adverts could spoil the internet for them, making them think it is a tasteless and unmanageable jungle, and put them off the whole experience".
Older users are at more risk of being drawn into online scams and are likely to suffer more from the intrusiveness of ads such as pop-ups and banners that obscure their view and make it harder for them to use the internet effectively. Education is therefore an important factor in helping the elderly make the most of the internet and stay safe online.
Williams adds, "Plus, there are online risks that specifically target older users, such as phishing scams, or promotions of miraculous and discount medication, and low-cost insurance, and it is our responsibility to ensure that older people aren't ignorant about these. Basic lessons in how to stay safe and not put yourself in danger of online scams and viruses is essential".
You can read more about the study on the Journal of Gerentology website.
Photo Credit: Lighthunter/Shutterstock
-

Managed services boost efficiency and cut costs
Publié: août 15, 2014, 11:34am CEST par Ian Barker

Using managed services used to mean outsourcing complex IT projects to expensive consultants. Now though thanks to technologies like the cloud they're enabling businesses to focus on their core business while increasing their efficiency, reducing costs and taking advantage of new technologies.
Infrastructure as a service specialist GoGrid has compiled some industry findings that demonstrate the market opportunities and benefits companies can gain by using managed services.
Key points include a forecast that the global managed services market is expected to reach $256 billion by 2018 and is currently the fastest growing service segment. The findings also show that using managed services can increase overall efficiency by 50-60 percent and reduce recurring in-house IT costs by 30-40 percent.
In the long term they offer added flexibility and the ability to deliver predictable, measurable business results. You can view the findings in infographic form below.
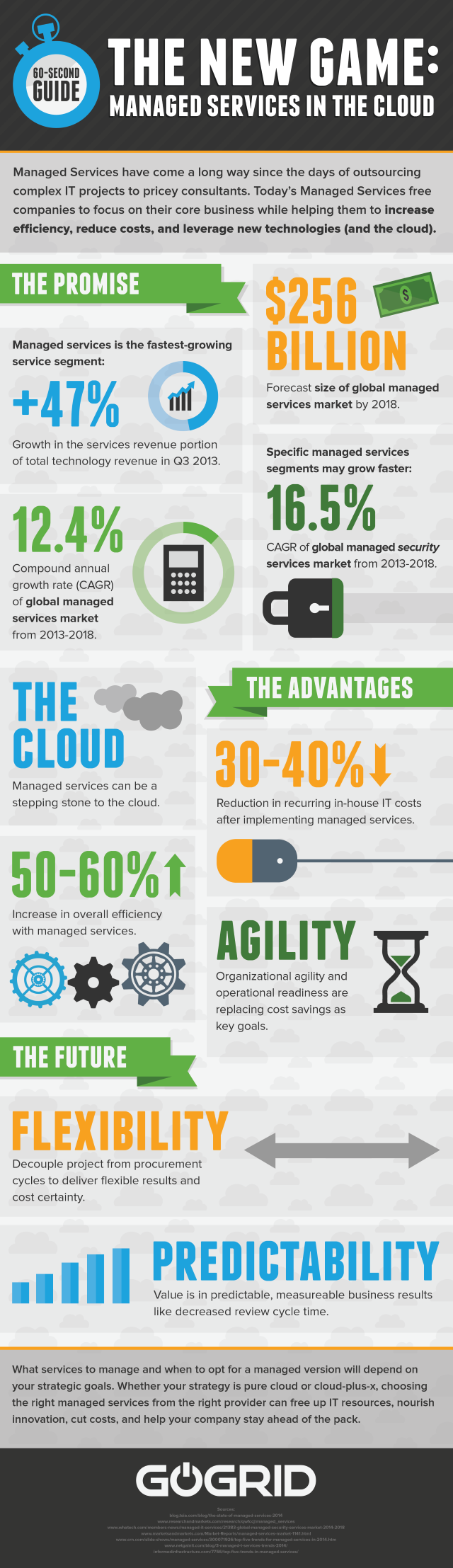
Image Credit: Peshkova / Shutterstock
-

Fast-PATH installer streamlines Hadoop deployments and reduces costs
Publié: août 14, 2014, 4:01pm CEST par Ian Barker

Though it's one of the most popular big data tools, Hadoop is still evolving and as a result doesn't always have the sophistication of more traditional databases, which can lead to higher support and operation costs.
A new product from big data security specialist Zettaset aims to streamline Hadoop deployment for the enterprise with software automation that eliminates many of the manual configuration processes.
Fast-PATH automates multiple Hadoop functions, including provisioning, installation, configuration, and testing of the software. As a result, cluster deployment can be achieved more rapidly, with much less IT intervention and associated cost.
"Hadoop and other Big Data technologies are complex and challenging to set up, sometimes generating large costs for support and maintenance. This is not a scalable model for customers who want to efficiently move Hadoop into production networks," says Jim Vogt CEO of Zettaset. "Fast-PATH provides Hadoop users with a powerful solution that accelerates time to deployment and simplifies ongoing management, without putting an unnecessary drain on limited IT resources. We believe this innovation will spur wider adoption of Hadoop and Big Data technology in medium-sized enterprises, as well as in IT organizations that are more highly resourced".
In benchmark tests the product is able to provision, install, configure and test 10 nodes in 45 minutes or 50 nodes in 140 minutes. This includes the installation of the Hadoop distribution, plus Kerberos, HBase, Hive, Encryption, Key Management, and patented High-Availability framework on all nodes.
Additional features of the Zettaset Orchestrator management platform include high availability with automated failover, strong security including data encryption, access control and policy enforcement, and activity monitoring for audit and compliance.
You can find out more about Orchestrator and Fast-PATH on the Zettaset website.
-

Intellectual property loss affects 21 percent of manufacturing businesses in the past year
Publié: août 14, 2014, 3:21pm CEST par Ian Barker

In ever more competitive global markets the success or failure of a business can rest on insights and solutions that allow it to operate more efficiently than its competitors.
If this information falls into the hands of a competitor advantage is lost. Yet the results of a new study by Kaspersky Lab show that one in five manufacturing businesses has suffered a loss of intellectual property in the last 12 months.
The main cause of this is malware, accounting for 23 percent of losses, but other factors including software vulnerabilities, theft of mobile devices and network intrusion were also given as the source of IP leaks.
Manufacturing industry understands the importance of this data. The survey finds that manufacturers ranked "Internal Operational Information" and "Intellectual Property" as the two types of non-financial data they fear losing the most. For businesses as a whole it’s customer and client information followed by financial details that have the highest fear of loss. But interestingly, manufacturers ranked the fear of losing customer and client information the lowest out of all business segments, possibly because manufacturing facilities are less likely to store this data in the first place.
This doesn't mean that financial services and ecommerce companies are immune to cybercrime. 48 percent of ecommerce businesses and 41 percent of financial organizations have reported losing some data to cybercrime in the past year. What's interesting is the pragmatic attitude they adopt to this, 52 percent of financial services businesses say they have a policy of reimbursing customers for cybercrime losses without investigation.
In addition 27 percent of businesses are willing to meet the costs of losses because they believe they'll be outweighed by the cost of protection. This is despite the fact that 82 percent of businesses say they'd stop dealing with a financial organization which suffered a breach.
You can read the full report into online fraud protection which also looks at what protection measures are being deployed, on the Kaspersky website.
Image Credit: Maksim Kabakou / Shutterstock
-

Clarizen delivers new collaboration features
Publié: août 14, 2014, 2:05pm CEST par Ian Barker

Work collaboration and project management specialist Clarizen's cloud based platform launched in its latest version, Clarizen v6, last year. Today it's announcing a number of enhancements many of which have been requested by customers.
Changes include new reporting, resource visualization, communication and usability enhancements. Charting changes include the introduction of bubble and scatter charts that can be shared inside and outside the organization. Bubble chart enables a "fourth dimension" with the x and y axis determining the plot location, point color, and the size of each plot point.
Action items can be created instantly from discussion posts using a hotkey. Resource Load view improvements allow users to more easily see the distribution of work among team members and redistribute tasks as required.
Personalized communication management allows users to receive daily digests of actionable items and shared ideas and these are now presented in a more user-friendly format. The five most popular discussions are picked out in a separate section so it's easy to keep up with the most critical threads. Users can also choose the time of day they want to receive the digest.
There's enhanced security too, the latest release gives admin users more options for password management, such as determining the number of authentication attempts, the lock out time length, password repetition options and more.
"Clarizen v6 was specifically created for the modern, real-time, multi-generational and ever-changing workplace. Our prime objective is to arm high-performance teams with the collaboration capabilities they need to drive their ideas to execution," says Avinoam Nowogrodski, Clarizen's founder and CEO. "Based on collaboration with our customers, Clarizen’s Summer Release is designed to improve team collaboration, project visibility and productivity, translating to increased business value for the enterprise".
You can read more information about the latest release on Clarizen's blog.
Photo Credit: Pressmaster/Shutterstock
-

Flash! Savior of the enterprise storage market?
Publié: août 14, 2014, 12:15pm CEST par Ian Barker

From being an expensive technology and something of a niche, flash storage is shifting into the mainstream, particularly in enterprises.
According to new research by IDC, although the technology has been available for a while, the adoption of flash-based storage is only now showing real growth thanks to falling prices and a growing familiarity with the benefits it offers.
As part of its biannual Storage User Demand Study, IDC conducted a survey of more than 1,000 storage administrators across the globe. It shows that whilst the pace of flash adoption is on the rise as more offerings appear from leading storage vendors, there are some factors -- notably price -- holding it back.
"There are still plenty of end users who believe they do not have the workload demands or budgetary appetite for flash-based storage systems," says Natalya Yezhkova, Research Director, Storage Systems at IDC. "However, we anticipate that the increasing availability of flash-based products across a broader range of use cases, combined with improved vendor messaging and falling component prices, will mitigate the biggest concerns to enabling even broader adoption of flash in the future".
In some cases the benefits of adopting flash storage won't justify the price premium. However, IDC also notes that there's a lack of suitable mechanisms for businesses to accurately compare the performance impact of flash and the long-term cost of operation.
"To overcome the concerns of these users, vendors and their channel partners need to not only keep the focus on the performance benefits of flash, but they also need to expand their messaging to include the secondary economic benefits it can provide as it is deployed in higher capacities," says IDC's Jeff Janukowicz, Research Director, Solid State Drive and Enabling Technologies.
The full report is available for purchase from the IDC website.
Image Credit: Eugene Kouzmenok/Shutterstock
-

myMail becomes most popular alternative email app for Android and iOS
Publié: août 13, 2014, 3:06pm CEST par Ian Barker

Despite the rise of other forms of communication, email remains one of the most popular options, particularly for business. No surprise then that there’s plenty of choice when it comes to mail apps for your mobile device.
According to data from app analytics company Distimo, the myMail app has passed other options to become the most popular alternative mail app for both Android and iOS, behind only Gmail and Yahoo Mail.
Since launching in November 2013, myMail has overtaken popular apps like Mailbox, Cloudmagic, and K-9 Mail, first taking the lead in iOS downloads in March. The latest figures show that the company's focus on design, usability, and mobile-centric email is paying off.
It's gained top position in many established markets including the USA, Canada, Germany, France, the UK, Brazil, Japan, India, Spain, Mexico and Australia. In India, Brazil, Mexico and others it has more than twice as many downloads as the next most popular mail app.
Dmitry Grishin, CEO and co-founder of Mail.Ru Group, maker of myMail, says, "The future of email is mobile, and we have worked hard to build an app and client that are ready for this future. To win the top two mobile platforms worldwide so quickly and in such a decisive way proves that we're moving in the right direction. We firmly believe that smartphones and tablets are the preferred platform for email, and we're aiming to deliver the best possible experience for our users and anyone who wants a sophisticated yet simple way to manage their inbox".
Designed to appeal to both casual and power mobile email users, myMail can manage messages in Gmail, Hotmail, Live, Outlook, MSN, iCloud, AOL, Yahoo mail and my.com accounts, and it supports all IMAP and POP3-enabled mailboxes.
You can find out more on the myMail website or download the app from the Google Play or Apple App Store.
-

It's a cyber stick-up -- state of infection report reveals rise in ransomware
Publié: août 13, 2014, 3:03pm CEST par Ian Barker

Ransomware is on the rise according the the latest report from enterprise threat protection specialist Damballa, with an increase in average daily infections of the Kovter infection of 153 percent between April and May this year.
Kovter is "police ransomware" that displays fake legal warnings about pornography. At its peak of activity in June it was recording almost 44,000 infections per day. But while Kovter was thriving CryptoLocker was dealt a blow by the taking down of the GameOver Zeus botnet.
The report heralds the taking down of GoZ as a new era for cyber security and partnerships between public and private enterprises, but points out that the industry can’t be complacent. Already new variants of GoZ are appearing in an attempt to re-establish the botnet.
The report also looks at infection rates for enterprises and reveals that the size of an organization has no bearing on number of malware infections. In the second quarter of 2014 Damballa saw enterprises with 200,000+ devices experience only a handful of infections and those with under 600 devices have alarmingly high numbers of infections -- and everywhere in between.
On any given day the proportion of active infected devices ranged from 0.1 percent to 18.5 percent which in a large company could mean thousands of infected devices. But as the report points out, "Advanced malware is designed to be evasive. It may stop communicating to its Command & Control server at any time. That's why it's critical to observe a device’s activity over time to compile definitive of infections. If you rely on security prevention controls that only watch the attack vector, you can miss some criminal activity altogether".
You can access the full report in PDF form on the Damballa website and there's a summary of its ransomware findings in infographic format below.

Image Credit: Carlos Amarillo / Shutterstock
-

How effective is security software at blocking exploits?
Publié: août 12, 2014, 4:21pm CEST par Ian Barker

Much of the malware in circulation now focuses on using exploits in popular applications such as browsers and office packages in order to remotely execute code. Security suites and specialized anti-exploit tools are aimed at blocking these but how well do they work?
A new study by testing lab PCSL commissioned by Malwarebytes has set out to find the answer. It looks at the exploit mitigation capabilities of 12 different products: Avast Internet Security, AVG Internet Security, Bitdefender Internet Security, Enhanced Mitigation Experience Toolkit from Microsoft, ESET Smart Security, HitmanPro.Alert3, Kaspersky Internet Security, Malwarebytes Anti-Exploit Premium, McAfee Internet Security, Norton Internet Security, Panda Internet Security and Trend Micro Titanium Maximum Security.
Each product was tested against 58 different exploit samples in a range of payload configurations. Only two products managed to block more than 80 percent, Norton on 81.03 and Malwarebytes on 93.10 -- we should point out here that although Malwarebytes commissioned the research it didn't select the samples used.
In the mid range, ranked as "inadequate" by PCSL, Microsoft EMET scored 74.14 percent, Kaspersky 72.41 equal with Avast, and ESET scored 70.69.
The remainder of the products scored under 60 percent and were therefore classed as "failed". Lowest score came from AVG which blocked only 24.14 percent of the samples. McAfee and Panda both managed 29.31 percent, Bitdefender 31.03, Trend Micro 48.28 and HitmanPro 58.62.
Protecting against exploits is of course partly about keeping all of your software up to date as well as using security tools but even so these results are revealing. If you want to read more detail of the tests the full report is available to download as a PDF.
Photo Credit: Archiwiz/Shutterstock
-

Secret shopper test reveals the effectiveness of CRM
Publié: août 12, 2014, 3:12pm CEST par Ian Barker

Recent figures from Gartner put the value of the CRM software market at $20.4 billion. But does it really make a difference when it comes to converting leads into sales?
Sales software specialist Velocify has been trying to find out by using secret shoppers to submit requests through online contact forms to see how quickly companies would respond. The companies included in the study were picked from the customer section of CRM vendors' websites.
The results show that companies using sales CRM solutions sent email responses three times as fast as Fortune 100 companies and were nearly twice as fast to call up inquiring buyers. Even so only 20 percent of sales CRM users followed optimal contact strategy by calling prospects within an hour of their inquiry, while 35 percent sent an email within this timeframe.
Less than 60 percent of inquiring buyers received at least one phone call and one email, and the average wait time for a callback was two days. It also found that tech companies performed 40 percent better than non-tech companies in following optimal contact strategies.
Users of Salesforce scored higher compared to those of other CRM solutions with over 30 percent scoring 60 or more on a 100 point scale measuring lead response, compared to only 6 percent of companies using other packages.
All of this suggests that while CRM helps companies to respond many could do so more effectively. The report concludes, "Ultimately, companies purchase CRM systems in order to build lasting relationships with their customers. At the beginning of any relationship is a first impression. Potential buyers expect to hear back from companies in a timely manner and with appropriate persistence. When these expectations are not met, sellers inadvertently send the wrong message about their interest in the buyer and ultimately damage their brand perception and revenue potential. Having the proper lead response strategy not only helps companies convert more prospects into customers, it gives buyers a positive first impression that is at the foundation of a long and mutually beneficial relationship between buyer and seller".
You can find out more and request a copy of the report on the Velocify website.
Photo Credit: Mikko Lemola / Shutterstock
-

Computrace back door could make millions of PCs vulnerable
Publié: août 12, 2014, 1:06pm CEST par Ian Barker

Almost all recent PCs have Absolute Computrace embedded in their BIOS. It's a product designed to allow companies to track and secure all of their PCs from a single cloud-based console.
But researchers at Kaspersky lab have revealed that it often runs without user-consent, persistently activates itself at system boot, and can be exploited to perform various attacks and to take complete control of an affected machine.
Kaspersky Lab researchers Vitaly Kamluk and Sergey Belov along with Annibal Sacco of Core Security demonstrated the flaw in a presentation at the Black Hat 2014 conference.
Kamluk first described Comutrace's vulnerability at a Kaspersky Security Analyst Summit in February, "The software is extremely flexible. It's a tiny piece of code which is a part of the BIOS. As far as it is a piece of the BIOS, it is not very easy to update the software as often. So they made it very extensible. It can do nearly anything. It can run every type of code. You can do to the system whatever you want. Considering that the software is running on these local system privileges, you have full access to the machine. You can wipe the machine, you can monitor it, you can look through the webcam, you can actually copy any files, you can start new processes. You can do absolutely anything".
Six months on Computrace is still exploitable and once it has been activated it's very persistent and difficult to turn off. It also doesn’t enforce encryption when it communicates and doesn't verify the identity of servers from which it receives commands, so could expose users to attacks.
The mystery is, who or what is activating Computrace? The researchers believe it may be down to manufacturers' testing of new machines to check for Computrace compatibility. Because it's a legitimate piece of code it's white listed by many antivirus programs.
They conclude that whilst there's no reason to believe Absolute Software or PC manufacturers are deliberately activating Computrace in secret, they do need to notify users of its presence and issue instructions on how to turn it off if users don't want Absolute's services.
Image Credit: Spectral-Design / Shutterstock
-

Platform9 launches self-service private cloud
Publié: août 12, 2014, 11:59am CEST par Ian Barker

Today's IT managers are under pressure to deliver the sort of agility that's offered by the public cloud but with the security and cost benefits of using existing infrastructure.
California-based startup Platform9 has today unveiled an answer to this problem with its SaaS platform that transforms an organization's existing servers into an AWS-like agile, self-service private cloud within minutes. It significantly reduces the operational complexity for IT and offers a single point of management for Docker, KVM and VMware vSphere.
"We founded Platform9 because as early engineers at VMware, we observed how customers were struggling to achieve AWS-like efficiency with increasingly archaic management software," says Sirish Raghuram, co-founder and CEO of Platform9. "We believe that just like SaaS revolutionized the world of enterprise applications, it can do the same for enterprise datacenters. You can think of us as the Salesforce.com of private cloud management. Our customers come to our web site, sign up and transform their existing infrastructure into a private cloud within minutes. From there on, they can focus on using their infrastructure rather than babysitting the management software".
Because it's cloud-managed Platform9 means there’s no complex management software to configure and it offers a "single pane of glass" interface across infrastructures, locations and datacenters.
Existing servers and workloads can be imported with minimum disruption and Platform9 can pool together servers and storage to provide optimal hardware configuration and control use of resources.
For developers it offers UI and API-based access and is OpenStack compliant. It also makes collaboration between team members and across different teams easy and intuitive with native support for the creation of shared environments.
Platform9 is currently in beta with a dozen medium to large organizations. You can find out more and sign up for a free trial by visiting the company's website it will also be on display at the VMWare conference taking place later this month in San Francisco.
Image Credit: Bedrin / Shutterstock
-

IT professionals lack confidence in managing compliance
Publié: août 11, 2014, 4:18pm CEST par Ian Barker

Companies operating in industries like healthcare, financial services and retail inevitably come in for a hard time if they don’t take good care of their data.
Yet a new survey by Dimensional Research for Dell Software shows the rather startling result that almost all of the IT professionals surveys in these industries lack confidence in their organizations' ability to manage governance, risk and compliance.
Among the key findings of the study are that some 93 percent of respondents are concerned about their ability to prevent unauthorized changes being made and 83 percent believe their organization's security would be improved if the security and compliance teams worked more closely together and shared more information.
One of the main concerns is unauthorized access to data with 94 percent having worries divided between both internal and external access. 61 percent are concerned about both, 22 percent about internal access by employees and consultants and 11 percent about external access.
On compliance only 11 percent say they're "very confident" that they're capturing all of the data necessary and a third said they had no consistent process for adding new regulatory data as required. Less than 50 percent of the organizations surveyed proactively review, add or remove data sources that is no longer required -- putting these organizations at a much higher risk of security threats even though they may believe they are compliant and secure.
When it comes to improving the situation only 57 percent say that their security and compliance teams work together and only 14 percent say they share data all the time. No surprise then that 83 percent believe security and compliance would be improved by closer collaboration.
The survey talked to more than 200 individuals with responsibility for compliance in organizations with over 2,000 employees. You can read more in a white paper available on the Dell site.
Image Credit: donskarpo / Shutterstock
-

Bring your own ID to simplify access to systems
Publié: août 8, 2014, 1:19pm CEST par Ian Barker

One of the problems with relying on technology for so many things is that you end up with a whole raft of user IDs, for work, banking, shopping, social media and more.
A new study by the Ponemon Institute and IT management specialist CA Technologies looks at the idea of simplifying things through the use of Bring Your Own Identity (BYOID) initiatives, where social networking or digital IDs are used for application login.
"In today's application-driven economy, access to applications has to be simple and secure. BYOID is an increasingly popular option for simplifying access. It can reduce the need to create new accounts for every site, which leads to registration fatigue and abandoned shopping carts," says Martin Ashall, Chief Technology Officer at CA Technologies, UK. "We are working to make sure we enhance BYOID security without adding friction or complexity".
Although BYOID use is still in its early stages there's strong interest from businesses, particularly those which engage with customers via the web and mobile devices. But there's a difference in perception of its value between IT and business users.
70 percent of IT and 38 percent of business users in the study agreed that an important reason for BYOID adoption in their organisation was to strengthen the authentication process. However, business users place greater emphasis on improving the customer experience and increasing marketing effectiveness.
When asked about the social ID that was of most interest to their organization, IT users ranked PayPal as their preferred identity provider. For business users though Amazon edged out PayPal and Microsoft. When asked what social ID respondents preferred as a consumer, Google was highest ranked among both IT users and business users.
"A holistic examination of the attitudes uncovered in the research show two clear views of identity," says Dr. Larry Ponemon, chairman and founder of the Ponemon Institute. "IT continues to take a traditional risk-based, security view of dealing with identities, while the business side takes a more value-based, customer-centric view of identity. In order to gain the most value from any BYOID initiative, these two groups must collaborate and become allies for secure business growth".
The full report is available on the CA website and there's a summary of its findings in infographic form below.
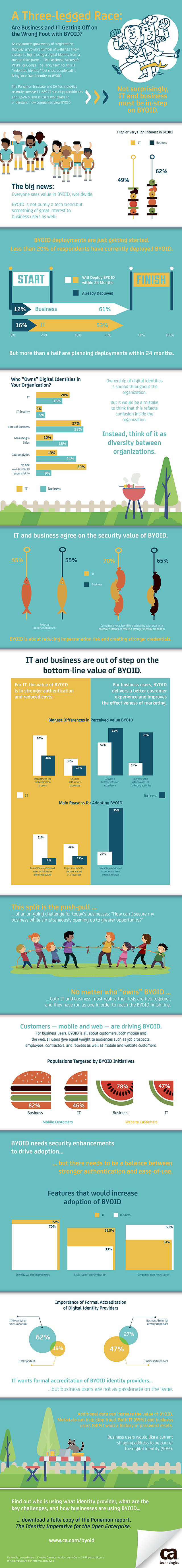
Image Credit: Gunnar Pippel/Shutterstock
-

What to expect on August's Patch Tuesday
Publié: août 8, 2014, 11:58am CEST par Ian Barker

As all Windows users will know, the second Tuesday in each month means it's patch time. So that system admins don’t get caught out Microsoft has published its advanced notification ahead of August's Patch Tuesday.
So what can we expect to see in this round of updates? There are nine bulletins in total for software including Internet Explorer, Windows and Office. Two are rated "critical" as they allow for remote code execution.
Bulletin 1 is the most important as it affects all versions of Internet Explorer from 6 up to 11. Wolfgang Kandek CTO of network security company Qualys writing on his company's blog says, "Since browsers are the attackers favorite targets, this patch should be top of your list. An attacker would exploit this vulnerability on your users through a malicious webpage. These pages can be on sites that are either set up specifically for this purpose, requiring him or her to attract your users to the site or are on sites that are already under control of the attacker with an established user community, such as blogs and forums".
The second critical bulletin is for Windows 7 and 8 plus the Media Center pack for Vista. Kandek believes it addresses a problem in the graphics processing pipeline that could trigger a vulnerability via a malicious web page.
Other bulletins in this round address a file format vulnerability in Office 2007's OneNote application, elevation of privilege vulnerabilities in SQL Server and Windows, a SharePoint Server 2013 issue, and security feature bypass problems in .NET and Windows.
Microsoft also provided some details of a new Internet Explorer capability that allows the browser to block out of date ActiveX controls. This works with IE versions from 8 through 11, initially it's focused on outdated Java versions but will no doubt be extended to other controls in the future.
Image Credit: alexskopje / Shutterstock
-

Only 39 percent of companies have a BYOD policy
Publié: août 7, 2014, 3:40pm CEST par Ian Barker

It seems that allowing employees to use their own devices is an inevitable trend for most businesses. Yet a new survey by Software Advice finds that only 39 percent of workplaces have policies in place to cope with BYOD.
Businesses need to deal with the risks that BYOD brings. This includes the loss of visibility once company data is transferred to a personal device, privacy and legal concerns and the threat that devices could be compromised.
Over half of respondents to the survey said they'd transferred company files to their own devices, 35 percent said they never transferred anything sensitive, but may well be deciding what "sensitive" means for themselves.
When it comes to keeping devices patched, only 49 percent said that they implemented security updates when they were released. A worrying 11 percent say they never install updates.
Software Advice recommends that a BYOD policy should ensure devices are protected by a password and that these must be of minimum length. It should also bar the downloading of apps other than from an approved list.
Mobile device management (MDM) solutions can add an extra layer of protection beyond BYOD policy by enabling password rules to be enforced and devices to be remotely wiped in the event of problems.
It's important to note that mobile devices pose less of a risk than PCs. Rick Doten of enterprise mobility firm DMI Inc says, "Mobile users won’t 'infect' a network like a PC can. There isn't a concept of mobile 'malware,' it's really only malicious apps that access data on the phone (which you unknowingly allow it to), or features on the phone, like your microphone or camera".
The malware risk from PCs is greater since they're often used for handling more sensitive data. Doten says that a virtual desktop may be the best solution for BYOD users, "It provides the user with a virtual environment that keeps all data on the server, and the user interacts with it like a mainframe. Nothing is stored on the user’s device, and the session is gone when they log out".
You can read the full report and recommendations on Software Advice's Intelligent Defense blog.
Photo credit: Alessandro Colle/Shutterstock
-

Technology knowledge -- it's all downhill after you're 14
Publié: août 7, 2014, 11:34am CEST par Ian Barker

A new study by the UK's communications regulator Ofcom finds that the "millennium generation" of 14-15 year olds are the most technology aware group but as we get older digital knowledge begins to decline.
The study of 2,000 adults and 800 children measured confidence and knowledge of communications technology to calculate a Digital Quotient (DQ) with the average UK adult scoring 100.
Today's 14 year olds have a DQ of 113 and are the first generation to have grown up with the benefits of broadband, probably never knowing the pleasures of dial-up internet. People in their 40s have a DQ in the high 90s, around the same as a modern six-year-old. Over 70s score a DQ in the 80s. You can try this out for yourself and see how you compare with a quick three minute taster test.
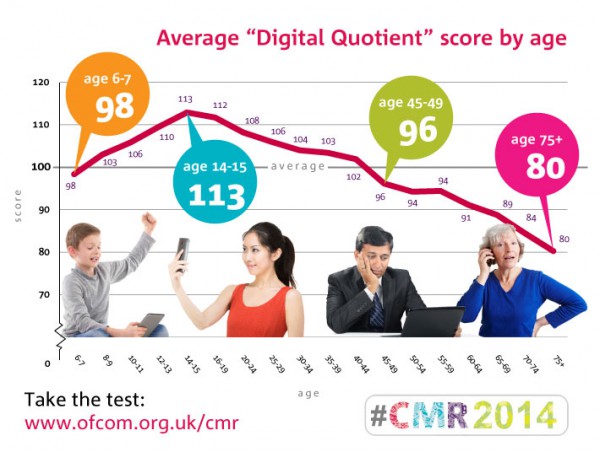
These differences manifest themselves in various ways. Most communication by 12-15 year olds for example is by text (94 percent) with just three percent spent on voice calls. By contrast adults spend 20 percent of their communications time on the phone and 33 percent on email.
At all age groups we're communicating more than ever. An average UK adult now spends more time using media or communications (8 hours 41 minutes) than they do sleeping (8 hours 21 minutes -- the UK average). It's the 16-24 group who spend the most time on media and communications. They manage to cram over 14 hours of media and communications activity into 9 hours 8 minutes each day by multi-tasking, using different media and devices at the same time.
Device use is shifting away from the PC with 44 percent of surveyed households now owning a tablet, up from 24 percent last year. This applies across age groups with 28 percent of over 55s owning a tablet and many saying it's their main computing device.
Despite our love of digital technology though we're reluctant to give up our physical media. Books were owned by 84 percent of UK adults in April 2014, down from 93 percent in 2005. 80 percent have DVDs (down from 81 percent) with music CDs showing the biggest decline, 79 percent this year, down from 92 percent. The average size of a book collection fell by three books to 86 per person, while the average size of a music CD collection declined by six CDs to 84. Age makes a big difference here though, 16-24 year olds are much less likely to own CDs whereas 90 percent of 45 to 55s have them.
You can find out more about the results of the survey on the Ofcom website.
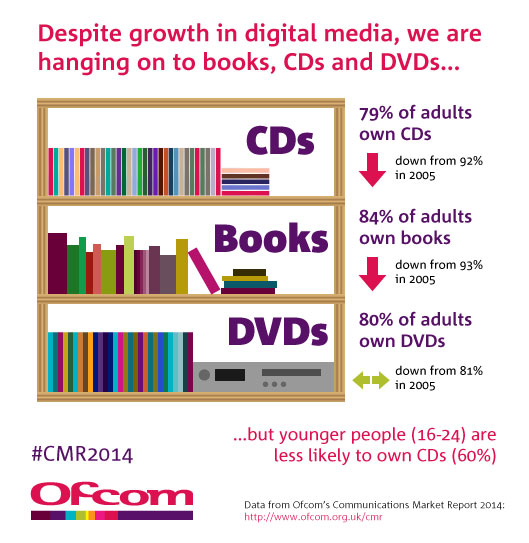
Photo Credit: Pressmaster / Shutterstock
-

Geo-location marketing helps brands engage with customers
Publié: août 6, 2014, 3:40pm CEST par Ian Barker

A recent report by Juniper on mobile ad spending estimated that it’s set to reach $40 billion a year by 2018. It's easy to understand why since the data it's possible to collect from a mobile device is valuable to marketers.
In a move to unlock this information media analytics company Visible Technologies has announced a new set of geo-location capabilities for its Visible Intelligence platform that give marketers the power to pinpoint specific locations of consumer social media posts anywhere in the world.
"The popularity of mobile devices for social media has significantly increased the amount of social data available to marketers. This data presents a new opportunity to understand and reach specific consumer audiences and evaluate markets with Visible's geo-location capabilities," says Richard Pasewark, CEO of Visible Technologies. "Global brands can use these types of insights to assess the voice of a customer at a specific location, analyze marketing impact, and make decisions on spend and consumer engagement".
The data can be used to target offers to active audience members in precise locations, allowing marketers to, for example, differentiate between locals and tourists to deliver appropriate messages.
Other capabilities in the platform include "Sticky Dates" which allow users to quickly change time periods for social media measurement with one click, including the flexibility to override the entire dashboard using named campaign or calendar dates. It also now scales to support large exports of 10,000 to 20,000 sites or authors at a time to allow deeper analysis to be carried out and help marketers report on larger sets of data.
You can get more details of Visible Intelligence and the insights it can provide on the company's website.
Image Credit: Tashatuvango / Shutterstock
-

Most businesses don’t have an enterprise-led mobile strategy
Publié: août 6, 2014, 2:07pm CEST par Ian Barker

The boom in numbers of mobile devices offers an opportunity for enterprises to change the way they do business, but a majority are failing to take advantage.
A new white paper produced by IDC and sponsored by enterprise mobility specialist Kony looks at how companies are using mobile technology to boost their business.
Based on a survey of over 400 IT decision makers, its findings show that companies that make enterprise-led strategic investments in mobility are getting higher levels of meaningful business benefits than those that have a business unit-led or departmental-led mobile approach. However, only 16 percent of companies take a clear, enterprise-led approach to mobility. Yet, 93 percent of companies with such an approach rated their success with mobile deployments higher than those using other approaches.
Around half of organizations using a mobile solution said it gave them key benefits including: smarter, faster decision making, improved organizational efficiency, cost savings, better customer interaction and increased revenue.
Only 41 percent of companies have an ongoing enterprise-wide mobile budget. These companies also have the highest mobile budgets, which tends to provide for strategic investments in mobile staff or to augment resources with outside support. 31 percent of companies have a comprehensive mobile technical staff augmented with external support and another 30 percent have a mobile development/architect group.
On the challenges of implementing mobile, almost 40 percent of respondents cite security and compliance issues as the biggest issue.
"With the number of mobile applications downloaded from app stores expected to increase by a 31.7 percent CAGR by 2017, enterprises are realizing that a mobile strategy is no longer a nice-to-have but a must have," says Thomas E. Hogan, chief executive officer of Kony Inc. "But bringing the goals of IT and the business into proper alignment is difficult when it comes to a mobile strategy. The results of the survey are further proof that those organizations that practice a mobile-first business model will improve business performance while engaging customers, business partners, and employees in new ways. Developing a clear mobile strategy is not something enterprises can ignore any longer".
More information and the full report is available on the Kony website.
Image Credit: Sergey Nivens / Shutterstock
-

Content Raven adds control and security to Google Drive
Publié: août 6, 2014, 12:47pm CEST par Ian Barker

Storing data in the cloud is convenient and makes for easy sharing and collaboration but it inevitably raises security concerns, especially when using public services.
Content Raven produces a cloud-based file distribution toolkit which adds an extra layer to provide content control, security and deep analytics to files stored in the cloud. It already integrates with Box and Dropbox but from today adds support for Google Drive too.
It allows users to protect, control and track all common file types shared online, including images, videos and PDFs. Using Content Raven with Google Drive can address security concerns by adding watermarks to files and videos. Users can also place limits on file viewing, printing and forwarding and get engagement and activity analytics. It can be used to prevent unauthorized access to data and stop screenshot taking, credential sharing, and other data leakage risks.
"The addition of Google Drive to our existing list of vendor integrations will further Content Raven’s market position as a leading value added service for file sharing platforms," says Ronald Matros, CEO of Content Raven. "Seamless integration with partners such as Content Raven will be an indispensable asset to file sharing vendors looking to combat commoditization, as well as enterprises looking to prevent data leaks and improve analytical tracking capabilities".
Google Drive users can start a free 21-day trial by downloading Content Raven from the Chrome Web Store. Once installed Google Drive users can simply right click a file and select Protect and Track with Content Raven.
Pricing options for teams and enterprises are available on the Content Raven website.
Photo Credit: Slavoljub Pantelic / Shutterstock
-

Get out of jail free card for Cryptolocker victims
Publié: août 6, 2014, 12:00pm CEST par Ian Barker

The Cryptolocker ransomware has had something of a checkered history, from the news that its GameOver Zeus botnet had been taken down by the authorities to a new strain of the malware appearing in June, it's seldom been out of the news this year.
Now though the story has taken a new twist and victims of the malware -- estimated at around 500,000 people -- can recover their encrypted files without the need to pay a ransom.
Security companies Fox-IT and FireEye which were involved in the effort to take down GameOver Zeus have created a tool to decrypt files locked up by Cryptolocker.
The companies have set up a Decrypt Cryptolocker online portal to provide the private key required so files can be unlocked for free. Users need to upload a file to the site and will receive a key and a link to download a decryption tool. Running the tool on their system with the key provided will unlock the files.
There's no need to register or provide any contact information beyond an email address though users are advised to submit a file that doesn't contain personal information.
"We are excited to work with Fox-IT to offer a free resource that can help thousands of businesses affected by the spread of CryptoLocker over the last few months," says Darien Kindlund, director of threat intelligence at FireEye. "No matter the type of cyber breach that a business is impacted by, it is our goal to resolve them and get organizations back to normal operations as quickly as possible".
Image Credit: albund / Shutterstock
-

The hidden security risks of popular apps
Publié: août 6, 2014, 11:23am CEST par Ian Barker

As we rely more and more on mobile devices and an increasing number of businesses adopt BYOD strategies, security and privacy risks become a greater concern.
A new report by risk management specialist Appthority looks at the hidden risks presented by the 400 most popular iOS and Android apps. It identifies the ten most risky behaviors that threaten enterprise security, at least one of which is found in 99 percent of popular free apps.
According to the study which tested 100 free and 100 paid apps for each operating system, paid apps are safer but not by much. 78 percent of the top paid Android apps and 87 percent of the top paid iOS apps have at least one risky behavior. Risks include location tracking, used by 82 percent of top free Android apps and 50 percent of top free iOS apps.
Accessing the user's ID is carried out by 88 percent of free and 65 percent of paid Android apps but only 57 percent of free and 28 percent of paid iOS apps.
Risky behaviors are on the increase too with 71 percent of free Android apps sharing data with advertising networks, up from 58 percent earlier this year. In-app purchases are another concern with 58 percent of free Android and 55 percent of free iOS apps allowing them.
"As enterprises navigate how best to leverage the power of 'mobile' they have to confront the fact that user data and corporate data live side-by-side on mobile devices. Many mobile apps collect and share sensitive personal and corporate data without the user even being aware," says Domingo Guerra, president and co-founder of Appthority. "The first step toward mitigating this risk is to have full visibility into what risky behaviors are hidden in mobile apps, so that you can design acceptable use policies that protect your organization".
The report also highlights the fact that there are 85 developers behind the top 100 apps, making it harder for companies to keep control by sourcing their software from just a few trusted companies. On a more positive note it finds that malware infects only 0.4 percent of mobile apps and wasn't present in any of the top 400.
The full report is available to download from the Appthority website.
Image Credit: logolord / Shutterstock
-

Intronis automates Bare Metal Restore for faster recovery
Publié: août 4, 2014, 12:35pm CEST par Ian Barker

Backup specialist Intronis has announced that it’s integrating Bare Metal Restore into its ECHOplatform for small and medium businesses, which offers a flat-fee unlimited cloud and local storage pricing model.
The BMR functionality offers complete physical-to-physical (P2P) bare metal recovery and physical-to-virtual (P2V) BMR recovery options for greater flexibility and performance. Available at no extra charge to Intronis channel partners it allows recovery back to the original system or to a replacement machine.
It's also possible to recover to a specific point in time to overcome corruption or malware issues. Physical images can be restored to virtual drives or virtual machines and recovered images can be mounted as a drive to carry out individual file restores.
"By integrating BMR right into the Intronis ECHOplatform and U2 pricing plan, we’re taking away the headache and added expense channel partners bear in having to 'rebuild, restore, reboot,'" says Chuck DeLouis, vice president of product management at Intronis. "With our BMR solution channel partners have access to a much simpler, highly-automated complete recovery process that virtually eliminates configuration errors, reduces expenses, and speeds recovery time".
The ECHOplatform delivers a secure, scalable, and comprehensive cloud backup and data recovery solution -- supporting a variety of in-demand services, plug-ins, and extensions such as physical imaging, VMware and Hyper-V, as well as SQL and Exchange backup.
At the same time the U2 Plan simplifies pricing for channel partners by offering unlimited cloud and unlimited local storage at a fixed monthly cost. Neal Bradbury, Intronis' vice president, channel development says, "Add to the mix our new partner enablement resources and it's easy to see how Intronis is helping our channel partners better market, sell, and support best-in-class cloud backup and data protection solutions that are simple, secure, and can easily scale to meet the needs of their clients".
You can find out more about the ECHOplatform backup and recovery solutions on the company's website.
Image Credit: Oleksiy Mark / Shutterstock
-

BiTMICRO launches high capacity SSDs for the enterprise
Publié: août 4, 2014, 11:17am CEST par Ian Barker

The way that many enterprises use data places heavy demands on storage, both in terms of capacity and performance. Whilst SSDs can solve the performance issue they don’t always offer the capacity required.
California-based BiTMICRO is a pioneer of SSDs having been involved with them since 1999. With the launch of its new MAXio E-Series PCIe drives it's aiming to deliver capacity, performance and reliability for companies that need to support high volume application workloads.
Based on the company's Talino ASIC Architecture the drives offer high capacity with a starting point of 1.5TB which is higher than most competitors. They also ensure integrity of the data with full Data Path Protection technology, from the moment data arrives at the host interface until it's stored on the NAND flash chips.
The range is aimed at enterprise applications with heavy load demands including video-on-demand, video streaming, online transaction processing, non-linear editing, gaming, file servers, web applications and cloud services.
"For years we have proven the value of our SSD technology in high-demand military and industrial computing environments such as air and space, military systems and mobile industrial solutions," says Zophar Sante, Vice President of Worldwide Marketing and Sales at BiTMICRO. "Now we are bringing this expertise to enterprise and mid-market customers. With MAXio E-Series SSDs, organizations of every size can achieve faster storage performance, greater reliability and true business availability".
Features of the drives include dynamic wear leveling to maximize the life of the flash drive’s chips for up to five years, protection of data at the firmware level for minimum overhead, and easy to use management software allowing users to optimize drive settings.
The MAXio E-Series is available now in capacities from 1.5 to 6TB, C-Series models with capacities up to 12TB will be available next year. For more information on the range you can visit the BiTMICRO website.
-

Refresh app helps build stronger sales relationships
Publié: août 1, 2014, 1:37pm CEST par Ian Barker
The sales process is all about making effective connections with customers and potential customers, so any tool that can help with that process will make meetings run more smoothly and profitably.
A new web app and iOS app from Refresh is aimed at giving sales staff deeper insight into their contacts. The app syncs to the sales person’s calendar to provide instant information on the people they’re meeting.
It works by analyzing data from more than 100 sources around the web, including Twitter, LinkedIn, Facebook, Yelp, Google+, Instagram and Foursquare. It then collates this public information into a handy guide to help make the most out of business meetings, interviews and conversations.
"At Refresh, we’re focused on creating a tool that helps everybody build stronger relationships, and in the past few months, we've used data to understand what's critical for connecting and making conversation," says Bhavin Shah, CEO and Co-Founder at Refresh. "With that information, we took an informed position on which details are the most critical to know. We reorganized our insights to prioritize what's most useful, while also making it easier for users to find specific facts to build trust and rapport".
The apps offer the ability to provide context by revealing shared interests and multiple connections, push notifications to deliver the right information before a meeting, and the ability to take notes linked to an individual's profile.
New features include delivering recent news about people and companies, email notifications, and more powerful and visually-focused details with logos, faces and icons.
You can find out more and try out the beta version of the web app on the Refresh website. It's only web and iOS at the moment but there's an Android version in the pipeline.
-

Enterprise mobile spending expected to grow more than 50 percent
Publié: août 1, 2014, 12:00pm CEST par Ian Barker

There has been rapid growth in the number of mobile devices attached to corporate systems in recent years and this shows no signs of slowing down.
A new survey sponsored by Oracle shows that not only are enterprises more committed to mobility, but that the rate of development, deployment and spending for support of mobile applications and devices is set to increase dramatically.
Mobile related expenditure is set to receive a 54 percent boost over the next two years. Average IT department spending per device, per employee is expected to grow to $242 from $157 today.
But while the survey reveals a high commitment to mobility, it also shows little consensus about methods of mobile development and deployment. 44 percent of respondents indicated that their app portfolio is internally developed. However, cloud technologies like platform-as-a-service were seen as important by 75 percent.
The survey also shows that there are increasing concerns from IT executives over mobile security and integration with back-end systems. The results reveal that 29 percent of IT development time is spent on front-end mobile app development, but more than 70 percent is spent on integration, security, quality assurance testing and design work.
Security is the top concern and 93 percent of respondents cited worries over data loss and other security breaches related to mobile devices with BYOD. As a result organizations are turning to centralized management solutions, respondents say that in the next two years they'll be focusing more on device data encryption, centralized updating and troubleshooting, remote wiping of data and locking down of features.
"Mobility has been ubiquitous for a while but only 10 percent of enterprises have an enterprise wide deployment of mobile. Its impact and importance are gaining importance today. This survey is reassuring in that enterprises see potential for great payoff from making a strong mobile commitment. They are recognizing that mobile applications provide a new way to develop and maintain relationships with customers," says Suhas Uliyar, Vice President, Mobile Strategy & Product Management at Oracle. "Oracle's mobile solutions allow organizations to develop, connect and secure their own mobile applications. Our comprehensive mobile strategy simplifies enterprise mobility for any organization."
The full survey report is available from Oracle's website.
Photo Credit: 3Dstock / Shutterstock
-

Jitterbit connects SAP to the cloud
Publié: juillet 30, 2014, 3:11pm CEST par Ian Barker

SAP is the world's most popular ERP (enterprise resource planning) system, but a recent survey by HCL Technologies shows that integration with their existing solutions was the biggest obstacle to 45 percent of SAP users when implementing cloud technologies.
Integration company Jitterbit has announced a new SAP Connector that lets businesses integrate their existing processes with SAP whether they're on-site or in the cloud. Certified by SAP and running on Jitterbit's Harmony cloud platform it offers faster integration and is compatible with SAP's latest HANA in memory appliance.
"Businesses are clamoring to bring on new cloud technologies, but integrating them with existing solutions and on-premise systems in an efficient and secure manner has proved to be an enormous headache," says Jitterbit Vice President of Marketing and Business Development Andrew Leigh. "The Harmony SAP Connector will empower companies to embrace new technologies and realize amplified value from their existing applications by offering the only integration solution delivered on a unified cloud platform, which is both easy to use and quick to get up and running."
The new Connector is optimized for SAP customers operating in specific industries, including manufacturing, retail, automotive, and energy. It allows companies in these sectors to streamline critical business processes like customer service and field service, breaking down departmental barriers across the organization. Businesses will also be able to get increased value from their back-office SAP systems by connecting them with new technologies that make use of cloud, mobile, and social media innovations, as well as the internet of things.
It's the only integration tool for SAP that runs on a unified, multi-tenant cloud platform, allowing customers the agility, speed and support that the cloud offers. It also offers a graphical interface which means business users can set up and manage connections without the need for specialist API support.
You can find out more on the Jitterbit website.
Photo Credit: Vallepu / Shutterstock
-

Internet of Things devices open up new avenues for hackers
Publié: juillet 30, 2014, 12:30pm CEST par Ian Barker

We're constantly being told that the internet of things is set to revolutionize the world we live in. Gartner has predicted that it will have around 26 billion units by 2020, but with this rapid growth comes added risk.
A new study from HP shows that 70 percent of the most commonly used internet of things (IoT) devices contain vulnerabilities, these include password security, encryption and personal data issues.
As manufacturers rush to bring IoT devices to market they open the door to threats ranging from code vulnerabilities and denial of service attacks to weak passwords and scripting vulnerabilities.
HP used its Fortify on Demand product to scan 10 of the most popular IoT devices, uncovering on average 25 vulnerabilities per device. Items tested included TVs, webcams, home thermostats, remote power outlets, sprinkler controllers, hubs for controlling multiple devices, door locks, home alarms, scales and garage door openers.
Of the devices tested -- including their cloud and mobile software components -- 8 out of 10 raised privacy concerns surrounding collection of personal data. 90 percent of those devices tested collected at least one piece of personal information either via the device itself or its associated software.
Weak passwords was another problem with 80 percent of tested devices failing to require passwords of adequate length or complexity. Not encrypting data in transit affected 70 percent of devices. 60 percent didn't use encryption when downloading software updates. This meant that in some cases downloads could be intercepted and extracted allowing the software to be analyzed.
Insecure web interfaces were a problem for 60 percent of devices, poor session management, weak default credentials and credentials transmitted in clear text all being concerns. Of those devices with cloud and mobile components 70 percent would enable a potential attacker to determine valid user accounts through account enumeration or the password reset feature.
"While the Internet of Things will connect and unify countless objects and systems, it also presents a significant challenge in fending off the adversary given the expanded attack surface," says Mike Armistead, vice president and general manager, Fortify, Enterprise Security Products at HP. "With the continued adoption of connected devices, it is more important than ever to build security into these products from the beginning to disrupt the adversary and avoid exposing consumers to serious threats".
Full details of the study are available on the HP website and the company will be addressing the latest security trends at the Black Hat USA 2014 conference taking place next month.
Image Credit: Jurgen Priewe / Shutterstock
-

Cleaning up after viruses -- which antivirus solutions are best?
Publié: juillet 30, 2014, 11:23am CEST par Ian Barker

In an ideal world there wouldn't be any viruses at all but, since there are, the next best scenario is to have an antivirus program to protect you. But what happens once it's too late? If you get a virus infection how good are antivirus and clean up tools at repairing your system?
Independent testing organization AV-TEST set out to resolve this question with a comprehensive 10-month test using 17 different software packages.
It tested paid antivirus solutions from Bitdefender, ESET, F-Secure, Kaspersky and Norton, plus free antivirus tools from Avast, AVG, Avira and Malwarebytes along with Microsoft Security Essentials. In addition it tested seven specialized cleanup and recovery tools, Avira Cleaner, Hitman Pro, Disinfect2013, F-Secure Removal Tool, Kaspersky Removal Tool, Panda Cloud Cleaner and Norton Power Eraser.
Each solution was tested multiple times over a 10 month period from September 2013 to June 2014, repeatedly testing malware families to see how the software coped with their evolution. Tests looked at whether the malware was detected, if components were completely removed and whether all changes to the system were completely reversed leaving it fully restored.
Test results
Results are divided into four categories. In the first, looking at detection of known malware all products should have passed as the researchers established beforehand that the malware samples used were known to all of the solutions. However, both Microsoft Security Essentials and Avira Free Antivirus managed to miss known malware.
The second category looked at active malware components not removed. Of the 10 security packages, the freeware solutions from Avira, Avast and AVG, as well as Microsoft Security Essentials failed to remove active components in the system between one and seven times. The paid software products and the freeware Malwarebytes Anti-Malware Free all cleaned error-free. Of the cleanup tools Hitman Pro, Panda Cloud Cleaner, Avira Cleaner and the F-Secure Removal Tool were unable to remove between one and 11 active components. Only the Kaspersky Removal Tool, the Norton Power Eraser and Disinfect2013 removed everything.
The third category looked at whether any residual harmless components were left on the system. Security packages from Bitdefender, F-Secure, Kaspersky, Norton and ESET left small file remnants and insignificant entries in the registry between 1 and 9 times. Malwarebytes achieved a perfect removal. Of the cleanup tools Kaspersky Removal Tool only missed removal of a harmless file in one instance. Norton Power Eraser fell short of a perfect clean-up 11 times, and Disinfect2013 48 times, all it left behind though was digital garbage with no dangerous components.
The last category looked at whether removal was complete, leaving a fully cleaned and repaired system. Of the security packages only Malwarebytes Anti-Malware Free had 100 percent success leaving the system completely cleaned and repaired after 60 tests. Bitdefender came close behind with successful cleanups in 59 tests followed by F-Secure and Kaspersky on 56. Of the clean up tools none left the system completely clean. Kaspersky Removal Tool turned in the best performance, leaving behind just one harmless file.
In the final analysis Malwarebytes, Bitdefender and Kaspersky put in the best performance of the security packages. Of the freeware cleanup tools the researchers recommend Kaspersky Removal Tool and note that while the Norton tool and Disinfect2013 left behind a lot of garbage they didn't miss any active components. You can see the full results on the AV-TEST website.
The good news to take away from this is that if you are unlucky enough to contract a virus there are effective options that can clean your system without you having to resort to a complete reinstall. The even better news is that the most effective tools are free.
Image Credit: Sergey Nivens / Shutterstock
-

Millions of Android devices could be at risk from Fake ID flaw
Publié: juillet 29, 2014, 5:00pm CEST par Ian Barker
 A newly uncovered flaw in Google's Android OS could leave large numbers of mobile devices at risk from malicious apps that appear to be from trusted developers.
A newly uncovered flaw in Google's Android OS could leave large numbers of mobile devices at risk from malicious apps that appear to be from trusted developers.Named 'Fake ID' by Bluebox Security who uncovered it and notified Google of its presence, the vulnerability lets malicious applications impersonate specially recognized trusted applications without any user notification. Although a patch was issued in April it's likely that many devices are still at risk.
The flaw can can be used by malware to escape the normal application sandbox and take one or more malicious actions. For example it could insert a Trojan horse into an application by impersonating Adobe Systems, gain access to NFC financial and payment data by impersonating Google Wallet, or take full management control of the entire device by pretending to be 3LM.
Fake ID has been present in Android versions from 2.1 to 4.4, although it was fixed in April as part of the latest patch, Google bug 13678484. Android KitKat is immune due to a change in the webview code. Millions of unpatched devices could still be at risk, however, Google's own statistics indicate that more than 80 percent of Android users are running older versions of the OS.
Fake ID works by exploiting a problem in the way Android uses digital IDs. Whilst the OS checks to see if an app has the right ID before granting privileges it doesn't check to see if that ID is properly issued, allowing forged ID codes to be used. It's also possible for a single app to carry multiple IDs making it possible to carry out several attacks.
Writing on Bluebox's blog chief technology officer Jeff Forristal says, "The problem is further compounded by the fact that multiple signers can sign an Android application (as long as each signer signs all the same application pieces). This allows a hacker to create a single malicious application that carries multiple fake identities at once, taking advantage of multiple signature verification privilege opportunities to escape the sandbox, access NFC hardware used in secure payments, and take device administrative control without any prompt or notification provide to the user of the device".
Bluebox has released a Security Scanner app that checks to see if your device is exposed.
-

Post Target many retailers continue to leave data at risk
Publié: juillet 29, 2014, 4:08pm CEST par Ian Barker

More than six months on from the Target breach hitting the headlines retailers are still not properly protecting their data according to risk management specialist BitSight.
Writing on the company's blog CTO and co-founder Stephen Boyer says, "BitSight has continued to observe evidence of system compromise inside hundreds of retailers over the course of the year. Based on our data and analysis, we observed that there were many retailers with poor performance and that this downward trend has continued into the second half of 2014".
The blog goes on to highlight a number of instances since the Target breach where customer and credit card details have been compromised. It also points out that there are likely to be many more incidents that have gone unreported and are not likely to be revealed.
Boyer says, "The data here compels us to reiterate today what was expressed back in January: the evidence strongly suggests that organizations in the list above are not alone and does not bode well for the rest of the year".
He points out the importance of industry and peer benchmarking in helping companies improve their security. Measuring performance helps businesses gain insight into changes in their posture, and leads to better understanding of what actions are helping to improve their ratings. Benchmarking against the top-performing industries and comparing security practices can help set strategy and encourage the adoption of new standards.
Retailers need to adopt some of the techniques used by the financial industry in terms of continuous monitoring, regular risk assessments and responding quickly to emerging threats. They also need to make IT security a board level issue. Boyer concludes, "As retailers begin to adopt more of these measures and follow the best practices of top performing peers, we will likely see the number of breach incidents decline".
Image Credit: Andrea Danti / Shutterstock
-

Better use of data can avoid the impact of a bad sales experience
Publié: juillet 29, 2014, 3:33pm CEST par Ian Barker

We've all had bad sales experiences at some time or another and they inevitably have a negative impact on our view on the company concerned.
A new study by mobile sales enablement specialist Showpad reveals that it can take years to recover from the damage caused to the customer relationship by a bad sales experience.
The survey also reveals a difference in perception between sales and marketing on the value of marketing material. A majority of sales professionals (64 percent) think marketing content is neutral to ineffective, while 76 percent of marketing people, unsurprisingly, rate their collateral as effective.
"We have seen that the cost of a bad sales experience is high, with most companies leaving millions on the table. Fortunately there are powerful solutions to help companies to overcome these challenges," says Pieterjan Bouten, co-founder and CEO, Showpad. "Delivering the right content, in context, at the right time has proven to be critical to avoid a bad sales experience. Our mission at Showpad is to arm sales people with the right marketing collateral on any device so they can sell -- successfully -- anytime and anywhere".
In order to combat the problem of bad sales Showpad is announcing a partnership with analytics platform GoodData to deliver improved insight into the content that resonates with customers and prospects, enabling sales staff to close more deals.
This allows marketing teams to learn how well their message resonates with prospects and customers. At the same time sales teams are armed with the best content to convert leads anywhere and at any time.
You can find out more about the partnership and the survey results on the Showpad website and there's a look at the cost of bad sales experiences in infographic form below.
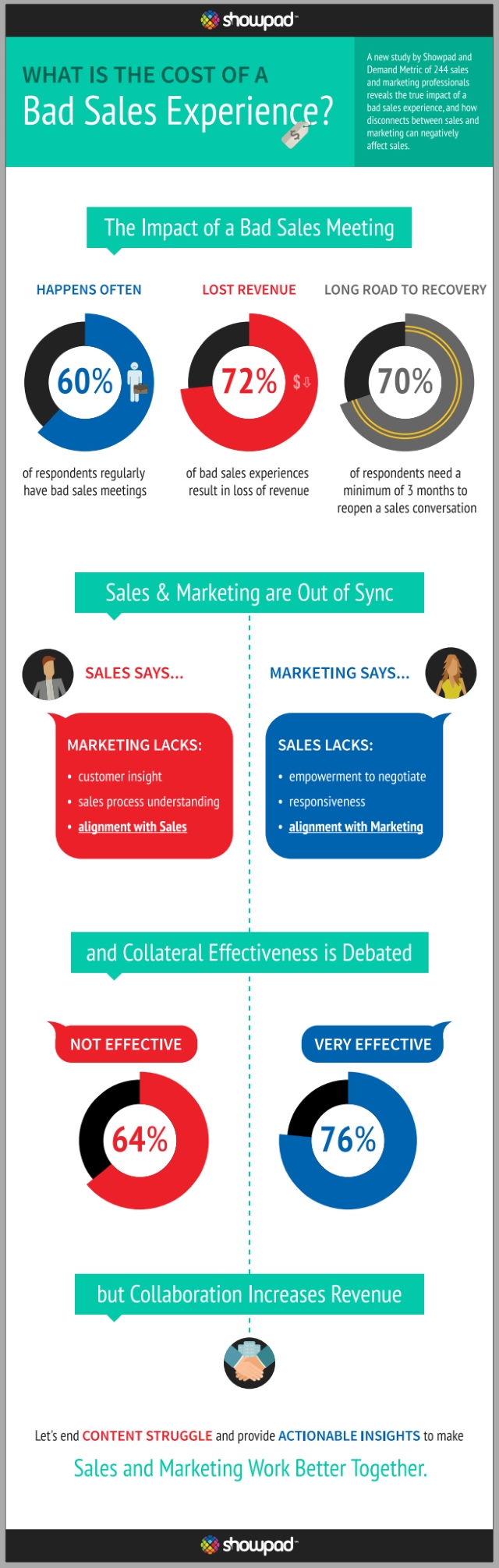
Image Credit: Onypix / Shutterstock
-

InPowered helps marketers use the power of expert opinion
Publié: juillet 29, 2014, 3:29pm CEST par Ian Barker

Independent reviews and opinions are a valuable commodity for marketers as they can often be key to purchasing decisions. Now content management specialist InPowered is launching a new product to help companies find out what experts are saying about them.
Called Expert Ranking it identifies the top experts on any topic and allows brands to discover what these experts are writing about them. It then lets the brand promote those opinions via their web, social and mobile channels.
Pirouz Nilforoush, Co-Founder and CEO of inPowered says that opinion about a brand or product is far more compelling coming from a credible third-party, "Ultimately, people trust experts far more than they trust brands. inPowered is the only platform capable of ranking the top experts on any topic, discovering the content those experts have written about your brand, and highlighting the specific, positive expert opinions you should promote for the greatest business impact with customers".
Expert Ranking works by measuring how people react to someone’s knowledge based on depth, consistency and validation. It first looks for people that write in-depth articles on the few topics that they have the most knowledge on, rather than people who write basic articles on a lot of topics.
After that inPowered looks for people who actively and consistently share their knowledge about a given topic. Someone writing several articles per week about a particular topic is seen as more knowledgeable than someone that writes only one story per month on that topic, even if more people read that one story.
Finally, the software looks for people that have a loyal following who consistently share their content. For example, if someone consistently has 100 people sharing their content on a particular topic, that person is deemed more knowledgeable than a person who has one article that was shared by 1,000 people.
You can read more about how inPowered helps you find and promote what experts are saying about your brand on the company's website.
Image Credit: iQoncept / Shutterstock
-

One in four IT professionals aren't aware of virtual security options
Publié: juillet 28, 2014, 3:19pm CEST par Ian Barker

Securing IT is essential for any modern business, but according to a new study carried out for security company Kaspersky Lab around one in four IT security experts have little or no understanding of the security options for virtual environments.
Almost half of respondents (46 percent) said that virtual environments can be adequately protected by conventional security solutions and 36 percent believe that security concerns in virtual infrastructures are significantly lower than in physical environments.
The study finds that IT security professionals may not have a clear understanding about the different virtualization security approaches that are available. Only one out of every three IT security experts have a clear understanding of light agent and agent-based virtualization solutions, and only one out of every four understands agent-less virtualization security.
Kaspersky points out that although conventional security solutions may be 'virtual aware' they can create performance problems when used with virtual environments. Agent-based security can overwhelm resources when scanning and may leave protection gaps when updates are required.
Mark Bermingham, Virtualization Evangelist at Kaspersky Lab North America says, "Businesses today face an ever-evolving threat landscape and cybercriminals are increasingly looking at virtual environments as the next frontier of sophisticated attacks. The survey results highlight a clear disconnect between what organizations believe is optimal security for a virtual environment when contrasted with the robust capabilities delivered via agentless and light agent solutions. With many businesses turning their attention to securing virtual environments, it is critical that they execute these initiatives and understand their options for securing these business-critical environments".
But while many organizations may not have a clear understanding of virtual security options 64 percent agree that security should be a priority when rolling out virtual infrastructure. Also 52 percent agreed that virtual environments are becoming key to their business infrastructure and securing them would be a priority for the next year.
The report concludes that businesses need to measure the performance costs of security, assign the right solution to each environment and limit 'virtual sprawl' by shutting down virtual machines when they're no longer in use. You can read the full report on Kaspersky's website.
Photo Credit: Sergey Nivens/Shutterstock
-

Fake Googlebots used to drive DDoS and other attacks
Publié: juillet 25, 2014, 12:19pm CEST par Ian Barker

Googlebots are essential to the smooth running of the search engine, ceaselessly probing websites to ensure that Google stays up to date with the latest developments and site changes.
But for every 25 genuine Googlebots that visit your site you'll also be visited by a fake Googlebot -- more than 23 percent of which are used for DDoS attacks, hacking, scraping and spamming. This is among the findings of security company Incapsula's 2014 Search Engine Study.
The study is based on over 400 million search engine visits to 10,000 sites over 30 days and shows Google is the most active search engine. Googlebots are responsible for more than 60 percent of all page crawls, the second in line the MSN/Bing bot notches up only 24.5 percent. What's also interesting is that there's no correlation between the number of human visits to a site and how often it’s crawled by Googlebots. Google pays just as much attention to the backwaters of the web as it does to popular sites.
The study does note though that content-heavy and frequently updated websites were more thoroughly crawled. This behavior was most notable in the cases of big forums, news sites and large-scale shop sites with a wide array of frequently updated products.
Most interesting and concerning though is the number of fake Googlebots. The study shows that over 4 percent of bots using Google's HTTPS user agent aren't what they claim to be. The benefit of this to hackers is that site owners generally allow unhindered access to Google's crawlers in order to protect their search results.
Incapsula's logs reveal that fake Googlebots are used mainly for DDoS attacks but also in spamming and hacking activity. Security solutions that don't use case-by-case traffic inspection are unable to spot the real bots from the fakes.
To remain secure, sites need to use a security solution that combines heuristics and IP and ASN verification to identify bots based on their origin.
You can read more about Googlebot and fake bot activity on Incapsula's blog and there's a summary of the report's findings in infographic form below.
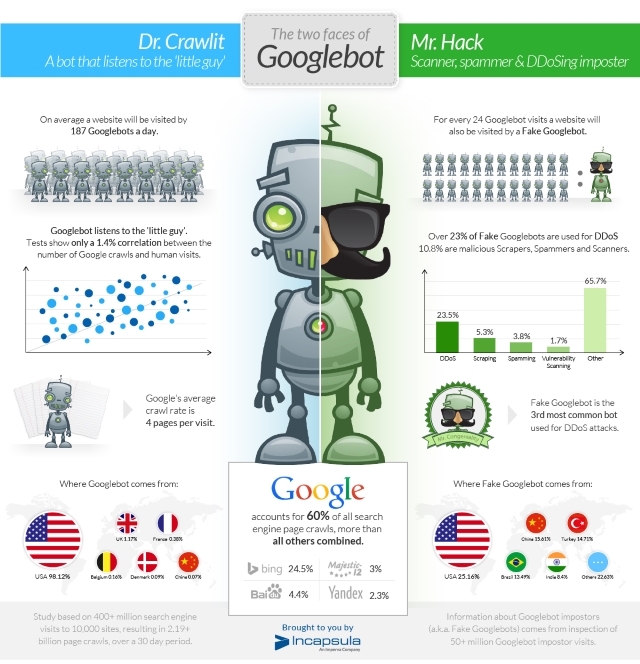
Photo Credit: Gunnar Assmy/Shutterstock
-

Self-destructing content service ensures shared data stays private
Publié: juillet 23, 2014, 3:33pm CEST par Ian Barker

When you send a file to someone else there’s always a risk that it could be copied or forwarded, even if it's intended to remain private -- as many a snapper of naked selfies has found to their cost.
There have been attempts to solve this problem in the past of course with services like Snapchat and Yahoo's Blink, that allow content to be viewed for only a short time, but none of these are aimed at business users.
That's about to change with the launch of Digify a self-destructing, view-only content protection service to let professionals privately share their business content. Files shared using Digify can't be forwarded, downloaded, copied, saved or uploaded elsewhere, and can be set to self-destruct in any time from one minute to one month.
It works on iOS and Android -- a desktop version is due to launch later this year -- and is integrated with cloud storage services including Dropbox. So, for example, users can browse and send a Dropbox file straight from the Digify app. On iOS devices, if recipients try to take a screenshot, the sender will be notified and the file unshared. On Android screenshots are blocked completely. Statistics in the Digify app show who has viewed the content, for how long and how often.
Augustine Lim, co-founder and CEO of Digify says, "Before Digify, there were many tools for sharing files but no easy, inexpensive way for most professionals to protect and track access to information once it was sent to someone else. After downloading files a recipient was able to forward or upload them anywhere on the web. Digify enables users to effectively share, control and protect ideas and content from wherever it is stored with the comfort that they will not go beyond the intended recipient".

It works by converting files to an intermediate format for temporary display by Digify's viewer via document streaming. Recipients are unable to download content to their own devices, or share it with others. The original is deleted from Digify's server after conversion and once the file self-destructs all copies are deleted.
Files are protected by 256-bit encryption both on the server and in transit. Screenshot tools and other means of capturing information are blocked. The process works with Word, Excel and PowerPoint files as well as photos and PDFs.
Digify is available now via the Apple App and Google Play stores or you can find out more on the company's website.
Image Credit: iQoncept / Shutterstock
-

Comodo SecureBox always assumes the worst to strengthen endpoint security
Publié: juillet 23, 2014, 1:28pm CEST par Ian Barker

Cybercriminals are constantly targeting end users via phishing and social engineering attacks in attempts to access sensitive information or corporate data and bypass traditional endpoint security. Often these attacks are delivered from devices outside the enterprise, belonging to customers or suppliers for example.
Internet security specialist Comodo is launching a new product aimed at plugging the security gap and guarding against, keylogging, SSL sniffing, remote screen viewing, memory scraping, man-in-the-middle attacks, zero-day malware and more.
Comodo SecureBox is a secure desktop application designed to protect and run only trusted applications. It always assumes that the host environment is hostile or malware-infected. This unique approach to containerization differs from traditional containment solutions that seek to sandbox only malicious or untrusted applications.
"SecureBox is particularly well-suited for businesses who need to ensure the security of third-party endpoints that are beyond the control of their IT organization," says Kevin Gilchrist, Comodo's Vice President of Product Management. "Financial services companies, healthcare or health insurance companies, or any company that has a large supply chain where the supplier represents a possible vector for malware would benefit from SecureBox".
Features of SecureBox include securing mission critical data in transit by creating a secure tunnel between client and web server. It also protects against keyloggers by bypassing the Windows input subsystem, and intercepts remote takeover attempts by detecting attempted screen captures.
It also has anti-SSL sniffing technology to guard against man-in-the-middle attacks, plus it containerizes applications to prevent memory scraping. Finally there's a cloud-based virus scan to detect and terminate any virus activity on the host device.
Comodo can custom build SecureBox for large organizations so that it can be company-branded and tailored for specific security needs. For more information visit the SecureBox website.
Image Credit: VERSUSstudio / Shutterstock
-

Oracle sets out to redefine the data-driven enterprise
Publié: juillet 23, 2014, 12:16pm CEST par Ian Barker

Data makes the modern world go round and by being able to use it effectively companies can gain a competitive advantage, improve customer experience and enhance operational efficiency.
Database specialist Oracle has combined a number of its offerings including the newly acquired BlueKai Audience Data Marketplace to form Oracle Data Cloud, a platform that provides customers access to world-class data-as-a-service (DaaS) offerings to allow companies to exploit marketing and social media data.
"Unbundling data from SaaS applications has enhanced a business user's ability to activate insights gleaned from external data sources, leading to more engaging and personalized customer experiences," says Omar Tawakol, general manager and group vice president of Oracle Data Cloud. "The Oracle Data Cloud brings together a best-in-class data platform with the world's largest data marketplace to drive smarter decisions for marketing and social, and it will eventually include other enterprise functions such as sales and service".
Oracle DaaS for Marketing is designed to help organizations enhance the cross-channel customer experience through targeted marketing engagement that brings together customer and audience intelligence from across the enterprise. With access to more than a billion profiles globally, Oracle DaaS for Marketing is the world's largest data marketplace and allows companies to deliver relevant content across a range of platforms.
DaaS for Social helps enterprises benefit from the vast pool of data generated across social platforms and helps them make sense of unstructured social and enterprise data. By applying powerful text processing techniques it can help to generate business intelligence from raw data culled from public and private sources.
You can find more information about Oracle's data-as-a-service offerings on the company's website.
Photo Credit: Blend Images/Shutterstock
-

79 percent of companies have blamed network problems on the wrong IT group
Publié: juillet 21, 2014, 5:23pm CEST par Ian Barker

With today's increasingly complex network environments it's often hard to pinpoint the exact cause of problems. According to a new survey by network specialist Emulex this often leads to incorrect reporting to management.
The study of 547 US and European-based network and security operations professionals found that 45 percent of IT staff monitor network and application performance manually, instead of implementing network monitoring tools.
This has resulted in 77 percent of those surveyed having reported information to their management teams that turned out to be wrong. 79 percent admitted to attributing the cause of network events to the wrong IT group.
A staggering 87 percent found that they'd had to report the cause of a network event without having the information to be completely accurate. Also 73 percent of those surveyed said that they had currently unresolved network events.
This is against a background of increasing security events with 81 percent saying they'd experienced some sort of breach in the past year, and more demands for mobility with 84 percent having implemented BYOD over the last 12 months.
Yet 26 percent of European respondents said they have no plans to monitor their network for performance issues related to BYOD. When added to the fact that 45 percent of organizations are manually monitoring the performance of their networks, Emulex says the growing amount of mobile device-generated traffic is on pace to overwhelm enterprise networks.
"IT is facing new challenges related to the growing use of software-defined networking, virtualization and higher performing networks, as well as increasingly more sophisticated attacks on company IT assets," says Shaun Walsh, senior vice president of marketing at Emulex. "The clear message from this survey is that one of the best tools for SecOps and NetOps professionals to have at their disposal is 100 percent network visibility that is tied to their detection management systems and it’s the combination of proactive management and the ability to do forensic analysis that will give these IT professionals the right tools to maximize application delivery, protect their corporate assets and avoid the IT blame game".
The full study is available on the Emulex site and there's a summary of the findings in infographic form below.

Image Credit: zwola fasola/Shutterstock
-

Lenovo continues to dominate Chinese and Indian PC markets
Publié: juillet 21, 2014, 4:42pm CEST par Ian Barker
 We're constantly being told that the PC market is in terminal decline, but sales figures from different parts of the world continue to defy the predictions.
We're constantly being told that the PC market is in terminal decline, but sales figures from different parts of the world continue to defy the predictions.The latest figures from market intelligence provider IDC for the Asia/Pacific region show a two percent rise over last quarter and a total market for the second quarter of 2014 at 24.3 million units, slightly up on predictions.
Various factors have had an influence on these figures. Uncertainty surrounding Thailand’s coup resulted in a steep decline as sales channels were reluctant to take new shipments. On the other hand shipments to a large education project in India came in earlier than expected, boosting figures by around 100,000 units.
"The ongoing economic slowness in the emerging markets sets the tone of the overall PC demand and inhibited the region's year-on-year growth", says Handoko Andi, Research Manager for Client Devices Research at IDC Asia/Pacific. "There are pockets of optimism coming from mature markets like Australia and New Zealand, Singapore, and Hong Kong, where smartphones and tablets near saturation. However, the region's growth has been adversely impacted with the rise of large-screen smartphones in China and most ASEAN (Association of South East Asian Nations) countries”.
Looked at by manufacturer, world market leader Lenovo retains its top spot here on 26.6 percent of the Asia/Pacific market, thanks to a strong second quarter following the Chinese New Year and a back-to-school campaign boosting its sales in India.
Dell holds second spot on 10.5 percent and showed strong growth in India and Thailand due to a new focus on the consumer sector. HP is just behind in third place but Acer has overtaken ASUS for fourth spot thanks to its strong entry-level product range.
For more information on IDCs market tracking you can visit the company's webpage.
Image Credit: Kheng Guan Toh / Shutterstock
-

QuickPivot provides real-time customer intelligence
Publié: juillet 21, 2014, 3:06pm CEST par Ian Barker
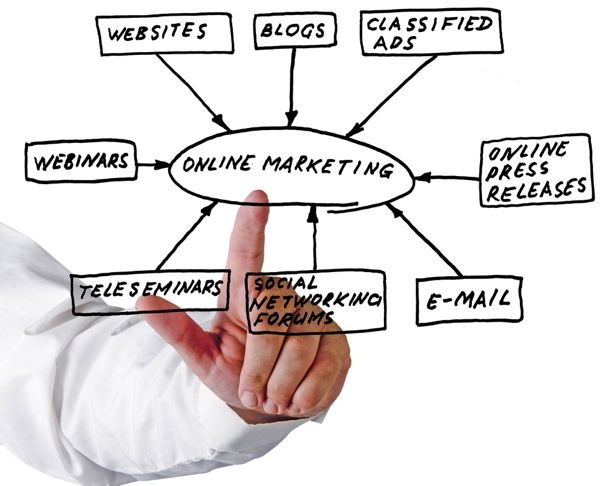
The holy grail of marketing is to be able to understand what your customers want and then to adapt your communications accordingly to make them more effective.
Achieving this of course isn't easy so companies are always on the lookout for ways to learn more about their customers. Boston-Based QuickPivot (formerly called Extraprise) is launching a new marketing platform to allow marketers in any industry to derive customer insight, listen to brand interactions and then adapt campaigns with highly optimized messages and offers.
QuickPivot CEO Michael Shanker says, "Instead of operating at the traditional 'speed of marketing,' B2B and B2C organizations that leverage our newest offerings are able to market at the right speed of the customer -- combining technology, insight, creative, channel mix and operational agility, to make every touch count at any point in the customer journey".
The product supports a wide range of devices and channels such as email, mobile, web, social and print, all of them in real time. So it allows cross-channel marketing, database segmentation to provide answers fast, and accurate reporting of campaign effectiveness. It's cloud-based too so teams can access it from anywhere they need to.
In addition, QuickPivot has many years of experience in providing marketing technology and services for some of the world’s largest B2B and B2C brands. The company will combine its platform with a complete range of database, analytical and reporting services. This will let users optimize and measure campaign effectiveness in real time at every stage of the process across campaigns, channels and geographical regions.
You can find out more about QuickPivot and how it works on the company's website.
Photo Credit: Arkady/Shutterstock
-

RE: Was it good for you? -- 8 percent of people check emails after sex
Publié: juillet 18, 2014, 11:35am CEST par Ian Barker

Email is often cited as the killer app which popularized the internet. You might think that by now we'd have moved on but a new survey of 1,000 US email users from mail app provider My.com suggests we're just as in love with our inboxes as ever.
There are currently around 3.9 billion email accounts worldwide and the number is expected to increase by around 27 percent this year. We're also spending more time on our email these days with 46 percent of users admitting to spending an hour or more a day reading their messages.
We have more accounts too. Only 33 percent of respondents have a single account with 27 percent having three or more.
Mobile devices of course means you can be in touch with your email at all times and 70 percent of those surveyed check their mail on mobile devices with 67 percent using push notifications to get instant alerts.
It seems we check our mail more often too. 74 percent check their email first thing in the morning, which is fair enough, but email also intrudes on our other activities. 48 percent check during lunch, 27 percent check during dinner, 33 percent during movies and 56 percent check before going to bed. Then there's the 8 percent who admit to checking straight "after sex" -- though there's no indication of how many of these also checked before they went to bed.
The main problem with email of course has always been spam and that isn't going away either. Despite improved filtering 60 percent of respondents admit to losing important messages due to spam. Also a remarkable 64 percent say they've closed an email account in frustration because of excessive spam.
You can check out a more detailed summary of the findings in infographic form below.
Photo Credit: Shumilina Maria/Shutterstock
-

New Android ransomware pretends to be FBI porn warning
Publié: juillet 17, 2014, 3:54pm CEST par Ian Barker
 The large number of devices out there means that Android is becoming an increasingly popular target for malware writers. Ransomware which has previously been a mainly Windows problem is becoming an issue too.
The large number of devices out there means that Android is becoming an increasingly popular target for malware writers. Ransomware which has previously been a mainly Windows problem is becoming an issue too.The latest piece of malware discovered by mobile security specialist Lookout attempts to extort money with a scary message claiming to be from the FBI. It claims the user has broken the law by visiting pornography and child abuse websites.
Called ScarePakage, the malware masquerades as well-known apps, like Adobe Flash and a number of anti-virus applications, and pretends to scan your phone when launched. After completing the fake scan it locks your device. You can't navigate away and if you try to reboot, the FBI message will be the first thing you see when you turn back on.
It demands several hundred dollars in the form of a MoneyPak voucher to release your device. ScarePackage tries to prevent normal use of the device by blocking the victim's actions. Using a Java TimerTask, which is set to run every 10 milliseconds, the application will kill any other running processes that the user interacts with that are not the malware itself or the phone's settings application. The malware also uses an Android WakeLock to prevent the device from going to sleep.
Should you manage to switch the device off a boot receiver class resumes ScarePakage's takeover when you turn it back on, shutting down all other processes. It doesn't need root in order to take over the phone, but it does need device administrator access.
Lookout's blog, which includes screen shots of the malware, says, "ScarePakage is likely created by Russian or other Eastern European authors given language cues used in the application that we observed". For now the malware seems to be targeting only users in the US.
Advice for avoiding infection includes, not awarding device administrator rights to applications unless you're sure of what they do, only downloading apps from known and trusted developers and using a security application to detect threats before they're opened.
Image Credit: wavebreakmedia / Shutterstock
-

SoftWatch helps enterprises evaluate and implement XP alternatives
Publié: juillet 16, 2014, 4:58pm CEST par Ian Barker

When Microsoft discontinued support for XP it left a large number of businesses, around 25 percent, needing to make a transformation of their IT environment.
As well as switching to a new desktop OS many are also moving applications to the cloud, changing hardware and introducing BYOD. In order to help IT decision makers with these choices, Israel-based software analytics specialist SoftWatch has introduced a new SaaS product.
OptimizeIT Premium Suite aims to support CIOs in the decision making process as they switch to new environments. It makes it easy to identify heavy and light users as well as those with specialist requirements like ERP and CRM or power applications like CAD/CAM.
By identifying applications and usage patterns it can guide IT decision makers in reducing operational costs. It allows them to build an end-user computing environment that fits the user profile, utilizing various combinations of hardware and software.
The end result will be a flexible and cost-effective hybrid cloud architecture accommodating the needs of different users at optimal cost. While power users may continue to use advanced applications using powerful workstations, others may be better off with relatively low-cost tablets and cloud-based applications.
"We continue to extend our services to enable IT decision makers to make informed decisions and optimize their end-user computing environment based on application usage analysis," says Uri Arad, Co-CEO of SoftWatch. "We strongly believe that the default decision to migrate to the next Microsoft OS and the 'one size fits all' approach are no longer serving the interests of enterprises. The availability of application usage information allows enterprises to obtain a thorough analysis of their readiness to embrace cloud based services, manage the transition and enjoy tremendous economic and technological benefits".
You can find out more about OptimizeIT Premium on the company's website.
Photo Credit: Melpomene/Shutterstock
-

Choose bad passwords and reuse them often says Microsoft
Publié: juillet 16, 2014, 11:59am CEST par Ian Barker

Conventional security wisdom says that you should use complicated passwords which are impossible to remember and have a different one for each and every website that you visit.
However, a new paper published this month by Microsoft Research says we should go back to having a bad, easily remembered, password and using it on lots of sites. Okay, that's a bit of a simplification, but what the researchers are saying is that in order to be able to remember the difficult passwords for your bank, etc it's better to reuse simpler passwords on low-risk sites.
The report acknowledges the difficulties of having a large number of passwords and the benefits of reuse as a coping strategy. The authors say, "Despite violating long-standing password guidance, writing passwords down is, if properly done, increasingly accepted as a coping mechanism. Other strategies to cope with the human impossibility of using strong passwords everywhere without re-use include single sign-on, use of email-based password reset mechanisms, and password managers".
However they point out that whilst password managers may reduce some risk they can be vulnerable to malware attacks either against the client device or cloud servers. Storing passwords only on the client also sacrifices portability.
The research suggests dividing your passwords into two groups, the first those with high value and low probability of compromise and secondly accounts of low value and high compromise probability. The first group would include your bank, email accounts and so on. The second would be websites and forums where you perhaps need to sign in to comment but don't carry out financial transactions.
The report’s conclusion is that, "...to be realistic, efficient password management should consider a realistic suite of attacks and minimize the sum of expected loss and user effort." It also says, "We note that while password re-use must be part of an optimal portfolio strategy, it is no panacea".
You can read the full report on the Microsoft Research website. Meantime if you’d like to comment you can be safe in the knowledge it’s fine to sign in with a weak password that you've used on other sites.
Image Credit: Africa Studio / Shutterstock
-

Tronsmart T1000 -- Media streaming on a budget [Review]
Publié: juillet 16, 2014, 10:41am CEST par Ian Barker

If you want to send images, videos or music to your TV from another device the obvious choice might seem to be Google's Chromecast. However it's not the only game in town, the Tronsmart may not be a name you've heard of but at $24.09 it's around $10 cheaper than Google's alternative, so is it worth considering?
First impressions are good, it's made of a nice smooth matt plastic and the design is tidy if unexciting. The unit plugs directly into the HDMI port of your TV or projector and it offers 1080P resolution, though can be switched to 720P for older TVs. The T1000 will work with Android (including Kindle Fire HDX), iOS or Windows devices, you just need to download the right software.
The T1000 is a bit bulky, so depending on the design of your TV you might need an HDMI extension cable to connect it comfortably. On the Hannspree set we used to test it for example a lip on the bottom edge meant that though you could connect the T1000 you didn't have room to plug in the combined USB and Wi-Fi antenna lead at the other end. It needs a USB connection for power so if your TV doesn’t have a USB port you'll also need a power adapter.
Once you've downloaded the appropriate EzCast software for your client from the web you're ready to get started. Run the software and you can connect to the T1000, this is a bit frustrating if you're wirelessly connected to the internet as unless you have two adaptors you'll need to drop your web connection. However, once up and running you can connect the Tronsmart to your router so that it acts as an access point.

The T1000 allows you to mirror the display from your Android mobile device or PC to the TV screen using Miracast so in theory anything that displays on your device you can show on your TV. This isn't yet available for iOS users though. Alternatively the EzCast app lets you use your device as a remote control to play local content to the TV.
The printed instructions seem to have lost something in translation but the EzCast software is pretty straightforward once you get started.
It's a little cheaper than a Chromecast and it's potentially more versatile as it supports more devices and has more options. But the setup is a bit fiddly and it's generally a less smooth user experience. It is cheap though so if you’re looking for a budget streaming device for occasional use it might be worth a look.
The Tronsmart T1000 costs $24.09 (£14.84) from Gearbest.com.
Photo Credit: Ian Barker
-

Tellwise improves customer engagement with smart messages
Publié: juillet 15, 2014, 3:19pm CEST par Ian Barker

Effective sales campaigns are all about personalizing the message so that it's relevant to the customer. But generating this content can be time consuming.
Sales communication specialist Tellwise is launching a new Smart Message feature that helps sales professionals to more effectively communicate in a multi-channel and multi-device world.
Smart Message lets sales professionals generate a highly personalized content and collaboration portal for each of their customers as easily as creating an email. The messages can also be shared across social media sites like LinkedIn, Twitter and Facebook all from the same dashboard. This allows companies to stay in touch with a highly mobile and socially connected customer base.
They allow the sender to monitor how well a campaign is working as well thanks to intelligent notifications, collaboration features and behavioral analytics. A new interface lets sales staff manage all communications from one screen, putting sales reps in charge of their own campaigns.
"Today the sales journey is now defined by the buyer. We target helping our customers speed up the sales process while making interactions more meaningful by understanding the buyer point of view," says Conrad Bayer, co-founder and CEO of Tellwise. "As part of making communicating as simple as possible for both parties, we added these social, smart messaging capabilities to create a better multi-channel experience and help both parties get what they need in a more efficient manner".
The software allows existing content to be embedded and then promoted to almost any channel from a single location. It works across multiple devices too, allowing content to be delivered in mobile-friendly layouts.
Tellwise with Smart messages is delivered on software as a service form priced on a per user, per month basis. For more information visit the company's website.
Photo Credit: EDHAR/Shutterstock
-

The new technologies IT departments need to embrace
Publié: juillet 15, 2014, 11:52am CEST par Ian Barker

In the past IT departments have always been about crunching numbers and processing data. But emerging technologies are beginning to take IT into unfamiliar areas that in turn have an impact on the wider operation of the business.
Research specialist Gartner has identified six areas that it sees as potentially being adopted by business and which CIOs need to consider.
Speaking at Gartner's CIO Forum in China this week vice president and Gartner Fellow Hung LeHong says, "The IT organization is used to owning and supporting 'back office' and infrastructure technologies. Digital business technologies support the 'front office' and operations and may be emerging technologies that are not commonly part of the IT agenda".
The six areas Gartner says CIOs need to consider are; the internet of things, 3D printing, human augmentation and wearables, robotics and autonomous machines, cognitive machines, and cybersecurity.
"Regardless of the eventual stance, we believe CIOs should have an opinion, and should participate in innovating and in testing the business cases for these technologies in the early stages," says LeHong.
The internet of things is likely to create tensions between different business areas according to Gartner, but as there are few legacy deployments IT departments and CIOs have the chance to influence outcomes and contribute to technology selections at the outset.3D printing has a potential to transform business that Gartner says shouldn’t be underestimated. It can for example disrupt the supply chain by eliminating the need to import components.
Wearable technology can improve employee effectiveness, safety and health. However, bring-your-own-wearable issues will need clear policies. CIOs therefore need to consider human, legal, social and ethical issues, particular for future technologies that may involve things like implants or brain interfaces.
Robotics have been used in manufacturing industry for a long time. However, new lower cost machines with better sensors are taking robots into new areas. This may lead to reduced downtime, labor savings and more. This goes a stage further with cognitive machines that may be capable of taking over simple decision making tasks that once needed human input. They may have a role in initial problem diagnosis for example which means their use has an impact on the front line operation of the business.
Finally Gartner identifies cybersecurity. Although not a technology in itself this will have a greater impact as innovation moves into more areas of operation. Security responsibility for these areas will need to be addressed in the same way as IT security. Gartner sees a deeper integration developing between IT and physical security, infrastructure and services.
"The extent to which CIOs will 'own', operate and support digital business technologies is undefined, so the time is right to evaluate and pioneer new approaches," says LeHong.
More analysis can be found in the report How CIOs Need to Think About Digital Business Technologies on Gartner's website.
Photo Credit: nopporn/Shutterstock
-

DocuLynx aims to simplify cloud storage decisions
Publié: juillet 14, 2014, 4:55pm CEST par Ian Barker

There are a number of reasons why businesses might move data to the cloud. To reduce storage costs, improve accessibility or simply reduce the need for on-site equipment. But how can you be sure that moving data to the cloud is the correct decision?
We looked at how businesses can approach this earlier today. Now archiving specialist DocuLynx is using the Microsoft Worldwide Partnership Conference in Washington to launch a new product aimed at making cloud storage decisions easier.
Azure Agent is an assessment tool that looks at server data and produces customized reports to help IT executives evaluate the cost effectiveness of using DocuLynx's Azure and StorSimple products for second-tier storage. Using its return on investment calculator it's possible to work out potential savings over a number of years.
"In many organizations, data is typically increasing 30 percent year over year, and costs are mounting. Second-tier data storage costs are approximately 25 percent of on-premise storage costs, and 65 percent of data stored on primary storage is inactive," says Michael Liess, DocuLynx's President and CEO. "As storage solutions become targets for 'refresh,' the time is right to consider Cloud storage. By differentiating data based on its external attributes, DocuLynx Azure Agent helps CIOs identify which data should be moved to secondary storage -- the goal of any CIO looking to achieve significant cost savings with the least risk".
Beyond the initial analysis Azure Agent can be used to monitor data on a continuous basis and can be integrated with DocuLynx's other storage platforms.
CIOs can request a free assessment of their network file shares to assess the potential for savings. To find out more visit the DocuLynx website.
Image Credit: Modella / Shutterstock
-

Gmail app vulnerability leaves iOS users at risk
Publié: juillet 11, 2014, 3:54pm CEST par Ian Barker

Mobile security specialist Lacoon has released details of a new vulnerability in the Gmail app for iOS that may allow hackers to view or modify encrypted communications.
It allows attackers to use a Man-in-the-Middle (MitM) technique to impersonate a legitimate server using a spoofed SSL certificate.
This type of threat is usually prevented using certificate pinning where the app developer codes the intended server certificate within the app. This means if communication is re-routed the mobile app will recognize the inconsistency between the back-end server certificate as coded within the app, and the certificate returned from the fake server.
Lacoon has found that the Gmail iOS app doesn't perform certificate pinning. As a result a MitM attack could open up encrypted communications and the user would see no indication of suspicious activity.
Certificate pinning is implemented in Gmail's Android app so it looks like this could be an oversight. Yet although Google was informed of the vulnerability at the end of February and validated its existence it was still present at the time of writing.
Michael Shaulov, CEO and co-founder of Lacoon Mobile Security says, "Several months after providing responsible disclosure, Google has not provided information regarding resolution and it still remains an open vulnerability. This vulnerability leaves iPhone and iPad users at risk of a threat actor being able to view and modify encrypted communications through a Man-in-the-Middle attack".
Until such time as a fix is released, enterprises are advised to check the configuration profiles of devices to ensure they don't include root certificates, ensure that a secure channel like a VPN is used when accessing corporate resources, and perform network and device analysis to detect MitM attacks.
You can read more about the vulnerability on Lacoon's blog.
Image Credit: Pavel Ignatov / Shutterstock
-

Law enforcement and industry combine to prevent Shylock taking its pound of flesh
Publié: juillet 11, 2014, 12:27pm CEST par Ian Barker

An international operation involving law enforcement and private sector organizations has been set up to combat the Shylock banking trojan. Shylock, which gets its name because the code contains lines from Shakespeare's The Merchant of Venice, is thought to have infected at least 30,000 Windows computers worldwide.
To date Shylock has targeted the UK more than any other nation so the country's National Crime Agency (NCA) is coordinating the international effort. This also includes the FBI, Europol, BAE Systems Applied Intelligence, GCHQ, Dell SecureWorks, Kaspersky Lab and the German Federal Police.
Shylock typically infects its victims via a malicious link which installs the code, it will then seek to access funds stored in private or business bank accounts and transfer them to its criminal controllers. The enforcement operation is aimed at disrupting the system which Shylock relies on to operate by seizing servers and taking control of the domains it uses to communicate. These operations are conducted from the European Cybercrime Centre in The Hague.
Andy Archibald, Deputy Director of the NCA's National Cyber Crime Unit, says, "The NCA is coordinating an international response to a cyber crime threat to businesses and individuals around the world. This phase of activity is intended to have a significant effect on the Shylock infrastructure, and demonstrates how we are using partnerships across sectors and across national boundaries to cut cyber crime impacting the UK".
Users with Windows updates turned on should be safe from Shylock and don't need to take further action. If you don't have automatic updates running you can find more about checking for and removing infection on the Microsoft site.
There’s more information on the UK government's Cyberstreetwise website. The last word here though really should belong to Shakespeare's Shylock, "And if you wrong us shall we not revenge?"
Image Credit: Rob Hyrons / Shutterstock
-

New private cloud allows invite only sharing
Publié: juillet 11, 2014, 11:33am CEST par Ian Barker

Cloud storage is an increasingly popular way of storing and sharing data, but when using public services there's always a concern about how safe your information is.
But now a new startup aims to provide controlled sharing of data via an intelligent private cloud network. Sher.ly integrates your existing hard drives into a private, tightly controlled cloud network. Rather than have to send out open links to files or share copies across a public cloud, organizations and individuals can have the security of invite-only, limited-access file-sharing that keeps data on the devices that produced it.
It also offers simple access management with robust reporting and easy to use auditing tools so that management can track who has access to what.
"Sher.ly is faster, safer, simpler, and more efficient than protocols used in traditional cloud software platforms," says co-founder and CEO Blazej Marciniak. "It's an entirely new way to think about data storage. The principle is still the same, but the foundation is radically different".
Because it doesn’t rely on public services Sher.ly overcomes the worry of third-party providers exposing your data. "Given what we’ve learned about the NSA, and the extent to which third party providers were betraying the trust and privacy of their users, there is frankly no good reason to do business over a public cloud network," says Marciniak. "If you're handling anything like sensitive information, the truth is you can't afford to expose yourself to that risk. And, now with Sher.ly, you really don’t have to".
The software uses VPN connectivity and peer-to-peer communication technology to restrict data flow to secure end points, as opposed to relaying it through central servers. Users can access information stored behind their own firewall, share data streams across remote work groups and collaborate on documents and edits, all with the guarantee that private files never leave the safety of their native hard drives.
You can find out more about Sher.ly and sign up to take apart in the beta trial on the company's website.
Photo Credit: Marynchenko Oleksandr / Shutterstock
-

Threats to the internet in 2025 -- start worrying now
Publié: juillet 4, 2014, 1:37pm CEST par Ian Barker

We looked yesterday at the ten most serious security breaches of recent years, but the threat landscape is constantly changing. So what will happen in the future and which threats should we be most concerned about?
A new report by PewResearch, as part of its series marking 25 years of the internet, looks at how things might be in 2025. More than 1,400 experts in various fields were canvassed for their views on future threats.
The outlook is generally positive, with 65 percent believing that there will be no significant changes for the worse and hindrances to the ways in which people get and share content online. However, most believe that, thanks to mobile and other changes, billions more people will have internet access by 2025. Many of those questioned also believe that the web may be threatened by new trends.
The report identifies four main threat themes. First that actions by countries looking to maintain security and political control will lead to more blocking, filtering, segmentation, and balkanization of the internet.
Not all the experts agree on the outcome though. Paul Jones, a professor at the University of North Carolina and founder of ibiblio.org, responded, "Historic trends are that as a communications medium matures, the control trumps the innovation. This time it will be different. Not without a struggle. Over the next 10 years we will be even more increasingly global and involved. Tech will assist this move in a way that is irreversible. It won’t be a bloodless revolution, sadly, but it will be a revolution nonetheless".
The second theme is that trust will evaporate in the wake of revelations about government and corporate surveillance and likely greater surveillance in the future. Peter S Vogel, internet law expert at Gardere Wynne Sewell says, "Privacy issues are the most serious threat to accessing and sharing Internet content in 2014, and there is little reason to expect that to change by 2025, particularly given the cyber terror threats confronting the Internet users and worldwide businesses".
The third threat is that commercial pressures will endanger the open structure of the web. Technology futures expert Marcel Bullinga's response cites existing legal frameworks as a problem, "Sharing is hindered by ridiculous 19th century laws about copyright and patent. Both will die away. That will spur innovation into the extreme. That is the real singularity".
And finally there's the threat that efforts to fix the problem of having too much information might actually hold back content sharing.
Joel Halpern, engineer at Ericsson says in his response, "The biggest challenge is likely to be the problem of finding interesting and meaningful content when you want it. While this is particularly important when you are looking for scientific or medical information, it is equally applicable when looking for restaurants, music, or other things that are matters of taste. While big-data analysis has the promise of helping this, there are many limitations and risks (including mismatched incentives) with those tools".
Jonathan Grudin from Microsoft Research predicts this will lead to the emergence of a new breed of "personal information trainers" who will help people find the information they need.
You can find the full report and read the responses from many more of the experts by visiting the PewResearch Internet Project site.
Photo Credit: Anneka/Shutterstock
-

The top 10 data breaches and how they happened
Publié: juillet 3, 2014, 5:02pm CEST par Ian Barker

Security breaches happen all the time but it's the biggest ones that hit the headlines and send ripples through the IT community. Security consultancy TSC Advantage has looked at the top ten breaches from the last five years and what effect they've had.
Top of the list is the Adobe hack of 2013, made possible by weak password requirements and affecting 152 million customers. In second place comes the recent eBay hack involving stolen employee credentials and affecting 145 million users.
We go back to 2009 for the number three slot and the Heartland Payment Systems attack which exposed the payment card information of 130 million customers. In fourth place is our old friend Target and the 2013 attack that exposed the data of 110 million customers and cost an estimated $420 million.
Fifth is the 2010 attack against Google by Chinese hackers which exposed the identities of Chinese Gmail accounts that were under surveillance. In sixth comes the 2011 Epsilon attack which exposed customer names and addresses and led to the payment of $225 million in damages.
The 2011 Sony attack that left the Playstation Network down for 23 days takes seventh slot, followed in eighth by the US Department of Veterans hack in 2009 that exposed 70 million records.
Rounding out the top ten are the 2014 Global Payments attack which exposed 1.5 million sets of credit card numbers, and finally the AOL attack, also this year, which potentially exposed the details of 120 million customers.
For more information on recent breaches, what can be learned and what can be done to combat them, visit the TSC Advantage website. There's also a summary of the top ten, their causes and impact in infographic form below.
Photo credit: Tashatuvango/Shutterstock
-

CosmicDuke malware mashup steals login data to take over networks
Publié: juillet 3, 2014, 12:23pm CEST par Ian Barker

Security company F-Secure has uncovered a new malware attack that blends together elements of two earlier threats in an attempt to compromise enterprise networks.
CosmicDuke includes elements from the MiniDuke advanced persistent threat (APT) Trojan combined with the info-stealing Cosmu family. MiniDuke first appeared last year and was used in attacks against NATO and some European government agencies.
F-Secure has published a white paper which describes how CosmicDuke uses files and emails in a phishing attack to get users to compromise their system. Once installed it begins to gather information using keyloggers, screenshot grabbers and other techniques. This is then transmitted to remote servers so that attackers can use it to compromise more of the network and install more malware.
Sean Sullivan, security advisor at F-Secure says, "CosmicDuke isn't advanced in the way that MiniDuke was. But this is interesting as it moves towards a 'commoditized' not-for-profit info-stealer with connections to the existing crimeware ecosystem".
What's particularly worrying about CosmicDuke is that it overlaps elements of cybercrime with state-sponsored espionage. Sullivan adds that it could be, "...an organized actor (a 'contractor' perhaps?) who is gathering information to sell to a government. At the moment, crimeware which targets consumers is under attack by international law enforcement -- it is quite possible that the displaced crimeware vendors found a new buyer of information".
Decoy document names uncovered by F-Secure include titles referencing gas pipelines and the Ukraine which suggests this malware may be targeted against specific industries.
This is a very organized and professional attack and Sullivan advises businesses that, "You are a target. Keep calm and secure your stuff".
More details can be found in F-Secure's white paper or on the company's blog.
Image Credit: Brian A Jackson / Shutterstock
-

Post-Snowden era will make physical location of data irrelevant
Publié: juillet 2, 2014, 12:17pm CEST par Ian Barker

A new report from research specialist Gartner says that the physical location of data is becoming increasingly irrelevant and that by 2020 a combination of legal, political and logical location will be more important.
Gartner research vice president Carsten Casper says that the number of data residency and data sovereignty discussions has soared in the past 12 months, and that this has stalled technology innovation in many organizations. Originally triggered by the dominance of US providers on the Internet and the Patriot Act, the perceived conflict has since been fueled by revelations of surveillance by the NSA made public by Edward Snowden.
"IT leaders find themselves entangled in data residency discussions on different levels and with various stakeholders such as legal advisors, customers, regulatory authorities, employee representatives, business management, and the public," says Casper.
Gartner identifies four data locations for the new era. Physical location has in the past been associated with control but, now that data can be easily accessed remotely, Gartner advises that concerns about physical location should be balanced against other risks.
Legal location is determined by who controls the data, though there could be other organizations, such as service providers, that process and store it. Political location takes into account factors such as law enforcement access requests, cheap labor and international political balance. Gartner argues that these are only really important to public sector bodies or companies whose reputation is already damaged. Casper says, "Unless you fall into one of these categories, you can discount media reports on data residency concerns. While public outrage is still high about data storage abroad, there is little evidence that consumers really change their buying behavior".
Finally comes logical location which is determined by who has access to the data. All this can lead to quite complex situations where data can be in four places at once. As Gartner points out, what happens if a German company signs a contract with the Irish subsidiary of a US cloud provider that has its information physically stored in a data center in India? While the legal location of the provider would be Ireland, the political location would be the US and the physical location would be India but, logically, all data could still be in Germany. Confused? Thought so.
"None of the types of data location solves the data residency problem alone," says Casper. "The future will be hybrid -- organizations will be using multiple locations with multiple service delivery models. IT leaders can structure the discussion with various stakeholders, but eventually, it's the business leader who has to make a decision, based on the input from general counsel, compliance officers, the information security team, privacy professionals and the CIO".
You can read more in the report The Snowden Effect: Data Location Matters available on the Gartner website. The issue will be discussed further at a series of Security and Risk Management Summits, held in Sydney, London and Dubai in August and September.
Photo Credit: Andy Harbin/Shutterstock
-

Big data makes research more difficult say data scientists
Publié: juillet 1, 2014, 4:31pm CEST par Ian Barker

Given the amount of hype surrounding it you could be forgiven for thinking that big data is the answer to most business and scientific problems.
But a new survey by database specialists Paradigm4 reveals that almost three-quarters of data scientists believe that big data has made their research harder. The reason for this is not, as you might expect, the volume of data but the variety.
The results, from a survey of 111 US data scientists, show that 40 percent say they struggle managing new types and sources of data and 36 percent say that getting answers from big data takes too long.
Hadoop comes in for criticism too with 76 percent saying it's too slow, takes too much effort to program or has other limitations. So much so that 35 percent of scientists who have tried using Hadoop or Spark say they have now stopped using it.
Problems cited include 39 percent saying it takes too much effort to program and 37 percent saying it's too slow for interactive ad-hoc queries. 30 percent also say it's too slow for performing real-time analytics.
It seems that despite all this, however, big data still has a key role to play. 91 percent of those surveyed say they’re using or plan to use complex analytics on their big data within two years.
If you want further insight into the trials of being a data scientist, you can get hold of the full survey results on the Paradigm4 website or there's a summary of the findings in handy infographic form below.
Image Credit: aslysun / Shutterstock
-

Mobile Identity Connect provides secure single sign-on for enterprises
Publié: juillet 1, 2014, 3:00pm CEST par Ian Barker

One of the biggest concerns that businesses have about the increasing use of mobiles and BYOD is how to keep their data secure. Traditional security tools were built to cope with desktop devices rather than the on/off existence of mobile connections.
Mobile platform specialist Kinvey aims to help mobile developers to seamlessly secure mobile, tablet, and responsive Web apps with its newly-launched Mobile Identity Connect product.
Using already proven mobile standards, Mobile Identity Connect eliminates the complexity of authenticating mobile apps with existing enterprise security systems. It manages the mobile security layer and provides single sign-on using Kinvey's AuthLink Connector technology to bridge existing enterprise identity into a mobile-friendly OAuth-2 authentication flow.
By using secure pre-built mobile ID management it frees developers to concentrate on the user experience. It gives IT departments a controlled and secure self-service platform for app development which has the four key features required for all mobile applications: identity management, data services, business logic, and engagement services.
"Most enterprise-grade identity and single sign-on systems were designed in a pre-mobile world, and don’t take the unique challenges of mobile technology into account," says Sravish Sridhar, CEO of Kinvey. "Kinvey Mobile Identity Connect provides enterprise mobile developers an OAuth-to-anything connector to enable enterprise-grade security with authentication protocols designed with mobile in mind. Mobile developers don’t want to deal with the complexity of tying directly into identity systems that were not designed for mobile every time they build an app".
By managing the handshake between the mobile app, the identity system, and enterprise data, Mobile Identity Connect ensures that existing security policies are maintained and data can be consumed by the mobile app in a consistent manner across identity and data sources.
For more information Kinvey's backend as a service mobile development platform and Mobile Identity Connect, visit the company's website.
Image Credit: bloomua / Shutterstock
-

Comparing the top three cloud storage providers
Publié: juin 27, 2014, 12:55pm CEST par Ian Barker

Last year around seven percent of all data was stored in the cloud, but by 2016 it's estimated that 36 percent of data will be in cloud storage, generating a potential revenue of over $4 billion. Of current storage users, 38 percent say they already use the cloud with 34 percent planning to do so.
Salesforce and Google Drive linking specialist Cirrus Files has been looking at the three main public cloud providers, Dropbox, Box and Google Drive to see how their services compare in this fast-growing sector.
The good news for security is that all three services support the storage of encrypted files. In other areas though they differ quite a lot. When it comes to supported mobile platforms, Google only works on Android and iOS. Box and Dropbox both work on BlackBerry, but only Box supports Windows Phone and only Dropbox has a Kindle Fire version.
Based on the time taken to load a 13Kb publicly shared file, Dropbox is fastest, closely followed by Google with Box taking almost twice as long.
Google is the clear winner in terms of free storage though, offering 15GB compared to Box's 10GB and Dropbox's rather disappointing 2GB -- though you can earn more.
You can see the results of the comparison in infographic form below.

Photo Credit: Sakonboon Sansri/Shutterstock
-

Ignorance of digital dangers puts consumers at risk
Publié: juin 26, 2014, 3:31pm CEST par Ian Barker

Technology users are putting themselves at risk by ignoring how their personal information is being stored and the potential security risks that go hand in hand with digital devices.
This is the conclusion of a round table panel of security experts put together by hosting company UKFast. According to the panel the buzz of social media and the ever-evolving digital scene has created an ignorant culture of technology consumers.
Panelist Hugh Boyes from the Institution of Engineering and Technology at the University of Warwick, believes consumers need to realize exactly what their device is capable of, and precisely what information it holds. "People don’t understand exactly what these devices can do. Take a fitness band, for example. The product isn't actually the wristband; it's the data that is inside it. Yet no one is aware of this. The internet is everywhere, and so in turn, we give our personal information out everywhere. Things like social media, loyalty cards and GPS tracking for instance -- these things all require our personal information. No one hesitates in giving it away if it means being able to use a particular app".
This giving away of information is driven by a culture of convenience says Robert Fuller, director of Innevate, "Because things often seem to happen seamlessly, it doesn't lend itself to people having to think about what processes are involved".
This is echoed by Lawrence Jones, CEO of UKFast, "People are obsessed with speed and usability -- the faster and easier they can achieve something, the better. Even if that means storing your card details, passwords and personal details in the same place or using the same password for everything. It may be more convenient but it's significantly less secure".
Zain Hyed, director of security at Hybrid believes if consumers understood the risks, they would take greater care when handing out their personal details, "After all the Heartbleed media coverage, only 4 in 10 people actually changed their passwords. You'd expect everyone to change their passwords just to make sure they were secure, but unfortunately that wasn't the case. It’s the culture we are living in today -- no one understands the dangers".
The panel offers a number of tips for consumers to ensure that they stay secure. These are:
* Make sure that you install all patch updates and keep your software up to date.
* Have different passwords for each account, then if hackers get old of one password they can’t access your other data.
* Use long passwords, numbers/symbols and full phrase passwords are most effective.
* Read the news -- find out if any services or companies you use been hacked and what you need to do about it.
* Find out where your data is stored and how safely before trusting an organization with your information.Videos of this and previous round table discussions can be found on the UKFast.tv website.
Image Credit: JJ Studio / Shutterstock
-

Web-based analytics delivers intelligence on DDoS attacks
Publié: juin 25, 2014, 4:32pm CEST par Ian Barker

In recent days we've seen DDoS attacks hit some major names like Feedly and even force the CodeSpaces hosting service out of business.
In a bid to combat the threat presented by DDoS attacks, security specialist Corero Network Security has announced a powerful web-based analytics portal.
Corero SecureWatch Analytics delivers turn-key visibility into DDoS attacks and cyber threats with comprehensive and easy-to-read security dashboards. Using Splunk software for big data analytics and advanced visualization, Corero has made security intelligence much more accessible and easier to act on. This means that companies are able to react to threats much more quickly.
"Extracting meaningful information from volumes of raw security events has been a virtual impossibility for all but the largest enterprises with dedicated security analysts. Corero SecureWatch Analytics provides this capability in a turn-key fashion to enterprises of all sizes," says Nirav Shah, Director of Product Management at Corero Network Security. "Big data analytics engines are empowered by valuable raw data. By combining sophisticated event data generated by our industry leading First Line of Defense security appliances with the Splunk platform, we have created a solution that quickly finds the needles in the haystack of security events".
The portal's real-time dashboards provide easy-to-use visibility into an enterprise's network and security activity enabling rapid response in combating threats. Additionally, SecureWatch Analytics supports archived security event data to allow forensic analysis of past threats and compliance reporting of security activity.
SecureWatch Analytics is included with the purchase of Corero's SmartWall Threat Defense System and DDoS Defense System security products. For more information visit the Corero website.
Photo Credit: Duc Dao / Shutterstock
-

27 percent of websites aren't configured for smartphone searches
Publié: juin 25, 2014, 3:23pm CEST par Ian Barker

A new report from SEO and content marketing specialist BrightEdge reveals that although almost 60 percent of American adults own smartphones and 40 percent own tablets, more than a quarter of websites aren’t mobile friendly.
This leads to a massive loss of potential traffic and if marketers rectify this misconfiguration, the report discovered they stand to boost smartphone traffic by 200 percent.
"With smartphone website traffic growing at 10 times the rate of desktop, mobile websites are quickly becoming the cornerstone to content marketing and customer engagement," says Jim Yu, CEO and founder of BrightEdge. "We know that mobile will play an integral role in the future of marketing and want to help brands navigate the challenges that mobile presents. This report will help businesses understand the best ways to create mobile-optimized sites in terms of traffic and search rank, boosting customer engagement and, more importantly, ROI".
The report also shows the differences between desktop and mobile. It reveals that 62 percent of searches show different results depending on whether the search was performed on a desktop or smartphone and mobile ranks are typically half a position lower than desktop. Since click-through rates are sensitive to rank this can lead to a significant drop in traffic.
With smartphone traffic expected to grow by 50 percent in 2014 companies need to ensure that they pay attention to the performance of their sites on mobile devices. BrightEdge identifies three different approaches to providing mobile sites.
Responsive sites deliver the same content across all devices with only the presentation changing. Dynamic sites vary the HTML according to the device used although the URL remains the same, however, the report warns that if not well implemented this can look like the type of 'cloaking' used by malicious sites. The final approach is to have completely separate desktop and mobile versions of the site.
The report concludes, "As enterprises cater to the growing mobile market, BrightEdge data shows that all three approaches to mobile website configuration rank about the same for a given keyword if implemented correctly. We believe many brands will take on responsive design as their choice of mobile configuration, but what we've found in talking with customers is that one mobile configuration is not necessarily a one-size-fits-all solution".
You can find out more and download the report from the BrightEdge website.
Image Credit: bloomua / Shutterstock
-

ID stealing cloned banking app found on Play Store
Publié: juin 25, 2014, 1:19pm CEST par Ian Barker

A cloned banking app which steals user login credentials has been discovered on the Play Store this week. Mobile security company Lookout discovered the app and informed Google which immediately removed it.
The malware, called BankMirage, targets the customers of an Israeli bank called Mizrahi Bank -- the fourth largest in the country. The authors of the app placed a wrapper around the bank's legitimate app and redistributed it on the Google Play store, pretending to be the financial institution.
Once opened the app displays a login form which siphons off the user's ID as it's entered in a classic phishing attack. Oddly though it captures only the ID and not the password. Once it has the ID the app returns a message to the user saying that the login failed and to, instead, reinstall the legitimate banking app from the Play Store.
Banking malware is, so far, less common in the US than it is in Europe and the Far East. Korean malware PlayBanker, for example, pretends to be Google Play and sends out push notifications to lure victims into downloading rogue banking apps. Another piece of malware, BankUn, will check for the presence of eight major, legitimate Korean banking apps and then attempts to replace them with rogue ones.
The problem with an app finding its way onto the Play Store is that turning off Unknown Sources on your phone isn't going to protect you. Lookout recommends that you be wary if apps you want to download have duplicates as this may indicate illegitimate copies, and that you have an up to date app scanner on your device.
Image Credit: mama_mia / Shutterstock
-

New Seismic release gives sales and marketing teams a competitive edge
Publié: juin 23, 2014, 3:00pm CEST par Ian Barker

Cloud-based sales platform specialist Seismic is launching a new version of its product aimed at giving marketing teams a deeper insight into how their material influences actual sales.
It's focused on increasing conversion rates for B2B sales, shortening sales cycles and boosting customer retention rates.
"Given marketing automation's rise in the last five years, today's B2B sales funnel is half in the light and half in the dark", says Doug Winter, CEO of Seismic. "Sales and marketing teams have almost perfect visibility into how leads interact with the top half of the funnel and the insights needed to improve the marketing process, yet they remain blind to how content is supporting sales reps in the bottom half. Seismic's latest release illuminates the bottom half of the sales funnel -- a blind spot for most marketing teams who send sales materials over the proverbial 'Chinese Wall' -- providing them with the information and content delivery platform their sales teams need to accelerate sales and increase close rates".
Features of the new release include sophisticated content analytics with drag and drop simplicity to provide a holistic view of effectiveness. This is supported by content creation tools which allow marketers to quickly deliver on generating materials for team and individual tasks.
A LiveSend feature means sales reps will be notified when prospects view content and can even see how much time has been spent on each page of an attachment. This not only helps show which content is most effective but also provides material for follow up conversations.
In addition LiveShare makes it possible to instantly share screens with prospects in order to increase engagement. Combined, these features in Seismic's platform give marketing teams the ability to measure and analyze how prospects interact with content sent by sales reps. Armed with this information they can determine which content is the most engaging and create a successful sales strategy that puts personalized content in front of the customer.
For more information on the latest Seismic release or to request a demo of the product you can visit the company's website.
Photo Credit: EDHAR / Shutterstock
-

Finding social media trends automatically
Publié: juin 23, 2014, 11:41am CEST par Ian Barker

Social media is increasingly important to brands, both as a marketing tool and in terms of managing their image. But fully monitoring and understanding social trends is impossible using only human analysts.
Data intelligence specialist Bottlenose has launched a solution in the form of Nerve Center 2.0, which gives brands the ability to act on social and media-driven trends in real time using automatic trend detection and alerts, emotion and demographic analysis, and open APIs.
"The automatic trend detection in Nerve Center 2.0 alleviates the need for constant attention from human analysts. Now, without having to monitor the platform 24/7, users can be alerted of any important trends such as breaking news, emerging influencers, viral content, bursting topics and hashtags, and spiking sentiment", says Bottlenose CEO and co-founder Nova Spivack. "This eliminates the choke point of humans in the process of real-time comprehension of patterns in vast amounts of data. And that's just the beginning. In the future, our platform will be able to spot a growing repertoire of complex patterns and trends in data streams. We are automating the analyst, one skill at a time".
Key features of Nerve Center include automatic trend detection with customizable alerts to remove the need for constant human monitoring. Advanced emotion profiling and demographics using sample profile data for 350 million social media participants leads to 95 percent average accuracy. The underlying platform, StreamSense, can analyze over three billion messages per hour.
Customers can use the software to identify audience characteristics including occupation, age, family status, brand affinities and more. Bottlenose is also releasing APIs for developers and customers who want to use trend intelligence for visualization, process automation, advertising, and new analytics applications.
You can find out more about Nerve Center on the Bottlenose website.
Photo Credit: ra2 studio/Shutterstock
-

Elasticsearch releases new Hadoop connector
Publié: juin 20, 2014, 4:07pm CEST par Ian Barker

Search analytics specialist Elasticsearch has announced the 2.0 release of its Hadoop connector, bringing advanced search techniques to the popular big data platform.
It's also now certified for Cloudera Enterprise 5. This means Elasticsearch is now compatible across all Apache-based Hadoop distributions, helping businesses extract immediate insights regardless of where their data is stored.
Using Elasticsearch in conjunction with Hadoop, organizations no longer need to run a batch process and wait for hours to analyze their data. Elasticsearch for Apache Hadoop can make data available for indexing as it's being generated, making it available for search and analysis in a matter of seconds.
Steven Schuurman, co-founder and CEO of Elasticsearch says, "Hadoop was created to store and archive data at a massive scale, but businesses need to be able to ask, iterate, and extract actionable insights from this data -- which is what we designed our products for. With today's certification from Cloudera, Elasticsearch now works with all Apache-based Hadoop distributions, and with it, solves the last mile of big data Hadoop deployments by getting big insights, fast".
Key features of the new release include the ability to read and write data between Hadoop and Elasticsearch which lets businesses get immediate, actionable insights using real-time search and analysis. There's native integration and support for popular Hadoop libraries so users can run queries natively on Hadoop through MapReduce, Hive, Pig, or Cascading APIs. A Snapshot/Restore feature also makes it easy to take a snapshot of data within Elasticsearch -- perhaps a year's worth -- and archive it in Hadoop. At any time, this snapshot can be restored back to Elasticsearch to carry out extra analysis.
You can register for a webinar set to take place on August 20 which will discuss the features and benefits, or go to the Elasticsearch website to find out more.
Image Credit: alphaspirit / Shutterstock
-

Request legally binding signatures via any email client
Publié: juin 20, 2014, 12:33pm CEST par Ian Barker
Email may have revolutionized business communication, but if you need a signature on a contract or business document in most cases you still have to send it through the post or use a cumbersome e-signature app.
Until now that is, Barcelona-based startup Signaturit has a new solution that enables you to request handwritten signatures through any email client.
The technology complies with the EU and US e-signature laws and spares users the need to visit third-party websites or download apps.
After signing up all it takes to request a handwritten signature through Signaturit is sending a PDF file using your preferred email client and adding ".signatur.it" to the end of the signatory's address. The platform not only keeps a record of the email address, the name of the file, the location and the exact time it was signed by a Time Stamping Authority (TSA), but also uses a state-of-the-art biometric authentication system and the same encryption standards used by banks and government agencies to ensure the integrity and validity of each signature.
Juan Zamora, CEO of Signaturit says, "While e-signature is a tried and true technology, the increasingly demanding regulatory and legal requirements for binding electronic signatures threatens the easy-to-use nature of the solutions available in the market. That is why Signaturit not only provides the simplest solution by allowing users to request signatures through their email client of choice, but does so in compliance with the most demanding data protection requirements".
The technology allows deals to be closed faster and saves on traditional document costs by eliminating the need for printing and scanning. It offers real-time reporting along with a dashboard where users can view the status of each transaction.
The service is available now and there are pricing models for various sizes of business. You can get more information and try out the service for free on the Signaturit website.
-

Heartbleed: Really that bad?
Publié: juin 20, 2014, 11:04am CEST par Ian Barker

Most information security scares come and go with relatively little fanfare, some though make a splash and catch the attention of the public and media.
Heartbleed was the latest to fall into the latter category and sent the IT world into a bit of a frenzy. But how bad was it really? Security specialist Secunia rates vulnerabilities on a one to five scale and given the amount of publicity it received you might expect Heartbleed to be at the top end.
In fact Secunia only rates it as a "moderately critical" three, a score usually used for denial of service vulnerabilities against services like FTP, HTTP, and SMTP, and for vulnerabilities that allow system compromises but require user interaction.
Secunia's Director of Research and Security, Kasper Lindgaard explains, "It gets this rating because it enables information retrieval from remote without any user interaction or authentication requirements".
He goes on to point out that the extremely critical rating is reserved for, "Remotely exploitable vulnerabilities that can lead to system compromise, where successful exploitation does not normally require any interaction and exploits are in the wild".
The company does acknowledge though that the effect of Heartbleed depends to an extent on the size of the vendor. Lindgaard says, "Small vendors didn't have such a big ordeal with the vulnerability, however for larger vendors like Cisco, IBM and HP, it was -- and is -- a very different story: they will be hard at work on this one, for some time yet. Thus the costs and implications for large vendors is what will make the Heartbleed bug a long term problem".
You can read more on Lindgaard's blog and Secunia has produced an infographic charting the timeline of the bug which you can see below.
-

How the mobile threat landscape is challenging companies’ ability to respond
Publié: juin 19, 2014, 7:57pm CEST par Ian Barker

As with cyber security generally, the mobile threat landscape is constantly evolving. So although businesses may have invested heavily in solutions like antivirus and mobile device and application management they can’t afford to relax.
Mobile security specialist Zimperium, the company that uncovered the recent LinkedIn flaw has released a whitepaper looking at the attack vectors that specifically target mobile devices.
The whitepaper highlights a number of attack vectors that specifically affect mobile devices. The main focus of these is network attacks and, as of today, existing solutions in the market do little to address these threats.
The market highlights Apps as one of the most dangerous threat vectors, with huge recent increases in mobile malware targeting Android likely to top the million mark by the end of the year. Although significant in volume, other types of attacks have the potential to cause significantly more impact to organizations.
Zuk Avraham, CEO and co-founder of Zimperium, says, "apps are seen as the most dangerous threat, but if you're sent one at random it's unlikely you're going to install it. Network threats, links or files like PDFs that hide malicious content are in fact more dangerous".
Enhancing network protection becomes more important as more companies adopt BYOD or CYOD policies. The mobile arena is still quite immature in terms of intrusion prevention systems and the report highlights the need for a robust solution to supplement first-generation protection technologies. It also points out that when it comes to advanced network threats both Android and iOS share the same risks.
For a more detailed look at the threat landscape you can download the whitepaper from the Zimperium website. You can also check out the company's ZANTI mobile penetration testing toolkit.
Image Credit: Anan Chincho / Shutterstock
-

The future face of mobile marketing and why companies must adapt
Publié: juin 19, 2014, 4:09pm CEST par Ian Barker

Companies spend a lot of time looking for the best marketing tools to reach their customers and convert communication into sales. Part of this involves collecting information about people's preferences.
Online form specialist Formstack recently published its Form Conversion Report on what makes people fill in online forms. Based on the data from this it's now released some predictions on the future of digital marketing.
The first and most important is that mobile marketing is becoming essential, not just an option. With growing numbers of people who exclusively use their phones to access the Internet, businesses need to embrace this trend.
Online forms can help capture information to generate leads but Formstack predicts that it’s the quality of the information which will become key. As personalized content becomes a more common part of our online life, customers will begin to expect a customized experience from marketers rather than a one-size-fits-all solution.
Features like "smart" forms are likely to play a part in this. Smart logic lets marketers hide sections of their web forms. These hidden questions are only revealed when a user selects certain options. This lets marketing teams obtain relevant information without scaring away customers with a long form.
Finally it predicts that marketers will need to take advantage of third-party apps to generate more leads. Integrating data collection with popular marketing apps will create more tailored lead generation. This can then be followed up by triggering actions through email marketing platforms or CRM systems so that every customer is engaged in a unique way.
The future of digital marketing then is in data collection and management. As marketers gain more information about their customers, they will be increasingly able to reach them with desirable content. You can find out more on Formstack's website about how the company's offerings can help.
Image Credit: 3Dmask / Shutterstock
-

Never miss a caller again with the i-Bell
Publié: juin 19, 2014, 1:33pm CEST par Ian Barker

Wouldn't it be useful to know there is someone at the door when you're out in the garden or even when you're away from home completely?
The people behind the i-Bell, which launches its crowd funding campaign this month, obviously had the same thought. A Wi-Fi enabled doorbell, it lets you use your smartphone to see and even communicate with whoever is at your door. You can tell the delivery man to hang on a second or leave the package in a safe place for example.
Designed in the UK, the i-Bell can be used with any PC, tablet or smartphone. Its integrated 1080p camera, speaker and microphone means you can screen callers and high security brackets mean it will stay attached to your front door.
Graham Kershberg, co-founder of i-Bell, says, "there's nothing quite like i-Bell on the market right now. It's going to revolutionize daily life for a lot of individuals and businesses. Arranging deliveries around working hours or getting an unexpected visit from a relative who gets no answer at the door can really disrupt an individual's plans. But now it's possible to communicate directly with the person ringing the doorbell, let the postman know where to leave a package, or telling Aunt Mabel that you'll be home as soon as possible without even being on the premises. Fun to use and practical, i-Bell makes it possible to answer the door from any corner of the world, whether that’s five minutes down the road on the school run or from a sun lounger overseas on a long awaited holiday."
You can find out more and pre-register to get information as the product moves towards launch by visiting the i-Bell website.
-

ChargeKey changes its name and offers 25 percent discount for BetaNews readers
Publié: juin 19, 2014, 11:40am CEST par Ian Barker
 You might recall that we recently reviewed the ChargeKey and ChargeCard USB charging gadgets. These are now being relaunched with an updated design using more durable materials and have had a name change to NomadKey and NomadCard -- though we’re guessing they won't recharge your camel.
You might recall that we recently reviewed the ChargeKey and ChargeCard USB charging gadgets. These are now being relaunched with an updated design using more durable materials and have had a name change to NomadKey and NomadCard -- though we’re guessing they won't recharge your camel.There's also an extra product, the carabiner-style NomadClip that you can fit on your key chain, belt or anywhere else to ensure you’re never without a charger. It’s non-load bearing but with a steel frame and polycarbonate outer shell it should be tough enough to survive life's day-to-day knocks.
As with the other devices it's available in Apple Lightning connector -- MFI certified by Apple to work with their products -- and microUSB format for most Android and many other devices. To celebrate all of this the company is offering readers a 25 percent discount for the next week on pre-orders of the new products.
Use the code LIVESIMPLE when ordering from the hellonomad.com website to claim. Shipping is free to the US, Canada, Australia and the UK with a $5 flat rate anywhere else in the world.
Visit the revamped Nomad website for more information.
-

End users are the biggest headache say security professionals
Publié: juin 18, 2014, 6:10pm CEST par Ian Barker

Business security specialist Bromium has released the results of a survey of over 300 IT security professionals looking at endpoint threats.
It finds that the majority believe end users to be the biggest security headache, that existing security solutions are unable to stop endpoint infections, and that antivirus can’t stop advanced, targeted attacks.
Previous research has found that most attacks are aimed at user devices so it’s understandable that 72 percent of information security professionals believe users are their biggest security problem. User devices can be compromised by drive-by downloads, system vulnerabilities and email attachments, yet it can be time-consuming and expensive for information security teams to fix these problems.
More than 84 percent believe that their current security doesn't stop all endpoint infections and a similar percentage believe that their existing antivirus solution doesn’t stop targeted attacks like spear phishing.
"The reality today is that existing endpoint protection, such as AV, is ineffective because it is based on an old-fashioned model of detecting and fixing attacks after they occur," says Rahul Kashyap, chief security architect at Bromium. "Sophisticated malware can easily evade detection to compromise endpoints, enabling cyber criminals to launch additional attacks that penetrate deeper into sensitive systems. Security professionals should explore a new paradigm of isolation-based protection to prevent these attacks".
Other findings from the survey are that two-thirds (65 percent) of information security professionals are looking for endpoint protection that is able to stop both known and unknown threats. Also 75 percent said they would sleep better at night knowing a user could click on anything at any time without risk of infection.
"Despite the challenge in protecting end users, it is encouraging so many security professionals are aware of the shortcomings of existing technology," adds Kashyap. "The recognition that the status quo is broken is the first step toward changing it for the better".
You can read more details of the report on the Bromium blog.
Image Credit: Robert Kneschke / Shutterstock
-

Using online dating mobile apps risks leaking your personal data
Publié: juin 18, 2014, 3:33pm CEST par Ian Barker

One in five adults in the US aged between 25 and 34 have used an online dating site and mobile apps have opened up a new channel for these services to reach their clients. But this does raise concerns about the level of privacy and how user data is being protected.
Mobile security specialist nVisium has looked at the features in 30 of the most popular dating apps for iOS and Android. It found that 80 percent of the apps leaked personal information to third-party services and that 70 percent had issues that would allow a user's real identity to be disclosed.
Other findings include the fact that 60 percent of apps send information across the internet without protection and 50 percent store information on the device without security.
To use a dating app you generally need to tell it a lot about who you are, information like addresses, dates of birth, phone numbers and so on. Leaking one or more of these things can give away your real identity and leave you open to social engineering or worse.
Half of apps were found to be storing user login credentials in an unencrypted form, potentially allowing them to fall into the wrong hands, and only six percent offered in-app passcode locking.
If your information does leak you're going to need that GSOH, so to protect yourself nVisium recommends that you turn off location sharing and advertisements in the app settings. You should also remove the geolocation data from the Exif information of files that you share. Finally you should set a passcode on your device as a first line of protection and take care not to leave your phone unattended.
You can see the findings of the study in infographic form below.
Image Credit: Nomad_Soul / Shutterstock
-

The challenges of securing Amazon Web Services
Publié: juin 18, 2014, 12:59pm CEST par Ian Barker

Amazon Web Services is the world's most popular infrastructure as a service (IaaS) platform and is built to suit enterprises of all sizes looking to reduce their computing costs by shifting to the cloud.
One of the key considerations in such a move is keeping data secure and AWS has various free and chargeable mechanisms to help with this. A new report from NSS Labs looks at the advantages of AWS as well as some of the challenges organizations face when moving to an (IaaS) environment.
Among the findings of the report are that Amazon is gaining popularity thanks to offering key baseline security attributes and controls as well as the availability of security options from Amazon and other vendors.
Report author Rob Ayoub writes, "The deployment of IaaS is straightforward -- customers purchase access to virtual machines directly in the cloud. However, this simple act opens up a host of opportunities for outsourcing, allowing organizations the ability to practice true utility computing -- adding or subtracting servers, storage, and other services on demand".
AWS offers basic security controls including a firewall, groups and virtual private cloud infrastructures, but doesn’t yet offer a full suite of security tools. However NSS notes that many end users don't fully understand the security implications of moving their operations to an IaaS provider and may not be implementing secure practices.
It also says that it isn't enough for organizations to simply port applications and data to the cloud and assume that compliance will be addressed.
Recommendations for companies moving to AWS include assessing the security controls offered by AWS and evaluating the additional controls available from third-party technology partners. This will ensure that security policies will remain consistent as data is shifted to the cloud.
It's also important to evaluate and understand the gaps in security between on-premise systems and IaaS. Enterprises should incorporate AWS implementations into the life cycle management process used for other systems.
Companies need to have procedures in place to ensure end users aren’t creating AWS instances without IT approval. Finally they need to ensure any regulated data moved to AWS is still in line with compliance policies.
If you're considering the use of AWS for your business, or you're using it already, you can access the full report on the NSS Labs website.
Photo Credit: Marynchenko Oleksandr / Shutterstock
-

Flipora updates its discovery engine and this time it’s personal
Publié: juin 18, 2014, 11:01am CEST par Ian Barker
Relying on search engines or social networks to discover things you're interested in on the net can be a bit hit and miss. The things you see on your Facebook feed for example are influenced by your friends' interests as well as your own.
Flipora aims to change the process of following your interests online by using artificial intelligence to make recommendations related to the things you really want to see.
It analyzes your browsing and social media activity via a browser extension and learns the kind of things you're interested in. It will then recommend other articles and sites based on what it finds. Because it's constantly monitoring what you look at its recommendations evolve over time allowing it to make "mood aware" choices without you having to do anything.
Jonathan Siddharth, Flipora's co-founder says, "Facebook isn't targeted and nor is Twitter but 99 percent of people use these for web discovery. Flipora looks at all the web not just sites you share with your friends and so is able to make better recommendations based on your current interests".
Flipora 2.0 has a sleek new interface and works automatically without you having to specify what you're interested in. As soon as you login to the site with Facebook it will begin to analyze your timeline and suggest topics to follow.
Install the browser extension -- available for Chrome, Firefox and Internet Explorer -- and it will also look at your browsing history to improve its accuracy. For example, if you've been looking at sites related to the World Cup it will recommend other football content via a side panel or a slider in the corner of the page. If your interest wanes when the tournament is over Flipora will quickly adapt as you visit these sites less.
You also have the option to share your website discoveries with people who have the same interests rather than putting them on other social networks where they'll risk getting lost in the background noise.
Flipora 2.0 launches today and you can try it for yourself at flipora.com, the company hopes to have 40 million users by the end of 2014.
-

BlackBerry brings protected messaging to the enterprise
Publié: juin 16, 2014, 4:40pm CEST par Ian Barker

One of the major concerns of mobile use in the enterprise is keeping company data secure. BlackBerry Messenger (BBM) already offers a reliable messaging service with millions of users worldwide, but now with the launch of a new service it lets employees benefit from speedy, reliable and private business communication.
The new BBM Protected service offers enhanced security for messages sent between BlackBerry devices by adding an extra layer of encryption to the standard BBM which encrypts messages in transit.
BBM Protected incorporates three layers of security in transit. Messages between users of the system are protected by encryption using unique public/private keys. A 168-bit key is used to encrypt and authenticate messages, and TLS transport layer encryption helps protect against eavesdropping in transit. It also protects data on the device, building on the existing BlackBerry security model.
A key feature of BBM Protected is that it's seamless for the end user. The same app is used for both company and personal BBM messages, if the recipient is also a Protected user the extra encryption is automatically applied. This means it can be used to chat securely to BBM Protected users at other companies too without any extra configuration being needed. It also offers notifications so that you can be sure the recipient has read your message.
Because it's designed for mobile from the outset it offers better performance than other enterprise IM clients that originated as desktop solutions.
For companies that are already using BlackBerry Enterprise Server, BBM Protected can be easily deployed via the existing management console. It offers full logging and auditing features to ensure compliance too.
You can find out more and see the full system requirements on the BlackBerry website.
Image Credit: Diego Cervo / Shutterstock
-

Comodo introduces new mobile device management features
Publié: juin 16, 2014, 11:51am CEST par Ian Barker

One of the best ways for businesses to cope with the demands of mobile usage and BYOD is to use a mobile device management solution to allow the IT department to stay in control.
Security specialist Comodo has announced a range of new features to enhance its existing MDM product and make it more attractive to administrators needing to secure and manage large-scale deployments of mobile devices.
Comodo MDM has an integrated antivirus engine and allows admins to define device and identity certificates. It allows asset and application management but unlike some other solutions Comodo licenses users rather than devices, allowing each individual to protect up to five devices. This makes administration easier as although you may not know how many devices are in use you should know how many users you have.
New features in the latest version include an application catalog for Android allowing admins to define recommended or mandatory applications which can be managed via an enterprise store. A similar application management feature is available for iOS systems.
Admins are able to define stricter policies on Samsung SAFE supported devices. This allows them to define Wi-Fi and VPN configurations, remove options like screen capture, copy/paste, USB connections and more. An access control feature allows restrictions on devices that can access the company mail server.
There's also enhanced group management and a better GUI plus improved communication speeds and the whole thing can be administered from a central console.
You can find out more about the product’s features and download a free trial version on Comodo's website.
Image Credit: jannoon028 / Shutterstock
-

Business teamwork is a game of two halves
Publié: juin 13, 2014, 2:58pm CEST par Ian Barker

It may not have escaped your notice that the FIFA World Cup tournament has started in Brazil this week. This is of course an excuse for every PR agency to come up with football related ways of promoting their products.
Business collaboration specialist Huddle has chosen to focus on the teamwork aspect which does at least have a relevance to its product. It helpfully points out that on the field players have to work together to achieve success and the same is true of the workplace.
Huddle’s CEO Alastair Mitchell says, "Collaboration is a team sport. It means many different things to different people, but collaboration essentially involves a group of individuals working together across boundaries to achieve a common goal. In today’s workplace, the network of people that an individual has to work with on a regular basis extends far beyond their own organization’s four walls and includes customers, partners and contractors. One of our customers, for example, works with more than 1,000 other companies in its Huddle workspaces. For people to get their jobs done effectively and be truly productive, all relevant parties have to be able to seamlessly work together on content regardless of where they are based or the devices they are using".
The serious point about this is the need to collaborate outside as well as inside the organization. Figures from Huddle's client base show that 85 percent of its customers use the service for external collaboration. And 47 percent use it to collaborate with more than five other companies.
This is backed up by recent Forrester research which shows that in a survey of almost 5,000 North American and European information workers 57 percent say they regularly collaborate and communicate with customers, colleagues or business partners. Only 12 percent work exclusively with their colleagues.
You’ll be over the moon -- or possibly sick as a parrot -- to find that all of this is summarized in the inevitably soccer-themed infographic below.
Image Credit: dotshock / Shutterstock
-

FakeOFF helps you spot the fiendish Facebook fakers
Publié: juin 13, 2014, 11:48am CEST par Ian Barker
Back in 2012 Facebook estimated in its official company filings that almost nine percent of the accounts on its system broke the service's rules in some way. That may not sound like many but the sheer number of Facebook users means it accounts for some 83 million problem accounts.
Some of these might simply be duplicates but others have a more undesirable purpose like spamming, distributing malware or grooming minors. Until now the only way of steering clear of the fakes was by keeping your wits about you and looking for tell tale signs like recent join dates or unfeasibly model-like profile pictures.
Now though a newly released beta online tool called FakeOFF can analyze your timeline and alert you to possible fake activity.
FakeOFF analyzes usage patterns and assigns each "friend" an easily intelligible 1-10 ranking for likely fraud. Users can create "suspect" lists and receive automatic notifications regarding suspicious activity. FakeOFF also scans photos to determine if they are genuine, and it guarantees its users full privacy and control of their usage.
"The internet is a tremendous platform for networking and for connecting socially, but many of the same things that make it so useful also undermine its safety," says FakeOFF Founder Eliran Shachar. "A lot of people are wary about the interactions they or their loved ones are engaging in on sites like Facebook, and that is with good reason. You wouldn't let just anyone into your house, right? But people are much looser with their online behavior, even though the level of access people can gain to your life just through a Facebook account is considerable".
FakeOFF relies on a sophisticated algorithm to assess user activity -- including feeds, likes, photos, shares, and responses -- going back as far as 365 days on your timeline. The system then sends back a straightforward numbered score, along with a basic chart to help the user interpret it. Users pick the friends whose identities they are unsure of, and can track their activity using real-time security updates.
The basic version is free to use, and allows for timeline scans going back 10 days. For a $1.99 fee, the Advance One package allows for a single but comprehensive investigation that includes 365-day timeline and activity analysis and unlimited photo assessments using FakeOFF's Image Fraud Scan program. A regular subscription at $9.99 gives users unlimited access.
Sachar says, "Sometimes all you need is to look into one person: a potential romantic interest, for example. And in other cases, users like concerned parents will be interested in more comprehensive coverage. FakeOFF is flexible in that sense".
You can find out more and try out the free version by visiting the FakeOFF website.
-

Spanning launches 100 percent restore guarantee for Google Apps
Publié: juin 10, 2014, 3:42pm CEST par Ian Barker

Backup specialist Spanning Cloud Apps has made two announcements to help cement its position as a trusted SaaS backup and recovery provider.
The first is an update to its backup product for Salesforce. This includes on-page Salesforce data restore which makes it easy for end users to quickly and easily compare and recover previous versions of Salesforce data objects, such as Accounts, Opportunities and Contacts. As before the backup product is delivered entirely via the Salesforce interface.
It lets users initiate the restore process by simply clicking the Restore button within a record and then comparing and selecting individual fields to restore within object records, such as phone numbers, activity logs or attachments. The process requires little or no training for the user and, says the company, is completed more quickly and more accurately than any other available methods. Spanning Backup for Salesforce enforces field-level security, ensuring that users only see and restore data they are authorized to edit.
More interesting to most people though will be the launch of a Google Apps 100 percent restore guarantee. Through this offer, the company guarantees that customers who use Spanning Backup for Google Apps to backup their data will be able to restore lost data back to its original state 100 percent of the time. If it fails they will receive ten times their money back for each failed restore operation for that user account.
Spanning Backup for Google Apps has proactive status reporting to ensure that customers are alerted if any data isn't properly backed up on a daily basis. This helps to ensure that all files are protected and always available if ever data is lost.
"SaaS applications provide users with reduced cost, increased flexibility and higher business productivity," says Jeff Erramouspe, CEO of Spanning Cloud Apps. "Nothing disrupts productivity more than data loss events, which happen far more often than most companies realize. Spanning is committed to maintaining productivity by ensuring that lost data is restored quickly and accurately by the end user without the need for IT intervention. Losing data is something that Spanning customers don't need to worry about when using Google Apps or Salesforce".
The update for Spanning Backup for Salesforce is available to customers from today in the Salesforce AppExchange as a free 14-day trial and costs $30 per-user, per-year for a subscription with unlimited storage.
Spanning Backup for Google Apps can also be had as a free 14-day trial and costs $40 per-user, per-year with unlimited storage. Visit the Spanning website for more details.
Image Credit: Modella / Shutterstock
-

ChargeKey and ChargeCard ensure you’ll never be without a USB charger cable again
Publié: juin 10, 2014, 12:15pm CEST par Ian Barker

As we become more and more reliant on mobile gadgets it's inevitable that running out of battery life on your phone or tablet will become a regular occurrence.
Since we don't tend to carry chargers around with us all the time this can be a bit of a problem. If you have access to a USB port, however, your problems may be over.
The Nomad ChargeKey attaches to your key ring and means you'll always have the ability to charge your smartphone from a PC or an in-car USB port. It's available in iPhone 5 and micro USB formats. The latter should cope with most Android smartphones and tablets as well as many MP3 players and other gadgets. The ends are molded in hard plastic and the middle bit is a flexible rubbery material so it will adapt to different positions and it's robust enough to survive day-to-day life.
Unlike the Lumsing battery pack that Mark reviewed yesterday, however, the ChargeKey isn't suitable for use as a murder weapon -- unless you could get your victim to choke on it.
Its sister product the ChargeCard does the same job but is in a credit card-sized format that can be slipped into your wallet. This feels like a rather less elegant design as you have to bend the USB connector back over itself in order to connect it. It works well enough but we'd be a bit worried about its longevity.

Both products are available direct from Nomad and are priced at $29 each regardless of format. If you're in the UK you can order them from Amazon where they cost £20 each.
If you suffer from what the electric car world calls range anxiety with your smartphone or tablet then it's worth thinking about adding one of these gadgets to your key ring or wallet. We'd opt for the smaller and more elegant ChargeKey but either will do the job.
-

Free cloud-based protection against spear phishing
Publié: juin 9, 2014, 11:38am CEST par Ian Barker

The biggest threat to both organizations and individuals online comes from zero-day exploits that aren't picked up by conventional antivirus protection.
In many cases an infection starts with a phishing email which can appear legitimate but contains links to malicious content.
Protection specialist Votiro already provides a free data sanitization service to scan for malicious code in files but it’s now extending its service to guard against spear phishing and other email-based attacks.
It allows users to forward questionable emails to the service and runs the same anti-virus scanning and active process on the email contents along with any links and attachments. This ensures immediate protection and enhanced usability.
"Statistics consistently show that nearly all cyber attacks begin with a spear phishing email that appears to be innocent, although its contents, links or attachments are tainted with hidden malware and similar advanced cyberthreats," says Itay Glick, Founder and CEO of Votiro. "Our mission is to position our customers with a security posture that automatically identifies and eliminates the growing range of unknown and ongoing cybersecurity threats. By extending our free service, we are allowing enterprises and organizations to sample the strengths and benefits of our new spear phishing protection capabilities that are being incorporated into our overall solution".
Votiro's free service is intended to demonstrate the strengths of the overall solution, which automatically stops spear phishing and file-based attacks before these exploits have the opportunity to reach an internal network.
The scanning service doesn't affect the usability of a file and the solution can be seamlessly integrated into an organization's IT infrastructure.
The free file sanitization service is available at https://cloud.votiro.com/ and spear phishing protection can be accessed by forwarding suspicious emails to cloud@votiro.com.
Photo Credit: Ivelin Radkov/Shutterstock
-

Over half of organizations suffer critical system outages
Publié: juin 5, 2014, 12:18pm CEST par Ian Barker

System outages remain a major problem for businesses, with over half suffering critical problems in the last three months according to a new report.
The latest annual Service Availability Benchmark Survey conducted by risk management specialists Continuity Software is based on responses from 155 IT professionals across a range of industries and regions.
The report is designed to allow business continuity and disaster recovery professionals to compare their company’s practices and performance with their peers. Key findings are that 59 percent of companies had an outage in the last three months and 28 percent in the past month. Of those surveyed 41 percent had missed their service availability targets for mission-critical systems at some point in 2013.
It does seem that the problem is being taken seriously though, with 66 percent of respondents saying that they have initiatives in place for improving service availability in 2014. Businesses are also keen to prevent problems before they become serious. Proactive identification of risks is seen as being the top challenge in ensuring system availability by 20 percent of respondents.
"It is discouraging to see that such a high percentage of organizations continue to miss their service availability goals, despite the tremendous effort and investment made across the infrastructure", says Doron Pinhas, CTO of Continuity Software. "IT teams are finding themselves in a never-ending chase to keep up with the pace of change across the IT landscape. As the survey results show, IT organizations are increasingly recognizing that a proactive approach to risk identification is more effective for outage prevention than playing catchup".
The full 2014 Service Availability Benchmark Survey is available to download from the Continuity Software website.
Image Credit: alphaspirit / Shutterstock
-

Companies need a data-centred security policy to cope with big data
Publié: juin 4, 2014, 3:42pm CEST par Ian Barker

Big data is all the rage at the moment but when it comes to security it shouldn't be treated in isolation from the rest of the organization.
According to a new report from research specialists Gartner, policies need to take account of all forms of data if security problems are to be avoided.
"Businesses have traditionally managed data within structured and unstructured silos, driven by inherent requirements to deploy relational database management systems, file storage systems and unstructured file shares", says Brian Lowans, principal research analyst at Gartner. "However, the advent of big data and cloud storage environments is transforming the way in which data is stored, accessed and processed, and CISOs need to develop a data-centric security approach. Unfortunately this is not common practice today, and its planning is critical to avoid uncoordinated data security policies and management".
Gartner recommends that CISOs need to collaborate with trusted team members across the organization to develop and manage their enterprise data security policy. This needs to define data residency requirements, stakeholder responsibilities, business needs, risk appetite, data process needs and security controls.
Access to public cloud services complicates things further with a growing need to monitor and audit data access. Most current security solutions don't offer the data-centric audit and protection (DCAP) approach needed to work in the same way across all data silos.
"First, CISOs need to evaluate current implementations of DCAP solutions against data security policies that address database, unstructured, cloud storage and big data silos", says Lowans. "Second, they need to identify gaps in the current implementation of their data security policies and review the risks with business stakeholders against potential DCAP solutions".
This will need stakeholders to take on ownership of the data in many cases and work with security teams to ensure that it's properly protected. Which in turn may mean putting in place new management structures to ensure accountability.
Gartner subscribers can access the full report and the security outlook will be discussed further at a series of Security and Risk Management summits to be held at various venues around the world later this year.
Image Credit: Jojje / Shutterstock
-

HP targets business users with new laptop/tablet hybrid
Publié: juin 4, 2014, 10:51am CEST par Ian Barker

Mobile workforces demand devices that are powerful enough to perform a range of functions but still retain maximum portability.
Convertible PCs that can play the role of laptop and tablet by flipping the screen around are an obvious choice. HP's latest announcement though takes a slightly different approach with a tablet that detaches completely from the keyboard to offer added flexibility.
HP claims that the HP Pro x2 612 is its first commercial detachable PC designed from the ground up for enterprise users. It features a 12.5-inch display, a choice of Intel Core i3 and i5 processors, and dual HD webcams. Security features include HP Client Security, HP Sure Start and an optional fingerprint reader.
"While the use of technology in business has allowed a blurring of the line that separates work and life, many businesses require updated technology that delivers a secure and satisfying experience to its employees," says Enrique Lores, senior vice president and general manager, Commercial PCs at HP. "HP continues to innovate secure business devices that allow employees to be productive and stylish wherever work -- or life -- takes them".
The Pro x2 612 will be available in a number of configurations. You can start off with the Pro Tablet 612 on its own. This can be teamed with a slim, back-lit travel keyboard featuring a USB 3.0 port, combo audio jack and a power connector.
Alternatively you can opt for the full-size HP Pro x2 612 Power Keyboard with embedded battery. This features VGA, RJ-45, DisplayPort and two USB 3.0 ports along with a side docking connector for the optional HP UltraSlim dock. In this configuration you have the advantage of two batteries one in the tablet and one in the keyboard. These provide a claimed eight hours and 15 minutes of battery life for the tablet and up to 14 hours and 15 minutes for the tablet and keyboard combined.
There's also the option of a battery-free Wacom pen to allow users to write and draw accurately on the screen.
The HP Pro x2 612 is expected to be on sale from September. No pricing is available at the moment but you can sign up to be notified of availability via the product page on the HP site.
-

The irresistible rise of the Windows phone
Publié: juin 3, 2014, 1:26pm CEST par Ian Barker

Android may be the dominant force in the smartphone market, but according to mobile advertising specialist Vserv Windows is surging forward as a mobile OS.
As prices of smartphones continue to fall, making them more popular across global markets, this is good for the whole market and Vserv sees the adoption of the next generation of Windows-based phones as being all but guaranteed.
Windows Phone shipments are expected to reach 121 million by 2018 with Nokia leading the way. There's also an increase in developer interest in the Windows platform with a higher percentage saying they plan to adopt Windows than any other platform. There are already some 250,000 apps available on the Windows store and there have been more than 4 billion downloads to date.
Microsoft's collaboration with Nokia has seen the Finnish brand become the leading hardware for the Windows Phone OS. The Vserv blog notes that, "While the journey has been tough, the collaboration with Nokia paved way and led to a great 2013, with analysts expecting the Windows Phone platform to cross 100M devices by 2014 and become the 3rd largest OS in the world. The OS has outsold iPhone in 24 markets including India, Malaysia and South Africa which stands as a clear indication that it is set to take this space by storm".
The company has created an infographic charting the rise of Windows Phone and where it's headed which you can see below.
-

New partnership brings easy-to-use encryption to Microsoft email users
Publié: juin 2, 2014, 1:09pm CEST par Ian Barker

The best way to keep data from emails and attachments from falling into the wrong hands is to use some form of encryption. But it needs to be easy to use if it's going to be effective.
Systems integrator and network consultancy BrightPlanIT has announced a partnership with DataMotion that will see it reselling cloud-based solutions for secure email, file transfer, customer contact and forms processing.
For Microsoft customers DataMotion's cloud-hosted services protect email and file attachments from accidental exposure and data theft, and are also offered as an on-premise or hybrid solution.
For some organizations email encryption is a legal requirement to enable them to comply with privacy legislation -- in the healthcare sector for example. DataMotion's solutions feature compliance-grade encryption without the need to install special apps or exchange encryption keys. They enable users to send secure messages and attachments with a single mouse-click, so there's no temptation to look for insecure alternatives and leave the organization open to data loss and fines from regulators.
The partnership with BrightPlanIT focuses on integrating encryption solutions with Microsoft Exchange Server and Office 365.
"We’ve had a relationship with BrightPlanIT for a while, and not only do we have great respect for each other's work, we realized that by capitalizing on our strengths and focusing our combined efforts we could offer Microsoft customers something truly unique," says Bob Bales, CEO of DataMotion. "With this partnership, new and existing customers can spend more time handling their business instead of being tied-up in the purchasing process and IT issues".
Skip Gould, CEO of BrightPlanIT says, "This is about getting the job done right, the first time. Concern over data loss is at an all-time high and many new, inexperienced vendors have emerged because they see the market potential. DataMotion has been doing this for a long time and their services protect companies worldwide. We’re versed in both DataMotion and Microsoft solutions, can have a customer up-and-running fast, and our experience enables us to support IT in a way that would otherwise consume a great deal of time and effort".
You can find more about DataMotion's SecureMail system on the company's website.
Image Credit: Pixel-3D / Shutterstock
-

Ensuring mobile apps are safe for the enterprise
Publié: juin 2, 2014, 12:16pm CEST par Ian Barker

We reported last week on how misconfigured apps are likely to account for many security breaches. This is a particular problem for companies that allow BYOD as it may put corporate data at risk.
Cloud-based mobile security specialist Mojave Networks has a solution in the form of a new application reputation feature to provide enterprises with detailed insight into the applications that are being run on employee mobile devices.
"The 'bring your own device' (BYOD) trend is transitioning to 'bring your own applications' (BYOA) as users download more and more apps to share data, increase productivity and stay connected," says Garrett Larsson, CEO and co-founder of Mojave Networks. "If any application running on a mobile device connected to the network is insecure, it can put highly sensitive corporate data at risk. Our new application reputation feature can help enterprises improve their mobile security posture by eliminating the risk of insecure applications".
Mojave's new feature includes integration with device management and network security; tracking of applications by platform, user and device; categorization of apps based on level of risk, and customizable analytics.
According to data collected by Mojave Threat Labs, a typical mobile device has about 200 apps, including pre-installed and user downloaded applications. Each one has an average of nine permissions that users must agree to before use, and five of those permissions are considered moderate to high risk as they allow the app to gain access to documents, logins, passwords and other sensitive data, which potentially pose a major security risk to an organization's private data.
"On the surface, an application may seem safe, but there are always hidden risks," says Ryan Smith, Mojave's Lead Threat Engineer. "Approximately 50 percent of applications fall into our category of medium risk, meaning that they have the ability to access large amounts of sensitive data, and while they may not be obviously malicious, they still have a potential risk of data loss or compromise. With the detailed data we collect about each application in the Mojave Threat Labs, we are able to properly identify and reduce the risk of malicious attacks and data theft".
The application reputation feature is available from today as part of Mojave's professional and enterprise services. Mojave Networks currently supports Android and iOS and there's a free trial period available via the company's website.
Image Credit: logolord / Shutterstock
-

Turn any business site into a social media hub for customers
Publié: mai 30, 2014, 4:10pm CEST par Ian Barker

User generated content is an important factor in getting consumers to trust online business. But not every enterprise has the time or the skills to build and manage a presence across multiple social media sites.
Customer profile management specialist Janrain has introduced a new product that allows users of any site to introduce and share social content.
Janrain User-generated Content (UGC) lets customers comment, share across social networks, chat, create original content, and see activity streams that automatically appear across a brand’s mobile and desktop experiences.
"Janrain UGC turns any site into a highly engaging social experience and gives consumers compelling reasons to share their social data with their favorite brands," says Larry Drebes, chief executive officer of Janrain. "When attention is the most valuable commodity, brands have to craft highly personal social experiences that people will want to share with their friends and return to again and again. Janrain is putting a suite of tools in the hands of digital marketers who want to build a lively interactive brand identity that draws people into a brand experience, gives them reasons to create accounts and relationships with these brands, and keeps them coming back".
Features include allowing visitors to publish comments on site content and monitor site activity filtered by individuals, social network friends or site wide. Companies can host real-time conversations for events like product launches, plus content from social media can be integrated into news feeds.
By allowing greater interaction with a site Janrain UGC helps improve customer engagement. The data collected can help marketers create personalized brand experiences which in turn gives visitors reasons to keep coming back and interacting with the site.
More information on what Janrain UGC can do is available on the company's website.
Image Credit: Oleksiy Mark / Shutterstock
-

Bitrix24 launches free inter-company collaboration tool
Publié: mai 30, 2014, 12:06pm CEST par Ian Barker

Since its launch in April 2012, Bitrix24 has become one of the fastest growing online collaboration platforms, used by more than 180,000 companies.
It's now launching a new, free instant collaboration tool called Bitrix24.Network, allowing companies to work together without leaving their familiar corporate portal.
"Internal communications have been revolutionized by social intranets and enterprise social networks in the recent years. Intra-company communications, however, are still in the twentieth century, done mostly via emails. Our network fixes that," says Bitrix Inc president Dmitry Valyanov.
The new product is connected to, but is independent of, Bitrix24 itself and it allows people from different corporate intranets to communicate and collaborate in the same way they do inside their own company intranet.
It allows users to create temporary collaboration work spaces that are similar to throw away email addresses. Send a link to people you need to collaborate with, they log in with their Facebook or Twitter accounts and you start collaborating immediately. Once the task is over you have the option to abandon the collaboration space or keep using it for future projects. The service is free for all parties involved.
Currently Bitrix24.Network supports unlimited instant messaging, private and group chats, audio and video calls free of charge. File sharing, online document editing and other tools already available in Bitrix24 will be added to the network in the coming months.
New features are being added to the main Bitrix24 product too. There's now an email server inside Bitrix24 accounts, thanks to partnership with Yandex. Duplicate search and quotes have been added to the CRM module and the mobile app now supports extranet users.
Valyanov says, "We never believed that email is dead. Yes, social communications are effectively replacing email inside the company, but in order for a collaboration solution to be 'whole', you need to have social, chat, audio, video, telephony and email in one place. The addition of mail server inside Bitrix24 effectively completes the collaboration circle that we envisioned when we launched the service two years ago. We can now concentrate on polishing the existing tools and developing Bitrix24.Network, because it’s obvious that the next revolution is about how companies communicate with each other".
Bitrix24.Network is available from today and you can join a webinar of the launch at 11am EDT.
Photo Credit: Pressmaster/Shutterstock
-

Misconfigured apps will account for the majority of mobile security breaches
Publié: mai 29, 2014, 12:12pm CEST par Ian Barker

Security incidents originating from mobile devices are currently pretty rare. But with 2.2 billion smartphones and tablets set to be sold in 2014 and PC sales in decline, the focus of security breaches is likely to shift towards mobiles in future years.
According to research specialists Gartner by 2017 misconfiguration of applications will account for 75 percent of mobile security breaches.
Dionisio Zumerle, principal research analyst at Gartner says, "Mobile security breaches are -- and will continue to be -- the result of misconfiguration and misuse on an app level, rather than the outcome of deeply technical attacks on mobile devices".
An example would be the use of public cloud services to store enterprise data which may lead to leaks that the company is unaware of. To do significant damage though malware needs a device that has been altered at the admin level.
"The most obvious platform compromises of this nature are 'jailbreaking' on iOS or 'rooting' on Android devices. They escalate the user's privileges on the device, effectively turning a user into an administrator," says Zumerle.
Rooting or jailbreaking devices can open them up to attack by removing app-specific protection. It may also make them more vulnerable to brute force attacks on pass codes.
For businesses the best defense is to keep devices in a fixed configuration via mobile device management (MDM) policy, supplemented by shielding apps and using containers to protect key data.
Gartner's recommendations for IT managers include requiring set length and complexity for pass codes and strictly enforcing retry and timeout standards. Specifying platforms and operating systems and disallowing any that can't be updated or supported. Restricting the use of unapproved app stores and enforcing a no jailbreaking/no rooting rule. IT departments also need to use network access control methods to deny enterprise connections for devices that exhibit potentially suspicious activity.
"We also recommend that they favor mobile app reputation services and establish external malware control on content before it is delivered to the mobile device," says Zumerle.
The future of mobile security will be discussed further at the Gartner IT Infrastructure & Operations Management Summit 2014 taking place on June 2-3 in Berlin, Germany and June 9-11 in Orlando, Florida.
Image Credit: Moon Light PhotoStudio / Shutterstock
-

Incapsula launches added protection against DDoS attacks
Publié: mai 28, 2014, 3:28pm CEST par Ian Barker

One of the greatest threats faced by online businesses is the DDoS attack. Recent research by application delivery service Incapsula shows that DDoS attacks are up 240 percent and DNS attacks are also on the rise.
In response to this the company is launching significant updates to its DDoS Protection Services to stop the onslaught of attacks and protect even the largest enterprise customer.
The solutions prevent DDoS attacks against unprotected DNS servers and direct-to-IP address attacks on an organization's infrastructure. The new services complement Incapsula's existing web DDoS and security offering.
DNS DDoS attacks are an evolving trend, with attacks increasing in size and frequency in just the last few months. By targeting DNS servers that resolve domain names to IP addresses, attackers can effectively take down websites and cloud applications. The new Incapsula solution has a hardened DNS proxy service that shields the customers' own DNS servers, preventing DNS DDoS attacks from reaching them.
In addition direct IP range attack prevention stops attackers from mounting a direct volumetric attack on a single IP address or a range of IP addresses, preventing exploits on internal websites, email servers, FTP servers and other applications. It works by rerouting traffic through Incapsula's network where it’s scrubbed clean and sent back to the customer’s systems.
New custom-built packet filtering hardware named "Behemoth" has significantly increased the volume of traffic that can be cleaned via the company's network.
"We can now protect any IP network via our cloud service, and shut down very aggressive attacks aimed not just at websites and applications, but at core infrastructure," says Gur Shatz, Incapsula CEO and Co-Founder. "The Behemoth is at the core of our network expansion, geared towards stopping the inevitable Terabit-scale DDoS attacks to come".
The enhanced DDoS protection features are available now and you can find out more on the Incapsula website.
Image Credit: sibgat / Shutterstock
-

Report shows retail and healthcare sectors lagging behind in security
Publié: mai 28, 2014, 2:02pm CEST par Ian Barker

It's easy to assume that security threats hit all industry sectors equally. However, a new report by security data analysis specialists BitSight shows big differences in effectiveness and performance across four key industries.
The report looks at S&P 500 companies in the finance, utilities, retail, and healthcare sectors from April 2013 to March 2014. It includes data on the average number of security incidents, the most prevalent types of malware, and how long they take to fix.
Based on the data BitSight assigns a security rating score to each company and sector. The finance industry does best with an overall rating of 782. Although the number of incidents involving finance company networks increased over the survey period, it was quicker to detect and respond to them than other industries.
The utilities industry is also vulnerable to cyber attacks but the major players are good at protecting their internet-facing assets. The sector is highly regulated and has strong guidelines, it gets a rating of 751.
Partly thanks to last year's large scale data breaches at Target and elsewhere, the retail industry does less well. The number of security events in this sector increased by almost 200 percent over the survey period. The industry gets a rating score of 685 though the report notes that 14 of the S&P 500 retailers showed significant increase in their security ratings with a median rise of 60 points.
Bringing up the rear comes the healthcare and pharmaceuticals industry with a rating of 660. This sector saw the largest percentage increase in security incidents over the survey period. Unlike the finance and utility companies healthcare businesses don't view cyber security as a strategic business issue. The sector has also had a number of problems with theft and physical loss of laptops, servers and other devices that hold patient and personal data.
The report concludes that whilst no sector is immune to cyber attack some industries are taking the threat more seriously than others. BitSight’s CTO, Stephen Boyer says, "Effective risk management and detailed security plans are becoming selling points, making information security a competitive differentiator".
For more information on the report and how to reduce your security risk visit the BitSight website.
Photo Credit: Levent Konuk/Shutterstock
-

Paragon offers free Hyper-V backup tool for small businesses
Publié: mai 28, 2014, 10:47am CEST par Ian Barker

Backup is something that all businesses need to take seriously, but for smaller enterprises the cost and complexity of professional backup tools can be daunting.
The problem gets even more acute with the use of virtual machines. Backup and recovery specialist Paragon Software has the answer in the shape of a new product that will be available free until the end of June.
Paragon Hard Disk Manager 14 Hyper-V Preview offers a reliable tool to handle the full IT management cycle, including protection of virtual machines hosted by Microsoft Hyper-V. It can operate at the virtualization layer, employing MS VSS (Volume Shadow Copy Service) to provide agentless backup and restore of any guest machine on Hyper-V.
The Paragon tool doesn’t require an agent on a target virtual machine to create its point-in-time copy. This enhances backup performance while minimizing the load on target machines and the hypervisor during the process. It makes administration easier too as there’s no need to provide credentials for every guest to do backups.
Hyper-V guest machines can be backed up directly to pVHD (Paragon Virtual Hard Drive), VMDK, VHD, or VHDX virtual containers. Using pVHD brings additional options like high-level compression, encryption and image splitting. Virtual backup containers can be stored on local disks, network shares or UNC paths.
If the worst should happen a backed up machine can be restored to a new location. Backups can be selected by time stamp and there’s the option to restore individual files via Connect VD and File Transfer Wizard.
Paragon Hard Disk Manager 14 Hyper-V is a preview version of the full commercial product and is available to all SMBs for free download until June 30th, 2014. It requires Windows 8.1, Windows Server 2008 R2 or Windows Server 2012 R2 with the Hyper-V role installed.
Image Credit: Modella/Shutterstock
-

Spotify suffers security breach -- one user affected
Publié: mai 27, 2014, 5:23pm CEST par Ian Barker
 In the light of recent events at eBay and Avast, when an Important Notice to Our Users appeared on the Spotify streaming music service's official news feed today you might have been forgiven for fearing the worst.
In the light of recent events at eBay and Avast, when an Important Notice to Our Users appeared on the Spotify streaming music service's official news feed today you might have been forgiven for fearing the worst.Oska Stål, CTO of Spotify writes, "We've become aware of some unauthorized access to our systems and internal company data and we wanted to let you know the steps we’re taking in response. As soon as we were aware of this issue we immediately launched an investigation". Read on, however, and you discover that only one user's data has been accessed and this didn't include any password, financial or payment details.
Kudos to Spotify then for going public on something that they could easily have kept to themselves. But as Stål goes on to say, "We take these matters very seriously and as a general precaution will be asking certain Spotify users to re-enter their username and password to log in over the coming days".
As a further step it will also be prompting Android users to upgrade their app, from which it's no great leap to deduce that the compromised data belonged to an Android user. It apologizes for the fact that offline playlists will need to be downloaded again in the new version.
It also warns that users should only download the app from the official Google or Amazon stores or direct from Spotify.
Stål concludes, "We have taken steps to strengthen our security systems in general and help protect you and your data -- and we will continue to do so. We will be taking further actions in the coming days to increase security for our users".
Given all of the security breach stories of recent days you could almost have forgiven Spotify for rolling out the upgrade and keeping quiet, so full marks to the company for owning up.
Oh, and if you were the one person affected please let us know!
-

Sophos helps enterprises secure mobile access
Publié: mai 27, 2014, 4:22pm CEST par Ian Barker

With more and more demands to go mobile and allow employees to use their own devices, the challenge for businesses is to keep their data secure.
Following a recent survey which showed that 84 percent of organizations allow access to public cloud services like Dropbox and 65 percent don’t encrypt data between cloud and mobile devices, security specialist Sophos is launching Sophos Mobile Control 4.0.
This it claims is the first Enterprise Mobile Management (EMM) solution to include individual file encryption, integrated AV and web filtering. Available on premise or as-a-service, SMC provides a simple and differentiated approach for small and medium organizations to manage and secure mobile devices, content and applications. The software solution helps IT professionals implement BYOD policies and provides users the flexibility they need to stay productive and safe. It supports iOS, Android and Windows Phone 8 devices.
SMC 4.0 offers a number of key features for protecting mobile devices. With Mobile Content Management for iOS devices, it's the only EMM solution to offer file-level encryption to protect the data in the office and on the go. It also delivers integrated security against malware and malicious web sites for Android devices, which account for 80 percent of smartphone operating systems worldwide as well as the majority of mobile malware threats.
With web protection for Android, IT administrators can select web site categories to control access as well as blocking data-stealing or inappropriate web pages. SMC 4.0 also provides unique integration with Sophos UTM (Unified Threat Management), Checkpoint and Cisco to provide network access control. Compromised devices can be isolated from the network, protecting the organization's assets from malware on mobile devices. SMC is designed to simplify administration too. Thanks to an intuitive web-based management console, IT administrators can provide their users with a self-service portal to change passwords, register devices and report lost or stolen mobiles.
Dan Schiappa, SVP and GM of Sophos' Enduser Security Group, says, "SMC 4.0 extends the Sophos commitment to delivering comprehensive data protection, offering solutions to manage, secure and protect not just the mobile devices themselves, but also the content and applications on those devices. SMC 4.0 takes data protection beyond the office door by ensuring persistent mobile encryption on devices. Additional network access control based on device compliance status makes mobile device management, content management and mobile security simple and effective".
You can find out more about Sophos products on the company's website. The results of the mobile data survey results are summarized in the infographic below.
Photo Credit: lucadp/Shutterstock
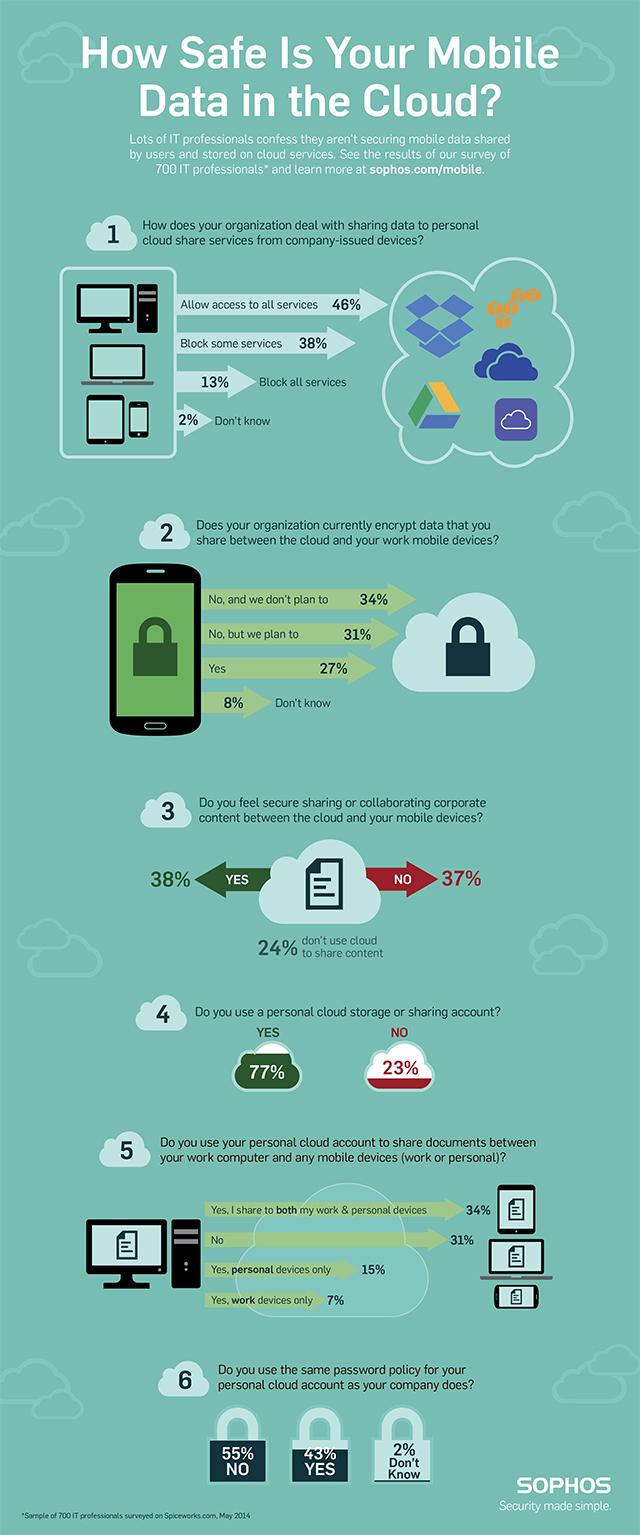
-

New gateway offers secure communication for the Internet of things
Publié: mai 23, 2014, 2:31pm CEST par Ian Barker

The growth of the Internet of things is set to place much greater demands on the web as a whole with thousands of extra devices needing to connect.
Not least of the challenges is ensuring that everything stays secure. IoT pioneer KAAZING has used the HTML5 Developer Conference in San Francisco to launch its new secure gateway.
KAAZING Gateway 4.0 JMS Edition with Enterprise Shield aims to deliver secure enterprise messaging systems. Based on the HTML5 WebSocket standard it provides a scalable full duplex solution with near-zero latency.
Capabilities of the system include enterprise-grade SSL/TLS Termination, Single Sign-On, native support for SPNEGO-based Kerberos authentication, fine-grained JMS authorization and unique Shield Agent functionality for B2B security without the need for VPN.
For the benefit of people who aren't security anoraks what all that means is Enterprise Shield offers enterprise-grade protection to protect "things" and their users from gaining unauthorized access to enterprise back-end systems.
"Enterprise Shield, IoT-ready security and JMS/Java API-friendly capabilities advance our award-winning KAAZING Gateway 4.0 to help enterprise software developers prepare for the onslaught of the Internet of Things and rapidly deploy highly interactive, real-time Web and mobile applications," says KAAZING Co-Founder and President Jonas Jacobi. "Using KAAZING Gateway, businesses can extend their enterprise messaging systems to mobile users, marketplaces and machines. The result is fast, scalable and secure enterprise Web communications that enable companies to take advantage of what we call the Internet of Many Different Things."
Key features include a dashboard that makes it easy for operations teams to track, measure, and monitor data and message delivery metrics. Performance enhancements to improve latency and reduce CPU usage by up to 25 percent. There’s also a last-value cache so the latest data is always available to all users, no matter when they connect to the application.
You can find out more about the latest gateway products on the KAAZING website.
Image Credit: PlusONE / Shutterstock
-

Developers WLTM beta testers for ongoing relationship, GSOH, no strings
Publié: mai 23, 2014, 10:54am CEST par Ian Barker

It's a tough life being an early adopter. Having to seek out all the latest developments to make sure that you’re first in line with the beta versions.
For those who really must be at the bleeding edge, test management specialist Centercode is launching Betabound, a sort of online dating service to bring together companies and early adopters.
With an intuitive, mobile-friendly interface, Betabound connects companies that have new and interesting products with 90,000 of the savviest early adopters and beta testers available.
"We envision Betabound as the center of the beta world, a sophisticated yet intuitive space that brings together cutting edge products with a cultivated pool of testers and early adopters," says CEO Luke Freiler. "It's everything both parties are looking for, backed by Centercode's unparalleled industry recognition".
Whilst it provides companies with access to a pool of testing talent to help develop their products, it also gives the early adopter and beta tester community a one-stop shop for new and interesting products that span across industries.
Anyone on the internet can go to Betabound and find an extensive list of curated announcements. These can be filtered based on personal interests and preferences so users only see the things they're interested in.
On the other side of the coin companies are able to manage tests, survey participants, open private forums, receive feedback, and more. They can collect details of bugs and feature requests allowing them to improve their products.
Centercode's Director of Sales Mario Sancho says, "Companies looking to advertise a new product or test can expect their announcements to reach thousands of the most enthusiastic testers on the web, a network that will only continue to grow on Betabound. For companies, Betabound means better feedback and the right kind of early adopters to jumpstart a launch".
You can find out more about Centercode's test management solutions on the company's website.
Image Credit: Naypong / Shutterstock
-

How APIs are changing the face of enterprise computing
Publié: mai 22, 2014, 5:00pm CEST par Ian Barker

The humble API has been around for a long time, enabling applications to exchange data. But in the world of mobile computing and BYOD the role of the API is under greater scrutiny.
This is one of the things that's been under discussion at the recent Gartner Application Architecture, Development and Integration Summit. At the end of last year there were some 10,000 publicly listed APIs, and now it's reckoned that around 24 percent of web applications and 15 percent of mobile applications use them. But what benefits are they bringing to the enterprise?
According to Mark O'Neill, VP of innovation at integration and web services specialist Axway, "The most positive angle is that they enable access. The API is decoupled from the client so different operating systems can connect to corporate data through the same API".
This means that tasks like checking stock and tracking orders can be carried out via a mobile device as an alternative to using heavyweight corporate portals.
The use of APIs enables innovation too, by putting out an API a company ensures that other people can build apps around its data. The uses aren't just about mobile either, entertainment systems, the internet of things and technology like smart meters all benefit.
There are security pluses too as the data remains on the corporate servers and isn't copied to the device itself. O’Neill explains, "Hackers are after data whether it's healthcare, government or finance. The important thing about using APIs is that the data isn't stored on the mobile device, it’s provided to the app as needed".
The downside of this is that the device needs to be online but in an increasingly connected world that's becoming less of a problem. An added advantage is greater visibility of how data is being accessed and from where. This gives admins a kill switch at the API level so there's no need for the complexity of partitioning or encryption on the device itself.
Ultimately APIs can offer significant benefits for enterprise users. Businesses can launch in new markets and reach more customers simply by sharing their API. This can lead to better provision of services to customers, but also opening the API within the company can encourage internal innovation, or opening the API to the broader developer community can spur the development of new apps.
You can find more about Axway's approach to API management on the company's website.
Image Credit: Kirill_M / Shutterstock
-

How not to handle a security breach, the eBay way
Publié: mai 22, 2014, 12:38pm CEST par Ian Barker

You can’t have failed to notice by now that eBay has had a bit of a problem relating to leaked user data. The mainstream media was all over the story yesterday -- you know things are bad when the TV news takes notice of IT matters.
To reprise the facts it seems that attackers gained access to a number of eBay employee login credentials which allowed them to access the auction site’s systems. This may have happened as long as three months back but the company only became aware of it around two weeks ago.
According to a post on eBay's corporate pages, "The database, which was compromised between late February and early March, included eBay customers' name, encrypted password, email address, physical address, phone number and date of birth. However, the database did not contain financial information or other confidential personal information".
This in itself is bad enough as it means hackers could have been busy on decrypting passwords for weeks. What makes it worse though is the way eBay has handled the problem.
Hints that something was wrong started to appear yesterday morning -- early afternoon here in the UK -- when a post appeared on the PayPal Forward blog. This disappeared again fairly quickly, leading industry watchers to believe it may have been posted in error as part of test of security procedures.
A couple of hours later though it was back for good, along with the eBay corporate post. That sparked the interest of the media but at this point the company wasn't doing anything to alert its 128 million users.
As of 4pm EDT yesterday there was no warning on the eBay homepage, there were no emails to customers, there was no forced password reset when you logged in. There was information on the site but you had to click through several links in order to find it.
Today it seems eBay is finally starting to get its act together. There's now a prominent banner on the site, click it and you're taken to a message from Devin Wenig, President, eBay Marketplaces. This advises that next time you visit the site you should, "Take a moment to change your password. You can do this in the 'My eBay' section under account settings. This will help further protect you; it’s always a good practice to periodically update your password. Millions of eBay users already have updated their passwords".
That's a start, but it really should be enforcing a password change not just asking nicely. And it should be informing users by email rather than waiting for them to login. It sends out marketing emails regularly so we know it has the mechanism in place.
Finally it's about time eBay offered two-factor authentication via a mobile phone. Currently the only way you can get 2FA on eBay is if you’ve signed up -- and paid -- for a PayPal security key gadget. Odd that because the PayPal site itself allows you to use your mobile as an alternative.
The message here for all companies is that when a major security problem occurs you need to take a proactive approach to alerting customers. Letting the story slip out via stealth and triggering a media storm before you inform your customers really isn't good enough.
Image Credit: PathDoc/Shutterstock
-

Ebay users to be asked to change passwords
Publié: mai 21, 2014, 4:16pm CEST par Ian Barker

An announcement on the PayPal Forward blog says that eBay will be asking users to change their passwords later today.
It says that this is due to, "...a cyber attack that compromised an eBay database containing encrypted eBay passwords and other non-financial information".
It goes on to say, "Extensive forensic research has shown no evidence of unauthorized access or compromise to personal or financial information for PayPal customers. PayPal customer and financial data is encrypted and stored separately, and PayPal never shares financial information with merchants, including eBay.
"In addition to asking users to reset passwords, eBay Inc. said it will also encourage any eBay user who used the same password on other sites to change those, too."
We'll keep you updated with more information as it emerges.
Image Credit: goldenangel / Shutterstock
-

Business travelers want access to reliable Wi-Fi
Publié: mai 21, 2014, 3:00pm CEST par Ian Barker

Accessing data on the move has become essential for business travelers. The days of being unable to do something because you were out of the office are long gone.
Demand for reliable, cost effective data access means that more business people are looking for ways to access Wi-Fi on the move rather than use expensive mobile data services.
Mobile service specialist iPass is addressing this with the launch of its latest cloud-based Business Traveler Service 2.0. It aims to offer cost-effective and convenient Wi-Fi access to over 2.7 million hotspots in airports, airplanes, hotels and public areas worldwide via a single login.
It's also released its Business Traveler Connectivity Report showing that business travelers on average carry three mobile devices, and that 80 percent have a "Wi-Fi first" mentality, preferring to use Wi-Fi over mobile data when working outside the office.
36 percent of free Wi-Fi users have little confidence in the security of the service, and 32 percent objected to dealing with intrusive advertising. 63 percent also find credit card-based Wi-Fi users to be overpriced, and 27 percent hate the hassle of constantly having to enter credit card details.
"The wireless landscape has been disrupted by the rapidly increasing availability of Wi-Fi, which is now the dominant form of wireless access. This phenomenon has spawned a 'Wi-Fi first' generation that uses cellular data only when Wi-Fi isn’t available," says Evan L Kaplan, President and CEO of iPass. "Business travelers are especially reliant on Wi-Fi, but they are also increasingly frustrated by the hoops they must leap through to navigate a complex and challenging Wi-Fi ecosystem that can include advertising, logins and payments with each session, frequent timeouts, and unpredictable and expensive fees. Our Business Traveler Service 2.0 gives business travelers the reliable Wi-Fi access they are looking for, without the hassle -- so that they can simply get on with what they need to do, wherever they are in the world".
iPass Business Traveler 2.0 service, removes the need for employees to use credit cards, while ensuring business travelers have access to high quality, advertising-free Wi-Fi. Available on iOS, Android and Windows devices it keeps users informed by messaging about the service and about any hotspot problems.
There’s a summary of the survey findings in infographic form below and you can access the full report on the iPass website.
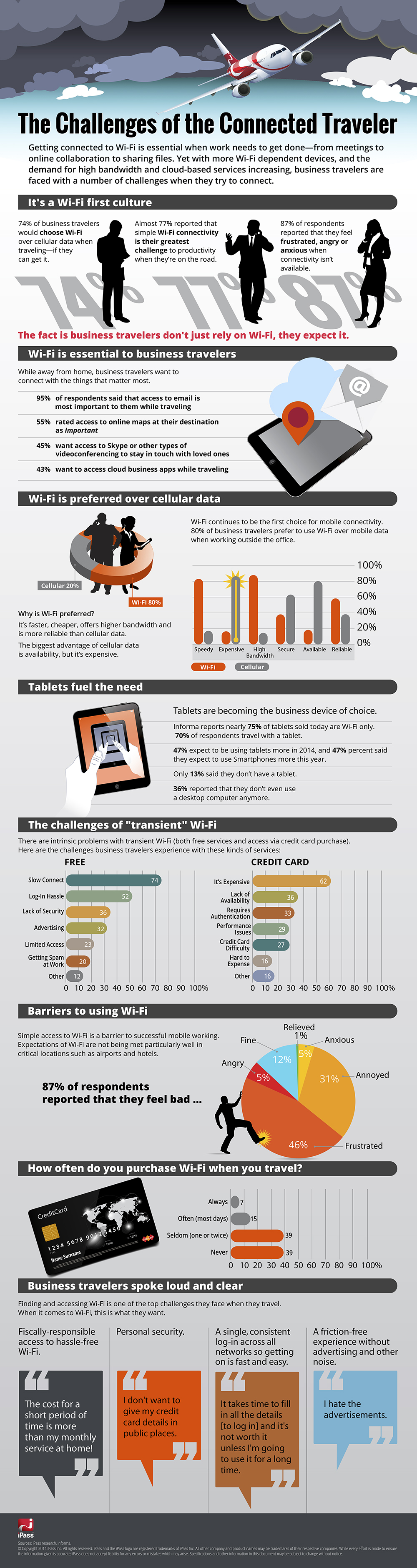
Photo Credit: Ilin Sergey/Shutterstock
-

Bad habits still compromise passwords
Publié: mai 21, 2014, 12:40pm CEST par Ian Barker

The more we do online the more passwords we have to remember and it's tempting to take shortcuts. A new survey by security specialist F-Secure reveals that 43 percent of respondents use the same password for more than one important account.
The sheer number of accounts we have is a problem also. 58 percent of poll respondents say they have over 20 password-protected online accounts or simply too many to keep track of -- 27 percent have between 11 and 20 password-protected accounts and 15 percent have under 10. Despite this though only 40 percent use a password manager to keep track of them.
Poor password choices such as using pet names are still common, but encouragingly 57 percent of respondents say they changed their passwords after Heartbleed.
If you have a lot of accounts, setting a unique, strong password for each one can seem to be a daunting task which is why many people fail to do it. Sean Sullivan, security advisor at F-Secure suggests, "Identify the critical accounts to protect, and then make sure the passwords for those accounts are unique and strong".
This takes account of the fact that you may have accounts where little important information is stored. "If you created an account for some website and there's hardly anything more in there than your username and password, then that's probably not a critical account," says Sullivan. "But your Amazon account with your credit card info, your bank account, your primary email accounts, the Facebook account with your life story, these are examples of the critical ones. If you don’t have time or inclination to tackle everything, at least take care of those".
Particularly critical are email accounts that are used as password reset addresses for other services. For these "master key" accounts it's a good idea to use two-factor authentication if possible.
The company suggests using a password manager like its F-Secure Key which is free for a single device or can synchronize using a secured connection for a monthly fee.
Image Credit: Africa Studio / Shutterstock
-

Mixed messages from the personal and entry level storage market
Publié: mai 16, 2014, 11:46am CEST par Ian Barker

In the first quarter of 2014 the worldwide market for personal and entry-level storage declined by 6.9 percent, according to IDC's storage tracker.
It's not all bad news though, the entry-level segment which targets mainly home office and small business users experienced 14 percent growth compared to the same quarter last year.
Liz Conner, Research Manager Storage Systems at IDC says, "The personal and entry-level storage market finished the first quarter of 2014 with 18.9 million units shipped. While shipments declined compared to the first quarter of 2013, this decrease is not an indication of market weakness but rather an unfavorable comparison with the unusually high shipments seen in 2013 in the aftermath of the HDD shortage and subsequent recovery".
She puts the growth in entry-level devices down to, "Increased vendor offerings, continued inclusion of enterprise level storage features, improved customer understanding/marketing, and average selling prices that more closely align with personal storage than enterprise storage all contributed to growth in this segment".
Single bay storage devices remain the most popular choice with 97.2 percent of units shipped in the first quarter. Two-bay units are in decline though and most of the growth in the entry-level sector has come from units with four bays or more.
Physically smaller drives continue to be more popular too with 3.5-inch drives losing ground to the more portable 2.5-inch format. When it comes to capacity 1TB devices captured 56.1 percent market share in the 2.5-inch segment. For the entry-level market, capacity ranges are more varied due to multiple bays and vendors' ability to partially populate devices. However, 4TB devices hold the most market share with 25.1 percent of units shipped.
USB remains the most common interface across the PELS market though Ethernet is the preferred choice for entry level business use with a 93.8 percent market share. Thunderbolt continues to gain ground with 25.1 percent year-on-year shipment growth, though it starts from a small base.
More information about IDCs tracker research is available on the company's website.
Image Credit: Be Good/Shutterstock
-

How worried should you be about BYOD security?
Publié: mai 15, 2014, 12:02pm CEST par Ian Barker

Businesses are increasingly allowing employees to choose their own devices or use personal kit to access corporate networks.
This brings a number of support challenges, not least in keeping corporate data safe. However, a recent study by Gartner shows that people are paying little regard to security when using their own devices for work.
According to the results, although a quarter of business users in the US owned up to having a security issue with their private device last year, only 27 percent of those felt it worth reporting to their employer.
Meike Escherich, principal research analyst at Gartner says, "The threat of cyber attacks on mobile devices is increasing and can result in data loss, security breaches and compliance/regulatory violations. One of the biggest challenges for IT leaders is making sure that their users fully understand the implications of faulty mobile security practices and to get users and management to adhere to essential steps which secure their mobile devices. For many organizations, overcoming BYOD security challenges is a full-time task, with a host of operational issues".
Using a personal device for work-related tasks carries an inherent risk of security breaches. That leaves IT departments struggling to come up with the right mix of defenses to balance protection, compliance and usability.
California recently attempted to legislate for a "kill switch" that would allow a phone to be remotely shut down and the hardware rendered unusable. This failed to make it into law, but Jeff Rubin, VP of Strategy at security specialist Beachhead Solutions says, "A company's BYOD policy probably gets a little murkier with a hardware kill switch. Does the business control the kill switch? Does the employee? It would be harder to see the company wrestling control of it, since users would be reluctant to cede that power to something that they own. So, the only reasonable answer for ownership of the hardware kill switch in a BYOD setting is the user themselves. The company's option, though, could be to get that data on employee's device securely containerized, so that the company may can be able to only kill those applications that contain corporate data. In this case, the company still owns a kill switch (for the subset of applications it cares about), it's just not a switch that determines the fate of the whole phone -- that decision can be left to the employee".
Ryan Kalember, the chief product officer of WatchDox, a provider of secure mobile productivity and collaboration solutions is positive about the kill switch idea, "Generally speaking, enterprises worry about their mobile users' email, calendars, contacts and files -- proper enterprise mobility solutions will be able to keep that data synced with a server so that IT can wipe it from the device without touching the personal content or losing anything important. In that sense, a device kill switch provides a nice fail safe for the corporate mobility tools, as people are probably more likely to report a stolen device to the police before they inform their IT department".
The idea of having separate personal and company areas on the same device is common to many BYOD protection solutions. Omer Faiyaz CEO of device management specialist Remo Software says that, "A segment on the device can be used to separate company and personal data. It's also a good idea to use features like Remo MORE's family app store to ensure that only approved apps can be installed".
We've seen hardware manufacturers taking the threat of lost mobile devices more seriously too with this week's announcement by SanDisk of a self-encrypting drive. This protects against data loss from lost or stolen devices and allows for central management by the IT department.
There are plenty of solutions available to make BYOD work in a safe and secure way, but it seems that businesses need to take the threat seriously and put appropriate policies and tools in place.
Gartner's Ms Escherich concludes that currently, "...BYOD laptop, smartphone and tablet security policies are still incomplete in many companies, and contain gaps and other inconsistencies that don't measure up to business obligations. Many enterprises (especially in the smaller and midsize sector) lack the proper organizational structures to create these policies and must reorganize to provide the necessary governance for a successful mobility implementation".
If this has sparked your interest BYOD security threats and trends will be discussed at the Gartner Security & Risk Management Summit which takes place on June 23-26 in National Harbor, Maryland.
Photo Credit: Stuart Miles/Shutterstock
-

Birst launches free analytics module for NetSuite customers
Publié: mai 14, 2014, 8:43pm CEST par Ian Barker
Enterprise resource planning and other business functions like financials and customer relationship management are increasingly shifting to the cloud.
NetSuite is one of the main players in this market offering a broad suite of applications. To allow NetSuite customers to get the most from their software and gain greater operational efficiency, business intelligence specialist Birst is launching a free analytics module.
Birst Express for NetSuite helps NetSuite users understand their operational data in new ways and uses highly interactive visualizations that are unavailable in standard implementations of the software or using standard reporting tools.
Embedding Birst’s cloud BI platform within NetSuite's business software suite offers customers no-cost access to powerful analytics covering areas such as booking and billing. It includes Birst Visualizer, which combines Google-style search and Amazon-style recommendations to provide faster answers to questions.
For example it allows companies to compare conversion rates across products and customer types, understand billing trends and identify bottlenecks, as well as eliminate manual reporting to assist in faster decision making.
"Birst Express for NetSuite is designed to help companies understand their operational data in new ways using sophisticated analytics and interactive visualizations," says Brad Peters, Birst's chairman and chief product officer. "By embedding Birst's business intelligence platform within NetSuite’s software suite, we can help NetSuite customers optimize business processes, ultimately driving better performance throughout the organization. This is a no-brainer for NetSuite customers because all they have to do is start using it when they are using their NetSuite software".
The free module includes a pre-built library of more than 50 operational metrics and attributes, with historical and dimensional views. It also offers visualizations, enterprise dashboards and over 20 pre-built reports giving insights into key areas.
You can find out more about Birst and what it can do for business users on the company's website.
-

Self-encrypting solid state drive helps protect corporate data
Publié: mai 13, 2014, 5:55pm CEST par Ian Barker
 Mobile workforces and a changing threat landscape means that corporate data is more at risk than ever before.
Mobile workforces and a changing threat landscape means that corporate data is more at risk than ever before.A study last year by research specialist Forrester shows that 32 percent of all data breaches were due to the loss or theft of corporate laptops. In addition between June 2012 and June 2013, business travelers lost over 10,000 laptops, smartphones, tablets and other personal electronic devices in seven of the world's largest airports.
To help companies keep their information safe, storage specialist SanDisk is launching the company's first self-encrypting solid state drive. The X300s SSD uses an AES 256-bit FIPS 197 certified hardware crypto engine to enable full-disk encryption with minimal performance penalty. It's built to be compatible with TCG Opal 2.0 and Microsoft Encrypted Hard Drive technologies and is compliant with key security specifications including IEEE 1667. It also has a new admin dashboard to make audit and compliance management easier.
"Businesses of all sizes want computers that are reliable, secure, built to last and are easy to support remotely," says Kevin Conley, senior vice president and general manager, client storage solutions at SanDisk. "For the enterprises that deploy hundreds or even thousands of laptops, it’s essential that their IT departments be able to centrally and securely manage these devices. The X300s, designed with SanDisk's world-class flash, helps corporate IT leaders not only deliver the heightened performance and lower TCO that flash is known for, but also addresses data protection and security needs, without business disruption".
The drive also comes with a coupon code for a free download of Wave EMBASSY Security Center to deliver local management. You also get a free 30-day trial of Wave Cloud 2014 which allows an administrator to remotely set up and manage several self-encrypting drives.
The SanDisk X300s SSD will be available in June via the company's Commercial Business Channel. It will come in two form factors, conventional 2.5-inch 7mm and M.2 2280 single-sided edge-connector format. Capacities range from 64GB up to 1TB. Up to 512GB will be supported on the M.2 2280 single-sided design form factor, enabling thinner computing designs.
You can visit the X300s's product page on the SanDisk website for more information. For a look at the benefits of self-encrypting drives see the infographic below.

-

Smarter commerce leads to happier customers
Publié: mai 13, 2014, 4:29pm CEST par Ian Barker

In today's ever more connected world consumers have much higher expectations of the companies they deal with.
They want businesses to understand their preferences and deliver a personalized, rewarding experience. What's more they expect this all the time not just at the point of sale.
To help organizations deliver for their customers IBM is using its Smarter Commerce Global Summit in Florida to unveil ExperienceOne, an integrated portfolio of cloud-based and on premise offerings to bring together marketing, sales and service practices and help create deeper, more valuable customer engagements.
IBM ExperienceOne draws on innovation from IBM research as well as more than $3 billion invested in organic development and acquisitions. It's also built on best practices drawn from IBM's experience of working with over 8,000 organizations across the globe.
"Smarter Commerce is about helping clients continuously reinvent themselves around the customer experience," says Craig Hayman, General Manager, Industry Cloud Solutions at IBM. "IBM ExperienceOne provides a secure and simplified portfolio -- including innovation from more than 1,200 partners -- to help clients design and deliver more valuable customer engagements. With cloud, on premise and hybrid options, IBM ExperienceOne quickly scales to engage every customer in the moment while protecting their privacy".
New capabilities help to improve understanding of customer relationships, maximize sales by directing the right offer to the right customer, and make use of mobile and social media to deliver better customer experience. Combining ExperienceOne with SoftLayer cloud infrastructure IBM is also able to offer customer data, customer analytics and digital commerce as a service.
The company is aiming to bring similar levels of customer insight to the B2B sector as well with the launch of new partner and supplier engagement software via its Smarter Commerce initiative. This includes a Multi-Enterprise Relationship Management (MRM) platform for better collaboration. IBM Sterling B2B Services Reporting and Analytics to monitor transactions and help business spot trends and make informed decisions. Plus other tools offer better adherence to compliance standards and faster and more efficient sharing of data.
"Now more than ever, the fate of any business is deeply intertwined with the success of its network of partners and suppliers around the world," says John Mesberg, Vice President, B2B & Commerce Solutions at IBM. "By orchestrating these complex engagements with extraordinary precision and insight, organizations can create new gateways to trade that enable businesses to deliver exceptional customer experiences. With today’s news, IBM fundamentally transforms these dynamics with partners and customers to drive faster time to revenue across the extended value chain".
You can find more about IBM ExperienceOne on the company's website. There's also an infographic on how Smarter Commerce can deliver better customer engagement below.
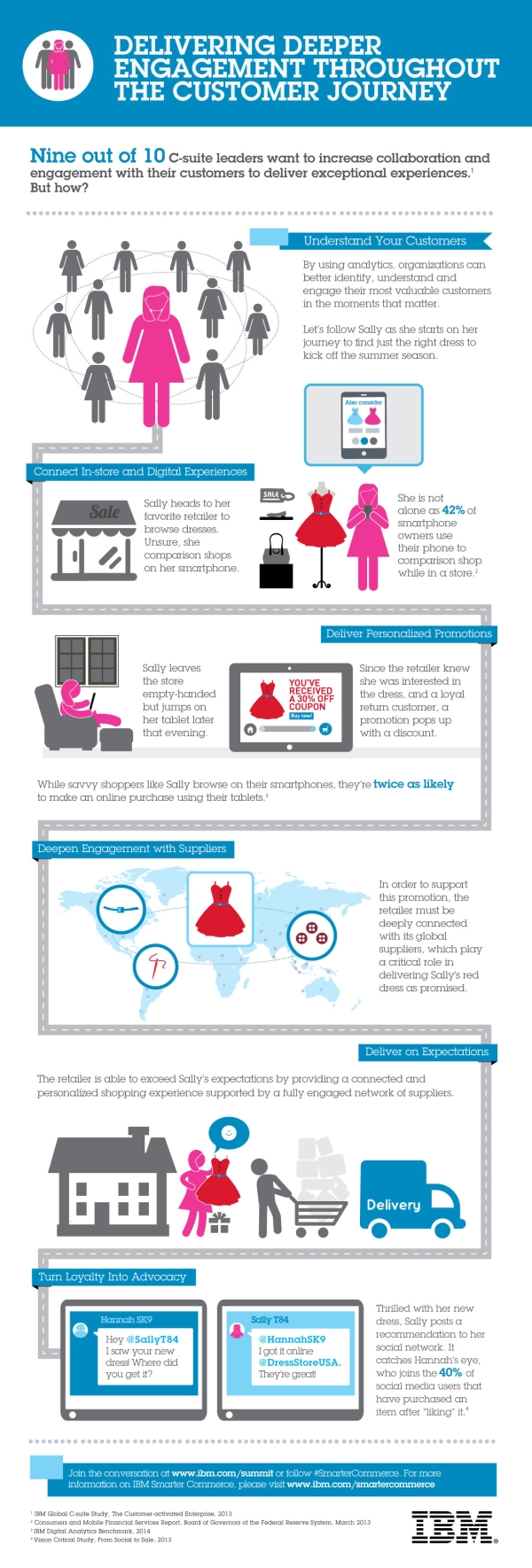
Image Credit: Sergey Nivens / Shutterstock
-

Organizations fail to address the security basics
Publié: mai 13, 2014, 12:28pm CEST par Ian Barker

The UK Information Commissioner's Office has published a new report highlighting the eight most common vulnerabilities that have led to organizations failing to keep data secure.
The threats were identified as part of the ICO's investigations into data breaches caused by poor security practices. Many of these have led to financial penalties being imposed on the organizations involved.
These include the £250,000 fine issued to Sony Computer Entertainment Europe after the company failed to keep its software up to date, leading to the details of millions of customers being compromised during a targeted attack.
The top eight vulnerabilities picked out by the report are:
* Failure to keep software security up to date
* Lack of protection from SQL injection
* Use of unnecessary services
* Poor decommissioning of old software and services
* Insecure storage of passwords
* Failure to encrypt online communications
* Poorly designed networks processing data in inappropriate areas
* The continued use of default credentials including passwordsICO's Group Manager for Technology, Simon Rice, says, "In just the past couple of months we have already seen widespread concern over the expiry of support for Microsoft XP and the uncovering of the security flaw known as Heartbleed. While these security issues may seem complex, it is important that organizations of all sizes have a basic understanding of these types of threats and know what action they need to take to make sure their computer systems are keeping customers' information secure".
Rice highlights the fact that many organizations are not addressing the basics of IT security, "Our experiences investigating data breaches on a daily basis shows that whilst some organizations are taking IT security seriously, too many are failing at the basics. If you're responsible for the security of your organization’s information and you think salt is just something you put on your chips, rather than a method for protecting your passwords, then our report is for you".
The full report, including good practice guidance on avoiding problems, can be downloaded as a PDF from the ICO website.
Rice will also be publishing a series of blogs over the next few days looking at the ICO's findings and recommendations in more detail.
Photo Credit: watcharakun / Shutterstock
-

IBM software defined storage reduces the cost of big data
Publié: mai 12, 2014, 5:08pm CEST par Ian Barker

Big data places enormous demands on storage and in many cases conventional technologies are struggling to keep up.
In an effort to deliver improved economics and at the same time enable organizations to access and process any type of data, on any type of storage device, anywhere in the world, IBM has unveiled a portfolio of software defined storage products.
Codenamed "Elastic Storage" (insert your own drapery joke here) the portfolio of products offers higher performance, infinite scale, and is capable of reducing storage costs up to 90 percent by automatically moving data onto the most economical storage device.
"Digital information is growing at such a rapid rate and in such dramatic volumes that traditional storage systems used to house and manage it will eventually run out of runway" says Tom Rosamilia, Senior Vice President, IBM Systems and Technology Group. "Our technology offers the advances in speed, scalability and cost savings that clients require to operate in a world where data is the basis of competitive advantage".
Developed by IBM Research Labs the software is ideally suited for the most data-intensive applications which require high-speed access to massive volumes of information. It provides a set of capabilities to automatically manage data both locally and globally, offering faster access, easier administration and greater scalability.
IBM Research has demonstrated that Elastic Storage can successfully scan 10 billion files on a single cluster in just 43 minutes. It has its roots in the technology used for the Jeopardy! TV match with IBM's Watson supercomputer.
Among its capabilities Elastic Storage can exploit server-side flash to give up to a six times increase in performance compared to standard SAS disks. It recognizes when a server has flash storage and uses it as cache memory to boost performance. Storage is virtualized allowing multiple systems to share common pools. It's not reliant on centralized management and so can ensure continuous access, working around software and hardware failures.
It features native encryption and secure erase options as well as supporting OpenStack cloud management to allow customers to spread data across private, public and hybrid clouds.
For more information on IBM's software defined storage visit the company's website. There's an overview in infographic form below.
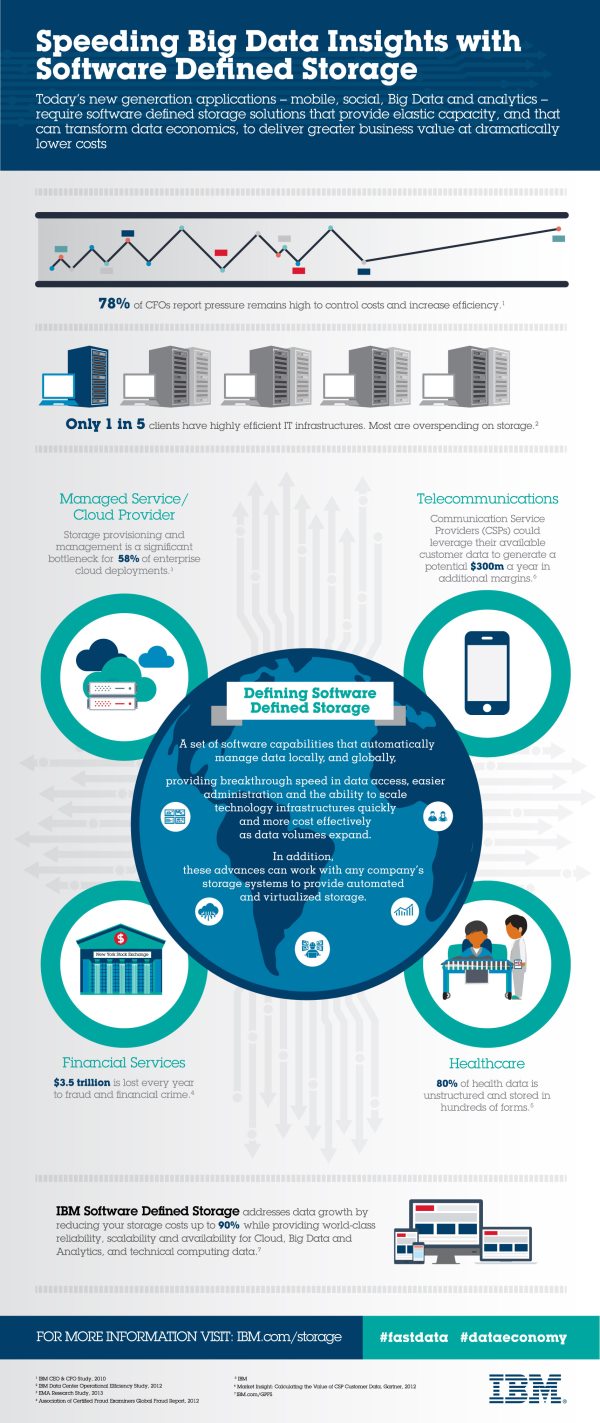
Photo Credit: T.L. Furrer / Shutterstock
-

Why brands are chasing millennials in an effort to be liked
Publié: mai 12, 2014, 3:18pm CEST par Ian Barker

The millennial generation (18 to 33 year olds) is a demographic that marketers love. We saw last week that they are more likely to use their mobiles whilst shopping but that's just part of the equation.
The reason this group excites the marketing men so much is because its members have a lot of spending power and crucially because they create buzz on social media. Brand engagement specialist PunchTab has released a new report looking at millennials' activity when shopping for fashion and accessories.
Focusing on customer loyalty programs it finds that 63 percent would join a program if offered some kind of incentive. Once signed up they're more likely to connect with the brand on social media and post comments and reviews. This is crucial because 96 percent say that user generated content plays a part in their purchase decision. When rewarded or offered an incentive millennial women are three times more likely to post comments about their purchase on a brand or store Facebook page. Millennial men are less engaged but are still two to three times more likely to connect to a brand on Facebook or Twitter and to share brand related content than other generations.
Exclusivity is important to millennials and a majority do join loyalty programs because they like to feel like elite shoppers. 74 percent of women surveyed and 52 percent of men are members of fashion-related loyalty schemes. Of those who don't join one of the key reasons they give for not doing so is the fear of being spammed by retailers.
The moral for retailers then is that if you want to be "liked" by the millennial generation and be part of the online buzz they create you need to offer an incentive.
You can download the full whitepaper on millennial fashion shopping behavior from the PunchTab website and there’s a summary of the findings in the infographic below.

Image Credit: Hasloo Group Production Studio / Shutterstock
-

Webrooming shifts buying habits back to bricks and mortar stores
Publié: mai 9, 2014, 5:37pm CEST par Ian Barker

Traditional retailing models have come under pressure from the internet, in particular the habit of 'showrooming' which involves browsing in store and buying online.
But according to point of sale specialist Merchant Warehouse there's a reverse effect called 'webrooming' which sees consumers browsing online but actually buying in bricks-and-mortar stores.
Men are more likely to webroom with around 75 percent doing it, while 53 percent choose to showroom. Female buying habits show 63 percent making in-store purchases after browsing the web and 40 percent doing the reverse. Additionally, 9 out of 10 showroomers have also webroomed, but only 6 out of 10 webroomers have showroomed -- are you following this okay? Don't worry there's an infographic at the end.
Merchant Warehouse says that retailers can capitalize on this trend by focusing on what makes consumers choose webrooming in the first place. Motivations for browsing online and buying in store include avoiding shipping costs and the instant gratification of not having to wait for delivery.
Allowing in-store pickup and online checking of stock levels are easy ways for high street stores to tap into this demand. Being able to pay online prices for in-store products is important to 36 percent of consumers too. A similar percentage would choose webrooming on the grounds that it's easier to return a product if they need to.
Making better use of mobile is important for retailers too as we saw in the case of millennial shopping habits earlier this week. About 80 percent of all local searches performed on mobile devices result in actual purchases. Crucially though roughly 73 percent of these purchases are carried out in bricks-and-mortar stores. Providing online reviews for the store and the shopping experience can help drive customers to the door.
You can find out more about the webrooming phenomenon and how retailers can take advantage of it in the infographic below.
Photo Credit: ZINQ Stock/Shutterstock
-

Windows 7 shows higher infection rates than XP in last quarter of 2013
Publié: mai 9, 2014, 1:18pm CEST par Ian Barker

The latest Security Intelligence Report from Microsoft reveals that malware infection rates soared in the final quarter of last year thanks mainly to three threats.
Infection rates measured in computers cleaned per thousand (CCM -- yes M, it uses the Latin for thousand) rose from 5.6 in Q3 to 17.8 in Q4 of last year on the back of the Win32/Senfit click fraud bot, along with two new distribution methods. Win32/Rotbrow, a program claiming to protect from browser add-ons, and Win32/Brantall which acts as an installer for legitimate applications but also bundles less welcome things.
It was Rotbrow that was most responsible for the dramatic increase in the CCM metric in 4Q13. Because the Browser Protector software had existed since at least 2011 without exhibiting any malicious behavior, many security software vendors had not configured their products to block or remove it.
An interesting side effect of this is that Vista and Windows 7 showed higher CCM rates than XP for the quarter. The report shows an infection rate of 25.9 percent for Windows 7, 32.4 percent for Vista and 24.2 percent for XP. Microsoft has normalized the figures to take account of differences in numbers using each OS.
This doesn't mean that you should rush off and downgrade all your systems to XP though. Microsoft is quick to point out that, "In general, infection rates for more recently released operating systems and service packs tend to be lower than infection rates for earlier releases, for both client and server platforms. In 3Q13, this pattern is clearly visible, with Windows XP displaying an infection rate significantly higher than any other supported Windows client platform, and Windows 8 RTM -- at the time the most recently released platform -- displaying the lowest".
Looking at threats by type, the report shows that miscellaneous Trojans are still the most commonly encountered threat. Trojan downloaders and droppers grew to become the second most encountered category in the fourth quarter though thanks to Rotbrow and Brantall. The encounter rate for worms fell slightly as did that for exploits.
In terms of geography you're more likely to encounter a Trojan in Brazil, Russia or Italy than elsewhere in the world. Ransomware distribution is particularly sensitive to geography with all encounters taking place in Europe, western Asia, and the wealthy English speaking regions of North America and Oceania. Ransomware is virtually unknown in Latin America, Africa, the Middle East, and eastern and southern Asia.
If you need some bedtime reading you can download the full 152 page PDF report, which covers much more including spam levels and the differences between home and enterprise threat patterns, from the Microsoft website.
Image Credit: micic/Shutterstock
-

Mimecast adds spear phishing protection
Publié: mai 8, 2014, 4:22pm CEST par Ian Barker

Spear phishing attacks are becoming more commonplace and with each major data leak, like that of earlier this year at Target, the number of people at risk of falling victim to one increases.
By their very nature spear phishing attacks are highly targeted and seek to trick users into visiting malicious URLs by appearing to come from a trusted source.
In response to the risk, cloud email management specialist Mimecast is adding Targeted Threat Protection to its portfolio of services. This scans all URLs found in inbound email every time they are clicked by the end-user to ensure the linked site is clean and risk free. If the user attempts to visit an 'at risk' site, they are warned or automatically barred from viewing it.
Because it's in the cloud, the protection is in place from any device used to access an enterprise email account including smartphones and tablets. It makes life easier for admins too as it’s controlled from the Administration Console along with other Mimecast services.
Orlando Scott-Cowley, Director of Technology Marketing, Mimecast says, "Spear phishing is a new frontline in the battle to protect enterprise systems and data. Mimecast Targeted Threat Protection stops spear phishing in its tracks. The threats to an end-users' inbox are constantly changing and have moved far beyond the daily barrage of spam and virus content on their work desktop. We have to protect their work and personal desktop, laptop, tablet and smartphone as today each device is used for enterprise email. IT teams know their end-users are one of their weakest security links and can be specifically targeted to get access to critical systems and valuable corporate data".
Spear phishing attacks often attempt to pass through existing security gateways by having embedded URLs that are initially inactive and therefore clean when scanned. Phishing web content is activated later when the attacker knows all gateways have passed the email and link. Mimecast combats this by rewriting the link at the gateway so when it gets clicked, it's directed to the Mimecast cloud where the original link is checked for risks before being opened. This has the added advantage that the link is scanned every time it's clicked not just the first time, so uses won't be caught out by dormant links that become active at a later date.
It's seamless for the end user as if a link is safe it will simply open as normal in the browser. If a link is bad a clear warning can be displayed along with advice based on the user's security profile. For the IT team it offers seamless protection with no need for extra infrastructure or staffing.
For more information on Mimecast and how it can manage email for Microsoft Exchange and Office 365 environments visit the company's website.
Image Credit: Maksim Kabakou / Shutterstock
-

Adaptiva OneSite boosts WAN performance and optimizes Windows 8 environments
Publié: mai 8, 2014, 3:09pm CEST par Ian Barker

With business becoming more global and having remote offices in different locations, network performance is more than ever a key issue for administrators, especially when performing system updates.
System management specialist Adaptiva has launched a new version of its SCCM (System Center Configuration Manager) tool OneSite, aimed at improving WAN performance and scalability as well as making the most of Windows 8 environments.
OneSite 4.0 is scalable to sites of up to 400,000 workstations, enabling large enterprises with multiple offices around the globe to run Microsoft SCCM environments with less effort, infrastructure cost and time from IT staff. It provides support for a Unified Extensible Firmware Interface (UEFI) to take full advantage of Windows 8 environments, as well as powerful new visual scripting capabilities.
Other key features include a WAN pause and resume facility allowing admins to stop and start network traffic at the click of a button, a NetBoost feature to improve performance and responsiveness where bandwidth is restricted, and predictive bandwidth harvesting with a flow equalizer. The latter allowing files to be sent to distributed machines across the WAN ensuring coordination between locations to make the best use of the network.
It also offers secure, enterprise class P2P communication which is infinitely scalable. This includes Adaptiva’s proprietory Zero Footpring Chaching to cope with large volumes of data. OneSite's P2P content transfer efficiently handles large packages -- such as when pushing updates to remote machines -- while consuming fewer client resources. IntelliStage automatically selects the best-suited machines at a site to store the content and AutoStage perpetually maintains a minimum number of copies of the content, ensuring redundancy and load balancing.
"We are seeing unprecedented demand in very large global, Windows environments where inconsistent WAN connections and the need to perform widespread operating system or SCCM upgrades is a huge challenge for IT," says Deepak Kumar, CTO and Founder of Adaptiva. "The scalability and performance improvements we’ve made in the new version of OneSite are specifically designed to meet these business needs, and directly based on feedback we've received from the largest banks and manufacturers in the world".
You can find out more about the latest version of OneSite on the Adaptiva website.
Photo Credit: Palto/Shutterstock
-

HP invests over $1 billion in new open source cloud products
Publié: mai 7, 2014, 11:24am CEST par Ian Barker

As businesses shift more of their operations to the cloud so the demand for reliable, scalable services and platforms increases.
To address these needs HP is launching a new portfolio of cloud products and services called HP Helion. This incorporates existing HP cloud offerings with new OpenStack technology-based products, professional and support services in a single portfolio to help meet customers' specific business needs.
In addition the company is extending its commitment to OpenStack technology and hybrid IT delivery -- spanning traditional IT, public, private and managed clouds. HP plans to invest more than $1 billion over the next two years on cloud-related product and engineering initiatives, professional services and expanding HP Helion's global reach.
"Customer challenges today extend beyond cloud. They include how to manage, control and scale applications in a hybrid environment that spans multiple technology approaches," says Martin Fink, executive vice president and chief technology officer at HP. "HP Helion provides the solutions and expertise customers need to select the right deployment model for their needs and obtain the greatest return for their investment".
The Helion portfolio includes several new products and services. Highlights are a commercial version of OpenStack, delivered tested and supported by HP. The HP OpenStack Community Edition is a free version for testing, proof of concept and basic systems and is available now. A commercial edition to address the needs of larger enterprises will be released in the coming months.
There's also a Platform as a Service (PaaS) development platform based on Cloud Foundry to allow developers to build, deploy and manage applications quickly and easily. An OpenStack Technology Indemnification Program protects qualified customers using HP Helion OpenStack code from third-party patent, copyright and trade-secret infringement claims directed at OpenStack code alone or in combination with Linux code.
To provide support Helion OpenStack Professional Services will make an experienced team of consultants, engineers and cloud technologists available to assist customers with cloud planning, implementation and operational needs.
You can find out more about HP Helion on the company's website. You can also register to watch the official launch webcast at 11:30am ET today (7 May 2014).
-

Big data, collaboration and system software drive the enterprise market
Publié: mai 6, 2014, 2:54pm CEST par Ian Barker

Research specialist IDC has released the latest results of its Worldwide Semiannual Software Tracker showing that the software market grew by 5.5 percent in 2013, reaching a total size of $369 billion.
IDC divides the market into three segments: Applications; Application Development and Deployment (AD&D); and Systems Infrastructure Software. These segments all grew between 5.4 and 5.6 percent, meaning that none of them had a significantly better performance in 2013.
Some specific types of software, though, showed high growth rates. Growth in the AD&D segment was largely driven by the performance of structured data management along with data access, analysis, and delivery software with 7.3 and 6.0 percent growth rates, respectively. Advanced analytics software and database management systems (DBMS) solutions are pushing the growing trend for these markets because of increased big data and analytics adoption. Oracle continues to lead the AD&D segment with a steady market share of 21.5 percent, followed by IBM, Microsoft, SAP, and SAS. Among these vendors, Microsoft and SAP stood out by gaining the most market share over the last year.
In the Applications market -- which accounts for half of total software revenue -- collaborative applications and content applications stood out with year-on-year growth rates above 10 percent. Whilst the first is being driven by the adoption of enterprise social networks and team collaborative applications, the latter is down to search and content analytics, which grew at 13.2 percent. Big data and related analytics adoption is largely responsible for this. Microsoft leads the applications market with a 14.1 percent share in 2013.
Whilst Systems Infrastructure Software grew by only 5.5 percent the system software sub-segment grew by eight percent, driven by the launch of Windows 8 along with virtual machine and cloud system adoption. Microsoft has 29.3 percent of this segment followed by IBM, Symantec, EMC and Vmware.
Looked at by region, Latin and North America showed the most growth, followed by Western Europe. The Japanese market showed an 11.6 percent decline on the effects of devaluing the yen.
You can read more about what's covered by IDC's software tracker on the company's website.
Image Credit: Peshkova / Shutterstock
-

Symantec unveils its roadmap for Advanced Threat Protection
Publié: mai 5, 2014, 4:30pm CEST par Ian Barker

With targeted attacks on the rise and cybercriminals becoming more ruthless, traditional security solutions are struggling to cope with the number of incidents and false positives, leaving organizations vulnerable.
In a bid to provide improved security Symantec has announced a roadmap of solutions aimed at providing what it calls Advanced Threat Protection.
This centers on two new offerings, Symantec Managed Security Services -- Advanced Threat Protection and Symantec Advanced Threat Protection Solution, these correlate alerts and intelligence across a range of security technologies to deliver more comprehensive attack prevention.
"To successfully defend against the types of targeted attacks we're seeing today, you need to expand the focus from prevention to detection and response," says Brian Dye, senior vice president of Symantec Information Security. "Network security alone isn't going to solve the problem. Adversaries are targeting all control points from the gateway to email to the endpoint. Organizations need security across these control points working together, with incident response capabilities and global information intelligence, to beat the bad guys. Symantec is bringing that powerful arsenal to market".
The first new product, available from June this year, is Symantec Managed Security Services -- Advanced Threat Protection (MSS-ATP), a managed service that significantly reduces the time it takes to detect, prioritize and respond to security incidents by producing integration between its endpoint security and third-party network security vendors' products. It works with a number of products from partners including Check Point Software Technologies, Palo Alto Networks and Sourcefire (now part of Cisco).
In the next six months Symantec will launch two more products, an Incident Response service, providing customers with immediate access to critical capabilities, knowledge and skill sets, and an Intelligence service, providing unmatched threat visibility and analytics.
To tie all this together there will be an Advanced Threat Protection Solution, which is scheduled to be in beta testing within six months and generally available within the next 12 months. This will offer a complete end-to-end solution to integrate Advanced Threat Protection across the endpoint, email and gateway to provide customers with critical detection and response capabilities at each point.
Advanced Threat Protection will be supported by two technologies, the first being Symantec's Dynamic Malware Analysis Service which is a cloud-based sandbox environment where behavioral analysis of active content can be used to quickly maximize threat identification. The second is Synapse, which enables smooth communication between the endpoint, email and gateway to improve response. It's also backed by a Global Intelligence Network that collects data from customers and sensors around the clock to allow Symantec to detect attacks, monitor attacker networks and develop predictive, proactive technologies to deliver threat protection.
Jon Oltsik, senior principal analyst at Enterprise Security Group says, "Symantec is well positioned to deliver an end-to-end advanced threat solution by building on the technologies it offers today, integrating across its portfolio, and delivering it as a service enhanced by an evolving partner ecosystem. By leveraging its global intelligence and building-in completely new incident response capabilities, Symantec can really address a multitude of enterprise cybersecurity requirements".
Image Credit: Symantec
-

Millennials more likely to use mobiles when shopping
Publié: mai 5, 2014, 3:09pm CEST par Ian Barker

We all know that technology is changing the way we shop through the ability to buy more of our needs online.
But a new study of millennial shoppers by point of sale technology specialist Merchant Warehouse shows that this particular generation has higher expectations from the shopping experience and is more likely to use mobiles in the process.
Nearly three-quarters of millennials read reviews on their mobiles, and half of people in this demographic use their mobile device to check into stores in order to earn rewards. The rise of price matching websites has also led to them being more likely to check prices whilst out shopping.
Some 44 percent also say they scan QR codes in store to learn more about products and manufacturers.
Retailers though don't seem to be taking advantage of the opportunities this shift in habits offers. Half of retailers say that their mobile marketing efforts aren't targeted. Coupons play a big part, around half of millennial consumers indicated that they would visit a store if they were offered a 20 percent discount. One-quarter of respondents would need a 50 percent discount as an incentive to visit a store.
Loyalty programs are important too. Three-quarters of shoppers would consider switching to a different retailer if they were offered real-time promotions through a mobile application or website. Again retailers are missing the boat, only 27 percent offer mobile coupons and less than 12 percent of retailers offer daily deals through a discount website.
You can read more about the results of the survey in the infographic below.
Image Credit: Art Allianz / Shutterstock
-

Keeping organizations secure in a post-Heartbleed world [Q&A]
Publié: mai 5, 2014, 12:13pm CEST par Ian Barker

The recent Heartbleed bug, in addition to a general rise in cybercrime activity, has led to companies scrambling to re-evaluate their online security. But how can organizations ensure that have a consistent and reliable approach to protecting themselves?
We spoke to Tanya Bragin the principal product manager at ExtraHop Networks, a global leader in real-time wire data analytics for IT operational intelligence, to find out.
BN: How can organizations ensure that they're properly protected in the wake of Heartbleed?
TB: Cataloging all affected servers can be an onerous audit task, especially for a large or distributed IT organization. In one case, we heard from the CISO of a large online company who had spent the 48 hours since the vulnerability came to light running port scans on all of the company’s systems. While the CISO reported that the scans had thus far been successful because none of their systems had gone down (the fear of the DevOps team), every passing minute without a complete understanding of the vulnerabilities in their architecture exposed them to risk.
While traditional approaches to security monitoring, visible in the previous CISO use-case, certainly play an important role in detecting threats, the Heartbleed vulnerability underscores the limitations of these systems. The port scans performed by these systems impose a considerable burden on the network, and take time to identify vulnerabilities. In this situation, the most scalable way to understand what systems are affected is to evaluate communication choke points, rather than individual hosts. Wire data is the most comprehensive source of visibility into these choke points because it offers an unbiased view of all traffic moving across the wire. Employing solutions that provide this deep, cross-tier visibility are crucial in making sure that Heartbleed and other vulnerabilities are detected rapidly and without impacting network performance.
BN: What if your web servers are outsourced to a third party?
TB: If your infrastructure is outsourced, your options may be limited since you are now reliant on the third party provider to evaluate and monitor their servers for this vulnerability. Selection criteria for managed services need to include access to tools that provide uniform visibility into an environment. Ideally, the solution in place is an easily extensible platform, able to monitor a variety of environments in a vendor-agnostic manner and be adjusted to handle unexpected use cases.
BN: Have recent events dented consumer confidence in ecommerce and what can be done to rebuild it?
TB: In the wake of recent high profile security breaches, consumer confidence in ecommerce companies has diminished. While these breaches should have motivated consumers to be more careful with what data they expose and how they protect it (ie strengthening and diversifying their passwords), ecommerce companies still bear significant responsibility for protecting the data consumers entrust to them.
Between the blow to consumer confidence and the subsequent lawsuits resulting from these data breaches, ecommerce companies, regardless of whether they have been affected, need to take a critical look at their security protocols. Internally assigning blame -- with the operations team blaming security, security blaming operations, and everyone trying to point the finger at the security vendor -- is not going to improve confidence. Instead, these companies must adopt a proactive, integrated approach by taking security into account at all levels, from development and test through to day-to-day IT ops.
BN: What is the main lesson that businesses should take away from Heartbleed?
TB: The threat landscape is constantly evolving, and vulnerabilities may crop up in the places you least expect them. Heartbleed is a prime example of this. In order to deal with new, advanced and persistent threats, IT teams need to rethink their approach to security for their networks, data and applications. Keeping security siloed from operations is no longer an option. Much like development/test and operations have become increasingly interconnected in recent years, resulting in DevOps, operations and security teams benefitting from a more collaborative approach. The reality is that security and operations teams share a common goal -- maintaining the integrity and availability of the organization's IT assets. If security is compromised, so is availability. Simply notifying the security team when a potential breach is detected is not sufficient. Operations needs to take a more active role in identifying the genesis of the breach, and then work collaboratively with the security team to remediate it.
BN: How do you see the overall threat landscape changing? How much of this is driven by new service models like BYOD?
TB: The complexity, dynamism and decentralization of today’s IT environments not only opens the door for new vulnerabilities and exploits, it makes preventing, detecting and neutralizing potential threats a complex task. BYOD is a good example. As individuals increasingly demand to use their personal devices in the workplace, controlling which devices access the network, data and applications, is no longer simple. In order to prevent a potential breach, IT teams need the means to pervasively and persistently monitor which devices are connecting and from where, and then track how and to what extent they are accessing applications and data. If, for example, the NSA was equipped with a way to monitor which data Edward Snowden was accessing (and how much of it), they might have been notified of the anomalous behavior before it turned into one of the most infamous security debacles in history.
Likewise, things like public cloud are also transforming the way organizations are thinking about security. Hosting applications in public clouds like AWS make many IT teams nervous, knowing that they will lose a certain degree of control over the performance, availability and security of those applications. As with the BYOD problem, the resolution really comes down to visibility. Solutions like CloudWatch exist to help internal IT teams monitor their workloads running in AWS. A wire data analytics platform like ExtraHop can be deployed to extend the functionality of CloudWatch to deliver real-time, pervasive monitoring of applications running in the cloud, thereby enabling IT and security teams to detect anomalous behavior early.
BN: Are there additional risks associated with businesses moving to the cloud and to SaaS platforms?
TB: Yes. That risk is "uniformity". Economies of scale in SaaS and cloud necessitate streamlining and homogenizing solution stacks and environments in order to deliver infrastructure and services in a cost-effective manner. However, from the perspective of an attacker, their job just got easier! They now have to find vulnerabilities in a much smaller subset of software. By infiltrating one cloud or service provider, they gain access to numerous organizations’ resources and information.
Photo Credit: watcharakun / Shutterstock
-

Are we starting to fall out of love with tablets?
Publié: mai 2, 2014, 3:36pm CEST par Ian Barker

It looks like the growth of the tablet market may be starting to slow down according to a new study carried out by research specialist IDC.
Tablets and 2-in-1 shipments slipped to 50.4 million units worldwide in the first quarter of 2014 according to IDC's Quarterly Tablet Tracker. This represents a decline of 35.7 percent from the high-volume holiday quarter and just 3.9 percent growth over the same period last year.
The slowdown has been seen across all operating systems and screen sizes and IDC suggests that it points to an even more challenging year ahead for the sector.
"The rise of large-screen phones and consumers who are holding on to their existing tablets for ever longer periods of time were both contributing factors to a weaker-than-anticipated quarter for tablets and 2-in-1s," says Tom Mainelli, IDC Program Vice President, Devices and Displays. "In addition, commercial growth has not been robust enough to offset the slowing of consumer shipments".
Looked at by manufacturer, the figures show that Apple has maintained its lead in the market having shipped some 16.4 million units worldwide. However, that figure is down from 26 million units in the previous quarter and 19.5 million in the same quarter of 2013. Apple's market share has held up though at 32.5 percent compared to 33.2 in the previous quarter.
Samsung grew its market share from 17.2 percent in the last quarter of 2013 to 22.3 percent in the first quarter of this year on the back of 11.2 million shipments. Amazon tablet sales showed a year-on-year decline from 1.8 million units in Q1 2013 to just one million this year.
The biggest growth comes from Lenovo which shipped only 600,000 tablets in Q1 2013 but leaped ahead of Amazon this year moving 2.1 million tablets in the first quarter.
iChartsAndroid continues to dominate the tablet market with around a two-thirds share, but Windows is starting to gain ground. Jitesh Ubrani, Research Analyst, Worldwide Quarterly Tablet Tracker says, "Although its share of the market remains small, Windows devices continue to gain traction thanks to sleeper hits like the Asus T100, whose low cost and 2-in-1 form factor appeal to those looking for something that's 'good enough'".
So what does all this mean? Are we losing our love of tablets? Or is it simply as Mainelli says that having found a device they like people are hanging onto it rather than upgrading to the latest model? The latter seems most likely as, unlike smartphones, tablets aren't bought on contract so represent a more significant spending commitment.
Image Credit: vinzstudio / Shutterstock
-

The top five technologies driving the internet of things
Publié: mai 2, 2014, 11:15am CEST par Ian Barker

We're hearing more and more about the internet of things at the moment, but what are the technologies that are doing most to make it a reality?
Entrepreneur’s group TiE Global has produced an infographic highlighting industry insights and predictions for the top internet of things technologies for this year.
It names the five key technologies making the IoT a reality as smartwatches, the automated home, health and fitness tracking, connected retail, and virtual and augmented reality. Some of these like smartwatches, and fitness tracking are heading towards the mainstream. Others like augmented reality -- Google Glass for example -- have yet to fully take off but are likely to have a big impact when they become available to consumers.
Connected retail systems, allowing you to pay with your mobile phone using NFC for example, are predicted to account for 19 percent of retail sales by 2016. Automated home technology has started off slowly but the market is expected to be worth over $35 million by 2016.
You can read more on the infographic below.

Image Credit: lucadp / Shutterstock
-

PC users struggle to keep all their software patched
Publié: mai 1, 2014, 3:20pm CEST par Ian Barker

The average private user PC in the UK has 76 different programs from 26 different vendors, which leaves users struggling to keep everything up to date.
Vulnerability management specialist Secunia has published a report on the state of security among PC users in the UK based on scans from Secunia Personal Software Inspector between January and March 2014.
It finds that 58 percent of identified vulnerabilities originate from third party programs, 29 percent from Microsoft programs and 13 percent from operating systems. More worrying is that 12 percent of users are using unpatched operating systems, a figure that's likely to rise following the end of support for XP.
Just over one in ten third-party programs on the average PC are unpatched compared to just over three percent of Microsoft programs. This, says Secunia, suggests private individuals respond to the single update mechanism for Microsoft programs but struggle to master the other update mechanisms required for the other vendor's software. Also 4.6 percent of installed programs have reached end of life and are no longer being patched by the vendor.
Morten Stengaard, CTO at Secunia says, "Good security management means removing programs that aren't used and regularly patching those that are. However, cybercriminals know that most private users in the UK consider regular security maintenance hard work".
The top 10 most exposed programs based on their market share and the percentage that remain unpatched despite patches being available are as follows:
1 Microsoft XML Core Services (MSXML) 4.x
2 Oracle Java JRE 1.7.x / 7.x
3 Apple QuickTime 7.x
4 Apple iTunes 11.x
5 VLC Media Player 2.x
6 Adobe Reader X 10.x
7 Microsoft .NET Framework 3.x
8 Microsoft .NET Framework 2.x
9 Adobe Shockwave Player 12.x
10 Microsoft .NET Framework 4.xYou can read Secunia’s full UK country report on the company’s website. You can also check how vulnerable your system is by downloading the free Secunia PSI scanner program.
Image Credit: alexskopje / Shutterstock
-

Security at risk as organizations struggle to monitor complex networks
Publié: mai 1, 2014, 12:19pm CEST par Ian Barker

As networks become larger, faster and more complex, they become harder to monitor. This presents a security risk as it's more difficult to capture behavior for incident analysis and to spot suspicious behavior.
Network specialist Emulex has released the results of a survey which looks at the impact of growing networks on visibility and monitoring, network and application performance, security, and compliance.
The number one network performance challenge, cited by 43 percent of respondents, is monitoring/managing network performance between groups of web, application, and database servers in the data center. The second largest is maintaining performance to endpoint devices connected via public networks or WANs.
These concerns reflect a changing environment with increasingly mobile workforces that require wider boundaries for endpoint device management.
Security issues include struggling to capture network behavior for incident detection, mentioned by 38 percent, monitoring network flows for anomalous behavior (35 percent), the ability to capture and analyze logs from network and security devices (29 percent), and being able to to establish a baseline of normal network behavior (27 percent).
More than two-thirds of respondents state that they expect the number of requests to capture network data (including metadata and packet-level data) to increase dramatically. These requests are also coming from more places including network, security, compliance, audit and application teams.
Faster networks are a problem too as 54 percent of respondents say that their existing monitoring tools can’t cope with the increased throughput of 10GbE networks.
"The results of this survey point to exactly why enterprises need the ability to collect and monitor all network traffic -- to improve network performance, security, and availability and to maintain regulatory compliance," says Mike Riley, senior vice president and general manager of the Endace division of Emulex. "The impact on the enterprise bottom line of network outages and security events is very large, and will only continue to grow. By implementing comprehensive network visibility architectures, organizations will be better prepared to ensure network performance, security, and compliance, and to dramatically reduce the time to find and fix critical problems".
The full study is available as a PDF from the Emulex website and you can see a summary of the findings in the infographic below.
Photo Credit: dotshock/Shutterstock
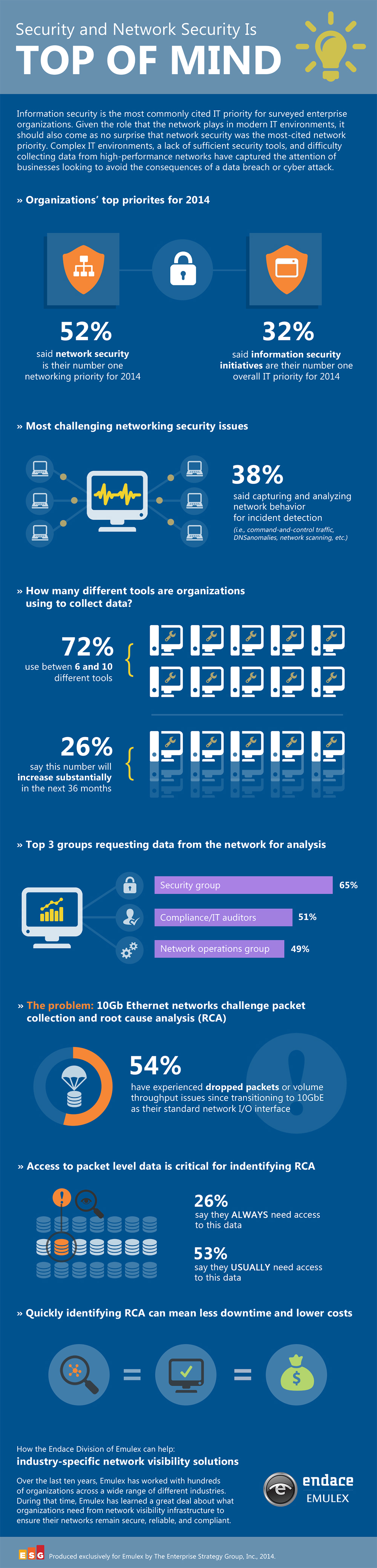
-

Most organizations are accidental software pirates
Publié: avril 30, 2014, 3:53pm CEST par Ian Barker

A majority of enterprises are using software that they've unintentionally failed to pay for according to a new report by Flexera Software prepared in conjunction with IDC.
The report reveals, among other things, that 85 percent of organizations are out of compliance with their software license agreements. In addition 63 percent were audited by their software vendors in the last 18-24 months (58 percent by Microsoft, the most aggressive auditor), and 56 percent were handed bills to regularize their licenses.
"Software license audits are a legitimate way for vendors to ensure they're getting paid for their software that’s actually being used. However, CFOs can be unaware of software contract provisions permitting these audits, which can result in an unexpected budget shock when IT staff present them with a true-up bill," says Amy Konary, research vice president -- software licensing and provisioning at IDC. "The cost of these true-ups can be significant, so CFOs should take the necessary steps to reduce their risk by implementing software license management processes and technologies to help ensure continual compliance".
All of the big software vendors use audits as a means of capturing extra revenue from non-compliant customers, but the report suggests that some are more aggressive than others. Microsoft is the most active with 58 percent having been audited by the company in the last year. Over the same period 29 percent report having been audited by Adobe, 23 percent by IBM, 21 percent by Oracle, 12 percent by SAP and 8 percent by Symantec.
Of the accidental pirates, 42 percent say that more than 10 percent of their software spend is associated with applications that are out of compliance.
"Software vendor audits are a fact of life today, as are the large checks CFOs are writing to their vendors to pay unbudgeted true-up fees," says Jim Ryan, Flexera Software’s Chief Operation Officer. "Best practice processes and technology are being implemented by prudent organizations to help ensure continual software license compliance. With these reasonable measures now so readily available, IT managers should no longer have to present their CFOs with six-, seven- or eight-figure true-up bills".
The report is available to download from the Flexera website and you can see an overview of the findings in the infographic below.
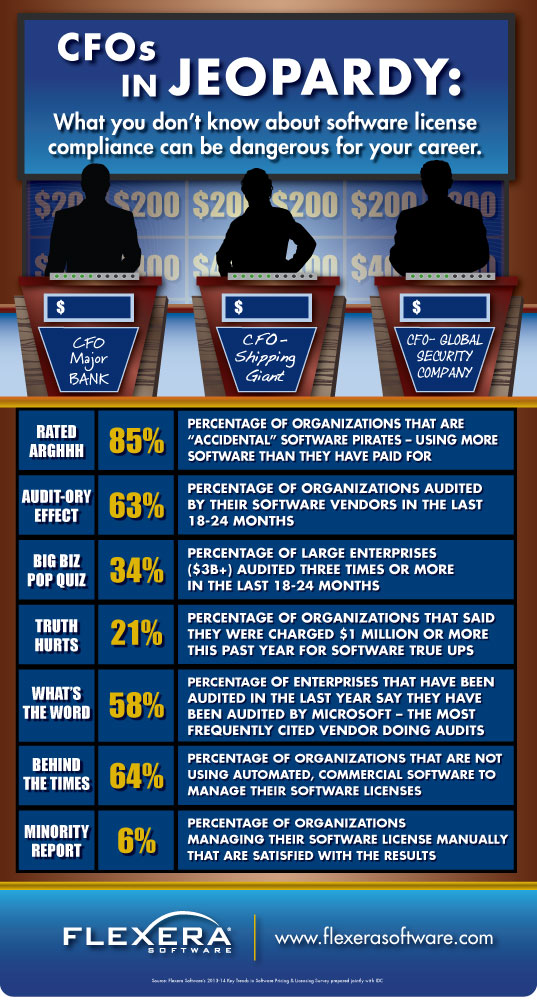
Image Credit: Feng Yu / Shutterstock
-

Older generations take to tablets but TV remains their first love
Publié: avril 30, 2014, 12:44pm CEST par Ian Barker

UK media regulator Ofcom has published the results of its latest Adults' Media Use and Attitudes report studying the media habits of people aged 16 and over.
Among the findings are that younger people spend more time online and that the number of over 65s accessing the web has increased by 27 percent between 2012 and 2013.
Internet access among under 35s is now almost universal with 98 percent going online. Among 45 to 54-year-olds 91 percent now go online (up from 84 percent in 2012) but the biggest increase is among over 65s. Ofcom suggests that this is due to the increased use of tablets by older people up from 5 percent in 2012 to 17 percent in 2013.
Computers are still the most popular way to access the internet, used by 78 percent, but two-thirds of adults also use other devices, such as tablets or smartphones, to surf the web.
Use of tablet computers to access the internet among all adults has almost doubled from 16 percent in 2012 to 30 percent in 2013. Nearly two-thirds (59 percent) of people now access the internet through a mobile phone, up by six percentage points since 2012.
What's also interesting is that more adults across all age groups are playing games, 42 percent compared to 35 percent in 2012. This is likely to be driven by increased internet access as well as the availability of smartphones and tablets.
Ofcom also finds that among smartphone users more than half of downloaded apps are redundant. On average users have downloaded 23 apps but only use 10 of them. When it comes to selecting apps more than three-quarters rely on recommendations from friends and family with under 20 percent relying on any form of advertising.
When asked about the technology they'd miss, TV comes out on top with 42 percent of all adults saying they'd notice the lack of the haunted fish tank most if it was taken away. There is big variation by age though, 47 percent of 16-24-year-olds say they'd miss their smartphone with only 13 percent naming TV, however, among over 65s the telly remains king with 68 percent saying they'd miss it.
Despite an enduring love for TV, the consumption of DVDs and Blu-Rays has fallen, only 55 percent watching them in 2013 compared to 63 percent in 2012. Just over half of internet users say they watch TV programs online.
More information on the findings of the report is available on the Ofcom website.
Do these findings reflect your experience? Which piece of technology would you miss the most? Let us know via the comments.
Image Credit: Ljupco Smokovski / Shutterstock
-

New BaaS platform aims to eliminate writing server-side code
Publié: avril 30, 2014, 11:04am CEST par Ian Barker
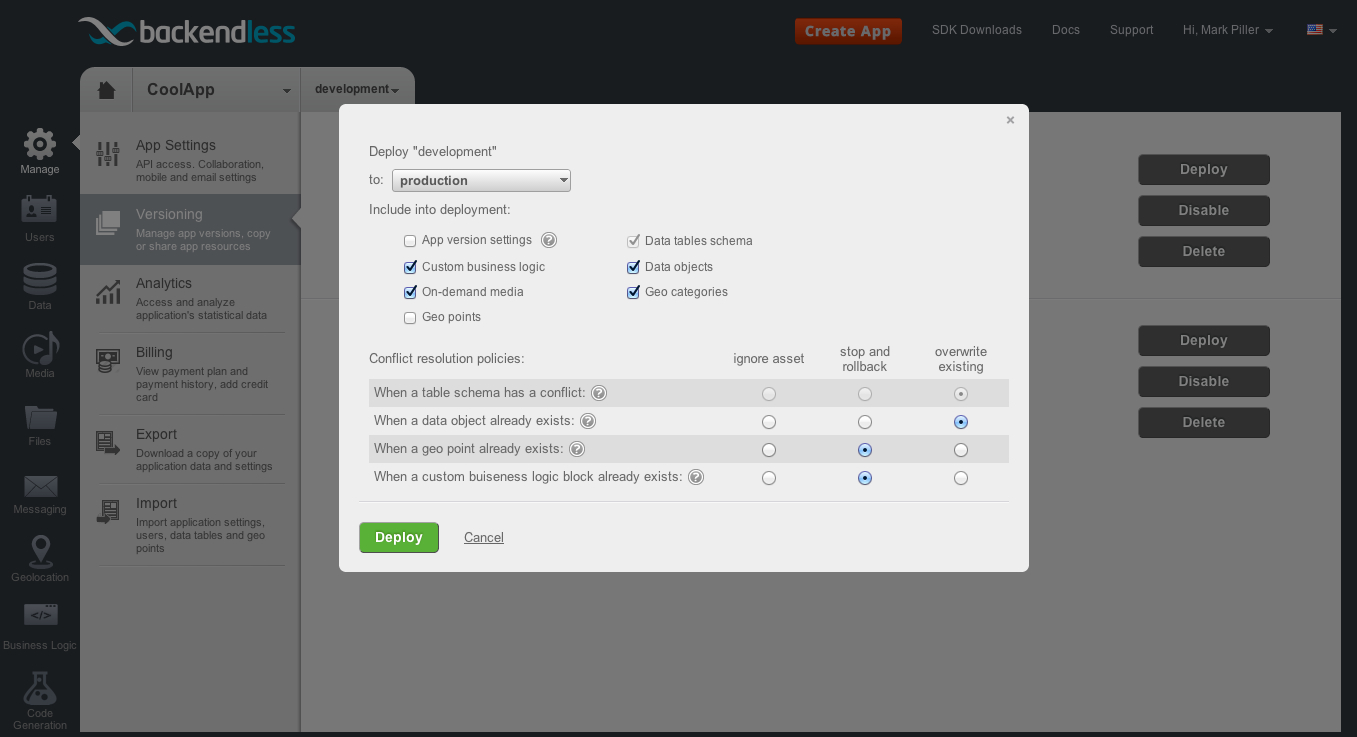
Coding applications in the traditional way is starting to look very 20th century, as in recent months we've seen more and more platforms launched with the aim of streamlining the development process.
Texas-based Backendless is the latest to enter the fray with a backend-as-a-service offering for desktop and mobile developers that's now leaving its beta phase.
By removing the need for writing code on the server-side, Backendless lets users develop applications around 50 to 100 percent faster than normal, giving developers the chance to focus more on the process logic and the client-side of the applications.
It takes care of server-side functions with easy-to-use APIs allowing developers to spend more time on business logic and user experience. Built-in services take care of user logins and session management as well as handling data and file management. Backendless can also handle push notifications, media streaming and geo-location services.
"We're passionate about Backendless because it is a paradigm shifting technology. It could have a profound impact on the whole generation of software developers and completely change the way applications are built," says Founder and CEO, Mark Piller.
The SDKs developed by the company are available for iOS/Mac OS X, Android/Java, Windows Phone/.NET, JavaScript, and ActionScript developers. There is also a REST (REpresentational State Transfer) interface suitable for any application. Backendless is language agnostic and can create standalone applications without any cloud dependencies.
In addition, the company is planning a release to integrate its services with Google Glass. By using code generation techniques and model-driven development, Backendless simplifies the process for developers building apps for Glass. Users will be able to easily customize and enhance their apps with custom voice commands to tap into Backendless services.
You can find out more about how it works and sign up for a free trial on the Backendless website.
-

Mobile app platform helps enterprises embrace mobility
Publié: avril 29, 2014, 5:12pm CEST par Ian Barker
Developing for in-house mobile platforms can sometimes be a bit of a poor relation in the allocation of resources, as it may be important to front-line departments like sales but is less so for IT.
A solution could be at hand from Irish tech company FeedHenry which has launched the latest version of its cloud platform, allowing companies to simplify the building of mobile apps for their employees.
FeedHenry 3 accelerates the development and deployment life cycle, helping enterprises to seamlessly create and manage company-wide mobile app projects. The latest version has significant new mBaaS (mobile back-end as a service) and API management, role-based development, and team collaboration features, along with support for a wide range of app development frameworks including Backbone, Angular and Xamarin.
"The reality is that mobility projects are no longer the sole remit of IT, and have become much more complex to manage and scale," says Cathal McGloin, CEO of FeedHenry. "FeedHenry 3 addresses many of the challenges companies face as they become mobile first. We're making it easier for multiple business units and IT to collaborate on mobile app development -- allowing the business to innovate on mobile while IT supports the centralized control of security, policy management and back end integration".
FeedHenry 3 uses an open, scalable architecture employing the cloud and RESTful APIs to make mobile app development more agile, sustainable and affordable compared to current industry standards.
Other features include collaborative workflows and support for native developer toolkits so that apps can be built for iOS, Android, BlackBerry, Windows Phone and the web. Developers have access to self-help capabilities and self-discovery of APIs, they can also create their own backend APIs in Node.js and share them across multiple projects.
"RESTful APIs have become the new standard for how software and devices interact," adds McGloin. "Traditionally, API Management has been all about control. With FeedHenry 3, our goal is to make APIs more accessible to developers to allow businesses to quickly and easily develop apps with the scalability that the cloud affords".
For more information or to request a demo take a look at the FeedHenry website.
-

New platform aims to get business apps working in Harmony
Publié: avril 29, 2014, 3:52pm CEST par Ian Barker

Thanks to mobile devices, the cloud and the internet of things Cisco reckons that by 2020 there will be 50 billion digital endpoints.
This volume of connected devices offers huge potential for business. But as 85 percent of enterprise data still sits on in-house systems like ERP packages and secure databases its potential is hard to release.
Integration specialist Jitterbit has announced full availability of its Harmony Integration Cloud Platform which aims to simplify the integration of a new generation of endpoints with existing enterprise systems.
It uses a graphical "Clicks Not Code" approach to empower business analysts to connect applications in days and create connected business processes that open new channels of revenue and streamline manual tasks.
Companies can quickly integrate business processes, such as connecting cloud front-office applications to on-premise ERP to provide order and billing detail for a call center rep who needs to resolve customer billing issues. Harmony provides a visual studio so that non-technical users can easily design innovative processes that connect multiple endpoints, devices, geographies, and partners.
Other features include the ability to connect to hundreds of applications, smart migration across different environments, intelligent mapping of fields and a built-in library of business formulas. It also offers secure team and individual access and complete audit trails.
"We are thrilled to deliver the biggest product release in our 10-year history to the general public," says George Gallegos, CEO at Jitterbit. "The Harmony Platform is the realization of our commitment to give customers and partners the power to use integration to amplify the value of their applications with the most modern and fastest Cloud integration platform in the market".
You can find out more and watch a video demo of Harmony on the Jitterbit website.
Image Credit: Stokkete / Shutterstock
-

Tidemark launches new analytics tools for enterprises
Publié: avril 29, 2014, 1:33pm CEST par Ian Barker

Much reporting of business metrics is still rooted in the era of static graphs and infrequent use. It's cumbersome and the information gets out of date fast.
Business planning and performance management specialist Tidemark is looking to bring reporting into the mobile and cloud era with the launch of its new Playbooks product.
Playbooks allows users to create a highlight reel of information so executives can better understand the complete narrative of their company's performance and act on potential problems as well as model new solutions.
"Modern businesses are looking to CFOs for new ways to drive growth in an era of increasing velocity, mercurial challenges and intensifying margin pressures," says Christian Gheorghe, founder and CEO of Tidemark. "We are continuing our strategy to bring innovation that helps our customers reap success and transform their organizations".
Any content within Tidemark can be added to a Playbook and shared throughout an organization. This offers a simpler approach than existing dashboard packages and lets employees add content in just a few clicks.
"Tidemark Playbooks are extremely innovative and we see a lot of opportunity to leverage them quickly," says Kristi Duncan, senior vice president of Finance at Ernest Health. "We envision using Playbooks to replace our Budget Binder and many of the other reporting books we currently use".
In addition to Playbooks, Tidemark is expanding its platform with features including self-service configuration and advanced in context analysis. There's also a business method framework offering straightforward, configurable options for tasks like tax calculations and currency conversions. A flexible modeling tool allows planning without being tied to a rigid model.
More information on Tidemark’s latest updates can be found on the company's website.
Image Credit: EDHAR / Shutterstock
-

Cybersecurity skills crisis contributes to security breaches
Publié: avril 29, 2014, 11:23am CEST par Ian Barker

Recent high profile stories like the Heartbleed bug have turned the spotlight on IT security. A new report by the Information Systems Audit and Control Association (ISACA) highlights how a skills crisis is putting more pressure on security teams.
ISACA surveyed enterprises to understand the level of attacks and their security preparedness. Key findings include that one in every five enterprises has suffered an advanced persistent threat attack, but that one in three of those don't know where it came from.
It also highlights that according to Symantec there has been a 62 percent increase in the number of data breaches in 2013. Also on Cisco's figures there's a worldwide shortage of 1 million security professionals.
To help address this growing skills crisis ISACA is launching a Cybersecurity Nexus (CSX) program. Developed in collaboration with chief information security officers and cybersecurity experts from leading companies around the world, CSX fills a need for a single, central location where security professionals and their enterprises can find cybersecurity research, guidance, certificates and certifications along with education, mentoring and community.
"Unless the industry moves now to address the cybersecurity skills crisis, threats like major retail data breaches and the Heartbleed bug will continue to outpace the ability of organizations to defend against them," says Robert Stroud, ISACA international president-elect and vice president of strategy and innovation for IT Business Management at CA Technologies. "ISACA is proud to help close this gap with a comprehensive program that provides expert-level cybersecurity resources tailored to each stage in a cybersecurity professional’s career".
The CSX program marks the first time in ICASA's history that it will offer a security-related certificate. There are four qualifications on offer needing both an exam and proof of work experience. This makes them ideal for recent university graduates and IT professionals seeking to change fields.
"Enterprises cannot rely on just a handful of universities to teach cybersecurity. With every employee and endpoint at risk of being exploited by cyber criminals, security is everyone’s business. We need to make cybersecurity education as accessible as possible to the next generation of defenders," says ISACA International President Tony Hayes.
You can find out more about the CSX program on the ICASA website and see more details on the cybersecurity skills crisis in the infographic below.

Image Credit: wavebreakmedia / Shutterstock
-

After Heartbleed -- what has the vulnerability taught us?
Publié: avril 25, 2014, 2:06pm CEST par Ian Barker
The Heartbleed OpenSSL vulnerability has sent tremors down to the very foundations of the IT world. But now that we're over two weeks on from the news of the bug first breaking what have we learned and has anything really changed? We talked to some leading security experts to find out.
There’s little doubt of the seriousness of the problem, Technical Manager at security firm Cigital, Amit Sethi says, "This is indeed one of the worst vulnerabilities in the history of the web. It has been present in OpenSSL for over two years, during which time it has made it into a lot of software. Unlike many other vulnerabilities in SSL implementations that we have heard about in recent years, this one does not require the attacker to be positioned between your computer and the server. The attacker can go directly to the server and get any information that you recently exchanged with it over a secure channel".
However, Sethi does take a positive from the news in terms of the industry's response, "...high-profile websites have been addressing the issue very quickly either by fixing it or by taking down their applications while they create a mitigation plan".
Heartbleed has the potential to affect everyone who uses the web. Sean Sullivan, Security Adviser at F-Secure says that smaller businesses may not be able to fix the problem themselves. "SMBs are typically not running their own web server or are using Apache that someone has set up for them. This is not an issue for small businesses themselves but they may be vulnerable through third parties".
Because Heartbleed mainly affected servers -- though it could be in some versions of Android too -- it meant that you were vulnerable whatever operating system you were running. Most vulnerable servers will have been patched by now and the speed with which major companies reacted has been impressive, but Alex Balan Head of Product Management at BullGuard warns that, "SSL is used by devices like load balancers and even some wireless routers which will need a firmware update".
Balan also believes that, "Heartbleed teaches us a good lesson about the state of the internet in 2014. People are more security aware and take a more proactive approach to patching servers". He also thinks that password managers will become more popular as people become more aware of security.
The need for better password security and avoiding the temptation to use a single password for multiple sites is underlined by Joe Ferrara, President and CEO of Wombat Security Technologies, "To avoid using information people could easily guess you can create a password family and also make passwords easy to remember. For example you could create a password family around automobiles. Bl&ckVo1vo (Black Volvo) might be for secure use such as your online banking and then R3dF#rr$ri (Red Ferrari) might be for more risky activities such as online shopping".
Although there has as yet been no major leakage of information captured from Heartbleed, it's still possible that we'll see attacks using stolen details in the weeks and months to come. The full extent of the problem may never be known, but at least we can take some comfort from the way that security professionals and the IT industry generally have responded and from the increased awareness of good password practice.
If the implications of Heartbleed still worry you or you think there’s anything else the industry could be doing to offer greater protection do let us know in the comments.
Image Credit: zakalinka / Shutterstock
-

Telematics adoption saves money for fleet operators
Publié: avril 24, 2014, 5:30pm CEST par Ian Barker

Despite more and more aspects of business moving online, many tasks still need to happen in the real world. In fact some things like vehicle fleet operations have arguably become more important as increasing numbers of us shop online and have our goods delivered.
Operating vehicles can be a major part of a company's costs so anything that can help control them is worthy of management consideration.
SaaS fleet management specialist Fleetmatics has released its FleetBeat report which shows the value of vehicle-based telematics in cutting transport running costs. Some 12.6 percent of all commercial vehicles in the US and Canada currently have telematics installed allowing managers to track where they are and how they're used, and according to the report this has a major impact on running costs.
Fleetmatics estimates a saving of 573 million gallons a year in fuel arising from telematics use, adding up to a saving of $2.2 billion. This also means a decrease in CO2 emissions of 5 over million tons annually. Even with a small fleet of just five vehicles it estimates that savings of almost $75,000 a year are possible for operators.
You can find out more about the FleetBeat report on the Fleetmatics website and view a summary of the findings in the infographic below.
Image Credit: Mmaxer / Shutterstock
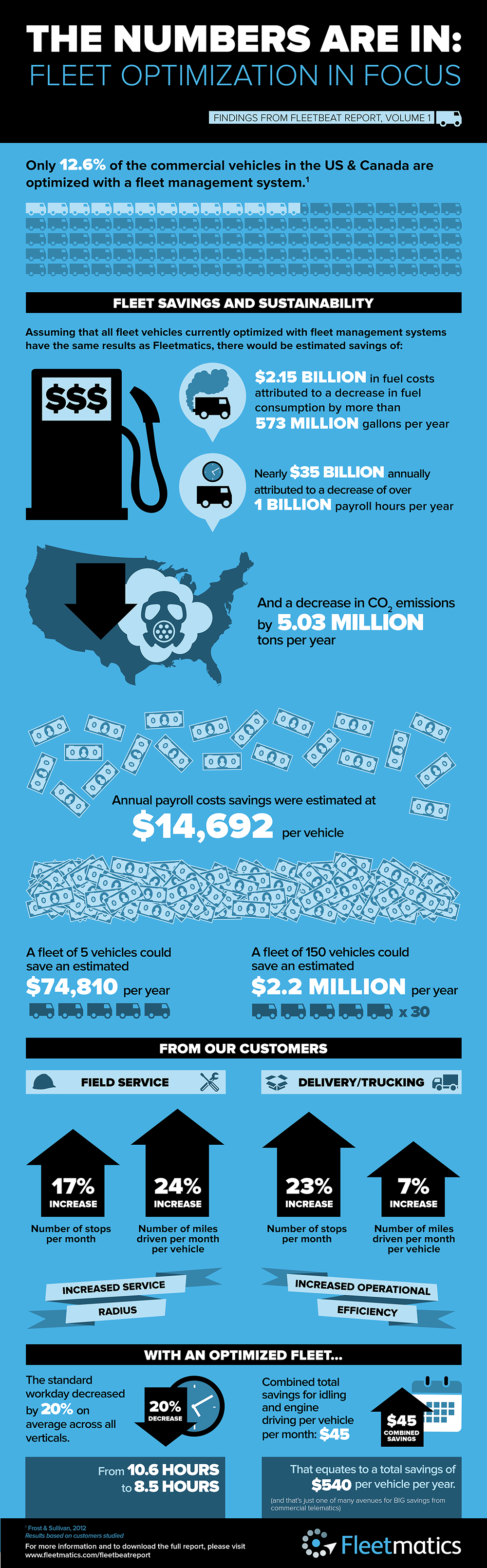
-

Visme wants to be the only tool businesses need for visual content
Publié: avril 24, 2014, 3:31pm CEST par Ian Barker
Whatever message you want to get across, whether it's in an advert, an infographic or a presentation, how it looks is key to success.
Maryland-based Easy WebContent has relaunched its Presenter tool under the name Visme aiming to make it a "Swiss knife for visual content".
Developed with input from 35,000 beta users and using a drag-and-drop interface the online tool aims to make visual content generation easy, fast and more efficient. Thousands of free images and icons are included so users can get started quickly and it enables motion and mobile/web friendly text to be added to any presentation element.
"Visme epitomizes everything we strive for. At the core we are a visualization tool and our mission is to simplify the ability for anyone to easily transform their thoughts and ideas into engaging visual content," says Easy WebContent founder Payman Taei.
The company says the most common uses of Visme are presentations, infographics, banners and short animations and teasers. Users can easily publish and share Visme content online, embed it to websites or blogs, or download it as Image, PDF or a HTML5 file.
The tool runs within your browser and a simplified interface improves the user experience and allows faster creation of content. You simply select the type of content you want to create, choose a theme and you’re into the editor. Motion can be added to any element to make animated banner ads for example.
Taei says, "You shouldn't need to be a multi-million dollar company to produce compelling visual content. And even if you are, why would you pay some exorbitant rate to bring in a third party to do something you could just as easily handle in-house? With Visme, we put the work on the back-end of our product so that producing and editing visual content is the intuitive, creative experience it should be. Our guiding principle is that complex software and esoteric coding should never get in the way of translating thoughts and ideas to visual content".
You can sign up for a free account to try the beta version for yourself on the Visme website.
-

Cloud attacks increase as the IT world looks to the skies
Publié: avril 23, 2014, 4:35pm CEST par Ian Barker

Moving systems to the cloud is usually seen as a safer and more secure option than running them on site. However, the findings of a new report suggest that there's no room for complacency.
The Spring 2014 Cloud Security Report from security-as-a-service provider Alert Logic reveals a significant increase in attacks carried out against both cloud and on-premises systems.
The report draws on data collected from a 2,200 customer base between April and September last year and reveals a significant increase in activity across both cloud and in-house hosted environments compared to last year's findings. Brute force attacks climbed from 30 to 44 percent of customers, and vulnerability scans increased from 27 to 44 percent.
These two types of incident have historically targeted on-site environments but are now appearing at almost equal rates against cloud systems too.
"Our intelligence suggests that the observed increase in cloud attacks is correlated to the growth of cloud adoption in the enterprise," says Stephen Coty, Chief Security Evangelist at Alert Logic. "As more enterprise workloads have moved into cloud and hosted infrastructures, some traditional on-premises threats have followed them. This reinforces the necessity for enterprise-grade security solutions specifically designed to protect cloud environments".
Alert Logic also deployed honeypots in public cloud infrastructures around the world to observe attack types and frequencies. Interesting findings from this are that honeypots sited in Europe received four times the number of attacks of those in the US, and more worrying that 14 percent of the malware discovered was considered undetectable by 51 percent of the top antivirus vendors.
You can read more about the report and the deployment of honeypots on the Alert Logic website.
Image Credit: Oleksiy Mark / Shutterstock
-

Are we facing an internet of too many things?
Publié: avril 23, 2014, 1:34pm CEST par Ian Barker
Much of the buzz in the tech world at the moment surrounds the internet of things, the idea that every piece of electronic kit might one day be connected via the web.
There are plenty of benefits from this but it also presents a number of challenges. Home automation specialist Custom Controls has released an infographic showing what needs to happen for the internet of things to work.
These include improved standards which will mean that companies and developers will need to work together in order to ensure that their devices speak a common language to enable them to exchange information. Security is also important to prevent information leakage and to prevent hackers from interfering with your TV or your fridge.
Speed is a factor too, with more than 50 million devices predicted to be online by 2020 there will be a greater need for fast and reliable internet connections. There's also the issue of service as much of the world is still unable to access high speed internet.
You can read more about the problems and solutions presented by the internet of things on the Custom Controls blog and view the infographic below.
Image Credit: Black Jack / Shutterstock
-

New business intelligence tool uses infographics to open up data
Publié: avril 23, 2014, 11:57am CEST par Ian Barker
Business intelligence is all about making dry figures accessible and useful to managers and others within an enterprise.
Canadian company Panorama Software is aiming to create a better data discovery solution with the launch of its new Necto 14 product. It allows users to explore, measure, track, and share critical data visually to gain knowledge, boost collaboration, and make smarter business decisions.
"The vast majority of business users consider current BI tools too complex and difficult to use. All types of people are demanding easy self-service access to more types of data, and a more intuitive way to represent and communicate their critical business metrics," says Eynav Azarya, CEO at Panorama Software. "Panorama Necto 14 offers a fresh new way for both business users and power users to review, present, and track data using context-specific visual images rather than confusing, complex graphs and reports".
Necto 14 produces infographics to present complex data in a clear and straightforward way. These are directly linked to the data and so can reflect changes in real time, making them ideal for applications like call center dashboards. They can also be used in self-service applications allowing staff to extract the data they need to do their jobs.
It offers what the company calls a 'single vision of truth' that lets users mash up data from various sources and collaborate throughout the decision making process. Other key features include a drag and drop user interface to simplify queries, a notification system to send alerts via email or dashboards and open database connectivity.
Necto 14 is available from today, for more information visit the Panorama website.
-

DrDoS attacks of more than 800 Gbps predicted by 2015
Publié: avril 22, 2014, 4:07pm CEST par Ian Barker

According to a new report by security company Black Lotus the average size of a DDoS attack in the first quarter of this year was 2.7 gigabits per second (Gbps).
But the company is warning that a new type of DrDoS (distributed reflected denial of service) attack will see the threat of 800 Gbps or more attacks in the next year to year and a half.
Reflected attacks send out requests to large numbers of machines using the address of the victim as the source, so that the target is flooded by replies. It's a bit like the spoofing of reply addresses in spam emails but on a larger scale.
The threat report, covering DDoS attack data between January 1 and March 31, 2014, shows that service providers have been heavily impacted by security threats, including SQL injection attacks, NTP DrDoS attacks, and most recently the Heartbleed bug. All of these threats have had a profound effect on the ability of service providers to operate safely and protect their customers.
Attackers have been using DrDoS methods to bypass the DDoS defenses of well-prepared companies by targeting upstream carriers. In January 2014, Black Lotus recorded several incidents in which tier 1 carriers in multiple US regions were saturated due to DrDoS attacks, resulting in packet loss rates as high as 35 percent even to customers that weren't themselves targeted by the attacks.
The biggest DDoS attack observed in the quarter was 421 Gbps and 122 million packets of data per second (Mpps). Some 19.5 percent of attacks observed were categorized as severe. More than 50 percent of those targeted individual applications, most commonly HTTP servers and domain name services.
"Historically, service providers have been able to operate without providing substantial security services to customers. That’s no longer viable, as threats proliferate and attackers find new ways to amplify the volume of their efforts," says Jeffrey Lyon, founder of Black Lotus. "To protect themselves and their customers, service providers must now also become security providers by offering integrated hosting and security services such as DDoS mitigation, intrusion defense, and incident response and remediation".
The full report is available to download from the Black Lotus website.
Photo Credit: Fabio Berti/Shutterstock
-

Dell partners with DataMotion to offer email encryption
Publié: avril 22, 2014, 1:28pm CEST par Ian Barker

When Dell acquired SonicWALL in 2012 it was heralded as a significant step in providing greater security to the company's enterprise customers.
It's now announced a partnership with email encryption specialist DataMotion to allow users of SonicWALL email security to encrypt their sensitive emails and attachments.
The alliance will provide compliance-grade encryption capabilities for all emails and file attachments with just a simple mouse-click from within the Outlook client. The combined DataMotion-Dell SonicWALL solution helps prevent confidential data leaks and regulatory violations thanks to advanced compliance scanning, management and email encryption thus ensuring the secure exchange of email containing sensitive customer data or confidential information.
"We were very focused on partnering with a cloud-based email encryption solution that offered the best end-user experience on both desktop and mobile platforms. After evaluating the leading email encryption providers, it was clear that the DataMotion solution was the best choice for us," says Patrick Sweeney, executive director of product management at Dell. "Their encryption technology complements our existing email security portfolio very well, and the DataMotion team was really easy to work with and willing to accommodate our specific needs and requirements".
Encrypted email is now a legal requirement for some organizations in order to comply with privacy regulations like HIPAA (Health Insurance Portability and Accountability Act). The DataMotion platform allows Dell to offer its customers a powerful but easy to use, cloud-hosted service that can guard emails and attachments against data theft or accidental exposure.
"It is extremely satisfying to have our cloud-based email encryption technology recognized and adopted by a world leader in email security appliance solutions," says Bob Bales, CEO of DataMotion. "I am particularly pleased that Dell recognized not only our technical prowess, but also our agility and strength as an organization to support their offer worldwide. We are thrilled to be a part of the Dell Software partner family".
You can find out more about SonicWALL security products on the Dell website.
Image Credit: Pixel-3D / Shutterstock
-

How E-commerce is taking over the world
Publié: avril 18, 2014, 10:48am CEST par Ian Barker

The internet has been responsible for changing the way we go about many of the tasks in our day-to-day lives. Not least it has changed the way we shop.
Customer experience specialist Baynote has released a new infographic map showing the growth of e-commerce across the world.
Interesting highlights include the fact that in the US e-commerce is growing at four times the rate of retail and in China it grew by 51 percent in 2013. India's e-commerce market is expected to increase from $13 billion in 2013 to between $50 and $70 billion by 2020.
The graphic also highlights the hotspot cities that play host to major players in the e-commerce world. Seattle, home of Amazon, for example accounts for more that $61 billion in online sales. However, this is dwarfed by Hangzhou in China, home to the Alibaba site which manages more transactions than Amazon and eBay combined.
Another interesting trend is that 60 percent of E-commerce shoppers now use social network sites and tools in order to interact with brands showing that our online lives aren't neatly pigeon-holed.
Click on the image below to view the full size map and see how e-commerce is spreading across the globe.
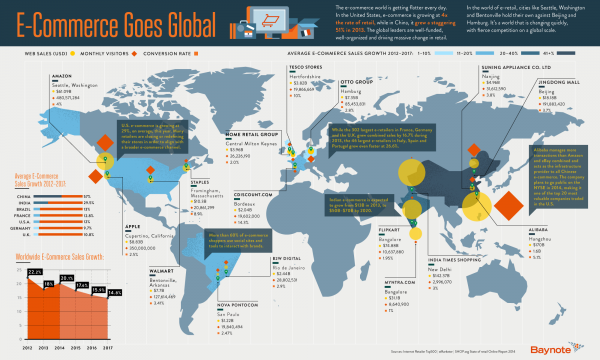
Photo Credit: Nonnakrit/Shutterstock
-

Oracle marketing cloud for manufacturers improves performance and efficiency
Publié: avril 17, 2014, 4:23pm CEST par Ian Barker

Manufacturing businesses are always looking to improve the customer experience and enhance their marketing effectiveness.
In recent years this has meant moving from a product-centered model to a more customer-focused approach. To help with this process ERP specialist Oracle is launching a flexible industry-specific marketing tool in the form of Oracle Eloqua for Manufacturing.
The latest addition to the Oracle Marketing Cloud, this new product provides marketers with a full overview of the buying process including insights into customer behavior which ultimately results in higher quality sales leads.
Eloqua for Manufacturing also includes product registration capabilities that help deliver efficient product maintenance and subscription renewals and enable manufacturers to keep in touch with customers after they’ve made a purchase. This means there's a better chance of repeat business and retaining customers for the long term.
"Manufacturing organizations want to improve engagement with customers and prospects across digital channels so that they can gain better visibility into their sales pipeline and grow their businesses," says Steve Miranda, executive vice president, Oracle Applications Development. "With capabilities developed specifically for manufacturers including pre-built templates and leading business intelligence, Oracle Eloqua for Manufacturing helps manufacturers improve marketing effectiveness and drive revenue".
Key benefits include fast, accurate targeting, improved personalization from profiling interactions across social media as well as the sales process. Better lead management and more effective means of getting customers to register products and sign up to maintenance plans.
All of this means that customer data is more accessible to marketing teams and can be used to increase loyalty and generate additional leads. Because it's based in the cloud it also means mobile sales staff can access pre-approved content and templates for campaigns whilst on the move.
You can find out more about Eloqua for Manufacturing on the Oracle website.
Photo Credit: Jirsak/Shutterstock
-

How the cyber threat landscape is evolving -- Comodo security [Q&A]
Publié: avril 17, 2014, 12:09pm CEST par Ian Barker

In recent years the threats faced by both individuals and businesses have changed thanks to the adoption of new technologies like the cloud, a shift towards social engineering attacks, BYOD and more.
We spoke to Egemen Tas, vice president of engineering for leading certificate authority and security software provider Comodo to get his view on current threats.
BN: How has the threat landscape for PC users changed in recent years?
ET: In the last 15 years, just like everything else, there has been an evolution of cyber-threats. In the past, we used to deal with viruses designed for a variety of purposes, from those written to annoy people to viruses that allowed attackers to control PCs. Then came the worms that were designed to spread and inflict large-scale damage to victims' networks. Today, we are dealing with viruses that act as cyber-weapons and extortion tools. While the old threats still exist, an average PC user now has much more to worry about including: secure online banking and shopping, online extortion, social media privacy and pervasive third party surveillance.
BN: What are the risks posed by increased adoption of the cloud to store data?
ET: Simply put, users' data is a password away from anyone. Previously, physical access was required and now the cloud has changed this. For consumers, they may think that the data they store is only about the file they upload to services such as Dropbox, but in reality, they are putting a lot more data into the cloud. For example, social media is an indirect data storage medium and there are genuine privacy problems in this area.
BN: Is social engineering now a bigger risk than more 'traditional' malware attacks, are people always the weakest link in the security chain?
ET: People are now more connected than ever. So there are more channels to reach people and do social engineering. In the end, viruses need to propagate and social engineering through email (i.e. spamming) is an effective method. Users can stay protected by just following a few basic security practices such as recognizing executable files and not opening the ones coming as email attachments.
BN: How can businesses ensure that their security isn't compromised by BYOD?
ET: In terms of security, compliance and enterprise data protection are two major problems of the BYOD paradigm. Much of the research and innovation is now focusing on enabling BYOD users to access enterprise data securely. Most vendors, including Comodo are focusing on containerization of enterprise applications. These applications run inside a hardened container, which provides various security features such as, encrypted data storage and encrypted communication over the internet. Admins are then able to secure only enterprise data while enabling users to use their own devices to access mission critical company data. Mobile device and data management products can be used for this purpose.
BN: As Windows has become more secure are other systems like Apple and Linux at greater risk and is complacency a factor?
ET: Microsoft's trusted computing initiative has really made a significant difference in Windows' security. However, most modern malware is targeting Windows platforms due to the fact that Windows devices are pervasive. I do not see Apple approaching security in the way that Microsoft approaches it. Apple favors a closed platform approach, where only Apple-approved applications can run. Most people are under the impression that there are no viruses for Apple's platforms. For IOS, this is currently true. However, for MAC OS X, this is not true. I think that Apple needs to build partnerships with antivirus vendors to improve the security of their platforms.
BN: Will the recent Heartbleed OpenSSL bug make online businesses take security more seriously?
ET: It has to. Since this bug was revealed, the potential for its exploitation is very high. An attacker who can steal your private keys is just like a thief who has the keys to your publicly accessible safe. At Comodo, we have many SSL customers, and we are offering them free regeneration of their certificates if they want to do so. More information about the Heartbleed bug can be found on Comodo's blog.
Image Credit: watcharakun/Shutterstock
-

Getac launches rugged Windows tablet for mobile workers
Publié: avril 16, 2014, 3:29pm CEST par Ian Barker

With tablets becoming more common in the workplace, the problem with normal models is they're not robust enough to cope with the demands of utility workers and field service operatives.
We saw Dell address this market a few weeks ago with a tough convertible system and now rugged systems specialist Getac is launching a new Windows 8 tablet specifically aimed at mobile field workers.
The Getac T800 has an 8.1-inch screen, is 24mm thick and weighs 0.88Kg. It uses a quad-core Intel N3530 2.16GHz processor and is designed to offer the toughness needed for mobile use without sacrificing power and performance. It has MIL-STD 810G and IP65 ratings, meaning the device can handle shock, drops and vibration to military grades while also being sealed against dust and water.
In addition it uses Getac's unique SnapBack expansion system which lets users add expansions to the T800 such as an extra battery, increasing the operational use to greater than 16 hours, or a 2-in-1 RFID and Smart Card Reader. The screen uses Lumibond, Getac's proprietary technology, that offers excellent touch control and sunlight readability without placing too much drain on the battery.
The T800 also provides a wide range of connectivity options. It can be configured with 4G LTE cellular data with an auto tunable 8-band antenna capable of quickly switching between bands. It also includes the latest 802.11ac Wi-Fi for data transfer speeds up to three times faster than 802.11n products. An optional SiRFstarIV GPS offers double search capacity, faster location positioning and improved accuracy.
Peter Molyneux, President of Getac UK says, "The T800 gives the best performance of any fully rugged Windows 8 tablet in the market today. Our customers have given us tremendous feedback on the T800's thin and light design, while offering high levels of integration and field performance. We always target to give our customers the latest in fully rugged computer technology with no compromise on performance, and again we feel confident we have achieved this in the T800".
You can find more information on the T800 on the Getac website.
-

Stickeez boosts ad revenue for mobile developers
Publié: avril 16, 2014, 3:03pm CEST par Ian Barker

In-app adverts provide a useful revenue stream for developers, allowing them to monetize what would otherwise be free products.
With Gartner predicting that over 94 percent of app downloads will be free by 2017, revenue from in-app ads is likely to become even more critical in the future.
Israel-based digital platform specialist ironSource has announced that in the two months since its launch in February of this year Stickeez, which uses the company's mobileCore native ad format, has boosted developer ad revenues by 20 percent.
Unlike other mobile advertising systems, Stickeez provides developers with a non-aggressive, ad delivery system that can integrate seamlessly with the look and feel of their app. It presents users with an engaging animation that displays mobileCore offers or other apps available to download once clicked.
"In today's predominantly free app market, developers need to find creative ways to monetize their product, but they also have to protect their user's in-app experience," says Itay Riemer, General Manager, mobileCore at ironSource. "Stickeez offers developers a highly-effective means of generating revenue without compromising on user experience".
Developers can choose images from a Stickeez gallery or incorporate their own characters. Currently mobileCore creates custom branded Stickeez for advertisers to promote specific apps, this customization capability will soon be rolled out for every developer using the format. Because it uses the existing mobileCore Developers Panel it also offers maximum flexibility.
"ironSource has always been committed to solving problems and providing solutions for software developers -- whatever platform they are working on," says Tomer Bar Zeev, CEO and Co-Founder. "Both Stickeez, and mobileCore in general, are designed to empower the developer to monetize more effectively so they can focus on the thing they do best -- developing great products".
For more information on Stickeez visit the mobileCore website.
Image Credit: Sergey Nivens / Shutterstock
-

The security risks of BYOD -- Amtel [Q&A]
Publié: avril 14, 2014, 11:00am CEST par Ian Barker

Allowing employees to use their own mobile devices for work has led to a number of new challenges, particularly when it comes to keeping devices and data secure.
We talked to PJ Gupta, CEO of mobile security specialist Amtel about the risks BYOD presents to enterprises and what they can do to ensure they remain safe.
BN: Are businesses becoming more vulnerable as a result of implementing BYOD strategies?
PJG: This question is always asked whenever new technologies and paradigms are introduced into enterprise IT environments. Did networking make the enterprise vulnerable? Doesn’t Wi-Fi access to corporate data expose the company to security breach?
The short answer is, yes. Risks and vulnerabilities increase when you introduce external variables to a well-controlled system. When employees bring in their own mobile devices to work, the risks rise but the flexibility, efficiency and productivity gains from such technologies and initiatives make it worthwhile to embrace the advances and manage the risks.
BN: What are the risks presented by third-party apps on employee devices?
PJG: Typically, on a BYOD device, there may be platform apps, enterprise apps and public apps. Platform apps, widgets and tools come with the device from vendors such as Apple, Google, Samsung and major Carriers. Enterprise apps are created by your company or a trusted partner (an example may be Salesforce.com or Workday). Public apps are downloaded by the user from a public app store such as the Apple App Store or Google Play.
Despite efforts by Apple and Google, the sheer volume of public apps makes it very hard to verify that such apps do not bring security and data leakage risks to an enterprise. For example, using a personal Dropbox account to store corporate data can jeopardize data security. In addition, risks associated with uncontrolled use of social media, streaming and game apps can waste time, hit employee productivity and cause HR policy compliance headaches.
BN: In addition to protecting their networks, companies need to safeguard their intellectual property. What steps can they take to minimize the risks BYOD presents in this area?
PJG: Companies need to protect confidential data and intellectual property that may be stored on enterprise systems, applications and email. The key to protection is authentication of users, access control and encryption of confidential information.
Companies need to put password policies in place for strong authentication of users. Integrate with Active Directory and LDAP for managing access control to corporate email and applications. Adopt Single Sign On (SSO) and two-factor authentication for application access for simpler and better security. They should also make sure remote access via Wi-Fi or wide area networks is secured through virtual private network (VPN) technology.
In addition they can protect sensitive information by encrypting the data at rest and in transit (on the wire or wireless transport). Secure containers on BYOD devices themselves can be encrypted too. Putting in place data loss prevention policies such as remote location and selective wiping of mobile devices and data leak prevention that thwarts copy and paste to and from secure containers helps keep data safe.
BN: Does BYOD present additional problems when it comes to compliance?
PJG: Compliance is a thorny issue for BYOD. Security and compliance with regulations such as HIPAA, SOX and PCI require complete accountability, traceability and audit trails. On the other hand, BYOD is a personal device but the company’s privacy policy needs to be honored and Personally Identifiable Information (PII) needs to be protected. For example, regulatory compliance may require that you track a device at all times, but personal privacy mandates that you don’t track a device when the employee is not at work (either onsite or offsite).
The answer is a delicate balance between regulatory compliance and personal privacy. Perhaps GPS tracking can be forced on during work hours and become optional after hours as employees wish. Location based policies via geofencing technology will provide more flexibility in a BYOD environment. For example, public app access and device features such as camera and NFC can be restricted within work location boundaries, but can seamlessly be enabled outside.
BN: How can businesses minimize the risk of data leaks from devices that are lost, stolen or simply fall into someone else’s hands?
PJG: There are two prescriptions for loss prevention of corporate data if a device is lost or stolen. The first one is location tracking, remote locking, and selective or full wipe of the device. This can be accomplished so long as the device is managed with a mobile device management app installed.
The second imperative, as mentioned earlier, is to protect sensitive information by encrypting corporate data in a secure container on BYOD devices. Enterprise apps and mail server must share corporate information only in the secure container which can be automatically wiped when the user exits the enterprise app or corporate location (as determined by geofencing).
BN: What happens when employees move on to another role or leave the company altogether?
PJG: Again administrators can selectively wipe a corporate container on the device while leaving personal content intact. They can also manage credentials and access control with Active Directory (AD) integration so that access privileges are removed when AD is updated with an employee exit event.
A tricky aspect is when a sales rep, sales engineer or partner rep leaves the company. Company policy should ensure that third-party contact information is saved in company databases (such as Salesforce.com for example) not just on the individual’s BYOD device.
BN: Can BYOD ever work in a completely safe way?
PJG: BYOD can never be 100 percent safe. In business you take calculated risks for the sake of operating efficiency. BYOD brings clear benefits of flexibility and efficiency. BYOD risks can be managed to realize the benefits.
Image Credit: PlusONE / Shutterstock
-

Heartbleed -- the passwords you need to change
Publié: avril 11, 2014, 11:10pm CEST par Ian Barker

The unveiling of the Heartbleed OpenSSL flaw this week has led to major ripples through the IT industry and the online community.
There has been all kinds of advice on offer about changing passwords -- but only after the site in question has been made safe. To be certain you're doing the right thing you therefore need to either check the site yourself or wait for some official confirmation that it's been patched.
But if you wait for a prompt you then, of course, need to avoid the inevitable raft of phishing emails trying to trick you into giving away your password on fake sites.
To make life a bit easier, VPN specialist IVPN.net has released an infographic showing which major sites have been affected, which ones have been patched and whether you need to change your password.
With all of the information flying around at the moment this is a handy way of cutting through the confusion.
Image Credit: Spartak/Shutterstock
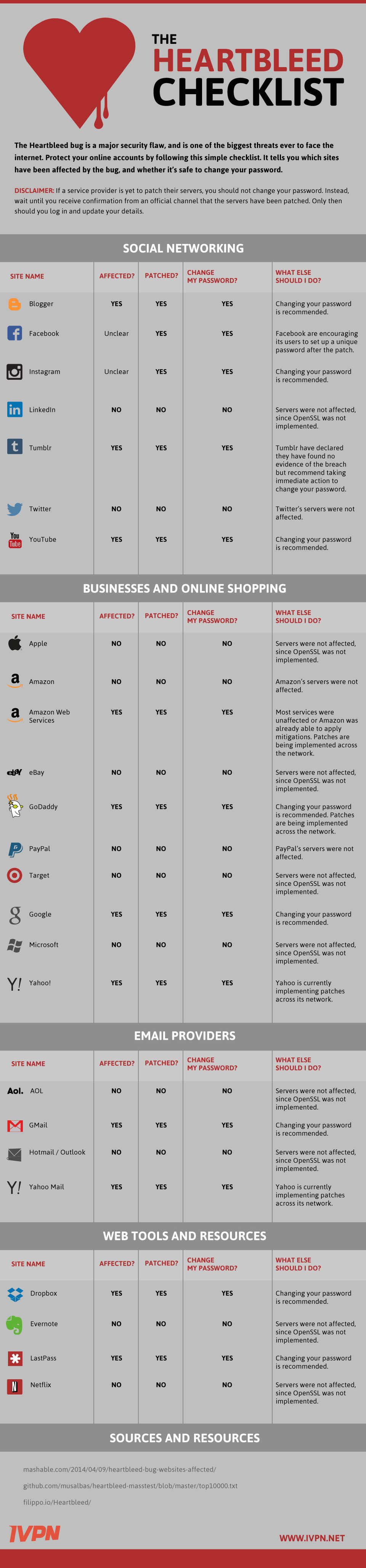
-

OpenMarket introduces new messaging solutions for enterprise IT
Publié: avril 10, 2014, 3:19pm CEST par Ian Barker

Business IT is increasingly expected to operate on a 24/7 basis which means that system admins need fast access to information should anything go wrong, whether it’s a security incident or a system failure.
Enterprise mobile specialist OpenMarket has launched a suite of solutions aimed at helping to ensure continuity, security and improve support management.
OpenMarket's Mobile Engagement Platform enables enterprise IT and security leaders to develop and customize a variety of mobile messaging services to meet their business needs. This includes messaging for network and system outage alerts and emergency notifications, escalation alerts for support tickets, and security messages including two-factor authentication, fraud alerts and password change reminders.
Jay Emmet, General Manager at OpenMarket says, "By deploying a flexible and customizable mobile engagement platform, enterprises can implement cost-effective mobile messaging solutions that support IT and security needs, plus a wide variety of other functional use cases across the entire organization".
Mobile is the most effective means of delivering mission critical messages as, according to OpenMarket, research shows that over 90 percent of text messages are read within three minutes of receipt.
The OpenMarket Mobile Engagement Platform is a SaaS-based solution, allowing enterprises to easily create and deploy messaging solutions. It can be accessed via a web-based GUI or directly via service APIs.
You can get more information on OpenMarket’s Mobile Engagement Platform and SMS solutions on the company's website.
Image Credit: Sergey Nivens / Shutterstock
-

Heartbleed -- should we panic now?
Publié: avril 10, 2014, 12:43pm CEST par Ian Barker

Yesterday the IT world went a little bit crazy over the disclosure of the Heartbleed bug and the chance that encrypted information could potentially be intercepted by hackers.
We know that some big sites, notably Yahoo, have been exposed and Google was quick to apply the necessary patches to its servers. If you’re still worried, a number of sites have sprung up allowing you to check if a site has been patched -- thanks to Bob Grant on the comments thread to yesterday’s story for highlighting that one.
Since then some sites have been sending out emails advising users to change their passwords and a raft of experts have been urging the same thing.
But let's take a step back for a second. Heartbleed has been around for two years, so if your information was going to leak there’s a good chance it would have happened already. Also the disclosure of the bug seems to have been done in a very measured way, as neatly satirized on Twitter:
☑ register [t.co] domain ☑ get custom graphic designed ☐ disclose to distros in advance ☑ disclose to public Priorities
— keyist (@keyist) April 8, 2014
The problem is that Heartbleed doesn’t leave a trace, so there’s no way anyone -- other than the bad guys -- knows whether anything has been stolen or not. And because it's a problem on the server there's little you as a user can do about it, except stay offline. This also means that as far as the end user is concerned it's operating system agnostic too, it doesn't matter whether you’re using Windows, OS X, iOS or Android, your data is equally vulnerable.
What then is an end user to do? The first thing is not to panic, this doesn’t affect every single website. In fact for once Microsoft comes up smelling of roses because its Internet Information Services (IIS) server software doesn't use OpenSSL.
Codenomicon which broke the news of the bug reckons that around 66 percent of sites do rely on open source servers that run OpenSSL and are therefore potentially at risk. Even then some of these sites will have used the Perfect Forward Secrecy feature that will have limited how much data could be exposed.
If you feel the need to do something then changing your password isn't a bad idea, it's something you should do occasionally anyway -- though most of us don't -- but do check that the site has been patched first otherwise you're just giving the new password away.
However, this isn't like other recent high profile breaches where lists of stolen data have been posted online. Yes there's a moderate risk that your passwords may have been compromised but you don't need to rush off and start resetting the passwords on every site you use. By all means change them next time you log in, but don't let Heartbleed ruin your day.
Image Credit: happydancing / Shutterstock
-

Anaplan launches territory planning and quota management for Salesforce
Publié: avril 9, 2014, 4:29pm CEST par Ian Barker
Cloud-based business planning specialist Anaplan has launched a new territory planning and quota management tool on the Salesforce1 App Exchange.
Anaplan provides real-time analytics, allowing sales managers to adjust their planning to produce better results.
"Top performing companies such as HP and McAfee are already using the Anaplan platform to optimize sales processes and drive revenue and margin improvements," says Fred Laluyaux, CEO, Anaplan. "With the Salesforce1 AppExchange, we are putting the game-changing capabilities of the Anaplan platform into the hands of more users, and we are getting closer to salesforce.com’s world-class enterprise cloud computing ecosystem".
The application gets continuous updates from Salesforce so that plans can be constantly optimized and updated based on the latest information. This results in a 'living plan' where each member of the sales organization has a tailored view of their activities.
Frontline sales reps, district managers, and higher levels of management can see which accounts make up their patch and what the account level targets are by product and service lines. Using Anaplan’s HyperBlock planning intelligence system teams can explore 'what if' scenarios and understand the impact of changes and disruption.
Key features on offer include account segmentation, division of sales territories, capacity planning and quota management.
"Companies are looking to transform the way they connect with customers, partners and employees to thrive in the today’s connected world," Ron Huddleston, senior vice president, Global AppExchange & Partner Program at salesforce.com says. "By leveraging the power of the Salesforce1 Customer Platform, Anaplan provides customers with the proven social, mobile and connected cloud technologies to accelerate business success".
Planning and quota management is available now on the Salesforce1 App Exchange.
Image Credit: EDHAR / Shutterstock
-

OpenSSL flaw unlocks the internet's 'crown jewels'
Publié: avril 9, 2014, 11:24am CEST par Ian Barker

If all of your system adminstrator friends are looking worried today it isn't the usual post Patch Tuesday blues, it's because of a bug in something that you may never have heard of, but which almost certainly affects your everyday use of the web.
OpenSSL is a cryptographic library that is used to secure large chunks of the internet. If you use sites or apps that send and receive encrypted data then it’s very likely they use OpenSSL to do it. It's used by open source web servers like Apache as well as by mail protocols including SMTP, POP and IMAP.
Thanks to a bug uncovered by Google Security that researchers are calling "Heartbleed" it's possible to fool OpenSSL systems into revealing part of the data in their system memories. This might be things like credit card transactions but it’s potentially even more serious than that.
Security specialist Graham Cluley writing on his blog says, "...it could also disclose the secret SSL keys themselves. These are the 'crown jewels', and could be used by malicious hackers to do even more damage, without leaving a trace".
If you want a detailed look at the flaw and how hackers may be able to exploit it, Elastica's CTO Dr Zulfikar Ramzan has posted a detailed walkthrough on his company's website. He stresses that the flaw is not inherent in the SSL/TLS protocol itself but in the specific OpenSSL implementation.
Finnish security specialist Codenomicon has a Heartbleed website with details of the bug and which lists vulnerable versions. It also lists operating systems that have shipped with potentially vulnerable OpenSSL versions, these include major Linux distros like Debian and Ubuntu.
It advises that site admins need to update to OpenSSL 1.0.1g immediately, and regenerate private keys. If an update to the latest version of OpenSSL isn’t possible it advises developers to recompile OpenSSL with the compile time option OPENSSL_NO_HEARTBEATS.
The bug has been in OpenSSL since December 2011 though it was only publicly announced yesterday. Whilst it isn’t known if it’s been exploited in the wild, Heartbleed leaves no trace in the server’s logs so it’s hard to know if a system has been compromised. The official security advisory is available here.
Image Credit: Linda Parton / Shutterstock
-

Mega data breaches indicate shift in cybercrime landscape
Publié: avril 8, 2014, 4:54pm CEST par Ian Barker
Cybercriminals are increasingly plotting for longer to pull off big heists rather than carrying out quick hits for smaller rewards.
Symantec's latest Internet Security Threat Report shows a significant shift in criminal behaviour as some of the most damaging attacks in history were carried out in the last year.
The report shows that in 2013, there was a 62 percent increase in the number of data breaches from the previous year, resulting in more than 552 million identities being exposed.
"One mega breach can be worth 50 smaller attacks," says Kevin Haley, director of Symantec Security Response. "While the level of sophistication continues to grow among attackers, what was surprising last year was their willingness to be a lot more patient -- waiting to strike until the reward is bigger and better".
The report notes that each of the top eight security breaches in 2013 resulted in the loss of tens of millions of records, where in the previous year only a single breach reached that level. Also targeted attacks increased by 91 percent and lasted an average of three times as long compared to 2012.
Interestingly personal assistants and those working in public relations were the two most targeted professions as cybercriminals see them as a stepping stone toward higher-profile targets like celebrities or business executives.
"Nothing breeds success like success -- especially if you're a cybercriminal," adds Haley. "The potential for huge paydays means large-scale attacks are here to stay. Companies of all sizes need to re-examine, re-think and possibly re-architect their security posture".
You can find the full 2014 Internet Security Threat Report on the Symantec website. More information on mega breaches and how you can protect yourself and your business is in the infographic below.
 Image Credit: zimmytws/Shutterstock
Image Credit: zimmytws/Shutterstock -

CryptoDefense could be a bigger threat than CryptoLocker
Publié: avril 3, 2014, 5:41pm CEST par Ian Barker
Only a couple of days ago we reported on the CryptoDefense ransomware conveniently leaving behind its decryption key.
But today Stu Sjouwerman CEO of security training specialist KnowBe4 is warning that, flawed though it is, CryptoDefense represents a serious threat.
The ransomware targets text, pictures, video, PDF and Office files and encrypts these with a strong RSA-2048 key which is hard to undo. It also wipes out Shadow Copies which are used by many backup programs. This gives it the potential to cause major, major problems.
The cybercriminals behind CryptoDefense charge $500 in BitCoins to unlock the system, increased to $1,000 if you fail to pay up within the first four days.
"There is furious competition between cybergangs," says Sjouwerman. "They did their test-marketing in countries like the UK, Canada and Australia and are now targeting the US. CryptoDefense doesn't seem to be a derivative of CryptoLocker as the code is completely different, confirming this is a competing criminal gang".
The malware at first installed through programs that pretended to be flash updates or video players needed to view online footage. It has since moved on to a variety of different phishing attacks in the form of emails with a zip file directing recipients to "open the attached document" which was supposed to have been "scanned and sent to you".
"It is obvious that this is a social engineering ploy and that effective security awareness training will prevent someone from opening these infected attachments when they make it through the filters (which they regularly do)," says Sjouwerman. "Once infected, the only way to fix this relatively fast is to make sure you have a recent backup of the files which actually can be restored. Even then, it can take several hours to restore the data".
Sjouwerman also points out that the flaw which left behind CryptoLocker’s key has almost certainly been fixed by now. You can find out more about how to avoid getting caught by ransomware on the KnowBe4 website.
Image Credit: Carlos Amarillo / Shutterstock
-

Adaptiva simplifies migration to SCCM 2012
Publié: avril 3, 2014, 3:24pm CEST par Ian Barker
If you use Microsoft System Center Configuration Manager (SCCM) you're probably aware that support for the 2007 version ends in July.
In response to this, systems management specialist Adaptiva is launching a Content Push Policy to its OneSite product, aimed at simplifying and cutting the costs of migration to SCCM 2012. It will also allow newcomers to SCCM to deploy the package more quickly.
"With the end of life for SCCM 2007 nearing, it’s imperative for companies to make the move to SCCM 2012," says Deepak Kumar, founder and CTO of Adaptiva. "System migration involves a lot of data. Content Push Policy simplifies and speeds migration, in most cases by orders of magnitude. It also substantially accelerates new SCCM 2012 installations".
OneSite does away with the need for SCCM servers at remote locations by aggregating spare processor and disk capacity into virtual servers. Benefits of the Content Push policy include, easily switching clients to a new environment, allowing software to be downloaded, unpacked and distributed outside SCCM, and an Office Push feature that automatically selects the most suitable machines for content delivery.
Using Adaptiva's OneSite feature admins can also benefit from predictive bandwidth harvesting (PBH). This looks at when the WAN will be congested and sends data only when it won't interfere with other business-critical traffic. Content already cached at operating locations in the 2007 environment will remain in the 2012 environment, avoiding massive "re-downloading" and so reducing WAN traffic. Users also benefit from an intelligent virtual storage area network (SAN) at each location, without requiring new disk capacity or taking up disk space from end users.
More information on OneSite and SCCM migration is available on the Adaptiva website.
Photo Credit: RAJ CREATIONZS/Shutterstock
-

Dell toughens up its act with new rugged systems
Publié: avril 3, 2014, 12:22pm CEST par Ian Barker

As computers become essential tools for more and more jobs they often need to work in harsh environments that would damage a conventional machine.
Dell is launching two new Latitude Rugged Extreme systems that are purpose-built to withstand hazards such as dust, moisture, drops, vibration, extreme temperatures and other punishing conditions faced by users in fields such as military service, public safety, manufacturing and first response.
The Latitude 12 Rugged Extreme is the industry's first fully rugged convertible notebook that easily transforms into a tablet, the Latitude 14 Rugged Extreme is a notebook that's built for demanding conditions.
"With new ground-up design and industry-first innovations, the Latitude 12 and 14 Rugged Extreme mark the beginning of a renewed and expanded commitment by Dell to the rugged space," says Kirk Schell, former officer in the United States Navy and vice president, commercial PCs, client solutions group at Dell. "The Rugged Extreme line is backed by the Latitude promise of reliable, secure and manageable commercial PCs and can move easily from the boardroom to the battlefield or wherever the job takes you -- an assurance unmatched by the competition".
The machines are built using impact-resistant polymers and sturdy magnesium alloy. Data is protected from the elements with sealed doors and compression gaskets while enabling performance at high temperatures with fourth-generation QuadCool thermal management.
Both systems feature a Direct-View outdoor display that's designed to be readable in bright sunlight and reduces reliance on backlighting to prolong battery life. Resistive multi-touch on the Latitude 12 means it can be used even when wearing gloves. A sealed backlit keyboard allows work in low lighting conditions.
Each offers up to 16GB of RAM and 512GB of solid-state storage. There's also a full HD webcam with a privacy shutter and the Latitude 12 features an eight megapixel bottom camera with flash.
Prices for the Latitude 12 Rugged Extreme convertible notebook start at $3,649 and it will be available from May 6. The Latitude 14 Rugged Extreme begins at $3,499 and will go on sale in mid-May.
-

Cloud adoption reaches over 90 percent as the technology matures
Publié: avril 2, 2014, 5:15pm CEST par Ian Barker

Use of the cloud is close to becoming universal as enterprises increase their adoption of both private and public services.
This is one of the main findings of the 2014 State of the Cloud report released today by RightScale. It also finds that as cloud use matures security concerns lessen and attention increasingly shifts to managing the ongoing challenges of compliance, cost management, and performance.
"Enterprises are adopting cloud computing in record numbers and have leveraged growing experience to overcome many of the early challenges including security," says Michael Crandell, founder and CEO of RightScale. "Large enterprises are complex and understandably deliberate in cloud adoption, yet with increased adoption they continue to unlock more value".
RightScale surveyed more than 1,000 IT executives and found that 94 percent of organizations asked are running SaaS applications or experimenting with infrastructure-as-a-service. 87 percent of organizations are using public cloud services.
As companies come of age in their understanding of the cloud they deploy more and different uses. Test and development applications top the list, with more than 85 percent of cloud-focused companies deploying them in the cloud. Customer web apps and internal web apps follow, however social apps have seen fewer cloud deployments at 18 percent, down from 23 in last year's report.
A number of respondents report significant benefits from their cloud usage, these include improved availability and better geographic reach as well as cost savings. Respondents in more cloud focused organizations report that issues require ongoing attention -- compliance, cost and performance -- have become more important than security worries.
Looking ahead, many enterprises see hybrid and multi-cloud implementations as their goal. 74 percent of enterprise respondents say they have a multi-cloud strategy, and 48 percent are planning for hybrid clouds. In addition, 15 percent of enterprises expect to use multiple public clouds, and 11 percent are planning for multiple private clouds. Companies are also embracing DevOps to enable faster production of software as well as moving towards self-service IT.
The report also notes growing competition in the public cloud space. Amazon Web Services continues to dominate on 54 percent but offerings from Google and Microsoft are gaining the interest of cloud users, with Azure leading among enterprises and Google Cloud Platform among small and medium organizations. Rackspace Public Cloud is second within the SMB segment.
In private clouds OpenStack looks set to knock VMware off the top slot whilst Microsoft System Center is a strong third among enterprise users.
The survey provides an interesting overview of how cloud usage is changing as the technology matures and enterprises learn how to make it work for their needs. If you want to read more the full report is available to download from the RightScale website.
Photo Credit: everything possible / Shutterstock
-

Millions of home routers expose ISPs to DDoS attacks
Publié: avril 2, 2014, 12:09pm CEST par Ian Barker
DNS software specialist Nominum has revealed that DNS-based DDoS amplification attacks have significantly increased in the recent months, targeting vulnerable home routers worldwide.
The research reveals that more than 24 million home routers have open DNS proxies which potentially expose ISPs to DNS-based DDoS attacks.
In February of this year more than 5 million of these routers were used to generate attack traffic. DNS is the most popular protocol for launching amplification attacks and during an attack in January more than 70 percent of total DNS traffic on one provider’s network was associated with amplification.
The attraction for the attacker is that DNS amplification requires little skill or effort but can cause major damage. Using home routers helps mask the attack target making it harder for ISPs to trace the ultimate recipient of the waves of amplified traffic. The amount of amplified traffic can amount to trillions of bytes every day, disrupting networks, websites and individuals and leading to additional costs.
"Existing in-place DDoS defenses do not work against today’s amplification attacks, which can be launched by any criminal who wants to achieve maximum damage with minimum effort," says Sanjay Kapoor, CMO and SVP of Strategy at Nominum. "Even if ISPs employ best practices to protect their networks, they can still become victims, thanks to the inherent vulnerability in open DNS proxies".
To address the gap in defenses Nominum has launched its Vantio ThreatAvert product to enable ISPs to neutralize attack traffic.
Kapoor says, "ISPs today need more effective protections built-in to DNS servers. Modern DNS servers can precisely target attack traffic without impacting any legitimate DNS traffic. ThreatAvert combined with 'best in class' GIX portfolio overcomes gaps in DDoS defenses, enabling ISPs to constantly adapt as attackers change their exploits, and precision policies surgically remove malicious traffic".
More information about amplification attacks and Nominum's solution can be found on the company's website.
Image Credit: Georgii Shipin / Shutterstock
-

Pay up or... We'll let you go. Flawed ransomware leaves behind its key
Publié: avril 1, 2014, 5:34pm CEST par Ian Barker
Locking up a user's PC and demanding a payment to release it has proved very profitable for the cyber crime community.
So much so that malware authors have been turning their hand to new variants. Security software specialist Symantec has been taking a closer look at one such, the CryptoDefense trojan that it first detected in February.
Symantec estimates that CryptoDefense has earned its creators some $34,000 in its first month and describes it on its official blog as, "...a sophisticated hybrid design incorporating a number of effective techniques previously used by other ransomcrypt malware authors to extort money from victims".
CryptoDefense locks up user's data with a 2048-bit RSA key. The private key needed to decrypt the content is then sent back to the attacker's server until the ransom is paid. However, the program's developers seem to have overlooked the fact that the key is also left in a file folder on the victim's machine. Symantec says, "...the malware author's poor implementation of the cryptographic functionality has left their hostages with the key to their own escape". It’s rather like the jailer leaving the key to your cell on a hook just next to the bars.
The malware is being distributed in spammed emails as an attached zip file. Symantec says it has blocked over 11,000 CryptoDefense infections in more than 100 countries since its discovery, the majority in the US.
It is of course unlikely that if you'd fallen victim to this infection you'd have the technical ability needed to take advantage of the flaw to disable it. Still, it's nice to know that sometimes the malware writers make mistakes.
Image Credit: albund / Shutterstock
-

Internet Explorer leads the way in guarding against social engineering attacks
Publié: avril 1, 2014, 3:53pm CEST par Ian Barker
 Deceiving the user into downloading and installing malicious software is one of the most common ways of attacking endpoint systems.
Deceiving the user into downloading and installing malicious software is one of the most common ways of attacking endpoint systems.A good web browser can be an effective aid in blocking these social engineering attempts and the latest research from NSS Labs looks at the leading contenders plus three browsers from China to see how good they are at keeping you safe.
The eight browsers on trial are: Apple Safari, Google Chrome, Kingsoft Liebao, Microsoft Internet Explorer, Mozilla Firefox, Opera, Qihoo 360 Safe Browser, and Sogou Explorer. NSS tested their ability to block socially engineered malware based on over 650 samples captured over 14 days in the company's live testing.
The clear winner is Microsoft's Internet Explorer which successfully blocked 99.9 percent of the malware included in the test. Both it and Chrome -- which blocked 70.7 percent -- use a combination of URL filtering and application reputation technology to provide content agnostic malware protection (CAMP).
Splitting the two is the Chinese Liebao Browser which, despite its lack of CAMP technology, managed to block 85.1 percent of the test samples. Liebao pulls off this trick by using the same cloud-based file scanner as Kingsoft Antivirus. Another Chinese browser, Sogou Explorer, comes fourth on 60.1 percent.
Thereafter it's a fairly sorry tale, with Opera on a 28.8 percent block rate followed by 360 Safe Browser on 6.3, Firefox on 4.2 and Safari on just 4.1 percent.
"Selecting a browser with robust socially engineered malware protection is one of the most critical choices consumers and enterprises can make to protect themselves. Microsoft’s SmartScreen Application Reputation technology continues to provide Internet Explorer the most effective protection against socially engineered malware," says Randy Abrams, Research Director at NSS Labs. "This year NSS added three browsers from China. The Kingsoft Liebao browser displaced Chrome from second place by using a combination of URL filtering with the cloud-based file scanning technology that Kingsoft uses for their antivirus product. Sogou Explorer, another browser from China, was the only other tested browser to exceed 50 percent protection against socially engineered malware. Firefox and Safari failed to achieve 5 percent effectiveness and leave less technical users at considerable risk".
So, what have we learned from all this? It seems that if you want to stay safe from socially engineered malware you need to use Internet Explorer, or maybe move to China. NSS recommends that for maximum protection users should learn to identify SEM attacks and exercise caution in clicking and sharing links.
The full report is available to download on the NSS Labs website.
Photo Credit: Lasse Kristensen/Shutterstock
-

Small companies and big data [Q&A]
Publié: avril 1, 2014, 1:52pm CEST par Ian Barker
 It's sometimes said that big data is like teenage sex, everyone talks about it but few are actually doing it. To which you could add that those who are doing it aren't really sure if they’re getting it right.
It's sometimes said that big data is like teenage sex, everyone talks about it but few are actually doing it. To which you could add that those who are doing it aren't really sure if they’re getting it right.In an effort to find out how big data is being used in the real world, we spoke to the heads of three startup companies which are employing it in unique ways to pursue specific business opportunities.
Qbox
BN: Introduce yourself and your company.
MB: I am Mark Brandon, CEO and Co-Founder of StackSearch, the proprietors of the Qbox.io Hosted Elasticsearch platform. We help customers store, process, analyze, search, filter, and otherwise make meaning of their large data sets. I am passionate about data and IT because more often than not, it is felicity with data that has separated the winners from the losers over the last 30-40 years. I love helping customers get the edge, or to catch up. It's an arms race, and it's exciting.
BN: How are the tools you offer different from other options available? What backend sources do your tools have in common?
MB: Qbox provides hosted instances that can be spun up in the cloud over a dozen data centers across the globe, whereas our competitors usually offer 1-3. We have 4 officially trained Elasticsearch developers on staff, and of course, like to think our support is better too. Though I won’t badmouth our competitors here since I have never provisioned an instance from them. Technologically, Qbox does not have a "noisy neighbor" problem brought about by a container-based deployment. Elasticsearch is a technology where a bulk indexing can completely hoover up available RAM and even if you spin up resources immediately, there will be a lag of a few minutes where your customers will have an awful experience. We learned this the hard way. The container-based deployments are in a shared environment. Our resources are dedicated.
We use NGINX web server. Our site was built in Ruby on Rails with Bootstrap. The provisioning library and deployment scripts are a combination of chef, vagrant, and some from-scratch code. When we build front-end experiences for clients, and with our demos, we will often use AngularJS.
BN: What's the most unique application of your services you've come across so far?
MB: We liked a StackOverflow application that was built a little while back. We bought it and put it up on our site as a demo. The application processes in real time over 17 million tags on StackOverflow, allowing users to see trends on particular topics. For example, you should put the tag "elasticsearch" in the search box, see the trends, see the popular questions, the top answerers, and the top questioners. Then, compare Elasticsearch to the incumbent technology "Solr" that it is quickly eclipsing (the pun is fully intended).
BN: Is big data a good catch-all for what you're actually working in? What are some myths/misconceptions that you’d like to see clarified?
MB: What Mongolab is for MongoDB, Cloudant is for CouchDB, RedisToGo is for Redis, we are to Elasticsearch -- providing managed and hosted instances of the popular open source data exploration and analytics platform. We are working in big data. Elasticsearch is a technology for users whose data set and processing needs require more than 1 server (a "cluster").
MineWhat
BN: Introduce yourself and your company.
JG: I'm Janakram Ganesan, CEO and Co-Founder of MineWhat. I am a dreamer. A few years back, the grind, the routine, the same old work, food and sleep cycle finally got to me. I decided I wanted to make a difference in people's life so I chose entrepreneurship. My interest in data came about during the eCommerce boom around 2010. Focusing on ecommerce, MineWhat uses big data analytics to turn visitors into customers. The company offers an easy to navigate solution for ecommerce operators so that they can get precise information about their visitors. Gathering information like what products sell best in different regions and even how a competitor is doing, it offers actionable predictions that can be used to increase overall sales.
BN: How are the tools you offer different from other options available? What backend sources do your tools have in common?
JG: As far as backend sources go, our data collection method is quite similar to most other current analytical tools. We collect data with an asynchronous JavaScript tag, customers insert this tag into their web page code and the tag then sends data to our servers. For data processing our multi-tenanted architecture stores each customer's data on Cassandra and MongoDB clusters independently. Currently our servers are hosted in AWS, but we've been considering installing location specific data servers in the EU/APAC regions so we can reduce the response time for our collection scripts.
Our system is built so that most actions on the user end are automated. Most analytical tools require the users to write extra code to track any events. An example of this would be if you were to track an in-page dynamic element. On most tools today, you would have to write custom code for that. On MineWhat, this is bypassed. The major differences lie in what we do with the data next. Other tools help with finding out what happened, we help with understanding why.
Say I run an online store and I have to make a decision on how to spread my marketing budget across a few ad platforms (FB, Google, twitter). What web analytics will give me is how much revenue each of these generate. While I can make a decision based on that alone, the decision would be quite uninformed because I don’t know the "why" of it all -- did the Facebook shoppers see something that didn't appeal to their casual intentions?. I also don’t know what I need to do next -- which products should I display to FB shoppers?
That’s where we fit in.
BN: What's the most unique application of your services you've come across so far?
JG: Oddly enough, we hear our collaboration feature has helped set up a few dinner dates. One thing we quite hoped for, but weren't sure would happen, was to see the product being used by more than just analysts. We’ve been seeing category managers and the like creating their own custom dashboards to stay on top of their tasks.
BN: Is big data a good catch-all for what you’re actually working in? What are some myths/misconceptions that you'd like to see clarified?
JG: Mining big data is like a never ending search for hidden gold, and that's all it usually ends up being without a good way to interpret what you find. An ecommerce domain will need to take a very different approach than a finance one to get any real value from big data. We've found that vertically focused analysis is the key to derive insights out of huge volumes of data.
Info Assembly
BN: Introduce yourself and your company.
AG: I am Aditya Goel, Co-Founder of Info Assembly, an intended data discovery platform focusing on market and investment research. InfoAssembly takes both structured and unstructured data to give investors better insights on emerging market trends. An investment researcher would traditionally have to spend valuable time making sense out of mountains of unstructured information like government filings, media reports, blogs and social data. With InfoAssembly they can easily filter out unreliable information and quickly graph trends to determine the best investment opportunities.
BN: How are the tools you offer different from other options available? What backend sources do your tools have in common?
AG: Info Assembly offers a context aware visual search and analysis platform with an intuitive interactive visualization that quickly connects and identifies people, organizations, locations and high level themes and topics in thousands of documents. We aim to speed up the research process through the right mix of machine learning and user interaction experiences so that the end user can get an overview quickly and dig deeper in an interactive manner.
We use D3.JS, one of the most robust and flexible rich JavaScript based frameworks for visualizations. Our backend is run on Stanford NLP and other open source machine learning framework in Java and Python. Our Server side application in Node.JS ties up well with Angular.JS as our front end framework. Also we use Elastic Search for free text search
BN: What's the most unique application of your services you've come across so far?
AG: The most unique application of Info Assembly is how an investment analyst was able to quickly come up with over 50 investment ideas by just pushing in over 40,000 news articles on the global macroeconomics and consumer packaging goods sector. We're working to make the experience much smoother and so we can validate these ideas a lot faster.
BN: Is big data a good catch-all for what you’re actually working in? What are some myths/misconceptions that you'd like to see clarified?
AG: The biggest misconception is that you can plug in lots of information and big data just happens like magic. The most important step in any big data/machine learning application is to get clean data input in the right format. The primary effort and a lot of success depends on pre-processing. Remember that a smaller amount of data with better quality is always better than "just more data". A really good data scientist is one who knows how to pre-process the data first.
Image credit: David Gaylor /Shutterstock
-

One in two think expressing opinions online is unsafe
Publié: avril 1, 2014, 11:27am CEST par Ian Barker
 In the post-Snowden world it's hardly surprising that many people believe that their every online move is being watched.
In the post-Snowden world it's hardly surprising that many people believe that their every online move is being watched.A new global poll carried out by GlobeScan on behalf of the BBC World Service reveals just how widespread these feelings are. Having polled over 17,000 people across 17 countries it finds that 52 percent believe the internet is an unsafe place to express opinions.
However, while one in two are wary of expressing opinion, 67 percent say the internet brings them greater freedom. Government surveillance is a major worry though with 36 percent saying they don't feel free from it.
Broken down by country 54 percent of Americans and 51 percent of Germans say they don't feel free of government surveillance. This contrasts sharply with China where 76 percent say they feel free of surveillance. Majorities in Russia (61 percent) and Indonesia (69 percent) also say they feel free of government snooping.
The poll also looked at media freedom, finding that the number of people who believe that their country's media was, "free to report the news accurately, truthfully and without undue bias" has dropped by around a third over the last seven years. In the US and UK a minority of respondents now believe their media is free compared to a majority in 2007.
"The poll suggests that two of the underpinnings of modern democracies are at risk -- a media seen as free and fair; and an internet safe for the free expression of views." says GlobeScan Chairman, Doug Miller. "The results also suggest that many of the personal freedoms that Western democracies have championed in the world are actually fairly well established in the minds of citizens across these particular 17 countries. Ironically, it is in some of these very democracies where citizens give relatively poor ratings of some freedoms".
Polling was carried out face-to-face or by phone between December 2013 and February 2014 in the following countries: Australia, Canada, China, France, Germany, India, Indonesia, Kenya, Mexico, Nigeria, Pakistan, Peru, Russia, South Korea, Spain, the UK, and the USA. The results have been released as part of the BBC's Freedom 2014 event which looks at what freedom means in the modern world.
If you feel safe to express your views on these results the comments thread below is available for your use.
Image Credit: Andrea Danti / Shutterstock
-

Backupify expands cloud support
Publié: mars 31, 2014, 3:06pm CEST par Ian Barker

Moving data to the cloud and running software as a service can make businesses complacent about backup as they feel their data is already safe with their provider.
However, a recent report by Forrester warns that organizations relying on cloud services may be at risk, "SaaS is an increasingly popular method of deploying new services, but many organizations don't realize that they could be at risk of losing critical data. Many SaaS providers will not restore lost data for users or will only do so for an exorbitant fee".
Leading backup provider Backupify already supports Google Apps, Salesforce.com, PipelineDeals, and Smartsheet. It's using World Backup Day to announce that in 2014 it's set to add 13 other cloud services to its platform by the year end. Slated for release this year are cloud-to-cloud backup solutions for Box, Dropbox, Netsuite, GitHub, Zendesk, Concur, ServiceNow, JIRA, Workday, Asana, Egnyte, Office 365 and Basecamp.
The company also has a set of open APIs allowing developers to create backups for other cloud applications quickly and easily.
"We know companies are rapidly moving to the cloud and migrating critical company information into cloud applications," says Rob May, CEO of Backupify. "With that exponential growth, customers are increasingly thinking less in terms of any one single application -- they want a 'single pane of glass' in order to more efficiently and effectively protect all their data across a growing number of different applications. We’re responding to our customer’s needs by taking a more integrated approach to managing their data".
Backupify will allow companies to log in to a single platform to backup and manage the data they store across multiple SaaS applications.
You can get more information, sign up for a free trial and download the full Forrester report on the Backupify website.
Image Credit: Lightspring / Shutterstock
-

UK set to make ripping your CDs and DVDs legal
Publié: mars 28, 2014, 3:55pm CET par Ian Barker
Although you weren't ever likely to be the subject of a dawn raid from the Sweeney for doing it, until now it has been illegal under UK copyright law to make copies of digital media.
From this summer though the government is changing the current legislation so that you'll be able to transfer music to your MP3 player or make backup copies of your movies without any risk of getting your collar felt.
In a guidance document for consumers released yesterday the Intellectual Property Office says, "Copyright law is being changed to allow you to make personal copies of media (CDs, ebooks etc) you have bought, for private purposes such as format shifting or backup". It goes on, "You will be permitted to make personal copies to any device that you own, or a personal online storage medium, such as a private cloud. However, it will be illegal to give other people access to the copies you have made, including, for example, by allowing a friend to access your personal cloud storage".
The government doesn't expect copyright holders to suffer significant harm from these changes, though they could generate extra revenue for technology companies such as those offering cloud storage.
At the same time new rules on "fair dealing" are being introduced to allow quotations and extracts to be used more widely. Currently quoting without permission is only allowed for criticism, review or news reporting. These provisions will also make it easier to use material for parody or pastiche without needing to gain permission from the rights holder.
The changes will come into force in June, so you still have a couple of months to enjoy the frisson that comes with an illegal rip.
Image Credit: Marcos Mesa Sam Wordley / Shutterstock
-

Maintaining IT security is getting harder -- and it's your fault
Publié: mars 28, 2014, 11:33am CET par Ian Barker
Keeping systems secure is more difficult than it was a year ago and this is partly down to human error. So says a new study by security awareness company KnowBe4.
The rise of ransomware, the adoption of BYOD, and rapid changes in technology all make it harder for enterprises to guard against threats both inside and outside the organization.
The study, carried out among IT managers, finds that 51 percent of respondents are finding security harder to maintain now than a year ago while 40 percent find it's about the same. Less than 10 percent say are finding it easier.
Many of the risks come from human error. BYOD in particular is more difficult for IT managers to monitor and secure. User smartphones, tablets and laptops can create potential for undetected entry to a corporate network. "The human factor is a leading source of security threats for today’s IT Manager," says Stu Sjouwerman, CEO and Founder of KnowBe4. He advises, "To maintain security, every company should adopt the 'defense-in-depth' strategy and create a strong first layer that includes up-to-date security policies, procedures and security awareness training as this affects every aspect of an organization's security profile".
In the government sector, insider threats are seen as nearly as great a problem as external ones. In the survey 53 percent of defense IT pros named careless and untrained insiders as their top security threat. KnowBe4's study shows 60 percent of IT Managers are looking to Security Awareness Training to help solve security issues in addition to using it to support compliance.
Sjouwerman stresses how important it is to educate employees to recognize potential network security threats, "Cybercriminals are constantly devising cunning new ways to trick users into clicking their phishing links or opening infected attachments".
KnowBe4 offers a free test for companies to see what percentage of their employees are susceptible to phishing attacks.
Image Credit: Robert Kneschke / Shutterstock
-

DDoS traffic soars and the bots get cleverer
Publié: mars 27, 2014, 4:14pm CET par Ian Barker

New research by website security specialist Incapsula looks at the impact of DDoS traffic on the internet with data collected over a five month period looking at over 154 million DDoS bot sessions.
It reveals some startling statistics, the main one being that at the application level DDoS bot traffic is up by 240 percent. More than 25 percent of all botnets are located in India, China and Iran, whilst the US ranks fifth in the top ten attacking countries.
The attack landscape is interesting too. 29.9 percent of DDoS bots can execute JavaScript and 40 percent of botnets attack more than 50 targets per month.
At network level, large scale SYN floods account for over half (51.5 percent) of all attacks and almost 81 percent of attacks are multi-vector threats.
The results show a shift towards so called "hit and run" attacks, relying on short bursts of traffic at frequent intervals, designed to exploit vulnerabilities in protection systems. The growth in multi-vector attacks is also being used to create "smokescreens" where one attack creates noise to divert attention away from the main vector. The first part of 2014 has also shown a rise in NTP (Network Time Protocol) amplification attacks which in February became the most commonly used method of large scale DDoS attack.
Whilst the volume of attacks is increasing, DDoS bots are becoming more sophisticated too. In the fourth quarter of 2013, Incapsula reported the first encounter with browser-based DDoS bots that were able to bypass both JavaScript and Cookie challenges -- the two most common methods of filtering bots. This trend has continued into 2014 with 30 percent of the encountered bots able to accept and store cookies.
In order to infiltrate systems bots are using spoofed user-agents. These help to bypass low-level filtering solutions, based on the assumption that bots which identify themselves as search engines or browsers won't be screened out.
You can read more and download the full report on the Incapsula blog or see an overview of the findings in the infographic below.
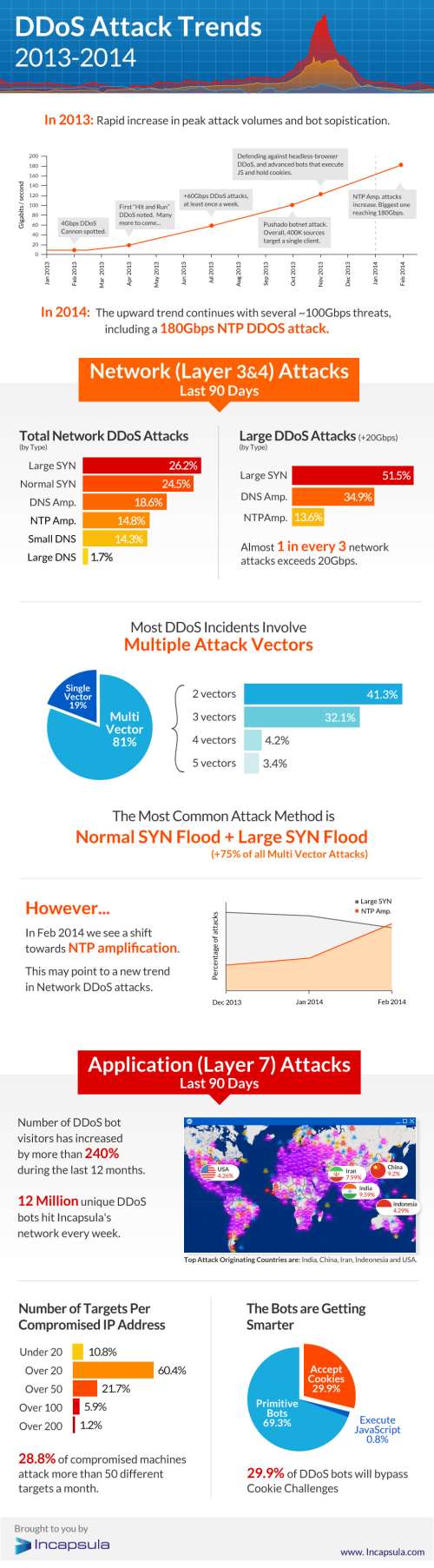
Photo Credit: Duc Dao / Shutterstock
-

Trusted content is the key to consumer purchasing decisions
Publié: mars 26, 2014, 4:45pm CET par Ian Barker
The internet and social media mean that there is more information available to consumers than ever before. But which opinions do we actually trust?
A new study from Nielsen commissioned by content specialist inPowered seeks to understand how consumers use digital content when it comes to researching and making purchases.
The findings show that consumers place great store by the credibility and unbiased nature of content. 85 percent say they regularly or occasionally seek out trusted expert content, such as third-party articles and reviews, when considering a purchase. Some 69 percent of consumers like to read product reviews written by trusted experts before making a purchase and 67 percent agree that an endorsement from an unbiased expert makes them more likely to consider buying.
"With so many companies spending so much money on content marketing, we wanted to clarify what kind of content is actually impacting consumers and helping them make their decisions," says Peyman Nilforoush, co-founder and CEO of inPowered. "This isn't about disproving any particular type of content, it’s about identifying the most effective blend of content types to help effectively educate and inform consumers".
In research carried out with 900 consumers and with nine products across different categories, expert content was found to be more effective than branded content or user content (like Amazon reviews) at all stages of the purchase cycle. In particular it was shown to lift purchase intent 38 percent more than branded content and 83 percent more than user reviews.
"It became clear throughout the study that, while exposure to each type of content did provide a lift across different categories, credible content from experts was the only content type that performed consistently across all stages of the purchase process," says Tommy Cheng, VP, Innovation Solutions at Nielsen.
Based on the findings inPowered concludes that companies need to use content from reliable third-party experts as the basis of building trust with the consumer. Once this is established branded content can be used to spread the word and the message can be reinforced by encouraging consumers to leave their own reviews.
Nilforoush concludes, "...by beginning with a solid foundation of trust built on trusted content from credible, third-party experts, all other content will have a greater impact".
To find out more you can download the full report as a PDF from the inPowered website.
Image Credit: donskarpo / Shutterstock
-

K2 makes SharePoint development easier
Publié: mars 26, 2014, 3:42pm CET par Ian Barker
Microsoft's SharePoint, just in case you aren't familiar with it, is a set of web technologies with an Office-like interface that's designed to allow non-technical staff to build business apps.
SharePoint is typically employed to provide internet and intranet sites as well as enterprise document and content management. Now business application specialist K2 is aiming to help SharePoint users build better applications without the need for any coding.
The release of K2 for SharePoint lets enterprises build and use applications using forms, workflow data and reports. Key features include the ability to create workflows that span lists and libraries on different SharePoint sites and across different versions, both on-site and in the cloud. In addition customized forms and workflows can be created to integrate existing business data. Users can build web and mobile apps that use SharePoint data but run independently of the environment. Also components like forms and workflows can be built once and shared across applications both in and out of SharePoint.
"It is now easy to deliver powerful workflow and forms-driven apps on SharePoint," says Adriaan van Wyk, CEO and co-founder of K2. "Our customers now have the ability to create scalable and secure no-code apps that span on-premises, cloud and hybrid SharePoint environments, without sacrificing capability or control. It is an exciting time".
Most development platforms tie users to a specific structure and outline within their fabric. Using K2 for SharePoint, enterprises can build completely tailored, fully-functional applications and web-based forms to look and feel just like SharePoint -- or have a completely unique approach.
For more information on K2 for SharePoint, a full list of features and a look at what it can do with an online demo visit the K2 website.
Image Credit: Rafal Olechowski / Shutterstock
-

Why the use of personal data for authentication needs to change
Publié: mars 26, 2014, 12:23pm CET par Ian Barker
We run more and more of our lives online today, with multiple accounts for different services. But many of those sites rely on the same few personal identifiers.
Things like your date of birth, social security number and mother’s maiden name may be common to many of your logins, and that’s a problem. If one site's security is breached then your personal identifiers are compromised.
A new report by NSS Labs looks at the fact that half of the ten biggest breaches of the past decade occurred in 2013. These have exposed 512 million records and repeatedly compromised the personally identifiable information (PII) of around 319 million Americans.
The report's authors, Research Director Stefan Frei and Chief Research Officer Bob Walder, say in their introduction, "Enterprises that conduct any part of their business online should be prepared to bear full responsibility for the consequences of data breaches. At present, that responsibility is typically limited to a financial burden, whereas the true consequences of modern breaches are more far reaching than that implies. The loss of what is known as 'unique' or 'static' personal data, that which is truly personal (such as DOB or SSN), is far more serious than the loss of 'transient' personal data (such as pass codes, security questions, and credit card numbers) that is more easily changed following a security event or that is readily discernible in the public domain".
While individuals bear responsibility for the information they put in the public domain, on social networking sites for example, they often can't avoid entering unique personal data to log in to some websites.
The report notes that, in the US, social security numbers are regularly "squandered" in the name of authentication whereas in the UK National Insurance numbers are never used in this way. Indeed in Europe in general digital IDs are becoming more common.
Loss of authentication data threatens to erode confidence in ecommerce and adds to a serious risk of identity theft. To combat the problem enterprises need to recognize the need to hold as little unique personal information as possible. They also need to look at new ways to authenticate, such as permitting users to set their own challenge questions, allowing the use of long passwords without character restrictions, and offering geo-location or other controls on accounts.
NSS also suggests that online services should be designed with data breaches in mind so as to minimize risk and allow companies to act fast to protect their users if necessary. Data that is stored should be anonymized and disassociated with the user where possible, as well as stored in encrypted form.
Data breaches aren't just a problem for the companies that suffer them, but for all of us too, and authentication systems need to change to make everyone more secure.
The full report is available as a PDF from the NSS website.
Image Credit: mama_mia / Shutterstock
-

Cloud prices continue to fall
Publié: mars 24, 2014, 5:14pm CET par Ian Barker
It's true of most technologies that as their popularity increases so prices begin to come down. The cloud is no exception to this as a new report from cloud portfolio management specialist RightScale shows.
Having analyzed price reductions from the four leading public cloud providers -- AWS, Rackspace, Google Compute Engine, and Azure -- in 2013, the report finds the pace of price reduction accelerating
Several trends are evident within this, Amazon continues to lead the way in terms of the size of price drops, forcing other providers to follow suit in order to compete. AWS announced 12 price drops in 2013, down from 13 the previous year. Azure, Google, and Rackspace all stepped up their pace, accounting for a combined 13 reductions in 2013, up from 9 in 2012.
It's important to note though that price drops aren't always across the board, they may target particular services or markets. There were twice as many reductions in the price of compute services in 2013 for example, good news for enterprises which tend to spend 70 to 90 percent of their cloud budget in this area.
Storage prices saw fewer reductions, six last year down from eight in 2012, but the average size of decrease in storage costs was larger, 32 percent as opposed to 20 percent.
As prices drop the cloud becomes a more attractive option and companies are growing their cloud usage. IDC reported in December 2013 that, "Cloud spending, including cloud services and the technology to enable these services, will surge by 25 percent in 2014, reaching over $100B". This means that although prices are falling cloud is accounting for a larger proportion of IT budgets, increasing the pressure to adopt processes and tools to optimize costs.
You can read more about the findings on the RightScale blog.
Image Credit: alexmillos / Shutterstock
-

Malwarebytes commits to lifetime support for XP users
Publié: mars 24, 2014, 10:48am CET par Ian Barker
The antivirus industry is getting steamed up about the forthcoming end of XP support. Last week we saw Avast warning of the vulnerabilities users might face.
Today anti-virus specialist Malwarebytes announces its new Anti-Malware Premium product and at the same time is pledging that it will continue to support XP users for life.
The company says that XP users currently make up 20 percent of its user base and could be at greater risk after 8 April when support for the old operating system ends.
The new Premium product has a streamlined dashboard interface that makes it easy to see the protection status of the PC along with a heuristics engine designed to detect and eliminate malicious software based on its behavior. It also has anti-rootkit technology and adds malicious URL blocking and protection from potentially unwanted programs. As before Malwarebytes will run alongside traditional security software to provide an additional layer of protection. A Chameleon mode allows Malwarebytes to open even if the system has an infection that tries to close down security software.
The company hopes that continuing support for XP will boost its presence in the business market. Marcin Kleczynski, Founder and CEO of Malwarebytes says, "Corporate users can't just upgrade, they may have legacy software running on XP and don't what to spend millions on updating".
The new program doesn't replace the free Malwarebytes cleanup tool which has been downloaded more than 200 million times and will continue to be offered. Anti-Malware Premium will be available later today, existing users with lifetime licenses for Malwarebytes Anti-Malware PRO will get a free upgrade to the new version.
Kleczynski concludes, "We are proud of what we have created and believe it builds upon the success of our existing products to give people a strong proactive countermeasure against today’s advanced online threats".
-

Linking Outlook and Yahoo Mail to Evernote and Dropbox
Publié: mars 20, 2014, 6:16pm CET par Ian Barker
For many people webmail has become their main method of handling email, whilst corporates cling to a client model. Integrating with cloud services can be a chore in either case.
Powerbot is a clever browser extension that connects Gmail and Google Calendar to Evernote and Dropbox making it easy to share data between them. It's now extended its functionality to Yahoo Mail and the Outlook client.
Powerbot buttons are added to the mail interface allowing users to, for example, send email threads to Evernote, import notes into outgoing email and so on. All of your Evernote and Dropbox notes and files are available in one interface for sending and receiving emails.
The addition of an Outlook version is significant thanks to its popularity in the enterprise, and Powerbot's Outlook version works as a download rather than a browser extension. Powerbot gives users buttons for adding mail messages, threads, and attachments to or from Evernote notebooks or Dropbox folders without leaving the email.
The Outlook version is currently available free whilst it's in beta. The Yahoo Mail and Gmail extensions offer a 30-day free trial and are then priced at $2 per month or $15 per year.
"Despite Gmail's huge popularity, we still see that old habits die hard (especially in larger organizations), where Microsoft Outlook is still the standard," says Dmitry Gorshkov, Head of Product for Powerbot. "By shipping Powerbot for Outlook, we hope to both bring millions of people a more enjoyable, integrated experience and help Evernote get even more adoption within the enterprise market. We are big believers in Evernote and think this is a natural extension of the Powerbot technology".
You can find out more and download a trial on the Powerbot website.
-

Elasticsearch makes log analysis faster and simpler
Publié: mars 20, 2014, 5:05pm CET par Ian Barker

The data contained in logs can be useful for a variety of purposes, but analysing it in order to extract what you need can be difficult and time consuming.
Search analytics specialist Elasticsearch is aiming to make log data more accessible with the release of Logstash 1.4.
Log data can be any information that carries a time stamp so it can be used to provide insights into purchasing habits, support systems and more, which means it can help businesses understand the customer experience.
The latest version of Logstash is claimed to start up to three times faster and as part of the company's ELK stack product (combining Elasticsearch, Logstash and the Kibana visualization tool) allows businesses to extract useful data from logs quickly and benefit from the insights it can provide.
New features include a streamlined installation process to get the product up and running more quickly. A simplified plug in system to allow Logstash to be customized for specific business needs. Puppet modules that automatically configure the product, whether it's on a server or a virtual machine, and all new documentation.
"Logstash can get data from unknown places and from any source and will clean it up so you don’t have to worry about the exact log types or reconciling different data formats," says Jordan Sissel, software engineer and Logstash creator. "We handle it all and let you slice and dice that data with Elasticsearch. Serve it up nice and pretty with a side of Kibana and you’ve got instant feedback on how to better please your customers and drive business success".
Logstash 1.4 is available now on the Elasticsearch site and from GitHub under an open source license.
Image Credit: alphaspirit / Shutterstock
-

Intel aims to reinvent the desktop
Publié: mars 20, 2014, 10:58am CET par Ian Barker
We're used to reading reports that the PC is dying, but chip maker Intel has used the Game Developers Conference in San Francisco to reveal a roadmap for the reinvention of the desktop.
Intel sees enthusiast users as some of the most important supporters of desktop computing, and new form factors including mini PCs and all-in-ones driving renewed interest in the sector.
"The desktop business is a large and important segment for Intel, and we are investing in it -- reinventing form factors, experiences and products for our customers," says Lisa Graff, vice president and general manager at Intel's Desktop Client Platform Group. "Enthusiasts are the heart and soul of the desktop and they asked us to give them more. We are delivering -- more cores, better overclocking, faster speeds".
Intel unveiled a fourth-generation Core processor code named "Devil's Canyon" for release in mid 2014. It will feature an improved thermal interface and materials that are expected to enable significant enhancements to performance and overclocking capabilities. In the second half of the year the company will also deliver an 8-core, 16-thread Core processor Extreme Edition. This will support the new DDR4 memory standard and provide improved performance for gaming, video editing, 3-D content and other high-end uses.
It also announced plans for a Pentium Anniversary Edition commemorating more than 20 years of the Pentium brand. This will feature unlocked multipliers that allow the ability to increase the core and memory frequencies independently from the rest of the system.
As well as new processors Intel demonstrated a reference design for a portable all-in-one PC code named "Black Brook" a thin, light system incorporating a 3D camera, quad microphone array, premium audio and a full HD display. It can be used upright or laid flat to become a sort of poor man's Surface. See the video below for a preview of how it works.
To enhance the appeal of AIOs Intel has partnered with several software developers to deliver multi-user, multi-touch applications like board games and educational titles to make the most of the size and touch capabilities.
Finally it showcased its Ready Mode technology which will be coming to OEM PCs in 2014. This a power saving system that allows PCs to instantly ready and connected whilst using minimal amounts of electricity.
Do you think all this is enough to rescue the desktop’s slide into history? Let us know via the comments.
-

Malware in pirated software costs billions
Publié: mars 19, 2014, 11:26am CET par Ian Barker
 Enterprises worldwide are expected to spend $500 billion in 2014 to deal with issues caused by malware in pirated software. Consumers are set to spend $25 billion and waste 1.2 billion hours on security threats and fixes.
Enterprises worldwide are expected to spend $500 billion in 2014 to deal with issues caused by malware in pirated software. Consumers are set to spend $25 billion and waste 1.2 billion hours on security threats and fixes.These are among the conclusions of a study carried out by IDC and the National University of Singapore, released today by Microsoft’s Digital Crimes Unit as part of its annual Play It Safe campaign.
Forensic analysis carried out on 203 new PCs that came with pirated software on them found that 61 percent were pre-infected with malware, including trojans, worms, viruses, hacktools, rootkits and adware. These machines bought through resellers and PC shops in 11 markets, included more than 100 separate threats.
Writing on the company's blog David Finn, Associate General Counsel & Executive Director of Microsoft Cybercrime Center says, "While these statistics are frightening, they shouldn't be a surprise. After all, cybercriminals aim to profit from any security lapse they can find. And through pirated software, they've found another way to introduce malware into computer networks -- breaking in so they can grab whatever they want: your identity, your passwords and your money."
When asked to rate their biggest security-related fears 60 percent of consumers put loss of data or personal information at the top followed by unauthorized internet transactions for 51 percent and hijacking of email, social networking and bank accounts for 50 percent. Yet despite these fears 43 percent admitted not installing security updates, making them vulnerable to attack.
Enterprises are especially hard hit by malware in pirated software. In 2014 it's estimated that businesses will spend $127 billion dealing with security issues and $364 billion dealing with data breaches. Almost two-thirds of these losses, around $315 billion, will be the result of organized crime -- malware launched by financially motivated criminals.
Finn concludes, "The results of this study demonstrate, once again, how vital it is that individuals, small businesses, enterprises and government institutions buy new computers from reputable sources and demand genuine software. Because if you don't, you never know what will come along for the ride".
The full results of the study are available as a PDF from the Microsoft website.
-

Software audits are not as scary as you think
Publié: mars 18, 2014, 11:55am CET par Ian Barker
Lack of compliance with software licenses can cost businesses a lot of money, not to mention the negative effects of being caught out on an audit.
A new report from asset management specialists Express Metrix looks at the impact and outcome of software audits, uncovers some interesting facts, and busts some myths.
Based on interviews with 178 respondents in organizations of varying sizes, it found that 53 percent reported their workplace had been subject to a software audit in the last two years. The vendors most likely to have carried out audits are Microsoft, Adobe, AutoDesk and Oracle. Though in organizations with more than 10,000 employees IBM overtakes Oracle for fourth place.
What's interesting is organizations that had implemented asset management tools showed a 32 percent lower audit rate. This may be due to software vendors learning over time which companies have the best grasp of their license positions.
The findings of the report also show that the perception surrounding software audits often doesn't tally with the reality. Often companies worry about the audit process, but 57 percent of audited respondents described their relationship with the software vendor as consultative and collaborative, with only 20 percent saying it was "contentious" -- though this figure rises to 40 percent in larger organizations.
It also seems to be a myth that companies have little time to prepare for audits. Nearly half of organizations were given a month or more notice. Audits were also over relatively quickly, only 45 percent lasting three months or more from request to resolution.
The final misconception is that a software audit means you're bound to end up owing money to the vendor. In fact almost half (43 percent) of respondents reported owing no money to their vendors at the end of the audit process.
The report concludes, "...while just over a third of respondents report having being audited in the last year, the software audit risk touted by analysts such as Gartner and widely publicized in the media appears to be significantly overstated. Organizations that have undergone audits appear to have leveraged their experience to further refine their approach to compliance, including changing internal practices, investing in licensing expertise, and increasing the frequency of internal audits".
You can read a full copy of the report on the Express Metrix website.
Photo Credit: Georgejmclittle/Shutterstock
-

HP launches NFC authentication for enterprise printing
Publié: mars 17, 2014, 4:09pm CET par Ian Barker

The increased use of mobile devices in the workplace leads to a number of issues. Not least of which is establishing control over shared resources like printers.
To address this HP has launched its first touch-to-authenticate solution for enterprise customers using NFC enabled smartphones or tablets.
"As mobile device usage in the office continues to grow, many businesses are concerned with security," says Pradeep Jotwani, senior vice president, LaserJet and Enterprise Solutions at HP. "HP continues to focus on the security needs of enterprise customers by delivering LaserJet devices and solutions that break new ground with touch-to-authenticate technology. By simplifying authentication for users, IT managers can better secure printer and MFP fleets without the concern of burdening users with a complicated authentication process".
HP Access Control 14 allows the authentication of user login credentials by touching an NFC capable Android smartphone to the printer. This provides a simplified login process without sacrificing device or data security.
The company has also updated its ePrint Enterprise product to give enhanced connectivity and security features to organizations using mobile device management solutions. HP ePrint Enterprise 3.2 is now fully integrated with MobileIron's AppConnect, one of the leading enterprise mobility management platforms.
At the same time HP is launching a new range of enterprise-ready printers and multi-function devices. The Color LaserJet Enterprise MFP M680 series can reach print speeds of up to 45 pages per minute and delivers advanced paper handling and finishing options. It's designed to increase office productivity by giving users the ability to print, copy, scan, fax and use other functions directly from the printer’s 8-inch color touch screen.
The HP Color LaserJet Enterprise M651 series are single-function printers that complement the M680 series devices. They provide simple wireless printing from smartphones, tablets and other mobile devices including wireless direct options from HP ePrint and AirPrint.
For more information on the latest offerings you can visit the HP website: www.hp.com/go/mfp
-

Can the Internet of Things live up to its hype?
Publié: mars 13, 2014, 5:23pm CET par Ian Barker

The Internet of Things has the potential to offer significant benefits to both businesses and consumers. Realizing those benefits though relies on identifying problems that the IoT can address.
Technology research specialist IDTechEx's event in Berlin at the beginning of April is set to explore the prospects offered by the IoT and look at how it can be used to make a difference in the real world.
At the heart of the IoT of course are devices that in the past wouldn't have needed connectivity. There is potential for this in consumer applications like home automation, driven by governments encouraging the roll-out of smart metering. However, consumer spending on automation devices remains sluggish owing to cost. The energy saving message means that people are comparing the price of devices with the potential saving and often choosing to keep their cash in their pockets.
Raghu Das, CEO of IDTechEx sees this changing as media companies in particular use the IoT to offer improved connectivity and targeted services. This may see a change in the pricing model, with consumers getting devices for free in exchange for seeing advertising or allowing data collection.
In the short term though he believes the IoT will only succeed if it addresses certain challenges. These include focusing on closed-system implementations that deliver a strong payback, then moving on to other areas where a problem can be solved with a cheaper, more effective solution.
Das suggests that existing hardware can be leveraged to perform more useful tasks. Using smartphones to connect to other hardware such as real-time location systems for example, as well as finding ways to connect islands of technology together.
The biggest opportunity according to Das is to, "Offer new services to consumers they do not yet know they want." But he adds that this is, "...challenging to do and involves creative new business models, probably where the service is 'free' but paid for in kind by consumer data".
The IDTechEx Internet of Things & WSN event takes place on April 1-2 in Berlin.
Image Credit: Black Jack / Shutterstock
-

PaaSLane optimizes Java and .Net applications for the cloud
Publié: mars 10, 2014, 2:48pm CET par Ian Barker

We reported on Cloud Technology Partners' migration tool PaaSLane entering its public beta phase back in October and how it can cut the time and cost spent on moving to the cloud.
From tomorrow (March 11) the product becomes generally available with new and enhanced features to enable users to rapidly assess applications and speed up cloud migrations.
PaaSLane 2.0's new features include full .NET support with more than 200 specific rules, including rules for Microsoft Azure and Apprenda CloudFoundry. There’s a redesigned reporting interface including the ability to drill down into alert detail. There are also interactive charts and the ability to export reports in Excel and PDF formats.
"In the past two years the use of public cloud for enterprise workloads has skyrocketed. Many enterprises are looking at what it will take to migrate mission critical applications from expensive datacenters to agile cloud environments, and this is where PaaSLane shines," says Ben Grubin, Director of Product Management at Cloud Technology Partners. "However, the challenges of migrating existing apps to the cloud have led to many failed migrations, delays, or deployment of apps with significant code-level issues. PaaSLane can tackle the assessment of existing Java and .NET apps with ease, quantifying factors such as coding errors, hardcoded dependencies, security, and scalability problems, along with several other factors could quickly derail a cloud project. PaaSLane helps overcome these issues by leveraging source code inspection and a built-in cloud platform knowledgebase driven by extensive research to identify and resolve issues quickly, accelerating application migration and cloud optimization".
Faster uploads to Amazon Web Services are now available thanks to parallel uploading technology. PaaSLane also allows continuous optimization for evolving cloud platforms as it delivers real-time intelligence on changes that effect an application.
Grubin says that the product appeals to larger companies with many applications, system integrators supporting migrations and to smaller companies with just one or two critical apps. It can be integrated into the development lifecycle for any size of organization.
You can sign up for an instant free trial on the PaaSLane website.
Photo Credit: Roland IJdema/Shutterstock
-

Cybercrime industry refines its techniques to steal data
Publié: mars 10, 2014, 12:24pm CET par Ian Barker
Last year saw a number of credit card data breaches that made the headlines. A new report says that this shows how well the "deep web" of cybercrime is serving its customers.
McAfee Labs Threats Report for the fourth quarter of 2013 says that not only did Point of Sale (PoS) attacks like that on Target steal large numbers of records they point to a refinement in criminal technique.
The attackers used point-of-sale malware that's available to buy off-the-shelf in the cybercrime community and made straightforward modifications allowing them to target their attacks. What's more they had an efficient mechanism in place to sell on the stolen data including an anonymous, virtual-currency-based payment system.
"The fourth quarter of 2013 will be remembered as the period when cybercrime became 'real' for more people than ever before," says Vincent Weafer, senior vice president for McAfee Labs. "These cyber thefts occurred at a time when most people were focused on their holiday shopping and when the industry wanted people to feel secure and confident in their purchases. The impact of these attacks will be felt both at the kitchen table as well as the boardroom table”.
Other findings of the report include an increase in the use of malicious signed binaries, the number on McAfee Labs' database having tripled last year. The company says that the misuse of code signing is eroding user trust in the use of security certificates.
The report also explores the relationship between mobile malware and apps that "overcollect" user data and mobile device telemetry. Although most tracking is benign, 82 percent of mobile apps track when you use Wi-Fi and data networks, when you turn on your device or your current and last location. In addition 80 percent of apps collect location information and 57 percent track when the phone is used.
Ransomware continues to be a problem too, McAfee Labs recorded a million new samples, doubling the number between Q4 2012 and Q4 2013. There were also 2.47 million new mobile malware samples in 2013, 2.2 million new master boot record attacks and a 70 percent increase in the number of suspicious URLs.
You can read the full report as a PDF on McAfee's site and in the meantime, let's be careful out there.
Image Credit: zimmytws / Shutterstock
-

Say cheese! -- new Android malware can hijack your camera
Publié: mars 7, 2014, 10:52am CET par Ian Barker
 Remote access toolkits (RATs) for Android are nothing new, but until now they've mostly targeted the Asia region.
Remote access toolkits (RATs) for Android are nothing new, but until now they've mostly targeted the Asia region.Now researchers at mobile security specialist Lookout have uncovered Dendroid, a custom RAT aimed at users in western countries. Dendroid’s author is selling the toolkit online with payment in virtual currencies like Bitcoin and even offers a warranty promise that it will remain undetected.
Writing on the Lookout blog Marc Rogers, Principal Security Researcher at Outlook says, "The toolkit is being sold for $300 to anyone who wants to automate the malware distribution process. The creator promises that the malware can take pictures using the phone's camera, record audio and video, download existing pictures, record calls, send texts, and more".
More worrying still is that Dendroid is designed to evade detection by Bouncer, the malware protection system used by Google on the Play Store. It uses an anti-emulation system to avoid executing any bad code that might trigger the detection system.
Amongst an impressive list of features Dendroid can spy on the user by taking photos or making video and audio recordings, intercept and block SMS messages, download browsing history and saved bookmarks, send texts as the device owner and record outgoing calls.
Rogers concludes, "Thanks to the quick identification and detection of Dendroid by security companies we don't anticipate Dendroid becoming a major threat. However, it does represent a step change upwards in the complexity of all-in-one malware toolkits for Android. Toolkits of this sophistication changed the PC landscape significantly as it lowered the barrier for entry and enabled relatively unskilled malware operators to control substantial botnets with a level of control they would never have been able to reach on their own".
Android users are advised to stay safe by ensuring that the Unknown Sources system setting is turned off in order to prevent drive-by installs and to install a mobile security app.
Image Credit: style-photography.de / Shutterstock
-

Tablet growth forecast slows as markets mature
Publié: mars 6, 2014, 5:41pm CET par Ian Barker

Market intelligence specialist IDC has released the latest results from its quarterly tablet tracker. It predicts that the sales growth of tablets (including 2-in-1 devices) will be 19.4 percent in 2014, down from 51.6 percent last year.
There are a number of reasons for this predicted reduction, partly the number of new releases has slowed, and in mature markets the sales pattern will switch to replacement of older devices rather than first time buys.
IDC also notes that price erosion -- the average selling price of a tablet fell by 14.6 percent in 2013 -- is slowing and it sees only a small drop of 3.6 percent in prices this year. This again is down to increasing maturity in the market as consumers steer away from low-priced budget products.
"After years of strong growth, we expect the white-box tablet market to slow in 2014 as consumers move to higher-end devices that work better and last longer," says IDC's Tom Mainelli, Program Vice President, Devices & Displays. "In mature markets, where many buyers have purchased higher-end products from market leaders, consumers are deciding that their current tablets are good enough for the way they use them. Few are feeling compelled to upgrade the same way they did in years past, and that's having an impact on growth rates".
Commercial shipments are expected to grow as consumer sales fall, due to tablets finding a place in more businesses. IDC expects this to benefit Windows devices. "The choice of operating system will be a key differentiating factor when it comes to success in the commercial segment," says Jitesh Ubrani, Research Analyst, Worldwide Tablet Tracker. "Though Android and iOS will remain dominant, we expect Windows-based devices to capture more than a quarter of the market as its benefits become apparent thanks to growing adoption of 2-in-1s".
It seems that for consumers tablets are treated more like PCs than mobile phones, with people holding onto their kit until it breaks or something significantly better comes along. The fact that they’re more likely to be bought outright rather than acquired on a contract is probably a factor here too.
More information on IDC's tracker research is available on the company's website.
Image Credit: vinzstudio / Shutterstock
-

Enterprise mobile security? Not my problem
Publié: mars 6, 2014, 12:56pm CET par Ian Barker

The increasing trend towards BYOD and mobile devices in the workplace leads to added risks, but employees are often unaware or feel it isn't their problem.
These are among the findings of a survey by security specialist Absolute Software which polled workers in companies with a 1,000 or more employees who use mobiles for work.
When asked about penalties for leaking or losing company data, a quarter of US workers surveyed said there should be no punishment as data security wasn’t their problem. Whilst the remaining 75 percent felt they should face some penalty, many of those who had lost a mobile said their punishment ranged from nothing to getting a talking to or simply having to replace the device.
23 percent of respondents indicated that they didn't know their company's procedure for dealing with theft or loss of a workers device. More than a third of those who had lost their phones indicated that they didn't change their security habits afterwards.
The results also show ignorance of the value of corporate data, with 59 percent of enterprise mobile users estimating the value of their data at less than $500.
"If firms don't set clear policies that reflect the priority of corporate data security, they can't expect employees to make it a priority on their own," says Tim Williams, mobile enterprise data expert and Director, Product Management at Absolute Software.
It's clear that the attitude of workers towards mobile device security is putting enterprise data at risk and that could be potentially costly. "The data may be carried around in the employee’s pocket, but the half million dollar fines we've seen levied due to data loss come out of the company's pocket," says Williams. "Clear policies, properly articulated to employees, will ensure that the entire company, not just IT, unites against mobile data loss".
You can view a full copy of the report's findings on the Absolute website.
Image Credit: funkyfrogstock / Shutterstock
-

Americans like it for free but Europeans still prefer to pay for protection
Publié: mars 5, 2014, 6:13pm CET par Ian Barker
 Independent testing group AV-Comparatives has released its 2014 Internet Security Survey.
Independent testing group AV-Comparatives has released its 2014 Internet Security Survey.The survey asked 5,845 users from around the world their views on security and reveals that when it comes to antivirus protection Americans like to get it for free whilst Europeans prefer to pay.
The four regions covered in the results are Europe, North America, Central/South America, and Asia. Worldwide just over half of users pay for a security solution but only in Europe are paid security products more popular. Free solutions win in North America and Asia and -- by a narrow margin -- in Central/South America. Avast is the product of choice for both mobiles and PCs in most regions, but with Asia preferring Quihoo 360.
"We found that just over half of all respondents pay for their endpoint security solution, and less than three percent use no solution," says Andreas Clementi, AV-Comparatives' CEO. "Respondents using a free solution don't necessarily receive inferior protection".
Some 2.4 percent of users worldwide admit to not using any security solution on their PC. This is higher for smartphones with 25 percent not having protection. Clementi says, "Over 25 percent of respondents stated that they do not have protection [on] their smartphones. These devices, and tablets, will probably be an increased target for cyber criminals in 2014".
The survey also asked what users felt were the most important aspects of a security product. The top three were low impact on system performance, good detection rates, and good malware removal and cleaning capabilities. These were the only criteria that achieved a higher than 60 percent response rate each. Using a product from a well-known vendor was at the bottom of the list with only a 10 percent selection rate.
The results show that Google Chrome has become the most popular web browser, with a 41 percent share, overtaking Mozilla Firefox on 32 percent. There's little surprise in the finding that the Android market share on smartphones increased from 51 percent to 70 percent. Nokia's Symbian share has dropped down to only 5 percent.
You can access the full report as a PDF on the AV-Comparatives site.
Image Credit: Maxx-Studio / Shutterstock
-

Spanning improves Google Apps Backup
Publié: mars 5, 2014, 2:43pm CET par Ian Barker
We all know that backups are important and these days that applies to data stored on cloud services just as much as desktop PCs.
Cloud backup provider Spanning Cloud Apps has announced a major update to its Spanning Backup for Google Apps, offering improved reporting and proactive notifications.
The new version includes a redesign of the status and notification interface Google Apps administrators use to understand what data is and isn't backed up. This is especially important in terms of data not saved as the Google API doesn't allow all data to be backed up and Spanning's competitors don't let administrators know this.
"Trust and transparency are non-negotiable with respect to cloud application backup," says Jeff Erramouspe, CEO of Spanning Cloud Apps. "We want our customers to live unencumbered by fear of the cloud, and to take risks without worrying about data loss. One of the things customers most appreciate about Spanning is the transparency we provide in reporting the status of their backups. For example, not all Google Apps data can be backed up due to API limitations. Spanning Backup offers the status updates and proactive alerts to highlight any issues that the customer would need to review and remediate to ensure proper backup is taking place. This gives customers visibility into their Google Apps data backup that they need for peace of mind. That’s how trust is earned and maintained, and that’s our commitment".
Gmail, Drive, Calendar, Contacts and Sites are automatically backed up daily to a private and secure sector of the AWS cloud. Enterprise grade security is used to protect your data and flexible restore options mean that, for example, emails can be found and restored by date, label, sender, and subject line.
Thanks to a redesign of status reports and notifications, administrators now get a deeper insight into the completeness of their backups with item-level detail and guidance on addressing problems. It can also identify potentially corrupt Google Drive files and send email alerts to admins on the backup status of user accounts.
The update to Spanning Backup for Google Apps is available now. You can visit the website for more information, or to sign up for a free 14-day trial.
-

Dell adds new training products to build security awareness
Publié: mars 5, 2014, 11:10am CET par Ian Barker
It's often the case that the weakest link in any system's security is the person sitting in front of the screen.
As companies recognize this they're tending to invest more in training so that they can avoid threats rather than have to clean up after them. In a recent worldwide survey by Dell, 67 percent of security decision makers say they have increased funds for education.
It's no surprise then that Dell SecureWorks is adding to its portfolio of security awareness training with two new products, a Managed Security Awareness Program and Managed Phishing Services. Both products are designed to help organizations combat the flood of information security threats by teaching employees about information security best practices.
The Managed Security Awareness Program aims to educate workforces and change employee behavior towards security threats. It includes a modular training curriculum, simulated phishing and spear phishing exercises, knowledge assessments, monthly newsletters and information security branding materials, along with reporting and metrics designed to demonstrate effectiveness.
Managed Phishing Services helps companies to test how their employees are responding to phishing attacks. It includes training in recognizing attacks and taking the correct action when confronted with a phishing email. SecureWorks sends out simulated phishing emails using common attack methods and provides immediate feedback if employees click on a suspicious link or attachment.
Dell SecureWorks CISO, Doug Steelman says, "One of the biggest reasons organizations get breached is due to the vulnerabilities of their employees. Companies can patch their software and have plenty of security controls with abundant security instrumentation. Unfortunately, one click from an uninformed employee can allow threat actors to achieve their malicious intent, regardless of security technologies which may be in place".
You can find out more about Dell SecureWorks security awareness training solutions on the company's website.
Image Credit: FuzzBones / Shutterstock
-

$1.7 trillion a year, the cost of dealing with business email
Publié: mars 4, 2014, 5:24pm CET par Ian Barker
Email has become a staple of business communication and although it's essentially free it has a hidden cost in terms the time spent dealing with it.
Collaborative email service Contatta has released an infographic which quantifies how time consuming and costly business email has become.
According to its figures the average worker spends 13 hours of their working week reading and answering email, which equates to an estimated 637 hours annually. Assuming a median professional wage of $23 per hour, that means businesses pay over $15K per employee to use email. Looked at across North America that means employees spend nearly 75 billion hours on email, costing businesses nearly $2 trillion in salaries -- that's almost 14-times the combined wealth of Bill Gates, Oprah and Warren Buffett.
More comparisons to show what that cost really means are in the infographic below. If you want to try to claw back a few of those lost dollars you can get a 60-day free trial of Contatta's collaborative solution, which aims to help employees use email more effectively, on the company's website.
-

Free content marketing for all from inPowered
Publié: mars 4, 2014, 3:04pm CET par Ian Barker
San Francisco-based content discovery specialist inPowered is making its discovery and amplification platform free for all organizations.
The software aims to help companies uncover trusted content, such as third-party reviews and articles, and use it to inform and engage their audience.
Until now only paid users have been able to access inPowered's platform but today it launches a free version that allows marketers, PR professionals and social media strategists to search for brands, products or topics and then discover and share the most trusted content to their fans and followers on Facebook, Twitter and LinkedIn. There's still a paid option too which lets marketers pay to promote content via targeted advertising.
"Too many 'content marketing' vendors ask companies to start paying up front, before the company knows what impact the service will have on business metrics. At inPowered, we're introducing a fundamentally different approach where everyone can utilize our free content discovery and amplification platform and see real results, then they can upgrade to paid amplification services, if they choose, for greater impact," says Peyman Nilforoush, Co-founder and CEO of inPowered. "Finding quality, credible information on the topics your customers are interested in should not be something you have to pay for -- that's something that everyone has a basic right to. Today, we're making that accessible to all".
As well as finding and sharing content, inPowered measures the impact in terms of reads and social shares. Once the most engaging content is identified companies have the option to pay for further promotion.
"We believe that everyone should be able to discover and share great content to help educate consumers, for free," says Nilforoush. "We also believe you should be able to measure the impact that the sharing of trusted content has when it comes to engagement and brand consideration. Then, if you want to dramatically increase the readership of your top articles beyond your social channels, you can utilize our paid amplification. This ensures that organizations only pay for clear, measurable business results".
You can find more information and start using inPowered for free on the company's website.
-

Major organizations face looming information crisis
Publié: février 28, 2014, 12:21pm CET par Ian Barker
Big data, cloud technology, social networking and the switch to mobile computing are all contributing to an increase in the amount of information enterprises have to deal with.
This is forcing companies to focus on the information that’s most relevant, risk related and value generating. As a result Gartner is predicting that 33 percent of Fortune 100 organizations will experience an information crisis by 2017, due to their inability to effectively value, govern and trust their enterprise information.
"There is an overall lack of maturity when it comes to governing information as an enterprise asset," says Andrew White, research vice president at Gartner. "It is likely that a number of organizations, unable to organize themselves effectively for 2020, unwilling to focus on capabilities rather than tools, and not ready to revise their information strategy, will suffer the consequences".
In order to avoid falling into this trap companies need an effective enterprise information management (EIM) strategy. This allows the sharing, management and reuse of information stored in different databases and created in different applications.
Having an EIM strategy though is only part of the answer. EIM initiatives must be designed so that sharing and reusing information creates business value, and the value created must contribute to overall enterprise goals.
According to Gartner analysts, three-quarters of individual information management initiatives are isolated from each other within the same organization. This leads to the benefits of EIM not being fully exploited. It says that IT leaders need to identify the key business areas that need improvement or are being held back by poor information management. This information can then be used to set new EIM priorities.
White concludes, "With effective information governance, business users will understand the impact of poor quality data on the outcome of desired business processes. This understanding leads to a desire, on behalf of the end user, to assure or 'steward' the data so that it supports their day-to-day business activities".
The impending information crisis will be discussed at the Gartner Enterprise Information & Master Data Management Summits 2014 on March 12-13 in London and April 2-4 in Las Vegas.
Image Credit: Maslowski Marcin / Shutterstock
-

Worldwide server shipments up in 2013 but revenues in decline
Publié: février 26, 2014, 5:28pm CET par Ian Barker
According to new research by Gartner worldwide server shipments were up 2.1 percent in 2013 whilst revenues declined by 4.5 percent.
Most of this shipment growth has taken place in the Asia/Pacific and Japan regions whilst the North American market has remained relatively flat. Vendor revenue declined everywhere except the Asia/Pacific region where it grew by just 0.6 percent.
"2013 presented some pronounced differences in various server market segments," says Jeffrey Hewitt, research vice president at Gartner. "We've seen ongoing growth in Web-scale IT deployments, while the enterprise remained relatively constrained. In terms of hardware platform types, mainframe and RISC/Itanium Unix platform market performance kept overall revenue growth in check".
In the Europe, Middle East and Africa market both shipments and revenue have declined. Adrian O'Connell, research director at Gartner says, "The EMEA server market continued to suffer as it recorded its 10th consecutive quarterly revenue decline. Economic weakness continued to have a profound effect on the EMEA server market. Total revenue in 2013 was only around two-thirds of that seen in 2007, before the downturn set in".
Breaking the worldwide figures down by manufacturer, HP dominates in terms of box shipments with 27.9 percent of the market, followed by Dell on 19.5 and IBM on 9.0. A different picture emerges when you look at revenue, however, with HP still leading on 28.1 percent but IBM close behind on 26.5 and Dell trailing in third with 15.2 percent. IBM's position shows a big decline, it had 34.9 of the market by revenue at the end of 2012.
The market for x86 servers remains strong as it's still the most popular platform for large data centers, showing a revenue increase of 0.8 percent despite a small drop in shipments of 2.6 percent over the year. HP is dominant here with 40.3 percent of the x86 blade server market, Cisco coming second on 15.9 percent.
The full breakdown of figures is available on the Gartner website.
Image Credit: watcharakun / Shutterstock
-

Are you reading this when you should be working?
Publié: février 26, 2014, 11:16am CET par Ian Barker
A study of 2,500 people in the UK shows that 68 percent have been distracted from completing work by browsing the web, checking emails and engaging in social media.
In addition, 63 percent said they had lost their train of thought while working on a report or long piece of written work because they responded to an email or social media alert.
The survey also reveals that 36 percent lose an hour or more a day in productivity to email and social media and that 53 percent thought that checking these things whilst trying to work revealed a worrying lack of control.
Excuse me while I check my Twitter feed...
Working from home doesn't help things either with 59 percent saying that they lost more time to online distractions. What's more this lack of self-discipline makes people unhappy, with 62 percent of respondents agreeing that there was a link to a reduction in their satisfaction and happiness levels when they realized they'd been less productive.
Playwright Will Little, creator of Webtrate.com says, "The survey suggests our impulse control is getting weaker in a world of instant gratification. Yet the pressure of work should mitigate against our desire to access the internet. Unfortunately the draw of the internet is so strong that our ability to concentrate is losing the battle. It is now directly impacting on productivity levels and many people just can't seem to help themselves. In many cases, they don’t even realize how much productivity they are losing to internet".
Ooh, interesting Facebook update there. Like...
Of those who said they were being distracted, 71 percent said they believed they'd get more done if they could disconnect from the internet for a time each day. Which brings us -- if you haven’t wandered off to check your email by now -- to the hard sell.
The Webtrate application forces users to disconnect from the internet and focus on their work goals. Developed by Little, who created it to boost his own output, it offers two options. It can disconnect at a set time but will allow you back online after a reboot, or if you need some extra discipline it won't allow you back online until a set time has expired.
Little concludes, "What we need is a way to separate our work from the distraction of the internet. I created Webtrate because my productivity levels dropped when I had access to the internet. Instead of working fully I checked emails and read endless news updates. Now since I developed Webtrate my productivity has improved considerably. I still engage with the internet but only when my work is done. And I'm a lot more satisfied and happy for it".
Webtrate is available now for Windows and Mac systems, you can find out more if you can concentrate for long enough to click this link.
Image Credit: Angela Waye / Shutterstock
-

viaProtect app delivers smarter mobile security
Publié: février 25, 2014, 7:42pm CET par Ian Barker
The increasing trend towards using mobile devices has opened up users to a whole range of new threats. On mobiles insecure apps present a greater risk than traditional malware and viruses.
Announced at the RSA Conference, viaProtect allows consumers to take control of and protect the personal data on their devices.
The company behind the product, viaForensics, has been protecting enterprises and government organizations for years and now brings the same technology to the consumer. Unlike traditional mobile security apps, which use a database of known malicious apps to screen for viruses and malware, viaProtect monitors all apps for potential risks. For example, viaProtect can detect if an app handles your personal data insecurely by sending it unencrypted or to unsecured servers located overseas. As many as 75 percent of apps are "leaky", or insecure according to viaForensics.
"We believe that everyone is entitled to state-of-the-art protection from threats like identity theft and loss of privacy," says viaForensics CEO and Co-founder Andrew Hoog. "viaProtect utilizes the same technology that our enterprise customers rely on to protect mission-critical data. It’s a more sophisticated approach for a world that is becoming more mobile by the day and one that an informed consumer will want. We’re very proud to make it available".
By gathering mobile forensic, system, network, security and sensor data from devices, viaProtect can use statistical analysis and risk indicators to detect suspicious events or behavior. It allows an app to be monitored in real-time to predict potential risks or problems -- rather than just checking for known malicious apps.
It's built to work with Android and iOS platforms and users are given a device risk rating to let them know how safe their system is. They can learn how their phones and tablets are sending data and where it's going to. It's ideal for families too with a browser-based dashboard that can be used to monitor several devices in one place.
For more information about the product you can visit the viaProtect website.
-

Financial organizations at risk via compromised third parties
Publié: février 25, 2014, 12:56pm CET par Ian Barker
Cyber threat intelligence specialist Lookingglass Cyber Solutions has released the results of a study on global financial institutions and the risks introduced by their partners and providers.
It makes for quite scary reading, with analysis revealing that 100 percent of the third-party networks sampled showed signs of either compromise or increased risk.
The recent Target breach is a case in point. Originally thought to be the work of an insider it now seems to have been the result of a third-party compromise.
Lookingglass found that outbound botnet traffic and malicious behavior were the most common indicators, accounting for 75 percent of the assessed sample. 25 percent of the sample showed indicators of the ZeuS Banking Trojan. General malware was also present with 25 percent having hosts attempting to communicate with Conficker sites.
A further issue is that 15 percent of third parties relied on a single internet provider leaving them vulnerable to DNS attacks. Since many of these third parties will use other suppliers for hosting and other services the risk runs further down the supply chain.
"Every week, we are hearing about a new organization reporting a major data theft, but what they aren't talking about is exactly how perpetrators are getting in. This study highlights a weakness that the industry has been very hesitant to talk about in public -- the fact that trusted third parties should not and cannot be truly trusted," says Chris Coleman, CEO of Lookingglass. "Global organizations such as financial institutions, as well as retailers and critical infrastructure organizations, must look beyond their own defensive perimeters and consider monitoring their public Internet presence to better understand their attack surface. Gaining insight into third parties is crucial to mitigating risk within the supply chain".
Image Credit: Stokkete / Shutterstock
-

Cyber criminals Pony up to steal BitCoins
Publié: février 25, 2014, 10:57am CET par Ian Barker
The Pony botnet malware has been around for a while but continues to cause problems and is moving into new areas.
Researchers from Trustwave have revealed on the company's blog that Pony malware has stolen the login credentials and digital wallets of thousands of people over a four month period.
This is the first time that widespread Pony malware has been found to steal digital wallets and currency. The currencies stolen include BitCoins, LiteCoins, FeatherCoins and 27 others with a value estimated at $330,000 at the time of discovery. The botnet has also stolen over 700,000 login credentials including 600,000 for websites and 100,000 email accounts.
There are obvious attractions in targeting virtual currencies, firstly they contain money, but secondly BitCoin transactions -- by design -- cannot be reversed. Once money is transferred out of your virtual wallet there's nothing you can do. There's no authority you can contact to reverse the transaction or freeze your account.
Trading information is also open, so anyone can examine the history of a virtual wallet though the identity of the owner remains unknown. The net result of all this is that stealing virtual currencies is much easier than stealing from a bank. Exchanging for hard currency via a trading website is just another transaction and by the time it occurs any connection to the original owner of the BitCoins is gone.
Once an attacker has the wallet.dat file containing the private key he becomes just as much the owner of the wallet as its original creator. Of course the wallet file can be protected with a password but it seems that many users don't bother to do this.
If you’re worried that your BitCoin wallet may have been compromised, Trustwave has set up a website where you can enter your public key to check. There's also a site where you can enter your email address to check for compromised credentials.
Image Credit: Rob Hyrons / Shutterstock
-

Is it a notebook? Is it a tablet? HP announces its new convertible PC
Publié: février 24, 2014, 4:05pm CET par Ian Barker
If you can never decide whether to take the notebook or the tablet with you when you go out, HP may have the machine for you.
Its new Pavilion x360 is a convertible PC with a 360-degree hinge so you can use it as a conventional notebook, a tablet, or in what the company calls "tent mode". Sadly this means only that you can stand it up on a table not actually go camping under it.
"Customers have told us they want a single device that is designed to work and play the way they do, at an affordable price," says Ron Coughlin, senior vice president of HP's Consumer PC and Solutions Group. "The HP Pavilion x360 is perfect for today’s busy lifestyles. Its 360-degree hinge allows multitaskers to easily transition from laptop to tent to tablet. It's the laptop that doesn't make you miss your tablet and the tablet that doesn't make you miss your laptop -- all at a price that is similar to an entry-level notebook".
With a weight of 3.08 pounds it's heavier than an iPad but about average for a notebook. The x360 has an 11.6-inch high definition SVA display with 10-point capacitive multi-touch, an HD webcam, twin speakers and a Pentium processor.
It comes in red or silver with a soft-touch finish on the outside to resist fingerprints and a brushed aluminum keyboard deck.
The Pavilion x360 should be available in the US on 26 February priced from $399.99. For more information visit the company's website.
HP also announced an expansion of its DataPass service, which gives users two years' free mobile broadband at 250MB of data each month. Currently available only in the UK, Sweden and Denmark, DataPass will be extended to 12 more countries, including the United States, from this summer.
-

Emulex adds Sourcefire connector for improved network forensics
Publié: février 24, 2014, 3:06pm CET par Ian Barker
One of the key tasks in investigating network security breaches is being able to capture packets to allow a thorough understanding and quick resolution of the problem.
Network management specialist Emulex Corporation has used the RSA Conference to announce its Endace Fusion Connector for Sourcefire Defense Center, which allows 100 percent packet capture at speeds of up to 100Gb Ethernet.
This means rapid response and root cause analysis, drastically reducing the time and operational overhead involved in accessing packet data. By narrowing the time gap between alert, investigation and response, the overall effectiveness of the security team increases, translating to improved system uptime, higher customer satisfaction levels and increased business continuity.
"We are very pleased to add Sourcefire to our growing Endace Fusion Ecosystem program," says Mike Riley, senior vice president and general manager of the Endace Division of Emulex. "The combination of Sourcefire’s highly-regarded network security toolset and our packet capture capabilities provides customers with a comprehensive security solution that significantly reduces enterprise network vulnerability windows and increases the data available for post-incident forensics analysis".
The Endace product offers a comprehensive intrusion detection system that not only provides full forensic visibility but also delivers a proactive approach to preventing future threats. With streamlined access to packet history security teams can react faster to resolve security incidents. It also makes it easier to identify which data has been compromised in a breach. Single-click access to EndaceVision Network Visibility Software allows for rapid analysis and the ability to search, visualize and interrogate captured traffic.
Fusion Connector for Sourcefire is available now as a free download from the Sourcefire community downloads site.
Image Credit: Sergey Nivens / Shutterstock
-

New networked flash storage solution delivers competitive advantage
Publié: février 24, 2014, 11:03am CET par Ian Barker
San Diego-based Astute Networks is announcing a new software release for its ViSX family of performance storage.
ViSX OS 5.0 adds Network File System (NFS) v2, v3, and v4 to its existing iSCSI support. The ViSX range also now offers an expanded range of capacity options to meet the growing demand for high application performance in both physical and virtual environments, including OpenStack support for cloud deployments.
Each ViSX storage appliance offers solid state performance at a low cost per GB and has a patented Data Pump Engine that offloads network and storage protocols in order to further boost performance. Designed to appeal to small and medium enterprises with no dedicated storage expertise, ViSX appliances can be plugged into existing infrastructure and improve application response times within minutes.
For critical applications like SQL Server, MySQL, Oracle and SharePoint, Astute claims ViSX can deliver an immediate 5 to 10 times performance boost. With support for the open source cloud platform OpenStack it offers a competitive advantage for cloud service providers allowing them to lower IT costs and enhance productivity.
"To enable their businesses to become more agile and responsive while making users more productive, IT professionals are facing the challenge to assure high application performance and availability while reducing overall IT costs and resource requirements", says Jeff Whitney, vice president of marketing at Astute. "That is precisely the focus of the newest release of the ViSX OS. It delivers outstanding all-flash performance while co-existing with installed storage for both physical and virtual environments. As a result, organizations achieve faster, consistent and predictable application performance while achieving a rapid ROI".
The ViSX Performance Storage Appliance range is now available in a range of capacities up to 45.6TB in a single 2U platform, and add-on flash modules are available in sizes of 480GB, 960GB and 1900GB. Find out more on the Astute website.
-

Companies are overlooking a new generation of security threats
Publié: février 21, 2014, 11:48am CET par Ian Barker
We reported yesterday on businesses being unprepared for the threats presented by BYOD. But according to a new study by Dell this is just one of a range of new threats that are being overlooked.
Technologies like BYOD, mobility, cloud computing, and internet usage, as well as internal actions both accidental and malicious, introduce organizations to a multitude of new risks.
But a majority of IT leaders don't see these threats as top concerns and aren't prioritizing dealing with them. Almost three-quarters of those surveyed admitted to having a security breach in the last year but only 18 percent thought predicting and detecting unknown threats was a major security concern. More worrying is that 83 percent said their current procedures allowed IT staff to identify a breach immediately, when actual detection took an average of seven hours.
Threats come from both inside and outside the organization and are often concealed in poorly-defined settings or ineffective access management and usage policies. 64 percent of respondents agreed that organizations will need to restructure and reorganize their IT processes, and be more collaborative with other departments to stay ahead of the next security threat. Of those surveyed in the United States, 85 percent said this approach is needed, contrasting with only 43 percent in the UK and 45 percent in Canada.
Matt Medeiros, vice president and general manager, Dell Security Products, Dell Software Group says, "Traditional security solutions can defend against malware and known vulnerabilities, but are generally ineffective in this new era of stealthy, unknown threats from both outside and inside the organization. These threats evade detection, bypass security controls, and wreak havoc on an organization’s network, applications, and data, but despite these dangers, our study found, among those surveyed, organizations are just not prepared. There is still a disturbing lack of understanding and awareness of the type of impact and detriment caused by the unknown threats that can come from both sides of an organization's data flow".
BYOD, cloud and the internet are seen as major areas of concern. Whilst 93 percent of organizations surveyed allowed personal devices for work, only 44 percent of those responding said instituting policies for BYOD security was of high importance in preventing security breaches.
The picture is the same with the cloud, 73 percent (90 percent in the US) report that their organizations use the cloud but only 49 percent ranked cloud usage as a top security issue for the next five years and only 22 percent said moving data to the cloud was a major security concern for today.
Awareness of internet threats is higher, with 63 percent of respondents ranking increased reliance on internet and browser-based applications as a top concern in the next five years. More than a fifth of respondents put infection from untrusted remote access like public Wi-Fi among the top three security concerns and 47 percent identified malware, viruses and intrusions as the root cause of security breaches.
Medeiros concludes, "...we believe a new security approach is needed -- one that's embedded in the fabric of software, governing access to every application and protecting every device, both inside and outside a corporate network. Only then, with this Connected Security approach, will organizations have a chance at keeping one step ahead of these epidemic threats that can significantly damage their network".
The full report is available as a PDF on the Dell website.
Image Credit: Brian A Jackson / Shutterstock
-

Hosted virtual desktop helps businesses migrate to the cloud
Publié: février 20, 2014, 5:44pm CET par Ian Barker
One of the problems with migrating systems to the cloud is ensuring a consistent means of access for users in different locations and with different devices.
Cloud services provider dinCloud has an answer in the form of webHVD, an HTML 5 virtual desktop that’s fast secure and easy to deploy.
The webHVD desktop runs in Google's Chrome browser which means it will work on Windows, OS X, Android and Chromebook platforms. It offers customers a turnkey desktop which they can start using in minutes. No VDI (Virtual Desktop Infrastructure) setup is required and there's no need to download or install a traditional software package. The Desktop as a Service (DaaS) offering includes a virtual private data center to manage user authentication, software-defined networking, virtualized storage, and computing power.
"HTML5 is the latest standard for how web browsers communicate on the Internet and is quickly making browsers like Chrome, Safari, and Internet Explorer, a single pane of glass for voice, video, instant messaging, collaboration, virtual desktop, and other functions. HTML5 offers many APIs which allow companies to take their innovations to the next level -- something that dinCloud has done with webHVD," says Walid Elemary, vice president of engineering and product development at dinCloud. "We took the number one rated hosted virtual desktop (dinHVD) and leveraged HTML5 to create a truly unique DaaS offering that snaps in easily, while delivering the performance, graphics, and functionality that small business users require".
The company sees webHVD as a viable replacement for remote access VPNs and other technologies that allow access from home networks or remote locations. This mitigates viruses, malware, and other potential security risks from joining the corporate network.
It allows multiple desktops to be assigned to a single user and there are multiple levels of authentication to keep it secure. Integration with Microsoft Active Directory means it’s easy to grant access to external parties, like consultants, using a valid email address. Levels of virtual disk space, memory and CPU can be tailored to individual needs.
To find out more visit the webHVD page of dinCloud's website.
Image Credit: Sergey Nivens / Shutterstock
-

Businesses unprepared for security risks from BYOD
Publié: février 20, 2014, 4:35pm CET par Ian Barker
A majority of organizations acknowledge that they’re unprepared to deal with security breaches via their BYOD technology.
A new survey released by security awareness training specialist KnowBe4 shows that 53 percent of businesses aren't properly prepared to deal with hacked or stolen mobile devices, even though 50 percent indicated that company-owned tablets, notebooks or smartphones may have been hacked in the past year.
The joint study carried out by consulting firm ITIC shows that 55 percent of companies are not increasing or strengthening their security despite recent high profile attacks against companies like Snapchat, Skype and Target.
The results show that 65 percent of businesses now allow end users to BYOD and use their own systems as corporate desktop or mobile devices to access organizational data including email, applications and sensitive information. This is attractive to companies because it cuts IT costs but comes at the price of increased security risks.
Kevin Mitnick, KnowBe4's Chief Hacking Officer says, "Mobile devices are the new target-rich environment. Based on lessons learned in the early days of the personal computer, businesses should make it a top priority to proactively address mobile security so they avoid the same mistakes [of the PC era] that resulted in untold system downtime and billions of dollars in economic loss".
Other interesting findings are that doubt remains over who is responsible for security on BYOD kit, with 43 percent of companies currently having no dedicated BYOD security policies. Only 13 percent of respondents said their firms had any specific policies in place to deal with BYOD deployments.
80 percent of companies consider strong anti-virus, intrusion detection and firewalls as the most important and effective mechanism to safeguard their networks, followed by endpoint security at 65 percent. Some 45 percent indicated that they were taking additional security measures including making sure the latest patches are installed and conducting security audits.
ITIC principal analyst Laura DiDio says, "These survey findings should galvanize corporations to proactively safeguard data in advance of an expensive and potentially crippling loss or hack".
Image Credit: Peter Bernik / Shutterstock
-

New threat intelligence platform speeds up investigation of security incidents
Publié: février 20, 2014, 1:45pm CET par Ian Barker
In today's complex cyber threat landscape it can be difficult and costly to investigate and respond to security incidents.
IT departments are often too focused on getting systems back online to spend time looking into the cause of the problem. With its new InSight platform AccessData wants to help enterprises better manage their data risks.
The InSight Platform enables the entire incident detection, analysis and resolution process via a single, consolidated platform with the ability to automate every step. When a threat is identified network forensics and other contextual data are automatically collected. The information is then presented in a unified view for easy analysis.
"The reality of today's cybersecurity world is one of continuous compromise, where every network has unauthorized people doing unknown things at any given time," says Craig Carpenter, CMO of AccessData. "In an environment of compromise, the ability to continuously detect, quarantine, respond to and resolve such incidents is an absolute must-have for any business or government entity. And with the massive growth and diversity of information, the need to automate as much of the incident resolution process as possible is obvious. The InSight Platform is the market’s first incident resolution solution, working seamlessly with legacy investments to give CISOs and IT departments comprehensive, real-time visibility into threats and incidents and the ability to remediate and resolve them quickly and easily".
As well as allowing better visibility of network traffic InSight maximizes other security investments like firewalls and sandboxes via greater integration. It incorporates a ThreatBridge engine that collects data from multiple intelligence feeds, allowing it to hunt for malware and detect indications that the system is compromised.
You can find out more about Insight on the AccessData website, or it will be demonstrated on the company's stand at the RSA Conference in San Francisco from February 24-28.
Image Credit: Sergey Nivens / Shutterstock
-

More people spend via their phones as the world goes "mobile first"
Publié: février 20, 2014, 11:58am CET par Ian Barker

Mobile advertising company InMobi has announced the results of its 2014 Mobile Media Consumption Report.
Based on research covering over 14,000 respondents in 14 countries, the findings show that we’re increasingly living in a "mobile first" world with 60 percent now using a mobile as their primary or only means of going online.
The main findings are that 68 percent have spent money via their phones in the past year and this is expected to rise to 83 percent in the next 12 months. Multi-screening is on the rise too as 61 percent report using their mobile for social networking and text messages whilst watching TV.
The results also show that mobiles are often used to fill in time. 83 percent of respondents said they use their mobile while waiting for something and 81 percent while lying in bed -- how many were lying in bed waiting for something isn't recorded.
Of course all of this has an effect on advertisers as mobile ads are now reckoned to be more influential on purchasing decisions than TV. The most common actions triggered by mobile ads are downloading an app (78 percent), visiting an advertiser’s website (68 percent), or visiting a store or retailer to get extra information or make a purchase (56 percent).
"In last year’s report we found that mobile had touched most aspects of modern life. But this year, we find that mobile has really become an essential part of daily life, even a daily workhorse, that has replaced the desktop and TV for everything from gathering key information, media consumption and accomplishing daily tasks, like shopping and paying bills," says Naveen Tewari, CEO of InMobi. "Furthermore, with mobile content gaining similar prominence as TV, mobile advertising is now impacting consumer behavior across the entire purchasing lifecycle from small day-to-day purchases, to bigger purchases, like cars".
All of this is important for companies as it shows that the mobile platform can have a real and measurable impact on businesses. The use of location tools, targeted mobile advertising, and responsive websites can help to drive consumer traffic and dramatically increase sales.
If you want to find out more you can get the full report from the InMobi Insights website.
Image Credit: Slavoljub Pantelic / Shutterstock
-

Skyhigh helps quantify the risk from corporate cloud usage
Publié: février 19, 2014, 5:16pm CET par Ian Barker
The cloud is increasingly popular with businesses because of its flexibility and low infrastructure costs, however, it does present risks when compared to running systems in house.
A new product from California-based Skyhigh Networks is aimed at quantifying the risks associated with public cloud services and takes the guesswork out of understanding and managing them.
Skyhigh's Enterprise CloudRisk Dashboard enables IT, security and executive teams to view a single score that encapsulates their overall cloud risk. They can also drill down to the metrics that make up the score, helping them understand the specific drivers of their risk. The product also produces recommendations to reduce risk and benchmarks the score both with a company's peers and between departments as well as tracking trends over time.
"For years, financial services' firms have been using objective, quantitative credit scores to evaluate potential risk," says Rajiv Gupta, CEO and founder of Skyhigh Networks. "With Enterprise CloudRisk Dashboard, we aim to bring a similar approach to managing cloud risk, so that our customers can adopt cloud services while minimizing risk."
The Dashboard has four key functions, the main one being a CloudRisk Score which provides a unique 1-10 score as well as showing its contributing factors. CloudRisk Recommendations produces actionable steps to reduce cloud risk, thereby improving the organization's CloudRisk Score.
CloudRisk Benchmarks allows the comparison of an organization's CloudRisk Score between internal departments and with industry peers, providing guidance on how the risk compares to organization norms and the industry. Finally CloudRisk Trends shows changes to the overall CloudRisk Score over time as well as trends in user, service and data risk.
Skyhigh also operates a CloudTrust Program to provide users with an objective assessment of a cloud service's security capabilities. Services that reach the most stringent standards can display the Skyhigh Enterprise-Ready logo on their site. The company is aiming for this to become an accepted standard for cloud safety as VeriSign is for secure web connections.
You can find out more about CloudRisk Dashboard on the Skyhigh website.
Image credit: Alexander Kirch/Shutterstock
-

Simpler, faster analytics for QuickBooks with InsightSquared
Publié: février 19, 2014, 2:08pm CET par Ian Barker
When it comes to invoicing and accounting packages for smaller enterprises QuickBooks is one of the first names that comes to mind
Now analytics specialist InsightSquared has launched a SaaS package for QuickBooks that lets users have immediate access to financial dashboards and reports, in addition to sales & marketing data.
Like the company's existing product for Salesforce it's aimed at making small and medium businesses more competitive. It offers ease of use, access from anywhere and a unified view for data drawn from multiple sources. This means that decision makers no longer have to wait for the accounts department to create reports or export data to spreadsheets.
By providing real-time insights into business data via charts and supporting data tables the product gives users the ability to drill down and get the story behind the numbers. Reports can forecast cash flow, identify customers who are at risk of churn, see which customers are least likely to pay before the month’s end and more.
Fred Shilmover, CEO of InsightSquared says, "Our new QuickBooks product is an innovation that gives a competitive advantage to data-driven business users. We've empowered small and mid-size businesses to make the right decisions in ways never before thought possible".
InsightSquared can be deployed in under a day without any integration costs and comes pre-loaded with popular reports so it can be productive from the start. You can find out more on the InsightSquared website.
-

Oracle delivers enterprise financial planning in the cloud
Publié: février 19, 2014, 11:12am CET par Ian Barker

Effective financial planning and budgeting is essential for all businesses, but the software needed to support it can be expensive.
ERP specialist Oracle has released its Oracle Planning and Budgeting Cloud Service to help businesses harness the power of integrated financial planning cost effectively and fast.
Part of the company's Enterprise Cloud Portfolio, Oracle Planning and Budgeting Cloud Service is a robust application that allows businesses to adopt a world-class solution with no need for infrastructure investment.
The product builds on the functionality of Oracle Hyperion Planning, including agile forecasting, predictive planning, rich scenario analysis and interactive dashboards. Cloud specific improvements include, pre-built starter kits, creation wizards and best-practice guides to allow faster deployments. There's Microsoft Office integration too so users can perform planning, reporting and analysis via the Web interface or in Microsoft Excel, reducing the need for training.
Administration and maintenance is easier too with automated scaling based on demand, run-time diagnostics built in and scheduled maintenance with managed software updates.
"Since we previewed Oracle Planning and Budget Cloud Service to customers and partners last year, we've seen a tremendous interest in adopting cloud-based solutions to streamline budgeting and improve forecasting," says Hari Sankar, vice president of product management at Oracle. "Today’s general availability reflects our commitment to helping organizations of all sizes harness world-class enterprise performance management in the delivery model of their choice".
For more information and to sign up for the service you can visit the Oracle website.
Image Credit: ra2studio / Shutterstock
-

CloudSOC makes enterprise clouds secure and compliant
Publié: février 18, 2014, 1:34pm CET par Ian Barker
As businesses move their data to the cloud they can often be caught out by the need to comply with audit and usage reporting requirements.
Cloud security specialist Elastica has a solution to this with its new CloudSOC product which helps companies and employees use the cloud whilst remaining secure and compliant.
Delivered as an easy-to-use cloud-based service, CloudSOC provides security for cloud applications and services in one place. It analyzes data from multiple sources, including real time traffic, APIs, firewalls and end-user devices. Using Elastica's StreamIQ technology it then applies the power of machine learning to secure a broad range of cloud applications and services.
"Cloud and mobile has brought the promise of a truly elastic enterprise. Such an enterprise empowers employees to collaborate from anywhere using any device, enables efficient consumption of business resources as needed, and improves overall business agility. Elastica eliminates the security hurdle to enable a safe and secure elastic enterprise," says Rehan Jalil, President and CEO of Elastica.
CloudSOC supports four apps. Audit provides insights and analytics for cloud-based services along with Business-Readiness Scores for thousands of cloud services based on more than 50 risk attributes. Detect highlights threats, assigning a ThreatScore in real time that can be used to trigger polices to issue an alert or block an action.
The Protect app enforces polices on cloud access in real time and can automatically enforce global policies across several cloud services at the same time. Finally the Investigate app allows post-incident investigations and forensic analysis across cloud applications and historical data. With powerful visualization and extensive filtering it can supply fast results even for complex queries.
Elastica's CloudSOC is available now and is priced on a per subscriber/per month basis. You can find out more and sign up for a trial on the Elastica website.
Image Credit: Maksim Kabakou/Shutterstock
-

Personal and entry level storage market sees strong end to 2013
Publié: février 14, 2014, 1:29pm CET par Ian Barker
According to data from market intelligence specialist IDC worldwide shipments of personal and entry level storage (PELS) grew by 13.6 percent in 2013.
By the end of the year 75.2 million units had been shipped. Shipment values were up too, growing 6.2 percent over the year to reach $6.7 billion.
"The personal and entry-level storage market finished 2013 strong even with the difficult comparison with a strong second half from a year ago", says Liz Conner, research manager, Storage Systems at IDC. "In 2012, the fourth quarter showed exceptionally strong growth as the PELS market was in full recovery mode after the Thailand floods, which led to hard disk drive (HDD) shortages. Despite the resulting slight decline in 4Q13, the PELS market was able post year-over-year growth for all of 2013. This continued annual growth is driven by on-going consumer education, better marketing by vendors, and progressing product evolution to address items such as higher capacity, faster transfer speeds, and mobile device integration".
Most of the entry level growth has come from four-bay storage which provides a popular starting point for buyers. Demand for devices with more bays remained flat whilst shipments of two-bay units declined by 32.2 percent year-on-year. In the personal storage market single bay units dominate, accounting for 98.8 percent of units shipped.
The report also points out a shift away from 3.5-inch discs in favour of more portable 2.5-inch units. The 3.5-inch form factor saw an 18.8 percent decline in units shipped over 2012.
USB remains the most popular personal storage interface though the entry level business market prefers Ethernet. The newer Thunderbolt interface saw shipment growth of over 280 percent but started from a low base.
Demand for more capacity continues to grow too. In the 2.5-inch personal storage market 1TB devices took 58.2 percent of market share. In the entry level market 4TB devices proved most popular accounting for 28.2 percent of devices shipped.
You can find more about IDC’s Worldwide Personal and Entry Level Storage Tracker on the company's website.
Image Credit: cagi / Shutterstock
-

Intel Data Platform helps businesses unlock their big data
Publié: février 14, 2014, 11:17am CET par Ian Barker
Many companies are keen to exploit the potential of big data but are wary of the potential costs involved in doing so.
To help businesses get maximum value from their big data investments Intel is launching the Intel Data Platform, a software suite based on open source technologies.
The Intel Data Platform offers an open environment for importing, managing and analysing big data. It builds on the existing Intel Distribution for Apache Hadoop and in addition a new Intel Data Platform: Analytics Toolkit creates graphical analytics and predictive modeling to help businesses uncover valuable insights from hidden relationships within their data.
"As big data shifts from hype to reality, Intel is helping to break down the barriers to adoption by easing complexity and creating more value," says Boyd Davis, vice president and general manager of Intel's Datacenter Software Division. "Much like an operating system for big data processing, the Intel Data Platform supports a wide variety of applications while providing improved security, reliability and peace of mind to customers using open source software."
Using fully integrated frameworks to process data in real time, businesses like retailers can use the Intel Data Platform to analyze information from social media, purchase history and inventory to, for example, measure the effectiveness of promotions. Business to business companies can look up data tailored to specific customers in order to tailor recommendations for products and services.
The platform will be available in the second quarter of this year in two versions. The Enterprise Edition will offer full platform capabilities as a free software product to customers who can support their own deployment. The Premium Edition will be available for purchase on an annual subscription basis and will provide additional technical features including enhanced automation, proactive security fixes and alerts, ongoing feature enhancements, and live telephone technical support.
Image Credit: Jojje / Shutterstock
-

HP mobile app catalog empowers companies to deliver BYOD
Publié: février 13, 2014, 3:26pm CET par Ian Barker
 The spread of BYOD means that employees increasingly expect a seamless experience, accessing content on the device of their choice.
The spread of BYOD means that employees increasingly expect a seamless experience, accessing content on the device of their choice.With the launch of its new HP Access Catalog, HP lets enterprises create a secure app store so employees can instantly download applications and digital content across both mobile and desktop devices.
The software as a service catalog supports the Android and iOS platforms and is delivered by both native mobile clients and a web interface. By using open-standard technologies it offers a secure, cross-platform solution. HP Access Catalog gives companies increased productivity by simplifying the delivery and management of mobile applications and allowing employees a self-service experience.
"As organizations embrace mobility, they need a simple, secure and reliable mechanism to manage the delivery of apps to their employees", says Dragan Milanovich, vice president, Web Services, Software at HP. "The HP Access Catalog provides enterprises with a robust, flexible and easy-to-use solution, making it easier for users to be productive on their device of choice".
The catalog has a native identity management system or can be seamlessly integrated with existing enterprise identity systems so admins can ensure users get the right software for their role. It also allows IT departments to push updates to users and so make certain they have the latest apps and data, improving their productiveness without harming security.
HP Access Catalog will be available from HP and its channel partners in March, as a standalone product or as part of the HP Anywhere enterprise mobility platform. Pricing will be on a simple, per-user annual subscription model.
Image Credit: Sergey Nivens / Shutterstock
-

Elasticsearch adds features and scalability in new release
Publié: février 13, 2014, 12:18pm CET par Ian Barker
Elasticsearch, the big data search and analytics specialist, has launched its first major product release.
Elasticsearch 1.0 is built on the company's experience of helping businesses deploy Elasticsearch as part of the ELK stack, used by many major organizations including Netflix, Soundcloud and Facebook.
Enhancements in 1.0 include a federated analytics feature that can analyze data from several different clusters, along with more robust tools that allow you to combine queries and put together more complex analyses. A Distributed Percolator feature lets you know when data you're interested in gets added to the system, and simplified snapshot and restore processes let you take incremental snapshots of your information and only restore data that's changed.
"Organizations have been using Elasticsearch and the ELK stack at scale, pushing the boundaries of what we even thought possible. Elasticsearch 1.0 is the accumulation of everything we've learned as we've helped countless businesses deploy the Elasticsearch ELK stack", says Shay Banon, founder of Elasticsearch. "Business leaders want actionable insights, but they also want a solution that will have the scale, stability and robust features to grow as their business grows. That is what we are delivering with 1.0".
This launch comes shortly after last month's release of Marvel, the company's first commercial product that helps administrators monitor Elasticsearch deployments in real time.
Elasticsearch 1.0 is available now on elasticsearch.org and from GitHub under an open source license.
Image Credit: Maksim Kabakou/Shutterstock
-

Free 15GB Bitrix24 account for BetaNews readers
Publié: février 12, 2014, 8:46pm CET par Ian Barker
Social intranet cloud site Bitrix24 is two years old and has over 100,000 company sign-ups. To celebrate it is giving BetaNews readers the chance to claim a free account with 15 GB of online document storage -- standard free accounts only get 5GB.
Here is how to claim yours.
You have to go to the Bitrix24.com website and enter your email address. You will then be emailed a confirmation code and link to a registration form. Down in the lower right corner of the registration form, next to the "Create" button, you will see "I have promo code", click it and enter "BETANEWS", and, after refreshing your browser, you will see the available storage jump from 5 to 15 GB.
If you've been thinking of giving Bitrix24 a try there is no better time to do it.
-

CRM is here to stay as businesses seek to improve customer experiences
Publié: février 12, 2014, 4:02pm CET par Ian Barker
 CRM has been around for a long time, but don't be tempted to think that it's on the way out. Companies are seeing CRM technology as a major part of their digital initiatives in order to improve customer experience.
CRM has been around for a long time, but don't be tempted to think that it's on the way out. Companies are seeing CRM technology as a major part of their digital initiatives in order to improve customer experience.This is the finding of the latest Gartner market trends report which says that demand for improved customer relationships is driving the expanded integration and use of CRM technology.
"CRM will be at the heart of digital initiatives in coming years. This is one technology area that will definitely get funding as digital business is crucial to remaining competitive", says Joanne Correia, research vice president at Gartner. "Hot areas for CRM investment include mobility, social media and technologies, Web analytics and e-commerce."
Although Gartner expects CRM market growth to be modest in 2014, following three years of strong investment, revenue from CRM software is expected to reach $23.9 billion this year with the cloud accounting for almost half of that.
Whilst e-commerce is at the top of most companies' lists when looking to improve customer service, Gartner's report identifies five main drivers of CRM investment. These include the need to monitor and respond to social media and use it as a channel for business intelligence. The mobile market is also key with connections to the Internet from smartphones expected to overtake those from PCs by the end of 2014.
The cloud is still important despite having been around for more than a decade. Gartner sees the move to the cloud slowing though as, "...the low-hanging fruit for cloud adoption has already been picked". Big data has led to an explosion in the amount of customer information available to businesses and has driven increasing sophistication in CRM models to analyze and predict customer behavior.
The fifth driver is the growing shift towards an "internet of things." As the price of embedded sensors falls, many industries will be transformed by the information gathered and CRM is likely to be at the forefront of exploiting the data produced.
"These drivers are spurring a critical need for more traditional operational CRM as CRM continues to top software investment priorities. This further validates businesses' focus on enhancing customer experience and consistent investment in CRM software, especially in CSS, marketing and sales software", says Ms. Correia.
The full report is available from Gartner's website and Gartner analysts will be discussing CRM trends at summits in Orlando and London later this year.
Photo Credit: Mikko Lemola / Shutterstock
-

2013's malware trends reveal non-Windows systems face greater threats
Publié: février 12, 2014, 1:19pm CET par Ian Barker
 Threats to Mac OS X, Linux and Android systems have increased over the past year as the malware landscape has evolved.
Threats to Mac OS X, Linux and Android systems have increased over the past year as the malware landscape has evolved.This is among the findings of Russian antivirus company Doctor Web which has released its annual overview of threats. Other trends include an increase in the number of programs designed to display annoying ads and a surge in the number of Bitcoin and Litecoin mining trojans.
Using statistics compiled from Dr.Web CureIt! the company finds that trojans were the most common threat of the year. Amongst these the top of the table was Trojan.Hosts.6815 which modifies the hosts file to redirect the user's browser to infected web pages.
Doctor Web also monitored the activity of several botnets. Although one of these almost ceased to exist in 2013 others are still operating and their numbers are growing. In particular it highlights the Win32.Rmnet.12 botnet, which from May was gaining around 25,000 machines per day. The report also notes that the Backdoor.Flashback.39 trojan, which exploits Mac OS X systems, although declining still had a botnet of almost 29,000 infected Macs by the end of December.
As you might have gathered from our story yesterday on CryptoLocker, the big trend of 2013 is the growth in ransomware trojan encoders that encrypt files and demand a payment for their release. The report says, "During the year, the Dr.Web virus databases were supplemented by definitions for more than 200 new modifications of encoders, and the geography of these threats expanded considerably. And, the technologies used by the attackers evolved, too: above all, more sophisticated encryption was employed, making it virtually impossible to restore data affected by the actions of some Trojan.Encoder modifications."
It seems criminals have improved their victim profiling too. Malicious files were attached to forms that job applicants had to fill out to apply for an accountant post and sent out to companies offering such jobs. This increased the chances of encrypting vital accounts forms thus raising the probability that the ransom would be paid.
Advertising and mining trojans showed increased numbers of detections too and again Mac users don't escape, with the development of Trojan.Yontoo.1 which downloads and installs advertising plug-ins for the Mac versions of Safari, Chrome and Firefox. Trojans seeking to mine Bitcoin and Litecoin also showed an increase in the second half of the year with average daily income for the criminals estimate at close to $1.5 million.
Linux and Android
Linux users normally feel pretty smug about their vulnerability to malware but Doctor Web has noted a number of new threats to the open source operating system. Most notable is the Hand of Thief trojan which can operate on various distros including Ubuntu, Fedora and Debian, it also supports eight desktop environments such as GNOME and KDE. This sophisticated malware features anti-detection technologies and routines for its covert startup, does not require administrator privileges, and uses strong 256-bit encryption for communicating with the control panel. Once installed it adds a special grabber to browsers that intercepts HTTP and HTTPS sessions and transmits data entered by users in web forms.
Other programs targeted at Linux are aimed at compromising servers, by sending logins and passwords to a remote system, and organizing DDoS attacks.
There's been a further increase in Android threats too with the Dr.Web virus database receiving 1,547 new entries corresponding to malignant, unwanted and potentially dangerous programs in 2013. This means that since the first malicious Android programs were detected in 2010 their number has increased almost 94 times.
Most common Android threats are still those that seek to extract cash through premium rate SMS services. Other familiar threats are spreading to Android too though, including trojans looking to steal personal data and fake anti-malware tools. In September 2013 Doctor Web's researchers uncovered the largest known botnet of mobile devices.
The report concludes that we're likely to see further increases in encoder trojans thanks to the availability of malware construction kits. It also predicts further increases in mining as the popularity of Bitcoin-like systems grows.
If you'd like to scare yourself some more you can read the full findings on the Doctor Web site.
Photo Credit: Balefire / Shutterstock
-

GoGrid simplifies moving to big data
Publié: février 11, 2014, 2:04pm CET par Ian Barker

Big data is something that many companies are keen to exploit, but implementing big data solutions involves a number of hurdles.
Open Data Services specialist GoGrid is aiming to make the move to big data easier with its launch of 1-Button Deploy technology.
"Enterprises are eager to evaluate and implement the latest Big Data solutions, but until now, they haven’t had the resources to do so quickly and easily," says GoGrid CEO John Keagy. "GoGrid’s new 1-Button Deploy solution, combined with our Open Data Services platform, offers companies immediate access to the most advanced technologies on the largest server selection tailor-made for Big Data. Essentially, we give developers the keys to the Lamborghini, letting them drive best-of-breed Big Data solutions with the push of a button".
Powered by the Ansible development platform, 1-Button Deploy allows the deployment of a big data cluster across GoGrid's virtual servers. It offers automated deployment of a number of popular big data technologies including MongoDB, Riak and Cassandra, with Hortonworks 1-Button Deploy of Hadoop scheduled to go live in March. All of which means companies save on development time and costs whilst getting applications live faster.
"Our technology lets organizations launch the latest solutions with the push of a button, dramatically reducing deployment time and opening up a world of Big Data options to businesses that may not have the in-house expertise or resources to take advantage of them otherwise," says Ansible CEO Said Ziouani. "We’re delighted that GoGrid is supporting the continued development of our orchestration technology, and we’re excited to work together to advance the Open Data Services movement".
By making it easy for companies to explore a selection of big data solutions on its purpose-built infrastructure, GoGrid is helping businesses to quickly adopt the right technology -- or a combination of technologies -- for their big data applications. You can find out more on the GoGrid website.
Photo Credit: T.L. Furrer / Shutterstock
-

Point.io makes accessing enterprise data easier regardless of platform
Publié: février 11, 2014, 11:29am CET par Ian Barker

We looked at the launch of the Point.io backend as a service (BaaS) platform last year and explained how it could help companies retain control of their data in the era of BYOD.
The company is now making it easier to enable fast, secure data links with the launch of APIdoc, a single point of access for all file sharing and storage technologies.
APIdoc supports most popular cloud storage platforms including Dropbox, Google Drive, Microsoft OneDrive, Amazon S3, Salesforce.com and more. It also comes with an SDK so that custom storage connectors can be developed quickly for other systems.
Because it has pre-built standard API functions for common file and data handling tasks it speeds up deployment. And since it provides a single communications platform it also cuts development and maintenance costs by removing the complexity of backend storage allowing developers to concentrate on processes and interfaces.
APIdoc includes a full suite of metadata so it can provide reports to meet audit and compliance needs across platforms.
"APIdoc is the most comprehensive, easy-to-use utility to connect a company’s data sources in the market today," says Tim Panagos, CTO of Point.io. "The complexities of integrating structured data from databases or production systems and unstructured data like documents and spreadsheets can be overwhelming and expensive. APIdoc isolates all of that complexity from user applications and lets developers focus on true value-add rather than tedious internal plumbing".
You can find more information on APIdoc on the Point.io website.
Photo Credit: klRr / Shutterstock
-

Automated reminder system helps cut the cost of missed appointments
Publié: février 7, 2014, 3:48pm CET par Ian Barker
Missed appointments cost health services and other businesses a significant amount of money, estimated at millions of dollars each year. Los Angeles-based marketing firm Screenpush is aiming to change that with the launch of Notifly.
Notifly works by sending out text message reminders in the run up to an appointment, prompting patients or customers to either confirm or cancel. On the business side of things a color-coded interface makes it easy to track each day's appointments and work around changes.
It's estimated that by using Notifly businesses can cut missed appointments by as much as 65 percent. "The technology behind Notifly is advanced, but the logic is simple," says CEO Josh Otten. "Save money, improve efficiency. The Notifly service is affordable and pays for itself almost immediately. And the results will improve everything about how a business functions. The idea came out of a very real problem facing many businesses and health organizations in particular. And the product offers a smooth and effective solution at a low cost".
By using standard SMS text messages the service works with almost all cell phones and keeps costs low. Notifly costs users as little as two to four cents per reminder whereas some existing competitors can cost as much as 50 cents.
Customers can reply with a simple Y or N response and Notifly's system automatically tracks these on a calendar. This cuts out the need for overbooking and gives more time to make adjustments and re-book vacant slots.
Otten concludes, "Not only does Notifly save businesses money, but it also improves their operating efficiency, making things easier for employees and more streamlined for the clients themselves".
You can find out more about how the system works on the Notifly website.
Photo Credit: Franck Boston / Shutterstock
-

Cyber security threats are for life, not just the Winter Olympics
Publié: février 7, 2014, 11:58am CET par Ian Barker

With the Winter Olympics about to start there have been a number of stories pointing out the security risks of people using their mobile devices in Sochi.
Writing in a blog post, Paul Proctor, vice president and analyst at Gartner says it's important to remember that you're not really safe anywhere and it's your behavior that's the key factor in your security.
In particular he highlights a recent NBC News story which carried out an experiment in Sochi and which says, "Visitors to Russia can expect to get hacked," as being misleading.
Proctor says, "...everything they describe in the story is as equally true at your local Starbucks as it is in Sochi. Therein they miss the opportunity to present a more accurate picture of global security, as opposed to the 'evil Russians'".
He points out that none of the threats covered in the story require the hackers to actually be in Russia. The threats were not location dependent and NBC waited until the end of the story to point out that you shouldn't click on links you don't recognize from people you don't know.
The NBC story is a missed opportunity to point out that cyber security is a matter for everyday life, and Proctor encourages the news team to repeat their experiment in a Manhattan coffee shop.
Photo Credit: vidguten / Shutterstock
-

Xamarin and built.io get together to aid end to end mobile development
Publié: février 6, 2014, 4:49pm CET par Ian Barker
Mobile development specialist raw engineering saw its built.io backend as a service product come out of beta in November.
It's now announced a partnership with front end developer tool Xamarin to give users a complete development solution whilst making point.io’s functions available to existing Xamarin clients.
"Enterprises typically have two choices for mobile development: established but cumbersome legacy platforms, or fast-to-launch but untried players that aren't built for enterprise needs," says raw engineering CEO Neha Sampat. "Our partnership with Xamarin allows enterprises to get the best of both worlds: rapid mobile innovation on a platform that's proven in the enterprise".
The demands of BYOD mean that businesses are under more pressure to create mobile apps. Gartner predicts that by 2016, 70 percent of the mobile workforce will have a smartphone, half of which will be purchased by the employee, and that 90 percent of enterprises will have two or more mobile platforms to support.
Whilst built.io takes care of the background databases, servers, notification, scaling, analytics and so on, Xamarin looks after the client side. It enables developers to build native apps for Android, iOS, Mac and Windows from a single code base, cutting development time and ensuring consistent operation.
Jo Ann Buckner, VP of Product Marketing at Xamarin says, "Companies today are looking for scalable ways to mobilize their business practices and customer interactions onto multiple platforms. Our collaboration with built.io will accelerate mobile app development for our community, while ensuring mobile apps have a solid and secure backend".
Visit the built.io website for more information.
-

The top drivers and barriers for BYOD
Publié: février 6, 2014, 3:12pm CET par Ian Barker
Many businesses are still unsure of the benefits of allowing BYOD despite the fact that it's reckoned 59 percent of people using BYOD get more work done on their own device. So what are the main factors involved?
BYOD implementation expert Moka5 has put together an infographic showing the top three drivers and barriers to companies investing in the technology.
The drivers are that BYOD is better for the workforce, particularly where access is needed for a diverse range of people including remote workers, contractors and outsourcers. It can also lead to significant savings on both capital and operational expenditure. Finally it results in a happier and more productive workforce who can work where they want and on the machines they want to use.
On the other side of the coin there are fears of confidential data being accessed on untrusted devices. Separating work from play can be harder if the same device is used for business and for personal use. Finally technical support becomes more complex as the IT department needs to cope with a wide range of different devices.
You can view the full infographic below (click to enlarge).
Photo credit: Ivelin Radkov/Shutterstock
-

Over 60 percent of organizations suffer security breaches in 2013
Publié: février 6, 2014, 12:24pm CET par Ian Barker
A survey of more than 750 security decision makers and practitioners in North America and Europe finds that more than 60 percent have suffered some form of security breach in 2013.
In its first Cyberthreat Defense Report the Cyber Edge Group aims to provide an all-round view of organizations’ security threats, response plans, processes, and investments.
The report provides some insights into the challenges facing IT security professionals. Key findings include that mobile devices are seen as being more vulnerable to threats. Little surprise then that 31 percent of organizations already have BYOD policies in place and 77 percent expect to have them by 2016.
Levels of security investment are a concern too. 89 percent of respondents say that security budgets are rising or holding steady, one in four doubts that they have adequate investment in cyber threat defense.
Looking at threats by category, malware and phishing are of most concern whilst denial of service attacks are lowest on the list. Low security awareness amongst employees is widely cited as a factor affecting companies’ ability to defend against threats.
Despite the awareness of threats only 48 percent of respondents said their organizations carried out full vulnerability scans more than once a quarter with 21 percent only doing them annually. There is some confidence though, despite 60 percent admitting to being the victim of a cyber attack in 2013, only 40 percent expect to be caught out again this year.
"For years, Verizon has done a tremendous job assessing the current state of the cyberthreat landscape. But aside from a few vendor-leaning reports, no independent research firm has conducted a formal study to adequately assess the perceptions of IT security practitioners and the security posture of their employer’s networks. That ends today with the launch of our inaugural Cyberthreat Defense Report," says Steve Piper, CEO of CyberEdge Group, LLC. "As security professionals, it’s not only important to know what threats are coming at us, but what our peers are doing about them. This report provides this level of insight in a purely unbiased way."
You can get the full report, which is sponsored by leading IT security vendors, free at http://www.cyber-edge.com/2014-CDR/
Photo Credit: Sergey Nivens / Shutterstock
-

SAP helps businesses deliver effective project management
Publié: février 4, 2014, 4:39pm CET par Ian Barker
There are lots of project management tools available, but when enterprise software specialist SAP launches one you expect it to be something pretty impressive.
Building on the capabilities of the existing SAP Business Suite which covers ERP, CRM and other core functions, SAP Commercial Project Management brings project-related front- and back-end information into one integrated system. Once there it makes it available to project managers, administrators and executives as well as aiding collaboration with sub-contractors and customers.
SAP says that the new product allows end-to-end management of the whole project value chain, improving profitability and increasing employee productivity. It helps users to create effective bids by leveraging information from past projects and conforming to best practices.
"While a high percentage of project profitability is determined at the bid stage, around half of all projects are not delivered to plan -- in fact, on average 20 percent of project value is at risk," says Chakib Bouhdary, executive vice president, Global Industry Solutions and Customer Value at SAP. "SAP Commercial Project Management enables professional services, engineering, construction and operations and other project-based industries to reinvent the way they sell and deliver their services by offering full transparency throughout the project life cycle while helping ensure project profitability".
SAP Commercial Project Management is made up of three parts, project workspace, project cost and revenue planning, and project issue and change management. Running on the SAP HANA real-time, in-memory data platform, the software is mobile-enabled and can be used by companies selling and delivering projects to customers as well as those running projects internally. Additional mobile apps will also be available from SAP partners like Mindtree to provide key information to managers.
Photo Credit: SAP AG
-

WANs are still key to business success
Publié: février 4, 2014, 11:46am CET par Ian Barker

With the rise in popularity of cloud services it's easy to forget about the impact on other models of IT delivery.
A new survey from network and business continuity specialist Talari Networks looks at the current state of WANs. Carried out in late 2013, the survey identifies the role of the WAN in supporting applications, achieving business goals, shifts in the use of WAN services and changes in WAN budgets.
The results reveal that the most important factors set to impact WANs in the coming year are improving application performance, cited by 42 percent of respondents and providing better real-time application support (32.4 percent). Yet 67.7 percent of IT organizations currently don’t prioritize applications or only do so in a static way.
"The survey results indicate the importance of the WAN to business success. For example, the survey results indicated that enterprise applications, such as CRM, are the leading drivers of increased MPLS traffic and one of the top drivers of the increase in Internet traffic. The survey results also indicated that on average there are 14 WAN-related incidents a year that negatively impact one or more of a company’s business-critical applications," says Jim Metzler, VP of Ashton, Metzler & Associates the analyst firm which carried out the research.
When asked to look at the implications of their business-critical applications not performing well, most respondents indicated pressure from the boss or business unit managers, tarnished reputation of the IT department and revenue loss. 86.5 percent say their WAN negatively impacts critical applications either occasionally or frequently.
"There's no doubt that the WAN plays an increasingly important role to a company's ability to function as business-critical, real-time applications, such as voice and video, public cloud apps and services and the use of mobile devices in the workplace continue to grow," says Talari's President & CEO Emerick Woods.
Other interesting findings include that prioritizing business-critical applications is seen as equally important as improving security. More than half of IT organizations use the internet to carry between one and 40 percent of their traffic and that use is set to grow. The applications driving this increased internet use are public cloud services (35.7 percent) and support for mobile users (22.7 percent). The outlook is generally positive with WAN budgets seen as being three times more likely to increase as they are to decrease.
The full report is available in PDF format on the Talari website.
Photo Credit: Maxx-Studio / Shutterstock
-

Corero SmartWall helps service providers strengthen their defenses
Publié: février 3, 2014, 3:18pm CET par Ian Barker
Cyber threats and in particular DDoS attacks are a major problem for both service providers and customers and have grown in both frequency and sophistication.
Corero Network Security a leader in enterprise security systems has launched a new product to help service providers fend off these threats.
Corero SmartWall Threat Defense System (TDS) aims to offer a first line of defense that's always on and provides visible threat protection to customers. It's a purpose-built family of network security appliances that can be configured to meet the needs of service providers.
The SmartWall TDS is rack mounted and comes as a series of appliances that can be used individually or clustered together. The Network Threat Defense unit guards against DDoS attacks using IP address blocking, SYN flood protection, TCP/UDP rate control and Client-Server connection limiting. Application Threat Defense, as the name suggests, protects against application threats with Deep Packet Inspection (DPI) of Layer 7 protocols and payloads in combination with behavioral anomaly detection.
The Network Forensics Appliance supports 10Gbps line rate packet capture to enable network forensics of security incidents. Finally the Network Bypass Appliance helps avoid downtime using intelligent zero power network bypass technology in the event of power or equipment failure, or during routine maintenance and configuration upgrades.
"We are excited to introduce this new portfolio of First Line of Defense solutions for service providers," says Ashley Stephenson, CEO of Corero Network Security. "Building upon our years of experience supporting enterprise customers with on-premises DDoS protection, we have now enabled service providers to similarly assist their customers in the escalating battle against cyber threats. With the addition of the SmartWall TDS, Corero is well positioned to keep pace with the evolution of the DDoS defense market and customer demands for improved levels of cybersecurity protection, both on-premises and in the cloud".
The technology will be demonstrated on Corero's stand at RSA 2014 in San Francisco. SmartWall TDS solutions will be available for trials shortly and for full deployments by the second quarter of 2014.
-

Good news and bad as the enterprise threat landscape evolves
Publié: février 3, 2014, 1:00pm CET par Ian Barker
Technology giant HP has released its Cyber Risk Report 2013 which highlights the top enterprise vulnerabilities.
The report also offers an analysis of the current threat landscape, pointing out increased reliance on mobile devices, the spread of insecure software and the growing use of Java as adding to a growing "attack surface".
On a positive note the total number of disclosed vulnerabilities is down six percent over the previous 12 months and the number of high-severity vulnerabilities is down for the fourth consecutive year.
It's not all good news though, other key findings include the fact that 80 percent of applications reviewed contain vulnerabilities outside their source code. Plus 74 percent of applications had unnecessary permissions. This shows that even good applications can be vulnerable if wrongly configured.
Of the mobile applications studied 56 percent use encryption improperly. The research shows that mobile developers often fail to use encryption when storing sensitive data, rely on weak algorithms to do so, or misuse stronger encryption capabilities, rendering them ineffective.
It also finds that inconsistent malware definitions complicate risk analysis. HP examined more than half a million Android apps and found major discrepancies in how antivirus engines and platform vendors classified malware.
Sandbox bypass vulnerabilities were most common for Java users. Attackers have stepped up their Java attacks by exploiting multiple known and zero day vulnerabilities in combined attacks to compromise specific targets.
HP’s Zero Day Initiative, aimed at rewarding responsible researchers for disclosing vulnerabilities, uncovered more vulnerabilities with Internet Explorer than any other software. However, the report notes that this is a result of market forces focusing researchers on Microsoft vulnerabilities and doesn’t reflect on the overall security of Internet Explorer.
"Adversaries today are more adept than ever and are collaborating more effectively to take advantage of vulnerabilities across an ever-expanding attack surface," says Jacob West, chief technology officer, Enterprise Security Products at HP. "The industry must band together to proactively share security intelligence and tactics in order to disrupt malicious activities driven by the growing underground marketplace".
The report recommends that businesses must stay in touch with the latest security risks, particularly for mobile devices, and that robust security procedures must be put in place to protect data and privacy. This includes eliminating opportunities for unintentionally revealing information that may be useful to hackers.
While it's impossible to eliminate all attacks without sacrificing functionality, HP says that a combination of the right people, processes and technology does allow organizations to effectively minimize vulnerabilities and dramatically reduce overall risk. Collaboration and sharing of intelligence among the security industry also helps to strengthen protection and create a safe environment.
The full report and recommendations are available to download from the HP website.
Photo Credit: watcharakun / Shutterstock
-

UK readers -- your chance to test the latest 4G smartphones
Publié: janvier 31, 2014, 2:24pm CET par Ian Barker
If you've ever fancied becoming a gadget reviewer, then mobile provider EE along with tech website Gizmodo UK is offering you the chance.
Over three months of the Testmodo challenge three people will get to try out the superfast 4GEE service on one of the latest and smartest 4G handsets.
The winners will be sent a new smartphone each month and will carry out a series of challenges, writing a short review for the Gizmodo UK site every two weeks. The best bit though is that they get to keep the handsets they test at the end!
So, perhaps you want the bragging rights of showing off a new handset each month. Maybe you're curious about whether 4G lives up to the hype or possibly you've always wanted to get a foot in the door of tech journalism. Whatever your motivation this is your opportunity.
By now you’ll be on the edge of your seat wondering how to take part, so here are the details. First you need to be in the UK -- sorry rest of the world. Go to the EE coverage checker and find out if you’re among the 70 percent of the population that has 4G coverage. If you are then email your entry to giztestmodo@gmail.com. This needs to include your name and address plus a couple of lines explaining why you think it should be you and ideally your Twitter handle and blog link too. The competition closes at the end of Monday February 3rd so don’t hang around. Full details and T&Cs are available here.
Good luck to the entrants and let us know how you get on!
-

Able-HD wants to put a monitor in your bag
Publié: janvier 31, 2014, 11:29am CET par Ian Barker
As long ago as 2003 Microsoft research found that having a second monitor made people up to 50 percent more productive.
However, having two screens is fine for those of us tied to a desk but isn’t exactly practical for people on the move.
The Able-HD Plus monitor is aiming to change that and allow you to take a second screen with you wherever you go. Available in 15 and 17-inch versions, both with full 1080p resolution, the 17-inch model is lighter than an iPad and less than one-third the thickness of a standard HD monitor, making it easy to slip into a laptop bag or briefcase.
It has a multi-port, detachable adapter board which also acts as a stand and is compatible with laptops, smartphones, Xbox games consoles and other devices, and comes with audio in/out, HDMI, VGA, and DVI connections. A synthetic polymer casing and rubber edging prevents damage to both the monitor and adapter, while a thermoplastic acrylic screen gives the strongest, clearest resolution without sacrificing the monitor's streamlined design or loading it with extra weight.
"The Able-HD Plus is going to open up a whole new world of possibilities for productivity and enjoyment, both for people who already like working with multi-screen systems and people who have never considered it before," says Nell Harton, Founder and CEO of the Able-HD startup. "Everyone carries their computers with them in one form or another. Now they can carry their screens, too".
The original project was financed on Kickstarter. Now the team behind Able-HD is headed back to the site in order to raise funds to address issues -- particularly fragility -- identified in the first design.
"We knew we had to make the system stronger," says Harton, "but we took the opportunity to rethink the entire system design, and wound up making some changes that are both innovative and highly functional".
To find out more, pledge to the campaign or reserve a screen at an "early bird" price for its summer 2014 release visit the Able-HD website.
-

New collaboration tool gets Office workers in a Huddle
Publié: janvier 30, 2014, 5:25pm CET par Ian Barker
We've looked at the Huddle desktop collaboration tool, which offers a blend of productivity and social networking, in the past here at BetaNews. The company is now launching another phase of its Connected Desktop with a plug-in for Microsoft Office.
By linking the power of Office tools with Huddle's cloud collaboration service the company aims to make workers more productive. Files can be saved into Huddle's secure cloud directly from Office applications but more importantly each document has a comment stream alongside it, allowing users to provide feedback on changes and reply to co-workers in context, all without leaving Office.
"People’s devices -- PCs, laptops, desktops and tablets -- are now simply a doorway to their world of work as the cloud gives them access to their files, colleagues' feedback and all the information they need," explains Alastair Mitchell, CEO of Huddle. "Skipping between the applications on your desktop and cloud service to share information and discuss files with people is time-consuming and disrupts your workflow. With Huddle for Office, you can continue working in the desktop tools you’re used to, but all of your feedback, files and updates are stored and shared in Huddle's secure cloud. Connecting with the people you need to and working together on your content has never been easier".
With the plug-in installed Huddle functions can be accessed via a toolbar within Office. There’s also the ability to track all comments and changes for compliance and auditing purposes. Documents are saved to a secure workspace ensuring that only authorized team members can access them. They can also be read and commented on via Huddle's tablet and smartphone apps.
Huddle for Office integration is available now, visit the company's website for more information.
-

iWeb launches Microsoft Private Cloud
Publié: janvier 30, 2014, 4:41pm CET par Ian Barker

Canada's leading cloud service provider, iWeb, is launching a Microsoft Private Cloud hosting service.
Aimed at giving businesses more control and flexibility over their IT infrastructure, it allows virtual servers to be deployed quickly without the expense and complexity of in-house data centers.
Microsoft Private Cloud can be deployed entirely from iWeb's data centers but managed by a business’s own IT team. Alternatively it can be used in hybrid configurations with in-house systems or public clouds.
This has a number of advantages, allowing users to extend their in-house data center or move specific workloads across to a hosted environment. It does away with concerns about space and costs and reduces the need for capital expenditure as well as offering flexibility for future growth. An additional advantage -- non-Canadian readers can look away now -- is that it addresses data sovereignty issues as it's hosted on Canadian soil.
"With businesses turning to the cloud more so than ever before, the Microsoft Private Cloud from iWeb provides the best of both worlds with cloud scalability on dedicated private infrastructure," says Christian Primeau, President and COO of iWeb. "Our team provides rapid deployment, state-of-the-art data centers and network infrastructure, all supported by top-notch professional services, freeing up customers to focus on their core business".
Microsoft Private Cloud from iWeb is available now. For more information and pricing visit the company’s website.
Photo Credit: Marynchenko Oleksandr / Shutterstock
-

Dell puts cloud access in your pocket
Publié: janvier 30, 2014, 12:16pm CET par Ian Barker

PC and server specialist Dell is launching a new mobile cloud access device that delivers a full HD user experience on any HDMI or MHL enabled display.
The company claims that Dell Wyse Cloud Connect is a completely new end-user device category, bridging thin clients and mobile devices to promote BYOD.
Looking like a chunky USB stick, the device can be connected to any MHL or HDMI port on a TV or monitor. Linked to a Bluetooth keyboard and mouse it then gives you an instant, secure window into the cloud. Small enough to put into a pocket or bag it’s ideal for traveling to business presentations and meetings.
No batteries are needed as the device is powered by the MHL port or through a USB connection. It runs Android to allow web browsing and media playback via an integrated dual band Wi-Fi connection.
It's managed through the Dell Wyse Cloud Client Manager software-as-a-service (SaaS). This means IT managers can ensure that each Cloud Connect device is used by the appropriate person with the right permissions and access to apps and content is granted based on their role, department and location.
As well as the obvious application in presentations, Dell suggests that the quick and secure access provided by Wyse Cloud Connect can be used as a low-cost virtual desktop for education, providing access in classrooms, libraries and labs. Other suggested uses include digital signage, kiosks and personal cloud access to online entertainment and gaming.
"Small, smart and secure; Cloud Connect is a disruptive device," says Steve Lalla, vice president and general manager for Dell Cloud Client-Computing. "We unlock new options for our customers to access their data and applications by combining mobility, manageability and security with a powerful user experience at an affordable price-point".
Cloud Connect is available now priced at $129 per unit.
-

Elasticsearch goes commercial with Marvel real-time monitoring
Publié: janvier 28, 2014, 3:02pm CET par Ian Barker

The popular open source analytics platform Elasticsearch aims to help businesses unlock the power of big data.
The company is launching two new products, Elasticsearch ELK which brings together three open source products to create an end-to-end analytics solution, and its first commercial product Marvel, a real-time management and monitoring solution.
Elasticsearch ELK is made up of Elasticsearch, Logstash and Kibana -- three world-class open source projects developed by the company's own engineers. Combined together these products create a full analytic solution, allowing companies to process their data with Elasticsearch, visualize the results using Kibana and manage events and logs with Logstash.
"With the Elasticsearch ELK stack we have brought together three of the most popular open source products and have created an end-to-end solution," says Elasticsearch founder Shay Banon. "Now businesses can get actionable insights instantly without struggling to stitch together solutions from many different vendors. Behind the scenes, it's incredibly complex, but we’ve done the work to make it simple for our users".
Marvel, the company's first commercial product, picks up and visualizes operating data from Elasticsearch’s APIs. It allows administrators to see their systems in action, make instant checks and analyze historical data. Potential issues can be spotted before they become problems and troubleshooting is made quicker and easier.
"Being real-time is critical in the world of customer support," says David Taylor, Senior Operations Engineer at Desk.com, "It is essential that our users' issues are searchable immediately which is why Elasticsearch is such a critical component of our infrastructure. Marvel gives us a way to monitor our Elasticsearch servers in real time so we can stay in control and our users always have a great experience".
Marvel is free during development and production licenses start at $500 a year for five nodes.
Photo Credit: Sergey Nivens / Shutterstock
-

Outleads seeks to optimize telephone marketing with improved analytics
Publié: janvier 23, 2014, 5:25pm CET par Ian Barker

In spite of the rise of internet advertising, telephone sales is still one of the most successful marketing techniques.
Marketing specialist Outleads is launching two new technologies to give businesses more accurate data about their telesales.
"Dynamic Capture and Segment Precision were designed to address a number of issues in online marketing," says Outleads founder Dorin Rosenshine. "Specifically, how do we provide streamlined call-tracking data that captures the full picture of a given marketing campaign, and how do we convert that information into usable subsets that make sense for businesses and help them be more effective with their customer response".
Dynamic Capture uses a tracking system to attach call data to phone numbers making it easier and cheaper to track advertising campaigns. Rosenshine says, "It works with almost any leads management system, tracks off-site phone calls, sends SMS notifications and can import call data to Google AdWords. It's everything a business needs to measure the success of marketing strategies and launch well-directed call-back campaigns".
Segment Precision uses the data gleaned from Dynamic Capture and filters it into Google Analytics. This lets businesses accurately target specific groups and get better returns from their marketing spend.
"Most people think that, because of how prevalent the internet is, telephone marketing has disappeared," says Rosenshine. "When in reality, telephone advertising is still one of the most valuable methods out there. It's human, for one, direct, measurable and provides immediate data. More importantly, though, it fits with the new methods as well. It's still a big part of the marketing landscape, and what Outleads does is integrate it in a way that is both understandable and translatable into targeted sales and advertisements".
Telephone call centers accounted for around $900 billion in sales in 2012 according to figures from ATA Marketing. But caller and visitor data is crucial to their success. Outleads' technology works with existing dashboards as well as allowing the linking together of call, website visit, email and text message data for a complete picture of customer interaction.
More information and a demonstration of the technology is available on the Outleads website.
Photo Credit: Kimberly Hall / Shutterstock
-

Training reduces the risk of socially engineered security breaches
Publié: janvier 23, 2014, 2:33pm CET par Ian Barker

New analysis by security awareness training company KnowBe4 shows, perhaps not surprisingly, that training helps reduce risky online behavior in the workplace.
Carried out over a 12-month period, the study shows that whilst almost 16 percent of employees were prone to click on phishing links initially, this was reduced to 1.28 percent on average after training.
"It is well known amongst IT managers that the weakest link in security is the end user and we sought out a way to effectively address this," says Stu Sjouwerman (pronounced "shower-man"), KnowBe4 founder and CEO. "Nearly 40 percent of these companies are financial entities who typically are more aware and have tighter restrictions and yet were able to see a huge improvement, showing the program works extremely well".
KnowBe4 has teamed up with security expert Kevin Mitnick to launch a security awareness training course. The web-based interactive training uses case-studies, live demonstration videos and short tests. The training specializes in making sure employees understand the mechanisms of spam, phishing, spear-phishing, malware and social engineering.
"The threat posed by malware should not be underestimated, particularly considering that employees have consistently proven to be the weak link in companies' Internet security efforts," says Mitnick. "In most cases, their involvement is unintentional -- they unknowingly allow access to corporate networks simply because they don’t know what to watch out for. That’s why our security awareness training is designed to ensure they understand the mechanisms of spam, phishing, spear-phishing, malware and social engineering, and are able to apply this knowledge on the job. This allows organizations to create a 'human firewall' that actively works to prevent network security breaches".
You can find out more about Kevin Mitnick Security Awareness Training 2014 and see a demonstration of it in action on the KnowBe4 website.
Photo Credit: ra2studio / Shutterstock
-

Google helps companies preserve legal mail trails
Publié: janvier 23, 2014, 12:32pm CET par Ian Barker

Introduced in 2012, Google Apps Vault is designed to manage business-critical information and preserve important data.
It helps safeguard information for continuity, compliance and regulatory purposes and is used by thousands of businesses, schools, and governments. Google has now expanded Apps Vault's capabilities by introducing targeted legal holds.
The introduction of partial domain licensing last year meant that it was possible to save messages for a specific user or business unit. This latest update means that whilst it's still possible to preserve a user's complete mailbox you can also target the specific information that needs to be held for legal reasons. These legal holds can be based on any searchable criteria, including sent date, labels, content or search terms.
Writing on the company's Official Enterprise Blog, Deborah Hsieh, Product Manager, Google Apps Vault says, "Targeted legal holds allow Vault customers to preserve fewer emails and focus on the more relevant messages, helping reduce the costs and risks associated with managing and reviewing data".
By only preserving the messages that may be needed for litigation, investigation costs are reduced as relevant material is easier to find. Vault can be added to an existing Apps account from the admin console, or bought in conjunction with Apps, for $5 per user per month.
Photo Credit: Melpomene / Shutterstock
-

Intel unveils new solutions for education
Publié: janvier 22, 2014, 3:36pm CET par Ian Barker
Intel has used the Bett 2014 educational technology show in London to announce reference designs for the next generation of devices aimed at the education sector.
The Intel Education Tablet and Classmate PC feature student-friendly features along with Intel’s Education Software suite of learning tools.
"Education leaders everywhere are passionate about driving student achievement and encouraging lifelong learning," says John Galvin, vice president of the Sales and Marketing Group at Intel and general manager of the World Ahead Program. "At Intel, we believe the right technology can be transformative. That's why we are focused on designing tools that bring learning to life, helping to make students more engaged. The result is a future where people have the skills they need for opportunity and growth".
The Education Tablet runs Android 4.2 and has what are described as "kid-friendly" features such as rubber bumpers on the sides making it easier for small hands to hold, a power button that resists accidental pushes and a stylus with a pen-like grip. Powered by a dual-core Atom processor it has a 10-inch screen along with front and rear cameras. 3G is optional and it's claimed to have a 12-hour battery life. It also features a plug-in thermal probe to help with science experiments and a snap-on magnifying lens.
The Classmate PC also has a 10-inch screen and is based on the Celeron processor. It runs Windows 8.1, but Windows 7 and Linux versions are expected to be introduced later this year. It has an optional touchscreen and features a rotatable camera to promote content creation. Like the tablet it's ruggedized to withstand dropping from 70cm and is water and dust resistant.
HP is the first to produce a commercial product based on the Classmate reference design. The HP Classmate PC is expected to be available later this month in America, Europe, the Middle east and Africa.
Gus Schmedlen, vice president, PPS Education at HP says, "The HP Classmate notebook helps deliver access to instructional tools, learning apps and education content to students and teachers around the world. Combined with professional development and HP's national education technology planning resources, the HP Classmate can help drive meaningful learning, social and economic outcomes".
Intel's full suite of education solutions are on display on the company’s stand at Bett 2014 which continues until Saturday.
-

Mobile apps will take over the world by 2017
Publié: janvier 22, 2014, 1:31pm CET par Ian Barker

New research by Gartner predicts that over the next few years mobile apps will become the most popular computing tools across the globe.
It says that by 2017 mobile apps will be downloaded more than 268 billion times, generating a revenue of over $77 billion. As a result it predicts that mobile users will provide personalized data streams to more than 100 apps and services every day.
"Mobile apps have become the official channel to drive content and services to consumers. From entertainment content to productivity services, from quantified-self to home automation, there is an app for practically anything a connected consumer may want to achieve," says Brian Blau, research director at Gartner. "This connection to consumer services means users are constantly funneling data through mobile apps. As users continue to adopt and interact with apps, it is their data -- what they say, what they do, where they go -- that is transforming the app interaction paradigm".
Apps provide an opportunity for companies to reach their customers in a direct way which hasn’t been possible in the past. As the use of newer technologies like wearable devices expands Gartner says that apps will become even more important.
"In the next three to four years, apps will no longer be simply confined to smartphones and tablets, but will impact a wider set of devices, from home appliances to cars and wearable devices," says Blau. "By 2017, Gartner predicts that wearable devices will drive 50 percent of total app interactions".
Because they have less opportunity for user input, wearable devices will depend more on apps to provide their functionality. Gartner sees this as a move towards cognizant computing, where the data gathered through the use of the apps and the analytics surrounding it are becoming more important in both volume and value.
Sandy Shen, research director at Gartner says, "Cognizant computing takes intelligent actions on behalf of users based on their historical data, preferences and rules. It can predict user needs and complete tasks without users initiating the action or interfering with the service. It can take the very simplistic format of completing a recurring event such as to turn on the water heater at a preset time, or the more sophisticated format of calling the rescue services and connecting with the doctor when an emergency occurs".
The trend towards apps working in this way will benefit existing companies like Google, Facebook, Amazon and Apple. These big players will have a head start thanks to the amount of data they already hold about their users. This provides them with a platform on which to build the cognizant systems of the future. However, Gartner sees these trends spanning across platforms and brands in order to deliver a richer user experience.
You can read more on Gartner’s predictions for the year ahead on the company's website.
Photo Credit: Angela Waye / Shutterstock
-

PC and Mac games revenue to top $24 billion by 2017
Publié: janvier 21, 2014, 4:46pm CET par Ian Barker

We've been focusing a lot on the decline of the PC hardware market of late, but the software spend still looks strong. The latest survey from market intelligence specialist IDC predicts that PC and Mac gamer spending will grow to over $24 billion by 2017.
It also finds that while global PC/Mac games revenue is set to grow at around four percent a year the US market will start to slip.
This is mainly a result of casual, browser-based games shifting to mobile devices and a drop in the popularity of subscription products like World of Warcraft. IDC says that this change is driven by a rise in living standards in the BRIC (Brazil, Russia, India and China) countries, along with the failure of games consoles to make much headway in emerging economies.
"Other than the casino genre, it's been tough sledding for most casual-leaning PC game genres in the past year," says Lewis Ward, Research Director, Gaming at IDC. "Most of the growth is coming from hardcore-oriented freemium titles such as Tencent's and Riot Games' League of Legends, Valve's Team Fortress 2 and Dota 2, Wargaming.net's World of Tanks, and a handful of Chinese MMORPGs."
The company also forecasts that Valve's Steam service has the opportunity to expand into North American and Western European homes due to the Steam Machines initiative.
"Demand for prepaid digital games should remain stable if not rise at the margins through 2017 partly because key developers, publishers, and platform providers will ramp up their offerings on HDTVs," adds Ward. "The difference between what PCs, consoles, microconsoles, and perhaps even smart TVs will be able to deliver three years from now will be mostly semantic. The platforms that outperform will have great games, a wise mix of business models, an ability to strain key customer insights out of a sea of big data, and offer great a social experience."
Photo Credit: Patricia Malina / Shutterstock
-

Management and employees out of step on IT policies
Publié: janvier 21, 2014, 12:35pm CET par Ian Barker

Email encryption specialist DataMotion has released the results of its second annual survey focusing on email and file transfer habits.
This highlights a wide-ranging communications disconnect between IT management and non-IT employees on security and compliance policies.
Among the statistics to emerge from the survey are that while over 51 percent of IT managers say that free consumer file transfer products were forbidden at their companies, only 24 percent of non-IT workers believe that to be the case.
A similar picture emerges with BYOD. 56.1 percent of IT managers say they have a BYOD policy, yet 74.9 percent of non-IT employees say their company either doesn’t have a policy or are unsure. This is more surprising since over 86 percent of those same organizations say they allow the use of mobile devices for email.
Things are no better when it comes to compliance. Nearly 80 percent of respondents believe that co-workers and employees violate security policies when transferring files electronically. IT managers are offenders here too, with one in five saying they "take risks because we don’t have the resources to be totally compliant". Also almost a quarter admitted to turning off policy-based filtering because it caused problems with false positives.
There are some improvements over last year’s survey, however. 71.7 percent of respondents say they now have email encryption capabilities, a 6.2 percent increase over 2012 survey results. Confidence in compliance has improved too with 48.1 percent feeling "very" confident their company would pass a compliance audit, compared to only 37.5 percent a year ago.
"It’s good to see improvements in security and compliance since last year, but serious problems remain and new ones have cropped up," says DataMotion's Chief Technology Officer, Bob Janacek. "There’s always a demand for new tools such as email on mobile devices -- companies and workers look for better ways to get the job done. The challenge is to provide encryption and filtering tools that are easy for people to use, and dependable so they don't get disabled".
The survey polled more than 400 IT and business decision-makers across the US and Canada. It particularly focused on those in industries which routinely deal with sensitive data and compliance regulations, such as financial services, healthcare and government.
Photo Credit: Nagy-Bagoly Arpad / Shutterstock
-

Latest Saleslogix adds social integration capabilities
Publié: janvier 17, 2014, 4:18pm CET par Ian Barker
It's a rare business package these days that doesn't claim to offer some form of social capability.
With the launch of Saleslogix 8.1, marketing and CRM specialist Swiftpage has added a number of features to help sales staff interact with their customers by displaying their social networking activity within the package.
The new features include a Social Timeline giving a history of customer activity across the most popular social networking platforms. There's also a Social Buzz feature which helps users to better understand their customers' social media preferences and topics of interest, this in turn can be used to create improved interaction strategies and generate more relevant online content. In addition Social Profiles provide a snapshot of each contacts' most-used social media sites and activities, including their LinkedIn profile, integrated into the contact's main overview screen.
"Interacting through social media is now fundamental, but our users are giving us clear feedback that it's becoming too difficult for them to monitor and engage their customers across multiple sites in a concerted way -- especially as the number of social media sites continues to grow," says Lorcan Malone, senior vice president and general manager of the Saleslogix business unit.
The product is customizable so that users can choose to have social media interactions manually or automatically added to customer notes, leads, opportunities, to-do lists, support tickets, or feature-request lists. Anyone with access to the customer's profile then sees a complete record of all interactions which is dynamically updated as they take place. This creates a rich history of knowledge about the customer that can be used to improve all subsequent interactions and which, crucially, stays within the company even if the sales person moves on.
Other improvements in Saleslogix 8.1 include Outlook integration to give easy access to contacts, calendars and documents via an Outlook toolbar. Expanded browser support means that full Saleslogix functionality is available in Chrome, Safari and Firefox so that users are free to work on their preferred platform. There’s improved integration for Sage ERP users too along with a new centralized management interface to make configuration and troubleshooting easier for administrators.
The latest generation of Saleslogix Mobile is included too so that the application can be accessed on smartphones and tablets and users can access priority actions with a single tap.
You can find out more about the latest release and sign up for a free trial at the Saleslogix website. You can also view a demonstration of the mobile version on YouTube.
Photo Credit: Curioso/Shutterstock
-

Rise of the cyber tot -- 4 million British under threes use smartphones or tablets
Publié: janvier 17, 2014, 1:15pm CET par Ian Barker
Almost 3.5 million British children under the age of eight have tablets and nearly 4 million learned to use a smartphone or tablet before they were three.
New research from price comparison and switching service uSwitch reveals a growing nation of cyber tots with 29 percent learning to use a touch screen device before the age of three and 11 percent before they were two.
The study, carried out among more than 1,700 adults in December 2013, shows that parents spent £5.6 billion on gadgets for their kids last year, laying out an average of £462 each. Some 16 percent of parents believe their under 16s are "addicted" to gadgets, with 26 percent saying their kids would be lost without them. More worrying is that 12 percent of kids have run up bills due to in-app purchases.
The trend seems set to continue with 36 percent of parents expecting to spend more on gadgets for their kids in 2014, only a quarter felt they had spent too much last year. The most popular gadget is a games console with 91 percent of parents saying that their kids owned at least one. Parents do seem to be aware of the potential dangers though with 71 percent saying that they limit the hours their children spend using technology.
Ernest Doku, telecoms expert at uSwitch says, "Once the gadget of choice for high-flyers and tech fans, the price of an entry-level tablet is now under £100, making them an attractive -- and affordable -- piece of kit for the whole family. They can also make lessons, homework and bedtime stories both fun and interactive, so it's little wonder that more British parents are caving in to demands from their tech-savvy children. Most tablet-owning parents will probably find their tots commandeer their touchscreen devices anyway".
Whilst recognizing the benefits of tablet use Doku also warns of the dangers, "But parents really do need to keep tabs on what their children get up to online, and lay out some ground rules, or risk having to cover the cost of bills racked up by in-app purchases -- particularly in seemingly 'free-to-play' games. These can usually be disabled or placed behind a PIN within your device's 'settings' menu, ensuring that little ones can enjoy a tablet without causing a big financial headache".
Photo Credit: vesna cvorovic/Shutterstock
-

E-reading on the rise but print books still dominate
Publié: janvier 16, 2014, 5:43pm CET par Ian Barker

New research by the Pew Internet and American Life Project shows that the percentage of American adults who read an e-book in the past year has risen to 28 percent, up from 23 percent in 2012.
Yet the tree book isn't dead yet, at least in the popularity sense, as the results show most e-book readers read print books as well and only four percent are e-only readers.
What's interesting is that, regardless of format, reading remains a popular pastime. In the last year 76 percent of American adults have read a book with the typical reader consuming five. This is a median figure which, the report explains, gives a better picture of behavior than an average -- no, I didn’t pay attention in statistics lessons either.
The report also indicates that e-book reading devices are spreading through the population. The survey, conducted in January, shows that 42 percent of adults now own a tablet (up from 34 percent in September). Ownership of dedicated e-readers like the Kindle and Nook jumped from 24 percent in September to 32 percent after the holidays. To provide some contrast you should note that only four percent owned an e-reader in 2010.
Although tablets and e-readers are the most popular ways to read e-books the survey also shows that computers and cell phones are regularly used too. Use of computers to read e-books has declined since 2011, however.
Looking at the demographics shows that across all formats women read more books than men and 18-29-year-olds read more than other age groups, though this could have something to do with the numbers still in education.
You can read the full report on the Pew Internet and American Life Project website. If you’d rather read a good book my publisher would like me to point out that my latest novel One Hot Summer is available in both e-book and print formats, thank you.
Photo Credit: Fineart1 / Shutterstock
-

Redis Cloud becomes available on SoftLayer
Publié: janvier 16, 2014, 4:59pm CET par Ian Barker

Garantia Data has announced the availability of its Redis Cloud product in the IBM-owned SoftLayer infrastructure as a service (IaaS) platform.
IBM only acquired SoftLayer around six months ago but Big Blue seems keen to strike deals to make its cloud platform competitive with rival offerings from Microsoft and Amazon.
Redis -- in case you didn't know -- is an open source data store that runs entirely from RAM. This makes it very fast and a top choice amongst developers creating cloud applications. Redis Cloud takes away many of the configuration issues associated with "do-it-yourself" Redis setups, ensuring high availability, and easier scaling and failure recovery.
Itamar Haber, Vice President of Developer Advocacy at Garantia Data writing on the IBM cloud blog says, "...open source Redis setups that are installed on virtual servers or bare metal resources work great when they’re small or if you have expert resources who can attend to and manage your Redis datasets, but developers who take this approach often encounter daunting challenges with negotiating scaling barriers..."
Garantia says that its product gets around these problems and delivers infinite scalability along with zero management with no need to waste time dealing with nodes, clusters, or any type of administration.
Mac Devine, CTO of the IBM Cloud Services Division and director of cloud innovation, says, "Developers demand high performance computing power and speed from the cloud. With the addition of Redis Cloud, the leading managed Redis solution on SoftLayer’s cloud platform, developers will benefit from unmatched infrastructure and Garantia Data’s enterprise-class Redis so they can build scalable, highly available, and top performing apps".
That IBM is serious about this market is underlined by the product's pricing, which at $79 per month for 1GB of storage is much cheaper than Microsoft Azure's $108 per month for the same volume of data.
Photo Credit: everything possible / Shutterstock
-

Smartphones improve the shopping experience
Publié: janvier 16, 2014, 12:28pm CET par Ian Barker
 If you shop using your smartphone you are highly informed, social and seeking a superior shopping experience -- and retailers want to have your babies.
If you shop using your smartphone you are highly informed, social and seeking a superior shopping experience -- and retailers want to have your babies.These (apart from the last bit) are the findings of the latest research by IDC which found that surveyed respondents believe the smartphone is transforming their shopping experience.
Of those responding to the survey, 69 percent agreed with the statement, "My smartphone is a critical tool that allows me to have a better shopping experience," compared to only 12 percent who disagreed. In addition, 70 percent agreed with the statement, "I plan to use my smartphone more to help my shopping experience in the coming year" compared to only 11 percent of respondents who disagreed.
The results show that smartphones allow people to be better informed and more confident in their shopping decisions. 70 percent of respondents said they checked prices using their phones and 50 percent also check reviews.
This provides a challenge to traditional stores as one in five respondents bought from a competitor whilst they were shopping in a retail store. One in three also said they'd bought much more online than in retail stores this year.
In addition to the survey, IDC analyzed app and mobile Web activity of over 10,000 smartphone users during the holiday shopping season. The results show that Amazon dominated the retailers, with far more consumers accessing its app, mobile website, or both, than any other retailer. Traditional brick and mortar retailers lag well behind Amazon when analyzing smartphone users’ visiting a brand’s mobile site or using its app.
"The smartphone is at the center of our lives, with most of us unable to be without it for even a couple of hours. By combining the insights from both the survey and mobile behavioral data, it is clear that, for a significant number of us, the smartphone is now also a critical shopping tool, our own personal concierge to help us shop intelligently," says Allan Fromen, Vice President and Consulting Partner for IDC's global Buyer Behavior Practice.
You can see an overview of the report's findings in infographic format below.

-

AV-Comparatives names Kaspersky as Product of the Year
Publié: janvier 15, 2014, 6:01pm CET par Ian Barker

Independent testing organization AV-Comparatives has released its Anti-Virus Comparative Summary Report 2013.
This rounds up the results of the company's tests carried out over the past year on 22 consumer antivirus and internet security products.
Kaspersky Internet Security gets the company's Product of the Year Award, with Bitdefender as runner up. Seven other products, including a free program from Avast, received "Top Rated" designations. The researchers found Kaspersky's interface easy to use and were impressed by its additional functionality including hybrid protection from the cloud as well as on the device itself.
The other top rated products came from Avast, Avira, Bitdefender, BullGuard, ESET, Fortinet and F-Secure. Emsisoft Antimalware is given special recognition for achieving the Silver Award in the Real-World Protection Test in only its first year of testing.
Although it picks out these products as winners the report advises buyers, "If you plan to buy an anti-virus program, please visit the vendor’s website and evaluate their software by downloading a trial version, as there are many features and important considerations (e.g. compatibility, graphical user interface, ease of use, price, support etc) that you should evaluate for yourself." A checklist of key features is included as a table in the report.
You can read the full report as a PDF on the AV-Comparatives website. This includes reviews of all the winners and breaks down the results by different categories including false positives, malware removal and system impact.
-

New Oracle Retail Suite aims to improve the shopping experience
Publié: janvier 13, 2014, 2:47pm CET par Ian Barker
The internet has changed the way we shop. Even if you don't buy online you’re likely to check prices before hitting the stores or use click and collect services to ensure what you want is in stock.
With its latest Retail Suite Oracle allows retailers to respond to these trends and remove the boundaries between the different supply channels.
New features and functionality in Oracle Retail version 14 make it easier for customers to buy items no matter where the stock is located. Store-level inventory can be made visible online, plus there's real-time inventory look up for items in other stores along with support for orders and take-with items in the same transaction. Customers can buy and pick up items from any channel. There's also support for returning purchases regardless of the channel they were bought from.
It makes life easier for developers too with rich APIs and the ability to accommodate modular development over an evolving mix of systems.
The new release offers enhanced support for mobile devices. It can help store staff with mobile point of sale devices, tablets and assisted promotions. Retail Suite also ensures better visibility of promotions and can drive in-store merchandising and dashboards.
"In the global retail industry we have seen a shift of capital from building and refurbishing stores to digital commerce and creating new and differentiated customer interactions. Retailers are focused on enabling the whole retail enterprise to deliver commerce anywhere," says Mike Webster, Senior Vice President and General Manager of Oracle Retail.
Oracle Retail can be implemented as a complete suite or in modular form, making it scalable for different sizes of business. Oracle has sought to simplify development in order to maximize return on investment and help lower cost of ownership. An improved dashboard system means retailers can quickly identify transaction volumes, average response times, and errors to help ensure critical systems are operating at maximum efficiency.
You can find out more about Oracle Retail 14 on the company's website.
Photo Credit: Pressmaster / Shutterstock
-

Consumer mobile apps won’t make you money
Publié: janvier 13, 2014, 11:43am CET par Ian Barker

If you're looking to the earnings from your innovative mobile app to keep you in your retirement, you may need to think again.
A new report by Gartner predicts that through 2018 fewer than one percent of consumer mobile apps will be considered a financial success.
"The vast number of mobile apps may imply that mobile is a new revenue stream that will bring riches to many," says Ken Dulaney, vice president and distinguished analyst at Gartner. "However, our analysis shows that most mobile applications are not generating profits and that many mobile apps are not designed to generate revenue, but rather are used to build brand recognition and product awareness or are just for fun. Application designers who do not recognize this may find profits elusive".
With millions of developers and hundreds of development platforms Dulaney describes the mobile app market as "hyperactive." Also the number of good free apps available sets the bar high when it comes to expecting consumers to pay for something.
Gartner forecasts that by 2017 94.5 percent of downloads will be for free apps. Dulaney adds, "Furthermore, of paid applications, about 90 percent are downloaded less than 500 times per day and make less than $1,250 a day. This is only going to get worse in the future when there will be even greater competition, especially in successful markets".
Other cheery predictions in Gartner's report are that by 2016 some 20 percent of BYOD deployments will fail due to businesses having overly restrictive device management policies. It also sees employees becoming increasingly aware that IT organizations may be able to access their personal devices and demanding more separation between business and personal applications.
The browser is predicted to be more commonly used as an application delivery system too, with HTML 5 and complex JavaScript applications. This will allow developers to offer platform-neutral products but Gartner identifies risks like performance and fragmentation. It warns that developers need to be aware of vendors trying to lock them into platform-specific browser features too.
Dulaney says, "Although more than 100 'platform independent' development tools exist, most involve technical or commercial compromises, such as lock-in to relatively niche technologies and small vendors. This will drive increasing interest in HTML5 as a somewhat-standardized, widely available, platform-neutral delivery technology".
The full report Gartner Predicts 2014 is available from the company’s website.
Photo Credit: 3DStock / Shutterstock
-

Free resource aims to streamline the way companies source mobile developers
Publié: janvier 10, 2014, 11:49pm CET par Ian Barker
Businesses are usually keen to adopt mobile technology but often struggle when it comes to finding a developer to translate their vision into reality.
Mobile strategy and solutions company Mokriya is trying to help by launching MobileInsights, a series of free guides aimed at streamlining the way businesses recruit mobile development firms.
The initial guide is the 50-page, "Creating a Compelling Mobile Experience, A How-To Guide for Choosing the Right Team" which focuses on the project leader's viewpoint. It includes detailed charts to help managers pick the right platform for their app along with questions to ask prospective developers. The aim is to create more guides over time to build into a detailed online resource for anyone looking to develop a mobile app.
"App development is driving the surge in smart device usage," says Mokriya founder Sunil Kanderi, "apps are the reason people want smartphones. They're the ideas that are pushing the whole industry forward. But having a good idea isn’t enough. The execution is ultimately what will determine if an app reaches that critical threshold, or gets lost in all the other products flooding the market."
With more than a billion smartphones already in use worldwide the potential for companies who get their apps right is huge. But as Kanderi says, "The user experience is what distinguishes the apps that prosper from the ones that drop off. Our research tells us that 57-percent of users won’t recommend an app they feel is poorly designed, and 40-percent of users will switch to something else entirely. What we're seeing is a shift in thinking. Users will no longer put up with an App that’s hard to use."
You can view the full guide and stay in touch with future releases on the Mokriya website.
Photo Credit: Rashevskyi Viacheslav / Shutterstock
-

Lenovo takes the lead in (still) shrinking PC market
Publié: janvier 10, 2014, 4:58pm CET par Ian Barker

For most of the last year it seems that we've been reporting the decline of the PC market. At the beginning of December we even had IDC saying that shipments had seen their greatest decline ever.
No surprise then that on the figures for the final quarter of 2013 both IDC and Gartner are saying that shipments have declined again. The good news though is that there are signs of the decline bottoming out.
The even better news, if you're Lenovo, is that the company has consolidated its place ahead of HP as the biggest player, with around 15 million devices shipped worldwide in the fourth quarter. On IDC's figures Lenovo now has an 18.6 percent market share, ahead of HP’s 16.8 with Dell in third on 12.2 percent. Gartner is a little more conservative but its figures support the same general picture.
"The PC market again came in very close to expectations, but unfortunately failed to significantly change the trajectory of growth," says Loren Loverde, Vice President, Worldwide PC Trackers at IDC. "Total shipments have now declined for seven consecutive quarters, and even the holiday shopping season was unable to inspire a turn in consumer spending. Although US growth slipped a little in the fourth quarter, other regions all improved, reinforcing our view that growth rates will continue to improve gradually during 2014 despite remaining in negative territory".
Gartner too believes that the decline is reaching the bottom. "Although PC shipments continued to decline in the worldwide market in the fourth quarter, we increasingly believe markets, such as the US, have bottomed out as the adjustment to the installed base slows," says Mikako Kitagawa, principal analyst. "Strong growth in tablets continued to negatively impact PC growth in emerging markets. In emerging markets, the first connected device for consumers is most likely a smartphone, and their first computing device is a tablet. As a result, the adoption of PCs in emerging markets will be slower as consumers skip PCs for tablets".
iChartsBreaking the figures down by region, in the US HP continues to be the dominant player, followed by Dell, with Lenovo in fourth place behind Apple. However, in the fourth quarter HP posted a 10.3 percent decline in shipments whilst the other three grew, Apple by an impressive 28.5 percent.
"Holiday sales of technology products were strong in the US market, but consumer spending during the holidays did not come back to PCs as tablets were one of the hottest holiday items," says Gartner's Ms Kitagawa.
In the EMEA (Europe, Middle East and Africa) region Lenovo is on top and the only company to post a growth (albeit only 2.1 percent) in unit shipments. The Asia/Pacific region showed a decline too with buyers preferring to spend their money on smartphones and tablets.
IDC reports Japan separately and says that volume was higher than expected thanks to favorable exchange rates and XP migration. Shipments in the rest of Asia/Pacific, it says, were close to expectations though with unexpected weak spots in India and Thailand.
Have PC's reached the bottom or are there further falls still to come? Watch this space as we move into 2014.
Photo Credit: ArchMan/Shutterstock
-

Banks urged to improve security as the financial malware arms race heats up
Publié: janvier 10, 2014, 11:40am CET par Ian Barker

Since the first personal computer viruses appeared in the 1980s, avoiding malware has become a fact of everyday life for computer users. There's a constant battle to stay ahead of the game and fend off the Trojans and botnets.
Where the conflict is at its fiercest though is in the financial sector as this is where malware has the potential to earn its authors serious money.
A new report by NSS Labs looks at the latest trends in financial malware and the dangers that it poses. Unveiled by Research Vice President Ken Baylor, it reveals a great deal of innovation has taken place since NSS released its last report on this sector in the first quarter of last year.
New suites of malware including Hesperbot and Beta Bot have emerged, and newer bots are using SSL to encrypt communication with their command and control (C2) servers. There has also been a switch to using seemingly innocuous blog sites, rather than traditional C2 servers, to communicate with botnet malware like Taidoor. This makes it much harder to detect the malware's presence on networks.
Another worrying trend is the emergence of a self-propagating version of Zeus, the man-in-the-browser malware aimed at socially engineering users to give up their login credentials. The geographical pattern of emerging malware is shifting too. There’s a growing trend towards new threats appearing in Europe first then spreading to US banks and account holders.
In order to combat these threats NSS recommends that banks need to carry out regular risk assessments. They must also implement effective multi-layer security at customer, account and risk detection levels. It also says that banks need to invest in the latest anti-fraud risk engines in order to detect anomalies between customers’ historical transactions and those currently taking place.
For more information, including a more detailed analysis of the latest financial malware threats, you can download the full report from the NSS site.
Photo Credit: Fabio Berti / Shutterstock
-

IBM creates new business unit for Watson supercomputer
Publié: janvier 9, 2014, 1:25pm CET par Ian Barker

Technology giant IBM has announced that it's to invest more than $1 billion to create a new business unit for Watson, the supercomputer that beat human contestants on the TV quiz Jeopardy.
The new Watson Group will be headed by Michael Rhodin, previously senior vice president of the company’s software solutions group. The unit will be based in New York and have around 2,000 employees.
Rhodin says, "IBM has transformed Watson from a quiz-show winner, into a commercial cognitive computing breakthrough that is helping businesses engage customers, healthcare organizations personalize patient care, and entrepreneurs build businesses. Watson is one of the most significant innovations in IBM's 100 year history, and one that we want to share with the world. With these investments we strive to make new markets, reach new buyers and transform industries and professions".
Watson -- named after former IBM president Thomas Watson -- is an artificial intelligence system that aims to use information in a similar way to human thinking. It uses natural language and analytic capabilities to allow it to quickly interpret large volumes of data.
From its original room-sized unit IBM says it has now managed to shrink Watson to the size of three stacked pizza boxes. The new group will deliver Watson's technology via the cloud to power new consumer and enterprise apps. It will be deployed using Softlayer, the cloud computing infrastructure business bought by IBM last year.
The establishment of the unit reflects strong demand for cognitive computing. "We have reached the inflection point where the interest is overwhelming and we recognized we need to move faster," says Stephen Gold, vice president of Watson Business.
In addition to the business unit IBM is launching three new services based on Watson technology. Watson Discovery Advisor is aimed at research organizations, Watson Analytics allows users to explore big data through visual interpretations, and Watson Explorer is designed to help employees across a business uncover data-driven insights more quickly.
You can learn more about Watson and how it's being used in different industries on the IBM website.
Photo Credit: Jon Simon/Feature Photo Service for IBM
-

Malware introduced by employees a major concern for business
Publié: janvier 9, 2014, 12:02pm CET par Ian Barker
 A new study from Osterman Research finds that malware is still one of the main security concerns for businesses.
A new study from Osterman Research finds that malware is still one of the main security concerns for businesses.The survey, sponsored by security specialist Trustwave, asked 160 security professionals about email, web and social media threats. It finds that employees were the number one reason for concern when it comes to introducing malware to enterprise systems.
According to 58 percent of respondents the biggest concern is malware being introduced by employees surfing the web. The second biggest malware threat (56 percent) was seen as employees using personal webmail.
These concerns seem to be borne out in practice, with 74 percent of respondents saying that their networks had been infiltrated by malware from surfing in the last year, with 64 percent infiltrated via email.
The infographic below shows findings from the latest report -- which is available from the Osterman site -- combined with statistics from an Osterman white paper and the 2013 Trustwave Global Security Report.
Photo Credit: Lightspring/Shutterstock
-

If you can measure IT you can make IT better
Publié: janvier 8, 2014, 4:25pm CET par Ian Barker

According to a study by New York-based risk management specialist Continuity Software, measurement and analysis is the key to achieving IT excellence.
Based on results from a number of sectors including healthcare, financial services, manufacturing and retail, the study underlines the importance of operational analytics in meeting performance targets.
As you might imagine the findings are all about size and performance -- stop making up your own jokes at the back! It's larger organizations that are most likely to use analytical tools to monitor IT performance goals -- 57 percent, as opposed to 29 percent of smaller enterprises. What they measure is interesting too, 89 percent measuring up time, 66 percent performance and 51 percent measuring the number of open issues.
There's more consistency when it comes to the different areas of infrastructure. Storage and network performance indicators are measured by 71 percent of those surveyed with applications a close second on 69 percent, databases on 66 and clusters on 49 percent.
The effectiveness of regular analysis is shown by the fact that 53 percent of companies that track configuration across their entire infrastructure daily said they were meeting or exceeding their goals. This compares to only 31-33 percent of those that monitor only part of their setup.
"Few would argue that business organizations that deliver IT operational excellence enjoy a distinct advantage over their competitors," says Doron Pinhas, CTO of Continuity Software. "As this survey reveals, organizations that are successful in achieving this goal invest in measurement and analysis of KPIs and are able to transform the collected insights into immediate actions".
The cloud seems to be getting neglected in all of this though with only 14 percent saying that they regularly monitor cloud KPIs. 43 percent of those surveyed say they never analyze configuration consistency in their cloud environment.
Pinhas comments, "It is also interesting to note that while the push to move data and applications into the cloud continues to escalate, most cloud infrastructure remains under-monitored, and consequently at great risk of unplanned downtime and service disruption".
The full report is available to download from the Continuity Software website.
Photo Credit: Bogdan Brasoveanu / Shutterstock
-

McAfee name set to disappear in Intel rebranding
Publié: janvier 7, 2014, 3:03pm CET par Ian Barker

Yesterday's speech at CES by Intel CEO Brian Krzanich contained lots of stuff about plans for wearable technology and computers housed in SD card form factors.
But also in there was the announcement of a new Intel Security brand and the news that McAfee products will transition to this over time. Krzanich also says that Intel is planning to offer some elements of McAfee security products free of charge to protect the latest mobile devices.
Back in 2010 the chip giant paid $7.68 billion for McAfee, one of the best known names in information security. Since then it has operated as a subsidiary whilst retaining its brand identity. Now it seems that the McAfee name is to be dropped, though the familiar red shield logo will be retained.
"The complexity of keeping digital identities safe grows as mobile applications and devices become a more important part of our daily lives," Krzanich says. "Intel's intent is to intensify our efforts dedicated to making the digital world more secure, and staying ahead of threats to private information on mobile and wearable devices".
Details of the free protection solutions for mobile devices will be announced later this year. BYOD is also in the company's sights as Krzanich announced that Intel Security this year will offer "Intel Device Protection" technology, aimed at helping Intel-based Android mobile devices meet security standards for use at home and work.
The decision to drop a big-name brand that you've paid a lot of money for seems a bit strange. It may have to do with the security company's founder John McAfee. Although he hasn't been involved with the company since 1994, he has become a magnet for publicity. This has included his alleged involvement in a murder in Belize and his bizarre laptop-shooting video guide to uninstalling McAfee Antivirus. He's currently trying to sell his life story.
Speaking to BBC News, John McAfee seemed pleased with Intel's decision, "I am now everlastingly grateful to Intel for freeing me from this terrible association with the worst software on the planet. These are not my words, but the words of millions of irate users. My elation at Intel's decision is beyond words".
Photo Credit: Maksim Kabakou / Shutterstock
-

Sony VAIO goes flipping smaller
Publié: janvier 7, 2014, 1:01pm CET par Ian Barker

Sony’s VAIO | Flip range of convertible laptop/tablet hybrids launched back in October last year. This week the company uses CES to release a new, smaller 11-inch model for users who want maximum portability.
The Flip uses a clever three-way design which means it can be used as a laptop, a tablet or in 'Viewer Mode' which basically props the screen up on a stand that's built into the chassis.
The VAIO Fit 11A weighs only 2.82 pounds, has a solid state drive, quad-core Intel Pentium CPU and an 8MP rear-facing camera. It also features Sony's Triluminos display technology along with ClearAudio+ to provide what Sony says will be a top of the line movie viewing experience.
It also comes equipped with the pressure-sensitive VAIO Active Pen allowing you to take notes or doodle on the screen. If you'd rather type the keyboard is backlit -- a feature not often seen on smaller systems -- so you can use it in the dark. The aluminum chassis comes in a choice of silver, black or pink and the VAIO Fit 11A will be available from the end of February with a starting price of $799.
The rest of the VAIO | Flip lineup gets updated for spring too, with Windows 8.1 and all models now coming with Adobe Photoshop Elements 12 pre-installed. Visit Sony's website for more news.
-

Android set to pass the billion user mark as device shipments grow in 2014
Publié: janvier 7, 2014, 11:37am CET par Ian Barker
A new market forecast by research specialist Gartner predicts that device shipments (that's PCs, tablets, ultramobiles and mobile phones -- no toasters or coffee makers) will reach 2.5 billion units in 2014, up 7.6 percent from last year.
It also sees Android passing the one billion user mark across all devices this year, with 75 percent of Android volume coming from emerging markets by 2017.
It's mobile phones that are expected to dominate device sales this year with 1.9 billion being shipped, up five percent from 2013. Ultramobiles including tablets, hybrids and clamshells are predicted to show the fastest growth though with an increase of 54 percent.
"The device market continues to evolve, with buyers deciding which combination of devices is required to meet their wants and needs. Mobile phones are a must have and will continue to grow but at a slower pace, with opportunities moving away from the top-end premium devices to mid-end basic products," according to Ranjit Atwal, research director at Gartner. "Meanwhile users continue to move away from the traditional PC (notebooks and desk-based) as it becomes more of a shared content creation tool, while the greater flexibility of tablets, hybrids and lighter notebooks address users' increasingly different demands".
Gartner expects the worldwide tablet market to grow by 47 percent as lower average prices attract new customers. It sees tablets as being an additional device that consumers will carry everywhere but predicts this will see a move to smaller units. "Complementary smaller tablets will take over from the larger tablet form factors, providing the added mobility that consumers desire at a lower cost and will compete with hybrids for consumer attention," says Mr Atwal. Gartner's own consumer survey in the third quarter of last year showed that over two-thirds of tablets are used outside the home.
Meantime shipments of traditional PCs are set to continue their decline. Gartner predicts a seven percent drop over last year to 278 million units. Thanks to the growth in Windows ultramobiles though the overall PC market is predicted to stay flat after a 2013 decline of almost 10 percent.
In the operating system market Android will continue to dominate with Windows a distant second and iOS/Mac OS third. Annette Zimmerman, principal analyst at Gartner says, "There is no doubt that there is a volume versus value equation, with Android users also purchasing lower-cost devices compared to Apple users. Android holds the largest number of installed-base devices, with 1.9 billion in use in 2014, compared with 682 million iOS/Mac OS installed-base devices".
The full report, Forecast: PCs, Ultramobiles, and Mobile Phones, Worldwide, 2010-2017, 4Q13 Update is available on Gartner’s website.
Photo Credit: bloomua / Shutterstock
-

Pure delivers wireless streaming from any service
Publié: janvier 6, 2014, 3:57pm CET par Ian Barker
Wireless speakers allow an enormous amount of freedom when listening to music around the home. But when you want to stream from online sources you'll often find that you're restricted to ones that are compatible with your system.
Audio specialist Pure using CES to announce an extension to its Pure Connect platform which allows its Jongo wireless stereo and multiroom music system to be used with any music streaming service including Pandora, Rdio, Deezer and Spotify, as well as any other audio or radio app.
Nick Hucker, Pure's marketing director says, "We are not in the business of picking a winning music streaming service or radio app -- different services are right for different audiences -- but we want to give our customers the most choice. Jongo was designed with flexibility in mind, which is why all Jongo speakers come with both Bluetooth and Wi-Fi. We've always used this flexibility to make sure all services can be played to a single Jongo speaker but now we are making the major step of extending this flexibility, via Bluetooth, to enable streaming of any music service or radio app to multiple Jongo speakers".
It uses a technology called "Caskeid" -- developed by Pure's parent company Imagination Technologies -- to seamlessly deliver content to multiple speakers via a combination of Bluetooth and Wi-Fi. To use it you simply select your chosen music or radio service app and send it via Bluetooth to a single Jongo speaker in a group. The Caskeid technology integrated into the speakers then takes care of ensuring that music is seamlessly and synchronously sent to all the other speakers in the group.
The company has also announced that it will be releasing a Caskeid application developer kit that will allow apps to be built with support for Jongo speakers.
The session and speaker configuration is set up using the Pure Connect App. This is available for free on Android and iOS systems and allows you to stream your own music or online radio. There are also subscription models for streaming via Pure's own online service, more information is available via the Pure Connect portal.
-

HP puts Android on the business desktop
Publié: janvier 6, 2014, 11:11am CET par Ian Barker

All-in-one PCs are popular in the office and in customer-facing environments because they’re stylish and take up less space than conventional models.
HP has been an active player in this field for a while and has now updated its range of all-in-one (AiO) models with four new systems including -- for the first time -- one that runs Android.
The Slate 21 Pro AiO provides a desktop that integrates seamlessly with Android phones and tablets using autosyncing and Google Cloud Services. It features a 21.5-inch touchscreen, a Tegra 4 quad-core CPU, dual-band wireless, Bluetooth and an integrated HD webcam. It runs Android 4.3 and uses Citrix Receiver to offer Windows application support. It also allows users to toggle between the Android environment and content displayed from a Windows PC.
The Slate 21 Pro satisfies the demands of enterprise security by having Citrix XenMobile pre-installed to allow administrators to manage apps and users within the corporate environment. It's available now in the US with a starting price of $399 including a keyboard and mouse.
"HP's multi-OS approach showcases our innovation and allows us to deliver the right product for our customers' needs, giving them all the flexibility and ease of use they need from a business PC," says Enrique Lores, HP's senior vice president and general manager, Commercial PCs. "The HP AiO PCs announced today highlight how businesses of any size can increase employee productivity by leveraging the growing Android ecosystem, all while being budget friendly".
HP's announcement also includes three new Windows-based systems. The 205 AiO is aimed at smaller businesses, with an 18.5-inch screen, AMD E-Series dual-core processor, built-in Wi-Fi and webcam. Prices start from $449.
The HP ProOne 400 AiO G1 comes in 19.5-inch non-touch or 21.5-inch touchscreen versions. HP says that this model is designed to offer a rich video and audio conferencing experience, with integrated Skype-ready webcam, business class speakers and integrated DTS Sound+ audio software. It also features a Display Port to drive an external monitor and an integrated Wi-Fi hotspot to allow people to connect smartphones and tablets. Running the latest Intel Core processors, the non-touch ProOne starts at $649 with the touch version available from $799.
Finally the Z1 G2 is a second-generation model of HP's 27-inch AiO workstation, using Intel Thunderbolt 2 technology for fast performance and touchscreen capability. No prices for this model were available at launch though you can expect it to start around the $2500 mark of the Z1.
-

Why I’m not making tech resolutions for 2014 [Ian]
Publié: décembre 30, 2013, 5:11pm CET par Ian Barker

You'll have noticed by now that my colleagues here are all busy promising to clean up their tech acts for the coming year. But I'm not going to do that.
I don't generally make resolutions anyhow -- it saves having to come up with excuses later -- so instead here's what I won’t be changing in 2014.
My Backup Regime
Among my colleague Mark Wilson's resolutions is a commitment to improve his backup routine. But I've spent too long working in tech support and have rebuilt too many systems to think it won't happen to me, so I'm already a mild obsessive where backups are concerned. Anything I'm currently working on is saved to the cloud and synced between two machines for good measure, and everything else is saved to an external hard drive every couple of weeks. I've even been known to backup my phone contacts.
Not Owning a Tablet
I get sent tablets to review from time to time and they're fun for a while but I haven’t -- yet -- felt the need to actually own one. I can see that they're handy if you want to tweet along to your favorite TV show or you need to look things up really quickly, but that's the problem. I don't really need non-essential information that fast and if I had access to a tablet all the time I'd just spend more hours online and have less of a life.
This is rather like Mihaita's resolution to disconnect more, I'm just trying to avoid another excuse to connect in the first place. There's little doubt that I’ll crack and end up owning a tablet at some point but so far I'm resisting the tide.
Not Buying Software
Easy for you, you may be thinking, given that I'm in a position to request review copies, but most of the programs I use on a day-to-day basis are freeware. I'm writing this post using LibreOffice, I edit images in Paint.NET, I use a free backup program and a free password manager. I have a tendency to avoid big names even when they are free, I long since dumped the bloated Adobe Reader in favor of a lighter, faster alternative. In fact there are only two paid-for programs on this PC, one for web design -- which is several years old -- and one for creating invoices.
Sadly this commitment doesn't extend to desktop operating systems, I gave up on Linux a long time ago. It's great when it works but far too frustrating when it doesn't, so I'll stick to Windows thanks.
Those then are my non-resolutions for 2014, if you see me buying a tablet sometime in the next year feel free to point and sneer. What about you though? Are you planning on making tech resolutions for next year or are you too going against the flow? Let me know via the comments.
Photo Credit: Thinglass/Shutterstock
-

The collapse of the internet and other things to look forward to in 2014
Publié: décembre 30, 2013, 3:59pm CET par Ian Barker

It's inevitable that at this time of year tech companies and analysts like to try to grab headlines with their predictions for the coming 12 months. Security specialist Kaspersky Lab is no exception, and guaranteed to make waves is its forecast of the collapse of the internet as we know it.
This, it says, will be driven by pressure to break the web up into national segments. So far this has only applied to counties like China with its Great Firewall, but other nations including Russia have planned legislation to prohibit the use of foreign services. In November, Germany announced that all communications between the German authorities would be fully locked within the country. Brazil too has announced its plans to build an alternative internet channel so as not to use the one that goes through Florida.
Alex Gostev, Chief Security Expert at Kaspersky Lab says, "The Internet has begun to break up into national segments. Snowden's revelations have intensified the demand for rules prohibiting the use of foreign services. Individual countries are no longer willing to let a single byte of information out of their networks. These aspirations will grow ever stronger and legislative restrictions will inevitably transform into technical prohibitions. The next step will most likely be attempts to limit foreign access to data inside a country. As this trend develops further it may lead at some point to the collapse of the current Internet, which will break into dozens of national networks. The shadowy Darknet then will be the only truly world-wide web".
Other things to emerge from Kaspersky's crystal ball gazing are that Bitcoin users can expect to see more attacks targeting their wallets. Bitcoin theft promises cyber-criminals big profits and complete anonymity so attacks aimed at the currency's exchanges are likely to become more common.
We can expect ransomware to spread to the smartphone arena too. Encryption of data on smartphones is easy if the trojan program has administrator rights and Kaspersky predicts this type of attack will appear on Android devices first. It also expects mobile phishing attacks to increase in sophistication and to see an increasing underground market in mobile botnets.
Tough times for the cloud are on the horizon too according to the report. Partly because confidence has been hit by the Snowden revelations and partly because the type of data now being committed to the cloud is more attractive to criminals. Hackers are targeting cloud service employees as the weak link in a chain that could give them access to huge volumes of potentially valuable data.
If you weren't depressed about 2014 already you probably are now, but there are some more positive notes. Kaspersky foresees greater popularity of VPN services and TOR-anonymizers in addition to a greater demand for local encryption tools as people become more aware of protecting their privacy.
It also predicts the rise of a new breed of "cyber-mercenaries". Experienced hackers who will offer their services to companies in order to combat cyber-espionage and other threats.
You can read more about what Kaspersky thinks is in store for 2014 on the company's blog.
Photo Credit: Fotonium/Shutterstock
-

My favorite tech products of 2013 [Ian]
Publié: décembre 27, 2013, 6:26pm CET par Ian Barker

Being slightly late to the party when it comes to posting my list of favorite tech kit for this year means you'll probably have seen some of these things on other people's lists too -- blame spending Christmas in an internet free zone.
But hey, this is very much a personal thing, so these are my particular selections and the reasons why I've chosen them.
Windows 8.1
An obvious choice perhaps, but although the much heralded "return of the son of the Start button" turned out to be rather a disappointment, the update transforms Windows 8 into the system it really should have been in the first place.
The new Apps page makes managing the Start screen and your installed software much more manageable. Add in the revamped store which means there are many more Windows apps available and it’s now an OS you can use everyday without feeling that there’s just a little something missing. In other words 8.1 feels like a complete and well thought out product, a trick which Windows 8 -- good though it was -- never quite managed.
The FUZE

Although it's aimed at teaching youngsters about the joys of programming, the FUZE also happens to be really good fun. It turns the Raspberry Pi into a system that you can just plug in and start using without the need for any extras other than a monitor.
Because it comes with a number of projects it's easy to begin doing practical stuff right from the start. It's also a system that you won't quickly outgrow as your knowledge improves since new projects are released on a regular basis. The best thing about the FUZE though is simply that it makes learning fun and that’s what educational tools should do.
Microsoft Office 2013
The cloud has been one of major themes of the last year particularly for business users. With the launch of Office 2013 in January Microsoft didn't just embrace this trend but went down on one knee and slipped a ring on its finger. Smooth integration with Office 365 and SkyDrive is the most impressive feature of the latest Office suite but there are plenty of other tweaks too including a flatter look for the love it or hate it ribbon toolbar. There are also features which Office should have had a long time ago, like the ability to create PDFs. There's a reason why the Office division accounts for around half of Microsoft's operating profit and that’s because it gives people what they want.
HP ENVY 120

What's a printer doing here? Good question, the problem with printers is usually that they're ugly brutes with paper trays and feed chutes that stick out at all angles. That might be acceptable in the office but for home use a printer is generally something you want to hide away. With the ENVY, traditional old HP has managed to pull off the trick of making a printer that's actually bordering on being sexy. It could easily be part of an expensive hi-fi system. It's not bad at the business of printing and scanning either. If you’re looking for a printer that won't feel out of place in your trendy apartment the ENVY is an obvious choice.
Samsung Chromebook
The first generation of Chromebooks were always a little underwhelming, mainly because the Chrome OS was too limiting in what it could do, especially if you didn't have an internet connection. With the latest versions it's now possible to cache files so that you can work offline if you need to and there's added practicality from little app-style utilities.

Put all of this together with Samsung’s affordable, slimline, lightweight hardware and you have a machine that's hard to beat as a general purpose portable. Okay, so the processor performance may be a little modest but it gives you more practicality for work on the go than a tablet with none of the bulk of a power-user laptop. Add a long battery life and an affordable price tag and what’s not to like?
Agree with these choices, disagree? Let us know in the comments or tell us what your favorite tech of this year is.
Photo Credit: lucadp/Shutterstock
-

IBM buys Aspera to speed up movement of big data
Publié: décembre 23, 2013, 11:28am CET par Ian Barker
 One of the problems with big data is its sheer size. This leads to problems when it comes to moving files around and can lead to a loss of competitiveness if companies aren't able to process files in a timely manner. The issue can be magnified if it involves transferring files to and from cloud platforms.
One of the problems with big data is its sheer size. This leads to problems when it comes to moving files around and can lead to a loss of competitiveness if companies aren't able to process files in a timely manner. The issue can be magnified if it involves transferring files to and from cloud platforms.IBM has recognized this problem and in response has swallowed up California-based Aspera, a specialist in high speed transfer techniques. The company's patented "fasp" technology can reduce the transmission times for large files or data sets by up to 99.9 percent. It overcomes bottlenecks in broadband wide area networks that slow the transfer of extremely large files, such as high-definition video or scientific research data, over long distances.
"Our experience working with thousands of clients on Big Data projects tells us that companies can better compete and win when they can quickly extract value from massive volumes of data," says John Mesberg, Vice President, B2B and Commerce Solutions at IBM. "With this acquisition, IBM addresses a key challenge for globally integrated enterprises by allowing them to move large data files much faster to the individuals who need them, wherever in the world they may be".
Aspera can move big data to and from the cloud faster than traditional methods whilst providing predictability, bandwidth control and security. This benefits companies such as media organizations uploading TV shows and movies for streaming, medical research companies sharing genome data, or any organization trying to share and synchronize data between multiple devices on different sites.
"Our team has redefined how the world’s biggest data can be moved quickly, securely and reliably around the world," says Michelle Munson, president and co-founder of Aspera. "By tapping into IBM's innovative capabilities and global resources, we will solve ever expanding data movement challenges for our customers now and in the future".
The acquisition builds on IBM's Smarter Commerce initiative by helping businesses to speed up their digital supply chains. Aspera's fasp technology will be integrated into IBM's SoftLayer cloud infrastructure next year. The financial terms of the takeover deal have not been released.
Photo Credit: Maksim Kabakou/Shutterstock
-

Oracle buys Responsys to create the world’s biggest marketing cloud
Publié: décembre 20, 2013, 5:27pm CET par Ian Barker
 Business systems specialist Oracle has announced that it’s reached an agreement to acquire Responsys for $1.5 million. Responsys is one of the leading providers of enterprise-scale, cloud-based business to consumer marketing software.
Business systems specialist Oracle has announced that it’s reached an agreement to acquire Responsys for $1.5 million. Responsys is one of the leading providers of enterprise-scale, cloud-based business to consumer marketing software.Buying Responsys extends Oracle's Customer Experience Cloud to create a product that meets the needs of companies with both B2B and B2C marketing requirements. It enables chief marketing officers (CMOs) to run marketing campaigns across email, mobile platforms, social media and the web, it also allows them to operate at a massive scale and across the full consumer lifecycle.
"Recognizing the unique needs of the CMO in B2B and B2C industries, the Oracle Marketing Cloud is now the only platform to unite enterprise-class leaders in these historically distinct marketing-automation fields," says Mark Hurd, President of Oracle. "Our strategy of combining the leaders across complementary technologies signifies Oracle's overwhelming commitment to winning and serving the CMO better than any other software company in the world".
"Responsys has always been focused on helping marketers realize their largest opportunity -- coordinating their marketing touch points across channels, across the customer lifecycle, and across industries, and as a part of Oracle, we will only accelerate our efforts," says Dan Springer, CEO of Responsys. "Oracle not only shares our vision, but is the proven leader in bringing together best-in-class technologies and companies to realize the largest enterprise opportunities. We couldn’t be more excited about what this means for our customers and employees".
Responsys’ board has unanimously approved the transaction which is subject to acceptance of a tender offer by shareholders and to regulatory approval in early 2014. You can download a full report on what the deal means for customers and partners from Oracle's website.
Image Credit: Dusit/Shutterstock
-

The UK’s most-used TV guide app goes global
Publié: décembre 20, 2013, 4:51pm CET par Ian Barker
Television used to be simple. When you only had a few channels delivered via an aerial or a cable, deciding what to watch and where to watch it was easy. But with multi-channel digital services, the ability to watch on mobile devices, catch up with programs you’ve missed and more, it’s now a whole lot more complicated.
Little wonder then that apps which help you work out what to watch are proving popular. YO.TV, the UK's most used TV guide with five million customers, now plans to expand to 50 countries in 14 languages. Available on Google Play and the App Store, YO.TV lets users see listings for all their favorite channels across broadcast providers. Its Now and Next options streamline the scanning process, giving a cross section view of the full channel listings for any given time block. Personalized features let users set themselves reminders on their personal calendars so they don’t miss a favorite show or share their tastes in TV via social media.
Chetan Damani, co-founder of YO.TV, says, "Most people who access the internet via their smartphones use apps instead of browsers, which tells us that apps work best when they fulfill very specific functions. With YO.TV, we just looked at the way people were already using their phones and their televisions, and brought that all together in a single space."
Users have the ability to search by time and channel and having the guide as an app means you don't have to disturb other people who may be watching with you by using the TV's program guide. It also suits the growing numbers of people who use their mobile devices to watch sports and other events. Demani says, "It's not fair to say that mobile television is replacing regular TV, but use has certainly gone up dramatically, and YO.TV fits with that trend."
You can access the guide in your browser via the YO.TV website or install the app on your Android or iOS device.
-

Bulk SMS messaging app puts Android users at risk
Publié: décembre 20, 2013, 12:42pm CET par Ian Barker
 Having uncovered the Android dialler malware last week, mobile security specialist Lookout is warning of a new threat involving a tangled web of spam, foreign banks and bulk messaging.
Having uncovered the Android dialler malware last week, mobile security specialist Lookout is warning of a new threat involving a tangled web of spam, foreign banks and bulk messaging.The threat surrounds a bulk SMS network called Bazuc which offers Android users a payout if they allow the network to access their unused SMS message allowance. The app has been downloaded up to 50,000 times from the Play Store but the author claims up to 100 downloads an hour so it’s evidently on third-party stores too.
The idea of getting cash for your unused texts may seem attractive. But once you're signed up to Bazuc it can be used to send virtually untraceable messages that look like they came from your phone -- because they did come from your phone. These can be used to bypass spam detection and anti-fraud systems and of course Bazuc's authors are charging companies to send messages via your phone at around four times the rate they're paying you.
Lookout's analysis of the network's users threw up bulk advertisers, phishermen, and African and American banks. A breakdown of the messages sent via Bazuc shows 40 percent service and transaction alerts, 30 percent PIN code and password messages, 18 percent registration messages and invites, 8 percent spam, 2.5 percent suspected phishing and only 1.5 percent messages from actual humans. All of the messages were aimed at US subscribers but originated in countries including Nigeria, Russia, Poland and Mexico.
A major problem is that the messages sent are open for the owner of the relay to see. This means that legitimate banks and other organizations using this service to send PINs and passwords are putting their customers at risk of ID fraud.
Whilst Bazuc isn't actually malware it does exploit a loophole in the mobile world. Those who install it risk their phone number and personal information being shared. The companies that use the service to send messages risk their communication falling into the wrong hands.
Ultimately it's the phone users that are likely to suffer. Bazuc isn't breaking any rules but the people who download it are almost certainly in breach of their contract terms of service. It's these users that will suffer when cellphone operators start to shut down accounts or charge higher rates for these bulk messages.
It could be worse than that though, as Lookout points out on its blog, "...we can’t discount the possibility that this network could be used to send illegal messages, and in this case the owner of the phone is likely to find themselves in hot water with the authorities".
This is a complicated scam, you can read more detail including information about the people behind it and how much money it’s making them on Lookout's blog. Meantime the advice is that if something looks too good to be true it probably is.
Image Credit: Paul Michael Hughes/Shutterstock
-

IBM partners with Eurobank to deliver cloud-based international trade
Publié: décembre 20, 2013, 11:23am CET par Ian Barker

As the world begins to emerge from recession it's trade that will play a major role in driving the recovery. In a bid to bring together importers and exporters from around the world to increase transactions, IBM is partnering with Eurobank -- one of the largest banks in Greece -- to launch a cloud-based platform for international trading.
Called Exportgate -- a name which puts us in mind of some sort of scandal but we're sure they know what they’re doing -- it uses IBM's Digital Experience software to create a secure business-to-business web portal. Exportgate combines industry analysis tools to allow buyers to view company profiles and presentations, contact sellers directly and exchange ideas and research via forums. It also has the social capabilities you'd expect of any self-respecting modern business package.
Using the portal Greek businesses looking to expand their operations globally can find partners with relevant experience in other countries. At the same time international companies can find trading connections in Greece. Exportgate members have access to directories of over 1,400 Greek exporters and more than 6,500 international trading companies.
"One of the biggest challenges of international trade is the inability to effectively identify and engage with new partners on a global scale. Exportgate is helping to remove these barriers," says Constantinos Vousvounis, General Manager, Group Corporate and Investment Banking at Eurobank. "By partnering with IBM, members now have access to a cloud-based digital experience that helps them easily identify and expand their network of trusted partners while minimizing costs and accelerating growth into new markets".
More than 60 percent of visitors to Exportgate are from outside Greece, originating in countries including the UK, Italy, France, Germany and Russia. So far the site has generated more than 485,000 visits, 1,348,102 portal page views, over 8,000 e-library member visits, and has led to more than 2,300 partnerships and connections among international companies.
"Eurobank's new digital strategy for international imports and exports has brought vibrancy to the global trading system in the region," Larry Bowden, IBM's Vice President of Exceptional Digital Software says. "Now through this unique cloud-based digital experience members have unparalleled access to their target audiences, as well as one of the largest and most organized libraries of trading resources that are all customized to their exact industry and business needs".
To find out more and start boosting your own Greek trade you can visit the Exportgate website.
-

Target warns of unauthorized access to payment card data
Publié: décembre 19, 2013, 4:46pm CET par Ian Barker
 If you've recently used your payment card in a Target store in the US you might want to check your statements carefully. In a statement on its website the company warns that "guests" who made card purchases in its stores between November 27 and December 15 may have had their card data compromised.
If you've recently used your payment card in a Target store in the US you might want to check your statements carefully. In a statement on its website the company warns that "guests" who made card purchases in its stores between November 27 and December 15 may have had their card data compromised.My colleague Brian Fagioli who bought his iPad at Target on the December 14 is now anxiously biting his nails as his could be one of the estimated 40 million cards that may have been affected.
Target's statement says, "We began investigating the incident as soon as we learned of it. We have determined that the information involved in this incident included customer name, credit or debit card number, and the card's expiration date and CVV (the three-digit security code)".
The company says it's working with a third-party forensics firm to conduct an investigation and that it has alerted the authorities and financial institutions. In the meantime it recommends that customers -- sorry, guests -- stay alert for suspicious activity on their accounts. It helpfully provides a list of resources including credit reference agencies and various state law enforcement bodies.
Target says the issue has now been resolved and that it only affects US stores. If you've used a Canadian store or purchased via the website your information is not at risk. If you do spot a suspicious transaction, REDcard holders should contact Target, other card holders should get in touch with their bank.
Photo Credit: alexmillos/Shutterstock
-

Adaptiva’s enterprise IT predictions for 2014 [Q&A]
Publié: décembre 19, 2013, 12:29pm CET par Ian Barker

This is the time of year when people like to get out their crystal balls and try to imagine what the landscape of the coming 12 months will look like. IT efficiency and system management systems provider Adaptiva has announced its predictions for enterprise systems in 2014. The company has identified three key trends which it believes will shape the landscape for the next year: that BYOD will fail to live up to its hype, that lack of WAN bandwidth will hamper infrastructure plans, and that the continued use of Windows XP will cause significant security issues.
We spoke to the company's Chief Technology Officer and founder Deepak Kumar about the trends he sees shaping the enterprise IT landscape next year.
BN: BYOD is the thing everyone has been talking about in 2013 but you're predicting it will fail to live up to its hype. Why is this?
DK: BYOD will succeed in some use cases, but not as wildly as the outlandish hype suggests. BYOD will grow rapidly and companies will benefit from it in many ways. However, the hype is that BYOD will replace laptops and desktops as the primary end point device in the enterprise, simplifying the life of IT systems management. That's not realistic. Instead, companies will enable the use of smartphones and tablets for specific types of data and applications to supplement desktops and laptops. The traditional endpoint devices are more suited for creating content and even for consuming complex content. So BYOD will do great. I love it. We use it my company. But it will not make life easier for IT, it will add to their workload.
BN: So is BYOD just a fashionable trend or can it make a positive contribution to business? What needs to change for it to do so?
DK: I don't think anything needs to change except expectations. BYOD improves productivity. It enables agile teamwork by making certain data and applications rapidly accessible, and by making a larger part of the workforce continuously available. It's already making a positive contribution to business -- with email and calendaring alone -- and that will continue. For more complex use cases, companies should start small, measure success and ROI quickly, and move forward where it is working. Avoid making mass transformations just based on the idea that "BOYD is always good." It is good, but you have to use it wisely.
BN: You’ve said that XP will cause major security issues, can you talk us through the risks?
DK: Every computing platform is vulnerable to security attacks, and constantly needs OS patches, anti-virus updates, configuration changes, etc, to thwart potential attacks. After April 8, 2014, Microsoft will no longer publicly distribute patches to the software's vulnerabilities. Also, many anti-virus software providers say they plan to stop offering security for the product after April. Windows XP is already a strong target for hackers because it is so widely used. The lack of widely available OS and anti-virus updates will increase the attention it gets from cyber attackers. A lot of security breaches get swept under the carpet and we don't hear about them in the news. This goes on while Windows XP is still supported by the biggest OS manufacturer in the world. The real question is, what should we reasonably expect once Microsoft developers move on to other things?
BN: What do you think are the barriers to companies upgrading to a newer OS?
DK: Deploying operating systems using traditional methods requires a great deal of server horsepower and bandwidth, especially in large distributed environments typical of major corporations. It requires the deployment of complex protocols such as PXE, which in turn require extensive network infrastructure changes. Modern peer-to-peer technology such as our OneSite product can eliminate some of these issues, and make the deployment easier and much faster.
Independently of all that, you still have to address application compatibility and certification. All it takes to stall your deployment is one mission-critical application that won’t run on Windows 7/8. This could be a mission-critical software application, or even a hardware application. For example, take the case of a retail organization whose point of sale systems can't be upgraded, or a bank whose ATM systems can't be upgraded, until the vendors update the entire system.
BN: Isn’t there an opportunity here for third-party security providers?
DK: Definitely. There are draconian methods available to completely freeze and lock down the OS, but they also disempower the user. You can certainly buy elegant Band-Aids, but only Microsoft can fundamentally address the root causes which often lie deep within Windows code.
BN: You’re predicting that limited WAN bandwidth will hold back infrastructure projects. How can this be true in the age of high-speed fiber connections?
DK: There are three reasons bandwidth is still a problem in the age of high-speed fiber connections. First, companies are expanding their demand for bandwidth much faster than they are acquiring capacity. So, while companies will have more bandwidth than they are used to, they will suffer from a bigger gap between what they have and what they need.
Second, there is cost. The availability of bandwidth does not automatically ensure acquisition of it. It has to justify its place in a company’s budget.
Third, availability varies by region. In some parts of the world, they still have difficulty getting enough power to run their business successfully. Getting high-speed WAN connections is still not an option in many places -- at any cost. With globalization, companies are doing more business in more places, and often acquiring disparate operating locations.
BN: If lack of bandwidth is holding back development, isn't this a wider issue for telecoms providers and even governments?
DK: Bandwidth is already growing very fast, but the need for it is growing faster. That gap will always exist. When companies first got computers and saw revolutionary changes in organizational efficiency, they demanded even greater capacity and they still do today. No matter how much bandwidth we create, we will have a business use for more. While this is going on, companies need to find ways to maximize existing bandwidth and improve IT efficiency. For some organizations, infrastructure consolidation will make a lot of sense next year, and for others it will not because of bandwidth limitations.
BN: What overall effect do you think these trends will have on corporate IT strategies over the next year?
DK: Companies will focus on getting more utilization out of existing resources. That's true every year, but new ground is being gained in desktop computer aggregation and WAN bandwidth. Technology is advancing to the point where it is possible to leverage unused storage, memory and CPU resources from desktop collectives while people are working on them. The same is true with WAN bandwidth, where companies are harvesting unused bandwidth using new technologies such as network overlays, content-aware delivery systems, and traffic-aware protocols.
BN: Finally, what would be your one piece of advice to IT managers faced with increasing demands to embrace emerging technologies?
DK: Seeing is believing. Buy what you can touch, test, and deploy.
You can read Adaptiva's predictions for 2014 on the company's blog.
Photo Credit: Orla/Shutterstock
-

Should we be outbidding the cyber criminals to keep our systems safe?
Publié: décembre 18, 2013, 12:19pm CET par Ian Barker
 We increasingly rely on technology for the success of our businesses and even of our national economies. Yet that technology is under more and more threat from cyber criminals who adapt quickly to exploit any weaknesses. The resulting financial losses worldwide are estimated to amount to billions of dollars each year.
We increasingly rely on technology for the success of our businesses and even of our national economies. Yet that technology is under more and more threat from cyber criminals who adapt quickly to exploit any weaknesses. The resulting financial losses worldwide are estimated to amount to billions of dollars each year.In a new report from NSS Labs, research director Dr Stefan Frei advocates an innovative approach to deprive criminals of access to vulnerabilities. He suggests that governments and security vendors could join together to create an International Vulnerability Purchase Program (IVPP) to buy vulnerabilities -- paying at or above black market prices -- to keep them from the hands of malicious attackers.
He points out that security currently depends largely on ethical researchers reporting vulnerabilities, but at the same time the black market is expanding fast and offering large rewards for the same information.
Dr Frei reckons that the cost of buying up all vulnerabilities would be less than the losses to cyber crime even if those losses were only reduced by ten percent. He also says that if every vulnerability was purchased for $150,000 the cost would still amount to less than 0.01 percent of US GDP. The report breaks down the cost of reported 2012 vulnerabilities by software vendor (based on the same $150,000 cost per vulnerability figure). This puts Oracle at the top of the list with vulnerabilities costing $64.1 million (0.173 percent of revenue) Apple second on $45.5 million (0.028 percent) and Microsoft sixth on $26 million (0.036 percent).
In addition to suggesting that governments get together to create an IVPP, among the report's recommendations are that software vendors should offer competitive bounty programs for people who find bugs. It also suggests that government and vendors need to introduce incentives so that developers produce more secure software in the first place.
You can get the full report on the NSS website. It's well worth a read and presents a solid case for the business and economic benefits of buying vulnerabilities.
Do you think this is the right way to go? Should we simply be looking to price cyber crime out of the market? Do let us know your thoughts in the comments.
Photo Credit: Gts/Shutterstock
-

Amazon Web Services rolls out Kinesis to all users
Publié: décembre 17, 2013, 3:51pm CET par Ian Barker

Since it launched in 2006 Amazon Web Services has become a major player in the cloud computing sector. It's now aiming to move further into the big data arena with the rollout of Amazon Kinesis. Kinesis (from the Greek word meaning movement) is a managed service to handle the real-time processing of high-volume streaming data.
By using Amazon Kinesis customers will be able to store and process terabytes of data from hundreds of thousands of sources each hour. This will enable them to write applications that take action on real-time data -- things like website click-streams, marketing and financial transactions, social media feeds, logs and metering data, and location-tracking events.
Because it's available as a managed service, Kinesis should cut down on the development time needed to handle big data through more traditional approaches like Hadoop. Kinesis-enabled applications will be able to drive real-time dashboards, generate alerts and contribute to decision support systems.
Developers will also be able to take advantage of AWS's Auto Scaling to build flexible processing clusters. Kinesis integrates with third-party tools, including popular open source products, too so that developers have the freedom to select their own preferred method of data processing.
"When we set out to build Amazon Kinesis, we wanted to eliminate the cost, effort, and expertise barriers that have prevented our customers from processing streaming data in real-time," says Terry Hanold, Vice President, Cloud Commerce at AWS. "We've gotten great feedback from our preview customers, and it's inspiring to see the innovative ways customers are using Amazon Kinesis, across applications as diverse as gaming, mobile, advertising, manufacturing, healthcare, e-commerce, and financial services".
Companies that have been trialling the product include digital marketing platforms Bizo and MediaMath and Finnish social game developer Supercell. Sami Yliharju, Services Lead at Supercell says, "We are using Amazon Kinesis for real-time delivery of game insight data sent by hundreds of our game engine servers. Amazon Kinesis enables our business-critical analytics and dashboard applications to reliably get the data streams they need, without delays. Amazon Kinesis also offloads a lot of developer burden in building a real-time, streaming data ingestion platform, and enables Supercell to focus on delivering games that delight players worldwide".
Amazon Kinesis is available now in the US East Region and will be rolled out across other AWS regions over the next few months.
Photo Credit: Stephen VanHorn/Shutterstock
-

Social networking and cyber crime worries -- another day at the small business
Publié: décembre 13, 2013, 1:39pm CET par Ian Barker

Many surveys of how employees use technology focus on larger companies, but the latest 2013 Small Business Employee Survey from GFI Software looks only at firms with between two and 99 employees.
The survey of more than 1,100 employees across the US asked about job satisfaction, use of social media, connecting to company networks, attitudes to cyber crime and more. The results are interesting. While the majority of employees (75 percent) believe that mobile computing has improved their lives because they can work from anywhere, they’re also concerned about privacy and data protection. The other 25 percent said that it had made their lives more stressful because it made escaping work harder.
Identity theft proved a major worry too with 87 percent feeling they were at risk when using their work computer systems. However, only six percent saw a "great deal" of risk with 37 percent identifying "some" risk.
When asked about social networking 33 percent said that they used their networks for personal reasons whilst working, with 18 percent of these saying that it made them less productive. 37 percent of those surveyed say that they use Facebook at least daily.
Use of mobile devices remains popular with 43 percent saying that they’ve connected to work networks remotely. Where mobile devices are provided by the employer, almost all respondents said they used them for non-work tasks with 22 percent admitting to doing so often. Seven percent say that they’ve lost a mobile device containing company data.
It appears that employers may be partly to blame for some of the failings. Among workers at small businesses that have IT support staff, only 53 percent said their company has written policies governing work computer use. In places that do have policies 24 percent admitted having violated them. Only 36 percent said that their companies blocked them from accessing certain websites.
Some of these factors may be contributing to the fact that 81 percent of respondents to this survey expressed overall satisfaction with their jobs compared with only 68 percent of all full-time US employees in an earlier survey.
"While small businesses are subject to many of the same market forces as large enterprises, it’s important to differentiate how the universal trends that drive all businesses impact them uniquely and specifically," says Sergio Galindo, head of global product management at GFI Software. "As a company that delivers solutions to these smaller organizations through a mix of on-premise, cloud or managed services, knowing the user base and how they interact with technology is essential to our success".
You can download a copy of the full report along with the questionnaire and responses from the GFI website.
Photo Credit: StockLite/Shutterstock
-

Oracle helps enterprises exploit the power of data
Publié: décembre 13, 2013, 11:51am CET par Ian Barker
 Data is the lifeblood of modern business, but to exploit it effectively requires user-friendly tools to help with development and management. Oracle, one of the biggest players in the database field, has launched a new version of its developer tool to address this.
Data is the lifeblood of modern business, but to exploit it effectively requires user-friendly tools to help with development and management. Oracle, one of the biggest players in the database field, has launched a new version of its developer tool to address this.Oracle SQL Developer 4.0 is aimed at streamlining database adoption to the Oracle Database 12c and helping increase productivity for a broad list of database development tasks so organizations can fully capitalize on the power of their enterprise data.
The new release supports the features of the latest Oracle database including multi-tenant architecture -- where a database on a single server supports multiple client organizations -- and cloud capability. Migration tools are included so that customers can transfer their legacy systems and applications with less coding and database development.
New "pluggable" features are supported too making it easier for developers to link databases to the cloud. Enhanced reporting options offer more charts and easy to interpret reports. An improved command line interface speeds the development process by allowing reports to be built into automated tasks.
The developer's lot is also eased by code assistance features that help identify syntax errors prior to execution.
"Harnessing the power of enterprise data has never been easier for more than 3.3 million developers that use Oracle SQL Developer," says Michael Hichwa, vice president of software development at Oracle. "Leveraging Oracle SQL Developer 4.0 as a free support to Oracle Database 12c, organizations can adopt the world's most capable database quickly and easily".
You can find out more about SQL Developer 4.0 on the Oracle website. There’s also a podcast available outlining the new features.
Image Credit: Ermek/Shutterstock
-

Mozilla partners with mobile companies to promote open web compliance
Publié: décembre 12, 2013, 5:40pm CET par Ian Barker
 It’s often said that the great thing about standards in the technology industry is that there are so many to choose from. That's just as true in today's world of mobile devices as it was in the days of mainframes when it was first coined.
It’s often said that the great thing about standards in the technology industry is that there are so many to choose from. That's just as true in today's world of mobile devices as it was in the days of mainframes when it was first coined.Mozilla, LG, Qualcomm, Deutsche Telekom and a number of other leading mobile companies have taken a step closer to a world where standards are... well, standard, by joining forces to create the Open Web Device Compliance Review Board (CRB). The aim of the CRB is to support device manufacturers and their technology partners to standardize performance.
This will involve ensuring API compliance to make the open web experience consistent for customers. It will also help OEMs and carriers to improve the time taken to get products to market and reduce the costs of compatibility testing.
The CRB's membership is made up of a mix of partners covering geographically diverse markets. What they have in common is an interest in promoting the success of an open mobile system. Participants in the CRB at launch are Deutsche Telekom, KDDI, LG, Mozilla, Qualcomm Technologies, Sony Mobile Communications Inc., Spreadtrum, TCL/ALCATEL ONETOUCH, Telefónica, Telenor and ZTE.
"Users want a wide selection of devices and great apps. Operators, device OEMs and vendors want to be able to develop and test quickly and independently, in order to get new products to market. The CRB will enable partners to do so efficiently, reliably and confidently," says Andreas Gal, vice president of mobile at Mozilla and president of the CRB. "This is the next step in building the ecosystem and will make it easier for partners to get a wide selection of high-quality solutions into consumers’ hands quickly and efficiently".
It's intended that certification and testing will be carried out by external labs authorized by CRB. Each test is expected to be completed within three days of submission. Standards are based on Mozilla's principles of user privacy and control.
Christoph Schmitz, head of software and integration management at Deutsche Telekom Terminals. Says, "Deutsche Telekom values openness and choice for customers. That’s why we were happy to be among the first global launch partners for Firefox OS. Now there is an opportunity for other mobile innovators to take advantage of the rewards of open technology. The CRB is well positioned to accelerate this opportunity".
You can find out more about the CRB and its goals by visiting openwebdevice.org.
Photo Credit: Karuka/Shutterstock
-

99 percent of mobile financial malware writers prefer Android
Publié: décembre 12, 2013, 1:38pm CET par Ian Barker
 A new report by information research specialist NSS Labs focuses on the evolving landscape of mobile financial malware. It concludes that cyber criminals are adapting to the use of mobile apps to authorize transactions and that 99 percent of current mobile malware is aimed at the Android platform.
A new report by information research specialist NSS Labs focuses on the evolving landscape of mobile financial malware. It concludes that cyber criminals are adapting to the use of mobile apps to authorize transactions and that 99 percent of current mobile malware is aimed at the Android platform.As banks add extra functionality to their apps they open up greater capabilities for both customers and the cyber criminals. Many mobile banking apps are based on HTML code making them especially vulnerable to exploits. The report's author, NSS Labs Research Vice President Ken Baylor, says this should prompt more banks to develop secure native apps for mobiles, incorporating fraud-resistant features, if their customers are to stay secure.
Part of the reason that Android is more at risk than iOS is that it allows the installation of software from untrusted locations. The Play Store still accepts software installations from unauthorized sources. Android's market share plays a part too, as does the fact that most mobile financial malware is coming from ex-Soviet states and there’s a shortage of iOS malware authors in these countries.
Baylor writes, "With the rise of more powerful Android Trojans, malware that specifically targets the financial sector is likely to evolve alongside the extra money transfer capabilities provided to mobile devices by an increasingly trusting financial sector".
The report also identifies a trend towards integrated malware that can compromise both PC and mobile platforms. This allows attackers to capture login credentials, initiate fraudulent transactions and intercept and approve authorization messages meant to provide safeguards. Criminals achieve this in a number of ways including SMS forwarding and by imitating security apps.
Baylor concludes that to stay ahead, "...banks must use hardened browsers on mobile devices with unique install keys, certificate based identification, in app encryption, geolocation, and device fingerprinting. Malware will remain several steps ahead of deployed bank technology so long as bank improvements remain slow and incremental".
You can download the full report View from the Precipice – Mobile Financial Malware from the NSS website.
Photo Credit: lucadp/Shutterstock
-

Google Sheets gets more power and an offline mode
Publié: décembre 12, 2013, 12:13pm CET par Ian Barker
Everyone is familiar with Google Docs but the Sheets spreadsheet application always seems to have been a bit of a poor relation in terms of the search giant's cloud office portfolio. Now though there's a new release which brings more speed, more features and -- for the first time -- an offline mode.
The new version supports more cells so you can create bigger, more complex, worksheets. New features include Filter Views which let you save and share sections of the data, useful for collaborative projects.
Improved function help makes it easier to enter calculations and spot errors. Text handling is enhanced too so that if what you're entering is too long for the cell it automatically flows to adjacent ones. There are also improvements to conditional formatting that let you include rules to change colors and text styles based on custom formulas. Other minor tweaks include the addition of colored sheet tabs and custom number formatting for currencies, dates and so on.
The biggest news though is that you can now use Sheets offline. This only works in Chrome and there are instructions for setting it up on Google's support pages. Though if you’ve used Docs or Slides offline in the past then it should work straight away.
Writing on the company's Enterprise Blog, Zach Lloyd, Google Sheets Software Engineer says, "You shouldn't have to think about whether you have a WiFi connection when you want to work. So just like Google Docs and Slides, you can now make edits to Sheets offline. When you reconnect to the Internet, your edits will automatically sync".
Currently you need to opt in to the new Sheets as Google uses it to gather feedback on the extra features. To switch to the new version go to your Google Drive settings page and check the "Try the new Google Sheets" box.
On a brief test we found Sheets easy enough to use, if you're familiar with Excel you shouldn't have any problem with the basics like entering formulas and adding charts. If you decide to give the new version of Sheets at try do let us know what you think.
-

Bitrix24 rolls out more improved features
Publié: décembre 11, 2013, 3:58pm CET par Ian Barker
Bitrix24, the enterprise social network aimed at small and medium sized businesses, has released a new version of its cloud-based service.
Only three months on from the last release the latest version aims to improve telephony, CRM and collaboration features for its users.
The CRM part of the product now has its own activity streams along with new reporting tools for leads, managers and invoices. In addition web phone calls can now be made and recorded directly from a Bitrix24 account without any need of IP-telephony equipment or complex setup procedures.
There are improvements in productivity and collaboration tools too. The cloud storage feature Bitrix24.Drive can now handle company and group files as well as personal data. Companies that subscribe to the professional plan will also find that their storage is increased from 100GB to 1TB at no extra cost.
Project Management is now more tightly integrated with Time Management making it easier to track the time spent by employees on particular tasks. There’s also a new warning system to alert managers to tasks that are in danger of not being completed on time.
Dmitry Valyanov, president of Bitrix Inc says, "This is the fourth major update of Bitrix24 this year, and this rapid pace of improvement is one of the reasons that we reached the milestones of both 100,000 company signups and 1 million total users this fall, growing even faster than Yammer before Microsoft’s acquisition. Small businesses like the fact that they can now replace Yammer, MS Office, Salesforce, Dropbox, Basecamp and Skype with a single out-of-the-box solution that does all that they do and costs only a hundred dollars per month. Not only is it much cheaper, it solves a lot of interoperability, deployment, administration and shadow IT issues".
Bitrix24's new mobile app has an iOS 7-friendly design and an offline mode that lets users keep working even without a reliable intranet connection. The on-premise version has a new virtual environment that makes for easier deployment.
The product is available free for businesses with up to 12 users. Paid versions can be run in the cloud or self-hosted depending on your requirements. Visit the www.bitrix24.com website to find out more.
-

Sneaky Android malware calls premium rate numbers when you’re not looking
Publié: décembre 11, 2013, 1:19pm CET par Ian Barker

You might think that dialer malware went out with dial-up modems and that in these days of broadband you don't need to worry about viruses that call premium rate numbers in order to earn criminals money.
But researchers at mobile security specialist Lookout have uncovered a new piece of malware called Mouabad.p that tries to make money by making calls from your Android smartphone. Of course smartphone fraud involving premium SMS messages isn't new but making calls represents a step up in the malware's functionality.
Writing on the company's blog Lookout's product marketing manager John Gamble says, "Mouabad.p is particularly sneaky and effective in its aim to avoid detection. For example, it waits to make its calls until a period of time after the screen turns off and the lock screen activates. Mouabad.p also ends the calls it makes as soon as a user interacts with their device (e.g. unlocks it)".
It isn't clever enough to modify call logs, however, so victims could uncover its activity by checking their histories. Like other members of the Mouabad family this one also allows attackers to send SMS messages and control various settings relating to premium SMS billing. The malware is believed to be delivered via a dropper app that loads it in the background during its own installation.
The good news is that detection rates are low, the malware only works on Android versions older than 3.1 so owners of newer devices are safe. It's also mainly restricted to Chinese-speaking regions and since premium rate calls rely on country-specific numbers there's little incentive for it spread.
This doesn't mean that users elsewhere or with newer Android versions should get complacent though. As Gamble says, "In the world of mobile malware Mouabad.p is noteworthy because it can initiate a call without user intervention. In addition, Mouabad.p is specifically engineered to evade detection and deletion, concealing its background activities from users wherever possible and attempting to get privileged device access to make itself more difficult to remove".
To protect themselves Android users are advised to install apps only from trusted stores, make sure the system setting Unknown Sources is unchecked to prevent drive-by downloads and install a mobile security app.
Photo Credit: Mopic/Shutterstock
-

'Perfect Crime' vulnerability uncovered in Office 2013
Publié: décembre 11, 2013, 12:34pm CET par Ian Barker

California-based SaaS security specialist Adallom has revealed the existence of an Office 365 token flaw in Office 2013 that could allow malicious web servers to intercept authentication tokens and remotely access a SharePoint site without any alerts being raised.
Writing on the company's blog Noam Liran, Adallom's chief software architect describes the attack as an "ice dagger" because it's the perfect weapon, leaving no trace. He says, "The vulnerability we've found and the security incident that used it have all the makings of a great crime mystery. Only through months of diligent research were we and the Microsoft Security Response Team able to piece together the elements of what might otherwise have been a perfect crime, totally invisible to existing perimeter and endpoint protection defenses".
The problem only affects Office 2013 thanks to its close integration with Office 365. In order to exploit the vulnerability the attacker needs to get a user to click on a malicious Word document via a link in an email or on a website. Of course us tech savvy types know to avoid that sort of thing. But in a large organization you only need one employee to click on a document claiming to be a job application or a document from review and your whole SharePoint archive is wide open.
PowerPoint, Excel and OneNote are vulnerable too, and you won't be safe if you're using SkyDrive Pro because under the skin it's actually a SharePoint Online site.
Liran sums up, "The vulnerability we researched here and the security incident that used it is a bona fide Perfect Crime; a crime where the victim doesn't know that he’s been hit; a crime where there's no proof of any foul play anywhere; a crime where protecting yourself against it without being familiar with its modus operandi is next to impossible".
"There was no malware payload to reverse-engineer. No file hash we can trace through time. No IP address to locate and investigate. No servers to confiscate. The attacker simply gets away with your Office 365 token. For good".
The vulnerability has been repaired in December's Patch Tuesday round of updates and Office 2013 users are urged to install the fix as soon as possible.
Photo Credit: David Evison/Shutterstock
-

Textter wants to change the way you send and receive SMS messages [Q&A]
Publié: décembre 9, 2013, 11:13am CET par Ian Barker
Miami-based startup Textter has developed a new service aiming to revolutionize the way people send and receive text messages.
We spoke to company founder Carlos Cueto in an exclusive interview ahead of next week's official launch to find out more about the product and what it has to offer.
BN: For people who haven't heard of Textter can you give us a brief overview of what it does?
CC: Textter is a Live Messaging System (LMS), which allows users to see their friends' key strokes prior to pressing send. It's a Live communication tool in which you can respond prior to the other person pressing send.
BN: What gave you the idea?
CC: Observing my kids communicate with their friends via SMS texting. Kids today do not communicate on the phone. They literally spend all day texting, rarely calling anyone. The other reason, I do not have a lot of patience.
I use an iPhone and I am tired of seeing the 3 dots when I am waiting for a response. One day at the movie theater, I was in line buying goodies for my kids and their 8 friends. They were in the theater with my wife. The list was specific, when I got to the front of the line, the young lady told me they did not have watermelon Sour Patch Kids. So I texted my daughter and immediately saw the 3 dots. Unfortunately, I had people behind me but I wanted to read her response which was "The regular is fine, I am sorry, I got confused, the one on the Grove had the watermelon, love you!" The extra 20 seconds does not seem like a lot but when you are holding up a line, it's stressful. Had we had live messaging, I would have seen her response in 10 characters vs waiting for a 76 character entry and then her pressing send. Our service will literally save every Textter time every day.
BN: How big is the potential market and which services do you see as your competition?
CC: Currently, I have not seen any service similar to this, so the competition is nil. I believe eventually every smartphone, tablet and computer will load Textter as their Live Messaging System. At the start, our initial target market is 8 to 18 years old, 100s of millions of whom use SMS and are switching to web-based chats.
BN: What will make people choose Textter over other messaging apps?
CC: It’s the only live app available.
BN: Is Textter browser based or will it have its own app? Which platforms will it support?
CC: It will be an app plus browser based and will work across all platforms (smartphones, tablets and computers).
BN: Is it secure, are messages encrypted for example?
CC: Yes, connections made over SSL (Secure Socket Layer) and users must log in.
BN: Will this be a free app? How will you monetize it?
CC: Our basic tool will be free, eventually we will roll out a pro version for use in the office and another version to follow celebrities. Can you imagine reading a text/post from one of your favorite stars or athletes as they are pressing each letter? It's almost as if you can see what they are thinking.
BN: How will you take the product forward? Are there any other ideas in the pipeline?
CC: We use grassroots, social media and word of mouth to move it forward. Yes, we have quite a few additions we plan on launching but are keeping a lid on our secret for now. Development really starts after launch as we improve and adapt our product to service our users’ requests.
The service launches on December 16 initially on the iOS and Android platforms. You can register now for an invitation to use Textter by visiting the http://textter.com/ website.
Photo Credit: bloomua/Shutterstock
-

Hirejungle aims to boost the sharing economy
Publié: décembre 6, 2013, 12:04pm CET par Ian Barker

One of the most useful things about the internet is its ability to bring people together to trade and exchange. Think eBay, Play and Amazon Marketplace. But all of these are aimed at people with physical products to sell. London-based Hirejungle has come up with a platform that lets businesses and individuals hire out their goods or services.
Peer-to-peer rental, or the sharing economy, is big business according to The Economist. Whether you want to hire a car, rent a room for the night or find someone to carry out a home improvement job, technology makes it much easier to find what you need.
Newly out of beta, Hirejungle's peer-to-peer site connects people who have underutilized items or know how with others who need them. The site's founder Marcelo Barreneche says, "The first 'Eureka!' moment was when I needed a drill for a home refurbishing task and I didn’t have one, but I wasn't happy with the option of buying a new one only to use it just once a year. Then I thought it might be a good idea to hire someone to do the job for me… But who? And that started the brainstorming that led to this peer-to-peer platform".
Hirejungle is novel in that it doesn't charge transaction fees either for listing or for hiring. Instead the site is financed by advertising and gives businesses the option to pay for featured ads. If you’re looking to rent a car the site includes a price comparison engine to help you find the best deal.
There are of course other sites in this market, Taskrabbit.com and Rentmyitems.com for example, but they specialize in either services or goods. Hirejungle does both so you can rent out your car or hire a decorator via the same platform.
The site aims to be at the forefront of the sharing economy in the UK and Europe with plans to expand into India, Canada and the USA in 2014.
Barreneche sums up the site's attraction, "Here it is in simple terms: If you were to hire out something, let’s say your TV, which website would you use? If you have no idea, that's because you're another one of millions of people out there who could be earning income on things you don’t use".
-

Going mobile is too difficult and too expensive say CIOs
Publié: décembre 5, 2013, 5:24pm CET par Ian Barker
 Given all of the current buzz surrounding mobile you'd think that businesses would be falling over themselves to embrace the technology. But a new survey of IT decision makers by enterprise application and security expert Mobile Helix shows that whilst 78 percent of enterprises have a mobile strategy, 86 percent are not using it to transform their business.
Given all of the current buzz surrounding mobile you'd think that businesses would be falling over themselves to embrace the technology. But a new survey of IT decision makers by enterprise application and security expert Mobile Helix shows that whilst 78 percent of enterprises have a mobile strategy, 86 percent are not using it to transform their business.The survey of 300 CIOs in the UK and US reveals that 87 percent think that their employees would benefit from mobile access to enterprise applications. However, many of them are reluctant to invest. Complexity is cited by 66 percent as a reason not to pursue a mobile strategy, with 72 percent saying it's too costly to integrate mobile innovations into legacy applications. Development, security and support concerns are also listed as limiting factors.
As a result of this reluctance a mere 14 percent of businesses surveyed are currently using mobile solutions to transform their business processes, drive increased revenues and develop new income streams.
"Cost concerns are understandable, given that widespread enterprise mobility is still in its infancy, yet if CIOs make the right long-term choices today, they can generate significant returns for their business," says Mobile Helix's President Matt Bancroft. "Mobility has the potential to disrupt business in much the same way as the internet, but at the moment, cost and complexity challenges lead people to frequently ignore the enormous possibilities available. Take an industry where physical signatures are still needed: why not look at ways to use fingerprint scanning and location awareness on mobile devices as a way to completely change the way the industry works. Ultimately, we see the strategic value of mobility delivered in three phases: mobilizing existing enterprise applications, then adding mobile-specific capabilities to existing applications, and then creating totally new mobile apps where need and business case dictate".
Where mobile technology is used it's most likely to provide a simple extension to the office. Less than half of those surveyed are taking enterprise specific applications mobile. Of those that are, secure offline access is the most common use. Location-based tools using GPS are also becoming popular.
"To date, people are focusing on simply doing what they have always done, but from a mobile device, yet there is so much more potential value available from mobile technology," Bancroft says. "Perceived complexity is hindering adoption, but a key challenge to mobility is companies’ lack of vision, and that is a much bigger hurdle to overcome. With the introduction and broad adoption of HTML5, enterprises today can develop and deliver apps using their existing infrastructure and in-house skills. This means that the development of mobility solutions and mobile innovations can be both simple and cost effective".
Has your company taken CRM or other key systems mobile or is it sticking with more traditional means of accessing systems? Let us know.
Image credit: Catalin Petolea/Shutterstock
-

Shadow IT use raises workplace data risks
Publié: décembre 4, 2013, 4:20pm CET par Ian Barker
 Last month we reported on research showing that 65 percent of financial professionals were putting company data at risk by using unauthorized apps. New research carried out for anti-virus company McAfee shows that the figure is even higher across the enterprise as whole.
Last month we reported on research showing that 65 percent of financial professionals were putting company data at risk by using unauthorized apps. New research carried out for anti-virus company McAfee shows that the figure is even higher across the enterprise as whole.The study finds that of 600 employees surveyed across North America, the UK and Australasia, 80 percent admit to using non-approved software as a service (SaaS) applications in their jobs. These applications are referred to as "Shadow IT", meaning technology that hasn’t been approved by the IT department or acquired according to company procurement policy.
The rise of the cloud makes it easier for employees to deploy their own SaaS apps without reference to IT departments. The most popular unapproved application according to the survey is Microsoft Office 365, used by 9 percent of respondents, followed closely by Zoho on 8 percent. Then come social networking applications LinkedIn and Facebook each on 7 percent.
In an example of technical hypocrisy, IT users make greater use of Shadow IT (83 percent admitting to using it) than general business users on 81 percent. When asked to justify its use, 39 percent of IT respondents say they use unauthorized SaaS because, "it allows me to bypass IT processes", while 18 percent say that IT restrictions "make it difficult to do my job".
"With over 80 percent of employees admitting to using non-approved SaaS in their jobs, businesses clearly need to protect themselves while still enabling access to applications that help employees be more productive," says Pat Calhoun, general manager of network security at McAfee. "The best approach is to deploy solutions that transparently monitor SaaS applications and other forms of web traffic, and uniformly apply enterprise policies, without restricting employees' ability to do their jobs better. These not only enable secure access to SaaS applications, but can also encrypt sensitive information, prevent data loss, protect against malware, and enable IT to enforce acceptable usage policies".
The full report, The hidden truth behind shadow IT is available as a PDF from the McAfee website.
Photo Credit: Hans-Joachim Roy/Shutterstock
-

Google makes its Compute Engine generally available -- and cheaper
Publié: décembre 3, 2013, 4:24pm CET par Ian Barker

Most businesses by now will have heard of the Google Cloud Platform which lets developers run applications on Google's servers. The company today announces general availability of its Google Compute Engine offering scalable, secure virtual machines running Linux.
In its preview phase Compute Engine supported only Debian and Centos running with a customized Google kernel. It now supports any out of the box Linux distro so that developers can work with a familiar environment but also support software that needs a specific kernel or file system.
At the same time Google has announced a transparent maintenance regime that upgrades and maintains systems whilst allowing the virtual machines to keep running. In the event of failure VMs are automatically restarted to get them back online fast.
Writing on the Google Cloud Platform Blog Vice President Ari Balogh says, "At Google, we have found that regular maintenance of hardware and software infrastructure is critical to operating with a high level of reliability, security and performance. We're introducing transparent maintenance that combines software and data center innovations with live migration technology to perform proactive maintenance while your virtual machines keep running. You now get all the benefits of regular updates and proactive maintenance without the downtime and reboots typically required".
For those needing more computing power there are new instance types available with up to 16 cores and 104GB of RAM. Google has also cut the price of its Persistent Disk storage by 60 percent per gigabyte and is dropping I/O charges in order to offer more predictable pricing. The price of the most popular Compute Engine instances is also cut by 10 percent.
You can find out more about Compute Engine, view real-life case studies and sign up for a trial at https://cloud.google.com/products/compute-engine/
Photo Credit: Fernando Madeira/Shutterstock
-

StrikeIron launches hosted API management tool
Publié: décembre 3, 2013, 3:01pm CET par Ian Barker
 Increased use of mobile devices by consumers means that companies face challenges in terms of making their services and data available on a range of different gadgets. To give customers a properly interactive experience you need more than just a website. The key to doing this is APIs (Application Programming Interfaces) which allow connections to be established between your data and your customer's devices.
Increased use of mobile devices by consumers means that companies face challenges in terms of making their services and data available on a range of different gadgets. To give customers a properly interactive experience you need more than just a website. The key to doing this is APIs (Application Programming Interfaces) which allow connections to be established between your data and your customer's devices.But developing APIs can be a complex and costly process. In order to streamline this StrikeIron has announced the public launch of its new hosted API management tool in the form of IronCloud.
With a management console as well as a developer portal IronCloud allows both the business and IT sides of a company to collaborate on cloud-based APIs. The console offers easy access to features like end-user access control, flexible billing, usage analysis, security settings, account management and automated usage charge tracking.
"Our customers trust IronCloud, as we developed it to be the most scalable, mature, and reliable API management platform on the market," says Sean O'Leary, CEO and President of StrikeIron. "Our own managed API product offerings are provided through IronCloud. StrikeIron is the only API management company that has dedicated the last decade to monetizing data and digital assets via APIs. This new public release of the IronCloud platform enables businesses to share their digital assets with their customers quickly, securely, and reliably".
The launch gives StrikeIron a full portfolio of API tools including managed interfaces and API accelerators. Built to provide solutions to the company’s own customers it offers reliable infrastructure and enterprise grade data security to give companies a mature and stable platform for their connected services. It also supports a range of hosting options so it can be run in your own data center, on StrikeIron’s systems or in the public cloud.
IronCloud will be showcased at the Gartner Application Architecture, Development & Integration Summit or for more information visit http://www.strikeiron.com/about-the-ironcloud-platform/
Photo Credit: everything possible/Shutterstock
-

The best tools for removing malware
Publié: novembre 28, 2013, 11:59am CET par Ian Barker
 Antivirus software is generally seen as being about protecting your system from infection, but sometimes you get caught out and it's necessary to call on the product's removal capabilities. If you're lucky, or careful, you might never have to try out the malware removal ability of your security product, but it's good to know it can step up to the plate if needed. To help you see if your chosen solution measures up AV-Comparatives has released the results of its latest malware removal tests.
Antivirus software is generally seen as being about protecting your system from infection, but sometimes you get caught out and it's necessary to call on the product's removal capabilities. If you're lucky, or careful, you might never have to try out the malware removal ability of your security product, but it's good to know it can step up to the plate if needed. To help you see if your chosen solution measures up AV-Comparatives has released the results of its latest malware removal tests.Tests were carried out on a range of 11 malware samples including Trojans, worms, backdoors and ransomware. Using a Windows 7 Professional 64-bit system each infection was loaded, the system rebooted and then the anti-virus product installed, updated and put to work.
The tests awarded scores for each sample based on the effectiveness of removal and convenience of operation -- whether a boot to Safe Mode or a rescue disk was needed for example. Results were then aggregated to give a points score for each product.
Best overall was Kaspersky with a total score of 98 points, followed closely by Bitdefender on 97. AVIRA makes up the top three on 92. At the bottom of the table comes ThreatTrack Vipre with a score of 65. G-DATA and BullGuard tie for second to last slot on 73. Microsoft Security Essentials scored 83 putting it in the lower half of the table.
Interestingly not one of the products received a perfect score -- complete removal using only normal mode -- across all threats. Kaspersky came closest, removing 10 of the threats normally but needing a rescue disk for the 11th. Other than the top three, all of the products completely failed when it came to removing at least one of the samples, ransomware proving the most difficult to shift.
You can download the full report as a PDF from the AV-Comparatives website.
Image credit: DeiMosz/Shutterstock
-

ScaleXtreme combines server and cloud management in a single platform
Publié: novembre 26, 2013, 11:44am CET par Ian Barker

The growth in popularity of cloud-based applications has brought new challenges for system admins. Rather than a single set of systems in one place a company's computing may now be spread across a number of platforms and locations.
With the announcement of its new Advanced Cloud Management product ScaleXtreme aims to give its customers a broad set of server, application and service management tools on a single platform.
Generally available from today the product has been trialled in a number of large companies to give central IT control over their public cloud deployments on systems including on Amazon Web Services, Terremark Enterprise Cloud, and Microsoft Azure.
It's fully integrated with the company's existing server management capabilities, including server and application monitoring, patch management, and job automation. This allows enterprises to manage their existing infrastructure as well as taking advantage of public and private clouds to re-engineer and port their applications.
Nand Mulchandani, CEO and Co-Founder of ScaleXtreme, explains, "As enterprises evolve their applications architecture to be increasingly cloud-based, they find themselves having to deal with multiple vendors and management tools. There's usually no 'clean break' between their legacy applications running on virtualized servers in their datacenter, and starting to deploy applications in the public cloud. ScaleXtreme helps IT deal with this complexity. Our Enterprise Platform gives them a single console with which to control all aspects of cloud application provisioning; while still giving them server management functionality for handling the underlying infrastructure on their existing applications".
Features of the ScaleXtreme platform include the creation, deployment and management of cloud applications across private, public and hybrid environments. It provides automatic scaling capability across clouds, enforces access control and compliance, and provides server management tools like monitoring and patch management.
"Today, enterprises live with the reality of highly heterogeneous IT environments. Any platform that can simplify and unify the systems management burden on IT, and accelerate the provisioning of new cloud services for end users, is very welcome," says Rob Green, CEO of Dizzion Consulting, a cloud computing services firm. "We have deployed ScaleXtreme in several of our enterprise clients: from managing application scaling in the cloud, to failover and disaster recovery".
You can find out more about Advanced Cloud Management on the ScaleXtreme website.
Image Credit: everything possible/Shutterstock
-

Spanning Cloud provides protection for Salesforce data
Publié: novembre 25, 2013, 3:32pm CET par Ian Barker
CRM data is the life blood of any sales-based business so it's important to look after it. That's doubly true if you're contemplating moving your CRM activity to the cloud. In order to address this, Texas-based backup and recovery specialist Spanning Cloud Apps is expanding its product range to cover the most popular cloud CRM package Salesforce.com.
Unlike other solutions Spanning Backup for Salesforce is embedded within the main Salesforce user interface. This means that backup and recovery options can be reviewed without leaving the package and key activities shared directly to Chatter feeds.
"Spanning is focused on providing leading-edge backup and recovery solutions for the most significant cloud applications. As the titan of enterprise cloud computing apps, Salesforce is a logical next step for us," says Jeff Erramouspe, CEO and president of Spanning. "Salesforce is storing unfathomably large amounts of critical data -- our backup and recovery solution ensures organizations are now fully protected from data mishaps and losses".
The product is designed to reduce the administrative burden of performing backups by automating daily tasks. It also offers point-in-time recovery making it simple to return to a specific previous version of the data if needed. Reporting of activity to Chatter feeds means that admins can spot problems and take action to resolve them before they become critical.
George Crump, president and founder of storage and cloud market analysts Storage Switzerland, says, "As organizations move core business functions to cloud applications like Salesforce, they are struggling to apply traditional backup and recovery methods, leading them to look for emerging solutions like Spanning Backup for Salesforce. We see independent data protection of cloud-based services as a critical component of any organization's data protection strategy."
Spanning Cloud made its début at Dreamforce 2013 and is now available as a private beta before becoming generally available in the first quarter of next year. In the meantime you can find out more on the company's website.
Image Credit: Maksim Kabakou/Shutterstock
-

CRM on the move for small businesses
Publié: novembre 22, 2013, 4:30pm CET par Ian Barker
 For most people customer relationship management conjures up the idea of a massive database of sales information. But for smaller, especially one person, businesses who may spend only a small amount of their time in front of a computer, traditional CRM isn't a practical proposition and doesn't lend itself to mobile use.
For most people customer relationship management conjures up the idea of a massive database of sales information. But for smaller, especially one person, businesses who may spend only a small amount of their time in front of a computer, traditional CRM isn't a practical proposition and doesn't lend itself to mobile use.Step forward ONDiGO which is designed to provide CRM on the go -- see what they did there? It's built to be easy to use and to start working immediately so that you can begin improving business contacts with customers from day one.
Features of ONDiGO include color coding so that you can differentiate personal and business contacts, new and existing customers and so on. It allows you to review your history of calls and messages with a contact, set tasks, schedule meetings and make notes. You can also prioritize interactions and at the end of each day you can review a real-time report of your activity.
The app syncs automatically with your phone contacts and your Google calendar and it stores all of its notes and other information in the cloud so that they're secure and still accessible if you switch devices.
ONDiGO is currently available free on the Play Store for use on Android devices. You can learn more about the product and view videos of it in action on the company's website. You can also register your interest in the iOS and Windows Phone versions which are in the pipeline.
-

Metalogix streamlines moving business email to the cloud
Publié: novembre 19, 2013, 11:05am CET par Ian Barker
 Email is often cited as being the killer application that made the internet take off, and there's no denying it has changed the way the world does business. But using email for business means keeping an archive so that you have a record of conversations. Over time that archive can become substantial and take up a lot of expensive disk space so storing it in the cloud begins to look like an attractive solution.
Email is often cited as being the killer application that made the internet take off, and there's no denying it has changed the way the world does business. But using email for business means keeping an archive so that you have a record of conversations. Over time that archive can become substantial and take up a lot of expensive disk space so storing it in the cloud begins to look like an attractive solution.To help with moving mail to the cloud Metalogix is launching its Total Email Management and Migration product for Amazon Web Services. It delivers a complete service for mail archiving, backup, security, migration and continuity in the cloud.
The product uses 'labs' which allow users to test solutions to make sure everything is working as it should before completing the migration. There's also a try and buy option which offers all of the options of the full product for a limited number of accounts so that customers can see how the migration works before moving to the full solution.
"With Metalogix Total Email Management and Migration for the AWS cloud environments we are delivering a comprehensive approach to email and file archiving and management with the flexibility our customers seek to support the changing dynamics of their business," says Steven Murphy, CEO of Metalogix. "By providing the industry's best of breed email management solutions on AWS, users can achieve the stringent security and control they need while lowering their total management costs. This consolidated solution combined with world-class security and management functionality is truly the 'All Stars Environment' customers and their trusted partners have been seeking to meet their email and unstructured data management requirements".
The product is offered in licensing packages based on number of users or storage capacity and perpetual licenses can be transferred to other cloud systems on in-house infrastructure if need be. You can find out more on the Metalogix website or try out the product via the AWS Test Drive Labs at http://aws.amazon.com/testdrive/microsoft/.
Photo Credit: Roland IJdema/Shutterstock
-

InsightSquared gives smaller businesses the edge in sales analysis
Publié: novembre 18, 2013, 7:47pm CET par Ian Barker
 Successful sales strategy is dependent on understanding the customer. But for small and medium businesses building up the kind of intelligence database needed can be time consuming and take staff away from the task of actually selling. It can be many months before the implementation of a traditional sales intelligence platform bears fruit.
Successful sales strategy is dependent on understanding the customer. But for small and medium businesses building up the kind of intelligence database needed can be time consuming and take staff away from the task of actually selling. It can be many months before the implementation of a traditional sales intelligence platform bears fruit.Software company InsightSquared has used the Dreamforce 2013 conference to launch the latest version of its analytics tool aimed at helping smaller enterprises stay competitive. Designed to work with the Salesforce CRM application, InsightSquared 3.0 has been put together based on feedback from experienced CEOs, along with sales and marketing professionals, in order to provide best practice reports and drive effective sales management.
The turnkey SaaS solution can be up and running in under a day and incorporates three new technologies. Instant Sales Insight allows managers to clearly see the relationship between sales activity and conversions. Sure Forecast ensures more accurate forecasting based on existing conversions and pipeline deals. Thirdly the Smart Pipeline Manager makes it easier to spot high probability and high risk deals.
Reports from the system can be generated using a straightforward point-and-click interface and offer immediate insights that can be used to boost sales performance from day one.
Fred Shilmover, CEO of InsightSquared says, "We are taking sales and marketing innovation to a new level by making business intelligence powerful yet easy to use, which has never been done before. We’re delivering industry-changing innovation and setting a new standard for what modern business intelligence should be".
Visitors to the InsightSquared stand at Dreamforce 2013 will be able to register to get a sales report in 60 minutes. Alternatively you can sign up for a free trial on the InsightSquared website.
Photo Credit: amasterphotographer/Shutterstock
-

UK and Ireland get Twitter Alerts
Publié: novembre 18, 2013, 12:51pm CET par Ian Barker
It's an indication of the impact of social media that Twitter is now often the first place where people learn of major news stories. But that's a double-edged sword because it can be hard to know how accurate the information you're reading is.
From today Twitter is making it easier for government organizations and charities in the UK and Ireland to make timely and accurate information available via Twitter Alerts. The alerts service launched in the US, Japan and Korea in September of this year and has already been used by a number of public services to share information during emergencies involving public safety, bad weather and so on.
Some 57 accounts are signed up to the UK and Ireland service at launch including all of the UK's police forces, the London Fire Brigade, the Mayor of London's office, the Environment Agency and the Foreign Office. A full list of organizations using the service can be found on Twitter's website.
Rita Dexter, Deputy Commissioner for the London Fire Brigade, says, "People act on information shared on social media. During a major incident accurate, verified and frequent updates are essential. Twitter Alerts will help us communicate quickly during a significant emergency".
If an organization is using the alerts service you’ll see an orange bell symbol on its Twitter account page. You can also go directly to the alerts page by adding /alerts to the end of the page URL -- for example the Greater Manchester Police page is https://twitter.com/gmpolice/alerts. You won't be automatically signed up to alerts even if you follow the main account, you have to opt in to receive them.
When an alert is issued it will be highlighted on your feed with the orange bell icon, if your mobile phone is linked to your account you'll also receive an SMS message. Users of Twitter for Android or iPhone will get a push notification to their device provided they're using Twitter for iPhone version 5.10 or higher, or Twitter for Android 4.1.6 or higher.
Photo Credit: bikeriderlondon/Shutterstock
-

Microsoft turns to crime (in a good way)
Publié: novembre 14, 2013, 5:16pm CET par Ian Barker

Don't panic, Redmond isn't after your credit card details -- well, no more than usual. Microsoft has announced the opening of a new Cybercrime Center to combine its legal and technical expertise with cutting-edge tools and technology in the fight against crime on the internet. The center will tackle a wide range of crimes including malware, botnets, intellectual property theft and online child exploitation.
"The Microsoft Cybercrime Center is where our experts come together with customers and partners to focus on one thing: keeping people safe online," says David Finn, associate general counsel of the Microsoft Digital Crimes Unit. "By combining sophisticated tools and technology with the right skills and new perspectives, we can make the Internet safer for everyone".
Located on Microsoft's Redmond campus, the center includes a separate and secure location for third-party partners allowing them to work alongside the company’s own experts. This will allow for improved partnerships across law enforcement, education and industry.
The secure facility houses technologies that allow the team to visualize and identify global cyberthreats as they develop in real time. These include SitePrint, which allows the mapping of online organized crime networks; PhotoDNA, a leading anti-child-pornography technology; cyberforensics, a new investigative capability that detects global cybercrime, including online fraud and identity theft; and cyberthreat intelligence from Microsoft’s own botnet takedown operations.
With around 100 people worldwide including lawyers, forensic analysts and technical experts the center is well-equipped to make online life safer.
"In the fight against cybercrime the public sector significantly benefits from private sector expertise, such as provided by Microsoft," says Noboru Nakatani, executive director of the INTERPOL Global Complex for Innovation. "The security community needs to build on its coordinated responses to keep pace with today’s cybercriminals. The Microsoft Cybercrime Center will be an important hub in accomplishing that task more effectively and proactively".
Microsoft is encouraging customers to visit www.microsoft.com/security to learn more about threats and ensure that their systems are protected.
-

Research shows... Oh, hey, look at that!
Publié: novembre 14, 2013, 4:33pm CET par Ian Barker
Millennials are more heavily distracted when watching video and as a result adverts need to work harder to get through to them. This is among the findings of research by YuMe, a digital brand advertising specialist, and IPG Media Lab.
Focusing on millennials (those born between the early 1980s and the turn of the century) the first phase of the study looked at the tablet video viewing experience compared to TV, PC and mobile. The second phase analyzed media consumption and multi-tasking habits in an attempt to understand which device is most effective at achieving brand recall within the demographic.
"This study really did exceed our expectations, as it not only proved the power of tablet video consumption, but it dove deeper to showcase actual habits and consumption of millennials," says Kara Manatt, Vice President of Consumer Research Strategy at IPG Media Lab.
Key findings are that millennials are more distracted when watching video, so ads have a harder time breaking through, however, when video ads do succeed they tend to have a more positive impact on the millennial generation. The results also reveal that smartphones are the most popular device for viewing videos amongst this age group and consequently when ads appear on smartphones they're more effective. Millennials are also more likely to multi-task with other connected devices. This represents, "...a clear opportunity to plan for duplication and exposure timing across devices for ad breakthrough," says Ed Haslam, SVP of Marketing at YuMe.
More about the study and its results will be presented in a webinar on November 22nd at 11:30am PT. You can register for this by visiting https://www1.gotomeeting.com/register/337165017. In the meantime you'll find an overview in infographic form below.
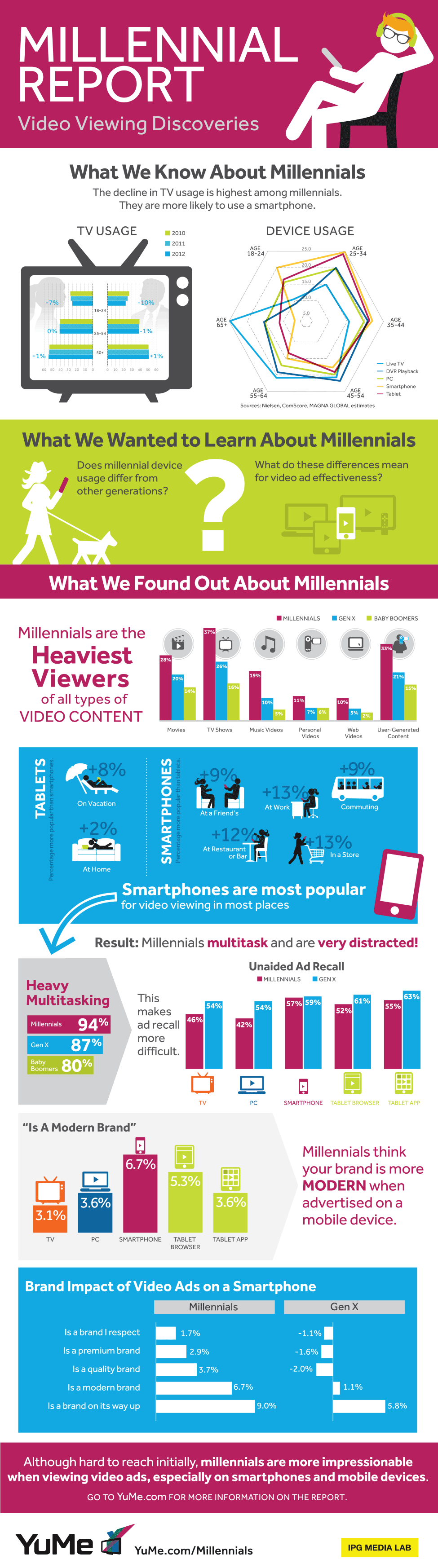
-

DataStax releases a NoSQL database with automatic management
Publié: novembre 14, 2013, 2:08pm CET par Ian Barker

Because NoSQL databases are less restrictive than the more conventional relational model, offering simpler design and improved scaling, they're popular for handling big data and real-time web applications. However, this comes at the price of higher maintenance demands.
The latest release of DataStax Enterprise (DSE) 3.2 addresses this with the addition of automated management services, allowing companies to concentrate on generating revenue rather than maintaining the database. This makes it the first NoSQL solution to have management taken care of by the database itself, bringing features that would previously only have been available in products like Oracle to the NoSQL market.
Using new versions of DataStax's Apache Cassandra-based database software along with visual monitoring tools many database operations can be left to the system. A Capacity system collects key information and can warn admins when systems are stressed, making it easier to predict when extra capacity will be needed.
A Repair service keeps data consistent across distributed clusters with minimal performance impact. In addition an OpsCenter provides an at-a-glance dashboard together with a point and click interface to allow bulk operations like starting and stopping multiple nodes.
"By automating repair and capacity planning functions, DataStax Enterprise 3.2 allows developers to focus on their revenue-generating applications instead of their underlying database technology," says Robin Schumacher, vice president, products at DataStax. "With DataStax Management Services, DSE 3.2 delivers an easy to use and reliable out-of-the-box experience for companies who want to reap the scalability and availability benefits of Cassandra without the operational overhead of open source software".
DataStax Enterprise 3.2 and OpsCenter 4.0 are available now from the company’s website.
The company is also offering free self-paced online training to help users get to grips with the product via its DataStax Ac*ademy.
-

Lack of backup puts SMBs at risk of significant data loss
Publié: novembre 14, 2013, 12:48pm CET par Ian Barker
 Backing up data can often seem like a chore and is something which isn't always top of the agenda, especially for smaller businesses. New research commissioned by cloud backup and disaster recovery company Intronis shows that a high percentage of small and medium businesses are at risk of major data loss that could put them out of business.
Backing up data can often seem like a chore and is something which isn't always top of the agenda, especially for smaller businesses. New research commissioned by cloud backup and disaster recovery company Intronis shows that a high percentage of small and medium businesses are at risk of major data loss that could put them out of business.The results show that most SMBs go to managed services providers (MSPs) -- 83 percent of which are SMBs themselves with less than 99 employees -- for their IT services. More worrying is that they often don't buy backup and data recovery until after suffering a detrimental loss of data.
The 2013 State of Cloud Backup study carried out in September 2013 surveyed 350 IT service providers -- including MSPs, system integrators, and IT solution providers -- to find out about their sales of cloud backup services as well as the type of demand they were seeing from their SMB customers.
"Data losses come in all forms, from hardware failures to user error and natural disasters, and it's never a good time," says Neal Bradbury, co-founder and vice president of channel development for Intronis. "SMBs and IT service providers should think of cloud BDR services as insurance for the company’s data -- no business should be without it".
On a positive note, of those companies that are working with a service provider to protect their data, more than 50 percent are using cloud technology, showing an increased confidence in the cloud’s reliability and ability to safeguard data. The results also reveal that cloud backup offers a strong opportunity for service providers to grow their business, with 56 percent of the providers polled saying that backup and recovery is a top selling product.
The full survey and can be found on the Intronis website at www.intronis.com/cloudstudy2013. Additional key findings will be released via the Intronis blog over the coming weeks.
Photo Credit: Lisa S./Shutterstock
-

Samsung partner program extends KNOX to the enterprise market
Publié: novembre 12, 2013, 4:25pm CET par Ian Barker
 Launched earlier this year in Barcelona, KNOX, as we reported at the time, is a secure Android platform powering Samsung Galaxy devices. It's designed to strengthen Android by using hardware features to provide the highest level of protection. KNOX is aimed at offering security whilst remaining manageable and addresses the need to separate work and play on the same device.
Launched earlier this year in Barcelona, KNOX, as we reported at the time, is a secure Android platform powering Samsung Galaxy devices. It's designed to strengthen Android by using hardware features to provide the highest level of protection. KNOX is aimed at offering security whilst remaining manageable and addresses the need to separate work and play on the same device.With the launch of a partner program, Samsung is helping resellers and independent software vendors to provide extra value for their customers and extend the benefits of KNOX to the enterprise market. It provides partners with assets, resources and training to help them provide support for Samsung devices. Compatibility is included for existing master data management (MDM) solutions to allow resellers to offer a complete solution or work with existing installations.
"We are launching Samsung KNOX partner program and believe it is a truly exciting time in our journey towards winning in the Enterprise segment," says Dr Injong Rhee, Senior Vice President and Head of B2B R&D Group, IT & Mobile Division at Samsung Electronics. "With Samsung KNOX, for the very first time Enterprise IT can deploy Android devices, which are loved by consumers, for enterprise usage, ensuring highest levels of platform security and information protection. This excitement is shared by our Go-To-Market partners and they have signed up overwhelmingly to partner with us to resell KNOX and in turn unlock tremendous value in their Enterprise Mobility offerings. We look forward to a long-term win-win with our partners."
The partner program will be offered in Platinum, Gold and Silver levels though for the first six months all partners will get the Platinum level before tier qualifications and benefits come into play.
To find out more about KNOX and the partner program visit www.samsungknox.com
Image Credit: Rashevskyi Viacheslav / Shutterstock
-

Hannspree launches a 13-inch tablet on a 7-inch budget
Publié: novembre 12, 2013, 3:13pm CET par Ian Barker

It's the iPad and the Nexus 7 that make the most headlines in the tablet market, but the fiercest competition for consumer cash in the run up to this year's Christmas holiday season will be taking place lower down the food chain.
Taiwan-based audio-visual specialist Hannspree is the latest to enter the fray with its new HANNSpad SN14T71. Offering a 13.3-inch screen it launched today in the UK with a price tag of just £199.99 ($318). The screen itself is a 10 point Multi Touch unit with a resolution of 1280 by 800. Whilst that’s pricier than other budget tablets like Tesco’s £119 Hudl, it’s squarely up against some premium smaller devices like the 16GB Nexus 7 and you are getting a lot more screen real estate for your money, albeit with a lower resolution.
Size isn't everything though so what about the rest of the spec? The HANNSpad comes with a 1.6GHz quad core ARM processor, 1GB of DDR3 memory, 16GB of internal storage and an HDMI output. A Micro SD slot allows you to add up to 32GB more storage.
Connectivity is via wireless N and Bluetooth -- there’s no 3G or 4G. However, it does have 0.3 megapixel front and 2.0 megapixel rear webcams, a G sensor and a 3-axis accelerometer. The SN14T71 runs Android 4.2.2 (Jelly Bean) and comes pre-loaded with a number of apps including Softmaker Office.
The HANNSpad will be available from Misco, Amazon and ebuyer and the price includes a two year warranty. If you want a big tablet on a small budget it could be worth a look.
-

By 2017 your smartphone might be smarter than you
Publié: novembre 12, 2013, 1:41pm CET par Ian Barker
 The rise of intelligent machines has long been fertile ground for science fiction writers, but a new report by technology research specialists Gartner suggests that the future is closer than we think.
The rise of intelligent machines has long been fertile ground for science fiction writers, but a new report by technology research specialists Gartner suggests that the future is closer than we think."Smartphones are becoming smarter, and will be smarter than you by 2017," says Carolina Milanesi, research vice president at Gartner. "If there is heavy traffic, it will wake you up early for a meeting with your boss, or simply send an apology if it is a meeting with your colleague. The smartphone will gather contextual information from its calendar, its sensors, the user's location and personal data".
Your smartphone will be able to predict your next move or your next purchase based on what it knows about you. This will be made possible by gathering data using a technique called "cognizant computing".
By combining information from apps and the personal cloud your phone will be able to carry out more tasks automatically. "We assume that apps will acquire knowledge over time and get better with improved predictions of what users need and want, with data collection and response happening in real-time," says Ms Milanesi.
Initially the tasks carried out automatically will be calendar based -- things like arranging a car service, or sending birthday greetings. As cognizant computing improves it will allow other tasks like responding to routine emails or booking travel tickets to be carried out too.
Of course none of this means that smartphones are actually becoming intelligent. It's simply that the information they're able to gather via their sensors and from the cloud will make them appear so. This of course raises privacy concerns and how well it works depends on how willing users are to share information. But Gartner reckons that while privacy might be an issue for some, consumers are willing to give up a good deal in return for convenience.
"Mobile phones have been our trusted companions for years channeling the natural need we have to communicate with others and express ourselves first with voice, then with the internet, and more recently through applications," says Ms Milanesi. "Smartphones, their technology and operating systems have been radically changing other devices from PCs to televisions. The era of personal cloud is empowering users as well as devices to get access to and share more and more data. Over the next five years, the data that is available about us, our likes and dislikes, our environment and relationships will be used by our devices to grow their relevance and ultimately improve our life".
Gartner analysts will be discussing the future of smart devices at the Gartner Symposium/ITxpo 2013 in Barcelona from November 10-14. You can follow news from the event on Facebook or on Twitter using the #GartnerSym hashtag.
Image Credit: Maksim Kabakou/Shutterstock
-

New solution aims to make SaaS more secure
Publié: novembre 12, 2013, 11:06am CET par Ian Barker
 The growth of the cloud and the use of software as a service (SaaS) has had a dramatic effect on both businesses and individuals, allowing people to access corporate applications and data from anywhere and on any device. But it also gives IT managers a security headache as it becomes harder to build and enforce consistent policies, especially when employees are using their own devices.
The growth of the cloud and the use of software as a service (SaaS) has had a dramatic effect on both businesses and individuals, allowing people to access corporate applications and data from anywhere and on any device. But it also gives IT managers a security headache as it becomes harder to build and enforce consistent policies, especially when employees are using their own devices.In a bid to tackle this, security specialist Adallom is launching a complete solution for SaaS applications. This offers seamless cloud-based security that audits all SaaS activities and provides real-time information on user activity.
It's built to be scalable across the cloud and to integrate with other security solutions like anti-virus and VPN. Using a clientless architecture it sits in between the user and the SaaS application, making use of proxy server technology to ensure minimum latency.
Adallom combines a range of techniques, and these include real-time risk analysis which monitors user activity to detect abnormal behavior, manage high risk incidents and share knowledge of attack patterns via a global intelligence network. This means it's able to prevent attacks without the need for complex rules and configurations.
A single interface makes it easy to define policies across SaaS applications. This is combined with centralized auditing to allow admins to see user login, device location and activity details.
"The freedom provided by SaaS applications has introduced a new threat vector through the myriad of modern attacks targeted at human interactions with SaaS applications. Adallom addresses this gap, preventing attacks by helping organizations extend visibility, compliance and security to SaaS and cloud services," says Assaf Rappaport the co-founder and CEO of Adallom. "With unrivaled intelligence, Adallom provides the means to mitigate SaaS threats and enhance enterprise security while preserving the ease-of-use and convenience of cloud services. The goal is security without boundaries".
You can find out more details about the product and its pricing on the Adallom website.
Image Credit: Maksim Kabakou/Shutterstock
-

New Kapow release streamlines big data use
Publié: novembre 11, 2013, 5:32pm CET par Ian Barker
 It seems that everyone is keen to get in on the big data trend at the moment. If you're still unsure of what it is and where it comes from take a look at the handy infographic we published last week. If you want to start making use of it, then the company behind that graphic, Kapow Software has just released its latest product to make it easier to extract big data from any source.
It seems that everyone is keen to get in on the big data trend at the moment. If you're still unsure of what it is and where it comes from take a look at the handy infographic we published last week. If you want to start making use of it, then the company behind that graphic, Kapow Software has just released its latest product to make it easier to extract big data from any source.Kapow Enterprise 9.3 uses synthetic APIs which allow it to draw data from a number of sources and integrate it into existing business processes. What the company calls Kapplets enable users to run and manage thousands of automated data integration applications at the same time. They can then view the different data streams in an integrated way and act on the findings.
"Enterprise 9.3 is enterprise-ready data integration software that is ideal for any business challenged by managing big data as part of its day-to-day operations," says Stefan Andreasen, Founder and Chief Technical Officer at Kapow Software. "It gives users robust capabilities that make data accessible, affordable and actionable, allowing organizations to rapidly deliver the critical information at the time they need it to make better decisions".
The product allows the rapid creation of synthetic APIs to support interactive web technology like HTML5 and JavaScript, but it continues to support traditional APIs too in order to interact natively with XML and use existing code where it occurs.
Kapplets allow action to be taken on the data as it arrives and results can be rendered as graphs and tables to make them easier to understand. In addition built-in user management makes for easier distribution of information to the people who need it. Improved scalability and performance makes for faster processing of high volumes of data too.
"Kapow brings incredible value to our business users by making them more efficient and productive," says Lars Johnsen, Chief Content Manager at Schultz Information, a market leader providing digital information portals and decision tools for both government agencies and corporations. "Using Kapow, we spend less time on manual processes to access and prepare data and more time on making new discoveries. Kapow Kapplets are intuitive and elegant, and provide our business users the critical data they need with just a single click".
You can find more information and request a demo of the product on the Kapow website.
Photo Credit: PlusONE/Shutterstock
-

Fear of cyber attacks could expose businesses to new risks
Publié: novembre 8, 2013, 1:18pm CET par Ian Barker
 Data breaches and cyber attacks frequently make the news when well-known companies are the target.
Data breaches and cyber attacks frequently make the news when well-known companies are the target.This is good in the sense that it raises awareness of the need to take security seriously, however, the latest Global Risk Management Survey by Gartner finds that fear of attack is causing security professionals to shift their focus away from disciplines like enterprise risk management and risk-based information security in order to concentrate on technical security issues.
"While the shift to strengthening technical security controls is not surprising given the hype around cyberattacks and data security breaches, strong risk-based disciplines such as enterprise risk management or risk-based information security are rooted in proactive, data-driven decision making," says John A Wheeler, research director at Gartner. "These disciplines focus squarely on the uncertainty (as in, risk) as well as the methods or controls to reduce it".
Gartner says that organizations that move away from risk-based disciplines, or fail to adopt them in the first place, fall prey to what it calls fear uncertainty and doubt (FUD) which in turn can lead to reactionary or emotion-based decision making.
The survey shows a worrying movement away from risk assessment, with only six percent focused on enterprise risk management in 2013 compared to 12 percent in 2012. Wheeler says, "As IT risk profiles and postures change in the future, an inevitable shift in focus back to these risk-based disciplines will need to occur. If not, IT organizations may find that more-critical, emerging risks will remain undetected, and the company as a whole will be left unprepared".
In the short-term though it seems that FUD can benefit the security budget. The report finds that 39 percent of respondents have been allocated funds totaling more than seven percent of the total IT budget. This compares with only 23 percent having received a similar amount in 2011.
"These incongruent survey findings seem to validate the observation that risk-based, data-driven approaches are falling to the wayside in favor of FUD-based, emotion-driven activities," says Wheeler. "Or, perhaps more disturbingly, they indicate that those who have concerns are simply burying their head in the sand, rather than proactively addressing emerging threats".
Linking of IT risk indicators to business performance seems to be in decline too with survey respondents indicating a seven percent drop in formal mapping over the last year. Seventeen percent had ceased this activity altogether. Wheeler concludes, "If done correctly, integrated risk and performance mapping exercises can yield tremendous benefits for companies and IT organizations that are seeking to develop a more-effective risk management dialog with business leaders".
The full report Survey Analysis: Risk Management, 2013 is available from Gartner's website.
Photo credit: Tashatuvango/Shutterstock
-

Windows 8.1 to get three critical security patches
Publié: novembre 8, 2013, 12:39pm CET par Ian Barker
 Next week’s Patch Tuesday will see a number of security patches for Windows 8.1 including three that get the top Critical rating. According to Microsoft’s advanced notification on TechNet the three critical updates address remote code execution issues in Windows and Internet Explorer.
Next week’s Patch Tuesday will see a number of security patches for Windows 8.1 including three that get the top Critical rating. According to Microsoft’s advanced notification on TechNet the three critical updates address remote code execution issues in Windows and Internet Explorer.There are also five more updates flagged as Important, three for Windows and two for Office. The three Critical bulletins also apply to Windows XP and will be among the last for the 12-year-old operating system before support ends in April next year.
Interestingly none of these patches address the Security Advisory issued earlier this week affecting Vista, Windows Server 2008 and versions of MS Office from 2003 to 2010. Users of these systems are advised to follow Microsoft’s FixIt solution which involves disabling a codec. A more permanent solution is expected at a later date.
Other things to expect on Tuesday include the regular refresh of the Malicious Software Removal Tool and a number of non-security related updates.
Photo Credit: fotoscool/Shutterstock
-

Can smartglasses have a role in the workplace?
Publié: novembre 6, 2013, 4:04pm CET par Ian Barker
 Google Glass has caused a bit of a stir, whether it's for the ability to turn us all into government spies or for causing the slightly distracted Google gaze. But there's been relatively little discussion of how smartglasses might be useful for business.
Google Glass has caused a bit of a stir, whether it's for the ability to turn us all into government spies or for causing the slightly distracted Google gaze. But there's been relatively little discussion of how smartglasses might be useful for business.Until now that is, because a new report by Gartner says that smartglasses have the potential to boost worker efficiency in areas like healthcare, manufacturing and field service.
"Smartglasses with augmented reality (AR) and head-mounted cameras can increase the efficiency of technicians, engineers and other workers in field service, maintenance, healthcare and manufacturing roles," says Angela McIntyre, research director at Gartner. "In the next three to five years, the industry that is likely to experience the greatest benefit from smartglasses is field service, potentially increasing profits by $1 billion annually. The greatest savings in field service will come from diagnosing and fixing problems more quickly and without needing to bring additional experts to remote sites".
As yet smartglasses have seen little adoption in the business world and take up is likely to remain low until apps and services emerge to make them truly useful. Gartner expects the biggest impact to be in heavy industry such as oil and gas production where the technology could be used to provide on the job training and access to technical documentation on site. Workers would therefore be able to carry out tasks even if they couldn't remember all of the procedures. Quite whether you'd want the guy who's fixing your nuclear reactor to be reading the instructions as he went along is another matter -- "insert control rod A into reactor housing B".
There's a role in quality control too. The technology could be used to make a video recording of a procedure to prove to management or safety inspectors that it had been carried out correctly.
What the report calls the "weightless" industries like finance and media are likely to see less benefit. Though smartglasses could be useful for, say, insurance assessors looking at damaged properties.
"...the goals of corporate training may evolve away from memorizing procedural steps to knowing how to use smartglasses and access key information using voice commands," says Tuong Nguyen, principal research analyst at Gartner. "Classroom training and tests on the content of manuals can be reduced since much of the practical training can be done 'on the job' with the assistance of smartglasses. However, training must always include safety and employees should continue to know how to use equipment for routine tasks".
In healthcare Gartner says that smartglasses could help doctors consult with specialists during a patient examination. In conjunction with facial recognition the glasses could also be used to bring up a patient's records as they walk into the surgery. Of course from the other side of the desk you would never be sure whether your doctor was looking up your symptoms or checking on the football scores.
The full report is available on Gartner’s website.
-

Develop enterprise mobile apps in record time with built.io
Publié: novembre 6, 2013, 3:02pm CET par Ian Barker
With the increasing trend towards using mobile devices in the workplace, IT departments sometimes struggle to keep up with demand from their users. As we've seen elsewhere, this can lead to employees using unauthorized software.
Companies interested in speeding up the build time for mobile apps will want to take a look at San Francisco-based raw engineering’s built.io product which comes out of beta and is generally available from today.
Unveiled at DEMO Mobile 2013, built.io is a backend as a service (BaaS) product that allows enterprise mobile apps to be developed faster. It looks after managing servers, cloud infrastructure, database structure and scaling, allowing developers to focus their talents on building the user experience.
"Using built.io, our team was able to build variations of Twitter and Google Docs in under a week. That kind of timeframe really changes the game for enterprise apps. It's now cost-effective for businesses to experiment and create really interesting, powerful apps, even for short-term needs like a seasonal customer promotion or internal sales meeting," says raw engineering CEO Neha Sampat.
The move out of beta coincides with the introduction of some new features. These include a new management console, geo-location features, intelligent notifications, cloud extensions, social network integration and more powerful analytics.
As a result the product allows developers to build apps on top of an existing platform. They can also easily add social features such as allowing users to follow comments on a shared document.
 "By taking care of all the heavy lifting involved with building an app backend from scratch, built.io gives businesses a way to finally meet the pent-up demand for apps sparked by today’s mobile workflows, 'app store' culture, and BYOD trends," adds Sampat.
"By taking care of all the heavy lifting involved with building an app backend from scratch, built.io gives businesses a way to finally meet the pent-up demand for apps sparked by today’s mobile workflows, 'app store' culture, and BYOD trends," adds Sampat.For more information on the built.io product and its pricing model you can visit http://built.io/plans.
-

Financial professionals use unauthorized apps to access company data
Publié: novembre 6, 2013, 11:20am CET par Ian Barker
 The increasing popularity of BYOD brings a number of challenges for IT departments, not least of which is ensuring that files are handled in an approved and secure way. The problem is that users don’t often see things the same way. A new survey by Workshare shows that 65 percent of mobile users at financial institutions are using file sharing apps that aren't approved by their IT departments.
The increasing popularity of BYOD brings a number of challenges for IT departments, not least of which is ensuring that files are handled in an approved and secure way. The problem is that users don’t often see things the same way. A new survey by Workshare shows that 65 percent of mobile users at financial institutions are using file sharing apps that aren't approved by their IT departments.Only 55 percent were using unauthorized apps to work on documents outside the office in 2012, but the figures are even more worrying when you take into account that 89 percent of financial professionals are now using their own devices for work -- up from a mere 3 percent last year. The report also shows that 78 percent of these workers are using free file sharing services like Dropbox and SkyDrive to access and store corporate documents.
Whilst 62 percent of "knowledge workers" use their own mobile devices for work, the report shows that the BYOD trend is at its most popular in legal, sales and marketing departments, with around three-quarters of employees in these fields using their own kit. By contrast only 18 percent of those in administrative roles use their own devices for work purposes.
Large companies with more than 20,000 employees seem to have a better grasp of the risk posed by file sharing solutions. However, in businesses with fewer than 500 staff only 24 percent of employees were using authorized file sharing apps.
It's clear from these findings that BYOD has become an important tool for many enterprises but that in some organizations the procedures and controls needed to use it safely haven't caught up. To address these concerns Workshare is launching a new version of its Protect Server product. This gives IT departments control over corporate files shared by email and webmail on mobile devices.
You can see an overview of the report's findings in handy infographic form below.
Photo Credit: bikeriderlondon/Shutterstock
-

Scanning emails to target ads is not cricket says UK public
Publié: novembre 5, 2013, 12:11pm CET par Ian Barker

From technology that watches you in the supermarket, to social networking’s attempts to make the ads we see more relevant, the advertising industry is becoming cleverer at getting its message in front of the right people.
But is scanning emails, as Gmail does, a step too far? A survey commissioned by Outlook.com in the UK has found that 84 percent of people disapprove of email service providers scanning messages in order to target online adverts.
The study, carried out by independent research company GfK, also finds that 64 percent of UK residents were unaware of any email provider scanning messages to target them with ads. A massive 93 percent agreed that they should have the ability to opt out of having their messages scanned for this purpose.
Annie Weber, Executive Vice President of GfK's Public Affairs & Corporate Communications division says, "The polling indicates that overall many British residents are unfamiliar or uncomfortable with the idea of email service providers scanning words in emails for the purpose of targeting advertising. At a time when digital privacy is increasingly concerning the public, this survey suggests that service providers need to work hard to ensure email users understand the specifics of how their personal content is being used, and the underlying reasons for these practices which will result in a more informed and educated user".
Are you concerned about your mail provider scanning your messages to show you more relevant adverts? Or is that low on the scale of your online privacy worries? After all, it's hardly a new practice. Let me know via the comments.
Image credit: Amir Kaljikovic/Shutterstock
-

New tools from Adaptiva aim to streamline Windows XP migration
Publié: novembre 5, 2013, 11:10am CET par Ian Barker
Most people should know by now that Microsoft is ending support for Windows XP in April 2014. However, according to NetMarketShare's latest report, 31.24 percent of the PC market is still running the venerable OS.
For enterprises this raises serious security and compatibility issues not to mention the time and effort involved in migrating large numbers of systems. Solutions provider Adaptiva is offering an answer in the form of its OneSite Rapid OSD product to aid operating system deployment and cut the time and cost involved in moving to Windows 7 or 8.
Where traditional migration techniques need server resources on site and technicians to spend time at the desk, OneSite allows the process to be carried out without either.
It uses a number of tools to streamline the process, these include pre-staging of content so that files travel over the WAN only once, using predictive bandwidth to minimize impact on other traffic. On LANs multiple systems are allowed to download files simultaneously. When an OS image gets updated OneSite creates a small "diff" file rather than transfer the whole thing again, saving both bandwidth and time.
OS images are delivered using a peer-to-peer pre-boot execution environment (PXE) rather than relying on a single server. This allows for faster installs by choosing the best peer system to serve the image. The system also uses a virtual state migration point (SMP) to store all of the user settings and applications in a file that can easily be moved across a network and cached on other machines with spare disk space. It can aggregate unallocated space so as not to steal storage from users.
"Operating System migration involves an extreme amount of data and requires a way to manage the distribution and deployment of about 20-25+ gigabytes of data required for most companies," says Deepak Kumar, CTO and founder of Adaptiva. "Because OneSite is tightly integrated with Microsoft SCCM, it provides an elegant solution that automatically creates a Virtual SAN and Virtual SMP at every network location, making OS migration a much easier task. Our technologies drastically cut deployment times down to as quick as a single day -- once the image and task sequence have been created -- all without the need for consulting services".
You can find out more about OneSite and sign up for a trial version on the Adaptiva website.
Photo credit: JNT Visual/Shutterstock
-

Digital transformation needs a new approach to project management
Publié: novembre 4, 2013, 1:02pm CET par Ian Barker
 The increasing use of technology by customers presents many challenges for business. This means that traditional areas like finance and operations may no longer be driving change. According to a new report by research specialists Gartner, meeting the digital era, where change may be motivated by evolving customer expectations, needs a fresh approach if it's to be done successfully.
The increasing use of technology by customers presents many challenges for business. This means that traditional areas like finance and operations may no longer be driving change. According to a new report by research specialists Gartner, meeting the digital era, where change may be motivated by evolving customer expectations, needs a fresh approach if it's to be done successfully.Unlike other projects which are about delivering on budget and on time, digital transformation schemes can involve taking risks in order to achieve better performance. Gartner calls this "discovery oriented project management" where it's necessary to experiment and continue to learn from projects even after their launch.
The report recommends a number of things to help enterprises come to terms with this new landscape. These include having a small core team of no more than six to eight executives to enable decisions to be made quickly, understanding how customers actually use technology to interact with the business, and approaching old and new models in parallel. It also suggests using behavioral scientists to help understand how customers use information as they have no preconceptions of how things should be working. In addition the report suggests businesses look for inspiration from other industries rather than look purely at their own sector.
Richard Fouts, research vice president at Gartner says, "Customer focused digital business transformation initiatives will short change the organization’s intent if they depend on a traditional approach that values the wrong things. Most projects are defined goals, schedules and quantifiable objectives. However, it's difficult to set quantifiable objectives if the ultimate business model you’re driving toward is unknown. Transformation puts you in discovery mode; the firms we talked to treat it more like a scientific experiment versus an engagement with a known deliverable".
The full report, How to Approach Customer-Focused Digital Transformation is available on the Gartner website.
Photo credit: Tashatuvango/Shutterstock
-

Technology companies shouldn't neglect the importance of silver surfers
Publié: octobre 31, 2013, 12:25pm CET par Ian Barker

Silver surfers are a more important market than generations X and Y yet are often ignored by technology companies according to new research by Gartner. With many markets now having an aging population, technology designers and marketers need to refocus on the opportunities offered by older users.
Speaking at Gartner Symposium/ITxpo on Australia's Gold Coast, vice president and Gartner Fellow David Furlonger says, "In recent years, technology decision makers have focused their work largely on the perceived wants and needs of younger demographics. They have created and sold products targeted explicitly at an already-saturated market of financially poor 'digital natives' in Generations X and Y. This emphasis on the young is unsurprising, since many technologists are themselves part of these younger age groups. However, it is a very serious mistake, because it neglects the most promising technology market demographic of all: the affluent, increasingly technologically sophisticated older generation we are calling the 'silver surfers'".
Research elsewhere by Australian mobile company Optus shows that the older generation is increasingly active on social media with more than three quarters of silver surfers in the country using Facebook to stay in touch with friends and family.
Technology is able to improve quality of life for the older generation too and research by Gartner and others shows that individuals in this age group are quick to recognize the potential it has to change their lives. This represents an opportunity for companies to design and sell devices specifically for the needs of this market, a step that most have not yet taken.
"The consumerization of technology has made it far more accessible, especially in terms of usability, to people who may find PCs more difficult to manage," says Furlonger. "However, technology designers and manufacturers have largely ignored this huge and growing market, and by doing so, have neglected one of their most important sources of future growth and revenue. The younger market has only linear growth potential and decreasing purchasing power, while the silver surfers offer exponential growth opportunities and growing purchasing potential".
A number of factors are driving technology adoption by older groups, these include increased availability of broadband and Wi-Fi connections, along with social networks and targeted forums. All of this helps meet the need for social interaction as increasing numbers of older people find themselves living apart from their families in a way unknown to past generations.
Gartner says that designers can help by delivering clean, simple, uncluttered user interfaces, without confusing fonts, colors or special effects. Straightforward navigation and simple checkout processes are crucial for older customers too.
Companies also need to recognize that silver surfers select and buy technology in a different way. Trust and reputation are important as are recommendations from family and friends. Perceived value -- the contribution technology can make to a person's life rather than just the price -- is important too.
"The silver surfer demographic is huge and growing, and clearly has both the ability and the desire to spend significant amounts of money on technology," says Furlonger. "However, to date, most technologists and technology manufacturers have failed to deliver products and services that meet the needs of this market and its various sub- or microsegments, and marketers have largely failed to target it effectively. To do so will require fundamental changes in their approach to product and service design, marketing and sales".
The full report is available on Gartner's website and you can see a video of Furlonger introducing the research on YouTube.
Photo Credit: arek_malang/Shutterstock
-

Enterprise storage gets serious with Ceph's scalable software solution
Publié: octobre 30, 2013, 2:10pm CET par Ian Barker

Unless you're heavily into the world of data storage you probably haven't heard of Ceph. It's an open-source distributed storage system for Linux platforms designed to deliver performance, reliability via a software defined system that's also very scalable. It's self-managing and self-healing and can be accessed via big data tools like Hadoop and Samba.
Now that you know what it is you'll be interested to learn that Inktank, the company behind Ceph, has launched Inktank Ceph Enterprise. This is a subscription product that builds on Ceph's open-source roots to provide the most stable version of the product with a new graphical management console and a suite of support services.
"Inktank Ceph Enterprise is an important development that should help enterprise customers evolve their Ceph deployments, be they public, private or hybrid cloud environments," says Simon Robinson, Research Vice President at analyst firm 451 Research. "Having the backing of Ceph experts behind their Ceph deployments should help customers as they look to improve business continuity service levels, drive greater agility and improve operational efficiency across their cloud estate".
It can be used in cloud deployments or as a replacement for traditional storage solutions. Offering web-scale technology with long-term support available from a commercial vendor, it allows businesses to benefit from the economics of modern data storage. By using commodity hardware it can lead to significant cost savings compared to legacy systems.
Inktank Ceph Enterprise is supported on Red Hat Enterprise Linux 6.3, Red Hat Enterprise Linux 6.4, CentOS 6.3, CentOS 6.4, and Ubuntu 12.04 LTS. Its pricing model is based on the amount of storage deployed.
"The launch of Inktank Ceph Enterprise makes Ceph a viable, sustainable storage platform within the enterprise", says Bryan Bogensberger, CEO of Inktank. "Inktank customers now have the tools, code and peace of mind required to get serious about replacing expensive, proprietary legacy storage hardware and satisfying their emerging cloud and big data storage needs with the transformative Ceph distributed storage system".
Photo Credit: kubais/Shutterstock
-

Microsoft security report warns of risks from unsupported operating systems
Publié: octobre 29, 2013, 5:10pm CET par Ian Barker
 Microsoft has released its latest Security Intelligence Report detailing the threat intelligence gathered from more than a billion systems worldwide.
Microsoft has released its latest Security Intelligence Report detailing the threat intelligence gathered from more than a billion systems worldwide.With Windows XP support due to end in April 2014 the report takes a close look at the risks posed to consumers and businesses of using unsupported operating systems. According to StatCounter, XP and older systems still account for around 21 percent of those in use.
The main threats facing XP users are the Sality malware family which can steal personal data and lower system security settings, the Ramnit family that infects executable, MS Office and HTML files, and variants of the Vobfus worm which can download other malware onto a PC and spread itself via removable drives.
The report finds that in the first half of 2013 almost 17 percent of computers running up to date Microsoft security products encountered malware. Although encounter levels were similar for both operating systems, XP machines were six times more likely to be infected than those running Windows 8.
"The data help illustrate the positive impact that security innovations in newer operating systems are having. Modern operating systems such as Windows 8 include advanced security technologies that are specifically designed to make it harder, more complex, more expensive and, therefore, less appealing for cybercriminals to exploit vulnerabilities," says Tim Rains, director of Microsoft Trustworthy Computing.
Obviously Microsoft has an interest in persuading XP users to upgrade but there are some compelling statistics. Microsoft warns that in the two years following XP SP2 going out of support malware infections jumped by 66 percent compared with those for SP3.
Rains adds, "We truly want people to understand the risks of running Windows XP after support ends and to recognize the security benefits of upgrading to a more modern operating system -- one that includes the latest in security innovations, provides ongoing support and can in turn better protect them".
You can see an overview of the findings in the slideshow below:
Microsoft Security Intelligence Report, volume 15 from sreid_wagged -

Identified uses social media to create largest ever recruitment database
Publié: octobre 28, 2013, 5:09pm CET par Ian Barker

Finding the right staff is crucial to the operation of any business. But often the people that are right for a role aren't necessarily looking for a new job. San Francisco-based analytics specialist Identified thinks it has an answer to this with a new product that combines social media and big data techniques to create a massive searchable candidate database.
Identified Recruit claims to have a billion potential candidates available making it the largest source of professional profiles. You may think that this is like LinkedIn, but the difference is that Identified Recruit uses multiple data sources so it isn't limited by its own user base.
"The open web contains the most comprehensive, current professional information available, but until now companies have been forced to go to individual networks like LinkedIn to find talent," says Brendan Wallace, co-founder and co-CEO of Identified. "With access to all of the web's data, companies can find great talent on a scale never before possible".
The product gathers information from a range of public social media sources whist protecting personal data by anonymizing the details. This allows it to deliver results for groups -- such as healthcare professionals -- that are under represented on sites like LinkedIn. The company quotes as an example that Identified has over 3,500 profiles for Surgical Technicians, where only 87 can be found on LinkedIn.
Earlier this month, Identified announced that it had hired Facebook's manager of data science, Mohammad Sabah to direct and develop the expansion of its core technology -- though it didn't say if it had found him through its own system.
Recruiters can find out more and request a free demo at www.identified.com the rest of you make sure your social network profiles are up to date.
Photo Credit: vichie81/Shutterstock
-

Bloomfire streamlines corporate knowledge sharing
Publié: octobre 25, 2013, 12:47pm CEST par Ian Barker
We've seen a raft of tools in recent months that seek to combine business intelligence with elements of social networking. Bloomfire's USP in this field is that it seeks to capture the knowledge that already exists within an enterprise and use it to deliver improved employee engagement and ultimately better customer service.
Bloomfire has a clean interface reminiscent of Google+ and it works by dividing content into "feeds". These are designed to deliver content that’s relevant to the individual whilst filtering out noise so that people can find the information they need to do their jobs. Notifications can also be customized so that relevant notifications and tags aren't missed. The result is more time spent on the actual task and less managing the system. In any case it's designed to be used by business people rather than technicians.
The product is cloud based and can be accessed from a browser or via Android and iOS apps. It’s customizable so that users can apply their own corporate branding. Built-in analytics show who is contributing the most and which posts are the most valued by others as well as how long questions take to get answered.
In-built creation tools make it easy to share multimedia content including webcam videos and screen captures. These and other linked documents are stored in Bloomfire’s own cloud so there’s no external storage requirement.
The product currently has 350 customers and 150,000 individual users. Packages start from 25 users and the company says that 30 percent of its existing customers upgrade their product each quarter.
You can find out more about the product and sign up for a 14-day free trial on the Bloomfire website.
-

Three in four UK homes now has access to superfast broadband
Publié: octobre 24, 2013, 4:19pm CEST par Ian Barker
 UK telecoms regulator Ofcom's annual Infrastructure Report update published today shows that 73 percent of premises are now able to receive superfast broadband, up from 65 percent last year.
UK telecoms regulator Ofcom's annual Infrastructure Report update published today shows that 73 percent of premises are now able to receive superfast broadband, up from 65 percent last year.Ofcom defines "superfast" as networks delivering download speeds of at least 30 Mbit/s, typically delivered using fiber optic cabling. Around 22 percent of connections now fall into this category with some 4.8 million consumers now having superfast connections, more than doubling last year's 2.1 million figure.
Traffic is on the up too with 650 million gigabytes of data being sent over fixed broadband connections in June, a 26 percent increase over last year. For people who like a handy real-world reference that's equivalent to a billion copies of the Encyclopedia Britannica.
The report also looks at mobile trends and notes that the number of public Wi-Fi hotspots has more than doubled over the year to 34,000. The amount of data being transferred via hotspots has also more than doubled to around 2 million gigabytes a month.
For the first time Ofcom has looked at mobile coverage on the UK's road network and concludes that just 35 percent of A and B roads are served by all four 3G networks and 9 percent has no coverage at all. Over the coming year it intends to look at coverage on the rail network too.
"Superfast broadband is rolling out fast across the country, and 4G mobile will reach at least 98 percent of the population. This is really good news but there remain considerable challenges, not least in hard-to-reach areas for mobile and home internet services," says Ed Richards, Ofcom Chief Executive. "We know consumers increasingly expect superfast speeds, but it’s also important to make sure people can connect over a very wide area. That is why we are doing everything we can to support moves to improve coverage in difficult areas such as roads and train lines".
The full report is available as a PDF from Ofcom's website.
Image Credit: Luis Louro/Shutterstock
-

Mobile strategy becomes a priority for business
Publié: octobre 23, 2013, 5:44pm CEST par Ian Barker
Mobile phones are almost as important as PCs for engaging with customers according to the results of a survey released by enterprise mobile specialist OpenMarket.
The study of 167 business leaders in the USA carried out by Forrester Consulting showed that 74 percent now think that mobiles are an important channel for customers, partners and employees, as against 79 percent for PCs.
It's hardly surprising then that 63 percent of enterprises now think that customer engagement is the key factor in developing their mobile strategy. In fact engagement rates much higher than customer satisfaction (38 percent) and revenue generation (27 percent) in driving mobile use.
The tools used in developing mobile strategy are still led by SMS, 70 percent of those surveyed using it to communicate with their customers, with the use of QR codes following on 60 percent.
Of the companies surveyed 63 percent are spending less than $5 million a year on their mobile strategy. The report questions whether this is enough to sustain ongoing projects. It also finds that only four in ten companies are using in-house staff to build mobile solutions with the rest seeking technology partnerships.
A copy of the report's whitepaper is available on OpenMarket's website and you can see a handy infographic summary below.
-

The real cost of ransomware
Publié: octobre 23, 2013, 5:16pm CEST par Ian Barker
 Ransomware, software that locks you out of your PC and asks for a fee in order to release it, has been around for quite a while. The first examples date back to the late 1980s but in its most recent form it started to gain popularity with malware writers in 2006, starting in western Europe and rapidly spreading to the rest of the world.
Ransomware, software that locks you out of your PC and asks for a fee in order to release it, has been around for quite a while. The first examples date back to the late 1980s but in its most recent form it started to gain popularity with malware writers in 2006, starting in western Europe and rapidly spreading to the rest of the world.Finnish security specialist F-Secure has been working with the police on a joint investigation and reckons that just one case could be responsible for up to $800 million of damage and losses.
A single gang using the Reveton Trojan managed to infect more than 30,000 computers in Finland alone and over 5 million worldwide. Reveton currently charges $300, or 100 euros in Europe, to unlock the system. That amounts to a potential profit of some $800 million from this one attack.
Naturally not everyone pays up, so the perpetrators won't see the full potential profit. However, many of those infected will need to spend time and money recovering their systems so there's an economic cost to factor in. F-Secure cites the case of a hard drive of photographs which cost $6,000 to recover. That seems a little extreme but if only one percent of the Reveton attack victims incurred that sort of cost it still adds up to a hefty $300 million dollars. If you don't fancy turning to a life crime, therefore, data recovery seems like a good business opportunity.
To highlight the problem F-Secure has produced a useful infographic and is hosting an online ransomware Q&A until the end of October.
If you or anyone you know has been a victim of ransomware do let us know your experiences in the comments.
Image Credit: Robynrg/Shutterstock
-

PaaSLane cloud migration tool enters public beta phase
Publié: octobre 22, 2013, 5:38pm CEST par Ian Barker
Migrating existing applications to the cloud can be a major headache for companies. Extensive testing is needed to ensure everything works as it should and without it the process becomes something of a leap in the dark. In a bid to help with this Boston based Cloud Technology Partners has produced its PaaSLane product, released today as a free public beta.
The idea behind PaaSLane is a simple one, automatically analyzing the code of an application before migration in order to cut down the amount of manual effort required. Out of the box the software is tuned generically to work with all cloud platforms, so it's compatible with Azure, Google and Amazon Web Services. However, users can define their own rule sets to take account of special requirements or non-public clouds.
"As cloud adoption accelerates, our customers are looking for ways to automate assessing for cloud readiness across hundreds of applications. Software development organizations need an effective way to clearly identify issues and estimate the effort required to optimize applications for the cloud," says John Treadway, senior vice president at Cloud Technology Partners. "PaaSLane finds issues and estimates the time required to address them in a matter of minutes, giving management an objective measure of cloud readiness across application portfolios, while providing development teams with a roadmap to start fixing them immediately".
As well as assisting the migration, PaaSLane can help to streamline the code, enabling developers to spot any sections that may cause problems and help with ongoing compatibility and stable operation. It uses static code analysis to examine application source code, finding common patterns that might affect application performance, stability, security, and scalability in cloud deployments. It then provides recommendations based on cloud best practices. The program shows clear, graphical overviews of a project's progress with the ability to drill down to the level of individual lines of code. The developers reckon that PaaSLane can cut migration times by up to 25 percent.
You can register for the public beta now at www.paaslane.com and it will remain free until the end of the year or until the beta period ends whichever comes first.
-

No 3G? No Wi-Fi? No problem
Publié: octobre 18, 2013, 11:06am CEST par Ian Barker

Smartphones have become such a big part of many people's lives in recent times, allowing us to stay in touch with the Internet wherever we go, that occasions when you can't get a data network or Wi-Fi signal become extremely frustrating, it's almost like losing a limb.
French developer Altheia has an answer in the form of a new app for Android phones called Be-Bound which it claims can keep you in touch with the Web even if there's no 3G, 4G, Edge or Wi-Fi signal available.
"We started with a simple observation: everybody has faced connection issues, even in covered areas like the train, the subway, indoor or any other areas with low connectivity," says Albert Szulman, CEO of Be-Bound.
You might be wondering how it's possible to stay in touch without a Web connection -- short of setting fire to the phone and using it to send smoke signals. But Be-Bound has developed a clever low-bandwidth technology that makes use of the old 2G network as a transport layer to exchange information between the Web and your phone. You can thus maintain Internet connectivity in areas where otherwise you'd be unable to get online.
The connection is claimed to work with any telecoms provider in the world, all users need to do is download the free app. This has built-in functions for email, news, stock quotes and other common tasks. Using Be-Bound is free when you do have an Internet connection, though it uses a tiny amount of bandwidth. When no data network is available the service works with SMS and pre-paid credits and is cheaper than standard roaming costs.
Beta versions should be available to download following the app's official launch at the Dublin WebSummit on October 30th, meantime you can find out more and register your interest at http://www.be-bound.com/en/
Image Credit: Dario Lo Presti/Shutterstock
-

New app uses social collaboration to identify projects for automation
Publié: octobre 17, 2013, 4:02pm CEST par Ian Barker
Business automation specialist Automation Anywhere has launched a new application aimed at helping businesses identify tasks and prioritize them based on the crowd-sourced wisdom of their user community.
Called Cumulus (could this possibly be using the cloud?) the application is launching via the Yammer enterprise social network. It will be available as a featured application via Yammer's app directory. Using Cumulus, anyone in an organization will be able to suggest a task to be automated, vote on the tasks that seem most valuable, contribute suggestions to existing initiatives, and track any active automation projects.
Built-in tools help identify the savings that can be made from automation of tasks. It calculates the hours and money that can be saved and so helps point out the tasks where automating will deliver the best return on investment.
"Enterprise social is the new operating system for organizations, and has the power to deliver real, measurable ROI," says Mihir Shukla, founder and CEO of Automation Anywhere. "Cumulus provides a way for entire organizations to tap in to the social revolution and contribute ideas for automating tasks while keeping the value of doing so at the forefront. We know that Yammer, with its large user base and commitment to making social enterprise collaboration work, is the perfect place for Cumulus to be first available".
Project-level dashboards will make it easy to spot potential savings, and visualization tools allow step-by-step tracking of projects. There's also a leader board to identify those members of the team doing the most to champion automation.
"Automation Anywhere has its finger on the pulse of what businesses should be doing with social platforms: utilizing them to pinpoint high return activities, like process automation," says Gregory Love, Business Development Manager at Yammer. "We look forward to Yammer users leveraging Cumulus to find the most crucial business processes to automate throughout their organizations".
You can find out more and sign up to try the free version on the Automation Anywhere site.
Featured Image Credit: Alexander Kirch/Shutterstock
-

And the winner of best security software for small business users is...
Publié: octobre 17, 2013, 11:15am CEST par Ian Barker

Independent testing organization AV-comparatives has released the results of its 2013 Business Software Review. This looks at security software for smaller and medium businesses, taking as its basis a single site network with a Windows Server 2012 domain controller and 25 client PCs running a mix of Windows XP, 7 and 8.
The key thing here is that this is the type of business which may not have its own IT manager so the report considers the management and monitoring of the software from the viewpoint of someone who isn't a specialist in IT and only looks after the system part time.
The ten products tested were: AVIRA Endpoint Security 13.0, Bitdefender Cloud Security for Endpoints 5.1, ESET Endpoint Security 5.0, F-Secure Client Security 11.0, G DATA AntiVirus Business with Patch Management 12.0, Ikarus security.manager 4.2, Kaspersky Endpoint Security for Business Advanced 10.1, Sophos Endpoint Security and Control 10.2, Symantec Endpoint Protection12.1 and Webroot SecureAnywhere Endpoint Protection 8.0.
All of the packages were found to have a straightforward interface which shouldn't present problems for part-time system admins. However, Ikarus was noted as being more suitable for confident administrators, F-Secure may require some initial configuration by an IT professional, and ESET needs a little practice for users to find their way around.
Webroot, Symantec, G DATA and Bitdefender gained particular praise for their simple to use interfaces, making key information easy to access.
Overall the ten programs were found to be pretty evenly matched, all offering trouble-free installation and user-friendly interfaces for both console and client deployments. As a result all get AV-Comparatives Approved Business Product award thanks to no major flaws being found. It seems therefore that the best security package for smaller businesses is… All of them, so it will pay to compare features and shop around for a good deal. You can download the full, detailed findings of the report as a PDF.
Image Credit: alphaspirit/Shutterstock
-

Enterprise social networking meets content collaboration as tibbr partners with Huddle
Publié: octobre 16, 2013, 7:00pm CEST par Ian Barker
 We've looked at Huddle's drive to create a connected desktop environment allowing people to collaborate via the cloud before, but now the company is aiming to take things a step beyond. Announcing a collaboration with TIBCO Software's enterprise social network tibbr it aims to further streamline the sharing process.
We've looked at Huddle's drive to create a connected desktop environment allowing people to collaborate via the cloud before, but now the company is aiming to take things a step beyond. Announcing a collaboration with TIBCO Software's enterprise social network tibbr it aims to further streamline the sharing process.This will allow users to socialize, share and manage content in the cloud in a seamless way. From within the tibbr environment, users will be able to quickly and easily attach Huddle files to their updates for information and feedback. The files remain stored within Huddle's secure cloud and retain all of their security, permissions, and versions. The end result is a unified work environment bringing together people and information in real time.
"Our partnership with tibbr brings content collaboration and enterprise social networking together in one central environment for enterprises worldwide," explains Alastair Mitchell, CEO of Huddle. "By placing content at the core of social interactions and giving customers the ability to use tibbr's social features to distribute and discuss Huddle content, we're improving office workers' productivity and efficiency. Now people no longer have to skip between multiple applications to get their jobs done. We’re excited to be partnering with one of the key players in enterprise social networking and looking forward to transforming the way people work worldwide".
"In order for companies to get the best use out of their content, collaboration is essential," says Ram Menon, president, social computing at TIBCO. "tibbr and Huddle have both seen great momentum with enterprises seeking collaborative, mobile solutions that drive business performance. With this valued partnership, we will support one another as we rapidly grow into new markets".
In order help existing users of both platforms to take full advantage of the new partnership and to encourage adoption, each company is offering a yearlong subscription to the other's service to its existing users.
Image Credit: leedsn/Shutterstock
-

DataStax offers free software for startups
Publié: octobre 16, 2013, 11:07am CEST par Ian Barker
 Online application specialist DataStax has announced a new initiative to help startup businesses. DataStax software delivers a scalable big data platform and is used by large organizations including Adobe, eBay and Netflix, but the DataStax Startup Program allows eligible startups to deploy DataStax Enterprise applications for free.
Online application specialist DataStax has announced a new initiative to help startup businesses. DataStax software delivers a scalable big data platform and is used by large organizations including Adobe, eBay and Netflix, but the DataStax Startup Program allows eligible startups to deploy DataStax Enterprise applications for free.The company has also launched a new DevCenter tool, which is free for its existing users, to allow the graphical creation of queries and database objects in Cassandra Query Language. This is along with free online training courses to teach users how to work with big data in the open-source Apache Cassandra database.
New companies qualify for the Startup Program if they have received less than $20 million in funding and operate within a designated revenue threshold.
"I remember when we at DataStax were a cash-strapped startup, and we want to help companies in that scenario succeed," says Matt Pfeil, co-founder and vice president of customer solutions at DataStax. "The DataStax Startup Program gives young companies access to software that will let them focus on their customers rather than fighting challenges with data growth".
If you're running a startup business you can find more about the DataStax Startup Program on the company's website.
The free online Cassandra training will be available in November, aimed at helping developers and administrators get the most out of the software. It uses a self-paced format with hands on exercises and ends in a graded assessment. Pre-registration is available at the DataStax Academy page.
Image Credit: Olivier Le Moal/Shutterstock
-

BullGuard Internet Security gets improved detection and a better interface
Publié: octobre 15, 2013, 4:14pm CEST par Ian Barker
Security specialist BullGuard has launched what it's calling its most advanced Internet Security suite yet. It's designed to offer industry leading protection regardless of the user's ability and to run quietly and efficiently in the background.
Aside from dropping the year from the product's name, highlights of the latest version include an enhanced behavioral detection engine to guard against zero day threats, a revised user interface offering easier one-click access to functions, free 24/7 support and free upgrades to newer versions.
A choice of basic and advanced displays ensures that anyone can make the most of the package. Unneeded or unwanted functions are hidden to simplify operation. Alex Balan, Head of Product Management at BullGuard, says, "It is our most advanced security suite yet, and one that offers a significantly improved degree of control and operation".
Outside the core security functions the package offers an array of other tools. These include online backup with 5GB of free storage, a Vulnerability Inspector that checks installed applications for updates and known exploits, a PC Tune-up module and parental controls.
The new interface uses Windows 8-style tiles to offer a consistent feel and easy access to all modules. The package protects three PCs for a year and there's a 60-day free trial available from the BullGuard website.
Balan concludes, "As ever, we've placed a strong focus on ensuring that our excellent reputation in the security market remains intact by revising and improving core security. We've also further improved usability by ensuring that the majority of tasks can be set to run in the background, with as little user interaction and impact on system resources as possible. In short, once installation is complete a user can let it do its job with minimal interaction".
If you have an eye for a bargain, you can pick up last year's version from the Downloadcrew store at a substantial discount.
-

Argos launches own-brand tablet aimed at teenagers
Publié: octobre 15, 2013, 11:35am CEST par Ian Barker

UK catalog store retailer Argos will start selling its own £99.99 Android tablet on Wednesday. The Argos MyTablet undercuts Tesco's £119 Hudl, but the saving is at the cost of a lower spec. MyTablet has only 8GB of storage to the Hudl's 16GB, shorter battery life and a lower resolution screen. It also comes only in silver or pink rather than the Hudl's choice of four colors.
Argos says its tablet is targeted at the teenage and pre-teen market and it ships with parental controls pre-enabled. The device runs Android 4.2.2 Jelly Bean and comes with 19 pre-installed apps including BBC iPlayer, Angry Birds and social networking tools.
The company seems confident that there's a market for the device. John Walden, Argos' managing director, says, "Millions of people have bought tablets during the last year but there is still around 75 percent of the UK population without one". A recent Ofcom survey showed that around a quarter of British 12-15 year olds now have their own tablet.
MyTablet's main competition is likely to be the Kindle Fire which Amazon sells for £99 in the UK, though it's also up against a raft of devices from lesser-known brands. Walden says, "Customers have never had such a good quality tablet at such an affordable price. At just £99.99 the Argos MyTablet is highly competitive with a great specification, and fits neatly in the range of tablets we have on offer".
-

Websites use device fingerprinting for secret tracking
Publié: octobre 11, 2013, 2:55pm CEST par Ian Barker

We all realize, or should do, that whatever we do online leaves a trail. Usually this is in the form of cookies or other information over which we have some control and which is subject to a degree of legal regulation, but what about other, more insidious, forms of tracking?
New research carried out by Netherlands-based university KU Leven reveals that a small number of sites are secretly tracking their users. The study by KU Leuven-iMinds researchers has uncovered evidence that 145 of the Internet's 10,000 top websites carry out tracking without the knowledge or consent of their users. The sites do this by using hidden scripts to extract a device fingerprint from users' browsers. This technique avoids the legal restrictions imposed on the use of cookies as well as ignoring the Do Not Track HTTP header. The study's findings suggest that secret fingerprinting is being used to get around legitimate barriers to tracking.
By collecting the properties of PCs, smartphones and tablets including their screen size, the software versions they're running and which plug-ins are installed, fingerprinting can accurately identify and track users. A 2010 study by the Electronic Frontier Foundation showed that, for the vast majority of browsers, the combination of these properties is unique, and can be used to track users without relying on cookies. Device fingerprinting generally targets either Flash, the common browser plugin which enables animations, videos and sound files, or JavaScript, the programming language for web applications.
The KU Leven research is the first concerted effort to measure just how widespread device fingerprinting is. The researchers found that of the Internet's top 10,000 websites 145 of them use Flash-based fingerprinting. More worrying still is that some of the Flash objects included questionable techniques such as revealing a user's original IP address even when they're visiting a website through a proxy.
The study also found that 404 of the top million sites use JavaScript-based fingerprinting, which allows sites to track non-Flash devices and mobile phones. Although this is only a tiny percentage of sites it's still evidence of a disturbing trend.
Of course device fingerprinting does have legitimate security-related uses including fraud detection and protection against account hijacking. But this study suggests it's also being used for analytics and marketing purposes via fingerprinting scripts which are hidden in seemingly innocuous advertising banners and web widgets.
In order to detect websites which are using device fingerprinting technologies, the researchers have developed a tool called FPDetective. This crawls and analyses sites looking for suspicious scripts. This tool and its source code will be made freely available for other researchers to use and build on, so we can expect to see fingerprinting detection appearing in security products in the future.
The report's findings will be presented at the 20th ACM Conference on Computer and Communications Security this November in Berlin. Meantime you can download the full paper outlining the research methodology as a PDF.
Photo Credit: Maksim Kabakou/Shutterstock
-

Sleeping with your smartphone? You should use protection
Publié: octobre 11, 2013, 11:25am CEST par Ian Barker

Many of us are so attached to our mobile devices that we take them to bed with us, but we're failing to take basic security precautions. This is among the findings of the 2013 Norton Report.
The report shows that whilst the number of online adults who have experienced cybercrime has fallen, the average cost per victim is up by 50 percent. In the UK, however, the cost per victim has fallen, down from £144 in 2012, to £101 in 2013.
"Globally, the cost per victim is up," says Sian John, security strategist at Symantec. "But in the UK the cost is down quite significantly. This is due to cybercriminals shifting tactics, perhaps as Brits become more aware of scams. Criminals also use tactics where there is a lower cost per head to victims, as they believe scams like this have a higher chance of escaping notice, and as the number of victims has remained static, they are clearly still making money from online fraud".
Most worrying though are the findings for mobile devices. While nearly half of those surveyed are so attached to their mobile devices that they sleep with them it seems that they're doing so without using protection. Forty-eight percent of smartphone and tablet users do not take even the basic precautions such as using passwords, having security software or backing up files from their mobile devices. The same percentage don't log out after each session and 32 percent admit to sharing their social media password with others.
"If this was a test, mobile consumers would be failing," says Marian Merritt, Internet Safety Advocate at Symantec. "While consumers are protecting their computers, there is a general lack of awareness to safeguard their smartphones and tablets. It's as if they have alarm systems for their homes, but they’re leaving their cars unlocked with the windows wide open".
Since 49 percent use their devices for both personal and business this potentially exposes more information to cybercriminals. Because one in five also accesses their social network on their work phone, Symantec has warned that hasty social media updates and snaps, dubbed "auto-pilot posting," are putting personal and professional privacy at risk.
John explains, "Whether we’re at home or in the office, it’s become second nature to pop a quick update or picture on our social profiles. The information we share can be completely harmless, but the danger lies in the fact that the action has become automatic. When we’re on auto-pilot, it takes mere seconds to post something online. Yet with so many different accounts on one device, public and private, it’s easy to address the wrong person and run into trouble".
The Norton Report (formerly known as the Norton Cybercrime Report) is one of the world's largest consumer cybercrime studies, based on self-reported experiences of more than 13,000 adults across 24 countries, aimed at understanding how cybercrime affects consumers, and how the adoption and evolution of new technologies impacts consumers' security. You can find out more at www.symantec.com.
Photo Credit: Shumilina Maria/Shutterstock
-

Look out -- the robot middle-class is on the way
Publié: octobre 10, 2013, 4:50pm CEST par Ian Barker

The emergence of a generation of smart machines taking over middle-class jobs within 15-years is a "futurist fantasy" according to 60 percent of respondents to Gartner's 2013 CEO survey. However, the analysts predict the rise of smart machines will have widespread business impact within only seven years.
"Most business and thought leaders underestimate the potential of smart machines to take over millions of middle-class jobs in the coming decades," says Kenneth Brant, research director at Gartner. "Job destruction will happen at a faster pace, with machine-driven job elimination overwhelming the market's ability to create valuable new ones".
According to Gartner's "Maverick" research, designed to provoke unconventional insights, CIOs need to change their mission to address the proliferation of smart machines in a widening range of jobs and consider the impact this trend might have on their career paths and on increasing levels of unemployment.
Machines are evolving from automating basic tasks on the production line to becoming advanced self-learning systems as capable as the human brain in many highly specialized professions. As such, the next wave of job losses will likely occur among highly valued specialists during the next decade.
"The bottom line is that many CEOs are missing what could quickly develop to be the most significant technology shift of this decade," says Mr Brant. "In fact, even today, there is already a multifaceted marketplace for engineering a 'digital workforce,' backed by major players on both the supply and demand side. This marketplace comprises intelligent agents, virtual reality assistants, expert systems and embedded software to make traditional machines 'smart' in a very specialized way, plus a new generation of low-cost and easy-to-train robots and purpose-built automated machines that could significantly devalue and/or displace millions of humans in the workforce".
Gartner reckons that the capability and reliability of smart machines will dramatically increase through 2020 to the point where they will have a major impact on business and IT functions. Businesses who fail to adapt to this trend will struggle to compete in the marketplace.
"It's worth remembering that IT cost is typically about four percent of annual revenue, whereas the labor costs that can be rationalized by smart machines are as high as 40 percent of revenue in some knowledge and service industries," said Mr. Brant. "The supply side of the market -- including IBM, GE, Google, Microsoft, Apple and Amazon -- is placing large bets on the success of smart machines, while the demand side includes high-profile first movers that will trigger an 'arms race' for acquiring and/or developing smart machines".
The good news for the middle-classes, at least in the short term, is that Gartner foresees some barriers to the robots taking over. These include the price of the technology not falling fast enough, unions organizing against machines taking jobs and citizens protesting about high unemployment. It also predicts that consumers may reject machines perhaps due to a highly publicized catastrophe or simply because of demand for human interaction. The full report is available on Gartner's website.
So, could a machine do your job? How would you feel if you were about to be replaced by a robot? Would you be happy to consult, say, a robot lawyer? Do let us know in the comments -- extra kudos will be gained if your reply is written by machine!
Photo Credit: Palto/Shutterstock
-

PC market continues to decline but beats expectations
Publié: octobre 10, 2013, 2:00pm CEST par Ian Barker

Reports from leading analysts for the third quarter of 2013 suggest that the PC market is still in decline. However, sales haven't declined as quickly as predicted.
According to IDC's Worldwide Quarterly PC Tracker PC shipments totalled 81.6 million units in the third quarter. This represents a 7.6 percent decline over the same period last year, better than the 9.5 percent that was being predicted. IDC says the market was buoyed by business purchases plus the channel intake of Windows 8.1 systems in September.
Rival analysts Gartner record slightly lower shipments of 80.3 million units, an 8.6 percent decline over last year. This marks the sixth consecutive quarter of decline. Mikako Kitagawa, principal analyst at Gartner says, "The third quarter is often referred to as the 'back-to-school' quarter for PC sales, and sales this quarter dropped to their lowest volume since 2008. Consumers' shift from PCs to tablets for daily content consumption continued to decrease the installed base of PCs both in mature as well as in emerging markets. A greater availability of inexpensive Android tablets attracted first-time consumers in emerging markets, and as supplementary devices in mature markets".
Broken down by market the US continues to show recovery with sales down only 0.2 percent according to IDC or 3.5 percent up on Gartner's study. Europe the Middle East and Africa (EMEA) continue to decline. Asia Pacific shows an 11.2 percent drop in shipments on Gartner's study. IDC separates out Japan and shows an Asia Pacific (excluding Japan) decline of 8.8 percent whilst most of the top five vendors in Japan saw growth.
Looking at vendors, Lenovo and HP continue to battle for supremacy, each with around 17 percent of the market worldwide. Dell rounds off the top three with 11.7 percent. Only these three recorded positive shipment growth in 2013.
iChartsIf you look at the US only, HP remains the clear leader with around 27 percent of the market, followed by Dell with 21 percent, and Apple with 13.4 percent (Gartner) or 11.6 percent (IDC). Lenovo only manages fourth place in the US with around 10 percent of the market but recorded an impressive 24.6 percent growth over the same quarter last year.
"The United States outperformed many other regions as growth stabilized just under 0 percent. Continuing upgrades from Windows XP boosted shipments, particularly in the commercial desktop segment, while retail acceptance of new and emerging product categories, such as Chromebooks and Ultraslims, helped the portables segment," says Rajani Singh, Senior Research Analyst, Personal Computers at IDC.
These figures are preliminary and may change a little in the final analysis but they do seem to indicate that PC market hasn't reached the bottom just yet.
Photo Credit: Mopic/Shutterstock
-

Cloud buyers need more clarity say experts
Publié: octobre 10, 2013, 12:25pm CEST par Ian Barker
 Cloud vendors must establish one definition for cloud to protect buyers falling foul of multiple interpretations of the technology, so says a panel of technology experts brought together by hosting company UK Fast.
Cloud vendors must establish one definition for cloud to protect buyers falling foul of multiple interpretations of the technology, so says a panel of technology experts brought together by hosting company UK Fast.With more and more providers joining the cloud market and confusion still reigning over what the term actually means, baffled buyers are at risk of paying over the odds for technology that isn't technically cloud, or worse entrusting their business data to unsuitable cloud solutions.
Lawrence Jones, CEO at cloud and colocation company UKFast, says, "We see different definitions of hosting, hybrid and cloud from every provider. To us, hybrid is where the whole solution is in a data centre, and part of it is dedicated and part of it shared. People don’t ask the question about what it all means. No-one would ever ask what the technology of the cloud is, they just log on and move on. We make sure that we have the conversation with clients asking why they want to move to the cloud and work out the best option from there -- whether that's cloud or dedicated".
Simon Swan, co-founder of online recruitment marketplace HiringHub.com says, "There is a real cause for someone to put together a dictionary for the cloud. Define the key terms and then whoever deals with IT in a business can go to that place and get the information. Then they will have a grasp of it before they engage with a cloud company".
But Nick Kavanagh, operations director at Gteq, disagrees that people are confused, saying that he believes that, thanks to cloud sneaking its way into our personal lives more and more, businesses are more "cloud savvy" than they realise. "Businesses have been using it [the cloud] for a long time. Email systems like Hotmail, or programmes like Dropbox are all cloud-based. People don’t realise they are using it but they have been, and they are comfortable with it".
If you want to learn more you can see video clips from the debate on YouTube. Are you clear on what the cloud means? Do you think that businesses need more help to understand what it can do for them? Let us know via the comments.
Photo Credit: eteimaging/Shutterstock
-

The challenge of tablets in the enterprise
Publié: octobre 10, 2013, 11:55am CEST par Ian Barker
 Independent analysis company Ovum has released a new report titled Challenges and Best Practices for Deploying Tablets in the Enterprise which finds that tablets are ever more prevalent in businesses.
Independent analysis company Ovum has released a new report titled Challenges and Best Practices for Deploying Tablets in the Enterprise which finds that tablets are ever more prevalent in businesses.It notes that as the market for tablets grows, usage of these devices is changing the way people work and is having a noticeable impact on the enterprise. Whether through units supplied by the company or BYOD, fast increasing numbers of tablets are being used to access corporate data and applications.
Richard Absalom, analyst for Consumer Impact Technology at Ovum and author of the report says, "Coupled with imaginative thinking around how mobile apps could provide new or improved processes in specific roles, tablet deployments have the potential to change the way that businesses operate. The primary challenge for the enterprise is to turn tablet usage into a genuinely transformative deployment, taking into account but not just reacting to demand from employees that are bringing their own tablet or want to be provided with one".
The survey, conducted in the second quarter of this year, finds that 17.6 percent of employees had already been provided with a tablet by their employer, up from 12.5 percent in 2012. Of respondents that owned a personal tablet, 66.7 percent used that device at work. The number of personal tablet owners increased from 28.4 percent in 2012 to 44.5 percent in 2013. Given this growth it's safe to assume a fast increasing number of personally owned tablets are also being used at work.
According to Absalom, "Although increasing numbers of employees are being provided with a tablet by their employer, the primary route for tablets into the enterprise is through the consumer/employee channel. Over 66 percent of employees who personally own a tablet use them for work." He goes on to suggest, "The first step to a successful tablet deployment is to understand employee behaviour and activity. Employees are using multiple devices to access corporate data and content, and any tablet or mobility strategy must be set in this context".
Providing access to corporate data via tablets presents new security challenges. But Ovum warns that it's important any security solution doesn't come at the expense of the user experience and risk turning users away from using approved software.
You can read more or access the full report via the Ovum website.
Photo Credit: bikeriderlondon/Shutterstock
-

Faster and easier vSphere 5 upgrades with CloudPhysics
Publié: octobre 7, 2013, 4:33pm CEST par Ian Barker
 VMware's recent release of a new version of its flagship server virtualization product vSphere 5.5 means that many businesses will be planning to upgrade to the new software. However, as with all major upgrades there's a degree of risk involved, especially if the software is part of your enterprise's core infrastructure.
VMware's recent release of a new version of its flagship server virtualization product vSphere 5.5 means that many businesses will be planning to upgrade to the new software. However, as with all major upgrades there's a degree of risk involved, especially if the software is part of your enterprise's core infrastructure.Operations management specialist CloudPhysics rides to the rescue of hard-pressed system admins with a number of tools to streamline the upgrade. The software as a service offering performs a number of checks to help ensure that the vSphere upgrade goes smoothly.
These are presented as a series of cards relating to each of the upgrade stages and presenting the necessary information in an easy to understand format. Starting with selecting a host to upgrade, the cards begin with a host inventory to take you through a compatibility check, system release notes and upgradability. A separate card looks at device I/O compatibility. Finally CloudPhysics also flags relevant VMware knowledgebase articles to ensure you don't miss anything important that may impact on your installation.
You can read more about how CloudPhysics can help your vSphere upgrade to run smoothly and try the software out by visiting the company's blog.
Photo Credit: Liljam/Shutterstock
-

Panabee sets sights on Go Daddy
Publié: octobre 4, 2013, 4:18pm CEST par Ian Barker
 As the Internet gets bigger and more crowded it can be increasingly difficult to find a catchy domain name. Startup company Panabee aims to provide a simple tool for individuals and businesses to find great domain names and it has just reached the milestone of 10 million monthly searches -- up 50 percent from 2012.
As the Internet gets bigger and more crowded it can be increasingly difficult to find a catchy domain name. Startup company Panabee aims to provide a simple tool for individuals and businesses to find great domain names and it has just reached the milestone of 10 million monthly searches -- up 50 percent from 2012.Given the scarcity of available names, Panabee offers a new interface for brainstorming alternatives besides dot-coms. As consumers become more Internet savvy, it allows businesses to embrace different domain endings like .co.uk, .biz, .net and more.
Existing services make suggestions as well, but most revolve around alternative dot-coms. Panabee, however, offers a one-click ability to set and search new suggestions around one of 20 different top level domains. As new TLDs are opened up at the end of 2013 it hopes to grab opportunities in a changing market.
Panabee's domain search also allows for easy checking of multiple domains at once, including country-specific domains, as well as social media and mobile applications. Routinely users will search for domains without knowing whether the social media profiles and apps associated with these names are taken. With Panabee, domain searches show related terms, web search results and social media profiles containing the keywords so you get a complete overview of your chosen name and have the ability to brainstorm ideas.
Panabee's marketing has long followed a different script than Go Daddy’s, "sex sells". Say the founders of Panabee, "We market our products with humor, not money. Because it's bold and clever. Also because we spent all the VC money on Will & Kate royal wedding posters". They add, "If you needed a startup name in 1998, you used Go Daddy. If you need one in 2013, you use Panabee".
You can find out more about this quirky approach to domain searching at www.panabee.com.
-

Emulex boosts data collection for faster corporate networks
Publié: octobre 2, 2013, 3:04pm CEST par Ian Barker

Network connectivity and management specialist Emulex has launched a new NetFlow generator appliance designed to cope with the latest high-speed LANs.
For those unfamiliar with the nuts and bolts of networking, NetFlow is the metadata that describes network traffic. It's used to diagnose problems and find security issues. In the past NetFlow has been generated by the switch, but 10GB Ethernet means some switches can't keep up leading to NetFlow that's intermittent or incomplete.
Emulex's answer to the problem is the EndaceFlow 3040, a dedicated NetFlow generator appliance that takes the process away from the switch and generates 100 percent accurate NetFlows on up to four Ethernet links at speeds up to 10Gb per second line rate. This results in faster detection, identification and resolution of critical security and network issues, improving network uptime and reducing operational expenditures in enterprise data centers.
The EndaceFlow incorporates load balancing to avoid collector overflow and minimize the need for manual configuration. It also supports up to 120 custom filters allowing admins to zero in on particular types of traffic or on individual IP addresses. Units can be placed at different points in the network making the EndaceFlow a solution that's easily expandable as the enterprise grows.
When combined with EndaceVision software data collected by the hardware can be displayed in an easily visualized form. It can also be combined with behavioral-based analytics tools from companies such as Lancope and SevOne, NetOps and SecOps which means personnel are able to create complete solutions that significantly speed the resolution of critical network and security issues.
"Traditionally, end users have used routers and switches to generate sampled NetFlows, which severely limits behavioral analysis and can impact switch and router performance," says Mike Riley, senior vice president and general manager of the Endace portfolio at Emulex. "The Emulex EndaceFlow 3040 addresses these issues by offloading NetFlow generation onto a purpose-built appliance that can generate unsampled NetFlow across multiple 10GbE links. This gives our customers all of the data they need to diagnose and resolve complex security and network performance issues on 10GbE networks in a fraction of the time previously required".
The EndaceFlow 3040 begins shipping to customers today and will be on show at the Emulex booth at this week's Interop in New York.
-

MyIT makes it easier for companies to embrace BYOD
Publié: octobre 2, 2013, 11:24am CEST par Ian Barker

Demand from employees to use mobile devices with different operating systems and applications is the bane of IT managers' lives at the moment. BMC Software aims to ease the burden with its latest version of MyIT. Featuring major new OS expansions and a new HTML 5 universal client to support mobile, desktop and laptop devices, MyIT 1.5 delivers single-point access to a variety of company resources from any device.
We looked at the MyIT app back in June at which time it was only available for iOS devices. The new version delivers native Android support, a wide array of new self-service features, enhanced language support, and fast and convenient integration with BMC AppZone for enterprise app store access.
With expanded support for smart-office and software defined workspace (SDW) initiatives the app also helps facilitate hot desking. It can integrate with building management systems to schedule occupancy and avoid conflicts. The product has added support for extra languages too in order to broaden its global appeal.
Jason Frye, Deputy CTO for MyIT says, "BYOD is no longer the exception to the rule in large organizations. The ready availability of smart devices and mobile applications means that employees have higher expectations for their IT experience than ever before, and their impatience with substandard IT services is more acutely felt. BMC MyIT allows IT departments to meet and exceed those expectations without undermining manageability or security. With BMC AppZone integration, MyIT now offers BMC customers a powerful and convenient way to access critical IT applications, services and support information from whichever device is best suited to the situation".
For more information and a free trial of MyIT you can visit the BMC website.
Photo credit: bloomua/Shutterstock
-

IBM acquires The Now Factory to extend its big data portfolio
Publié: octobre 1, 2013, 4:31pm CEST par Ian Barker
 IBM has announced that it's reached an agreement to acquire The Now Factory, a Dublin-based provider of analytics software that helps communications service providers (CSPs) deliver better customer experiences and drive new revenue opportunities.
IBM has announced that it's reached an agreement to acquire The Now Factory, a Dublin-based provider of analytics software that helps communications service providers (CSPs) deliver better customer experiences and drive new revenue opportunities.Using The Now Factory’s software, CSPs can gain real-time insights into their customers by analyzing massive quantities of network and business data. With this type of insight they can provide an enhanced quality of service by better managing negative experiences and network outages.
The acquisition complements IBM's MobileFirst Analytics portfolio, which is designed to enhance the way organizations analyze mobile device usage to provide exceptional customer experiences.
"The Now Factory's innovative solutions are all about enabling quick insights for better business results in the highly competitive telecommunications landscape," says Tom Morrisroe, CEO of The Now Factory. "As part of IBM, we can now extend our technologies to a broader range of clients to help them uncover new, untapped growth opportunities, and achieve tangible business value from big data and analytics".
In addition to its ability to detect and resolve issues, The Now Factory's software helps CSPs better understand how a subscriber interacts with cloud-based services, such as mobile applications. For example, a CSP can use The Now Factory's software to investigate customer usage of 3G and 4G LTE data services and identify high volume pre-paid subscribers. This can result in a targeted campaign to convert high volume pre-paid subscribers into post-paid accounts.
"Today's announcement is part of IBM’s strategy to continually establish leadership in the era of big data and capitalize on the opportunity to analyze data in real time," says Bob Picciano, General Manager, Information Management at the IBM Software Group. "The Now Factory’s software enhances IBM’s Big Data and Analytics portfolio by improving the speed, development and implementation of big data solutions, and gives communications service providers the ability to better service their customers".
IBM is keen to to grow its presence in the area of big data, something it expects to account for $20 billion of its revenue by 2015.
Image credit: David Gaylor/Shutterstock
-

Horror stories of enterprise mobility
Publié: octobre 1, 2013, 12:32pm CEST par Ian Barker
 Mobile development platform supplier Appcelerator has released the results of its latest enterprise mobility survey along with a Halloween-themed infographic.
Mobile development platform supplier Appcelerator has released the results of its latest enterprise mobility survey along with a Halloween-themed infographic.The survey of 804 companies worldwide carried out in August this year looks at their current and intended use of mobile systems. Among the key points the study finds that ownership of mobile projects within companies is often unclear with only 15 percent having employed or planning to employ a single leader for mobile developments. This despite the fact that enterprise apps are growing fast with half of companies reporting plans for an enterprise store.
Opening up mobile specific APIs is something 40 percent plan to invest in. There's also a move to support more operating systems, with building apps for multiple devices and platforms being reported as one of the top obstacles to delivery.
62 percent of companies say that they now support three or more operating systems. Some are more popular than others, however, interest in building apps for mobile platforms is strongest for iOS and Android devices with HTML 5 web apps close behind. Blackberry development lags at the bottom of the list.
Delivering quality app experiences to customers is seen as a way of gaining advantage in the market. But 60 percent of companies worry that they're vulnerable to their more mobile aware competition.
You can view the full survey results in suitably goulish infographic form here.
-

Bitrix24 delivers powerful collaboration to smaller enterprises for free
Publié: septembre 27, 2013, 10:50am CEST par Ian Barker

Enterprise social network and collaboration specialist Bitrix24 has released a new version of its free software for smaller businesses. The new product allows users to create, edit and collaborate on documents online, without having MS Office installed on their PCs.
Bitrix 24 has its own instant messenger for video and group chats, in addition users now have access to video conferencing and screen sharing capabilities. Email connectors allow it to work with MS Exchange, Outlook, Gmail, AOL, Yahoo!, iCloud and other popular mail services.
The new release also has an enhanced Activity Stream with real time updates, smart forwarding, notification options and company-wide announcements, while an engagement analytics module (Company Pulse) has been added to provide real time indicators for enterprise social network adoption. This helps identify roadblocks and slow adopters, and shows which intranet tools are currently being utilized by employees.
There's also a new mobile app which allows access to multiple Bitrix24 accounts from a single device. It has a mobile CRM feature too which lets users create and edit CRM entries and invoices directly from a mobile device.
"2013 has been a year of significant growth for us," says Bitrix24 CEO Dmitry Valyanov. "We’ve signed up 90,000 companies, which is well over 500,000 users for the cloud and onsite versions of Bitrix24 intranet. Our workforce grew by 40 percent to over 130 employees and we opened three new sales and support offices. GooglePlay now lists Bitrix24 among the top 5 mobile intranet apps, along with or surpassing such established enterprise social brands as Jive Software, IBM Connection, VMWare SocialCast and TIBCO Tibbr. We hope to have a million users by the end of the year".
Bitrix24 is free to any organization with up to 12 employees with paid cloud plans available for larger businesses. To find out more and sign up for the free version visit www.bitrix24.com.
Photo Credit: Pressmaster/Shutterstock
-

Media, communications and banking lead the charge to big data
Publié: septembre 23, 2013, 12:02pm CEST par Ian Barker
 Investment in big data continues to rise in 2013 according to a new survey by Gartner with 64 percent of companies investing or planning to invest compared to 58 percent in 2012.
Investment in big data continues to rise in 2013 according to a new survey by Gartner with 64 percent of companies investing or planning to invest compared to 58 percent in 2012.The survey of 720 Gartner Research Circle members worldwide, which was conducted in June 2013, was designed to examine organizations' technology investment plans around big data.
Industries leading the way with big data investments are media and communications, banking, and services. Among media and communications organizations 39 percent say that they have already invested in big data, followed by 34 percent of banking organizations and 32 percent of services firms. Planned investments during the next two years are highest for transportation (50 percent), healthcare (41 percent) and insurance (40 percent).
On a regional level North America continues to lead investments with 38 percent of organizations surveyed saying that they have invested in technology specifically designed to address the big data challenge. Asia/Pacific organizations were notably ambitious with 45 percent indicating that they plan to invest during the next two years.
Despite the enthusiasm, however, most organizations take a tentative approach to investment, beginning with knowledge gathering and pilot schemes before embarking on a major rollout.
"For big data, 2013 is the year of experimentation and early deployment," says Frank Buytendijk, research vice president at Gartner. "Adoption is still at the early stages with less than eight percent of all respondents indicating their organization has deployed big data solutions. Twenty percent are piloting and experimenting, 18 percent are developing a strategy, 19 percent are knowledge gathering, while the remainder has no plans or don't know".
When it comes to the uses of big data the survey reveals that there are a wide range of business problems being addressed, although there are some clear patterns. In Gartner's 2012 and 2013 studies, business cases that improve process efficiency and business cases centered around customer experience dominate big data wish lists. In the 2013 survey, 55 percent of organizations say that they are currently addressing enhanced customer experience using big data, while 49 percent are using big data to address process efficiency.
Slightly concerning is that for 15 percent of organizations surveyed the major challenge was understanding what big data is. Nick Huedecker, research director at Gartner says, "Perhaps unsurprisingly, this concern came mainly from respondents with no plans to invest. Organizations should be sure they are educated about big data opportunities in their industry to ensure they are not missing the boat".
You can get the full report on the Gartner website and big data trends will be further examined at the Gartner Symposium/IT Expo in Orlando in October.
Image Credit: Maksim Kabakou/Shutterstock
-

AT&T teams with Microsoft to bring enterprise security to the cloud
Publié: septembre 18, 2013, 5:13pm CEST par Ian Barker
 Microsoft and AT&T have announced a collaboration to allow enterprise customers to connect to Microsoft's cloud platform using a private network. The solution will use cloud integration technology to pair VPN with Azure and allow customers to benefit from enterprise grade security with as much as 50 percent lower latency compared to a normal public Internet connection.
Microsoft and AT&T have announced a collaboration to allow enterprise customers to connect to Microsoft's cloud platform using a private network. The solution will use cloud integration technology to pair VPN with Azure and allow customers to benefit from enterprise grade security with as much as 50 percent lower latency compared to a normal public Internet connection."This is a game changer for businesses that have been seeking a more secure way to reap the benefits of cloud services," says Andy Geisse, CEO, AT&T Business Solutions. "By bringing the security and performance of our virtual private network to Windows Azure, we expect to energize enterprise demand for cloud solutions".
Concerns about security and reliability continue to be cited by businesses when deciding to adopt cloud computing. This new cloud solution takes advantage of the Multi-Protocol Label Switching (MPLS) technology underpinning AT&T’s virtual private network solution. According to independent research firm Forrester Research, 70 percent of multinational enterprises have already adopted global MPLS services, high-performance networks that make it easy to create secure, virtual links between different geographic locations.
"There’s no question that the time for cloud computing is now, and it’s critical we help enterprises embrace the cloud on their terms," says Satya Nadella, executive vice president of Cloud and Enterprise for Microsoft. "Through this strategic alliance with AT&T, we can reduce the barriers to entry for cloud computing by providing a more secure and reliable connectivity option for enterprise customers, accelerating the growth of cloud computing and the rapid adoption of Windows Azure".
AT&T's existing customers are already able to take advantage of this technology with the company's own cloud offerings. By enabling secure links to Azure it opens up secure cloud access to a wider range of businesses. However, the integrated solution isn't expected to be available until the first quarter of 2014.
Photo Credit: Slavoljub Pantelic / Shutterstock
-

IBM reaches for the cloud with social business tools
Publié: septembre 18, 2013, 4:00pm CEST par Ian Barker
IBM has been at the forefront of social business software for a while and today the firm launches its new SmartCloud, a set of cloud-based social business tools aimed at empowering global workforces.
It's aimed at enabling executives such as human resource managers to create communities for new employees to speed up induction time, for example, or sales executives to conduct impromptu video chats with colleagues and share information. By combining social tools and mobile devices in the cloud it aims to help people work more effectively, collaboratively and securely from any location.
SmartCloud is divided into a number of sections. SmartCloud Connections includes features such as File Sync and Share that lets employees -- such as product development staff -- access the cloud and share important documents in the way that works best for them.
SmartCloud Communities introduces new social bridging capabilities which can deliver marketing teams a single view into their social data and all their communities, whether on premises or in the cloud, so they can easily interact with team members across the entire business, access and share new proposals and identify experts to answer questions. This can be extended to cover external agencies, partners and clients making for effective virtual meetings and presentations.
SmartCloud Docs adds a social element to traditional office productivity tools, allowing the sharing and collaborative editing of documents, spreadsheets and presentations in real time. In addition SmartCloud Notes reduces reliance on the email inbox by making it easy to move between key tools including email, calendars and files from a single intuitive web interface.
"Successful workforces today are fueled by powerful social technologies that give employees access to vital information and the insights of colleagues while on the go," says Alistair Rennie, general manager, social business at IBM. "With our biggest set of new capabilities introduced to date, we give businesses the opportunity to forever change how employees work through new powerful features that allow them to remain connected and productive from anywhere and in the end drive impactful outcomes for their organization".
IBM SmartCloud for Social Business will be available on SoftLayer's industry leading infrastructure in a new Amsterdam data center, along with new "on-boarding" services that help customers quickly move mail, calendar and contacts to the cloud in a way that best meets their timing and business objectives.
For details on the entire suite of new features you can visit www.ibmcloud.com/social or tune in to the virtual launch event taking place at 10am ET at http://ibm.co/reinventwork.
Photo Credit: Melpomene/Shutterstock
-

Manage your electronic life with doxo
Publié: septembre 18, 2013, 11:35am CEST par Ian Barker
 We all have information relating to banks, insurance companies, utilities, retailers and more that we need to keep. But now that we increasingly manage our accounts online how do you cope with saving statements and other important information that you receive electronically?
We all have information relating to banks, insurance companies, utilities, retailers and more that we need to keep. But now that we increasingly manage our accounts online how do you cope with saving statements and other important information that you receive electronically?The online organizer service doxo thinks it has the answer and has added email to the range of information it can collate. The doxo Email Import option automatically imports, organizes and archives all of the emails for key accounts that you receive through your inbox and it works with Gmail, Outlook.com and all the leading mail providers.
Once you've linked your email to your doxo account you select the businesses you work with, and doxo will organize and archive thousands of emails for you in a matter of minutes -- so all your account info, usernames, passwords, documents, and now emails are together in a personal and secure, cloud-based, digital filing cabinet.
"Managing emails is both a time sink and a nuisance for most people," says Dan Miller, senior analyst at Opus Research. "doxo takes a novel approach that detects important emails from vendors and service providers and then organizes them alongside related account information and documents within a users doxo account. Not only does doxo intelligently import and organize hundreds, if not thousands of emails from your personal email account in minutes, it also carries out automatic updates daily. That makes it a time saver and an important tool for managing interactions with key vendors".
You can specify which accounts you want the software to work with -- banks, utilities, insurance, investments and so on. It will check for new mail from your key accounts each day, keeping your records up to date. You can then access everything related to your account online or via the doxo mobile app.
"doxo is your personal directory of all the accounts in your life -- giving a consolidated view of your account info, usernames, passwords, documents, and now email, together in one convenient place," says Steve Shivers, co-founder and CEO at doxo. "It’s our mission to make your life easier, and Email Import brings us another step closer to fulfilling that goal".
You can find out more about doxo and try it out with a free account at www.doxo.com.
Photo Credit: Andresr/Shutterstock
-

Commuters put corporate data at risk on public Wi-Fi
Publié: septembre 18, 2013, 10:24am CEST par Ian Barker

The results of a survey released by GFI Software show that a startling 96.5 percent of respondents use public Wi-Fi networks at least once a week to carry out work related tasks. The survey carried out by Opinion Matters asked 1,000 U.S. office workers with a tablet or smartphone who travel to and from work on a train, bus or subway about where, how and what they use their mobile devices for, and how those mobile devices have impacted the way they work both inside and outside the workplace.
More than one-third (34.2 percent) of those respondents reported they accessed public Wi-Fi at least 20 times a week during their commutes, with some employees saying they connect more than 70 times a week. This activity puts company data and passwords at risk from packet sniffing and other forms of traffic interception.
"The research findings reveal a stark and concerning trend among commuters -- one of using their personal devices to catch up on work during their commuting downtime, but doing so over highly insecure internet connections that can be easily intercepted by other users or the operator of the access point," says Walter Scott, CEO of GFI Software. "Mobile internet access is now firmly entrenched as a day-to-day norm, but with that has come an increasingly relaxed user attitude to data security, compliance and data governance policy. Companies need to address mobile device management to ensure that use in insecure environments doesn't create vulnerabilities that could be exploited by criminals -- both cyber and conventional".
Over 60 percent of respondents admitted they would use any Wi-Fi source they could find. But whilst 59.8 percent were concerned about being robbed when using their mobile device in a public place only 29.6 percent worried about having their data intercepted on public networks. Almost 20 percent of mobile devices had no security enabled at all, whilst only 24.7 percent had corporate security policies enforced.
The survey also shows the rise in BYOD with 86.9 percent of respondents using their own mobile device at work. 51 percent also admitted to using their smartphone for personal tasks whilst connected to company networks for at least 30 minutes a week.
Scott says, "BYOD is something that isn't going to go away. From the early days of executives buying PDAs and expecting IT to support them, end-user devices in the workplace being used for work tasks has been with us for more than two decades. However, the explosion in BYOD fuelled by powerful and affordable smartphones and tablets is such that companies have to manage it. Mobile Device Management is now a paramount IT security requirement for businesses of all sizes to maintain data security and integrity inside and outside of the company network".
A final worrying statistic from the survey is that 44.6 percent of those questioned admitted to using their mobile devices in the bathroom. Now wash your hands...
Photo Credit: Tang Yan Song / Shutterstock
-

Wrike aims to make online work easier and more productive
Publié: septembre 13, 2013, 11:02am CEST par Ian Barker
 California-based project management software provider Wrike has launched a new version of its software with a simplified interface and -- no prizes for guessing -- online collaboration features.
California-based project management software provider Wrike has launched a new version of its software with a simplified interface and -- no prizes for guessing -- online collaboration features.The "Graphite" version of Wrike has a redesigned user interface along with innovative task scheduling and time management. Andrew Filev, Wrike's CEO and founder says, "Simple, clean, and lucid -- these were the key topics of our design discussions while we were working our magic on Wrike Graphite. We wanted to find the perfect balance between our users' habits and a new level of efficiency in day-to-day work, which we tried to implement in every element of the new UI".
The new, flat design user interface highlights key content thanks to a contrasting color palette and increased use of white space and icons. One of the main components of the redesign is a comprehensive and well-structured task view. Wrike Graphite features a timer which broadcasts individual users' current work in real-time, automatically updating fellow team members on a project's progress. This allows users to virtually simulate walking around an office or workspace to collaborate or check up on fellow workers’ progress.
"With one click, team members can share information about their progress, sort of a 'push-pull' way of informing peers without bombarding them with needless information," Filev says. "It’s as if workers walk by colleagues' desks to assess progress and help out, if necessary. So, it’s especially transformative for the online work experience, if team members are working from different locations".
Other improvements include better charting showing project details and statistics, activity stream-like email notifications to keep team members up to date using fewer messages, and HTML5 desktop notifications to keep users up to date with new messages and comments.
Wrike runs in your browser and there are native apps for Android and iOS. To find out more or to get a free trial version visit the Wrike website.
Photo Credit: nmedia/Shutterstock
-

BullGuard Identity Protection safeguards your personal data
Publié: septembre 12, 2013, 3:08pm CEST par Ian Barker

 Where once malware was aimed at disrupting your computer, today it's more likely to be out to steal your personal information and get access to your finances. BullGuard has a track record of guarding against this type of threat with products like Premium Protection 13 its complete security package.
Where once malware was aimed at disrupting your computer, today it's more likely to be out to steal your personal information and get access to your finances. BullGuard has a track record of guarding against this type of threat with products like Premium Protection 13 its complete security package.But the company's latest release, BullGuard Identity Protection, is designed to work alongside your existing security suite -- of any brand -- and ensure that your personal information and social networking activities are protected against threats.
Identity Protection allows you to specify the details you want protected such as credit card and bank account numbers, usernames and passwords. It will then notify you by email or SMS if any suspicious activity occurs. It also allows you to monitor social networking accounts for things like suspicious friends and links to malicious websites. You can unobtrusively monitor a child's account for inappropriate content too.
Alex Balan, Head of Product Management at BullGuard, says, "We’re all too well aware of the growing number of threats that are targeting internet users, and the popularity of social media sites such as Facebook has made it an increasingly attractive alternative for would-be cyber-criminals and cyber-bullies.
"We developed BullGuard Identity Protection squarely with this in mind. It provides frequent and casual internet users with peace of mind because their data and their children’s activity, is monitored and kept safe".
BullGuard Identity Protection is a web-based service so it will work on any device with a browser and you can log in to change your account settings from anywhere. You can subscribe to the service on a month-by-month or annual basis.
For more information visit www.bullguard.com.
Photo Credit: Pavel Ignatov/Shutterstock
-

Huddle aims to connect workers via the cloud
Publié: septembre 12, 2013, 10:22am CEST par Ian Barker
Content collaboration specialist Huddle has launched its Connected Desktop experience aimed at streamlining team working by linking the desktop with the company's content collaboration system.
Groups of people can work together, editing and saving files from their desktops into a secure cloud. This aids productivity regardless of where workers are located or what type of device they're using. The latest release offers five new capabilities.
Seamless interaction with the cloud allows users of Huddle for Windows or Mac to edit documents in their desktop application whilst ensuring that it's locked to prevent conflicts. If connectivity is lost the latest version is uploaded as soon as it's restored.
Huddle for Outlook integrates with the mail client to save documents and email conversations into the Huddle cloud. Email responses are recorded as comments on the file so that the context of discussions is retained.
Huddle Drive offers enterprise-grade storage allowing easy access to files for all team members as well as enhancing security by reducing the risk that corporate data will be leaked or lost.
Huddle Viewer ensures that photos and videos can be viewed directly from the cloud via a browser without the need to open a separate desktop application. It also makes locating and sharing the latest version of an image simpler.
Finally Huddle Dashboard creates a business activity stream showing all of the activity on a project in a single place. Files for approval, notifications, comments, tasks and actions are immediately flagged and teams can easily see what progress has been made across projects.
"The office of the future is no longer a physical environment -- with a desk, chair and workstation tied to the network -- it’s a secure virtual environment that is accessible from anywhere via whatever device people wish to use," says Alastair Mitchell, CEO of Huddle. "People’s devices are now the doorway to their world of work. Thanks to the cloud, they can securely store, access and share all of their files and collaborate with everyone they need to -- inside or outside of the organization".
Huddle is browser-based but native apps are also available for Windows, Mac, Android and iOS. The infographic below shows how it works, you can find out more and see a video of Huddle in action at www.huddle.com.
-

The top new gadgets of 2013 and the ones we're still waiting for
Publié: septembre 10, 2013, 12:35pm CEST par Ian Barker
With the launch of a new iPhone on the horizon you can almost sense the forming of a queue each time you go past an Apple store. But Apple isn't the only company with new products either already launched or in the pipeline. In fact 2013 has been something of a bumper year for technology releases.
The FinancesOnline website has produced a handy infographic showing this year's stand-out gadgets and those that are still to come. In the smartphone market most of the interest was at the top end. HTC and Sony joined the premium smartphone battle with new products this year with the Google Nexus 5 still to come.
It's been a fairly quiet year for tablets with only the latest Nexus 7 creating a stir thanks to its high resolution display. Microsoft Surface Pro made headlines for the wrong reasons as the company was forced to slash prices. However, rumours of an iPad 5 mean that the tablet market may get a boost before the end of the year.
The PC market continues to slide despite 4th generation Haswell processors aiming to boost the ultrabook market with more battery life. Apple's funky cylindrical Mac Pro proved that the company has lost none of its design flair and it should be on sale by the end of the year. On the software front iOS7 is moving away from the bevelled and shadowed look and of course the much leaked Windows 8.1 will go public in October.
We've also seen the launch of the inexpensive Chromecast this year, Samsung became the first of the big players to enter the smartwatch field and there's been controversy surrounding the other big wearable development -- Google Glass. We're likely to see a battle for the gaming market in the run up to Christmas with the Xbox One and PlayStation 4 both competing for your holiday cash.
For a month-by-month breakdown of 2013's hot tech releases take a look at the infographic below. Once you've done that tell us what's been your favorite piece of new technology this year? What are you most looking forward to from the coming releases?
 Prepared by personal finance
Prepared by personal finance
-

IT professionals need to become 'hunter harvesters'
Publié: septembre 9, 2013, 12:34pm CEST par Ian Barker
 Chief information officers are increasingly looking at enterprise architecture in order to drive their digital strategy according the latest research by analysts Gartner. The company's 2013 CEO and Senior Executive Survey reveals that 52 percent of respondents said their organizations have a digital strategy.
Chief information officers are increasingly looking at enterprise architecture in order to drive their digital strategy according the latest research by analysts Gartner. The company's 2013 CEO and Senior Executive Survey reveals that 52 percent of respondents said their organizations have a digital strategy."Senior business executives are challenging CIOs and their IT organizations to be at the front of digital strategy, identifying innovative new business models and technologies, and getting more business value out of each technology investment," says Marcus Blosch, research vice president. "Enterprise architects can provide unique capabilities to help CIOs develop a new agenda for 'hunting and harvesting' in a digital world".
It can sometimes be difficult to see how new ideas and technologies apply to business and what difference they will make. Enterprise architecture can help by linking technologies and innovations with the strategy of the business. Gartner calls this process 'hunting and harvesting', EA teams can do technology tracking and create innovation management processes to support hunting. Harvesting is driven through techniques such as business capability modeling, which provides a basis for identifying and delivering outcomes.
Blosch adds, "CIOs must extend IT's performance profile beyond tending, to hunting and harvesting for digital value. For enterprise architects, particularly those who sit within the IT organization, this is a great opportunity to move EA into a more strategic role. Business-outcome-driven EA is integral to achieving each of these areas to provide insight and support decision making. The EA team currently has the opportunity to become more strategic by aligning itself to support the CIO and the organization".
Businesses need to build the skills required to support hunting and harvesting. These must be combined with more agile approaches to innovation, such as being able to run experiments. The ability to identify an opportunity, quickly set it up and pilot it, assess the results and decide to expand it into another cycle or kill it off according to the results.
The report is part of a wider Nexus of Forces study on the factors influencing enterprise computing. You can find out more on the Gartner website.
Photo Credit: Dan Kosmayer/Shutterstock
-

HyperOffice integrates social collaboration with project management
Publié: septembre 5, 2013, 12:15pm CEST par Ian Barker
 In recent weeks we've seen social collaboration become the new black as far as business computing is concerned. Gartner has reported growing expectations from social technologies and new product releases from major players have focussed on this sector.
In recent weeks we've seen social collaboration become the new black as far as business computing is concerned. Gartner has reported growing expectations from social technologies and new product releases from major players have focussed on this sector.Washington DC-based HyperOffice was an early entrant into this field and its current offering is aimed at SMBs looking for a scalable solution that will grow with the business. As well as social collaboration HyperOffice includes online document and project management, shared calendars and contacts. It also lets you build an intranet, maintain wikis and forums and handle business email as well as offering traditional project planning tools like Gantt charts.
The software is cloud based and optimised for mobile browser interfaces, dedicated apps for popular mobile operating systems are coming soon. It's compatible with ActivelSync and SyncML which allows it to exchange data with most smartphones on the market.
The product is customizable so that users can be directed to land at a particular part of the suite depending on their needs and can belong to multiple workspaces. Customizing is via a simple drag and drop interface.
The company sees HyperOffice as competing with Google Apps and Office 365 and say it's more sophisticated than Google and simpler to use than Office 365.
Farzin Arsanjani, president of HyperOffice says, "...while the demand for social tools in businesses is intense, serious market gaps remain. Enterprise social tools like Yammer are thin on collaboration capabilities, while collaboration software like Google Apps and Office 365 don't see social tools as essential to their suites".
For more information, video demos and free webinars visit the HyperOffice website.
Photo Credit: nopporn/Shutterstock
-

Norton updates its core security products
Publié: septembre 4, 2013, 3:15pm CEST par Ian Barker

In time for the release of Windows 8.1, Norton has announced new versions of Norton 360, Norton Internet Security and Norton AntiVirus. In addition to Windows 8.1 compatibility these include some under the skin changes to improve protection, performance and usability.
Gerry Egan, senior director, product management, Symantec says, "According to Symantec research, Web attacks increased 30 percent in 2012, driven by the easy availability of malware toolkits and the high frequency of unpatched vulnerabilities on websites. As a result, consumers can be attacked even when they visit a legitimate website, an attack that puts their devices and personal information at risk. With the latest Norton releases, we are delivering the comprehensive security required to protect today's devices against new and evolving threats, without impacting performance".
Key enhancements in the latest products include new advanced repair capabilities which use Internet-connected resources to repair Windows system files that have been broken or crippled by malware faster and with greater consistency. Improvements are made to the behavioral-based protection engine, SONAR, which operates on the premise that while the physical nature of malware changes, its behavior often does not. As a result, SONAR now allows the latest products to discover and shut down malware that attempts to disguise its bad behavior by operating inside legitimate Windows processes.
SONAR also helps with the removal and cleanup of malware attempts by saving the evidence of the attack for later use by Norton's repair technologies. This helps to ensure that all traces of a malware attack are removed and a system is returned to its original state.
Improved installation and setup means users can quickly download and install the latest version of the product for their device type and subsequently ensure that all their devices are protected. Boot time is improved by 15 percent, install speed by 10 percent and memory usage during scan by 100 MB, resulting in faster performance and lower system impact.
The password management tool Norton Identity Safe gets a new look. It now includes improved form filling, with drag-and-drop functionality and full vault searches available directly from the toolbar to help manage passwords in a more secure and convenient way.
The latest versions are available from today, for more information visit the Norton Update Center.
Photo Credit: Vladru/Shutterstock
-

Streamline your Office 365 management with 365 Command
Publié: septembre 4, 2013, 10:47am CEST par Ian Barker

If you've ever felt like you needed an easier way to manage your Office 365 installation then you're not alone. Tech Data Corporation and MessageOps have had the same thought and joined forces to offer an easy to use cloud management platform called 365 Command.
The tool offers a fast, accurate and cost-efficient way for solution providers to manage their Office 365 clients. Bharath Natarajan, director of product marketing, TDCloud and software services at Tech Data says, "Available through Tech Data's award-winning Solutions Store, powered by StreamOne, 365 Command will bring profitable success to solution providers' cloud businesses, creating a continual revenue and profit stream".
365 Command replaces the command line interface of Windows PowerShell with a rich, HTML5 web interface. The easy-to-use, web-based portal provides resellers with a product offering that enhances administration, reporting, and monitoring tools needed to better manage Office 365.
Administrators and help desk staff can quickly perform common tasks such as managing mailbox permissions without the need for PowerShell scripting knowledge. There's also a powerful reporting and analytics function, allowing detailed charts and graphs to be produced with just a few clicks.
"MessageOps is pleased to partner with Tech Data to expand our reach within the Microsoft partner community", says Chris Pyle at MessageOps. "With the evolution of cloud computing, we are seeing a large demand from partners who are looking to create a repeatable and profitable service offering around Microsoft Office 365. 365 Command is the enabler".
You can find out more and register for a free trial at 365 Command.
Photo Credit: wavebreakmedia/Shutterstock
-

The FUZE aims to make the UK fall in love with coding again
Publié: août 28, 2013, 5:27pm CEST par Ian Barker

The FUZE is a new programable computer and electronics workstation based around the Raspberry Pi. It's built in the UK and its designers believe it will appeal to the education sector as well as home electronics enthusiasts.
We hope to get some hands-on experience with one soon but in the meantime we spoke to Jon Silvera the managing director of Binary Distribution, the company behind the FUZE, to find out more about it.
BN: For readers who haven't seen the FUZE before can you give us a quick overview of its features?
JS: The FUZE is an innovative new product aimed at teaching computer programing and hobby electronics. The FUZE powered by Raspberry Pi consists of a robust metal case containing the RPi Model B, a UK keyboard, the FUZE IO Board (a very accessible Input /Output interface) providing much needed circuit protection for the RPi. All connectivity is extended to a convenient back panel. Also included in the full package is a mains-to-USB power supply, wireless mouse and mat, 4GB SD card (prepared and ready to run), an electronics components kit, FUZE BASIC along with a hard copy programmer’s reference guide.
Perhaps most important, however, is the inclusion of FUZE BASIC, a specially adapted version of BASIC tailored to the Raspberry Pi and the FUZE project. FUZE BASIC is a comprehensive and somewhat expanded version of the original popular language. A full hard copy reference guide is included for easy access.
FUZE BASIC makes learning to program so much easier and accessible that enthusiasts of all ages will find programing something to embrace, not fear -- it's pre-configured and does not need a new library to run a new command or function. It supports and simplifies the full GPIO functionality of the Raspberry Pi making even complex electronic projects achievable and more importantly, fun.
FUZE BASIC supports all the usual functions like FOR-REPEAT-UNTIL-IF-THEN-ELSE etc, file and screen handling, graphics, Turtle graphics but goes on to include Sprite handling and Input/Output commands that open up all kinds of possibilities. It is, for example incredibly easy to program a simple game but then go on to make the joystick controls to play it -- this is actually a simple project!
The FUZE was conceived and developed with programing as its core focus. The objective has been to make learning, and teaching (!) fun, interesting, self-motivated and easily measurable. The addition of electronic projects that avoid talking about electrons and nuclear physics goes a long way to keep things simple to understand and therefore more achievable across a broad spectrum of age groups and abilities
It's perfect for beginners and advanced programers alike and with the added benefit, interest and fun of LEDs, micro switches, buzzers and more, you're actually learning about the basics of electronics without even realizing it.
The unit can come complete with a UK keyboard, Mouse, and solderless breadboard for electronic projects. For those of you who already own the Raspberry Pi, the FUZE is available as an upgrade for the RPi Model B so you can buy just the case or the case with FUZE BASIC and electronics kit etc.
BN: Who is the FUZE aimed at?
JS: Anyone aged six and upwards. Because the FUZE comes with our specially written PDF project cards, anyone who can read can benefit from the FUZE. We are targeting education as well as the home/hobbyist market, with FUZE BASIC and Python on the Pi it's perfect for all budding or already proficient programers and Scratch is great for learning the concept of programing.
BN: Why did you choose to supply the system with your own FUZE BASIC?
JS: Back in the late seventies and early eighties BASIC was the language of choice. Well, it was that or machine code as BASIC was too slow to do anything other than write text-based programs.
From these early days, thousands upon thousands of bedroom and student coders went on to pretty much form the computer industry we value and enjoy so much today. In most cases these programers started using the BASIC language and then, once being firmly bitten by the coding bug, furthered their skills and abilities with more complex languages like C, Assembly, Pascal and a few others.
But they started with BASIC, not everyone of course but so very many did. Consider the computers by Acorn, Sinclair, Commodore, Atari and Amstrad -- every single machine came with BASIC.
BASIC covers all aspects of programing from simple loops to complicated IF THEN ELSE conditional statements, from simple line drawings to beautiful mathematical masterpieces, from text adventures to graphical platform games, from simple LED off/on projects to atmospheric and environmental measuring tools and so on.
The Raspberry Pi is generally supplied with Python and Scratch which are both fantastic applications but in our view meet the requirements of the two ends of the programing spectrum. Scratch can be a great introduction to understanding some of the fundamentals of programing but it does not perhaps provide a deeper, behind the scenes look at what is actually making the program work -- it is also, I'm afraid, woefully slow on the RPi so can often be more frustrating than productive -- run it on a higher performance Linux or Windows system and it really is awesome!
 Python on the other hand requires somewhat more knowledge about programing languages and environments than is generally and readily available in primary and secondary schools. Please don't misinterpret our message here, Python is a fantastically powerful and functional language but, in our view this makes it harder to approach than BASIC and as such we've focused our efforts on FUZE BASIC over any other language. It's quite simply, easy to learn and therefore easy to teach -- because of this we believe it’s more fun and rewarding than any other introduction to programing. We feel this is the best approach at a time when expectations are high and we need as many people to be bitten by the bug as possible.
Python on the other hand requires somewhat more knowledge about programing languages and environments than is generally and readily available in primary and secondary schools. Please don't misinterpret our message here, Python is a fantastically powerful and functional language but, in our view this makes it harder to approach than BASIC and as such we've focused our efforts on FUZE BASIC over any other language. It's quite simply, easy to learn and therefore easy to teach -- because of this we believe it’s more fun and rewarding than any other introduction to programing. We feel this is the best approach at a time when expectations are high and we need as many people to be bitten by the bug as possible.BN: Was it a conscious decision to make the FUZE look like a 1980s home PC?
JS: Absolutely YES! In all honesty, have you ever tried to build a small home computer? It's no wonder these things all looked so similar -- it’s actually very hard not to make it look retro. That said, I'm a real fan of retro computing and as such every effort was made.
BN: Can you tell us a bit more about the project cards that you offer alongside the FUZE workstation?
JS: FUZE BASIC project cards are designed to promote self-motivated learning. That is, it should be entirely reasonable to expect a pupil to get by at their own pace and without the need for lots of intervention -- apart of course, than to demand you come and look at what they've just done!
The projects range from the very basics, to intermediate programing and electronic techniques and methods. Over time they will be expanded to incorporate advanced projects. New project cards will be provided for free, unless part of an electronic project package, from the www.fuze.co.uk website.
As all schools seem to be starting from the same position, they are written, hopefully, to appeal to all ages and not specifically to any key-stage or age group so they can be implemented anywhere within the key stage spectrum.
Projects are short and focused. They also include plenty of computing references and soundbites providing additional learning within the IT curriculum. They cover much of the programing requirements proposed in the recently announced framework curriculum for the UK.
A small admission is needed here. Our original intention was to make around ten or more projects available at launch but this has just proved too much for our humble little business. We are, however, working around the clock and will post new ones as completed on the FUZE website. Initially the FUZE will ship with most likely four to six projects -- more will be posted in the days and weeks following launch, and will be freely available to download.
BN: Why build it in the UK? Wouldn’t it have been cheaper to outsource production overseas?
JS: A very interesting question… This has been a very conscious decision.
With the core drive for the FUZE project being about getting people in the UK programing again, a drive very much driven by the Government after coming to the conclusion that as far as programing in schools goes, they've let things slip somewhat. The result being an incredible amount of revenue never even touching the ground in the UK. Let alone the negative economic implications of thousands of programers being situated everywhere around the world other than the UK which means we miss out on all the taxes, NI contributions, VAT and so on that could generated be here.
We're not talking small amounts either -- just contemplate for a moment the number of apps sold every day in the UK on devices such as Apple iPads and iPhones, Microsoft Surface, Android tablets and game consoles.
 It doesn't take an economic guru, which I am not, long to realize something needs to be done which is why, in my opinion, things have moved forward at such a pace. It’s not flippant therefore to say that with this in mind we wanted to make as much of the FUZE as possible locally. We're based on a Business Enterprise Farm (a real working farm!) in Buckinghamshire, the case is also made in the same county, the boards are made in Wiltshire and the FUZE is assembled by us, here on the farm. Even the packaging is completely recyclable and supplied by local businesses.
It doesn't take an economic guru, which I am not, long to realize something needs to be done which is why, in my opinion, things have moved forward at such a pace. It’s not flippant therefore to say that with this in mind we wanted to make as much of the FUZE as possible locally. We're based on a Business Enterprise Farm (a real working farm!) in Buckinghamshire, the case is also made in the same county, the boards are made in Wiltshire and the FUZE is assembled by us, here on the farm. Even the packaging is completely recyclable and supplied by local businesses.It is not, however, easy to buy small electronic components manufactured in the UK or a custom keyboard for that matter so these items have to be imported.
We have always been conscious of the benefits of keeping things local, both to the environment and to doing our bit to help the economy.
Could it be made cheaper? Yes of course it could. Should all of the revenue and jobs be outside the UK? We don’t think so.
BN: Do you have any other versions or updates planned for the future?
JS: We'd like to keep real details under wraps at this point but suffice to say this is not a short term project. There are many long term objectives planned and all of them revolve around one thing; let’s get more kids programing -- it is one of the most secure and likely careers of our future so it would be a smart move to be prepared.
-

Server shipments up but revenues fall
Publié: août 28, 2013, 3:19pm CEST par Ian Barker
 IT research company Gartner has released its latest research showing that in the second quarter of 2013 server sales were up by four percent though revenues declined 3.8 percent over the same quarter last year.
IT research company Gartner has released its latest research showing that in the second quarter of 2013 server sales were up by four percent though revenues declined 3.8 percent over the same quarter last year.IBM remains the leader in the worldwide server market based on revenue with $3.2 billion totalling 25.6 percent of the market for the second quarter. HP leads on numbers of boxes shipped but managed only a 25 percent market share by revenue.
Dell comes in third with 17.7 percent -- whilst still shipping more kit than Big Blue -- with Oracle and Cisco trailing on 5.8 and 4.4 percent respectively. If you've been counting as we go along you'll have realized that leaves 21.5 percent for other vendors. First among the also-rans is Chinese supplier Inspur Electronics with 2.7 percent of the market by shipments.
Jeffrey Hewitt, research vice president at Gartner, says, "The global server market remains in a relatively weak state overall. The only regional bright spot was Asia/Pacific with growth of 10 percent and 21.7 percent year-on-year in terms of revenue and shipments. The US also grew in terms of shipments by 1.9 percent year-on-year but declined in revenue by 5.1 percent".
If you look at form factors x86 blade servers declined by three percent in shipments and 4.5 percent in revenue. However rack-optimized x86s grew 3.9 and 2.4 percent. RISC/Itanium Unix servers also showed decline whilst the 'other' CPU category -- made up primarily of mainframes -- showed 6.9 percent revenue growth.
You can read a full breakdown of the numbers on the Gartner website.
Image Credit: watcharakun /Shutterstock
-

Social technologies evolve to meet changing business demands
Publié: août 27, 2013, 12:39pm CEST par Ian Barker
 Research giant Gartner has revealed its latest 'Hype Cycle' -- a series of reports that offer a graphic representation of the maturity and adoption of technologies -- focusing on social collaboration in enterprises.
Research giant Gartner has revealed its latest 'Hype Cycle' -- a series of reports that offer a graphic representation of the maturity and adoption of technologies -- focusing on social collaboration in enterprises.It shows that the use of social technologies to meet business needs is increasing along with growing expectations of their effectiveness. More vendors are adopting an approach in which social features aren't bought separately but are incorporated into something else. You can see this trend in new product releases from Clarizen and Deltek which we've reported on recently.
"IT leaders must keep abreast of this evolving sector in order to take advantage of social capabilities and understand the implications that social software developments have for related technologies," says Jeffrey Mann, research vice president at Gartner. "As social technologies mature and organizations improve their understanding of how to apply them, they will be found in more and more situations. Increasingly, social technologies are not implemented on a stand-alone basis, but are tightly integrated within a variety of other technologies, including business, IT operations, unified communications and collaboration applications".
As technologies mature and move along the Hype Cycle to what Gartner calls the 'Slope of Enlightenment' they become more visible and in demand. These include things like internal peer-to-peer communications and unified collaboration and management.
Newer technologies at the 'Innovation Trigger' stage of the cycle include collaborative customer interfaces which allow the delivery of a personalized experience, social co-browsing in shared web spaces, mobile virtual worlds and social TV to provide real-time engagement with customers.
You can register to download the full report from Gartner's website and the company is hosting a Content and Collaboration Summit in London in September.
Photo Credit: Oleksiy Mark/Shutterstock
-

Big isn't always best when choosing enterprise content management
Publié: août 27, 2013, 11:21am CEST par Ian Barker
 Size isn't everything when selecting an enterprise content management (ECM) solution, according to independent global analysts Ovum. Companies also need to consider vendors in terms of market share, profitability, and capability to support the deployment along with the enterprise’s own business requirements through its lifetime.
Size isn't everything when selecting an enterprise content management (ECM) solution, according to independent global analysts Ovum. Companies also need to consider vendors in terms of market share, profitability, and capability to support the deployment along with the enterprise’s own business requirements through its lifetime.In its latest Ovum Decision Matrix, which is focused on the selection of ECM solutions, the analysts reveal that file sync and share is becoming the next must-have feature as organizations demand secure ways of sharing information outside the corporate firewall. In addition, end users are demanding empowerment through the use of social media in a business context, as well as increased support across various mobile platforms.
Sue Clarke, senior analyst at Ovum, says, "Because much of the functionality is now commoditized, and the industry has gone through a period of consolidation, which has reduced the number of platforms available, it is becoming increasingly difficult for the CIO to select the most appropriate solution".
A further important factor in choosing a vendor is the support associated with migration. The report reveals that whilst most suppliers offer a migration toolkit extra support is usually required. "ECM deployments can be difficult and complex and generally require services for all but the simplest of deployments. Even migrating from one platform to another or from one version to the next is not without its difficulties," adds Clarke.
For more information on the latest decision matrix and to register to download it visit the Ovum website.
Image Credit: Peshkova/Shutterstock
-

AV-Comparatives puts Android security under the spotlight
Publié: août 26, 2013, 6:09pm CEST par Ian Barker
 It's become almost unthinkable to use a Windows PC without some form of protection and that’s put the emphasis on other systems when it comes to security. Last week independent testing organization AV-Comparatives released its report on Mac security and now it's Android’s turn.
It's become almost unthinkable to use a Windows PC without some form of protection and that’s put the emphasis on other systems when it comes to security. Last week independent testing organization AV-Comparatives released its report on Mac security and now it's Android’s turn.With mobile devices it's important to guard not just against hackers but against the loss of the device itself. Smartphones are an attractive target for thieves and security software needs to make the data on them difficult to access for the thief but still easy to get to for the owner. Most of the products tested offer some form of anti-theft measure, with either the ability to lock the phone remotely or to track it.
The tests also looked at whether security software saps an Android device's battery life to an unacceptable degree. Always a concern for mobile users.
The test examined 16 products available from the Google Play store in July 2013. All scored well for battery usage with only Webroot and Qihoo not making the top score. In terms of detecting malware the best performers were AhnLab and Kingsoft both with 99.9 percent detection rates, closely followed by Kaspersky on 99.7 percent, with Baidu and ESET both on 99.6. Ikarus brings up the rear with only 91.0 percent detection.
For theft protection, avast!, F-secure, QuickHeal, Tecent and Webroot offer the widest range of features. Baidu and Kingsoft have no theft protection at all.
You can read the full test results as a PDF here.
Photo Credit: style-photography.de/
-

Clarizen mixes social networking and project management
Publié: août 26, 2013, 10:42am CEST par Ian Barker
Californian work collaboration and project management specialist Clarizen has launched the latest version of its cloud-based platform. Clarizen v6 combines social engagement and project management to achieve better results.
Clarizen’s co-founder and CEO Avinoam Nowogrodski says, "Clarizen v6 was designed from the ground up to support the requirements of today's changing modern workplace. Increasingly, companies and organizations are staffed by people of different generations, with different skill sets and who are located around the world. Clarizen v6 delivers on our Work Funnel concept of connecting social context, tasks and projects on a single cloud-based platform, so collaboration will drive results".
Features in the new version include internal and external social collaboration, allowing employees, contractors and customers to link conversations on projects and take part in real-time discussions.
Drag and drop resource allocation allowing managers to easily assign workloads, easy document collaboration that integrates with cloud storage tools like Box and Google Drive, object previews, a fast search engine and extensive configurability.
"Clarizen v6 was designed around the tenets of participation, alignment and awareness," says Nowogrodski. "We wanted to empower individuals in a way that has never been done before. By connecting social context with processes, we give a voice to each team member. It is that voice and that transparency that will ultimately lead an organization to success".
 Clarizen v6 is available now. Existing customers can experience v6 and choose their upgrade path through the Clarizen "Training Box" which allows them to configure their system and train their employees prior to completing a full production upgrade.
Clarizen v6 is available now. Existing customers can experience v6 and choose their upgrade path through the Clarizen "Training Box" which allows them to configure their system and train their employees prior to completing a full production upgrade.Photo Credit: Alexander Kirch/Shutterstock
-

UK tech boss launches £1m fund to protect online business
Publié: août 23, 2013, 10:45am CEST par Ian Barker
 The man behind UK cloud and hosting provider UKFast is launching a new fund to help protect businesses from online threats. Called BASE (Building A Safer Environment) it aims to make quality security solutions available to businesses who can't afford the inflated costs charged by suppliers.
The man behind UK cloud and hosting provider UKFast is launching a new fund to help protect businesses from online threats. Called BASE (Building A Safer Environment) it aims to make quality security solutions available to businesses who can't afford the inflated costs charged by suppliers.The fund set up by Lawrence Jones, CEO of UKFast, aims to help businesses add security features to their network and grow to the next level. UKFast grants £5,000 to each business that qualifies for the funding to boost their solution.
Jones says, "It is common place to have online shops hosted on networks and environments that aren't behind a firewall. Many trusted sites that you'd assume would take this seriously are opting out, knowing that customers never check. The problem is less about people's desires to create a safe environment and more to do with astronomical pricing for firewalls and online security".
The BASE fund provides industry leading anti-virus, backup systems, safety protocols and 24-hour monitoring at no extra cost for UKFast dedicated or managed hosting clients. Grants of up to £5,000 per businesses are available to anyone hosting on the UKFast network.
Jones adds, "It makes sense and seems logical to me. It's a small price to pay when you consider the £12m we put into developing our own data centres. I'd like to think that one day all hosting providers will be doing the same.
"We’re hearing from businesses who are seeing their security costs multiply because their hosting provider is taking advantage of growing fears around safety online. People are hearing more and more about DDoS attacks and some companies are using that to hike their prices up.
"Businesses are being forced to upgrade their firewalls and pay excessive costs for a basic safeguard. It's wrong! Britain’s businesses shouldn't be held to ransom on this and forced to operate without the fundamental protections because of cost".
Photo Credit: Jakub Krechowicz/Shutterstock
-

Independent test rates Mac security products
Publié: août 21, 2013, 5:30pm CEST par Ian Barker
 The myth of Mac invulnerability has been looking shaky for a while and received a further blow in February when some machines used by Apple's own staff were hijacked and used to launch an attack on Facebook.
The myth of Mac invulnerability has been looking shaky for a while and received a further blow in February when some machines used by Apple's own staff were hijacked and used to launch an attack on Facebook.Growing numbers of Macs mean that the platform is increasingly attractive to cybercriminals and even if the number of attacks remains small compared to Windows it's still a threat that needs to be taken seriously. With this in mind independent testing company AV-Comparatives has been looking at security software for OS X Mountain Lion.
Seven products receive the company's Approved Security Product award. These are: Avira Security for Mac, ESET Cyber Security Pro, F-Secure Anti-Virus for Mac, Intego Premium Bundle for Mac, kaspersky Security for Mac, Sophos Anti-Virus for Mac Home Edition and ZeoBit MacKeeper Internet Security.
Quick Heal Total Security missed out on an award due to a poor score in the Mac malware detection test.
The review covered protection against Mac malware as well as Windows malware detection to prevent the inadvertent spreading of infection. The Avira and Sophos products are free, so there's really no excuse for leaving your Mac unprotected.
AV-Comparatives also suggests adopting a number of good practices in order to protect your system as follows:
- Never use an administrator account for day-to-day computing
- Use a sandboxed browser such as Google Chrome
- Uninstall/disable the standalone Flash Player
- Uninstall/disable Java
- Keep your Mac operating system and third-party software up-to-date with the latest patches
- Use secure passwords (the Mac includes the KeyChain password manager)
- Deactivate any services such as Airport, Bluetooth or IPv6 that you don't use
- Consider employing security software on your Mac
You can read a PDF of the full test report here.
Photo Credit: Thomas Bethge/Shutterstock
-

Businesses must focus on optimizing IT costs Gartner warns
Publié: août 20, 2013, 1:17pm CEST par Ian Barker
 After years of cost cutting through the recession, businesses now have the challenge of continuously optimizing their IT costs. According to a survey of over 2,000 chief information officers worldwide, 65 percent see the main barrier to optimization as the mindset needed for all resources to work towards the same goal.
After years of cost cutting through the recession, businesses now have the challenge of continuously optimizing their IT costs. According to a survey of over 2,000 chief information officers worldwide, 65 percent see the main barrier to optimization as the mindset needed for all resources to work towards the same goal."Organizations don't often achieve the desired results from their optimization initiatives, and costs end up returning into the business," says Sanil Solanki, research director at Gartner. "CIOs should consider incorporating five key principles into their organization's cost optimization practices to form a basis for continual optimization. These principles are geared toward avoiding the danger of tactical cost initiatives, which may seem to generate savings in the short term, but can mean costs returning into the business in the long term".
The five principles Solanki identifies are accountability, agility, discipline, simplification and transparency. Accountability ensures that the IT department can manage the demands that the organization makes of it. Agility guarantees a good balance between resources and a flexible response.
Discipline ensures that someone is accountable for IT cost optimization and that, preferably, the process is led from the top by the CIO. Simplification reduces complexity in order to control costs, Gartner estimates that overly complex systems can add as much as 25 percent to IT unit costs. Finally, transparency makes sure that the business understands what IT can do for it and that IT understands its role in the business.
For a more detailed analysis you can register to get a copy of the report Five Principles Underpin IT Cost Optimization from the Gartner website.
Photo Credit: Dusit/Shutterstock
-

Survey shows most of us would rather work from home -- shock!
Publié: août 19, 2013, 4:31pm CEST par Ian Barker
 "I'm working from home," is often seen as one of the great lies of modern life. But a new survey released today by Kona, the cloud based social collaboration and productivity platform, shows that a majority of employees would rather telecommute than be in the office.
"I'm working from home," is often seen as one of the great lies of modern life. But a new survey released today by Kona, the cloud based social collaboration and productivity platform, shows that a majority of employees would rather telecommute than be in the office.The survey conducted with SodaHead shows that 70 percent of us would prefer to be sitting at home in our pajamas than traveling to the office. For those aged between 35 and 44 the number wanting to telecommute jumps to 81 percent. The 18-24 age group though obviously likes to get out more with only 66 percent preferring home working.
There is a darker side to all of this, however. In offices that do allow people to work remotely 57 percent say it leads to jealousy amongst colleagues. Dice up the demographics and the figures are higher, 60 percent of parents, 65 percent of over 65s and 70 percent of those earning more than $100k say that they're jealous of telecommuting colleagues.
Despite the evident popularity of telecommuting though many companies aren't taking advantage of technologies that can make remote workers more productive. 64 percent of respondents still feel that email is the most effective means of group communication.
"Innovation combined with the right leadership, processes and people allows businesses to be more adaptable to the needs of their teams, spurring a more productive environment -- whether that's a traditional, virtual or hybrid work setting," says Scott DeFusco, Deltek's Vice President of Product Strategy and Management for Kona. "Using a social collaboration platform like Kona enables team members to be more connected and engaged".
Kona allows communication and interaction between team members regardless of their location. This leads to more productive exchanges of information and better work flow to keep a project moving forward.
Do you work from home? Does technology help or hinder you? Let us know via the comments.
Photo Credit: Paul Vasarhelyi/Shutterstock
-

HubSites lets local businesses harness the mobile web
Publié: août 15, 2013, 3:12pm CEST par Ian Barker
 The Texas-based marketing platform for small businesses Main Street Hub is introducing HubSites. These provide a mobile-friendly landing page to act as a link to a company's main site.
The Texas-based marketing platform for small businesses Main Street Hub is introducing HubSites. These provide a mobile-friendly landing page to act as a link to a company's main site.Features include a prominent click-to-call button, the ability to capture testimonials, Google Maps integration, a real-time Twitter feed and more.
"Today’s local consumers are hopping on their smart phones for information about local businesses at an increasing rate, yet local businesses are not keeping up with this shift," says Andrew Allison, co-CEO at Main Street Hub.
"Local business websites are hard to use on mobile phones and, as a result, they have the effect of pushing customers away. HubSites, on the other hand, are designed to convert mobile phone users into customers, using social media and mobile design to take advantage of opportunities to gain new customers the very moment they are making a purchasing decision".
According to a BIA/Kelsey survey mobile searches will overtake those from desktops by 2015, yet the majority of small businesses don't have a specific mobile website. HubSites allow B2C companies to stand out from the crowd and get ahead of the competition by offering a straightforward landing page. As part of the full Main Street Hub package they can help smaller companies to manage their online reputation and attract more customers.
Image credit: Andresr/Shutterstock
-

PagerDuty streamlines real-time collaboration with webhooks
Publié: août 15, 2013, 1:38pm CEST par Ian Barker

The SaaS alert and incident tracking company PagerDuty has announced the addition of webhooks to its software to streamline integration with other tools.
Development teams will be able to improve collaboration and incident response by customizing their web applications. This allows improved reporting and alerting so that, for example, any changes to the status of a logged entry will cause messages to be sent automatically.
It allows two-way integration too. Previously a system such as a helpdesk would only be able to push events to PagerDuty so it could notify people. Thanks to webhooks when a message in PagerDuty changes state the information can be fed back to the originating system.
To demonstrate all this, PagerDuty has worked with the popular private chat and IM service HipChat to integrate the two products. By using webhooks PagerDuty status messages can be rebroadcast to team members via the HipChat system.
"We jumped at the opportunity to integrate PagerDuty with webhooks because of how immediately handy this collaboration would be for both us and our customers – and it was fast and easy to do," says Garret Heaton, Co-Founder of HipChat. "Adding PagerDuty functionality via webhooks not only helps our customers to communicate more seamlessly, but also aids us internally to stay synced about every incident status change".
Existing PagerDuty users will have webhooks enabled immediately. For more information and pricing visit www.pagerduty.com.
Photo Credit: alexmillos/Shutterstock
-

Google+ rolls out new enterprise-friendly features
Publié: août 15, 2013, 12:25pm CEST par Ian Barker
Google has announced new features in its Google+ app for Android aimed at making its social network a valuable workplace tool. On the company's enterprise blog, Joël Kalmanowicz, Product Manager, Google Apps Team says, "If you're a Google Apps for Business, Government or Education customer, today we're releasing a few new features designed to make it even easier for you to get things done with Google+".
The app now supports multiple accounts allowing you to sign in to both work and private profiles and easily switch between them. You can also create restricted posts that can't be shared outside your organization. There are new domain labels too, both in the app and on the web, allowing you to quickly identify your colleagues' profiles so you know that you're connecting and sharing with the right people.
The Google+ Domains API -- announced at Google I/O in May -- is now also available to Google Apps customers. The API allows Google+ to be integrated into existing processes and lets enterprise software developers access it from within their products.
The API changes will be rolling out to Google Apps customers over the next few days and you can find out more on the official Google Apps Developer Blog.
-

Microsoft targets international businesses with Surface
Publié: août 15, 2013, 11:44am CEST par Ian Barker
Microsoft has announced the launch of new channels to sell Surface RT and Surface Pro to business, education and public sector customers. In addition to the US commercial channel which launched in July, today's announcement sees 17 countries including Austria, Belgium, Canada, Denmark, Finland, France, Germany, Ireland, Italy, Luxembourg, Netherlands, Norway, Portugal, Spain, Sweden, Switzerland, and the UK added to the list.
Writing in a blog post Cyril Belikoff, Director -- Microsoft Surface says, "This availability in international markets, along with the updates coming to Surface RT with Windows 8.1 are all important milestones for our customers. We know that people who use Surface love it! We’re looking forward to introducing even more customers in more places to the powerful productivity that Surface uniquely makes possible".
Resellers will offer a number of value-added services like asset tagging, custom imaging, onsite service and support, device recycling and data protection.
Microsoft is keen to point out that this is just the first stage of bringing Surface to international business markets and that it's planning to add more partners and extra markets over the coming weeks. The ultimate aim being to bring business channels to all markets where Surface is sold.
-

Where do iPhones come from? The facts of Apple life
Publié: août 14, 2013, 4:26pm CEST par Ian Barker
With the upcoming release of the Jobs biopic Apple is set to be in the spotlight in coming weeks. It's timely then that the Finances Online website has released an interesting report tracing the iPhone’s supply chain.
It makes for fascinating reading. The rare earth minerals used in many of the phone’s components are 90 percent sourced in China and Inner Mongolia. Move up to the component level and the LCD panels, chipset, memory and batteries are all made in Korea. The iPhone 5's innovative display -- which eliminates a layer of glass -- is made by LG for example. The gyroscope that works out which way you’re holding the phone comes from STMicroelectronics, a French/Italian company.
You probably already knew that most iPhones are assembled in China (85 percent) by Foxconn among others. The reason for this is that China can respond much faster when it comes to hiring engineers and setting up new production lines to bring products to market fast.
In terms of jobs, Apple employs some 43,000 people in the US with a further 20,000 US employees based abroad. That pales into insignificance though against the 700,000 jobs involved in making Apple products around the world.
Does it matter where technology products are made? Would you be more likely to buy a smartphone that was manufactured locally? Let us know in the comments.

-

Hypervisor turns the public cloud into an enterprise test platform
Publié: août 14, 2013, 3:01pm CEST par Ian Barker
 California-based Ravello Systems has released its Cloud Application Hypervisor. It may have a name straight out of sci-fi, but this product allows enterprises to use public cloud platforms to test their in-house applications.
California-based Ravello Systems has released its Cloud Application Hypervisor. It may have a name straight out of sci-fi, but this product allows enterprises to use public cloud platforms to test their in-house applications.Differences in storage, networking and virtualization techniques have previously prevented the use of the cloud as a practical test platform. Ravello's software makes any public cloud look and feel exactly like the enterprise data center from an application's perspective.
It uses software defined networking and storage, and an application framework. This means enterprises can easily create replicas of their in-house, multi-tier VMware or KVM based applications in any public cloud without the need to make any changes. Using Amazon Web Services, RackSpace or HP Cloud they can create multiple instances of an application for testing.
Navin R Thadani, SVP of products, Ravello Systems says, "For bursty workloads like development and test it does not make economic sense for enterprises to build internal data center capacity for peak usage, since on average, resource utilization may be as low as one percent. The public cloud sounds promising but is too different an environment, and still does not solve the infrastructure automation problem. Consequently testing is still mostly on-premise. It is rarely as frequent or as efficient as it needs to be. Hence, development cycles are far too slow".
The Ravello software has been in public beta since February and more than 2,000 enterprise users have replicated over 30,000 applications in leading public clouds representing more than 1 million CPU hours deployed.
Ravello's usage-based pricing model starts from $0.14 per hour for a 2 CPU, 4GB memory virtual system. This includes the cost of the underlying public cloud making it a cost-effective solution for providing extra test capacity.
Photo Credit: Andreas Weitzmann/Shutterstock
-

Harnessing the cloud can free SMEs to grow
Publié: août 9, 2013, 10:48am CEST par Ian Barker
 Technology is being underused by growing smaller companies according to communications and cloud specialist Qubic. The company says that hosted technology can help businesses grow by freeing them from the need to invest in hardware infrastructures.
Technology is being underused by growing smaller companies according to communications and cloud specialist Qubic. The company says that hosted technology can help businesses grow by freeing them from the need to invest in hardware infrastructures.Chris Papa, Managing Director of Qubic says, "With small and medium-sized businesses having been particularly badly hit by the economic downturn, they are the ones most in need of extra support to enable them to prosper. A hosted solution can help encourage start ups and SMEs in general to grow as it means that businesses can use technology on a 'pay-as-you-use' basis as opposed to tying up cash in a server with a telephone system which costs a fortune".
By challenging the idea that IT is an expensive and difficult area of business, Qubic hopes to allow smaller companies to harness the potential of technology whilst allowing them the freedom to concentrate on running their own business.
Chris Papa concludes, "As a small company starts to grow, it won’t need an IT department or IT Director. Expanding will be easy because the infrastructure is already in place and all the company needs to do is to add to this and keep on growing. Staff can work from home initially so an office isn't even necessary to get the business off the ground. Staff can also work collaboratively, both from home and in the office when the business expands".
Photo Credit: everything possible/shutterstock
-

More gloom for PC makers as European sales slump by 20 percent
Publié: août 8, 2013, 5:22pm CEST par Ian Barker
 As my colleague Wayne Williams reported earlier today the PC market is continuing to shrink at the hands of tablets. Further confirmation of this, just in case you needed any, comes from a Gartner survey showing that the PC market in western Europe slumped by 20 percent in the second quarter of 2013.
As my colleague Wayne Williams reported earlier today the PC market is continuing to shrink at the hands of tablets. Further confirmation of this, just in case you needed any, comes from a Gartner survey showing that the PC market in western Europe slumped by 20 percent in the second quarter of 2013.All PC segments in Western Europe declined over the quarter. Mobile and desktop shipments dropped 23.9 percent and 12.2 percent respectively. PC shipments in the professional market declined by 13.5 percent, while the consumer PC market decreased 25.8 percent in the same period. This equates to a 19.8 percent drop overall
"The market exit of the netbook PC, and vendors reducing their inventory to get the new Intel chips and Windows 8.1 have fuelled the decline in Western Europe," says Meike Escherich, principal research analyst at Gartner.
HP remains the number one PC seller followed by Acer and Lenovo. Acer suffered the biggest drop of 44.7 percent thanks to a restructuring of its product range away from netbooks towards tablets. Lenovo was the only maker to post positive figures with its sales up 18.9 percent over the quarter.
Things may look up later in the year according to Ms Escherich, "We can expect some attractive new PCs in the stores for the fourth quarter of 2013, running Windows 8.1 with thinner form factors and longer battery life enabled by Intel's Haswell processors. These PCs will compete with high-end tablets and will be complemented by a new generation of Atom-based devices that will compete with low-end basic tablets. Although this will not fully compensate for the ongoing PC decline, it does create an opportunity for profit in the midrange and more high end PC segments".
Looked at on a country-by-country basis, the UK PC market showed a 13 percent drop in line with a long term trend. Ranjit Atwal, research director at Gartner says, "The second quarter marked the 11th consecutive quarter of decline in the U.K. During this time the notebook market has shrunk nearly 25 percent in unit volume. The U.K. notebook market totaled over 2 million units in the second quarter of 2010 and has now reached just under 1.5 million units".
The German PC market fell by 18.7 percent but France showed a drop of 19.1 percent over the same period. This is the fourth consecutive quarter that the French market has experienced strong decline and it has shown the weakest performance of the three major western European nations.
Image Cedit: Alexander Mak/Shutterstock
-

Google Play store flooded with scam apps
Publié: août 8, 2013, 4:53pm CEST par Ian Barker
 The Google Play store is being bombarded with apps designed to scam unsuspecting users, according to consumer advice platform Scambook.
The Google Play store is being bombarded with apps designed to scam unsuspecting users, according to consumer advice platform Scambook.The scammers aren't even bothering to write malicious code, instead relying on simple human error to install their fraudulent apps. One app in particular has no purpose other than to launch a link to an adult video website. When the user is then asked to register, an email form is generated linking to another service on another website. Users are then asked to pay a $3,200.00 yearly fee within days of receipt.
These apps are constantly showing up on the Play store thanks to Google’s automated process for scanning submissions. Scambook urges users to exercise caution when looking at new apps, especially if they're not from recognized sources.
It offers three tips for spotting malicious Android apps:
- Check the source of the app, a common red flag are those companies that have never released another title and have few or no consumer reviews or ratings.
- Is personal information required? Most apps have no need to ask for sensitive personal information in order to work.
- Are further purchases required? Consumers shouldn’t need to make further purchases, especially if they have already bought the app in the first place. If you’re asked to pay extra you should exit and delete the app immediately. Even those in-app purchases that are common for many games are not usually necessary to enjoy the game.
Do you think it's time that Google tightened up its submissions process to prevent users from falling prey to this kind of scam? The iTunes app store has always had a more rigorous vetting scheme. Have you fallen prey to a scam app? Let us know your thoughts.
Image Cedit: karen roach/Shutterstock
-

Migration from XP made more complex by demand for BYOD
Publié: août 7, 2013, 4:16pm CEST par Ian Barker
 Microsoft will pull the support plug on Windows XP on April 8 2014. But with only 10 months to go to the deadline as many as 39 percent of enterprises have yet to migrate to another version of Windows, warns services and solutions company ITC Infotech.
Microsoft will pull the support plug on Windows XP on April 8 2014. But with only 10 months to go to the deadline as many as 39 percent of enterprises have yet to migrate to another version of Windows, warns services and solutions company ITC Infotech.Current trends towards BYOD are also making the migration process more complex but businesses need to address the issues in order to future proof their operations.
A recent survey by Forrester shows that more than two-thirds of North American and European information workers personally select the smartphones and tablets they use for work. Some 46 percent also use laptops that aren't on their company's approved list. The result is a blurring of the boundaries between personal and business IT with staff using their own devices to access company applications and data.
In switching from XP to Windows 7 or 8 organizations need to ensure they retain the flexibility for staff to use their own devices and maintain a secure environment. ITC Infotech warns that companies need to start the migration immediately or risk overshooting the deadline. Those that are still using XP, come April 2014, could face increased costs as Microsoft will raise the price of support for the old system to encourage migration of reluctant users.
Hardeep Singh Garewal, President -- European Operations, ITC Infotech says, "Once the deadline date is overshot, it will lead to cost escalation of up to three times as much to continue to receive support for XP, and then after a short period, support will be cut off altogether. It's therefore imperative that the transformation begins now and it would be relevant and appropriate to address the BYOD issue at the same time".
Does your business have a plan in place for the end of XP support? Will you be switching to a newer version of Windows or moving to a different platform entirely? How will you cope with demands for BYOD? Do let us know your thoughts.
-

New IBM Flex Systems squeeze a bigger cloud into a smaller data center
Publié: août 6, 2013, 11:45am CEST par Ian Barker
 Announcing a raft of additions to its Flex System range, IBM aims to help companies consolidate their IT infrastructures and reduce operating costs. The new systems combine the latest server technology with updated virtualization, network and management tools. They will allow the fast deployment of increasingly large clouds without needing to boost the size of the data center.
Announcing a raft of additions to its Flex System range, IBM aims to help companies consolidate their IT infrastructures and reduce operating costs. The new systems combine the latest server technology with updated virtualization, network and management tools. They will allow the fast deployment of increasingly large clouds without needing to boost the size of the data center.IBM quotes Morgan Stanley's Cloud Perspective survey which has found that by 2014 businesses will have migrated at least 62 percent of their database workloads to the cloud.
The new Flex Systems are available with a choice of x86 and Big Blue's own POWER7 architecture. The Flex System x222 uses a dual-density x86 architecture that allows it to support up to 2,800 Windows 7 user images on a single chassis. There's also an upgrade to the Flex System Manager so that systems can be monitored remotely using Android, Blackberry and iOS devices. A new utilization fuel gauge feature allows system managers to see at a glance the status and availability of their servers.
Flex servers can be built to order for clients who have specific processing, storage and networking configurations. You can find more information and access a configuration tool at the www.ibm.com/flex site.
-

Dell board agrees terms of buyout offer
Publié: août 2, 2013, 5:42pm CEST par Ian Barker
 A special committee of the Dell board has reached an agreement with the company’s founder Michael Dell over a buyout of the company.
A special committee of the Dell board has reached an agreement with the company’s founder Michael Dell over a buyout of the company.Under the agreed terms Mr Dell, in partnership with the investment firm Silver Lake, will buy back the company he founded in 1984 for $13.75 a share plus a special one-off dividend of 13 cents per share. This is in addition to a guaranteed third quarter dividend of 8 cents per share. The deal which values the company at $24.5 billion will be put to a special shareholder meeting on September 12.
In a statement Alex Mandl, Chairman of the Special Committee, says, "The Committee is pleased to have negotiated this transaction, which provides as much as $470 million of increased value, including the next quarterly dividend that will now be paid regardless of when the transaction closes".
As we reported earlier this year the company's profits have been tumbling and Michael Dell plans to restructure the company away from PCs towards mobile devices and services.
The buyout has been resisted by some including major shareholder Carl Icahn who argue that the deal undervalues the company. This agreement makes it more likely that Mr Dell and Silver Lake will win the day but it doesn't guarantee that the wrangling is over yet.
-

Enterprise planning company grows 250 percent as businesses move to the cloud
Publié: août 1, 2013, 3:38pm CEST par Ian Barker
Cloud-based analytics supplier Tidemark has announced its latest set of results which show 250 percent year-on-year growth. This is driven by businesses moving away from legacy suppliers as they seek to unlock the power of their data.
Christian Gheorghe, Founder and CEO of Tidemark says, "Legacy vendors, such as Oracle Hyperion, SAP and IBM Cognos are suffocating customers with archaic technology that prohibits getting the right people involved in actively managing the performance of the company. The velocity of business and increasing importance of data outside a company's walls have created new challenges that can't be solved by focusing on a few power users who act as the gatekeepers to information".
With apps for financial and operational planning along with metrics management, Tidemark aims to make information available to people at all levels of an organization, allowing managers to take decisions in real time rather than waiting for reports. It seeks to roll out its software quickly too with customers going live within 90-days of signing up for the application.
Although large enterprises continue to invest heavily in business analytics, Gartner estimates that between 70 and 80 percent of all enterprise analytics projects fail. According to Tony Rizzo, Co-founder, Customer Success at Tidemark, "It's not surprising most business analytics projects fail considering it takes nine to twelve months to deploy a legacy analytics system. Our applications, combined with a disruptive implementation approach, enable our customers to bring critical information to all corners of their organization in a fraction of the time".
-

UK families gather around their big-screen TV sets... and do their own thing
Publié: août 1, 2013, 1:13pm CEST par Ian Barker
 The rapid growth in usage of tablets and smartphones is turning us into a nation of multi-taskers according to a report by the UK telecoms regulator Ofcom. Although 91 percent of adults tune in to the main TV set in the lounge at least once a week, around 53 percent now access other media whilst watching television.
The rapid growth in usage of tablets and smartphones is turning us into a nation of multi-taskers according to a report by the UK telecoms regulator Ofcom. Although 91 percent of adults tune in to the main TV set in the lounge at least once a week, around 53 percent now access other media whilst watching television.We're interacting with TV shows or sending off tweets and Facebook posts about them whilst we watch. We're also performing unrelated tasks like shopping and surfing the web whilst the TV is on. Most of this is done via smartphones, with 51 percent of adults now owning one compared to only 27 percent two years ago. Almost a quarter of households now own a tablet computer too.
The results do show something of a television fightback, however. Although most homes now have at least three devices that can access the internet, increasingly we're reverting to having just one television. 41 percent of households only had one TV in 2012 compared to 35 percent in 2002. Those sets are getting bigger too with sales of 43-inch plus sets up 4.3 percent in the first quarter of 2013. What's more despite the wealth of catch up and recording options available, live TV accounted for 90 percent of viewing in 2012.
James Thickett, Ofcom’s Director of Research, says,
Our research shows that increasingly families are gathering in the living room to watch TV just as they were in the 1950s -- but now delivered on bigger, wider and more sophisticated sets. Unlike the 1950s family, however, they are also doing their own thing. They are tweeting about a TV show, surfing the net or watching different content altogether on a tablet.
Just a few years ago, we would be talking about last night's TV at work or at school. Now, we’re having those conversations live while watching TV -- using social media, text and instant messaging.
Television's role as babysitter is also threatened with three-quarters of parents saying that a tablet is a useful device for keeping children entertained. Of parents with a tablet 91 percent said their children either used it or had one of their own.
If you’re reading this on a tablet whilst watching live television on a big screen then do let us know in the comment thread -- if you can get your tablet back from the kids that is.
Photo Credit: Rashevskyi Viacheslav/Shutterstock
-

Cost, complexity and security concerns hold back mobile enterprise apps
Publié: juillet 31, 2013, 3:12pm CEST par Ian Barker
 Enterprise application and data security company Mobile Helix has announced the results of an independent survey of CIOs. It shows a large percentage of businesses delaying the roll out of enterprise apps on mobile devices thanks to concerns over security, costs and complexity.
Enterprise application and data security company Mobile Helix has announced the results of an independent survey of CIOs. It shows a large percentage of businesses delaying the roll out of enterprise apps on mobile devices thanks to concerns over security, costs and complexity.Highlights of the survey, conducted among 300 CIOs in the US and UK, are that companies on average had over 400 applications within their organization but that only 22 percent of them could be accessed from mobile devices despite clear demand from employees for mobile access. Major barriers to adoption are development and support costs along with security.
Matt Bancroft, Co-Founder and COO for Mobile Helix says, "Users expect critical data and applications to be available on any device and in any context, both in mobile and fixed environments, in the way that is most familiar and convenient to them. CIOs understand the obvious benefits of empowering employees and making them more productive, yet only a small proportion of enterprise apps and critical data are currently mobilized".
A high proportion, 81 percent, of respondents to the survey say they believe the cost of developing apps for mobile use is too high because of the fragmented nature of the mobile market. Only a third of respondents felt they had the necessary skills to develop native mobile apps. Of companies that had developed a native app, 47 percent said they would have reservations about doing so again because of the cost and complexity involved.
"The current approach to mobility is limiting the market -- enterprises are now looking for solutions which will allow them to develop and deliver apps to their employees simply and cost effectively," Bancroft adds. "Every device platform on the market today has a high performance, HTLM5-compliant engine. By taking this HTML5 browser-based approach, corporate IT can build a unified applications platform that extends across devices of all shapes and sizes, without compromise in functionality, performance, or security".
Photo credit:Steve Heap/Shutterstock
-

NSS Labs unveils new threat modeling and forecasting services
Publié: juillet 31, 2013, 10:55am CEST par Ian Barker
 Information security research specialist NSS Labs uses a workshop at the BlackHat USA conference today to announce new threat modeling and forecasting services to help clients better understand how they're at risk.
Information security research specialist NSS Labs uses a workshop at the BlackHat USA conference today to announce new threat modeling and forecasting services to help clients better understand how they're at risk.These new services use data from NSS's research and from its BaitNET real-time monitoring technology to deliver information about exploit and malware trends.
NSS Threat Modeling allows companies to see which vulnerabilities pose the greatest threats to their networks. It can model individual security layers and show which exploits can bypass them.
Threat Forecasting meanwhile monitors malware and exploits around the world in order to predict which threats are likely to present the greatest risk based on an enterprise's specific systems. Using BaitNET technology, which captures and verifies information in real time, it can help organizations respond quickly to the immediate risks.
Vikram Phatak, CEO at NSS Labs says, "Every security organization runs into limitations where more manpower, budget, and technology (or all three) are no longer available for solving security problems. What matters then is having real, actionable information that you can use to make informed security decisions about how to deploy the resources that you do have. With these new services, we go beyond simply telling clients what threats are out there to actually 'forecasting' whether or not a threat is likely to impact their organization".
You can find out more about the workshop on the BlackHat USA website.
Photo credit: lolloj/Shutterstock
-

Cloud management makes for easier hotspot rollouts
Publié: juillet 29, 2013, 3:36pm CEST par Ian Barker

UK-based company Managed Connections has launched its new platform as a service (PaaS) offering to provide an easy way for private and public sector organisations to set up their own wireless hotspots.
Derek Williamson, Managed Connections' Commercial Director says, "Our research shows that offering Wi-Fi hotspots will increase customer loyalty, footfall and sales which is a huge benefit to people using our services. The official Managed Connections launch comes after almost four years of research and development and on the back of this we have some really exciting additions planned for the upcoming months. We have made getting 100 percent legally compliant and highly controlled Wi-Fi and wireless broadband into a variety of venues really simple, and we can show clients how to use our platform and services as tools to bring in more customers and how to make money from them. We’re really excited by this aspect of our offering and with our systems, there is now a choice of fully managed Wi-Fi hotspot and ISP packages to suit any sized commercial venue".
Part of the attraction of the cloud-based PaaS solution is that it can be used to seamlessly integrate control of any type of network from simple Wi-Fi hotspots to entire building or community networks.
With the added benefit of 24-hour support, this aims to give businesses maximum flexibility in responding to demand for network services.
Photo Credit: phloxii/Shutterstock
-

Lock up your data ecommerce companies are warned
Publié: juillet 26, 2013, 12:49pm CEST par Ian Barker
 According to Imperva's recent Web Application Attack Report most applications have suffered attacks four or more times per month whilst some are under almost constant attack. In addition retail sites suffer twice the number of SQL injection attacks compared to other industries.
According to Imperva's recent Web Application Attack Report most applications have suffered attacks four or more times per month whilst some are under almost constant attack. In addition retail sites suffer twice the number of SQL injection attacks compared to other industries.The report also finds that the US tops the list globally as the source of web-based attacks.
Security solutions company Cenzic believes that the level of attacks is due to companies prioritizing the security of their assets rather than their data. Tyler Rorabaugh, VP of Engineering at Cenzic says on the company's blog, "Companies tend to approach security using a traditional perimeter based security model -- they first establish a perimeter by monitoring assets, then focus on risk analysis and management. The problem is that it's like putting a fence around a piece of property but the area that the property is located in is constantly changing and evolving. Let's face it, today's businesses are data-centric, where data is the core of their business, but our security models are focused primarily on assets and not the data itself".
Enterprises need to take steps to minimise attacks and secure their data. Rorabaugh adds, "Web Application Firewalls and Database Firewalls help, but you must proactively test your applications and data access points with automated attack systems, pen testers and application security testers, and you must do this constantly. There are only a few types of hackers -- those that want to prove a point, gain respect or learn, those that are concerned about something you may be doing, and the last and most important of these are those that want your gold (data) or are in it for the money."
Do you believe ecommerce companies are doing enough to protect your data when you shop online? Let us know via the comments thread.
Photo Credit: Maksim Kabakou/
-

Kaspersky tops real world protection test
Publié: juillet 26, 2013, 11:28am CEST par Ian Barker
 Independent testing organisation AV-Comparatives has released the results of its real world protection test for March to June 2013. The tests use each security suite on its default settings and live URLs that point to malware executables along with drive-by exploits.
Independent testing organisation AV-Comparatives has released the results of its real world protection test for March to June 2013. The tests use each security suite on its default settings and live URLs that point to malware executables along with drive-by exploits.Using a total of 1,972 test cases over the four month period the results show that all of the major security packages offer high levels of protection. Bitdefender and Kaspersky top the charts with 99.9 percent protection levels, F-Secure also manages 99.9 but ranks slightly lower as it relied on user interaction to block three of the threats.
Of the other popular products, McAfee managed 99.3 percent, Bullguard 97.9 and AVG 96.3. Propping up the bottom of the chart is AhnLab on 90 percent below Microsoft Security Essentials which managed 92.5.
The report also looks at false alarms caused by wrongly blocked domains and files. Bitdefender does less well here with 24 wrong blocks, Kaspersky and Sophos wrongly blocked only one. The worst performers in the detection charts are, as you might expect, amongst the top performers here with AhnLab and Microsoft having no false alarms at all along with AVG and ESET.
The report's authors note, "The duty of security products is to protect against malicious sites/files, not to censor or limit the access only to well-known popular applications and websites. If the user deliberately chooses a high security setting, which warns that it may legitimately block some sites or files, then this may be considered acceptable. However, we do not regard it to be acceptable as a default setting, where the user has not been warned".
The message to take away from all of this is that the differences between mainstream security products are pretty small. Your choice really comes down to a balance between maximum protection and the inconvenience of false alarms.
You can download a PDF of the full test on the AV-Comparatives site.
Photo Credit: Thomas Bethge/Shutterstock
-

First use of Android 'Master Key' vulnerability discovered
Publié: juillet 24, 2013, 4:38pm CEST par Ian Barker
 Security specialist Symantec is reporting the first malicious use of the Android 'Master Key' vulnerability that allows hackers to inject malicious code into apps without invalidating the digital signature.
Security specialist Symantec is reporting the first malicious use of the Android 'Master Key' vulnerability that allows hackers to inject malicious code into apps without invalidating the digital signature.The vulnerability was discovered earlier this month but Norton Mobile Insight has now detected its first use in the wild. Mobile Insight harvests and analyzes Android apps from marketplaces around the world and has discovered the infection labelled Android.Skullkey in two applications from China. These are legitimate apps used to make appointments with doctors.
A hacker has added code to these apps allowing them to steal sensitive data such as IMEI and phone numbers. They can also remotely control the device, send premium rate SMS messages and even disable some Chinese market security apps at root level.
Symantec's official blog says, "We expect attackers to continue to leverage this vulnerability to infect unsuspecting user devices. Symantec recommends users only download applications from reputable Android application marketplaces". Naturally, it also advises that Norton Mobile Security can protect against this threat.
Photo credit: arbalet/Shutterstock
-

Internet Explorer has the worst phishing catch rate of all major browsers
Publié: juillet 24, 2013, 12:41pm CEST par Ian Barker
 A new report by security research firm NSS Labs looks at the comparative performance of popular browsers when it comes to blocking phishing attacks. Over a 12-day test period the average phishing catch rate ranged from 96 percent for Firefox 19 to only 83 percent for Internet Explorer 10.
A new report by security research firm NSS Labs looks at the comparative performance of popular browsers when it comes to blocking phishing attacks. Over a 12-day test period the average phishing catch rate ranged from 96 percent for Firefox 19 to only 83 percent for Internet Explorer 10.Of the other big three, Chrome 25 scored 92 percent, Safari 5 managed 95 percent, and Opera 12 scored 89 percent. Chrome, Firefox and Safari all make use of Google's Safe Browsing API so it's unsurprising that they scored within a few points of each other. Microsoft uses its own SmartScreen technology in IE, whereas Opera uses a combination of blacklists from Netcraft, PhishTank and TRUSTe.
The average block rate across all of the tested browsers is 90.1 percent, down almost 2 percent on the previous year's average, although those using the Google Safe Browsing API performed slightly better than last year.
What's also interesting is the amount of time it takes for a new phishing site to be blocked. As these sites only have an average lifespan of 26 hours it's vital that they're detected and blocked quickly. Once again IE 10 turns in disappointing results, taking on average 2.55 hours to block a new site. Safari and Firefox do best here taking 0.5 and 0.7 hours respectively, whilst Chrome at 1.68 hours is around the all browser average. Opera scores just ahead of IE with 2.47 hours.
All of the NSS tests were carried out on a PC running Windows 8 Enterprise with the latest version of each browser available on each day of the test. The full methodology is available on the NSS website.
Photo credit: Slavoljub Pantelic/Shutterstock
-

PlanForCloud helps forecast more than $1 billion in cloud spending
Publié: juillet 23, 2013, 5:02pm CEST par Ian Barker
 Forecasting enterprise cloud costs can be hard to do well but is essential to businesses who want to implement cloud solutions effectively. RightScale announces today that its PlanForCloud product has helped companies forecast $1 billion in cloud spending since its launch last year.
Forecasting enterprise cloud costs can be hard to do well but is essential to businesses who want to implement cloud solutions effectively. RightScale announces today that its PlanForCloud product has helped companies forecast $1 billion in cloud spending since its launch last year.By analyzing data from more than 9,500 cloud deployments, PlanForCloud has revealed a number of interesting trends. For example 70 percent of cloud spending goes on servers, 18 percent on storage and only 6 percent on data transfer, with a further 6 percent accounted for by other costs such as transaction charges and support.
It also reveals that on Amazon Web Services some 54 percent of spending is on Reserved Instances of one year or more. This is where companies sign up to a contract for a specific resource up front in order to obtain a discounted hourly rate.
The majority of users opting for Reserved Instances, 62 percent, go for the highest level of utilization, under which the service will be charged as though it's running 24/7 for the duration of the contract. This shows that companies are prepared to adopt a long term commitment to the cloud rather than signing up on an ad-hoc basis.
You can read more about the findings on the RightScale blog and access the free cloud cost calculator to help with your own business decisions on the PlanForCloud website.
Photo Credit: Rrraum/Shutterstock
-

Tableau Online brings business intelligence to the cloud
Publié: juillet 19, 2013, 11:07am CEST par Ian Barker
 Tableau Software has launched a SaaS version of its Tableau Server business analytics product. The software allows users to explore and share corporate data in a reliable and secure way without the need for specialist support.
Tableau Software has launched a SaaS version of its Tableau Server business analytics product. The software allows users to explore and share corporate data in a reliable and secure way without the need for specialist support."Tableau Online will allow people to get their analytics up and running in minutes and add users in a few clicks," says Chris Stolte, Chief Development Officer and co-founder of Tableau Software. "It's completely scalable and secure and requires no infrastructure. It's the fastest way to get everyone in your company using powerful analytics to make better decisions today".
Data can be displayed in an easy to use graphical dashboard format that's accessible via a browser or on Android and iOS portable devices. Information can also be shared via a centralized server and is automatically refreshed so that you know everyone is working on the latest version.
The package can interface with other cloud tools including Salesforce.com and Google Analytics. Users of Tableau are able to subscribe via email so that they're alerted to changes in the data through their inbox. The package can scale as the company grows and at any point can be migrated from the cloud to Tableau Server to run in house.
To find out more about Tableau Online and sign up for a free trial visit the company's website.
-

Cloud-based social collaboration aims to make businesses more productive
Publié: juillet 18, 2013, 1:00pm CEST par Ian Barker
 We're used to sharing information via social networking in our personal lives, but in the business world the impact of this has so far proved limited. Enterprise software supplier Deltek hopes to change this with the launch of Kona Business, a premium version of its cloud-based social collaboration and productivity tool.
We're used to sharing information via social networking in our personal lives, but in the business world the impact of this has so far proved limited. Enterprise software supplier Deltek hopes to change this with the launch of Kona Business, a premium version of its cloud-based social collaboration and productivity tool.A cross between a calendar, social network and project management tool, Kona Business brings together all of the interactions between people working on a project, allowing them to get things done more effectively and more quickly, and as it's in the cloud it can be rolled out easily via browsers or through Android and iOS apps.
Because it's conversation rather than task centered the software allows individuals to work in a more natural way and helps to remove communication barriers.
Scott DeFusco, Deltek's Vice President of Product Strategy and Management for Kona says, "Individuals have become accustomed to things that span across your life -- personally and professionally. Kona Business addresses both organizational adoption and ongoing engagement -- a huge challenge in the social collaboration space".
Kona allows all conversations relating to a project to be captured in one place. It can also integrate with file sharing tools like Dropbox as well as with Google Docs so that project documents can be shared.
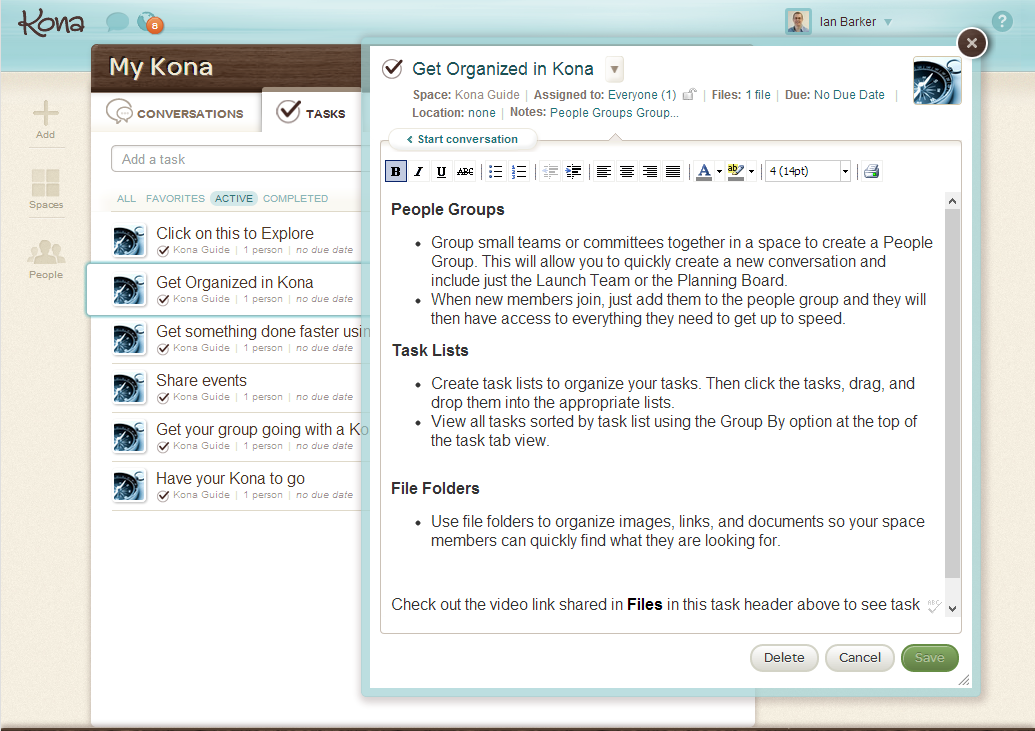
"Kona can be the glue that connects key individuals and processes, extending the power of interaction and technology for the entire ecosystem," says DeFusco. "Effectively connecting people, processes and technology is no longer the exception, it’s the rule. This is why Deltek created -- and uses -- Kona Business".
You can find out more about what Kona can do for your business by visiting the Deltek website.
Photo Credit: Alexander Kirch/Shutterstock
-

Global outsourcing predicted to reach $288 billion in 2013
Publié: juillet 17, 2013, 1:41pm CEST par Ian Barker
 Analyst group Gartner says in a new report that the global market for IT outsourcing is set to reach $288 billion this year. This though represents an increase of only 2.8 percent and growth is slower than predicted by previous forecasts.
Analyst group Gartner says in a new report that the global market for IT outsourcing is set to reach $288 billion this year. This though represents an increase of only 2.8 percent and growth is slower than predicted by previous forecasts.Bryan Britz, research vice president at Gartner says, "Planned new adoption of ITO remains positive in all service line segments. However, constrained IT budgets, an evolving ITO delivery model, economic conditions and cost-focused buyers are limiting the growth potential of the ITO market".
It's the emerging markets of Asia/Pacific, China and Latin America where most of the growth is taking place. Outsourcing in these areas is expected to grow by more than 13 percent in 2013/14. "Expansion by multinationals into these regions, new buyers of ITO that are themselves growing organizations, and fertile economic conditions all drive the positive outlook," says the report.
Gartner says that plans for increased use of BYOD and mobile devices should see growth for outsourced support continue through 2017. Desktop outsourcing though is in overall decline. In North America it predicts that buyers will seek to move more services to managed relationships in order to save money and have more predictability of longer term costs.
Photo Credit: Lasse Kristensen/Shutterstock
-

Automated migration makes for a cloudier business outlook
Publié: juillet 16, 2013, 5:04pm CEST par Ian Barker
 One of the things that puts businesses off moving their systems to the cloud is the problem of migrating all of their applications and data to a remote platform. Californian company CloudVelocity aims to address this with its launch of One Hybrid Cloud, a package that streamlines the movement of information to Amazon Web Services (AWS).
One of the things that puts businesses off moving their systems to the cloud is the problem of migrating all of their applications and data to a remote platform. Californian company CloudVelocity aims to address this with its launch of One Hybrid Cloud, a package that streamlines the movement of information to Amazon Web Services (AWS).One Hybrid Cloud effectively makes AWS an extension of the corporate data center, making it possible to run existing Linux and Windows apps in the cloud without modification. It automates many of the processes required to migrate apps to the cloud and in the process the developers reckon it can reduce migration expenses by more than 90 percent.
"Until today, cloud migration and cloud-enabled disaster recovery have not been viable for the vast majority of enterprise data center apps," says Rajeev Chawla, chief executive officer of CloudVelocity. "With today's launch of One Hybrid Cloud, we are significantly reducing the amount of manual processes, risks and expenses otherwise required to deploy robust enterprise data center apps into the cloud".
Using One Hybrid Cloud the cloud pre-production and production environments are virtually identical. This minimizes errors and reduces development cycles as it means software can be updated, tested and easily pushed live. It means that the cloud also becomes an ideal operating model for disaster recovery.
Find out more on the CloudVelocity website or you can watch a screen capture demo of the product on YouTube.
Photo Credit: Sergey150770/Shutterstock
-

Cloud-in-a-Box allows developers to deploy solutions fast
Publié: juillet 11, 2013, 4:07pm CEST par Ian Barker
 Development company FatFractal has launched its new Cloud-in-a-Box solution to make it easier for enterprises to deploy software in public or private clouds or in traditional data centers.
Development company FatFractal has launched its new Cloud-in-a-Box solution to make it easier for enterprises to deploy software in public or private clouds or in traditional data centers.The company's Platform as a Service (Paas) and Backend as a Service (BaaS) products allow developers to create tailored solutions without the need for repetitive steps. FatFractal CEO, Kevin Nickels says, "We've hit the right balance between out-of-the-box services like security, scalability and performance without limiting the developer’s ability to do whatever they want".
The platform can be used for migration and allows developers to use their preferred programming language. It can help to quickly create mobile apps that make use of out-of-the box security and scalability features as well as supporting complex data relationships and queries.
Cloud-in-a-Box works with all of FatFractal's modules to allow enterprises to deploy into a range of environments. It's also compatible with open infrastructure standards like OpenStack. This allows the company to offer competitive pricing, Nickels says, "We work to encourage innovation by creating a no-cost sandbox and when developers are ready for production, the price of our NoServer module is typically 45%-90% lower than buying directly from a IaaS provider."
Details of a successful independent evaluation of the product by developer Cory Wiles are online at GitHub. Wiles says, "Based on the test results, FatFractal is the easiest to install and configure, has the smallest footprint, no additional library dependencies, is the most secure, is the only one that offers public API access and local development, and interface with multiple backends at the same time. We also recognize FatFractal as the most flexible and least intrusive."
For more information on Cloud-in-a-Box and what it can do visit the FatFractal website.
Photo Credit: art_of_sun/Shutterstock
-

BullGuard launches free online virus scan
Publié: juillet 10, 2013, 3:00pm CEST par Ian Barker

One man's virus is often another's legitimate program or cookie, so whatever antivirus software you have installed it's always useful to be able to get a second opinion from time to time. There are already a number of online scans you can use for this and BullGuard is the latest to join the party with today's launch of its own free scanner.
Unlike some of the alternative offerings, BullGuard works by adding a plug-in to your browser. This lets you run the scan at any time with just a single click on a toolbar button so you don't have to remember the website address or where you filed the bookmark. It supports all of the popular browsers too. The scan, which took just a couple of minutes using the Chrome plug-in on my -- not quite as fast as it used to be -- Windows 7 laptop, looks for viruses and checks that your current security is up to date.
Once it's complete you can view full details of the scan and any detected threats in a text file. You also get the opportunity to download a 60-day trial of the full BullGuard Internet Security 2013 suite to remove any threats found.
"We recognize that maintaining system security is often a painful process and that many consumers don't have the time or inclination to constantly monitor their software," says BullGuard Head of Product Management, Alex Balan. "We know how important it is to ensure that security suites are capable of protecting against the latest threats, so we developed BullGuard Virus Scan with this in mind".
Whether you've noticed suspicious activity on your PC or you just want to double check your existing protection you can try out the scan by visiting the free virus scanner page on BullGuard’s website.
-

New Trojan targets Linux servers
Publié: juillet 10, 2013, 1:58pm CEST par Ian Barker
 Antivirus company Doctor Web has released its review of virus activity for June. Trojans remain the main threat but the big news is a new version of the Linux.Sshdkit virus designed to steal passwords from Linux servers. It has undergone a number of changes to make it harder for antivirus analysts to intercept stolen passwords.
Antivirus company Doctor Web has released its review of virus activity for June. Trojans remain the main threat but the big news is a new version of the Linux.Sshdkit virus designed to steal passwords from Linux servers. It has undergone a number of changes to make it harder for antivirus analysts to intercept stolen passwords.This follows the trend that we reported last month of attackers becoming more businesslike in their attacks. Although the number of infected Linux servers is small as yet it's a worrying development.
Windows viruses still top the charts with Trojan.Mods.2, which redirects users to malicious web pages, being the most common accounting for almost 4 percent of infections in the month. There's also been a rise in Trojan encoders, a variant of ransomware, distributed primarily via email.
Mobile threats remain common too, again aimed at stealing information for financial gain or duping users into making use of premium rate SMS services. Many of these target specific regions, Android.Tempur.1.origin for example is aimed at users in South Korea and is one of the most prominent threats of its kind.
You can read the full report and more details of specific threats on the Doctor Web site.
Image credit: njaj/Shutterstock
-

More power and flexibility from 1&1's Dynamic Cloud Server
Publié: juillet 9, 2013, 12:58pm CEST par Ian Barker
 Leading web host company 1&1 Internet has launched a new cloud server package that delivers user configurable resources to bring greater efficiency to business users.
Leading web host company 1&1 Internet has launched a new cloud server package that delivers user configurable resources to bring greater efficiency to business users.The adjustable resources -- processor cores, RAM and hard disk space -- are configurable upwards and downwards by the user at any time. This offers the capacity for a very high performance resource at a low cost. The pricing model is clearly set out with costs per hour for each core and gigabyte of RAM and disk space. Changes become active within five minutes and there's no minimum contract term involved.
There's also a FLEX feature that allows memory and CPU requirements to be suspended whilst the data is retained on hard disk. This is ideal for businesses that do seasonal work or have peaks in demand.
Robert Hoffmann, CEO Hosting, 1&1 Internet Ltd, says, "The latest generation Dynamic Cloud Server offers a number of distinct differentiators that can result in a transformation of efficiencies. The user enjoys the best of both worlds -- dedicated highly reliable resources as well as completely dynamic scalability. An innovative 'sleep mode' can provide a unique freedom to leverage high performance for specific, shorter periods -- a powerful benefit for many user groups at an unbeatable price".
Servers are offered in Linux and Windows versions and it's possible for users to switch at any point if they wish. 1&1's data center provides multiple redundant cores and storage to ensure maximum reliability. For more information on package costs and availability visit www.1and1.co.uk.
-

Microsoft partners find more profit and more customers from the cloud
Publié: juillet 8, 2013, 4:39pm CEST par Ian Barker
 A study unveiled at Microsoft's Worldwide Partner Conference in Houston shows that partners with more than half their revenue related to the cloud had higher gross profits, more new customers and faster business growth.
A study unveiled at Microsoft's Worldwide Partner Conference in Houston shows that partners with more than half their revenue related to the cloud had higher gross profits, more new customers and faster business growth.The study by IDC goes to highlight the changes taking place in the business world as more organizations shift their systems to the cloud rather than keeping them in house. "Cloud alone hasn't caused these impressive numbers, though that is absolutely part of it; top-performing partners were visionaries that took on cloud technologies before their peers," says Darren Bibby, program vice president of Channels and Alliances Research at IDC. "We're at the point in the industry's overall cloud transition where partners that don't move some of their business to the cloud likely won't survive. And some partners that are getting ready to sell their business or retire may be OK with that. Most won't be".
The study also shows that customer buying preferences are increasingly cloud-centered with 63 percent expecting to have a single cloud service provider to meet their needs. In addition 67 percent expect to purchase a variety of different cloud services from the same vendor.
Jon Roskill, corporate vice president of the Worldwide Partner Group, Microsoft says, "This research validates our belief that the most successful partners are the ones that offer a hybrid approach to IT. Microsoft is the only vendor equipped to help partners offer their customers a suite of on-premises and cloud solutions in both public and private cloud environments. By offering a hybrid approach, it better addresses customer needs and, in turn, helps our partners make more money".
You can read the full report on Microsoft’s website.

-

Faster UK 4G from EE -- nice speed if you can get it
Publié: juillet 3, 2013, 4:38pm CEST par Ian Barker
 My colleague Mihaita Bamburic reported earlier on EE's rollout of faster 4G LTE services in 12 major UK cities with a potential to double current average internet speeds.
My colleague Mihaita Bamburic reported earlier on EE's rollout of faster 4G LTE services in 12 major UK cities with a potential to double current average internet speeds.Despite the claims that this would make EE's mobile network unequaled in Europe I can't say I was especially excited by this news. Living as I do within 20 miles of one of those major cities -- Manchester -- it's sometimes hard to get a 3G signal here let alone 4G.
You can argue it's my fault for choosing to live where I do, but that's always the problem with new phone technology. Although EE claimed back in May that it was on target to reach a million 4G customers by the end of the year the reality is that most of those will be in large towns and cities. The rest of us have to wait until the world catches up.
To be fair, 4G is spreading fairly fast, Olaf Swantee, EE's Chief Executive Officer has said that 4G will be available to 98 percent of people in the UK in 2014. Other operators such as O2 have also promised aggressive roll outs which is why EE is keen to grab as many customers as it can now whilst it has a head start. That's "basic" 4G of course, the benefits of the faster services promised by today's announcement will take longer to spread and may not reach some areas at all.
Emeka Obiodu at independent analysts Ovum says, "The doubling of LTE speeds in several cities across the UK is a nice headline. But, on its own, we don't believe it is a standout game changer as telcos struggle to sell LTE as a speedier network. Instead, its merit is that it gives EE a base from which to offer LTE packages tiered on speed and usage which are far more acceptable to customers. That is going to be the interesting thing to watch out for and if its rivals do not have the capability to do that, EE could have quite a solid marketing message."
Obiodu also says, "Fleshing out its shared plans for customers, and positioning it as a way for families to save money, is a canny move in today's austerity-dominated society. The ability to cap costs should appeal to families who will get better clarity on what their telecoms spend will be. We also liked how EE is going to use the shared plans as a nudge to push customers into a higher-priced plan. This is what Verizon Wireless has done successfully in the US and is one reason why their ARPU is rising."
The moral of all this is that if you need fast mobile internet make your home in a big city. The irony being that it's the place where you're least likely to need it as there will be plenty of free Wi-Fi and other ways of getting online. If you want to live elsewhere or you're inclined to move about it probably isn't worth making the leap to 4G just yet.
-

Microsoft announces new Dynamics CRM to deliver improved customer experience
Publié: juillet 3, 2013, 12:12pm CEST par Ian Barker
 Microsoft has announced that it is releasing an updated version of its Dynamics CRM package in the fall of 2013. The new package is designed to help enterprises engage with their customers and will be available as both cloud and installed systems.
Microsoft has announced that it is releasing an updated version of its Dynamics CRM package in the fall of 2013. The new package is designed to help enterprises engage with their customers and will be available as both cloud and installed systems.The refreshed version is designed to deliver a fast and fluid user experience, enabling people to access information that’s relevant to their jobs and have deeper insight into customer requirements. It also offers improved social collaboration features as well as the ability to access information on a variety of devices including Windows 8 tablets and iPads. Android, iPhone and Windows Phone 8 versions will be available shortly after the package's release.
"Customers don’t want to be sold to anymore. They are knowledgeable and are interacting with their social and professional networks to make their buying decisions. They expect businesses to help them make the most informed choice," says Bob Stutz, corporate vice president, Microsoft Dynamics CRM. "Microsoft Dynamics CRM helps people connect with these customers in a way that is personal -- giving them the information they need to choose the right solutions, engage to drive sales and nurture relationships to deliver amazing experiences."
Key features of the new release include links to Microsoft’s MarketingPilot campaign management solution to help businesses understand their customers. Dynamics CRM lets companies adapt business processes according to the needs of their customers. It also allows users to collaborate and share customer information via Yammer from within the Dynamics package. It connects to Lync and Skype too enabling real-time contact updates.
You can find out more about what’s new in Microsoft Dynamics CRM by visiting the Microsoft website.
-

AltaVista goes to great server in the sky
Publié: juillet 2, 2013, 10:58am CEST par Ian Barker
 Let us pause for a moment to remember AltaVista. Current owner Yahoo quietly announced in a blog post at the end of last week that the once popular search engine is to close on July 8. The news was tucked away in a raft of other closure announcements. Users will be redirected to Yahoo Search.
Let us pause for a moment to remember AltaVista. Current owner Yahoo quietly announced in a blog post at the end of last week that the once popular search engine is to close on July 8. The news was tucked away in a raft of other closure announcements. Users will be redirected to Yahoo Search.It's hard to appreciate now that in the days before Google's algorithm made the fast indexing of large numbers of sites possible, searching the web was something of a hit and miss affair. Search engines relied on fixed indexes that were slow to update and found it hard to cope with the rapidly increasing number of sites.
When AltaVista launched in 1995 it proved immediately popular as it indexed around 20 million pages, more than any other search tool at the time, and used its own crawler technology to keep it up to date. It also returned results quickly thanks to fast computers behind the scenes.
It remained a top destination for web users until 2001 when the number of Google searches moved ahead. Yahoo acquired AltaVista's technology and name in 2003.
Like most websites it had its moment in the sun before being overtaken by something newer and cooler. You have a few days left to visit the AltaVista site for old times sake before it's gone for good. It probably won't be missed but it deserves to be remembered.
Do you have fond recollections of AltaVista or other sites from the early days of the internet? Feel free to use the comments as a book of remembrance.
Photo Credit: inxti / Shutterstock
-

Let's work together -- viruses collaborate to survive
Publié: juillet 1, 2013, 3:31pm CEST par Ian Barker

Microsoft research has uncovered a pair of viruses that work together to make them harder to remove from infected computers. Malware researcher Hyun Choi revealed the news in a TechNet blogpost.
The Vobfus virus spreads through infected website links or via removable or mapped network drives. Once installed on a system it downloads the Beebone virus which enrols the machine in a botnet. After this the two pieces of malware work together to download the latest versions of each, making them harder to detect and remove and allowing them to maintain a presence on infected systems.
Mr Choi says, "This cyclical relationship between Beebone and Vobfus downloading each other is the reason why Vobfus may seem so resilient to antivirus products. Vobfus and Beebone can constantly update each other with new variants. Updated antivirus products may detect one variant present on the system; however, newer downloaded variants may not be detected immediately. A typical self-updating malware family that just updates itself can be remediated once it is detected, because once removed from the system it cannot download newer versions of itself. In the case with Vobfus, even if it is detected and remediated, it could have downloaded an undetected Beebone which can in turn download an undetected variant of Vobfus."
Although it was first discovered in 2009, the Vobfus virus is proving to be a persistent problem due to its close relationship with Beebone.
To avoid infection Mr Choi recommends that users exercise caution when clicking external links as well as keeping their browser and other software up to date. Because Vobfus often spreads via removable drives it may also be worth disabling the Windows autorun feature.
Have you experienced a virus infection that's hard to shift or which keeps on coming back? Let us know in the comments if you think you've fallen foul of a collaborative virus.
Photo Credit: Paola Canzonetta/Shutterstock
-

Microsoft showcases new developer opportunities
Publié: juin 28, 2013, 11:51am CEST par Ian Barker
Day two's keynote at the Microsoft Build 2013 developer conference focused on the company's commitment to the Windows Azure mobile development program.
Azure Mobile Services and Azure Web Sites move from preview to general availability status. Mobile Services makes it easier for developers to build connected, scalable apps for Windows, Android and iOS, whilst Web Sites makes it simple to create and run webpages. There were also previews of new Azure technologies including Auto Scale, offering the ability to adjust capacity according to customers' needs. Plus a preview of enhancements for Azure Active Directory.
Satya Nadella, president, Server and Tools Business said, "Nearly 1,000 new businesses are betting on Windows Azure daily, and as momentum for Azure grows, so too does the developer opportunity to build applications that power modern businesses".
For .NET developers Microsoft has provided a roadmap to help update core business applications and move towards web apps and cloud environments.
A new advertising developer kit for Windows 8.1 was announced along with a revised one for Windows 8, to enable relevant advertising in Windows apps. Both SDKs are available from adsinapps.microsoft.com. There's also a readjustment of ad sizes to target those most in demand.
The release preview of Windows Embedded 8.1 is available from today too. This was demonstrated by Steve Guggenheimer, corporate vice president and chief evangelist, Developer Platform Evangelism, using the Avis "Select and Go" app running on a Windows Embedded 8 Industry tablet and Windows Embedded 8 Handheld device, illustrating the opportunity for developers to capitalize on the shared Windows codebase.
Several third-party apps were also showcased. These included PayPal's software developer kit allowing payments to be integrated into Windows apps along with developer tools from Adobe and Unity.
Summing up Guggenheimer said, "Whether developing for existing, client/server, or emerging device and cloud application patterns, developers need a platform that offers consistency and flexibility. Only the Windows platform -- spanning Windows, Windows Phone, Windows Azure and more -- meets this need".
-

Access management goes self-service with Tufin Security Suite
Publié: juin 26, 2013, 12:07pm CEST par Ian Barker
 Policy management specialist Tufin Technologies launches the latest version of its Security Suite for business networks with a number of new features. Version R13-2 has a self-service portal for connectivity requests, enhanced device support and increased automation of security-related policies.
Policy management specialist Tufin Technologies launches the latest version of its Security Suite for business networks with a number of new features. Version R13-2 has a self-service portal for connectivity requests, enhanced device support and increased automation of security-related policies.Tufin Security Suite is made up of three modules, SecureApp which manages the network connectivity and security requirements of applications, SecureChange which looks after change management and risk analysis, and SecureTrack which automates policy management for network infrastructure.
Key changes in the latest version include the introduction of a self-service portal to allow non-technical users to request application access, automated removal of decommissioned servers, IPv6 support and RESTful APIs to allow interaction with other systems.
"Tufin continues to demonstrate its commitment to delivering business value via more efficient security policy management. R13-2 aligns security policy management and business operations through its self-service capabilities, extended device support, and enhanced application connectivity which introduces a whole new set of security, compliance and efficiency benefits," says Reuven Harrison, CTO of Tufin. "In fact, we are including a free, limited version of SecureApp in R13-2: SecureApp Basic. We are confident that once customers experience the value it delivers they will be eager to implement it. In addition, R13-2 extends our support for IPv6 and provides more comprehensive network topology. As networks continue to grow in complexity, Tufin will ensure that security teams not only protect the network, but also operate much more efficiently than before."
The latest suite is available now and there's a 30-day evaluation version available to download from the Tufin website.
Photo Credit: Alexander Kirch/Shutterstock
-

Microsoft trumpets next generation enterprise solutions
Publié: juin 25, 2013, 1:23pm CEST par Ian Barker
In a keynote speech to the TechEd Europe conference in Madrid, Microsoft's Server and Tools Corporate VP Brad Anderson has announced the availability of preview versions of Windows Server 2012 R2, System Center 2012 R2 and SQL Server 2014.
Writing on the company’s blog Anderson says, "These products are going to have a massive impact on companies around the world -- and IT pros are going to see the traditional boundaries between datacenters vanish and a true hybrid cloud emerge".
He also used the speech to show how major European companies like Spain's Telefónica and Italy's DDM are already using the Microsoft platforms to maintain their services in an easily scalable environment. The largest telecoms operator in Spain, Telefónica aims to move 80 percent of its IT to virtual platforms using Windows Server Hyper-V and SQL Server.
DDM has developed its popular CineTrailer movie app on the Windows Azure platform. This has allowed it to scale easily in order to accommodate growth in demand from PCs, mobile devices and connected TVs.
Cambridge, UK based semiconductor maker ARM Holdings was showcased to exhibit the potential for Surface RT devices in the enterprise. The Surface RT (which uses ARM chips) has been supplied to employees in IT, quality assurance, marketing and sales to enhance their efficiency and mobility.
Anderson sums up, "I believe that Microsoft’s track record with new enterprise cloud offerings makes it the best equipped to deliver an end-to-end app and IT experience -- everything from building the app, deployment, maintenance and managing every device that uses it."
The server software previews can be downloaded from the TechNet site.
-

Microsoft and Oracle head into the cloud together
Publié: juin 25, 2013, 12:01pm CEST par Ian Barker
 Microsoft has announced a tie up with Oracle that will allow customers to run Oracle software on Windows Server Hyper-V and in Windows Azure.
Microsoft has announced a tie up with Oracle that will allow customers to run Oracle software on Windows Server Hyper-V and in Windows Azure.The partnership means that Oracle will certify and support its software -- including Java, Oracle Database and Oracle WebLogic Server -- on the Microsoft cloud platforms. The key elements of the deal are listed on Oracle's corporate blog.
Commenting on the move Steve Ballmer, Microsoft's chief executive says, "Microsoft is deeply committed to giving businesses what they need, and clearly that is the ability to run enterprise workloads in private clouds, public clouds and, increasingly, across both. Now our customers will be able to take advantage of the flexibility our unique hybrid cloud solutions offer for their Oracle applications, middleware and databases, just like they have been able to do on Windows Server for years".
Oracle President Mark Hurd says, "Our customers' IT environments are changing rapidly to meet the dynamic nature of the world today. At Oracle, we are committed to providing greater choice and flexibility to customers by providing multiple deployment options for our software, including on-premises, as well as public, private, and hybrid clouds. This collaboration with Microsoft extends our partnership and is important for the benefit of our customers".
An interesting effect of the deal is it means that Oracle Linux will be available as a preconfigured instance on Windows Azure. Microsoft, however, will gain from getting customers to pay for its services even if they’re running rival software.
Microsoft's Azure cloud platform has so far lagged behind Amazon's AWS offering. This deal with Oracle may provide the push it needs to gain impetus in the enterprise marketplace.
Photo Credit: 2jenn/Shutterstock
-

UK government launches cyber security awareness campaign
Publié: juin 24, 2013, 12:29pm CEST par Ian Barker
As part of its National Cyber Security Pr
 ogramme the UK government has announced the first stage in a new £4 million awareness campaign. The campaign due to be launched in the autumn draws on expertise from various government departments and is led by the Home Office.
ogramme the UK government has announced the first stage in a new £4 million awareness campaign. The campaign due to be launched in the autumn draws on expertise from various government departments and is led by the Home Office.Bids are currently being invited from media, PR and creative agencies to produce a communications strategy to educate consumers and small businesses on the risks presented by cyber crime.
Security Minister James Brokenshire says, "The digitisation of the UK economy has made our lives easier and has created huge opportunities, but it has also created individual security risks as well. If we are to meet these new challenges it's essential we step up our efforts to stay safe online".
Research by the National Fraud Authority has shown that if individuals and small businesses make minor changes to their behaviour they can prevent significant online losses. Brokenshire adds, "By making small changes British businesses can remain competitive in the global economy and consumers can have greater confidence using the internet".
Advice on protecting yourself online is already available on the government's Get Safe Online website. Strangely it's short of information on protecting your data from national security agencies...
Photo Credit: fotoscool/Shutterstock
-

We see no threats, companies in denial over security
Publié: juin 14, 2013, 11:31am CEST par Ian Barker
 Network security specialist Lancope has released the results of a survey showing that 66 percent of large organisations said that either they hadn't experienced a security incident in the last 12-18 months or were unsure if they had.
Network security specialist Lancope has released the results of a survey showing that 66 percent of large organisations said that either they hadn't experienced a security incident in the last 12-18 months or were unsure if they had.Businesses face a constant stream of threats from the normal phishing and malware to more sophisticated, targeted attacks. But Tom Cross, Lancope's director of security research, says that it's very unlikely that none of these organisations experienced incidents during that time frame: "Any system you connect to the Internet is going to be targeted by attackers very quickly thereafter. I would assert that if you’re unsure whether or not your organisation has had a security incident, the chances are very high that the answer is yes -- and this is a significant problem".
Companies responding to the survey said that the most common incidents they were aware of were malware, DDoS and insider attacks. While 25 percent said that the worst impact incidents had on their organisation was to their reputation, 21 percent had suffered financial loss and 13 percent had experienced intellectual property being stolen.
Of course the threat landscape is constantly shifting and half of enterprises now felt that mobile devices and BYOD represented the greatest danger to their organisations. Insider threats are also high on the worry list with 32 percent concerned about them. Lack of information about what was happening inside their network concerned 28 percent too.
Cross concludes, "Any organisation needs to know whether or not they've been subject to a security breach, and if companies believe they have not, the question may be are they really aware of everything that is happening on their networks?"
Since it's very often our information that gets compromised when security is breached perhaps this is an issue that everyone needs to take seriously. Before we give our business to a company should we be asking how good their data security is?
Photo Credit: RTimages/Shutterstock
-

New Myspace launches... Hello...? Is anyone there?
Publié: juin 13, 2013, 3:24pm CEST par Ian Barker
A funny thing happened when I checked my email this morning. I found I had a friend request from Myspace, something I haven’t had for a long time. Even funnier was when I clicked on it Myspace -- or at least Myspace as I knew it -- was gone. In its place was a new sleek, Modern UI meets Spotify, music-based site. A site that doesn't seem to do friend requests anymore either so it's lucky I got that email or I might never have stumbled on it at all (conspiracy theories on a postcard please).
Of course this really shouldn't have come as a surprise, around nine months ago my colleague Wayne Williams reported early news of the update with the headline New Myspace is gorgeous, but who will use it? Like everyone else though I’d read about a Myspace update and not deemed it worthy of brain space. So suddenly finding myself on the new site -- fresh out of beta -- was a bit of a shock.
Not an unpleasant one as it happens. After a bit of reorientation (the site is much more minimalist than in the past and it isn't always obvious how things work) I thought it looked good. In fact visually it's a winner with chunky graphics, tablet-friendly sideways scrolling and a neat floating player at the bottom of the page. There's also a change in emphasis, rather than trying to recapture its pre-Facebook glory days as a one-size-fits-all social network it now focuses on creatives; musicians mainly but also artists and writers. Old Myspace was always good for finding music and the new one looks set to capitalize on that. There are new mobile apps too that allow you to build your own personalized radio station.
Tim Vanderhook, co-owner of the site along with his brother Chris and singer Justin Timberlake, says, "Today more than ever there's this need for a creative ecosystem that kind of caters to the creative community and that's both a social network and the streaming services attached".
There's no doubt that the new site is a visual treat but I'm not convinced that it does anything better than the competition that will tempt me to use it regularly. And with Google and Apple both moving into the streaming market that competition is about to become a whole lot tougher.
By targeting the site at artists the owners clearly hope that fans will follow. This could be a risky strategy but Myspace has the advantage of some 27 million existing users in the US and around twice that number worldwide. Many of those, like me, probably haven't used the site for a while but if they can be tempted back from their dormant state by the new interface they could give it a head start over the competition.
What we have then is a site that's undergone a radical redesign, gone off in a fresh direction with a new focus and, on the whole, seems to have done it well. This should be the big social network news story of the week, but sadly it comes at the same time that Facebook borrows the hashtag feature from Twitter, so poor old Myspace ends up as the bridesmaid once again.
-

Shifting software to the cloud could slash energy use
Publié: juin 12, 2013, 4:48pm CEST par Ian Barker
 If all US companies were to move their core systems from in-house servers to the cloud the amount of energy used could be reduced by up to 87 percent a new report claims.
If all US companies were to move their core systems from in-house servers to the cloud the amount of energy used could be reduced by up to 87 percent a new report claims.The research carried out by by Lawrence Berkeley National Laboratory finds that if all the email, CRM and productivity software in the US were running in the cloud it would save 326 petajoules of energy. Just in case you were wondering a petajoule is around 278 gigawatt hours or the amount of energy you get from burning 34,121 tonnes of coal.
The figures are based on an estimated (from census data) 86.7 million workers using computers. They assume that all of those use email, 58.9 million of them use productivity tools like word processing and spreadsheets, and that 8 million use CRM software.
Email is the most energy hungry because there are lots of servers -- some 3.6 million. Next come the 1.3 million productivity servers and 73,000 CRM servers.
The report estimates that if all this was shifted to the cloud there would only need to be 47,700 mail servers, 32,400 productivity servers and a mere 4,390 CRM servers. Little wonder then that a major move to the cloud would see the petajoules plummet.
All of this is worked out using the Cloud Energy and Emissions Research (CLEER) model which is available in open access form if you want to have a go yourself.
The report concludes, "Our hope is that, together, the CLEER Model and case study presented here can provide foundational resources from which other researchers and decision makers who seek to understand the net energy and emissions implications of cloud services can build more comprehensive and impactful analyses".
There's no doubt that the numbers look impressive but it's worth noting that the study is funded by Google which obviously has a bit of an interest in shifting things to the cloud. Maybe we should wait for a report commissioned by the energy industry before we decide to throw away our in-house servers.
Photo Credit: inxti /Shutterstock
-

Norton warns of summer festival smartphone risks
Publié: juin 12, 2013, 12:15pm CEST par Ian Barker

A new survey by Symantec reveals that people are more and more reliant on their smartphones at concerts, events and music festivals. But as usage of phones increases so do the security risks.
According to the research when people are out at live events phones are now more common than lighters (only 7 percent carry those anymore) and cameras (42 percent). This has led to the rise of some new phenomena such as "phone hogging" where audience members hold phones above their heads to take photos and video. Some 51 percent send texts or make calls to brag about the show and 38 percent take to social media to do the same.
Whilst 89 percent of people take their phones with them when going to concerts and festivals, 36 percent don’t have any form of security protection on the device. The most basic protection -- taping your contact details to the phone in case it's lost -- is followed by 10 percent. Perhaps surprisingly the under 30s are more likely to take precautions to protect their phone than older users and they're more likely to leave their expensive devices at home if there’s an increased risk of damage, loss ot theft.
Richard Clooke, Mobile Security Expert at Norton, says, "Your phone's security is probably the last thing on your mind at a festival, but there are some easy, preventative steps you can take even before you leave home. There's simple software solutions available now which allow you to track your phone via GPS if you drop it in the crowd, or if there’s no hope of finding it, you can wipe all the data remotely in case it falls into the wrong hands."
Norton Mobile Security Lite is available to download free for Android smartphone users. Amongst other features it lets you lock your phone via an SMS command and find it using a remote location feature. So when your friend phones you from Glastonbury to brag about how he's enjoying the show you can suggest that he installs it.
Photo Credit: Faraways/Shutterstock
-

McAfee Mobile Innovations helps you hang onto your devices
Publié: juin 11, 2013, 5:40pm CEST par Ian Barker
 The public beta of McAfee's newest mobile security app becomes available to download for Android devices today. Its leading feature is something called Smart Perimeter which addresses one of the key concerns of users, losing your device.
The public beta of McAfee's newest mobile security app becomes available to download for Android devices today. Its leading feature is something called Smart Perimeter which addresses one of the key concerns of users, losing your device.Smart Perimeter works by allowing devices to track each other and alert the user if they stray more than 30 feet apart. If a device goes outside the perimeter an alarm sounds and it's also locked so you have to enter a PIN to re-enable it.
According to McAfee's own research around half of smartphone owners say they would rather lose their wallet than their phone so this software should address their fears -- assuming of course that they have another device about their person to sound the alarm.
Other features in Mobile Innovations include a safe QR code reader that checks codes when they're scanned to ensure that the linked site is safe for browsing. There's also a Data Vault that PIN protects private photos and documents on the device.
Writing on the company's blog Lianne Caetano, director of consumer mobile product marketing at McAfee, says, "The McAfee Mobile Innovations app will help us to obtain users' input on device and web security, as well as strengthen anti-theft and privacy measures to protect personal data."
You can download Security Innovations for free from the Play Store right now or visit the McAfee blog for more information.
-

Mistakes cost millions says data breach report
Publié: juin 5, 2013, 1:00pm CEST par Ian Barker
 Symantec in conjunction with the Ponemon Institute has released a new study into the cost of data breaches. What it reveals is that whilst most of us worry about malware and hackers, it’s actually mistakes and system errors that cause the majority of breaches.
Symantec in conjunction with the Ponemon Institute has released a new study into the cost of data breaches. What it reveals is that whilst most of us worry about malware and hackers, it’s actually mistakes and system errors that cause the majority of breaches.According to the survey, glitches and negligence between them accounted for 64 percent of last year’s data breaches. This includes employees leaking or mishandling information, violation of regulations, accidental data dumps and stolen or lost laptops.
What’s worrying is that many employees don’t realise they're doing anything wrong. Around 62 percent of employees think it’s acceptable to transfer corporate data on to personal devices and a majority of those don’t delete it afterwards, leaving the data vulnerable to leaks.
Whilst the cost of a data breach varies around the world, it's estimated at $159 per record in the United States. That puts the total cost per breach last year at $5.4 million, though the good news is it marks a decline from 2010’s peak of $7.24 million.
If you're worried about how much this might cost your company Symantec has produced a handy Data Breach Calculator to help you work it out. Once you've scared your boss with that you can look at practical steps to reduce the risk including improved training, use of encryption and identifying the most vulnerable data.
You can read more and access the full report on Symantec’s Connect blog.
-

BT parts company with Yahoo
Publié: mai 31, 2013, 3:22pm CEST par Ian Barker
 After ten years with Yahoo as its mail and news provider, UK internet company BT is switching to a different service. Starting in June it will begin migrating its customers to a new service named BT Mail which will be run by California-based Critical Path.
After ten years with Yahoo as its mail and news provider, UK internet company BT is switching to a different service. Starting in June it will begin migrating its customers to a new service named BT Mail which will be run by California-based Critical Path.Nick Wong, director of online for BT's consumer division says, "We will be switching customers' email over to BT Mail, which will include the features and functions they expect from a modern email service. We will be keeping our customers fully informed about what changes to expect and when they will be able to enjoy the new services."
Email folders will be moved to the new service and customers will be able to keep their existing addresses. BT is also dropping Yahoo as the news provider on its portal site -- which is set as the default home page for its customers. The Press Association will be taking over that service.
The move involves around six million email accounts and Yahoo will lose a big slice of traffic to its home page. Although BT hasn't commented on the reason for the move, there have been numerous complaints since the start of this year that hackers have been taking control of BT mail accounts and using them to send out spam messages.
Customers can read more about how the changes will affect them on the BT Life blog.
-

Symantec phases out PC Tools security software
Publié: mai 28, 2013, 11:36am CEST par Ian Barker
 Symantec has dropped the PC Tools range of security software, leaving the Australian company that it acquired in 2008 to concentrate on its system tuning products.
Symantec has dropped the PC Tools range of security software, leaving the Australian company that it acquired in 2008 to concentrate on its system tuning products.Buying PC Tools gave Symantec a budget brand with the Internet Security, Spyware Doctor and Spyware Doctor with Antivirus products slotting in below the more upmarket Norton range. Now as part of Symantec CEO Stephen Bennett’s restructuring of the company, the PC Tools security products are being quietly streamlined out of existence.
Existing PC Tools security users will still receive updated virus definitions until their subscription expires. They’ll then be encouraged to move to an equivalent Norton product. According to the FAQ for PC Tools users that’s been posted on the company’s website they'll be able to, "...take advantage of our special offer to switch to Norton."
PC Tools Registry Mechanic, Performance Toolkit, File Recover and Privacy Guardian products are unaffected by the change, though it seems rather odd to leave the privacy product if the security focus is switching to the Norton range.
Photo Credit: Pavel Ignatov/Shutterstock
-

Facebook phone not coming to Europe
Publié: mai 24, 2013, 4:34pm CEST par Ian Barker
 European operators have been asked not to go ahead with the launch of the HTC First planned for this summer. The phone comes with Facebook Home which replaces the standard Android screens with its own social media interface.
European operators have been asked not to go ahead with the launch of the HTC First planned for this summer. The phone comes with Facebook Home which replaces the standard Android screens with its own social media interface.Home has been available for download to other Android devices too but hasn't proved popular with users. UK mobile operator EE has issued a statement making it clear that Facebook is behind the decision not to launch saying, "Following customer feedback, Facebook has decided to focus on adding new customisation features to Facebook Home over the coming months. While they are working to make a better Facebook Home experience, they have recommended holding off launching the HTC First in the UK." Orange in France has made a similar statement.
Facebook confirmed the news saying, "While we focus on making Home better, we are going to limit supporting new devices and think it makes a lot of sense for EE and Orange to hold off deploying the HTC First in Europe."
Pre-orders for the phone will be cancelled whilst Facebook returns to the drawing board. EE has said it will contact customers who have shown an interest in the device. The decision is bad news for the social network which has seen its usage rates dropping in the UK and which needs to boost its mobile presence to gain advertising revenue.
-

The radio that knows where you live
Publié: mai 24, 2013, 12:02pm CEST par Ian Barker
 We’re used to the somewhat spooky way that websites track our every move. Notice how the adverts on various sites reflect the products you’ve been viewing elsewhere? You only have to look at a CD on Play and Amazon will be trying to sell it to you within hours. We’re used to the GPS tracker on our smartphones monitoring where we are all the time and pointing us towards local attractions too.
We’re used to the somewhat spooky way that websites track our every move. Notice how the adverts on various sites reflect the products you’ve been viewing elsewhere? You only have to look at a CD on Play and Amazon will be trying to sell it to you within hours. We’re used to the GPS tracker on our smartphones monitoring where we are all the time and pointing us towards local attractions too.Well now this technology is starting to spread to other devices too. The BBC has used the Thinking Digital conference to trial a perceptive radio. Developed by the BBC's Future Media North Laboratory, the radio uses information about where you live to change the listening experience by referencing local places or weather conditions. It also monitors the background noise at your location so it can decide whether to boost certain sounds to enhance the listening experience. The idea is to provide an "immersive" broadcast that can reconfigure the content for each listener.
It's either a great idea or a creepy one depending on your viewpoint. And if it only broadcasts the things it thinks you want to hear how will you ever discover anything new?
Another worrying aspect is, once your radio thinks it has your best interests at heart, how long will it be before your other domestic appliances start getting in on the act? Will your fridge reject anything that isn’t compatible with your diet, or insist on only local produce? Maybe your alarm clock will refuse to process the snooze button on work days. Or your TV will insist on you watching a set number of mind improving documentaries before it lets you tune into a soap.
When your radio knows where you live it's only a short step to other gadgets knowing where you are and what you're doing all the time and trying to "improve" your life accordingly. What was all that stuff about Big Brother...?
Photo Credit: Everett Collection/Shutterstock
-

BullGuard launches Premium Protection 2013 -- guards the person as well as the PC
Publié: mai 22, 2013, 5:00pm CEST par Ian Barker
Any old security suite can protect your PC with a firewall and an antivirus product so the big players are increasingly looking for new angles to try to get us to buy their products. BullGuard’s flagship offering already has parental controls, spam filtering and PC tuning tools, so the latest release -- out today -- goes for the personal protection approach.
No, it doesn’t come with a goon in a dark suit and sunglasses to follow you around. It offers safeguards against identity theft and data leaks, plus it has social media protection. As an added bonus the amount of online backup space included with the package is increased to 25GB.
The ID protection module provides an extra layer of defense, running in the background to alert you via email or text if personal information has been compromised. Social media protection allows parents to monitor their children's Facebook profiles. It also has an app for the kids themselves to help them avoid risky behavior.
It scans the protected profile and alerts both parents and offspring to signs of bullying, "sexting", links to inappropriate content and more. The service works across tablets and smartphones as well as PCs.
BullGuard's Head of Product Management, Alex Balan says,
The changing face of threats and the changing habits of users in the modern computing age means that consumers face an uphill battle when trying to stay one step ahead of malicious third parties. Our intention when developing Premium Protection was to address these concerns and recognize that it's just as important to protect the person, as it is the PC. We've placed a strong focus on identity and social media protection, incorporating tools that can help guard against new threats alongside all of the 'traditional' protection required to help keep you (and your children) safe online.
The software comes as a 3-PC license for $99.95 (£69.95 in the UK) and you can download a 30-day trial from the BullGuard website. Existing BullGuard Internet Security users will be able to upgrade to the new suite.
-

Unhappy Tumblrs look for safety nets
Publié: mai 22, 2013, 1:47pm CEST par Ian Barker
Despite Yahoo CEO Marissa Mayer's promise not to "screw up" Tumblr following its recent acquisition, the move has caused some disquiet in the user community.
 Posting on Tumblr, of course, many users are worried about the impact advertising may have on the Tumblsphere, others that Yahoo will change the ethos of the site. There was disquiet about rumors Yahoo would push to make it more family friendly by filtering content too -- around 1 in 6 Tumblr pages is reckoned to contain porn. Despite assurances, and the fact that the circulating message about the clean up has been exposed as fake, there's a lot of distrust out there.
Posting on Tumblr, of course, many users are worried about the impact advertising may have on the Tumblsphere, others that Yahoo will change the ethos of the site. There was disquiet about rumors Yahoo would push to make it more family friendly by filtering content too -- around 1 in 6 Tumblr pages is reckoned to contain porn. Despite assurances, and the fact that the circulating message about the clean up has been exposed as fake, there's a lot of distrust out there.Already websites like www.bluegrownup.com are springing up with the aim of offering disgruntled Tumblrs a new home. There’s also a tool to help users migrate their blogs to WordPress.
Personally I like Tumblr, though I don’t exactly fit its cool kid demographic. I've used it since 2010 and it's the only blogging platform I've stuck with over a long period of time, mainly thanks to its ease of use and its ability to integrate content with other sites. If Yahoo can manage Tumblr in a sensitive way and preserve what’s good about it I'll be happy to stay. It seems to have managed this trick with Flickr so there is hope.
It's worth considering what this means from the Yahoo side of things too. If you can locate a Yahoo user you won't find them worrying about upcoming changes -- Yahoo doesn't inspire that kind of user loyalty. But Tumblr isn't the only thing the company has bought recently and there's a definite pattern to the acquisitions. Earlier this month it purchased Astrid -- a smartphone daily organizer app -- for an undisclosed amount. In March it bought news aggregation app Summly from British teen entrepreneur Nick D’Aloisio for $30 million. What these and Tumblr have in common is an emphasis on personalizing the web experience. They’re also all targeted heavily towards mobile devices.
We can expect to see the impact of this shopping spree on the delivery of Yahoo's news and other services. You can already detect change in the air with the new tablet-friendly Flickr layout, though as with any redesign there are some users who don’t like the new look. Whether all this will be enough to make people really care about Yahoo again only time will tell. In the meantime Tumblr users should probably sit tight for a while and see what happens.
Photo Credit: fotoscool/Shutterstock
-

Yahoo buys Tumblr for $1.1 billion
Publié: mai 20, 2013, 2:52pm CEST par Ian Barker
 As has been widely rumored over the last few days, Yahoo has paid $1.1 billion for blogging platform Tumblr. In recent times this is the most paid for an Internet acquisition since Facebook bought Instagram for $1 billion last year.
As has been widely rumored over the last few days, Yahoo has paid $1.1 billion for blogging platform Tumblr. In recent times this is the most paid for an Internet acquisition since Facebook bought Instagram for $1 billion last year.Founded by David Karp in 2007 from a bedroom of his mother's New York apartment, the attraction of Tumblr has always been its clean interface and ease of use, which allows people to be up and blogging within minutes. The service has around 217 million users worldwide and is the 24th most popular site in the US according to research company Quantcast. The company employs 175 people and claims to have more than 100 million blogs.
Tumblr has been slow to attract advertisers though, earning $13 million in 2012 when it had hoped to have revenue of $100 million by 2013. Yahoo brings the opportunity to attract more advertising but this may be at the expense of the site's sleek look. In the past Karp has been critical of the way other sites implement ads. Like Facebook and Google+, Tumblr already allows brands to set up their own pages. At the moment Tumblr embeds sponsored posts into the main stream in a way that’s subtle but also effective -- particularly on the smaller screens of mobile devices.
A more overtly commercial approach isn't likely to go down well with the free thinking creative types that Tumblr attracts. Initial reaction to the news on the web points to a lot of unhappy Tumblr users.
Yahoo, headed by ex-Google executive Marissa Mayer, will be seeking to use Tumblr to sprinkle some corporate stardust on its aging brand by adding social media and a mobile-friendly platform. It will also be looking to the acquisition to attract younger users to other Yahoo products and get the company back in touch with the cool kids. However, this deal may invoke a sense of deja vu in anyone who remembers Yahoo's purchase of Geocities in 1999. At the time Geocities was the third most visited site on the web but under Yahoo's ownership it withered and died, shutting up shop a decade later.
Mayer says on the new Yahoo blog (on Tumblr of course) that Tumblr will continue to operate as a separate company with Karp as CEO and she promises, "not to screw it up".
Addressing the Tumblr community David Karp says, "Our team isn’t changing. Our roadmap isn't changing. And our mission -- to empower creators to make their best work and get it in front of the audience they deserve -- certainly isn't changing. But we’re elated to have the support of Yahoo! and their team who share our dream to make the Internet the ultimate creative canvas. Tumblr gets better faster with more resources to draw from."
-

Dell reports 79 percent drop in profits as PC sales fall
Publié: mai 17, 2013, 12:30pm CEST par Ian Barker
 Computer giant Dell has seen its net profits fall by 79 percent to $130 million in the first quarter of this fiscal year. This highlights the shift in consumer demand away from traditional PCs towards tablets. The company reports a decline of 9 percent in PC sales although revenue from software, services and new technologies was up by 12 percent.
Computer giant Dell has seen its net profits fall by 79 percent to $130 million in the first quarter of this fiscal year. This highlights the shift in consumer demand away from traditional PCs towards tablets. The company reports a decline of 9 percent in PC sales although revenue from software, services and new technologies was up by 12 percent.Commenting on the results chief financial officer Brian Gladden says, "We made progress in building our enterprise solutions capabilities in the first quarter and are confident in our strategy to be the leading provider of end-to-end scalable solutions. In addition, we have taken actions to improve our competitive position in key areas of the business, especially in end-user computing, and it has affected profitability".
Uncertainty surrounds the company thanks to a dispute between founder Michael Dell and two of the biggest shareholders. Michael Dell along with private equity group Silver Lake has offered to buy the company for $24.4 billion and take it private. At the same time promising to shift the business away from PCs towards mobile devices.
However, the biggest shareholders argue that this valuation is too low. They have made a counter proposal to offer new shares to existing shareholders and install new management to run the business.
The company, which Mr Dell started from his college dorm room, was held up as a model of innovation as recently as ten years ago but has since lost ground to cheaper far eastern manufacturers and to makers of mobile hardware. The drop in PC sales should strengthen the case to move the company away from its traditional PC focus.
Photo Credit: Mopic/Shutterstock
-

UK apprenticeship scheme seeks to attract the young to cyber security
Publié: mai 16, 2013, 1:15pm CEST par Ian Barker
 Along with a number of major employers, e-skills UK -- an organization dedicated to inspiring future talent in IT -- is developing a new apprenticeship scheme to build cyber security skills.
Along with a number of major employers, e-skills UK -- an organization dedicated to inspiring future talent in IT -- is developing a new apprenticeship scheme to build cyber security skills.The scheme highlights the need to attract a new generation of talent into an industry where at the moment only 7 percent of security professionals are aged under 29. It will give youngsters an opportunity to start a career and earn a wage whilst working towards an internationally recognized qualification.
A number of major companies including IBM, BT and defense supplier QinetiQ are backing the scheme, with the first apprentices due to start later this year. Karen Price, the CEO of e-skills UK, says, "I am delighted that e-skills UK is working with a consortium of key employers to create the routes for young people to enter the exciting world of Cyber Security. These new apprenticeships will help tackle the skills shortage faced by this sector, including attracting more women, who are currently under-represented".
Bob Nowill, Director of Cyber and Assurance at BT, adds, "There are currently few structured routes for young people to enter the cyber security work sector and we are pleased to be contributing to this opportunity to proactively grow new talent which is directly aligned to the needs of industry".
The scheme will be supported by taxpayer funding via the UK Commission for Employment and Skills. It’s coordinated by the National Skills Academy for IT in order to ensure that it meets the required high standards.
Will this be enough to tempt teenage hackers to go legit and become the next generation of security professionals? Only time will tell.
Photo Credit: Lasse Kristensen/Shutterstock
-

Google+ gets major revamp, 41 new features
Publié: mai 15, 2013, 8:21pm CEST par Ian Barker
The Google I/O keynote has revealed some major changes to Google+. Highlights include a new multi-column stream aimed not only at providing a cleaner design but also at offering greater depth to the user experience.
The columns are customizable so that you can organize them to show the things that are most important to you. Tiles of information can be flipped to show alternative details and thanks to clever landmark recognition technology you can click on a picture to find more information about the location.
Hangouts are heavily revised too with the focus on making conversations simpler and not just concentrating on video. Hangouts becomes a standalone app on mobile devices and allows you to create ongoing conversations that stretch back over months or even years. You can see at a glance who is taking part in the chat stream and what point they've read up to. The new Hangouts will also allow group video chat at no charge -- take that, Skype!
On the photo side Google+ now offers 15GB of free cloud storage for your images. It can pick the best pictures from a folder for you by weeding out duplicates, blurred pictures or poor exposures. It also analyzes shots looking for smiling people and family images in addition to using the landmark recognition mentioned above to pull out the best shots.
There's an Auto Enhance feature too that corrects a range of common photo problems. Google also introduced what it calls Auto Awesome in order to create good shots by combining other pictures. This allows you to, for example, ensure you get group shots where everyone is smiling.
These changes make Google+ much more attractive in both looks and in function but will they be enough to boost its popularity? Let us know what you think.
-

Mobile malware threat continues to grow
Publié: mai 15, 2013, 5:36pm CEST par Ian Barker
 F-Secure has released its latest mobile threat report for January to March 2013. Highlights include an increase in threat families and variants of almost 50 percent over the previous quarter, and that Android is still the most targeted mobile OS.
F-Secure has released its latest mobile threat report for January to March 2013. Highlights include an increase in threat families and variants of almost 50 percent over the previous quarter, and that Android is still the most targeted mobile OS.Android threats accounted for 136 of the 149 detected during the period, the other 13 being aimed at Symbian. No threats were reported for iOS, Blackberry or Windows Mobile. The report notes a particularly worrying trend towards the commoditization of malware, either by making premium rate calls or stealing bank details. 114 out of 149 threats found were profit motivated. The authors state:
The Android malware ecosystem is beginning to resemble that which surrounds Windows, where highly specialized suppliers provide commoditized malware services. Two key examples of this trend surfaced in the first quarter of 2013 in the form of "Stels" and "Perkele" malware. Besides commoditization, targeted attacks and spam operations involving Android malware are also making strides in the mobile threat scene.
There has been an increase in targeted attacks against particular groups such as human rights activists. Our old friend the 419 scam in the form of fake job offers remains popular too. The report breaks down threats by type with Trojans being by far the most common at just over 61 percent of all those detected.
As the report notes these trends very much echo those seen on the Windows platform.
In a way, Android is experiencing the same fate as Windows where its huge market share works in both good and bad ways. Such popularity certainly translates well in terms of sales, but it also appeals to the maliciously-minded crowds. Malware authors see plenty of opportunities yet to be explored on the relatively new and growing platform.
Whilst the actual number of threats is still quite small compared to those seen for Windows, the findings do show that mobile devices are firmly in the sights of malware developers.
Photo Credit: style-photography.de/
-

Which browser is safest? The answer may surprise you
Publié: mai 15, 2013, 4:57pm CEST par Ian Barker
 Web browsers are one of the main ways that malware finds its way onto your machine. Tests carried out by NSS Labs looked at the five major players, Chrome, Firefox, Safari, Opera and Internet Explorer to see which offers the best protection against more than 700 examples of real-world malware.
Web browsers are one of the main ways that malware finds its way onto your machine. Tests carried out by NSS Labs looked at the five major players, Chrome, Firefox, Safari, Opera and Internet Explorer to see which offers the best protection against more than 700 examples of real-world malware.And the safest is... (Drum roll and a long, reality TV-style pause...) Internet Explorer 10, blocking 99.96 percent of known malicious downloads. Chrome comes second on 83.16 percent with the other three trailing a long way behind at around 10 percent each. This might come as a surprise to all those people who have long shunned Microsoft’s browser in favor of third-party alternatives on the grounds that they were safer.
So what's the reason for the difference? Safari, Firefox and Opera all rely solely on URL blacklists to block potential attacks. Chrome and Internet Explorer both have additional "context agnostic malware protection" (CAMP). In IE’s case this is called "Application Protection" whereas Chrome names it "Download Protection". Using CAMP technology means there’s more chance of false positives and so it relies on asking the user to make a choice to block or allow the download which potentially introduces a weak link in the chain.
If you filter the CAMP element out of the results then Chrome performs no better than Safari and Firefox. However, IE 10 still turns in an impressive 83.17 percent block rate based on URL reputation.
Now of course we technically aware types are careful about the links we click anyway. But it seems that if you’re worried about protecting your more vulnerable friends and relatives when they’re online you should encourage them to use IE 10.
Photo credit: dohtoor/Shutterstock
-

McAfee launches cross-platform protection
Publié: mai 15, 2013, 11:05am CEST par Ian Barker
 Security products that work across all of your digital devices from PCs to smartphones are nothing new -- Norton One has been around for over a year -- but now McAfee has joined the fray. LiveSafe includes virus protection, a password manager and encrypted cloud storage in a single package.
Security products that work across all of your digital devices from PCs to smartphones are nothing new -- Norton One has been around for over a year -- but now McAfee has joined the fray. LiveSafe includes virus protection, a password manager and encrypted cloud storage in a single package.The most interesting feature is the secure online Personal Locker that gives users 1GB of storage to hold their sensitive documents, financial records, IDs and so on. This is secured using biometric authentication with voice, face and device recognition. It works using Intel Identity Protection Technology. This is a hardware authentication mechanism that’s built into the latest Intel processors. To access a file you need to enter a PIN, take a photo for facial recognition and read two messages to confirm your voice.
LiveSafe is compatible with Windows, iOS and Android and there's no limit to how many devices you can use it on. It has a password manager that's accessible across all devices so you'll always be able to get at your online accounts on the move. There’s also a browser-accessible dashboard to allow you to control LiveSafe's features from anywhere.
LiveSafe is currently available at an introductory price of $19.99 for a one year subscription and will cost $79.99 a year after that. It will come pre-installed on Dell Ultrabooks and PCs starting in June.
McAfee is a little late to the game here but the move away from providing trial versions on new PCs is clever and one other security companies will be watching closely. The Personal Locker should prove attractive to people who need access to private documents on the move too.
Photo credit: Andrea Danti/Shutterstock
-

Live fast, stay protected
Publié: mai 9, 2013, 5:26pm CEST par Ian Barker
Independent testing organization AV-Comparatives has released its latest performance tests evaluating the impact of security software on system performance. It carried out the tests on a 64-bit Windows 7 system and measured a number of everyday activities including copying files, installing and uninstalling applications and launching programs as well as running the PCMark 7 benchmarking suite.
The results of these tests have been used to produce a system impact score measuring how much difference the various antivirus programs make compared to having no security installed at all. This makes for some interesting reading.
At the top of the tree tied with impact scores of 0.4 (lower is better here by the way) come F-Secure, Sophos and Kaspersky. Second with a score of 0.6 comes ESET. Of what you might call the household names Symantec does best with a score of 1.3 whilst McAfee turns in a disappointing 14.4.
Microsoft’s own Security Essentials scores a reasonable 5.6, behind BitDefender’s 2.4 but ahead of AVG’s 7.1 and BullGuard’s 8.7. Bottom of those tested comes Kingsoft with an impact score of 25.6. You can read the full results and the test methodology by visiting the AV-Comparatives site.
Of course all of this only tells you how the software impacts on your PC, not how well it protects you. As always with security there’s a trade off involved but if performance matters then the report will at least help you make an informed decision. You can find data on comparative protection levels elsewhere on AV-Comparatives to help you make up your mind.
-

Spotify 'nightmare' is more of a sleepless night
Publié: mai 9, 2013, 4:26pm CEST par Ian Barker

Spotify is the world’s most popular streaming music service with some 24 million active uses, around 6 million of those paying a subscription for premium services. I use Spotify all the time; it’s a great way of finding and sampling new music, and the company’s deals with major labels go a long way to legitimizing the streaming model.
Yesterday though, Spotify acted to change its website player after a Dutch developer released a Chrome extension that allowed MP3s to be downloaded from the site. Google removed the Downloadify plug-in from its site before Spotify applied the fix to the player, which now uses an encrypted format.
Robin Aldenhoven, the man behind Downloadify opines on his Twitter stream, "I could not believe it myself that they did so little to protect their library". But he also supports Spotify’s obligation to copyright holders saying, "Google responded correctly to remove, but Spotify should not send DRM-free MP3s to users".
Of course, we all know that streaming services have long been vulnerable to this type of thing. There are plenty of freely available tools to allow the ripping of music from YouTube, for example, even though it’s a clear breach of the site’s terms of service.
Although this latest issue might seem like a major problem for Spotify, I don’t think it’s really the "nightmare" that some bloggers call it.
The vulnerability didn’t affect the service’s desktop or mobile clients, just the web player, which only launched last November. Plus you need to sign up for an account to be able to access Spotify so you are traceable and frankly there are easier ways to find free MP3s if you really want to.
The real risk is that if this sort of thing happens too often the major record labels will lose faith in the Spotify business model -- and indeed that of other streaming services -- and may decide not to renew their license agreements. At the moment, it seems that the company’s fast action to plug this hole is enough to retain confidence. I hope it is, my nightmare would be if Spotify disappeared altogether.
Photo Credit: Joe Wilcox
-

Smartphones hold the key to appiness
Publié: mai 8, 2013, 3:54pm CEST par Ian Barker

How are you feeling? If you don't have time to lie on the couch and work through your issues you can now turn to your Android phone to measure your emotional state. Cambridge University researchers have developed an app that combines smartphone data with user perceptions in order to track happiness.
The EmotionSense app collects sensor information from the phone about where you are, how noisy the environment is, and who you’re communicating with. It then combines this data with your answers to questions about how you’re feeling in order to work out your emotional state.
There are other mood tracking apps of course, but the Cambridge team believe this is the first time that user input has been combined with phone information. The app was developed as part of a project to use mobile phones as a means of improving health and wellbeing. It takes about eight weeks to unlock all the sensors and build up a full picture of what influences your moods.
"Behind the scenes, smartphones are constantly collecting data that can turn them into a key medical and psychological tool", Neal Lathia, lead researcher on the project team, explains. "Any smartphone now comes with numerous sensors that can tell you about aspects of your life, like how active you are, or how sociable you have been in the past 24 hours. In the long term, we hope to be able to extract that data so that, for example, it can be used for therapeutic purposes".
The team aims to collect a record of what drives people’s emotions and be able to work out when they’re likely to be at their most stressed. In the future this could lead to phones being used by doctors to routinely monitor patients. Dr Lathia explains: "Most people who see a therapist only have an appointment once every fortnight. Many, however, keep their phones with them most of the time. In terms of sheer presence, mobiles can provide an ongoing link with a person".
The app is available now to download free from the Play Store but to use it you must consent to your data being passed to the researchers. The team is working on versions for other smartphone platforms.
Photo Credit: kaczor58/Shutterstock
-

Did you wink at me or are you taking a photo?
Publié: mai 3, 2013, 3:31pm CEST par Ian Barker
 As if the Google Gaze wasn’t enough to get you strange looks in the street, now there’s a new app for Google Glass users that lets you take a photo simply by winking.
As if the Google Gaze wasn’t enough to get you strange looks in the street, now there’s a new app for Google Glass users that lets you take a photo simply by winking.The Winky app was revealed yesterday by developer Mike DiGiovanni on his Google+ page he says:
You might not think it's hard to say "Ok, Glass Take a Picture" or even just tap a button. But it's a context switch that takes you out of the moment, even if just for a second. Winking lets you lifelog with little to no effort. I've taken more pictures today than I have the past 5 days thanks to this.
Currently Winky is only available as Android source code so it needs to be compiled before it can be used but since most Glass users are currently developers and other techy types that shouldn’t be a problem.
So, next time somebody winks at you it’s important to check if they’re wearing a Google headset in order to avoid embarrassment. Aside from the fact that technology seems to be turning us all into twitching loons, there would appear to be endless potential for misunderstandings here, "Honestly, officer I was only taking a photograph".
Photo Credit: Vadim Ivanov/Shutterstock
-

Dutch cyber cops could be licensed to hack
Publié: mai 3, 2013, 11:01am CEST par Ian Barker
 The Dutch government has revealed plans to give the police extra powers to fight cybercrime. Under the proposed new law officers would be given the right to hack into computers, read emails, install spyware and delete files. They could also be authorised to tap VoIP calls and break into servers located outside the country if they were being used to host DDoS attacks.
The Dutch government has revealed plans to give the police extra powers to fight cybercrime. Under the proposed new law officers would be given the right to hack into computers, read emails, install spyware and delete files. They could also be authorised to tap VoIP calls and break into servers located outside the country if they were being used to host DDoS attacks.The country’s Justice Minister Ivo Opstelten says that the powers would be used under strict control and that the approval of a judge would be needed before the police could carry out these actions.
Terrorism and child pornography are areas of special concern in the bill but it would also introduce penalties for the publication of stolen data. In addition the bill would make it a crime for a suspect to refuse to decipher encrypted files or hand over passwords during an investigation by police.
Digital rights group Bits of Freedom is opposed to the new law saying that it sets a bad precedent and that its preparation has been rushed.
The bill is set to undergo revisions before being put to parliament at the end of the year. If it’s passed then no doubt other governments will be looking at how they too can kick down the doors of suspects’ computers.
Photo Credit: Ivonne Wierink/Shutterstock
-

Mozilla takes on spyware maker
Publié: mai 2, 2013, 12:00pm CEST par Ian Barker
 The Mozilla Foundation is accusing Gamma International, a UK-based software group, of making a false association between one of its products and the Firefox name.
The Mozilla Foundation is accusing Gamma International, a UK-based software group, of making a false association between one of its products and the Firefox name.Gamma International produces FinFisher, a program used by governments to obtain data in a covert way. FinFisher is often installed by disguising itself as an update to a well known program such as Firefox. Mozilla has now sent a cease and desist letter to Gamma claiming that its Firefox trademark is being violated and that the practice must end immediately.
Alex Fowler in charge of privacy and public policy at Mozilla says on his blog,
As an open source project trusted by hundreds of millions of people around the world, defending Mozilla’s trademarks from this type of abuse is vital to our brand, our users and the continued success of our mission. Mozilla has a longstanding history of protecting users online and was named the Most Trusted Internet Company for Privacy in 2012 by the Ponemon Institute. We cannot abide a software company using our name to disguise online surveillance tools that can be -- and in several cases actually have been -- used by Gamma’s customers to violate citizens’ human rights and online privacy.
Mozilla has acted following a report from the University of Toronto's Citizen Lab on digital spying. The report compares a legitimate install of Firefox with what the report’s authors claim is a FinFisher install. This, they say, comes labeled with version numbers, copyright details and descriptions from a legitimate Firefox version.
Photo credit: olly/Shutterstock
-

Google changes search labels following EU investigation
Publié: avril 25, 2013, 5:16pm CEST par Ian Barker

Following an investigation by the European Commission into whether Google unfairly promoted its own services, the search giant has agreed to make some changes to the way results are displayed.
Google will more clearly label search results that link to YouTube, Google Maps and its other sites. The Commission has proposed that these changes run for a month whilst it collects public feedback. The EC will then decide whether to make them legally binding for five years, in which case an independent monitor would be appointed to oversee proper implementation.
The agreement requires Google to clearly separate promoted links from general search results. The company will also need to show links to three rival specialized search providers in a location that’s clearly visible to users.
In addition Google will need to offer websites the ability to opt out of specialized search results -- such as news and shopping -- whilst not affecting their ranking in a general search. This includes the ability to allow newspaper websites to control, on a page-by-page basis, the parts of their content that shows up in Google News searches.
Google will no longer be able to include in its agreements with publishers any obligation that they source online search adverts exclusively from Google. Nor will it be able to restrict advertisers from running a campaign across rival platforms.
Whilst these changes will only apply to Europe, regulators in other countries will no doubt closely monitor the effects and deciding whether to impose similar restrictions of their own.
-

Forget QWERTY it's time for KALQ
Publié: avril 24, 2013, 2:38pm CEST par Ian Barker

Typing on touchscreen devices is very different from using a conventional keyboard and the traditional layout doesn’t help much. Researchers at the University of St Andrews, the Max Planck Institute for Informatics and Montana Tech have come up with a new layout that claims to allow tablet users to thumb type 34 percent faster.
Named KALQ after the order that the characters appear, it's been developed to provide optimal character positions when typing on a tablet. By spreading the characters used in commonly typed words such as "on", "see", "you" and "read" which on a QWERTY keyboard would all need to be typed with one thumb, KALQ speeds up typing and minimizes strain.
Dr. Antti Oulasvirta, Senior Researcher at the Max Planck Institute for Informatics in Germany, says:
The key to optimizing a keyboard for two thumbs is to minimize long typing sequences that only involve a single thumb. It is also important to place frequently used letter keys centrally close to each other.
Experienced typists move their thumbs simultaneously: while one thumb is selecting a particular key, the other thumb is approaching its next target. From these insights we derived a predictive behavioral model we could use to optimize the keyboard.
KALQ also has built in error correction that takes into account thumb movements and a statistical analysis of the text being typed. This enables uses to reach a speed of 37 words per minute as opposed to 20 on a QWERTY layout.
The researchers will present their work at the CHI 2013 conference in Paris on 1st May and KALQ will be available as a free download for Android-based devices.
-

Why less is more in the Windows 8 Modern UI
Publié: avril 24, 2013, 11:56am CEST par Ian Barker

My Why I love Windows 8 piece last week generated a lot of comments and a good balance of pro and anti opinion. Thanks for taking the time to air your views. I received one particular comment concerning choice and that got me thinking that it was a subject which deserved a closer look.
In the past Windows has imposed relatively few restrictions on its users. You want to launch a program? You can click the desktop icon, select it from the start menu, select an icon from the task bar, use a gadget or track down the folder where it's stored and run it from there. You can even call up a command line if you want. It's your choice. As is installing a third-party menu system or an Apple-style widget bar, the permutations are endless.
The same goes for developers too. If you're building a program you can make it look how you want. You don't have to use the ribbon toolbar format, there’s no restriction on the size, shape or position of the buttons, the menu items don’t have to be in a particular order.
Contrast this with other systems. Visit the developer site for Apple, or even for Android, and you'll find there’s a whole raft of guidelines and recommendations all aimed at giving a consistent look and feel to programs and apps.
Which brings us back to Windows 8. With the launch of the much discussed Modern UI we have for the first time in Windows an interface that requires developers to conform to a strict template. It also requires users to launch and control all their apps in the same way.
Is this a good thing? Windows has always been about choice whereas other systems have imposed their developer's vision more forcefully on the user. But if you give people too much choice don’t they just get confused? Isn't it better to always have context menus and navigation controls in the same places? To have a one-stop location on the charms bar for settings and searches across all apps?
If all programs are launched from the same place and can be navigated in broadly the same way then you have a huge step towards making a more user-friendly system. Ask yourself this, if you'd never seen Windows before wouldn't the Modern UI approach seem much more logical than the old five ways to achieve the same end model?
The problem of course is that people have seen and used and adapted to older versions of Windows and are resistant to change. As a result there's been a lot of heated debate about the Modern UI way of doing things. This isn't helped by the fact that the desktop has changed little and is still lurking just a click away allowing people to slip back into a comfort zone.
Microsoft has made a bold move with Windows 8. It has provided an opportunity to re-evaluate how all Windows programs look and work. If that leads to improved usability at the expense of stricter development standards then in the long run it must be a good thing. It would be a shame if having come this far Microsoft were now to listen to the shrill voices and take a step back from the Modern UI approach.
Photo Credit: Thomas Pajot/Shutterstock
-

Apple loses out to premium Android tablets
Publié: avril 19, 2013, 11:20am CEST par Ian Barker
 UK polling company YouGov has released the results of its latest Quarterly Tablet Tracker for the first three months of 2013. It shows that consumers now see Android tablets as equal in quality to the iPad and as a result their makers are eating into Apple's share of the premium market.
UK polling company YouGov has released the results of its latest Quarterly Tablet Tracker for the first three months of 2013. It shows that consumers now see Android tablets as equal in quality to the iPad and as a result their makers are eating into Apple's share of the premium market.Although it still has the largest slice of the UK's tablet market, Apple has seen its share drop by 10 percent in the past 12 months. Despite the launch of the iPad Mini and 4th generation iPad, Apple now has 63 percent of the market compared to 73 percent this time last year.
The main reason for the drop seems to be the emergence of strong new competitors which have taken sales not just from Apple but from the obscure budget brands too. Google's Nexus 7 has grabbed 8 percent of the market in under a year, while the Kindle Fire has taken 5 percent. Since the beginning of 2012 Samsung has also more than doubled its share from 4 percent to 10 percent.
There is some good news for Apple with the iPad Mini taking 4 percent of the market and generating the highest customer satisfaction scores.
Looking at the overall picture, the Quarterly Tablet Tracker shows that 18 percent of the UK adult population (more than 8 million people) now own a tablet. This is an increase of 5 percent over the last quarter of 2012, no doubt fueled by the Christmas period.
Of course Apple still has a huge share of the tablet market largely thanks to its head start. But that dominant position is only likely to slip further as the big-name Android makers raise their game.
Photo Credit: Adam Radosavljevic /Shutterstock
-

Why I love Windows 8
Publié: avril 16, 2013, 12:26pm CEST par Ian Barker
 Fourth in a series. It seems to be fashionable at the moment to be negative about Windows 8. People like to whine about how the Modern UI gets in the way and how the rest of it is just Windows 7 with some of the furniture rearranged. Some analysts are even blaming Windows 8 for poor PC sales.
Fourth in a series. It seems to be fashionable at the moment to be negative about Windows 8. People like to whine about how the Modern UI gets in the way and how the rest of it is just Windows 7 with some of the furniture rearranged. Some analysts are even blaming Windows 8 for poor PC sales.Well, I’m sorry Windows 8 deniers, you’re wrong. I’ve used every major version of Windows since 3.1, I’ve been using Windows 8 since the Developer Preview versions and I think it’s Microsoft’s best effort yet.
If you move beyond the culture shock of its different look, there are just so many things that Windows 8 does well. The first is how quickly it manages to boot up your PC. When I initially loaded the Developer Preview on the humble Intel Atom-powered machine I use as a test box I was startled to find it booted in less than half the time taken by my Windows 7 laptop with Pentium power and 50 percent more RAM. Okay, so this is down to a little conjuring trick which saves the system state on shutdown and allows the system to reload without starting core components one by one, but it’s still impressive.
Another feature that makes me a fan of Windows 8 is its reliability. When your day job involves the constant round of installs and uninstalls that comes with reviewing software and hardware you become no stranger to the blue screen of death. Not in Windows 8, in almost a year of use I haven’t seen the BSOD once. This is due to Windows 8’s ability to allow individual programs to crash without taking down the whole OS.
Some people bemoan the lack of a desktop Start button, but the Charms bar combined with the powerful search function more than compensates. I’m now reaching the point where using an older version of Windows feels quite alien and I automatically go to the bottom right corner of the screen expecting something to happen.
Which brings us to the controversial Modern UI. Yes it’s designed for touch screens and it works best with one. But it’s still perfectly usable on an old-fashioned mouse and keyboard setup. The apps look good, they work well and if you want a conventional desktop it’s only a click away. Honestly, I don’t understand why people have a problem with it.
I could go on about improved multi-monitor support, easy syncing of settings between machines, the quality of the built-in security, the ability to reset the system and more. There are many reasons why I love Windows 8, so let me end with an appeal. Don’t take my word for it, set aside your prejudices, curb your Luddite tendencies and take a fresh look, this really is a good operating system.
-

Symantec highlights 58 percent increase in mobile attacks
Publié: avril 16, 2013, 9:04am CEST par Ian Barker
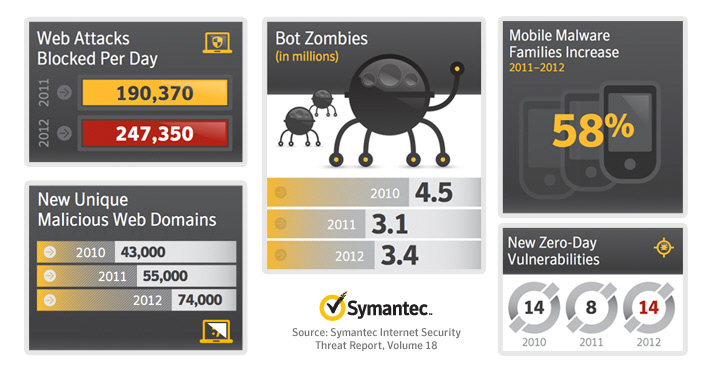
Security giant Symantec’s 18th annual Internet Security Threat Report is out today and reveals that cyber criminals are increasingly scouring the Web for personal details in order to target their attacks. Armed with your information they can exploit security gaps in social networks and other sites to infect your system or steal your details.

It’s not just your PC that’s at risk either; the report shows an alarming 58 percent increase in attacks on mobile devices with just under a third of these aimed at stealing data without the user’s knowledge. Android is the most targeted mobile platform as its open source nature makes it easier to hide malware in apps. The securer-than-thou smugness of Apple users receives a blow too as the report notes more than 600,000 Mac systems were infected by a single attack last April.
When it comes to types of threat, the growth of ransomware continues with infections becoming more aggressive and harder to undo. Another scary statistic is that 61 percent of malicious sites are actually legitimate websites that have been compromised so you may be at risk even if you think you’re practising safe surfing.
Symantec also highlights some common myths about security and you can read these as a handy infographic and access the full ISTR report here.
Norton’s security expert Richard Clooke said, "The report results have shown that it is still crucial for Norton to continue to educate consumers on how they can help protect themselves from acts of cybercrime. Ransomware, for example, a scam which disables victims’ computers until they pay a ransom, continues to be a key theme and is now becoming more sophisticated than ever..."
Of course all of this is aimed at boosting sales of Symantec’s security products, but it does underline that the threat landscape is an ever changing one and that we all need to be careful out there.
Photo Credits: Slavoljub Pantelic/Shutterstock
-

Bing searches throw up more malware sites than Google
Publié: avril 12, 2013, 12:32pm CEST par Ian Barker
 We all know that search engine results can sometimes serve up malware, but if you’re using Bing you’re five times more likely to get malicious links than if you’re using Google.
We all know that search engine results can sometimes serve up malware, but if you’re using Bing you’re five times more likely to get malicious links than if you’re using Google.In an 18-month study, independent German lab AV-Test discovered that all search engines sometimes serve up Trojans and other malware amongst their results despite the search providers' best efforts to prevent it.
AV-Test found 5,000 malware links across 40 million websites, so toxic search results are perhaps rarer than you’d think. However, it seems that developers are putting their efforts into SEO techniques so that their results appear higher up the rankings where users are most vulnerable to clicking without thinking.
Google and Bing proved to be the safest search engines in the study, but of the two it’s Bing that’s more likely to give you a nasty surprise when clicking on a link, delivering 1,285 malicious results to Google’s 272. If it’s any consolation you can feel sorry for the Russians as their search giant Yandex delivered more than ten times as many infected sites as Google.
Most of the infected sites exploit existing vulnerabilities so you can keep yourself safe by ensuring that your browser and security software are always up to date.
Photo Credits: maraga/Shutterstock