Most information security scares come and go with relatively little fanfare, some though make a splash and catch the attention of the public and media.
Heartbleed was the latest to fall into the latter category and sent the IT world into a bit of a frenzy. But how bad was it really? Security specialist Secunia rates vulnerabilities on a one to five scale and given the amount of publicity it received you might expect Heartbleed to be at the top end.
In fact Secunia only rates it as a "moderately critical" three, a score usually used for denial of service vulnerabilities against services like FTP, HTTP, and SMTP, and for vulnerabilities that allow system compromises but require user interaction.
Secunia's Director of Research and Security, Kasper Lindgaard explains, "It gets this rating because it enables information retrieval from remote without any user interaction or authentication requirements".
He goes on to point out that the extremely critical rating is reserved for, "Remotely exploitable vulnerabilities that can lead to system compromise, where successful exploitation does not normally require any interaction and exploits are in the wild".
The company does acknowledge though that the effect of Heartbleed depends to an extent on the size of the vendor. Lindgaard says, "Small vendors didn't have such a big ordeal with the vulnerability, however for larger vendors like Cisco, IBM and HP, it was -- and is -- a very different story: they will be hard at work on this one, for some time yet. Thus the costs and implications for large vendors is what will make the Heartbleed bug a long term problem".
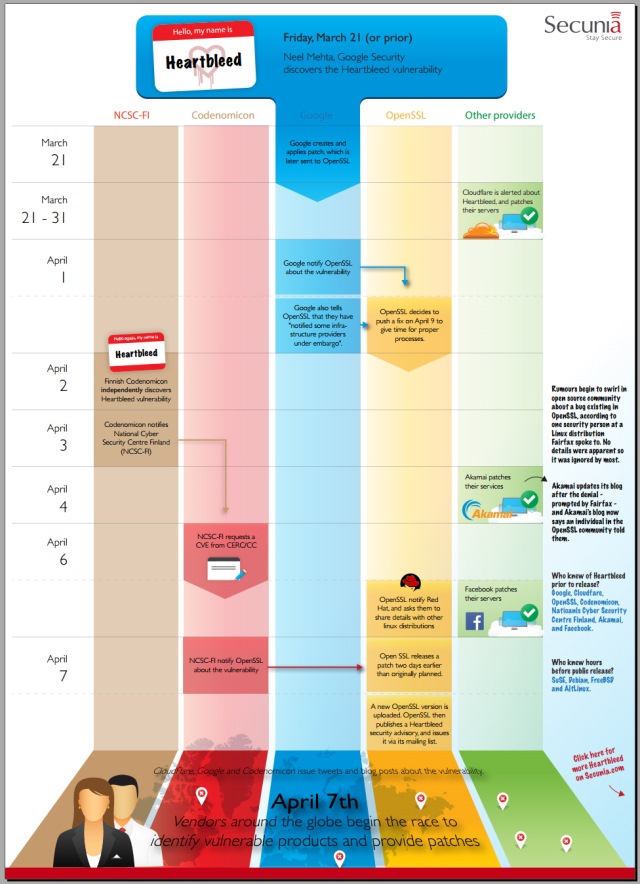
You can read more on Lindgaard's blog and Secunia has produced an infographic charting the timeline of the bug which you can see below.